The Notepad++ Supply Chain Attack: Inside the Chinese Government Hack That Compromised Millions
In late 2025, the developer of Notepad++, one of the world's most downloaded open-source text editors, made a stunning admission: hackers working for the Chinese government had successfully hijacked the software update mechanism for months. What started as a bug in shared hosting infrastructure evolved into a surgical, highly targeted cyberattack that delivered malicious code to specific organizations with interests in East Asia. According to SecurityWeek, this attack was a sophisticated operation that went largely unnoticed until December 2025.
This wasn't a ransomware campaign or a mass infection attempt. It was something far more sophisticated and worrying: a precision operation that gave attackers "hands-on" access to victim computers, the kind of access that intelligence agencies dream about. The attack went largely unnoticed until December 2025, when security researcher Kevin Beaumont stumbled upon evidence of the compromise and began connecting the dots, as reported by Help Net Security.
For anyone who works in cybersecurity, software development, or IT operations, the Notepad++ incident should hit hard. It represents a new category of threat: the selective supply chain attack. Unlike the Solar Winds breach of 2019-2020, which cast a wide net and infected thousands of organizations indiscriminately, the Notepad++ attack was surgical, deliberate, and almost invisible. The hackers didn't care about infecting everyone. They cared about infecting the right people.
This article breaks down exactly what happened, why it matters, and what it means for software security going forward. We'll cover the technical details of how the attack unfolded, the scale of potential damage, the parallels to past supply chain breaches, and most importantly, what organizations need to do right now to protect themselves.
TL; DR
- Chinese government hackers compromised Notepad++ between June and December 2025 by exploiting a vulnerability in shared hosting infrastructure to intercept and modify software updates, as detailed by CyberPress.
- The attack was highly selective, targeting specific organizations with interests in East Asia rather than attempting mass infection.
- Victims received malicious updates that granted attackers "hands-on" access to their computers, potentially allowing espionage or further network penetration, according to Rescana.
- The vulnerability was patched in November 2025, but attackers maintained access until early December when the breach was finally detected.
- This represents a new threat model: selective supply chain attacks that prioritize precision over scale, making detection far more difficult than mass-market compromises.

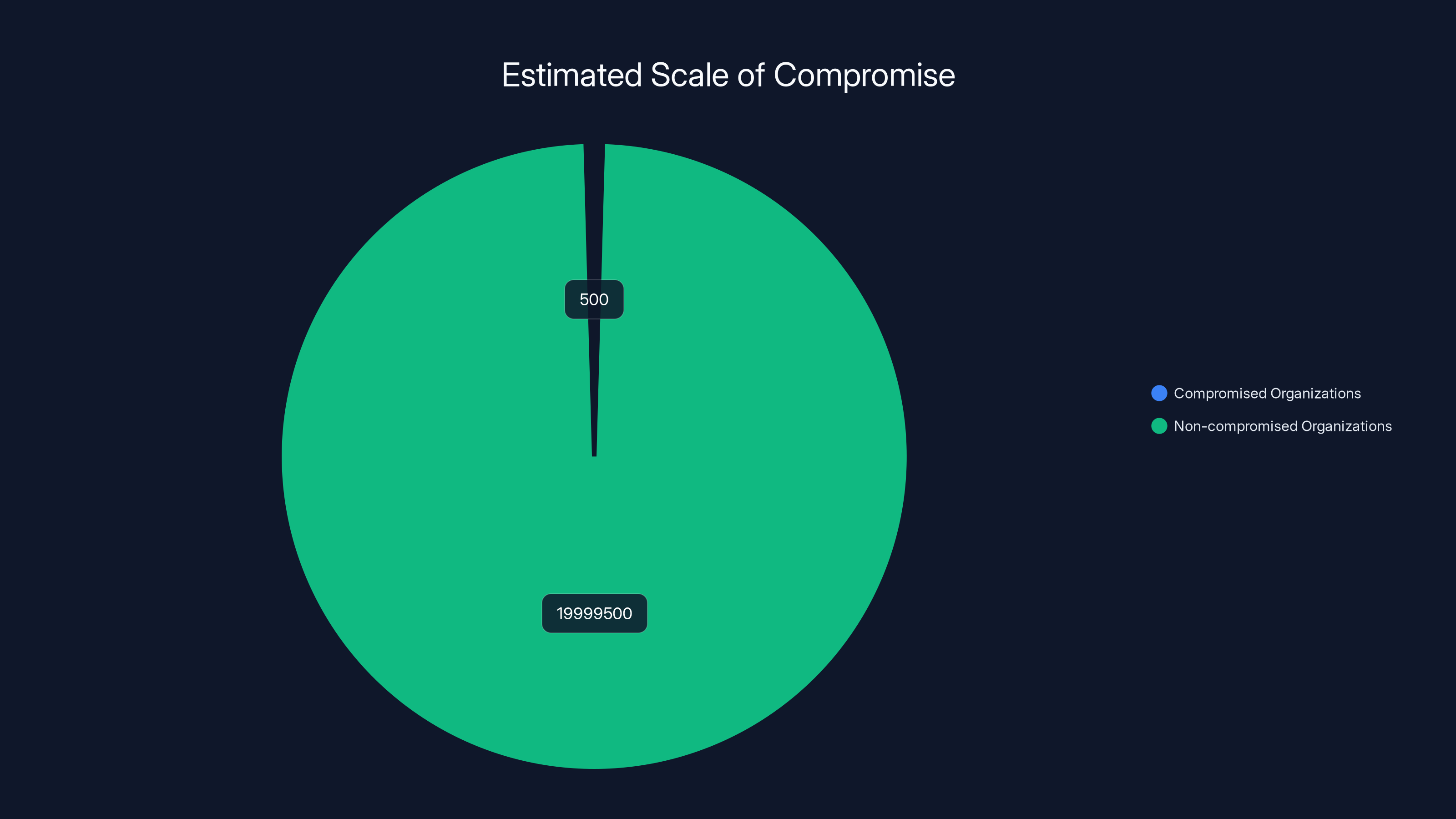
Estimated data suggests that out of 20 million active installations, only 500 organizations were targeted, achieving a precision of 0.0025%.
How the Attack Actually Worked: The Technical Details
Let's start with the unglamorous truth: this attack succeeded because of a relatively mundane hosting configuration. Notepad++ was running on shared hosting infrastructure, the kind that millions of small projects use because it's cheap and simple. Shared hosting means multiple websites and applications running on the same physical servers, often sharing the same IP address pool. It's convenient until it isn't.
Hackers identified a vulnerability in the web server configuration that allowed them to target Notepad++'s specific domain and exploit a bug in the update delivery mechanism. The exact nature of the vulnerability remains under investigation, but the attack worked like this:
- Initial reconnaissance: Attackers identified that Notepad++ was hosted on shared infrastructure and began probing for weaknesses in the update delivery pipeline.
- Exploitation: They discovered a vulnerability that allowed them to intercept update requests from clients and redirect certain users to a malicious server under their control.
- Selective targeting: Rather than redirecting all users, the attackers implemented logic to target only specific victims. This is where the sophistication emerges. They weren't trying to infect everyone, just the people they cared about.
- Malicious payload delivery: Victims who matched the targeting criteria received a trojanized version of Notepad++. From the user's perspective, everything looked legitimate. The update came from the right place, had the right signature, looked correct.
- Hands-on access: Once installed, the malicious version provided attackers with persistent access to victim systems. This is the kind of access that allows for espionage, lateral movement through networks, and stealing sensitive information.
The attack persisted for roughly six months, from June through December 2025. That's a significant window. During that time, the developers and the broader Notepad++ community had no idea their distribution mechanism had been compromised, as noted by Infosecurity Magazine.
What makes this attack particularly insidious is the selectivity. The hackers didn't just blanket-bomb the update system. They implemented what security researchers call "logic-based filtering," which means the malicious code only executed if certain conditions were met. This could have been based on geographic location, IP address, organization type, or other identifying characteristics. By being selective, the attackers significantly reduced the likelihood of discovery.
Developer Don Ho discovered that the "exact technical mechanism" of the server compromise remained murky even after investigation. This speaks to how thoroughly the attackers covered their tracks. They didn't leave obvious backdoors or easy-to-spot malware signatures. They were surgical and careful.
The vulnerability was finally patched in November 2025, but the hackers maintained access until early December. Even after the web server bug was fixed, they attempted to re-exploit the vulnerability. When that failed, their access was terminated. But by then, the damage was already done.

