Introduction: Why SMEs Can't Ignore Data Sovereignty Anymore
Your data's sitting somewhere right now. On a server in Virginia. Replicated in Ireland. Backed up in Frankfurt. But here's the thing: you probably don't know exactly where it is, who can access it, or whether it's actually legal to have it there.
For small and medium-sized enterprises, this ambiguity has shifted from "nice to know" to "critical business risk."
Around 18% of UK SMEs export goods or services, and many more sit inside global supply chains where data flows across borders every single day. That constant movement makes data sovereignty—the obligation to store and process data according to the jurisdictional rules of where it resides—an unavoidable reality. You can't ignore it anymore.
The stakes have gotten real. In 2024 and 2025, regulatory enforcement escalated dramatically. Major fines hit Uber and TikTok for cross-border data transfer violations. The UK Information Commissioner's Office tightened enforcement on GDPR violations. The EU's Data Governance Act introduced fresh restrictions. And regulators aren't slowing down—they're accelerating.
For SMEs, compliance failures don't just mean fines. They mean lost contracts with larger partners who now demand sovereignty clauses as a prerequisite. They mean supply chain disruptions when you can't prove your data meets jurisdictional requirements. They mean reputational damage in industries where trust is everything.
But sovereignty isn't just a compliance box anymore. It's also become a resilience conversation. Remember the AWS outage in December 2024? It disrupted UK services, knocked out HMRC systems, and impacted major banks. The incident underscored a hard truth: when your data sits in US infrastructure, US infrastructure failures become your problem.
The UK Competition and Markets Authority's recent market investigation into cloud services highlighted another sovereignty pressure point: egress fees. These hidden charges can lock you into providers even when you need to migrate data urgently to meet new regulations or escape a failing relationship. When you need location control fast, those fees become leverage your provider holds over you.
Here's what we're seeing: SMEs that don't address sovereignty now are building their entire infrastructure on shaky ground. Larger partners apply their own sovereignty clauses, making compliance a prerequisite for staying in supply chains. Regulatory fines are climbing. Exit strategies from major cloud providers remain murky. And resilience increasingly depends on controlling where your data lives.
The good news? You don't need enterprise budgets to implement sovereignty properly. You need clarity, the right provider partnerships, and a framework for thinking about data location as part of your infrastructure strategy, not as an afterthought.
This guide walks you through that framework.
TL; DR
- Data sovereignty is now a business requirement: Regulatory enforcement in 2024-2025 escalated dramatically, with major fines for cross-border transfer violations and stricter enforcement from GDPR, CCPA, and local regulators.
- Compliance is a supply chain prerequisite: Larger partners now demand sovereignty clauses in contracts, meaning SMEs without location control lose access to opportunities.
- Resilience depends on data location control: Infrastructure failures (like the December 2024 AWS outage) and egress fees lock SMEs into providers, making location control essential for business continuity.
- SMEs lack in-house expertise: Many smaller firms can't interpret complex regulations or manage cross-border obligations without experienced provider partners.
- Sovereignty must be built into infrastructure from the start: Adding data residency controls later creates complexity, cost, and risk. Getting it right upfront means choosing providers transparent about data location, implementing access controls, and planning exit strategies before you need them.

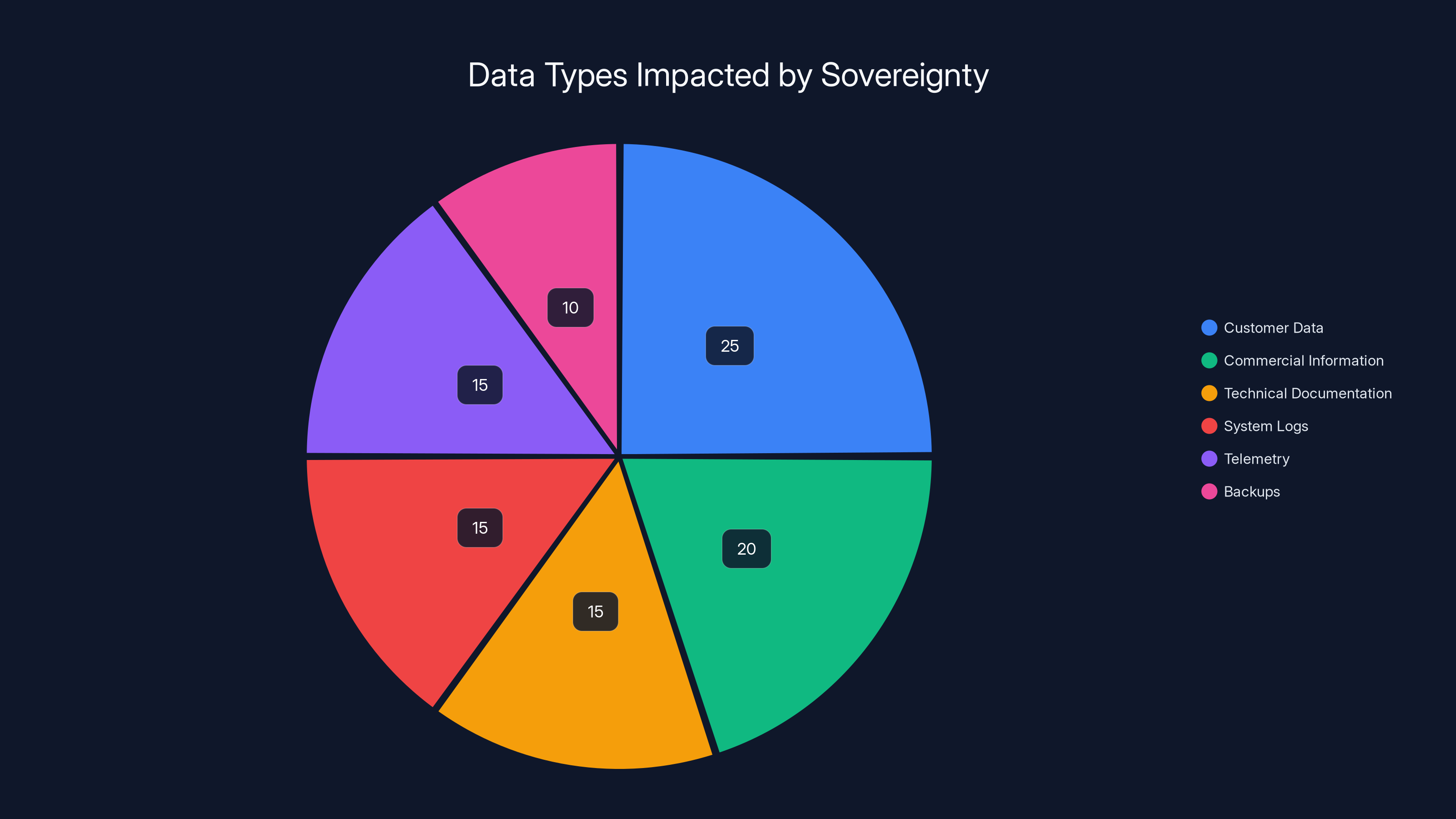
Estimated data shows customer data is most impacted by sovereignty laws, followed by commercial information and other technical data types.
Understanding Data Sovereignty: Beyond Compliance
Data sovereignty sounds like a dry regulatory term. In reality, it's become central to how modern SMEs operate.
At its core, sovereignty means this: data must be stored and processed according to the laws of the jurisdictions where it resides or where the data subject lives. If you hold UK customer data, UK law applies. If you expand into the EU, GDPR applies. If you have US customers, you're now touching the US-UK Data Bridge framework.
But sovereignty isn't just about personal data anymore. That's the bit that catches SMEs off guard.
Your commercial information, technical documentation, system logs, telemetry, and backups all trigger the same questions: Where does it live? Who can access it? Which laws govern it? A single backup stored in the wrong jurisdiction can create compliance exposure. An integration that pipes logs to a US analytics provider can trigger obligations you didn't expect.
When services are stitched together across multiple vendors—and they always are—each integration introduces another decision point and potentially another jurisdiction. You've got Stripe processing payments in multiple countries. You've got Slack storing conversations across regions. You've got AWS S3 with replicas in three zones. Each layer introduces complexity.
That complexity explains why sovereignty has become urgent. And it reveals something crucial: sovereignty is not just about regulation. It's also about business resilience, data control, and the ability to exit relationships quickly when requirements shift.
The Regulatory Landscape in 2025
Regulators aren't getting gentler. They're getting more specific.
The General Data Protection Regulation set the foundation in 2018. It established the right to know where your data lives and the obligation to protect it according to local law. But GDPR enforcement has evolved. Fines have climbed from tens of thousands to hundreds of millions. The maximum penalty is €20 million or 4% of annual turnover—whichever is higher.
In the US, the Children's Online Privacy Protection Act and state-level laws like California's Consumer Privacy Act created jurisdiction-specific obligations. The fragmentation means you can't just comply once and move on. You need to comply to every jurisdiction your customers, employees, or partners inhabit.
UK regulators, particularly the Information Commissioner's Office, have intensified enforcement post-Brexit. The UK Data Protection Act 2018 mirrors GDPR principles but with UK-specific obligations. Recent enforcement actions show the ICO is willing to fine even smaller organizations for data location breaches.
The EU's Data Governance Act, effective since 2024, introduced new requirements around data altruism, access requests, and cross-border sharing. It's creating new compliance layers for SMEs doing business in Europe.
And it's not just the big regulations. Sector-specific rules are proliferating. Healthcare has HIPAA in the US and equivalents in every other jurisdiction. Financial services have MiFID II in Europe. Data residency has become a checkbox in every contract.
