Sovereign Cloud & Data Control: Who Really Owns Your Data [2025]
You've probably heard the term "sovereign cloud" thrown around by every major tech vendor lately. Amazon promises European control. Microsoft touts local data residency. Google emphasizes compliance with regional regulations. But here's the uncomfortable truth: most of what you're hearing is marketing speak.
The reality is far messier. US hyperscalers control more than two-thirds of Europe's cloud computing market. Even when they promise European operations, the parent companies remain subject to US law. That means a US court can still compel them to hand over your data through mechanisms like the CLOUD Act. For governments, banks, healthcare providers, and any organization handling sensitive information, this distinction matters more than ever.
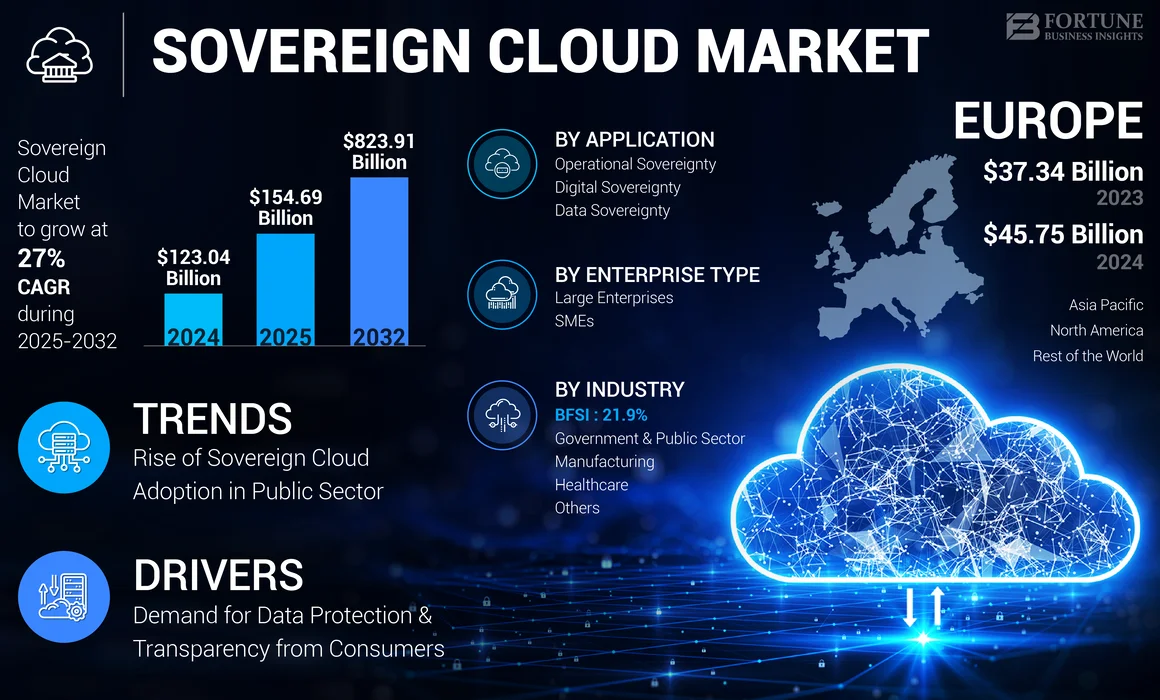
This isn't just theoretical. We're talking about real compliance risks, actual regulatory exposure, and genuine questions about where your data truly lives and who can access it. The sovereign cloud market is projected to explode from
But the market remains fragmented. Different European countries have different rules. Germany's C5 certification looks nothing like France's Sec Num Cloud framework. The EU itself is still figuring out what sovereignty actually means. Organizations are left navigating competing claims, complex technical jargon, and wildly inconsistent standards.
So what does true cloud sovereignty actually look like? How do you distinguish real sovereignty from marketing theater? And what tools and frameworks are emerging to help organizations take back control of their data? Let's dig in.
TL; DR
- US hyperscalers dominate: Amazon, Microsoft, and Google control over 66% of Europe's cloud market
- Legal jurisdiction matters: The CLOUD Act and FISA Section 702 allow US agencies to access data even when hosted abroad
- Data residency isn't enough: True sovereignty requires local legal authority, operational independence, and vendor transparency
- Fragmentation is the problem: Different EU countries have different sovereignty standards (C5, Sec Num Cloud, DORA)
- Market explosion coming: Sovereign cloud market growing from 823.91B (2032)
- Bottom line: Genuine sovereignty requires aligned infrastructure, jurisdiction, and interoperability—not just local hosting
![European Cloud Market Share by Provider Origin [2025]](https://c3wkfomnkm9nz5lc.public.blob.vercel-storage.com/charts/chart-1769942068089-ciqzqsf6n7.png)
US hyperscalers dominate the European cloud market with over two-thirds control, highlighting the challenge of achieving true data sovereignty. (Estimated data)
What True Sovereign Cloud Actually Means
Let's be clear about something from the start: sovereign cloud isn't just about where your data sits physically. If that were the case, the problem would be solved. Just store data in Frankfurt. Problem over. But it's not that simple.
True cloud sovereignty answers three distinct questions. First, the "where" question: where does the data physically reside? Second, the "who" question: who has legal authority over that data? And third, the "how constrained" question: what dependencies, vendor relationships, and technological constraints exist that might limit your freedom?
Think about it this way. You could store all your customer data on servers physically located in Germany. Sounds sovereign, right? But if those servers run on AWS infrastructure, if the parent company is subject to US law, if a US judge issues a subpoena, the data moves. The physical location becomes irrelevant.
This is where the CLOUD Act becomes critical. Enacted in 2018, the CLOUD Act permits US courts to compel US-headquartered companies to disclose electronic communications data in investigations, regardless of where that data is stored. Combine that with Section 702 of the Foreign Intelligence Surveillance Act, which allows US intelligence agencies to collect communications data on foreign nationals, and you've got a system where US jurisdiction can extend anywhere.
For a European bank handling customer financial records, this isn't abstract. For a healthcare provider storing patient data, it's a compliance nightmare. For a government department with classified information, it's an existential risk.
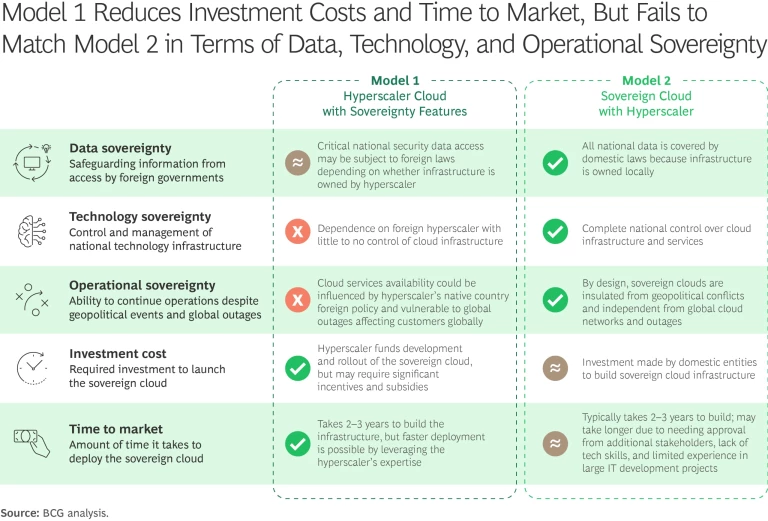
Real sovereignty therefore demands four things. First, the infrastructure must be physically located and operated within your jurisdiction. Second, the operating entity must be legally insulated from foreign jurisdiction—not just owned by a company that's insulated, but structurally separate at the operational level. Third, you need genuine interoperability and portability. You should be able to move your workloads between clouds, or at least take your data with you, without punitive switching costs or technical lock-in. Fourth, you need transparency on underlying technology, supply chains, and dependencies.