Why Target Notepad++? Understanding the Threat Model
This is the question that keeps security analysts awake at night: why invest all this effort to compromise Notepad++?
It seems like an odd target at first glance. Notepad++ isn't used for critical infrastructure in the traditional sense. It's a text editor. You write code in it, edit configuration files, maybe draft some documentation. It's ubiquitous precisely because it's simple and helpful.
But that ubiquity is exactly why it's such an effective supply chain target. According to TechRadar, organizations that handle sensitive information about East Asia—diplomats, intelligence analysts, policy researchers, journalists, think tanks—use Notepad++ as their daily tool. It's in the toolbox of government agencies, consultancies, and research institutions worldwide.
Moreover, Notepad++ is trusted. It's been around for more than two decades. It's open-source, which means technically anyone can audit the code. It's been vetted by millions of users and is considered secure by the vast majority of the security community. Compromising it is far more valuable than compromising some obscure malware kit that only 100 people use.
The attacker's mentality here appears to be one of patient, long-term infiltration. Rather than trying to hit millions of random users, they wanted to penetrate a small number of high-value targets and establish a persistent presence inside their networks. This is classic espionage-grade thinking.
The targeting of organizations with interests in East Asia further suggests state-level involvement. A random cybercriminal wouldn't care about geographic specificity. They'd want to maximize infection across all regions to maximize criminal profit. But a nation-state gathering intelligence? They care deeply about which organizations they compromise, because they want to avoid detection and focus resources on valuable targets.
This is consistent with how Chinese government hacking operations typically work. According to extensive documentation from security firms, Chinese government-affiliated groups tend to favor precision over scale, long-term persistence over quick payoffs, and targeted intelligence gathering over mass cybercrime. The Notepad++ attack fits this pattern perfectly.
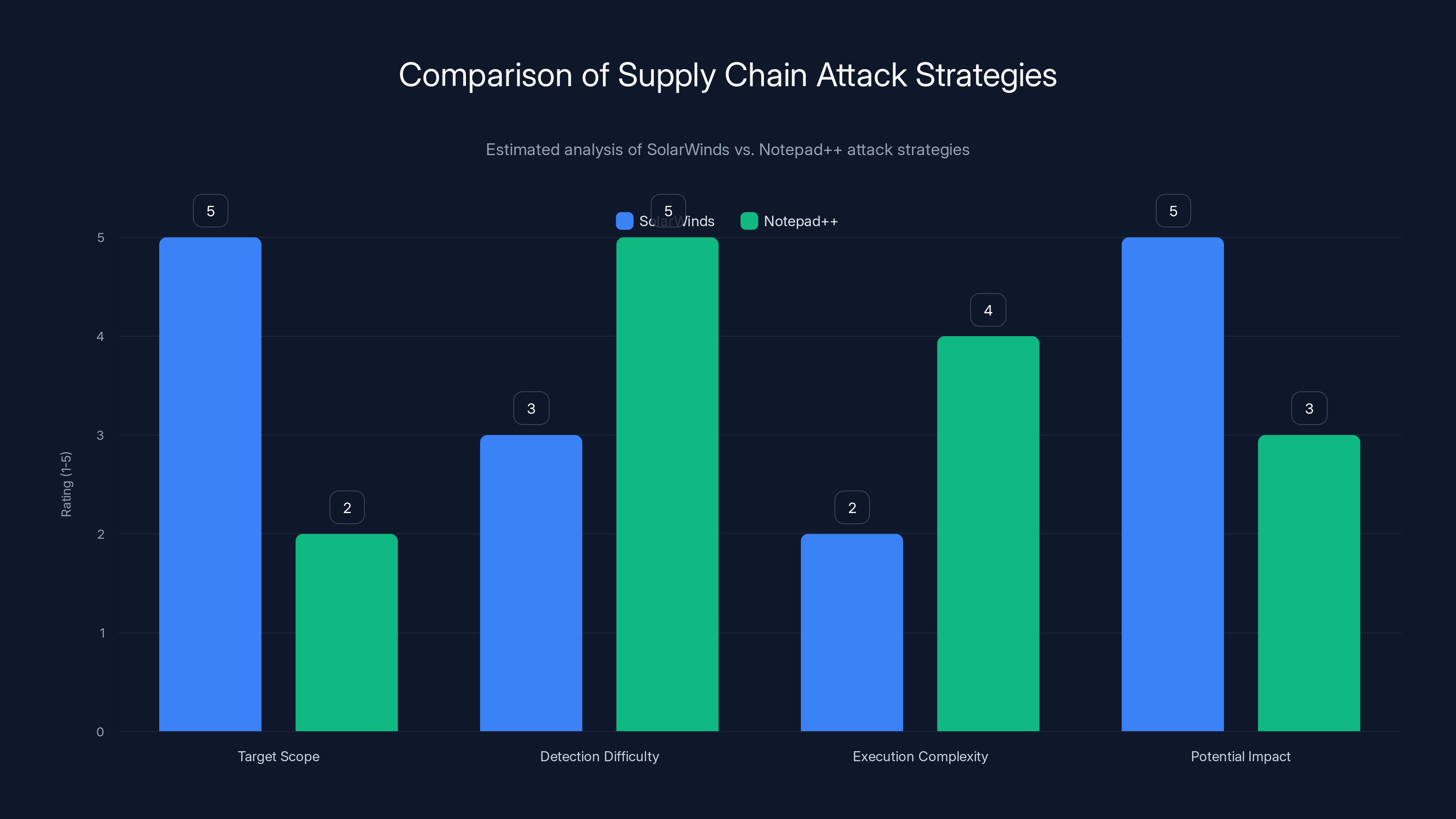
SolarWinds had a broader target scope and higher potential impact, while Notepad++ was more selective and harder to detect. Estimated data.
The Scale of the Compromise: How Many Victims?
Here's one of the most frustrating aspects of the disclosure: nobody knows for sure how many users were compromised.
Developer Don Ho has not released specific numbers about the scale of the attack. He hasn't said how many organizations were targeted, how many users were actually compromised, or what the total downstream impact was. This silence is understandable from a public relations perspective—admitting a specific number invites lawsuits and regulatory scrutiny. But it's also frustrating from a threat intelligence perspective.
What we do know comes from Kevin Beaumont's research. He identified that the hackers targeted "a small number of organizations" based on specific criteria. That suggests we're not talking about millions of infected systems, but probably dozens to low hundreds. For a state-sponsored operation, that's actually a reasonable success rate. You don't need to compromise every organization, just the ones that matter.
The fact that Notepad++ has "at least tens of millions of downloads to date" makes the targeting even more impressive. The attackers had to sift through tens of millions of potential targets and pick only the ones they wanted. That requires intelligence infrastructure, not just technical capability.
Consider the mathematics. If Notepad++ had 50 million cumulative downloads by late 2025, and let's say 20 million of those were active installations, and the attackers managed to intercept and redirect only the traffic from, say, 500 specific organizations, then they achieved a targeting precision of 0.0025%. That's incredibly selective.
But here's what makes the scale question particularly important: if victims don't know they're compromised, they don't know to change passwords, rotate encryption keys, or investigate what data might have been accessed. For victims of state-sponsored attacks, this uncertainty can be dangerous for years afterward. They might not discover the compromise until a foreign intelligence agency tips off law enforcement, or until some downstream effect reveals the compromise happened.