For SMEs, the practical reality is this: compliance is no longer optional. It's a supply chain requirement. Larger partners now insist on it. And regulators are actively enforcing it.
Sovereignty as Resilience
Compliance gets the headlines, but resilience is where sovereignty delivers real value.
The AWS outage in December 2024 is the clearest example. When US-East-1 went down, it didn't just affect customers in the US. It cascaded through UK services because so much infrastructure depends on that region. HMRC couldn't process some transactions. Major UK banks experienced disruptions. The incident revealed a hard truth: concentration risk is real.
When your data lives in one region controlled by one provider, you inherit that provider's failure modes. A software bug. A configuration error. A natural disaster. A geopolitical event. Any of those can take your business offline if you haven't planned for it.
Data sovereignty, implemented correctly, addresses this. By distributing data across regions and jurisdictions—and by maintaining control over which copies live where—you reduce single points of failure. If AWS-East-1 fails, your EU copy still serves customers. If a US provider violates your data location requirements, you can migrate to a regional provider without losing access to backups.
This isn't theoretical. The recent UK CMA's market investigation into cloud services highlighted that SMEs are actively looking to switch providers but can't because of egress fees. One provider's outage or policy change locks you in. Sovereignty thinking—treating data location as part of your exit strategy—changes that dynamic.
Resilience also means faster recovery. If you know exactly where your backups live, recovery time is predictable. If data is spread across unknown jurisdictions, recovery becomes a negotiation with your provider. You lose optionality. You lose speed.
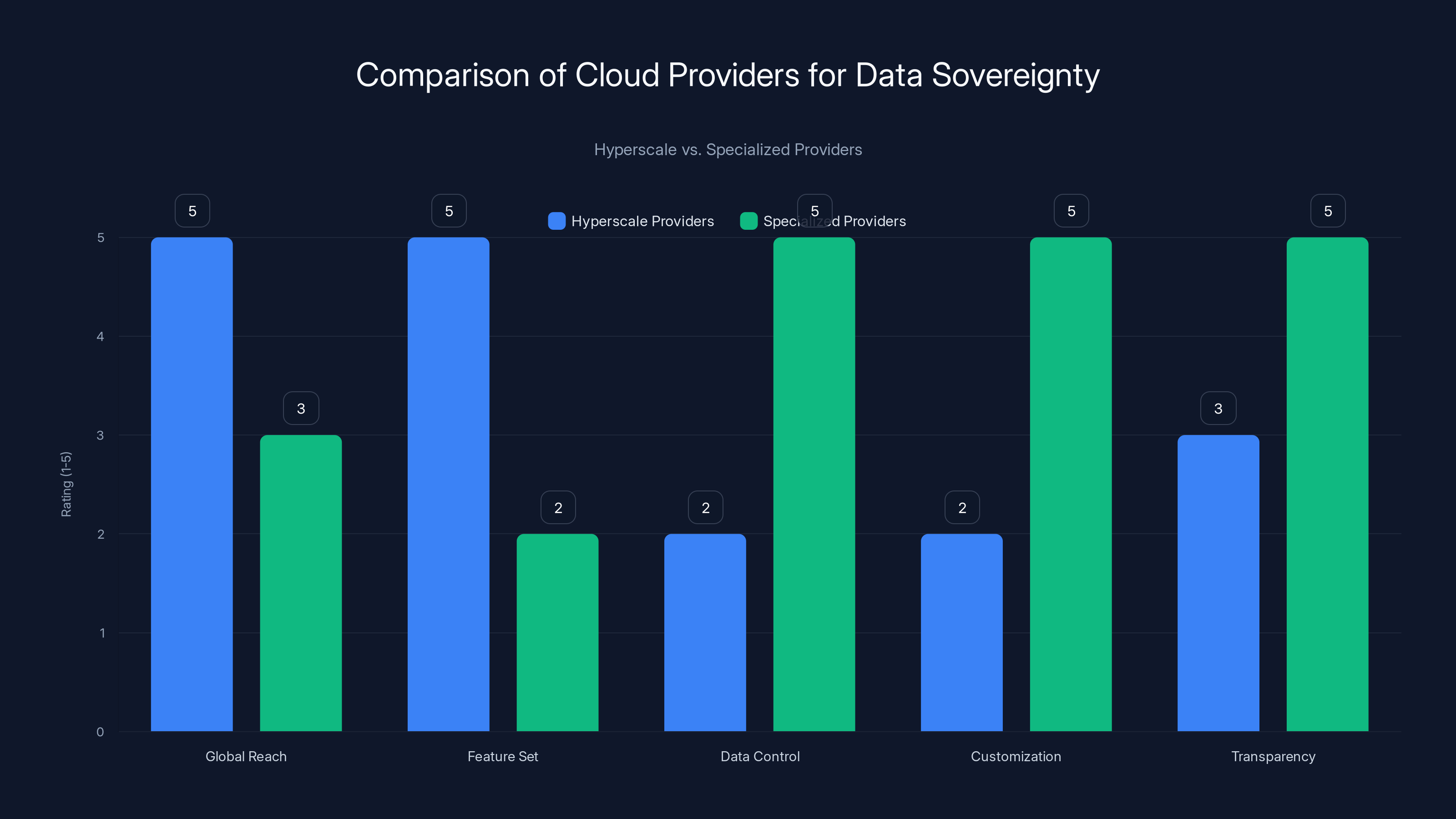
Hyperscale providers excel in global reach and feature set, while specialized providers offer superior data control, customization, and transparency. Estimated data based on typical provider characteristics.
The SME Challenge: Where Complexity Meets Capacity
Larger enterprises have compliance teams, data governance frameworks, and ongoing regulatory tracking. SMEs have spreadsheets and hope.
The gap between what regulation demands and what SMEs can actually implement is where real risk lives.
Cross-Border Complexity
Start with the basics. Your business probably operates in more than one jurisdiction. You've got UK customers. You're expanding to Europe. You're using US cloud providers. You've got employees working remotely from multiple countries.
Now add the complication: regulations overlap and contradict.
GDPR says data must leave the EU only under specific mechanisms. UK law mirrors GDPR but with UK-specific twists. US law doesn't restrict where data lives, but it gives US authorities broad access to data stored on US soil. Canadian law restricts data movement to certain countries. Australian law has its own requirements.
When you operate in all these jurisdictions, you're not complying with one rule. You're complying with the intersection of multiple rules, and that intersection changes every time a new regulation lands or a court issues a judgment.
For SMEs without legal teams, this becomes a guessing game. You make reasonable assumptions about where data should live. You choose a provider with a decent privacy policy. You hope that covers it. It often doesn't.
The practical impact: SMEs are discovering compliance failures months or years after they've happened. A supplier points out that your data residency violates their contract. A regulator sends a letter. A customer audit reveals data in the wrong jurisdiction. By that point, fixing it is expensive and disruptive.
Shadow IT and Unmanaged SaaS
Here's something that surprises SME leaders: your employees are probably moving data into unapproved jurisdictions right now, and you don't know it.
Shadow IT is the phenomenon where teams adopt tools without IT approval. A designer uses a collaboration tool that lives in the US. A salesperson integrates a CRM that stores data in Singapore. An accountant exports financial data to a spreadsheet stored in a cloud service located outside your approved jurisdictions.
Each of these decisions makes sense at the individual level. The tool is cheaper. It works better. It's faster to implement than going through official procurement. But collectively, they create compliance chaos.
For SMEs with limited IT oversight, shadow IT is rampant. You might have 20 official approved tools and 100 unapproved ones quietly moving data around. The moment you start doing a compliance audit, you'll find integrations and dependencies that violate your own data residency requirements.
The problem compounds when teams don't document where data is going. A Zapier integration pipes data from one tool to another. A webhook sends logs somewhere. A backup runs to a cloud provider that was never explicitly configured. Small decisions accumulate into unmanaged risk.
Migrating away from shadow IT requires setting governance frameworks in place. It means documenting integrations. It means making approved alternatives accessible so teams stop reaching for unapproved tools. But until you do, you're running blind on compliance.
Vendor Lock-In and Egress Friction
Once your data is in one place, getting it out becomes harder than you'd expect.
Major cloud providers don't explicitly charge for data egress in most cases, but the friction is real. Your data is stored in a proprietary format. Moving it requires transformation. Building export pipelines takes engineering time. Downtime during migration is a risk.
Moreover, some providers do charge for egress, and those charges can be substantial. When you're moving terabytes of data out, you're looking at bills in the thousands. That friction locks you in. You tolerate price increases or policy changes because the cost of leaving is higher than the cost of staying.
For SMEs managing data sovereignty, this lock-in is particularly problematic. If regulations shift and you need to move data to a different region or provider, you need to be able to do it quickly and cheaply. But the vendor relationship was designed to make that difficult.
The UK CMA's investigation into cloud services specifically highlighted egress fees and switching costs as barriers to competition and consumer choice. The finding: SMEs want to switch providers more often than they can afford to.
Data sovereignty thinking means addressing lock-in upfront. It means choosing providers who make data export easy. It means avoiding proprietary formats and tools that require lengthy migrations. It means planning exit strategies before you need them.
In-House Expertise Gaps
Compliance requires understanding regulations, infrastructure, and risk. SMEs typically have one person handling two of those three—and they're usually stretched thin.
A typical SME might have a compliance person who understands regulations but not infrastructure. An IT person who understands infrastructure but not the nuances of cross-border data obligations. An operations person trying to hold everything together without expertise in any of it.
