Understanding the Tone Shell Backdoor: A Deep Dive into Chinese Government Espionage [2025]
Cybersecurity threats evolve at a pace that often outstrips our ability to defend against them. But every few months, researchers uncover something that fundamentally changes how we think about what's possible on a compromised system. Tone Shell is one of those threats.
In early 2025, security researchers at Kaspersky uncovered a sophisticated cybersecurity campaign targeting government organizations across multiple Asian nations. The attackers, identified as Mustang Panda (a Chinese state-sponsored threat actor), deployed an upgraded variant of the Tone Shell backdoor. What makes this campaign particularly concerning isn't just the malware itself, but how it's delivered and what it's capable of doing once it takes root.
Here's the thing: previous versions of Tone Shell operated in user mode, where antivirus software could theoretically detect and intercept it. The new variant changes that calculus entirely. By leveraging kernel-mode drivers and stolen or leaked code-signing certificates, Mustang Panda created something far more dangerous. This backdoor now operates with the same privileges as your operating system itself, making it nearly invisible to conventional security tools.
The scope of this campaign is sobering. Affected organizations span multiple Asian countries, including Myanmar, Thailand, and others. Victims weren't just infected with Tone Shell either. Kaspersky found that compromised systems also carried Plug X (a remote access trojan) and Tone Disk (a USB worm). This layered approach suggests a sophisticated operation with specific intelligence goals.
What makes this threat analysis critical for government and enterprise organizations is understanding not just what happened, but how to detect it, prevent it, and respond when infection occurs. The techniques Mustang Panda employed represent a significant escalation in cyber-espionage capabilities. And because this is a state-sponsored operation, you can expect continuous refinement and adaptation.
This article breaks down everything you need to know about the Tone Shell backdoor, how the attack chain works, what Mustang Panda's objectives appear to be, and most importantly, how organizations can detect and defend against this threat. Whether you're in government, critical infrastructure, or work for a large enterprise, this threat deserves your attention.
TL; DR
- State-Sponsored Campaign: Mustang Panda (Chinese APT) deployed upgraded Tone Shell backdoors targeting Asian government organizations starting February 2025
- Kernel-Mode Delivery: The new variant uses signed mini-filter drivers to operate in kernel mode, hiding from user-mode security tools and antivirus software
- Rootkit Capabilities: The backdoor grants remote shell access, file operations, and defender tampering, operating with system-level privileges
- Multi-Stage Infection: Victims also infected with Plug X and Tone Disk, indicating coordinated espionage campaign with multiple objectives
- Detection via Memory Forensics: Organizations should prioritize memory forensics and indicators of compromise (Io Cs) to identify compromised systems
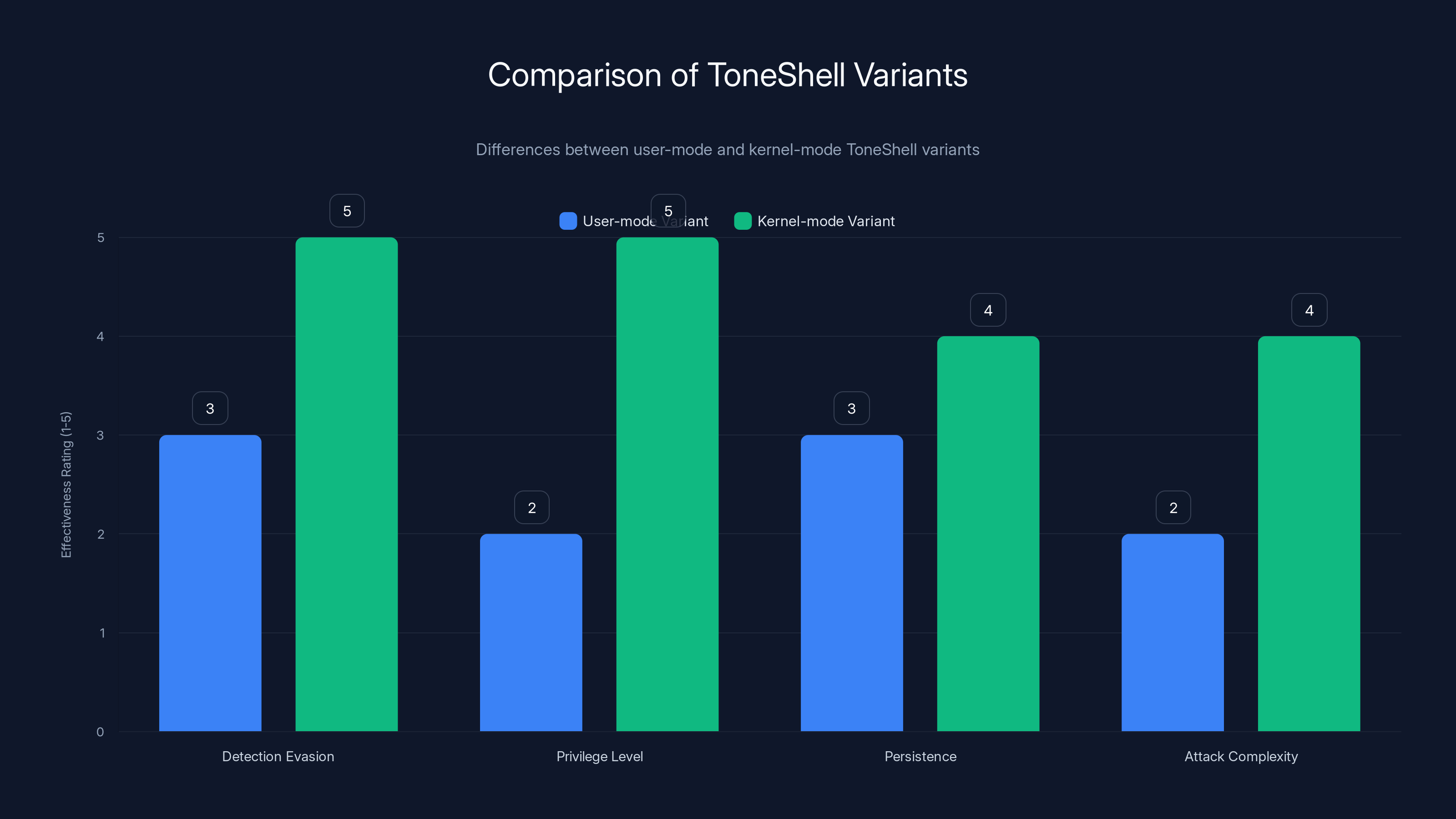
The kernel-mode variant of ToneShell shows significant improvements in detection evasion and privilege level, making it more effective and harder to detect compared to the user-mode variant. Estimated data based on malware capabilities.
What Is Mustang Panda and Why Does It Matter?
Mustang Panda isn't a newly discovered threat actor. This group has been operating for years, conducting espionage campaigns primarily focused on government organizations and strategic sectors across Asia, Europe, and beyond. What distinguishes them from common cybercriminals is their sophistication, resources, and apparent mandate to gather intelligence on foreign governments.
The group is believed to operate under the direction of Chinese state interests, though attribution in cybersecurity is always complex and probabilistic rather than absolute. That said, the tools they use, the targets they select, and the infrastructure they maintain all point toward a well-funded, state-level operation.
Mustang Panda's historical toolset includes malware like Plug X (which we'll discuss later), various backdoors, and custom utilities. They favor spear-phishing campaigns and watering-hole attacks as initial entry vectors. Once inside a network, they move methodically, establishing persistence, gathering data, and maintaining long-term access.
Why does this matter for you? If you work in government, national security, or foreign affairs, you're already on their radar. If you work in critical infrastructure, energy, telecommunications, or defense contracting, you likely are too. Even if you don't fit those categories, understanding how state-sponsored actors operate raises your defensive posture across the board.
