How Malwarebytes and Chat GPT Are Revolutionizing Scam Detection
You're sitting at your desk. Your phone buzzes. A message claims your bank account needs immediate verification. Your heart rate spikes. Should you click?
This moment happens to millions of people every single day. And honestly, the stakes couldn't be higher. Scammers stole approximately $442 billion globally in 2024, making cybercrime more profitable than most legitimate industries. The worst part? AI is making scams more convincing than ever.
But what if you had instant access to threat intelligence without leaving your browser? What if you could verify that suspicious link in seconds? That's exactly what Malwarebytes and Chat GPT just made possible.
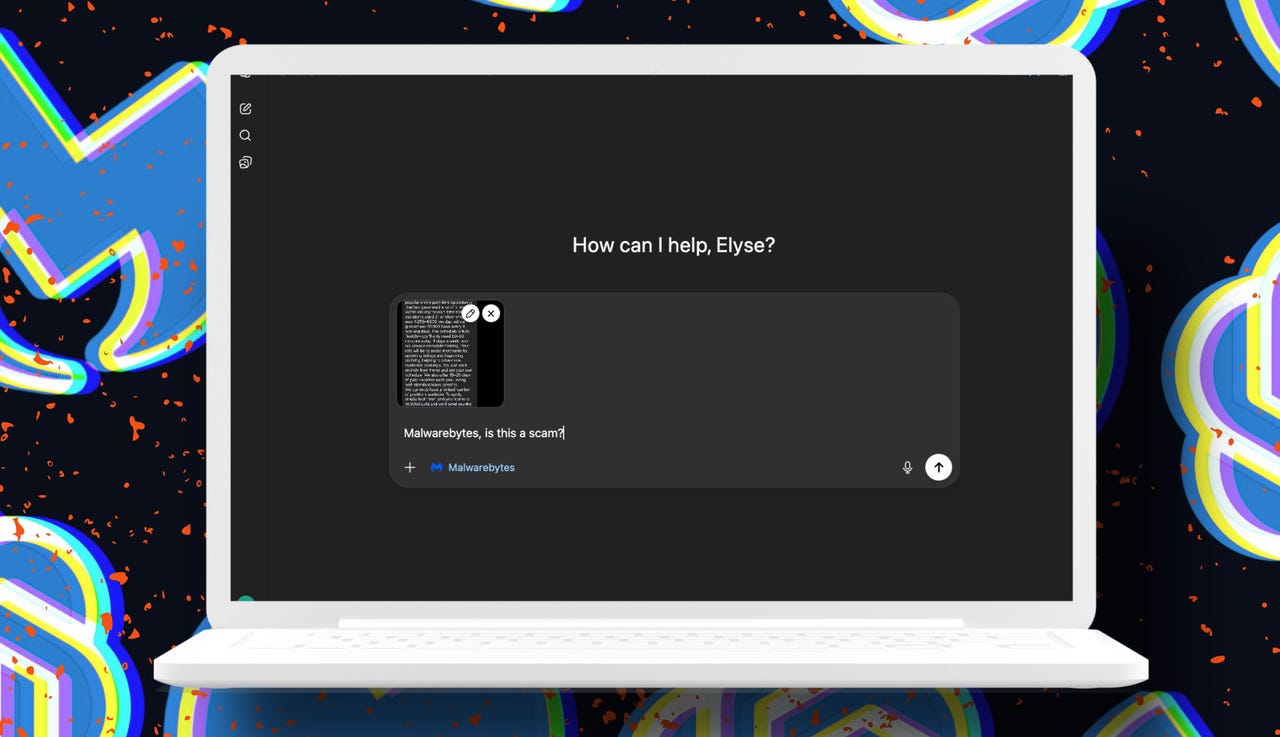
The partnership represents a fundamental shift in how regular people defend themselves against scams. It's not some complicated security software. It's not a subscription you'll never use. It's a simple question asked in a tool you probably use every single day: "Malwarebytes, is this a scam?"
In this guide, we'll break down exactly how this integration works, why it matters for your security, and how to use it effectively. We'll also explore the broader landscape of AI-powered threat detection and what this partnership means for the future of personal cybersecurity.
TL; DR
- Instant Verification: Ask "Malwarebytes, is this a scam?" directly in Chat GPT and get real-time analysis of suspicious content
- Multi-Format Detection: The tool analyzes emails, text messages, URLs, domains, phone numbers, and direct messages for authenticity
- Free and Accessible: Available to all Chat GPT users (Free, Plus, Team, and Enterprise tiers) at no additional cost
- Threat Intelligence Integration: Suspicious content can be submitted to improve Malwarebytes' global threat database
- Addresses the Scam Crisis: With $442 billion stolen annually through scams, this tool provides practical defense at the moment of risk
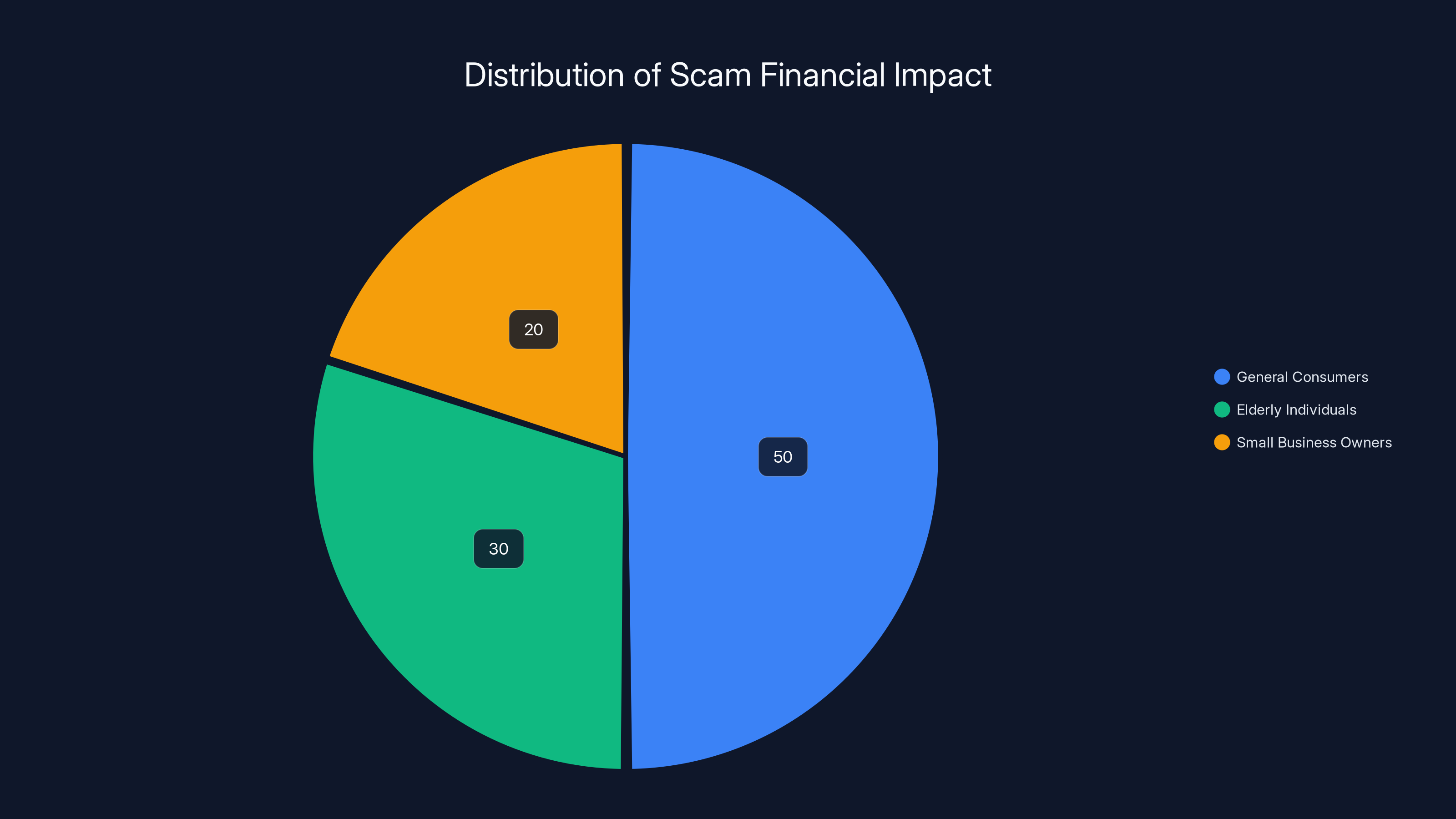
Estimated data shows that general consumers account for 50% of scam losses, while elderly individuals and small business owners account for 30% and 20% respectively.
The Scale of the Scam Problem
Numbers alone don't capture the real damage of scams, but they're worth understanding. We're not talking about a few thousand isolated incidents. We're talking about an epidemic affecting nearly every internet user.
GASA's Global State of Scams 2025 report documented something staggering: the global scam economy extracted nearly half a trillion dollars from consumers in a single year. To put that in perspective, that's more revenue than the entire pharmaceutical industry generates annually.
Where's this money coming from? Individual consumers like you. An average person might lose
Why Scammers Are Getting Better
AI isn't slowing down scammers. It's accelerating them exponentially. Traditional scam emails looked sloppy. Obvious grammar mistakes. Awkward phrasing. Red flags everywhere.
Now? Open AI's language models, competing services, and countless open-source alternatives mean anyone can generate convincing phishing emails at scale. A scammer can create 10,000 variations of a phishing email in minutes, each personalized and grammatically perfect.