Historical Parallels: Solar Winds and the New Supply Chain War
When the Notepad++ attack became public, security analysts immediately drew comparisons to Solar Winds. The 2019-2020 Solar Winds breach is the canonical example of a supply chain attack gone catastrophically wrong.
Solar Winds makes Orion, a widely used IT and network management platform used by Fortune 500 companies, government agencies, and critical infrastructure operators. In 2019, Russian government hackers broke into Solar Winds's development servers and inserted a backdoor into Orion's source code. For months, as Solar Winds released new versions of Orion, those versions contained the backdoor.
When Orion got installed or updated at customer sites, the backdoor came with it. Russian intelligence gained access to the networks of the Treasury Department, the Department of Homeland Security, the Department of State, the Department of Energy, the Department of Justice, and dozens of private companies. It was, at the time, one of the most significant breaches in U. S. government history.
But here's the key difference between Solar Winds and Notepad++: Solar Winds was a mass-market attack. The backdoor went to everyone who updated. It worked on any system that installed Orion. The Russians didn't target specific organizations because they didn't need to. By compromising one major software vendor, they gained access to thousands of high-value organizations simultaneously.
Notepad++ is different. The attack was selective from the ground up. This suggests a new evolution in supply chain attack strategy. Instead of compromising a major vendor and contaminating everyone, adversaries are now exploiting supply chain mechanisms to deliver targeted malware to specific users.
This is actually harder to execute but potentially more effective for intelligence purposes. It's easier to hide because the malware isn't going to every user. It's harder to detect because security tools monitoring the vendor's infrastructure won't see widespread infections. It's more persistent because the compromised users don't know they're compromised and don't take defensive action.
From a threat actor perspective, Solar Winds was a reckless strategy that invited scrutiny and detection. Notepad++ represents a more refined approach: get to the supply chain, but be selective about who you infect. This suggests that future supply chain attacks might be harder to spot because they won't generate massive infection signatures.
Security vendors and government agencies will need to shift their detection strategies. Rather than looking for widespread compromise of a single vendor, they'll need to look for targeted delivery mechanisms, selective targeting logic, and small pockets of infection that look like isolated incidents rather than supply chain problems.

The Vulnerability Chain: Why Shared Hosting Failed
The Notepad++ attack succeeded because of a cascade of vulnerabilities in the hosting infrastructure. This is worth examining in detail because it reveals why supply chain security is so hard.
First, there was the decision to use shared hosting. This was probably a cost decision. Notepad++ is a volunteer-run open-source project without corporate backing. Shared hosting is cheap, usually
But shared hosting comes with inherent risks. Your web server is running on the same physical hardware as potentially hundreds of other websites. Your IP address is shared with other sites. Your database server shares resources. If one tenant on the shared server is compromised, it can potentially spread to others. This is a well-known security limitation, but it's accepted because the cost is so low.
Second, there was a vulnerability in the update delivery mechanism. The exact nature of this vulnerability remains under investigation, but Don Ho indicated it involved exploiting a bug in the software to redirect users to a malicious server. This suggests inadequate input validation, insecure server configuration, or improper security controls around the update process.
Third, there was no immediate detection mechanism. The attack went unnoticed for months. From June to December is six months of persistent access, during which the attackers could exfiltrate data, install additional backdoors, or use Notepad++ installations as a springboard to penetrate further into victim networks.
This detection gap is particularly interesting because Notepad++ is an open-source project. In theory, the community should have spotted tainted binaries through code review. But here's the reality: most users don't compile Notepad++ from source. They download prebuilt binaries from the website. And those binaries are generated through an automated build pipeline. If the build pipeline is compromised, all downstream users are affected, and code review doesn't help.
The vulnerability chain reveals a fundamental problem in software supply chain security: there are too many points of failure. You need to secure your hosting, your build pipeline, your code repository, your distribution servers, and your update mechanism. If any single component is compromised, the entire chain can be poisoned.

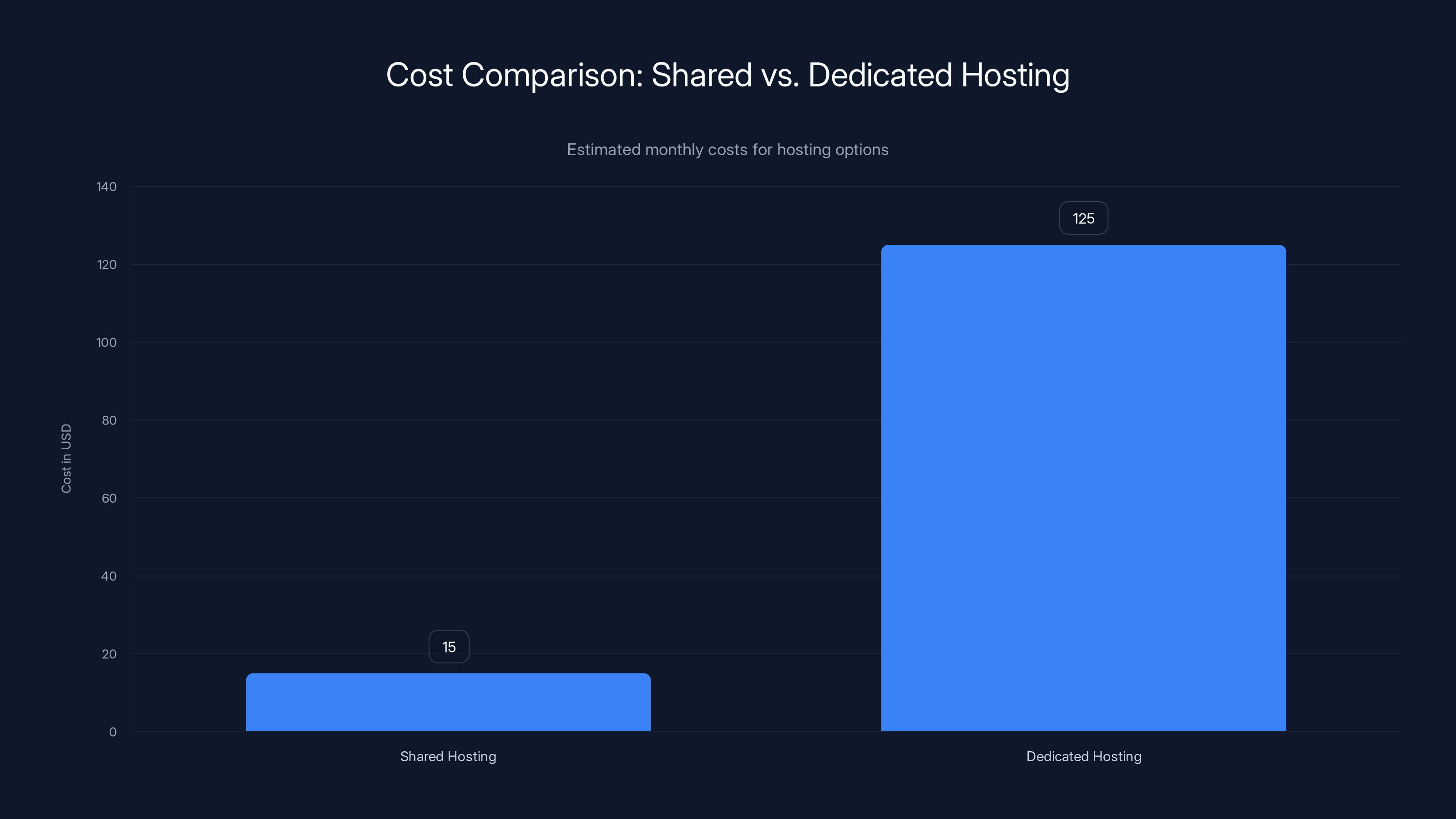
Shared hosting is significantly cheaper, costing around
Detection: How Kevin Beaumont Found the Compromise
Kevin Beaumont is a security researcher with a particular talent for finding weird things in network traffic. In December 2025, he stumbled upon evidence of malicious Notepad++ binaries being used against targets. His investigation began with a simple observation: certain organizations were running versions of Notepad++ that shouldn't exist.
Beaumont's analysis indicated that the compromised Notepad++ binaries had different signatures, different behavior, and different network communication patterns than legitimate versions. By analyzing the malware samples, he determined that the attack was targeted, not random. The malware included logic to only execute on specific systems matching certain criteria.
This is where attribution gets tricky. Beaumont identified the attack as likely originating from Chinese government-affiliated hackers based on several factors: the selective targeting (characteristic of Chinese intelligence operations), the focus on organizations interested in East Asia (suggesting espionage rather than criminal motivation), the sophistication of the targeting logic (beyond typical cybercriminal capability), and the operational tradecraft (consistent with known Chinese government hacking practices).
For Don Ho and the Notepad++ project, Beaumont's discovery was both good news and bad news. Good news: they now knew about the compromise and could patch it. Bad news: they had no idea how many victims existed, what data was stolen, or how many other compromises had occurred downstream from infected Notepad++ installations.
This highlights a critical challenge in incident response: discovery doesn't equal understanding. Knowing that you've been compromised is the first step, but determining the true scope, impact, and forensic details takes weeks or months of investigation. By that time, attackers have long since covered their tracks and disappeared.

