Japanese Hotel Chain Hit by Ransomware: What You Need to Know [2025]
A major Japanese hotel brand just became the latest hospitality giant to fall victim to a ransomware attack, and the details reveal a troubling pattern in cybersecurity across the industry.
Washington Hotel, operated by Fujita Kanko, confirmed it was hit with ransomware in mid-February. The attack compromised internal systems, exposed sensitive business data, and left customers wondering if their information was stolen. The investigation is ongoing, and details are still emerging, but what we know so far shows how quickly these attacks can escalate and how unprepared even established brands can be according to CISO Series.
Here's the thing: this wasn't some small operation getting hit. Washington Hotel operates over 30 properties across Japan with more than 11,000 rooms and nearly five million guests annually. That's a massive surface area for attackers to exploit, and they apparently found their way in as reported by TechRadar.
What makes this case particularly interesting is what it reveals about how hotels handle data. Customer information from the "Washington Net" membership system was stored on external servers, which actually worked in customers' favor this time. The company confirmed unauthorized access to business data on their internal servers, but the membership information—the crown jewel for attackers—wasn't compromised. At least, not yet as noted by Bleeping Computer.
This article breaks down everything that happened, why it matters, how the attackers likely got in, and most importantly, what you should do if you're a customer or run a hospitality business yourself.
TL; DR
- Attack Confirmed: Washington Hotel (Fujita Kanko brand) suffered ransomware attack on February 13, 2025
- Data Exposure: Unauthorized access to internal business data confirmed, but customer membership data stored externally appears safe
- No Ransom Demand Yet: No threat actors claimed responsibility and no data leaked publicly as of investigation date
- Operational Impact: Minor point-of-sale disruptions reported, but no major business interruptions
- Industry Pattern: This is the latest in a series of major hospitality sector cyberattacks affecting international brands

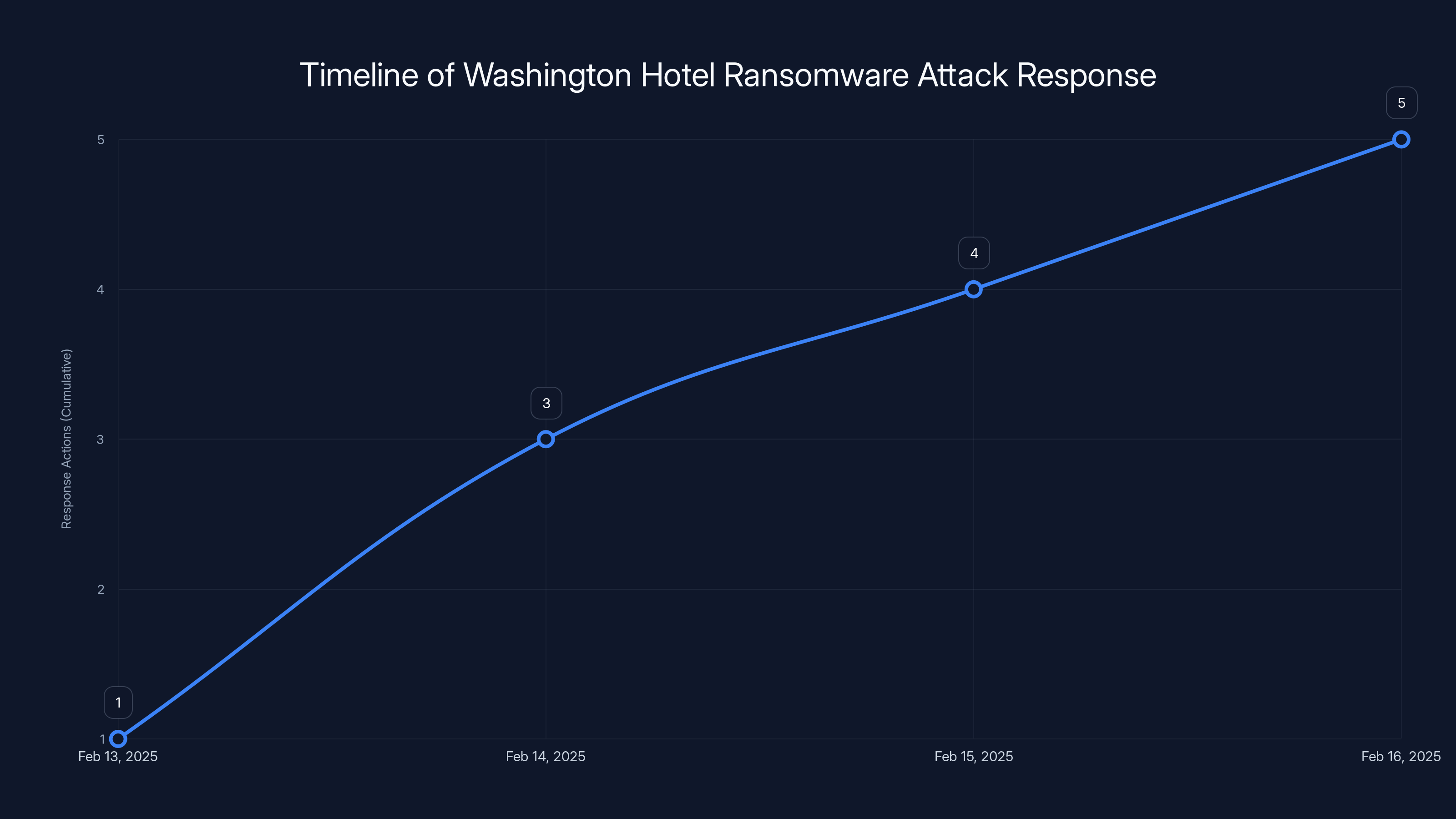
The Washington Hotel responded swiftly to the ransomware attack, escalating from detection to full investigation within 24 hours. Estimated data based on typical response actions.
Understanding the Washington Hotel Ransomware Attack
Let me start with what we actually know, because there's a lot of confusion floating around.
On February 13, 2025, Washington Hotel detected unauthorized access to their internal systems. Late discovery is actually important here—it suggests attackers had access for some time before being detected. The company moved fast once they realized what was happening, cutting off attacker access within hours and implementing emergency protocols.
The hotel immediately assembled an internal task force and contacted police and external cybersecurity experts. This is textbook incident response, and credit to them for moving quickly. Within 24 hours of discovery, they had experts involved and were investigating the scope of the breach as detailed by Bleeping Computer.
What got compromised? The company confirmed "unauthorized access to various business data stored on the server." That's deliberately vague, and honestly, that's typical for early announcements. Business data could mean employee information, operational data, financial records, booking systems, or internal communications. Without specifics, we can't know the full scope yet.
What didn't get compromised (probably)? Customer information from Washington Net, the membership program. The company stressed this data is stored on external servers outside their primary infrastructure, which actually protected customers this time. It's one of those rare cases where not storing everything in one place paid off.
The point-of-sale systems—the terminals where guests pay for rooms and services—experienced some disruptions, but the company said there were "no major disruptions" to business. This suggests attackers either didn't target the payment systems specifically or didn't have time to cause widespread damage before being locked out.
As of the last update, no threat actors claimed responsibility, and no stolen data appeared on dark web marketplaces. That's unusual for ransomware attacks, where attackers typically either leak data or demand payment. Either the investigation scared them off, or they're playing a longer game as noted by Halcyon.