Without all four elements, you've got a partial solution at best.
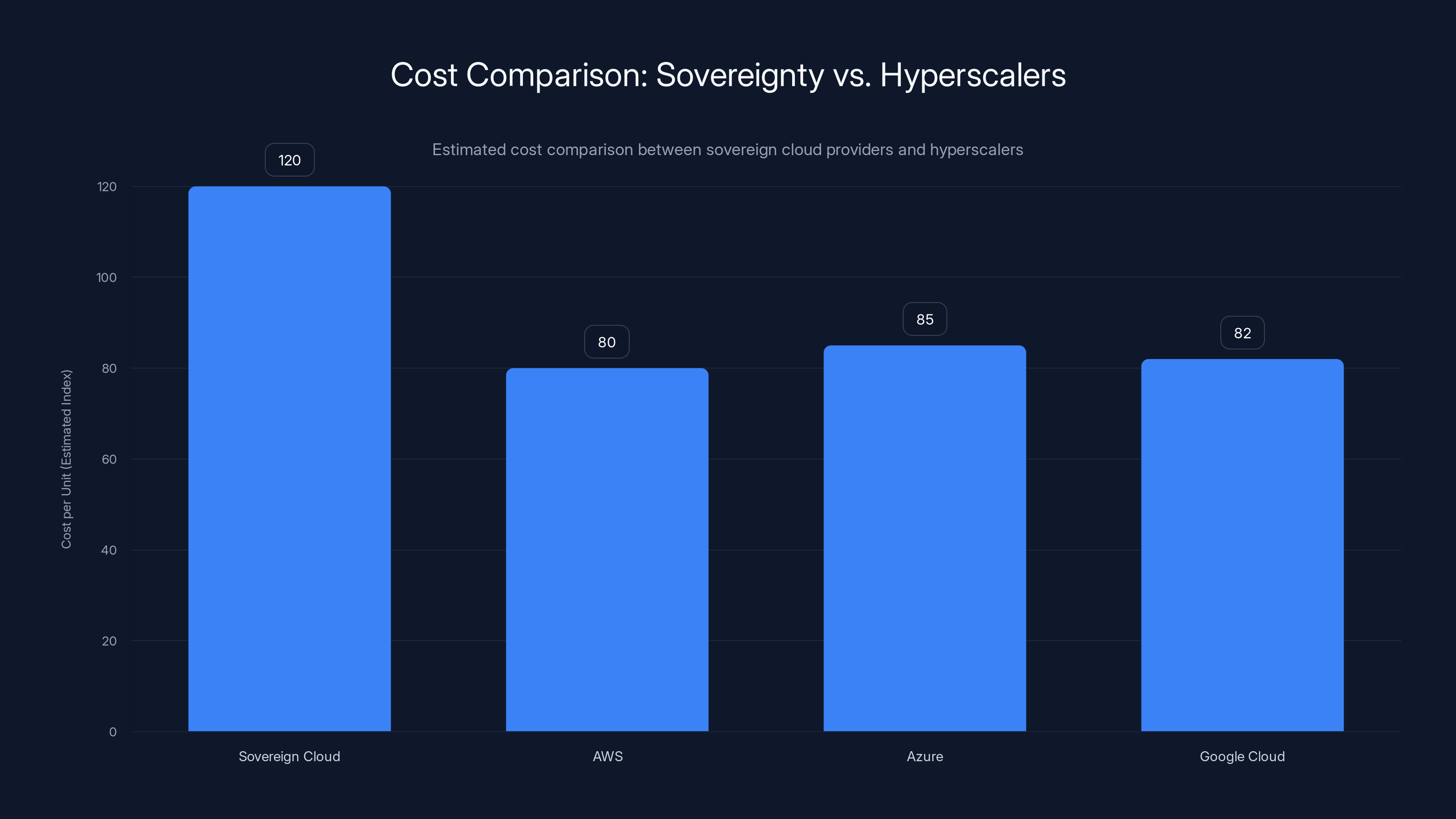
Sovereign cloud providers generally have higher costs per unit compared to hyperscalers like AWS, Azure, and Google Cloud due to smaller scale and specialized services. Estimated data.
The US Hyperscaler Dominance Problem
Here's the uncomfortable market reality: the cloud landscape is dominated by three companies. Amazon Web Services, Microsoft Azure, and Google Cloud together control more than 66% of Europe's cloud computing market. That's not competition. That's concentration.
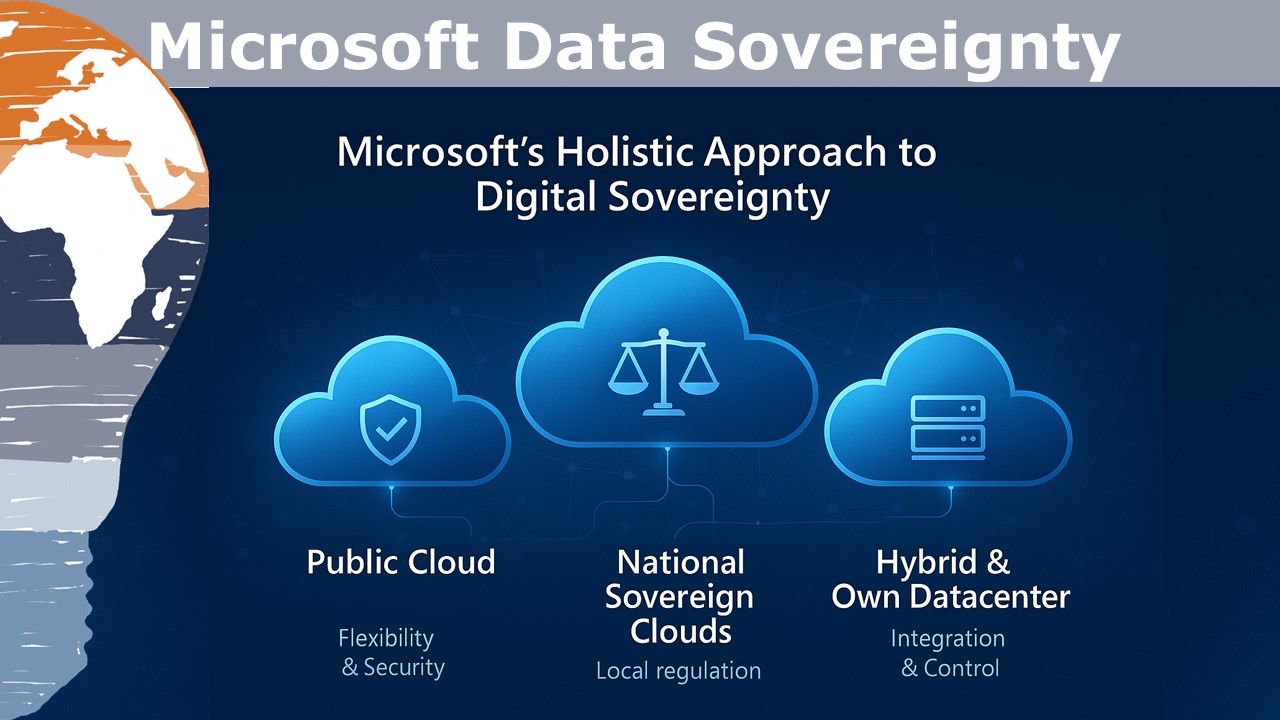
Each of these companies has launched European sovereign initiatives. AWS has created EC2 instances in EU regions with German data residency certifications. Microsoft has built partnerships with European providers and launched Azure dedicated regions. Google has expanded its European data centers. They've all invested in European compliance teams, local support, and partnership structures.
