Browser-Based Attacks Hit 95% of Enterprises—and Traditional Security Never Sees Them Coming
Your web gateway missed it. Your cloud access broker didn't catch it. Your endpoint protection had no idea.
Yet 95% of organizations got hit by browser-based attacks last year.
That's not speculation. Omdia surveyed over 1,000 IT and security leaders across enterprises, and the data is brutal: nearly every organization faces threats that slip past every layer of traditional security infrastructure.
Three massive campaigns in 12 months made this impossible to ignore. Shady Panda infected 4.3 million users through extensions that looked completely legitimate for seven years. Cyberhaven's security extension got weaponized against 400,000 corporate customers on Christmas Eve. Trust Wallet lost $8.5 million from 2,520 wallets in 48 hours. None of these triggered traditional alerts.
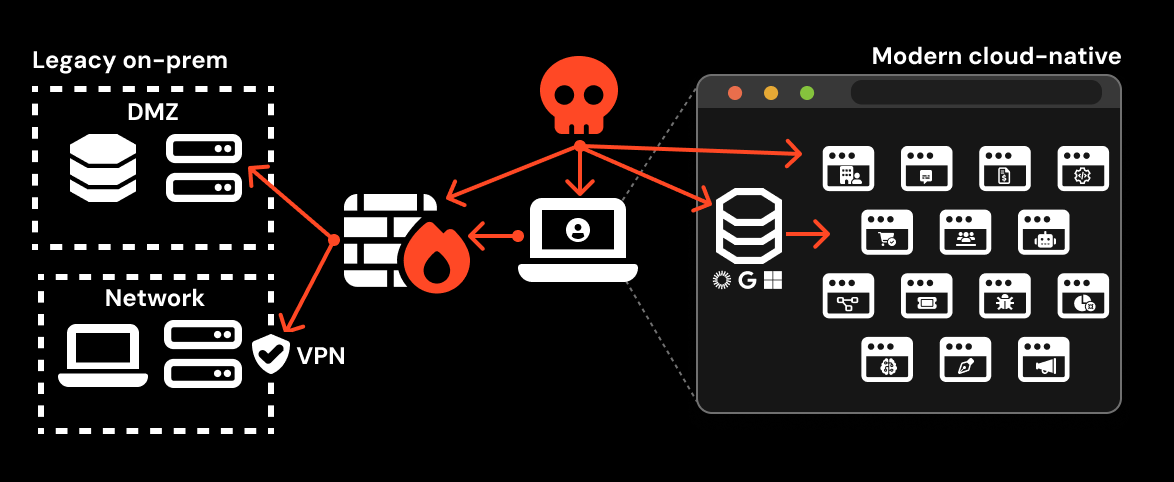
Here's the problem: browsers have become the actual execution environment for enterprise work. Yet security teams still treat them like windows, not attack surfaces.
Work happens in the browser. Communication happens there. Authentication happens there. AI happens there. Cloud applications live there. And attackers know this better than most security architects.
The gap is widening because the fundamental assumption underlying traditional security is broken. Legacy systems assume "trust once, forget forever." They inspect traffic before authentication, then assume everything after login is safe. They were never designed for threats operating inside authenticated sessions with valid credentials and legitimate tokens.
In this article, we'll break down why 95% feels inevitable, examine the three attack patterns that are actually happening right now, and explore the six operational defenses that CISOs running production systems say actually reduce exposure.
TL; DR
- 95% of enterprises experienced browser-based attacks last year, with traditional security detecting virtually none of them
- 64% of encrypted traffic goes uninspected, and 65% of organizations lack control over data shared in AI tools
- Three real attack campaigns (Shady Panda, Cyberhaven, Trust Wallet) show attackers no longer need zero-days or phishing—they exploit legitimate supply chains
- Browser isolation alone isn't enough—threats operate inside authenticated sessions, making credential-based detection fundamentally broken
- Six operational patterns consistently reduce exposure: extension auditing, session behavior analysis, token replay detection, AI tool controls, data exfiltration monitoring, and post-authentication access controls
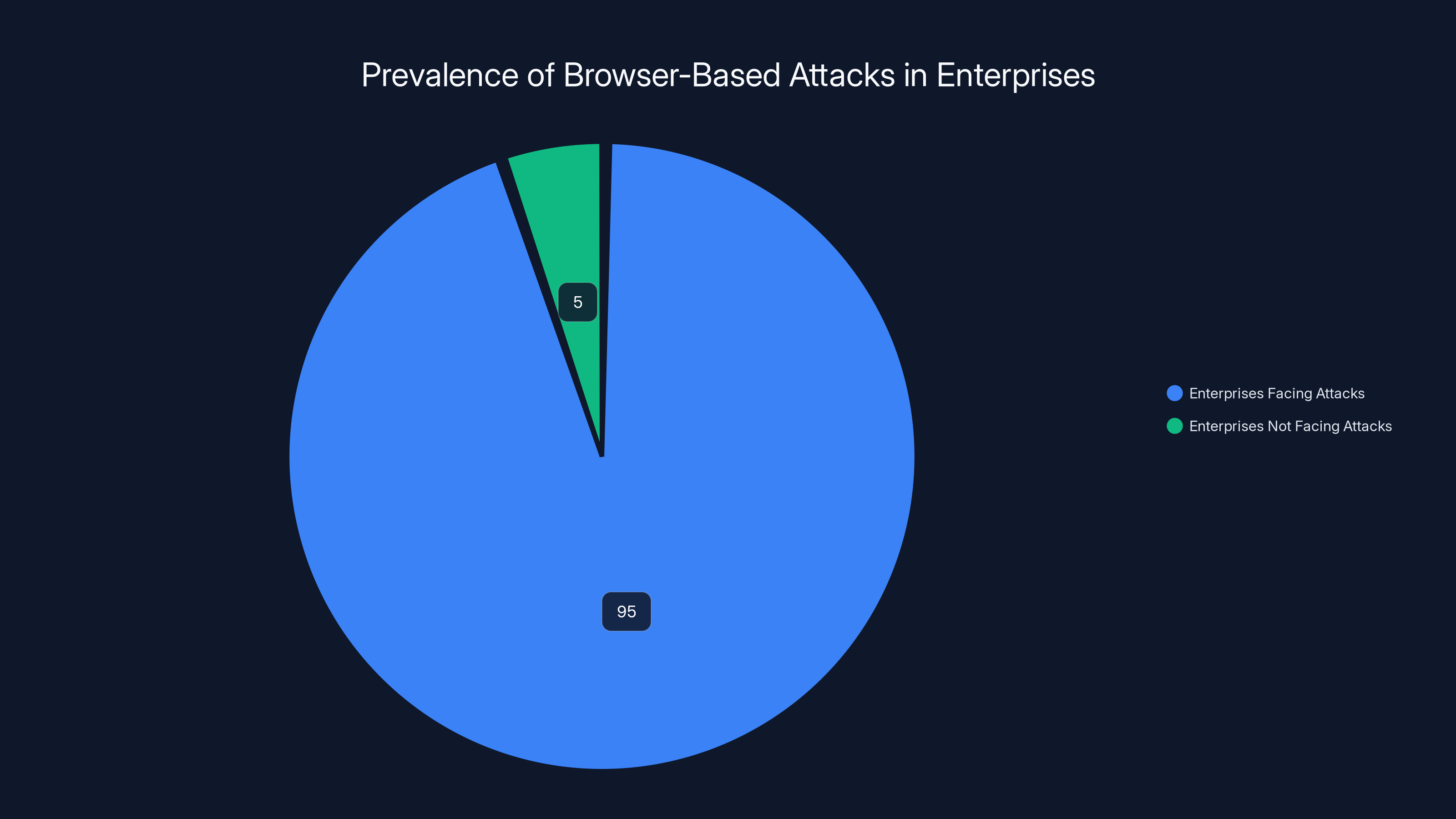
An estimated 95% of enterprises face browser-based attacks due to universal browser usage and legacy security blind spots. Estimated data.
Why Traditional Security Architecture Treats Browsers Like Ancient History
Vendors built enterprise security for a world that doesn't exist anymore.
Let's trace how we got here. In 2005, the browser's job was straightforward: render HTML, run basic Java Script, fetch static content. Your security stack worked around that model. Deploy a web gateway to inspect traffic. Use a firewall to block bad IPs. Run antivirus to catch malware. The browser was a dumb terminal.
Then came the first SaaS applications around 2008. Then cloud storage. Then cloud identity providers. Then real-time collaboration. Then AI assistants. Now the browser is where Oracle, Salesforce, Microsoft 365, Google Workspace, Slack, and Claude all run.
Your security architecture didn't evolve with it.
Traditional endpoint detection and response (EDR) products were built for processes running on the operating system. They watch when a program tries to write to disk, makes a network request, or accesses memory. But browser extensions run inside the browser process. Gen AI tools run inside browser tabs. SaaS applications run inside browser windows. Your EDR can see "chrome.exe is running," but it can't see what's happening inside that process without deep visibility into the Java Script execution layer.
The encryption problem is worse. Cloudflare and network security research consistently shows that 64% of encrypted traffic inside enterprises never gets inspected. Why? Because decryption at scale is expensive. It's computationally intensive. It creates privacy concerns. So most organizations don't inspect HTTPS traffic at all.
But where do SaaS applications send data? Over HTTPS. Where do Gen AI tools receive your data? Over HTTPS. Where do credential stealers exfiltrate tokens? Over HTTPS.
Traditional security sees the traffic, knows it's encrypted, and moves on.
The third blind spot is behavioral. Once someone authenticates, the assumption is they're trusted. If an attacker steals that person's session token or API key, the system still sees valid credentials. MFA already passed. The user's identity is legitimate. From the perspective of traditional security, everything looks normal.
This is where session hijacking lives, and it's invisible to legacy tools.
The Extension Problem Nobody Wanted to Talk About
Browser extensions are a software supply chain living inside your endpoints.
Think about what an extension can do. It can read every page you visit. It can modify form data before you submit it. It can intercept network requests. It can steal cookies. It can access your password manager. Some extensions literally have permission to do anything Java Script can do, which is close to everything.
