Notepad++ Supply Chain Attack: What You Need to Know [2025]
In February 2025, one of the internet's most beloved open-source text editors faced a nightmare scenario. The update system for Notepad++, a lightweight code editor trusted by millions of developers worldwide, had been hijacked by suspected state-sponsored hackers. For six months, attackers had quietly maintained control of the update infrastructure, selectively delivering backdoored versions to targeted users. The breach wasn't discovered until nearly a year after it began.
This wasn't some random ransomware operation or script-kiddie exploit. This was a sophisticated supply chain attack orchestrated by actors with nation-state-level resources and patience. The implications ripple far beyond Notepad++. If such a ubiquitous tool could be compromised so thoroughly, what other software in your environment is at risk?
Let me walk you through what happened, why it matters, and exactly what you need to do about it.
TL; DR
- The Compromise: Notepad++ update infrastructure was hijacked for 6 months (June 2024 to December 2024) by suspected Chinese government hackers as reported by SecurityWeek.
- The Attack Vector: Attackers exploited weak certificate validation and HTTP traffic interception to redirect specific users to malicious update servers according to The Hacker News.
- The Impact: At least three organizations experienced hands-on-keyboard attacks from backdoored Notepad++ installations, with victims having interests in East Asia as detailed by CyberPress.
- The Fix: Update to version 8.8.8.8 or higher immediately; disable auto-updates if running older versions as advised by Rescana.
- The Lesson: Supply chain attacks target trusted tools because they bypass traditional defenses. No software is too small to attack.
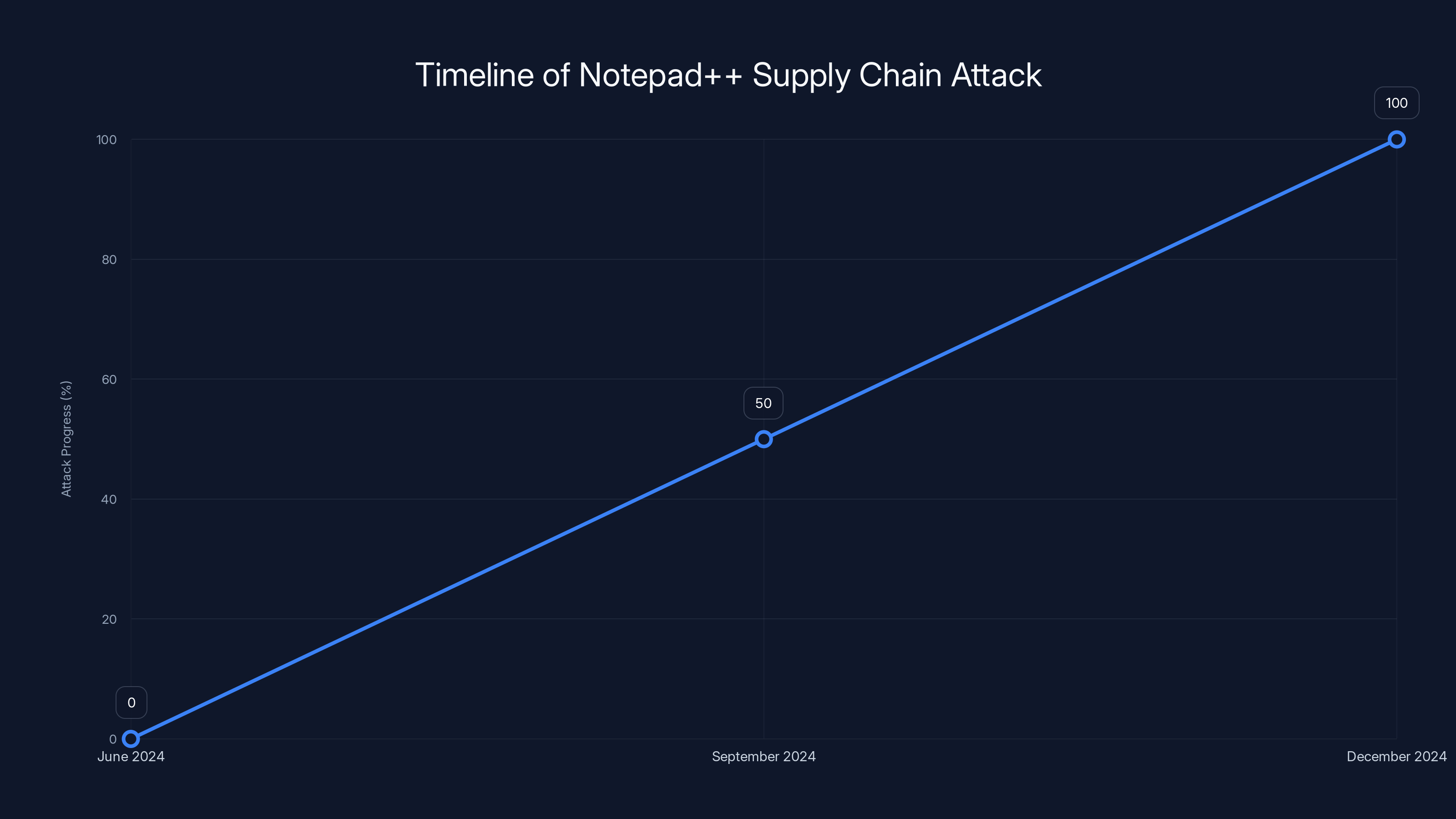
The attack on Notepad++ updates lasted from June to December 2024, with partial discovery in September. Estimated data.
The Timeline: How a Six-Month Compromise Went Undetected
The Notepad++ supply chain attack unfolded across an entire year, with different phases revealing how patient and methodical the attackers were. Understanding this timeline shows how sophisticated state-sponsored operations move at a pace completely different from typical cybercrime.
In June 2024, the attack began with what Notepad++ developers described as an "infrastructure-level compromise." This phrase matters. The attackers didn't just find a vulnerability in the Notepad++ code itself. Instead, they compromised the hosting infrastructure that delivered updates to users. This is a fundamentally different kind of attack—one that requires compromising third-party systems, not just the application as reported by Ars Technica.
The attackers gained the ability to intercept update traffic destined for notepad-plus-plus.org. Once they had that capability, they could selectively redirect certain users to malicious servers. Not everyone got the backdoored version. Instead, the attackers chose their targets carefully. This selective approach is classic tradecraft—it reduces the chance of detection because not every user is affected simultaneously.
For months, nobody noticed. The attack continued through the summer and into the fall. In September 2024, incident responders finally discovered the breach while investigating the hosting infrastructure, but the attackers maintained access to internal credentials. Let that sink in. Even after being partially detected, the bad actors kept going. They retained their ability to redirect update traffic until December 2024, a full six months into the campaign according to Industrial Cyber.
The attack might have continued even longer if Notepad++ developer Don Ho hadn't noticed something suspicious in the version history. In November 2024, version 8.8.8.8 introduced hardened security checks to the update mechanism. This wasn't a response to a known attack at that point—it was proactive patching based on research by independent security analyst Kevin Beaumont, who had published theories about Notepad++ vulnerabilities months earlier.
Beaumont's public research in December 2024 (before the official disclosure) proved prophetic. His working theory about how the attack likely worked matched almost perfectly with what the official investigation would later reveal. The developer's response and Beaumont's analysis gave security teams their first real warning.
The official disclosure came in February 2025, nearly two months after the attackers lost access in December. This delay between regaining control and disclosure matters for incident response. Organizations had a window where they might not have known they were compromised as noted by InfoSecurity Magazine.