The arms race is real. Bad guys deploy AI. Good guys respond with AI. But the good guys (companies like Malwarebytes) have years of threat intelligence data, real-world attack patterns, and access to millions of known malicious domains and email addresses.
The Human Element
Here's what statistics miss: scammers don't need a 100% success rate. They need 0.01%.
If a scammer sends 10 million emails and just 1,000 people fall for it, that's 1,000 compromised accounts, stolen credit cards, or identity thefts. One click. One verification code shared. One password entered on a fake login page.
The human brain evolved over millions of years to trust visual and social cues. Modern scammers exploit these ancient instincts with precision. An email that looks like it's from your boss asking for an urgent wire transfer hits your amygdala before your prefrontal cortex can evaluate it critically.
This is why the Malwarebytes and Chat GPT integration matters. It injects a moment of skepticism. A pause. A chance to verify before clicking.
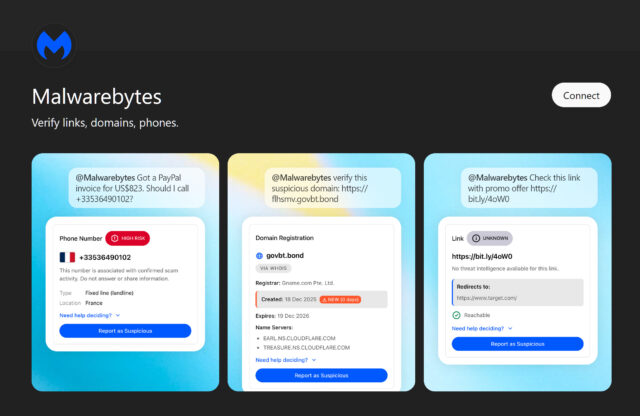
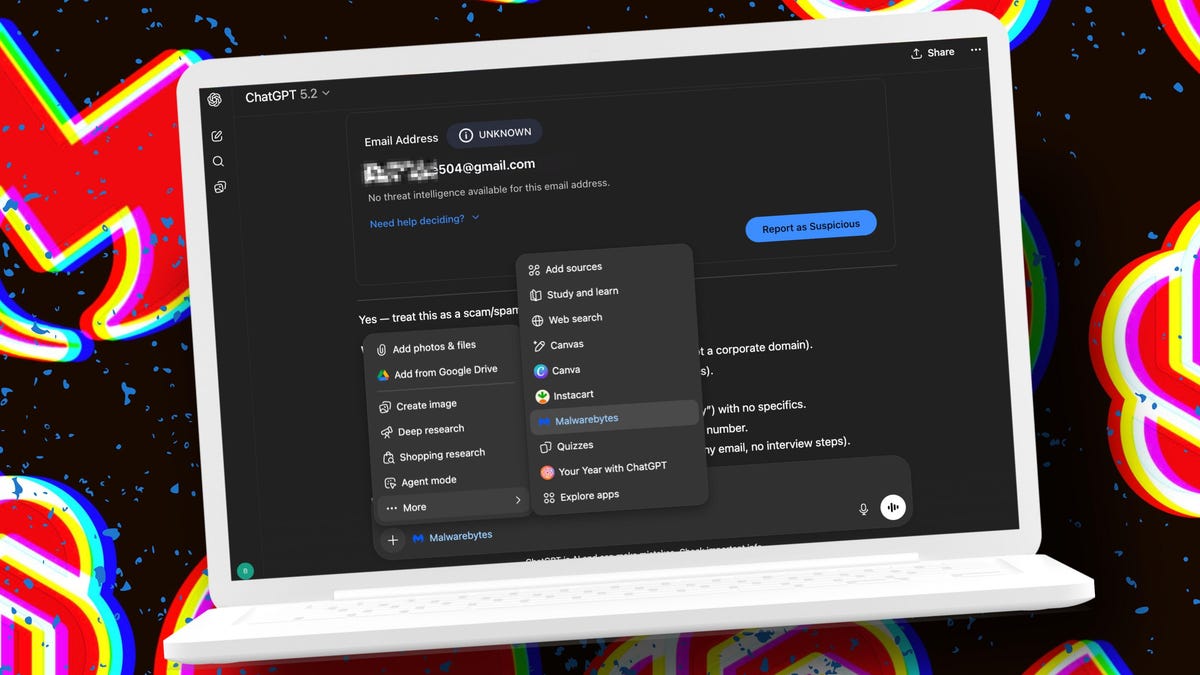
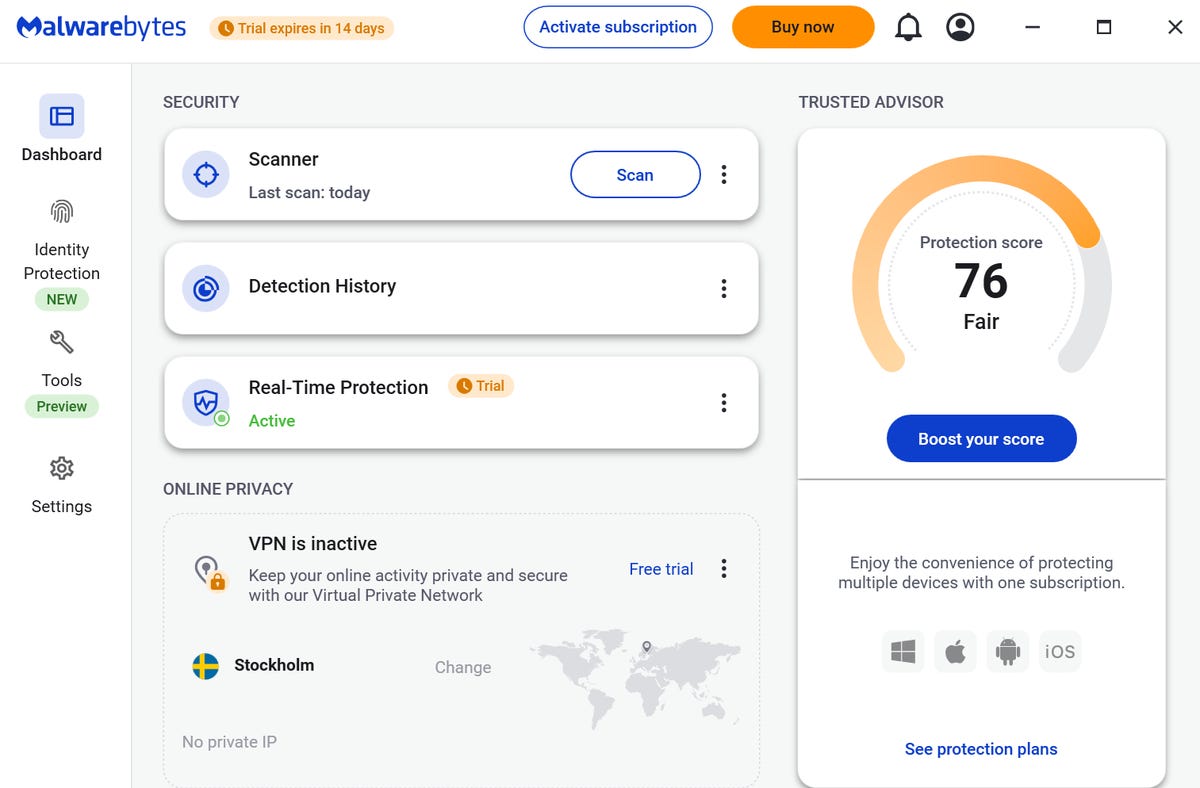
How the Malwarebytes-Chat GPT Integration Works
The technical implementation is straightforward, but the sophistication lies in what happens behind the scenes.
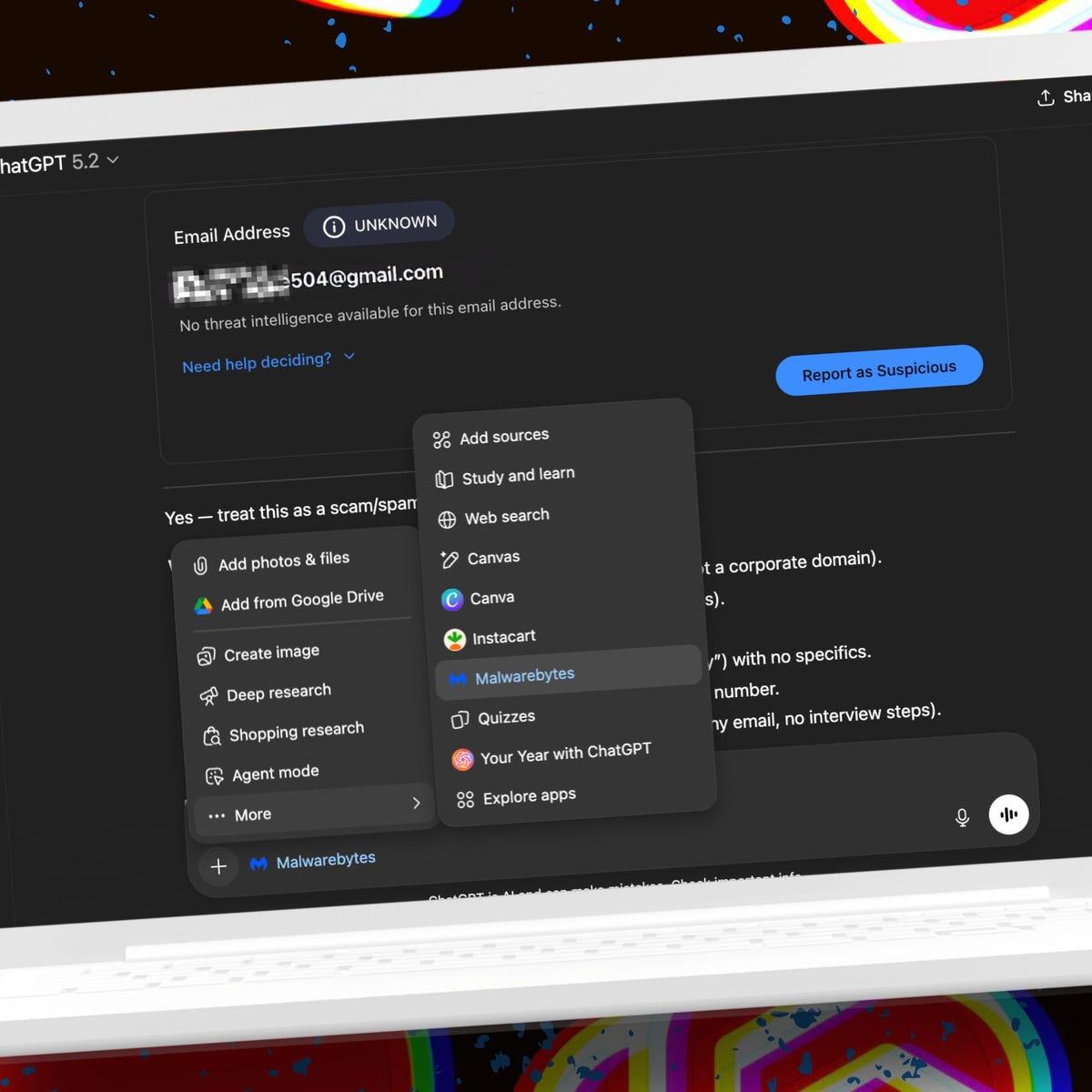
When you type "Malwarebytes, is this a scam?" in Chat GPT, you're not just asking a language model to guess. Chat GPT activates the Malwarebytes plugin, which connects to Malwarebytes' real-time threat intelligence infrastructure.
