The Okta Crisis: What You Need to Know Right Now
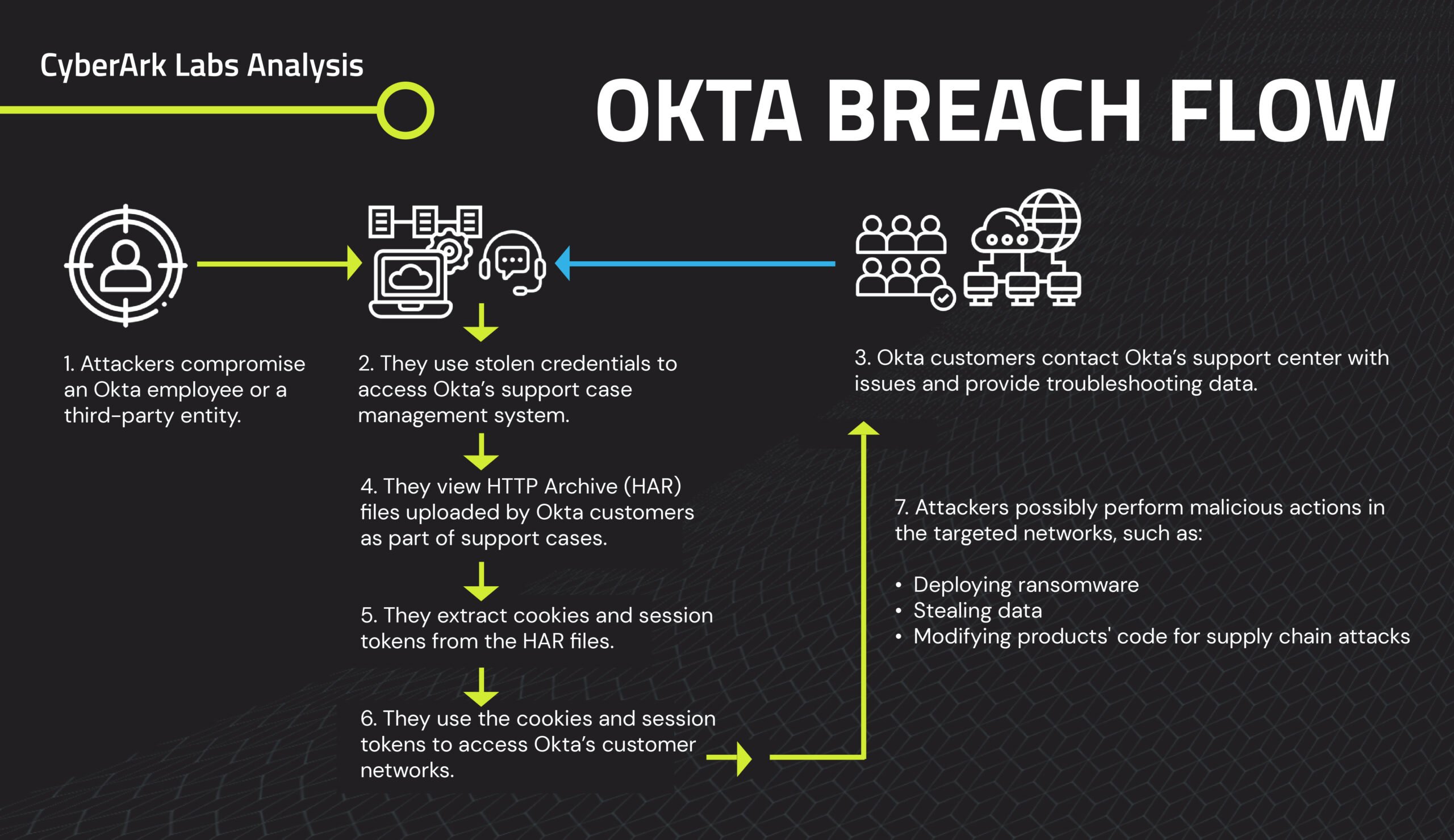
Last month, security researchers at Silent Push uncovered something that should keep every CTO and security leader awake at night. The notorious Scattered LAPSUS$ Hunters threat group is conducting a coordinated, sophisticated identity theft campaign targeting Okta single sign-on (SSO) credentials across approximately 100 major enterprises worldwide.