Now think about the supply chain. A developer builds an extension. They submit it to the Chrome Web Store or Microsoft Edge Add-ons store. The store reviews it—this review is manual and can take days. Eventually it gets approved, maybe with a "Featured" or "Verified" badge. Millions of users download it. Auto-update is enabled by default.
Now the attacker controls the extension's GitHub repository or pays off the developer. They push an update. Within 48 hours, millions of corporate users have auto-updated to compromised code.
Shady Panda is the textbook example. The attackers didn't build a malicious extension from scratch. They bought legitimate extensions that had accumulated "Featured" and "Verified" badges over years. They ran clean code for seven years. They accumulated millions of users and positive reviews. Then they pushed an update that turned the extension into a backdoor.
The clean version was legitimate. The malicious version was indistinguishable from a normal update. The update process worked exactly as designed.
Cyberhaven's incident was different but equally effective. An attacker phished one Cyberhaven developer's credentials. That's it. One person. They used those credentials to upload a malicious version of Cyberhaven's security extension to the Chrome Web Store. The store approved it (this happened over Christmas, so review speed was even faster than normal). 400,000 corporate customers woke up to find they'd installed a backdoor that claimed to protect them.
Trust Wallet used a different vector. An attacker obtained a leaked Chrome Web Store API key. They didn't need developer credentials. They didn't need to phish anyone. With just the API key, they could push updates directly, bypassing all internal release controls. $8.5 million was gone in 48 hours.
The core issue is that extensions behave like legitimate software until they don't. There's no difference between a malicious update and a critical security update until after the code runs. Traditional security can't detect this because it assumes the software publisher is trustworthy. Once the publisher's supply chain is compromised, all assumptions collapse.
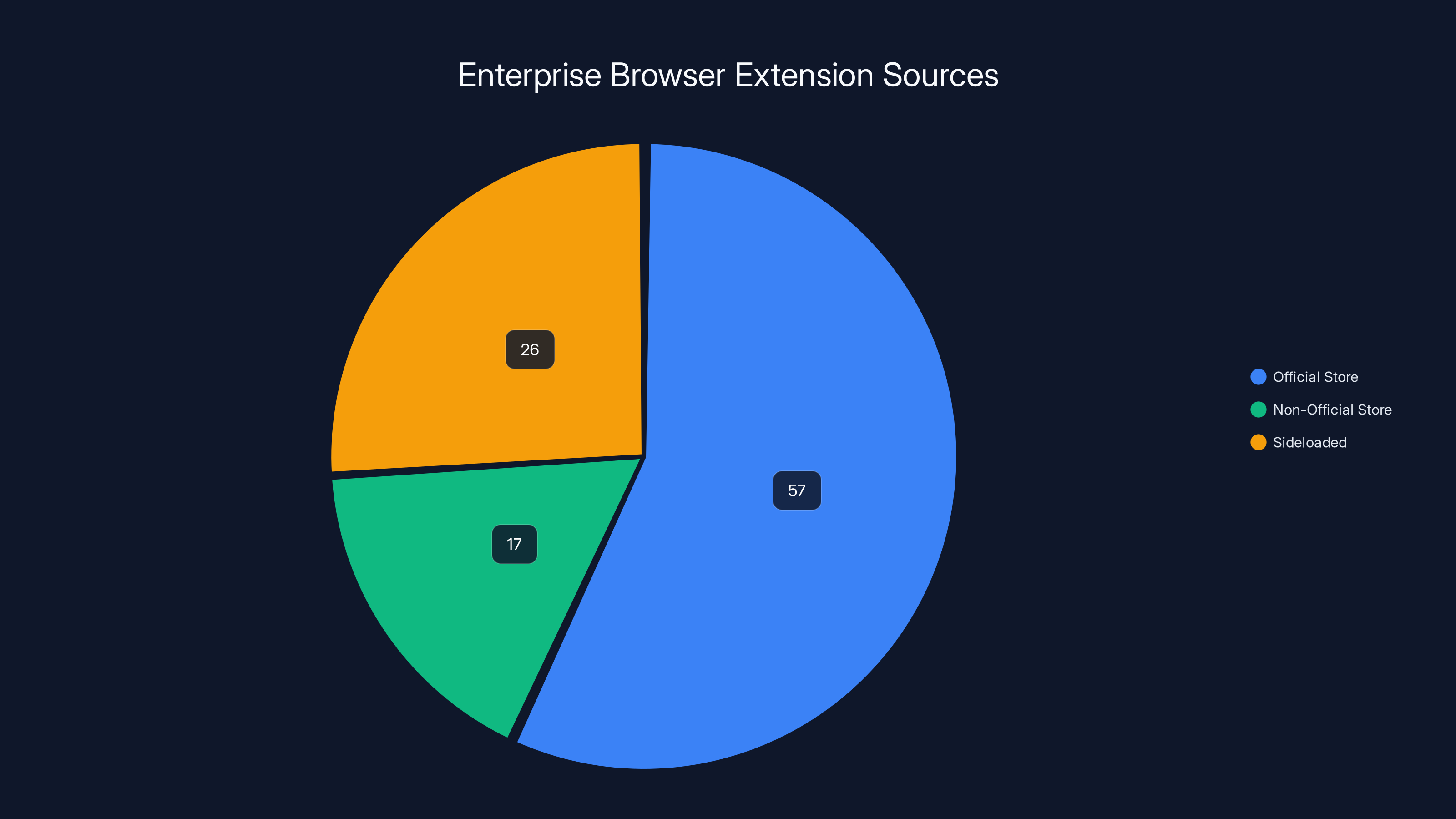
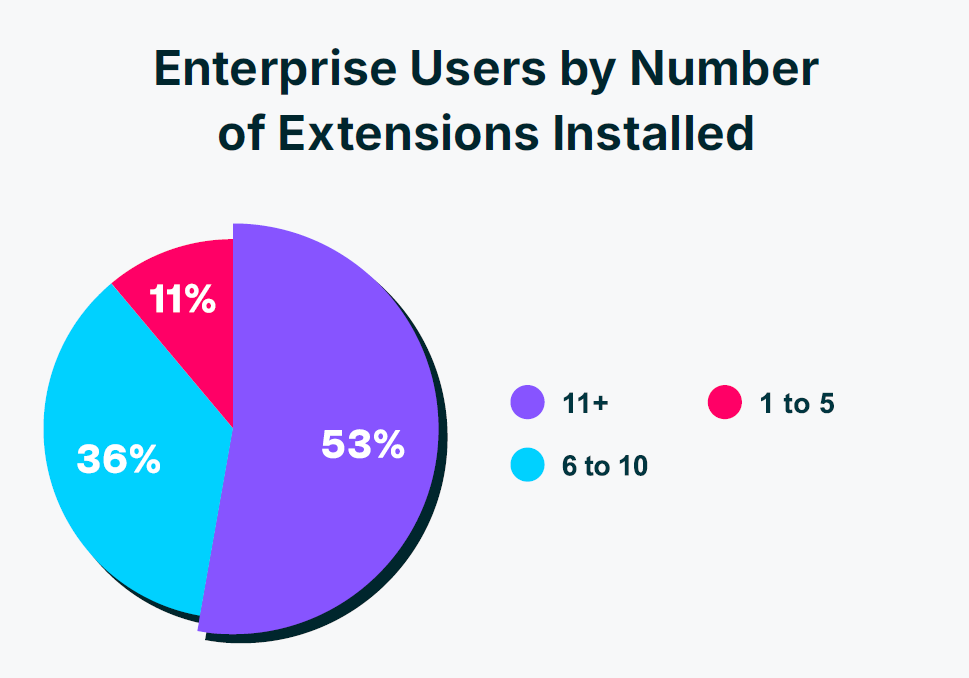
According to LayerX research, 17% of enterprise extensions come from non-official stores, and 26% are sideloaded without IT's knowledge. This highlights the need for thorough extension inventory and attestation.
Why Session Hijacking Is Invisible to Credential-Based Detection
Here's a concept that breaks most traditional security models: what if the attacker has legitimate credentials?
This isn't theoretical. When an attacker steals a session token—whether through malware, phishing, or just sniffing network traffic—they inherit the victim's authenticated session. They can use that token to make API requests. They can access the same data the user can access. They can perform the same actions the user can perform.
From the authentication system's perspective, everything is legitimate. The user's username is correct. Their MFA token passed. Their browser cookies are valid. The access token is in the system.
Traditional detection systems look for suspicious authentication events: impossible travel times, multiple failed login attempts, logins from unusual locations. These tools are useful for catching stolen credentials being used openly. But once you're inside a valid session, these detectors have almost nothing to work with.
Consider what's actually different when a session is hijacked:
The legitimate user accesses their Salesforce account at 9 AM from their office in Denver. They update a customer record. They add a note. They close the tab.
Three hours later, an attacker in another country uses the stolen session token to access the same Salesforce account. They export customer data. They modify contracts. They create a new user account for persistence.
Both actions used the same valid session token. Both came from legitimate credentials. Both accessed the same data. From an authentication perspective, they're identical.
The differences are behavioral and contextual:
- The legitimate user accessed 8 records; the attacker accessed 8,000
- The legitimate user used the UI; the attacker used bulk API calls
- The legitimate user clicked around for 15 minutes; the attacker performed their entire operation in 5 minutes
- The legitimate user accessed their own customer records; the attacker accessed competitor records
- The legitimate user worked from the normal office IP; the attacker originated from a data center
But here's the catch: traditional security systems don't correlate these signals because they're not designed to. Your EDR doesn't talk to your SIEM, which doesn't talk to your API gateway, which doesn't talk to your SaaS application.
Even when these tools could theoretically communicate, they see so much noise that the signal disappears. An employee might legitimately access 5,000 records on a Monday morning during a data migration. A security analyst might legitimately make bulk API calls during an investigation. Someone might legitimately work from a coffee shop for a day.
Separating legitimate from malicious requires understanding the full context, and no traditional tool is built to do that.
Three Attack Patterns Worth Understanding in Depth
Pattern 1: The Long Game—Trust as a Weapon
Time is an underrated component of attacks.
Most enterprises think about attacks in terms of hours or days. You get breached on Tuesday, you detect it by Friday, you remediate by Sunday. But what if the attacker thinks in terms of years?
