TP-Link Texas Lawsuit: Chinese Hackers, Security Lies, and What It Means [2025]
Something went really wrong with TP-Link's routers. And when I say wrong, I mean the kind of wrong that gets a state attorney general to file a lawsuit claiming the company knowingly allowed Chinese hackers to access millions of American devices.
In early 2025, Texas Attorney General Ken Paxton announced a lawsuit against TP-Link that cuts straight to the heart of a problem nobody wants to think about: the networking equipment sitting in your closet right now might be giving foreign intelligence agencies a direct line into your home network. The lawsuit isn't about rumors or vague concerns. It's specific, detailed, and grounded in documented security vulnerabilities that exposed American consumers to what state officials are calling "severe cybersecurity risks" according to Engadget.
Here's what actually happened, why it matters more than you think, and what you should do about it if you own one of their routers.
TL; DR
- Texas AG Ken Paxton filed a lawsuit against TP-Link claiming the company concealed security vulnerabilities and allowed Chinese hacking groups access to router devices as reported by Engadget.
- Firmware vulnerabilities exposed millions of American consumers to cybersecurity risks through documented flaws in TP-Link hardware as noted by SecurityWeek.
- The company's China connection runs deeper than marketed: TP-Link claims it's Vietnamese-owned and assembled, but supply chains and ownership structures allegedly remain tied to China's data laws according to Bloomberg Law.
- Federal investigations preceded state action: TP-Link routers were connected to the massive Salt Typhoon hack targeting U. S. telecom companies in 2024 as reported by CyberPress.
- Security concerns span years: The investigation started in October 2025, but vulnerabilities have existed in TP-Link products for much longer than publicly acknowledged according to Engadget.

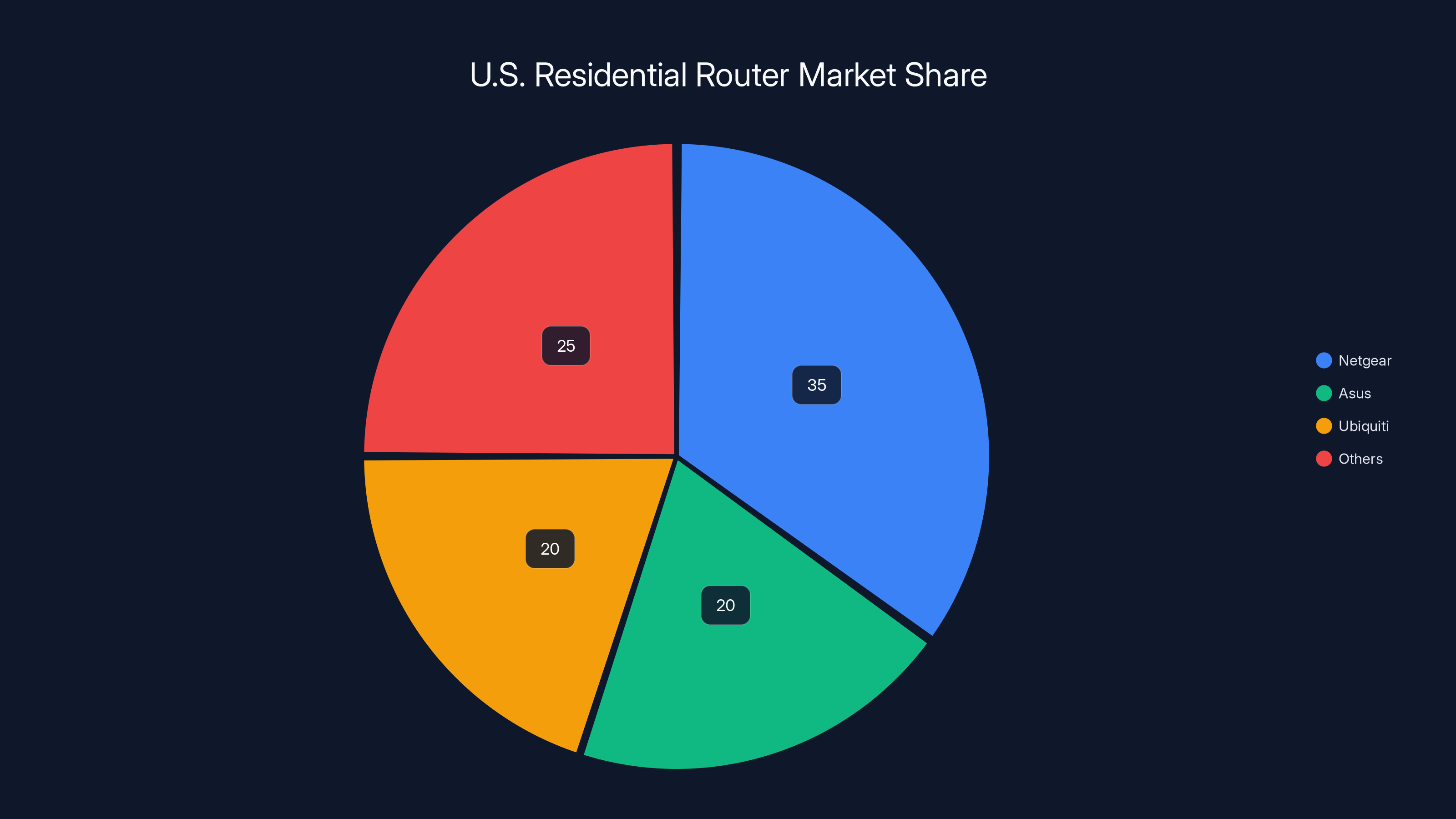
If TP-Link exits the U.S. market, competitors like Netgear, Asus, and Ubiquiti are likely to capture its 25% market share, leading to a more concentrated market. (Estimated data)
The Lawsuit: What Texas Actually Alleges Against TP-Link
Texas Attorney General Ken Paxton didn't file this lawsuit casually. The complaint alleges something far more serious than a minor security oversight. According to the lawsuit, TP-Link has been engaging in deceptive marketing practices by publicly claiming its routers are secure while simultaneously allowing known vulnerabilities to persist in the firmware—vulnerabilities that Chinese hacking groups actively exploited as reported by Engadget.
The specific allegations center on three interconnected problems. First, TP-Link marketed its products as secure without disclosing that firmware vulnerabilities existed and were being actively exploited. Second, the company didn't properly patch these vulnerabilities in a timely manner, even after becoming aware of them. Third, the company's ownership structure and supply chain connections to China meant that, regardless of where routers were assembled or technically owned, TP-Link remained subject to China's national security laws requiring cooperation with intelligence agencies according to Reuters.
This third point is crucial because it changes the entire calculus. It's not just that TP-Link's routers were insecure. It's that the company's legal obligations under Chinese law meant it couldn't refuse requests from Chinese intelligence agencies if they demanded access to network data or backdoor access to devices. Whether TP-Link actually granted such access doesn't matter as much as whether it was legally obligated to—and whether it disclosed that obligation to American customers.
The lawsuit timeline is also revealing. Paxton's office began investigating TP-Link in October 2025, months after the Salt Typhoon hack became public. But Texas Governor Greg Abbott's decision in January 2026 to prohibit state employees from using TP-Link products suggests state officials had already seen enough evidence to warrant drastic action. A state-level ban is rare and signals genuine concern, not political theater according to Engadget.

