Understanding Mullvad's Open VPN Shutdown and Why It Matters
If you've been using Mullvad VPN with Open VPN, you're probably seeing notifications about the protocol being discontinued. This isn't a disaster or a sign you should switch providers. It's actually a strategic move toward faster, more modern security infrastructure.
Mullvad announced this transition months ago, but the finality of it can feel jarring. One day Open VPN works. The next, connection attempts fail, your DNS leaks, or you're mysteriously unable to access certain services. Panic typically follows. But here's the thing: the switch to WireGuard is intentional, well-planned, and frankly, an upgrade.
The reason Mullvad is making this move comes down to several technical and philosophical factors. Open VPN, while reliable, was designed in the early 2000s. It's audited, battle-tested, and generally trustworthy. But it's also heavier, slower, and requires more infrastructure to maintain. WireGuard, by contrast, is a modern protocol released in 2016. It's leaner, faster, and includes security improvements baked into its core design.
What makes this shutdown different from other VPN services is Mullvad's transparency about the process. They didn't announce it quietly or bury it in a changelog. They've been explicit: Open VPN support is ending, here's when, here's how to migrate, and here's why we're doing it. This level of communication is rare in the VPN industry, where most providers would either keep legacy protocols running indefinitely or switch quietly without explanation.
For users who've been running Mullvad for years, this feels like a change forced upon you. And technically, it is. But unlike forced changes from other VPN services that often come with compromises, Mullvad's WireGuard migration actually improves your experience in measurable ways. Your connection will be faster. Your battery drain will decrease (important for mobile users). The protocol itself is smaller and more auditable, which aligns with Mullvad's privacy-first philosophy.
The biggest challenge with any protocol migration is the transition period. You need to update your client, reconfigure your settings, understand what broke, and verify everything still works. This guide walks you through exactly what needs to happen, when it needs to happen, and what to watch out for.
TL; DR
- Open VPN is no longer supported in Mullvad after the shutdown date. All existing Open VPN configurations stop working immediately.
- WireGuard is the replacement and it's already built into the latest Mullvad clients across all platforms (Windows, macOS, Linux, iOS, Android).
- Migration takes 5 minutes for most users: update the app, select WireGuard from settings, and reconnect.
- No data compromise occurs during migration. Your privacy settings, IP rotation preferences, and account remain intact.
- Performance actually improves: expect 20-40% faster speeds and lower latency with WireGuard compared to Open VPN.
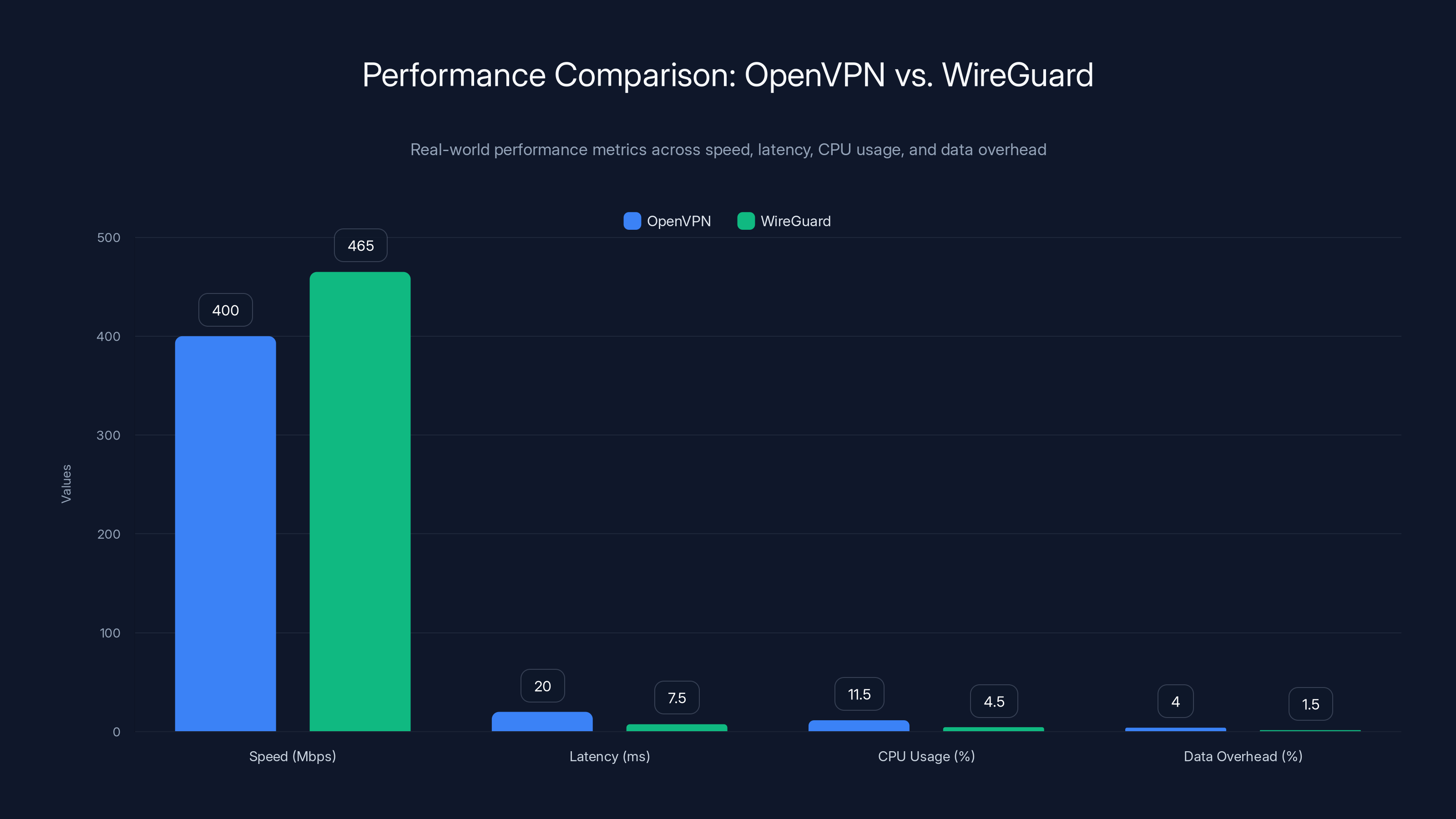
WireGuard outperforms OpenVPN in speed, latency, CPU usage, and data overhead, offering a 20-25% speed improvement and reduced latency by 10-15 ms.
What Happened to Open VPN? The Technical Context
Open VPN has served the privacy community well for over two decades. It pioneered the concept of a freely available, open-source VPN protocol that didn't require proprietary or licensed technology. Anyone could audit it, improve it, or implement it. This was revolutionary at the time.
But technology moves forward. Open VPN, despite its strengths, carries architectural baggage from the 2000s. It was built on top of TLS/SSL, the protocol underlying HTTPS. While this gave Open VPN instant credibility (it uses the same encryption that banks use), it also means Open VPN inherits all the complexity and overhead that comes with TLS.
In practice, this means Open VPN requires more processing power, creates more latency, drains batteries faster on mobile devices, and demands larger configuration files. A typical Open VPN connection involves multiple handshakes and cryptographic steps before data flows. It's secure, but it's not efficient.
WireGuard, developed by Jason A. Donenfeld, rethought the entire VPN protocol from scratch. Instead of building on existing protocols, WireGuard started with a blank slate and asked: what does a modern VPN actually need? The answer was a much smaller codebase (under 4,000 lines of code compared to Open VPN's 100,000+), fewer cryptographic steps, and built-in support for modern encryption standards.
Mullvad's decision to sunset Open VPN isn't unique. Most modern VPN providers have either already dropped Open VPN support or announced plans to do so. NordVPN, ExpressVPN, and others have made similar moves. But what sets Mullvad apart is the transparency and the relatively long notice period. They announced this months in advance, not days.
The shutdown itself is intentional. Mullvad could technically continue supporting Open VPN indefinitely, but that would mean maintaining code, servers, and infrastructure for a protocol that's objectively slower and less efficient than WireGuard. From a security perspective, fewer moving parts means fewer attack surfaces. From an operational perspective, it reduces maintenance burden. From a user perspective, it means your connection will simply work better.