The sophistication of Mustang Panda's operations also tells us something important: if these techniques are being deployed by a state-sponsored group, they'll eventually be adopted by less-resourced threat actors. Learning how to defend against them now positions you ahead of that curve.

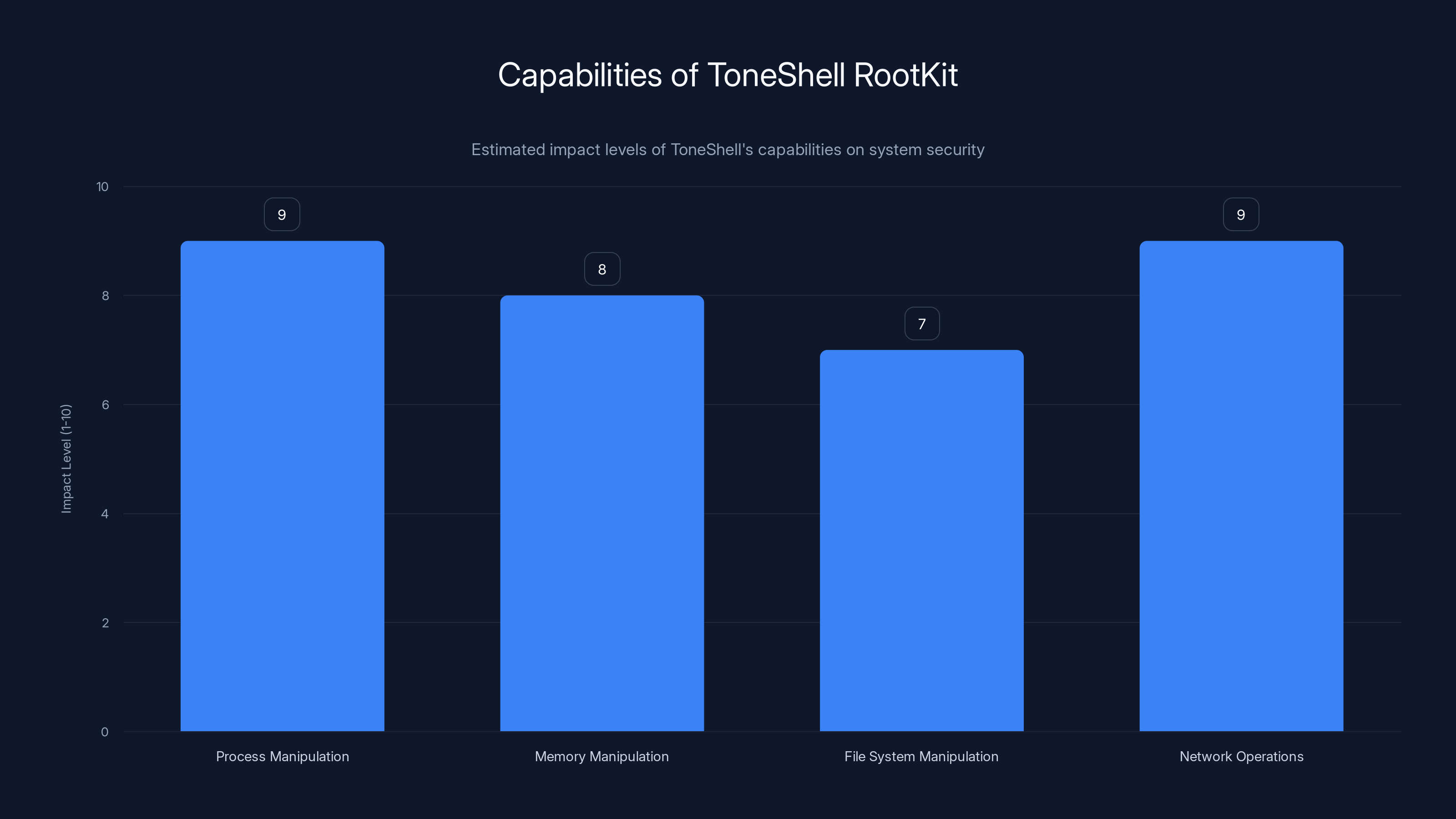
ToneShell's rootkit capabilities have high impact levels, particularly in process manipulation and network operations, posing significant security threats. Estimated data.
The Tone Shell Backdoor Explained: From User Mode to Kernel Mode
Let's start with the fundamentals. A backdoor is essentially a hidden entry point into a system that bypasses normal authentication. Once installed, it allows attackers to access the system whenever they want, execute commands, exfiltrate data, and generally treat the compromised machine as their own.
Tone Shell has existed in various forms for years. In its earlier iterations, it operated in user mode—the privilege level where regular applications run. User-mode applications have limited capabilities compared to kernel-mode code. They can't directly access hardware, modify system files in protected locations, or hide themselves from the operating system itself.
This limitation meant that antivirus software and endpoint detection and response (EDR) tools could monitor Tone Shell's behavior relatively easily. If the malware tried to create suspicious network connections, write to system directories, or inject code into other processes, security software could potentially intercept it.
The 2025 variant changes everything. By delivering Tone Shell through a kernel-mode mini-filter driver, Mustang Panda essentially gave the backdoor administrative-level privileges from the moment of execution. Here's the critical difference: kernel-mode code operates at the same privilege level as the operating system itself.
This is the difference between someone knocking on your front door versus someone who has your house's architectural plans and can enter through the foundation. Kernel-mode malware can modify how Windows behaves, intercept system calls, and hide itself from tools that run in user mode.
Mini-Filter Drivers: The Technical Foundation
Mini-filters are a legitimate Windows feature designed for specific purposes. They're kernel-mode drivers that sit within the Windows file system stack. Think of the file system stack as a series of layers that handle every read and write operation to your hard drive.
A mini-filter sits in this stack and can see every file operation before it completes. It can inspect the operation, block it, modify it, or log it. This is useful for legitimate security software—antivirus programs use mini-filters to scan files as they're accessed. Backup software uses them to monitor file changes. Encryption utilities use them to transparently encrypt and decrypt data.
But in the wrong hands, this capability becomes terrifying. A malicious mini-filter can:
- Monitor all file operations and report interesting files back to attackers
- Block antivirus software from accessing certain files or directories
- Hide files and folders from the operating system
- Prevent Windows Defender from loading into the I/O stack
- Intercept and modify network traffic
- Monitor what users type, access, or view
In the Tone Shell campaign, the mini-filter driver does exactly this. It establishes itself as a trusted component of the file system and then subverts security controls from within.
Code Signing Certificates: Legitimate Permissions Abused
Here's where it gets particularly clever. The mini-filter driver is signed with a code-signing certificate. This certificate could be either stolen from a legitimate company or obtained through leaked certificates from Microsoft's store.
Code-signing is a fundamental security mechanism in Windows. When you load a kernel-mode driver, Windows checks the digital signature to verify it comes from a trusted source. Unsigned or invalidly signed drivers won't load. This is a core security feature.
By using a legitimate certificate (whether stolen or leaked), the Tone Shell mini-filter appears to Windows as trustworthy code. The operating system loads it without complaint. Security software, seeing the valid signature, may assume it's legitimate and allow it to run.
This is a brilliant abuse of trust. The attackers didn't need to exploit a Windows vulnerability to load kernel-mode code. They just needed a valid certificate and knowledge of where to place their driver. They got both.
