Understanding Proton VPN's Major Security Overhaul
Proton VPN just made a move that's got security-conscious users paying attention. The company announced it's killing off legacy OpenVPN configurations, and if you haven't updated yet, you've got a hard deadline: February 28, 2025.
Here's what's happening. Proton VPN is sunsetting support for older OpenVPN protocol versions that, frankly, are showing their age. These legacy configurations rely on encryption methods and security standards that don't meet modern security requirements anymore. The company isn't doing this to annoy people. They're doing it because the old stuff is actually vulnerable to newer attack vectors that security researchers have identified over the past few years.
What makes this interesting is that most users won't even notice the change if they're using Proton VPN's native apps. The native clients automatically use the newer, more secure protocols. But if you're running custom OpenVPN configurations, manual setup files, or older VPN clients that haven't been updated since the Obama administration, you're in the crosshairs.
The deadline matters because after February 28, the old configurations simply won't work anymore. Your VPN connection will fail. You won't be able to tunnel through Proton's servers using the legacy setup. This is a hard cutoff, not a gradual phase-out or a "we'll try to support it" situation.
Why now? The security landscape has shifted dramatically. Encryption standards that seemed solid five years ago have weakened as computing power improved and new attack methodologies emerged. Organizations like the Electronic Frontier Foundation and security researchers have been pushing VPN providers to upgrade their protocols for years. Proton VPN is essentially saying, "Okay, the time for gradual migration is over. We're moving forward with modern security standards whether people are ready or not."
This move actually puts Proton ahead of other VPN providers in terms of security posture. Many competitors are still supporting legacy protocols because they're afraid of alienating users who prefer the familiar. Proton is making the uncomfortable choice to prioritize security over comfort.
The Technical Details Behind the Deprecation
Let's dig into what's actually being deprecated here. Legacy OpenVPN configurations typically use older TLS versions, outdated cipher suites, and encryption protocols that are no longer considered cryptographically strong enough for sensitive applications.
The specific technical issue centers around cipher strength and authentication methods. Older OpenVPN setups sometimes relied on SHA-1 hashing for authentication, which has known collision vulnerabilities. They might also use 128-bit encryption for the control channel instead of 256-bit, which reduces the margin of security when you factor in advances in cryptanalysis.
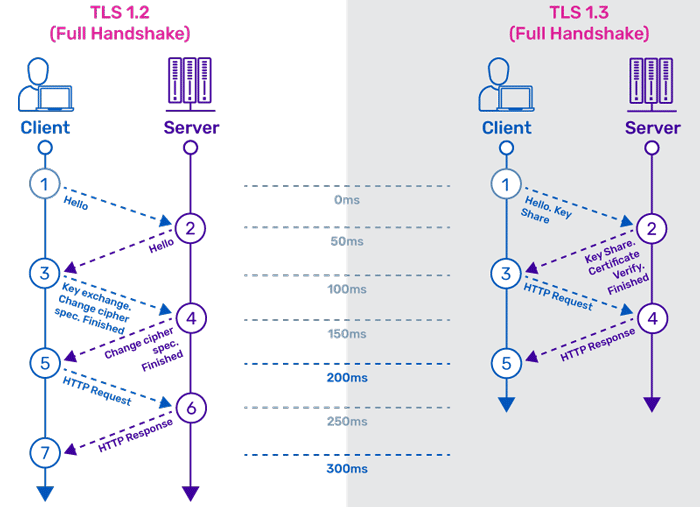
Proton VPN's new configurations mandate TLS 1.3, which is significantly more robust than TLS 1.2 that many legacy setups used. TLS 1.3 has simplified the handshake process, which paradoxically makes it more secure because there are fewer moving parts and fewer opportunities for misconfiguration.
The company is also enforcing stronger cipher suites like ChaCha20-Poly1305, which is resistant to timing attacks and other side-channel vulnerabilities that can affect older algorithms. These aren't marginal improvements. They're the difference between encryption that's suitable for protecting your browsing habits and encryption that can withstand sophisticated state-level attacks.
Why Legacy Configurations Became a Security Liability
OpenVPN is about two decades old now, which makes it ancient in software terms. The protocol was designed in an era when computing power was limited and certain security tradeoffs made sense. You could afford to use smaller key sizes because brute-force attacks took years instead of hours.