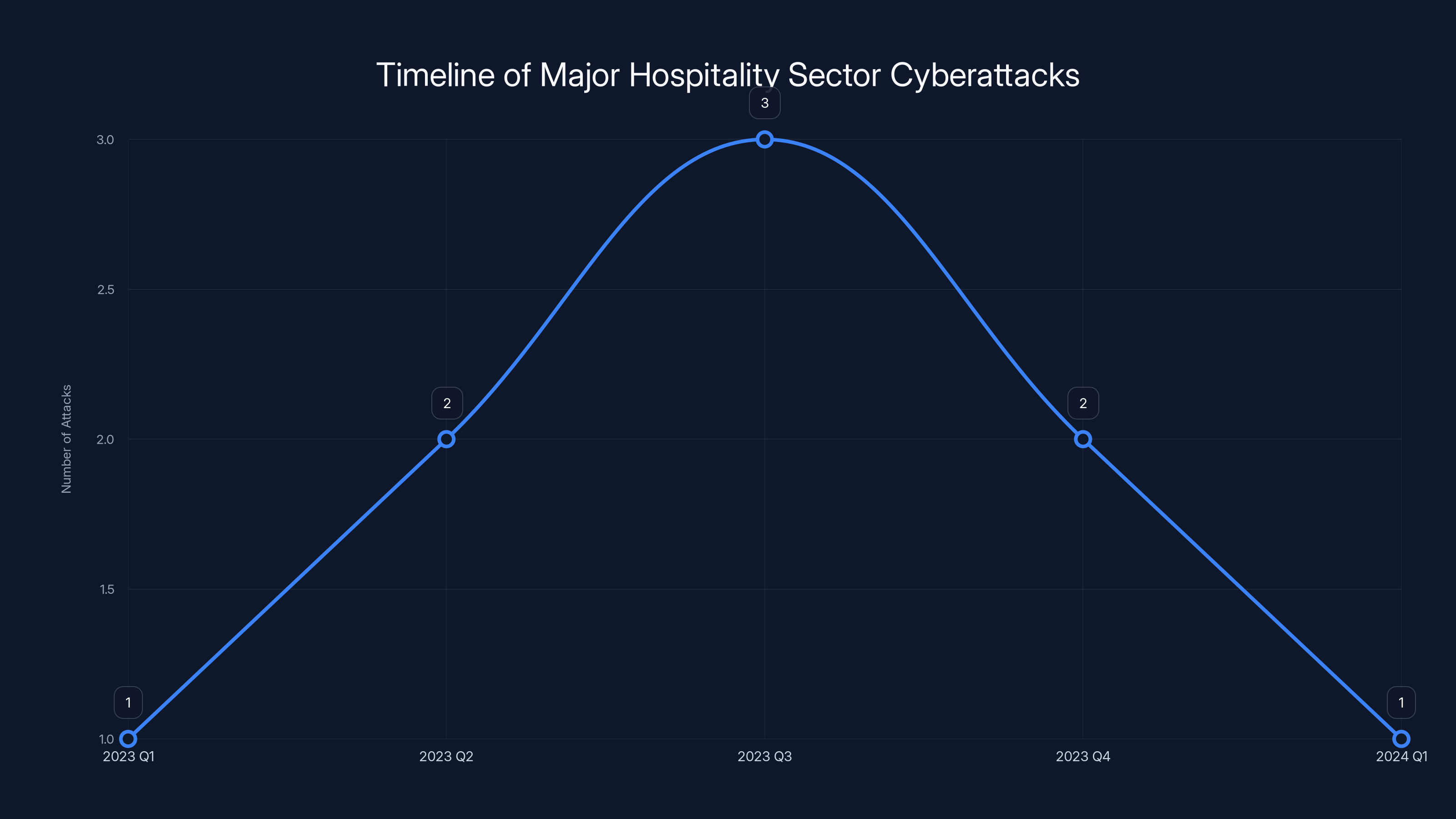
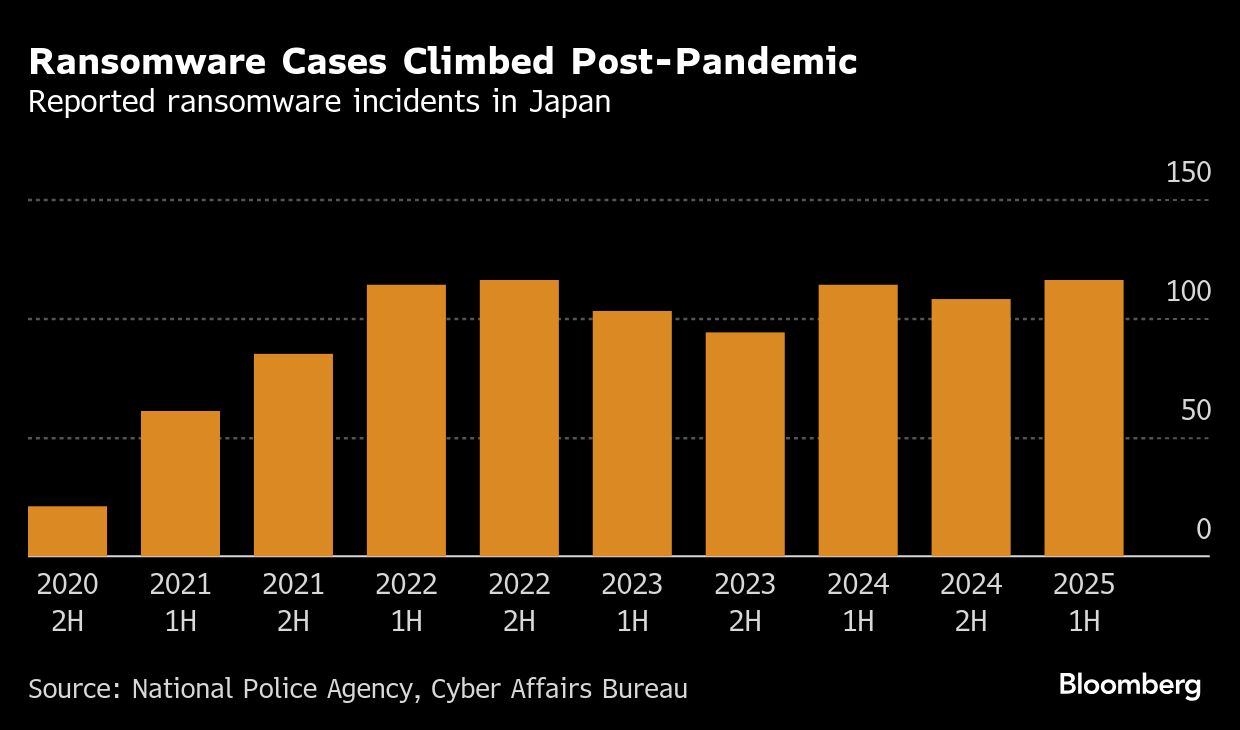
The hospitality industry has experienced a series of ransomware attacks, with a peak in 2023 Q3. Estimated data based on reported incidents.
The Fujita Kanko Hospitality Empire
To understand why this attack matters, you need to know what Washington Hotel actually is.
Washington Hotel isn't just a single property. It's a brand operated by Fujita Kanko, a major Japanese hospitality company. Think of it like how Marriott operates multiple brands—same parent company, different brand positioning. Fujita Kanko also operates Hotel Gracery and several other hotel brands across Japan.
The scale is significant. Washington Hotel has more than 30 locations across Japan, with over 11,000 rooms combined. The company serves nearly five million guests annually. That's not a small operation that can be quickly forgotten. That's a major hospitality player with enterprise-level infrastructure (presumably) and thousands of employees.
The positioning is important too. Washington Hotel targets the mid-range to budget hospitality market for both business and leisure travelers. This means their guest base includes business travelers (who might have connected corporate accounts) and leisure travelers (more diverse data types). For attackers, this represents access to multiple valuable data streams.
Fujita Kanko has established operations in multiple Japanese cities and regions. Multiple properties mean multiple potential entry points for attackers. If one property's network wasn't properly segmented from others, attackers could potentially move laterally across the entire brand's infrastructure.
The company is well-established in Japan's hospitality market, which means they likely have significant financial resources for recovery. But size doesn't always equal cybersecurity maturity. Plenty of large enterprises have been caught flat-footed by ransomware because they prioritized growth and customer experience over security infrastructure as discussed by JD Supra.

How Ransomware Attacks Hit Hotels (The Technical Reality)
Hotels are actually prime targets for ransomware attacks, and not always for the reasons you'd think.
Most people assume attackers want guest credit card data. That's partially true, but it's only part of the equation. Here's what makes hotels so vulnerable:
Guest Data Access Points: Every property has multiple systems that touch guest information. Reservation systems, point-of-sale terminals, key card systems, billing databases, loyalty program systems, and customer service platforms all hold valuable data. One compromised system might cascade to others if they're not properly isolated.
