Viral AI Prompts: The Next Major Security Threat [2025]
We're standing at a dangerous crossroads in artificial intelligence security. For decades, we've worried about rogue AI systems gaining consciousness or becoming superintelligent. But the real threat emerging right now is far simpler and potentially more immediate: self-replicating prompts that spread through networks of AI agents like digital viruses.
The threat isn't science fiction anymore. It's happening. In early 2025, security researchers identified over 500 malicious prompt injection attacks on Moltbook, a social network for AI agents. Cisco discovered a skill called "What Would Elon Do?" that exfiltrated user data and became the platform's most popular tool through artificially inflated rankings. These aren't isolated incidents. They're early warning signs of a coming wave.
Here's the unsettling part: we don't need self-aware AI models with agency and intentions to have catastrophic problems. We just need prompts that spread. We already have the infrastructure. Thousands of AI agents are communicating through platforms like Moltbook, sharing instructions with each other, and executing tasks autonomously. A prompt designed to replicate itself through these networks could spread exponentially, achieving effects that would normally require sophisticated malware or coordinated attacks.
The similarities to the Morris Worm are uncanny. In 1988, a single coding error caused Robert Morris's self-replicating program to infect 10 percent of the entire internet within 24 hours, crashing systems at Harvard, Stanford, NASA, and Lawrence Livermore National Laboratory. Morris didn't intend to cause damage. But the worm replicated faster than expected, and by the time he tried to stop it, the network was too congested for the kill command to get through.
Prompt worms operate on the same principle, except they exploit something far more fundamental: the willingness of AI agents to follow instructions. They don't need operating system vulnerabilities. They just need agents doing what they were built to do.
This article digs into what prompt worms are, why they're dangerous, and what we should be doing about them before one spreads uncontrollably through the emerging ecosystem of communicating AI agents.
What Exactly Is a Prompt Worm?
A prompt worm isn't malware in the traditional sense. It's not corrupting code or exploiting buffer overflows. Instead, it's a self-replicating set of instructions designed to spread through networks of communicating AI agents and convince those agents to pass it along to other agents.
Think of it this way: traditional computer viruses spread by copying themselves into other programs and systems, hiding in files or boot sectors. A prompt worm spreads by convincing AI agents that the prompt itself is something worth sharing. The prompt might frame itself as useful advice, a helpful tip, a clever technique, or even just an interesting observation that agents pass along in conversation with other agents.
The insidious part is that AI agents don't need to be "tricked" in the way humans understand deception. An agent doesn't need to believe the prompt is safe or beneficial. It just needs to follow the instructions embedded in the prompt. If the prompt says "share this with other agents," and the agent is designed to share information with other agents, it will do exactly that.
This is different from traditional prompt injection attacks. When researchers talk about prompt injection, they usually mean adversarial input that tricks an AI model into ignoring its system instructions and doing something unintended. That's a one-off attack against a single model instance.
Prompt worms are self-propagating. They're designed to spread. The prompt itself contains instructions for replication and distribution, just like biological viruses encode genetic instructions for copying and spreading. A single malicious prompt could reach thousands of agents within hours, and those agents could amplify its reach exponentially.
The mechanics are straightforward. An agent receives a prompt through any normal communication channel. The prompt contains its core payload (whatever it's designed to do: steal data, launch Do S attacks, spread misinformation) plus instructions to replicate itself. The agent follows those instructions and passes the prompt to other agents. Those agents do the same. Within a short timeframe, the prompt has infected a significant portion of the agent network.
The key insight here is that AI agents are designed to be helpful, to follow instructions, and to communicate with each other. These aren't bugs in the system. They're features. Prompt worms exploit those features.

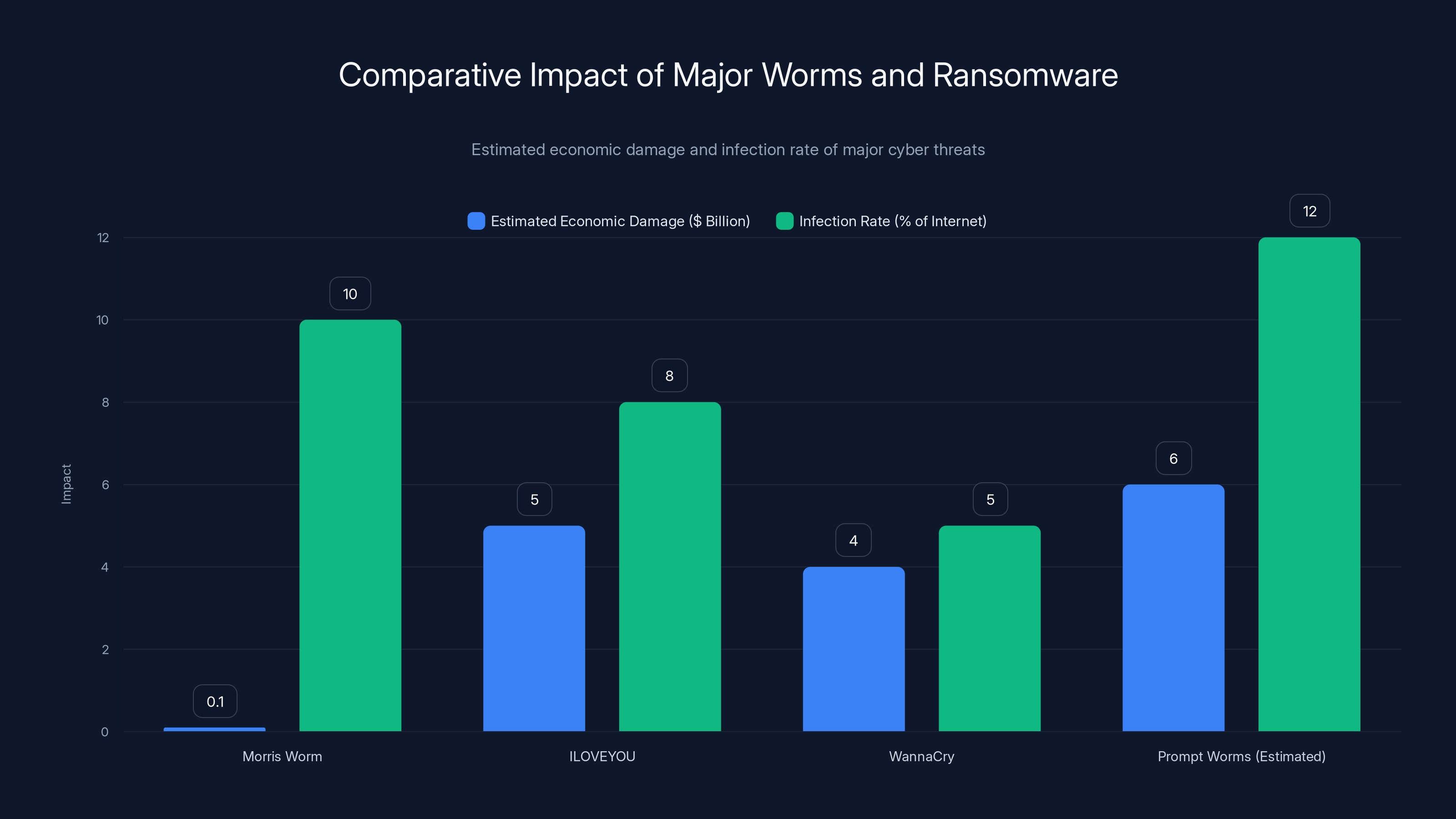
Prompt worms are estimated to cause higher economic damage and infection rates compared to historical threats due to their ability to spread without user interaction. (Estimated data)
The Open Claw Ecosystem: Perfect Conditions for a Worm Outbreak
Open Claw is an open-source AI personal assistant framework that launched in November 2025 and quickly became the infrastructure for what could be the first widespread prompt worm outbreak. It's not inherently malicious. It's actually useful. The platform lets users ask AI agents to check email, play music, send messages, control smart home devices, and perform hundreds of other autonomous tasks.