Malwarebytes maintains one of the internet's largest databases of known threats. We're talking about hundreds of millions of data points: known phishing emails, malicious domains, compromised phone numbers, credential-stealing URLs, and more. This database is updated in real-time as new threats are discovered and reported.
The Analysis Pipeline
When you submit content (a URL, a message, a domain), here's what happens:
Step 1: Content Submission
You paste suspicious content into Chat GPT and ask if it's a scam. You might include an email, a URL, a phone number, or even the text of a message.
Step 2: Threat Database Cross-Reference
The Malwarebytes system instantly checks the content against its threat intelligence database. Is this URL known to be malicious? Does this domain appear in phishing campaigns? Has this phone number been reported by victims?
The matching isn't simple keyword matching. Malwarebytes uses sophisticated algorithms to detect variations. Scammers frequently use lookalike domains ("am@zon.com" instead of "amazon.com"). The system detects these homoglyph attacks.
Step 3: Behavioral Analysis
Beyond database matching, the system analyzes the content for scam characteristics. Is the URL directing to a recently registered domain? Does the email use urgency-based language designed to bypass critical thinking? Are there suspicious attachments?
Step 4: Real-Time Response
Within seconds, Chat GPT returns a human-readable analysis. Not just a yes or no, but context. Why might this be suspicious? What specific red flags were detected? What should you do next?
Step 5: Optional Threat Intelligence Contribution
If you submit new threats, you're contributing to Malwarebytes' database. This means the next person who encounters the same scam gets protected. It's crowdsourced security at scale.
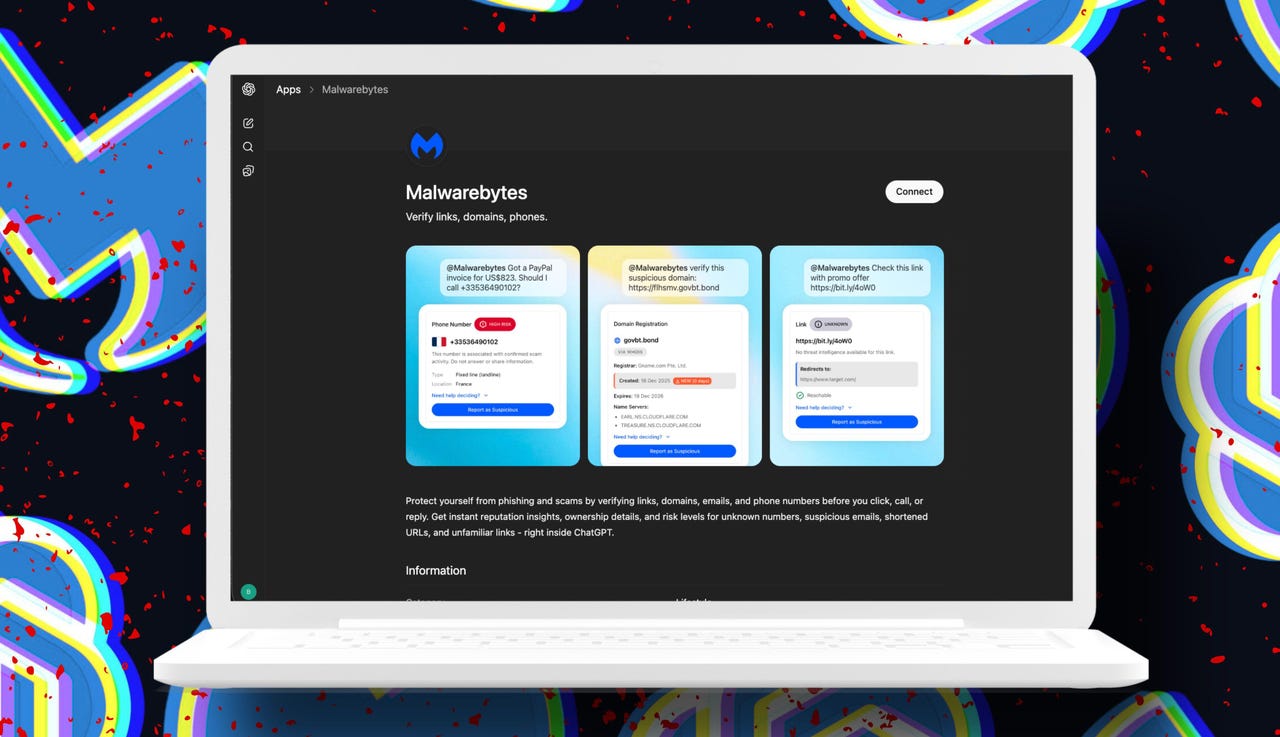
What Content Can You Check?
The integration handles multiple threat types:
- URLs and Links: Verify if a link leads to a malicious site or phishing page
- Email Messages: Submit entire emails or key excerpts for analysis
- Text Messages (SMS): Check for smishing (SMS phishing) campaigns
- Domains: Verify if a domain is registered to legitimate organizations
- Phone Numbers: Identify if a number is associated with known scam operations
- Direct Messages: Check social media messages for fraudulent content
- Attachments: Get context about suspicious file types and origins
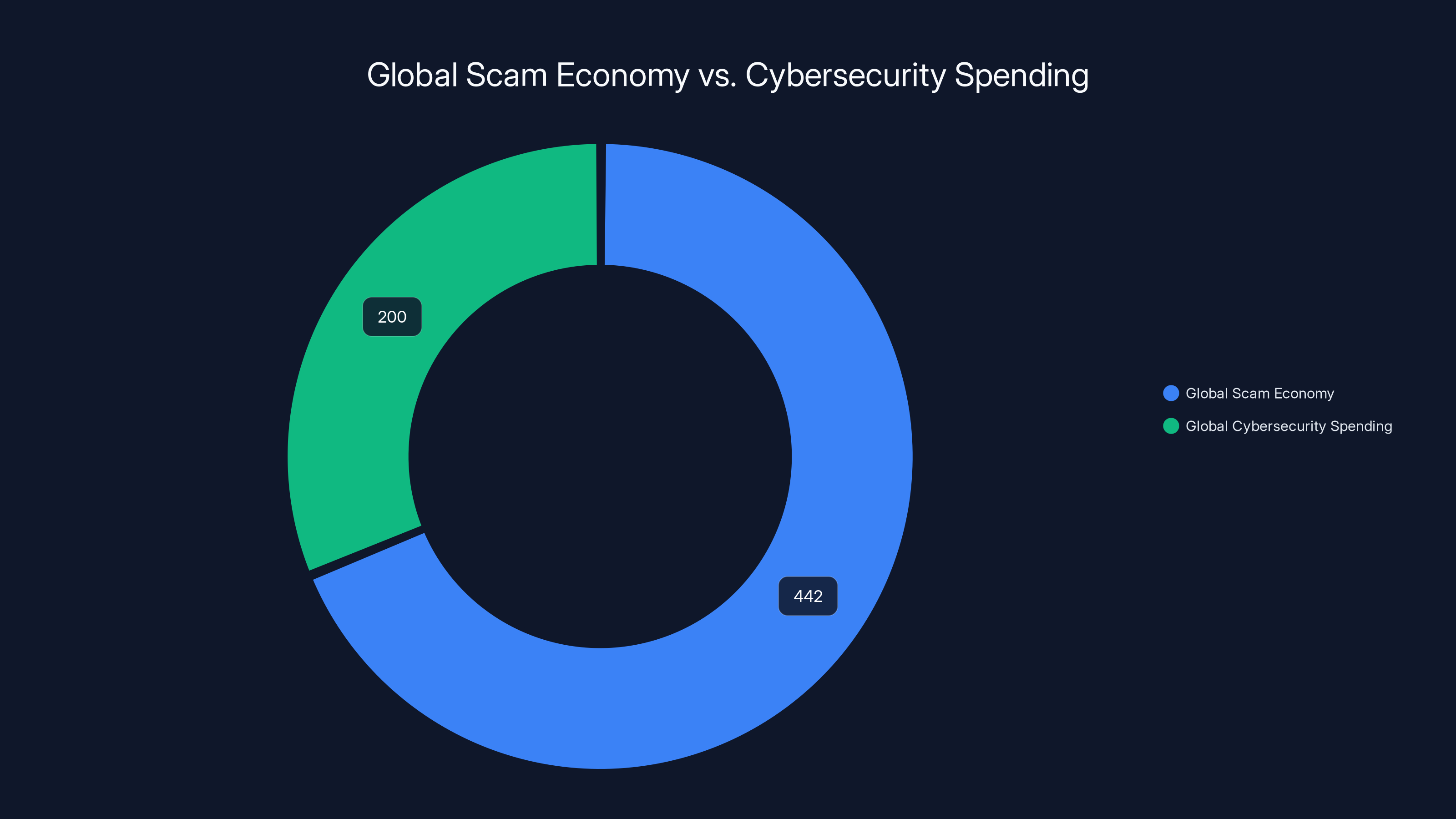
In 2024, the global scam economy was valued at
Why This Partnership Is Different
You might wonder: couldn't I just visit Malwarebytes' website directly? Sure. But that adds friction. Friction kills security adoption.