Remote Access Vulnerabilities: Hotels often have remote access systems for management, maintenance, and corporate oversight. During COVID-era closures, many hotels rapidly deployed remote access tools without proper security vetting. Those VPNs and remote desktop protocols often become the entry point for attackers.
Third-Party Connections: Hotels use property management systems (PMS), booking engines, payment processors, and accounting software from multiple vendors. Each vendor represents a potential entry point. If one of those vendors gets compromised, attackers can use it to access hotel networks.
Outdated Infrastructure: Many hotels, especially established chains, run legacy systems that haven't been updated in years. Windows Server 2008 installations, unsupported software versions, and unpatched operating systems are still common in the industry. These systems have known vulnerabilities that attackers exploit routinely.
Overworked IT Staff: Hotels typically don't employ large IT teams. A 30-property chain might have only 5-10 IT people managing thousands of devices, systems, and locations. That's an understaffed situation that makes consistent security practices nearly impossible.
Ransomware Delivery Methods: The actual infection vector usually comes through phishing emails, compromised websites that serve malware, or exploitation of unpatched vulnerabilities. An employee clicks a link in a phishing email, malware gets installed, and within hours, attackers have lateral movement through the network.
Once attackers are inside, they typically:
- Spend time exploring the network to understand what's valuable
- Establish persistence (meaning they can maintain access even if one entry point is closed)
- Escalate privileges to admin-level access
- Exfiltrate sensitive data (copy it to their servers)
- Deploy ransomware to encrypt files and systems
- Demand payment with a deadline
The Washington Hotel attack likely followed this pattern. The February 13 discovery suggests attackers had been inside for some time before being detected. This isn't an overnight attack; it's a multi-stage operation that probably took days or weeks to execute fully as noted by Britannica.
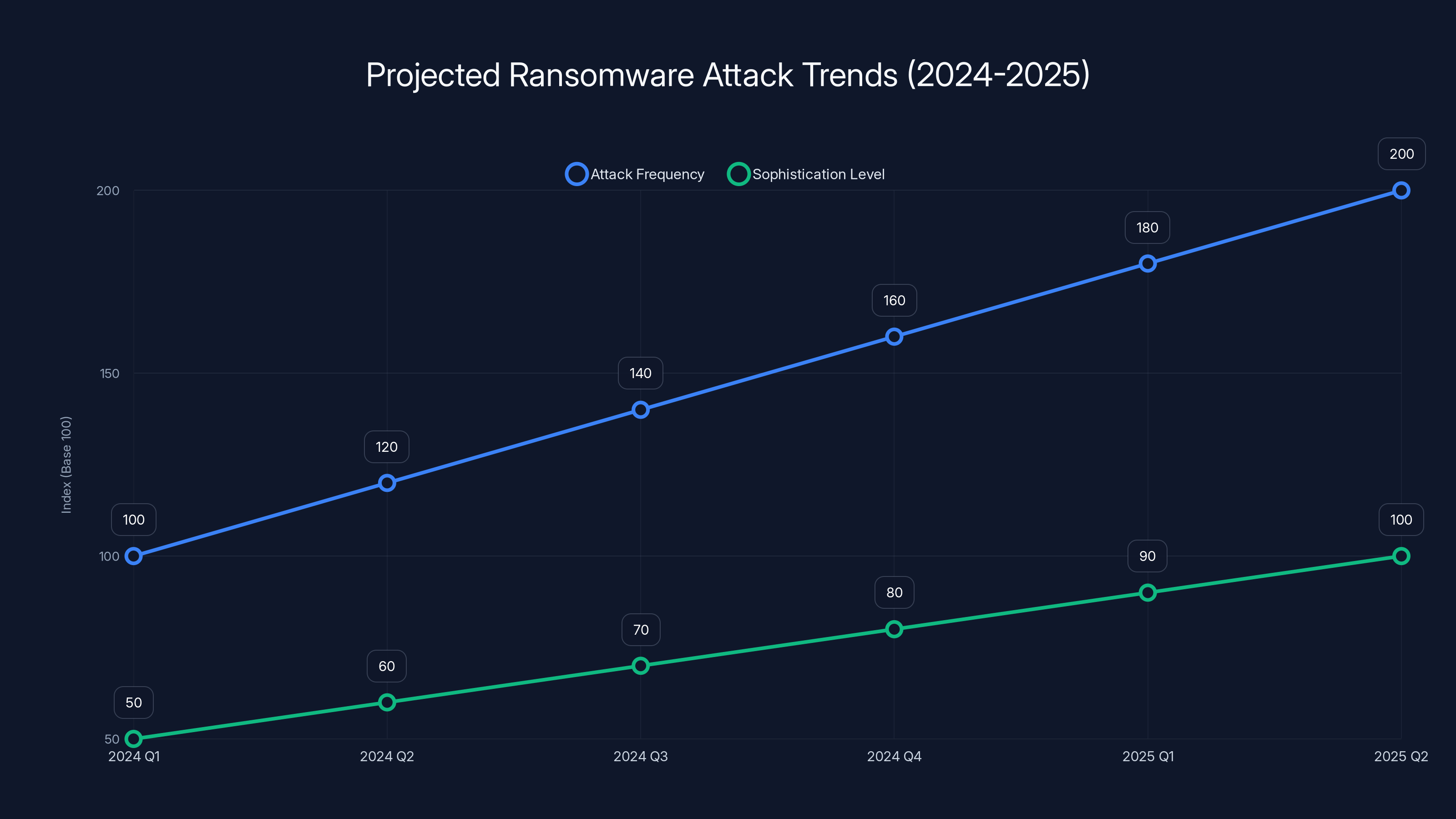
Ransomware attacks are projected to increase in both frequency and sophistication from 2024 to 2025. Estimated data.
The Broader Pattern: Why Hotels Keep Getting Hit
This attack didn't happen in a vacuum. Washington Hotel is just the latest in a concerning pattern of ransomware attacks targeting the hospitality industry.
Consider the timeline of major hospitality sector cyberattacks:
Hyatt Hotels (2023-2024): Multiple Hyatt properties across the US and Canada reported ransomware infections affecting payment systems and guest data. The company paid millions in response.
MGM Resorts (2023): One of the largest casinos and hotel operators in the world suffered a massive ransomware attack that disrupted operations across multiple properties, costing the company an estimated $100 million in recovery and business interruption.
Marriott (Multiple Incidents): The world's largest hotel chain has disclosed multiple data breaches over the years, affecting millions of guests' personal information.
IHG Hotels: Inter Continental Hotels Group disclosed ransomware attacks affecting various properties.
Why is the hospitality industry such a consistent target?
High Ransom Payments: Hotels are profitable businesses that can afford to pay ransoms. An attack that shuts down a 300-room hotel for even one day costs $30,000-50,000 in lost revenue. Attackers know hotels often pay rather than rebuild systems from scratch.
Guest Data Value: Credit card information, passport numbers, home addresses, phone numbers—hotel reservation systems are gold mines for identity thieves. This data sells on dark web markets for $5-100 per record depending on completeness.
Operational Criticality: Hotels can't just shut down for a week while they recover. Guests have reservations. Staff need to work. Revenue stops immediately. This pressure makes hotels more likely to pay ransoms quickly.
Fragmented Networks: Large hotel chains often have poorly integrated IT infrastructure. Corporate headquarters doesn't directly control every property's systems. This fragmentation means security protocols vary widely, and one weak link breaks the chain.
Legacy Systems: Many hotels run property management systems from the 1990s or early 2000s with minimal updates. These systems have known vulnerabilities that modern malware exploits easily.
The Washington Hotel attack fits this pattern perfectly. They're a large operation with multiple properties, likely running varied IT infrastructure across locations, serving millions of guests annually. For attackers, it's a high-value, high-probability target as highlighted by AERA.
What Data Was Actually Compromised?
This is where things get murky, and it's important to be honest about the uncertainty.
The company confirmed "unauthorized access to various business data stored on the server." That's the official statement. In plain English, it means attackers got into systems holding business data, but the company hasn't specified what that entails.
What We Know Wasn't Compromised: Customer membership data from Washington Net. This is stored on external servers outside the company's primary infrastructure. The company specifically mentioned this wasn't affected, which is noteworthy because it's what most customers care about.
