Introduction: The Cloud Security Paradigm Shift Nobody Was Expecting
Cloud security has always felt like a game of catch-up. Your infrastructure scales faster than your team can monitor it. New services spin up in minutes. Workloads vanish just as quickly. Meanwhile, your security tools sit around looking at empty playgrounds from the outside, trying to guess what's happening inside.
That fundamental mismatch is what Upwind Security identified back in 2021, when founders with zero traditional security background decided to attack a problem that's plagued enterprises for years: the gap between what security teams can actually see and what's actually running in their cloud environments.
Now, after four years of grinding through customer adoption challenges, technical obstacles, and skeptics asking if anyone even needed their solution, Upwind just secured
But here's what makes this funding announcement different from typical startup success stories. Upwind's journey reveals something crucial about how enterprise technology shifts: the disruption doesn't come from better versions of existing tools. It comes from founders who think differently about the problem because they come from a different world.
The team that built Upwind previously founded Spot.io, a cloud compute optimization platform that NetApp acquired for approximately $450 million in 2020. They weren't security people. They were infrastructure people. They understood how clouds actually work from the inside because they'd spent years building systems that operated at scale across dynamic, ephemeral environments.
That perspective matters. A lot.
Why Runtime-First Security Actually Makes Sense (Even If It's Unconventional)
Before digging into what Upwind does, we need to understand why their approach felt heretical when they started.
The traditional cloud security playbook goes something like this: deploy an agentless scanner that sweeps your environment externally, catalogs everything it finds, flags vulnerabilities, and hands security teams a massive list to triage. This is called "outside-in" security. It's easy to deploy. No agents to manage. No performance overhead. Security teams love it because it requires minimal coordination with infrastructure teams.
The problem? You're trying to understand a dynamic, moving system by looking at its shadows. You see the services that are exposed at the network edge. You see the configurations from the outside. You see what's public. But you miss context. You don't see which API endpoints are actually being called. You don't know whether that exposed database is critical or a test instance nobody uses. You don't understand the traffic patterns or the actual attack surface.
The result is noise. So much noise that security teams essentially ignore half the alerts, which defeats the purpose of having alerts in the first place.
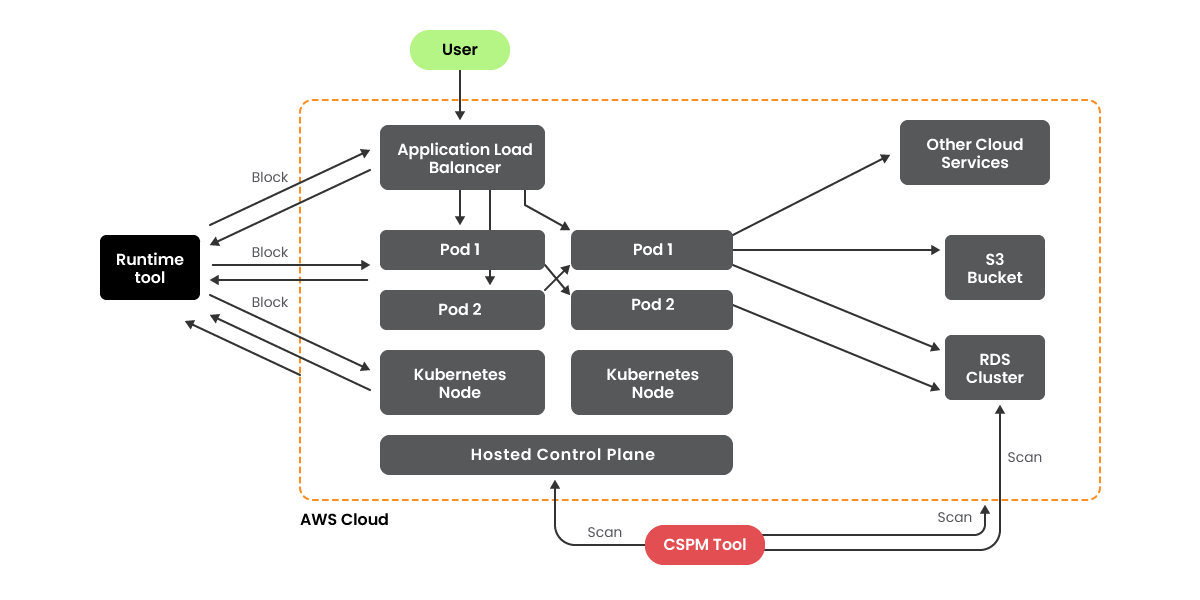
Upwind flipped this. Their "inside-out" approach means deploying lightweight sensors into the actual infrastructure to observe what's happening in real time: network requests, API traffic, process execution, data flows. Instead of guessing what's critical based on external configuration, you see what's actually active. You observe which services are talking to each other. You understand the network topology from the perspective of someone inside the system.
This matters especially for modern cloud architectures. Containers spin up and down constantly. Serverless functions execute for milliseconds and vanish. AI agents talk to each other and to external APIs in patterns that change daily. Ephemeral databases and caches appear when needed and disappear when done. Your Kubernetes cluster looks completely different at 3 AM than it did at noon.
You simply cannot map this complexity from the outside. You need to be inside the system, observing in real time, to understand what's actually running and what actually matters.