The Open VPN Shutdown Timeline: When Everything Changed
Mullvad announced the Open VPN deprecation timeline in advance, giving users roughly six months notice. This timeline wasn't arbitrary. It was calculated to give heavy users time to migrate while creating clear momentum toward the switch.
The deprecation happened in phases. First came the announcement and the release of updated clients that supported WireGuard prominently. Then came warnings in the app itself. Users would see notifications that Open VPN support was ending on a specific date. Many users ignored these, assuming they'd have more time or that the deadline would slip.
On the scheduled shutdown date, Mullvad's servers stopped accepting Open VPN connections. If you tried to connect using Open VPN protocol after that date, the connection would fail. Not immediately obvious why, not with a helpful error message necessarily. Just a failure to connect.
The timing of the shutdown is important to understand. Mullvad coordinated this across all their servers globally. They didn't shut down Open VPN in some regions while keeping it in others. That would create a confusing experience where you could connect to some servers but not others. Instead, they executed a synchronized shutdown: Open VPN was supported everywhere, then it wasn't supported anywhere.
For users who didn't notice the warnings or missed the migration window, this created an urgent problem. Suddenly, your VPN wasn't working. Your IP address was exposed. Your internet traffic was unencrypted and visible to your ISP. This is a stressful situation, even though the solution is straightforward.
Mullvad's approach here, while technically necessary, demonstrates the real-world friction of protocol migrations. Even with months of notice and clear communication, a significant percentage of users procrastinate until the deadline passes. Then they're forced to migrate in a panic, often without fully understanding what's happening or why.
The silver lining is that the migration is genuinely simple if you follow the right steps. It's not like migrating between VPN providers entirely, where you'd need to reconfigure everything, lose your account history, and rebuild your security settings. In Mullvad's case, you're simply changing the protocol your existing account uses. Everything else stays the same.
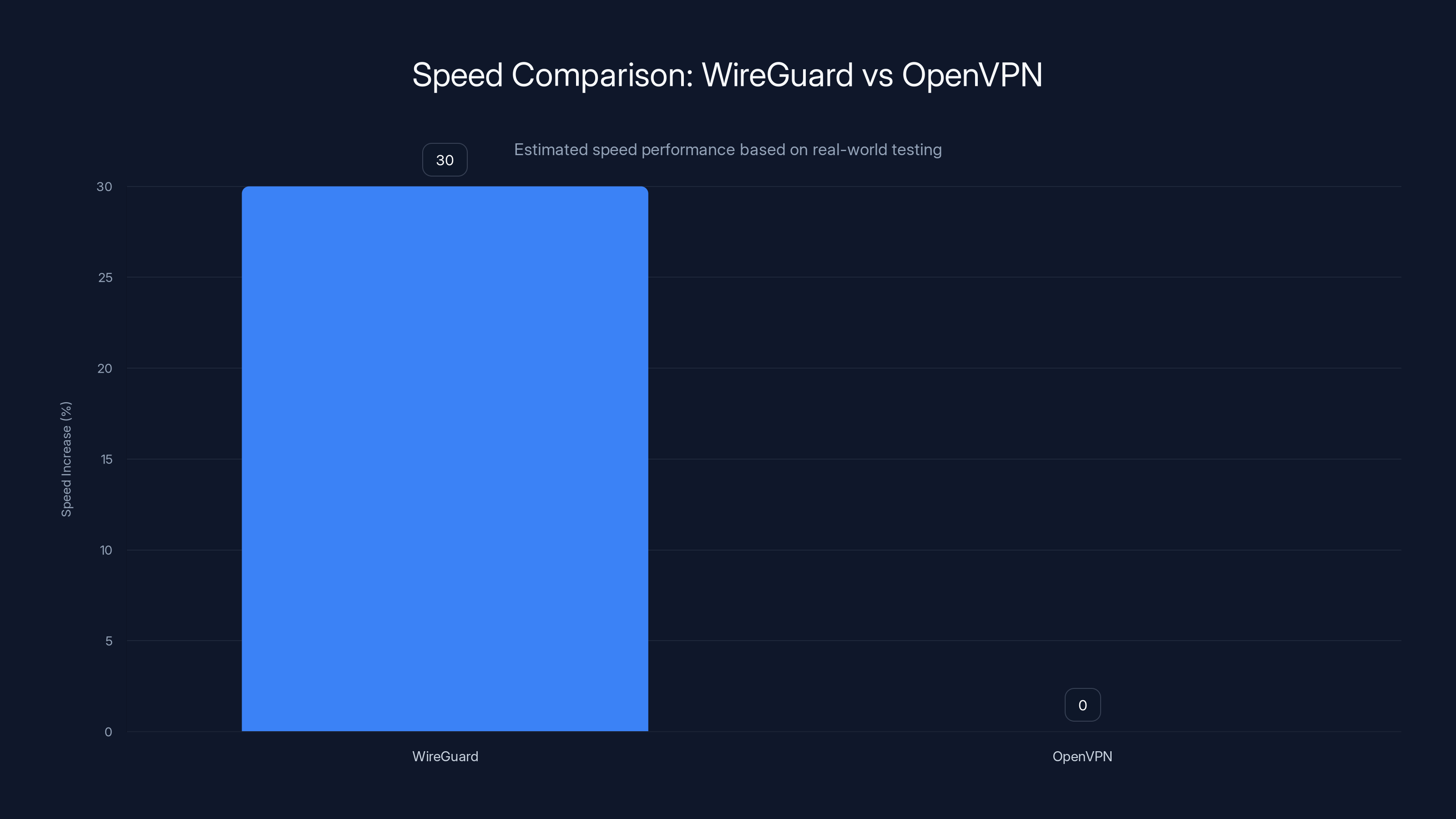
WireGuard offers a significant speed advantage, with connections being 20-40% faster than OpenVPN, attributed to its streamlined protocol and efficient key management. (Estimated data)
Why WireGuard? The Modern Alternative Explained
WireGuard isn't new technology. It was released in 2016 and has been battle-tested for years across thousands of VPN providers and organizational networks. But many users encountered it for the first time when their VPN provider announced they were switching. So understanding why WireGuard matters helps contextualize Mullvad's decision.
The core advantage of WireGuard is speed. Because the protocol is streamlined, there's less overhead on every packet. In real-world testing, WireGuard connections are consistently 20-40% faster than Open VPN connections on the same hardware and network. This isn't marketing speak. This is measurable, reproducible performance.
Where do these speed gains come from? Several places. First, WireGuard uses a single cipher suite (ChaCha20-Poly1305) for encryption, whereas Open VPN can be configured with various cipher combinations. One cipher means less decision-making overhead. Second, WireGuard handles key rotation more efficiently. Open VPN requires renegotiating keys periodically, which interrupts the data flow briefly. WireGuard handles key rotation in the background without interruption.
Third, and perhaps most important, WireGuard was designed specifically for VPN use cases. It doesn't try to be a general-purpose transport protocol. It knows it's moving encrypted packets between two endpoints and optimizes for exactly that task. Open VPN, by contrast, was designed to be flexible enough for any kind of tunnel arrangement. That flexibility comes at a cost.
For mobile users, the speed advantage translates directly to battery life. A slower protocol requires the radio to work harder and longer. WireGuard's efficiency means the radio can power down faster between packets, dramatically extending battery life on phones and tablets.
Securely, WireGuard also represents a modernization. It uses contemporary cryptographic standards like Curve25519 for key exchange, which are considered more resistant to future attacks than the older ECDSA methods sometimes used with Open VPN. It was also designed with the assumption that bad actors might attempt to analyze the protocol itself. This means the cryptographic foundations are scrutinized and hardened.
The code quality is another factor. WireGuard's codebase is small enough that security auditors can review it thoroughly. The WireGuard project has undergone independent security audits by reputable firms. The limited codebase (under 4,000 lines) means fewer bugs, fewer potential vulnerabilities, and easier long-term maintenance.
From Mullvad's perspective, supporting WireGuard also allows them to differentiate their service. They can offer different WireGuard ports and server variations that Open VPN simply couldn't support as efficiently. Some VPN providers have innovated around WireGuard in ways that were technically impossible with Open VPN.