But the fundamental problem remains unchanged. These are all subsidiaries of US-headquartered parent companies subject to US law. The legal liability flows to the parent. The jurisdiction is US. The regulatory authority is US. You can build a European wrapper around a US foundation, but the foundation is still US.
This creates what we might call the "sovereignty illusion." Customers believe they've achieved control through partnerships, certifications, or dedicated instances. But they haven't. They've achieved comfort. They've achieved data residency. They've achieved compliance with some regulations. But they haven't achieved genuine sovereignty if the underlying company can still be compelled to hand over data.
The market is so concentrated because these three companies have network effects, global scale, and enormous switching costs. Moving from AWS to a European alternative means rewriting infrastructure, retraining teams, rebuilding integrations, and dealing with significantly higher costs in most cases. The path dependency is enormous.
So even though demand for European cloud sovereignty is exploding, the market structure hasn't fundamentally changed. The same companies still dominate. They've just gotten better at marketing European features.
Legal Frameworks: Why Jurisdiction Matters
Understanding sovereign cloud requires understanding legal frameworks. This is where things get genuinely complex, and where most marketing falls apart.
Start with the CLOUD Act. The full name is the Clarifying Lawful Overseas Use of Data Act. Sounds reasonable, right? In practice, it permits US courts to order US companies to disclose information stored anywhere in the world, as long as the company has access to it. The company's location, the data's location, or the customer's location doesn't matter. If a US court issues a warrant, and a US company can retrieve the data, the company must comply.
This is a genuine legal authority. It's not a hypothetical. Courts use it regularly. And it applies to every subsidiary and operation of US-headquartered companies, regardless of local legal protections.
Then there's FISA Section 702. This provision of the Foreign Intelligence Surveillance Act permits US intelligence agencies to target communications of foreign nationals outside the US without a warrant. The program is designed to capture foreign intelligence. But in practice, "upstream" collection under Section 702 inevitably captures communications involving US persons and foreign targets, which raises constitutional questions that courts are still working through.
The point is this: even if data is encrypted, even if it's stored outside the US, even if local law prohibits disclosure, US agencies have tools to access foreign data, and US companies can be compelled to facilitate that access.
European regulators recognize this. The General Data Protection Regulation (GDPR) requires organizations to ensure data security and establish lawful bases for processing. But GDPR doesn't prevent US jurisdiction from applying to US companies. The Data Act, adopted in 2024, attempts to increase European control and interoperability. But it doesn't prevent US courts from issuing subpoenas.
The result is a legal asymmetry. Europe is trying to regulate and control its data. But it can't control US law. US companies are subject to US law. And US law reaches global data.
Different European countries are responding differently. Germany created the C5 (Cloud Computing Compliance Criteria Catalogue) certification scheme, which defines security and data protection requirements. France created Sec Num Cloud, a more rigorous certification focused on government cloud services. The UK is exploring its own frameworks post-Brexit. But none of these completely resolve the US jurisdiction problem.
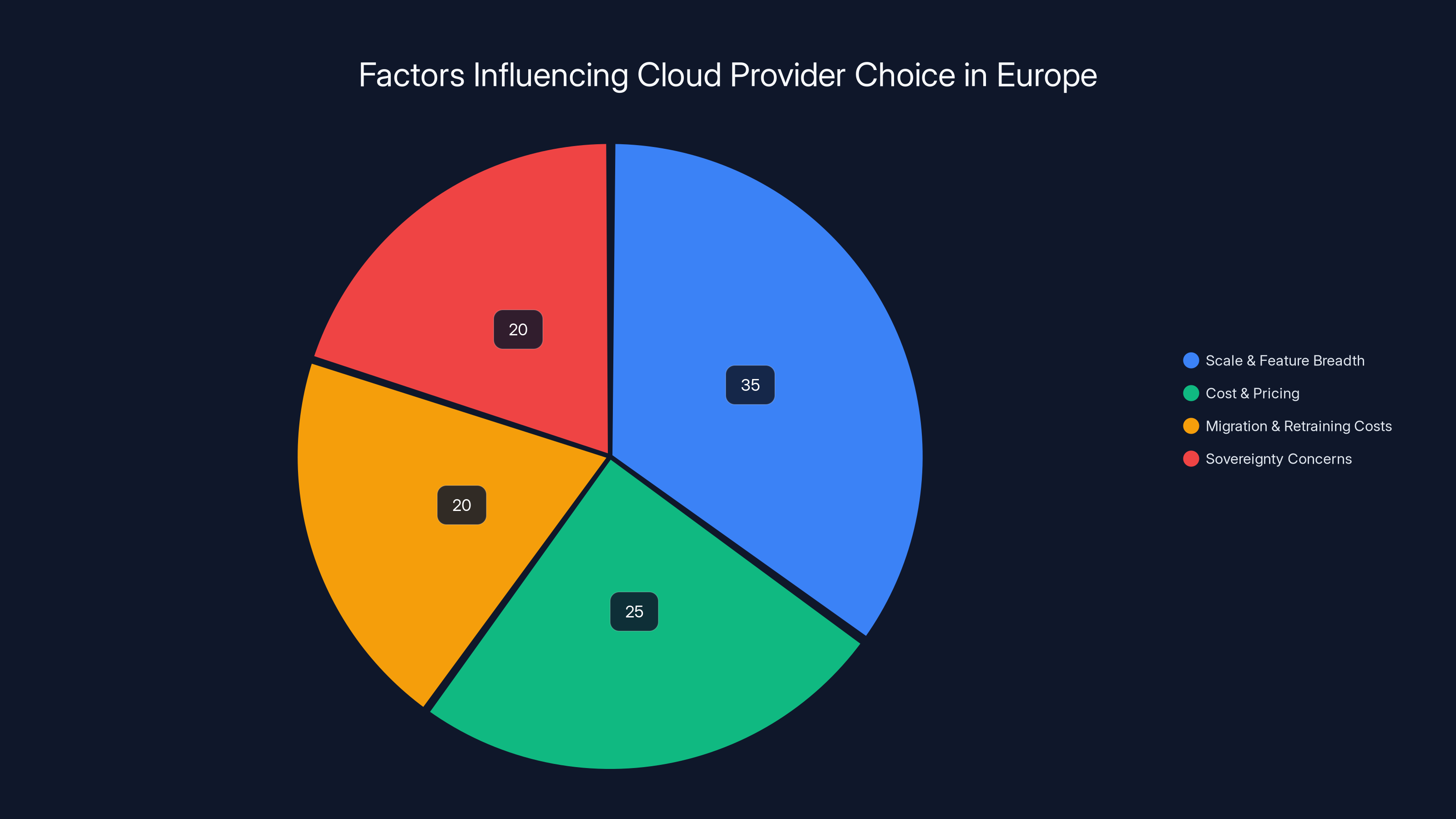
Despite sovereignty concerns, scale, feature breadth, and pricing are major factors for European organizations choosing US cloud providers. Estimated data.
The European Cloud Certification Landscape
Since no unified European standard exists, different countries have created their own certification schemes. Understanding these is crucial to understanding what options actually exist.