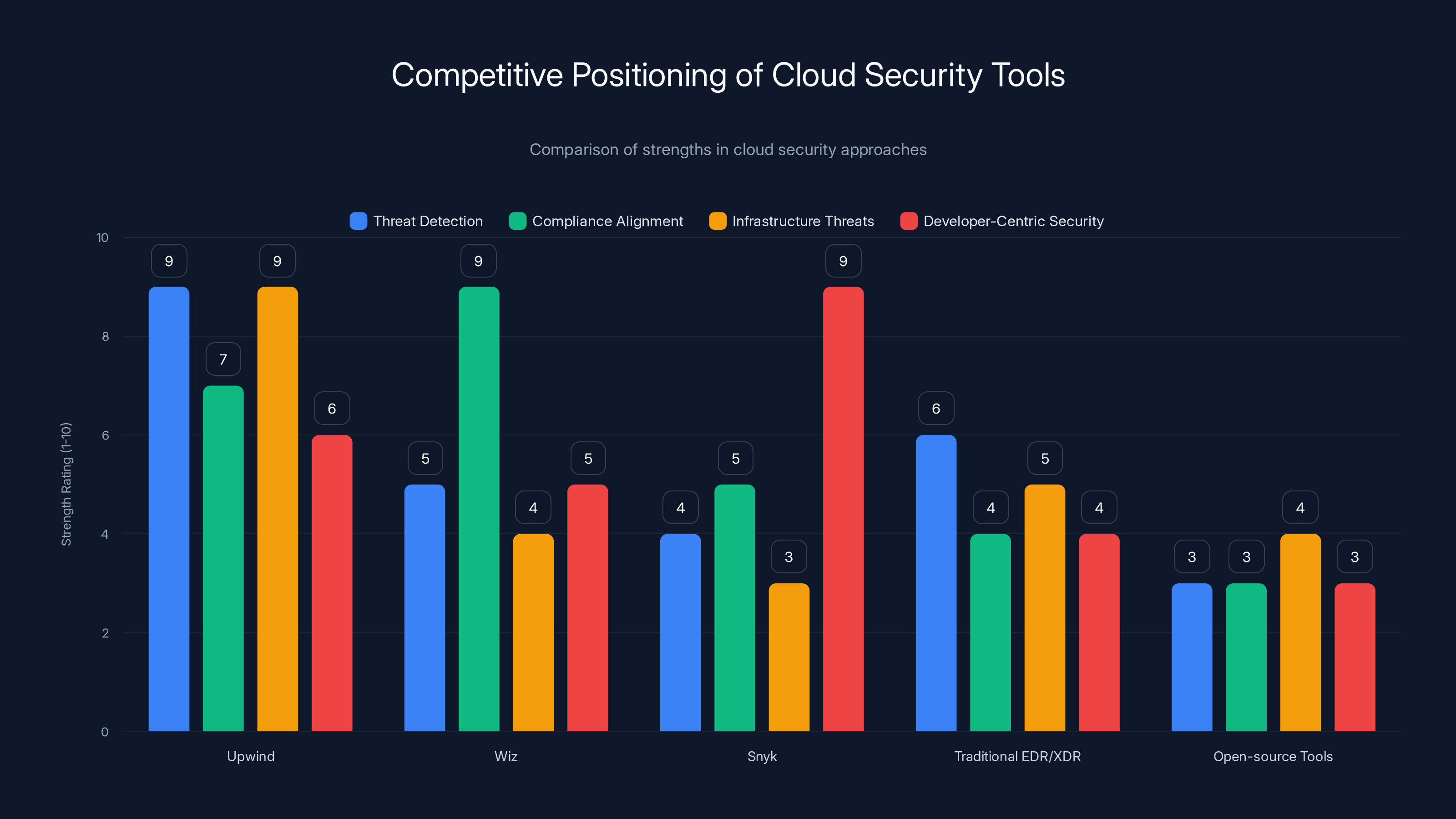
Upwind excels in threat detection and infrastructure threats, while Wiz leads in compliance alignment. Snyk is strong in developer-centric security. Estimated data based on competitive positioning.
The Original Problem: Why Enterprise Cloud Security Stayed Broken
When Upwind's founders came from Spot.io and integrated into NetApp post-acquisition, they got a front-row seat to a crisis happening inside every large enterprise: the fundamental breakdown of communication between infrastructure teams and security teams.
Infrastructure teams (Dev Ops, platform engineers, SREs) understand how cloud services work. They know which APIs are exposed intentionally and which are misconfigured. They understand the data flows. They know which components are critical and which are ephemeral.
Security teams understand threats, compliance requirements, and attack vectors. But they often lack the operational context about how the infrastructure actually works. When they scan an environment and flag issues, they're flagging potential problems based on configuration recommendations and threat models, not based on actual usage patterns.
The result? A security team sends a report saying: "You have 847 security issues." An infrastructure team reads it and thinks: "Yeah, but like... 800 of those don't actually matter in our environment." Nobody's wrong. They just have different information.
This is especially problematic because it creates two outcomes:
First, alert fatigue: Security teams get overwhelmed. They have to manually investigate hundreds of reported issues to determine which ones are actually exploitable given the specific infrastructure context. This is incredibly time-consuming and creates burnout.
Second, missed actual risks: Because teams are drowning in false positives, genuine threats sometimes get overlooked. Or security teams deprioritize investigation because historical experience tells them "90% of these won't matter."
Upwind realized this wasn't a tool problem. It was a visibility problem. The fix required deploying agents into the infrastructure itself so that security teams could see what was actually happening, get better context about which vulnerabilities were real risks versus theoretical ones, and focus their limited time on actual threats.
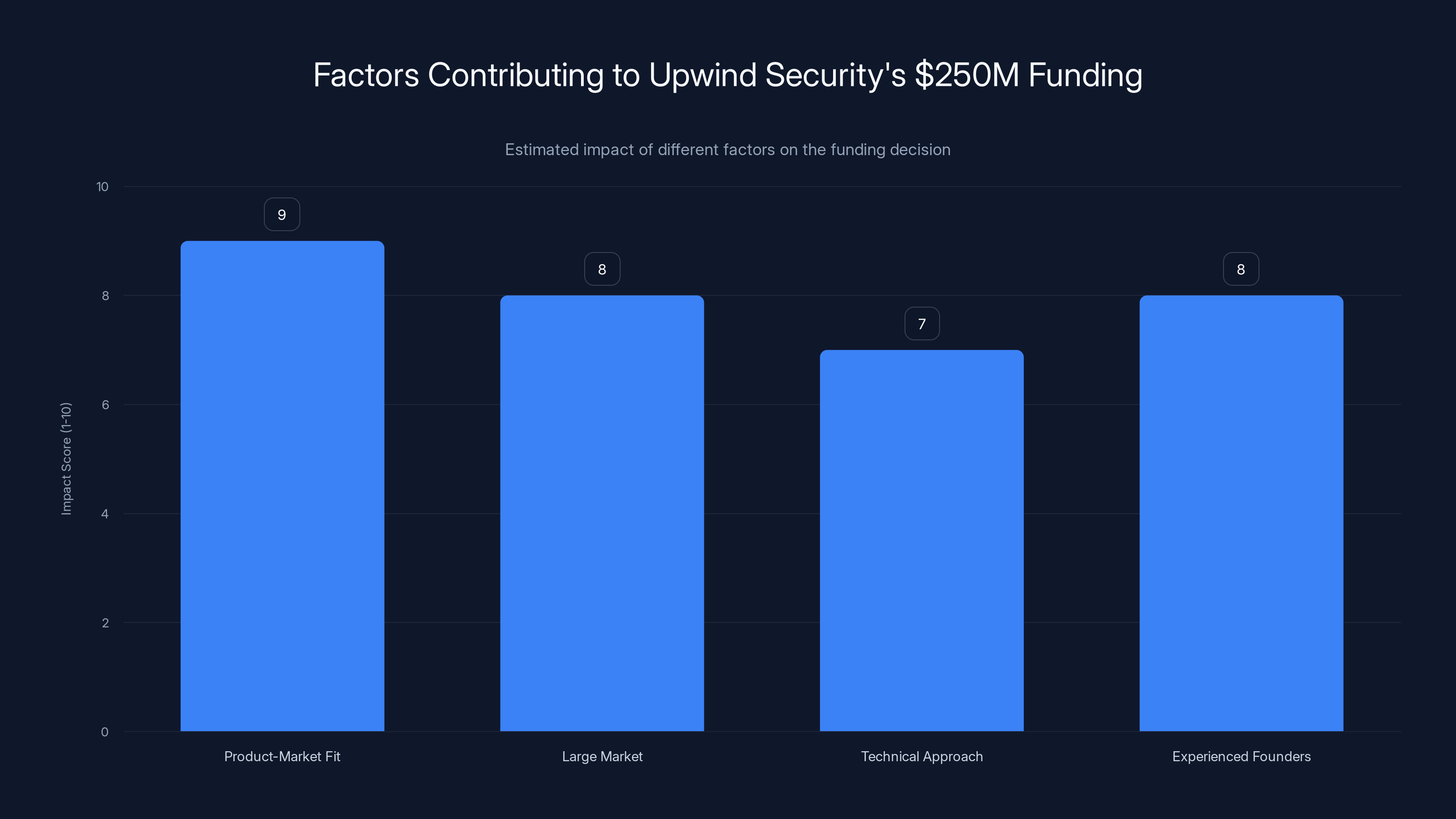
Estimated data: Product-market fit and experienced founders were key factors in Upwind Security's $250M funding, each scoring high in impact.
