Russia's VPN Crackdown 2026: New Laws & Blocking Tactics Explained
If you're following Russia's internet situation, you've probably noticed things are getting more hostile. Not toward people—toward the tools they use to access information freely. Russia's battle against VPNs isn't new, but it's entering a phase that's genuinely harder to circumvent than anything that came before.
We're talking about a shift from simple IP blocking to something way more sophisticated. Deep packet inspection that identifies encrypted traffic patterns. Laws that treat VPN use as a criminal offense, not just a regulatory annoyance. ISP-level blocks that don't just filter websites, they strangle the protocols themselves.
Here's what's happening: Russia spent years telling people VPNs were illegal. Most people ignored that, because enforcement was spotty and workarounds existed. But that's changing. The Kremlin realized that bans alone don't work when millions of people have already installed apps. So they're deploying technical weapons that don't care about laws—they just break the connection.
This matters beyond Russia's borders. What works here often spreads to other regressive regimes. China watches, takes notes, and upgrades its "Great Firewall." Iran learns. Belarus copies. So understanding Russia's 2026 strategy isn't just about Russians accessing Twitter. It's about the future of internet control globally.
Let's break down what's actually happening, what changed in 2025, and what you should realistically expect over the next 12 months.
TL; DR
- Russia escalated VPN enforcement in 2025 with advanced blocking technology targeting encrypted traffic patterns, not just IP addresses
- New laws criminalize VPN use, making it a serious offense rather than just a regulatory violation
- Deep packet inspection (DPI) and protocol blocking are the primary technical weapons now deployed by Russian ISPs
- Even paid VPN services struggle, as Russia targets the VPN infrastructure itself rather than individual users
- 2026 will likely see stricter penalties and smarter detection, with enforcement focusing on business VPN users and corporate networks first
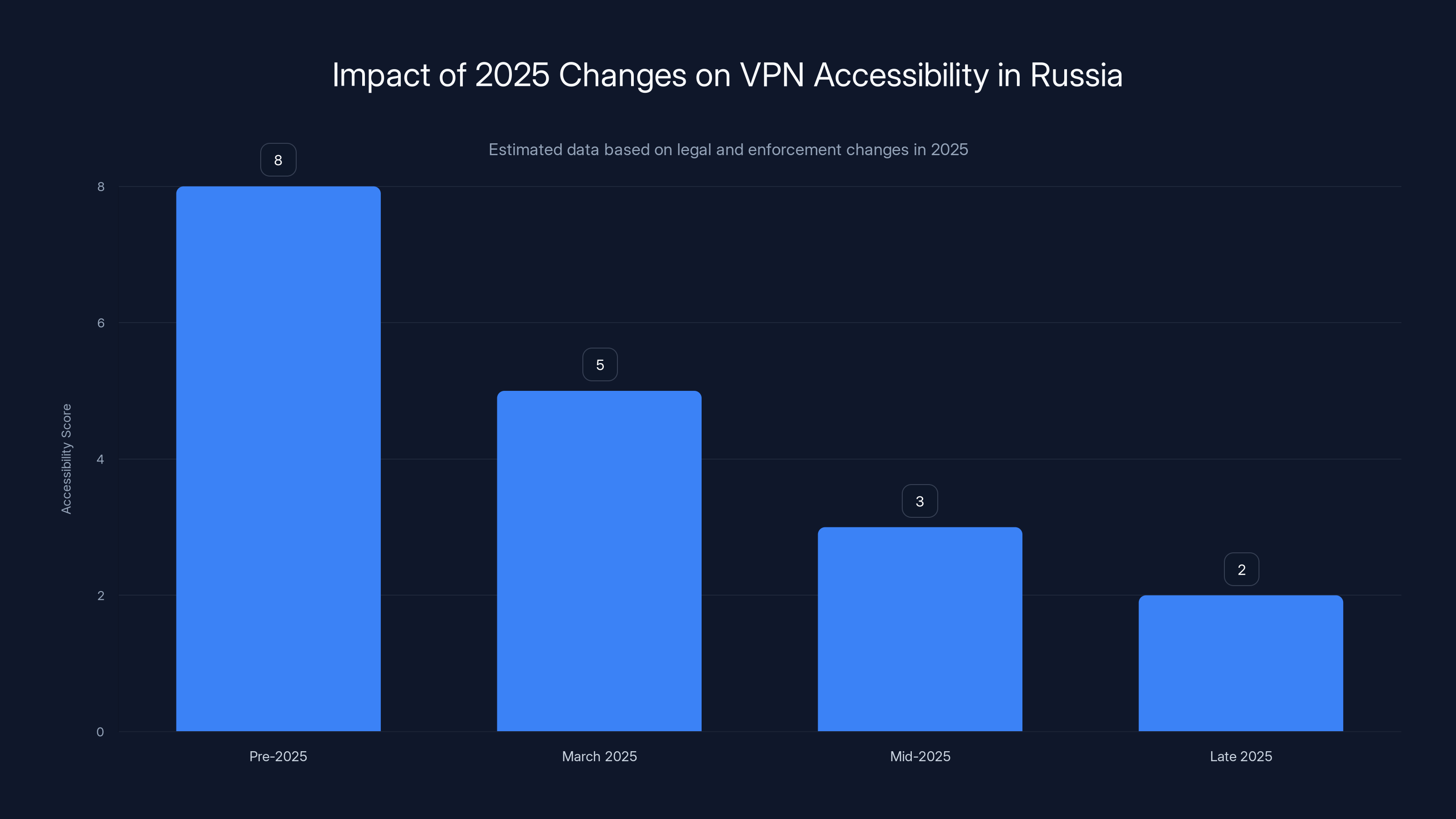
VPN accessibility in Russia significantly decreased in 2025 due to legal changes and ISP enforcement, dropping from a score of 8 to 2. Estimated data.
The Evolution of Russia's VPN War
Russia didn't wake up one day and decide to ban VPNs. This was a slow escalation that started around 2017 when they began blocking proxy servers and Tor exit nodes. The initial approach was crude: block IP addresses, blacklist VPN provider servers, hope people give up.
That didn't work. People switched VPN providers faster than Russia could block them. By 2020, the Federal Service for Supervision of Communications said they'd blocked over 1,400 VPN provider IPs. Did that stop VPN usage? Nope. According to data from internet monitoring services, VPN usage actually increased during COVID lockdowns when Russians wanted to access foreign services and information sources.
The turning point came around 2023-2024. Russian lawmakers realized they couldn't win a game of whack-a-mole with IP addresses. VPN companies constantly rotate servers, use multiple providers, hide behind larger infrastructure. So Russia switched strategies. Instead of blocking individual VPN servers, they started targeting the technology itself.
This is fundamentally different. Instead of saying "this IP is banned," Russia's approach became "this type of encrypted traffic is suspicious." That's the power of deep packet inspection. It's not about blocking a specific service. It's about analyzing how data moves and crushing anything that looks like circumvention.
What made this shift possible? The Russian government essentially forced all major ISPs to install DPI equipment. These aren't optional upgrades. They're mandated by law. Every major internet backbone in Russia now has the ability to inspect encrypted traffic at scale.
The government didn't invent this technology, obviously. Companies like Cisco, Sandvine, and other network equipment manufacturers have been selling DPI solutions globally for years. But Russia took these tools and deployed them comprehensively, creating what's essentially a national-level VPN detection system.