But here's the problem with supporting old configurations indefinitely. Security research doesn't stop. New vulnerabilities get discovered. Better attack methodologies emerge. Once you know about a weakness, continuing to support it makes you responsible if someone exploits it.
Legacy configurations also tend to have weaker forward secrecy properties. Forward secrecy means that even if someone cracks your encryption key, they can't decrypt old sessions. Older OpenVPN setups sometimes didn't implement this properly, or implemented it in ways that are now understood to have flaws.
There's also the human factor. Legacy configurations are often more manual and harder to get right. People might copy setup files from old forum posts that have minor misconfigurations. These configurations might work, but they're not optimal from a security standpoint. Modern VPN clients handle all this complexity internally.
Proton VPN's decision to cut support also sends a signal to security researchers that they should focus their efforts on current technology instead of wasting time looking for vulnerabilities in deprecated systems. It's a way of saying, "We're not interested in 'secure-enough.' We want actually secure."
Which Users Are Actually Affected
If you're using Proton VPN on Windows, macOS, iOS, or Android with the official app, you're completely fine. The native apps already switched to modern protocols years ago. You won't see any change, and you don't need to do anything.
The people who need to take action fall into specific categories. First, there's anyone using OpenVPN directly through a third-party client on their computer. If you downloaded a .ovpn configuration file from Proton VPN's website more than three years ago and you're still using it, that's a problem.
Second, there are power users running VPN tunnels on routers, servers, or network appliances. If you've got a Linux server configured with an old Proton VPN setup file for some specific use case, you need to update it.
Third, some people maintain custom automation or scripts that rely on specific OpenVPN configurations. Maybe they've got a deploy script that spins up VPN connections with hardcoded parameters. Those scripts will break on February 28 unless they're updated.
Officially, Proton estimates that less than 5 percent of their user base is actually affected. That's because the vast majority of VPN users just download the app and use it without thinking about the underlying protocol. But that 5 percent represents potentially millions of people globally, and they all need to take action in the next few months.
How to Check If You're Using Legacy Configurations
You can determine whether you're affected by checking a few things. First, open your VPN client and look for version information. If it says you're running Proton VPN version 3.0 or earlier on Windows, or version 2.5 or earlier on macOS, you've got legacy software.
If you're using OpenVPN directly, check your configuration files. Open a command terminal and run grep "tls-version" yourconfig.ovpn. If the output shows anything like tls-version 1.0 or tls-version 1.1, that's legacy. Modern configurations specify tls-version 1.3 or at minimum tls-version 1.2.
You can also check the cipher suite being used. Run grep "cipher" yourconfig.ovpn. If you see cipher AES-256-CBC or cipher BF-CBC, those are older configurations. Newer ones should show cipher ChaCha20-Poly1305 or cipher AES-256-GCM.
Proton VPN also released a diagnostic tool on their website where you can paste your configuration file and it will tell you immediately if it's deprecated. This is genuinely helpful because you don't have to parse technical parameters yourself.
Another way to check is simply trying to visit Proton VPN's settings page and seeing if there's a warning message. Proton has been gradually rolling out notifications to affected users for several months, so if you've got an account, check your email for deprecation warnings.
The Migration Process Explained
Migrating to new OpenVPN configurations isn't complicated, but it requires a few steps and you need to do it before the deadline.
First, log into your Proton VPN account on their website. Go to the downloads section and look for OpenVPN configuration files. You'll see they're organized by country and server type. Download the new configuration files that match what you were using before. These will have the modern TLS 1.3 and updated cipher suites built in.
If you're using a third-party OpenVPN client, locate where you have your old configuration files stored. On Windows, this is usually C:\Users\Your Username\App Data\Local\OpenVPN\config. On macOS, it's typically ~/Library/Application Support/OpenVPN. On Linux, it varies but is often /home/username/.config/openvpn/.
Back up your old configuration files before doing anything. This takes thirty seconds and prevents you from accidentally deleting something you needed. Then delete the old .ovpn files and replace them with the new ones you downloaded from Proton.