What Likely Was Compromised: This is speculative but based on typical hotel system architecture:
- Employee Data: Names, addresses, phone numbers, social security numbers, salary information, tax documents
- Operational Data: Financial records, booking data, reservation systems, pricing information
- Internal Communications: Emails, documents, strategic plans
- Vendor Information: Payment details for suppliers and contractors
- Financial Records: Banking information, invoices, accounting data
What Might Have Been Compromised: This depends on system integration:
- Guest Payment Information: If point-of-sale systems were integrated with other databases (some were disrupted)
- Corporate Account Data: If Washington Hotel hosts corporate accounts with business travelers
- Third-Party Integration Data: Information shared with booking partners, loyalty programs, payment processors
The point-of-sale system disruptions are notable. Some ransomware attacks specifically target payment systems because they're isolated from other networks (for PCI compliance). But if payment systems were disrupted, that suggests attackers either had access to those isolated networks or the hotel's network segmentation wasn't as strong as it should be.
Here's the honest assessment: without a full forensic report, we won't know exactly what was taken. The attackers know. The incident response team knows. But the public statements are deliberately vague, which is standard practice during investigations.
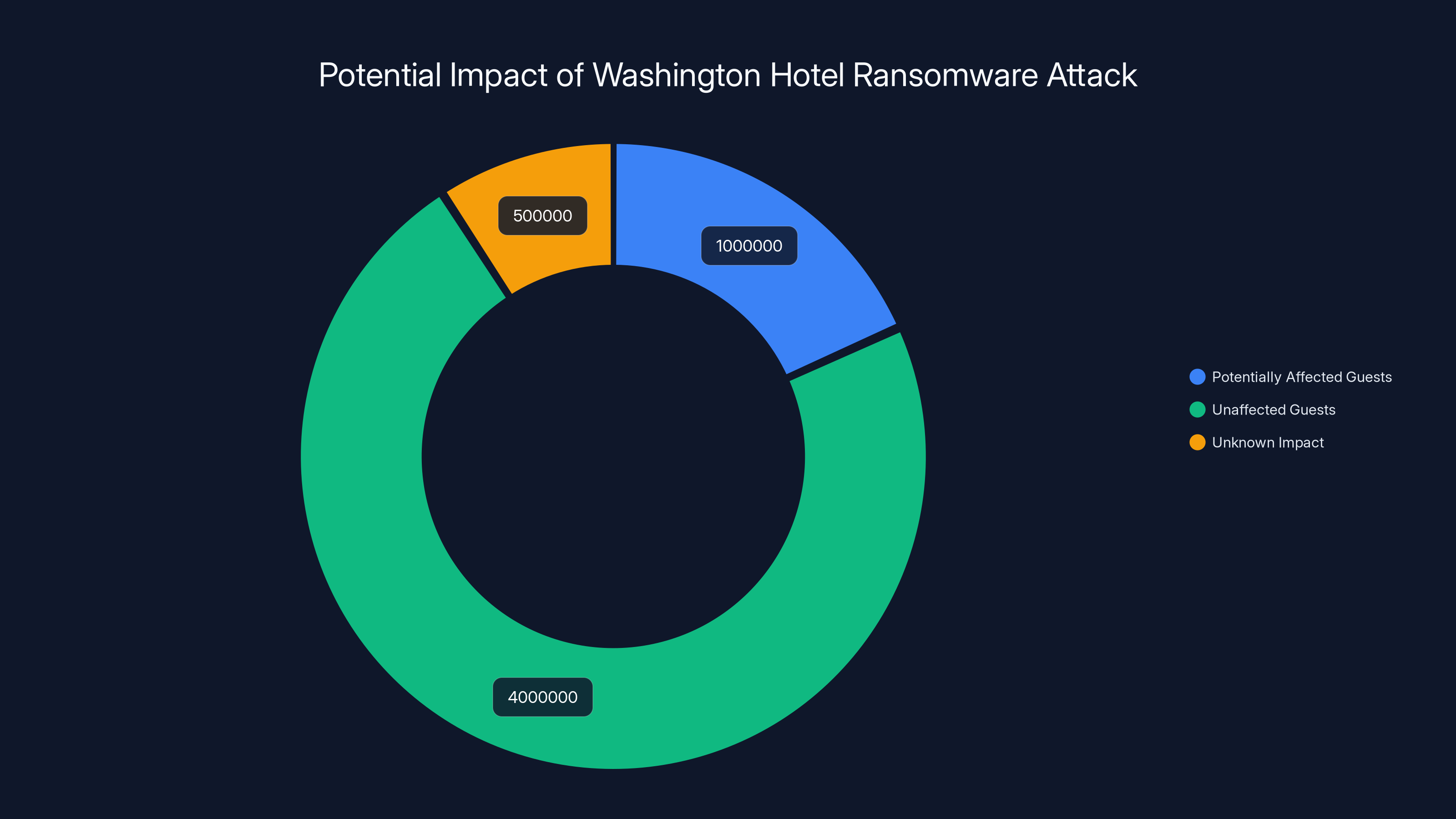
Estimated data suggests that up to 1 million guests could potentially be affected, although the exact impact remains unknown.
Timeline: How the Attack Unfolded
Understanding the timeline helps explain how the attack escalated to the point of public disclosure.
Before February 13: Attackers had already penetrated Washington Hotel's network. They conducted reconnaissance, explored systems, and identified valuable data. This phase might have lasted days or weeks. Nobody inside the hotel knew they were there.
February 13, Late Evening: Washington Hotel's security team discovered unauthorized access to systems. The discovery could have come from multiple sources: unusual network traffic, file modifications, security alerts, or suspicious user activity. Once detected, the company moved into incident response mode.
February 13-14: The company cut off attacker access, assembled an internal task force, and contacted law enforcement and external cybersecurity experts. This first 24 hours is critical—it determines whether attackers can maintain access or are fully removed.
Days 1-7: Forensic investigation begins. Security experts examine system logs, identify entry points, determine what data was accessed, and assess the scope of compromise.
Week 2: The company prepares public disclosure. They consult with legal counsel, insurance companies, and PR teams about what to announce and how to frame it. The statement released acknowledges the breach but emphasizes that membership data wasn't compromised.
Investigation Ongoing: As of the public statement, no threat actors had claimed responsibility, and no data had appeared on dark web marketplaces. This is unusual, and there are a few possibilities:
- The attackers scared by rapid response and decided to move on
- They're waiting to make demands through private channels
- They're selling the data quietly without public announcements
- This was a competitor or state-sponsored attack focused on espionage rather than ransom
The absence of public responsibility claims is actually somewhat positive. It suggests either the attack was disrupted before completion or the attackers aren't following the typical ransom extortion model as noted by The Points Guy.
Point-of-Sale System Disruptions: What That Means
The company mentioned that some hotels reported issues with point-of-sale terminals, but stressed there were "no major disruptions." This statement deserves deeper analysis.
Point-of-sale systems are the terminals at front desks, restaurants, and service areas where guests pay for rooms, food, and services. They're critical infrastructure—if they go down, hotels can't collect payment. But they also represent security vulnerabilities.
Why Attackers Target POS Systems:
Credit card data flows through these systems constantly. If attackers can intercept that data or install malware on the terminals, they gain access to payment information. Modern POS systems are networked, which means they're connected to other systems—and that connection can be exploited.
What "No Major Disruptions" Likely Means:
This phrasing suggests that while some properties experienced POS issues, the problems were limited in scope or duration. Possible scenarios:
- The ransomware tried to encrypt POS systems but failed due to network segmentation
- Only a few of the 30+ properties experienced actual disruptions
- The disruptions lasted hours or less before being resolved
- Manual payment processing (paper receipts, phone calls) kept operations running
If this was a full-scale ransomware attack affecting all POS systems across all 30 properties simultaneously, the damage would be catastrophic. The fact that it wasn't suggests either the attack didn't spread that far or the company recovered quickly.
From a technical perspective, the most likely scenario is that the ransomware primarily targeted business systems (accounting, reservations, internal servers) rather than focusing specifically on POS terminals. The POS disruptions might have been collateral damage from broader network disruption rather than targeted attacks.