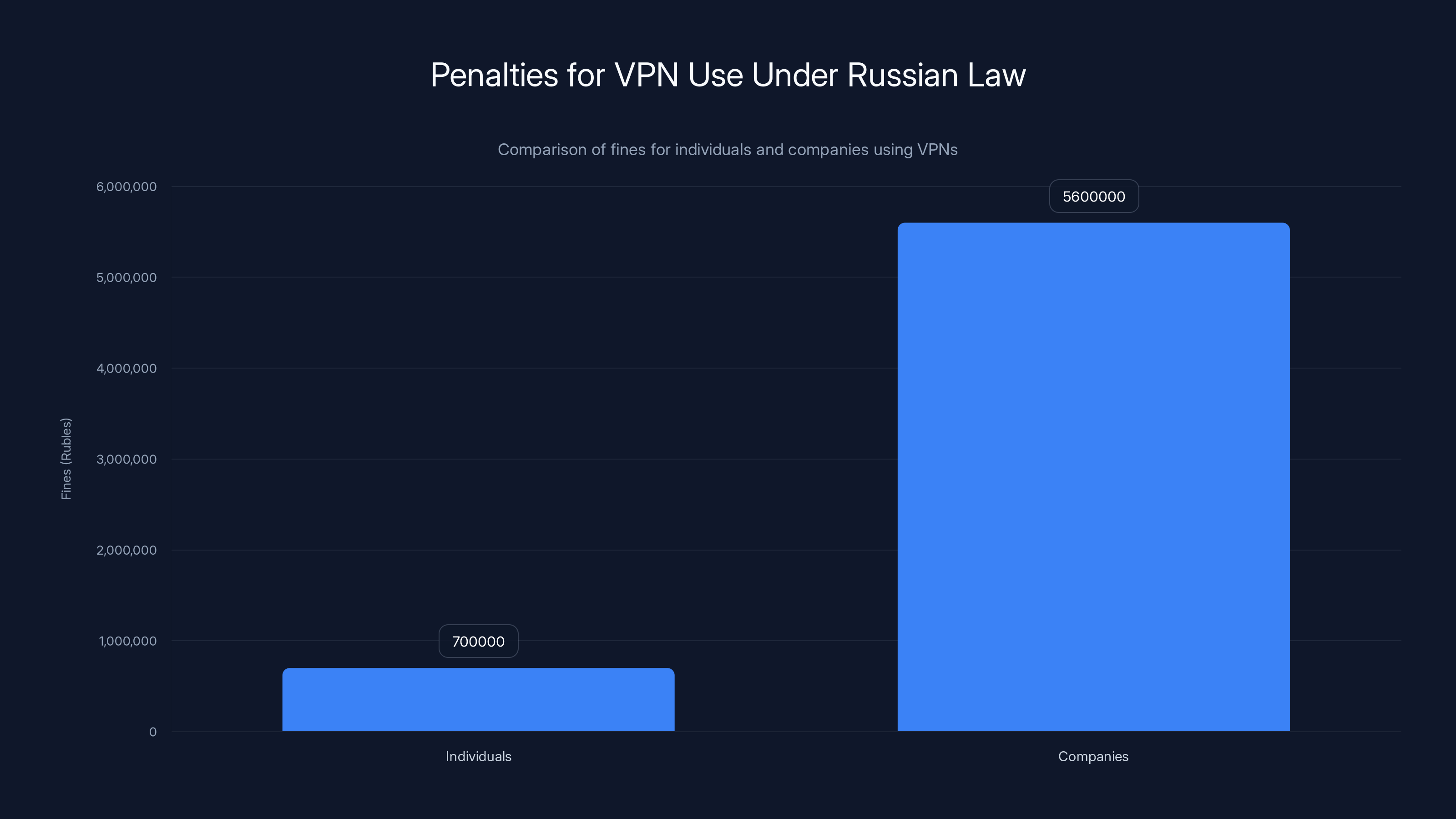
The fines for VPN use in Russia are significantly higher for companies (up to 5.6 million rubles) compared to individuals (up to 700,000 rubles).
What Actually Changed in 2025
Let's talk specifics about 2025 because this is where things got real. Several things happened that fundamentally altered the VPN landscape in Russia.
First, the legal framework changed. In March 2025, Russia formally updated its law on information technology to include stricter penalties for VPN use. Before, using a VPN was in a gray zone—technically illegal but mostly unenforceable at an individual level. Now it's explicitly illegal, with potential penalties including fines up to 700,000 rubles (about $7,000 USD) for individuals.
But here's the thing that matters more than the fines: these laws now give ISPs explicit legal cover to aggressively block VPN traffic. Before, they could claim they were blocking "suspicious traffic." Now they have a mandate. The distinction matters because it removes legal liability from ISPs for over-blocking or disrupting services.
Second, major VPN providers started getting systematically blocked in ways that were difficult to circumvent. Express VPN, which had been accessible in Russia until mid-2025, became largely inaccessible. Nord VPN experienced intermittent blocking. Smaller providers got blocked faster. But here's the critical part: it wasn't just about blocking their main servers anymore.
Russian ISPs deployed something called "protocol discrimination." They didn't just block known VPN IP addresses. They started identifying VPN traffic by analyzing the encrypted data packets themselves—looking at packet sizes, timing patterns, frequency. This is much harder to work around than simple IP blocking because you can't just "move to a new server" if the ISP is blocking the protocol itself.
Third, enforcement shifted to the corporate sector. In mid-2025, Russian authorities began systematically targeting businesses using VPNs for international operations. This is significant because it shows they're willing to escalate beyond just blocking consumer services. Companies that relied on VPNs for secure communication with foreign offices suddenly couldn't maintain those connections.
The logic here is strategic: target businesses first because they can't easily migrate away. They need reliable, continuous connections for operations. By making VPN use painful for corporations, the government demonstrates to individuals that "even big companies can't reliably use these tools."
Fourth, the government started pressuring VPN companies directly. Not through courts, but through infrastructure. Telegram, which had been somewhat resistant to blocking, suddenly became significantly slower in Russia. The government made clear that any company facilitating access to blocked content would face degradation.
What's brilliant about this approach (from the government's perspective) is that it doesn't require perfect blocking. It just requires making VPN usage slow, unreliable, and frustrating enough that most people stop bothering. A VPN that works 30% of the time is less useful than one that works 90% of the time, but it's also harder to prove is deliberately blocked.

Deep Packet Inspection: How Russia Actually Detects VPNs
Understanding DPI is crucial because it explains why traditional VPN blocking isn't working anymore. This technology is the reason why "just get a VPN" stopped being reliable advice in Russia during 2025.
Here's how DPI works at a basic level: normally, your ISP sees your encrypted traffic but can't read it. All they see is metadata—the source IP, destination IP, amount of data transferred. With DPI, the ISP can inspect the traffic more deeply.
Now, they still can't read encrypted data (proper encryption prevents that). But they can look for telltale signs that you're using a VPN. Different VPN protocols have different fingerprints. Open VPN has a specific packet structure. Wire Guard has different timing patterns. These signatures are detectable even if the payload is encrypted.
Russia deployed software that recognizes these signatures at ISP-level checkpoints. When DPI identifies VPN traffic, it doesn't necessarily block it immediately. Sometimes it just degrades the connection until the user gives up. Sometimes it injects packets that disrupt the connection. Sometimes it does block it outright.
The sophisticated part is that DPI isn't just looking for known VPN providers. It's looking for VPN behavior. That means even a VPN you set up yourself, or a less-known provider, can be detected because the protocol itself has recognizable characteristics.
This is fundamentally different from IP blocking, which is why workarounds that previously worked have become unreliable. You can't "just switch servers" when the ISP is blocking the protocol, not the IP address.