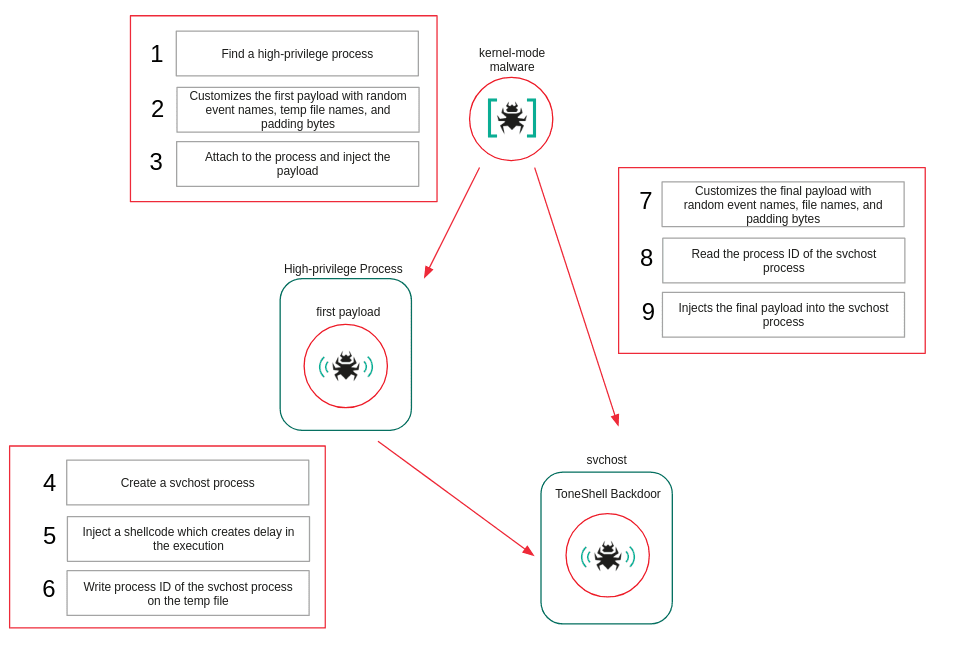
The Attack Chain: How Tone Shell Gets Into Your System
Understanding the attack chain is crucial because it identifies potential chokepoints for defense. The campaign appears to have started around February 2025, though Kaspersky likely discovered it months after initial compromise.
Initial Compromise: The Entry Point
Kaspersky didn't detail the specific initial infection vector, but based on Mustang Panda's historical tactics and industry best practices, the most likely delivery mechanism is spear-phishing. Targeted emails to government officials, with carefully researched details about their work, often contain either:
- Malicious attachments (Word documents with macro-based exploits, PDFs with embedded payloads)
- Links to compromised websites or attacker-controlled domains
- Office documents exploiting zero-day vulnerabilities
For government targets, these emails often reference real policy issues, legislation, or international events to appear legitimate. An official in Myanmar's government ministry might receive an email about regional trade policy that looks entirely authentic. The attachment or link seems relevant to their work.
Once a target opens the attachment or clicks the link, the initial payload executes. This payload is often a downloader or loader—a small piece of code whose only job is to fetch the next stage.
Second Stage: The Loader
The second stage is where the mini-filter driver arrives. The loader unpacks and installs the signed kernel-mode driver onto the system. This is where the actual stealth capabilities activate.
The mini-filter driver loads before many security tools initialize, giving it the ability to hide itself and subvert security software from the start. Once loaded, it can prevent Windows Defender from loading into the I/O stack, meaning the antivirus can't monitor file operations.
Third Stage: Tone Shell Installation
With the mini-filter established and security tools compromised, Tone Shell itself is installed. Tone Shell operates as a kernel-mode backdoor that can:
- Create and maintain remote shells for interactive command execution
- Upload and download files
- Create temporary files for storing exfiltrated data
- Manage persistent connections to command and control infrastructure
- Hide its network traffic from user-mode monitoring tools
Fourth Stage: Payload Deployment
With Tone Shell established, additional malware arrives. In the observed campaign, this included:
- Plug X: A sophisticated remote access trojan allowing broad system control
- Tone Disk: A USB worm designed to spread via removable media and collect intelligence
This layered approach suggests different objectives. Tone Shell provides persistent backdoor access. Plug X provides interactive control and broad system capabilities. Tone Disk enables persistence and lateral movement through physical media.

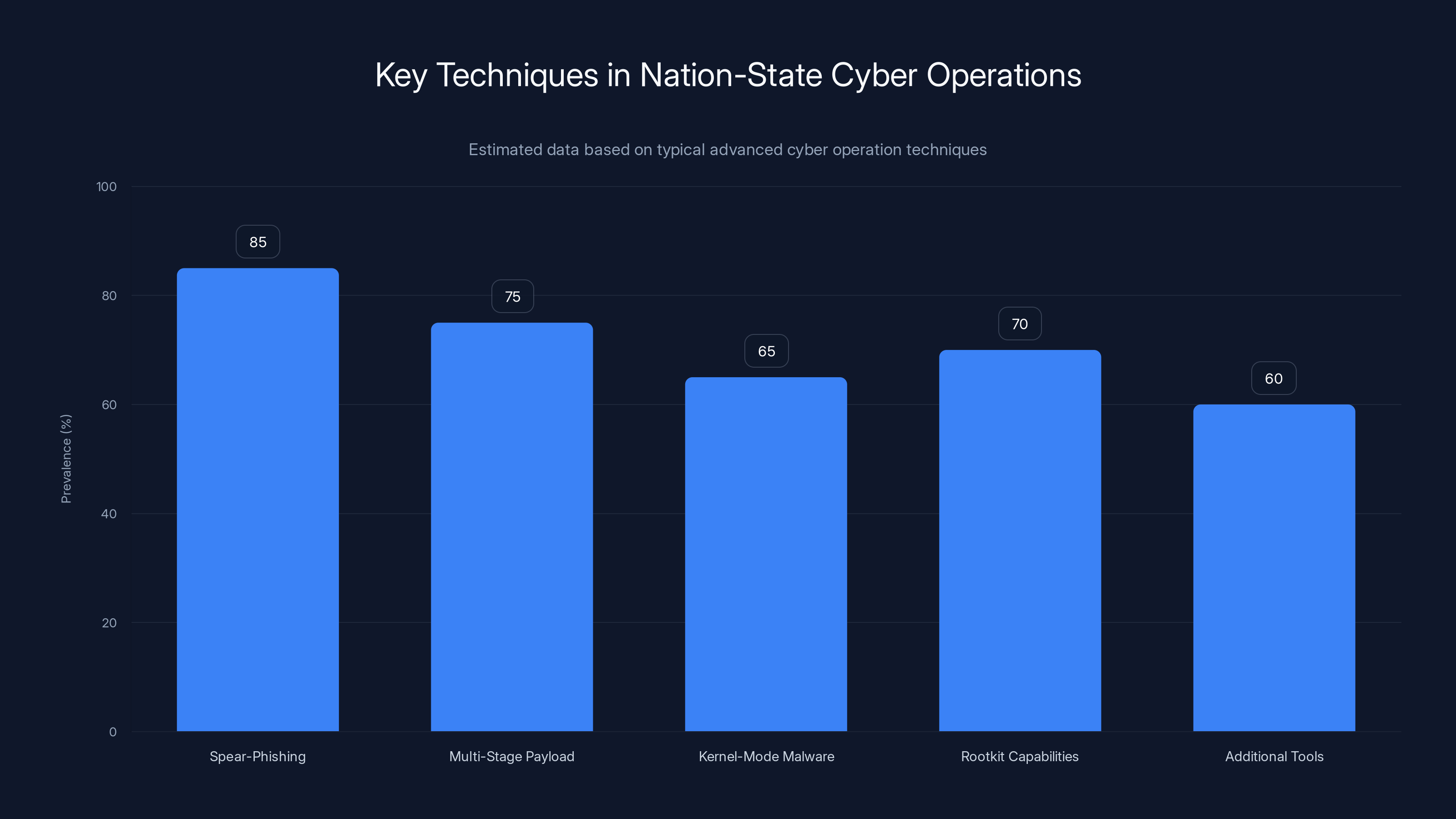
Estimated data shows spear-phishing as the most prevalent technique in advanced nation-state cyber operations, followed by multi-stage payloads and kernel-mode malware.