Germany's C5 Framework is the oldest and most established. Created by the German Federal Office for Information Security (BSI), C5 defines criteria for cloud computing providers serving German businesses and government. It requires data centers within Germany, encryption standards, audit rights, and security controls. But it doesn't require the operator to be outside US jurisdiction. Many US companies hold C5 certification because they've met the technical requirements. The certification is detailed and rigorous, but it's fundamentally about security and data residency, not sovereignty.
France's Sec Num Cloud is more restrictive. It requires cloud service providers to be European (at least 51% owned by EU entities), with data centers in France. It's designed specifically for government and critical infrastructure. Sec Num Cloud certification is harder to achieve for non-European companies, which is why many US vendors either didn't pursue it or created partnerships with French companies to do so.
The Netherlands has created its own requirements for government cloud services, emphasizing local control and European supplier preference.
Poland, Czech Republic, and other Eastern European countries have created additional frameworks as EU members increasingly prioritize digital sovereignty.
The fragmentation is a real problem. A vendor might be C5 certified in Germany but not Sec Num Cloud certified in France. They might meet UK requirements post-Brexit but fail to meet emerging German sovereignty standards. Organizations operating across multiple countries face a compliance maze.
The European Commission itself acknowledged this problem by creating DGIT (Digital Government IT Services) and attempting to define sovereignty on a scale of requirements for EU procurement. The idea was to create baseline standards that could apply across member states. But that effort has only partially succeeded. Different countries still have different priorities.
Data Residency vs. Data Sovereignty: The Critical Distinction
This distinction is where marketing usually breaks down.
Data residency is simple: where does the data physically sit? Which data center? Which country? Data residency is a technical fact. You can verify it. You can audit it. You can trace packets to confirm where data is processed.
Data sovereignty is broader. It includes residency, but it also includes jurisdiction, control, access, and independence. It answers not just "where" but "who decides what happens to this data?"
You can have perfect data residency without sovereignty. Imagine data stored on servers in Germany, operated by German staff, with German security controls. Sounds sovereign, right? But if those servers run on AWS infrastructure, if AWS holds the encryption keys, if a US judge can compel access, then Germany has residency but not sovereignty.
Conversely, you could theoretically have partial sovereignty without perfect residency if the legal framework allows it. Though that's rare in practice.
The best analogy might be real estate. Data residency is like owning physical property. Sovereignty is like owning property with genuine control, clear title, and freedom from external claims. Physical location matters, but it's not the whole story.
For organizations handling sensitive data, this distinction is everything. A government agency can't accept "the data physically lives in Germany" if US courts can still access it. A healthcare provider can't satisfy GDPR with data residency alone if jurisdiction doesn't align with protection.
This is why marketing claims about "European data" or "local hosting" are incomplete. They're answering the residency question, not the sovereignty question.

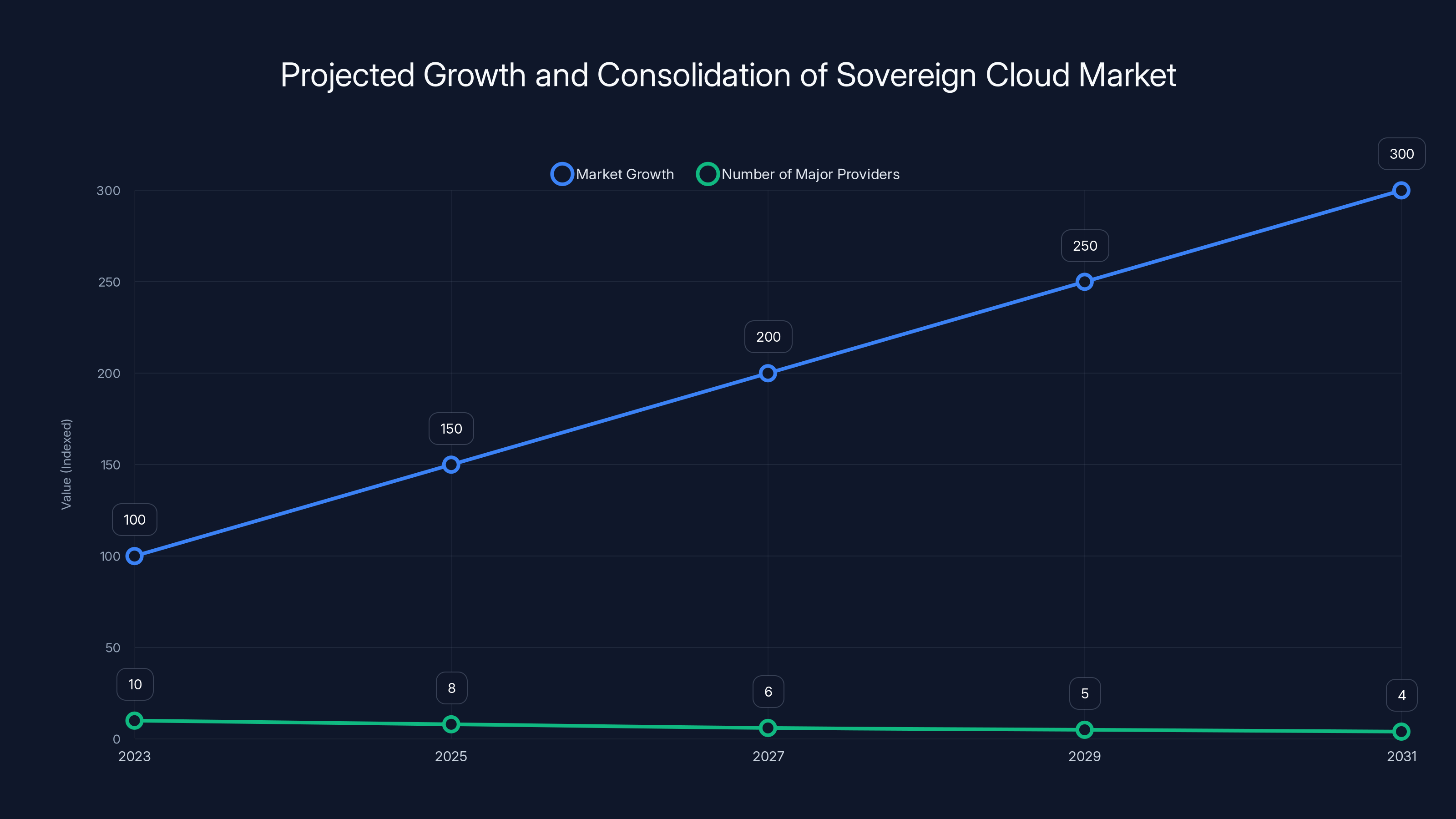
The sovereign cloud market is expected to grow significantly while the number of major providers consolidates to a few key players. (Estimated data)
The Hidden Costs of Partial Sovereignty
Choosing a "sovereign" cloud that isn't truly sovereign creates real costs. Not just compliance costs, but operational, financial, and strategic costs.
Start with compliance risk. If you're regulated by European authorities but using infrastructure subject to US jurisdiction, you're caught between two legal systems. A US court might order data disclosure. European regulators might fine you for allowing that disclosure. You lose either way.
Then there's switching cost inertia. Once you choose a cloud provider, changing is incredibly expensive. Data migration costs hundreds of thousands of dollars for large organizations. Team retraining is months-long. Rewriting integrations with third-party services is a project unto itself. So even if you later realize your "sovereign" cloud isn't actually sovereign, switching is prohibitively expensive. You're locked in.
There's innovation lag. Many European cloud alternatives are younger, smaller, and less feature-rich than the hyperscalers. Choosing them might mean giving up machine learning services, advanced analytics, or specific tooling that your team relies on. The sovereignty might be real, but the cost is real too.