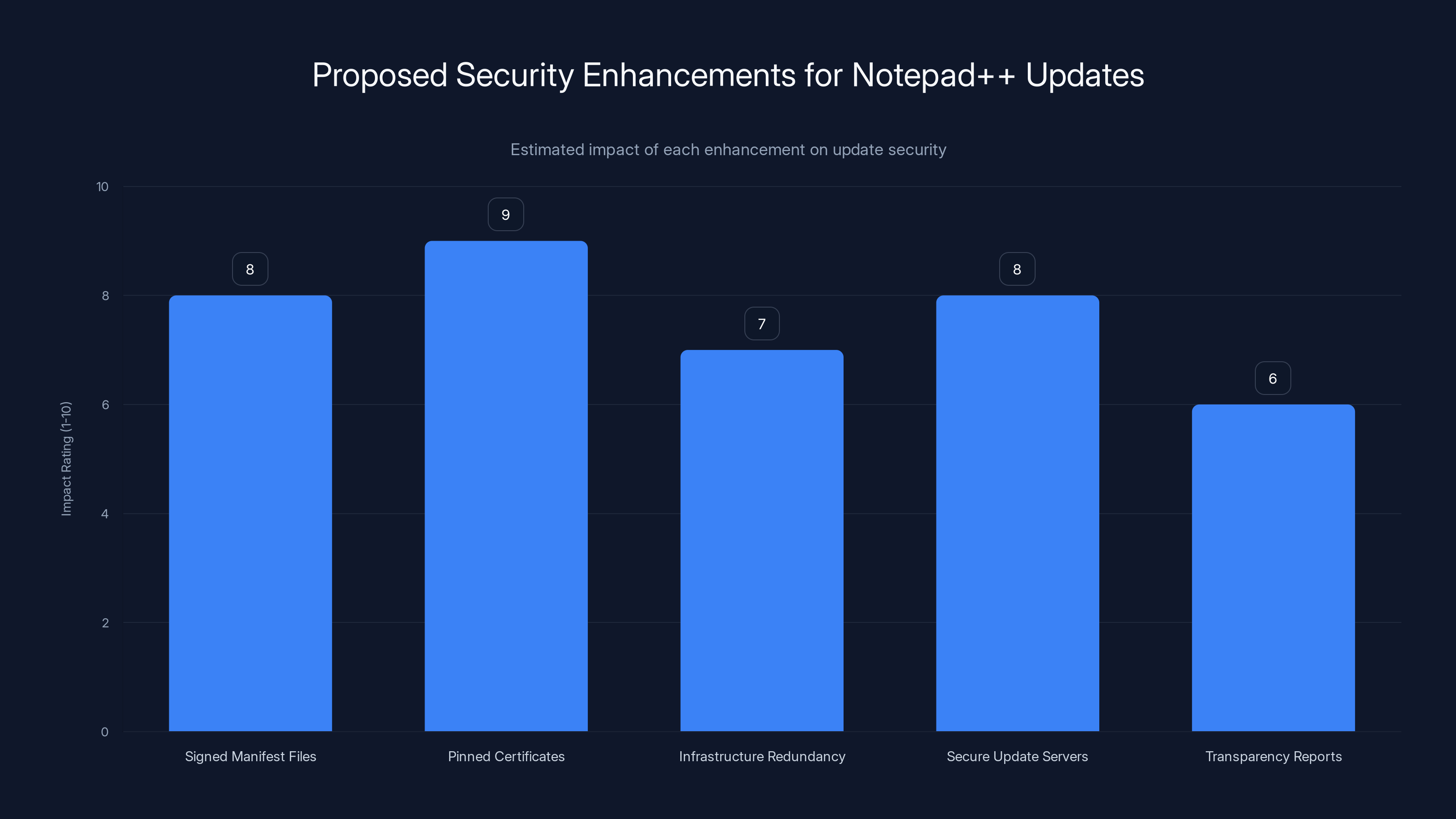
Estimated data: Pinned certificates and signed manifest files are projected to have the highest impact on securing Notepad++ updates.
The Technical Attack: How Certificate Validation Became the Weak Link
Once you understand how the Notepad++ attack actually worked technically, you realize how many layers of security it exploited. This wasn't a zero-day in the application code. It was something more dangerous: a break in the supply chain assumptions that the application was built on.
Notepad++ uses a custom update mechanism called GUP (Generic Update Program), also known as Win GUP. Every time you run Notepad++, the gup.exe process checks for updates by reaching out to https://notepad-plus-plus.org/update/get Download Url.php. The server responds with a URL pointing to the actual update file, stored in a file called gup.xml.
Here's the critical part: in older versions of Notepad++, this traffic wasn't even encrypted. It ran over plain HTTP. That's like sending someone's credit card number in a postcard through the mail. If an attacker sits anywhere on the network path between your computer and the Notepad++ servers, they can see everything and modify it.
Even after the migration to HTTPS in later versions, the certificate validation had problems. The signed updates themselves relied on certificate checking, but here's where it gets messy: earlier Notepad++ versions used self-signed certificates that were publicly available on Git Hub. A self-signed certificate means nobody verified that the certificate came from Notepad++. It's like using a fake ID that anyone can print themselves.
Version 8.8.7 and earlier reverted to using Global Sign certificates for code signing, which is better. But the overall update verification process still wasn't robust. The system relied too heavily on the assumption that the traffic would come from the legitimate server. If you could intercept traffic at the ISP level and use TLS interception—something nation-states have capability to do—you could potentially redirect users to a different download location.
The attack exploited exactly this vulnerability. Because notepad-plus-plus.org receives relatively sparse update traffic compared to mainstream software companies, the attackers could sit at chokepoints in the network and selectively intercept certain requests. They modified the URL in gup.xml to point to their malicious servers instead. When the selected targets downloaded what they thought was a legitimate Notepad++ update, they actually received a backdoored version as detailed by Rescana.
The sophistication here reveals a key insight about supply chain attacks: they don't always need zero-days or brilliant exploits. They need access to infrastructure and the patience to exploit existing weaknesses in a system that was never designed with adversaries controlling the delivery mechanism.

Understanding the Backdoors: What Infected Versions Actually Did
The Notepad++ advisory didn't provide exhaustive technical details about the backdoored versions themselves. That's partly because the full forensic analysis takes time, and partly because sharing complete technical specifications could help copycat attackers. But we know enough to understand what was at stake.
According to independent researcher Kevin Beaumont, at least three organizations discovered that their networks had experienced "hands-on-keyboard" attacks. That phrase is cybersecurity shorthand for the absolute worst-case scenario: actual human attackers with interactive access to systems. They're not just running automated malware. They're logging in, moving around the network, and conducting targeted operations as reported by CyberPress.
All three organizations Beaumont identified had interests in East Asia—some operations, investments, or business activities focused on that region. This wasn't a mass-distribution backdoor trying to hit everyone. It was a targeted espionage campaign.
Based on the behavior pattern and the fact that these were nation-state actors, the backdoored Notepad++ versions likely contained one or more of the following capabilities:
Command and control callbacks allow the malware to receive instructions from the attacker's servers. The infected Notepad++ could phone home periodically, reporting system information and waiting for commands. This gives attackers the ability to do reconnaissance on the infected machine before deciding what to do next.
Credential harvesting captures usernames, passwords, and authentication tokens. A text editor that runs with user privileges can access keystroke data, clipboard contents, and files being edited. For an analyst, developer, or researcher, this is incredibly valuable information.
Data exfiltration silently copies sensitive files and sends them to attacker-controlled servers. A compromised editor used by someone working on sensitive projects would naturally have access to those files.
Privilege escalation hooks exploit local system vulnerabilities to gain elevated permissions. Once you have a beachhead on a system, the next step is usually getting administrator privileges to do something more impactful.
Lateral movement tools allow attackers to spread from the infected user's machine to other systems on the network. This is how a single compromised workstation becomes a network-wide breach.
The exact capabilities in the backdoored versions remain partially redacted in public disclosures. But the fact that real organizations experienced hands-on-keyboard attacks means the backdoor was functional and useful for actual espionage operations.
What's particularly chilling is that Notepad++ is such a legitimate, trusted tool that it would pass most detection mechanisms. A user running a backdoored version would see no obvious signs of compromise. The application would work normally. Updates would still happen. Security warnings wouldn't trigger. This is the essence of supply chain attacks: they exploit trust.