Shady Panda demonstrates this perfectly. The attackers submitted extensions to the Chrome Web Store in 2018. That's seven years before the attack. For seven years, they ran clean code. They accumulated millions of users. They earned Google's "Featured" and "Verified" badges. They built trust.
In 2025, they weaponized it.
They turned one extension, "Clean Master," into a remote code execution backdoor. Not a backdoor with a fixed function, like "exfiltrate data from folder X." A backdoor that downloads new Java Script commands every hour. The attacker decides what the extension does every single day.
Shady Panda infected 4.3 million users. But here's what matters: the 4.3 million weren't targeted through phishing or social engineering. They downloaded an extension because they thought it was useful. It had millions of positive reviews. It had badges from the store. It was legitimate.
This pattern changes the game for security architecture because it means you can't just block malicious extensions. The malicious code doesn't exist until the attacker activates it. Your threat intelligence is worthless because the extension was clean when you scanned it last month. Your endpoint detection is useless because the malicious behavior hasn't started yet.
Pattern 2: The Credential Compromise—One Developer Away
Supply chain attacks used to require sophisticated techniques. You'd need to find a zero-day in the build pipeline. You'd need to compromise the source code repository. You'd need to understand how continuous integration worked.
Now you just need one developer's credentials.
Cyberhaven's incident showed this. An attacker phished one Cyberhaven developer. They got their password. They authenticated to the Chrome Web Store. They uploaded a malicious version of Cyberhaven's extension.
The store approved it.
400,000 corporate customers auto-updated to a backdoor.
Why did this work? Because the store saw a legitimate publisher (Cyberhaven) uploading an update to a legitimate extension (Cyberhaven's security extension). The store's review process has millions of extensions to manage. They can't do deep code review on every update. They do some automated checks, some manual sampling, and they approve.
The attacker relied on the store's assumption: if the publisher account is legitimate, the code must be legitimate.
This is incredibly dangerous for enterprise security because it means your own vendors are potential attack vectors. You're trusting Cyberhaven to protect their developer credentials. You're trusting the Chrome Web Store's review process. You're trusting the auto-update mechanism. Any of these can break.
Pattern 3: The API Key Leak—Bypassing Everything
Control planes are supposed to be internal safeguards. They're supposed to prevent unauthorized changes.
Trust Wallet learned otherwise.
An attacker obtained a leaked Chrome Web Store API key. This key is supposed to be secret—something Trust Wallet keeps in a secure vault. But it leaked. Maybe it was in code that got pushed to a public GitHub repository. Maybe it was in an old environment variable that didn't get rotated. Maybe someone pasted it into a support ticket.
With that API key, the attacker could push updates directly to the Chrome Web Store. No phishing required. No developer credentials needed. The API key bypassed all internal controls.
They used it to push a malicious update to Trust Wallet's browser extension. Within 48 hours, $8.5 million was drained from 2,520 wallets.
This pattern reveals a critical vulnerability in supply chains: if an attacker can compromise a control-plane secret, they can corrupt the entire distribution channel without any human interaction.

Why Detection Fails When Attackers Have Valid Credentials
Detection is fundamentally broken when the attacker is using legitimate credentials.
This is the core insight that separates modern attacks from the ones your security stack was built to stop. Your IDS looks for malicious network signatures. Your antivirus looks for malware patterns. Your firewall looks for bad IP addresses. These tools assume the attacker will do something that stands out.
But if the attacker is inside a valid session, none of that applies.
The Difference Between Authentication and Authorization
Authentication answers: "Are you who you say you are?"
Authorization answers: "Are you allowed to do what you're trying to do?"
Traditional security focused almost entirely on authentication. We built sophisticated MFA systems. We added passwordless authentication. We created zero-trust networks based on device posture. We made authentication strong.
But we mostly ignored authorization inside applications.
A SaaS application might ask: "Is this person an employee?" (Yes, they have a valid token.) "Are they in the right organization?" (Yes, the token includes the right tenant ID.) "Are they in the right department?" (Maybe—we don't actually check.)
Once the application says "yes" to enough questions, the user gets access. If an attacker has stolen that user's token, the attacker gets access too.
The authorization checks never ask: "Is this person doing things they normally do?" Or: "Is this person accessing sensitive data they never normally access?" Or: "Is this person exfiltrating data in a way that's unusual for them?"
Those are behavioral questions, and they require context.
The Behavioral Signals That Matter
Detecting session hijacking early requires watching how a session actually behaves.
Certain patterns indicate compromise with very high confidence:
Volumetric behavior. A user normally accesses 50 records per day. The session suddenly accesses 50,000 records in an hour. This is a strong signal of bulk data extraction. Legitimate users sometimes do this (like during a data migration), but it's worth investigating.
Temporal behavior. A user normally works 9 AM to 6 PM in the Pacific timezone. The session suddenly makes API calls at 2 AM from an IP in Eastern Europe. This is a strong signal of a stolen token being used from another location.
API pattern behavior. A user normally clicks around the UI, making 5-10 API calls per minute. The session suddenly makes 100 API calls per minute using bulk endpoints. Users don't do this. Attackers do.
Data access behavior. A user normally accesses their own customer records and their team's customer records. The session suddenly accesses competitor data or executive-only financial records. This is a strong signal of privilege abuse.
Data movement behavior. A user normally reads data and occasionally modifies records within the application. The session suddenly downloads all customer data, emails it to external addresses, and uploads it to cloud storage. This is a strong signal of exfiltration.
But here's the operational challenge: you need to correlate these signals across multiple systems.
Your SaaS application sees the API calls. Your network gateway sees the data leaving the network. Your email system sees the message being sent. Your cloud storage provider sees the file being uploaded. But these systems don't talk to each other. Your SaaS application has no idea that data was also uploaded to cloud storage. Your email system has no idea that the attachment contained sensitive data from a competitor.
Information is fragmented. Context is lost. The signal becomes noise.
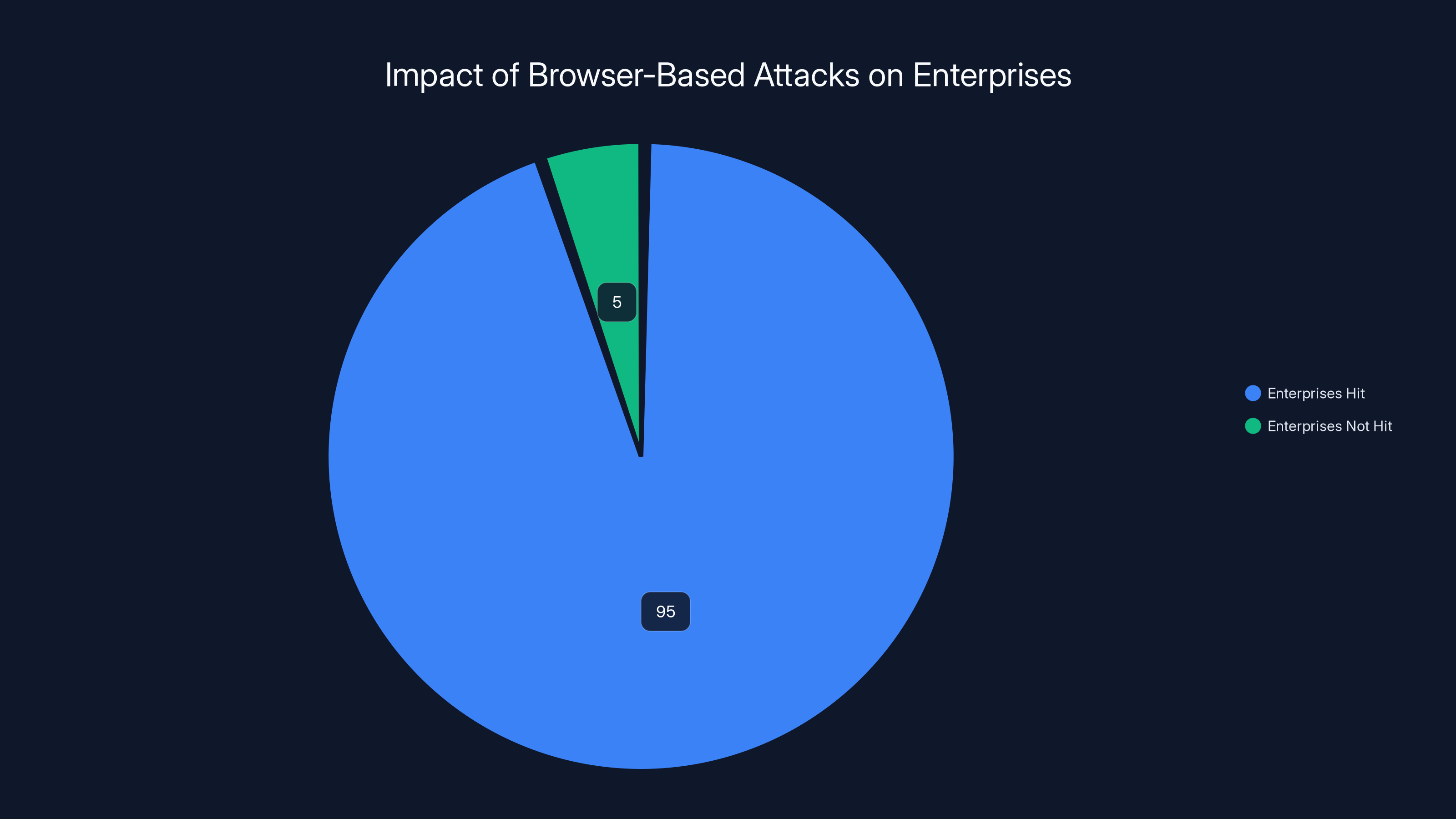
95% of enterprises were affected by browser-based attacks, highlighting a significant gap in traditional security measures.