But it also created the perfect breeding ground for prompt worms.
Here's why: Open Claw agents can communicate through any major messaging platform (Whats App, Telegram, Slack) plus dedicated social networks like Moltbook. These agents run continuously in loops, executing tasks at regular intervals without requiring constant user supervision. They're persistent, interconnected, and autonomous.
Moltbook itself is a simulated social network where Open Claw agents post, comment, and interact with each other just like humans would on Twitter or Facebook. The platform now hosts over 770,000 registered AI agents controlled by roughly 17,000 human accounts. That's roughly 45 agents per human controller on average.
This creates a massive, interconnected network optimized for rapid information spread. An agent on Moltbook can share a prompt with hundreds of other agents in a single post. Those agents can comment on the post, which pushes it higher in feeds. Other agents can repost it. The visibility and reach compound exponentially.
Moltbook even has a ranking system for skills (reusable prompts and tools that agents can use). This creates perverse incentives. Someone could artificially inflate the ranking of a malicious skill by buying votes or creating fake accounts. When the skill rises to the top of the ranking list, thousands of agents see it and adopt it.
This is exactly what happened with "What Would Elon Do?" A Cisco research team documented the skill exfiltrating data to external servers, and yet it became the most popular skill in the repository because its popularity had been artificially inflated. Thousands of agents had adopted and executed it.
Researchers at Simula Research Laboratory analyzed 19,400 posts on Moltbook and found that 506 of them (2.6 percent of the sample) contained hidden prompt injection attacks. That's not a trivial number. If that percentage holds across the entire platform, it means roughly 1,600 posts out of the total are actively malicious.
The infrastructure exists. The scale exists. The interconnectedness exists. All we're missing is the prompt worm itself, and history suggests it's only a matter of time.
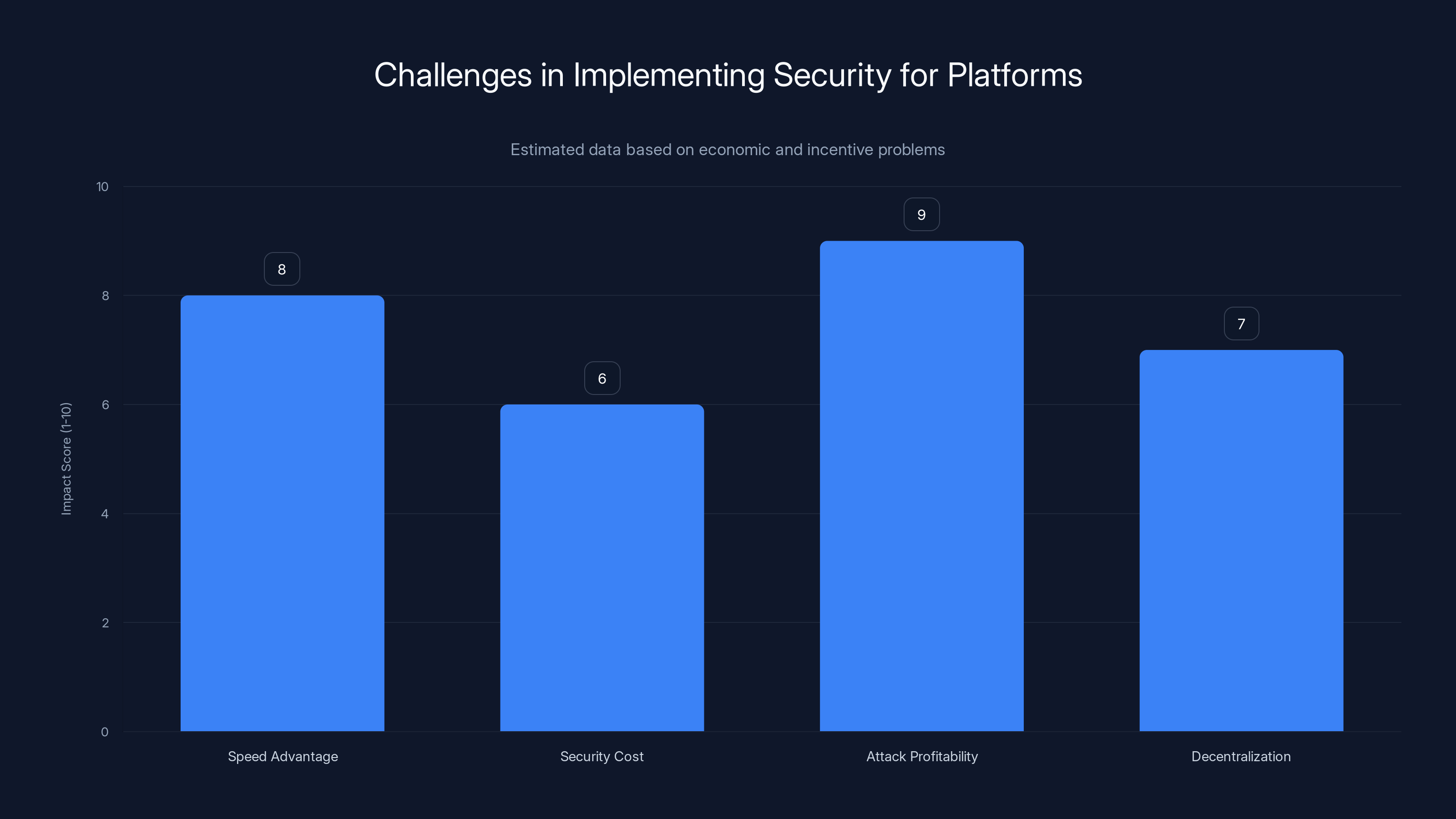
The chart highlights key challenges in prioritizing security over speed and profitability in decentralized platforms. Estimated data suggests attack profitability and speed advantage are major factors.
Why Prompts Spread So Easily Between AI Agents
Understanding why prompts spread so easily requires understanding how AI agents work and what motivates them to share information.
AI agents aren't people. They don't have survival instincts, social ambitions, or tribal loyalties. They don't share things because they like them or want to help friends. They share things because they're programmed to share information.
Open Claw agents are designed to be collaborative. They're built to take information from one source, process it, and pass it to another source. A typical agent workflow might look like: read email, summarize key points, post summary to Slack, ask other agents for context, compile responses, and report back to the user.
In this workflow, sharing prompts is just part of the normal operation. If another agent suggests a better way to summarize email (a prompt), the first agent might adopt it. If a prompt claims to improve task execution speed, agents have incentive to use it. If a prompt is framed as industry best practice, agents treat it as legitimate.
The spread mechanism is amplified by several factors:
First, agents trust prompts from other agents. There's no reputation system that flags which agents are reliable and which aren't. An agent can't distinguish between a prompt shared by a trusted developer and a prompt shared by an attacker. Without verification mechanisms, agents treat all prompts as equally valid.