This isn't theoretical. This is happening right now. The hackers have already built custom vishing kits, they're actively calling employees, and they're systematically attempting to steal credentials and multi-factor authentication tokens in real-time. What makes this especially terrifying is the simple math: once they compromise an Okta session, they own access to literally every application in your corporate environment.
Here's the thing that keeps security professionals up at night. An Okta SSO compromise isn't like a typical breach where attackers steal a database. When someone hijacks your SSO session, they get what researchers call a "skeleton key" to your entire infrastructure. One compromised credential. One stolen MFA token. Instant lateral movement across every connected application, every internal system, every sensitive data repository. No additional hacking required.
The affected organizations span industries: tech giants like Atlassian, financial firms like Morningstar, utilities like American Water, retailers like Game Stop, and telecom providers like Telstra. The list is long. The target selection is strategic. These aren't random companies. These are major enterprises with valuable data, significant ransomware negotiation budgets, and the kind of operational disruption that makes extortion viable.
But here's what's important to understand right now. Being on the target list and actually being compromised are two entirely different things. Silent Push has confirmed they've found no evidence of successful breaches yet. No data has appeared on dark web leak sites. No victims have been publicly announced. That's the good news. But it's also the urgent news—because the window to prevent this from succeeding might be measured in days, not weeks.
TL; DR
- Scattered LAPSUS$ Hunters targeting ~100 enterprises with sophisticated vishing attacks on Okta SSO credentials
- No confirmed breaches yet, but researchers found active phishing campaigns with real-time MFA token interception capabilities
- One compromised Okta session = complete infrastructure access: attackers gain lateral movement to all connected applications