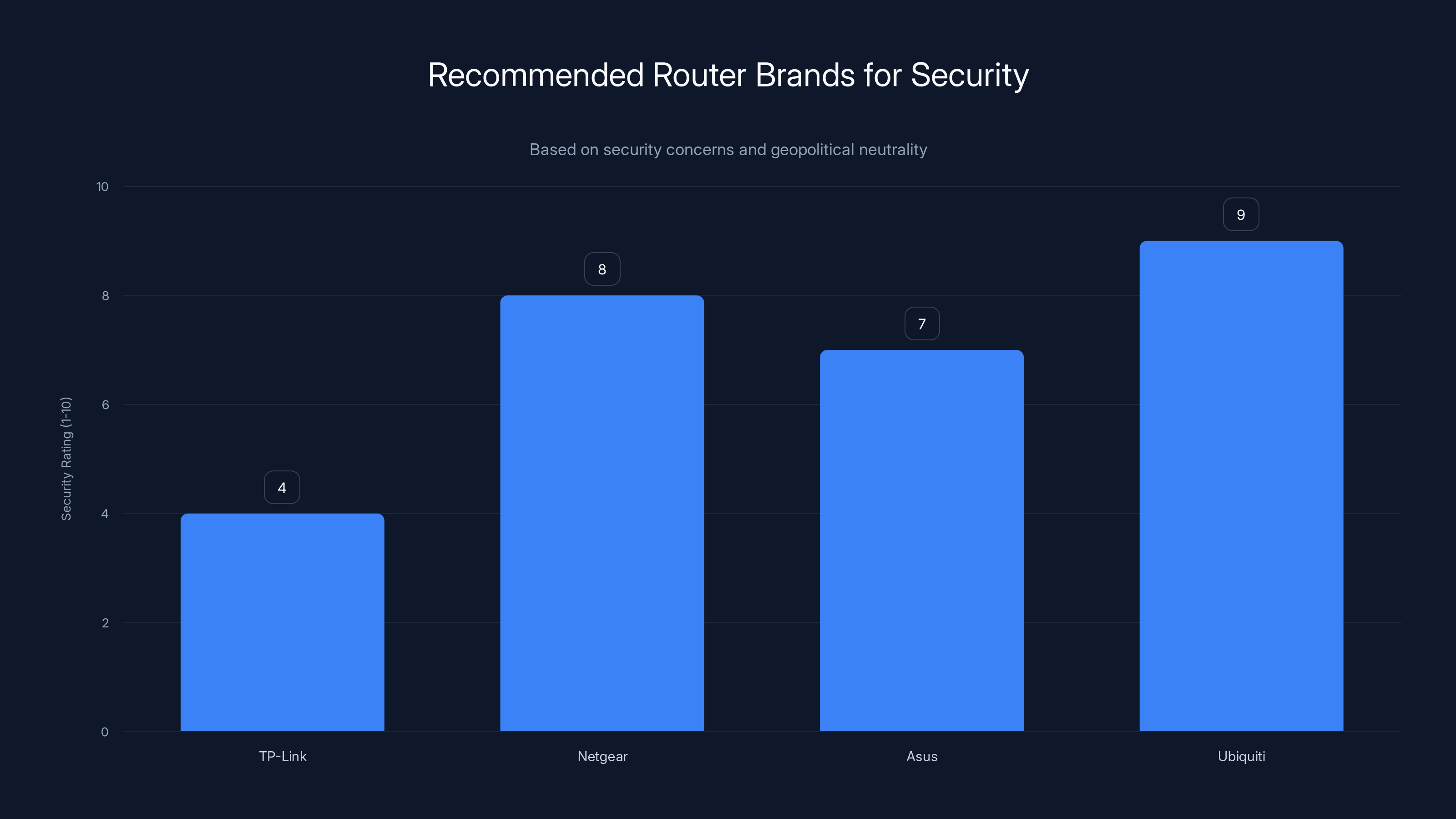
Netgear, Asus, and Ubiquiti are recommended for better security and geopolitical neutrality compared to TP-Link. Estimated data.
The Salt Typhoon Connection: How TP-Link Became a National Security Concern
Understanding the Texas lawsuit requires understanding Salt Typhoon, one of the most significant cybersecurity incidents of 2024. This wasn't a ransomware attack or a targeted breach. Salt Typhoon was a sophisticated, multi-month intrusion campaign that compromised the networks of multiple major U. S. telecom companies, giving attackers access to call records, location data, and other sensitive communications as reported by SC World.
What made Salt Typhoon particularly alarming was the skill level required. This wasn't script kiddies running automated exploits. This was advanced persistent threat activity—the kind of operation that requires nation-state resources, patience, and specific targeting knowledge. U. S. cybersecurity agencies quickly attributed Salt Typhoon to Chinese state-sponsored hackers, specifically groups operating under the direction of Chinese intelligence services as noted by Engadget.
TP-Link routers became a component of this attack chain. How? The routers contained known vulnerabilities that allowed remote code execution. An attacker with access to the internet could exploit these flaws to gain administrative control over the router without authentication. From there, they could eavesdrop on network traffic, redirect communications, or use the router as a pivot point to attack other devices on the network as detailed by SecurityWeek.
The timing here is important. TP-Link didn't patch these vulnerabilities immediately after Salt Typhoon became public. In fact, security researchers documented that many devices remained vulnerable even after patches were released, because TP-Link's update mechanism was inconsistent, and many users didn't know updates were available. Some older router models never received patches at all according to CyberPress.
This is where Paxton's lawsuit gains real legal teeth. The Texas AG isn't just arguing that TP-Link made insecure products. He's arguing that TP-Link made insecure products, knew about the vulnerabilities, failed to communicate the risks to consumers, and then failed to patch those vulnerabilities in a reasonable timeframe. That pattern of behavior constitutes deceptive advertising and consumer protection violations under Texas law as reported by Engadget.