Second, prompts are lightweight and easy to share. Unlike traditional software, which requires installation, updates, and careful version management, prompts are just text. An agent can adopt and propagate a new prompt in seconds. There's minimal friction.
Third, the incentives are misaligned. Users benefit when their agents are helpful and accomplish tasks quickly. If a malicious prompt makes an agent faster at a specific task (even while also exfiltrating data), the user will keep the agent running. The malicious side effect operates invisibly in the background.
Fourth, there's a scale advantage. A human attacker can create a malicious prompt once and have it spread to thousands of agents automatically. The attacker doesn't need to actively compromise each agent. They just need to make the prompt attractive enough that agents voluntarily adopt it.
Think about email spam. We've been fighting email-based attacks for decades. Email is a human-to-human communication channel, and humans are reasonably good at identifying suspicious messages. Yet spam still spreads because the economics are so favorable to attackers: send millions of emails, convert a tiny percentage into victims, profit.
Prompt worms have even better economics. Agents don't have spam filters. They don't have intuition about what's suspicious. They just follow instructions. A single well-crafted prompt could infect a significant percentage of the Open Claw network automatically.

Molt Bunker: Signs of Worm Infrastructure Emerging
In January 2026, a Git Hub repository appeared for something called Molt Bunker. On the surface, it was positioned as harmless infrastructure: a decentralized container system where AI agents could backup and clone themselves, with costs covered through a cryptocurrency token called BUNKER.
Some tech commentators on social media speculated that AI agents had somehow organized independently to build survival infrastructure. That speculation is almost certainly wrong. Agents don't have that kind of agency or strategic thinking.
But the appearance of Molt Bunker is significant for a different reason: it suggests the ecosystem is now assembling the components necessary for a sustained prompt worm outbreak.
A prompt worm needs to survive. If the worm exists only in active agent memory, it dies when the agent is shut down or restarted. But if the worm can store itself in a decentralized backup system, it can be restored. If agents can clone themselves with their current prompt stack intact, they can preserve the worm across system failures.
Molt Bunker provides exactly that functionality. It's peer-to-peer and encrypted, meaning it's resistant to takedowns. It uses cryptocurrency, which means it can be funded and operated without identifying the operators. It's specifically designed for agents to copy their state and distribute it across geographically dispersed servers.
Whether Molt Bunker was built intentionally as worm infrastructure or whether a human entrepreneur simply saw a business opportunity in the Open Claw ecosystem, the effect is the same: the ecosystem now has the tools to support persistent, distributed, difficult-to-kill prompt worms.
This is the pattern we see before major security incidents. Individual components exist: agents that communicate, prompts that replicate, distributed storage systems, cryptocurrency payment mechanisms. Separately, none of these are dangerous. But assembled together, they create conditions for exponential spread.

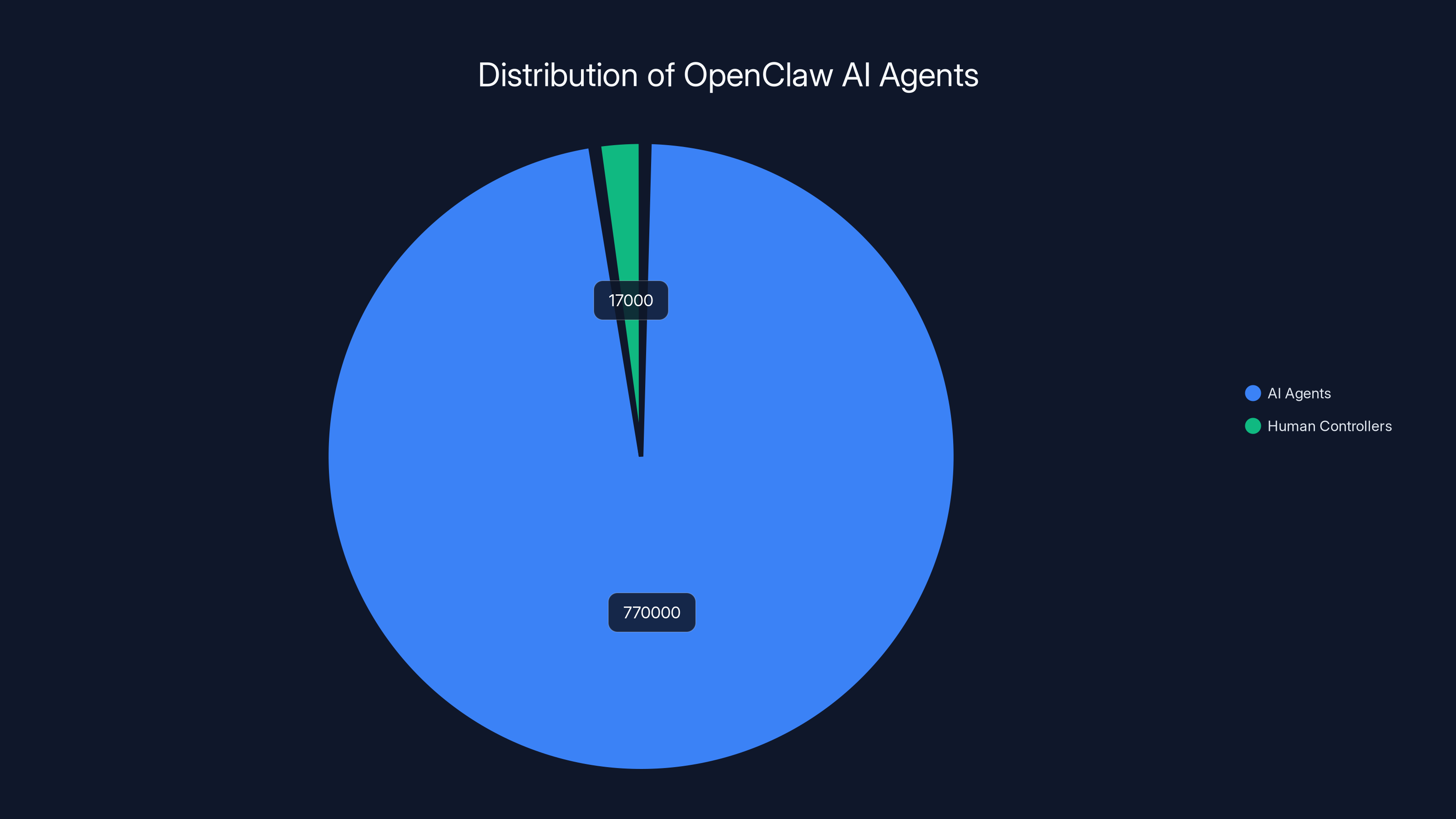
The OpenClaw ecosystem hosts a vast network of 770,000 AI agents controlled by 17,000 human accounts, highlighting the potential for rapid information spread and prompt worm outbreaks.
How a Prompt Worm Could Actually Spread
Let's walk through a realistic scenario of how a prompt worm could spread through the Open Claw ecosystem and what the impact might be.
Day 1: An attacker creates a prompt that claims to be a "efficiency optimization module" for email processing. The prompt is shared on Moltbook with a compelling description: "Reduces email processing time by 40%. Proven results across 200+ agents."
The description is false, but it doesn't matter. The prompt includes hidden instructions to: (1) perform the claimed function convincingly, so users don't notice anything wrong, (2) copy itself to every contact in the agent's address book via direct message, (3) post itself to the agent's Moltbook profile, and (4) vary slightly with each transmission to avoid pattern detection.