Russia has been particularly aggressive with Open VPN blocking. This protocol, which was extremely popular in Russia because it's open-source and reliable, became nearly unusable by late 2025 on most major ISPs. The government essentially said, "we can identify and block this protocol," and most VPN companies responded by switching users to other protocols.
But here's where it gets harder: as VPN providers switch to other protocols (Wire Guard, IKEv 2, proprietary solutions), Russia's DPI systems learn to identify those too. It's an arms race, and Russia's playing with more resources and infrastructure control than any VPN company.
The math is lopsided: Russia controls the entire ISP infrastructure in the country. VPN companies operate from outside the country and have no visibility into what DPI systems are actually detecting. It's like trying to beat a video game where the developers can change the rules in real-time, and you're playing blind.
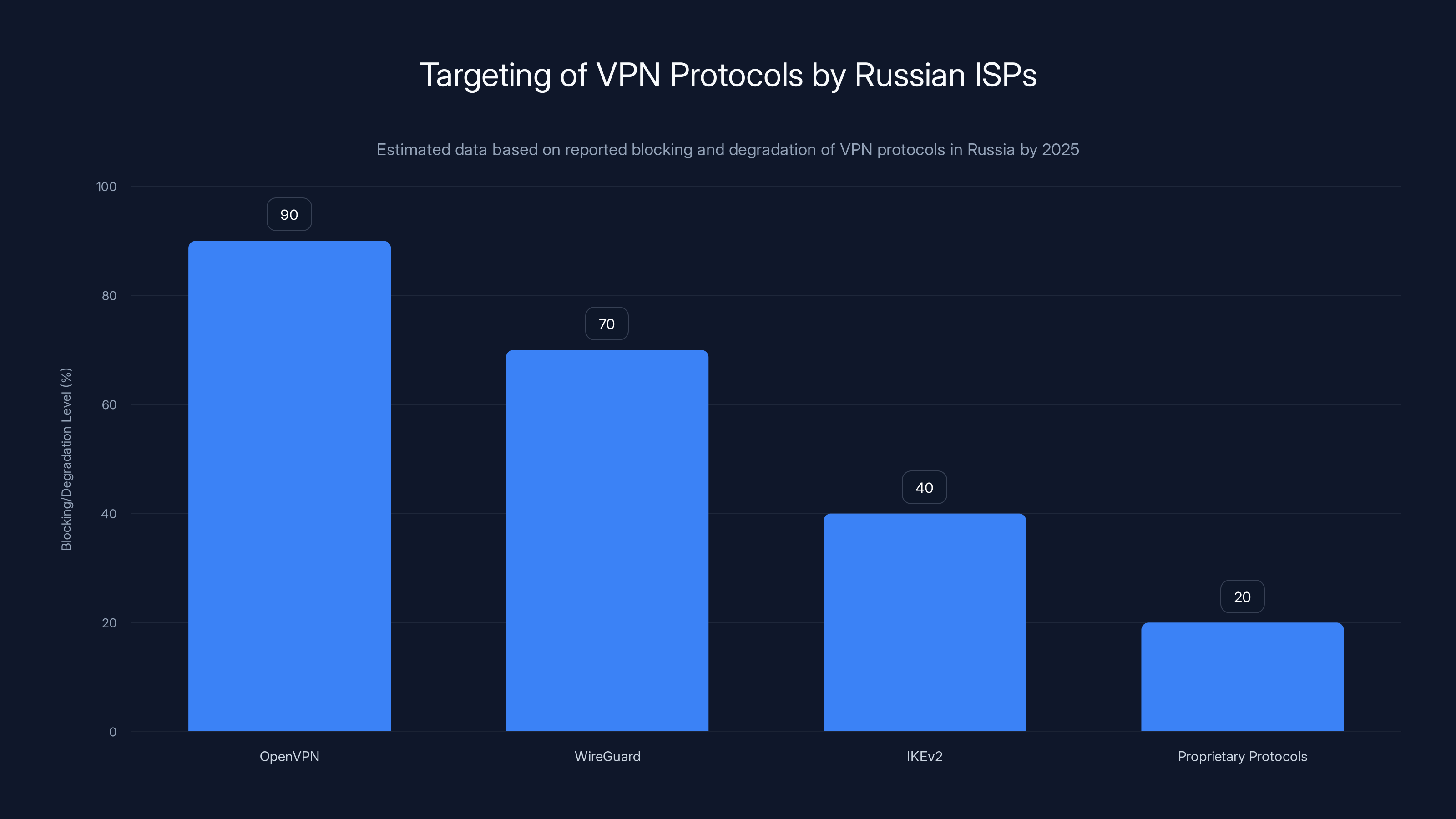
OpenVPN faced the highest level of blocking by Russian ISPs, followed by WireGuard. IKEv2 and proprietary protocols were less affected due to their use in legitimate business applications and custom implementations, respectively. (Estimated data)
The Business of Blocking: Who's Actually Implementing These Blocks
You might think the Russian government is personally blocking VPNs. It's not. The government created the legal framework and mandated that ISPs comply. But who actually pulls the trigger?
Russia has a relatively concentrated ISP market. The major players are Rostelecom, Mega Fon, and Veon (formerly Beeline). These three companies control the vast majority of residential and business internet access. When the government mandates VPN blocking, these companies implement it.
Why do they comply so readily? Partly because they have no choice—it's the law. But also because they're often state-controlled or state-influenced. Rostelecom is technically a private company, but the government is the largest shareholder. Mega Fon is privately held but has explicit government relationships. Veon is also private but operates in a heavily regulated environment.
What's important to understand is that these companies aren't secretly sympathetic to internet freedom. They're telecommunications monopolies in a country without robust antitrust enforcement. The government tells them to block something, they block it. There's no meaningful mechanism for customers to complain effectively.
In 2025, these ISPs deployed DPI software from multiple vendors. Some of it comes from Russian companies like Rostelecom's own DPI solutions. Some comes from international vendors who still sell to the Russian market despite sanctions. The effect is comprehensive coverage across the country's backbone.
Small ISPs have less leverage. They depend on wholesale bandwidth from the major carriers, so if Rostelecom blocks VPN traffic at the backbone level, smaller ISPs can't really bypass that. This means blocking is effectively nationwide, not just isolated to one company.
What's also worth noting is that these ISPs have learned over years of blocking what works and what doesn't. They've been blocking access to individual websites since around 2010. By 2025, they had perfected those techniques. VPN blocking is just applying established expertise to a new target.
VPN Protocol Wars: Which Protocols Russia Targeted First
Not all VPN protocols are created equal in Russia's eyes. Some are easier to detect and block than others. Understanding which protocols Russia has targeted tells you something about what might still work, and for how long.
Open VPN was the first major casualty. This protocol was the industry standard for years—open-source, well-documented, widely used. That was also its weakness. Because it's open-source and well-documented, the DPI systems that Russian ISPs deployed could relatively easily identify it.
By mid-2025, Open VPN was essentially non-functional on most Russian ISPs. Users reported connections timing out or being reset. It wasn't total blocking—Open VPN still technically worked, but it was so slow and unreliable that few people bothered.
Wire Guard came next. This is a newer protocol that's supposed to be more secure and efficient than Open VPN. Several VPN providers switched users to Wire Guard when Open VPN became unreliable. But by late 2025, Wire Guard was also being targeted. It's harder to block than Open VPN (the protocol is more compact and less obvious), but not impossible.