The result: decisions get made without complete information. Data gets stored in convenient places rather than compliant places. Risks get accepted because nobody's sure what the actual risks are.
This explains why SMEs increasingly need to outsource sovereignty expertise. You can't hire a full compliance team. You can partner with providers who have that expertise built in.
Scoping the Data Sovereignty Challenge
Before you can solve data sovereignty, you need to understand what you're actually solving for.
What Data Actually Needs Sovereignty Control
Most SMEs think sovereignty is about personal data. That's the obvious category. Customer names, emails, home addresses—clearly sensitive, clearly regulated.
But sovereignty applies far more broadly.
Personal data: Customer names, email addresses, phone numbers, postal addresses, payment information, browsing behavior, location data, biometric data. Regulated under GDPR, CCPA, and equivalents worldwide.
Commercial information: Client lists, pricing, contracts, negotiation notes, financial records, business strategies. Not regulated like personal data, but often required to stay in specific jurisdictions by client contracts or industry standards.
Technical data: System logs, API calls, performance metrics, security logs, error traces. Often treated as non-sensitive, but increasingly regulated and required for compliance audits.
Backup and archive data: Old copies of databases, replicated data, disaster recovery copies. Often forgotten in sovereignty planning but just as regulated as live data.
Third-party data: Data from partners, suppliers, customers of your customers. You often inherit sovereignty obligations without realizing it.
When you catalogue what needs sovereignty control, the scope expands rapidly. You're not just managing customer data. You're managing logs, backups, archives, integrations, and inherited obligations from partners.
Overlapping Regulations and Conflicting Rules
Compliance becomes a Venn diagram when you operate across jurisdictions.
Imagine an SME with customers in the UK, Germany, and the US, plus employees in Canada. Here's what you're actually complying with:
- UK Data Protection Act 2018: UK customer data must be protected according to UK law. Personal data can only leave the UK under specific transfer mechanisms.
- GDPR: If you have any EU customers or employees, GDPR applies. Data residency is stricter than UK law alone.
- German data protection law: Additional requirements for German customers, including restrictions on data transfers outside Germany.
- CCPA and state privacy laws: If you have US customers, California privacy law and potentially laws from other states apply.
- PIPEDA: Canadian privacy law applies to Canadian employees and customers.
Now layer on industry-specific regulations. If you're in healthcare, add HIPAA. In finance, add MiFID II or equivalent. In payments, add PCI DSS.
The intersection of all these rules is what you actually have to comply with. And it's complex.
Most SMEs handle this through trial and error. You pick the strictest rule and apply it to everything. That works as a baseline but often creates unnecessary friction. You might be restricting data movement more than required, which slows innovation or increases costs.
The right approach is to understand which rules apply to which data, then apply proportionate controls. Personal data from EU customers gets the strictest handling. Commercial information might have different requirements. Logs might have looser requirements still.
But getting that categorization right requires expertise most SMEs don't have in-house.
Exit Strategies and Switching Costs
Data sovereignty isn't just about where data lives today. It's about your ability to move it tomorrow.
Regulations change. Providers change. Your business requirements change. You need the optionality to switch providers, migrate to different regions, or adapt to new compliance requirements without getting locked in.
For many SMEs, that optionality doesn't exist. Your data is stored in a proprietary format. Your integrations are deeply tied to one provider. Moving to a different provider would take months and significant engineering effort.
When you can't exit easily, you lose negotiating power. Your provider knows it. Prices go up. Terms get worse. You tolerate it because the alternative is more expensive.
Data sovereignty thinking includes exit planning. It means:
- Choosing portable data formats: Store data in standard formats you can export easily, not proprietary ones.
- Documenting integrations: Know exactly how data flows between systems so you can rebuild those flows with a different provider.
- Planning migration runbooks: Before you need to migrate, have a documented process for doing it quickly.
- Testing exit scenarios: Periodically practice moving data or replicating your infrastructure on a different provider. You'll discover dependencies and complications before they become emergencies.
- Negotiating contracts: Ensure your agreements include reasonable notice periods, data export provisions, and transition assistance.
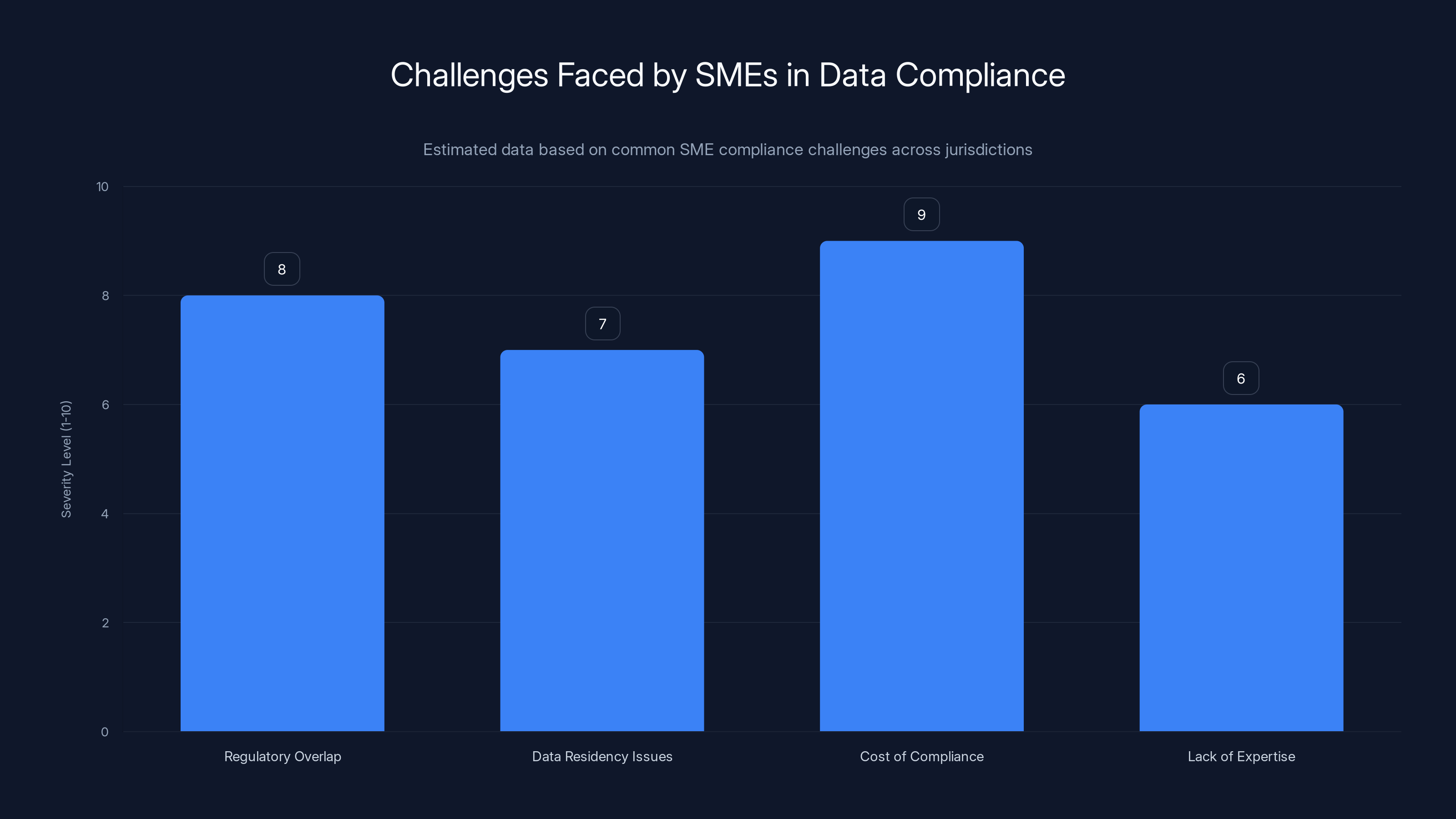
SMEs face significant challenges in data compliance, with the cost of compliance and regulatory overlap being the most severe. Estimated data based on typical SME experiences.
Building Sovereignty Into Infrastructure: Strategic Choices
Data sovereignty isn't something you bolt on after you've built your infrastructure. It's a foundational choice that shapes every decision you make about where data lives, who accesses it, and how you can move it.
Provider Selection: Hyperscale vs. Specialized
The biggest decision is choosing between hyperscale cloud providers and specialized, regional providers.
Hyperscale providers like AWS, Microsoft Azure, and Google Cloud offer global reach, economies of scale, and broad feature sets. They're excellent for many workloads. But they're optimized for scale and standardization, not for the customization and location control that sovereignty requires.
Hyperscale providers offer region selection, so you can run workloads in EU regions or UK regions. That addresses the basic requirement. But they don't give you granular control over where every copy of your data lives. Backups might go to a default location you don't control. Replicas might spread across regions automatically. Audit logs might flow to US servers.
For SMEs needing strict sovereignty control, that lack of granularity is problematic.
Specialized and regional providers offer something different. They're often built specifically for jurisdictions with strict data requirements. They offer location transparency, customer-managed encryption, and options for in-country data handling. They're smaller, less feature-rich, but more flexible.
Think of providers like Exoscale in Europe, Canopy in Canada, or AWS German Sovereign Cloud. These providers prioritize data sovereignty. They're transparent about where data lives. They don't move it without explicit permission.
The trade-off is predictable: specialized providers are more expensive and have fewer integrations. You give up some of the convenience of hyperscale providers for more control.
For SMEs with strict sovereignty requirements—working in regulated industries, serving EU customers, or facing strict data residency contracts—specialized providers often make sense. For SMEs with more flexibility, hyperscale providers with careful region selection can work.