The Funding Landscape: Why 1.5B Makes Sense Now
To understand why Bessemer Venture Partners and other investors are willing to write $250 million checks for a runtime security platform, you need to understand the market opportunity.
Cloud security is one of those markets that simultaneously feels huge and fragmented. Enterprise spending on cloud security has been growing at 20-25% annually, with the market approaching $20+ billion globally. But unlike earlier security eras (firewall era, endpoint era), cloud security hasn't consolidated around a single category leader.
There's Wiz (founded 2020, recently valued at $12 billion), focused on cloud posture management and misconfiguration detection. There's Snyk, originally known for developer-first security but expanding into runtime protection. There's Datadog, Cloudflare, and dozens of point solutions for specific cloud security problems.
But here's the pattern Upwind saw that differentiated their opportunity: the market was fragmenting not because the problem was solved, but because the problem wasn't fully solved by any single category.
Configuration scanning (misconfigurations are real and dangerous, but they only represent one dimension of risk). Vulnerability scanning (identifies potential issues, but without context about actual exploitation). Network monitoring (useful, but limited to network layer observations). Application security (critical, but often disconnected from infrastructure context).
No single tool was integrating all of these perspectives. And enterprise teams didn't want to buy 10 different tools for cloud security—they wanted platforms that were broad enough to reduce tool sprawl but deep enough to actually solve problems.
Upwind positioned itself as that integrated platform: runtime-first (which differentiates them from the outside-in crowd) but comprehensive enough to address multiple cloud security dimensions.
Investors care about this because it represents a larger addressable market than point solutions.

The Business of Selling Unconventional Security Solutions
Here's something most startup funding announcements gloss over: selling a fundamentally different approach is incredibly hard, especially in security.
Security teams are risk-averse by definition. They'd rather use boring, proven tools than try something different, because deploying the wrong security tool creates liability. If you deploy a tool and it misses something, your company gets breached, and someone needs to explain to regulators and customers why the security tool failed.
Additionally, security teams don't make unilateral technology decisions. They need to coordinate with infrastructure teams. And if the solution requires "deploying agents into production," infrastructure teams get involved (and infrastructure teams are even more skeptical about new tools than security teams are).
Upwind faced this head-on. The traditional sales cycle for security went something like: "We're agentless and easy to deploy." The Upwind pitch was: "We need to deploy agents, but we'll give you better visibility." That's a harder sell, especially to conservative enterprises.
What eventually worked was finding an answer to a question that enterprises were asking but not finding good solutions for: "How do I separate actual cloud security risks from theoretical ones?"
The customers who found Upwind's approach valuable shared certain characteristics:
They had large, complex cloud footprints spanning multiple cloud providers, with hundreds or thousands of services running simultaneously. For these organizations, the false positive problem from agentless scanners wasn't just annoying—it was operationally paralyzing.
They had mature Dev Ops practices where deploying agents was already normal (because they deploy monitoring agents, observability agents, etc.). So the "agent friction" was much lower.
They processed sensitive data at scale, making risk prioritization critical. Healthcare companies, financial services, major platforms. These organizations couldn't afford to miss actual threats because they were drowning in false positives.
The customers Upwind landed—Siemens, Peloton, Roku, Wix, Nextdoor, Nubank—fit this pattern exactly. These are organizations that run massive cloud infrastructure, process sensitive data, and have mature platform engineering teams.
Once Upwind proved this worked, sales acceleration kicked in. Between the Series A in 2024 and the Series B announcement just announced, the company posted 900% year-over-year revenue growth and doubled its customer base. That's not "interesting startup growth." That's "we found something enterprises actually want and are willing to pay for" growth.

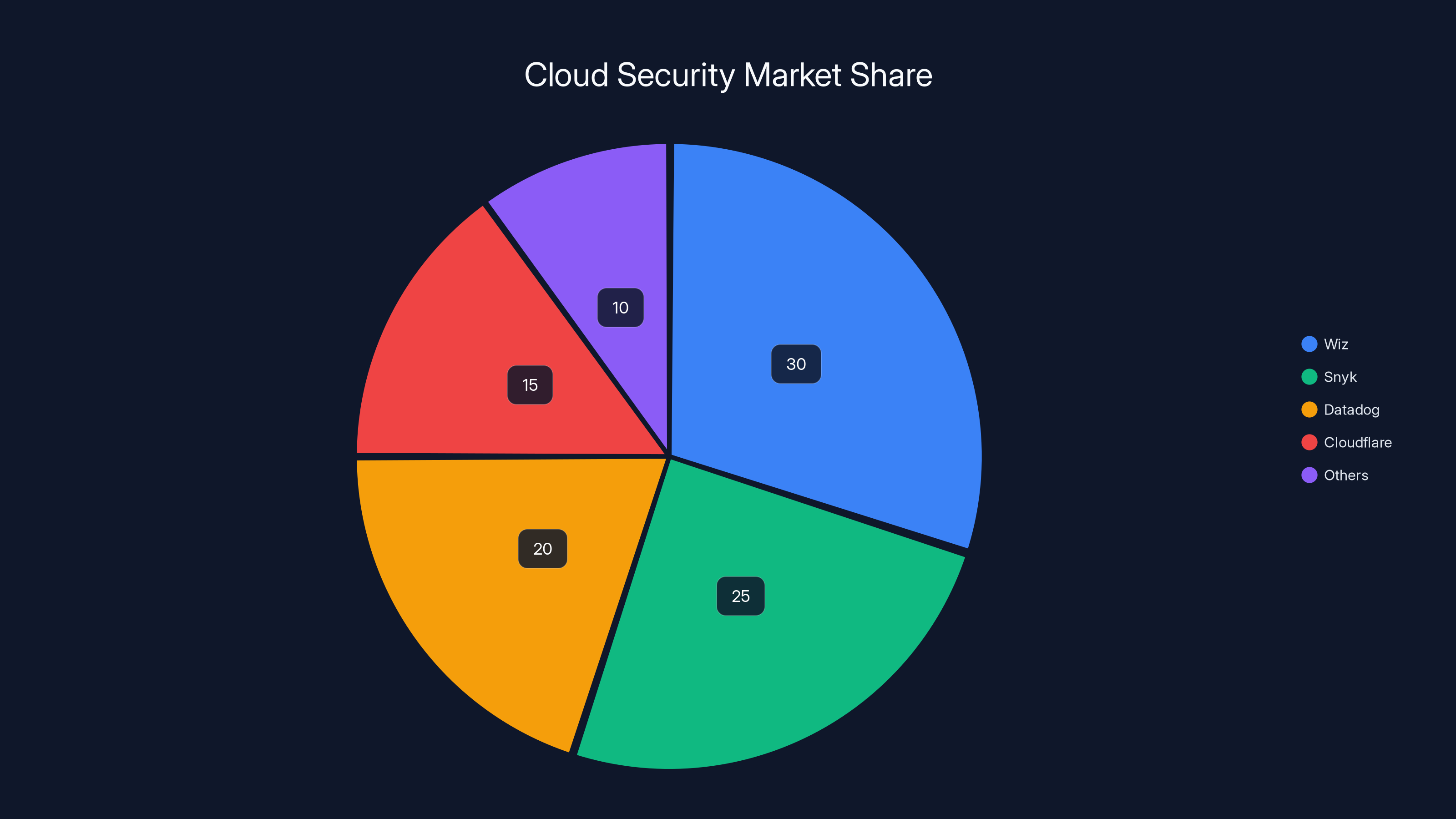
Estimated data shows Wiz leading the cloud security market with a 30% share, followed by Snyk and Datadog. The market remains fragmented with no single dominant player.