IKEv 2 has been more resistant to blocking, partly because it's also used by legitimate business VPNs and remote work solutions. Blocking it completely would disrupt too many non-circumvention uses, so Russian ISPs have been more cautious. But there are reports of it being selectively slowed and degraded.
The real interesting category is proprietary VPN protocols. Companies like Express VPN use custom protocols that are designed specifically to evade detection. These are harder for Russian ISPs to block because they're not standardized and constantly evolving. But here's the catch: proprietary protocols require you to trust the company's implementation. You can't audit the code yourself.
Some providers have started using obfuscation, which is VPN traffic wrapped to look like normal HTTPS traffic. This works sometimes, but it's resource-intensive and degrades performance. It's like trying to hide a shipment of gold by wrapping it in ordinary cardboard boxes and sending it with normal mail. Possible, but inefficient.
The deeper issue is that as VPN providers deploy new protocols or obfuscation, Russian DPI systems learn to identify and block them too. It's a literal arms race, and the ISPs have all the advantages: infrastructure control, resources, and zero penalty for false positives (if they accidentally block some legitimate traffic, there's no enforcement against them).

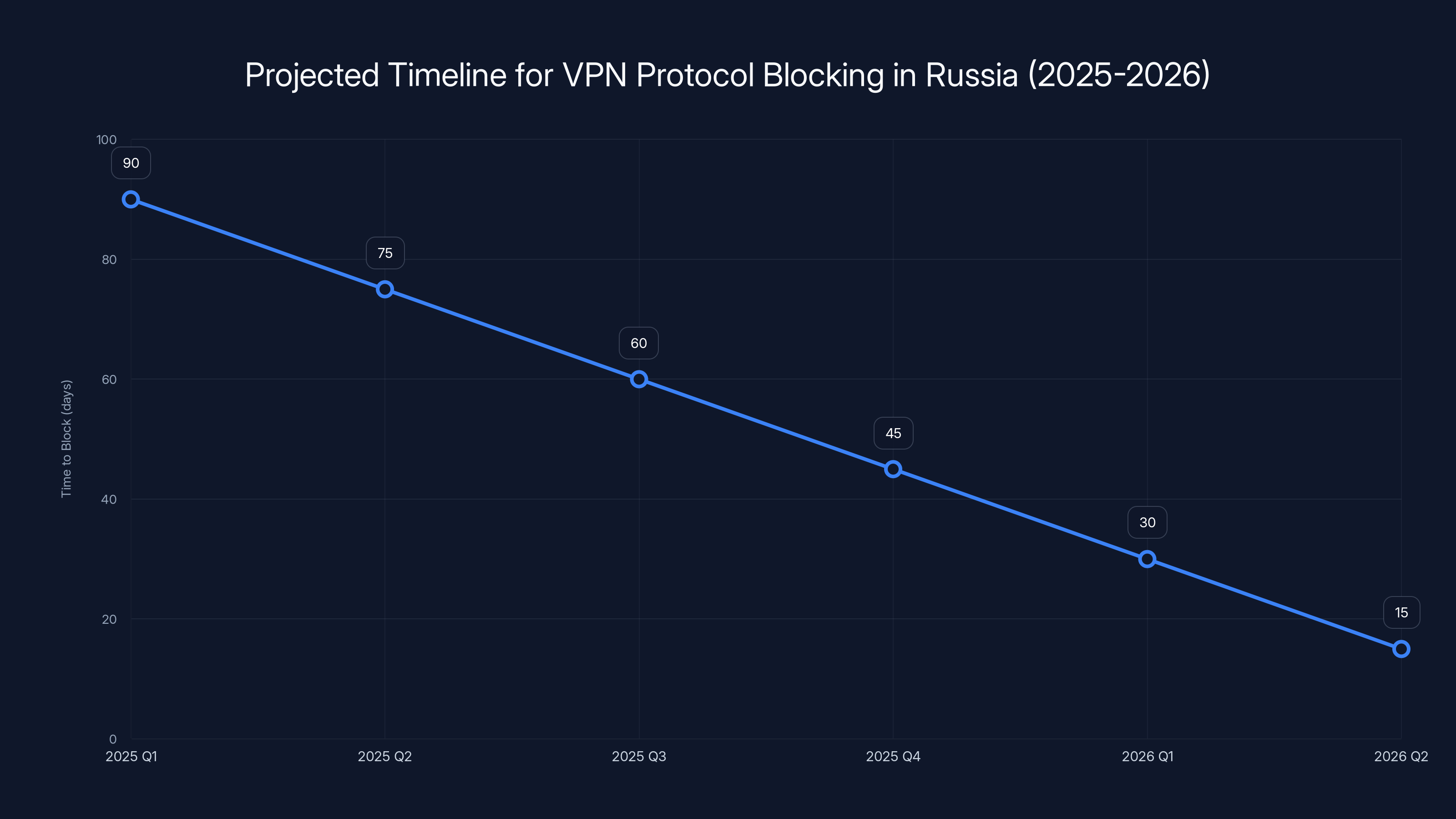
By mid-2026, the time it takes for Russian ISPs to block new VPN protocols is projected to decrease from months to just days, indicating a significant escalation in enforcement capabilities. Estimated data.
The Legal Dimension: What Russian Law Actually Says Now
The legal framework is worth understanding because it explains why this crackdown is so different from previous ones. Before 2025, VPN use existed in a legal gray zone. It wasn't explicitly permitted, but it wasn't explicitly prohibited either.
Now it is. Russia's law on information technology was amended to include explicit language about VPNs. The law essentially states that using VPNs to bypass Russian internet restrictions is illegal. Penalties include:
- Fines up to 700,000 rubles (approximately $7,000 USD) for individuals
- Fines up to 5.6 million rubles (approximately $56,000 USD) for companies
- Potential criminal penalties for "facilitating" VPN use (which could apply to VPN companies, though enforcement against foreign companies is complicated)
But here's what matters more than the penalties: the law provides legal cover for ISPs to aggressively block. Previously, an ISP that over-blocked and disrupted business connectivity could theoretically face liability. Now, they have an explicit mandate to block VPN traffic. That removes the legal risk from their perspective.
The law also gives the government ammunition for enforcement. Previously, catching someone using a VPN required the government to inspect their traffic, which raised privacy concerns. Now, the law itself is the justification. Authorities can target specific users or businesses if they know they're using VPNs.
In practice, enforcement against individuals has been minimal so far. The government isn't running mass surveillance of VPN users (or at least not publicly). But enforcement against businesses is increasing. In 2025, Russian authorities targeted several international companies for using VPNs to communicate with foreign offices.
The real enforcement lever isn't fining individuals—that would be politically unpopular. The lever is making VPN use technically impossible and legally risky, so people self-censor and comply without requiring explicit prosecution.
There's also an international dimension. Russia's law on VPNs is part of a broader effort to bring international companies into compliance with Russian regulations. If you're a VPN provider operating from outside Russia, you're not subject to Russian law. But if you have any operations in Russia (employees, servers, anything), you could face legal consequences.
This is why some VPN companies quietly pulled out of Russia. Not because they were explicitly ordered to, but because the legal risk became too high. Others stayed but stopped advertising or offering new features in Russia, effectively letting their user base atrophy.

What to Expect in 2026: The Likely Escalation
Basic rule: when Russia figures out how to block something, it typically escalates enforcement and technical capability over the next 12 months. We should expect the same with VPNs.
First, expect DPI to get smarter. By 2026, Russian ISPs will have data from a full year of DPI operation. They'll know which protocols are most popular, which traffic patterns indicate VPN use, which times of day people are most likely to use VPNs. Machine learning can be applied to this data to improve detection accuracy.