Restart your OpenVPN client. If you're using the command line, run sudo openvpn --config /path/to/newconfig.ovpn to test the new configuration. If the connection establishes without errors, you're done.
For router or server setups, the process is similar. Access your device's configuration panel, locate the VPN settings, and replace the old configuration file with the new one. If you're running this through a script or automation tool, you'll need to update any hardcoded file paths or connection parameters.
One thing to watch for: some people have customized their OpenVPN configurations with extra parameters for their specific use cases. If you've added custom options, you'll need to preserve those when migrating. The new configuration files are the template, but you can add your own parameters as long as they don't conflict with the security settings.
Why This Deadline Approach Works Better Than Gradual Sunsets
Some companies would have dragged this out for years, offering a hybrid period where both old and new configurations work. Proton's decision to set a firm deadline is actually more responsible from a security standpoint.
Here's why. When you support multiple versions of encryption or authentication methods, you create complexity. Complexity is where vulnerabilities hide. The more code paths your system has to maintain, the more potential bugs you introduce. By making a clean break, Proton simplifies their infrastructure and reduces the attack surface.
A firm deadline also forces people to actually migrate instead of procrastinating indefinitely. If there was no deadline, people would keep using legacy configurations "just because it still works." This would eventually become a security liability for Proton. They could get exploited, and users would blame the company for not forcing them to upgrade.
From a business perspective, supporting legacy protocols also requires maintaining older OpenVPN server instances that are configured to accept the old TLS versions. This is resource-intensive. By sunsetting support, Proton can retire those server instances and consolidate their infrastructure, which actually reduces their costs and improves performance for everyone else.
It also sends a message to the security community that Proton is serious about staying on top of best practices. When users see that a VPN company is willing to break backward compatibility for security, it builds trust. It shows that profit margins aren't more important than actual protection.
How This Affects Other VPN Providers
Proton VPN's move puts pressure on competitors to do the same thing. When one major player in an industry raises the bar, others have to follow or they look negligent by comparison.
ExpressVPN, NordVPN, and CyberGhost have all been gradually deprecating legacy protocols, but they've been doing it more quietly and without hard deadlines. Proton's public announcement and firm deadline will likely accelerate their deprecation timelines.
This is good for users overall because it means the entire VPN industry is being pushed toward better security standards. But it also means other providers will eventually follow with similar migrations, so if you're using a different VPN service, pay attention to any announcements they make about configuration updates.
For users running multiple VPN services across different devices, this means you might have to coordinate several migrations over the next 12 months. It's worth keeping track of which services have which deadlines.
The Broader Context of VPN Security Evolution
This deprecation is part of a larger trend in the VPN industry toward adopting newer protocols entirely. OpenVPN has been around since 2002, and while it's still solid, newer protocols like WireGuard and the commercial variant Mullvad have demonstrated that significant improvements are possible.
WireGuard, for example, is about 4,000 lines of code compared to OpenVPN's 100,000+ lines. Less code means fewer potential vulnerabilities. It's also cryptographically more modern, using Curve25519 for key exchange instead of the RSA-based methods that older OpenVPN versions relied on.
Some VPN providers are already moving to WireGuard as their primary protocol. Proton VPN offers WireGuard as an option on newer clients, though they're still maintaining OpenVPN support for users who need or prefer it.
The trend is clear: the VPN industry is moving toward simpler, more modern protocols with stronger cryptographic foundations. Proton's deprecation of legacy OpenVPN configurations is just one step in this larger evolution.
What Happens If You Miss the Deadline
It's worth understanding what actually happens on February 28. Proton VPN won't delete your account or ban you. What will happen is simple: connections using legacy OpenVPN configurations will fail.
If you try to connect to Proton VPN using an old configuration file, the connection attempt will timeout or return an authentication error. Your OpenVPN client might show a message like "TLS 1.0 is not supported" or "Cipher negotiation failed." This will be confusing if you haven't been paying attention to the deprecation announcement, but the cause is straightforward: the configuration is too old.
At that point, you'll have to do the migration anyway, just in a panic on whatever day you realize your VPN isn't working. So it's much better to handle it proactively now.
Proton's infrastructure will simply stop accepting connections that try to establish TLS 1.0 or 1.1 handshakes. There's no special error page or grace period. The servers just won't negotiate the connection.