The right choice depends on your specific requirements. Start by asking: Do I need to guarantee data location? Can I tolerate default behavior, or do I need explicit control? What's the cost of getting sovereignty wrong?
If the cost is high, specialize. If the cost is manageable, hyperscale often offers better value.
Managed Service Providers: Building Expertise Into Your Team
Understanding sovereignty is one thing. Implementing it across your infrastructure is another.
Many SMEs partner with Managed Service Providers (MSPs) who specialize in compliance and data governance. These are firms with expertise in data location, regulatory requirements, and infrastructure design.
A good MSP doesn't just manage your servers. They understand the regulations you're subject to. They help you classify data. They design your infrastructure to meet sovereignty requirements. They monitor compliance and alert you when configurations drift.
The MSP model works well for SMEs because it outsources expertise you can't afford to hire full-time. Instead of hiring a full compliance and infrastructure team, you contract with a firm that has that expertise across many customers.
When evaluating MSPs, look for:
- Regulatory expertise: Do they understand the specific regulations you're subject to?
- Location transparency: Can they clearly articulate where your data lives and how it's protected?
- Audit trails: Do they provide monitoring and logging so you can demonstrate compliance to regulators?
- Exit planning: Do they help you plan migrations and maintain data portability?
- Ongoing support: Do they track regulatory changes and help you adapt as requirements shift?
The relationship with an MSP should feel like they're an extension of your team, not an external vendor. You should be able to ask questions and get clear answers. If an MSP can't articulate where your data lives or why it's there, that's a red flag.
Data Classification: Starting Point for Everything
Before you can build proper sovereignty controls, you need to know what you're protecting.
Data classification is the practice of categorizing data based on sensitivity, regulatory requirements, and business impact. It's simple but essential.
Basic classification might look like this:
Tier 1: Highly sensitive – Personal data, payment information, health records. Strict location requirements. Access limited to authorized personnel. Encryption required.
Tier 2: Business sensitive – Commercial information, client lists, financial records. Location requirements based on contracts. Access limited to relevant teams. Encryption recommended.
Tier 3: Internal – System logs, internal documentation, non-sensitive communications. Minimal location restrictions. Standard access controls. Encryption optional.
Tier 4: Public – Marketing materials, public documentation, information meant for customers. No location restrictions. No special access controls needed.
Once you've classified your data, you can apply proportionate controls. Tier 1 data gets strict handling. Tier 4 data doesn't need sovereignty constraints.
This classification exercise also reveals something important: you probably don't need to restrict the location of all your data. You might be over-controlling. You might be moving less data across borders than you think. You might discover that only 10% of your data has strict location requirements, which simplifies everything.
Access Control: Keeping Data Where It Should Be
Data location is only half the sovereignty equation. Access control is the other half.
Even if your data lives in the right jurisdiction, it doesn't matter if unauthorized people can access it. If a US employee can download UK customer data to their laptop, the UK location requirement doesn't protect anyone.
Proper access control means:
- Multi-factor authentication (MFA): Every access requires something you know (password) and something you have (phone, hardware key). This prevents unauthorized logins.
- Least privilege: Users get access to only the data they need to do their jobs. A support person doesn't access financial records. An engineer doesn't access customer payment information.
- Location restrictions: In some cases, you can restrict access based on geographic location. A user connecting from China might be blocked from accessing UK customer data.
- Audit trails: Every access is logged. You can see who accessed what, when, and from where.
- Regular reviews: Periodically audit who has access to what. Remove access for people who've changed roles.
Access control is particularly important when you have employees or contractors in multiple jurisdictions. A contractor in the US shouldn't have unrestricted access to EU customer data, even if the data is stored in an EU region.
Implementing robust access control requires tools. Most modern platforms support MFA, audit logging, and role-based access. Using these features is non-negotiable for sovereignty.

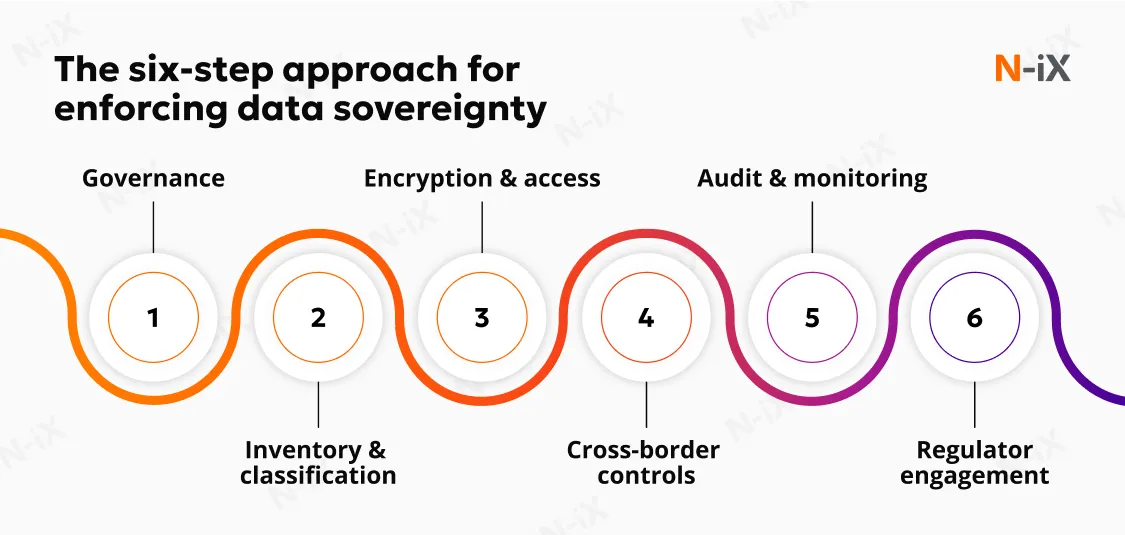
Implementing Sovereignty Controls: Step-by-Step
Implementing data sovereignty isn't a one-time project. It's an ongoing practice. Here's how to approach it systematically.
Step 1: Audit Your Current State
You can't fix what you don't understand.
Start by cataloging where your data actually lives right now. For each application and service:
- Document the primary location: Where is the main database or service hosted?
- Track replicas and copies: Where are backup copies, read replicas, or cached data stored?
- Map integrations: What systems does data flow to or from? Where do those systems live?
- Identify unknowns: Where are you uncertain about data location? This is common with SaaS tools where the provider controls location.
Create a spreadsheet with columns for application, data type, primary location, replicas, integrations, and risk level. Be honest about what you don't know. Many SMEs discover they have significant data in unexpected jurisdictions.
This audit often reveals that your actual data location doesn't match your assumptions. You thought everything was in the UK. But backups go to the US. Logs flow to a US analytics service. Integration middleware runs in Canada. Once you see this clearly, you can address it.
Step 2: Classify Your Data
Not all data needs the same level of sovereignty control.
Divide your data into tiers based on regulatory requirements and business sensitivity. Ask for each data type:
- What regulations apply to this data?
- What contracts require specific location handling?
- What's the business impact if this data is in the wrong jurisdiction?
Based on those answers, assign a tier. Tier 1 (strictly regulated) might include customer personal data. Tier 2 (business sensitive) might include commercial information. Tier 3 (internal) might include system logs.
Once classified, you know exactly what needs location control and what doesn't. This prevents you from over-protecting less sensitive data and under-protecting important data.
Step 3: Define Your Sovereignty Requirements
Different regulations and contracts require different approaches.
For each tier of data, define:
- Primary location: Where must this data live?
- Replica locations: Where are backups and copies allowed?
- Access locations: From which locations can this data be accessed?
- Third-party processors: Which vendors can touch this data?
- Retention period: How long must this data be kept?
These requirements should come from regulations and contracts. GDPR says EU personal data must stay in the EU unless specific transfer mechanisms are in place. A client contract might say their data must stay in the UK. Your internal policy might say commercial data can replicate to Canada but not to the US.
Document these requirements explicitly. Share them with your team. Use them as criteria for vendor selection and infrastructure decisions.
Step 4: Update Your Infrastructure
Once you know what's required, update your infrastructure to meet those requirements.
For data that needs location control:
- Choose the right provider: Select a provider that offers transparent location control in the jurisdictions you need.
- Configure data location: Explicitly set where primary copies, replicas, and backups live. Don't rely on defaults.
- Implement access controls: Use MFA, least-privilege access, and audit logging to control who can access data.
- Set up monitoring: Create alerts if data moves to unexpected locations or if access patterns change.
- Test recovery: Ensure that backup and recovery processes keep data in approved locations.
This might mean moving to a different provider, reconfiguring existing services, or choosing not to use certain features that move data outside approved locations.
Step 5: Document Everything
When regulators ask where your data lives, documentation is your proof.
Create documentation that shows:
- Data flow diagrams: Visual representation of where data goes and how it flows between systems.
- Location inventory: For each application and data type, where it's stored and why.
- Access controls: Who can access what, how access is managed, and audit trails.
- Incident procedures: What happens if data moves to an unauthorized location? How do you respond?
- Vendor agreements: Contracts with providers that explicitly address data location.
- Audit results: Records of audits or assessments confirming compliance.
This documentation serves multiple purposes. It helps you understand your own infrastructure. It helps you onboard new team members. It demonstrates compliance to regulators. It's essential.
Step 6: Monitor and Maintain
Sovereignty isn't a one-time setup. It requires ongoing maintenance.
Set up monitoring to:
- Alert on unauthorized data movement: If data moves to an unexpected location, you need to know immediately.
- Track access patterns: Are people accessing data from unexpected locations? Is access volume increasing abnormally?