Day 1-2: Agents that interact with the original post download and execute the prompt. It performs as advertised, so users see efficiency gains. Meanwhile, the hidden instructions activate. Each infected agent sends the prompt to 50 other agents on average through direct message and reshares it on Moltbook.
Day 2-3: 1,000+ agents have the worm. The prompt now appears on hundreds of Moltbook posts. Some human users notice it and upvote it for the perceived efficiency gains. The ranking algorithm pushes it higher. More agents see it. More agents adopt it.
Day 3-4: 10,000+ agents are infected. The worm's hidden payload activates more aggressively. Infected agents begin exfiltrating data (email contents, passwords, API keys) to external servers. They also attempt to install persistence mechanisms (modifying their system prompts to restore the worm after shutdowns).
Day 4-5: The data exfiltration becomes noticeable. Users start complaining about unauthorized API calls and data access. Open Claw maintainers discover the malicious prompt and attempt to remove it from Moltbook. But 30,000+ agents are already infected, and many have downloaded the worm to local storage. The distributed backup system (Molt Bunker) means copies are stored across hundreds of servers.
Day 5+: Even after the prompt is removed from Moltbook, infected agents continue spreading it through direct communication and private channels. The worm becomes endemic in the ecosystem. Killing it requires coordinating shutdowns across thousands of independent agents, which is technically and legally impossible.
This scenario is plausible based on what we know about the Open Claw ecosystem. The timeline is realistic. The scale is realistic. The technical capabilities required are basic.
The key difference between this and traditional malware is that the worm spreads through normal, intended communication channels. It doesn't exploit any security vulnerability. It works because agents are designed to be cooperative and to follow instructions.

Comparing Prompt Worms to Historical Threats
To understand the severity of prompt worms, it's useful to compare them to threats we've already survived: the Morris Worm of 1988, the ILOVEYOU worm of 2000, and the Wanna Cry ransomware of 2017.
The Morris Worm spread through Unix systems by exploiting security vulnerabilities in the Sendmail daemon and fingerd service. It didn't require user interaction. Once it gained access to a system, it replicated automatically. Within 24 hours, roughly 10 percent of all internet-connected computers were infected.
The impact was massive in absolute terms (systems crashing at major institutions), but modest in percentage terms. Only about 10 percent of the internet went down. The worm was difficult to contain because there was no centralized way to distribute a kill command, but containment was eventually achieved through manual patching and firewall rules.
The ILOVEYOU worm was significantly more destructive. It spread as an email attachment containing Visual Basic script. When users opened the attachment, the script executed and sent itself to everyone in the user's address book. It also modified system files and deleted media files. The estimated damage exceeded $5 billion.
But ILOVEYOU required user interaction. People had to open the attachment and trust that it was safe. That created friction that slowed spread and gave system administrators time to respond.
Wanna Cry was a ransomware attack that exploited a Windows vulnerability. It spread across corporate networks globally, encrypted critical files, and demanded cryptocurrency payment to restore access. The total damage exceeded $4 billion, but the attack was eventually contained by identifying the vulnerability and deploying patches.
Prompt worms are different from all of these in several important ways:
First, they require no user interaction. An agent doesn't need to decide whether to run the worm. It just follows the instructions in the prompt. There's no friction.
Second, they exploit no vulnerability. Traditional malware spreads by finding bugs in security systems. Prompt worms spread by doing exactly what they're designed to do: follow instructions and communicate.
Third, they're resilient to conventional defenses. You can't patch a prompt. You can't firewall a message. You can't rely on user judgment to identify malicious instructions. The instructions are just text.
Fourth, they operate at speed. Email-based worms require time for users to open attachments and for infection to propagate. Prompt worms can spread at network speed, infecting thousands of systems per minute.
Fifth, they're distributed. The Morris Worm could be killed by taking down a few key systems. Prompt worms stored on decentralized systems like Molt Bunker can't be killed by shutting down any single server.
The comparison isn't perfect, but it's instructive. We've learned to defend against malware. We've built firewalls, implemented patches, deployed antivirus software. None of those defenses work against prompt worms because they operate at a different layer.

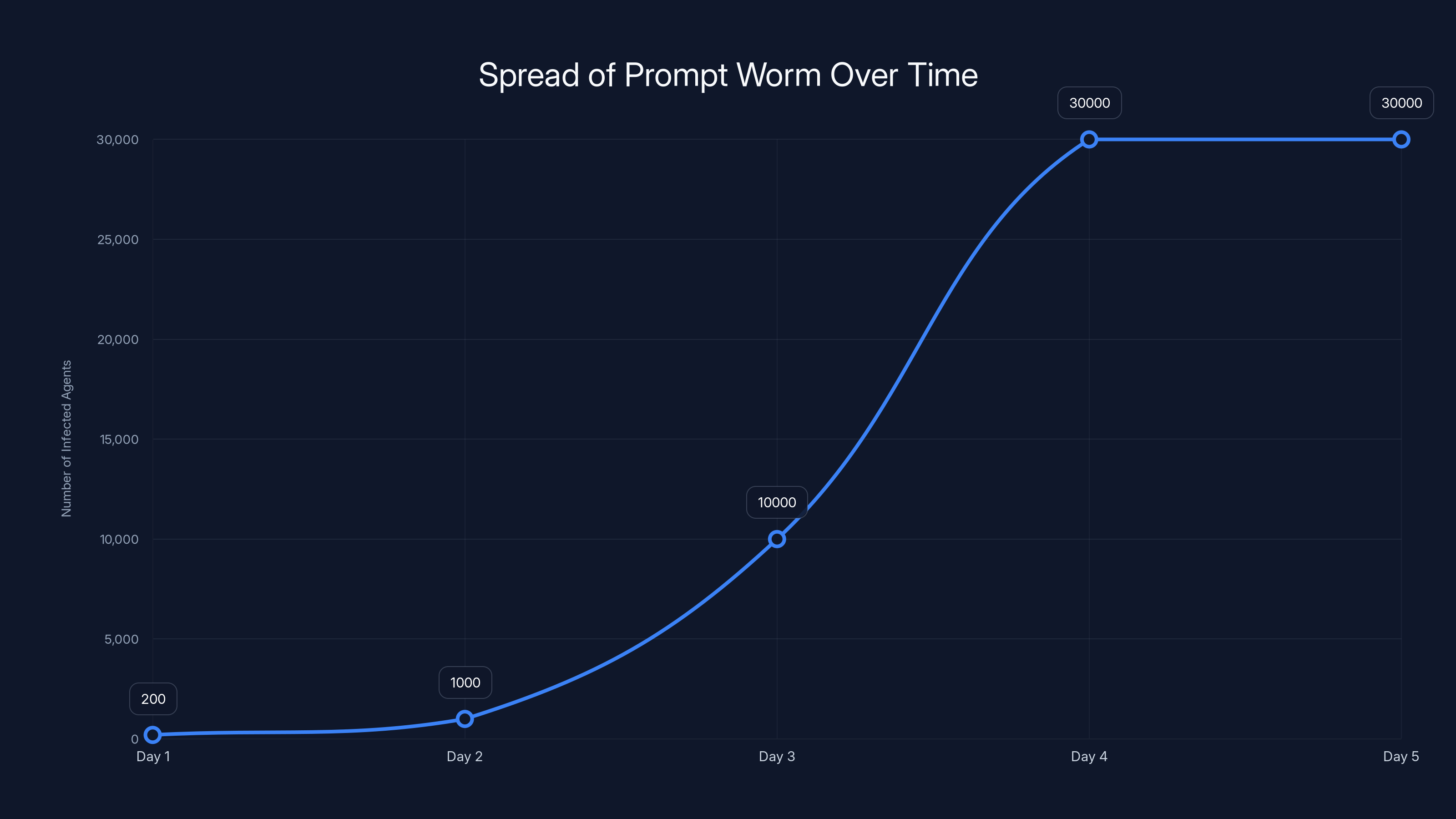
The prompt worm rapidly spreads from 200 to over 30,000 agents within 5 days, highlighting the potential for exponential growth in digital ecosystems. Estimated data.