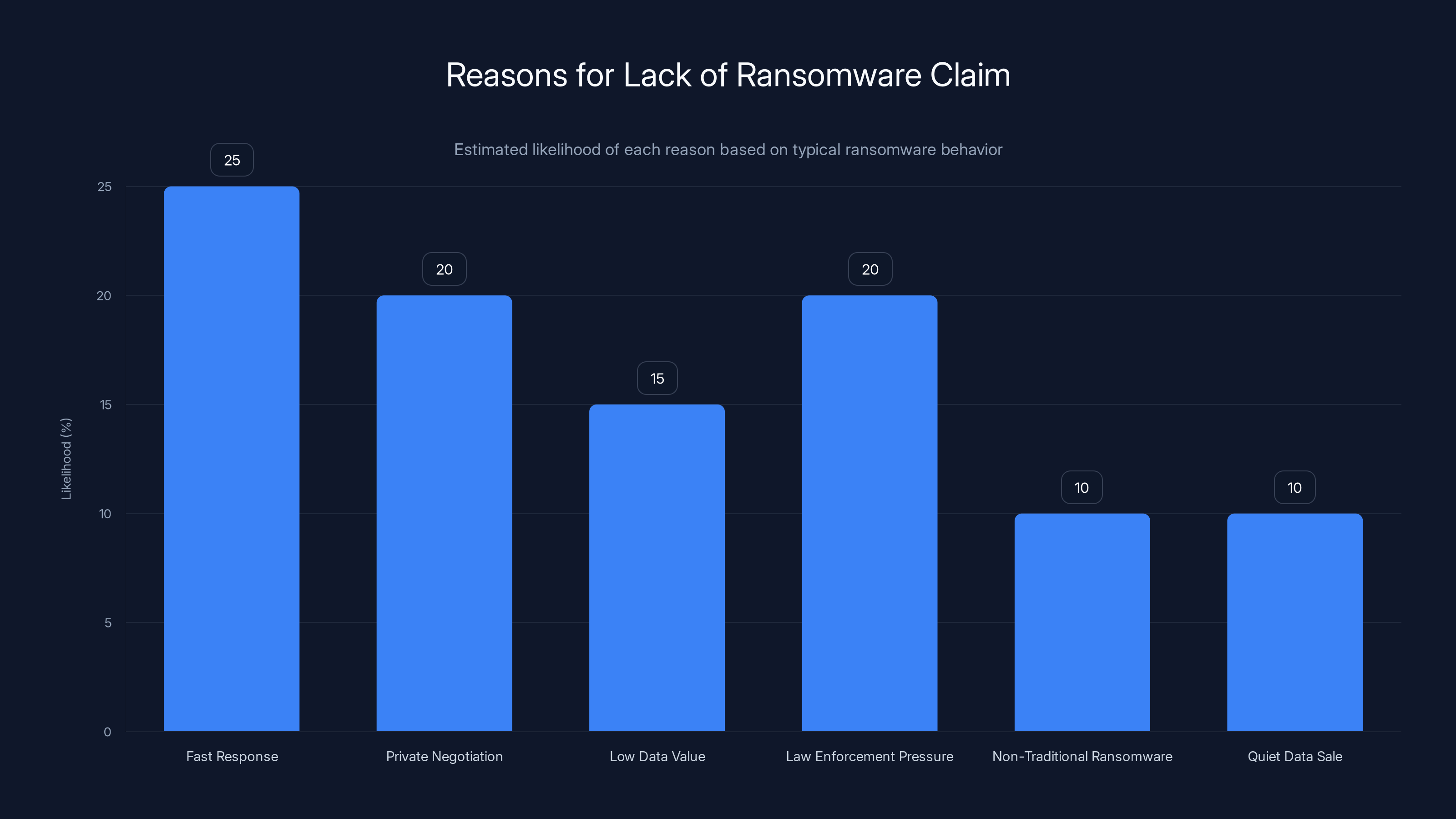
Fast response and private negotiation are estimated to be the most likely reasons for the absence of a public claim in this ransomware case. Estimated data based on typical scenarios.
Why No Threat Actors Claimed Responsibility Yet
This is unusual enough to warrant its own analysis. Most ransomware attacks follow a script: attackers encrypt files, leave a ransom note, and contact victims with payment demands. The absence of public claims or dark web leaks is notable.
Possible Explanations:
1. The Response Was Too Fast
Washington Hotel detected the breach relatively quickly and cut off attacker access within hours. This speed might have interrupted the attackers' timeline before they could establish full persistence or exfiltrate all data they wanted. They might have abandoned the attack to avoid detection by security researchers.
2. Private Negotiation
Attackers often contact victims through private channels (anonymous email, chat services, dark web messages) before going public with leaks or ransom demands. It's possible negotiation was happening behind the scenes while the public investigation continued.
3. Data Wasn't Valuable Enough
If the attackers primarily got access to operational data rather than customer data, they might have decided the intelligence wasn't valuable enough to monetize. Business data is less predictable in value—customer data has clear market prices on dark web forums.
4. Law Enforcement Pressure
The involvement of Japanese police and the activation of international incident response teams might have signaled that this attack would receive serious law enforcement attention. Some ransomware gangs prefer to avoid high-profile cases that attract FBI and Interpol involvement.
5. This Wasn't Traditional Ransomware
The attack might have been targeted espionage or intellectual property theft rather than financially motivated ransomware. Competing hotel groups, business intelligence operatives, or nation-states might have been interested in Fujita Kanko's operational data, pricing strategies, or expansion plans—not customer data to ransom.
6. The Data Is Being Sold Quietly
Some attacks result in data being sold through private channels rather than publicly leaked. The attackers might be quietly offering the data to interested buyers (competitors, resellers, etc.) without announcing it publicly.
The most likely scenario combines multiple factors: rapid incident response disrupted the attack, the data obtained wasn't what attackers hoped for, and law enforcement involvement created additional risk. This confluence of factors might explain why no public extortion followed as analyzed by Bright Defense.

Customer Data Storage Architecture: The Accidental Defense
Here's something interesting that actually protected customers: Washington Hotel's customer membership data wasn't stored on the compromised servers.
This sounds like good luck, but it's actually a design decision that worked in their favor. The company explicitly mentioned that Washington Net membership information is "located on a server outside the company," separate from the main infrastructure. This external storage means the membership database wasn't vulnerable to the ransomware attack that compromised internal business systems.
How This Protects Customers:
If membership data is stored on a completely separate system (different servers, different network, different security infrastructure), then compromising the main business systems doesn't automatically give attackers access to customer accounts. Each system needs to be attacked separately.
The Trade-off:
Externalizing data storage typically means using a third-party service provider—possibly a dedicated membership platform, a cloud service, or an outsourced data provider. This creates a different security responsibility structure. Instead of the hotel protecting all data, that external provider bears responsibility for membership data.
This is actually a smart architecture decision, though it creates other dependencies. The hotel depends on that external provider's security, which could be better or worse than their own infrastructure. But in this case, it worked out because attackers focused on the main business systems and didn't target the external service.
What This Means for Other Data:
While membership data was protected, the compromise of internal business systems likely exposed other information:
- Booking records (before they reach the membership system)
- Employee data
- Operational information
- Financial records
- Internal communications
The fact that some data was protected doesn't mean customer privacy is fully preserved. The company's vague statement about "various business data" suggests there's still significant exposure beyond membership accounts as noted by Halcyon.