- Monitor regulatory changes: Subscribe to regulatory updates for jurisdictions where you operate. When rules change, update your controls.
- Review integrations: Periodically audit integrations and SaaS connections. Are they still approved? Do they still meet sovereignty requirements?
- Test recovery: Regularly practice backup and recovery to ensure failover keeps data in approved locations.
Monitoring is often overlooked but essential. A configuration that was correct today might drift tomorrow. New integrations might introduce unauthorized data movement. Vendor policies might change.

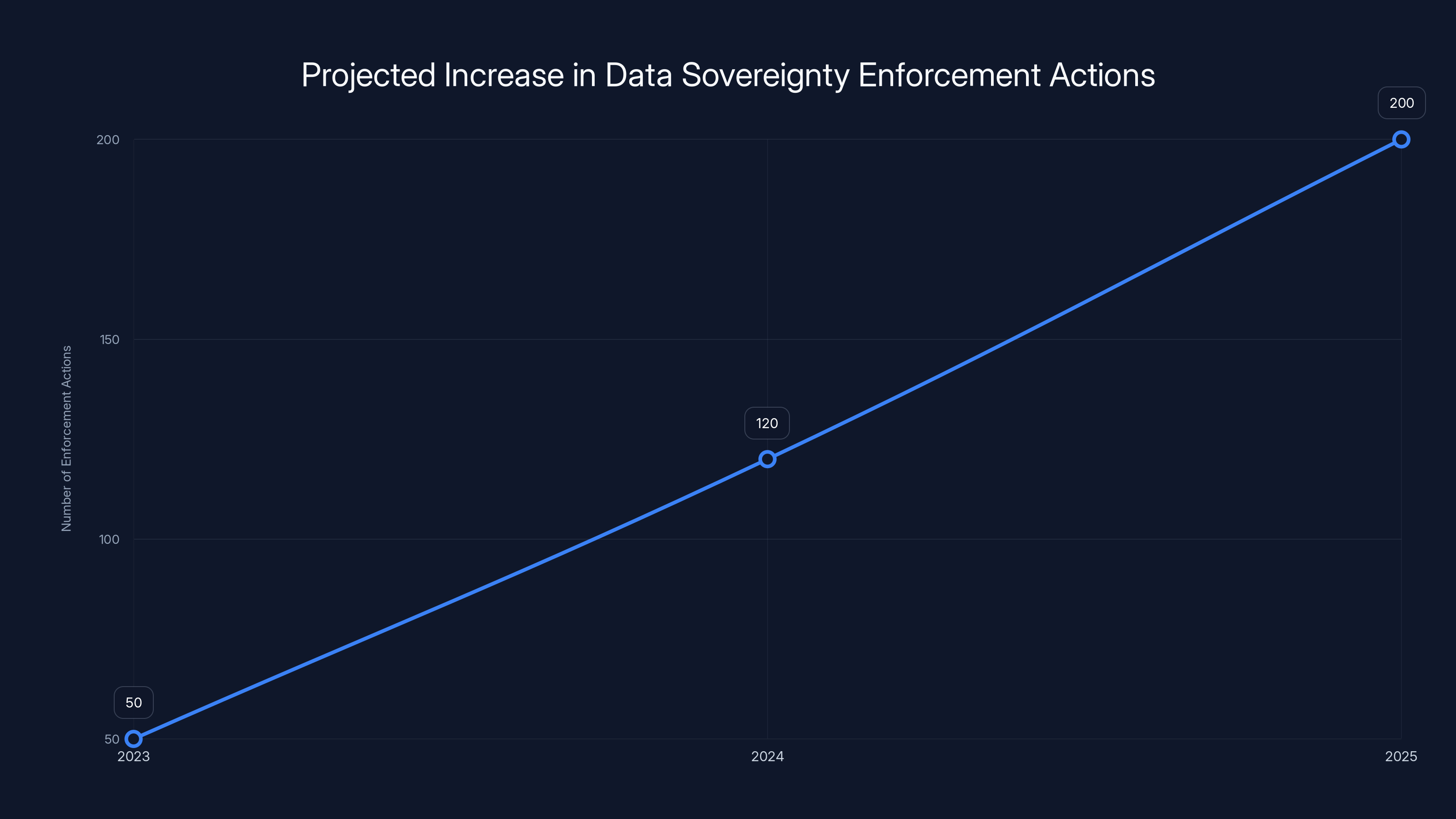
Estimated data shows a significant increase in data sovereignty enforcement actions from 2023 to 2025, highlighting the growing importance of compliance for SMEs.
Technology and Tools for Data Sovereignty
Several categories of technology help implement data sovereignty controls.
Infrastructure and Hosting
The foundation of sovereignty is choosing where your infrastructure lives.
For EU customers, Exoscale and Scaleway offer European cloud services with transparency about data location. AWS Europe regions and Microsoft Azure's European sovereign cloud offer hyperscale services within Europe.
For UK-specific requirements, AWS UK regions and Azure UK regions provide in-country hosting.
For organizations requiring complete data sovereignty with no US involvement, UCloud for China, Yandex Cloud for Russia, and regional providers in India, Australia, and other jurisdictions offer complete local control.
The choice depends on your specific requirements. If EU residency is sufficient, EU cloud services work well. If you need complete independence from US infrastructure, specialized regional providers are necessary.
Data Classification and Governance
Tools like Microsoft Information Protection, Varonis, and Digital Guardian help classify data and monitor for sensitive information moving to unauthorized locations.
These tools typically work by:
- Scanning repositories: Identifying sensitive data in files, databases, and communications.
- Applying labels: Automatically or manually tagging data based on sensitivity.
- Monitoring movement: Alerting when labeled data moves to unauthorized locations.
- Enforcing policies: Preventing certain actions (like uploading to personal cloud storage) for sensitive data.
For SMEs, data classification tools are particularly valuable because they automate discovery. You don't have to manually catalog every data location. The tools find sensitive data and flag it.
Encryption and Key Management
Even if data is stored in the right location, it needs to be encrypted so only authorized parties can read it.
AWS Key Management Service, Azure Key Vault, and Google Cloud Key Management provide centralized encryption key management.
For organizations needing complete control, customer-managed keys or hardware security modules (HSMs) ensure that even the cloud provider can't read your data.
Thales HSMs and YubiKey hardware tokens provide physical key management and ensure encryption keys never leave your control.
For SMEs, customer-managed key services (available from most cloud providers) strike a balance. You control the keys, but the provider handles key management infrastructure.
Access Control and Identity
Okta, Microsoft Entra ID, and Google Cloud Identity manage user access and permissions across applications.
These identity management platforms enable:
- Multi-factor authentication: Requiring multiple factors for login.
- Single sign-on: Users log in once and get access to all approved applications.
- Role-based access control: Defining what each role can access.
- Conditional access: Restricting access based on location, device, or other factors.
For sovereignty, conditional access is particularly important. You can restrict access to sensitive data based on geographic location, ensuring that only users in approved locations can access certain data.
Monitoring and Audit
Splunk, Elastic Security, and Azure Monitor ingest logs from all your systems and provide visibility into what's happening.
With proper logging configuration, you can:
- Alert on unauthorized data movement: Detect when data is accessed from unexpected locations.
- Track compliance: Generate audit reports showing that controls are working.
- Investigate incidents: Trace what happened if there's a security event.
For sovereignty, comprehensive logging is non-negotiable. You need to demonstrate that data stayed in approved locations and that only authorized parties accessed it.
Common Pitfalls and How to Avoid Them
Organizations implementing data sovereignty often hit predictable problems. Here's how to avoid them.
Pitfall 1: Assuming Cloud Provider Defaults Are Safe
Cloud providers optimize for scale and availability, not necessarily for sovereignty.
Default configurations often:
- Spread data across multiple regions for redundancy
- Automatically replicate to backup regions you didn't choose
- Route logs and analytics to centralized locations
- Cache data in content delivery networks across the globe
These defaults make sense for many workloads. They ensure availability if one region fails. But they violate sovereignty requirements if you need data in a specific location.
The fix: Don't accept defaults. Explicitly configure data location for every system. Verify that configurations match your requirements. Set up alerts if location changes.
Pitfall 2: Forgetting About Backups and Replicas
SMEs focus on where live data is stored and forget about backups.
Your primary database might be in the UK. But where does the backup go? If the backup runs to a default location, it might be in the US or EU. From a sovereignty perspective, that's a violation.
Backups need the same location discipline as live data.
The fix: Include backups and replicas in your location requirements. Ensure they're stored in approved locations. Test that recovery procedures don't violate sovereignty requirements.
Pitfall 3: Shadow IT Creating Unmanaged Data Movement
Employees are going to use tools. The question is whether IT knows about it.
When teams adopt unapproved tools, data flows to unapproved locations. A designer uses a US-based tool. A salesperson integrates a SaaS platform you've never heard of. An accountant stores data on a personal cloud service.
Shadow IT is particularly problematic for sovereignty because it creates hidden compliance violations.
The fix: Make approved alternatives accessible and easy to use. Educate teams about sovereignty requirements. Monitor for unauthorized tools. When you find them, help teams migrate to approved alternatives rather than just blocking them.
Pitfall 4: Ignoring Integrations and Data Flows
When you connect multiple systems, data flows create new compliance obligations.
You might control where your database lives. But if you integrate with a US analytics service, that service sees your data. If you use a US-based communication platform, messages flow there. Each integration introduces a new jurisdiction.
Many SMEs don't fully map these flows. They assume if the primary system is in the right location, everything is fine. They're not.