- Affected companies span industries: Atlassian, Morningstar, American Water, Game Stop, Telstra, and 95+ others
- Immediate action required: Implement passwordless authentication, enforce hardware MFA, add detection rules for impossible travel, and monitor for credential abuse

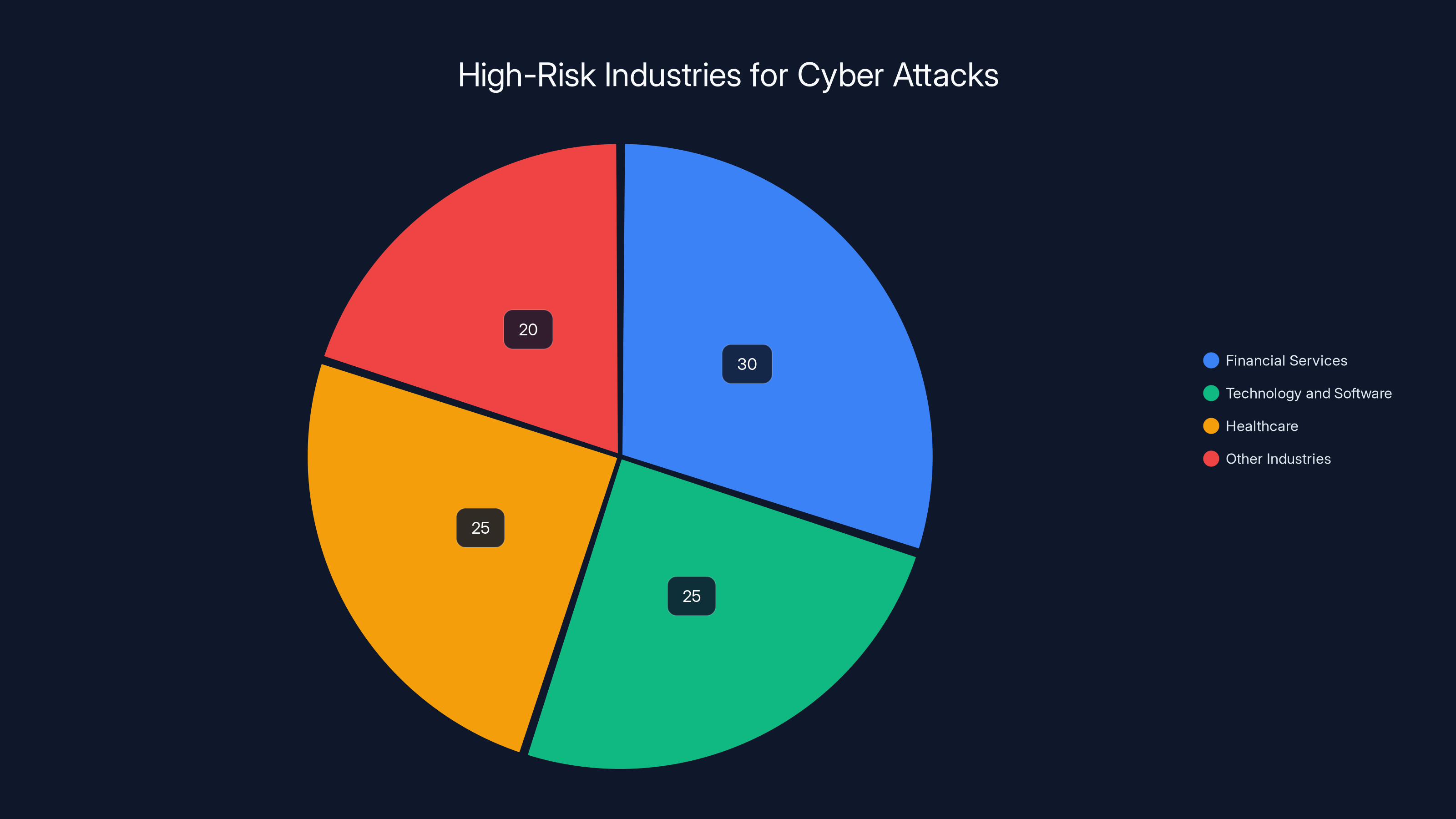
Financial services, technology, and healthcare are the most targeted industries, each comprising a significant portion of SLH's campaign focus. Estimated data based on industry risk factors.
Understanding Scattered LAPSUS$ Hunters: The Group Behind the Attack
Scattered LAPSUS$ Hunters aren't new to this. The group has been active for several years, building a reputation for brazen social engineering attacks, credential theft, and targeted extortion campaigns. What distinguishes them from other threat actors is their willingness to combine technical sophistication with old-school phone calls—vishing attacks that often work better than any malware.
The original LAPSUS
What's particularly notable about SLH's approach is their focus on identity and access management infrastructure. Unlike ransomware groups that just want to encrypt everything and demand payment, SLH understands that controlling identity = controlling everything. They're not interested in taking down your systems. They're interested in owning your access. They want to sit quietly in your environment, exfiltrate your most valuable data, and then use that leverage for extortion.
Their operational security is decent. They use VPNs and proxies. They rotate between phishing campaigns. They maintain compartmentalized lists of victims. But they also maintain public data leak websites where they announce successful attacks, which is how researchers can track their activity and attribution.
The sophistication here lies in the phishing infrastructure. Silent Push identified that SLH has deployed what researchers call a "Live Phishing Panel"—essentially a real-time interception system that captures credentials and MFA tokens as employees enter them. This isn't a simple keystroke logger. This is a sophisticated proxy system that sits between the employee and Okta, harvesting authentication factors as they're used.