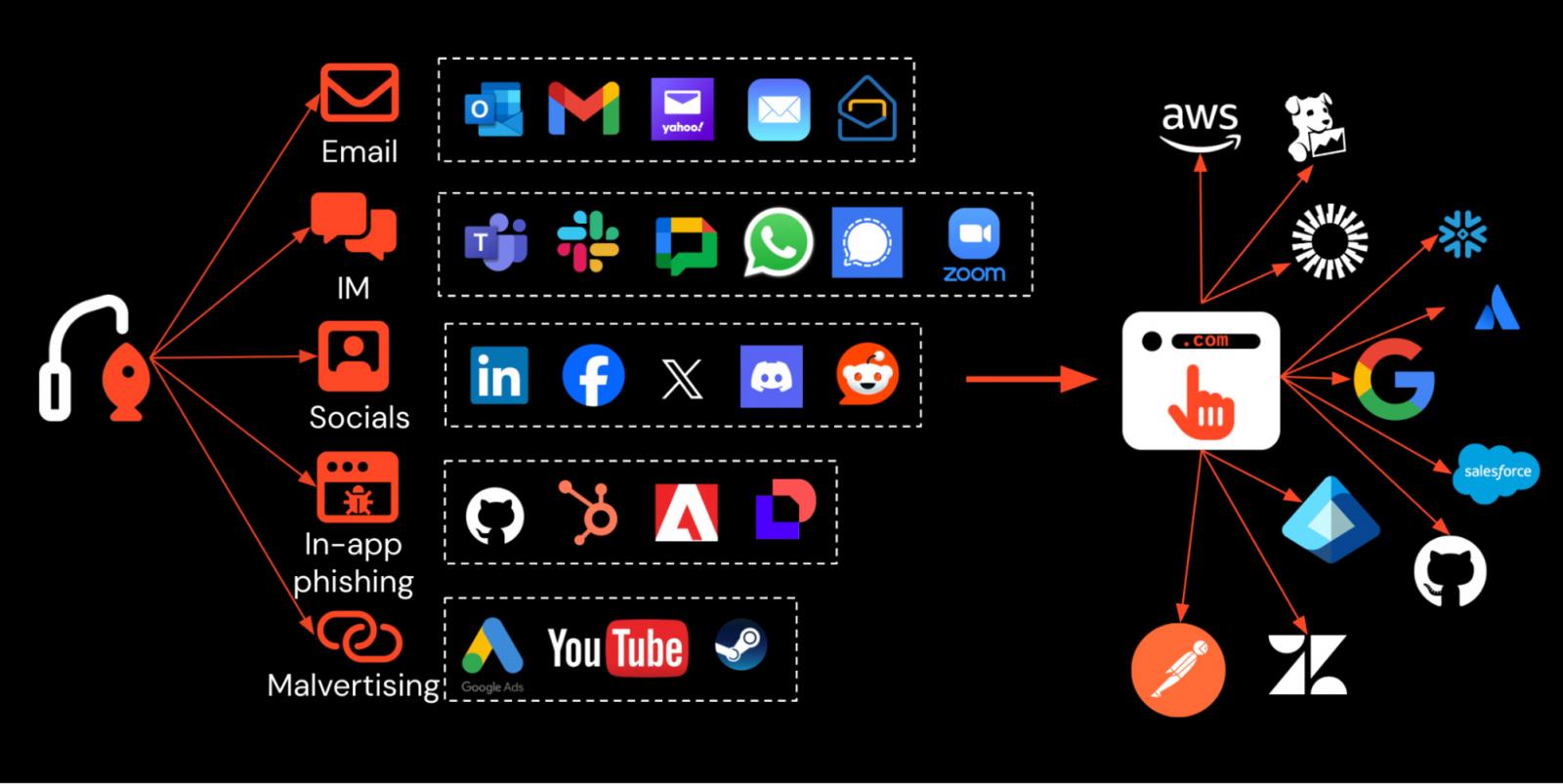
The AI Tool Problem: New Data Exfiltration Paths
Generative AI created a new class of security problem that traditional controls never anticipated.
Consider this workflow:
- You open Chat GPT in your browser
- You paste your company's customer list into the chat
- You ask Claude to analyze the data and suggest improvements
- You get a thoughtful analysis back
- You close the tab
What happened to your customer list? It's on OpenAI's and Anthropic's servers now. It was transmitted over HTTPS (so your web gateway didn't see the content). It was pasted into a web application (so your DLP couldn't scan it). It left your organization's control entirely.
Traditional data loss prevention (DLP) systems were built around a different model. They watch network traffic, looking for large volumes of sensitive data being transmitted externally. They watch endpoints, looking for sensitive files being copied to USB drives. They watch email, looking for sensitive documents being sent outside the organization.
But data going into a SaaS application is intentional. You're supposed to use SaaS applications. The question isn't whether data should be allowed to flow to SaaS—it should be. The question is which data and under what circumstances.
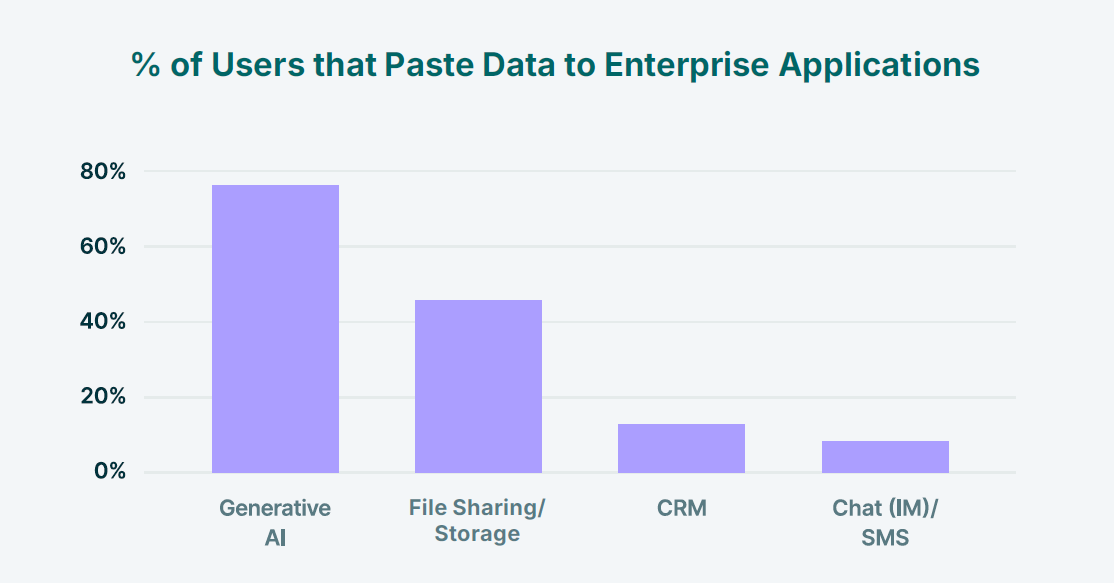
According to Omdia research, 65% of organizations lack meaningful control over data shared in AI tools. They don't have policies. They don't have visibility. They don't have enforcement.
Some organizations are trying to solve this by blocking Gen AI tools entirely. But that's unworkable. Employees will use them anyway (just through mobile hotspots and personal accounts), and you lose the productivity benefits.
The real solution is knowing what data is being shared. Who's using which AI tools? What data are they feeding into them? Is that data sensitive? Is it approved?
This requires browser-layer visibility because that's where the data enters the tools.
Six Operational Patterns That Actually Reduce Exposure
CISOs running production browser security controls identified six consistent patterns that reduce exposure. These aren't theoretical. These are things organizations have tested and deployed at scale.
These assume your identity and endpoint foundations are solid. You've got MFA everywhere. Your endpoints are patched. Your SIEM has logs. Given those foundations, here are the patterns that matter:
1. Extension Inventory and Attestation
You can't defend what you can't see.
This starts with knowing what extensions are installed across your organization. Not guessing. Not assuming. Knowing.
Full browser extension inventory requires endpoint visibility. You need to know on every device: which extensions are installed, when were they added, what permissions do they have, are they from an official store or sideloaded, what version are they running, and when was the last update.
According to Layer X research, 17% of enterprise extensions come from non-official stores, and another 26% were sideloaded without IT knowing. So most organizations don't actually know what extensions are installed.
Once you have inventory, you need attestation. For critical extensions (like your corporate VPN, your identity provider, your endpoint protection), you need to verify that they're legitimate and unmodified.
This might sound like just checking that an extension came from the official store. But remember Shady Panda—the extension was in the official store. Attestation means verifying the cryptographic signature of the extension code, comparing it against what you installed originally, and alerting if anything changed.
This operationally means you'll need to enforce extension policies. Some organizations do this through managed identity providers—forcing all logins through a corporate account that only works on compliant devices. Others use endpoint management to push a blocklist or allowlist of extensions. Some use browser management agents that report on violations.
2. Session Behavior Analysis
Detecting hijacked sessions requires understanding normal behavior.
Start by establishing baselines. For each user and service account: What's their normal API call rate? How many records do they typically access? What time of day do they work? Where do they typically log in from? What data do they typically access?
Once you have baselines, you can detect deviations with high confidence. If a user who normally makes 10 API calls per minute suddenly makes 1,000, that's worth investigating. If a user who normally logs in from Denver suddenly logs in from Russia and makes different API calls, that's worth investigating.
Behavior analysis requires real-time instrumentation of applications. You need APIs logging every request, SaaS applications reporting on data access, and all of this data flowing into a central analysis system.
The analysis itself can be rules-based or ML-based. Rules-based is: "If API calls exceed 100 per minute AND user normally averages 10 per minute, then alert." This is fast and interpretable. ML-based is: "This pattern is anomalous compared to the user's historical behavior." This is more sophisticated but requires training data.
3. Token Replay Detection
If an attacker steals a session token, they'll use it from multiple locations.
A legitimate session token is used from one IP address, one browser, one device. If the same token is used from two different IPs in the same minute, it's being replayed. If a token is used from Russia and then from the United States within 30 seconds, it's impossible for a human to travel that distance—the token must be stolen.
Token replay detection is conceptually simple: track which tokens are active, which devices/IPs they're using, and which devices/IPs they've historically used. If a token suddenly appears from somewhere impossible, challenge it.
Operationally, this requires token intelligence. You need: the token's creation time and location, all historical locations the token has been used from, the current location of the token, and the velocity between locations.
The challenge is false positives. A user might legitimately roam across networks. A service account might legitimately make requests from multiple IPs (like a load balancer). An authenticated token might legitimately be replayed through a proxy.