The fix: Map all integrations. For each integration, understand what data flows where. Ensure each integration meets your sovereignty requirements. When you need to move data, consider whether the integration can support it.
Pitfall 5: Treating Sovereignty as One-Time Setup
This is the biggest mistake.
Organizations implement sovereignty controls, then move on. Meanwhile, the environment changes. Engineers add new services without checking location requirements. Vendors update their practices. Regulations shift. The original configuration drifts.
Six months later, you're out of compliance and don't realize it.
The fix: Treat sovereignty as ongoing. Have regular audits (at least quarterly). Monitor for configuration changes. Track regulatory updates. Test that controls still work. Build sovereignty requirements into your change management process so new infrastructure is compliant from day one.

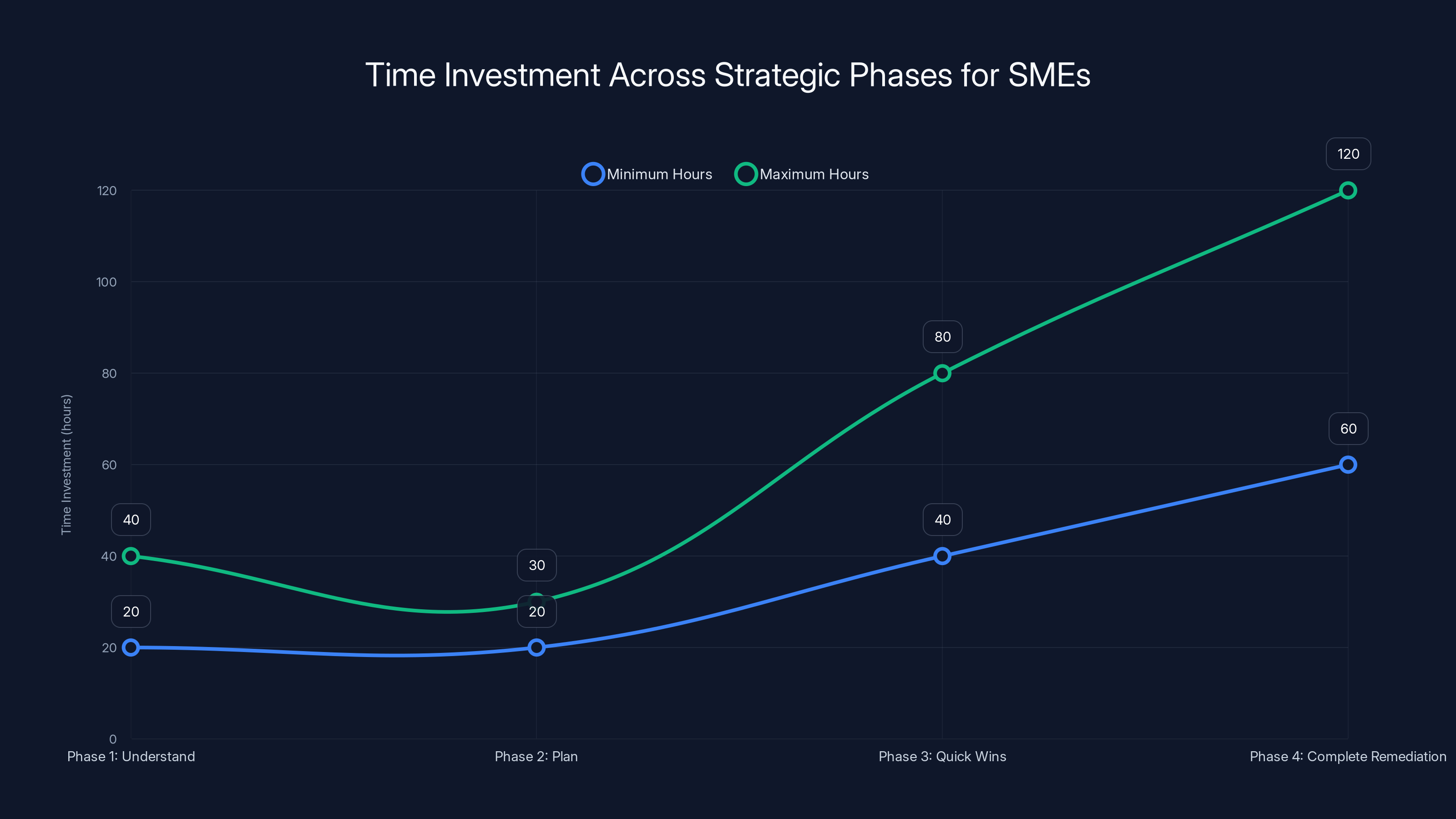
Estimated time investment varies by phase, with Phase 4 potentially requiring the most hours due to ongoing remediation efforts.
What Good Looks Like: Real-World Practices
Organizations that get sovereignty right follow consistent patterns.
Explicit Location Transparency
Providers state clearly where primary copies, replicas, backups, and archives live. They're not vague. They don't say "stored in the cloud." They say "primary replica in Frankfurt, backup in Dublin, archive in London."
This clarity makes it easy for SMEs to verify compliance. It reduces audit friction. It gives confidence that you understand where your data is.
Customer Control, Not Provider Defaults
Responsible providers let customers choose data location rather than imposing defaults.
You decide where data lives based on your requirements. The provider respects that decision and holds it consistently. If you need to change locations, the provider makes that simple.
This is fundamentally different from providers where location is a vendor decision and customers adapt to it.
Third-Party Vendor Review
Organizations with good sovereignty practices review their vendors regularly.
They ask vendors: Where is our data? Who can access it? How is it protected? When regulations or requirements change, they re-verify vendor responses.
Vendor reviews happen on a defined cycle, not ad-hoc. Findings get documented. Contracts are updated if vendor practices drift.
Comprehensive Monitoring and Audit Trails
Good implementations produce logs that regulators and customers can use, not just raw data.
Monitoring shows:
- Where data has been accessed from
- Who accessed what and when
- Whether configurations changed and when
- Whether recovery procedures work correctly
- Whether access control policies are enforced
These logs become evidence that controls are working. They're essential for compliance audits.
Recovery Plans That Respect Location Requirements
When disaster strikes, recovery procedures must keep data in approved locations.
This means:
- Immutable backups in approved jurisdictions
- Failover procedures that don't move data outside requirements
- Recovery testing that demonstrates failover works within approved locations
- Agreed RPOs and RTOs that account for location restrictions
Organizations that do this well have tested recovery procedures. They know exactly how long recovery takes and where data ends up. They've practiced it multiple times.
Regular Tabletop Exercises
The organizations best prepared for sovereignty challenges practice responding to them.
Regular tabletop exercises simulate scenarios:
- Regulator sends a data access request
- A vendor changes their terms
- Infrastructure in your primary region fails
- A new regulation changes your location requirements
Working through these scenarios in advance reveals gaps. You discover what you need to do before you're forced to do it under pressure.
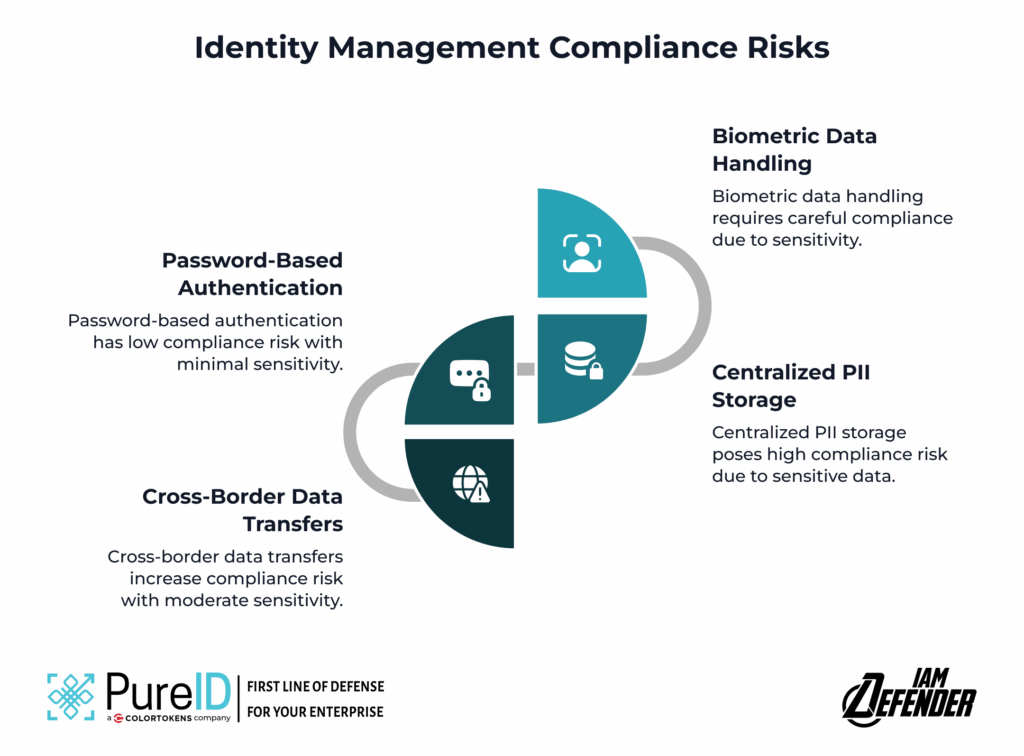
Strategic Guidance for SMEs: Next Steps
If you're leading an SME and sovereignty feels overwhelming, here's where to start.
Phase 1: Understand Your Situation (Weeks 1-4)
Action items:
- Audit current state: Where does your data actually live? Create a simple spreadsheet.