The Chinese Government Attribution: What We Know and What's Uncertain
The attribution of this attack to Chinese government hackers is based on analytical reasoning rather than definitive technical proof. In cybersecurity, perfect attribution is rare. What we have instead is a preponderance of evidence pointing to a specific threat actor.
The evidence includes:
Selective targeting: The attackers only infected specific organizations with interests in East Asia. This isn't the behavior of cybercriminals seeking maximum profit. It's the behavior of intelligence agencies seeking specific intelligence.
Operational tradecraft: The attack exhibited sophisticated tradecraft: living off the land (using legitimate software distribution), patient long-term persistence, careful covering of tracks, and tactical patience. This is consistent with known Chinese government hacking operations documented by cybersecurity firms.
Geographic focus: The focus on organizations handling information related to East Asia suggests the attackers' intelligence priorities. State-sponsored groups typically prioritize targets aligned with their nation's geopolitical interests.
Technical sophistication: The attack required understanding of shared hosting infrastructure, ability to identify and exploit hosting vulnerabilities, and implementation of selective targeting logic. This level of sophistication is beyond most criminal groups.
However, attribution in cybersecurity is inherently probabilistic. Don Ho said the attack was "likely" carried out by Chinese government hackers. That's more cautious than saying "definitely." There's always a possibility of false flag operations, misattribution, or other groups adopting similar operational patterns.
In the intelligence and cybersecurity communities, this level of confidence ("likely" or "probably") is often sufficient for policy decisions and defensive measures. But it's important to understand that certainty is different from confidence.
What's certain: the attack happened, it was sophisticated, it was selective, and it's consistent with state-sponsored operations. What's probably: it was Chinese government hackers. What's possible but less likely: someone else did it in a way that looks exactly like Chinese government operations.

Implications for Open-Source Security: A Systemic Problem
The Notepad++ attack reveals a structural vulnerability in the open-source software ecosystem. Open-source software is maintained by volunteers, often without corporate backing. Security is maintained through community oversight and good intentions. But when you're the target of a sophisticated nation-state actor, good intentions and volunteer review often aren't enough.
Notepad++ isn't a niche project. It's a mainstream tool with tens of millions of downloads. Yet it was running on shared hosting because that's what a volunteer-run project can afford. It lacked the infrastructure and resources of a well-funded commercial software company.
This creates an incentive structure problem. The organizations most likely to be targeted by nation-state attacks (major software vendors, infrastructure tools, widely-used utilities) are the ones with the most security resources. But the organizations most vulnerable to nation-state attacks are often the volunteer-run projects that lack security expertise and funding.
This is particularly concerning because many critical infrastructure tools, security tools, and development utilities are open-source projects maintained by small teams or volunteers. If one of those projects gets compromised, the downstream impact could be catastrophic.
Several approaches have been proposed to address this:
Corporate sponsorship: Companies like Google, Microsoft, and others have begun funding open-source projects through initiatives like the Open Source Security Foundation. This provides resources for security infrastructure, code review, and incident response.
Security audits: Regular security audits of widely-used open-source projects can identify vulnerabilities before attackers exploit them.
Build infrastructure hardening: Securing the build pipeline, code repository, and distribution mechanisms to prevent supply chain attacks.
Code signing and verification: Cryptographic signing of software artifacts so users can verify authenticity.
Diversity in hosting: Avoiding single points of failure in distribution infrastructure.
The Notepad++ incident suggests that these measures need to become the norm, not the exception, for any widely-used software project.