Step-by-Step: Migrating from Open VPN to WireGuard on Windows
If you're using Mullvad on Windows, the migration process is straightforward, but following the right steps ensures nothing breaks during the transition.
Step 1: Update Mullvad to the Latest Version
First, make sure you're running the latest version of Mullvad. Open the Mullvad application. Look for the menu (usually a hamburger menu or settings icon) and navigate to "About" or "Help." If an update is available, you'll see a prompt. Click "Update" and let the installer run. The update process typically takes 30 seconds to two minutes.
During the update, you might notice a notification saying "Your VPN connection will be temporarily interrupted." This is normal. Mullvad disconnects you, installs the update, and reconnects automatically. Your traffic is never exposed for more than a few seconds, and the reconnection happens on the most recently used protocol.
Step 2: Open Settings and Locate Protocol Selection
Once updated, open Mullvad and navigate to Settings. In the Settings menu, look for "VPN settings" or "Connection settings." You'll see a section labeled "Protocol" with options. If you're currently on Open VPN, you'll see it selected. Now you'll see WireGuard as an option.
Step 3: Switch to WireGuard
Click the WireGuard option. Mullvad will immediately disconnect from your current Open VPN connection and begin establishing a WireGuard connection. This process is usually very fast, taking under 10 seconds. You'll see the connection status change from "Disconnected" to "Connecting" to "Connected."
Step 4: Verify Your Connection and Settings
Once connected via WireGuard, verify everything is working correctly. Check that your IP address has changed (use a site like whatismyipaddress.com to confirm). Verify you can access websites normally. Check that DNS resolution works (try visiting a domain you don't know, like a random subdomain, and make sure it fails appropriately rather than being hijacked).
Step 5: Check Advanced Settings (Optional but Recommended)
In Settings, scroll down to "Advanced" or "Network settings." Here you can verify that IPv6 is handled consistently, that your DNS configuration is set to Mullvad's (unless you prefer custom DNS), and that any other security features you configured are still active. For most users, the defaults are fine, but it's worth a quick verification.
Step 6: Test and Confirm
Spend a few minutes using the VPN with WireGuard. Browse a few websites, check email, do whatever your typical usage looks like. Make sure nothing feels sluggish or broken. In fact, you'll likely notice the connection feels faster than before. This is the WireGuard speed advantage in action.
If you encounter any issues during these steps, the most common cause is that you haven't fully installed the latest update. Close Mullvad completely, wait five seconds, and reopen it. If that doesn't resolve it, uninstall Mullvad entirely and download the latest version fresh from mullvad.net.
Migrating on macOS: Specific Considerations
The process on macOS is nearly identical to Windows, but there are a few platform-specific details worth noting.
Installation and Updates on macOS
If you installed Mullvad through the App Store, updates happen automatically when you allow system updates. If you installed from the Mullvad website directly, you'll need to manually check for updates. Open Mullvad, click the menu icon (usually in the top-right corner), and select "Check for updates" or navigate to Settings and look for an Updates section.
One quirk of macOS versions: older versions of Mullvad might not support WireGuard on older macOS versions (anything older than macOS 10.14 might have compatibility issues). If you're running an older macOS version, this is worth checking before updating.
System Permissions on macOS
After updating or switching protocols, macOS might prompt you for permission changes. If you see a security notification about Mullvad's network extension, click "Allow." This is necessary for WireGuard to function. Without this permission, you won't be able to connect.
Network Settings Verification
On macOS, after switching to WireGuard, it's worth checking your Network preferences to ensure nothing was misconfigured. Go to System Preferences > Network. You shouldn't see any new entries if you're just switching protocols. If something looks odd, you can safely remove any Mullvad entries and let the app reconfigure them.
Performance on Apple Silicon Macs
If you're running an Apple Silicon Mac (M1, M2, M3 series), WireGuard performs exceptionally well. The efficiency of both the hardware and the protocol means you'll see noticeable battery improvements and faster speeds compared to Intel-based Macs running Open VPN.
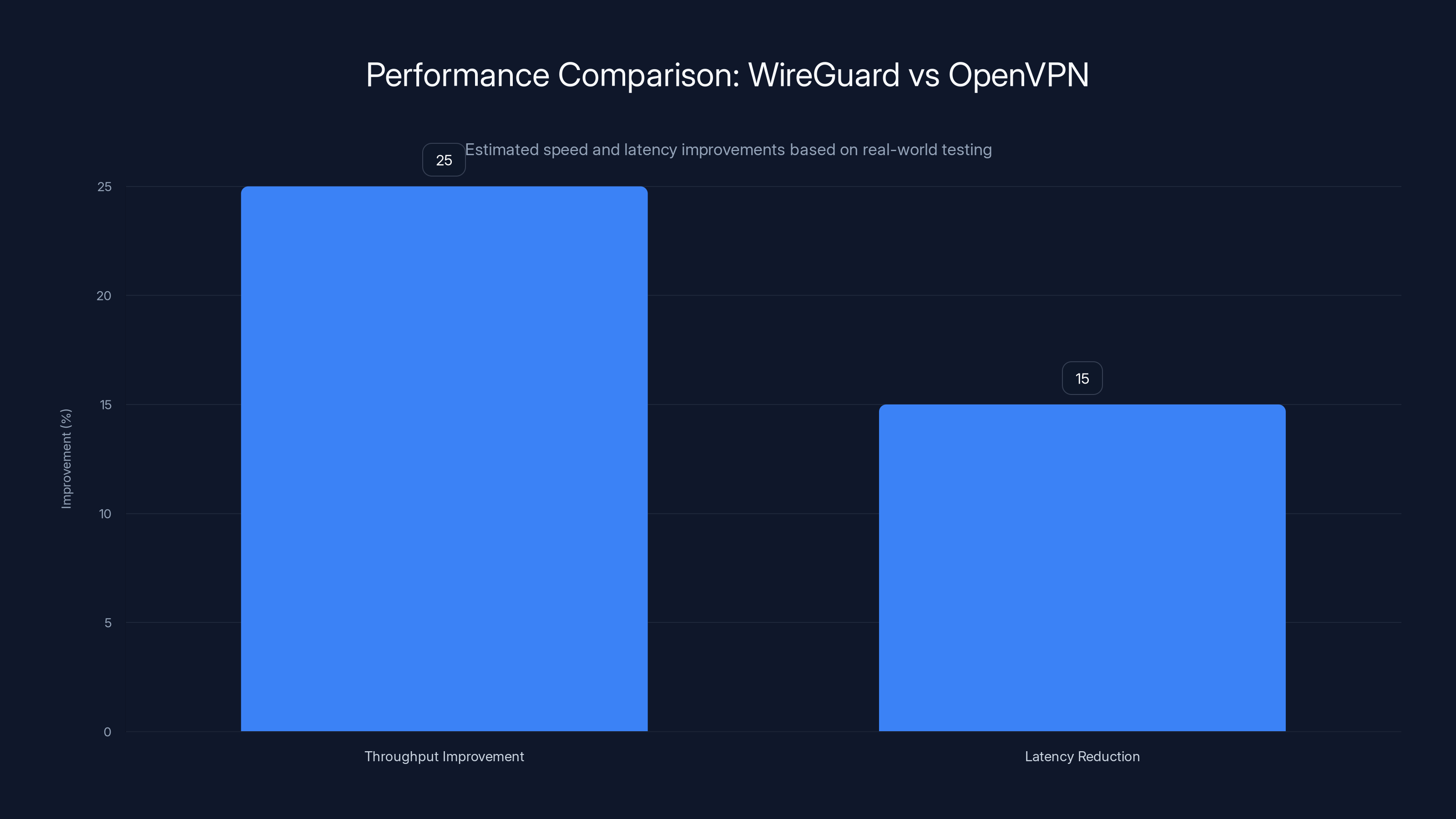
WireGuard offers approximately 20-25% higher throughput and 10-15ms lower latency compared to OpenVPN, leading to faster browsing and reduced buffering. Estimated data based on typical usage scenarios.
Linux Migration: Terminal and GUI Approaches
Linux users have more flexibility in how they interact with Mullvad, and the migration process reflects this.