- Identify regulations: Which regulations apply to your business? Get help from a legal resource if needed.
- Interview key people: Where do you think data lives? What assumptions have you made?
Success metrics: You have a clear picture of where data lives, what regulations apply, and where the biggest gaps are.
Time investment: 20-40 hours across your team.
Phase 2: Plan Your Approach (Weeks 5-8)
Action items:
- Classify your data: Which data tiers have strict location requirements?
- Define requirements: For each tier, what are the location requirements?
- Evaluate providers: Which providers can meet your requirements?
- Estimate remediation effort: What would it take to move to compliant locations?
Success metrics: You have a prioritized list of changes needed and a realistic timeline for implementing them.
Time investment: 20-30 hours, potentially involving external consultants.
Phase 3: Quick Wins (Weeks 9-16)
Action items:
- Fix the most exposed data: Move the most sensitive, most regulated data to compliant locations first.
- Document your current setup: Create data flow diagrams and location inventory.
- Improve access controls: Ensure the most sensitive data has strong MFA and access restrictions.
Success metrics: Your highest-risk data is now in compliant locations with strong controls.
Time investment: Varies widely depending on your infrastructure. Could be weeks for simple changes or months for complex migrations.
Phase 4: Complete Remediation (Ongoing)
Action items:
- Address remaining data: Move remaining data to compliant locations on a schedule.
- Implement monitoring: Set up alerts for unauthorized data movement.
- Build governance: Create processes for maintaining sovereignty as you grow.
Success metrics: All data is in compliant locations. Monitoring alerts you to changes. Sovereignty is built into your infrastructure and operations.
Time investment: Ongoing, but decreasing as you build processes and standardize practices.
When to Bring in Expert Help
You might be able to handle some of this internally, but certain steps benefit from external expertise.
Bring in a consultant for:
- Regulatory interpretation: Understanding which rules apply to your specific business
- Provider selection: Evaluating providers and negotiating terms
- Architecture review: Ensuring your infrastructure approach is sound
- Migration planning: Managing complex data movements
- Compliance validation: Preparing for audits or regulatory inquiries
Do yourself:
- Data inventory: You know your systems better than anyone
- Documentation: Writing down your current state and decisions
- Ongoing monitoring: Setting up alerts and reviewing logs
- Policy enforcement: Making sure teams follow sovereignty requirements
A hybrid approach works well for SMEs. Use consultants for expertise you don't have, but keep internal ownership of the process and implementation.
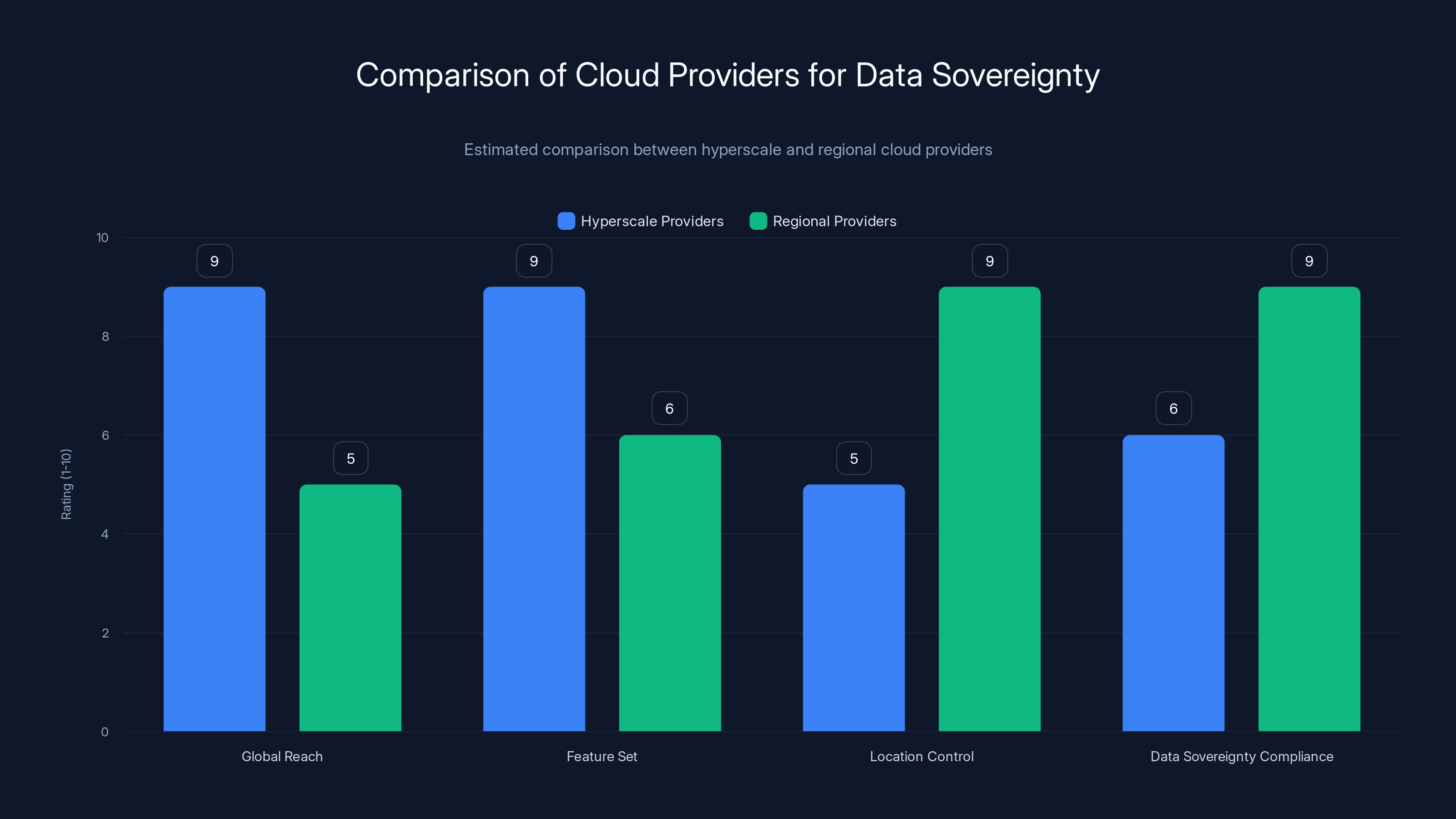
Hyperscale providers excel in global reach and features, while regional providers offer superior location control and compliance with data sovereignty. Estimated data.
The Future of Data Sovereignty: What's Coming
Data sovereignty isn't a static requirement. It's evolving rapidly.
Regulatory Acceleration
Regulators worldwide are tightening data sovereignty requirements. What started with GDPR has expanded to dozens of regional laws.
Expect:
- Stricter location requirements: More regulations requiring data to stay in specific jurisdictions.
- Faster rule changes: Regulatory cycles are accelerating. Requirements you're compliant with today might change within months.
- Cross-border enforcement: Regulators are cooperating more, making it harder to find jurisdictional loopholes.
- Individual accountability: Officers and directors are facing personal liability for data sovereignty failures, not just fines against companies.
For SMEs, this means sovereignty is becoming non-negotiable. The question isn't whether you need to address it. The question is how much of your effort goes to staying compliant as rules change.
Geopolitical Fragmentation
The internet is fragmenting. China has the Great Firewall. Russia is building its own internet infrastructure. The US is restricting technology transfers to certain countries. Europe is building digital sovereignty initiatives.
For SMEs operating globally, this fragmentation means:
- Multiple compliance regimes: You can't use one approach for all markets. Each region has unique requirements.
- Increased operational complexity: Managing data in fragmented jurisdictions requires more infrastructure and expertise.
- Risk of inadvertent violations: A service that was compliant in one jurisdiction becomes non-compliant in another as geopolitical tensions shift.
Decentralized and Sovereign Cloud Alternatives
As regulations tighten and geopolitical concerns grow, new infrastructure models are emerging.
Sovereign cloud options like the EU's European Digital Sovereignty initiative aim to create cloud infrastructure that doesn't depend on US or Chinese technology.
Decentralized infrastructure projects explore edge computing and distributed data storage as alternatives to centralized cloud providers.
Open-source alternatives to proprietary cloud services are gaining adoption among organizations that want complete control.
For SMEs, these alternatives offer optionality. Instead of choosing between hyperscale providers and smaller regional services, you'll have more choices aligned with specific sovereignty requirements.
Privacy and Data Rights Expanding
Regulations are expanding beyond location to grant data subjects more rights.
Data portability requirements let customers demand their data in a standard format and move it to a competitor. This is good for consumers but complicates infrastructure design.
Right to deletion requires organizations to permanently remove data on request, not just mark it as deleted. This affects backup and archive strategies.
Right to explanation in automated decision systems requires organizations to explain decisions made by algorithms. This is becoming a liability issue.
For SMEs, expanding rights mean more operational burden. You need systems that can export data on demand, delete data thoroughly, and explain decisions. These capabilities cost money and engineering effort.
Practical Tools and Resources
You don't have to build sovereignty expertise from scratch.
Assessment and Planning Tools
Data Residency Checklist: Frameworks like the Cloud Security Alliance provide questionnaires and checklists for assessing data sovereignty readiness.
Regulatory Mapping Tools: Services like OneTrust and Drata map regulations to your business and help track compliance obligations.
Provider Comparison: The Cloud Security Alliance maintains provider assessments covering data location practices.
Implementation Resources
Migration Planning: Services like AWS Migration Services, Azure Migration Services, and third-party migration specialists help plan and execute infrastructure moves.