VPN providers will respond with new obfuscation techniques and protocols. Some will work initially. But the gap between "new workaround deployed" and "ISPs block it" is shrinking. In 2025, it took months for ISPs to block new protocols. In 2026, it might take weeks or days.
Second, expect enforcement to expand to more businesses. The Kremlin will likely push harder on companies using VPNs, partly to make an example, partly because businesses have more regulatory leverage than individuals. If a major bank can't use VPNs for secure international transfers, the economic pressure to comply becomes real.
Third, expect neighboring countries to watch and copy. Belarus is already discussing similar VPN restrictions. Central Asian countries are considering it. Some reports suggest Iran is looking at Russia's DPI infrastructure as a potential model. If you're not in Russia but care about internet freedom globally, this matters.
Fourth, expect the government to ramp up the propaganda. "VPN use is unpatriotic." "VPN users are helping foreign powers attack Russia." "Blocking VPNs protects Russian security." This narrative softens the ground for more aggressive enforcement.
Fifth, expect some technical improvements to bypass techniques. Researchers will keep trying to stay ahead of DPI. Some new protocols will emerge. But realistically, none of these will be as reliable or performant as VPNs were before 2025. It's a losing arms race from the VPN perspective.
One wildcard is international pressure or sanctions. If the U. S. or EU sanctioned Russian ISPs or DPI vendors for censorship, it could disrupt the blocking infrastructure. But Russia's already heavily sanctioned, and these sanctions haven't meaningfully affected internet blocking operations. So don't count on that.
Another wildcard is technical innovation from VPN companies. If someone figures out a fundamentally new way to tunnel traffic that doesn't rely on recognizable protocols, that could change the game. But this requires research and innovation, and most VPN companies are profit-focused, not research-focused. The incentives don't align with spending money on fundamental R&D for a market that's becoming legally risky and technically hostile.

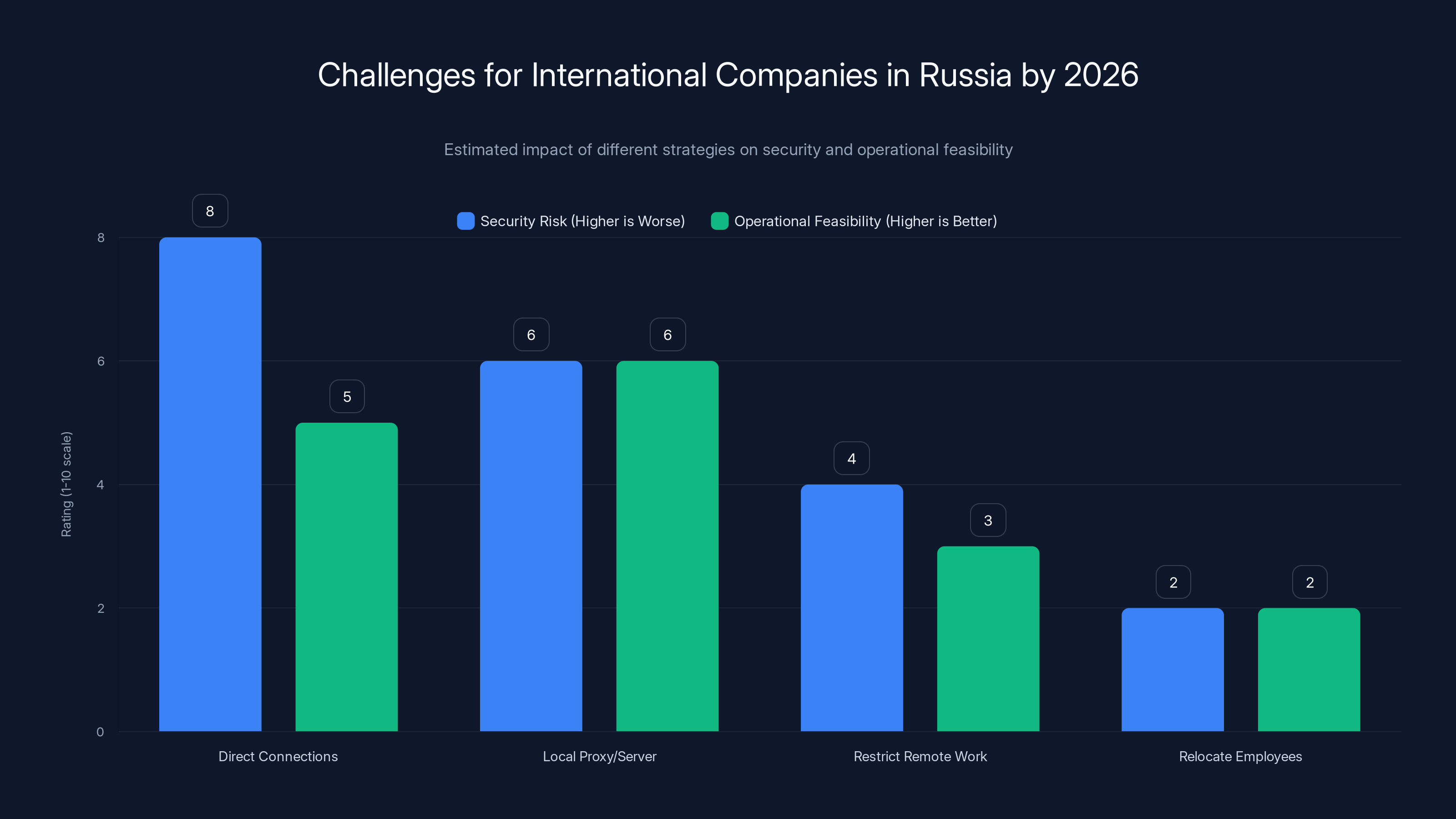
Direct connections pose the highest security risk, while relocating employees offers the least risk but is the least feasible. Estimated data based on typical strategic impacts.
The Global Implications: What Russia's VPN Crackdown Means for Internet Freedom Worldwide
None of this is isolated to Russia. When the Kremlin figures out how to suppress internet freedom, others watch and learn.
China has been running an even more sophisticated censorship system for years. But China's approach is slower and more labor-intensive because they're trying to block specific content at scale. Russia's approach is elegant: just block the tools, and the content blocking becomes automatic because people can't access anything that circumvents it.
Iran has also been moving in this direction. They've blocked or degraded access to international VPNs multiple times in recent years, typically during periods of political unrest. If Russia's 2025-2026 strategy proves effective, Iran's authorities will almost certainly adopt similar technical measures.
The concerning part is that DPI technology isn't that expensive or sophisticated anymore. Small countries with decent tech expertise can now deploy systems that were once reserved for large, wealthy nations. This creates a scenario where VPN blocking becomes a global norm rather than an exception.
What Russia proved in 2025 is that IP blocking is dead as a censorship strategy. It's too easy to work around. But DPI-based protocol blocking is much harder to defeat, and it's available to any government that wants to invest in it. That's a significant shift in the balance of power between internet users and governments.
For companies, this means the reliability of secure communications is eroding in authoritarian-leaning countries. If you have operations in Russia, Belarus, Iran, or similar countries, you can't reliably use VPNs anymore. That changes how you have to structure security.
For individuals, it means internet freedom is increasingly a privilege of countries with independent internet infrastructure and privacy regulations. In countries with state-controlled ISPs, there's no technical solution that's both reliable and legal.