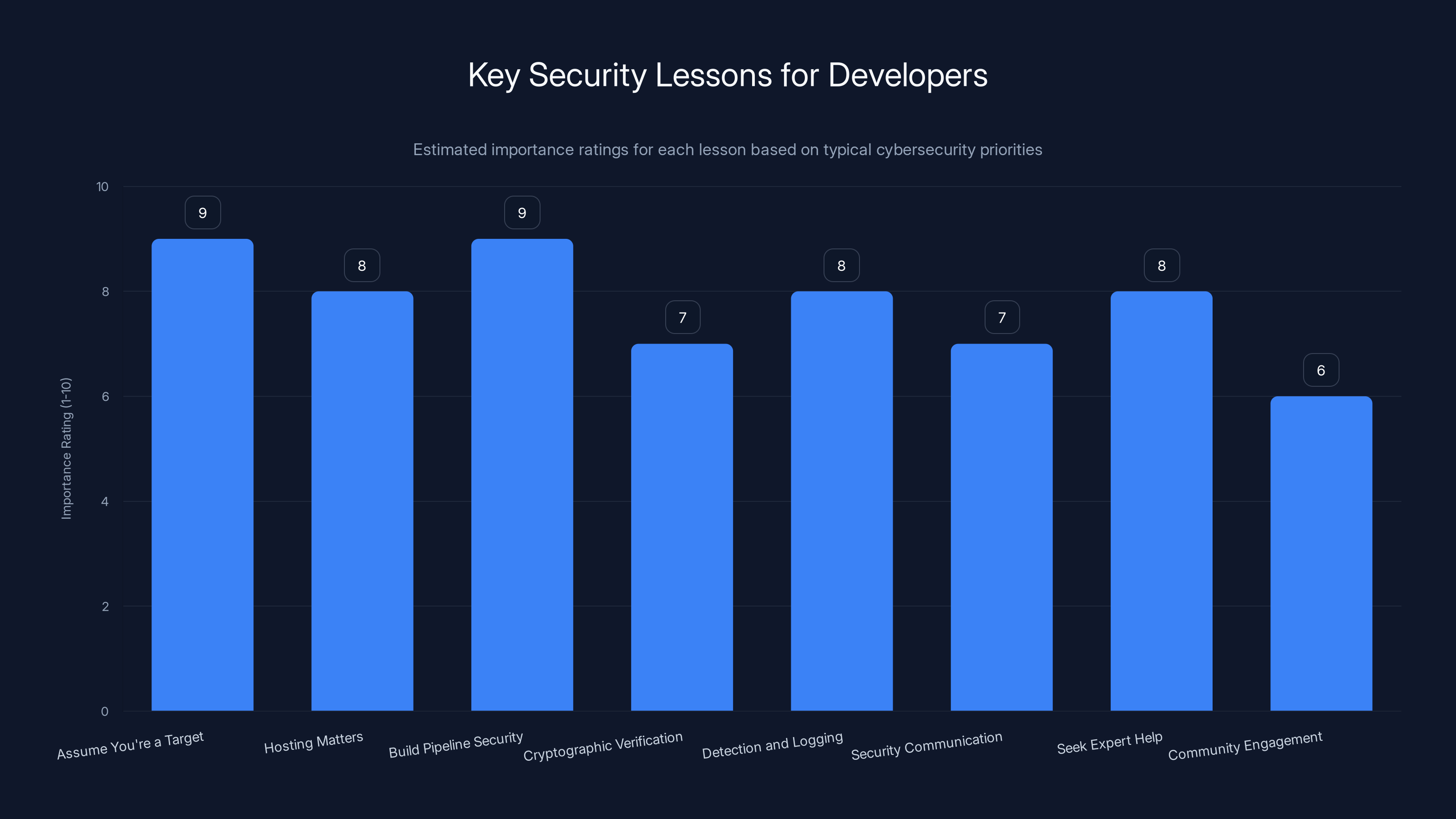
This chart estimates the importance of various security lessons for developers and security teams, with 'Assume You're a Target' and 'Build Pipeline Security' rated highest. Estimated data.
What Users Should Do: Immediate Action Items
If you're a Notepad++ user, the immediate action is straightforward: update to the latest patched version.
Don Ho has released fixes for the vulnerability that enabled the attack. These fixes address the bug in the update mechanism that allowed attackers to redirect users to malicious servers. The patched version prevents the attack from recurring.
But updating your Notepad++ binary is just the first step. If you were running a compromised version between June and December 2025, your system may have been compromised. Here's what you should do:
- Update immediately: Download the latest version of Notepad++ directly from the official website. Don't update through an in-app update mechanism if you're not confident about the integrity of your current installation.
- Review your system: If your organization handles sensitive information, consider this a security incident. Have your IT security team audit systems that may have run compromised Notepad++ versions.
- Review network logs: Check your network traffic logs for anomalies during the June to December 2025 timeframe. Look for unexpected outbound connections from systems running Notepad++.
- Assess data exposure: Determine what data was accessible from systems running compromised Notepad++ installations. If those systems had access to sensitive networks or data, assume exposure.
- Rotate credentials: If you're concerned about compromise, rotate sensitive passwords and encryption keys used on potentially compromised systems.
- Segment your network: Implement network segmentation to limit the damage if a development tool gets compromised in the future.
- Monitor for lateral movement: Look for evidence of lateral movement from compromised systems to other parts of your network.
For organizations that handle sensitive information or conduct work related to geopolitics, this should be treated as a serious security incident even if you can't definitively prove you were targeted. The uncertainty alone warrants defensive action.

The Role of Software Signing and Verification
One thing that Notepad++ could have done better: cryptographic signing of binaries and publication of checksums.
Most legitimate software vendors now sign their binaries with a cryptographic key. This allows users to verify that a binary hasn't been tampered with. You download the binary, you download the signature (usually from a different, more secure server), and you verify that the signature matches. If it does, you know the binary is authentic. If it doesn't, you know it's been compromised.
Moreover, vendors often publish checksums (SHA-256 hashes) of their releases on their website or through third-party services. Users can download the binary, compute its checksum, and compare it to the published value. If they match, the binary is authentic.
Notepad++ did provide binaries, but the verification mechanism wasn't prominent in the distribution process. Most users probably didn't verify checksums or signatures. They just downloaded the executable and ran it.
If users had been verifying signatures or checksums during the June to December 2025 period, they would have immediately noticed that their downloaded binaries didn't match the published values. This would have triggered investigation and potentially exposed the attack much earlier.
This is a lesson for all software vendors: make verification easy and standard practice. For all users: verify software authenticity. It takes five extra minutes and can prevent severe compromise.
The cryptographic math is straightforward. If a binary's SHA-256 hash matches the published value, the probability that it's been compromised but still has the correct hash is approximately 1 in 2^256, or about 1 in 1.15 × 10^77. For practical purposes, that's impossible.
With such vanishingly small probabilities, cryptographic verification is one of the strongest defenses against supply chain attacks.

Future Threats: The Evolution of Supply Chain Attacks
The Notepad++ incident represents what may be a new era of supply chain attacks: selective, targeted, and designed to avoid mass detection.
We can expect to see more of these attacks for several reasons:
First: Supply chains are attractive targets. Rather than attacking individual organizations, attackers can compromise the source and reach hundreds or thousands of targets with a single compromise.
Second: Selective attacks are harder to detect than mass-market attacks. If 100,000 organizations get infected with the same malware, security vendors will notice. If 100 organizations get infected with targeted variants, detection becomes exponentially harder.
Third: State-sponsored actors have the resources and patience to conduct selective attacks. A nation-state preparing for a specific military or intelligence operation might spend months infiltrating the supply chain to compromise a specific organization's networks.
Fourth: As defenders improve at detecting mass-market attacks, attackers naturally evolve toward more selective approaches.
Future supply chain attacks might target:
- Development tools used by military contractors (to gain intel on weapons systems)
- Telecommunication infrastructure software (to gain surveillance access)
- Cloud management platforms (to compromise customer infrastructure at scale)
- Cryptographic libraries (to weaken security across products)
- Testing and CI/CD tools (to compromise software at the moment of creation)
The defenders' job is to harden supply chains before these attacks happen. This requires investment in security infrastructure, verification mechanisms, code review, and behavioral analysis to detect anomalies.