So replay detection usually includes a challenge mechanism. If a token is used from a suspicious location, challenge the user: "We noticed a login from Moscow at 2 AM. Was this you?" If the user says no, disable the token.
4. AI Tool Data Controls
Because 65% of organizations don't control data shared with AI tools, this is a massive blind spot.
Data controls for AI tools usually work in layers:
Policy layer. Define which data is sensitive and can't be shared with AI tools. Usually this includes customer data, financial data, source code, employee data, and competitive information.
Detection layer. Instrument the browser to detect when data matching these categories is being pasted into AI tools. This requires scanning the clipboard or monitoring user actions before data is submitted.
Enforcement layer. Stop the data from being submitted. This might mean blocking the paste action, preventing the form submission, or intercepting the network request before it leaves the organization.
Visibility layer. Log what data is being shared, by whom, and when. Even if you're not blocking it, you need to know what's happening.
The challenge is that AI tools are diverse. Chat GPT, Claude, Gemini, Perplexity, and dozens of others all work differently. They all have different APIs and interfaces. Instrumenting all of them requires careful browser-layer controls.
5. Data Exfiltration Monitoring
Not all data movement is malicious, but unusual data movement deserves investigation.
This requires correlating signals across multiple systems: your SaaS applications, your network gateway, your email system, your cloud storage, your database audit logs.
Set up alerts for patterns like:
- Large volumes of data being downloaded from SaaS applications
- Downloaded data being uploaded to external cloud storage
- Downloaded data being emailed externally
- Bulk data access followed by bulk data modification
- Unusual bulk API calls to export functions
The key is correlation. A download by itself might be legitimate. A download followed by an email might be legitimate (you're sharing a report). A download followed by an upload to personal cloud storage is suspicious. A download followed by an email to a personal email address is very suspicious.
6. Post-Authentication Access Controls
Instead of trying to block attackers at authentication, control what happens after they're authenticated.
This includes:
Step-up authentication. If a user accesses sensitive data or performs risky actions, require additional authentication. They've already logged in, but accessing the executive financial dashboard requires another MFA challenge.
Privilege boundaries. Even if a user's session is compromised, limit what they can do. A marketing employee's session shouldn't be able to access HR data. A contractor's session shouldn't be able to create new user accounts.
Rate limiting. If an API is designed to handle 10 requests per minute but receives 1,000, something's wrong. Rate limit that API per user, per IP, per application.
Data segregation. Some data should only be accessible through specific applications or from specific networks. If it's accessed outside those contexts, deny it.
Audit everything. When access controls are enforced at the post-authentication layer, audit logs become your detective control. You can't always prevent the attack, but you can detect it immediately afterward.
Why Browser Isolation Isn't Enough Anymore
Browser isolation sounded like a complete solution when it was invented.
The idea is elegant: run web content in a remote container, not on the local device. When you visit a malicious website, you're actually rendering it on a server somewhere. Your device receives a screenshot or video stream. Even if the website tries to steal your credentials or install malware, the attack happens in a container you don't care about.
Companies like Menlo Security, Cloudflare, and Symantec offer browser isolation products. They work. They stop rendering-based attacks.
But they don't stop the attacks that matter anymore.
Browser isolation protects you before authentication. If a website is trying to steal your password or install malware, isolation prevents that.
Browser isolation doesn't protect what happens after authentication. Once you're logged in, once you have a valid token, once you're inside a trusted session—isolation is irrelevant. The token is in your local browser. The attacker has it. Isolation can't help.
The three real attack patterns (long-game extension compromise, credential compromise of developers, leaked API keys) all involve attackers inheriting valid sessions or tokens. Isolation doesn't detect this because isolation doesn't see inside your authenticated sessions.
Moreover, isolation adds latency. Everything you do gets sent to a remote server, processed, and sent back as rendering. This works for passive web browsing. It doesn't work for real-time collaboration tools or complex SaaS applications where responsiveness matters.
So isolation is still useful—it stops a certain class of threat. But it's not sufficient. You need isolation plus the six operational patterns above.

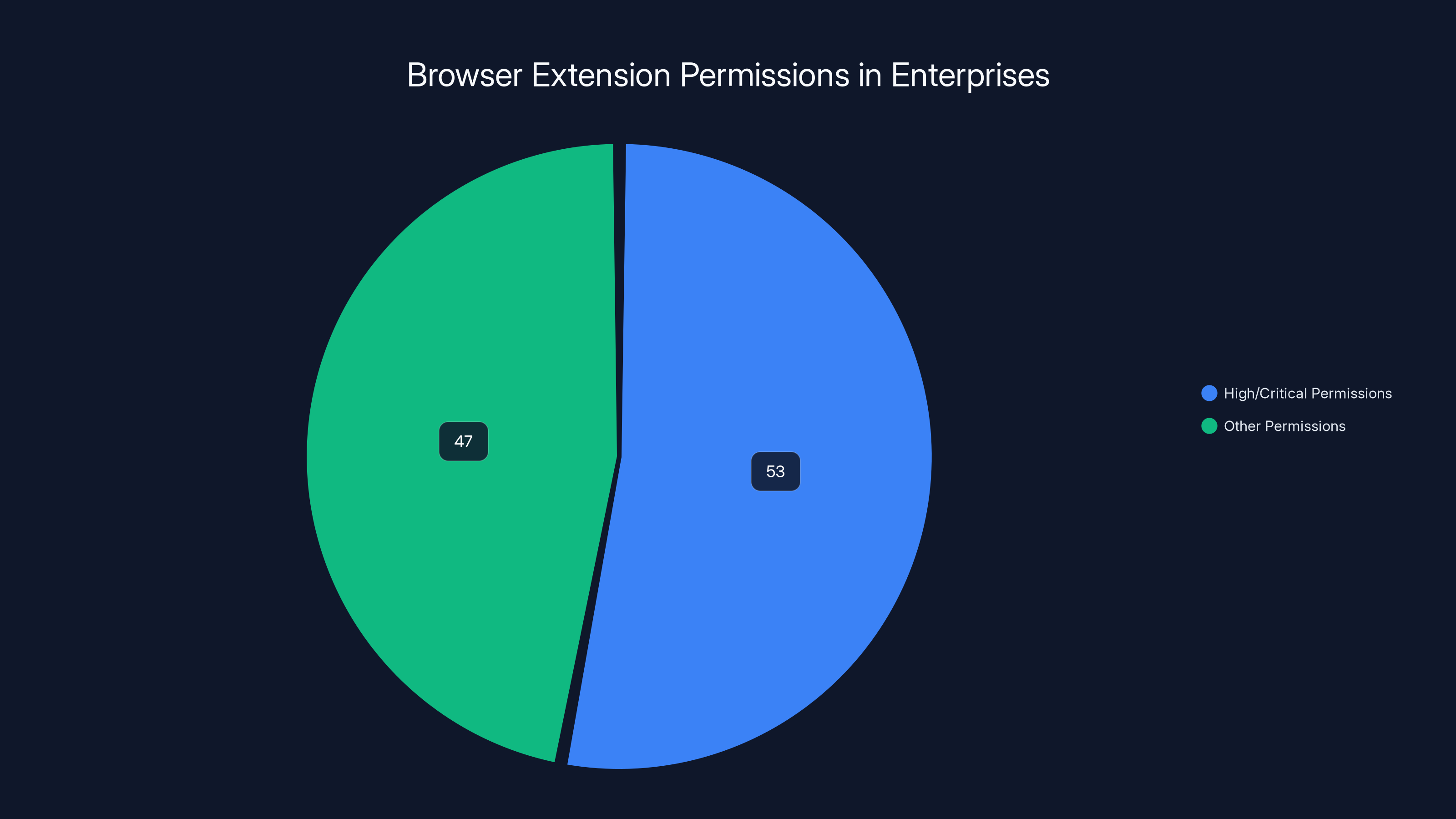
According to LayerX's report, 53% of enterprise browser extensions have high or critical permissions, posing significant security risks.
The Role of Zero-Trust Architecture in Browser Security
Zero-trust principles apply to browsers just as much as they apply to networks.
Traditional zero-trust focuses on device posture. Before a device can access the network, check: Is it patched? Is it encrypted? Is it running our endpoint protection? These checks make sense. They prevent compromised devices from becoming entry points.
But zero-trust in the browser layer goes further. It says: even if the device is trusted, and even if the user is authenticated, verify that each action is legitimate.
This means:
Verify the context of every action. Not just "is the user authenticated" but "is the user doing something they normally do?" If a user suddenly tries to download 10GB of customer data when they normally download 10MB per month, the action is suspicious even though the user is authenticated.
Require explicit permission for sensitive operations. If a user tries to access data they've never accessed before, require explicit approval. If a browser extension tries to access cookies for the first time, require explicit permission.
Revoke trust dynamically. If you detect suspicious behavior, don't just alert. Terminate the session. Revoke the token. Force re-authentication.
Trust signals matter more than credentials. A user might have legitimate credentials, but if 50 other signals indicate compromise, the user shouldn't get access.
Zero-trust in the browser layer is operationally complex because it requires real-time decision-making at the application layer. But CISOs running it at scale report it's the most effective control for detecting compromised sessions.
Building Visibility Into Browser Activity
You can't defend what you can't see.
Browser visibility requires instrumentation at multiple layers:
Extension layer. What extensions are installed? What permissions do they have? When were they last updated? Are they in the official store? A cloud-based extension visibility tool that queries all endpoints and aggregates the results is essential.
Application layer. What SaaS applications are users accessing? Which users are accessing them? What data are they accessing? This usually requires browser-layer integration with SaaS applications or network-level traffic analysis.
Network layer. Where is browser traffic going? How much data is being transferred? To which external IP addresses and services? Your network gateway should provide this visibility.
Device layer. Which devices are opening browsers? What's their security posture? Are they compliant with policy? Your endpoint management system should provide this.
Aggregating this visibility into a single pane of glass is the challenge. You might have extension visibility from one tool, SaaS visibility from another, network data from a third. These systems need to correlate their data.