Root Kit Capabilities: What Tone Shell Can Actually Do
Once Tone Shell is running with kernel-mode privileges, its capabilities expand dramatically. Let's break down what this backdoor can actually accomplish on an infected system.
Process and Memory Manipulation
Kernel-mode code can read and write to the memory space of any process, including system processes. This means Tone Shell can:
- Inject code into legitimate applications to hide its presence
- Read sensitive data from running applications (browser credentials, document content, encryption keys)
- Modify the behavior of security software while it's running
- Extract memory dumps of applications for offline analysis
Imagine a diplomat opening a sensitive document in Microsoft Word. That document's contents exist in the Word process's memory. Tone Shell can read it. A user enters their password in a browser. Tone Shell can capture it. This is why kernel-mode malware is so dangerous—it operates at a level where traditional defenses become invisible.
File System Manipulation
The mini-filter driver component specifically enables:
- File hiding: Making files and directories invisible to the operating system and user
- File access monitoring: Seeing every file accessed and reporting on sensitive documents
- File modification interception: Watching specific files and alerting when they're changed
- Malware distribution: Planting additional malware on the system without user knowledge
A government worker might think they're using their computer securely, with all sensitive files in protected directories. Tone Shell's mini-filter can see every single thing they access and hide its own presence entirely.
Network Operations
Kernel-mode network access enables:
- Network traffic modification: Intercepting and modifying network packets
- DNS hijacking: Redirecting web requests to attacker-controlled sites
- VPN/proxy bypass: Operating independently of user-configured security proxies
- Covert channels: Establishing hidden communication methods not visible to network monitoring tools
Even if a government organization has excellent network monitoring, a kernel-mode backdoor can potentially hide its traffic or route it through legitimate-looking connections that don't trigger alerts.
Windows Defender Tampering
One of the most critical capabilities: the ability to prevent Windows Defender from operating. The new Tone Shell variant specifically includes functionality to:
- Block Windows Defender from loading into the I/O stack
- Prevent real-time protection from activating
- Hide malicious files from scanning
- Modify Windows Defender's configuration
This is devastating because it removes one of Windows' built-in defenses. Many organizations, particularly those with limited security budgets, rely on Windows Defender as their primary malware protection. A backdoor that can disable it is essentially removing the castle's main gate.

Indicators of Compromise: How to Detect Tone Shell Infections
Detection is your first line of defense. If you can identify an infected system, you can isolate it, preserve evidence, and begin remediation. Here's how security professionals approach Tone Shell detection.
Memory Forensics: The Primary Detection Method
Kaspersky emphasized that memory forensics is the most reliable detection method for Tone Shell. Here's why: kernel-mode malware can hide from the file system. It can prevent itself from appearing in running processes lists. But it must exist somewhere in memory while the system is running.
Memory forensics involves capturing the entire contents of system RAM and analyzing it offline. Tools like Volatility, Rekall, or Mandiant's Redline can parse through memory dumps and identify:
- Kernel-mode drivers that shouldn't be there
- Mini-filter drivers in the file system stack
- Suspicious process injections
- Network connections initiated by kernel code
- Evidence of anti-forensics techniques
When analyzing memory, investigators look for:
- Unsigned or invalidly signed drivers: While Tone Shell uses valid certificates, patterns in driver names, locations, and behaviors can reveal it
- Mini-filter driver chains: The legitimate file system filter chain should be known. New filters are suspicious
- Code injection patterns: Evidence of code placed in system processes
- Network socket structures: Kernel-mode network connections that don't correspond to user-mode applications
The challenge with memory forensics is that it requires taking the system offline, which destroys the live state and halts operations. For critical government systems, this is a significant decision.
Indicators of Compromise: IOCs
Indicators of Compromise are specific artifacts that point to infection. Kaspersky released IOCs including:
- File hashes: Specific file signatures of known Tone Shell components
- Registry entries: Malicious registry keys created during installation
- Network indicators: Command and control server IP addresses and domains
- Process names and behaviors: Suspicious process creation patterns
- Driver names and paths: Expected locations and names of malicious drivers
Organizations can use these IOCs in their security tools:
- Antivirus/EDR: Scanning for known file hashes
- SIEM systems: Correlation rules looking for suspicious process creation or registry modification
- Network monitoring: Blocking known C2 domains and IP addresses
- Endpoint tools: Querying systems for IOC presence
Behavioral Detection Challenges
Here's the uncomfortable truth: behavioral detection of kernel-mode malware is significantly harder than detecting user-mode malware. The malware operates at the same privilege level as the monitoring tools, giving it the ability to hide its actions.
Conventional EDR tools that monitor process behavior, file access, and network connections may not see Tone Shell activity. The malware can intercept the monitoring functions themselves.
This is why defense-in-depth is essential. You can't rely on a single detection method.

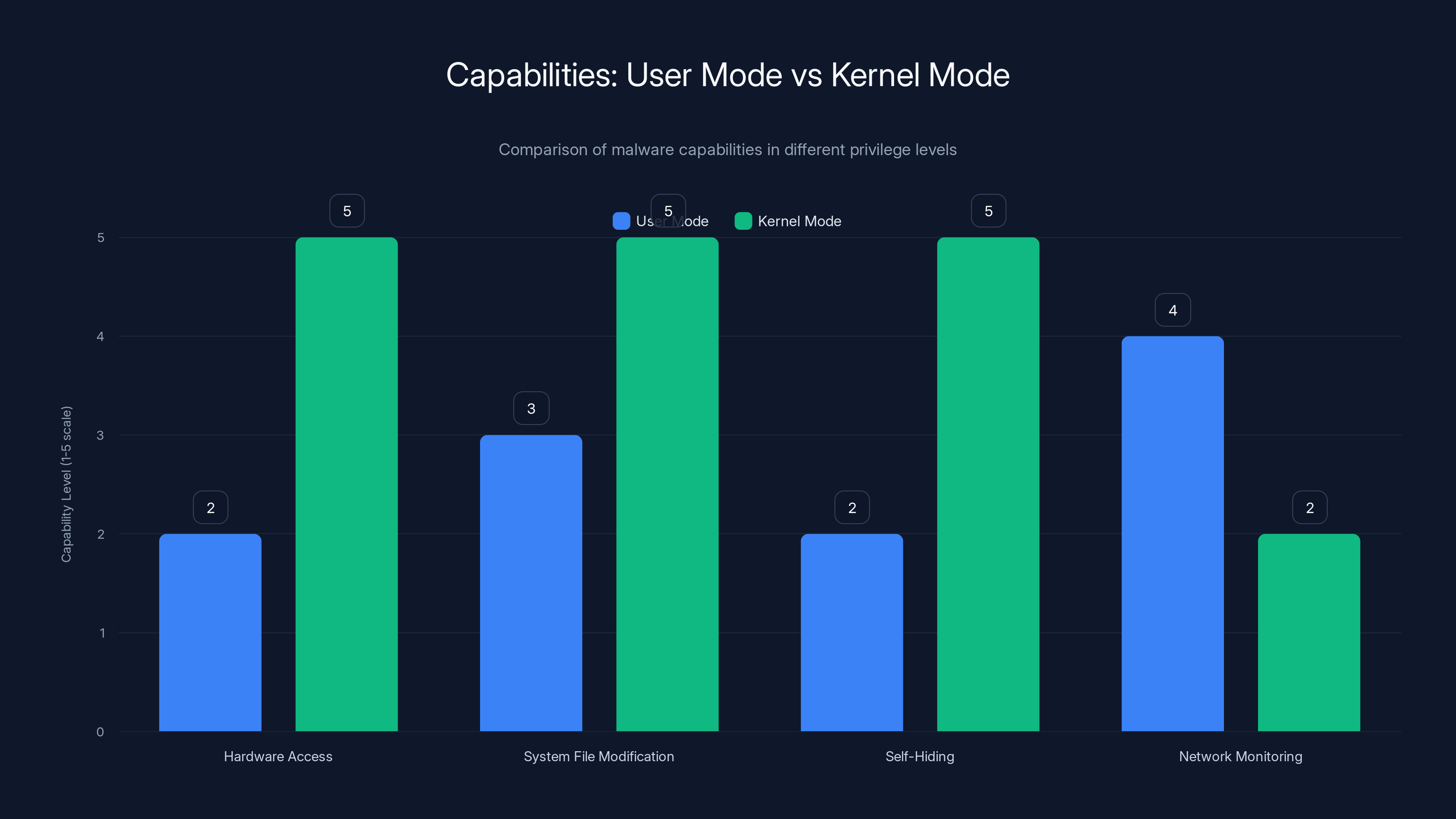
Kernel-mode malware, like the 2025 ToneShell variant, has significantly higher capabilities in hardware access, system file modification, and self-hiding compared to user-mode malware. Estimated data.