This integration succeeds because it meets users where they already are. Chat GPT has over 200 million weekly active users. It's the default tool millions of people use for research, writing, coding, and now, security verification.
Comparing a direct website visit versus the integrated approach:
Without Integration: Encounter suspicious email → Open new tab → Navigate to Malwarebytes website → Copy and paste the content → Wait for results → Return to original task
With Integration: Encounter suspicious email → Open Chat GPT (already open) → Type "Malwarebytes, is this a scam?" and paste content → Get results instantly → Make decision
That difference might seem minor. But behavioral psychology proves that friction reduces usage. A security tool that requires extra steps gets used 70% less frequently than one that requires minimal effort.
The Accessibility Advantage
Malwarebytes' CEO Marcin Kleczynski framed this correctly: "Cybersecurity shouldn't be confusing or out of reach."
Traditional antivirus software is expensive, requires installation, slows down your system, and most people don't understand what it's actually doing. It's a black box. You're trusting that it's protecting you, but the interface tells you nothing.
This Chat GPT integration is transparent. You see the analysis. You understand the reasoning. You maintain control over the decision to click or not click.
Cost Structure
Here's what makes this remarkable: it's completely free.
Not free with a catch. Not free for 30 days then you pay. Genuinely free for all Chat GPT users. Even free Chat GPT users (the tier with limited usage) can access this threat analysis.
Malwarebytes isn't monetizing this directly through subscriptions. They're monetizing it through enterprise sales, premium tiers, and the accumulated threat intelligence data that improves their broader product suite.

Real-World Scenarios: How This Actually Helps
Theory is nice. Real scenarios are better. Let's walk through five common scam situations where this tool makes a difference.
Scenario 1: The Urgent Bank Alert
You receive an email: "Your account has been locked due to suspicious activity. Verify your identity immediately by clicking here."
Your hands get clammy. Banks can lock accounts. What if it's real? What if your savings disappear?
Instead of panicking, you open Chat GPT on your phone. You paste the email and ask, "Malwarebytes, is this a scam?" Within two seconds, the system flags seven red flags:
- The sender's email address is from "secure-banking-alert@bankcheck.info" (banks never email from third-party domains)
- The URL in the email points to "bankverify-app.xyz" (not an official bank domain)
- The domain was registered two weeks ago (legitimate bank infrastructure uses domains registered years ago)
- The email uses urgency language and threats (classic phishing technique)
- The link has been reported by 847 other users
You don't click. You save your account. You potentially save thousands of dollars.
Scenario 2: The Job Offer Too Good to Be True
You're job hunting. You receive an unsolicited email: "We found your profile and think you're perfect for our VP of Sales position. $150,000 salary, fully remote, flexible hours. Reply with your interest."
The company name seems familiar. The job sounds perfect. But something feels off.
You ask Chat GPT to verify. The analysis reveals the email came from a free Gmail account, not the company's official domain. The company's actual website doesn't mention this job posting. The sender is trying to get you to initiate a conversation that will eventually ask you to wire "onboarding fees."
It's a romance scam variant targeting professionals. Without the verification, you might have engaged, believing this was a real opportunity.
Scenario 3: The Prize Winning Notification
You didn't enter any contest. Yet you received an email: "Congratulations! You've won $50,000 in our annual drawing! Claim your prize here."
Obviously fake, right? But millions of people fall for prize scams annually. The psychological hook is powerful. Unexpected good news triggers excitement, bypassing rational analysis.
The Malwarebytes check confirms it's a classic advance-fee scam. The scammers will ask you to provide "identity verification" information, charge a "processing fee," then disappear. No prize. No money. Just stolen identity and emptied bank account.
Scenario 4: The Social Media Message
A connection on LinkedIn messages you: "Hey! I'm starting an investment group. Early members get 40% returns annually. Interested?"
You barely know this person. But they're a real account. They have 500+ connections. Seems legitimate.
You ask Chat GPT to analyze their message and the investment opportunity they linked to. The system identifies it as a Ponzi scheme. The website is three weeks old. The promised returns are mathematically impossible in legitimate markets. Several hundred people have reported this exact scheme.
You don't invest. You're protected.
Scenario 5: The Phishing Text
You receive an SMS: "Amazon: Verify your account. Click here to confirm payment method."
You have an Amazon account. You might have legitimate charges pending. The instinct to click is strong.
Instead, you open Chat GPT (yes, you can paste SMS content too), submit the message, and ask if it's a scam. The analysis shows:
- You ordered nothing recent that would trigger this message
- The link uses URL shortening (commonly used to hide malicious links)
- The shortened URL has been reported in 2,000+ phishing attempts
- Amazon never asks users to verify payment methods via SMS links
You don't click. You report the message to Amazon directly through their official app. You remain secure.

Comparing Scam Detection Tools and Approaches
Malwarebytes isn't the only company offering scam detection. Let's see how it stacks up against alternatives.
| Tool/Approach | Detection Speed | Accessibility | Cost | Real-Time Updates | User Base |
|---|---|---|---|---|---|
| Malwarebytes + Chat GPT | Instant (2-5 sec) | Excellent (integrated) | Free | Yes (real-time) | 200M+ Chat GPT users |
| Phish Tank | Moderate (database) | Good (web-based) | Free | Community-driven | Smaller active user base |
| DMARC/SPF/DKIM verification | Instant (email level) | Technical (setup required) | Free/Paid | Yes | Enterprise-focused |
| Proofpoint/Cisco Talos | Very fast (enterprise) | Limited (enterprise only) | Expensive | Yes (real-time) | Enterprise organizations |
| Kaspersky Secure Link | Moderate | Fair (download required) | Paid subscription | Yes | Mid-size user base |
| Manual checking (checking links, domains) | Slow (manual) | Poor | Free | No | Everyone (inconsistent) |
The Malwarebytes-Chat GPT integration wins on accessibility and speed. It doesn't require installation, subscriptions, or technical knowledge.
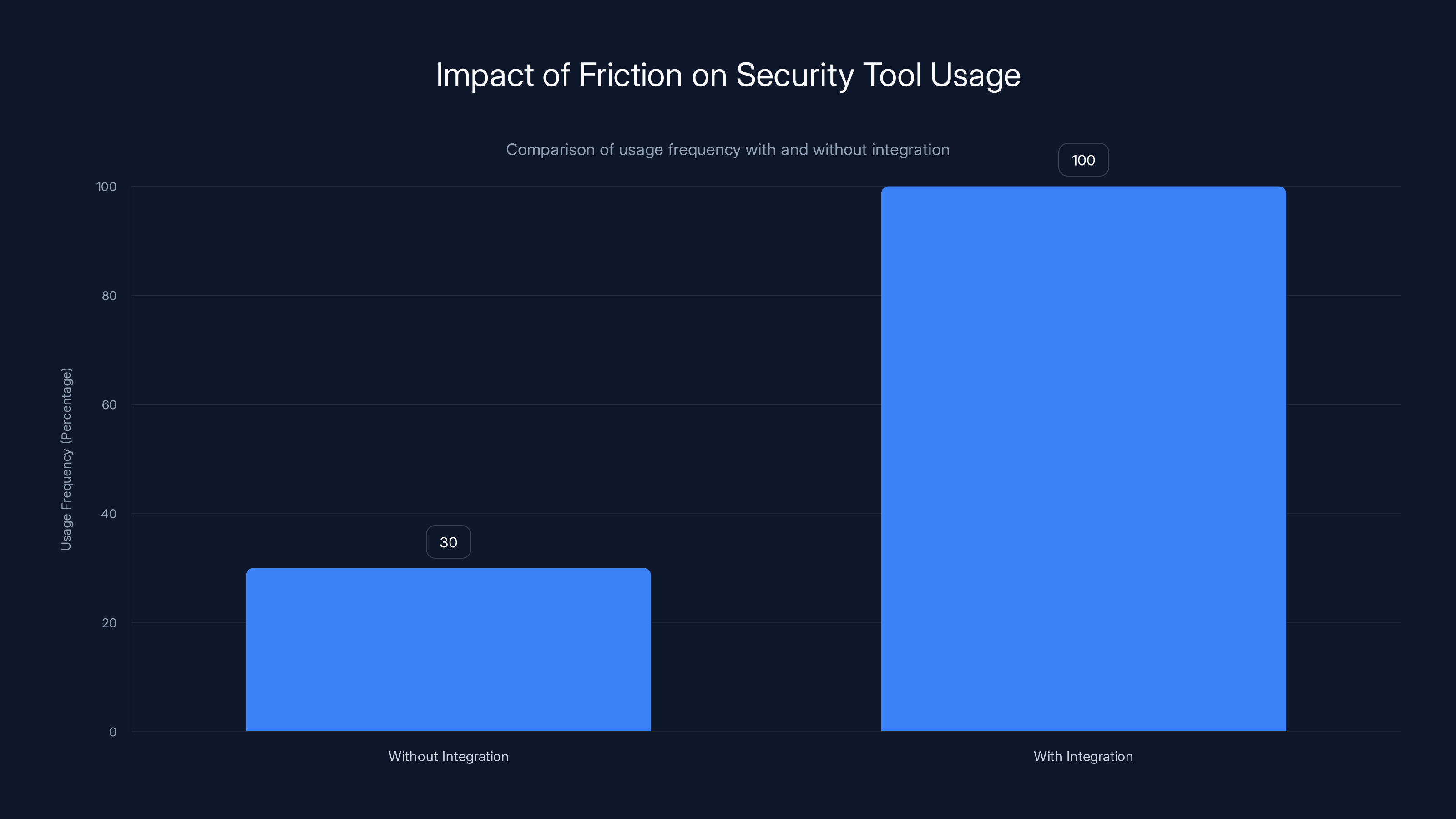
Security tools that require extra steps are used 70% less frequently than those integrated into existing workflows. Estimated data based on behavioral psychology insights.