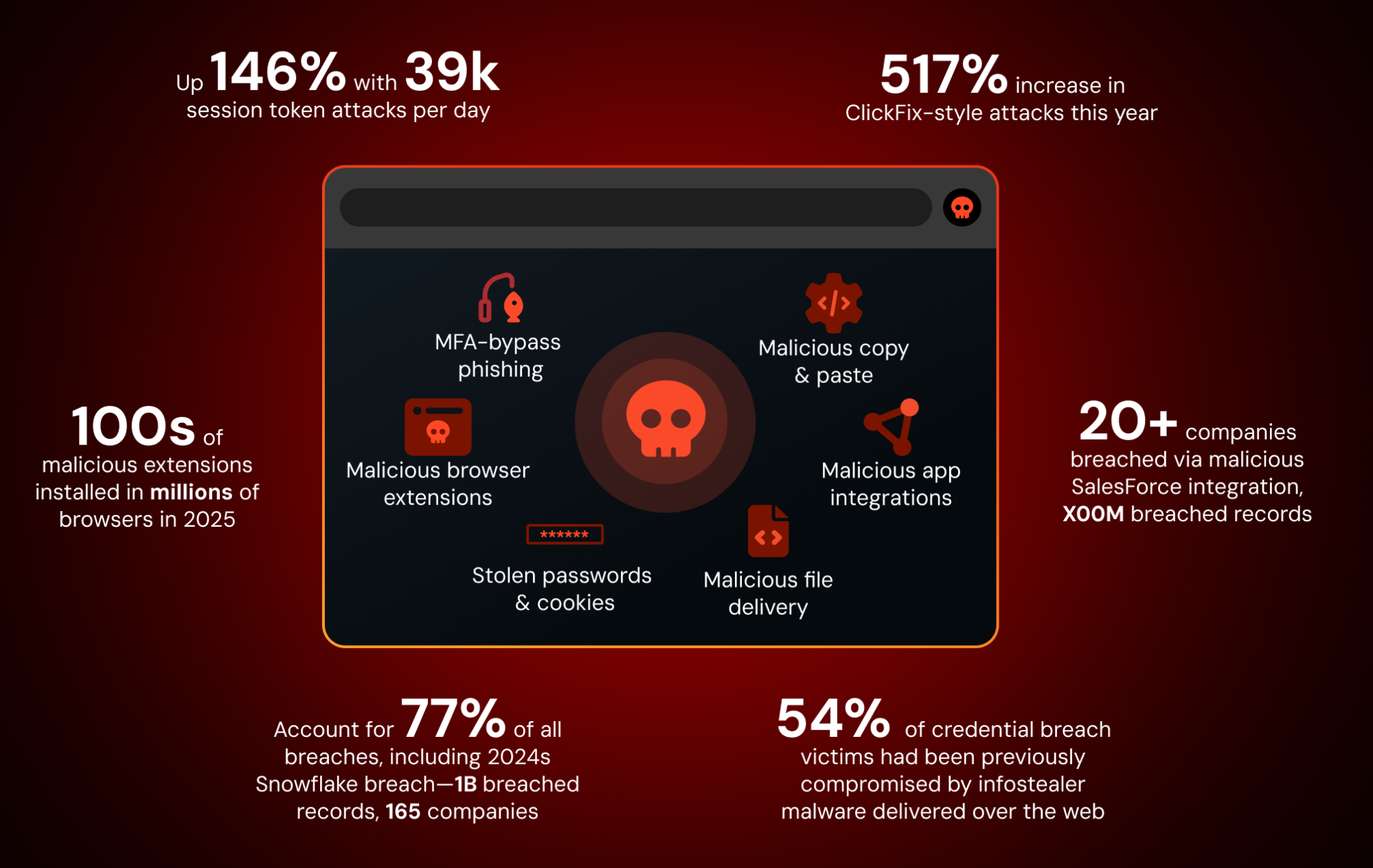
The Economics of Browser Compromise
Understanding why attackers focus on browsers requires understanding the economics.
From an attacker's perspective, browsers are the highest-ROI attack surface in enterprises. Here's why:
Access is universal. Every employee uses a browser. No exception. It's not like compromising a specific database or file server. Everyone has it.
Credentials are there. People use their browser to authenticate to every service they use. Session tokens, API keys, cookies—they're all in the browser. Compromise the browser, inherit the session.
Data flows through it. SaaS applications, cloud storage, email, cloud identity—data flows through the browser to these services. Compromise the browser, monitor the data flow.
Visibility gaps are massive. Security teams monitor networks, endpoints, and email. Most have no visibility into what's happening inside browser sessions. The browser is the most instrumented part of the endpoint, yet the least monitored.
Supply chain is vulnerable. Extensions come from a semi-trusted supply chain (the Chrome Web Store, Microsoft Edge Add-ons). The supply chain has been compromised before (Shady Panda) and will be compromised again.
Auto-update is default. Unlike traditional software where you have to actively install updates, browser extensions auto-update by default. An attacker who compromises the supply chain gets automatic distribution to millions of users.
From a defender's perspective, this is frustrating. Your firewall can't help. Your network detection can't help. Your endpoint protection can't help. You need new layers of defense.
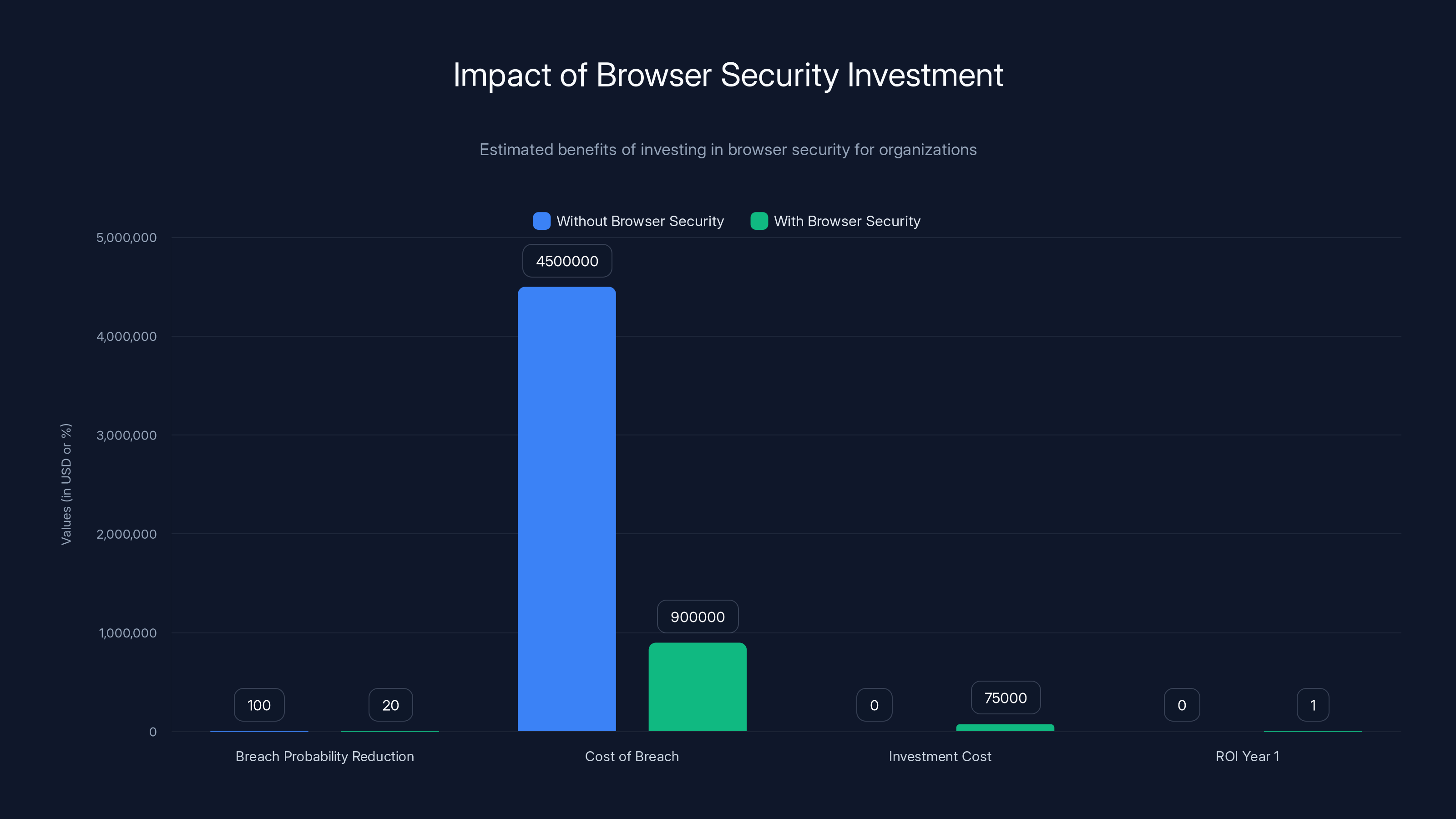
Implementing browser security can reduce breach probability by 80%, significantly lowering potential breach costs and achieving positive ROI within the first year. Estimated data.
Nation-State vs. Financial Motivation: Different Attacks, Same Blind Spot
Attack motivations vary, but the browser blind spot affects everyone.
Nation-state actors (government-sponsored threat groups) typically use browser access for long-term intelligence collection. They want persistence. They want to stay inside your network undetected for months or years, exfiltrating proprietary data, source code, and strategic information.
Financial threat actors (criminal groups) prioritize speed. They want to harvest credentials, session tokens, and sensitive data, then monetize it immediately. They sell credentials on the dark market. They liquidate stolen cryptocurrency. They hold data for ransom.
The tactics are different. The timelines are different. The targets are different.
But both rely on the same browser-layer blind spot. Both depend on traditional security missing their activity. Both operate inside trusted sessions with valid credentials.
Nation-state attackers might use a sophisticated 0-day in a browser to gain initial access. Financial attackers might use a phishing email to steal credentials. But once they're inside an authenticated session, the challenge is identical: stay undetected while exfiltrating data.
Detecting nation-state attackers requires understanding their long-term behavior patterns. What data are they interested in? What systems are they returning to? Are they modifying data or just reading? Are they expanding their access footprint?