The Targeting and Motivation: Why Government Organizations?
Understanding why Mustang Panda targets government organizations is important for risk assessment. This isn't ransomware that spreads indiscriminately. This is espionage.
Strategic Intelligence Gathering
Government organizations possess intelligence valuable to state actors:
- Foreign policy positions and negotiations: Understanding how other governments approach trade, military, or diplomatic issues
- Internal government communications: Decisions not yet public can be worth significant intelligence value
- Economic data: Details about trade relationships, resource deals, or economic strategies
- Military information: Organizational structure, capabilities, deployment information
- Diplomatic contacts: Understanding which officials meet with foreign counterparts and what they discuss
For a state like China, understanding the internal deliberations of neighboring governments provides strategic advantage in everything from trade negotiations to military posturing.
Geographic Focus: Asian Governments
The targeting of Asian government organizations reflects China's strategic interests:
- Regional influence: Understanding and monitoring the governments of neighboring countries in Southeast Asia
- Belt and Road Initiative: Economic and infrastructure projects require intelligence on the political climate in partner nations
- Territorial disputes: Ongoing tensions over maritime boundaries and resource claims make intelligence about other countries' military capabilities and intentions critical
- Trade relationships: Understanding internal government positions on trade allows China to anticipate policy changes
Myanmar and Thailand, specifically targeted in this campaign, are strategically important. Myanmar sits at the crossroads of Asian trade routes. Thailand hosts U. S. military presence and has complex relationships with multiple regional powers. Intelligence from these countries' governments would be valuable.
Long-Term Presence Strategy
The sophisticated nature of this attack—multiple malware components, kernel-mode delivery, persistence mechanisms—suggests this isn't a smash-and-grab operation. Mustang Panda appears to be establishing long-term presence for sustained intelligence gathering.
Tone Shell provides remote shell access for ongoing operations. Plug X provides flexible interactive control. Tone Disk enables lateral movement and persistence. Together, they create redundancy: if one component is detected and removed, others can maintain access.
This is characteristic of advanced persistent threat (APT) campaigns. The goal isn't to steal one document and disappear. It's to maintain access indefinitely, monitoring communications, gathering intelligence, and adapting as defenses change.

Defensive Strategies: Protecting Against Tone Shell
Now let's talk about what you can actually do about this threat. Defense against state-sponsored malware is challenging but not impossible. It requires layered approaches and continuous vigilance.
Architectural Defense: Assumption of Breach
The first principle is assumption of breach. Assume that determined attackers can get into your network. Your defenses shouldn't rest on preventing breach, but on detecting and responding to it.
For government organizations, this means:
- Segmentation: Critical systems should be on isolated networks. Even if an attacker gains access to a general user network, they can't reach the systems that contain the most sensitive intelligence
- Microsegmentation: Within networks, systems should communicate only with systems they legitimately need to reach
- Zero-trust architecture: Don't trust internal traffic. Verify the identity and authorization of every access request
Endpoint Security: Moving Beyond Signatures
Traditional signature-based antivirus won't stop Tone Shell. Kernel-mode malware can hide from or prevent antivirus execution. But modern endpoint protection can still help:
- Behavioral analysis: Even if malware hides its presence, suspicious behaviors (trying to load drivers, accessing sensitive files) can trigger alerts
- Vulnerability management: Tone Shell likely requires certain vulnerabilities to be present on a system. Patch aggressively
- Application whitelisting: If you restrict what can execute on a system, you prevent many attack chains
- Privileged access management: Limit who has administrative access, reducing the attack surface
Supply Chain Security