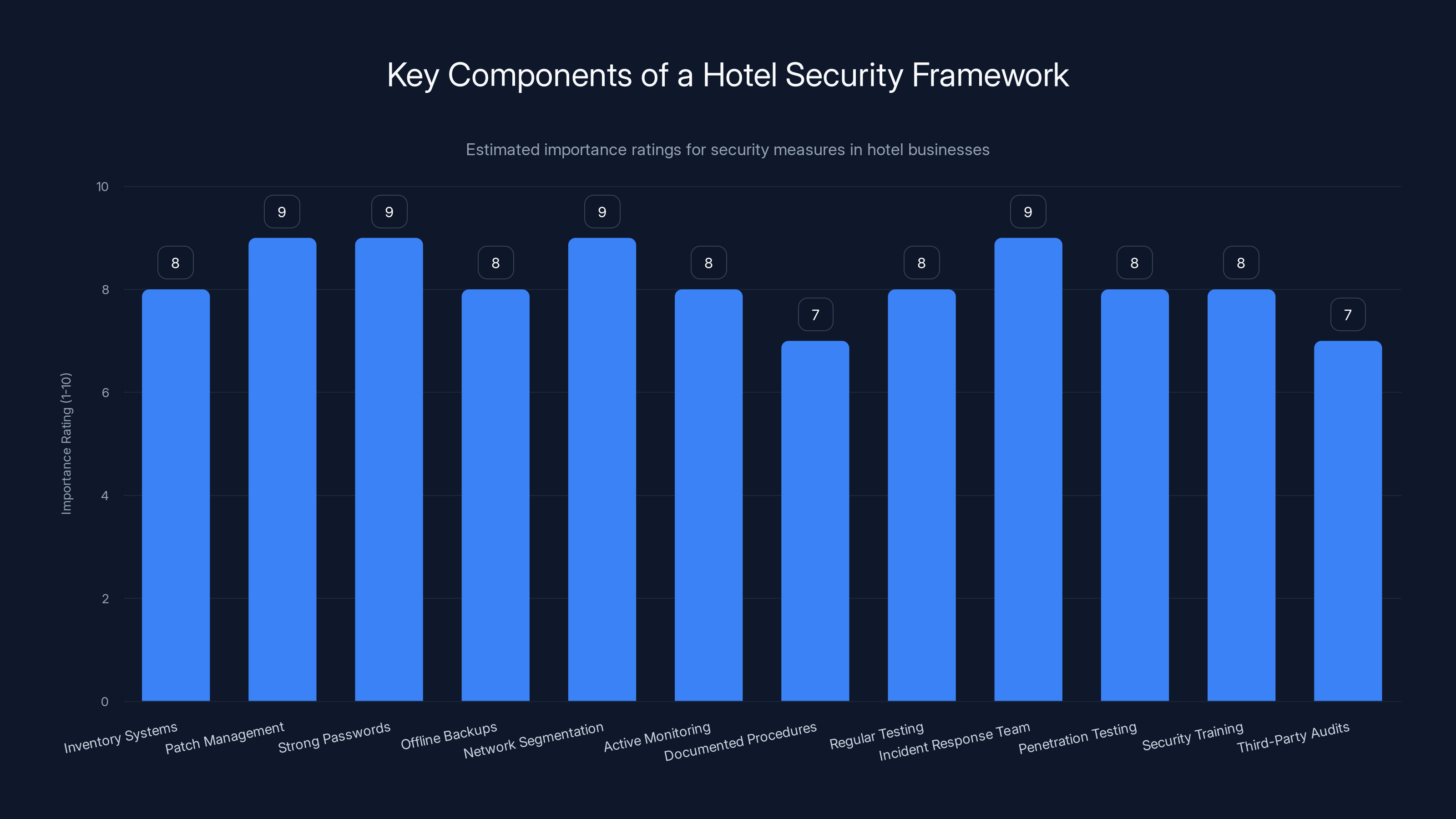
This bar chart estimates the importance of various security measures in a hotel business security framework. Patch management, network segmentation, and having an incident response team are rated highest in importance. Estimated data.
How to Check If You're Affected
If you stayed at Washington Hotel or have an account with them, here's what to do:
Immediate Actions:
-
Check Company Announcements: Visit the Washington Hotel website and look for official breach notifications. The company is required to provide details about affected individuals and data types.
-
Monitor Credit Cards: Review statements for unauthorized charges. Set up alerts on your credit card accounts to notify you of any unusual activity.
-
Check Email for Breach Notifications: The company should send emails to affected customers. Check spam folders in case notifications were misflagged.
-
Verify Account Access: Log into your Washington Net account if you have one. Check that only you have access and that no unauthorized changes were made.
-
Place Fraud Alerts: Contact the three major credit bureaus (Equifax, Experian, Trans Union) and request fraud alerts on your credit reports. This makes it harder for thieves to open accounts in your name.
Medium-Term Actions (Next 30 Days):
-
Monitor Credit Reports: Get free credit reports from www.annualcreditreport.com and check for accounts you didn't open.
-
Update Passwords: Change your Washington Hotel password and any other accounts that share similar passwords.
-
Enable Two-Factor Authentication: If Washington Hotel supports it, enable 2FA on your account.
-
Review Booking History: Check past reservations to confirm they match what you remember. Look for unauthorized bookings.
Long-Term Monitoring (6-12 Months):
-
Identity Theft Insurance: Consider purchasing identity theft protection if you don't have it.
-
Regular Credit Checks: Monitor your credit report every few months for signs of unauthorized activity.
-
Watch for Data Sales: Some data from breaches appears on dark web markets months or years later. Services like Have I Been Pwned track known breaches.
-
Track the Investigation: Follow news reports about the investigation. The company will eventually release a full forensic report.
Lessons for Hotel Operators and Hospitality Companies
If you run a hotel or hospitality business, this incident offers several lessons worth taking seriously.
1. Detection Speed Matters More Than Perfect Prevention
Washington Hotel didn't prevent the attack, but they detected it relatively quickly and responded immediately. That rapid response likely limited the damage significantly. The lesson: you won't prevent every attack, so focus on detecting them as fast as possible.
Actionable Steps:
- Deploy 24/7 security monitoring and alerting
- Establish clear escalation procedures for security alerts
- Conduct regular penetration testing to identify vulnerabilities before attackers do
- Maintain detailed logs of all system access for forensic investigation
2. Network Segmentation Is Non-Negotiable
The fact that membership data was stored separately and escaped compromise shows that network segmentation works. Payment systems should be isolated. Guest data should be isolated. Internal business systems should be isolated.
Actionable Steps:
- Audit your network architecture and identify systems that are overly interconnected
- Implement strict network segmentation between guest-facing systems and internal operations
- Ensure point-of-sale systems are isolated from general business networks
- Test segmentation regularly to confirm it actually works
3. Third-Party Risk Is Real
Many hotel system breaches come through compromised vendors. Property management systems, booking engines, payment processors, and accounting software all represent potential entry points.
Actionable Steps:
- Audit all third-party integrations and access
- Require vendors to maintain cybersecurity certifications (SOC2, ISO 27001)
- Establish vendor security requirements in contracts
- Limit third-party access to only the systems they actually need
4. Incident Response Plans Need to Be Practiced
The company's quick assembly of an internal task force, notification of law enforcement, and engagement of external experts suggests they had a plan. Plans that are practiced work better than plans that are theoretical.
Actionable Steps:
- Document your incident response procedures in writing
- Assign clear roles and responsibilities for different types of incidents
- Conduct tabletop exercises where you role-play a ransomware attack
- Test your backup and recovery procedures quarterly
5. Backup and Recovery Is Survival
Ransomware only works if you can't recover. If Washington Hotel had good backups, they could have recovered without paying a ransom (assuming they needed to pay at all).
Actionable Steps:
- Maintain offline backups that attackers can't encrypt
- Test restores regularly to ensure backups actually work
- Have multiple copies of critical data (on-site, off-site, air-gapped)
- Document your recovery time objectives and ensure backups can meet them
6. Communication Matters During Crisis
The company's relatively transparent statement about what happened and what wasn't compromised helped manage expectations and customer concern.
Actionable Steps:
- Develop a communication template for security incidents
- Identify who can approve public statements about security issues
- Communicate clearly and honestly about what you know and don't know
- Update customers regularly as investigation progresses
The Bigger Picture: Ransomware Trends in 2025
The Washington Hotel attack is one data point in a larger trend affecting businesses globally.
Ransomware Statistics for 2024-2025:
Ransomware attacks continue to increase in frequency and sophistication. Organizations across all industries report elevated attack volumes. The hospitality sector remains a top target because of the factors discussed earlier.