Best Practices for OpenVPN Configuration Management
Beyond just migrating to new configurations, there are some broader practices that make managing VPN setups easier going forward.
First, automate your configuration updates. If you're managing VPN settings across multiple devices, use configuration management tools like Ansible or Terraform to standardize deployments. This makes it trivial to push new configuration files across your entire infrastructure.
Second, document where your configuration files come from. If you downloaded them in 2019, write that down. When Proton or any other VPN provider announces deprecations, you'll immediately know which of your configurations are affected.
Third, set calendar reminders for deprecation deadlines. This sounds obvious, but people miss these all the time. The day you read about a deprecation, add it to your calendar immediately. Set it for one month before the deadline so you have time to plan.
Fourth, test your VPN connections regularly. Don't just set it and forget it. Every month, verify that your VPN is actually connecting properly. This catches configuration problems before they become crises.
Fifth, keep your VPN client software updated. This is the easiest way to avoid these problems. If you use the native Proton VPN app instead of raw OpenVPN configurations, updates happen automatically and you never have to think about protocol versions.
The Security Implications of Modern VPN Standards
The shift to modern protocols and cipher suites has tangible security benefits that you should understand.
With TLS 1.3 and modern cipher suites, the security margin against cryptanalytic attacks is significantly improved. The key exchange process is more resistant to eavesdropping attempts. Even if someone captures your encrypted traffic, the mathematical complexity of breaking it is orders of magnitude higher with modern standards.
Forward secrecy improvements mean that compromised keys don't retroactively decrypt past sessions. This is critical because it limits the damage if an attacker ever manages to steal encryption keys from Proton's infrastructure.
Modern cipher suites like ChaCha20-Poly1305 are also resistant to timing attacks, which are sophisticated attacks where adversaries measure how long cryptographic operations take to infer information about the keys. Older ciphers had subtle timing variations that could potentially leak information.
The authentication mechanisms are also stronger. Modern TLS uses HMAC-based constructions that are more resistant to forgery attacks than older authentication methods.
None of this means the old systems were completely broken. OpenVPN with TLS 1.2 and AES-256 is still reasonably secure. But "reasonably secure" isn't good enough for a security company. These improvements push from "probably won't be cracked" to "shouldn't be crackable with known techniques."
Implementation Considerations for Business Users
If you're managing VPN connections for a business, this deprecation requires some planning at an organizational level.
First, audit your VPN infrastructure. Find every device, server, and network appliance that uses Proton VPN configurations. Document when each was last updated. Create a spreadsheet listing each system and which configuration version it uses.
Next, create a migration plan. Group your systems by criticality. Business-critical systems should be migrated first, followed by less critical systems, with non-critical systems last. This lets you identify and fix problems on less important systems before you update your primary infrastructure.
Test migrations in a non-production environment first. If you've got a staging environment or test network, use that to verify that the new configurations work properly before touching production systems.
Communicate the migration to your team. If you've got multiple people managing infrastructure, make sure they all understand that the deadline exists and why. Assign clear ownership for the migration so it doesn't fall through the cracks.
Consider using Proton's premium business plan if you're running a significant VPN infrastructure for a company. The business tier includes dedicated support that can help with large-scale migrations.
Schedule your migration for a maintenance window. Don't migrate critical systems during business hours. Do it during a planned maintenance window when you can monitor the transition and quickly roll back if something breaks.
Comparing Proton VPN to Competing VPN Services
Proton VPN's aggressive stance on security standards is notable when compared to other major VPN providers.
ExpressVPN has been updating its protocols gradually but hasn't announced a hard deprecation date for legacy configurations. They tend to be more conservative about breaking changes.
NordVPN is in a similar position. They're moving toward newer protocols but supporting legacy setups for backward compatibility.
CyberGhost offers good modern security but is generally more focused on consumer convenience than technical optimization. Their deprecation approach would likely be gentler.
Proton VPN's approach is the most aggressive among major providers, which reflects their positioning as a security-first company rather than a convenience-first company. If you value cutting-edge security, this is a feature, not a bug. If you value minimal disruption, you might prefer a competitor with a more gradual approach.