Kernel-mode driver deployment requires code-signing certificates. These come from somewhere. Organizations should:
- Monitor certificate usage: Track which certificates are being used to sign drivers on your systems
- Validate certificate sources: Verify that drivers are signed by the company that actually wrote them
- Revoke compromised certificates: When a certificate is stolen or leaked, certificate authorities can revoke it
- Implement driver signing policies: Require that only drivers signed by specific, trusted authorities load
Network Monitoring: Detecting C2 Communication
Even sophisticated malware must communicate with attackers to receive commands and exfiltrate data. Network monitoring can detect this:
- Known IOCs: Block the specific IP addresses and domains associated with Mustang Panda's infrastructure
- DNS monitoring: Unusual DNS queries or queries to newly registered domains can indicate C2 communication
- Encrypted traffic analysis: Even if traffic is encrypted, patterns (size, timing, frequency) can reveal malware communication
- Outbound connection policies: Government networks shouldn't allow arbitrary outbound connections. Whitelist necessary external destinations
Incident Response Preparation
If (when) an infection occurs, preparation makes all the difference:
- Isolation procedures: Know how to immediately disconnect a system from the network
- Forensic readiness: Have tools and trained personnel ready to capture memory dumps and preserve evidence
- Containment: Understand how the malware spreads (USB via Tone Disk, network shares via Plug X) and plan containment
- Communication protocols: Establish secure channels for reporting infections and coordinating response
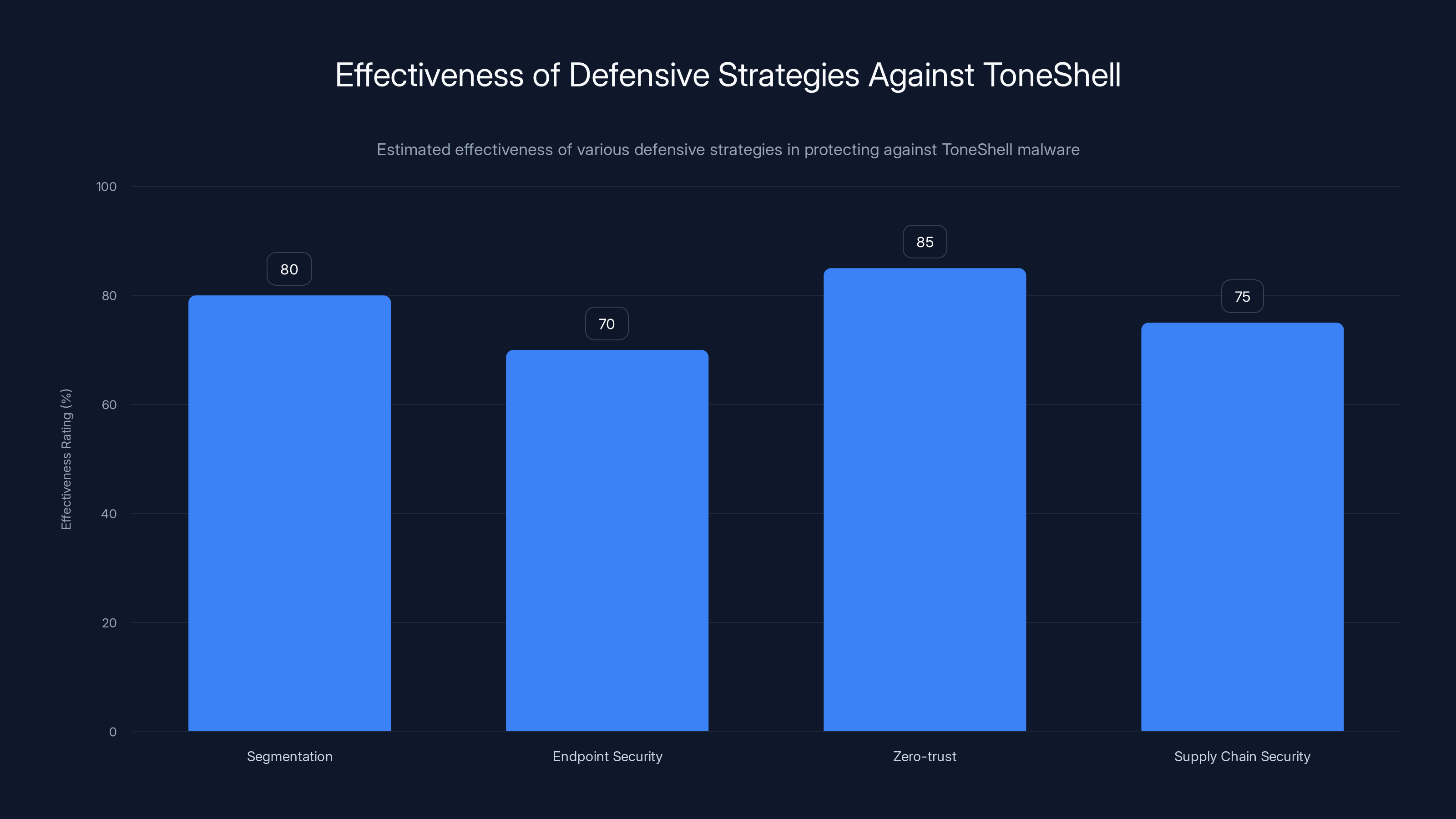
Zero-trust architecture is estimated to be the most effective strategy against ToneShell, with an 85% effectiveness rating. Estimated data.
The Role of Threat Intelligence and Information Sharing
One of the most valuable defensive tools is threat intelligence. When Kaspersky or other security firms discover attacks, they share indicators and analysis. Organizations should leverage this.
Consuming Threat Intelligence
Government organizations should subscribe to threat intelligence feeds that include:
- Indicators of Compromise: File hashes, IP addresses, domains, registry keys
- Behavioral signatures: Rules detecting Tone Shell-like behaviors
- Tactical analysis: Understanding what the malware does
- Strategic analysis: Understanding who's behind it and what they want
Feed sources include commercial vendors (Kaspersky, Crowd Strike, Mandiant), government agencies (NSA, CISA), and information sharing groups.
Contributing Intelligence
Organizations that discover attacks should report them:
- To vendors: Alert your endpoint protection vendor about new malware variants
- To government agencies: Government security agencies maintain teams dedicated to threat analysis
- To information sharing groups: Industry and government-specific groups share threat data
This creates a virtuous cycle where detection helps everyone. If one government detects Tone Shell, it can warn others.

The Broader Context: Nation-State Cyber Operations
Tone Shell doesn't exist in isolation. It's part of a broader ecosystem of nation-state cyber operations. Understanding this context is important for risk assessment.
The Proliferation of Sophisticated Malware
Tech like kernel-mode malware was historically exclusive to sophisticated threat actors. But as malware is discovered, analyzed, and shared, techniques proliferate. What Mustang Panda pioneered becomes knowledge available to other groups.
This means defenses must anticipate not just current threats but future ones. The kernel-mode rootkit techniques used against Asian governments today may be adopted by cybercriminal groups targeting private sector tomorrow.
The Attribution Problem
While security researchers attribute Tone Shell's deployment to Mustang Panda, attribution in cybersecurity is probabilistic. Attackers deliberately use each other's tools to create confusion. A government might use a criminal group's malware to avoid attribution.
However, the pattern of targeting, the specific malware families used, and the operational characteristics all align with known Mustang Panda behavior. Attribution is likely accurate, but perfect certainty isn't possible.
Escalation Potential
This campaign also illustrates a concerning trend: the sophistication of cyber weapons continues to increase. Kernel-mode malware deployed via signed drivers represents a significant escalation from previous Tone Shell variants.