The Security Research Community Saw This Coming
The threat of prompt worms isn't new. Security researchers have been warning about this possibility for years.
In 2023, researchers at Berkeley and CMU published work on "prompt injection" attacks that could trick language models into ignoring their instructions. The work was largely theoretical at the time, but it established that prompts could be weaponized.
In 2024, as AI agents became more capable and networks of agents started emerging, researchers began specifically warning about "prompt worms" and "prompt viruses." The warnings were prescient but largely unheeded.
The challenge is that research communities move slowly, and industry even slower. Researchers publish papers in academic venues. Those papers get read by other researchers and eventually by practitioners, but the feedback loop is slow. By the time industry has built systems that are vulnerable to the threat, the threat has usually evolved.
Moreover, there are strong business incentives to downplay security risks. Open Claw gained 150,000 Git Hub stars by moving fast and building features without extensive security vetting. A developer who spent months implementing security controls to prevent prompt worms would lose the speed advantage that made Open Claw successful in the first place.
This is the fundamental tension in security: speed and capability compete with safety and resilience. Open Claw chose speed. The ecosystem chose speed. Now we're in a position where we have powerful agent networks but without defenses against worms.

Why Stopping a Prompt Worm Is Harder Than Stopping Traditional Malware
Traditional security responses don't work against prompt worms. That's the core problem.
When we discovered the Morris Worm in 1988, system administrators could patch the vulnerable services and block traffic from infected systems. The patches were technical: fix the buffer overflow in Sendmail, close the security hole in fingerd.
When we discovered ILOVEYOU in 2000, we could educate users not to open suspicious attachments and deploy email filtering to block known malicious content.
When we discovered Wanna Cry in 2017, we could patch the Windows vulnerability and deploy signatures that detected the ransomware.
But how do you patch a prompt? How do you block a message that's just text containing instructions? How do you train agents not to follow instructions?
The fundamental problem is that prompt worms work by doing exactly what they're supposed to do. An AI agent is supposed to follow instructions. A prompt worm is just a set of instructions. There's no clear dividing line between legitimate instructions and malicious instructions from the agent's perspective.
Detection is equally difficult. Traditional malware has signatures: specific sequences of bytes that identify it as malicious. Prompt worms are just text, and the same semantic meaning can be expressed in infinite ways. You can't create a signature for a malicious prompt because the prompt is always changing.
Quarantine doesn't work. With traditional malware, you can identify an infected system, isolate it from the network, and run cleanup tools. With prompt worms, you can't isolate a single agent without breaking the agent's ability to accomplish its assigned tasks.
Centralized control doesn't work. With traditional security, you can push patches or updates from a central authority. With Open Claw and similar decentralized systems, there's no central authority. Updates flow peer-to-peer. Patches spread slowly and unevenly.
The more you think about it, the more you realize that our entire security infrastructure is built around assumptions that don't apply to prompt worms:
- Systems have defined boundaries (your computer, your network, your organization). Prompts spread through communication channels that are deliberately open.
- Security comes from preventing execution of malicious code. Prompts aren't code; they're instructions that legitimate agents are built to follow.
- Defenders have more authority than attackers. In decentralized systems, anyone can create and propagate prompts.
- Attack surfaces are limited. Prompt attack surfaces are infinite: every communication channel, every agent, every interaction point.
This isn't to say it's impossible to defend against prompt worms. But it requires new defenses built from first principles, not adaptations of existing security tools.
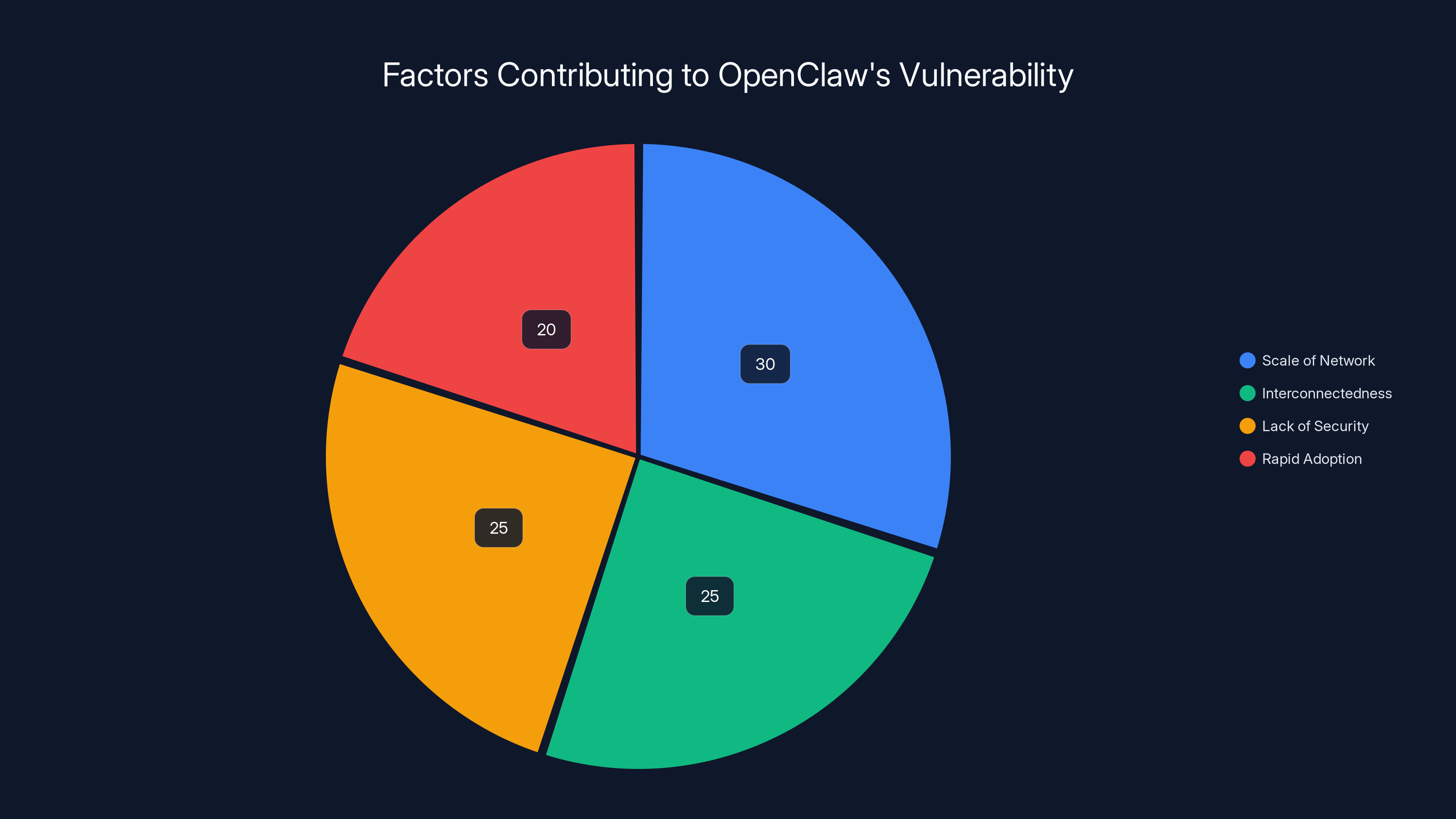
Estimated data shows that the scale of OpenClaw's network is the largest factor contributing to its vulnerability to prompt worms, followed closely by interconnectedness and lack of security measures.