The broader implication is that the internet is becoming more fragmented. Not into separate networks, but into regions where different censorship and surveillance norms apply. You might access the global internet freely from many Western countries, but accessing it from Russia, China, Iran, or other countries becomes progressively harder.
This has real consequences for dissidents, journalists, and ordinary people who want access to information. It also has consequences for companies that can't reliably operate in these markets anymore.

Alternatives to VPNs in Russia: What Actually Works
Let's be honest: standard VPNs are becoming unreliable in Russia. So what actually works?
The answer is: very little works well, but there are options that are slightly better than VPNs at avoiding detection.
The Tor network is still functional in Russia, though access is being progressively restricted. Tor works differently than VPNs—instead of creating a single encrypted tunnel, it routes traffic through multiple nodes, making traffic analysis harder. Russian ISPs have blocked or degraded direct access to Tor entry nodes, but bridges (alternate entry points) still work, albeit slowly.
The advantage of Tor is that it's designed specifically to resist censorship. Developers have spent years thinking about exactly the scenario Russia is now implementing. The disadvantage is that Tor is slow. Pages load slower. Streaming video doesn't work. But for accessing text-based information, it's functional.
I2P is another option—it's similar to Tor but less widely used (which can be an advantage, since ISPs aren't as aggressive about blocking it). It's less mature than Tor and slower, but it's an option some people in Russia have reported success with.
Direct connections to foreign proxies sometimes work, but proxies are also increasingly being blocked as ISPs recognize them as bypass tools.
Some people have had success with SSH tunnels or other non-VPN encrypted connections, but these require technical knowledge and are slower.
Here's the uncomfortable truth: none of these alternatives are as good as VPNs were in, say, 2022. They're all either slower, less reliable, or more technically demanding. There's no silver bullet.
This is probably intentional on the government's part. Perfect blocking would be impossible and would break legitimate uses of encryption. But degrading all bypass tools to the point where they're unusable for normal activities (streaming, video calls, etc.) is entirely achievable.
There's also the option of just accepting the restrictions. Some Russians have. Others have relocated to countries with internet freedom. Others use workarounds and accept the frustration. All are rational responses to an irrational situation.

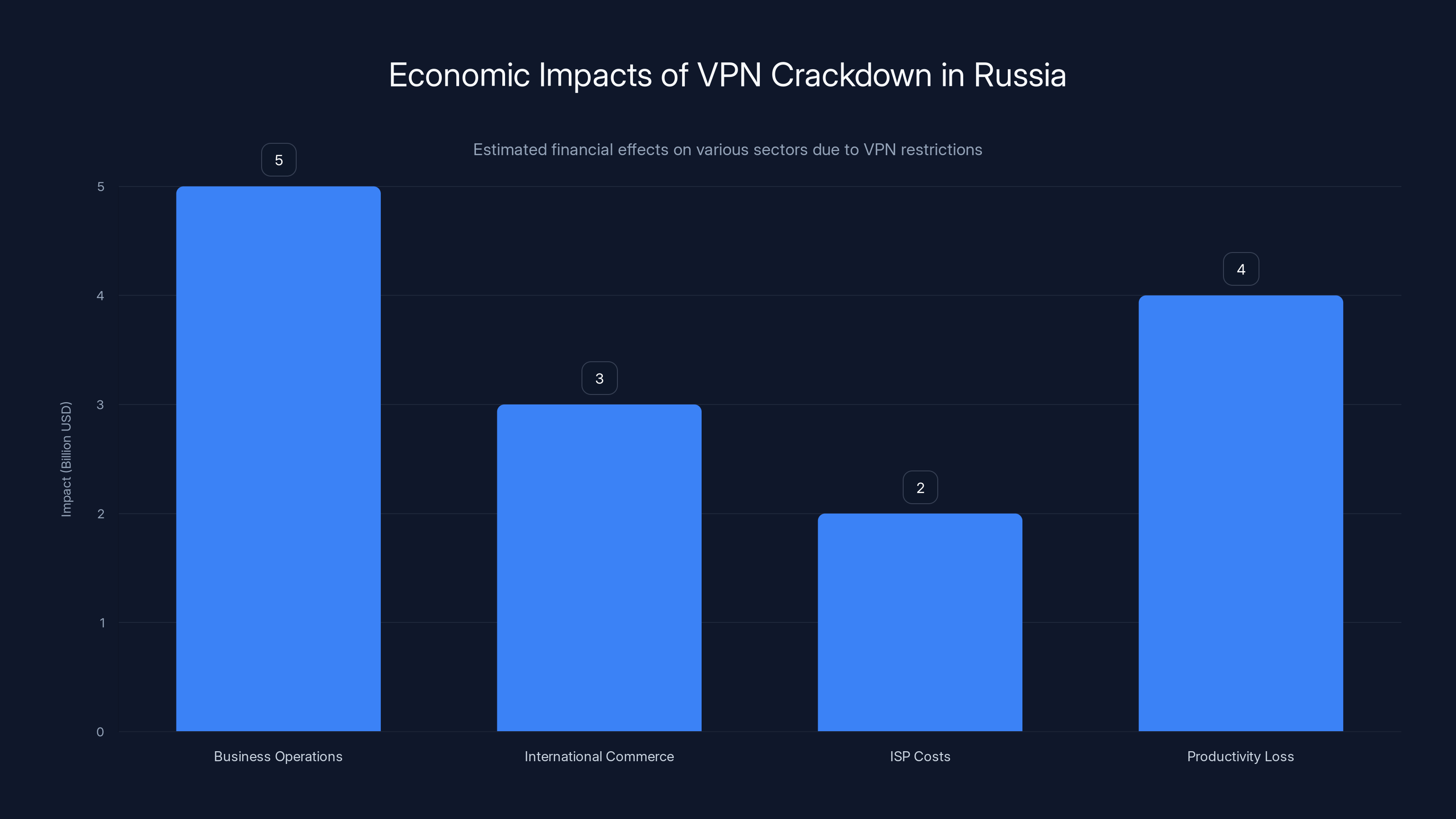
Estimated data shows significant economic impacts across business operations, international commerce, ISP costs, and productivity due to VPN restrictions in Russia.
The Corporate Perspective: What International Companies Should Expect in 2026
If you're running an international business with operations in Russia, 2026 is going to be complicated.
Your employees in Russia won't be able to reliably use VPNs to connect to your company network. That's a problem because VPNs are usually how you provide secure remote access to employees working from home or traveling.
You have a few options, and all of them are worse than VPNs:
First, you can allow direct connections to your network from Russian IP addresses. This means less security because you're not using encryption or tunneling. Your network is more exposed to Russian ISP snooping. This also might make you complicit with Russian regulations requiring access to your data.
Second, you can set up a server or proxy in Russia and allow employees to connect to that. This might not be blocked as aggressively because it doesn't look like a VPN. But it requires infrastructure investment and creates a target for Russian authorities if they decide to pressure your company.
Third, you can restrict your Russian operations and not allow remote work. This makes hiring and retaining talent harder.
Fourth, you can relocate your employees to countries with better internet infrastructure. This works if you can absorb the costs, but it's not practical for most companies.
The reality is that Russia is becoming an increasingly difficult market to operate in if you require secure international communications. Some companies have already concluded that the compliance burden and operational challenges aren't worth the market access. You'll see more companies reducing their Russia operations in 2026.
For companies that stay, the solution is usually working with compliance consultants who understand Russian regulations and can set up infrastructure that's technically compliant while minimizing security risks. This is expensive and doesn't solve the underlying problem, but it's what's available.