It's worth noting that Proton VPN also offers WireGuard protocol as an option, which is more modern than OpenVPN regardless of which configuration version you're using. If you're open to trying different protocols, WireGuard might be worth exploring alongside or instead of OpenVPN.
Timeline Expectations and Important Milestones
Understanding the full timeline helps you plan your migration.
As of now, we're roughly three months from the February 28 deadline. Proton has been sending notifications to affected users for several months already, so most people should be aware of the change.
In January 2025, you should expect Proton to increase their notifications as the deadline approaches. This is the point where you need to actually take action, not just read about it.
In early February, Proton might push an update to their documentation or release a migration guide. Pay attention to any official communications during this period.
By mid-February, ideally you should have completed your migration. This gives you a buffer in case you run into unexpected issues.
On February 28, Proton's servers will stop accepting legacy configuration connections. At this point, legacy setups are completely non-functional.
If you miss the deadline, you can still migrate afterward. There's no punishment. You just won't have VPN access until you complete the migration.
Automation Scripts for Large-Scale Migrations
If you need to migrate VPN configurations across multiple systems, automation can save significant time.
For Linux systems, you can create a simple bash script that downloads new configurations, backs up old ones, and restarts the VPN:
bash#!/bin/bash
BACKUP_DIR="/home/vpn/backup_$(date +%Y%m%d)"
CONFIG_DIR="/etc/openvpn/client"
# Create backup
mkdir -p "$BACKUP_DIR"
cp "$CONFIG_DIR"/*.ovpn "$BACKUP_DIR"/
# Download new configs
cd "$CONFIG_DIR"
wget https://protonvpn.com/download/OpenVPN_configs/linux/ProtonVPN_linux.zip
unzip -o ProtonVPN_linux.zip
# Restart OpenVPN
sudo systemctl restart openvpn-client@YourConfigName
echo "Migration complete. Old configs backed up to $BACKUP_DIR"
For Windows systems using PowerShell, you can create similar automation that downloads configurations from Proton's server and updates your OpenVPN client.
For network devices like Ubiquiti Edge Routers or pfSense boxes, the process is similar but varies by device type. Most modern network appliances support downloading configuration files via HTTPS, so you can automate the process through their REST APIs or SSH scripts.
The key principle is: automate what you can, document what you can't, and test everything before deploying to production.
Future-Proofing Your VPN Infrastructure
Beyond just migrating to current standards, you can take steps to make your VPN infrastructure more resilient to future deprecations.
First, plan to adopt WireGuard as your primary protocol if your use case supports it. WireGuard is simpler, faster, and more modern than OpenVPN. Most modern VPN clients and services support it, including Proton VPN.
Second, stay informed about VPN provider announcements. Subscribe to Proton VPN's security blog or email newsletter. When major providers announce protocol changes, you want to know about them early.
Third, maintain regular update cycles for your VPN infrastructure. Don't let configurations get stale. Schedule regular reviews of your VPN setup to ensure you're running current versions.
Fourth, build flexibility into your infrastructure so you can support multiple VPN providers. This sounds like overkill, but it means if one provider deprecates something, you're not locked in. You can easily switch or supplement with another service.
Fifth, document your VPN configurations thoroughly. Include comments about when they were last updated, why they use specific parameters, and what they're designed to protect. This makes it much easier to maintain them over time.
The broader point is that VPN security is an ongoing process, not a one-time setup. The infrastructure you deploy today will likely need updates in 2-3 years as standards evolve further. Building that expectation into your architecture makes future transitions smoother.
FAQ
What exactly is Proton VPN deprecating?
Proton VPN is discontinuing support for legacy OpenVPN configurations that use older TLS versions (1.0 and 1.1), outdated cipher suites, and weaker encryption methods. These configurations rely on cryptographic standards that are no longer considered sufficiently secure for modern threat environments. The deprecation affects custom OpenVPN setup files downloaded before approximately 2022, not the official Proton VPN native applications.
When is the hard deadline for this migration?
The hard deadline is February 28, 2025. After this date, Proton VPN's servers will no longer accept connections using legacy OpenVPN configurations. If you attempt to connect with an old configuration file, the connection will fail with a TLS negotiation or authentication error. There is no grace period or extension available.