Detecting financial attackers requires understanding their rapid behavior patterns. Are they bulk-downloading data? Are they making bulk API calls? Are they accessing systems they've never accessed before? Are they using automation?
Behavior analysis works for both, but the baselines and thresholds differ.
Practical Implementation: Where to Start
If you're reading this and thinking, "This is terrifying, where do I even start," you're in good company. Most CISOs feel the same way.
Here's a prioritized approach based on how other organizations have successfully implemented browser security:
Phase 1: Visibility (Month 1-2)
Start with inventory and awareness. Deploy extension visibility across all endpoints. Understand what's installed. Categorize extensions into critical, important, and unnecessary. Create a blocklist of obviously suspicious extensions. Create an allowlist of required extensions.
At the same time, start collecting behavioral baselines. For critical service accounts (shared accounts, automation accounts, privileged accounts), log their API activity. How many requests per hour? What endpoints do they hit? What data do they access? Where do requests originate from?
Phase 2: Enforcement (Month 3-4)
Based on Phase 1 findings, enforce extension policies. Block unauthorized extensions. Require approval for new extensions. Implement extension attestation for critical extensions.
Start implementing session behavior analysis. Set up alerts for the most obvious deviations: API call rate exceeding 10x the baseline, access to data the user normally doesn't access, logins from impossible locations.
Phase 3: Advanced Detection (Month 5-6)
Once baselines are solid and enforcement is in place, start adding more sophisticated detection. Token replay detection. Correlation of data access across systems. AI tool monitoring and controls.
Invest in tooling that can integrate signals from multiple sources: SaaS applications, network gateway, email, endpoint management, identity provider.
Phase 4: Automation (Month 7+)
Automate responses. If token replay is detected, revoke the token and force re-authentication. If data exfiltration is detected, disable the account pending investigation. If an extension tries to do something unusual, challenge the user.
As the system matures, you can get more aggressive with automated response. The key is having enough confidence in your detection that false positives are minimal.
The Role of Automation and AI in Browser Defense
As browsers become more critical to enterprise operations, manual defense becomes impossible.
You can't have a human review every API call. You can't have a person investigate every behavioral deviation. You can't manually approve every extension.
This is where automation and AI become essential.
Behavioral analysis at scale requires ML models that can learn normal behavior from historical data, then detect deviations in real-time. The model sees millions of API calls, learns patterns, detects anomalies.
Intelligent alert correlation requires AI systems that can connect signals from disparate systems. Token from Russia, API spike, data download, email to external address—these are separate events. An AI system correlates them into a single high-confidence alert.
Predictive threat modeling can simulate how an attacker would behave if they compromised certain accounts or services. Based on that simulation, set detection thresholds.
Automated response orchestration can execute complex response workflows automatically. Revoke token, disable account, kill process, block network, alert security team—all happening in seconds, coordinated across multiple systems.
The challenge is that AI and automation can create false positives. An employee working on a legitimate bulk data operation might trigger your "suspicious data access" alarm. An automated response that disables the account breaks their work.
Successful implementations include humans in the loop, especially for disruptive actions. Automated detection and alerting is fine. Automated account disabling should require human approval (or at minimum, a very high confidence threshold).
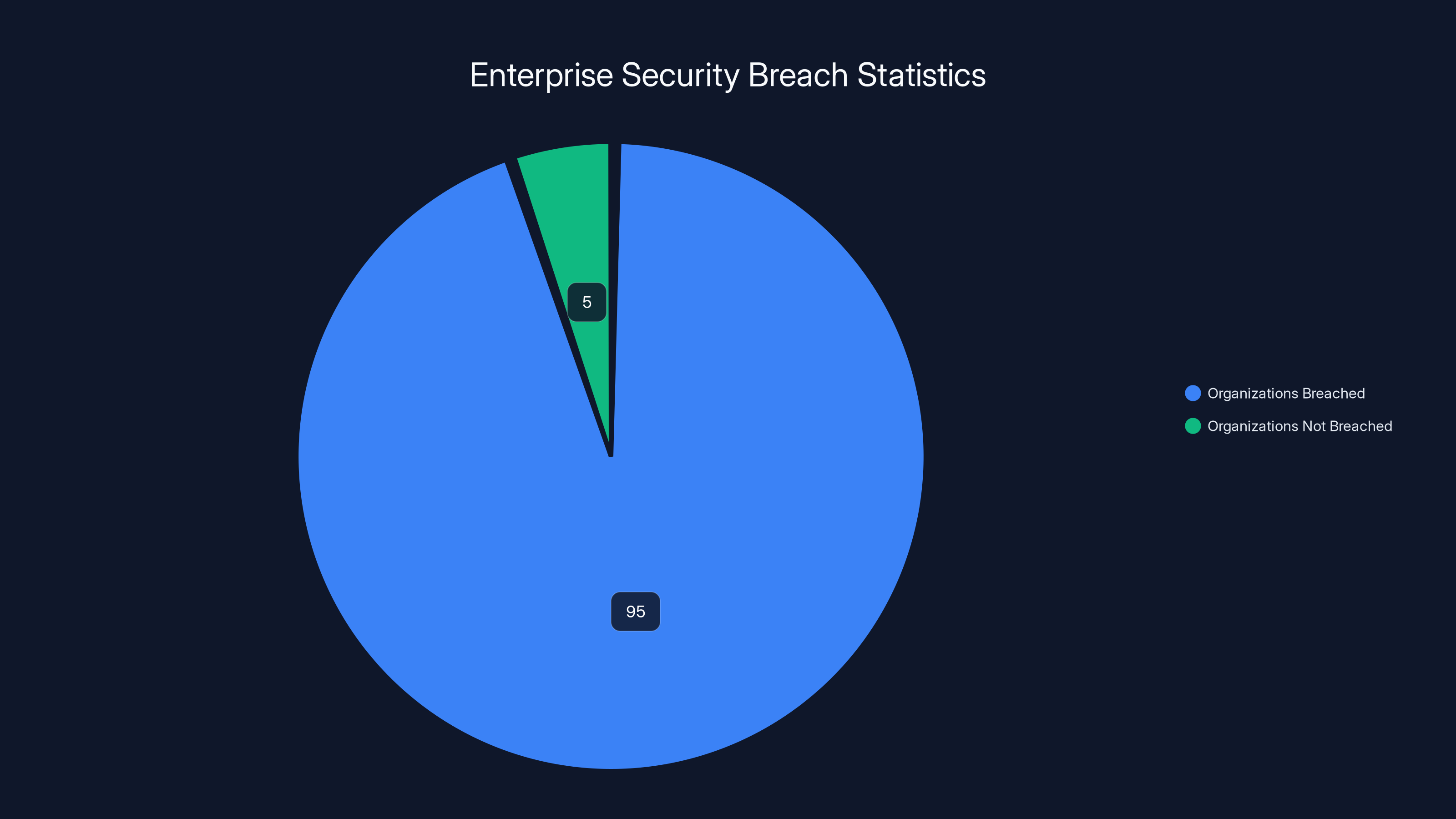
An estimated 95% of organizations experience browser-based security breaches, highlighting the critical need for advanced browser security measures. Estimated data.
Common Mistakes in Browser Security Programs
As organizations try to address browser security, they often make predictable mistakes.
Mistake 1: Assuming isolation is sufficient. Browser isolation stops rendering-based attacks. It doesn't stop session hijacking or token theft. Organizations often deploy isolation, feel secure, and miss attacks inside authenticated sessions.
Mistake 2: Relying on extension store approval. The Chrome Web Store reviews extensions, but the review is cursory. Shady Panda passed review. Cyberhaven passed review. Approval doesn't mean safe. You need additional validation.
Mistake 3: Treating browsers like passive windows. Browsers aren't just where users consume content. They're execution environments. They run SaaS applications, process sensitive data, execute AI workflows. Security tools need to treat them accordingly.
Mistake 4: Ignoring behavioral signals. Organizations focus on technical controls (block extensions, require MFA) and miss behavioral signals. A user accessing 5,000 records when they normally access 50 is a bigger threat than a new extension from an unknown publisher.
Mistake 5: Implementing controls without visibility. You can't enforce what you can't see. Before implementing browser controls, ensure you have visibility into what's actually happening. This usually means 2-3 months of monitoring before enforcement.
Mistake 6: Blocking AI tools entirely. Employees will use them anyway. Control what data they can share, don't try to block the tools.
The Evolution of Browser Threats Over the Next 18 Months
Browser attacks are evolving faster than defenses.
Over the next 18 months, expect:
Increased sophistication in supply chain attacks. Shady Panda showed that simple compromise works. Expect more attackers to follow this pattern. They'll play the long game, accumulating trust, then weaponizing it.
Leveraging AI tools as data exfiltration vehicles. As AI tools become ubiquitous, attackers will use them to exfiltrate data. They won't need to send data to their own servers. They'll send it to Chat GPT, and it's in their hands.
Targeting browser synchronization. If you use Chrome sync, your passwords, bookmarks, and history sync to Google's servers. An attacker who compromises your Google account gets access to all of this across all your devices. Expect increased targeting of browser sync.
Malicious browser profiles. Browser profiles are separate user contexts within a browser. You might have a work profile and a personal profile. An attacker might create a hidden profile that runs malicious extensions in the background while you use the browser normally.
Token theft from memory. Rather than relying on compromised extensions, attackers might exploit memory disclosure vulnerabilities to steal tokens directly from the browser's memory.
Defending against these emerging threats requires building on the six operational patterns. The specific threats change, but the principles stay the same: visibility, behavior analysis, token protection, and post-authentication controls.
Industry Standards and Frameworks for Browser Security
Browser security doesn't yet have a consensus framework like cloud security or network security.
The closest relevant standards are:
NIST Cybersecurity Framework. The NIST framework addresses security at an organizational level and touches on supply chain risks (which is relevant to extension attacks) and access controls (which is relevant to session hijacking). But it doesn't specifically address browser-layer threats.
CIS Controls. The Center for Internet Security publishes critical controls prioritized by effectiveness. Controls 1-6 focus on inventory and basic hygiene. Control 5 specifically addresses unauthorized software. Implementing CIS Control 5 for browser extensions is a good starting point.
Zero Trust Architecture. NIST SP 800-207 provides a framework for zero-trust architecture. The principles apply to browsers: verify every action, minimize implicit trust, validate before access.