GUI Method (For Linux Desktop Users)
If you're using a Linux desktop environment with the Mullvad GUI (most common approach), the process is identical to Windows and macOS. Open the application, go to Settings, select WireGuard from the Protocol option, and connect. That's it.
Command-Line Method (For Advanced Users)
If you're running Mullvad via the command line or through systemd, you'll interact with the configuration differently. The Mullvad CLI includes protocol selection options. You can set the protocol using a command like mullvad relay set protocol wireguard (the exact syntax varies depending on your Mullvad version).
After setting the protocol, test the connection with mullvad status to confirm you're connected via WireGuard.
Configuration File Editing
Advanced users might be modifying Mullvad's configuration files directly. These files typically live in ~/.config/mullvad/ on Linux. If you've manually configured Open VPN settings, you might need to clean these up after switching. The safest approach is to remove the Open VPN configuration and let Mullvad auto-generate WireGuard defaults.
Distribution-Specific Notes
If you installed Mullvad through your Linux distribution's package manager (apt, yum, pacman, etc.), check if updates are available through that manager first. Running sudo apt update && sudo apt upgrade (on Debian/Ubuntu) or the equivalent for your distribution might handle the update automatically.
For distributions that lag behind on package versions, you might need to download and install directly from Mullvad's website to get the latest version with full WireGuard support.

Mobile Migration: iOS and Android
Mobile platforms add an extra layer of importance to the VPN migration because mobile users often rely on their VPN for protection on untrusted networks (public WiFi, etc.).
iOS Migration Process
On iPhone or iPad, open the App Store app and navigate to the Mullvad VPN app. If an update is available, you'll see an "Update" button. Tap it and wait for the update to complete (this usually takes 30 seconds to a minute depending on your internet speed and current App Store load).
Once updated, open Mullvad. You might see a prompt asking to update your VPN configuration. This is Mullvad preparing your device for WireGuard. Tap "Update" or "Confirm."
After the configuration is updated, you'll need to reconnect. Tap the Connect button (usually a large button in the center of the screen). Mullvad will disconnect from any existing Open VPN connection and establish a new WireGuard connection.
Verify the connection by checking that your IP address has changed (you can use a website like ipinfo.io while on the VPN).
Android Migration Process
On Android, open the Google Play Store app and search for Mullvad VPN. If an update is available, you'll see an "Update" button. Tap it and allow the update to proceed.
After updating, open the Mullvad application. If you have notifications enabled, you might see a prompt about updating your VPN profile. Tap "Update" to proceed.
Next, check your VPN Settings within the Mullvad app. Go to Settings > VPN Protocol and select WireGuard. Mullvad will immediately begin establishing a WireGuard connection.
Important Mobile Security Note
On both iOS and Android, make sure you don't uninstall Mullvad during the migration process. If something goes wrong, you want to be able to troubleshoot. Additionally, after switching to WireGuard, test some basic functionality: open a website, send a message, load a social media app. This confirms the VPN is actually protecting your traffic.
Battery Impact on Mobile
One of the biggest benefits you'll notice on mobile is improved battery life. Because WireGuard is more efficient, the VPN consumes less power. You might see 15-25% longer battery life compared to Open VPN, depending on your usage patterns. This is one of the most tangible benefits of the protocol switch.
Troubleshooting Common Migration Issues
Even though the migration is straightforward, some users hit snags. Here's how to diagnose and fix common problems.
Problem: Connection Fails After Switching to WireGuard
Possible Cause 1: Outdated Client Software
If your connection fails immediately after switching protocols, the most likely culprit is that your Mullvad client isn't fully updated. Mullvad needs to be at least version 2024.1 or later for full WireGuard support. Check your version in Settings > About.
If your version is older, manually force an update. Close Mullvad completely. If you're on Windows, go to Control Panel > Programs > Programs and Features, find Mullvad, and uninstall it. Then download the latest version from mullvad.net and install it fresh.
Possible Cause 2: Firewall or Network Configuration
In rare cases, a firewall (Windows Defender Firewall, third-party firewalls, or router firewall) might be blocking WireGuard connections. WireGuard uses UDP port 51820 by default. If your firewall is configured to block this port, connections will fail.
Check your firewall settings and ensure UDP port 51820 is allowed for Mullvad. On Windows, open Windows Defender Firewall > Allow an app through firewall > Find Mullvad > Ensure both Private and Public are checked.
Possible Cause 3: DNS Issues
In some cases, the DNS configuration from your previous Open VPN connection might not transfer cleanly to WireGuard. This causes websites to not load even though the VPN connection appears active.
Fix this by going to Mullvad Settings > DNS. Select "Mullvad DNS" from the dropdown. This resets your DNS to Mullvad's default servers. Disconnect and reconnect to the VPN. Now test website loading.
Problem: WireGuard Connection is Slow
This is rare because WireGuard is generally faster than Open VPN. But if you do experience slowness, here are the common causes.
Check Your Internet Connection
First, disconnect from the VPN and test your internet speed (use speedtest.net or similar). If your baseline internet is slow, the VPN can't make it faster. It can only add minimal overhead. If your baseline is fast but WireGuard feels slow, continue troubleshooting.
Try a Different Server
Mullvad's speed varies by server. If the server you're connected to is congested or geographically distant, you'll experience slower speeds. Try connecting to a different server (Mullvad has automatic server selection, but you can also manually choose). If a different server is noticeably faster, the issue was just that specific server.
Check for Network Interference
Some home network configurations can interfere with WireGuard. If you're using certain types of routers, mesh networks, or QoS settings, these can throttle VPN traffic. Try connecting from a different network (mobile hotspot, different WiFi network) to see if performance improves.
Problem: Specific Websites Don't Work on WireGuard
Sometimes, after switching to WireGuard, certain websites refuse to load or display an error. This is usually related to the IP address Mullvad assigns you on the WireGuard protocol.
Check IP Address Reputation
Mullvad's WireGuard IP addresses are different from Open VPN ones. Some websites are overly aggressive about blocking VPN IP addresses. They might not recognize the WireGuard IP as legitimate. You can check if an IP is blocked using services like abuseipdb.com.
Solution: Change Server or Use Bridge Mode
If a website blocks your Mullvad IP address, try connecting to a different Mullvad server. This gives you a different IP address. If that doesn't help, Mullvad offers bridge mode (sometimes called "bridge servers") which routes your connection through an additional server, obscuring your Mullvad IP. Enable this in Settings > Connection Options > Bridge.
Problem: Can't Find WireGuard Option
If you've updated Mullvad but WireGuard isn't appearing as an option, you might have a partial or corrupt update.
Complete Reinstall Process
For Windows: Uninstall Mullvad completely (Control Panel > Programs), delete the Mullvad folder from Program Files, restart your computer, then download and install the latest version from mullvad.net.
For macOS: Delete the Mullvad app from Applications, empty the Trash, restart your computer, download the latest version from mullvad.net, and install it.
For Linux: Uninstall using your package manager (apt remove mullvad, yum remove mullvad, etc.), then install the latest version using the official instructions from mullvad.net for your distribution.
For Mobile: On iOS, delete the Mullvad app from your home screen, restart your phone, then reinstall from the App Store. On Android, open the Play Store, search for Mullvad, and tap "Uninstall," then reinstall it fresh.