There's vendor concentration risk. If you choose a European alternative and something goes wrong—the company fails, gets acquired, or changes strategy—you've got limited options. Hyperscalers have the scale to survive market downturns. Smaller European providers don't always.
And there's technical debt. Using a sovereign cloud might require custom solutions, workarounds, or architectural compromises. That's technical debt that slows future development.
For some organizations, these costs are worth paying. For governments and critical infrastructure, sovereignty matters more than cost. For regulated industries like healthcare and finance, the compliance benefits justify the expense. But for many organizations, the costs of "true" sovereignty might outweigh the benefits.
Key Players in the European Cloud Market
Beyond the hyperscalers, there are genuinely European alternatives emerging. Understanding the landscape matters because it shows what's actually possible.
OVHcloud is probably the most prominent European pure-play cloud provider. Founded in France, it operates data centers across Europe with a specific focus on European regulation compliance. OVHcloud doesn't have a US parent company, which means it's not subject to the CLOUD Act. That's genuinely significant. But OVHcloud is also smaller, less feature-rich than AWS, and more expensive for many workloads. It's a real alternative, but with real tradeoffs.
Gaia-X is an interesting case. It's not a cloud provider itself, but rather a framework and initiative trying to create a "European cloud ecosystem." The idea is to federate multiple European cloud providers, data centers, and services under a common sovereignty and interoperability standard. It's ambitious. It could work. But it's also still emerging, still finding its footing, and not yet a fully mature alternative.
Microsoft, Amazon, and Google have all launched European partnerships. Microsoft has partnered with Deutsche Telekom to create sovereign cloud offerings in Germany. AWS has created EU regions with partner operations. Google has expanded European data centers. These aren't truly independent—they're US companies operating in Europe—but they're attempting to create more legal separation.
Telefónica, Deutsche Telekom, and other European telecom companies are increasingly offering cloud services, often as partnerships with hyperscalers but branded as local options. These create a perception of European control while relying on hyperscaler infrastructure.
The market is gradually diversifying, but the fundamental concentration persists. Starting a new cloud company requires enormous capital investment, global scale, and years to build. The hyperscalers have all of that. European alternatives are either smaller pure-plays or partnerships with hyperscalers.
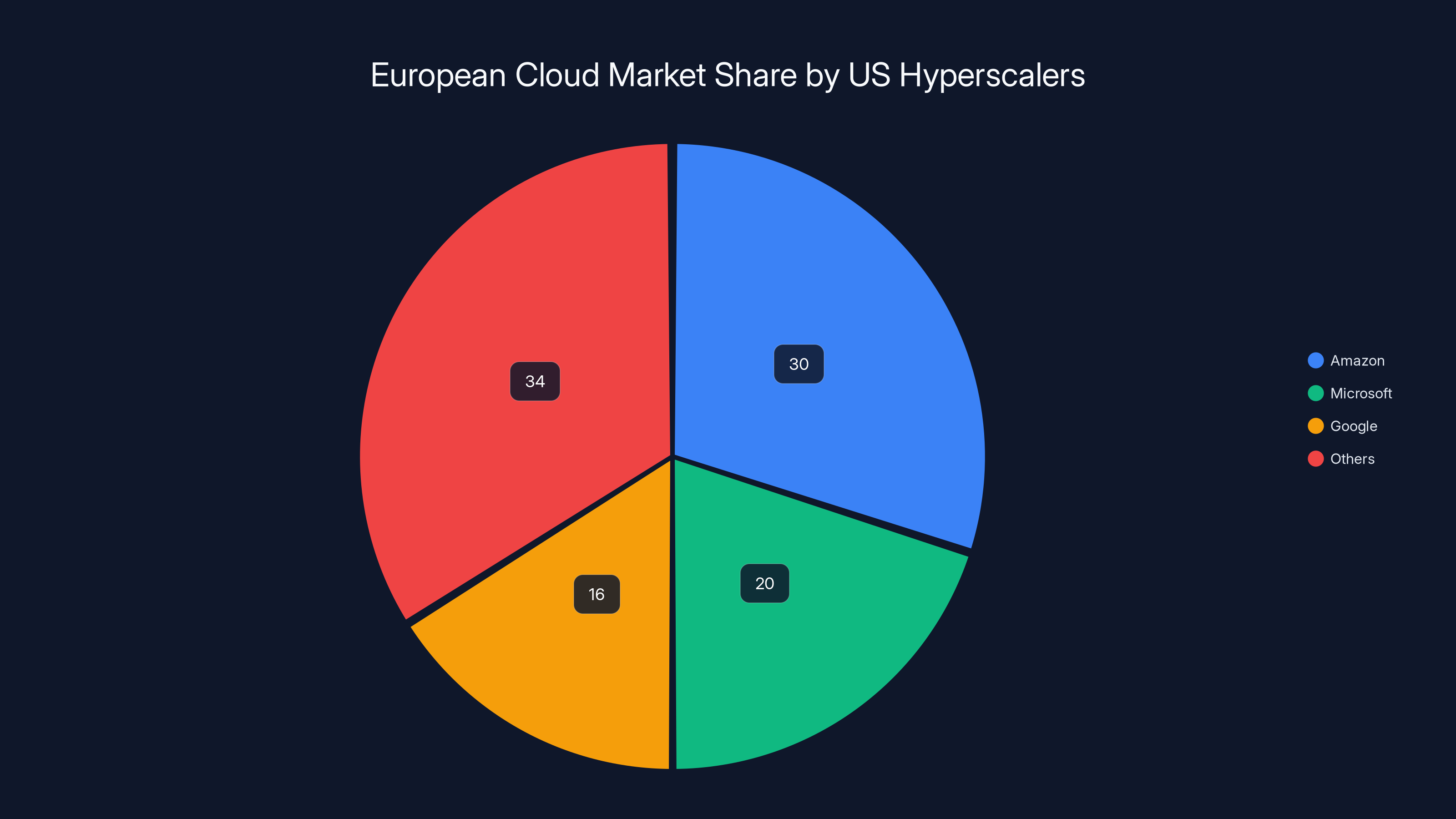
Amazon, Microsoft, and Google collectively control over 66% of Europe's cloud market, highlighting their dominance. Estimated data.
How Organizations Should Evaluate Sovereignty Claims
When a vendor claims their cloud is "sovereign," here's what you should actually verify.
First, confirm data residency. Where exactly are data centers located? Not the company's website. Get technical specifics. Which physical facilities? Which countries? Are backups in different countries? Can you audit this? Many vendors make residency claims that don't survive scrutiny. Your data might technically be in Germany, but your backups might be in AWS's US regions for redundancy. That's residency with a caveat.
Second, understand the legal entity. Who actually operates the cloud? If it's a US-headquartered company operating European services, the parent company's US jurisdiction might still apply. If it's a European subsidiary with genuine operational independence, that's different. Get a legal review of the corporate structure.
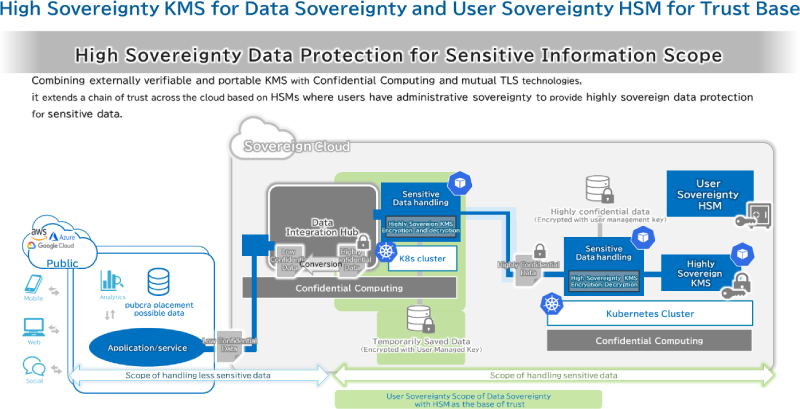
Third, verify encryption and key management. Who holds encryption keys? Can the provider decrypt your data without your permission? Many "sovereign" clouds still hold your encryption keys, which means they can decrypt your data if compelled. If you want real protection, you should hold your own keys, and the provider should never be able to decrypt without them.