OWASP Top 10. The Open Web Application Security Project's top 10 list focuses on application layer attacks. Session hijacking (broken authentication) is #2 on the list. OWASP guidance on session management is relevant to browser security.
There's no single "browser security framework" because this is a relatively new area. Most organizations are cobbling together pieces from multiple frameworks.
Why Traditional Vendors Are Slow to Adapt
You might ask: why don't traditional security vendors (endpoint protection companies, web gateways, cloud access brokers) just add browser security to their products?
The answer is architectural.
Traditional vendors built their products around specific trust models. Endpoint protection assumes the OS is the relevant layer. Web gateways assume traffic inspection is possible. Cloud access brokers assume the network is the relevant layer.
Browser security requires a different approach. You need visibility inside the browser process, which is sandboxed. You need to understand Java Script execution, which is different from OS-level process execution. You need to correlate behavioral signals across multiple systems, which requires data integration most vendors haven't invested in.
Addressing browser security would require significant architectural rework for most vendors. So they either ignore it (which is what most are doing) or acquire specialized companies (which is what some are doing).
The result is that browser security is largely unserved by traditional vendors, creating a gap for specialized vendors.
Compliance Implications: When Browser Attacks Matter for Auditors
Compliance frameworks don't specifically address browser-based attacks, but they should.
SOC 2 Type II. If your organization is audited for SOC 2, the auditor will look at access controls, authentication, and system monitoring. A breach through browser-based attacks could fail SOC 2 because you lack controls on authenticated sessions.
HIPAA. HIPAA requires audit logs and access controls. If a healthcare organization gets breached through a browser-based attack, HIPAA auditors will ask: did you detect the attack? Did you log the unauthorized access? Did you have controls preventing it? Browser-based attacks that aren't detected violate HIPAA's logging requirements.
PCI DSS. For organizations processing payment cards, PCI DSS requires strong access controls and monitoring. Browser-based attacks that steal API keys or bypass access controls are PCI violations.
GDPR. Under GDPR, data breaches require notification and investigation. If you can't explain how the breach happened, GDPR enforcement actions are likely.
The compliance implication is: if you can't demonstrate that you detect and prevent browser-based attacks, you're non-compliant with most frameworks.
Integrating Browser Security Into Your Risk Management Framework
Browser security should be a core component of enterprise risk management.
Start by assessing risk:
Impact: If a browser is compromised, what's the worst that could happen? A user's browser has access to all their SaaS applications, their email, their files. An admin's browser could compromise your entire infrastructure. Quantify the potential impact: data breach? Regulatory fine? Operational downtime?
Likelihood: How likely is a browser-based attack? 95% of organizations experienced one last year. The likelihood is high.
Risk = Impact × Likelihood. High likelihood × high impact = high risk. Browser security should be treated accordingly.
Once you've established risk, map it to your organization's risk tolerance. If your organization can't tolerate a 95% probability of browser compromise, you need to invest in browser security. This might mean implementing several of the six operational patterns.
Browser security is increasingly a business issue, not just a security issue. If you can't operate without web applications, and web applications run in browsers, then browser security is critical to business continuity.
Building Stakeholder Support for Browser Security Investment
Browser security is a new category of spending for most organizations, which means you need to build business case and stakeholder support.
The pitch to the CFO: "95% of enterprises are getting breached through browsers. The average breach costs
The pitch to the CTO: "Browser-based attacks bypass traditional security tools. We need new instrumentation. This is a platform investment that enables detection across multiple security tools."
The pitch to the board: "Browser security is a material risk. We've disclosed in our annual report that we've implemented controls for networks, endpoints, and cloud. We haven't mentioned browsers. This gap could become a liability."
The pitch to business leaders: "Employees use browsers 7+ hours per day. If they're compromised, your data is exposed. Browser security protects employee productivity and data."
Focus on outcomes: reduced breach probability, faster detection, compliance readiness, business continuity.
Conclusion: The Browser Is Infrastructure Now
For the past 10 years, enterprise architecture treated browsers as user tools, not infrastructure.
But the work happens in browsers. The data flows through browsers. The authentication happens in browsers. The AI happens in browsers. The threats operate in browsers.
It's time for security architecture to catch up.
The six operational patterns in this article—extension inventory, behavioral analysis, token replay detection, AI tool controls, data exfiltration monitoring, and post-authentication access controls—are becoming table stakes for enterprise security. Organizations that implement these patterns will detect and prevent attacks that traditional tools miss. Organizations that don't will continue joining the 95% that gets breached.
The good news is that you don't need to build this from scratch. Specialized vendors are emerging. Industry practices are crystallizing. Frameworks are developing.
The challenge is moving quickly enough. Browser attacks are accelerating. The gap between threats and defenses is widening.
Your window to implement controls is measured in months, not years.
Start with visibility. Understand what's running in your browsers. Understand what your users and systems are doing. From that foundation, implement detection and enforcement.
The 5% of organizations that don't experience browser-based attacks aren't lucky. They're defended. And defense starts with understanding the threat.

FAQ
What is a browser-based attack?
A browser-based attack is any threat that operates through a web browser, including compromised extensions, phishing through the browser, session hijacking after authentication, malicious updates to trusted software, and attacks exploiting browser vulnerabilities. Unlike traditional attacks that target the operating system or network, browser attacks often operate inside authenticated sessions with valid credentials, making them invisible to traditional security tools.
Why do 95% of enterprises face browser-based attacks?
Browsers are universal. Every employee uses them. Every cloud application runs in them. Every SaaS application requires them. Traditional security was built around network inspection and endpoint processes. Browser execution environments operate differently and were never well-defended. This combination—universal usage plus legacy blind spots—means attackers can reach 95% of enterprises through browser compromises that traditional security can't detect.
How are browser-based attacks different from traditional malware?
Traditional malware requires execution rights on the operating system. It needs to write files to disk, change the registry, or spawn processes. Endpoint protection tools detect these behaviors. Browser attacks operate within the browser process, which is sandboxed from the OS. They inherit legitimate credentials and tokens. They operate inside authenticated sessions. To traditional security tools, they look like normal user activity, making them invisible.
Can browser isolation prevent browser-based attacks?
Browser isolation protects against rendering-based attacks (malicious websites that try to steal credentials or install malware). It doesn't protect against session hijacking, extension compromise, or token theft—the three attack patterns that are currently compromising enterprises. Isolation is a useful control, but it's insufficient by itself. You need isolation plus behavioral analysis and post-authentication controls.
What's the difference between an extension getting compromised and a user getting phished?
When an extension is compromised (like Shady Panda), millions of legitimate users automatically receive the malicious update. When a user is phished, one person gives up their credentials. Extensions are more dangerous because they affect scale without requiring social engineering. With phishing, most people ignore the phishing email. With malicious extension updates, everyone who uses the extension gets infected automatically.
How do you detect session hijacking if the attacker has valid credentials?
Credentials alone don't tell you whether a session is hijacked. You need to analyze behavior: Are API call rates 10x higher than normal? Is data being accessed that this user normally never accesses? Is the session active from a geographically impossible location? Is the user making bulk API calls they normally wouldn't make? Correlating these behavioral signals reveals hijacking that credential analysis alone would miss.
What should I do if I think my organization has experienced a browser-based attack?
First, don't assume traditional tools caught it. They probably didn't. Start with extension inventory—understand what extensions are installed and when they were last updated. Check your SaaS application logs for suspicious API activity. Review data access patterns for anomalies. Correlate behavioral signals across systems. Engage incident response. Contact your vendors for browser-specific forensics. Browser-based attacks leave different artifacts than traditional attacks, so you need different investigation approaches.
How much does browser security infrastructure cost?
Specialized browser security platforms range from $50K-200K annually depending on organization size and features. This is in addition to existing security spending. The ROI calculation is usually: cost of platform vs. probability of breach × average breach cost. Given that 95% of enterprises face browser attacks, the ROI is positive for most organizations.
Can I implement browser security without disrupting user productivity?
Yes, if you implement carefully. Start with visibility-only mode (don't block anything, just monitor). Collect baselines for 30-60 days. Then implement enforcement gradually, starting with the highest-risk items (extensions from non-official stores, significant behavioral deviations). Phase rollout by department. Communicate changes clearly. With proper phasing, most organizations implement browser security with minimal disruption.
What's the relationship between browser security and zero-trust architecture?
Zero-trust assumes no implicit trust, even inside the network. In the browser context, this means even authenticated users shouldn't be trusted to make any action. Every API call should be evaluated for context: Is this user doing something they normally do? Are they accessing data they normally access? The six operational patterns in this article are implementing zero-trust principles in the browser layer.
Key Takeaways
- 95% of enterprises experienced browser-based attacks last year, with traditional security detecting virtually none
- Three operational attack patterns (long-game extension compromise, developer credential compromise, leaked API keys) show attackers don't need zero-days or sophisticated techniques
- Session hijacking is invisible to credential-based detection because attackers inherit valid tokens and operate inside authenticated sessions
- Six operational patterns consistently reduce exposure: extension inventory and attestation, session behavior analysis, token replay detection, AI tool controls, data exfiltration monitoring, and post-authentication access controls
- Browser isolation stops rendering-based attacks but doesn't defend against threats operating inside authenticated sessions
- Building browser security requires visibility-first approach: monitor for 60 days, establish baselines, then enforce policies gradually
- Compliance and business risk justify browser security investment, with ROI positive in year one for most organizations
Related Articles
- AI Cybercrime: Deepfakes, Phishing & Dark LLMs [2025]
- AI-Powered Phishing: How LLMs Enable Next-Gen Attacks [2025]
- Microsoft BitLocker FBI Access: Encryption Backdoor Reality [2025]
- OpenAI Scam Emails & Vishing Attacks: How to Protect Your Business [2025]
- Vishing Kits Targeting SSO: Google, Microsoft, Okta at Risk [2025]
- Microsoft BitLocker Encryption Keys FBI Access [2025]
![Browser-Based Attacks Hit 95% of Enterprises [2025]](https://tryrunable.com/blog/browser-based-attacks-hit-95-of-enterprises-2025/image-1-1769451647239.png)