The Technical Architecture: How Runtime Visibility Actually Works
To understand why investors are comfortable betting $1.5 billion on this company, you need to understand the technical problem they're actually solving.
Deploying agents into production infrastructure creates several challenges:
Performance overhead: If the monitoring solution slows down applications, infrastructure teams will rip it out. Period. So the agents need to be incredibly lightweight. We're talking imperceptible overhead at 99th percentile latencies.
Data volume: Cloud systems generate insane amounts of network traffic. A single moderate-sized Kubernetes cluster might process billions of events per day. You can't move all that raw data to a central system. The agent needs to aggregate, filter, and synthesize the data locally before shipping only meaningful signals upstream.
Context aggregation: A single security incident involves multiple pieces of context: what service was running, what configuration was present, what network traffic occurred, what API calls were made, what data was accessed. These signals might come from different parts of the infrastructure. The platform needs to correlate them.
Lateral integration: Cloud security doesn't exist in isolation. You need context from vulnerability databases (what known CVEs affect my running software), configuration standards (what does a secure deployment look like), threat intelligence (what attacks are happening in the wild), and compliance requirements (what do regulations require).
Upwind's technical approach addresses this by building a platform that combines lightweight runtime agents with a central data pipeline that correlates signals, applies threat and compliance logic, and surfaces actionable alerts.
The agents collect network metadata (which services talk to which services), process execution data (which applications are running, what they're doing), and API telemetry (what external APIs are being called). They ship this data to the central platform, which correlates it with configuration data, vulnerability intelligence, and threat models to determine what actually matters.
This is computationally complex, which is why you need a company with serious engineering talent to do it well.
Market Expansion: From US to Emerging Cloud Markets
Another signal that Upwind has achieved product-market fit: they're expanding geographically.
Most startups expand geographically when they've saturated their core market, or when they're struggling to find new customers. Upwind is doing it while growing 900% year-over-year, which tells you something important: the market opportunity is bigger than they originally thought.
They've now established presence in:
Established markets: US, UK, Israel (where the founders are from, which gives them cultural advantage)
Emerging markets: Australia, India, Singapore, Japan
Why these specific markets? Because they're where large enterprises are building serious cloud infrastructure. India has the fastest-growing cloud adoption rate globally, with companies like Flipkart, Paytm, and countless fintech startups running massive cloud infrastructure. Japan has financial services and industrial companies deploying cloud at scale. Australia and Singapore have financial services, healthcare, and government agencies with stringent compliance requirements and large cloud footprints.
This geographic expansion is significant because it suggests Upwind has solved something region-agnostic. The technical approach works the same way in Singapore's AWS region as it does in Northern Virginia. The enterprise customer profile (large organizations, sensitive data, mature engineering) exists everywhere.
This also opens up entirely new market opportunities. India's startup ecosystem is exploding, and many of these startups are cloud-native from day one. They have the same cloud security challenges as enterprises, just at smaller scale. Japan's financial services industry is regulated heavily and has serious compliance requirements that runtime security actually helps with.

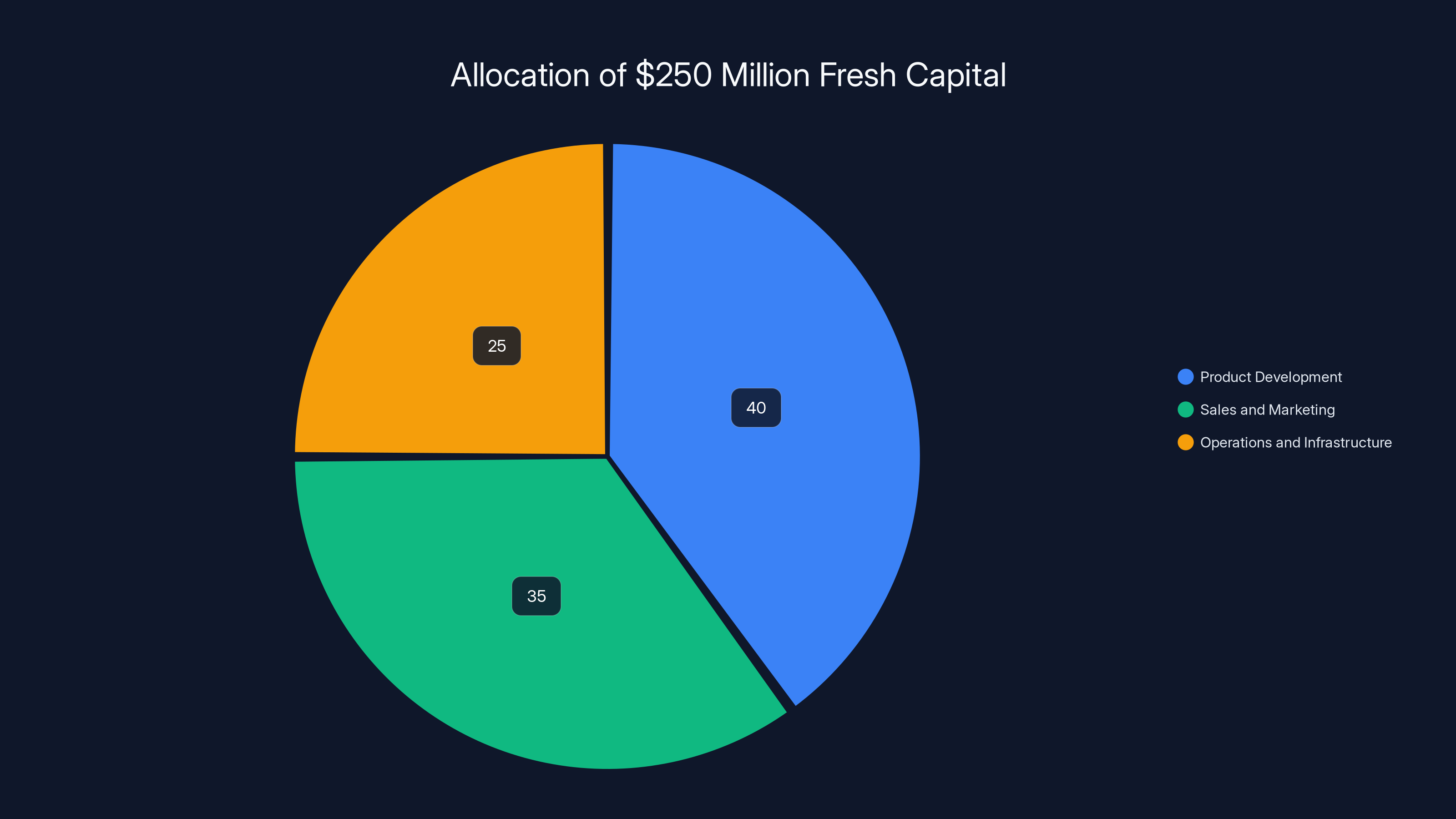
Estimated data suggests that Upwind allocates 40% of its new capital to product development, 35% to sales and marketing, and 25% to operations and infrastructure, supporting sustainable growth.