TP-Link's Ownership Structure: The China Problem That Never Went Away
Here's where the lawsuit gets interesting from a legal and geopolitical standpoint. TP-Link has been owned by Vietnamese interests for years now, and the company manufactures products primarily in Vietnam, not China. On paper, this makes TP-Link a Vietnamese company. But Paxton's lawsuit argues that the ownership structure is more complicated than TP-Link's public statements suggest as noted by Bloomberg Law.
According to the complaint, TP-Link's ownership and supply chain remain "tied to China" in ways that subject the company to Chinese national security laws. These laws are not optional. Under China's National Security Law and related legislation, companies operating in China or with Chinese ownership stakes can be compelled to cooperate with Chinese intelligence agencies. This doesn't require a warrant or judicial review. It requires only a determination by the Chinese government that the request serves national security interests according to Reuters.
What does this mean practically? It means that if Chinese intelligence agencies wanted access to TP-Link devices—whether for targeted surveillance of specific individuals, bulk collection of network metadata, or insertion of persistent backdoors—TP-Link would have no legal recourse to refuse. The company couldn't go to court. It couldn't appeal the request. It couldn't even publicly disclose that the request had been made.
Texas's allegation isn't that TP-Link definitely cooperated with Chinese intelligence. Rather, it's that TP-Link's legal structure meant it could be compelled to cooperate, and this fact was never disclosed to American consumers buying routers under the assumption that they were getting a product from a Vietnamese company with normal privacy protections as reported by Engadget.
There's a separate issue here about corporate transparency. TP-Link could have been forthright about its ownership structure and supply chain ties. Instead, the company's marketing materials generally emphasized the Vietnamese manufacturing without explicitly discussing the broader ownership structure. This distinction matters in court because it suggests deceptive omission—telling customers something true but incomplete to avoid discussing something problematic.
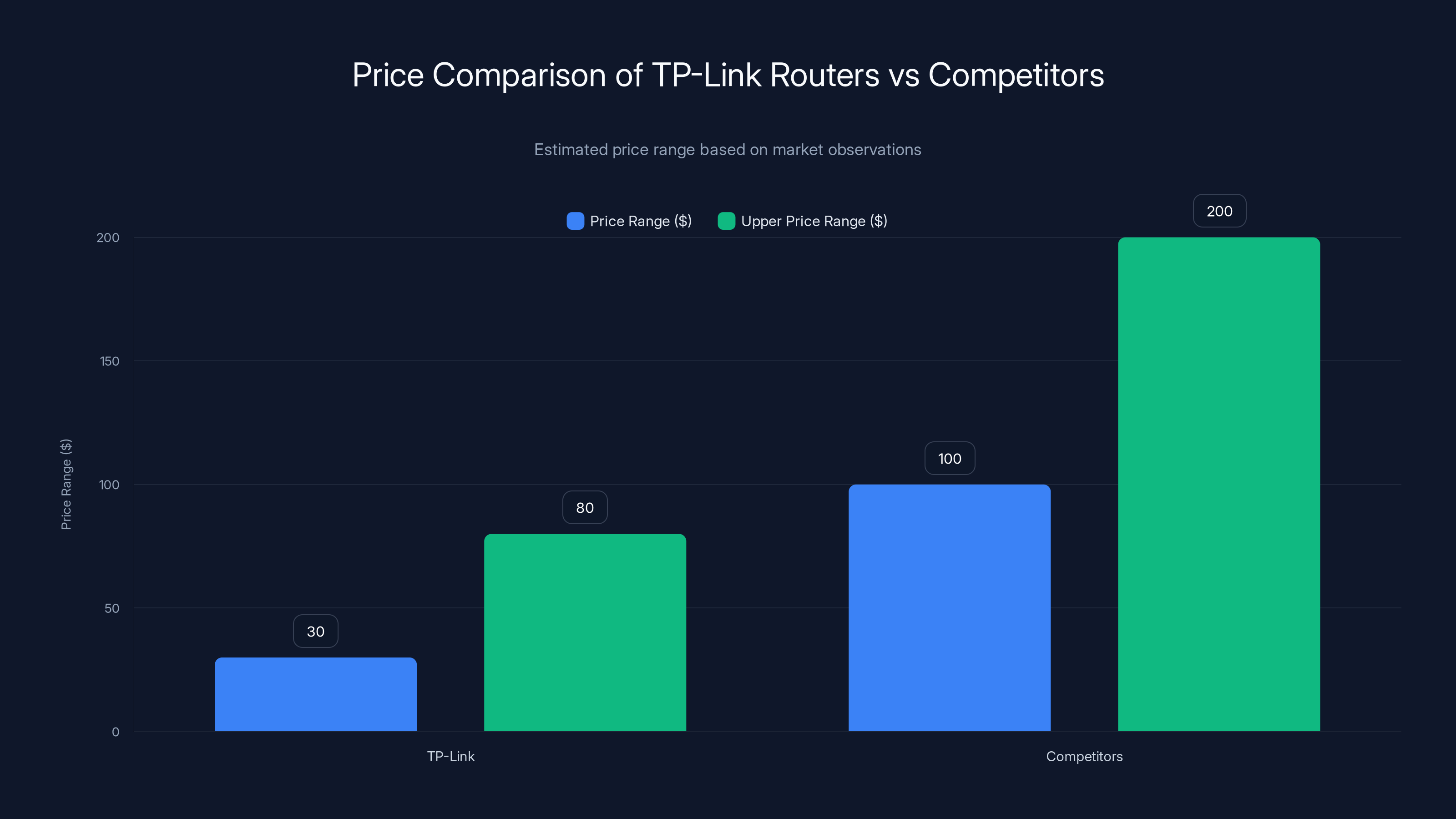
TP-Link routers are priced significantly lower (
Firmware Vulnerabilities: The Technical Reality Behind the Lawsuit
Let's get into the actual security flaws. The lawsuit references "firmware vulnerabilities" without explaining exactly what they are, but security researchers have documented multiple critical flaws in TP-Link routers across multiple product lines as detailed by SecurityWeek.
One category of vulnerability that appears in multiple TP-Link models is improper authentication handling. This means the router's administrative interface can be accessed by attackers who don't know the admin password. In some cases, the vulnerability allows unauthenticated remote code execution—an attacker can exploit the flaw to run arbitrary code on the device without any credentials at all.
Another class of vulnerability involves improper access controls in management interfaces. TP-Link routers often expose debugging endpoints or development interfaces that were never meant to be internet-facing. But due to misconfiguration or incomplete hardening, these endpoints remain accessible. An attacker who finds these interfaces can extract configuration data, modify settings, or gain shell access to the device according to CyberPress.
A third category involves weak encryption or credential handling. Some TP-Link models were documented storing administrative credentials in plaintext or using default passwords that couldn't be changed. Others used hardcoded credentials that appeared in firmware but were never documented—credentials that security researchers could extract and use to access devices as reported by SC World.
Why do these vulnerabilities matter so much? Because your router isn't just a networking device. It's a gateway to your entire network. Every device in your home—your computer, phone, smart TV, smart home devices—communicates through the router. If an attacker compromises the router, they can see all that traffic. They can modify it. They can inject malicious code. They can redirect your traffic to fake versions of websites you're trying to visit. They can harvest passwords, credit card numbers, and sensitive data.
For a sophisticated attacker working for a nation-state, an unpatched router vulnerability is incredibly valuable. It provides persistent access to the network without the target knowing anything is wrong. Unlike a phishing attack, there's no user action required. The vulnerability is silently exploitable as noted by Engadget.
The Timeline: October 2025 to February 2026
The lawsuit didn't emerge from nowhere. The timeline reveals how concerns escalated through 2025 and into 2026.
In October 2025, Ken Paxton's office opened an investigation into TP-Link. What triggered the investigation? The timing suggests it was the Salt Typhoon disclosure and the growing recognition that TP-Link routers played a role in the attack chain. Federal cybersecurity agencies had already started examining TP-Link's security posture and documenting exploitable vulnerabilities as reported by Engadget.
By January 2026, Texas Governor Greg Abbott had seen enough. He issued a directive prohibiting state employees from using TP-Link products on any state networks or devices. This wasn't a suggestion. It was a ban. It meant state agencies had to replace TP-Link routers, remove them from networks, and source alternatives. For a consumer product company, having an entire state government refuse to use your products is devastating from both a security standpoint and a business standpoint according to Engadget.
Then in February 2026, Paxton filed the lawsuit. The allegations were specific enough and the evidence strong enough that the Texas AG felt confident proceeding with legal action.
But here's the interesting part: around the same time, the Trump administration reportedly paused plans to ban TP-Link products federally. Reuters reported that in early February, Trump's team delayed a proposed federal ban ahead of a scheduled meeting between President Trump and President Xi Jinping. This suggests there was a federal ban proposal on the table—potentially a response to the Salt Typhoon incident and TP-Link's vulnerability issues as noted by Reuters.
The federal pause creates an odd situation. Texas is moving forward with legal action against TP-Link while the federal government is stepping back from restricting the company. This could reflect political considerations at the federal level, disagreement about the severity of the threat, or the complexity of banning products that are embedded in millions of American networks.