Will this affect me if I use the Proton VPN app on my phone or computer?
No, if you're using the official Proton VPN application on Windows, macOS, iOS, or Android, you are completely unaffected. The native apps have been using modern protocols for several years and updated automatically. You don't need to take any action if you rely on the official applications.
How do I know if I'm using a legacy OpenVPN configuration?
You can check by examining your .ovpn configuration file. Open it with a text editor and search for "tls-version" or "cipher". If you see TLS 1.0 or 1.1, or ciphers like AES-256-CBC or BF-CBC, your configuration is legacy. Proton VPN also offers a diagnostic tool on their website where you can paste your configuration file to instantly determine if it's deprecated.
What happens if I miss the February 28 deadline?
Your VPN connection using the legacy configuration will simply stop working. The Proton VPN servers will refuse connections that attempt to establish old TLS handshakes. You won't be able to access the VPN until you update to a new configuration file. There's no penalty or account suspension—you just won't have VPN functionality until you complete the migration.
How long does it take to migrate to a new configuration?
The actual migration typically takes 10-15 minutes. You download new configuration files from Proton's website, replace your old files, and restart your VPN client. The only complexity is if you've customized your configuration with special parameters—in that case, you need to merge those custom settings into the new configuration, which might take an additional 10-20 minutes depending on how complex your setup is.
Are WireGuard configurations also being deprecated?
No, WireGuard is a newer protocol that Proton VPN is actively promoting. It uses modern cryptography by design and doesn't have the same legacy compatibility issues as OpenVPN. If you're concerned about future deprecations, WireGuard is a good protocol to standardize on. Proton VPN supports it across their full platform.
Can I keep using the old configurations if I ignore the deadline?
No, this is a hard technical cutoff. Proton's servers are being reconfigured to not accept legacy TLS versions or cipher suites. It doesn't matter if you ignore the announcement—when February 28 arrives, your old configuration simply won't connect. You can't negotiate with the servers or request an exception.