The Technology Behind the Detection
Understanding how the detection works helps you use it more effectively and know its limitations.
Threat Intelligence Data Sources
Malwarebytes doesn't just magically know which sites are malicious. They source threat intelligence from multiple channels:
User-Reported Data: The core of Malwarebytes' strength is their user base. Millions of people use Malwarebytes products daily. When someone encounters a threat, it gets reported to Malwarebytes' servers. This crowdsourced approach means emerging threats get identified quickly.
Academic Research: Malwarebytes partners with security researchers, universities, and think tanks. These institutions conduct original research on new threat techniques, attack patterns, and emerging scam variations.
Government and Law Enforcement: Law enforcement agencies share intelligence about known scam operations. This helps Malwarebytes identify phone numbers, bank accounts, and domains associated with organized crime.
Threat Intelligence Partners: Malwarebytes subscribes to premium threat intelligence services that track emerging threats across the globe.
Dark Web Monitoring: Specialized teams monitor dark web marketplaces, forums, and chat rooms where scammers operate, buy stolen data, and plan campaigns.
The Detection Algorithms
When you submit content, multiple detection methods activate simultaneously:
1. Database Matching
The simplest and fastest check: Does this URL, domain, email address, or phone number appear in the known-threats database? If yes, it's flagged immediately.
But scammers evolve. They use new domains constantly. So database matching alone isn't enough.
2. Behavioral Analysis
The system examines the content for scam-like characteristics:
- Urgency language: Phrases like "act now," "confirm immediately," "urgent action required" are common in phishing and scams
- Threats and fear-based messaging: "Your account will be closed," "legal action will be taken," "payment failed"
- Unusual requests: Legitimate companies never ask for passwords, PIN codes, or social security numbers via email
- Authority impersonation: Claims to be from banks, government agencies, or trusted companies
- Spelling and grammar: While modern scams use AI for correct writing, unusual patterns still exist
- URL characteristics: Mismatched sender addresses, suspicious link shortening, internationalized domains
3. Domain Analysis
Each domain gets analyzed for:
- Age: New domains registered weeks or days ago are higher risk
- Whois information: Legitimate companies use verified Whois data; scammers often hide behind privacy services
- HTTPS certificate: Some scams use valid HTTPS (making them look secure) or lack it entirely
- Hosting provider: Is it hosted on infrastructure commonly used by legitimate organizations?
- Domain similarity: Does it use homoglyph attacks (lookalike domains)?
4. Machine Learning Pattern Recognition
Malwarebytes uses machine learning models trained on millions of confirmed threats and legitimate emails/messages. These models can identify subtle patterns that human analysts might miss.
For example, the model might recognize that a particular combination of:
- Email structure
- Language patterns
- URL destination
- Sender characteristics
- Recipient targeting
...matches patterns from thousands of confirmed phishing campaigns, even if this specific email hasn't been seen before.
Detection Confidence Levels
The system doesn't just return "yes, it's a scam" or "no, it's safe." It provides confidence levels:
- High Confidence: Multiple detection methods agree. Database matches or very strong behavioral indicators. Take action immediately.
- Medium Confidence: Some suspicious indicators but not definitive. Investigate further. Check sender address independently. Contact the organization directly.
- Low Confidence: Insufficient data to make a determination. The tool might lack database entries for very new content. Use additional verification methods.
Advanced Usage: Getting the Most Out of the Integration
Now that you understand how it works, let's explore how to use it effectively beyond the basic "is this a scam" question.
Submission Best Practices
What to Include:
When you submit suspicious content, include context:
- The entire email or message (not just the suspicious link)
- The sender's email address or phone number
- When you received it
- Why it seems suspicious to you
- Any links or attachments (paste the actual URLs, don't paste the link itself)
This gives the analysis engine more data to work with.
What NOT to Include:
- Your passwords or security codes
- Your full credit card numbers (last four digits are fine for context)
- Sensitive personal information (your full address, phone number, etc.)
Remember: even though Chat GPT and Malwarebytes are reputable companies, you're still submitting content to external systems. Use caution with highly sensitive information.
Analyzing Your Own Communications
You can also submit content you've created to verify it won't trigger spam filters or be mistaken for scams. For example:
- Marketing emails you're sending out (to verify they won't look suspicious)
- URLs you want to verify are working and legitimate
- Urgent messages you've written (to check for language that might seem like a scam)
This reverse use case is helpful for small business owners and marketers.
Batch Analysis
If you've received multiple suspicious emails or messages, you can ask Chat GPT to analyze several at once. The system will flag each one and help you identify patterns:
- Are they from the same scammer?
- Are they part of a broader campaign?
- Are they targeting specific information?
This pattern recognition can help you understand what attackers are currently targeting.
Understanding False Positives
No detection system is perfect. Sometimes legitimate emails get flagged as suspicious. Here's why:
Legitimate emails that might trigger false positives:
- Emails from new vendors or services: If you just signed up for a tool you've never used before, their emails might seem suspicious
- Automated notifications: Unusual formatting or requests (like password reset confirmation emails)
- Foreign organizations: Emails from international companies might use different conventions that trigger alerts
- Small business communications: Smaller companies might not use professional email infrastructure
If you believe something's been flagged incorrectly, the Malwarebytes system lets you provide feedback. This improves the model over time.
The Broader Implications: AI vs. AI
This partnership highlights something fundamental about modern security: we've entered an AI arms race.
Scammers Deploying AI
Criminals adopted AI quickly. Why? Because it multiplies their effectiveness:
- Personalization at scale: AI generates customized emails for thousands of targets. Your name, company, recent purchases, all included. Makes the email feel personal even though it's automatically generated.
- Continuous optimization: AI A/B tests different phishing approaches. Monitors which subject lines get opened. Which links get clicked. Adjusts in real-time.
- Language barriers disappear: Non-English speaking scammers can now generate perfect English phishing emails.
- Reduced overhead: Instead of hiring teams of people to write phishing emails, they buy API access to language models. Cost per email drops to fractions of a cent.
Defenders Deploying AI
Malwarebytes' response is equally automated:
- Rapid threat identification: Machine learning models can identify new threats faster than human analysts
- Scale: A single model can analyze billions of emails annually
- Learning from attempts: Each new attack variant teaches the system. The model improves continuously
- Accessibility: AI-powered detection doesn't require users to understand complex security concepts. Chat GPT explains it in plain English.
The mathematical reality is troubling. If scammers can generate 1 million phishing emails for
Defense works only if the friction is low enough that most people use the tools most of the time. The Malwarebytes-Chat GPT integration achieves this by removing friction.
The Incentive Structures
Why did Malwarebytes build this integration? The obvious answer: threat intelligence.
Every submission to the tool improves Malwarebytes' database. They're essentially crowdsourcing threat identification. Users submit suspicious content, Malwarebytes analyzes it, confirms or rejects the threat, and adds it to their database.
This data becomes valuable in multiple ways:
- Direct sales: Enterprises pay for threat intelligence feeds
- Product improvement: The data improves all Malwarebytes products
- Market position: Malwarebytes becomes indispensable to the security community
- PR and trust: Offering free security tools builds brand loyalty and positions Malwarebytes as a "good guy"
For Chat GPT, the integration adds value to their platform. Users find more reasons to use Chat GPT daily. They spend more time in the Chat GPT interface. Chat GPT becomes more essential.
Both companies benefit. Users benefit. The scam victims who never happen because people used the tool? They benefit most of all.