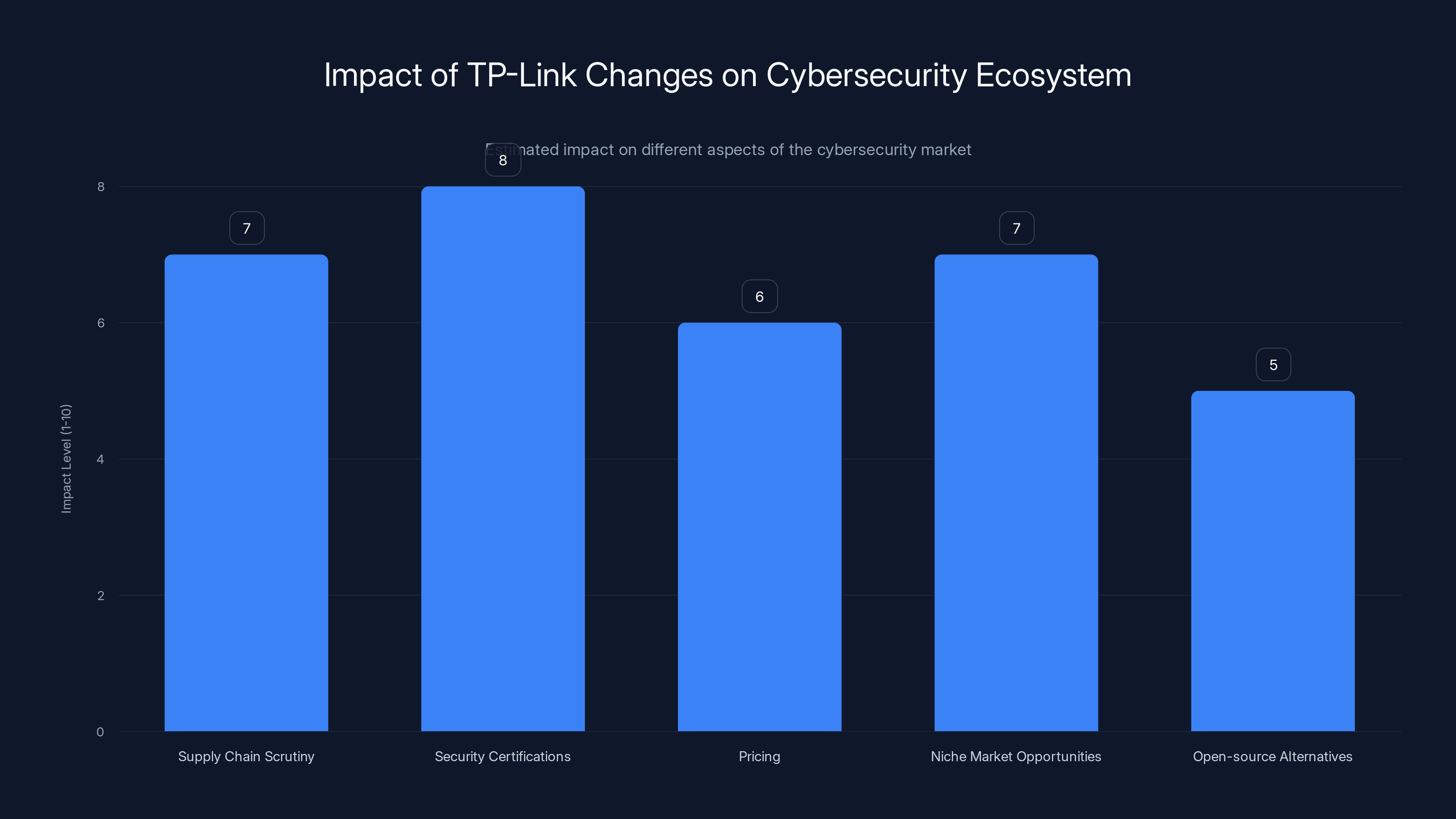
The potential changes in the cybersecurity ecosystem due to TP-Link's situation are significant, with increased scrutiny and emphasis on security certifications being the most impacted areas. (Estimated data)
National Security vs. Consumer Privacy: The Broader Implications
The TP-Link lawsuit touches on something much bigger than one company's security failures. It raises fundamental questions about how the United States should manage national security risks posed by network equipment manufactured or controlled by companies with ties to foreign governments.
This is the core tension: network equipment is national security infrastructure. The routers, switches, and firewalls that form the backbone of American communications networks are trusted with profound access to sensitive data. When those devices are manufactured by or have ownership ties to companies subject to Chinese national security laws, the potential for exploitation becomes unavoidable as noted by China Briefing.
China's approach to this problem is instructive. China restricts or bans many foreign networking products on security grounds, particularly from American companies like Cisco. China argues—credibly, from a security perspective—that allowing foreign companies to control critical network infrastructure creates unacceptable national security risks. The United States has historically been more open to foreign equipment, but TP-Link's issues are forcing a reevaluation according to Engadget.
The TP-Link lawsuit suggests the United States is moving toward a similar framework—carefully restricting products from companies with ties to adversarial governments, not because the companies are definitely cooperating with foreign intelligence, but because the legal and structural ties create unacceptable risk.
This has implications for consumers, businesses, and the broader technology ecosystem. If the United States restricts TP-Link products, it will benefit competitors like Netgear, Ubiquiti, and Asus—primarily companies with American or allied ownership. Prices might increase if competition decreases. Small businesses and budget-conscious consumers who have relied on TP-Link's affordability will face higher costs.
But from a national security perspective, the risk calculus might justify the cost. A single backdoored router in a critical infrastructure facility, hospital, or government office could have enormous consequences as noted by Engadget.