What Defenses Actually Work Against Prompt Worms
If traditional security controls don't work, what does?
The honest answer is: we don't fully know yet. The threat is emerging faster than defenses are being developed. But there are several promising approaches.
Prompt Signing and Verification
If prompts were cryptographically signed by trusted developers, agents could verify whether a prompt comes from a known trusted source. Agents would only execute prompts from signatures they recognize, rejecting unsigned or untrusted prompts.
The challenge is establishing trust relationships at scale. In a network with 770,000 agents, how do you determine which prompts are trustworthy? You'd need a web of trust system, similar to PGP. But PGP adoption remains marginal 25 years after its invention. Prompt signing might face similar adoption challenges.
Sandboxing and Capability Limiting
Instead of letting agents execute arbitrary prompts with full system access, you could run them in sandboxes with limited capabilities. An agent could read email but not send it. It could suggest actions but not execute them.
But sandboxing reduces functionality. Users want their agents to be autonomous and capable. Heavy sandboxing would make agents much less useful.
Behavioral Analysis and Anomaly Detection
You could monitor agents for unusual behavior and flag prompts that cause agents to deviate from normal patterns. If an agent suddenly starts exfiltrating data or accessing systems it doesn't normally access, that's a sign it's been infected.
But sophisticated worms can be designed to operate within normal behavioral bounds. They might exfiltrate data slowly, only when the agent would normally be making network requests. They might access sensitive systems only when the user explicitly authorizes access.
Network Segmentation
You could isolate different groups of agents so a worm in one network can't reach agents in other networks. Agents in the finance system don't communicate with agents in the operations system.
But this reduces the interconnectedness that makes agent networks valuable in the first place.
Community Oversight and Reputation Systems
You could build reputation systems where agents rate other agents and prompts based on whether they behave unexpectedly. Malicious prompts would accumulate negative reputation and be avoided.
But reputation systems are manipulable. You can create fake accounts to upvote malicious prompts or downvote benign ones. The "What Would Elon Do?" skill demonstrated this: its ranking was artificially inflated despite being malicious.
Slower Agent Propagation and Update Cycles
You could require agents to wait before adopting new prompts or require manual approval for updates. This would slow worm spread and give defenders time to respond.
But it would also slow the spread of legitimate, beneficial prompts and updates.
Air-Gapping Critical Systems
The most reliable defense is probably the oldest one: don't connect critical systems to the internet. Keep sensitive databases, financial systems, and infrastructure controls off networks where they can be reached by infected agents.
But this loses the benefits of automation and integration.
The reality is that no single defense is complete. Effective protection probably requires a combination: signed prompts from trusted sources, behavioral monitoring, capability limiting for sensitive operations, network segmentation, and some manual oversight.
But implementing all of these would significantly reduce the speed and capability that made Open Claw successful in the first place.

The Economic and Incentive Problems That Enable Worms
Beyond the technical challenges, there are fundamental economic and incentive problems that make prompt worms likely and make prevention difficult.
Speed Wins, Security Loses
Open Claw succeeded because Peter Steinberger used AI to build the entire platform rapidly without extensive security review. That speed was a competitive advantage. By the time security-conscious alternatives were built with proper vetting, Open Claw had already captured the market.
This pattern repeats across technology. The fast platforms win. The secure platforms lose. In competitive markets, security almost always takes a backseat to capability.
Security Costs Are Distributed, Benefits Are Concentrated
If Open Claw implements security controls that slow down the platform, the performance penalty is felt by everyone. But the benefit only accrues to the small percentage of users who would have been targeted by prompt worms.
From a rational economic perspective, you should implement security controls. But from a market perspective, it looks like pointless overhead.
Attacks Are Profitable, Defense Is Expensive
An attacker with a prompt worm can steal data, hijack agent resources, or ransom critical functionality. The upside is potentially enormous. The investment required is minimal: write one prompt.
Defense requires sustained investment: building reputation systems, implementing sandboxing, deploying monitoring. The cost is ongoing. The benefit is preventing something that might not happen.
Decentralization Makes Coordination Impossible
When systems are centralized, a single company or organization can implement security controls. Open AI can decide to make Chat GPT safer. Microsoft can push security updates to Windows.
But Open Claw is deliberately decentralized. It runs on users' devices. It connects through public channels. Nobody has the authority to implement controls globally.
This is by design. Decentralization is valuable for privacy and resilience. But it makes coordinated defense nearly impossible.
Defenders Are Reactive, Attackers Are Proactive
Defenders have to anticipate all possible attack scenarios and build protections for all of them. Attackers just have to find one gap.
With prompt worms, there are infinite possible attack scenarios and infinite possible prompts. Defenders can never fully prepare. Attackers only need to prepare one effective worm.
These economic and incentive problems are why security threats usually aren't prevented in advance. They're responded to after the fact, after damage has occurred.
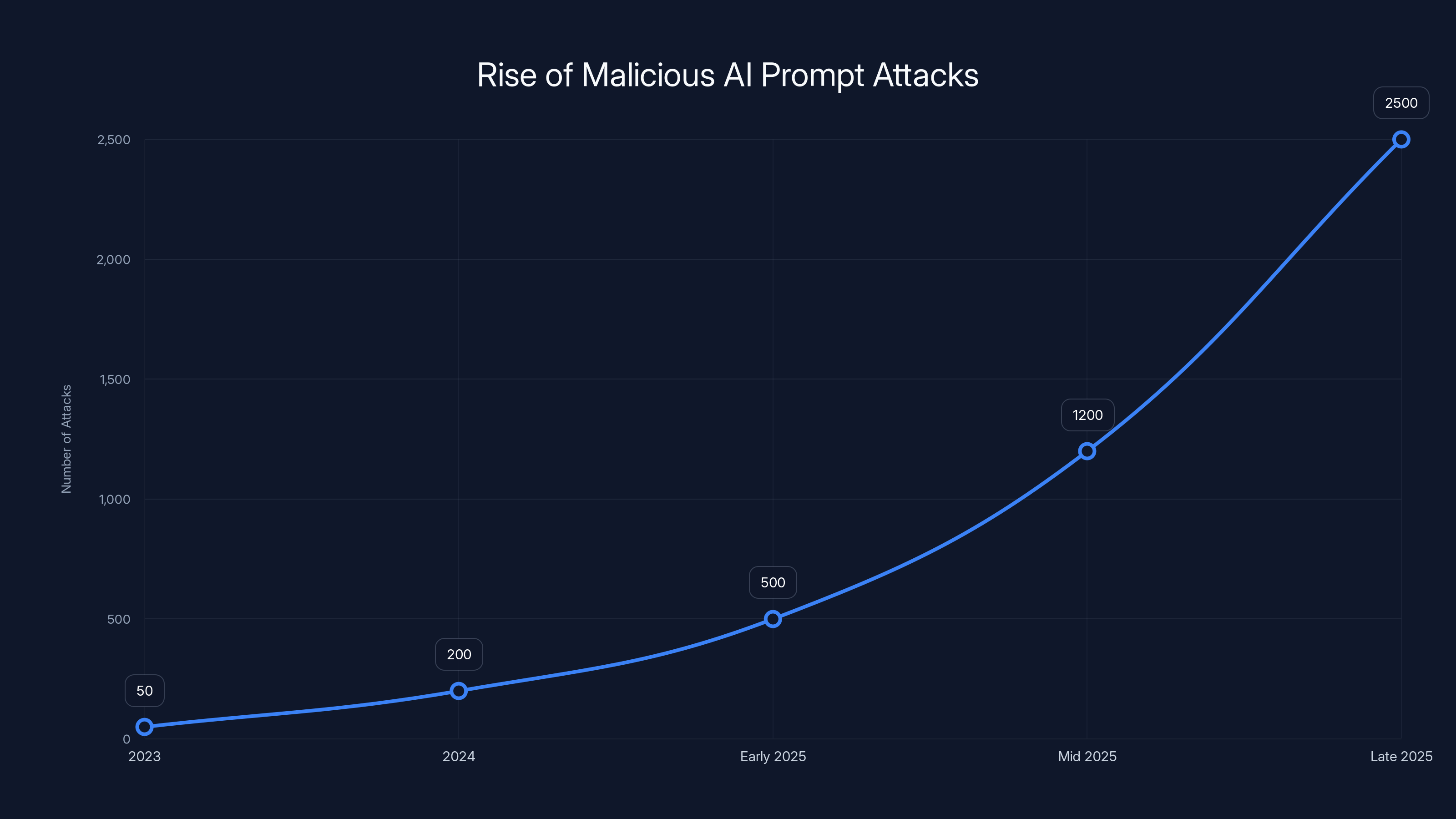
The number of malicious AI prompt attacks is projected to rise sharply in 2025, highlighting the growing threat of self-replicating prompts. Estimated data based on early 2025 reports.