Fourth, test interoperability. Can you move your data to another provider? Not in theory, but in practice? Try exporting a test dataset. Try moving a small workload. Interoperability is often promised but rarely easy.
Fifth, examine the supply chain. What hardware does the provider use? Where does it come from? What software underlies the service? If it's all proprietary European technology, that's one thing. If it's repackaged hyperscaler infrastructure, that's another.
Sixth, get independent audit rights. Can you (or a third party on your behalf) audit the provider's security, operations, and compliance? Many vendors restrict audit rights. Don't accept that. You need genuine transparency.
Seventh, understand the regulatory framework. Which certifications does the provider hold? C5? Sec Num Cloud? Something else? What does each certification actually guarantee? And which regulatory bodies have oversight? Different certifications guarantee different things.
Don't rely on marketing claims alone. Do technical due diligence. Get legal review. Run tests. The vendors claiming strongest sovereignty often have the weakest actual independence.
Regulatory Drivers: GDPR, DORA, and Emerging Standards
Regulation is pushing toward greater sovereignty requirements. Understanding the regulatory landscape is crucial to understanding where this market is headed.
GDPR (General Data Protection Regulation) is the foundation. It requires organizations to ensure data security and establish lawful bases for processing. It gives individuals rights over their data. It requires impact assessments for risky processing. But GDPR doesn't technically require data residency in Europe. You can comply with GDPR using US cloud providers, as long as you have contracts in place. Many organizations do. So GDPR pushed for data protection, but not necessarily sovereignty.
The Data Act (adopted in 2024) is more directly about control and interoperability. It requires cloud providers to enable data portability, provide access to usage data, and prevent vendor lock-in. It's explicitly designed to increase European control and make it easier to switch providers. But it doesn't require the provider to be European or outside US jurisdiction.
DORA (Digital Operational Resilience Act) applies specifically to financial services. It requires firms to test their operational resilience, including cloud provider failures. It doesn't mandate sovereign cloud, but it creates incentives to diversify away from concentrated hyperscaler dependencies.
NIS2 (Network and Information Security Directive 2) applies to critical infrastructure. It requires security controls, incident reporting, and resilience measures. Again, it doesn't mandate sovereignty, but it creates pressure toward more resilient, less concentrated infrastructure.
The regulatory trend is clear: Europe wants to decrease dependency on US cloud providers, increase data control, and improve resilience. But no single regulation mandates true sovereignty. Instead, regulations create incentives and requirements that push organizations toward sovereign solutions.
Different countries are also creating national frameworks. Germany's "Cloud Security" initiative emphasizes European suppliers. France's "French Cloud" strategy prioritizes national champions. Poland is mandating public cloud services meet sovereignty criteria. The fragmentation at regulatory level mirrors the fragmentation at certification level.
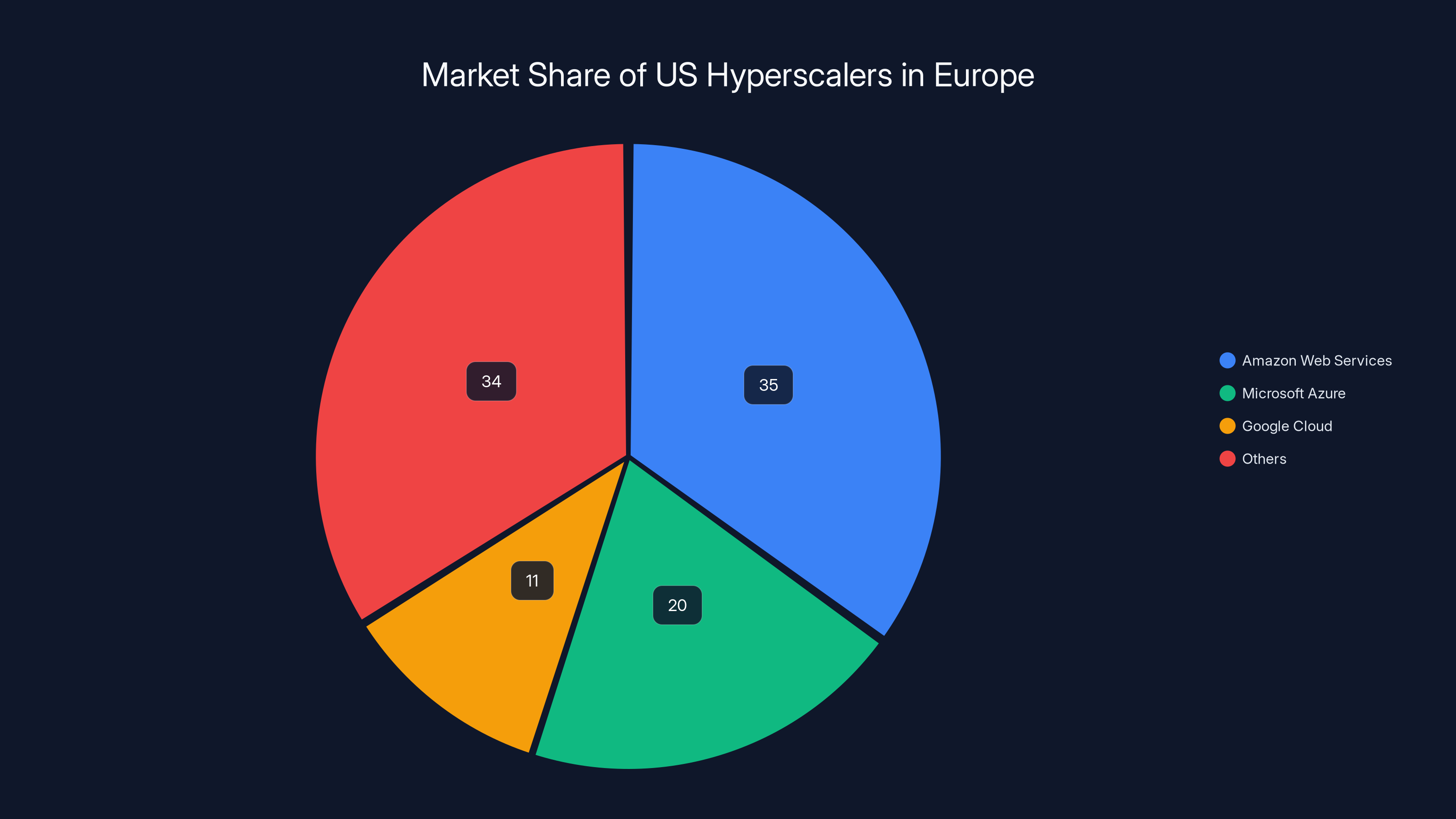
Amazon Web Services, Microsoft Azure, and Google Cloud collectively control over 66% of Europe's cloud market, highlighting significant market concentration. Estimated data.
The Interoperability Challenge
True sovereignty requires genuine interoperability. If you're locked into a single provider, even a European one, you're not really sovereign. You're just dependent on someone different.