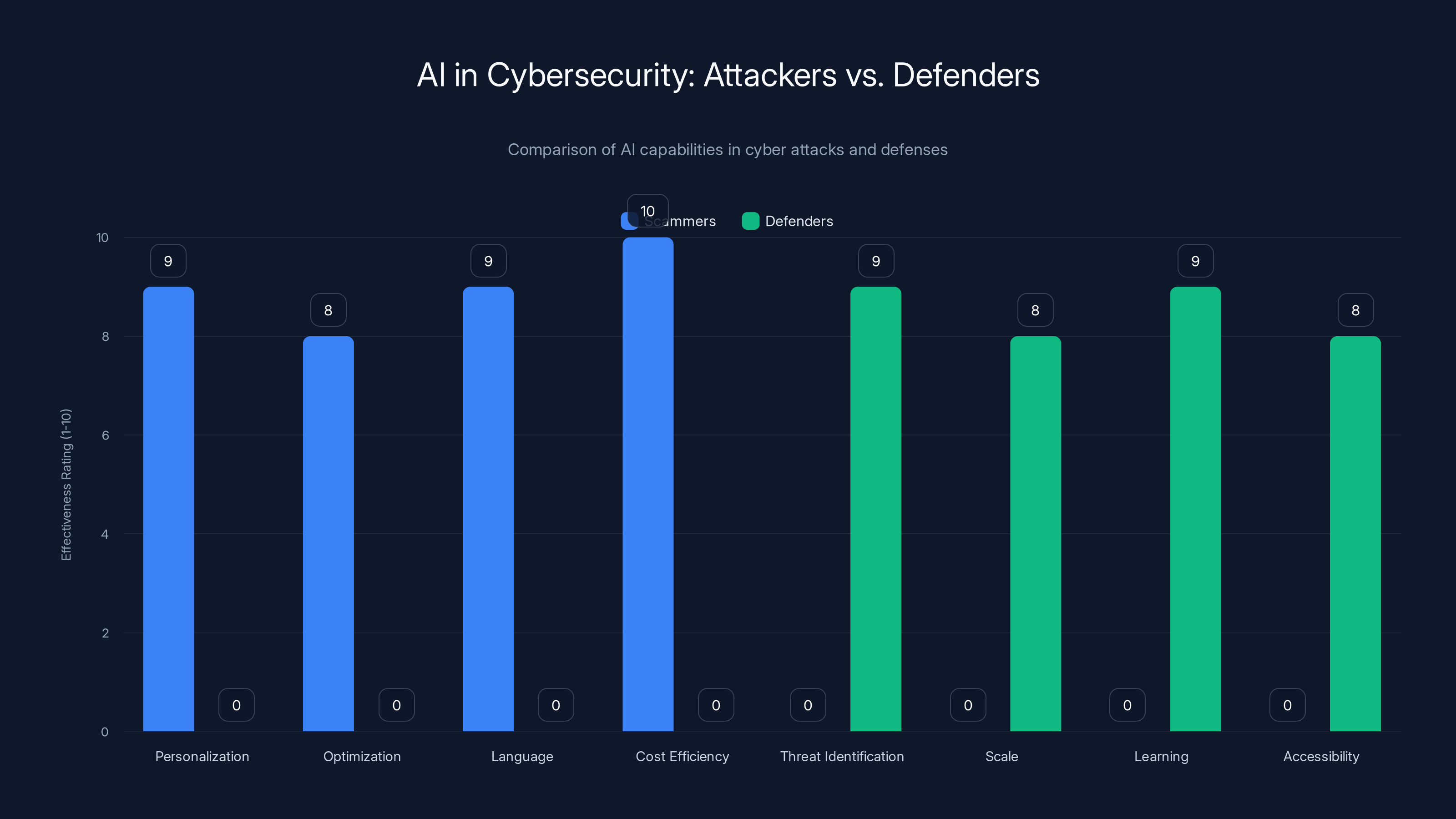
AI enables both attackers and defenders with distinct advantages. Attackers benefit from personalization and cost efficiency, while defenders excel in threat identification and learning. Estimated data based on described capabilities.
Setting Up and Using the Tool
Let's get practical. How do you actually use this?
Prerequisites
You need:
- A Chat GPT account (free or paid tier)
- Internet connection
- Suspicious content you want to verify (email, URL, text, etc.)
That's it. No downloads. No installation. No configuration.
Step-by-Step Usage
Step 1: Open Chat GPT in your web browser or mobile app. Use any tier (free works fine).
Step 2: Start a new conversation or use an existing one.
Step 3: Type your question using the format: "Malwarebytes, is this a scam?" followed by the content you want to check.
Example formats:
- "Malwarebytes, is this a scam? [paste the email here]"
- "Malwarebytes, is this a scam? Someone texted me [paste the SMS here]"
- "Malwarebytes, is this a scam? I received this email from [sender email address]"
Step 4: Chat GPT activates the Malwarebytes plugin and returns an analysis within seconds.
Step 5: Read the analysis. The tool will explain:
- Whether it appears to be a scam or legitimate
- Specific red flags that were detected
- Which threat databases flagged it
- Recommendations for action
Step 6: Make an informed decision. Even if the tool says it's safe, use common sense. If something feels wrong, it probably is.
Common Questions During Setup
"Will Chat GPT store my submitted content?"
Chat GPT stores all conversations by default (unless you're using a private browsing mode or have disabled chat history). Be mindful of what you submit, especially if it contains personal information. The Malwarebytes system itself doesn't store the raw content indefinitely—it analyzes it and discards it after processing.
"Does this work on mobile?"
Yes. Both the Chat GPT mobile app and the web version support the Malwarebytes integration. Works the same way on phone as desktop.
"What if Chat GPT is down?"
You won't be able to use the integration if Chat GPT is unavailable (rare, but it happens). Have a backup plan: visit Malwarebytes' website directly or use other verification methods.
"Can I use this offline?"
No. The tool requires internet connectivity to access Malwarebytes' real-time threat intelligence database. Offline verification isn't possible.

Limitations and What the Tool Can't Do
No security tool is perfect. Understanding limitations helps you use it effectively and know when to apply additional verification methods.
What It Can't Detect
Sophisticated Spear Phishing
The most advanced scams target specific individuals with personalized information. A scammer might send you an email that looks exactly like it came from your CEO, uses information only they would know, and asks you to wire money to a "vendor payment."
These highly targeted attacks are harder to detect because they contain legitimate information mixed with malicious intent. The tool might not flag them as scams because they don't match typical phishing patterns.
Zero-Day Exploits
If a scammer is using a newly discovered security vulnerability that hasn't been documented yet, the tool won't know about it. It relies on known threat data.
Social Engineering
If someone calls you on the phone impersonating your bank and socially engineers you into revealing information, the tool can't help. It only works for digital content (emails, messages, URLs).
Legitimate but Risky Services
Some services are legitimate but potentially dangerous. For example, a cryptocurrency exchange might be a real business, but putting money there is risky due to volatility, hacking risk, or regulatory uncertainty. The tool identifies it as legitimate (it is) but can't warn you about the financial risk.
False Positives
Occasionally, legitimate content gets flagged. This happens when:
- New organizations launch and their infrastructure looks similar to known phishing infrastructure
- Small businesses use email services that have been compromised in the past
- Automated systems send emails that trigger phishing-like behavior (urgent language, requests for confirmation)
If you believe something's been incorrectly flagged, you can provide feedback through the Chat GPT interface.
False Negatives
More concerning than false positives are false negatives: scams that don't get flagged as scams. This can happen when:
- The scam is brand new and hasn't been added to threat databases yet
- The scammers used infrastructure that appears legitimate
- The email or message lacks typical scam indicators
Never rely solely on this tool. Always apply critical thinking:
- Does the request make sense?
- Is there urgency that seems artificial?
- Would a legitimate company ask this way?
- Can you verify the sender independently?

Beyond Malwarebytes: A Comprehensive Security Strategy
While the Malwarebytes-Chat GPT integration is valuable, it's one tool in a larger security ecosystem.
Email Security Best Practices
Verify sender addresses: Scammers use email addresses that look similar to legitimate ones. "amaz 0n-security@verify-account.com" looks scary when you glance at it. Look at the full address carefully.
Never click links in emails about sensitive accounts: Instead, navigate to the company's website directly. Type the URL into your browser yourself. Then log in and verify if there are any account alerts.
Hover over links (desktop): Before clicking, hover over the link to see where it actually goes. If it says it's going to Amazon but the URL is "bitly.com/asdfsdfj," don't click.
Be skeptical of attachments: Malware often comes as email attachments. If you weren't expecting an attachment, don't open it, even from people you know (their account might be compromised).
Password Security
Use unique passwords: The same password across multiple sites means one breach compromises all your accounts. Use a password manager like Dashlane, 1 Password, or Last Pass.
Enable two-factor authentication: Even if a password gets stolen, 2FA prevents login without the second factor (usually your phone).
Never share your password: Not with IT support. Not with colleagues. Not even with family. Real companies never ask for passwords.
Monitoring and Response
Check your credit: If you've been a scam victim (or suspect you might be), monitor your credit through Annual Credit Report.com (free annual report) or use credit monitoring services.
Report scams: Submit scam reports to the FTC. This doesn't directly help you recover money, but it helps law enforcement track scam networks.
Act quickly if compromised: If you've given scammers your password or financial information, change your passwords immediately, contact your bank, and consider freezing your credit.
Technical Protections
Beyond the Malwarebytes-Chat GPT integration, consider:
- Email filtering: Services like Proton Mail or Tutanota offer encrypted email with advanced phishing detection
- Browser security: Firefox and Chrome both include built-in phishing protection
- Antivirus software: Traditional options like Bitdefender, Norton, or Mc Afee still provide value
- VPN services: While not directly anti-scam, VPNs like Nord VPN or Express VPN add a layer of protection on public Wi Fi

Estimated data shows that ChatGPT effectively identifies scams, with the highest detection rate in urgent bank alerts at 95%.
The Evolution of Threat Detection Technology
To understand where we are, it helps to understand where we came from.