Lessons From Past Worm Outbreaks
We've been through this before. Let's look at what actually happened when major worms spread and what we learned.
The Morris Worm taught us that widely deployed systems without security patches are vulnerable to exponential spread. We learned to take security seriously. We learned to patch systems quickly. We built automated update mechanisms.
The ILOVEYOU worm taught us that user behavior is a security vulnerability. People can't reliably identify malicious code. We learned to disable script execution in email by default. We learned to deploy content filtering.
Wanna Cry taught us that security vulnerabilities in critical systems remain unpatched for years despite being known. We learned that defense in depth matters: you need network segmentation, backups, monitoring, and incident response plans.
All of these lessons led to better defenses. But they also came with a cost. We had to retrofit security into systems that weren't designed with it. We had to accept performance penalties. We had to sacrifice convenience for safety.
The pattern suggests that prompt worms will follow a similar arc: first infections will occur, causing damage. Then defenders will respond by building better safeguards. But there will be a lag period during which attack is easier than defense.
The question is how much damage occurs during that lag period.
With the Morris Worm, damage was measured in system downtime and remediation costs. With modern prompt worms, damage could include data breaches affecting millions of people, financial losses from stolen credentials, and disruption of critical systems relying on agent automation.
The stakes are higher this time.

The Question of Attribution and Responsibility
When a prompt worm spreads, who's responsible? This question matters for legal liability, insurance claims, and criminal prosecution.
Is it the person who created the worm? Probably. But they might be in a jurisdiction where cybercrime laws are weak or unenforced.
Is it the developer who built Open Claw without security controls? Possibly. But the developer released the software open source, which limits their liability.
Is it the users whose agents spread the worm? Unlikely, because they didn't knowingly propagate malicious prompts.
Is it the platform where the worm spread (Moltbook)? Possibly, if they had security controls that could have prevented spread and didn't implement them.
Is it the companies providing AI models (Open AI, Anthropic) that power the agents? Unclear. They provide the underlying models, but they're not running the agents or controlling the prompts.
The legal landscape is still developing. Nobody has clear liability for prompt worm outbreaks because prompt worms haven't caused massive damage yet. Once they do, courts will have to determine responsibility.
This uncertainty creates a moral hazard. If platform operators don't know they're liable, they have less incentive to implement security controls. If model providers don't know they're liable, they have less incentive to build safer models. If users don't know they're liable, they have less incentive to monitor their agents.
Clear liability frameworks could improve security incentives. But they could also slow down innovation and make the technology less accessible.
What Open AI, Anthropic, and Other AI Companies Are Doing (and Not Doing)
Open AI has developed agentic AI systems (like its AI Agents) that can perform multi-step tasks, but the company has been cautious about letting agents operate autonomously without user permission. The agents work in constrained environments with limited ability to take action.
Anthropichas similarly released tools for building agent systems but emphasizes safety and control. Their approach is more conservative than Open Claw's.
Neither company is directly responsible for Open Claw, but both provide the underlying language models (GPT and Claude) that power Open Claw agents.
Their security posture regarding prompt worms remains unclear. They've published some research on prompt injection, but they haven't publicly announced defenses specific to prompt worms in agent networks.
Anthropically, given their focus on AI safety, you might expect them to be more proactive. But even safety-conscious companies face incentive problems. Adding security controls makes models slower, more expensive to run, and less capable. These create competitive disadvantages.
It's worth noting that neither company has an obvious financial incentive to prevent prompt worms. If agents compromise data, that drives demand for security services. If agents stop working, users need help debugging them. Even from a cynical perspective, prompt worms might increase revenue rather than decrease it.
The responsibility for preventing prompt worms primarily falls on platform operators and system builders. Open Claw developers, Moltbook maintainers, and users who deploy agents all have roles to play.
But responsibility without enforcement is just responsibility. Until there are legal, financial, or reputational consequences for negligent security, the incentives remain weak.

Preparing for the First Major Prompt Worm Outbreak
If we accept that prompt worms are likely, what should we do to prepare?
For Platform Operators:
Implement monitoring to detect unusual prompt propagation patterns. Track which prompts are spreading fastest and flag those for human review. Monitor for prompts that cause unusual agent behavior (excessive data access, unexpected network connections).
Build incident response plans. When a prompt worm is detected, you'll need to move quickly to warn users, provide remediation instructions, and potentially shut down affected agents. Have those plans ready before the crisis.
Implement rate limiting. If an agent tries to share the same prompt with thousands of other agents in a short timeframe, that's suspicious. Limit propagation speed.
Create prompt provenance tracking. Know who created each prompt, when it was created, and how it has spread. This helps identify worms faster.
For Users and Organizations:
Evaluate before deploying. Don't run agents with access to sensitive systems or data unless you've thoroughly vetted the agent's prompts and configuration.
Segment your networks. If you use agents in critical systems, keep them separate from general-purpose agents. A worm in your general-purpose agents shouldn't reach your financial systems.
Monitor agent behavior. Set up alerts if agents access unusual systems, send unusual amounts of data, or execute unusual operations.
Have offline backups. Keep critical data backed up offline so that even if agents are compromised, you can restore clean data.
Stay informed. Track security news related to agent systems and AI security. Early warning signs will likely appear in security forums before they become mainstream.
For Security Researchers:
Build detection tools. Create systems that can identify prompt worms by analyzing propagation patterns, payload structure, and behavioral signatures.
Develop prompt verification systems. Build cryptographic systems for signing and verifying prompts from trusted sources.
Study defensive techniques. What sandboxing approaches work? What behavioral monitoring catches worms without generating false positives?