What if I'm running VPN on a router or server?
The migration process is the same conceptually, but varies by device. You replace the old configuration file with a new one and restart the VPN service. For specific device types like Ubiquiti Edge Routers, pfSense boxes, or Linux servers, the specific steps differ, but the principle is identical. Proton's support documentation includes device-specific guides.
Why is Proton doing this instead of supporting old configurations indefinitely?
Supporting legacy protocols indefinitely creates security complexity and liability. Each additional protocol version increases code paths and potential vulnerabilities. By making a clean break, Proton simplifies their infrastructure, reduces attack surface, and signals to the security community that they're committed to modern standards rather than maximum backward compatibility. It also forces users to upgrade rather than indefinitely procrastinating on security updates.
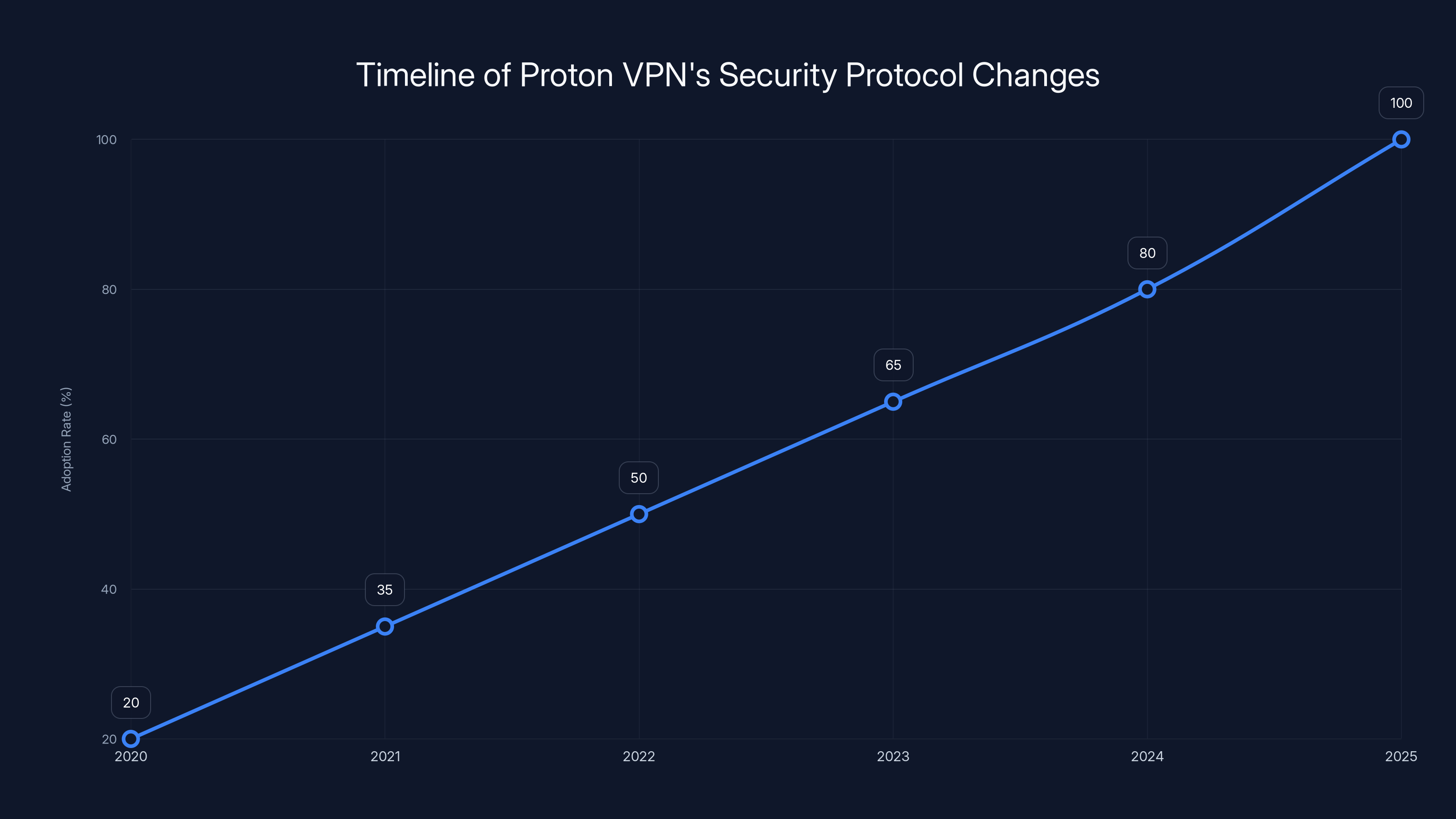
Proton VPN is transitioning to modern security protocols, with full adoption expected by February 2025. Estimated data shows a steady increase in protocol upgrades.
Key Takeaways
Proton VPN's deprecation of legacy OpenVPN configurations represents a significant but necessary step toward modern VPN security standards. Here's what you need to know:
The Deadline Is Real: February 28, 2025 is a hard cutoff. After this date, legacy configurations simply won't work. There's no extension or grace period available.
Most Users Are Unaffected: If you use Proton VPN's official applications on any platform, you don't need to do anything. The native apps already use modern protocols.
Power Users Must Act: Anyone using custom OpenVPN configuration files, router-level VPN setups, or server-based VPN connections needs to update to new configurations before the deadline.
Migration Is Simple: Downloading new configurations and replacing old ones takes about 15 minutes for most users. The actual technical process is straightforward.
This Improves Security: Modern TLS 1.3, stronger cipher suites, and updated encryption methods provide tangible security improvements against current and future threat vectors.
Industry Trend: Other VPN providers will likely follow Proton's lead, making this part of a broader industry shift toward better security standards.