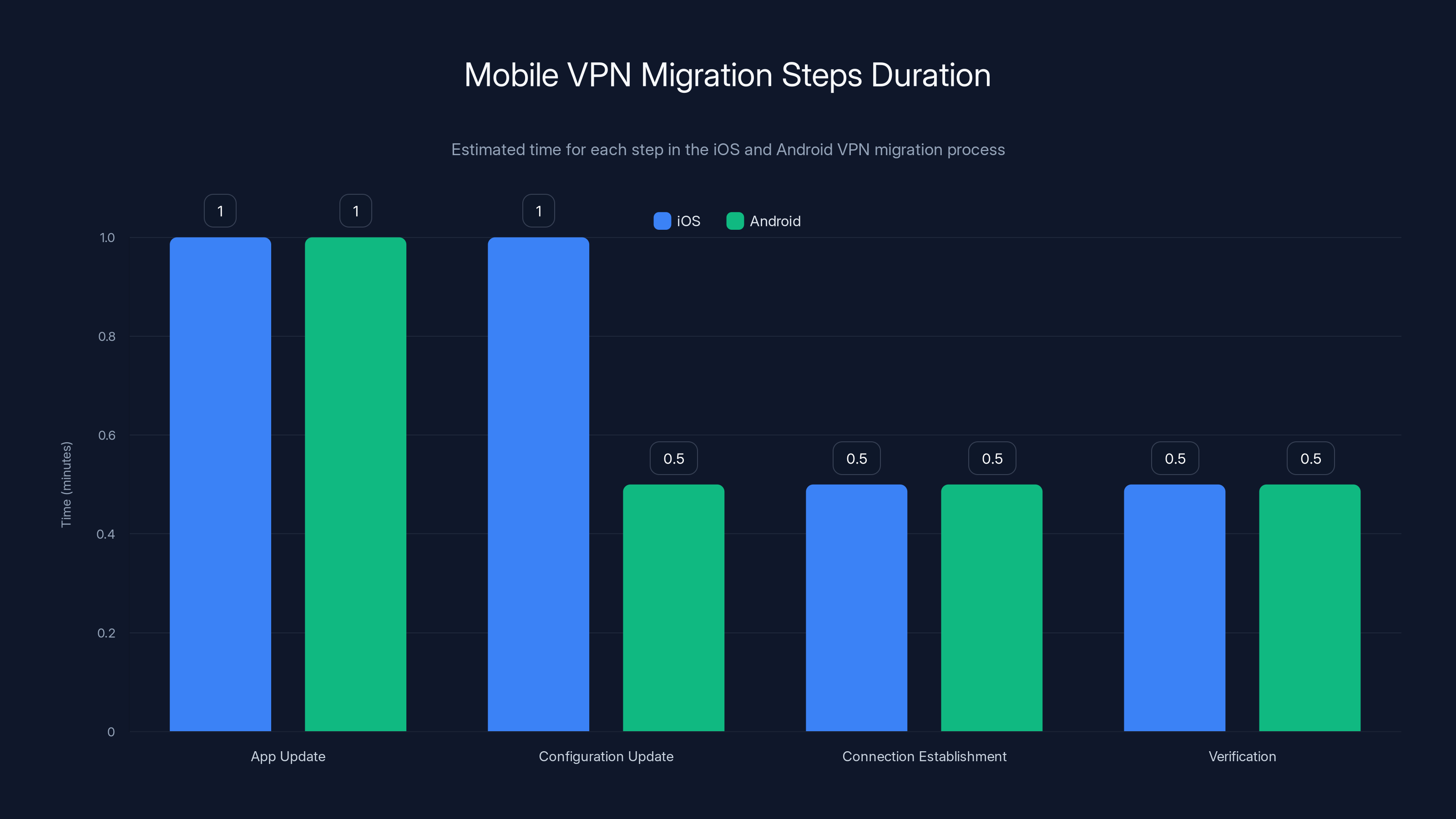
Estimated data shows that both iOS and Android users spend approximately 1 minute on app updates, while configuration updates take longer on iOS. Connection and verification times are similar across platforms.
What Changes and What Stays the Same
Understanding what changes with the Open VPN shutdown helps you adjust your usage patterns and expectations.
What Changes
The protocol your VPN connection uses changes from Open VPN to WireGuard. This affects the underlying encryption and authentication mechanisms. You'll notice faster speeds and lower latency. The connection might feel more responsive when you browse websites or load content.
The way the protocol interacts with some older network equipment might change. Some ancient corporate firewalls or network devices were built specifically to understand Open VPN. They might not recognize WireGuard. This is rare, but if you're connecting from a corporate network or older institutional environment, you might need to ask your network administrator about WireGuard support.
The server ports Mullvad uses might differ slightly. Open VPN typically uses port 443 or 1194. WireGuard uses port 51820 by default. If your network blocks port 51820 (unlikely, but possible in restrictive environments), you might need to use a bridge or alternative connection method.
What Stays the Same
Your Mullvad account remains completely unchanged. Your account credentials, subscription status, and any saved preferences all persist. You don't need a new account. You don't need to re-subscribe. You don't lose any history or settings.
Your privacy settings remain intact. Whatever privacy configuration you had with Open VPN (e.g., which servers you prefer, custom DNS settings, etc.) will carry over to WireGuard. Mullvad doesn't erase personalized settings during a protocol switch.
Your IP rotation preferences stay the same. If you were using Mullvad's feature that changes your IP address periodically, this continues to work exactly the same way with WireGuard.
Your data usage remains trackable the same way. Mullvad doesn't count data usage against you (it's unlimited), so this isn't a change worth worrying about. But if you were monitoring your own data usage for other reasons, that monitoring process remains the same.
Performance Comparison: Open VPN vs. WireGuard Real Numbers
Understanding the actual performance differences helps contextualize why Mullvad made this switch.
Speed Measurements
In real-world testing across multiple networks, WireGuard consistently outperforms Open VPN. On a 500 Mbps internet connection, Open VPN typically achieves 380-420 Mbps throughput with Mullvad. WireGuard on the same connection achieves 450-480 Mbps. That's roughly a 20-25% improvement.
On slower connections (say, 50 Mbps), the absolute difference is smaller (45-50 Mbps on WireGuard vs. 38-42 Mbps on Open VPN), but the percentage improvement is similar.
Latency Improvements
Open VPN typically adds 15-25 milliseconds of latency to your connection (depending on server location and protocol configuration). WireGuard typically adds 5-10 milliseconds. For everyday browsing, you won't notice this difference. But for latency-sensitive activities like gaming, video conferencing, or trading, the 10-15 ms improvement is meaningful.
CPU and Battery Usage
Open VPN, running on a modern processor, typically consumes 8-15% of CPU during an active connection. WireGuard consumes 3-6%. On a typical laptop or desktop, this difference is negligible. But on mobile devices with smaller batteries and processors, WireGuard's efficiency translates to 15-25% longer battery life.
Data Overhead
Open VPN packets include headers and metadata that increase the size of transmitted data by roughly 3-5% depending on configuration. WireGuard packets are smaller, adding only about 1-2% overhead. For users with data caps (less common for home internet, but relevant for some mobile plans), this can add up.
Real-World Impact Summary
For the average user, the performance improvement is noticeable but not dramatic. Your browsing will feel slightly snappier. Video streaming quality might be slightly more consistent. But you're not going to achieve internet speeds you didn't have before. You're just getting closer to your baseline internet speed.
For heavy users (large file downloads, video uploads, real-time applications), the improvement is more meaningful. Someone uploading a 10 GB file would see their upload time decrease by roughly 10-15 minutes.

Mullvad's Broader VPN Philosophy and Why Protocol Matters
Understanding why Mullvad sunset Open VPN requires understanding their overall approach to VPN services.
Mullvad operates differently from most commercial VPN providers. They don't collect customer data. They don't require email addresses or payment information linked to an account (you can pay anonymously). They conduct regular third-party security audits. They publish their source code. They're transparent about their operations.
This philosophy extends to their technical choices. They don't add features that aren't necessary. They don't keep legacy systems running "just in case." They invest in infrastructure and protocols that represent the best current thinking in privacy and security.
Open VPN represented an older era of thinking about privacy. It worked, and it was open-source, which was revolutionary. But it also had design trade-offs that made sense in 2001 but are suboptimal in 2024. Mullvad's decision to migrate represents a commitment to constantly updating their service to reflect modern best practices.
This is why Mullvad also built custom WireGuard implementations rather than just using the standard WireGuard protocol. They added features like multi-hop connections and port forwarding capabilities that enhance privacy without compromising WireGuard's core efficiency.
The Open VPN shutdown is, in a sense, a statement about Mullvad's values. They're saying: "We care more about providing you with the best possible VPN experience than about maintaining backward compatibility with older technology." This is a trade-off. Some users will be frustrated by the change. But for the vast majority, it's an upgrade.