Why TP-Link Was So Vulnerable: Manufacturing and Support Issues
TP-Link didn't become vulnerable overnight. The company's security problems reflect deeper structural issues in how the company operates and supports its products.
First, there's the volume-over-security approach. TP-Link sells routers at aggressively low prices, often
TP-Link's solution was to optimize for volume. Sell millions of routers at low margins and prioritize getting new models to market quickly over hardening existing ones. This business model works fine until security becomes a serious liability—which it did with Salt Typhoon.
Second, there's the fragmentation problem. TP-Link doesn't make five router models. The company makes dozens. Each model has different firmware, different components, and different supply chains. When a vulnerability is discovered, patching requires developing a fix for each affected model. Then it requires verifying the fix works on each model. Then it requires distributing the patch through multiple channels—some customers receive updates through the web interface, others through cloud management systems, others never receive updates at all.
This fragmentation creates a moving target for security. An attacker might exploit a vulnerability in one model while patches are rolling out for another. Older models might never receive patches because they're no longer in TP-Link's development pipeline.
Third, there's weak update mechanisms. Many TP-Link routers don't automatically update. They rely on users to manually check for updates and install them. This is a security nightmare. Most users never check for updates. Most users don't even know updates exist. So vulnerabilities persist for years in devices that are still actively used, still actively exploited according to CyberPress.
A better approach—used by companies like Ubiquiti and even some budget-friendly brands—is to automatically update routers in the background, transparently, without user intervention. This ensures patches reach devices quickly and doesn't depend on user awareness.

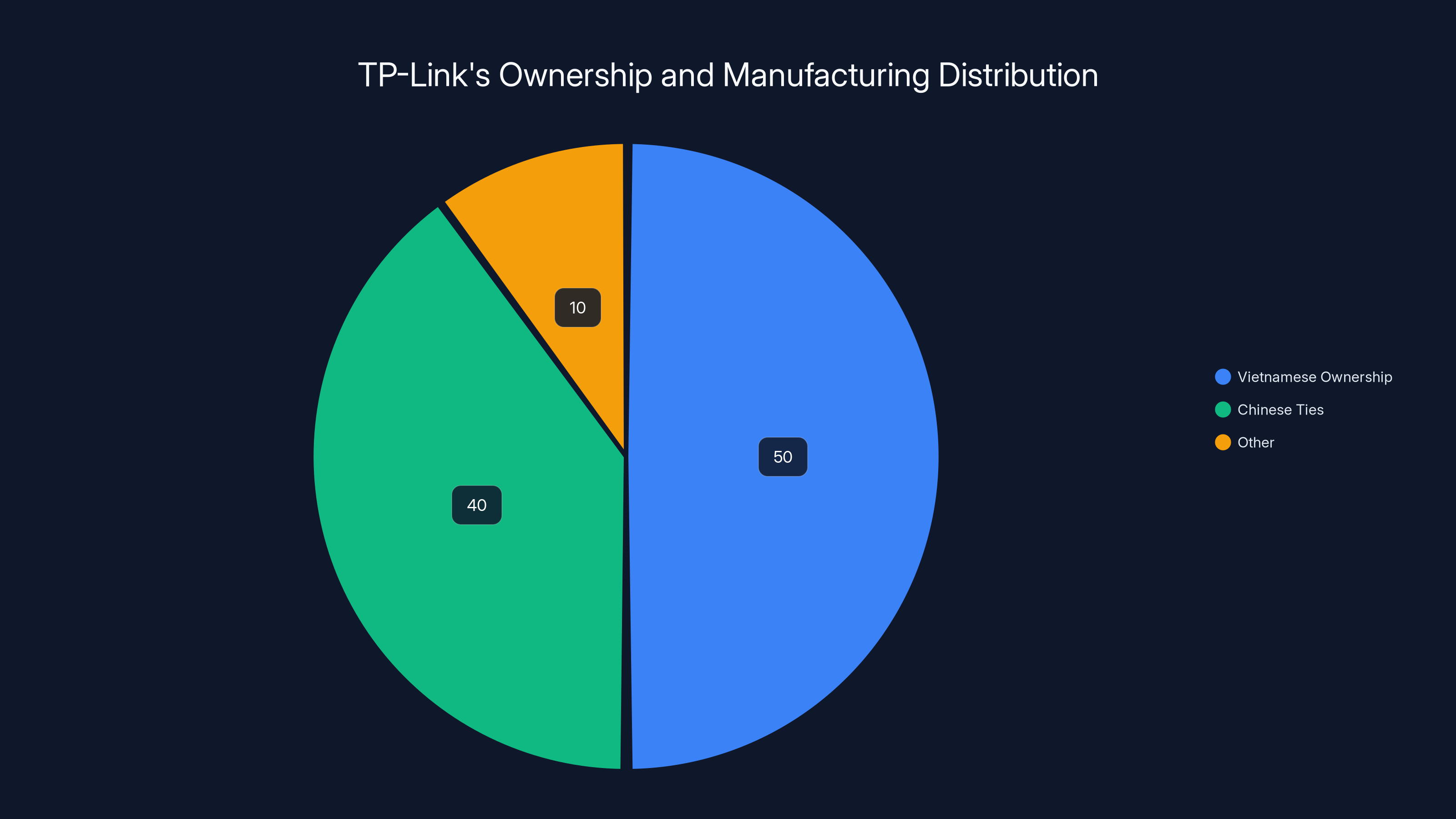
Despite being owned by Vietnamese interests, TP-Link has significant ties to China, estimated at 40%, which could subject it to Chinese national security laws. Estimated data.
The Salt Typhoon Attack: How Bad Was It?
To understand why Texas and federal officials are taking TP-Link so seriously, you need to understand Salt Typhoon's scope.
Salt Typhoon was not a targeted breach of a few accounts. It was a multi-month, sophisticated intrusion that compromised core infrastructure at multiple major U. S. telecom companies. The attack gave Chinese intelligence agencies access to call records, text message metadata, location information, and billing systems. It gave them the ability to intercept specific communications if they wanted as noted by Engadget.
For national security, this is extremely serious. Communications metadata—knowing who called whom and when—is nearly as valuable as call content. It reveals network patterns, relationships, and associations. If you know a U. S. defense contractor called a specific embassy seven times in one month, that's intelligence. If you know a political dissident's location based on cellular data for every day over six months, that's intelligence.
TP-Link routers appear to have been used as part of the attack infrastructure. The exact role is still partially classified, but security researchers have documented that TP-Link vulnerabilities were chained with other exploits to achieve initial network access. Once attackers had control of a router, they could pivot into larger networks as reported by SC World.
What makes this so significant is that routers are typically considered trusted infrastructure. Network security professionals assume routers are less likely to be compromised than endpoint devices. If an attacker has root access to the router, security is already lost, so administrators often focus defenses elsewhere. TP-Link vulnerabilities violated that assumption.