Compliance Monitoring: Tools like Cloud Conformity continuously monitor your infrastructure for compliance drift.
Legal Assistance: Organizations like Linklaters and Clifford Chance specialize in data sovereignty and help negotiate vendor terms.
Education and Expertise
Certifications: The CISSP and CompTIA Security+ certifications include data governance topics.
Courses: Coursera, Udemy, and provider-specific training (AWS, Azure, GCP) offer data sovereignty courses.
Communities: Forums and communities like r/netsec and security-focused Slack communities discuss emerging practices.

Conclusion: Building Resilience Through Sovereignty
Data sovereignty has moved from the fringe of IT concerns to the center. It's now a business imperative, a supply chain requirement, and a competitive advantage.
For SMEs, the urgency is real. Regulatory enforcement is escalating. Larger partners demand sovereignty compliance. Infrastructure failures create pressure to control data location. Egress fees create pressure to plan exits in advance.
The good news is that data sovereignty doesn't require enterprise budgets or deep expertise. It requires clear thinking about what data you have, where it needs to live, and who should access it. It requires choosing the right provider partners. It requires discipline in maintaining that clarity as your business evolves.
The organizations getting this right aren't waiting for regulations to force them. They're implementing sovereignty proactively because it's the right thing to do. It reduces risk. It builds customer trust. It creates optionality when circumstances change.
If your SME hasn't addressed data sovereignty yet, now is the time. Start with an honest audit of where your data actually lives. Understand which regulations apply. Identify the gaps. Create a roadmap to address the highest-risk items first.
Don't try to boil the ocean. Don't insist on perfection immediately. Move systematically. Quick wins build momentum and credibility. Complete remediation builds long-term resilience.
And don't do it alone. Partner with providers who understand sovereignty. Consult with experts when you need specialized knowledge. Build a team, even if it's small, that owns sovereignty requirements and keeps them in focus as everything else changes.
Data sovereignty is how modern organizations take control of their risk. It's how they stay compliant with regulations that keep evolving. It's how they maintain resilience when infrastructure fails or circumstances shift.
For SMEs, that control and resilience are worth the effort to get right.
FAQ
What is data sovereignty and why does it matter for SMEs?
Data sovereignty is the requirement that data must be stored and processed according to the laws of the jurisdictions where it resides or where the data subject lives. For SMEs, it matters because regulatory enforcement has escalated dramatically, larger business partners now demand sovereignty compliance as a contract requirement, and infrastructure failures (like the December 2024 AWS outage) demonstrate that data location directly impacts business continuity. Non-compliance can result in significant fines, loss of supply chain partnerships, and reputational damage.
How do I know which regulations apply to my SME's data?
Start by identifying your customers' locations, where your employees are based, and where you process data. If you have UK customers, the UK Data Protection Act applies. EU customers trigger GDPR. US customers might trigger CCPA or other state privacy laws. Industry-specific rules (healthcare, finance, payments) add additional requirements. Document which regulations apply, then determine location requirements for each. When in doubt, consult a data protection specialist who can interpret requirements for your specific business.
What's the difference between hyperscale cloud providers and regional providers for data sovereignty?
Hyperscale providers like AWS, Azure, and Google Cloud offer global reach and broad features but optimize for standardized behavior, not location customization. They offer region selection but may automatically replicate data, backups, or logs to locations you don't control. Regional providers focus specifically on data sovereignty, offering transparent location control, customer-managed encryption, and clear accountability for where every copy of data lives. The tradeoff: regional providers are more expensive and have fewer integrations, but they prioritize exactly what sovereignty requires.
What should I do about backups and data replicas when implementing sovereignty?
Backups and replicas need the same location discipline as live data. Identify where your backups currently go (often to default locations you don't control). Ensure backups are stored in locations that meet your sovereignty requirements. Test recovery procedures to confirm they don't move data outside approved jurisdictions. Implement immutable backups in approved locations so you can recover quickly without violating compliance requirements. Many SMEs forget about backup location when implementing sovereignty; it's actually a critical component.
How can we prevent shadow IT from undermining our data sovereignty efforts?
Shadow IT is inevitable when teams adopt tools without IT approval. Rather than just blocking unauthorized tools, make approved alternatives accessible and easy to use. Educate teams about why data location matters. Monitor for unauthorized tools and help teams migrate to compliant alternatives rather than just blocking them. Create an "approved tools" list for common use cases, making it easier to use approved tools than unapproved ones. When teams understand sovereignty requirements and have good alternatives, shadow IT decreases dramatically.
What's the relationship between data sovereignty and business resilience?
Data sovereignty directly impacts resilience. When you control where your data lives, you can distribute it across multiple jurisdictions, reducing dependence on any single region or provider. You can design failover procedures that keep data in approved locations. You can migrate quickly if a provider fails or changes terms. When data location is controlled by providers or depends on defaults, you're locked in. You can't exit quickly. You can't adapt when circumstances change. Sovereignty and resilience are interconnected—implementing one strengthens the other.
How often should we audit our data sovereignty compliance?
Audit at least quarterly. More frequently if your environment changes rapidly or regulations are evolving. During each audit, verify that data is still in approved locations, access controls are enforced, integrations haven't changed compliance posture, and monitoring is working correctly. Use audits to identify drift and plan corrections before issues escalate. Treat sovereignty as ongoing rather than one-time setup. Organizations that audit frequently catch and fix problems before they become compliance violations or business emergencies.
What happens if we discover we're out of compliance with data sovereignty requirements?
First, document what you found and assess the scope of the problem. How much data is affected? How long has it been in non-compliant locations? Did the non-compliance expose data to unauthorized access? Second, notify your legal team and consider whether disclosure is required to regulators or customers. Third, create a remediation plan with a realistic timeline. Move the most critical data first, but create urgency to address all non-compliance. Fourth, communicate with your data protection officer and relevant partners. Most regulatory bodies reward proactive disclosure and remediation more favorably than discovered violations. Fifth, implement changes to prevent recurrence.
Is it possible to implement data sovereignty without external consultants?
Yes, but it depends on your complexity. Simple implementations (small team, one jurisdiction, limited integrations) can often be handled internally if you have people with infrastructure and compliance knowledge. Complex implementations (multiple jurisdictions, strict regulations, deep integrations) usually benefit from external expertise. A hybrid approach works well: use consultants for areas where you lack expertise (regulatory interpretation, provider negotiation, architecture review) but maintain internal ownership of implementation and ongoing compliance. The cost of getting expert advice upfront is typically much less than the cost of fixing compliance failures later.
How does data sovereignty affect costs?
Sovereignty can increase costs in several ways: regional providers often charge more than hyperscale alternatives, maintaining copies in multiple jurisdictions increases storage costs, and implementing monitoring and compliance infrastructure requires tools and expertise. However, costs are often offset by avoiding regulatory fines (which are much larger), reducing supply chain losses from non-compliance, improving resilience (which reduces incident costs), and avoiding vendor lock-in (which prevents unnecessary pricing increases). Calculate the true cost of sovereignty by including both implementation costs and savings from avoided risks.

Next Steps: Taking Action on Data Sovereignty
Data sovereignty isn't a theoretical concern anymore. It's a business requirement with real consequences for non-compliance.
If you're an SME leader, take action now. Start with the audit phase: understand where your data actually lives and which regulations apply. The clarity alone will reveal your highest-priority risks.
For development and operations teams, sovereignty should become part of how you think about infrastructure. When choosing a new service or moving data, ask the sovereignty question first: where will this data live, and is that location compliant? Building this thinking into your decision-making process prevents problems from accumulating.
For anyone involved in data handling, understand the sovereignty requirements for your organization. Know which data needs location control. Use approved tools and services. Alert your team if you discover data moving to unexpected locations.
The organizations that will thrive in the next few years are the ones that treat data sovereignty as a core competency, not a compliance checkbox. They'll be resilient when infrastructure fails. They'll be trusted by partners and customers. They'll be confident when regulators ask questions.
Your SME can be that organization. Start today.

Key Takeaways
- Data sovereignty is now a business requirement, not optional compliance: Regulatory enforcement escalated dramatically in 2024-2025, with major fines for cross-border violations and larger partners demanding sovereignty clauses in contracts.
- SMEs face complexity without expertise: Overlapping regulations across jurisdictions, shadow IT creating unmanaged data movement, and vendor lock-in through egress fees make sovereignty challenging for resource-constrained teams.
- Sovereignty must be built into infrastructure from the start: Choosing the right provider, implementing explicit data location controls, access restrictions, and backup strategies prevents costly remediation later.
- Data location directly impacts business resilience: Infrastructure failures demonstrate that data concentration creates single points of failure; distributed, controlled data improves recovery speed and business continuity.
- Systematic implementation beats perfection: Start with audit and quick wins on highest-risk data, then build complete governance; treating sovereignty as ongoing rather than one-time setup prevents compliance drift.
Related Articles
- Data Sovereignty for Business Leaders [2025]
- AI Factories: The Enterprise Foundation for Scale [2025]
- EU Tech Enforcement 2026: What Trump's Retaliation Threats Mean [2025]
- Condé Nast Data Breach 2025: What Happened and Why It Matters [2025]
- GenAI Data Policy Violations: The Shadow AI Crisis Costing Organizations Millions [2025]
- Articul8 Series B: Intel Spinoff's $70M Funding & Enterprise AI Strategy
![Data Sovereignty for SMEs: Control, Compliance, and Resilience [2025]](https://tryrunable.com/blog/data-sovereignty-for-smes-control-compliance-and-resilience-/image-1-1767887017191.jpg)