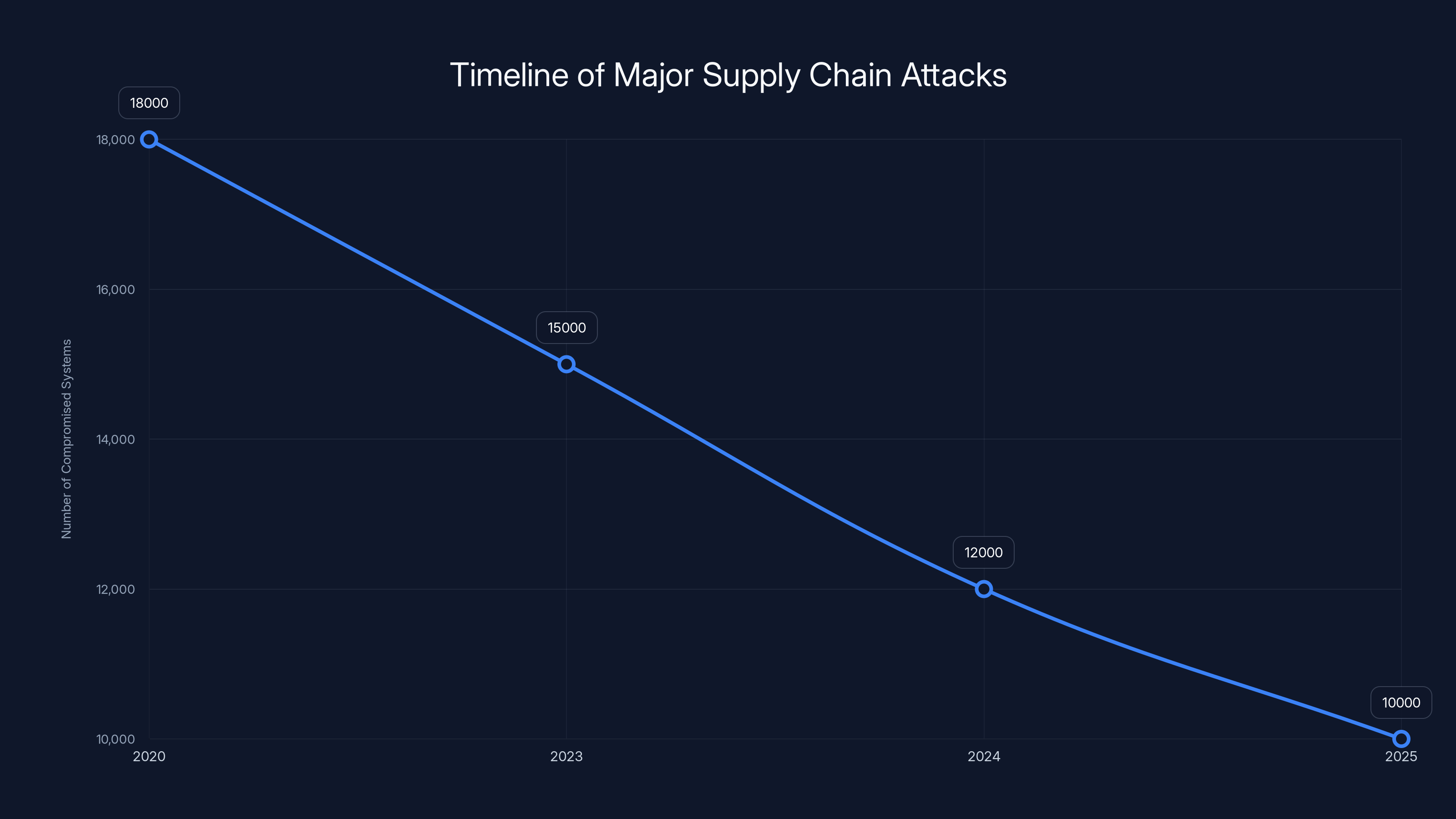
Supply chain attacks have shown a consistent pattern of compromising thousands of systems, highlighting the growing threat of these indirect attacks. Estimated data based on known incidents.
The Attribution Question: Why Believe These Were State Actors?
Multiple independent researchers and incident responders attributed this attack to Chinese government-backed threat actors. This is important context for understanding both the severity and the confidence level in attribution.
Attribution in cybersecurity is always imperfect, but certain evidence points strongly in this direction. First, the technical sophistication required to maintain ISP-level traffic interception and selective TLS manipulation is frankly beyond most cybercriminal organizations. You need access to backbone infrastructure, relationship with ISPs, and the ability to operate at that scale for months without getting caught. Those capabilities cluster around state actors as noted by SecurityWeek.
Second, the targeting pattern is classical espionage, not financial crime. The organizations hit were chosen based on their interests in East Asia, not their payment methods or financial value. A criminal group would try to monetize compromised systems—ransomware, banking credentials, cryptocurrency theft. These attackers were after intelligence and information.
Third, the patience is remarkable. Maintaining control of infrastructure for six months while selectively targeting victims requires discipline and long-term thinking. Most cybercriminal operations move quickly and try to extract value immediately. State actors can afford to wait, plan carefully, and operate over extended timescales.
Finally, the connection to Chinese government operations is informed by past behavior. China's Ministry of State Security and its affiliated groups have a documented history of targeting think tanks, research organizations, and companies with interests in Asia-Pacific geopolitics. The Notepad++ attack fits this pattern exactly.
None of this is absolute proof. Attribution often relies on reasonable inference from available evidence rather than definitive proof. But the confluence of technical sophistication, targeting pattern, operational patience, and historical precedent makes the conclusion more likely than alternatives.
The Vulnerability Chain: How Multiple Weaknesses Aligned
No single vulnerability made the Notepad++ supply chain attack possible. Instead, several weaker-than-ideal security practices aligned in a way that gave attackers an opening. This is the true lesson: security is a chain, and the attack exploited multiple weak links.
Weak link one: HTTP-based update checks in older versions. For a period, Notepad++ checked for updates over unencrypted HTTP. This is indefensible from a modern security perspective. An attacker with network visibility could trivially intercept and modify update URLs. Later versions moved to HTTPS, which raises the bar, but wasn't a complete fix.
Weak link two: Self-signed certificate validation. Using self-signed certificates that anyone can generate and that were even publicly documented on Git Hub means certificate validation provides less security benefit than intended. The signature check exists, but if the attacker controls the delivery mechanism, they can sign with their own certificate.
Weak link three: Update infrastructure wasn't sufficiently isolated. The hosting provider's systems were compromised in a way that gave attackers access to update distribution. This suggests the update infrastructure wasn't separated with air-gapping or other isolation techniques from other services. A breach in one area cascaded to the update system.
Weak link four: Insufficient monitoring of update traffic. Six months of compromise went undetected until incident responders explicitly looked for it. This suggests there wasn't robust monitoring of who was accessing the update servers, where requests were coming from, or what responses were being served.
Weak link five: Credentials remained valid after initial compromise detection. Even after the September discovery that the infrastructure was compromised, the attackers maintained valid credentials and continued operations until December. This indicates that the credential rotation process wasn't executed quickly or completely.
When security professionals design systems, they often think in terms of a single strong defense. But attackers think in terms of combining multiple small weaknesses into a complete compromise. The Notepad++ attack is a master class in this approach.
The developers quickly hardened the update mechanism in version 8.8.8.8, specifically addressing the certificate validation and update integrity checking. But the underlying lesson remains: supply chain security requires defense in depth across multiple layers.