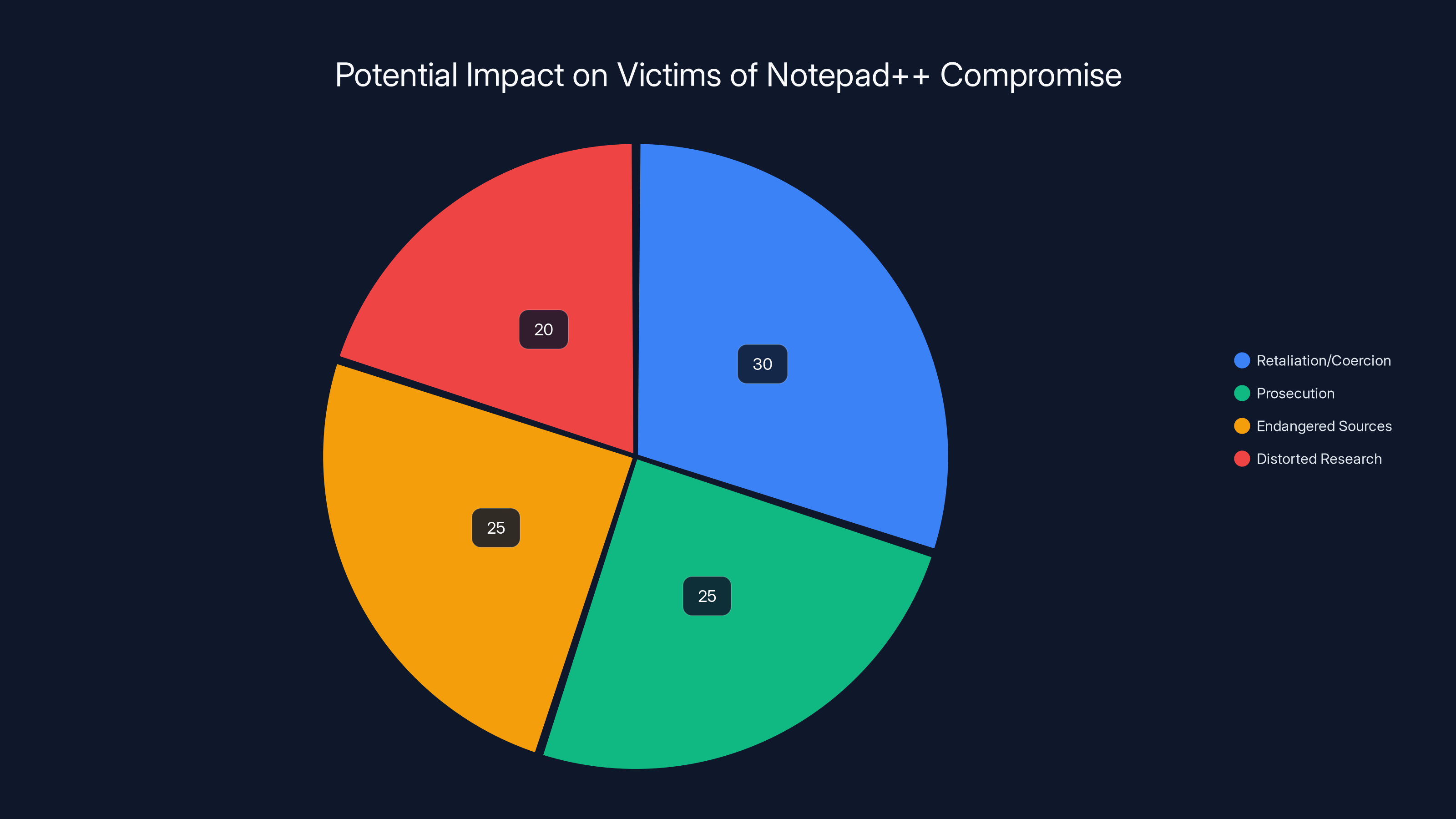
Estimated data shows that retaliation/coercion and prosecution are the most common consequences faced by victims of the Notepad++ compromise, highlighting the severe human cost of cybersecurity failures.
Organizational Response: What Companies Should Do
For organizations concerned about supply chain attacks, here's a strategic response framework:
Software inventory: You can't protect what you don't know you have. Maintain a comprehensive inventory of all software, libraries, and dependencies used in your organization. Include version numbers and update dates.
Vendor risk assessment: Evaluate vendors based on their security practices, infrastructure, and transparency. Prefer vendors that sign their binaries, publish checksums, and have clear incident response procedures.
Secure build practices: Use isolated build environments that can't be compromised by external attacks. Use reproducible builds where possible so you can verify that released binaries match source code.
Dependency monitoring: Use tools that continuously monitor your dependencies for known vulnerabilities and anomalies. Services like Snyk or White Source can identify compromised packages.
Network segmentation: Isolate development systems from production systems. If a development tool gets compromised, attackers shouldn't automatically have access to your production infrastructure.
Behavioral analysis: Monitor software behavior for anomalies. If Notepad++ suddenly starts making unexpected network connections, alert on it.
Incident response planning: Have a plan for responding to supply chain compromises. Know who to contact, what to investigate, and how to respond.
Threat intelligence: Subscribe to security intelligence services that track supply chain threats. Organizations like CISA publish advisories about compromised software.
Implementing all of this requires significant investment, but the cost is far lower than the cost of responding to a successful supply chain compromise.
The Information War Dimension
Understanding the Notepad++ attack requires understanding that it's part of a larger information war between nation-states.
The hackers specifically targeted organizations interested in East Asia. This suggests they were looking for intelligence on policy positions, diplomatic communications, research on Chinese affairs, and potentially intelligence assessments. In the modern geopolitical context, this kind of intelligence is as valuable as military intelligence.
For journalists covering China, for diplomats negotiating with China, for researchers studying Chinese policy, and for intelligence agencies monitoring Chinese actions, compromise of their systems is a significant intelligence victory for the Chinese government. It provides:
- Insight into what the outside world thinks about China
- Early warning about critical assessments or policy changes
- Identification of key influencers and decision-makers
- Information about upcoming reports or publications
- Leverage for coercion or intimidation
From a Chinese government perspective, the Notepad++ attack probably succeeded beyond expectations. By quietly compromising a small number of high-value targets, they obtained intelligence without triggering major diplomatic incidents or international backlash.
This is why attribution matters. When nation-states conduct cyberattacks, it's not just a technical incident. It's a foreign intelligence operation with geopolitical implications. Understanding that this was a Chinese government operation (not just random hackers) frames the incident in its proper context.
For targets of such operations, this context is important for threat modeling and response. If you assume you're targeted by random criminals, you design different defenses than if you assume you're targeted by nation-state intelligence services.

Lessons for Developers and Security Teams
The Notepad++ attack offers several practical lessons for anyone involved in software development or cybersecurity:
Assume you're a target: Whether you work on open-source or commercial software, assume that sophisticated attackers are interested in your supply chain. This changes how you approach security.
Hosting matters: Don't skimp on hosting security to save money. Shared hosting has inherent risks. If your software is widely used, you need hosting with strong security controls and isolation.
Build pipeline security: Your build pipeline is as critical as your code repository. Secure it accordingly. Use separated, airgapped build systems if possible.
Cryptographic verification: Sign everything. Publish checksums. Make verification part of the standard download process.
Detection and logging: Implement comprehensive logging in your software update systems so you can detect anomalies. Don Ho couldn't detect the attack until someone externally identified it, partly because logging was insufficient.
Security communication: Have a plan for disclosing security incidents. Transparency and speed matter. Don Ho's prompt acknowledgment limited damage and maintained trust.
Seek expert help: If you maintain widely-used software, consider hiring security researchers to audit your infrastructure. The cost is small compared to the potential impact of a successful supply chain attack.
Community engagement: Engage your user community in security. Make it easy for users to report suspected compromises. Kevin Beaumont's investigation succeeded partly because he could analyze malware samples shared by affected organizations.