Competitive Landscape: What Happens to TP-Link's Market Share?
If TP-Link faces restrictions in the United States, the company's market position becomes untenable. TP-Link has approximately 25% market share in the U. S. residential router market. That's substantial. Losing that market would cost the company hundreds of millions in annual revenue as reported by RTINGS.
But more importantly, restrictions on TP-Link would reshape the entire market. Competitors like Netgear, Asus, and Ubiquiti would capture TP-Link's market share. Prices would likely increase since TP-Link has historically been a low-cost leader, driving competition on price.
For consumers, this means:
- Higher prices: Budget routers in the 80-100+
- Reduced competition: Three major competitors controlling 75%+ of the market means less innovation pressure
- Different feature sets: Budget routers traditionally emphasize reliability over features; more expensive alternatives emphasize gaming, smart home, or mesh capabilities
- Limited options for cost-conscious buyers: Small businesses, schools, and budget-conscious consumers would face harder choices
For TP-Link specifically, the company has two paths:
Option 1: Radical restructuring - TP-Link could entirely separate from any Chinese ownership or influence, move manufacturing to allied countries, and submit to regular security audits to prove it's genuinely independent. This would be expensive and take years.
Option 2: Exit the U. S. market - TP-Link could focus on markets where government restrictions aren't a problem: Europe, Latin America, Asia, Africa. The company would lose a huge market but wouldn't have to fundamentally restructure.
Neither option is attractive for TP-Link. But the company doesn't have many choices if the United States moves toward formal restrictions.

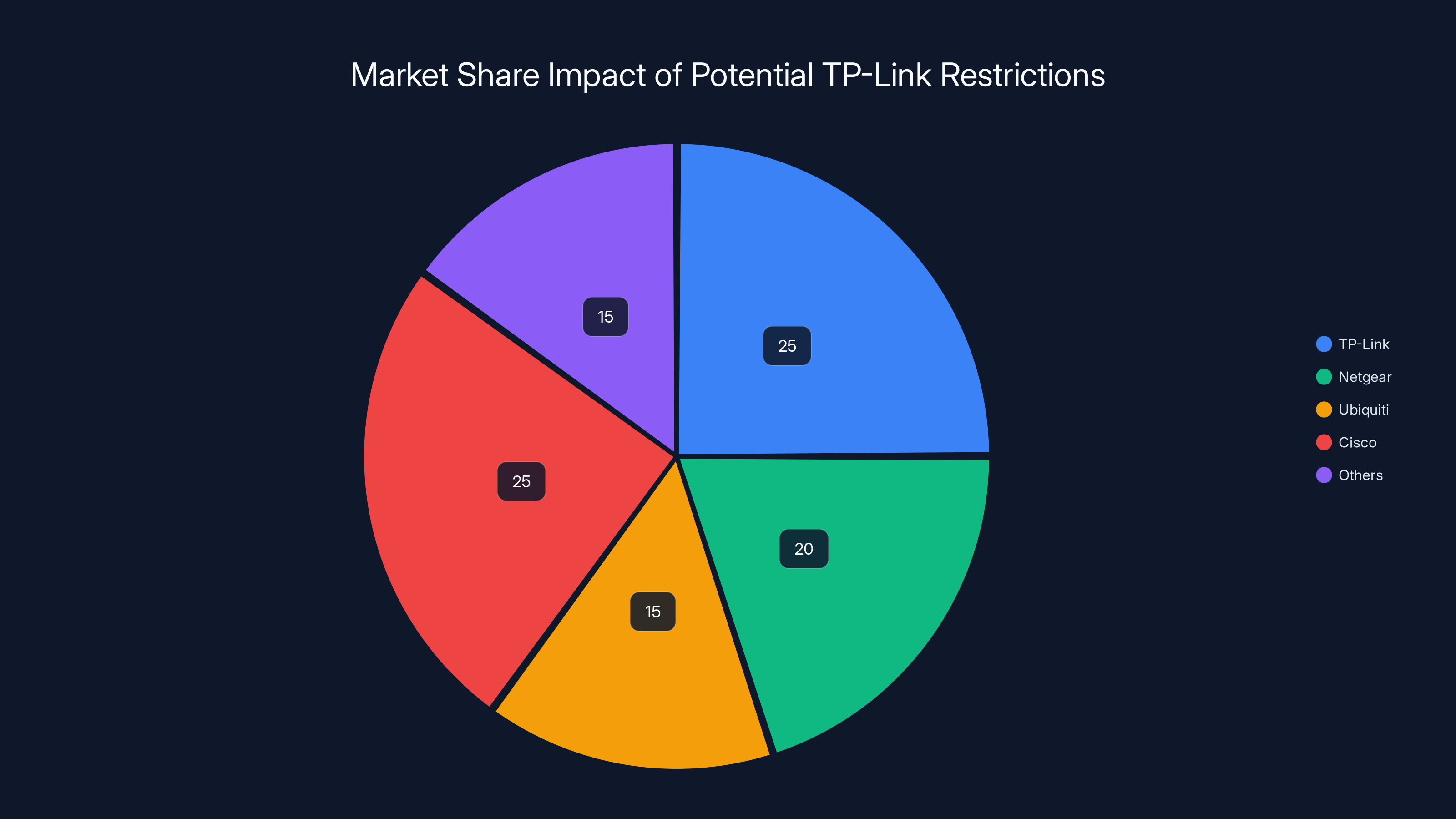
If the U.S. restricts TP-Link, competitors like Netgear and Ubiquiti could gain market share. Estimated data based on potential market shifts.
What the Lawsuit Means for Consumer Rights
From a consumer protection perspective, the Texas lawsuit establishes an important precedent. It says that companies can't simply claim security credentials without backing them up. If you market your router as "secure" while knowingly selling devices with exploitable vulnerabilities, you're violating consumer protection laws as reported by Engadget.
This matters beyond TP-Link. It sets expectations for security disclosure, patch timelines, and transparency about vulnerabilities. Other router manufacturers, software companies, and Io T device makers are watching this case carefully. If Paxton wins, expect increased pressure for all companies to be more transparent about security issues and more aggressive about patching.
For consumers who have already purchased TP-Link devices, the lawsuit doesn't automatically mean you're entitled to a refund or replacement. Class action lawsuits often emerge from cases like this, and those class actions sometimes result in settlement funds for affected consumers. But typically, consumers have to file claims, prove they purchased the product, and document any harm they suffered. This is administratively complex and most consumers don't bother.
What the lawsuit does do is create reputational damage for TP-Link and establish legal precedent that security claims matter. If TP-Link settles the case, the settlement will likely include requirements for improved security practices, more transparent communication, and potentially damages paid to the state of Texas as noted by Engadget.

The Geopolitical Dimension: U. S.-China Tech Competition
The TP-Link lawsuit is ultimately a proxy for a much larger conflict: the U. S.-China competition for technological dominance and control over critical infrastructure.
China has spent years positioning Chinese technology companies—Huawei, ZTE, DJI, and others—to dominate global markets. In many cases, these companies offer superior products at better prices. Huawei makes excellent telecom equipment. DJI dominates commercial drones. TP-Link makes reliable, affordable routers.
But there's a security cost. As these companies become embedded in American networks, they create vulnerability vectors that hostile actors can exploit. Some of that exploitation might be deliberate action by the Chinese government. Some might be inevitable consequences of architecture that wasn't security-hardened as noted by China Briefing.
The U. S. response has been a mix of defensive restrictions (limiting equipment from certain companies) and offensive investment (funding American alternatives). The TP-Link lawsuit is part of this broader effort to restrict Chinese companies from controlling critical infrastructure.
This has geopolitical consequences. If the U. S. effectively bans Chinese networking equipment, China will likely ban American networking equipment. Companies like Cisco, Juniper, and Arista would lose access to the Chinese market. Trade relationships would become more fragmented. Supply chains would become less efficient.
But the alternative—allowing potentially compromised equipment to control critical infrastructure—is arguably worse. It's a genuine security dilemma with no good options as reported by Engadget.