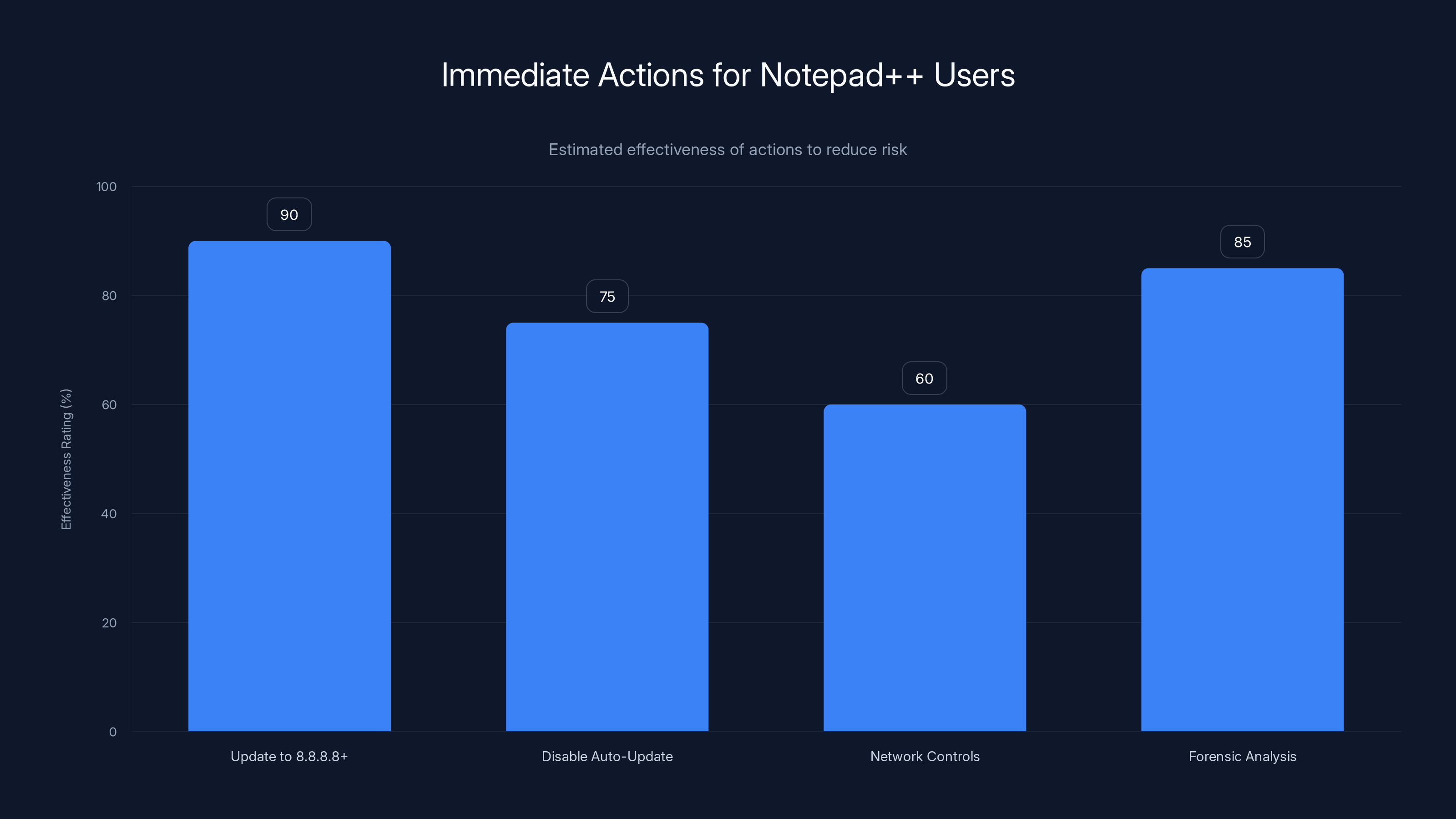
Updating to version 8.8.8.8 or higher is the most effective immediate action to reduce risk, followed by conducting forensic analysis in sensitive environments. (Estimated data)
Impact and Detection: Three Organizations Discovered Hands-On-Keyboard Attacks
The confirmed impact of the Notepad++ supply chain attack appears smaller than the potential scope suggests, but what was confirmed is serious.
At least three organizations discovered that systems with compromised Notepad++ installations had been subjected to hands-on-keyboard attacks. These weren't automated malware effects. Actual human threat actors had gained interactive access to systems, executed commands, and conducted reconnaissance as detailed by CyberPress.
Hands-on-keyboard attacks represent the deepest level of system compromise. An attacker with this access can:
- Explore sensitive files and databases
- Create additional backdoors for persistence
- Move laterally across the network
- Exfiltrate large volumes of data
- Establish command and control infrastructure
- Modify logs to cover their tracks
All three affected organizations had operations, interests, or focus areas related to East Asia. This aligns perfectly with the espionage hypothesis. The attackers weren't casting a wide net; they were hunting specific targets.
However, detecting the full scope of the attack remains ongoing. Several factors complicate the situation:
Not all infections were discovered. Some organizations may still have compromised versions running without detection. The attack was selective but not transparent. Only organizations that conducted thorough forensics discovered they were hit.
The timeline of infection is uncertain. Did every user of Notepad++ between June and December get offered a backdoored version? No. Were there users who installed it unknowingly? Almost certainly. How many is the open question.
Infection doesn't always lead to detectable compromise. Some infected systems may have had the backdoor but never had it activated. Others may have had limited backdoor activation that didn't meet the threshold for hands-on-keyboard incidents.
Organization detection capabilities vary widely. Large enterprises with threat hunting teams discovered the attack. Small organizations may have compromised systems they've never found.
The confirmed three organizations represent the known tip of an iceberg. The actual scope remains partially unknowable.

Why Notepad++ Was a Valuable Target
On the surface, Notepad++ seems like an odd target for nation-state attackers. It's a text editor. It's free. It's not as ubiquitous as Windows or Chrome. Why spend resources compromising the update infrastructure for something that seems peripheral?
The answer reveals important truths about how modern attackers think.
First, Notepad++ runs with user privileges across millions of systems globally. Every developer, sysadmin, analyst, and researcher who uses it is potentially a target. The users skew toward technical roles where they likely have access to sensitive information. A compromised Notepad++ gives you a window into what these high-value individuals are working on.
Second, Notepad++ has exceptional trust. It's open source. It has been around for decades. It's beloved by the technical community. Users don't suspect it. Endpoint protection software doesn't scrutinize it heavily because it's so obviously legitimate. This trust is valuable precisely because it provides cover.
Third, Notepad++ is often used for work that involves sensitive content. Developers editing configuration files with credentials. Researchers analyzing classified documents. Analysts working on geopolitically sensitive intelligence. Penetration testers preparing reports. The people using Notepad++ often have access to exactly the kind of information that nation-state intelligence agencies want.
Fourth, targeting Notepad++ is a asymmetric operation. The effort required to compromise the update infrastructure is high, but so is the value of the intelligence gained. Nation-states can afford the upfront investment because the potential payoff is enormous. A private cybercriminal organization couldn't justify the expense.
Fifth, Notepad++ is cross-platform and ecosystem-agnostic. Unlike tools that only work in specific corporate environments, Notepad++ works everywhere. If you want to target people with interests in Asia-Pacific geopolitics, they could be in government, private companies, NGOs, think tanks, or academia. Notepad++ reaches all of them.
When you look at it from the attacker's perspective, Notepad++ isn't a small target. It's a scalpel that reaches the exact people they want to survey, in a way that generates minimal suspicion.