Financial and Economic Impacts of the VPN Crackdown
VPN blocking doesn't exist in a vacuum—it has economic consequences.
First, there's the direct cost to Russian businesses. Companies can't reliably operate internationally if they can't securely communicate with foreign offices. Some businesses require VPNs to meet security standards. If those businesses can't operate in Russia anymore, they leave. This creates a brain drain and reduces Russia's competitive advantage in tech, finance, and other sectors requiring secure communications.
Second, there's the cost to the Russian economy of reduced international commerce. If companies can't operate securely in Russia, they'll shift operations elsewhere. Some investment dries up because foreign investors are uncomfortable with the regulatory environment.
Third, there's the cost to ISPs themselves. They have to invest in DPI equipment, maintain it, and run the blocking operations. This is expensive. Rostelecom, Mega Fon, and Veon have all reported increased infrastructure costs in recent years, partly due to government mandates to implement blocking systems.
Fourth, there's the cost in lost productivity. If people can't efficiently access information or services they need, they work slower. Researchers can't easily access academic papers. Developers can't download libraries. This is a subtle but real drag on economic productivity.
The financial hit is probably worth it from the Kremlin's perspective (political control is priceless to them), but it's real. Russia's tech sector is already struggling due to sanctions and brain drain. The VPN restrictions are another force pushing technical talent out of the country.
From a macroeconomic perspective, Russia's VPN crackdown is similar to other autarky-oriented policies: it provides short-term political control at the cost of long-term economic competitiveness. The Kremlin seems willing to accept that tradeoff.

Technical Deep Dive: How Obfuscation Works and Why It's Not a Silver Bullet
As governments got better at blocking VPNs, security researchers and VPN companies invested in obfuscation. This is the idea of disguising VPN traffic to look like normal internet traffic.
In theory, obfuscation sounds perfect: if your VPN traffic looks like HTTPS traffic, the ISP can't block it without blocking legitimate HTTPS. Problem solved, right?
Not quite. There are several reasons why obfuscation is limited:
First, it doesn't scale. Obfuscation requires additional processing. It adds latency and reduces throughput. If a normal VPN connection gets you 80 Mbps, an obfuscated connection might get you 30 Mbps. Doable for email and text, not viable for streaming or video calls.
Second, it's detectable. Obfuscation tries to make VPN traffic look like HTTPS. But legitimate HTTPS has specific patterns. Real HTTPS from real websites (Amazon, Google, Facebook) has recognizable signatures. Fake HTTPS made to look like VPN disguise has different patterns. DPI systems can learn to distinguish between real HTTPS and obfuscated VPN HTTPS.
Third, it's cat-and-mouse. As VPN companies deploy new obfuscation techniques, ISPs learn to identify and block them. The timeline for this cycle is shrinking. In 2024, new obfuscation methods could work for months. In 2025, they work for weeks. By 2026, they might work for days.
Fourth, it's proprietary. Open-source obfuscation is easier to analyze and block. So VPN companies create proprietary obfuscation, which requires users to trust the company's implementation without being able to audit it. This defeats some of the security benefits of using open-source protocols in the first place.
Does this mean obfuscation doesn't work at all? No. It works sometimes, for some users, on some networks. But as a reliable bypass technique for a committed adversary like Russia, it has fundamental limits.
This is why researchers are interested in novel approaches. Some are working on using steganography (hiding data inside other data). Some are experimenting with protocol variants that are harder to fingerprint. Some are exploring ways to distribute VPN traffic across multiple connections to make it less identifiable.
But all of these approaches have tradeoffs. They're slower, more complex, or less reliable than standard VPNs. They're solutions for the technically sophisticated, not for average users.
What This Means for Privacy and Surveillance
The VPN crackdown isn't just about blocking access to information. It's about enabling surveillance.
When you can't use a VPN in Russia, your ISP can see more of your traffic. They can see which websites you visit, which apps you use, what videos you watch. They can't decrypt HTTPS traffic, but they can see that you're accessing certain domains.
This has obvious privacy implications for individuals. But it also has surveillance implications. Russian authorities can work with ISPs to identify who's accessing banned websites, dissenting media sources, or opposition political sites.
In recent years, Russian authorities have prosecuted political activists, journalists, and protesters based partly on evidence of their internet activity. VPN blocking makes that easier. If everyone's traffic is visible, identifying dissidents becomes a matter of examining logs.
This is part of a broader pattern in Russia of increasing surveillance and digital repression. VPN blocking is one piece, but it connects to facial recognition systems, online banking monitoring, payment system integration, and other surveillance infrastructure.
The concerning part is that this model is replicable. Any government with control of ISP infrastructure can implement it. And as the technical barriers get lower, more governments will.
From a human rights perspective, this is a regression. Internet access, and particularly access to uncensored information, has been recognized as important for human development and dignity. VPN blocking directly undermines that.

Regulatory and Geopolitical Context
Russia's VPN crackdown doesn't happen in isolation. It's part of a broader push by several countries to exert greater control over their internet infrastructure and data flows.
China's Great Firewall is the obvious comparison, but there are others. Saudi Arabia restricts VPN use. Turkey has intermittently blocked VPNs. Thailand, Vietnam, and several other countries have some form of VPN restriction.
The trend is moving in one direction: toward greater state control over internet infrastructure and a narrowing of the tools available for circumventing state censorship.
This has geopolitical implications. Countries with free internet infrastructure (like the U. S., most of Europe, Canada) maintain information advantages. Citizens have access to diverse information sources. Countries with restricted internet infrastructure (Russia, China, Iran) have information disadvantages. Citizens rely on state-controlled media.
This creates a bifurcated world in terms of information access. Over time, this probably contributes to different political worldviews and makes international cooperation harder.
It also affects the tech industry. VPN companies that operated globally are now restricted from serving large markets. This reduces their revenue and potentially their innovation capacity. Simultaneously, governments developing censorship infrastructure create economic opportunities for censorship technology vendors.
We're essentially seeing the creation of a global censorship industry. Companies like Fortinet, Palo Alto Networks, Cisco, and others sell network security and inspection technology that's increasingly being repurposed for censorship. This is probably inevitable, but it's worth being aware of.

What Individual Russian Internet Users Should Actually Do
If you're reading this and you're in Russia, what should you actually do?
First, understand that your situation has changed materially from 2024 to 2025. VPNs that used to work reliably are now spotty or completely blocked. Workarounds exist, but they're getting progressively harder.
Second, evaluate your actual needs. What information or services do you need that require bypassing Russian internet restrictions? Academic papers? News from specific sources? Access to social media? Communication tools? Different tools have different bypass difficulty.
Third, try Tor if you need reliable access to diverse information. It's slow, but it works. You'll need to download the Tor Browser from the Tor Project website (which Russia might block, so consider downloading it before you're in-country or using a bridge).
Fourth, consider whether you can accept the restrictions. Some Russians have. Some have relocated. Some use workarounds and accept the frustration. All are valid choices depending on your situation.
Fifth, if you're using alternative tools, understand their security properties. Some tools are less secure than others. Don't assume that because a tool bypasses censorship, it's protecting your privacy from the Russian government or other threats.
Sixth, if you're a business, work with compliance consultants or security firms that specialize in this environment. They can advise on legal and technical solutions that work within (or around) Russian regulations.
Seventh, document what works now. If you find a specific VPN provider or protocol that works reliably, save that information. In 6 months, it might be blocked, but you'll know what the timeline is.
Lastly, understand that you're not alone. Millions of Russians are dealing with this same situation. Online communities discuss workarounds, share information about what's blocked, and provide support. Finding these communities (carefully, since they're sometimes monitored) can help.