Competitive Positioning: Why Runtime-First Matters in a Crowded Market
Cloud security in 2025 is crowded. Really crowded. There's Wiz, Lacework, Snyk, Sumo Logic, Datadog, Cloudflare Workers, Sysdig, Falco, Tracee. The list goes on.
Yet Upwind raised
Here's the differentiation:
Outside-in approaches (including Wiz's core posture management) are great at finding misconfigurations and compliance gaps, but they're limited on actual threat detection because they lack runtime context.
Endpoint-focused approaches (like traditional EDR/XDR platforms adapted for cloud) miss infrastructure-level threats because they focus on individual hosts rather than infrastructure patterns.
Network monitoring approaches (like traditional NSM tools) see the network layer but miss application context.
Upwind's "inside-out" approach integrates all three perspectives: it sees configurations, sees host-level activity, sees network patterns, and correlates them all into a coherent picture.
Competitively, this positioning has advantages:
Against Wiz: Wiz is stronger on misconfiguration detection and compliance alignment. Upwind is stronger on actual threat detection and anomaly identification.
Against Snyk: Snyk is stronger on developer-centric security (SAST, SCA). Upwind is stronger on infrastructure-layer threats.
Against traditional EDR/XDR vendors: Upwind is cloud-native from the ground up and understands ephemeral infrastructure. EDR vendors are adapting from endpoint-native design.
Against open-source tools (Falco, Tracee): Upwind provides integrated platform with threat intelligence, compliance mapping, and operational workflows. Open-source tools are powerful but require significant engineering investment to operationalize.
This differentiation matters to investors because it suggests Upwind has defensible positioning. They're not competing on price (they charge premium pricing for enterprises). They're competing on technical differentiation that's hard to replicate.

The Role of AI and Automated Threat Response
The funding announcement specifically mentions Upwind plans to invest in AI security capabilities within their cloud security platform.
This matters more than it might initially seem, because AI changes how runtime security works.
Traditional security relies on humans to triage alerts, investigate them, and decide on remediation. With the volume of data modern cloud systems generate, this is impossible to do manually. A single security incident might involve thousands of correlated events across dozens of services.
AI changes this in two ways:
First, AI can synthesize data faster than humans. Instead of a human security analyst spending 30 minutes investigating an incident (searching logs, correlating events, understanding the threat), an AI system can synthesize the same data in seconds. "These network anomalies correlate with this configuration change, combined with this vulnerability in this service, which creates this specific attack vector." Done.
Second, AI can learn normal patterns automatically. Runtime security's advantage is that it observes actual behavior. But "actual behavior" includes lots of legitimate variation. One team deploys services differently than another team. One region has different traffic patterns than another. AI can learn what normal looks like for your specific infrastructure, which makes anomaly detection work much better.
Upwind's plan to invest in AI suggests they understand this evolution. They're not just building a better rules engine. They're building systems that can learn, synthesize, and respond to threats at the speed of cloud infrastructure.
This also matters for developers. The announcement mentions plans to "extend its approach closer to developers to help prevent misconfigurations before they reach production." This is huge because it moves security left. Instead of finding problems in production and then scrambling to fix them, you catch them in development or CI/CD.
At runtime, you're observing what developers actually deployed. Armed with that observation, you can help developers understand the security implications of their configuration choices before they push to production. "You're about to deploy a database with no encryption key rotation. Here's why that matters." This is how security becomes an enabler rather than a blocker.