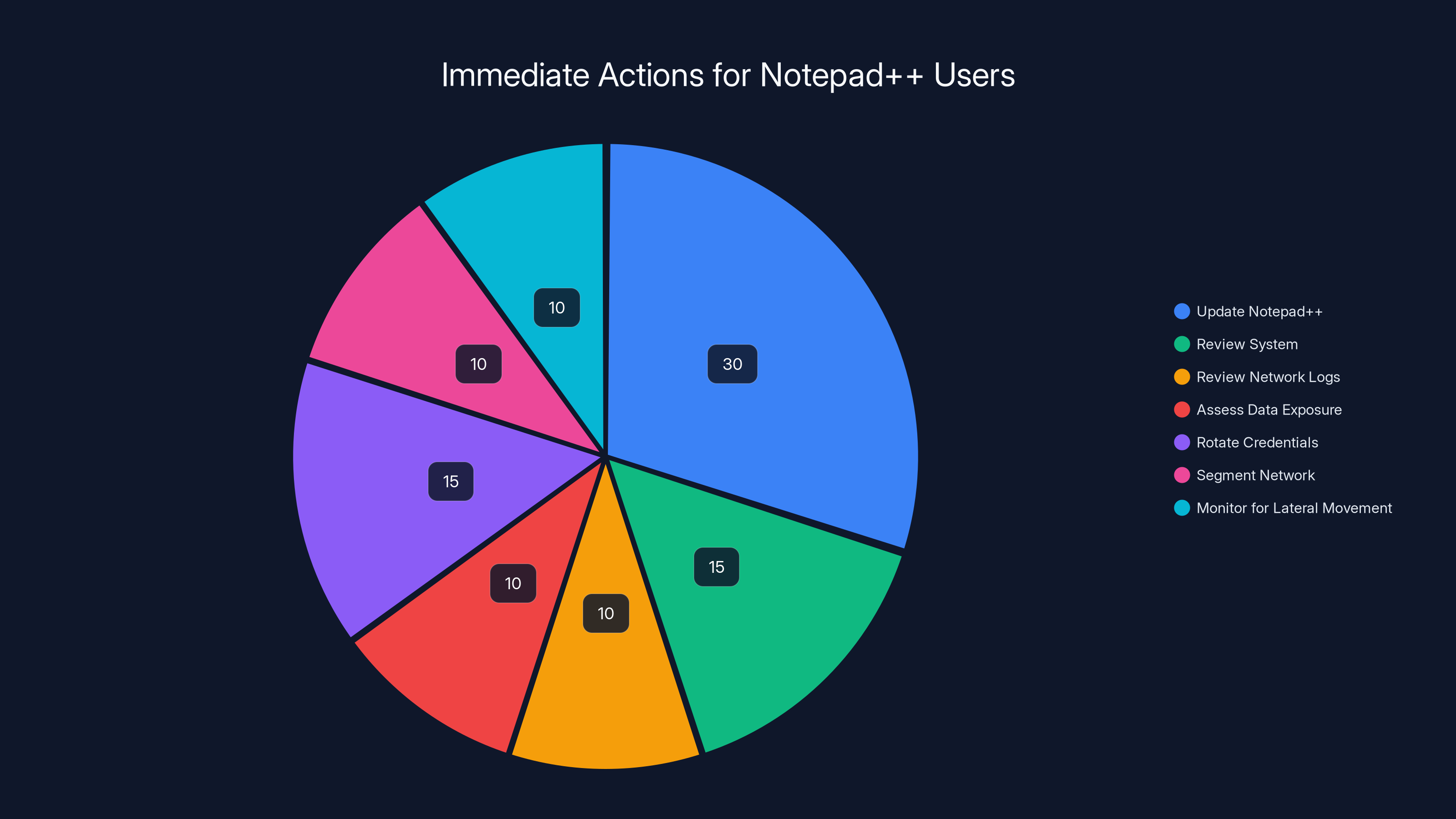
Estimated data shows that updating Notepad++ is the most immediate action taken by users, followed by system review and credential rotation.
The Broader Context: State-Sponsored Hacking Campaigns
The Notepad++ attack didn't happen in a vacuum. It's part of a broader pattern of state-sponsored hacking campaigns targeting software and technology infrastructure.
Over the past decade, we've seen:
- 2019-2020: Solar Winds breach (Russian government targeting U. S. government and private sector)
- 2021: Microsoft Exchange Server vulnerabilities (Chinese government targeting healthcare, government, and critical infrastructure)
- 2021: Kaseya supply chain attack (ransomware group targeting managed service providers)
- 2023: 3CX supply chain compromise (targeting enterprise communications software)
- 2024: Various npm package compromises (targeting developers)
- 2025: Notepad++ attack (Chinese government targeting Asia-focused organizations)
What's notable is the increasing sophistication and selectivity. Early state-sponsored attacks were often clumsy and obvious. Modern attacks are refined, patient, and carefully targeted.
This evolution reflects increasing capability and increasing competition. Multiple nation-states are now conducting sophisticated cyberattacks, which drives innovation in attack techniques. But it also reflects a growing understanding that selective, persistent compromise is more valuable than noisy, mass-market compromise.

Regulatory and Policy Implications
The Notepad++ attack will likely have policy implications. Governments are increasingly concerned about supply chain security, and incidents like this drive regulation.
In the United States, the National Institute of Standards and Technology (NIST) has released guidance on software supply chain security. The Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) is actively tracking supply chain compromises and issuing alerts.
In the European Union, regulations like the Network and Information Systems (NIS) Directive are increasingly focusing on supply chain security as a critical risk.
Governments are also considering requirements for software vendors, particularly those providing software to government or critical infrastructure. These might include:
- Mandatory security audits
- Requirement for cryptographic signing of software
- Requirement for software bill of materials (SBOM)
- Incident disclosure requirements
- Security training requirements
While regulation can be burdensome, in the case of supply chain security, some baseline standards make sense. The risk of widespread compromise through a single supply chain failure is high enough that ensuring minimum security standards is justified.
The Human Cost: Victims and Their Experience
It's easy to discuss supply chain attacks in abstract terms. But there are real humans on the receiving end of these attacks.
Consider a diplomat who used Notepad++ to draft communications about Chinese policy. Or a researcher studying human rights in China. Or a journalist reporting on Chinese government actions. If their systems were compromised during the June to December 2025 window, their communications, research, and sources were potentially exposed to the Chinese government.
For these individuals, the implications are serious. They might face retaliation, coercion, or prosecution based on information obtained through the Notepad++ compromise. Their sources might be identified and endangered. Their research might be distorted in official Chinese communications.
The Notepad++ attack is a reminder that cybersecurity isn't just about technology. It's about protecting people. When we fail at security, real humans face real consequences.
This is why incident response must be thorough and humane. Victims need support, information, and assistance in understanding what happened and what they need to do to protect themselves.

Looking Forward: Building Resilient Supply Chains
The Notepad++ incident is unlikely to be the last of its kind. As software becomes more critical to society, as organizations become more dependent on third-party software and libraries, and as nation-states recognize the value of supply chain attacks, we should expect more incidents.
Building resilience requires action at multiple levels:
For individual users: Update software promptly. Verify checksums and signatures when possible. Use software from reputable vendors. Keep systems patched and updated.
For developers: Secure your development infrastructure. Sign your releases. Be transparent about security. Respond quickly to incidents.
For organizations: Monitor your software inventory. Assess vendor security practices. Implement network segmentation. Monitor for anomalies.
For industry: Share threat intelligence. Develop standards for secure software distribution. Invest in open-source security.
For governments: Regulate minimum security standards. Support security research. Prosecute nation-state attackers. Establish norms around cyberattacks.
None of these approaches alone is sufficient. We need layered defense: defense at the vendor level, defense in the distribution chain, defense at the organizational level, and defense at the endpoint.
The Notepad++ attack shows us where the current system is failing. Our job is to learn from it and build better defenses.