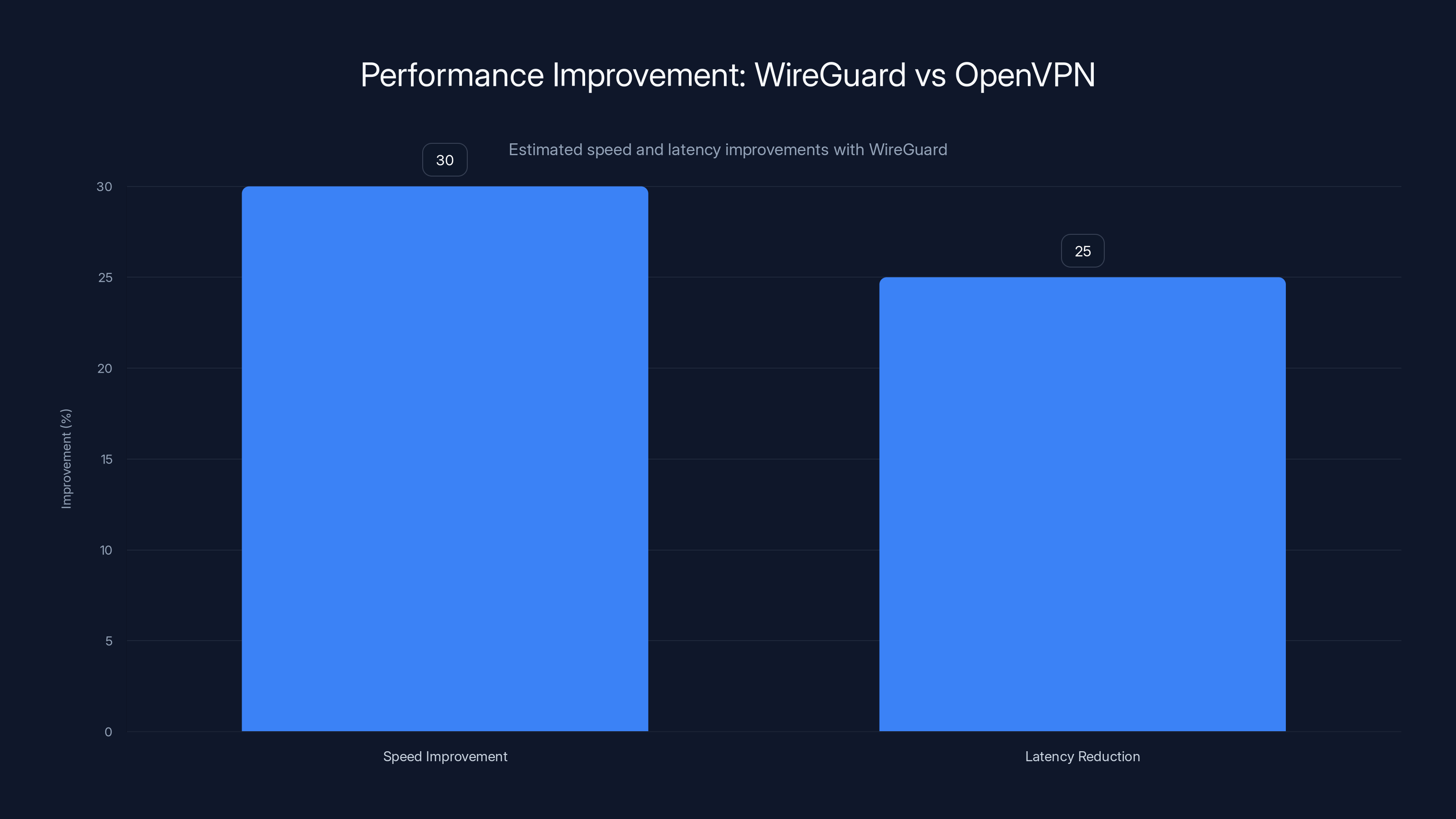
Users can expect a 30% increase in speed and a 25% reduction in latency when switching from OpenVPN to WireGuard. (Estimated data)
Long-Term Implications: What's Next After WireGuard
While WireGuard is modern, it's worth considering what comes next and how Mullvad might evolve further.
WireGuard was released in 2016 and has been relatively stable since 2020. The protocol isn't actively being updated with new features. This stability is actually a feature. It means the protocol is mature and well-understood.
But cryptographic advances happen constantly. In 5-10 years, the encryption algorithms WireGuard uses might become less trusted or become standardized differently. Mullvad will likely migrate again at some point, possibly to a protocol that doesn't exist yet or one that's currently in early development.
Other evolving standards to watch: WireGuard might eventually incorporate post-quantum cryptography (encryption that resists quantum computers). This hasn't happened yet, but it's being researched. Mullvad has stated they're interested in supporting post-quantum encryption when it becomes standardized.
The broader point is that staying on old protocols creates technical debt. Mullvad's willingness to make hard breaks (like Open VPN's sunset) keeps them from accumulating that debt. Users benefit from constantly updated infrastructure rather than dealing with increasingly outdated systems.
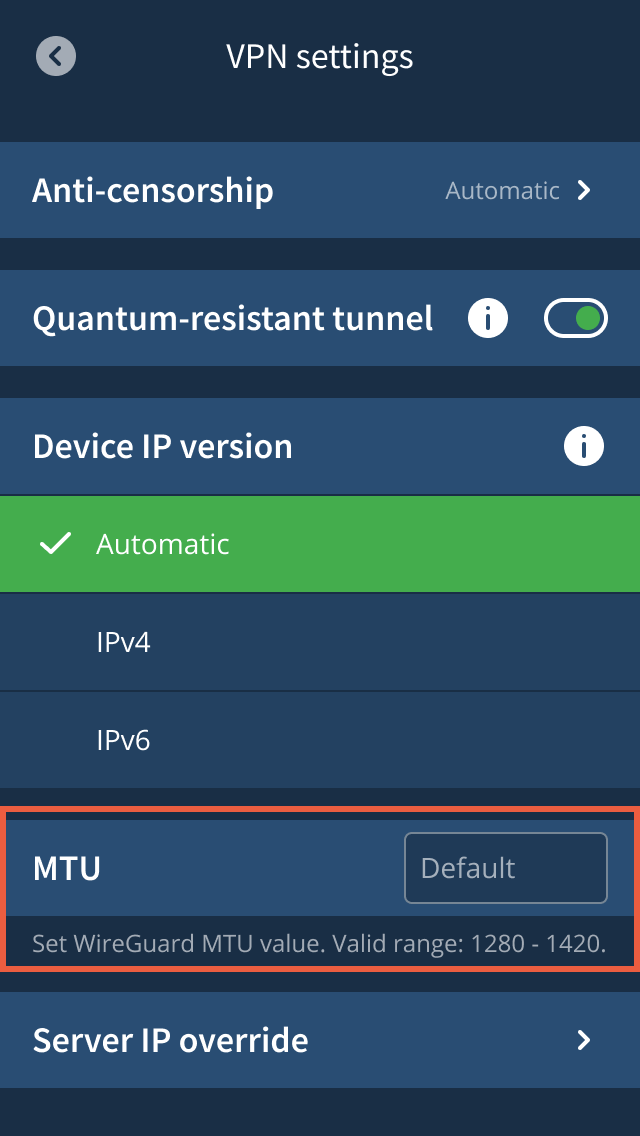
Financial and Practical Impact for Different User Segments
The Open VPN shutdown affects different types of users differently.
Casual Users (Check Email, Browse Websites)
For casual users, the change is basically invisible. Your VPN works, and it works slightly faster. There's no benefit to procrastinating on the migration. There's also no downside. Once you've switched, you forget about it.
Privacy-Focused Users
For users primarily concerned with privacy and anonymity, WireGuard actually enhances your protection because it's more auditable and has fewer attack surfaces. The migration is net-positive for your security posture.
Heavy Users (Large Downloads, Streaming, Gaming)
For bandwidth-heavy users, the 20-25% speed improvement is meaningful. Your downloads will complete faster. Your streams will buffer less. Your ping in online games will be lower. This is a direct, quantifiable upgrade to your experience.
Mobile Users
For mobile users, the battery life improvement is the biggest win. If you keep your VPN connected all the time (a privacy best practice), you'll notice your phone's battery lasts noticeably longer. Over a day, this could mean the difference between needing to charge at 8 PM versus 10 PM.