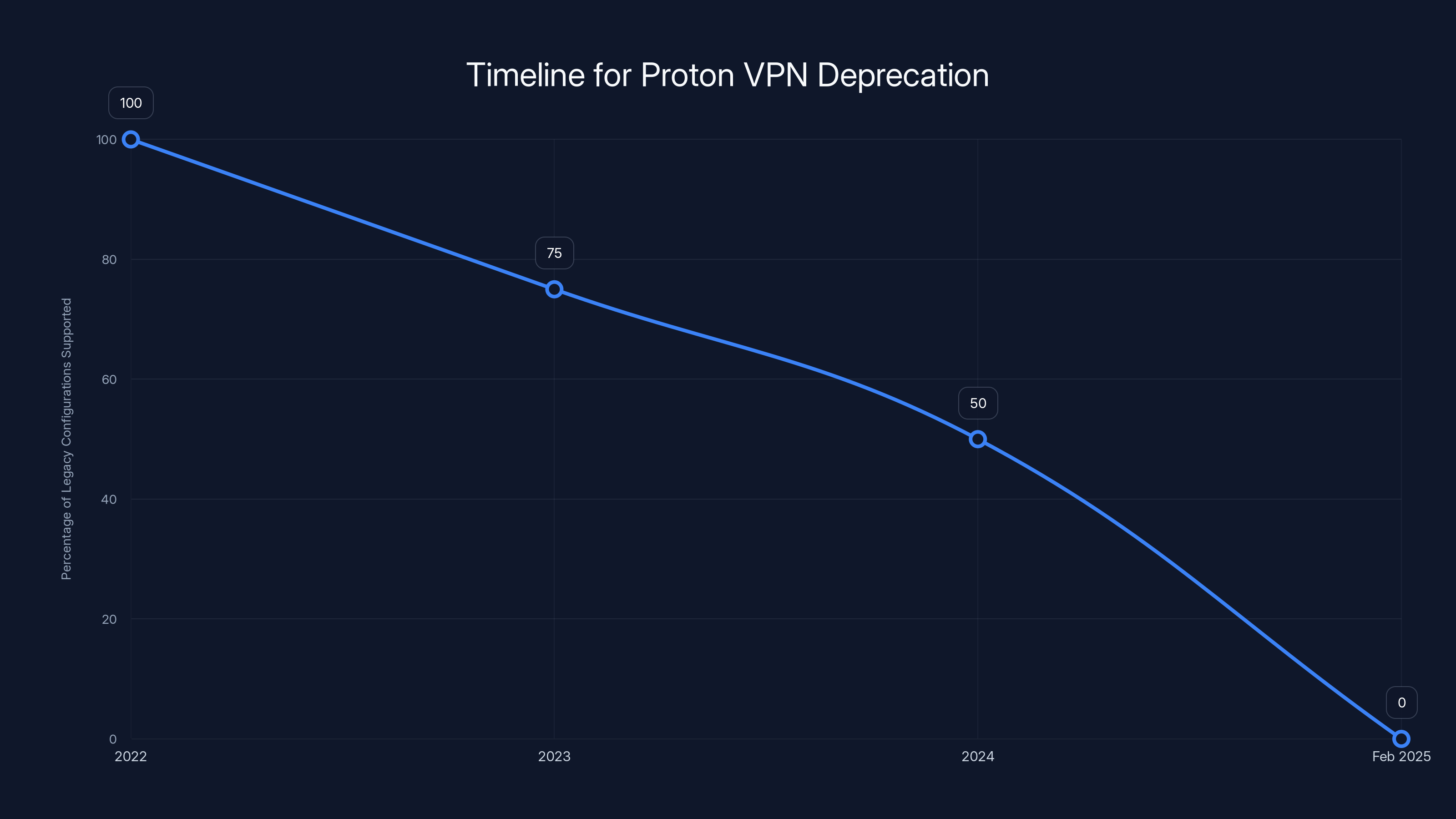
Proton VPN will discontinue support for legacy OpenVPN configurations by February 28, 2025. Users must migrate to updated configurations to maintain service.
Related Articles
- Best VPN Service 2026: Complete Guide & Alternatives
- Mullvad's OpenVPN Shutdown: Complete Migration Guide [2025]
- Microsoft's Windows 11 Emergency Fix: Shutdown Crisis Explained [2025]
- Supreme Court Hacker Posted Stolen Data on Instagram [2025]
- Gmail Email Address Change Feature: What We Know [2025]
- Grok's Deepfake Crisis: The Ashley St. Clair Lawsuit and AI Accountability [2025]
![Proton VPN Kills Legacy OpenVPN: What You Need to Know [2025]](https://tryrunable.com/blog/proton-vpn-kills-legacy-openvpn-what-you-need-to-know-2025/image-1-1768835290967.jpg)