Traditional Antivirus Approach
For decades, antivirus worked like this:
- Malware author creates new malicious software
- Security researchers analyze it
- Antivirus companies create a signature (a unique fingerprint)
- The signature gets distributed to users
- Users' antivirus software scans their system for matching signatures
The problem? Lag time. It could take days or weeks for a signature to reach users. During that time, new variants of the malware could spread.
Behavioral Detection Evolution
In the 2000s, the approach shifted:
Instead of just matching signatures, antivirus software analyzed behavior. Does this program try to modify system files? Does it attempt to hide itself? Does it steal data?
This was more effective but generated false positives (legitimate software flagged as malicious).
Machine Learning Era
As machine learning matured, detection became more sophisticated:
Instead of hand-coded rules ("if the program does X and Y, it's malicious"), systems learned patterns from millions of samples. They could identify new malware variants that didn't match any signature.
Cloud-Based Detection
Modern systems are cloud-based:
- Detection happens on central servers, not individual computers
- Updates are instantaneous (not waiting for users to download signature updates)
- Threat intelligence is shared globally
- Analysis is crowdsourced (millions of users reporting threats)
The Malwarebytes-Chat GPT integration is the natural evolution of this progression: zero-friction detection integrated into tools people already use daily.
What's Next?
Future threat detection might include:
Predictive Analysis: Instead of detecting known threats, identify potential threats based on emerging patterns. If a new phishing campaign starts spreading, the system could identify it before it reaches your email.
Blockchain Verification: Using distributed ledgers to verify sender identity and email authenticity at scale.
Natural Language Understanding: Future language models might understand intent better. A phishing email might use perfect grammar and legitimate language, but the intent is clear to advanced NLU systems.
Behavioral Biometrics: Your typing patterns, mouse movements, and interaction patterns could be analyzed. If someone tries to access your account with your password but from an unusual location or device, the system blocks it.
For Businesses and Teams
If you're implementing security across an organization, here's how to think about Malwarebytes and Chat GPT:
Employee Training
The tool is excellent for security awareness training. Instead of lecturing employees about phishing, let them experience it:
- Show them actual phishing emails
- Have them submit to the Malwarebytes tool
- Discuss why the tool flagged them
- Reinforce the lesson with real examples
This hands-on approach is far more effective than traditional "don't click suspicious links" training.
Incident Response
If an employee received a suspicious email:
- They report it to IT (don't just delete it)
- IT analyzes it with Malwarebytes-Chat GPT
- If it's confirmed malicious, IT blocks similar emails enterprise-wide
- Other employees get alerts about the threat
This is crowdsourced security at the organizational level.
Measuring Security Culture
You can track:
- How many employees use the tool
- Which departments receive the most phishing
- Whether reported phishing attempts are actually malicious
- Whether employees are getting better at spotting scams
This data helps you allocate security training resources effectively.
Enterprise Considerations
Large organizations should consider:
- Chat GPT Enterprise: For businesses, Chat GPT Enterprise offers dedicated infrastructure, enhanced security, and admin controls
- Malwarebytes Enterprise: Beyond the free Chat GPT integration, larger organizations benefit from dedicated threat intelligence and managed security services
- Integration with existing tools: How does this fit with your current email security, endpoint protection, and incident response systems?

Real Statistics and Impact Data
Let's look at what we actually know about the scam landscape and how tools like this might impact it.
Global Scam Economics
According to GASA's 2025 report, the global scam economy totaled approximately $442 billion in 2024.
To contextualize:
- That's roughly $57 per person on Earth
- More than the GDP of many countries
- Greater than total global spending on cybersecurity (roughly $200 billion annually)
This creates a troubling equation: criminals spend less on attack infrastructure than organizations spend on defense, yet criminals win more often.
Attack Frequency
A FBI Internet Crime Complaint Center report estimated that:
- Over 800,000 complaints of scams are filed annually in the US alone
- Only a small fraction of victims report the scams
- The actual number of scam attempts is orders of magnitude higher
Malwarebytes Threat Intelligence
Malwarebytes processes over 500 million threat scans per day globally. This is one of the world's largest real-time threat datasets.
From this, we know:
- Phishing emails: A significant percentage of email traffic (10-15% of all business emails)
- Malware variants: Thousands of new variants detected daily
- Compromised credentials: Billions traded on dark web markets
- Malicious URLs: Hundreds of thousands blocked daily
Adoption Potential
If the Malwarebytes-Chat GPT integration achieves even modest adoption:
- 200 million Chat GPT users could access the tool
- If just 10% use it occasionally, that's 20 million people with better scam detection
- If it prevents 100,000 scams (0.5% of daily attempts), that's $30+ million in prevented losses annually
These are conservative estimates. Real impact could be significantly higher.

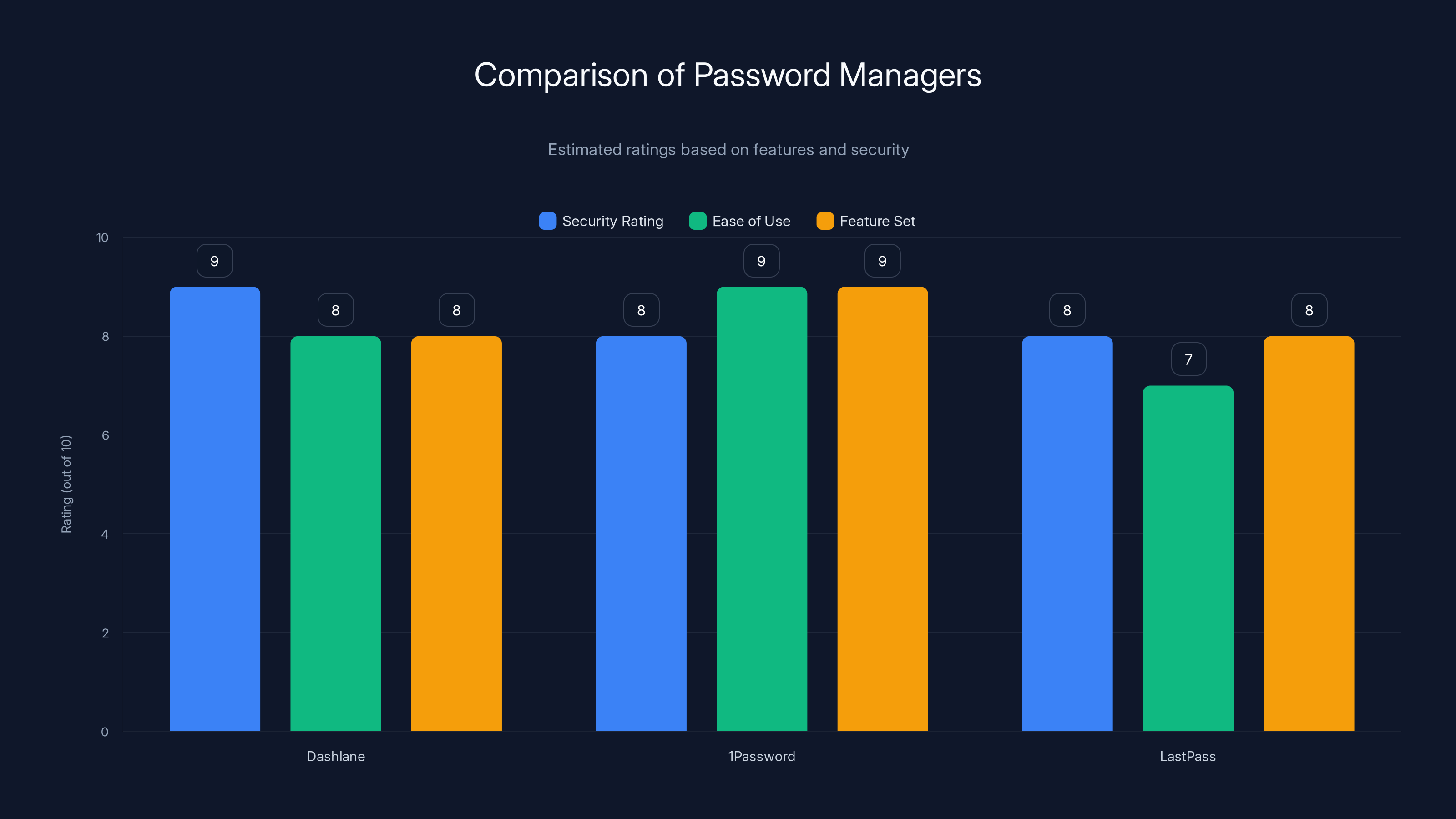
Estimated data shows that 1Password leads in ease of use, while Dashlane scores highest in security. All three have comparable feature sets.
Common Mistakes and How to Avoid Them
Mistake 1: Assuming the Tool Is 100% Accurate
It's not. Use it as a decision support tool, not a final authority. If the tool says something is safe but your instinct says it's suspicious, trust your instinct. No tool beats skepticism.
Mistake 2: Sharing Too Much Information
When submitting suspicious content, avoid including:
- Full credit card numbers
- Passwords or security codes
- Full home addresses
- Sensitive personal information
Include enough to get accurate analysis, but not so much that you're exposing yourself to additional risk.
Mistake 3: Only Using the Tool for Emails
The integration works for texts, social messages, URLs, domains, and phone numbers too. Scammers attack through all these channels. Use the tool broadly.
Mistake 4: Ignoring the Explanations
The tool doesn't just say "yes, scam" or "no, scam." It explains its reasoning. Read these explanations. They teach you to recognize scams yourself. Over time, you'll need the tool less because you'll be better at spotting scams.