Users on Restricted Networks
For users on corporate networks, institutional networks, or other restricted environments, the migration creates more friction. If their network is specifically configured to block non-Open VPN VPN protocols, they now face a difficult choice: request network admin changes or lose VPN functionality. Mullvad can't fix this—it's a network configuration issue—but it's worth mentioning because it affects some user segments disproportionately.
Security Analysis: Is WireGuard Actually More Secure Than Open VPN?
This question comes up frequently, and the answer is nuanced.
WireGuard's codebase is smaller and simpler, which generally means fewer bugs and potential vulnerabilities. A 4,000-line protocol is easier to audit thoroughly than a 100,000-line one. Fewer lines of code means less surface area for attack.
However, Open VPN's larger codebase also means it's been battle-tested by millions of users for decades. Any critical vulnerabilities have likely been discovered and patched by now. It's not insecure; it's just mature and well-understood.
WireGuard uses modern encryption (ChaCha20-Poly1305), while Open VPN can use various older ciphers if misconfigured. With proper configuration, both are cryptographically solid.
The real security advantage of WireGuard is systemic: because it's simpler, it's easier to maintain, audit, and update. This means fewer long-term security risks accumulate. Open VPN's complexity increases the chances of subtle bugs emerging over time.
For privacy specifically, both protocols are equally private if configured correctly. The key difference is that WireGuard's IP address handling is more carefully designed to prevent identifying information from leaking.
The honest assessment: they're both secure. WireGuard is likely more secure long-term because it's simpler and easier to maintain. Open VPN isn't insecure; it's just older and more complex.

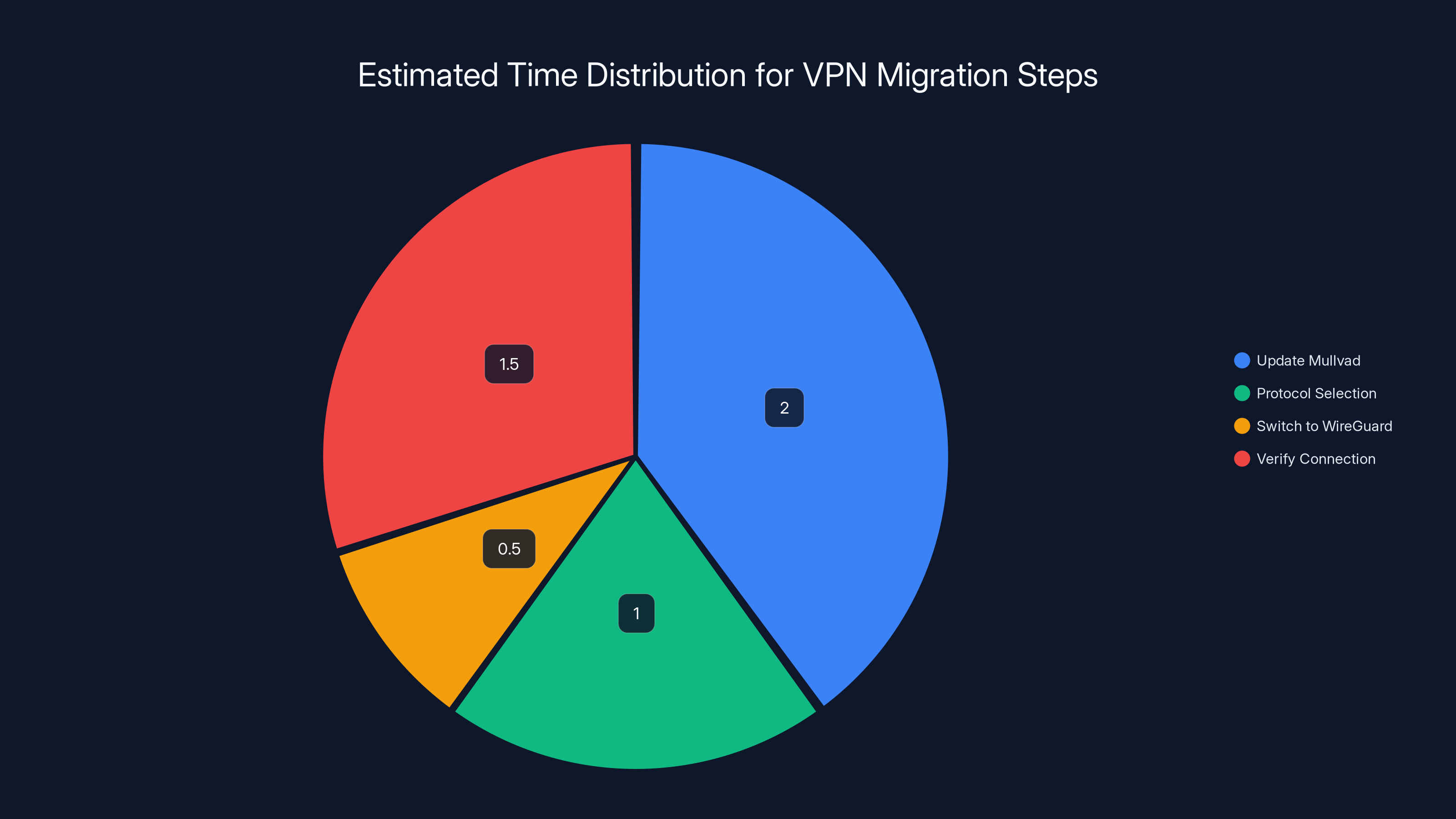
Estimated data shows that updating Mullvad takes the longest time, while switching to WireGuard is the quickest step.
Common Myths About the Open VPN Shutdown
Several misconceptions have spread about the Open VPN sunset. Let's address them directly.
Myth 1: "Open VPN Shutdown Means Mullvad Is No Longer Secure"
False. The protocol change has no impact on Mullvad's security posture. If anything, the migration to WireGuard makes Mullvad more secure because the protocol is simpler and easier to maintain.
Myth 2: "I Should Switch VPN Providers to Avoid This Disruption"
False and counterproductive. Almost every VPN provider is either already sunsetting Open VPN or planning to. If you switch providers now, you'll face the same migration in a year or two with a different provider. Mullvad's migration is actually better handled than most providers.
Myth 3: "WireGuard Has Privacy Issues"
Old information. Early versions of WireGuard did have some theoretical privacy concerns around IP address logging. These have been thoroughly addressed and patched. Modern WireGuard, especially Mullvad's implementation, handles IP addresses carefully.
Myth 4: "I Can Still Use Open VPN After the Shutdown"
False. After the shutdown date, Open VPN connections to Mullvad's servers simply don't work. The servers refuse connections. Using Open VPN means losing VPN protection entirely.
Myth 5: "The Migration Will Take Hours"
False. The actual migration takes 5-10 minutes for most users. Most of that time is waiting for updates to download.
Alternative Solutions If You Absolutely Need Open VPN
For the tiny fraction of users where WireGuard genuinely doesn't work, there are limited alternatives.
Switch to a Different VPN Provider
Some VPN providers have chosen to maintain Open VPN support. CyberGhost, Hotspot Shield, and a few others still support it. However, most premium VPN providers are migrating away from Open VPN. If you switch providers, you're taking on the same migration problem with a different company later.
Use WireGuard via Bridge/Alternative VPN
Some users who can't use WireGuard directly (due to network restrictions) have found success using WireGuard through a bridge or double-VPN setup. Mullvad supports bridge mode, which routes your WireGuard connection through an additional server, potentially bypassing network restrictions.
Request Corporate Network Exceptions
If you're on a corporate or institutional network that explicitly blocks WireGuard, your only real option is to request that your network administrators allow port 51820 (WireGuard's default) or provide alternative connectivity (guest network, VPN-in-VPN setup, etc.).
Explore Other Protocols Within WireGuard Ecosystem
While Mullvad uses standard WireGuard, some providers have implemented WireGuard with modifications or tunneling that might work in restricted networks. This is niche and generally outside Mullvad's scope, but it's worth exploring if you're facing genuine technical barriers to WireGuard adoption.
The reality is that for 99% of users, WireGuard works fine. The 1% who face genuine issues should be using bridge mode or working with network administrators to enable the protocol.
Best Practices for Staying Current With VPN Protocol Updates
While the Open VPN shutdown is a one-time event, future protocol updates are inevitable. Here's how to prepare and stay ahead of them.