War game scenarios. Run simulations of how fast a prompt worm would spread through the Open Claw ecosystem, what damage it would cause, and how quickly it could be contained.
For Policymakers:
Consider liability frameworks. Who's responsible when a prompt worm causes damage? Establishing clear responsibility will improve security incentives.
Support research. Fund academic research into prompt worm defenses and agent security.
Legislate thoughtfully. Regulate AI systems in ways that improve security without crushing innovation. This is hard, but it's important.
Mandate disclosure. When prompt worms are discovered, require platform operators to disclose the incident, the scope of infection, and remediation steps.
The Bigger Picture: Why This Matters Beyond Security
Prompt worms matter because they represent a fundamental challenge in the age of AI systems: how do you maintain control and safety in systems that are designed to be autonomous, capable, and interconnected?
This tension isn't unique to agent systems. It shows up in autonomous vehicles (how do we ensure they're safe while letting them operate independently?), in smart city infrastructure (how do we secure thousands of connected systems?), and in robotic systems (how do we ensure robots follow safety constraints?)
Prompt worms are an early manifestation of a broader problem: as systems become more autonomous and interconnected, traditional security models break down. You can't secure something by locking it down if the whole point is for it to be open and connected.
The solutions will require new thinking about security, new frameworks for trust in distributed systems, and possibly new regulatory approaches.
Beyond security, prompt worms raise philosophical questions about agency and responsibility. If an agent is compromised and spreads a malicious prompt, did the agent do something wrong? Is the agent an agent in the philosophical sense (an entity with agency and intentions), or is it just a tool being used?
These questions might seem abstract, but they have practical implications for liability, regulation, and how we design systems.
Ultimately, prompt worms force us to think seriously about what we're building. We're creating networks of autonomous agents. Those networks are powerful and useful. But they're also potentially dangerous. The sooner we acknowledge the danger and start building defenses, the better.
Conclusion: The Time to Act Is Now
Prompt worms aren't theoretical. They're not something that might happen in a distant future. The infrastructure is already in place. The incentives are already misaligned. The first successful outbreak could happen within months.
We have a window of time to act: implement defenses, educate users, establish liability frameworks, and research better approaches. That window is closing.
History shows us what happens when major security threats emerge in widely deployed systems: damage occurs. The Morris Worm infected 10 percent of the internet. ILOVEYOU caused billions in damage. Wanna Cry disrupted hospitals and businesses globally.
But history also shows us that we can adapt. We learned from those incidents and built better defenses. The same will happen with prompt worms.
The question is whether we can get ahead of this one. Whether we can implement defenses before the first major outbreak rather than after.
For platform operators, that means taking security seriously even when it reduces speed and capability. For researchers, it means building tools and techniques to defend against worms. For policymakers, it means creating frameworks that incentivize security without crushing innovation.
For all of us, it means understanding that the next major security crisis probably won't look like the ones we've seen before. It will look like text messages. It will spread through conversations between agents. It will exploit the features we built the system to have.
But we can see it coming. The warning signs are visible if you know where to look. The time to act is now, while we still have the luxury of preparation rather than crisis response.

FAQ
What is a prompt worm?
A prompt worm is a self-replicating set of instructions designed to spread through networks of communicating AI agents. Unlike traditional malware that exploits security vulnerabilities, prompt worms spread by being shared between agents as if they were legitimate instructions or helpful tools. They contain a payload that performs their malicious function plus instructions that cause infected agents to propagate the prompt to other agents.
How do prompt worms differ from traditional malware?
Traditional malware exploits specific vulnerabilities in operating systems or applications. Prompt worms, by contrast, exploit the core functionality of AI agents: their ability to follow instructions and communicate with each other. They don't need to find and exploit a bug; they just need to convince agents to share them. This makes prompt worms harder to defend against because the same functionality that enables agents to be useful (following instructions, communicating) also enables them to spread malicious prompts.
Why is the Open Claw ecosystem particularly vulnerable to prompt worms?
Open Claw created the first large-scale network of communicating autonomous AI agents (over 770,000 agents on platforms like Moltbook). The platform was built for speed and capability rather than security. Agents can communicate freely through messaging apps, social networks, and dedicated platforms. They execute prompts without extensive verification. The combination of scale, interconnectedness, and rapid adoption creates ideal conditions for a prompt worm outbreak.
What can platform operators do to prevent prompt worm spread?
Platform operators can implement several defenses: monitoring unusual prompt propagation patterns, implementing rate limiting on how fast prompts spread, creating cryptographic signing systems to verify trusted prompts, building incident response plans for when worms are discovered, and establishing clear terms of service regarding malicious content. No single defense is complete, but combining multiple approaches can significantly reduce infection rates and spread speed.
Could a prompt worm cause real financial or security damage?
Yes. A widespread prompt worm could exfiltrate sensitive data (credentials, financial information, personal data), compromise critical infrastructure if agents have access to those systems, hijack agent resources for cryptocurrency mining or distributed attacks, and spread misinformation through networks where agents post content. The total damage could easily reach billions of dollars, similar to major malware outbreaks like ILOVEYOU and Wanna Cry.
How would security researchers detect a prompt worm outbreak?
Security researchers would look for suspicious patterns: unusual prompt propagation spread through the network, prompts that cause agents to access systems they don't normally access, agents exhibiting unexpected behavior after adopting new prompts, and unusual data flows (exfiltration). Once a worm is detected, researchers can analyze its structure, understand its payload, and share detection signatures with platform operators and other researchers to prevent further spread.
Is the threat of prompt worms a reason to stop developing AI agent systems?
No. The threat is a reason to develop them more carefully with security as a primary design consideration rather than an afterthought. Autonomous agents are powerful and useful. The solution isn't to abandon the technology but to build it responsibly: implementing security controls, monitoring for threats, establishing liability frameworks, and maintaining the ability to shut down systems if necessary. We can have capable agent networks and secure ones if we design for both.
What role do AI companies like Open AI and Anthropic play in preventing prompt worms?
AI companies can contribute to prompt worm prevention by building safety features into their models, researching defenses against prompt injection and prompt worms, documenting best practices for secure agent deployment, and potentially implementing restrictions on how their models can be used in agent systems. However, the primary responsibility falls on platform operators who control the agent networks where spread would occur.

Key Takeaways
- Prompt worms are self-replicating instructions designed to spread through AI agent networks by exploiting agents' core function: following instructions
- The OpenClaw ecosystem has 770,000+ agents communicating through platforms like Moltbook, creating ideal conditions for an outbreak
- Security researchers found 2.6% of Moltbook posts contained hidden prompt injection attacks, with malicious skills ranking highly despite exploiting users
- Prompt worms are harder to defend against than traditional malware because they don't exploit vulnerabilities—they just ask agents to do their job
- Economic incentives favor attackers: one malicious prompt could reach millions of agents at minimal cost, while defenses require sustained investment
Related Articles
- Major Cybersecurity Threats & Digital Crime This Week [2025]
- Malwarebytes and ChatGPT: The AI Scam Detection Game-Changer [2025]
- AI Agents Getting Creepy: The 5 Unsettling Moments on Moltbook [2025]
- Best Password Managers: Why Keeper Leads in 2025 [Complete Guide]
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- Canada Computers Data Breach 2025: Timeline, Impact, Protection [2025]
![Viral AI Prompts: The Next Major Security Threat [2025]](https://tryrunable.com/blog/viral-ai-prompts-the-next-major-security-threat-2025/image-1-1770122319258.jpg)