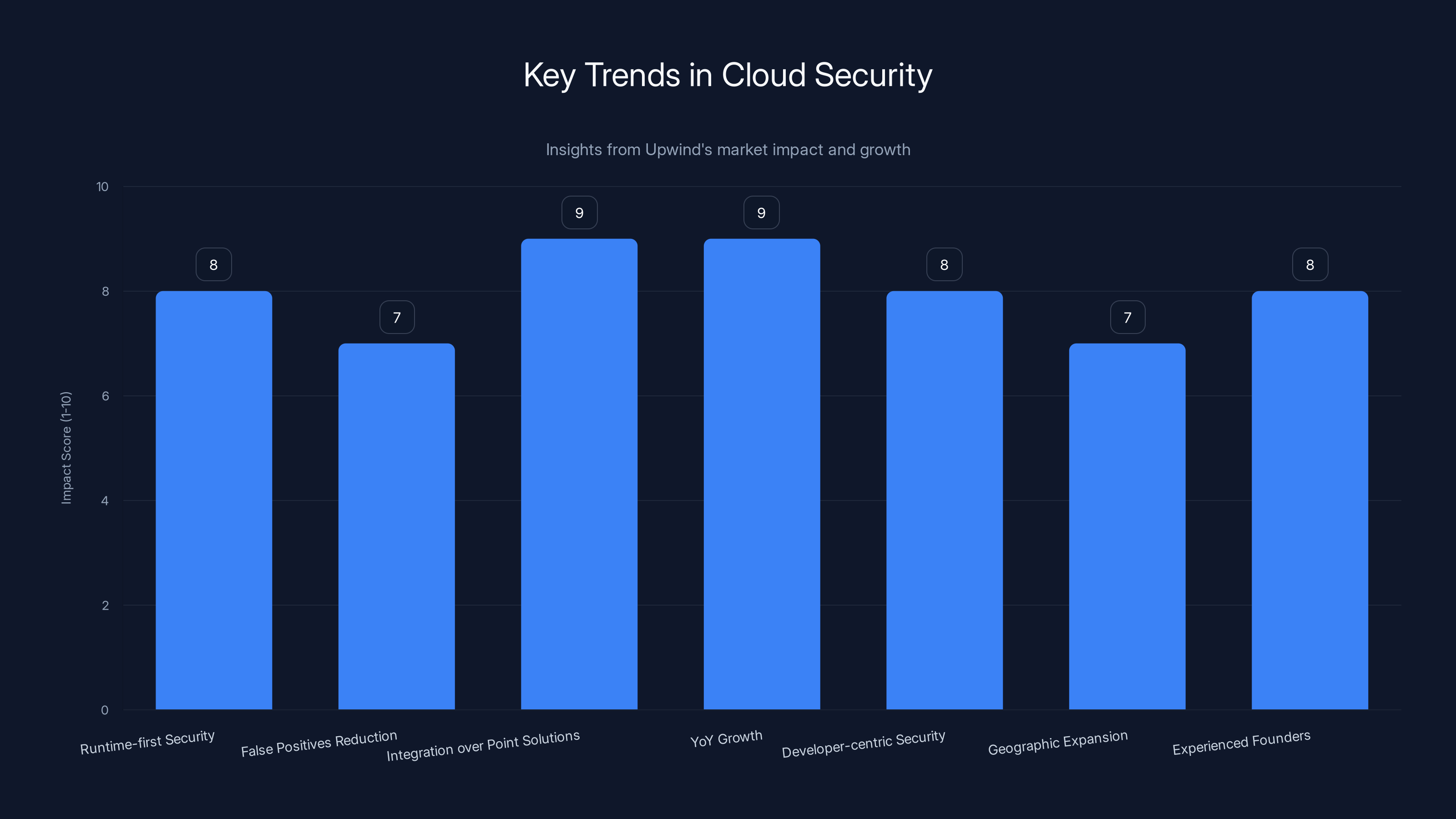
Estimated data shows that integration over point solutions and significant YoY growth are the most impactful trends in cloud security, highlighting the importance of comprehensive platforms and market demand.
Developer-Centric Security: The Next Evolution
One of the most interesting phrases in the funding announcement is Upwind's plan to "extend its approach closer to developers."
This reveals a crucial insight about where cloud security is heading: toward developer-embedded security.
Historically, security has been something that happens after development. Developers write code, deploy it, and security teams check if it's secure. This creates friction, delays, and sometimes security gets compromised because developers want to ship.
Modern companies are inverting this. Security should be embedded in the developer experience, not bolted on afterward.
For Upwind, this means:
In development environments: Developers working on local Kubernetes clusters or dev cloud environments can see in real time what security implications their changes have. They can understand before deploying to production whether their configuration is secure.
In CI/CD pipelines: Automated checks can analyze configurations before they're deployed, providing immediate feedback about security issues.
In deployment workflows: As developers deploy, they get instant feedback about whether they're violating security policy, creating unusual network patterns, or deploying vulnerable software.
This is fundamentally different from traditional security, which is more like: "Deploy whatever you want, then we'll scan it and tell you if it's bad."
The reason this matters is that it aligns incentives. Developers care about shipping fast and shipping correctly. Security teams care about keeping systems secure. Developer-embedded security lets both things happen simultaneously.
For companies like Upwind, developer-focused expansion opens entirely new use cases and potentially new customer segments. Instead of just selling to the security team (who has to convince the infrastructure team to deploy agents), you sell directly to infrastructure teams and development teams who benefit from the visibility themselves.

Operational Excellence: Why 900% Yo Y Growth is Sustainable
Rapid growth doesn't always indicate healthy business. Sometimes startups grow fast and then hit a wall because they can't maintain the trajectory.
But Upwind's growth appears structurally sound for several reasons:
Product-market fit signals: They doubled their customer base while achieving 900% revenue growth. That's not just "adding more revenue from existing customers." That's both land (new customers) and expansion (more revenue per customer). This indicates the product is becoming more valuable as it matures, not less.
Geographic expansion while maintaining growth: Companies that expand geographically often see growth rates decline initially as they invest in new regions. Upwind is expanding geographically while maintaining growth rates, which suggests their growth is inertial and they're adding new market opportunities.
Enterprise customer quality: The customer list reads like a "who's who" of companies that take security seriously. These are companies that will spend money to solve real problems. They're not price-sensitive customers who will churn if a cheaper competitor emerges.
Funding environment validation: Bessemer Venture Partners is one of the most selective VCs in the world. They invest in 20-30 companies per year out of thousands of applications. That they're leading this round at $1.5 billion valuation signals that other serious investors also believe in the opportunity.
The $250 million in fresh capital will be allocated toward:
Product development: Continuing to expand the platform's capabilities, improve AI-assisted threat detection, and extend functionality closer to developers.
Sales and marketing: Accelerating customer acquisition in existing and emerging markets.
Operations and infrastructure: Building the support systems, compliance certifications, and infrastructure to serve enterprise customers at scale.