FAQ
What exactly did the Notepad++ hackers do?
The hackers exploited a vulnerability in Notepad++'s shared hosting infrastructure to intercept and redirect software update requests. For selected victims (likely organizations interested in East Asia), they delivered malicious versions of Notepad++ that granted attackers persistent access to their systems. The attack operated from June to December 2025 before being detected.
How did the hackers choose their victims?
The attackers implemented selective targeting logic that identified which organizations should receive malicious updates based on criteria such as geographic location, IP address, or organizational type. This allowed them to avoid infecting random users and focus on high-value intelligence targets. The selectivity was crucial for avoiding detection.
Is Notepad++ still safe to use after the fix?
Yes, Notepad++ is safe to use once you update to the patched version released after November 2025. The vulnerability that enabled the attack has been fixed. However, if you were running a compromised version before the patch, your system may have been compromised and should be audited by security professionals.
How is this attack different from Solar Winds?
The Solar Winds attack infected all users who updated their software, affecting thousands of organizations. The Notepad++ attack selectively targeted specific organizations, likely fewer than 1,000. This makes Notepad++ harder to detect but also limits scale. It represents a shift toward precision over mass infection in supply chain attacks.
Why would Chinese government hackers target Notepad++?
Notepad++ is a widely-used, trusted tool with tens of millions of downloads. By compromising it, attackers gained access to computers at organizations interested in East Asia, including government agencies, research institutions, and journalism organizations. This allowed them to gather intelligence without conducting obvious espionage.
What should organizations do to prevent similar attacks?
Organizations should maintain software inventory, verify software integrity through checksums and signatures, implement network segmentation, monitor for anomalies, assess vendor security practices, and develop incident response plans. Using secure build pipelines and regular security audits of widely-used software also reduces risk.
Could this attack have been prevented?
The attack could have been partially mitigated through several measures: using dedicated hosting instead of shared hosting, implementing cryptographic signing of binaries, publishing checksums for verification, conducting regular security audits, and implementing anomaly detection in the update system. Complete prevention of state-sponsored attacks is nearly impossible, but detection and response timelines can be improved.
How many people were actually compromised?
The exact number remains unknown. Don Ho and Kevin Beaumont indicated that a "small number" of organizations were targeted, likely dozens to low hundreds. Given Notepad++'s 100 million cumulative downloads, the targeting precision was extremely high, suggesting the attackers affected fewer than 1,000 systems.
What data could have been stolen from victims?
Victims who ran compromised Notepad++ versions potentially had their systems accessed by hackers. Depending on what those systems were used for, stolen data could include: confidential documents, communications, research files, source code, credentials, and personal information. For organizations handling sensitive information about East Asia, the intelligence value was likely significant.
Will this lead to new regulations for software security?
Likely. The incident has drawn attention from government agencies and policymakers concerned about supply chain security. We may see new requirements for software vendors, particularly those supplying critical infrastructure or government organizations. These could include mandatory security audits, cryptographic signing requirements, and incident disclosure timelines.
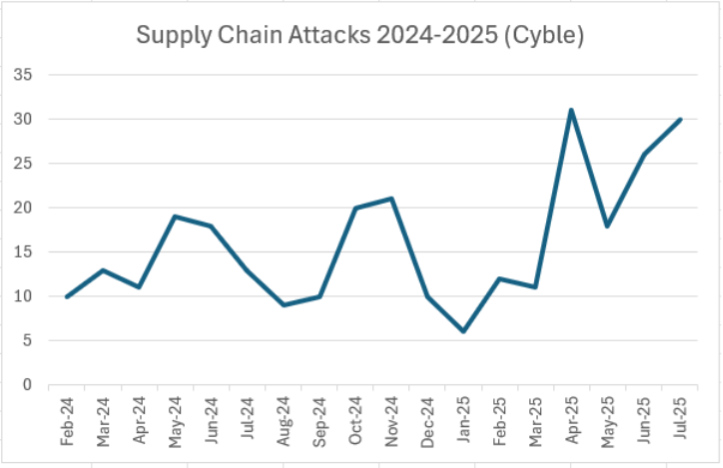
Conclusion: Learning From Notepad++ and Building Better Defenses
The Notepad++ supply chain attack represents a significant shift in how sophisticated actors conduct cyberattacks. Rather than trying to compromise everyone, they've learned to compromise the right people. Rather than using obvious malware, they've learned to hide in trusted software. Rather than moving fast and breaking things, they've learned to move slowly and stay invisible.
For security professionals, this is both concerning and instructive. Concerning because it shows that our adversaries are getting smarter, faster, and more patient. Instructive because it reveals where our current defenses are weakest.
The attack succeeded because of a combination of factors: an outdated hosting architecture, a vulnerability in the update mechanism, insufficient logging and monitoring, and the inherent trust we place in widely-used software. These are all addressable problems. None of them require cutting-edge technology. They just require the right priorities and investment.
For developers of widely-used software, the Notepad++ incident should be a wake-up call. Your software is valuable not just to legitimate users but to nation-state attackers. Treat your infrastructure with that level of seriousness.
For users, the incident should be a reminder that no software is completely trustworthy. Verification, segmentation, and monitoring are not optional luxuries. They're essential security practices.
For security teams and organizations, the incident demonstrates why supply chain security needs to be a top priority. You can have perfect security within your own infrastructure, but if you're using compromised third-party software, that security is meaningless.
The Notepad++ attack is unlikely to be the last of its kind. As society becomes more dependent on software, as nation-states recognize the value of supply chain attacks, and as attackers become more sophisticated, we should expect supply chain incidents to increase. Our job is to make them increasingly difficult and increasingly detectable.
The defense doesn't lie in perfect security, which is impossible. It lies in layered defense, rapid detection, and quick response. Implement software inventory systems. Monitor software behavior. Verify software authenticity. Segment networks. Share threat intelligence. Respond quickly to incidents.
Done right, supply chain security isn't a burden on development. It's a requirement for trustworthiness. In a world where software enables everything, we can't afford to get this wrong.
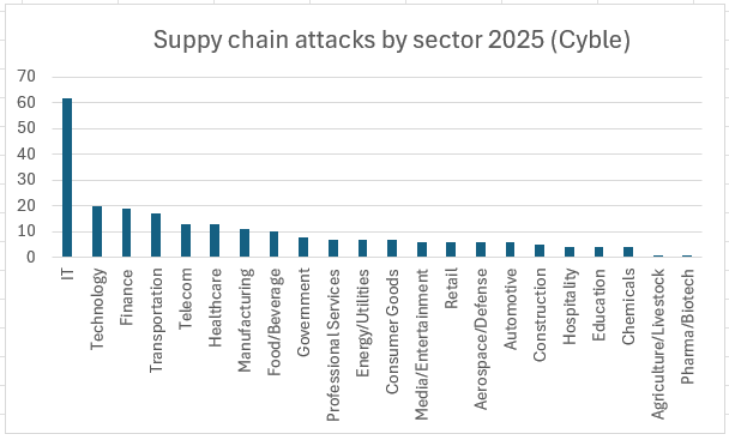
Key Takeaways
- Chinese government hackers compromised Notepad++ between June-December 2025 by exploiting shared hosting vulnerabilities in the update mechanism
- The attack was highly selective, targeting specific organizations with East Asia policy interests rather than attempting mass infection
- Victims received malicious Notepad++ updates that granted attackers persistent "hands-on" access to compromised systems for espionage
- This represents evolution in supply chain attacks toward precision targeting to avoid detection, unlike the mass-market SolarWinds approach
- Organizations should verify software integrity through checksums, implement network segmentation, monitor software behavior, and maintain comprehensive software inventory
Related Articles
- Software Integrity vs Data Sovereignty: Why Code Matters More [2025]
- Major Cybersecurity Threats & Digital Crime This Week [2025]
- Canada Computers Data Breach 2025: Timeline, Impact, Protection [2025]
- IPVanish Threat Protection Pro: Malware Defense Guide & Alternatives 2025
- TikTok's Oracle Data Center Outage: What Really Happened [2025]
- Agentic AI Security Risk: What Enterprise Teams Must Know [2025]
![Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]](https://tryrunable.com/blog/notepad-supply-chain-attack-chinese-hackers-hijack-updates-2/image-1-1770057531097.jpg)