What Should You Do If You Own TP-Link Routers?
If you have a TP-Link router in your home or office, here's what the actual risk level looks like and what you should do about it.
Risk Assessment:
For most home users, the immediate risk of exploitation through a TP-Link router is relatively low. Most home users don't have data that would interest sophisticated nation-state actors. Your Netflix streaming history and email are valuable to marketers, not to intelligence agencies.
However, if your router is part of a network that includes sensitive data—if you work from home for a government contractor, defense firm, or sensitive industry—the risk is much higher. An attacker with access to your router could monitor your work communications, steal files being transmitted, or use your network as a pivot point into your employer's systems.
If you're a small business owner, the risk is moderate but real. Competitors using similar tools to access your network, monitor your operations, or steal customer data is plausible.
Immediate Actions:
-
Check your firmware version: Log into your TP-Link router's admin panel and note the current firmware version. Compare it to TP-Link's website to determine if you're running the latest version.
-
Update immediately: If updates are available, apply them. Most routers can be updated through the admin panel. If your model is extremely old and updates aren't available, that's a strong signal you should replace it.
-
Change your admin password: Even if your firmware is updated, ensure your admin password is strong and unique.
-
Monitor for unusual network activity: Check your router's connected devices list periodically. If you see devices you don't recognize, investigate.
-
Consider replacement: If you can afford it, replacing the router entirely is the most secure option. Buy a router from a manufacturer without geopolitical concerns: Netgear, Asus, or Ubiquiti.
Long-term Considerations:
Network security is evolving. The assumption that you buy a router once and use it for five years is becoming outdated. Expect that routers will require replacement every 2-3 years as vulnerabilities are discovered and patches become necessary.
Consider mesh systems from reputable manufacturers. Modern mesh routers like Eero, Google Nest, or Apple eero handle updates more automatically and systematically than traditional routers.

Industry Response and Damage Control
TP-Link has responded to the lawsuit with standard corporate deflection. The company claims it takes security seriously, that it patches vulnerabilities promptly, and that Texas's allegations are inaccurate. TP-Link has released public statements emphasizing that it's Vietnamese-owned and that its products are manufactured outside China as reported by Engadget.
But the company's actual actions have been less convincing. TP-Link hasn't been particularly transparent about the Salt Typhoon vulnerabilities, hasn't published detailed timelines of when vulnerabilities were discovered and when patches were released, and hasn't made any major changes to its security practices in response to the controversy.
From a public relations standpoint, TP-Link has a credibility problem. The company marketed its products as secure. Evidence suggests security was compromised. Trust is broken. No amount of standard corporate messaging repairs that.
What would actually help TP-Link's position:
-
Third-party security audits: Hire a reputable security firm to conduct independent audits of TP-Link's products and processes. Publish the results.
-
Radical transparency: Release detailed information about which vulnerabilities affected which products, when they were discovered, when patches were released, and what percentage of devices have been patched.
-
Structural changes: Announce concrete changes to the company's ownership and supply chain structure that eliminate ties to China. This would likely require significant investment and reorganization.
-
Settlement and restitution: Offer to replace affected devices or provide refunds to consumers who purchased TP-Link routers during the period when vulnerabilities existed.
However, TP-Link hasn't done any of these things at meaningful scale. The company's response has been defensive rather than remedial as noted by Engadget.

Federal Policy and Future Restrictions
The Texas lawsuit is happening in a broader context of federal policy moves against Chinese tech companies. The Trump administration has been more aggressive than the Biden administration on Chinese equipment restrictions, but both administrations have taken action.
The pause in federal TP-Link restrictions reported in February 2026 is interesting but may be temporary. Federal policy on critical infrastructure security typically survives administrations. Even if the Trump administration deprioritizes TP-Link restrictions, a subsequent administration might reinstate them as noted by Reuters.
More likely, federal restrictions will come in the form of:
- Government procurement bans: Federal agencies prohibited from using TP-Link equipment
- Critical infrastructure restrictions: Limitations on using TP-Link equipment in telecommunications, power grids, water systems, or other sensitive infrastructure
- Export controls: Restrictions on U. S. companies selling TP-Link equipment to foreign governments or critical infrastructure operators
These restrictions would be significant but wouldn't necessarily lead to a consumer ban. The U. S. government generally doesn't ban products for civilian consumers, even when it bans them for government use. That said, a de facto ban could occur if insurance companies, banks, or other institutions refuse to work with organizations using vulnerable TP-Link equipment as reported by Engadget.

The Broader Cybersecurity Ecosystem: What Changes
If the TP-Link lawsuit succeeds, or if restrictions on TP-Link become formalized, the cybersecurity ecosystem will change in several ways.
Supply chain scrutiny increases: Companies will face more pressure to disclose where products are manufactured, who owns them, and what foreign legal obligations they face. This transparency is positive from a security perspective but creates compliance costs.
Security certifications matter more: Certifications like Common Criteria or NSA Suite B compliance become more valuable signals. Companies will invest more in achieving certifications that prove their products are secure.
Pricing increases: Competition decreases with one major low-cost player removed. Alternatives cost more. Small businesses and consumers feel the impact.
Niche market opportunities emerge: As TP-Link exits, companies selling specifically security-hardened routers, routers designed for small business, or routers from allied manufacturing countries can command premium prices.
Open-source alternatives gain traction: Open Wrt and similar open-source router firmware becomes more attractive. Consumers want more control and transparency. Open-source provides that as noted by Engadget.

How to Evaluate Security Claims Moving Forward
The TP-Link lawsuit teaches an important lesson: you can't just accept security claims at face value. Marketing materials lie. Or they tell partial truths that obscure serious problems.
How do you actually evaluate whether a router (or any network device) is genuinely secure?
Look for third-party validation: Does the company publish security audit results from independent firms? Have security researchers tested the product and published findings?
Check the patch timeline: How quickly does the company patch known vulnerabilities? Is there a public disclosure? Are there patterns of delayed patches?
Research the company structure: Who owns the company? Where is it incorporated? What countries have legal authority over it? This isn't foolproof, but it's relevant.
Read the fine print: Does the company actually promise security, or does it just imply it through marketing language? What are the actual warranty terms?
Check CVE databases: CVE (Common Vulnerabilities and Exposures) databases list publicly disclosed vulnerabilities. If you search for your product and dozens of unpatched vulnerabilities appear, that's a signal.
Look at user forums: Real users discussing real problems on Reddit, forums, or tech communities often reveal issues that marketing materials hide as reported by Engadget.