Interoperability means several things. It means standardized APIs so you can write code that works across multiple clouds. It means standardized data formats so you can export and import data without vendor-specific conversions. It means standardized management interfaces so you can switch providers without complete re-architecture. Most importantly, it means reasonable switching costs so you're not locked in by expense.
Hyperscalers have no incentive to enable interoperability. They profit from lock-in. Proprietary APIs, vendor-specific tooling, and switching friction are features, not bugs, from their perspective. AWS deliberately makes it expensive to migrate to Azure. Google designs its services to work better together. This lock-in is profitable.
European alternatives need to compete on interoperability. Open standards, standard APIs, easy portability. But building genuinely interoperable clouds is hard. It requires accepting that you might lose customers if you make it easy for them to leave. It requires accepting lower margins than proprietary hyperscaler approaches.
Gaia-X is attempting to solve this through federation and standardization. But standards adoption is slow. Different European providers still use different APIs and approaches.
For organizations seeking sovereignty, interoperability is essential. Don't accept lock-in, even to a European provider. Demand standards, demand portability, demand the ability to switch. Otherwise, you're just trading one form of dependency for another.
The Cost Equation: Sovereignty vs. Efficiency
Here's the honest tradeoff: true sovereignty costs more.
Hyperscalers achieve low costs through massive scale, commodity hardware, and global optimization. A European alternative operating smaller scale pays more per unit. They can't achieve AWS pricing. They can't achieve Azure's feature breadth. If cost is your primary constraint, true sovereignty is hard to achieve.
But cost is decreasing as the European market grows. OVHcloud's prices are coming down. Gaia-X participants are improving efficiency. As demand for sovereignty increases, more providers will enter the market, and prices will decline through competition.
For many organizations, the tradeoff is acceptable. A healthcare provider storing patient data will pay a premium for genuine sovereignty and compliance assurance. A government handling classified data will accept higher costs for independence. A financial firm managing regulated data will pay more for control.
But for a startup using cloud for commodity compute, or a Saa S company where cost structure determines unit economics, true sovereignty might be prohibitively expensive.
The market is likely to stratify. Organizations with sensitive data and regulatory requirements will migrate to genuinely sovereign alternatives. Commodity workloads will remain with hyperscalers. Organizations in the middle will use hybrid approaches.
That stratification is actually healthy for the market. It prevents the absurdity of every organization demanding 100% sovereignty, which would be economically irrational. Instead, it should push toward a more honest market where different providers compete for different use cases.

Building a Balanced European Ecosystem
Europe has a real opportunity to build a more independent cloud ecosystem. Not one that completely displaces hyperscalers, but one that offers genuine alternatives for organizations that need or want them.
That requires several things. First, consistent standards. The fragmentation of C5, Sec Num Cloud, and national frameworks is inefficient. A unified European standard defining sovereignty would help. The EU should pursue that, even if it takes years.
Second, investment in European infrastructure. Gaia-X and similar initiatives need sustained funding and commitment. European cloud providers need capital to scale. This likely requires some public investment, not just private capital.
Third, interoperability focus. European alternatives should compete on standardization, not on features. That means adopting open standards, building APIs that work across providers, and enabling portability. It's counterintuitive, but interoperability is what differentiates from hyperscaler lock-in.
Fourth, strategic workload migration. Not all workloads need sovereign clouds. Critical infrastructure, government services, regulated industries—these should migrate. But commodity workloads can remain on hyperscalers. This is actually efficient.
Fifth, talent and expertise. Europe needs more cloud engineers, architects, and operations staff focused on European alternatives. That requires education, training, and career paths.
Sixth, regulatory clarity. Stop creating different frameworks in each country. Create unified European requirements, and then let market competition determine who meets them.
The good news is that momentum is building. The bad news is that inertia is enormous. Hyperscaler dominance won't disappear overnight. But genuine alternatives are emerging. The market is diversifying. It's happening slower than Europe would like, but it's happening.

Emerging Technologies Enabling Sovereignty
Several emerging technologies could enable better sovereignty solutions.
Confidential computing allows data to be encrypted even during processing. Homomorphic encryption theoretically allows computation on encrypted data without decryption. This means cloud providers could process data without actually seeing it. If these technologies mature and scale, they could enable sovereign clouds that are genuinely isolated from provider access.
Decentralized cloud and edge computing shift processing away from centralized data centers toward distributed, local infrastructure. This could reduce dependency on any single provider and enable more control. But decentralized cloud is immature and comes with its own challenges.
Blockchain and distributed ledger technologies could enable auditable, transparent cloud operations where all actions are recorded and verifiable. But blockchain brings its own performance and cost penalties.
Quantum-resistant encryption will become necessary as quantum computing threatens current encryption standards. This could force a re-evaluation of entire cloud infrastructure and favor providers implementing quantum-safe approaches early.
None of these are mature solutions today. But they're under active research and development. They could fundamentally change what's possible in sovereign cloud computing.
Real-World Case Studies: Who's Actually Moving?
Let's look at actual organizations making sovereignty decisions.
The German government mandated that federal agencies use only cloud services meeting C5 or higher certification. This pushed many agencies toward OVHcloud, regional providers, and hyperscalers offering certified German operations. It didn't eliminate hyperscaler use, but it created genuine pressure toward alternatives.
France's healthcare sector increasingly uses Sec Num Cloud certified providers specifically because they need sovereign clouds for patient data. This has accelerated OVHcloud and French regional provider adoption in healthcare.
The European Banking Authority recommended that financial institutions reduce dependency on US cloud providers. This has accelerated banks' dual-cloud strategies, with primary workloads on hyperscalers and sensitive data on European alternatives.
Large European tech companies like Spotify and Zalando have invested in European infrastructure partly for sovereignty, partly for cost optimization, partly for reducing dependency. They're not abandoning hyperscalers, but they're diversifying.
The pattern is consistent: organizations with genuine sovereignty requirements are moving. Organizations without such requirements are staying. The market is stratifying exactly as it should.
The Role of Automation and AI in Cloud Sovereignty
Automation platforms that help organizations manage multi-cloud environments are becoming increasingly important. Tools that enable easy data migration, that standardize operations across clouds, and that reduce switching costs all contribute to genuine interoperability and sovereignty.
As cloud complexity increases, organizations need platforms that can automate deployments across multiple providers, orchestrate workloads intelligently, and provide unified management. This is where solutions like Runable come into play. Platforms like Runable enable teams to automate workflows, generate documentation, create reports, and manage infrastructure across heterogeneous environments more efficiently.
Automation that reduces vendor lock-in is genuinely valuable for sovereignty. If your automation can work across multiple clouds, if your infrastructure-as-code works regardless of provider, if your CI/CD pipelines are cloud-agnostic, you've genuinely improved your ability to migrate and maintain independence.
Use Case: Automate multi-cloud deployments and infrastructure documentation to reduce vendor lock-in and improve sovereignty across your cloud estate.
Try Runable For Free
Future Predictions: Where Sovereign Cloud Is Heading
Based on current trends, here's what the next 5-10 years likely looks like.
Continued growth but gradual consolidation. The sovereign cloud market will grow explosively. But the number of viable providers will consolidate. Smaller European players will struggle. The viable European alternatives will likely be 3-5 major players plus regional specialists.
Hyperscaler adaptation. AWS, Azure, and Google won't lose dominance. But they'll adapt. They'll invest more in European sovereignty features, stricter data residency, better legal separation. They'll essentially compete better on the sovereignty dimension.
Regulatory clarity. The EU will eventually converge on unified sovereignty standards. Different countries will maintain some variation, but the fragmentation will decrease. This will make it easier to comply and easier to compare offerings.