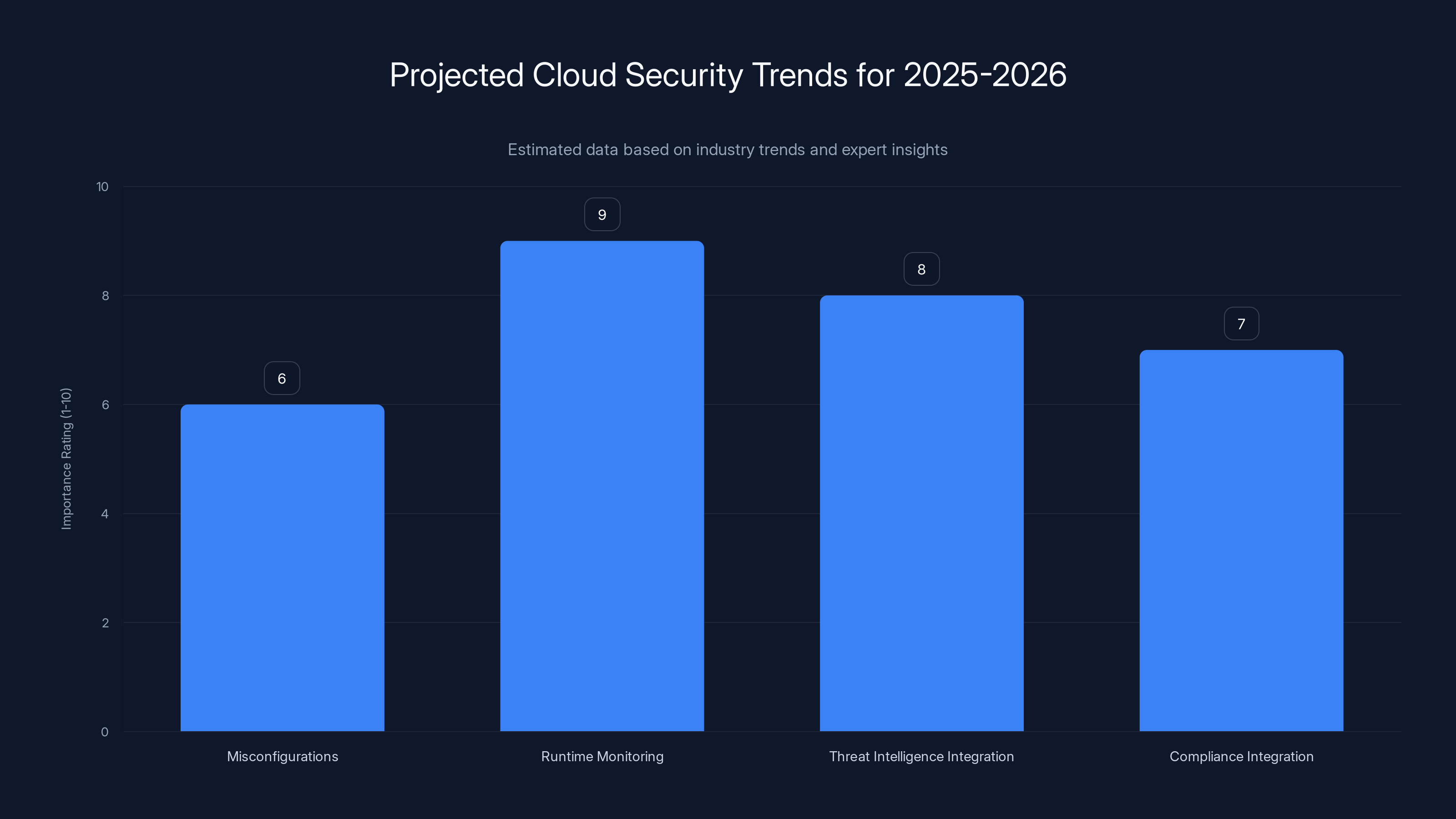
Runtime monitoring is projected to become the most critical focus area in cloud security by 2025-2026, reflecting a shift towards real-time threat visibility and response. Estimated data.
Looking Forward: The 2025-2026 Cloud Security Landscape
Why does this funding round matter beyond just a startup achieving a high valuation?
Because it signals a shift in how enterprises think about cloud security.
For the last 5-7 years, the default position was: "We need broader cloud posture management because we have misconfigurations everywhere." That's real. Misconfigurations are a massive category of cloud security issues.
But the next evolution is: "We need better visibility into what's actually running and what's actually threatening us, not just what could be threatening us."
This shift favors runtime-first approaches. It favors platforms that can correlate data from multiple sources. It favors approaches that integrate threat intelligence, compliance requirements, and development workflows.
Upwind's positioning and funding put them in an advantageous place for this shift. They're not trying to be the best outside-in scanner. They're not trying to be the best endpoint EDR platform adapted for cloud. They're building something different and proving that enterprises want it.
This will likely accelerate competition in the runtime security category. Wiz will probably add more runtime capabilities. Existing endpoint vendors will continue evolving their cloud features. But Upwind has first-mover advantage in the "inside-out cloud security platform" category, plus proven product-market fit, plus $250 million in capital to expand.
For enterprises evaluating cloud security, this matters because it validates an architectural approach that actually solves problems. If Upwind's approach was niche or limited, they wouldn't be at $1.5 billion valuation with major VCs backing them.

The Human Element: Why Founder Background Matters
There's a crucial detail in the Upwind story that's easy to gloss over: the founders come from infrastructure, not security.
This shaped their entire approach. They didn't think "how can we build a better security tool?" They thought "how can we give security teams the visibility that infrastructure teams have?"
This outside-perspective advantage is common in category-creating companies. The founders know something the category experts don't because they come from a different discipline.
It also affected how they handled early rejection. When customers said "we don't want agents," Upwind didn't give up. They understood why customers said this (risk aversion, operational overhead) and built a product that addressed those concerns (minimal overhead, operational benefits beyond security).
When the market seemed uncertain, the founders held conviction because they'd already proven they could build and sell technology at scale (Spot.io to NetApp for $450 million). They understood enterprise sales, customer problems, and technical execution. This confidence mattered during the years where "80% of the time it felt like we weren't heading in the right direction."
This matters to investors because founder-market fit is predictive of success. Experienced founders in new categories tend to outperform because they understand how to execute, survive ambiguity, and build enterprise relationships.

Implications for Enterprises and Development Teams
If you're an enterprise responsible for cloud security, this funding round signals something important: runtime-first approaches are becoming mainstream.
This means:
Agentless scanning is probably not enough for comprehensive cloud security. You need visibility into what's actually running and what's actually threatening you. If your current security platform is purely external scanning, you're probably missing things.
You should care about false positive reduction, not just alert generation. The ability to say "we have 10 real threats" instead of "we have 1,000 potential threats" is worth paying for.
Integration and consolidation matter. Cloud security is fragmenting into point solutions. Platforms that combine multiple perspectives (configuration, threat, runtime behavior) provide more value than narrow point solutions.
Developer alignment is increasingly important. Security platforms that work with developers instead of against them will be more successful at actually improving security.
For development teams, this matters because it means:
Security doesn't have to be friction. Modern platforms can provide security visibility without slowing you down or creating operational overhead.
Visibility is a capability you should expect. If your security platform can't tell you why something is risky ("this specific configuration creates this specific risk"), it's not sophisticated enough.
Left-shift is becoming feasible. You don't have to wait for production deployments to understand security implications. Tooling exists to catch issues in development.
Conclusion: Why This Round Matters More Than Typical Funding Announcements
On the surface, Upwind's $250 million Series B is a funding announcement. It's the kind of story that appears in Tech Crunch, gets shared in Slack channels, and then moves on.
But if you understand the underlying dynamics, this round signals something bigger: a fundamental shift in how enterprises approach cloud security.
For the last decade, cloud security was fragmented. You buy a posture tool to check configurations. You buy an endpoint tool to monitor hosts. You buy a network tool to watch traffic. You buy a vulnerability scanner. You buy threat intelligence. You buy a SIEM. You have ten tools, they don't talk to each other, your security team is drowning in noise, and you're still missing threats.
Upwind's approach—runtime-first, internally visible, correlated across the full stack—is compelling because it actually solves the fragmentation problem instead of adding to it.
The fact that Bessemer Venture Partners, Salesforce Ventures, and Picture Capital believe in this approach enough to write a $250 million check doesn't necessarily mean Upwind will dominate the market. (Markets are complex, competition is real, and capital doesn't guarantee success.)
But it does signal that serious investors believe enterprises want what Upwind is building. And investor capital tends to follow real market demand.
For companies building cloud infrastructure, or security teams responsible for protecting cloud systems, or developers deploying code at scale, this matters. It means the tools and approaches to actually solve cloud security are reaching maturity. The era of "cloud security is hard, there's too much noise, we'll do our best" is ending.