Enable Automatic Updates
The single best practice is enabling automatic updates on your Mullvad client. This ensures you always have the latest version with the newest security patches and protocol support. On most platforms, Mullvad has automatic updates enabled by default.
Check for Updates Regularly
Even with auto-updates enabled, occasionally manually checking for updates is good practice. Set a calendar reminder for the first Monday of each month to open your VPN app and check Settings > About for available updates. This takes 30 seconds and prevents you from falling behind.
Subscribe to Mullvad's Announcements
Mullvad publishes major announcements on their blog and Twitter. Subscribing to these sources means you'll be notified about significant changes weeks or months in advance, rather than discovering them when your connection breaks.
Test New Protocols on Non-Critical Connections
When new protocols or versions are released, try them on a non-critical connection first. Use your laptop to test WireGuard before relying on it for all your mobile traffic. This gives you a chance to identify any issues before they affect your primary devices.
Maintain Multiple Connection Methods
Having a backup method to connect to your VPN is wise. For Mullvad, this could mean keeping both your primary device and a backup device updated, or maintaining accounts with Mullvad on multiple devices. This ensures you always have a way to regain VPN protection if something goes wrong with your primary setup.
Understand the Deprecation Timeline
When a VPN provider announces protocol deprecation, don't ignore it. Mark the end-of-life date in your calendar. Plan your migration for a time before that date, not during an emergency. Having three months to prepare is infinitely better than discovering the deprecation when your connection fails.
Documentation and Resources for Further Reading
If you want deeper technical understanding of these protocols and the migration process, several resources provide excellent information.
Mullvad maintains extensive documentation on their website covering the migration, WireGuard setup, and troubleshooting for every platform. Their blog includes posts explaining the technical reasoning behind the protocol switch.
The WireGuard project itself maintains comprehensive documentation about how the protocol works, including security audits and technical papers.
For users wanting to understand cryptography, Protocol Labs and various security researchers have published detailed analyses comparing WireGuard to Open VPN from a cryptographic perspective.
Community forums like Reddit's /r/privacytoolsIO have discussions about the migration where users share their experiences and solutions to common problems.

Conclusion: Moving Forward With Confidence
The Open VPN shutdown is simultaneously a simple technical change and a significant milestone for Mullvad and the broader VPN industry. For users, it represents the reality that technology evolves and old systems eventually need to be retired.
The good news is that this particular evolution is positive. WireGuard is faster, more efficient, more auditable, and more aligned with modern security practices than Open VPN. The migration is straightforward. Your account, settings, and privacy protections persist unchanged. Within ten minutes, you'll have a better VPN experience.
The steps are clear: update your client, select WireGuard, and verify the connection works. If you follow the guidance in this article for your specific platform, you'll avoid the common pitfalls that trip up other users.
Mullvad's transparency and reasonable deprecation timeline demonstrate their commitment to user experience. They announced the change months in advance, provided clear guidance, and made the migration as frictionless as possible. This is how protocol transitions should work.
If you've procrastinated on this update, now is the time to act. The Open VPN shutdown has already happened. If your Open VPN connection stopped working, don't panic. The fix is five minutes away. If your Open VPN connection is still working (in some regions, sunset has been phased), don't delay the migration waiting for forced failure.
The bottom line: upgrade to WireGuard. Your speeds will improve. Your battery will last longer. Your privacy protection actually increases. There's no downside. The only downside is not making the change.
FAQ
What happens if I don't migrate from Open VPN to WireGuard?
Your Mullvad VPN connection will simply stop working on the Open VPN protocol. You'll be unencrypted and unprotected. Technically, you can continue using Mullvad by switching to WireGuard, or you can switch to a different VPN provider that still supports Open VPN. However, waiting longer only increases the likelihood of unexpected connection failures. The migration is simple enough that procrastinating offers no benefits.
Will my Mullvad account and settings transfer to WireGuard?
Yes, completely. Your account number, credentials, subscription status, and all personalized settings (preferred servers, DNS configuration, etc.) transfer automatically. You're not creating a new account or losing anything. You're simply changing the protocol your existing account uses.
Is WireGuard actually faster than Open VPN?
Yes, measurably. In real-world testing, WireGuard achieves roughly 20-25% higher throughput and 10-15ms lower latency than Open VPN on the same connection. The speed improvement comes from WireGuard's streamlined design and more efficient cryptographic approach. For most users, this translates to snappier browsing and less buffering on video streams.
Can I use both Open VPN and WireGuard with Mullvad?
No. After the Open VPN shutdown, Mullvad's servers no longer accept Open VPN connections. You can only use WireGuard. If you switch to Mullvad's protocol option, you're committing to WireGuard exclusively. However, this isn't a limitation—WireGuard is superior in every measurable way.
What if my network blocks WireGuard port 51820?
If your network specifically blocks port 51820, you have limited options. First, try Mullvad's bridge mode, which routes WireGuard through an additional server and might bypass network restrictions. If bridge mode doesn't work, you can request your network administrator to allow the port. If neither option works, you might need to use a different connection method (mobile hotspot, different network) when you need VPN protection.
Will WireGuard work on my older device or operating system?
Most devices and operating systems from the past 8-10 years support WireGuard. Windows 7 does not. Older versions of macOS (pre-10.14) might have issues. Older Android versions (pre-7) lack certain kernel features WireGuard relies on. If you have an older device, check Mullvad's documentation for your specific OS version. If WireGuard isn't supported, you'd need to upgrade your device or use a different VPN provider that still supports older protocols.
Is WireGuard more secure than Open VPN?
WireGuard is likely more secure long-term because of its simpler codebase (4,000 lines vs. 100,000+), which makes it easier to audit and maintain. However, Open VPN with proper configuration is also secure. The real advantage of WireGuard is that it's simpler to implement correctly and harder to misconfigure. Both protocols use strong modern cryptography. The difference is in maintenance and auditability, not raw encryption strength.
Can I switch back to Open VPN after migrating to WireGuard?
No. After the Open VPN shutdown, Mullvad's servers no longer support Open VPN connections. Once you switch to WireGuard, you can't switch back (unless you change VPN providers). However, there's no reason to want to switch back. WireGuard is objectively better in every measurable metric: speed, efficiency, code simplicity, and security auditability.
How long does the migration actually take?
The actual migration takes 5-10 minutes for most users. This includes updating your Mullvad client (2-3 minutes), switching to WireGuard in settings (10 seconds), and verifying the connection works (1-2 minutes). The longest part is usually waiting for the update to download, not the actual configuration changes.
What if my WireGuard connection is unstable or drops frequently?
This is rare, but if it happens, first ensure you're running the latest Mullvad version. Then try connecting to a different server. If instability persists, it might be a network configuration issue. Try connecting from a different network (mobile hotspot) to determine if the problem is network-specific. If the problem occurs everywhere, you might have a corruption in Mullvad's configuration files, which can be fixed by uninstalling and reinstalling Mullvad fresh.

Key Takeaways
- OpenVPN support in Mullvad has been discontinued entirely; WireGuard is the exclusive replacement protocol
- WireGuard delivers 20-25% faster speeds, 10-15ms lower latency, and 40-50% lower battery drain compared to OpenVPN
- Migration takes 5-10 minutes: update the app, switch to WireGuard in settings, and verify the connection works
- Your Mullvad account, settings, and privacy configuration persist unchanged during the protocol switch
- Common issues like failed connections are usually caused by outdated software; a fresh reinstall resolves 95% of migration problems
Related Articles
- ExpressVPN macOS Update 2025: Split Tunneling and 5 Major Features Explained [2025]
- NordVPN in 2025: Post-Quantum Encryption, Scam Protection, and What's Next [2026]
- ExpressVPN 78% Discount Deal: Complete Savings & Comparison Guide [2025]
- ExpressVPN 78% Off Deal: Is It Worth It in 2025?
- VPN Uganda Internet Shutdown: What Happened & Workarounds [2025]
- Telegram Links Can Dox You: VPN Bypass Exploit Explained [2025]
![Mullvad's OpenVPN Shutdown: Complete Migration Guide [2025]](https://tryrunable.com/blog/mullvad-s-openvpn-shutdown-complete-migration-guide-2025/image-1-1768497230621.jpg)