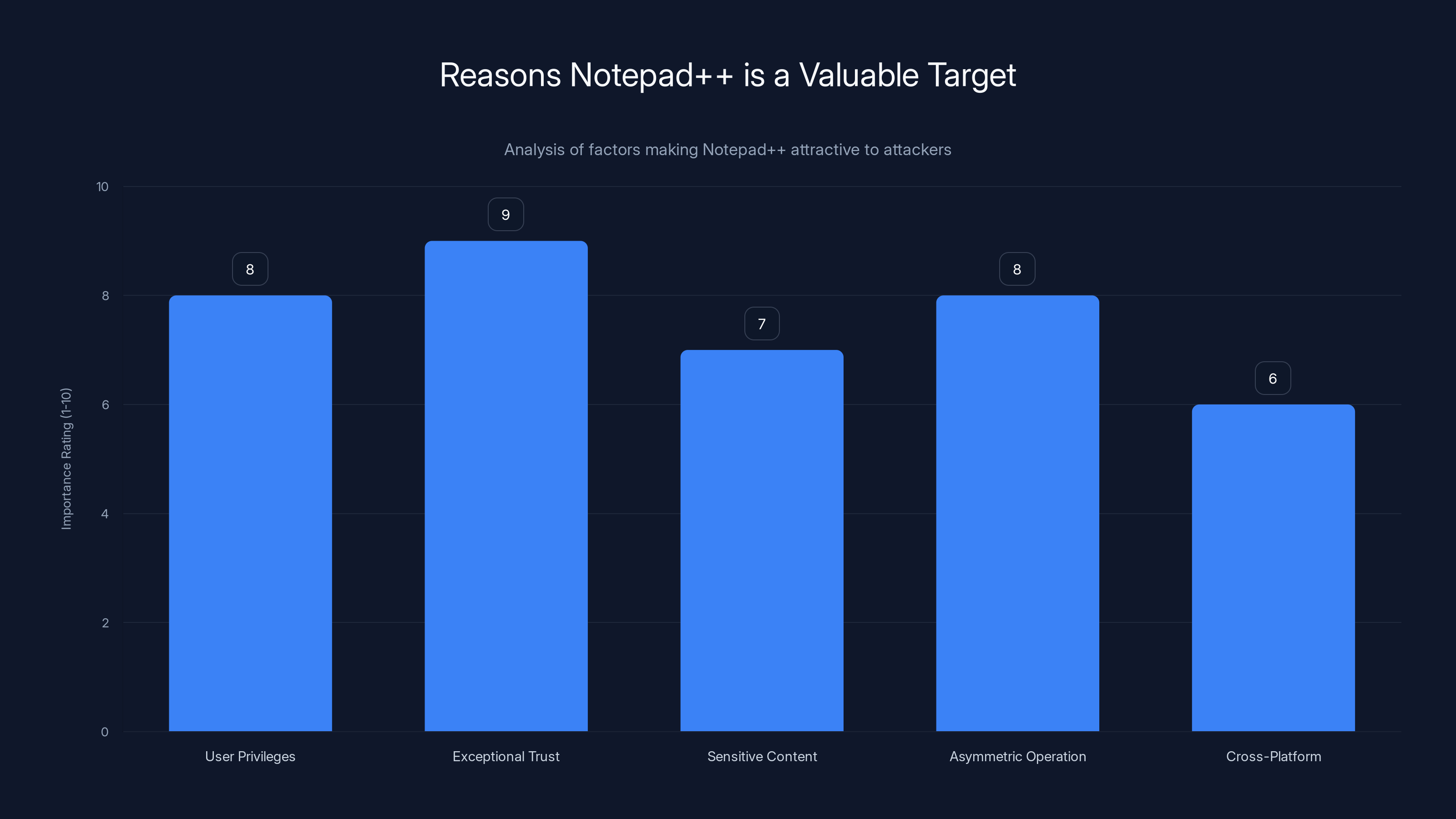
Notepad++ is targeted due to its widespread use, trust, and the sensitive nature of work done with it. Its cross-platform nature and the asymmetric value of compromising it make it a high-value target. Estimated data.
The Broader Context: Supply Chain Attacks as the Future of Espionage
The Notepad++ attack didn't happen in isolation. It's part of a larger trend in how nation-states conduct cyber operations.
Traditional malware and hacking targets systems directly. You find a vulnerability, exploit it, and establish a backdoor. This approach works but generates risk. Each attacked system is a potential detection point. Defenders can patch vulnerabilities. Endpoint protection improves.
Supply chain attacks invert this approach. Instead of attacking the target directly, attackers compromise the tools and software that targets already trust and use. When the software updates itself or when new users download it, they unknowingly receive the backdoor. The attacker relationship is to the vendor, not to the victim.
This offers several advantages:
Legitimacy. The backdoor comes from a trusted source. Users don't suspect it. Security controls don't block it.
Scale. A single compromise can potentially reach thousands of users simultaneously. The attacker invests effort once and reaches many targets.
Persistence. Every time the software updates, the backdoor propagates. Users can't remove it without uninstalling trusted software.
Misdirection. Defenders focus on endpoint protection, firewalls, and intrusion detection. They often don't think about supply chain compromise until it's too late.
The Notepad++ attack is one example in a pattern that includes:
- Solar Winds (2020): Attackers compromised Orion software updates, reaching thousands of US government and corporate networks
- 3CX (2023): The communication platform's update was compromised, affecting multiple critical infrastructure sectors
- XZ Utils (2024): An open-source compression library nearly had a critical backdoor snuck in
- Notepad++ (2024-2025): The text editor update mechanism was hijacked
Each attack teaches defenders something new. But the lesson is consistent: trusted software is a critical vulnerability surface.
Immediate Actions: What to Do Right Now
If you're a Notepad++ user or administrator, several immediate actions reduce your risk.
First, update immediately to version 8.8.8.8 or higher. Download directly from the official Notepad++ website at notepad-plus-plus.org. Don't use auto-update if you're on an older version, because the update mechanism itself was compromised. Go directly to the source and get the latest version manually.
Verify you're running a safe version by checking the Help menu and noting your version number. If it's below 8.8.8.8, you're running code that predates the security hardening.
Second, if you run an older version, consider not using auto-update. The update mechanism had security weaknesses that allowed selective redirection. While version 8.8.8.8 and higher addressed this, turning off auto-update removes a potential attack vector. Manually check for new versions monthly.
Third, organizations should consider network controls. Some organizations block certain update traffic at the network level. You could implement firewall rules that restrict gup.exe to specific IP ranges, or block notepad-plus-plus.org traffic if Notepad++ isn't business-critical.
Keyboard Beaumont suggested organizations "may also want to block internet access from the notepad++.exe process, unless you have robust monitoring for extensions." But he cautioned that for most organizations, this level of restriction is overkill and difficult to maintain without breaking functionality.
Fourth, conduct forensic analysis if you operate in a sensitive environment. Organizations with employees in roles involving East Asia operations, policy, research, or intelligence should examine logs and system artifacts from machines running Notepad++ between June and December 2024. Look for:
- Unusual network connections from Notepad++ processes
- Unexpected child processes spawned by gup.exe
- Log entries showing network access to non-standard IPs
- File modifications in user temporary directories
- Unexpected administrator account creation or privilege changes
Fifth, examine backup and archive data. If your organization has been compromised, attackers likely exfiltrated data. They may have accessed sensitive files that were later deleted. Check backup systems for evidence of unauthorized access or data copying.
Sixth, assume data confidentiality may be compromised. If your organization was hit by this attack and operated on sensitive geopolitical matters, threat intelligence, or research, assume that data was read by adversaries. Reassess information that could be valuable to competitors or hostile nations.