The era of "we have visibility into what's running, we understand actual threats, we're confident in our security posture" is beginning.
Upwind's
For everyone responsible for security in cloud environments, this is genuinely good news. It means better tools are coming, the industry is heading toward integration instead of fragmentation, and the false positive problem is becoming a solvable challenge rather than an intractable feature of cloud security.

FAQ
What is runtime cloud security and how does it differ from traditional cloud security approaches?
Runtime cloud security observes what's actually executing, communicating, and processing data in real time, rather than analyzing static configurations externally. Traditional "outside-in" approaches scan cloud environments from the outside, identifying misconfigurations and potential vulnerabilities. Runtime-first approaches deploy lightweight agents to observe actual behavior internally, providing context that helps distinguish real threats from theoretical ones. This internal perspective is particularly valuable for ephemeral infrastructure like containers, serverless functions, and Kubernetes clusters that are constantly changing.
Why did Upwind Security raise 1.5 billion valuation specifically?
The funding reflects several factors: first, strong product-market fit evidenced by 900% year-over-year revenue growth and doubling of the customer base. Second, a large addressable market for comprehensive cloud security platforms that reduce false positives and tool fragmentation. Third, a differentiated technical approach that competitors haven't fully replicated, giving them first-mover advantage in the runtime-first category. Finally, experienced founders with proven track records (prior $450 million exit with Spot.io) and the ability to navigate uncertain markets.
What are the main advantages of Upwind's "inside-out" security approach?
Inside-out security provides context that outside-in scanning cannot. By observing actual runtime behavior, Upwind can correlate network traffic patterns, process execution, API calls, and configuration data to understand what's actually risky in your specific environment. This dramatically reduces false positives because the platform understands which vulnerabilities are actually exploitable given your infrastructure, which services are genuinely critical, and which API exposures represent real risk. This contextual understanding means security teams can focus on genuine threats rather than investigating hundreds of alerts that don't matter.
How does runtime security help with the false positive problem in cloud security?
False positives occur when security tools flag potential issues that aren't actually risks in your environment. External scanners generate false positives because they lack context—they see a database is exposed to the internet and flag it as risky, but they don't know if that's intentional or if it's actually being accessed. Runtime security observes actual usage patterns: is the database actually being accessed? By which services? With what frequency? Is this normal? This context transforms a potential problem into an actual risk assessment. An exposed database that's never accessed has different implications than one that's actively being probed.
What specific customer problems does Upwind solve that other cloud security vendors don't?
Upwind primarily solves the alert fatigue and context problem. For large enterprises with massive cloud footprints (like Siemens, Roku, Nubank), external scanners generate thousands of alerts that require manual investigation. Upwind's integration of runtime visibility, threat intelligence, and configuration data means alerts come with context: "This specific misconfiguration is exploitable because this service is receiving inbound traffic from an untrusted network with this specific pattern." This lets security teams move from "what could be wrong" to "what is actually wrong," improving both security outcomes and operational efficiency.
How does Upwind's approach to developer-centric security differ from traditional security workflows?
Traditional security finds problems after developers deploy code. Upwind's developer-centric approach aims to shift security left, providing visibility and feedback during development and CI/CD stages. Developers can see in real time what security implications their configuration choices create. Instead of discovering in production that a deployment violates security policy, developers understand the implications before pushing. This alignment between developer incentives (ship fast and correctly) and security objectives (keep systems secure) makes security enablement rather than obstruction.
Why is geographic expansion to India, Japan, Singapore, and Australia significant for Upwind?
These markets have rapidly growing cloud adoption among enterprises that process sensitive data and face compliance requirements. India's fintech and startup ecosystem is growing explosively, with cloud-native companies from day one. Japan has stringent financial services regulation requiring sophisticated security controls. Australia and Singapore have healthcare, financial services, and government sectors with large cloud infrastructure. Expanding to these markets while maintaining growth rates suggests Upwind's technology is region-agnostic and the underlying customer profile (large enterprises, sensitive data, mature engineering) exists globally.
What role will AI play in Upwind's platform moving forward?
Upwind plans to invest in AI-powered threat detection that can synthesize runtime data, correlate events, and identify threats faster than manual investigation. AI can learn what normal behavior looks like for your specific infrastructure, making anomaly detection more effective. Additionally, AI can automate the investigation process—instead of humans spending 30 minutes correlating events across logs, the system can synthesize the same data in seconds. This accelerates threat response and makes the platform more effective at enterprise scale where data volumes are enormous.
How does Upwind's $250 million Series B funding compare to other cloud security companies' fundraising?
Upwind's funding is significant both in absolute terms and in context. Bessemer Venture Partners' leadership indicates confidence from tier-one investors. The
What should enterprises look for when evaluating cloud security platforms after Upwind's funding announcement?
Consider: Does the platform provide sufficient context to distinguish actual threats from theoretical ones? Can it reduce false positive investigation time? Does it integrate multiple security perspectives (configuration, runtime behavior, threat intelligence) or is it a point solution? Can it work with your development workflow or does it primarily operate post-deployment? Does it provide visibility into ephemeral infrastructure like containers and serverless functions? The fact that Upwind is achieving 900% growth while other platforms exist suggests enterprises increasingly care about these factors when making purchase decisions.
Key Takeaways
-
Runtime-first security is becoming mainstream: Upwind's $1.5 billion valuation validates that enterprises want visibility into what's actually running, not just what could be misconfigured.
-
False positives are becoming a solvable problem: The combination of runtime visibility, threat intelligence, and configuration data allows platforms to distinguish real risks from noise.
-
Integration beats point solutions: Fragmented cloud security tools create operational burden. Platforms that consolidate multiple perspectives have defensible positioning.
-
900% Yo Y growth indicates sustainable business model: Upwind's expansion suggests founder-market fit and genuine customer need, not just capital-fueled growth.
-
Developer-centric security is the future: Shifting security left into development and CI/CD stages aligns incentives and prevents problems earlier.
-
Geographic expansion validates global opportunity: Upwind's expansion to India, Japan, Singapore, and Australia suggests cloud security challenges are universal.
-
Experienced founders outperform in new categories: Upwind's team proved they could build, sell, and scale technology before attempting cloud security, which informed their execution.

Related Articles
- Outtake's $40M AI Security Breakthrough: Inside the Funding [2025]
- Browser-Based Attacks Hit 95% of Enterprises [2025]
- WinRAR Security Flaw CVE-2025-8088: Complete Defense Guide [2025]
- Enterprise AI Security Vulnerabilities: How Hackers Breach Systems in 90 Minutes [2025]
- Okta SSO Under Attack: Scattered LAPSUS$ Hunters Target 100+ Firms [2025]
- Europe's Digital Sovereignty Crisis: Breaking Free From US Tech Dominance [2025]
![Upwind Security's $250M Series B: Runtime Cloud Security's Defining Moment [2025]](https://tryrunable.com/blog/upwind-security-s-250m-series-b-runtime-cloud-security-s-def/image-1-1769692293494.jpg)