Attacker Tactics Are Evolving:
Modern ransomware operations aren't just encrypt-and-demand anymore. They're increasingly sophisticated:
- Double Extortion: Attackers steal data and threaten to leak it even if you pay the ransom
- Affiliate Models: Ransomware-as-a-Service operations where creators sell tools to other attackers
- Targeted Operations: Fewer spray-and-pray attacks, more carefully selected high-value targets
- Data Harvesting First: Many attackers extract valuable data before deploying ransomware, meaning the ransom is almost secondary
Regulatory Pressure Is Increasing:
Governments worldwide are implementing stronger data protection regulations. The EU's GDPR, California's CCPA, and similar laws require companies to:
- Report breaches within specific timeframes
- Notify affected individuals
- Demonstrate "reasonable security" measures
- Pay penalties for non-compliance
For hospitality companies, this means breach disclosure is mandatory, not optional. Washington Hotel's public announcement wasn't entirely voluntary—it was likely required by Japanese data protection regulations as noted by Halcyon.
Insurance Landscape Is Changing:
Cybersecurity insurance, which many companies relied on to cover ransomware costs, is becoming more expensive and restrictive. Insurers now require strong security practices before providing coverage. They're also refusing to cover ransom payments in some cases.
This creates pressure on companies to improve security proactively rather than relying on insurance to bail them out.
Nation-State Involvement:
While most ransomware is financially motivated, there's increasing evidence of nation-state actors using ransomware as a tool for espionage and sabotage. These attacks are harder to defend against because they have more resources and sophistication than criminal groups.

What Comes Next: Investigation and Recovery
As of the public announcement, Washington Hotel's investigation was ongoing. Here's what typically happens in the aftermath of a major ransomware attack:
Week 1-2 (Immediate Response):
- Secure all affected systems
- Engage forensic investigators
- Notify law enforcement
- Preserve evidence
- Brief legal and insurance teams
Week 2-4 (Investigation):
- Determine entry point and attack vector
- Identify all compromised systems and data
- Assess business impact and costs
- Begin recovery and rebuilding
- Prepare customer notifications
Month 2-3 (Recovery):
- Rebuild systems from clean backups
- Implement security improvements
- Restore normal operations
- Complete forensic investigation
- Release detailed incident report
Months 3-6 (Follow-up):
- Monitor for signs of persistent attackers
- Implement lessons learned
- Update security policies and training
- Work with law enforcement on attribution
- Manage customer and vendor concerns
Timeline Uncertainty:
The exact timeline depends on several factors: the sophistication of the attack, the quality of backups, the size of the organization, and the availability of forensic resources. Small breaches might be fully resolved in weeks. Large, complicated breaches can take months to fully understand.
For Washington Hotel, with 30+ properties and millions of customer records to protect, the investigation could take months. The company is facing significant pressure to:
- Restore normal operations quickly
- Investigate thoroughly to understand the full scope
- Improve security to prevent future incidents
- Manage customer trust and confidence
These goals sometimes conflict, which is why these investigations take time.
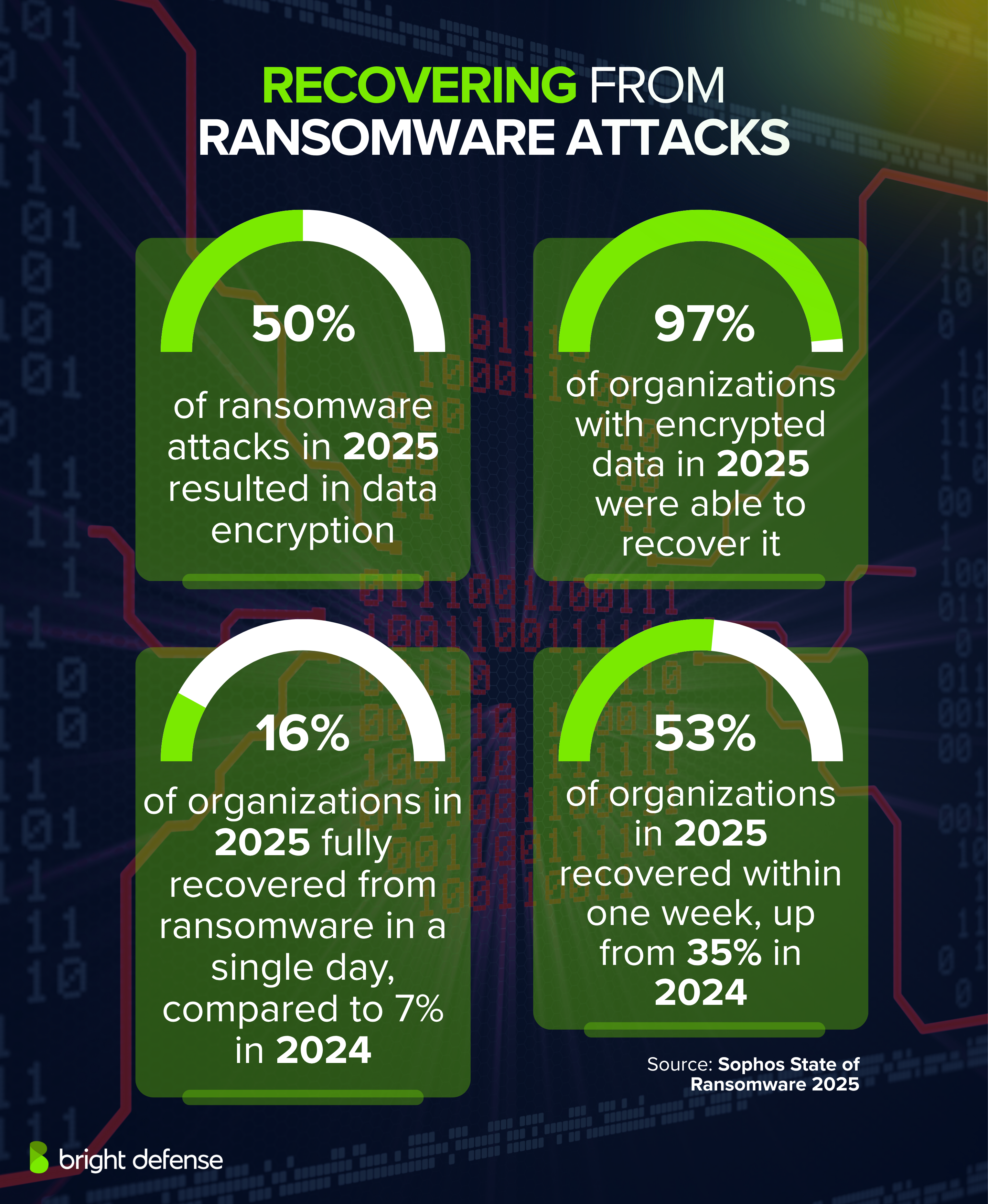
Protecting Your Hotel Business: Practical Security Framework
If you operate a hotel or hospitality business, you need a security framework that actually works. Here's a practical approach.
Foundation: The Basics (Do These First)
-
Inventory Your Systems: Document every system that stores data. Many breaches succeed because companies don't know what they have.
-
Patch Everything: Outdated software has known vulnerabilities attackers exploit. Establish a patching schedule and stick to it. This single practice prevents most attacks.
-
Require Strong Passwords: Use a password manager for accounts. Require multi-factor authentication for all administrative access.
-
Backup Everything Offline: Ransomware can't encrypt backups that aren't connected to your network. Store copies offline or in separate, air-gapped systems.
-
Segment Your Network: Isolate payment systems, guest data systems, and business systems so a breach in one doesn't compromise everything.
Layer 2: Detection and Response
-
Monitor Actively: Deploy security tools that alert you to unusual activity. You can't respond to attacks you don't know about.
-
Document Procedures: Write down exactly what happens when a security incident is detected. Having a plan written down means people follow it under stress.
-
Test Regularly: Run annual tabletop exercises where you role-play an attack scenario. This identifies gaps in your procedures.
-
Establish Incident Response Team: Define roles and responsibilities. Who contacts law enforcement? Who manages communications? Who coordinates recovery?
Layer 3: Continuous Improvement
-
Conduct Penetration Testing: Hire security professionals to try to breach your systems. Fix what they find.
-
Security Awareness Training: Human error is involved in most breaches. Regular training helps staff recognize phishing and suspicious activity.