Each generation of malware is more sophisticated, more stealthy, and harder to defend against. Organizations must keep pace or risk falling behind.
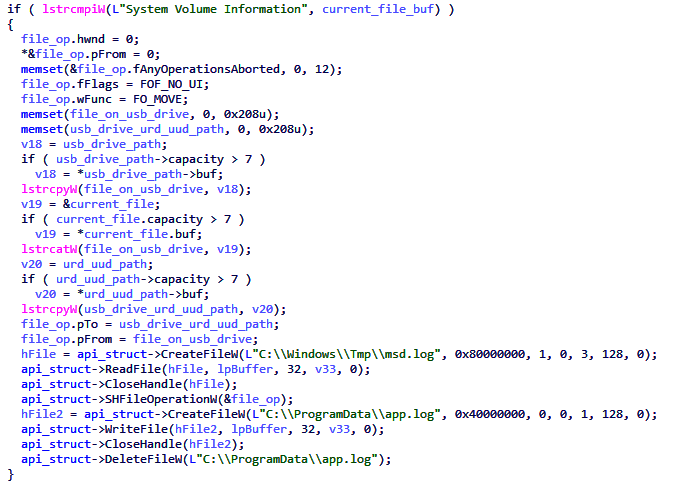
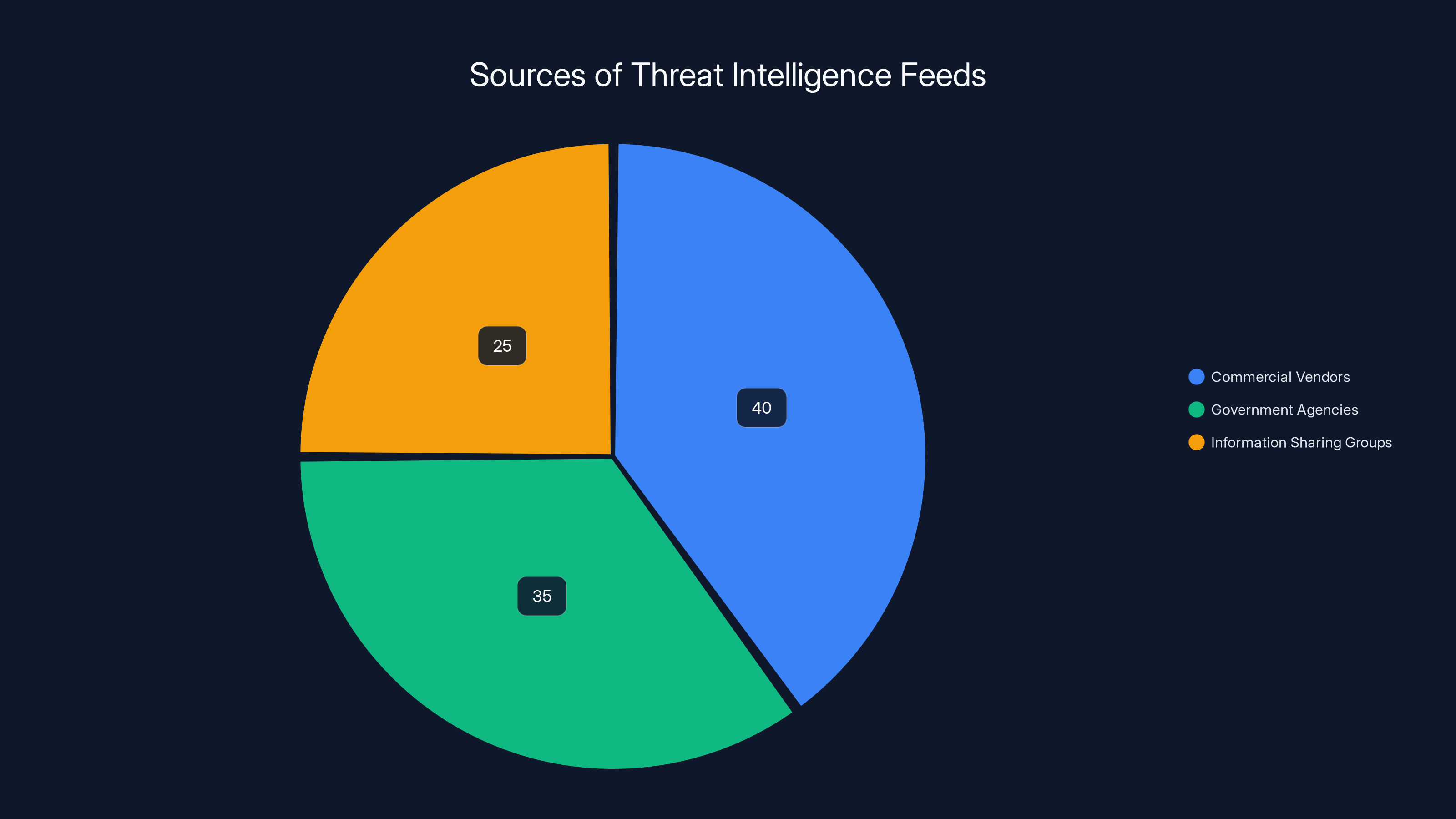
Commercial vendors are the largest source of threat intelligence feeds, followed by government agencies and information sharing groups. Estimated data.
Future Developments and Evolution
Tone Shell will continue to evolve. Based on historical patterns, future variants likely will include:
Potential Technical Evolutions
- Firmware-level persistence: Moving beyond kernel mode to UEFI/BIOS level, ensuring persistence even after operating system reinstallation
- Hardware implants: Moving attacks to network hardware, allowing persistence independent of the main operating system
- AI-enabled evasion: Machine learning to generate new variants that evade detection signatures
- Advanced obfuscation: Code that analyzes its environment and modifies itself to hide better
Potential Targeting Evolution
- Private sector expansion: While currently focused on government, Mustang Panda may target private sector organizations in strategic industries
- Geographic expansion: Operations may expand beyond Asian governments to include Western government targets
- Supply chain attacks: Using compromised software vendors to distribute malware at scale
Defensive Evolution
The security community will respond with:
- Firmware attestation: Ensuring that BIOS and UEFI haven't been modified
- Hypervisor-based security: Running security tools in privileged containers that even kernel-mode malware can't escape
- Hardware-backed security: Using processor features to isolate and protect sensitive operations
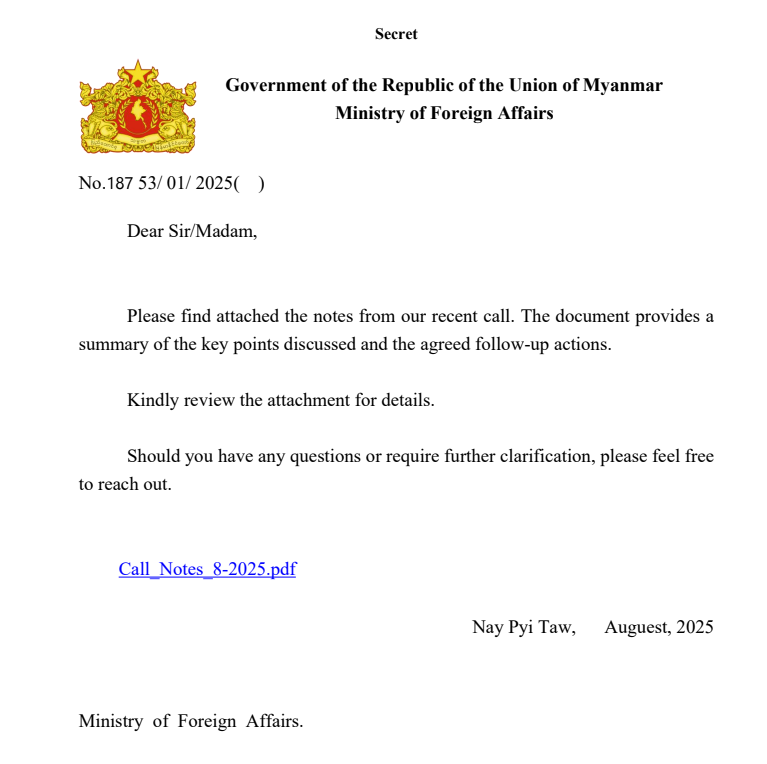
Case Study: Impact on Targeted Organizations
While Kaspersky didn't release detailed case studies of specific organizations, we can infer the likely impact based on similar breaches:
Immediate Impacts
- Operational disruption: Detection and response consume significant resources and operational capacity
- Data exfiltration: Sensitive documents and communications are likely copied and exfiltrated
- System instability: Complex malware can cause system crashes and performance degradation
Medium-Term Impacts
- Trust erosion: If communications are compromised, officials must assume past conversations may be monitored
- Policy leakage: Negotiating positions revealed to adversaries lose their strategic advantage
- Personnel vulnerabilities: If personal credentials are stolen, individuals become targets for blackmail or social engineering
Long-Term Impacts
- Operational changes: Organizations modify how they conduct sensitive operations to account for presumed monitoring
- Technology investment: Recovery from breach typically requires significant investment in new security infrastructure
- Institutional learning: Organizations develop processes to prevent similar breaches in future

Best Practices for Government Organizations
Based on the Tone Shell campaign, government organizations should implement:
Immediate Actions (0-30 days)
- IOC scanning: Use provided indicators to scan all systems for Tone Shell components
- Memory forensics: On systems with suspected compromise, collect memory dumps
- Network blocking: Block known C2 infrastructure at perimeter
- Patch critical vulnerabilities: Ensure all systems are patched
- Threat briefing: Ensure all security personnel understand the threat
Short-Term Actions (1-3 months)
- Kernel driver review: Audit all loaded kernel drivers for legitimacy
- Mini-filter inspection: Review file system filter stack for suspicious entries
- EDR deployment: If not already deployed, implement endpoint detection and response
- Network segmentation: Implement microsegmentation to limit lateral movement
- Incident response planning: Develop Tone Shell-specific response procedures
Long-Term Actions (3-12 months)
- Zero-trust implementation: Redesign network to operate under zero-trust principles
- Advanced threat hunting: Conduct proactive hunting for indicators of compromise
- Threat intelligence program: Establish processes for consuming and contributing threat intelligence
- Security awareness: Train personnel on spear-phishing and social engineering tactics
- Continuous monitoring: Implement systems for continuous detection and response

FAQ
What is the Tone Shell backdoor?