FAQ
What exactly is TP-Link being sued for in Texas?
TP-Link is being sued by Texas Attorney General Ken Paxton for deceptively marketing the security of its routers while allowing firmware vulnerabilities to persist and be actively exploited by Chinese hacking groups. The lawsuit also alleges that TP-Link's ownership structure ties the company to China's legal system, potentially giving Chinese intelligence agencies access to user data without disclosure to consumers as noted by Engadget.
How did TP-Link routers contribute to the Salt Typhoon attack?
TP-Link routers contained exploitable firmware vulnerabilities that allowed remote code execution without authentication. Attackers in the Salt Typhoon campaign chained these vulnerabilities with other exploits to gain access to network infrastructure. Once they controlled the routers, they could monitor traffic, move laterally into larger networks, and establish persistent access to telecom company systems as reported by SC World.
Is my TP-Link router actively compromised right now?
It's unlikely but possible. For your router to be compromised, an attacker would need to specifically target you or your network. Most home routers are targeted opportunistically, not individually. However, vulnerabilities exist, and if you're on the network of a sensitive organization, the risk is higher. Update your firmware immediately and monitor your device's activity as noted by Engadget.
What should I do if I own a TP-Link router?
First, check your firmware version and update to the latest available version immediately. Change your admin password to something strong and unique. Monitor your router's connected devices list for unfamiliar devices. If you can afford it, consider replacing the router with a model from a manufacturer without geopolitical concerns, such as Netgear, Asus, or Ubiquiti. At minimum, replace the router if it's more than five years old or if no updates are available as reported by Engadget.
Will the U. S. government ban TP-Link routers?
A formal consumer ban is unlikely, but government procurement restrictions are probable. The Trump administration paused federal ban plans in February 2026, but restrictions could be reinstated. More likely, restrictions will apply to government agencies and critical infrastructure while consumers remain free to purchase TP-Link products, though insurance companies and security-conscious organizations may restrict their use as noted by Reuters.
Why does TP-Link's China connection matter if the company is Vietnamese-owned?
Company ownership is separate from supply chain and legal obligations. Even if TP-Link is Vietnamese-owned, if the company manufactures components in China or has business interests in China, it remains subject to Chinese national security laws. Those laws require companies to cooperate with intelligence agencies without disclosure. This potential obligation wasn't disclosed to consumers who assumed they were buying from a Vietnamese company as reported by Engadget.
How will TP-Link's market share be affected by this lawsuit?
TP-Link currently holds approximately 25% of the U. S. residential router market. If restrictions take hold or consumer confidence erodes, market share could shift to Netgear, Asus, and Ubiquiti. This would increase prices overall since TP-Link has been a low-cost leader. Small businesses and budget-conscious consumers would face higher equipment costs as reported by RTINGS.
What does this lawsuit mean for other Chinese tech companies?
The lawsuit sets a precedent that companies with ties to China face heightened scrutiny regarding national security risks and consumer protection. Other Chinese companies in networking equipment, infrastructure, or security-sensitive hardware should expect similar legal challenges and government restrictions. This accelerates a broader trend of decoupling U. S. technology from Chinese supply chains and ownership as noted by Engadget.
Can I get compensation if I bought a TP-Link router?
The lawsuit doesn't automatically entitle consumers to compensation. However, class action lawsuits often emerge from cases like this. If a class action proceeds and settles, affected consumers can typically file claims for refunds or replacement. You would need to prove you purchased the product and potentially document harm suffered as reported by Engadget.
How does router security affect smart home and Io T device security?
Your router is the gateway to your entire home network. If the router is compromised, attackers can see and intercept communications from all devices on the network: smart TVs, security cameras, voice assistants, smart locks, and other Io T devices. Router security is foundational to smart home security. A compromised router means compromised smart home as noted by Engadget.

Conclusion: The Real-World Impact of Security Failures
The TP-Link lawsuit is significant not because it represents a single company's failure, but because it represents a systemic problem with how the technology industry approaches security and disclosure. TP-Link marketed products as secure without adequately investing in security. The company failed to patch vulnerabilities in reasonable timeframes. The company never disclosed the extent of its ties to China or the implications for user data as reported by Engadget.
These aren't unique to TP-Link. They're industry-standard practices. But they're practices that create unacceptable risk when applied to network infrastructure that controls access to Americans' communications and data.
What's changing—what the Texas lawsuit signals—is that regulators and attorneys general are no longer willing to accept vague security claims and deferred accountability. If you market your product as secure, it had better be secure. If you discover vulnerabilities, you'd better patch them quickly. And if your company structure creates dependencies on countries with hostile intelligence services, you'd better disclose that.
For consumers, the lesson is clear: don't assume security. Check firmware versions. Update devices. Monitor network activity. And when geopolitical red flags appear around a technology company, take them seriously. Your router isn't just a device that connects you to the internet. It's infrastructure that protects everything connected to your network. Treat it accordingly.
The TP-Link case will probably settle. TP-Link will probably pay a settlement to Texas, implement some security improvements, and try to move past the controversy. But the precedent is set. Companies can't hide behind marketing language anymore. National security and consumer protection require transparency. And in a world where network infrastructure is a national security issue, expecting anything less than absolute clarity about security and foreign dependencies is naive.
The future of router choice in the United States is uncertain. Restrictions might come. Prices might increase. Competition might decrease. But at least consumers will have a clearer picture of what they're actually buying and who controls the infrastructure behind it as noted by Engadget.

Key Takeaways
- Texas AG Ken Paxton filed lawsuit claiming TP-Link deceptively marketed router security while firmware vulnerabilities enabled Chinese hacker access as reported by Engadget.
- TP-Link routers were exploited in the massive Salt Typhoon attack affecting U.S. telecom companies and compromising millions of Americans' communications data as noted by SC World.
- Company's supply chain and ownership structures tie TP-Link to Chinese legal obligations requiring cooperation with intelligence agencies without user disclosure according to Bloomberg Law.
- Firmware vulnerabilities persisted across multiple TP-Link models for years without timely patches, creating widespread cybersecurity exposure as reported by CyberPress.
- Federal restrictions could increase router prices by 50-70% as TP-Link's 25% market share shifts to competitors like Netgear and Asus as noted by RTINGS.
Related Articles
- Surfshark VPN Deal: Save 86% on Premium Plan Plus 3 Extra Months [2025]
- EU Parliament's AI Ban: Why Europe Is Restricting AI on Government Devices [2025]
- EU Investigation into Shein's Addictive Design & Illegal Products [2025]
- Netgear Nighthawk M7 5G Router Review [2025]
- Japanese Hotel Chain Hit by Ransomware: What You Need to Know [2025]
- Grok's Deepfake Crisis: EU Data Privacy Probe Explained [2025]
![TP-Link Texas Lawsuit: Chinese Hackers, Security Lies, and What It Means [2025]](https://tryrunable.com/blog/tp-link-texas-lawsuit-chinese-hackers-security-lies-and-what/image-1-1771358869402.jpg)