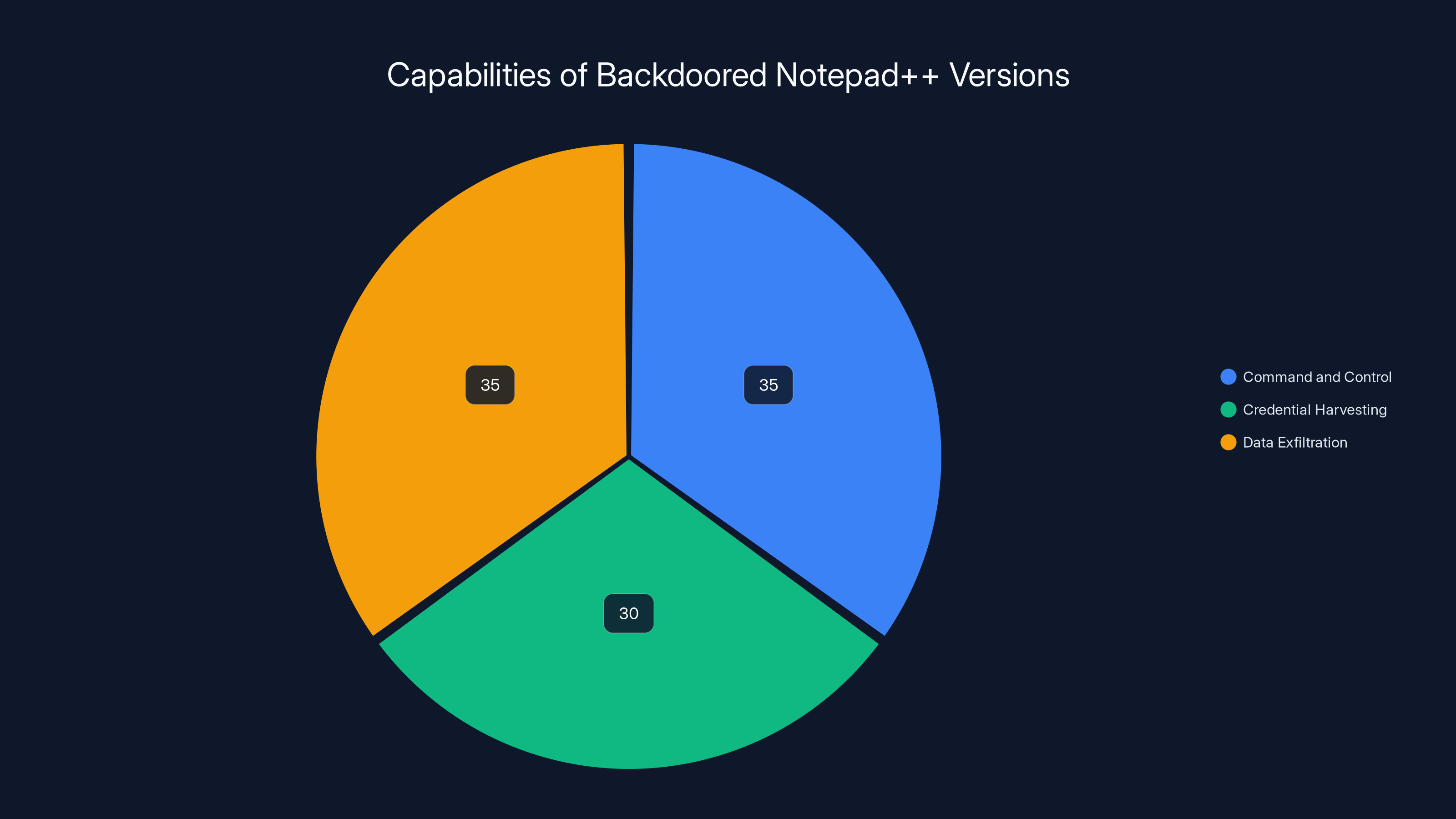
Estimated data shows that backdoored Notepad++ versions likely focused on command and control, credential harvesting, and data exfiltration, each with significant roles in targeted espionage.
Long-Term Defense: Building Supply Chain Resilience
Once you've addressed the immediate Notepad++ situation, consider how to prevent similar compromises in the future. Supply chain security isn't something you can patch once and forget. It requires ongoing attention.
Implement software bill of materials (SBOM) tracking. Know every piece of software installed across your environment, including version numbers. When vulnerabilities or compromises are disclosed, you can quickly identify affected systems.
Establish update verification procedures. Don't just install updates because they're available. Verify cryptographic signatures. Check release notes and security advisories before deploying. For critical software, stage updates in test environments first.
Isolate update infrastructure. If you host software or updates internally, separate that infrastructure from general network traffic. Use different credentials, different networks, and different monitoring than your primary systems.
Monitor unusual update traffic. Set up alerts for unexpected communication from update mechanisms. Most update checks follow predictable patterns. Deviations warrant investigation.
Develop incident response procedures for supply chain compromises. These attacks play by different rules than traditional breaches. You need specific procedures for identifying scope, containing the damage, and recovering systems.
Reduce dependency on single vendors where possible. In some cases, you can implement alternatives or redundancy. If you rely on a single tool for critical functions, diversify when possible.
Participate in security communities. Researchers like Kevin Beaumont often publish findings before official disclosures. Following security researchers and threat intelligence communities gives you early warning of emerging threats.
Assess the authenticity of update sources. Where does your software come from? Is it directly from the vendor? Through an intermediate distributor? The longer the supply chain, the more potential compromise points.
Supply chain security ultimately comes down to defense in depth. You can't make supply chain attacks impossible—but you can make them more difficult to exploit, easier to detect, and less damaging when they occur.

The Role of Open Source Funding in This Attack
Notepad++ is open source, maintained by volunteers and funded modestly. The application is free. The developers don't have a large commercial operation funding security researchers, infrastructure hardening, or comprehensive testing.
This reality matters for understanding why the attack succeeded. A well-funded software company with dedicated security teams might have:
- Implemented certificate pinning to prevent ISP-level traffic manipulation
- Used robust signed update manifests with timestamp verification
- Conducted regular security audits of the update infrastructure
- Implemented intrusion detection on infrastructure systems
- Rotated credentials on a strict schedule
- Had a dedicated incident response team ready to act
Notepad++ developers did none of these things, not because they were careless, but because they couldn't afford to. The open source ecosystem provides immense value to the internet's infrastructure, but it operates on shoestring budgets.
The irony is stark: billions of people depend on free and open-source software, but very few of those people or organizations contribute funding to maintain it. When a supply chain attack happens, it reveals this imbalance.
This doesn't excuse the attackers. Exploiting vulnerabilities in free software used by vulnerable populations is reprehensible. But it should prompt reflection in the tech community about how we fund and secure the software that everything depends on.
Some organizations are starting to address this. Bug bounty programs, security audits, and direct funding for open-source projects are increasing. But they're still wildly inadequate relative to the importance of open source in global infrastructure.
The Notepad++ attack should serve as a wake-up call: if we don't adequately fund security for the free tools that the internet runs on, state actors will continue to find entry points.