-
Audit Third-Party Access: Vendors and contractors often have unnecessary access. Audit and restrict it to the minimum needed.
-
Review and Update Policies: Security isn't static. Review your policies annually and update them based on emerging threats.
Metrics That Matter:
- Detection Time: How quickly can you detect a breach? Target: 24 hours or less
- Response Time: How quickly can you isolate affected systems? Target: 1-2 hours
- Recovery Time: How long to restore operations? Target: 24-48 hours
- Data Recovery: Can you recover from backups without data loss? Test quarterly
These metrics give you concrete goals to work toward rather than abstract security concepts.

Where Is Artificial Intelligence Helping (and Hurting) Security?
AI is transforming cybersecurity in both positive and negative ways, and it's worth understanding both sides.
AI Helping Security Teams:
Threat Detection: AI systems can analyze millions of events per second and identify patterns humans would miss. Modern security information and event management (SIEM) systems use AI to detect anomalies that might indicate attacks.
Predictive Analysis: AI can analyze historical attack patterns and predict where vulnerabilities might develop. This helps security teams focus on the highest-risk areas.
Automated Response: When AI detects a threat, it can automatically take protective actions: isolating systems, blocking accounts, shutting down services. This speed prevents propagation.
Threat Intelligence: AI analyzes millions of publicly available data sources to identify new threats and vulnerabilities before they're widely exploited.
AI Helping Attackers:
Phishing Sophistication: AI can generate convincing phishing emails that are harder to detect than human-written ones. Content that previously looked obviously fake now reads like legitimate communications.
Password Cracking: AI can attempt passwords more efficiently and identify patterns in how humans create passwords.
Social Engineering: Deepfakes and AI-generated content can be used to impersonate executives or create convincing false scenarios to trick employees.
Malware Adaptation: AI-powered malware can adapt in real-time based on detection and evasion attempts, making it harder to stop.
The Real Impact:
Overall, AI is probably helping defenders more than attackers right now, but that advantage is diminishing. As attackers get better at using AI, the advantage might shift. The key is for organizations to:
- Implement AI-powered security tools
- Don't rely solely on AI (human oversight is essential)
- Keep staff trained on evolving threats
- Update systems as threats evolve

FAQ
What exactly happened in the Washington Hotel ransomware attack?
Washington Hotel, operated by Fujita Kanko, detected ransomware on February 13, 2025. The attackers gained unauthorized access to internal business systems, but the company moved quickly to cut off their access. Customer membership data was stored separately and wasn't compromised, though some point-of-sale systems experienced disruptions. As of the investigation's conclusion, no threat actors had publicly claimed responsibility and no data had been leaked as reported by CISO Series.
How many people were affected by the Washington Hotel breach?
The exact number of affected individuals hasn't been disclosed. The company confirmed unauthorized access to business data but stated that customer membership information (the most sensitive data) wasn't compromised. Given that Washington Hotel serves nearly five million guests annually across 30+ properties, the potential exposure could be significant, but the actual impact depends on what data the attackers accessed during their time in the system as noted by Bleeping Computer.
Should I be concerned if I'm a Washington Hotel customer?
Yes, take precautionary steps even though membership data wasn't directly exposed. Monitor your credit card statements, check your hotel account for unauthorized activity, and place fraud alerts if you're concerned. The company confirmed unauthorized access to "various business data," which could include information from reservations, payment processing, or employee records connected to your stay as reported by TechRadar.
Why haven't the attackers claimed responsibility or demanded ransom?
Several factors could explain this: the rapid incident response might have disrupted the attack before completion, the data obtained might not have been valuable enough to monetize, law enforcement involvement created additional risk, or the attackers might be negotiating privately rather than publicly. It's also possible this was espionage-motivated rather than financially motivated, or the data is being sold quietly through private channels as analyzed by Bright Defense.
What can hotels do to prevent ransomware attacks like this?
Hotels need a multi-layered approach: implement network segmentation to isolate critical systems, maintain offline backups that can't be encrypted, patch software regularly, monitor networks 24/7 for intrusions, require multi-factor authentication, conduct regular security training, test incident response procedures, and audit third-party vendor access. No single tool prevents attacks, but this combination significantly reduces risk and limits damage if an attack does occur as noted by Halcyon.
How can I tell if my personal data from a hotel stay was compromised in a breach?
Check the company's website for official breach notifications (they're required to disclose affected data). Verify your email spam folder in case the notification went there. You can also check breached-data tracking services like Have I Been Pwned. Monitor your credit card statements, place fraud alerts with credit bureaus, and review your credit report for unauthorized accounts. These steps help catch fraud before it causes significant damage.
What is the typical ransom demand in hotel ransomware attacks?
Ransom demands vary widely based on company size and data sensitivity. For major hotel chains, ransoms typically range from $400,000 to several million dollars. Some companies choose to pay (especially if they believe backups are compromised), while others rebuild systems without paying. Law enforcement generally discourages ransom payments because they fund future attacks, but companies often feel payment is their best option to resume operations quickly according to Statista.
Is hotel customer data actually valuable to cybercriminals?
Yes, extremely. Hotel data includes credit card numbers, passport information, home addresses, phone numbers, travel patterns, and sometimes corporate account information. This data sells on dark web markets for $5-100 per complete record. Identity thieves use it to open fraudulent accounts. Corporate intelligence operatives use travel patterns to identify business relationships and opportunities. The comprehensiveness of hotel data makes it particularly valuable to criminals.
The Future of Hospitality Security
The Washington Hotel attack shows how serious cybersecurity threats are becoming for the hospitality industry. The future likely involves more attacks unless the industry collectively improves security posture.
Hotels need to recognize that cybersecurity is now a business-critical function, not an IT overhead. The same rigor applied to ensuring clean rooms and reliable service needs to apply to protecting customer data and operational systems.
For guests, the message is clear: assume your data might be compromised. This doesn't mean abandoning hotel stays, but it does mean:
- Monitoring financial accounts regularly
- Using credit cards or payment systems that offer fraud protection
- Being cautious about what information you provide
- Assuming that breach disclosures might not capture all compromised data
For the hospitality industry, this incident represents an opportunity to learn and improve before the next major attack occurs. The companies that invest in security now will gain competitive advantage as customers increasingly factor security into their hotel choices.
The Washington Hotel incident wasn't the first major ransomware attack on hospitality and won't be the last. But how the industry responds—whether they view it as a problem to be solved or a cost of doing business—will determine how severe future attacks become.
Real talk: the companies that take this seriously and invest in proper security infrastructure will experience fewer incidents and face lower costs when incidents do occur. Everyone else will eventually learn this lesson the hard way, at significantly higher cost as highlighted by Halcyon.
Key Takeaways
- Washington Hotel (Fujita Kanko) confirmed ransomware attack on February 13, 2025, affecting 30+ properties with 11,000 rooms and 5 million annual guests
- External data storage architecture protected customer membership information while internal business systems were compromised with unauthorized access confirmed
- Rapid incident response within 24 hours, police notification, and external expert engagement limited damage; no threat actors claimed responsibility by investigation conclusion
- Hospitality industry remains top ransomware target due to ransom payment likelihood, guest data value, operational criticality, and legacy system vulnerabilities
- Hotels must implement network segmentation, offline backups, 24/7 monitoring, incident response procedures, and third-party vendor audits to effectively defend against ransomware
- Customers should monitor credit statements for 6-12 months, place fraud alerts, enable two-factor authentication, and assume data breach despite company assurances
Related Articles
- Tenga Data Breach: What Happened and What Customers Need to Know [2026]
- Machine Credentials: The Ransomware Playbook Gap [2025]
- EU Parliament Bans AI on Government Devices: Security Concerns [2025]
- Tenga Data Breach 2025: How a Phishing Email Exposed Customer Data
- X Platform Outage: What Happened, Why It Matters, and How to Stay Connected [2025]
- Cybersecurity & Surveillance Threats in 2025 [Complete Guide]
![Japanese Hotel Chain Hit by Ransomware: What You Need to Know [2025]](https://tryrunable.com/blog/japanese-hotel-chain-hit-by-ransomware-what-you-need-to-know/image-1-1771335589994.jpg)