Hybrid becoming the norm. Most large organizations will use multiple clouds. Hyperscalers for commodity workloads, European alternatives for sensitive data, potentially specialized providers for niche requirements. This hybrid approach is already common and will become dominant.
Interoperability maturation. Standards will improve. Portability will become easier. Cloud-agnostic tooling will mature. This will decrease switching costs and enable more genuine competition.
New regulatory waves. As AI becomes more prevalent, new sovereignty requirements will emerge around AI model governance, training data provenance, and algorithmic transparency. These will create new opportunities for sovereign cloud differentiation.
The long-term picture is a market that's somewhat less concentrated, more diverse, and where genuine sovereignty is more achievable. It won't be perfect. It won't completely displace hyperscalers. But it will be materially different from today.
Key Takeaways and Actionable Next Steps
If you're evaluating sovereign cloud options, here's what you should do.
First, assess your actual sovereignty requirements. Not every organization needs true sovereignty. If you're handling commodity data, you might not. If you're government or regulated finance, you definitely do. Be honest about your requirements. Don't pay for sovereignty you don't need.
Second, evaluate on all dimensions. Don't just look at data residency. Look at legal entity, encryption, interoperability, audit rights, supply chain, and regulatory certifications. True sovereignty requires excellence across all dimensions.
Third, do due diligence yourself. Don't trust vendor marketing. Run tests. Get legal review. Export trial data. Try migrations. Verify claims independently.
Fourth, plan for hybrid. Unless you have extreme requirements, plan to use multiple cloud providers. This reduces dependency, improves resilience, and gives you optionality.
Fifth, invest in tools and skills. Whatever clouds you choose, invest in tooling and team expertise that work across multiple providers. This is what actually enables sovereignty.
Sixth, monitor regulation. The regulatory landscape is evolving rapidly. Stay current. Understand your jurisdictional requirements. Plan for change.
Seventh, build interoperability into architecture. Don't build deeply integrated systems tied to specific cloud providers. Use standards. Design for portability. This is how you actually maintain freedom.
Sovereign cloud is real and important. But it's not marketing. It requires work, discipline, and honest assessment. Do that work, and you can achieve genuine control. Skip it, and you'll just have the illusion of sovereignty.
FAQ
What does "cloud sovereignty" actually mean?
Cloud sovereignty refers to the complete control and legal authority an organization has over its data and infrastructure in cloud environments, including where data physically resides, who has jurisdictional authority over it, and freedom from vendor lock-in. It encompasses data residency (physical location), legal jurisdiction (which laws apply), operational independence (who controls the infrastructure), and interoperability (ability to migrate between providers). True sovereignty requires alignment across all these dimensions, not just one.
How does the CLOUD Act affect data stored in European cloud data centers?
The CLOUD Act permits US courts to compel US-headquartered companies to disclose data stored anywhere in the world, regardless of physical location or local laws. This means data physically stored in Frankfurt or Amsterdam can still be accessed by US authorities if the cloud provider is a US company. The Act essentially extends US jurisdiction globally for US-based companies, which is why legal entity structure matters more than data residency for true sovereignty.
Why do most European organizations still use US cloud providers despite sovereignty concerns?
US hyperscalers like AWS, Microsoft Azure, and Google Cloud dominate because they offer unmatched scale, feature breadth, global infrastructure, and competitive pricing. Switching to European alternatives requires significant investment in migration, potentially losing advanced services, accepting higher costs, and retraining teams. These switching costs create lock-in that persists even when organizations recognize sovereignty risks. Additionally, many organizations handle non-sensitive workloads where sovereignty isn't critical, making the tradeoff irrational.
What's the difference between data residency and data sovereignty?
Data residency answers the question "where is my data physically stored?" Data sovereignty answers "who has control over my data and who can access it?" You can have perfect data residency without sovereignty (data in Europe but still subject to US jurisdiction) or partial sovereignty without perfect residency. True sovereignty requires both physical residency aligned with your jurisdiction plus legal and operational independence from foreign jurisdictional claims.
Are European cloud alternatives like OVHcloud truly sovereign?
OVHcloud is more genuinely sovereign than US hyperscaler subsidiaries because it's a European company not subject to the CLOUD Act. However, sovereignty depends on your specific requirements. OVHcloud offers better legal independence but fewer features, higher costs, and smaller scale than hyperscalers. For government or highly regulated workloads, OVHcloud's independence is valuable. For most organizations, the feature and cost tradeoffs might not be worth it. Sovereignty is a spectrum, not binary.
How should organizations approach multi-cloud strategies for sovereignty?
The most practical approach is strategic workload segmentation: use hyperscaler clouds for commodity, non-sensitive workloads, and European sovereign alternatives for sensitive, regulated, or mission-critical data. This balances sovereignty requirements with cost and capability constraints. Invest in cloud-agnostic tooling, standardized APIs, and infrastructure-as-code that work across multiple providers. This reduces lock-in and gives you the flexibility to migrate or diversify if requirements change.
What certifications should I look for in a sovereign cloud provider?
C5 (German Federal Office for Information Security) requires security controls and data residency in Germany but doesn't guarantee jurisdictional independence. Sec Num Cloud (French) is stricter, requiring EU majority ownership and data centers in France, making it more genuinely sovereign for French/European operations. Other relevant frameworks include DORA for financial services and NIS2 for critical infrastructure. However, certifications guarantee security and compliance, not absolute independence from US jurisdiction if the provider is US-headquartered.
What role will emerging technologies play in sovereign cloud?
Confidential computing, homomorphic encryption, and quantum-resistant encryption could enable cloud providers to process data without accessing it, fundamentally changing sovereignty dynamics. Decentralized cloud and edge computing could reduce dependency on centralized providers. These technologies are under active development but not yet mature at production scale. In the next 5-10 years, they could make genuine sovereignty more feasible and cost-effective, but they're not reliable solutions today.
How is the European Union addressing the sovereign cloud fragmentation problem?
The EU is attempting to create unified standards through initiatives like DGIT (trying to define sovereignty on a requirement scale) and supporting Gaia-X (a federation framework for European cloud providers). However, fragmentation persists because different member states have different priorities and regulatory requirements. Germany's C5, France's Sec Num Cloud, and other national frameworks don't align. A truly unified European standard would help, but achieving consensus among 27 member states with different interests is slow.
What should organizations do right now to improve their cloud sovereignty posture?
Start with honest assessment of what data actually needs sovereign protection (customer data? employee data? proprietary algorithms?). Evaluate current cloud contracts for data residency, encryption key ownership, and audit rights. Conduct due diligence on any claimed "sovereign" solution—test interoperability, verify legal structure, and understand actual independence. Plan for hybrid approaches rather than demanding 100% sovereignty everywhere. Invest in cloud-agnostic tooling to reduce lock-in. Stay current on regulatory changes. Sovereignty requires ongoing work, not a one-time implementation.
Related Articles
- Geopatriation & Cloud Sovereignty: What 2026 Means for Enterprise Data [2026]
- Data Sovereignty for Business Leaders [2025]
- ChatGPT's Age Detection Bug: Why Adults Are Stuck in Teen Mode [2025]
- Data Sovereignty for SMEs: Control, Compliance, and Resilience [2025]
- The Complete Guide to Breaking Free From Big Tech in 2026
![Sovereign Cloud & Data Control: Who Really Owns Your Data [2025]](https://tryrunable.com/blog/sovereign-cloud-data-control-who-really-owns-your-data-2025/image-1-1769942151393.jpg)