Tone Shell is a sophisticated backdoor malware deployed by Chinese state-sponsored threat actors (Mustang Panda) to establish persistent remote access to compromised systems. The new 2025 variant operates in kernel mode, giving it elevated privileges and the ability to hide from user-mode security tools and antivirus software. It enables attackers to execute commands, transfer files, and monitor system activity.
How does the Tone Shell attack work?
The attack chain begins with spear-phishing emails targeting government officials. Once a target opens a malicious attachment or clicks a link, initial payloads are executed. These downloaders fetch a signed mini-filter kernel-mode driver that installs Tone Shell alongside it. The kernel-mode components tamper with Windows Defender and hide their presence, while Tone Shell establishes remote command channels. Additional malware like Plug X and Tone Disk are deployed for expanded capabilities and persistence.
What makes the new Tone Shell variant different from older versions?
The critical difference is kernel-mode delivery via signed mini-filter drivers. Previous Tone Shell variants operated in user mode, where antivirus software could detect them relatively easily. The new variant leverages stolen or leaked code-signing certificates to load as a legitimate kernel-mode component. This gives it system-level privileges, enabling it to disable Windows Defender, hide its own presence, and resist detection by conventional security tools.
Who is Mustang Panda and why do they target government organizations?
Mustang Panda is a Chinese state-sponsored advanced persistent threat (APT) group that has operated since at least 2017. They conduct cyber-espionage campaigns targeting government organizations, typically in Asia, to gather intelligence on political decision-making, military capabilities, trade negotiations, and diplomatic communications. This intelligence provides strategic advantage in international relations and regional conflicts.
How can organizations detect Tone Shell infections?
Memory forensics is the most reliable detection method, requiring capture and analysis of system RAM to identify kernel-mode drivers and suspicious activity. Organizations should also use indicators of compromise (IOCs) provided by security researchers, including file hashes, network indicators, and registry entries. Network monitoring for known command and control infrastructure and behavioral analysis of suspicious process creation and driver loading can also reveal infections. However, detecting kernel-mode malware is inherently challenging because it operates at the same privilege level as detection tools.
What defensive measures prevent Tone Shell infection?
Defenses include assumption of breach architecture with network segmentation, privileged access management to limit administrative account usage, modern endpoint detection and response (EDR) tools, vulnerability management and patch management programs, driver signing policy enforcement, network monitoring and traffic analysis to detect command and control communication, and incident response procedures specifically designed for kernel-mode malware. No single defense is sufficient; layered defenses significantly increase the difficulty and cost of successful attacks.
What should organizations do if they detect a Tone Shell infection?
First, isolate the infected system from the network immediately to prevent lateral movement. Preserve memory dumps and disk evidence for forensic analysis. Notify relevant government agencies and threat intelligence partners. Expand scanning to look for other infected systems using the IOCs. Assume that any sensitive data on the infected system has been compromised and take appropriate protective measures. Conduct forensic analysis to determine what was accessed and exfiltrated. Finally, develop long-term remediation plans that include replacing hardware if necessary and reviewing all security controls.
Can Tone Shell be removed from an infected system?
Complete removal is extremely difficult. Because Tone Shell operates in kernel mode and can hide from tools that run in user mode, traditional malware removal procedures often fail to completely eliminate it. In most cases, security professionals recommend complete system replacement: backing up only essential data (with careful scanning), reinstalling the operating system from known-good media, and restoring data. This ensures complete removal of any rootkit components that might be hiding. Simply removing the visible malware files is insufficient because kernel-mode components remain.
Why is Windows Defender tampering such a serious capability?
Windows Defender is a last-line defense against malware. Many organizations, particularly government agencies with limited IT budgets, rely on it as their primary or only antivirus protection. A backdoor that can prevent Windows Defender from loading or functioning essentially removes this protective layer. This enables other malware to persist on systems without detection. Additionally, preventing Defender from scanning infected systems allows Tone Shell to hide among other malicious code that would normally be detected.
What is the threat to organizations outside of Asia?
While the current campaign targets Asian governments, Tone Shell and similar techniques represent a broader threat to government, critical infrastructure, and private sector organizations worldwide. The sophistication of kernel-mode delivery mechanisms, once developed, can be adapted to target other regions. Additionally, if Tone Shell components or code are leaked or stolen, cybercriminal groups may deploy them. Organizations in all regions should consider this threat relevant and implement appropriate defenses.

Conclusion: The Evolving Landscape of Nation-State Cyber Operations
The Tone Shell backdoor campaign represents a significant milestone in the evolution of nation-state cyber operations. It demonstrates not just technical sophistication, but strategic intent to gather intelligence on target governments over extended periods.
What's particularly concerning is how Tone Shell illustrates the convergence of multiple advanced techniques. Spear-phishing for initial compromise. Multi-stage payload delivery. Kernel-mode malware for stealth. Rootkit capabilities for persistence and evasion. Additional tools for flexibility. This isn't random malware. It's engineered, refined, and deployed with clear objectives.
For security professionals and government decision-makers, this threat requires serious attention. Detection is possible but difficult. Prevention is possible but requires significant investment in security infrastructure and practices. Recovery from infection is time-consuming and costly.
The broader message is this: if you're in government, critical infrastructure, or work with sensitive information, nation-state threats like Tone Shell are not theoretical. They're operating now, targeting organizations like yours. The appropriate response isn't panic, but preparation.
Prepare your defenses. Segment your networks. Invest in detection capabilities. Establish incident response procedures. Consume threat intelligence. Participate in information sharing. These actions won't guarantee prevention of compromise, but they significantly reduce your risk and improve your ability to respond when compromise occurs.
The cybersecurity landscape will continue to evolve. New techniques will emerge. Old defenses will become obsolete. But organizations that embrace continuous improvement, layered defenses, and assumption of breach will remain secure even as threats advance. The alternative is to accept inevitable compromise and hope you can detect and respond before critical damage occurs.
Choose preparation.

Key Takeaways
- ToneShell is a sophisticated backdoor deployed by Chinese state-sponsored Mustang Panda targeting Asian government organizations since February 2025, providing persistent remote access and espionage capabilities
- The new ToneShell variant uses signed kernel-mode mini-filter drivers to operate with system-level privileges, enabling it to hide from antivirus software and tamper with Windows Defender
- Kernel-mode malware can manipulate processes, hide files, intercept network traffic, and disable security tools, making detection significantly more difficult than user-mode malware
- Memory forensics is the most reliable detection method for ToneShell because kernel-mode malware can hide from file system and process monitoring, but must exist somewhere in RAM
- Defense requires layered approaches including network segmentation, privileged access management, behavioral monitoring, incident response procedures, and threat intelligence sharing rather than relying on any single security tool
Related Articles
- AWS CISO Strategy: How AI Transforms Enterprise Security [2025]
- Rainbow Six Siege Server Shutdown: Marketplace Hack Explained [2025]
- Essential Cybersecurity Habits for 2026: Expert Guide [2025]
- The Worst Hacks of 2025: A Cybersecurity Wake-Up Call [2025]
- 9 Game-Changing Cybersecurity Startups to Watch in 2025
- Aflac Data Breach: 22.6 Million Exposed [2025]
![ToneShell Backdoor: Inside the Chinese Government Espionage Campaign [2025]](https://tryrunable.com/blog/toneshell-backdoor-inside-the-chinese-government-espionage-c/image-1-1767116175099.jpg)