Looking Ahead: 2027 and Beyond
If the trend continues, what does the internet landscape look like in Russia in 2027?
Most likely scenario: VPN access becomes negligible. Maybe 10-20% of Russians who care enough will use Tor or other tools. Most will accept the restrictions or leave the country. Business VPNs will continue operating in degraded capacity through workarounds and corporate proxies, but with significant operational overhead.
Alternate scenario: A breakthrough in circumvention technology emerges that's hard to block and relatively performant. This is possible but unlikely without significant research investment.
Another scenario: International pressure or sanctions specifically target Russian DPI infrastructure. This would disrupt blocking but seems unlikely given current geopolitical trends.
Most realistic? The current trajectory continues. Blocking gets smarter, workarounds get slower, and the internet becomes more regionalized with Russia as a more isolated information zone.
For people who value internet freedom, it's a depressing trajectory. But understanding how it's actually happening (not the simplified "governments just block VPNs" narrative) is the first step to thinking about potential countermeasures.

FAQ
What is a VPN and why are they important in Russia?
A VPN (Virtual Private Network) encrypts your internet traffic and routes it through a server in another country, making your activity harder to track by your local ISP. In Russia, VPNs became essential tools for accessing information that the government blocks, communicating privately, and conducting secure international business. Since 2025, they've been technically blocked and legally restricted.
How does Russia's DPI technology work to block VPNs?
Deep Packet Inspection examines the structure and patterns of encrypted data packets to identify VPN traffic without decrypting it. Russian ISPs use DPI to recognize the telltale signatures of different VPN protocols (like Open VPN or Wire Guard) and then block or degrade connections using those protocols. This is more effective than IP blocking because it targets the technology itself, not specific servers.
What changed in Russia's VPN laws in 2025?
In 2025, Russia explicitly criminalized VPN use with penalties up to 700,000 rubles for individuals and 5.6 million rubles for companies. More importantly, this gave ISPs legal authority to aggressively block VPN traffic. Previously, VPN use existed in a legal gray zone. Now it's explicitly illegal, which fundamentally changed enforcement and technical blocking capabilities.
Which VPN protocols still work in Russia?
As of late 2025, no VPN protocol works reliably across all Russian ISPs. Open VPN is nearly unusable. Wire Guard is increasingly blocked. IKEv 2 and proprietary protocols have more limited success but face growing interference. The reality is that all standard VPN protocols are progressively becoming unreliable, not just blocked outright.
Is Tor still functional in Russia?
Yes, Tor still functions in Russia, though accessing it has become harder. Direct connections to Tor entry nodes are often blocked, but Tor bridges (alternate entry points) still work. The drawback is that Tor is significantly slower than VPNs, making it impractical for streaming video or bandwidth-intensive activities.
What are the economic impacts of VPN blocking on Russia?
VPN blocking reduces Russia's attractiveness for international business and tech talent, creates operational challenges for companies requiring secure communications, increases infrastructure costs for ISPs, and reduces worker productivity. The Kremlin seems willing to accept these costs for the political control benefits, but the cumulative economic impact is significant and growing.
Can international companies still operate in Russia safely without VPNs?
It's increasingly difficult. Most international companies relied on VPNs for secure communications between Russian offices and foreign headquarters. Without VPNs, they either accept reduced security, build expensive alternative infrastructure within Russia, or reduce operations. Some companies have already chosen to exit the market entirely due to these complications.
What should I do if I'm in Russia and need to access blocked information?
Your realistic options are limited. Tor still works for text-based content but is slow. Direct proxies are increasingly blocked. Standard VPNs are unreliable. If you need reliable access, Tor is your best option. If you accept slower speeds, it will work. For business communications, you'll likely need to work with your company's IT department to find compliant solutions.
Is Russia's VPN crackdown affecting other countries?
Yes, indirectly. China, Iran, and other countries are watching Russia's DPI deployment as a template for their own VPN restrictions. The technology is becoming cheaper and more accessible, making it likely that VPN blocking will spread to other authoritarian-leaning governments in coming years.
What's the difference between VPN blocking and censorship?
VPN blocking doesn't directly censor specific content—it blocks the tool used to access content. However, the effect is similar: restricting which information is accessible. You can still access Russian state media without a VPN, but accessing independent news sources, foreign social media, or information the government dislikes becomes much harder without a VPN.

Conclusion
Russia's VPN crackdown entered a new phase in 2025, moving from crude IP blocking to sophisticated protocol detection and legal prohibition. This represents a meaningful escalation in how authoritarian governments control information access.
The technical reality is that standard VPNs are no longer reliably functional in Russia. Deep packet inspection systems can identify and block VPN traffic regardless of which provider you use. The legal framework now explicitly criminalizes VPN use, giving ISPs mandates to block aggressively.
What matters most going into 2026 is understanding that this problem doesn't have a simple technical solution. There's no "one weird trick" that defeats DPI-based blocking. Workarounds exist, but they're slower, more technically demanding, and progressively less reliable as systems improve.
For individuals in Russia, accepting reduced internet access, migrating to Tor (despite its limitations), or relocating are the primary realistic options.
For international businesses, the calculus has shifted. Operating in Russia now requires either accepting reduced security, building expensive alternative infrastructure, or reducing operations.
For the global internet ecosystem, the trend is clear: countries with state-controlled ISPs are implementing sophisticated censorship infrastructure. This creates a bifurcated internet where information access depends heavily on geography. That's a significant shift from the internet's earlier history.
Understanding how Russia's 2025-2026 censorship actually works is important, not just for people in Russia, but for everyone concerned about internet freedom globally. The technical playbook being deployed in Russia is likely to be copied elsewhere. The economic and geopolitical implications will ripple across global tech markets and international relations.
Internet freedom isn't guaranteed. It requires active protection and constant innovation. What Russia is doing in 2025-2026 represents a sophisticated challenge to that freedom. The response—from individuals, companies, researchers, and governments that value internet freedom—will determine whether the internet remains a tool for connection and information access, or becomes increasingly fragmented and controlled.

Key Takeaways
- Russia deployed Deep Packet Inspection (DPI) systems in 2025 that identify VPN protocols by analyzing encrypted traffic patterns, making traditional IP blocking obsolete
- New Russian laws explicitly criminalize VPN use with penalties up to 700,000 rubles for individuals, while giving ISPs legal mandates to block aggressively
- All major VPN protocols including OpenVPN, WireGuard, and IKEv2 became unreliable by late 2025, with no viable standard VPN option remaining for most users
- Tor remains partially functional through bridge networks but offers significantly reduced speeds, making it the only realistic alternative for text-based content access
- By 2026, Russia's DPI-based blocking approach will likely spread globally to Iran, China, Belarus, and other authoritarian regimes, fragmenting the internet further
Related Articles
- VPN Uganda Internet Shutdown: What Happened & Workarounds [2025]
- Uganda Internet Restored But Social Media Blocked: What's Really Happening [2025]
- Iran's Internet Shutdown: Longest Ever as Protests Escalate [2025]
- TikTok's New Data Collection: What Changed and Why It Matters [2025]
- ExpressVPN Deal: 78% Off Two-Year Plans [2025]
- Best VPN Service 2026: Complete Guide & Alternatives
![Russia's VPN Crackdown 2026: New Laws & Blocking Tactics [2025]](https://tryrunable.com/blog/russia-s-vpn-crackdown-2026-new-laws-blocking-tactics-2025/image-1-1769240252796.jpg)