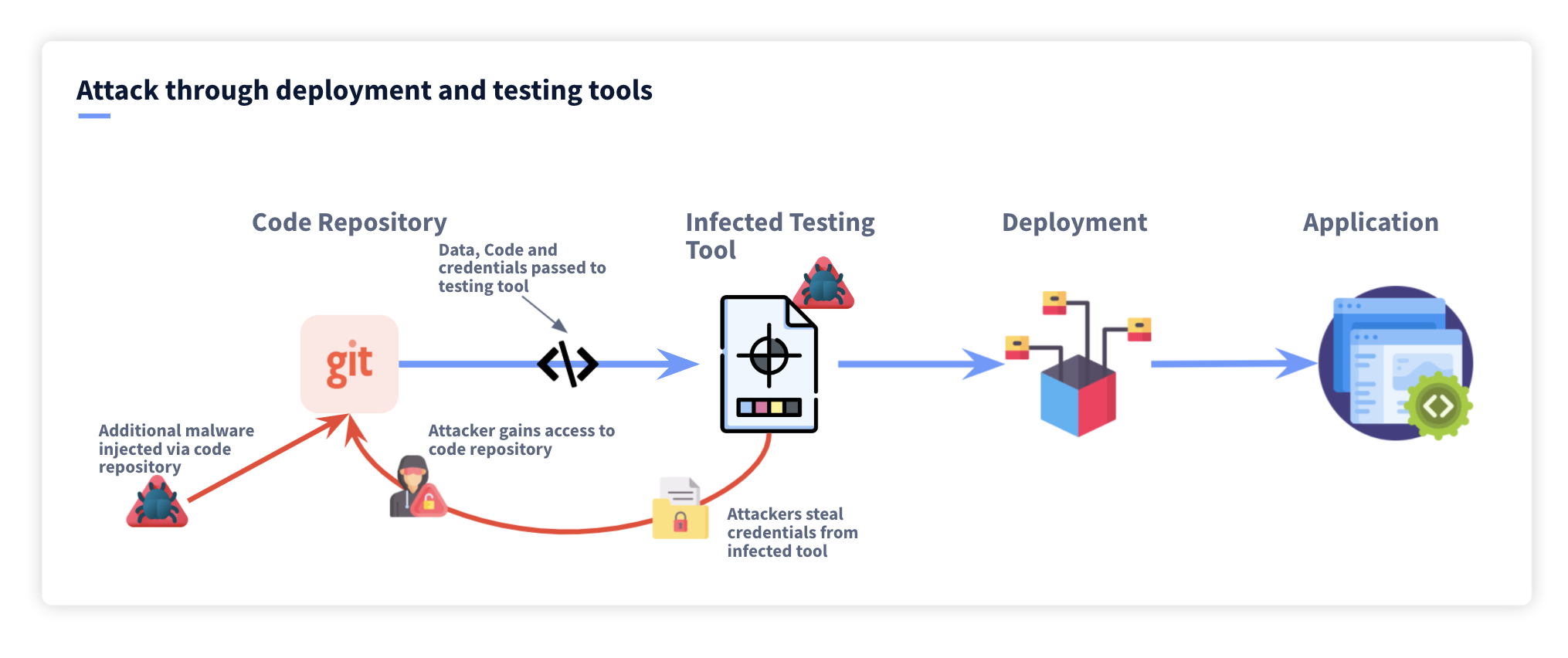
Indicators of Compromise: How to Spot If You Were Affected
If your systems may have been exposed to the Notepad++ supply chain attack, knowing what to look for can help you determine if you need to escalate your investigation.
Behavioral indicators are often the easiest to spot with the right tools. If you have network monitoring in place, look for unusual outbound connections from gup.exe or notepad++.exe processes. The hijacked update servers would have connected to IP addresses different from normal Notepad++ infrastructure. DNS queries to unusual domains from Notepad++ processes are another red flag.
File system indicators include unexpected files in the %TEMP% directory created around the same time as Notepad++ updates. The backdoored update would have been downloaded there before execution. Look for files with timestamps matching when you (or your users) updated Notepad++ between June and December 2024.
Process indicators involve looking at what gup.exe spawned as child processes. A legitimate update process downloads and runs an installer. An attacker-modified version might spawn command shells, execute scripts, or create network connections. If gup.exe ever spawned cmd.exe or powershell.exe, that's worth investigating.
Registry and scheduled task indicators suggest persistence mechanisms. Attackers often create scheduled tasks to ensure malware re-executes after reboots. Check Windows task scheduler for tasks related to Notepad++ created during the vulnerable period.
Log indicators in Windows Event Viewer might show unusual process creation, network connections, or authentication events. If you have centralized logging, query for events from infected systems during the vulnerable timeframe.
Authentication indicators look for credential theft evidence. If users whose machines were infected later had their credentials compromised in unrelated incidents, that's a potential connection.
The problem with most of these indicators is they require the right monitoring tools in place before the attack happens. Many organizations don't have this level of visibility. That's precisely why organizations with hands-on-keyboard attacks were discovered—they had advanced logging or threat hunting capabilities that flagged unusual activity.
For most organizations, the practical approach is: update to a safe version, review logs if you have capability to do so, and be alert for unusual activity on affected systems going forward.

Looking Forward: Changes in the Notepad++ Update Process
In response to the attack, Notepad++ made hardening changes to the update mechanism, but the underlying question remains: how do you make software update securely in an environment where attackers control network infrastructure?
Version 8.8.8.8 and beyond introduced stronger certificate validation, improved signature checking, and better verification of update integrity. But these are incremental improvements, not fundamental changes.
Longer term, the Notepad++ developers are considering several approaches:
Signed manifest files that list expected updates and their cryptographic hashes. This allows users to verify that what they downloaded is what the developer intended them to download, even if the delivery was compromised.
Pinned certificates that hardcode the expected certificate used to sign updates. This prevents ISP-level TLS interception from working, because the update process won't accept certificates from other providers.
Infrastructure redundancy that distributes updates across multiple delivery points. If one becomes compromised, others continue to work, and users downloading from different sources alerts the developers to the compromise faster.
Secure update servers with better access controls, monitoring, and credential management. The hosting provider's infrastructure should be hardened specifically for the purpose of serving updates.
Transparency reports where Notepad++ publishes statistics about update traffic, cryptographic verification failures, and unusual patterns. This allows the security community to help spot issues.
Implementing all of these costs money and developer time. It requires ongoing maintenance and monitoring. It's not a one-time fix. But the alternative is remaining vulnerable to supply chain attacks.
Other open-source projects facing similar questions are watching Notepad++'s response closely. The solutions developed here will influence how other projects approach update security.

Lessons for Every Software Organization
Even if you don't use Notepad++, the attack teaches critical lessons about how to secure your own software distribution and update mechanisms.
Lesson one: Update mechanisms are attack surfaces. Most organizations think about the code in their software as the security boundary, but the update process is equally critical. Attackers often target update distribution because it bypasses traditional defenses.
Lesson two: Supply chain security requires defense in depth. No single security control prevents supply chain attacks. You need multiple overlapping defenses: code signing, certificate validation, traffic encryption, infrastructure isolation, access controls, monitoring, and incident response procedures.
Lesson three: Selective attacks are harder to detect than mass attacks. The Notepad++ attackers didn't compromise every user. They chose targets. This approach reduces the chance of detection because there's no sudden widespread incident. Defenders must assume that selective compromise is possible and look for it proactively.
Lesson four: State-sponsored attackers operate on different timescales. The Notepad++ attack lasted six months of direct compromise with another three months of residual access. Most cybercriminals move quickly. Nation-states can afford to wait, plan, and execute methodically.
Lesson five: Funding matters for security. Well-resourced organizations can implement robust security practices. Under-resourced organizations cut corners. The attackers exploit the difference.
Lesson six: The security research community is part of your defense. Kevin Beaumont's research months before the official disclosure helped alert the community. Supporting independent security researchers benefits everyone.
The Bigger Picture: Supply Chain Attacks as a Permanent Threat
The Notepad++ attack isn't an anomaly. It's part of a growing pattern of state-sponsored and sophisticated criminal attackers targeting the software supply chain.
Why focus on supply chain attacks? Because they're asymmetrically efficient. An attacker who compromises a popular software tool reaches millions of users with minimal effort. The target organization can't patch away a problem that exists in the software they're using. The compromise bypasses the perimeter defenses that most organizations focus on.
As organizations improve endpoint security, network monitoring, and intrusion detection, attackers have shifted focus to softer targets: the supply chain. It's the path of least resistance.
Expect to see more of these attacks in coming years, targeting:
- Open-source packages widely used in software development
- Software components used across industries
- Managed service providers whose access reaches many organizations
- Cloud providers and hosting platforms
- Development tools used by critical infrastructure operators
The Notepad++ attack will become a case study in security training programs, not a cautionary tale that stops future attacks. The fundamental vulnerability—that we depend on a supply chain for software—can't be eliminated. It can only be managed.
Organizations that invest in supply chain security now—through SBOM tracking, update verification, vendor security assessments, and incident response procedures—will be better positioned to survive future attacks.
Those that continue treating supply chain security as someone else's problem will eventually discover otherwise.

FAQ
What exactly happened with the Notepad++ supply chain attack?