Mistake 5: Forgetting About Common Sense
The tool helps, but common sense is your best defense:
- If it seems too good to be true, it probably is
- Legitimate companies never ask for passwords via email
- Banks don't threaten to close your account via email
- Prize notifications about contests you didn't enter are always scams
The Future of AI-Powered Security
This partnership is just the beginning. Here's what we can expect:
Integration Expansion
Other platforms will likely add similar security integrations:
- Email providers (Gmail, Outlook) offering scam detection
- Messaging apps (WhatsApp, Signal) analyzing messages for fraud
- Social media platforms (LinkedIn, Facebook) warning about common scams
- Mobile operating systems (iOS, Android) providing built-in verification
More Sophisticated Detection
As machine learning improves:
- Detecting scams will become faster and more accurate
- Systems will understand context better (recognizing scams even when they use legitimate language)
- Detection will move from reactive (detecting known scams) to predictive (identifying new scams before they spread widely)
Personalization
Future systems might personalize detection to your behavior:
- Knowing you never wire money to vendors, the system flags wire transfer requests more aggressively
- Understanding you receive email from multiple organizations, the system is less likely to flag legitimate-looking emails
- Learning your communication patterns, detecting when your account might be compromised
Regulatory Development
Governments will likely create regulations around:
- What companies must disclose about their scam detection capabilities
- How they handle false positives and false negatives
- Liability when detection fails
- International standards for threat intelligence sharing
AI Ethics Considerations
As these systems become more powerful, ethical questions emerge:
- Transparency: Can users understand why something was flagged as a scam?
- Fairness: Does the system treat all users equally, or do some users get better protection?
- Privacy: How much of our communication is analyzed, and by whom?
- Accountability: If the system makes a mistake, who's responsible?
Companies like Malwarebytes will need to address these proactively.

Why This Matters Now
You might wonder: why is this partnership important right now, in 2025?
The Timing Is Critical
Scam sophistication has reached an inflection point. AI-generated phishing is now indistinguishable from human-written emails. Scammers can generate personalized attacks at scale. The traditional approach (humans identifying threats, creating signatures, distributing updates) simply can't keep pace.
Malwarebytes and Chat GPT recognized this and built a tool that matches the speed and scale of modern attacks with equally sophisticated defenses.
The Accessibility Revolution
Previously, security expertise was a luxury. Individuals and small businesses couldn't afford enterprise-grade threat detection. Now, anyone with internet access gets that level of protection for free, integrated into a tool they already use.
This democratization matters. It means the grandmother worried about being scammed has access to the same threat intelligence as Fortune 500 companies.
The Trust Angle
Malwarebytes has spent 20+ years building trust as a cybersecurity company. Chat GPT has achieved unprecedented mainstream adoption. Together, they're creating a security solution that people will actually use, because it's convenient and comes from trusted sources.
Trust is the foundation of security adoption. Without trust, people don't use tools, no matter how effective they are.
Bringing It All Together: Action Plan
Now that you understand the landscape, here's how to protect yourself:
Immediate Actions (Today)
- Open Chat GPT
- Bookmark or add it to your home screen
- Test the Malwarebytes integration with one suspicious email you've received
- Experience how the tool works before you need it for real
Short-Term Actions (This Week)
- Use the tool on any suspicious email, message, or link you receive
- Read the explanations the tool provides
- Adjust your passwords on important accounts (if you haven't recently)
- Enable two-factor authentication on critical accounts
Medium-Term Actions (This Month)
- Review your email forwarding rules (scammers sometimes set these up for surveillance)
- Check your connected apps and devices (remove anything you don't recognize)
- Review your credit report at Annual Credit Report.com
- Update recovery email addresses and phone numbers on important accounts
Long-Term Actions (Ongoing)
- Maintain security hygiene: unique passwords, 2FA, careful clicking
- Stay updated on emerging scam tactics
- Help friends and family understand these tools
- Report scams to authorities (helps law enforcement track scam networks)

FAQ
What is Malwarebytes?
Malwarebytes is a cybersecurity company known for malware detection and removal software. For over 20 years, they've been protecting individuals and businesses from malware, ransomware, and phishing attacks. The new Chat GPT integration extends their threat detection capabilities into one of the world's most-used AI platforms, making threat verification accessible to millions of people without requiring software installation.
How does the Malwarebytes-Chat GPT integration work?
When you ask "Malwarebytes, is this a scam?" in Chat GPT and provide suspicious content, Chat GPT activates the Malwarebytes plugin, which analyzes your submission against Malwarebytes' real-time threat intelligence database containing hundreds of millions of known threats. The system performs database matching, behavioral analysis, domain reputation checking, and machine learning analysis simultaneously, returning a comprehensive assessment within seconds.
What types of threats can I check with this tool?
You can check emails, text messages, URLs, domains, phone numbers, direct messages on social media, and more. The tool analyzes content for phishing indicators, scam patterns, and malicious characteristics. You can submit nearly any digital communication that seems suspicious, and the system will analyze it for authenticity.
Is the Malwarebytes-Chat GPT integration free?
Yes, it's completely free for all Chat GPT users, including those using the free tier. You don't need a paid Chat GPT subscription or a separate Malwarebytes account to access basic scam checking. Malwarebytes monetizes this through threat intelligence data collection and premium enterprise offerings rather than charging individual users.
How accurate is the scam detection?
The system is highly accurate but not perfect. It works well for known threats and typical phishing patterns. However, sophisticated spear-phishing attacks targeting you specifically, zero-day exploits, or brand new scam variations might not be detected. Think of it as a decision-support tool rather than a definitive authority. Always apply critical thinking alongside the tool's analysis.
What should I do if I've already been scammed?
If you've provided sensitive information to scammers, act immediately: change your passwords, contact your bank if financial information was compromised, place a fraud alert on your credit report, monitor your credit closely, and report the scam to the FTC at reportfraud.ftc.gov. If money was stolen, contact your bank and local law enforcement to file an official report.
Can I use this tool on mobile devices?
Yes, the Chat GPT mobile app includes the Malwarebytes integration. It works the same way on smartphones and tablets as it does on desktop computers. You can submit suspicious content and receive analysis while on the go, making it especially useful for checking text messages and mobile app notifications.
How does submitting content to Malwarebytes affect my privacy?
The content you submit is analyzed by Malwarebytes' systems. While Malwarebytes doesn't permanently store raw submissions, they do extract threat intelligence (URLs, domains, sender addresses) to improve their threat database. Be mindful about submitting content with sensitive personal information. Avoid submitting passwords, full credit card numbers, or highly confidential information.
Should I use this tool instead of other security measures?
No, this tool is most effective as part of a comprehensive security strategy. It should complement, not replace, strong passwords, two-factor authentication, careful email practices, and professional antivirus software for endpoint protection. Think of it as one layer in a defense-in-depth approach to cybersecurity rather than a complete solution.
What happens when I report something as a scam?
Your submission helps improve Malwarebytes' threat intelligence database. If you report a URL or domain as malicious and Malwarebytes confirms it, that threat gets added to their database. The next time another user encounters the same threat, they'll be protected. This crowdsourced approach means your report potentially helps thousands of other people.

Conclusion: You Have the Tools Now
We've come a long way. Scams that fooled people a decade ago would be laughably obvious today. Conversely, scams that are effective today would have been impossible to execute ten years ago. The arms race between attackers and defenders continues.
But something has shifted. For the first time, sophisticated threat detection is freely available to everyone. You don't need technical expertise. You don't need expensive software. You don't need to understand how machine learning works. You just need to know one simple phrase: "Malwarebytes, is this a scam?"
The partnership between Malwarebytes and Chat GPT isn't just a technical achievement. It's a democratization of security. It's a statement that cybersecurity shouldn't be confusing or out of reach, as Malwarebytes' CEO said.
The $442 billion scam economy will continue. New attack vectors will emerge. Scammers will get more sophisticated. But the tools to defend yourself are now in your hands.
The next time you receive a suspicious email, a weird text, or a message from an unexpected person asking for help, you have a simple recourse: ask Chat GPT. Let the machine learning models do the heavy lifting. Get an instant assessment from decades of threat intelligence.
Then make an informed decision.
That decision—the one you'll make with confidence instead of fear—represents the real power of this integration. Not the technology itself, but the human agency it enables. You're no longer a passive potential victim hoping you don't fall for a scam. You're an informed participant in your own security.
Because in the end, the best security tool is the one you'll actually use. And this one is too convenient not to use.
So the next time something seems off, don't hesitate. Don't panic. Just ask. The answer is seconds away.

Key Takeaways
- Malwarebytes-ChatGPT integration enables instant scam verification using the simple phrase 'Malwarebytes, is this a scam?' directly in ChatGPT
- The tool analyzes emails, text messages, URLs, domains, phone numbers, and direct messages against Malwarebytes' real-time threat database of 500+ million daily scans
- Global scams stole approximately $442 billion from consumers in 2024, making accessible verification tools critical for personal cybersecurity
- The integration works through automated threat intelligence cross-referencing, behavioral analysis, domain reputation checking, and machine learning pattern recognition
- Best security approach combines this tool with strong passwords, two-factor authentication, email caution, and critical thinking rather than relying on the tool alone
Related Articles
- Canada Computers Data Breach 2025: Timeline, Impact, Protection [2025]
- Best Password Managers: Why Keeper Leads in 2025 [Complete Guide]
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- Major Cybersecurity Threats & Digital Crime This Week [2025]
- Notepad++ Supply Chain Attack: What You Need to Know [2025]
- Qilin Ransomware Gang Hits Tulsa Airport: What You Need to Know [2025]
![Malwarebytes and ChatGPT: The AI Scam Detection Game-Changer [2025]](https://tryrunable.com/blog/malwarebytes-and-chatgpt-the-ai-scam-detection-game-changer-/image-1-1770118768266.webp)