Suspected Chinese government hackers compromised the hosting infrastructure that delivers Notepad++ updates for six months (June to December 2024). They intercepted update requests and selectively redirected targeted users to malicious servers that provided backdoored versions of Notepad++. The attackers maintained infrastructure-level access even after partial discovery in September until December, when they finally lost control. The attack was designed to target specific organizations with interests in East Asia geopolitics as reported by Ars Technica.
How did the attackers compromise Notepad++ updates?
The attackers exploited multiple weaknesses in the update mechanism. Older Notepad++ versions used HTTP (unencrypted) for update checks, making traffic easy to intercept. Even with HTTPS, certificate validation wasn't robust—self-signed certificates were used in some versions and were publicly documented. The attackers conducted ISP-level traffic interception and TLS manipulation to redirect users to malicious update servers. Because Notepad++ update traffic is sparse, the attackers could operate at that chokepoint without raising suspicion as detailed by Rescana.
How can I tell if my Notepad++ installation was compromised?
Update to version 8.8.8.8 or higher immediately from the official Notepad++ website. If you were running an older version between June and December 2024 and received an update during that period, you may have been exposed. Check your installed version in Help menu. If it's below 8.8.8.8, you were vulnerable. Organizations with advanced logging can look for unusual network connections from gup.exe or notepad++.exe processes, unexpected file creation in the %TEMP% directory, or child processes spawned by the update mechanism as noted by The Hacker News.
What should organizations do to prevent similar supply chain attacks?
Implement software bill of materials (SBOM) tracking, verify cryptographic signatures on updates before deployment, isolate update infrastructure from general networks, monitor unusual update traffic patterns, develop incident response procedures specifically for supply chain compromises, and assess vendor security practices. Additionally, reduce dependency on single vendors where possible, participate in security research communities for early warning of threats, and invest in the security of critical open-source projects your organization depends on.
Why were the attackers interested in Notepad++ specifically?
Notepad++ runs with user privileges across millions of systems globally, making it valuable for espionage targeting technical professionals. Its open-source status and decades-long track record create exceptional trust—users don't suspect it, and endpoint protection doesn't scrutinize it heavily. People use Notepad++ to work on sensitive materials like configuration files with credentials, research involving classified information, and geopolitically sensitive intelligence. The targeting pattern shows attackers selected victims with interests in East Asia, making it an ideal espionage tool rather than a mass-distribution malware platform as reported by CyberPress.
How does this compare to other supply chain attacks?
The Notepad++ attack follows a pattern seen in Solar Winds (2020), 3CX (2023), and XZ Utils (2024) compromises. Each demonstrates that trusted software is a critical vulnerability surface. What makes Notepad++ notable is that it's open-source and volunteer-maintained with limited funding, revealing how supply chain security depends partly on adequate resourcing. The attack also shows nation-state patience—maintaining access for six months before being discovered—which differs from criminal supply chain attacks focused on rapid monetization as noted by Industrial Cyber.
What changes did Notepad++ make to prevent future attacks?
Version 8.8.8.8 and beyond hardened the update mechanism with stronger certificate validation, improved signature checking, and better verification of update integrity. Developers are considering additional long-term approaches including signed manifest files to verify expected updates, pinned certificates to prevent TLS interception, infrastructure redundancy across multiple delivery points, better access controls and monitoring on update servers, and transparency reports publishing update traffic statistics and cryptographic verification data as detailed by InfoSecurity Magazine.
Should organizations block Notepad++ or disable its auto-update functionality?
Disabling auto-update is a reasonable precaution for organizations in sensitive sectors, as the update mechanism was exploited. However, completely blocking Notepad++ isn't necessary if users update to version 8.8.8.8 or higher. Organizations can implement network controls like firewall rules restricting gup.exe to specific IP ranges or blocking notepad-plus-plus.org traffic if Notepad++ isn't business-critical. According to researcher Kevin Beaumont, blocking internet access from notepad++.exe itself is overkill for most organizations and difficult to maintain without breaking functionality.
What does this attack reveal about open-source software security funding?
Notepad++ is maintained by volunteers with modest funding. Well-funded commercial software companies can implement robust security practices like certificate pinning, signed update manifests with timestamp verification, regular security audits, intrusion detection on infrastructure, and dedicated incident response teams. Notepad++ developers couldn't afford these investments, revealing how the open-source ecosystem provides immense value globally but operates on shoestring budgets. This imbalance means that state actors can find entry points in the free software that critical infrastructure depends on. The tech industry should consider better funding mechanisms for crucial open-source projects.
How can I verify that my Notepad++ updates are legitimate going forward?
Download directly from the official notepad-plus-plus.org website rather than relying on auto-update for older versions. Check that you're on version 8.8.8.8 or higher, which includes hardened update verification. If your organization wants additional assurance, you can manually verify cryptographic signatures of downloaded files (Notepad++ provides these on their releases page). For highly sensitive environments, stage updates in test systems first and monitor for unusual behavior before deploying to production systems. Disable auto-update and perform manual monthly checks if you want the most control.

Key Insights and Takeaways
The Notepad++ supply chain attack represents a significant evolution in how nation-state threat actors target the digital ecosystem. Rather than attacking endpoints directly, sophisticated attackers are increasingly compromising the tools and infrastructure that organizations depend on, turning trust itself into a vulnerability.
The attack's success reveals critical gaps in how we think about software security. Most organizations focus on protecting their own code and systems, but they're vulnerable to compromises in the supply chain—the thousands of vendors, services, and dependencies that deliver that software.
What makes this attack particularly chilling is its selective nature. By choosing targets carefully, the attackers reduced the chance of detection while maximizing intelligence value. This demonstrates that supply chain attacks aren't necessarily noticed quickly just because they affect popular software.
Moving forward, organizations need to fundamentally rethink their approach to third-party software. You can't rely solely on vendor reputation, open-source status, or years of stability. You need technical controls: software bill of materials, signature verification, isolated update infrastructure, network monitoring, and incident response procedures specifically designed for supply chain compromises.
Equally important is the recognition that adequate funding for security is a public good. Open-source projects that the internet depends on deserve investment in security infrastructure, audits, and maintenance. The cost of funding secure development is far lower than the cost of responding to supply chain attacks.
The Notepad++ attack won't be the last of its kind. But organizations that take these lessons seriously—implementing defense in depth, participating in security communities, and investing in the health of critical software infrastructure—will be better positioned to survive and recover when the next supply chain compromise emerges.
Start today: check your Notepad++ version, update if needed, and assess how supply chain security fits into your broader security strategy. The cost of preparation is minimal. The cost of ignoring this lesson is potentially devastating.
Key Takeaways
- Supply chain attacks target the tools organizations trust, bypassing traditional endpoint defenses by compromising vendors rather than victims directly
- The Notepad++ compromise exploited multiple weak links: HTTP update traffic, self-signed certificates, and ISP-level traffic interception capability
- At least three organizations experienced hands-on-keyboard attacks with demonstrated targeting of entities with interests in East Asia geopolitics
- Immediate action: update to Notepad++ version 8.8.8.8 or higher; disable auto-update on older versions and verify updates manually
- Long-term defense requires defense-in-depth: SBOM tracking, signature verification, isolated infrastructure, robust monitoring, and specific incident response procedures
- Open-source software security gaps exist because volunteer-maintained projects lack funding for infrastructure hardening and security audits
- Nation-state attackers operate on different timescales than criminals—maintaining access for six months while planning selective targeting demonstrates patience and resources
Related Articles
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- North Korean Labyrinth Chollima Malware Splits Into Three Entities [2025]
- ShinyHunters SSO Scams: How Vishing & Phishing Attacks Work [2025]
- Software Integrity vs Data Sovereignty: Why Code Matters More [2025]
- Major Cybersecurity Threats & Digital Crime This Week [2025]
- Agentic AI Security Risk: What Enterprise Teams Must Know [2025]
![Notepad++ Supply Chain Attack: What You Need to Know [2025]](https://tryrunable.com/blog/notepad-supply-chain-attack-what-you-need-to-know-2025/image-1-1770066780793.jpg)