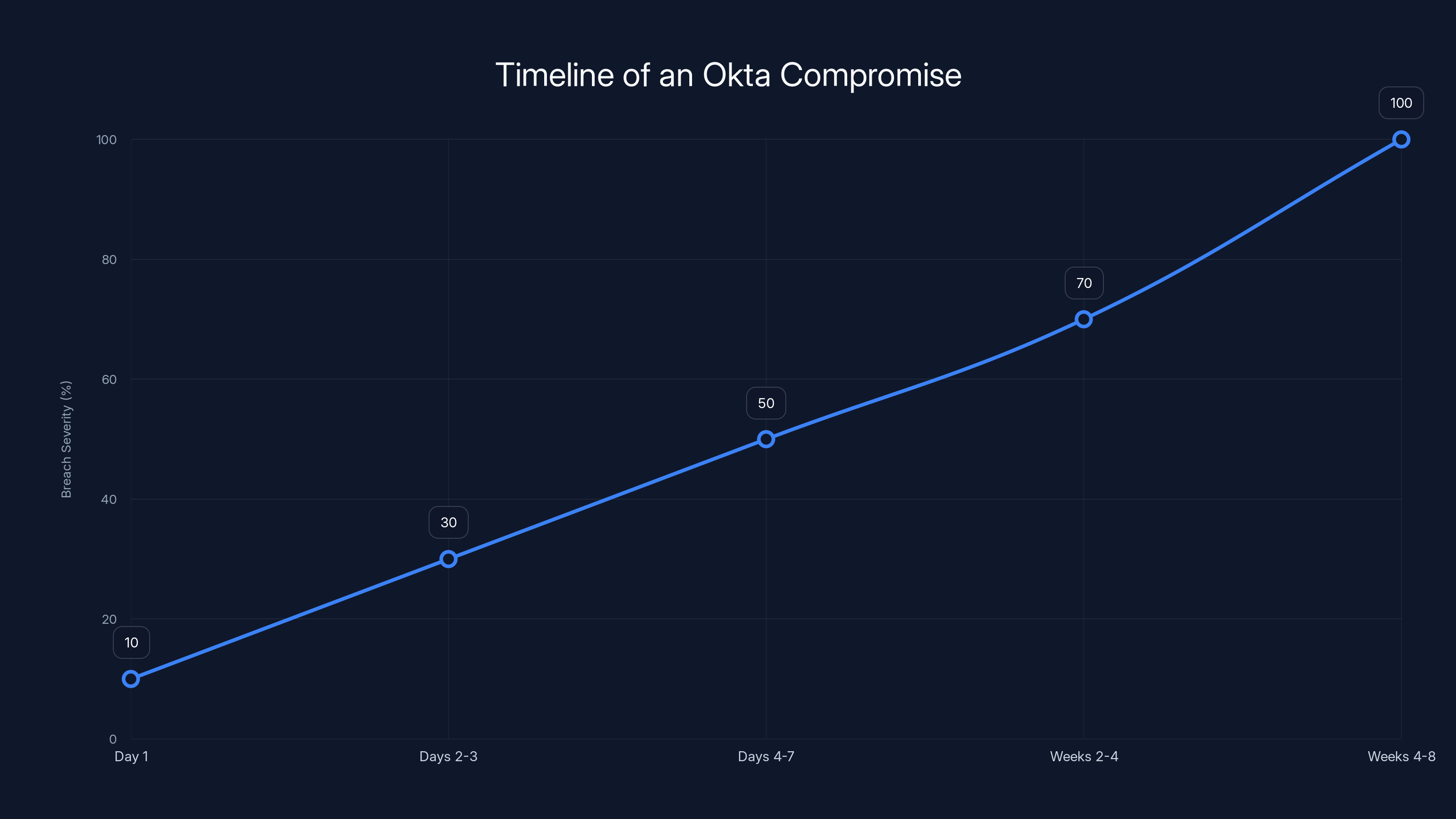
The severity of an Okta compromise increases significantly over time, with attackers establishing persistence, moving laterally, and eventually exfiltrating valuable data. Estimated data.
How Vishing Attacks Actually Work: The Social Engineering Foundation
Vishing stands for "voice phishing." It's not new. But when executed by experienced threat actors like SLH, it's devastatingly effective. Here's how it typically unfolds.
First, the attacker does reconnaissance. They find an employee on Linked In. They identify which company that person works for. They research the company's infrastructure. They might even identify the specific department—say, Sales Engineering or Finance—where that person works. They learn everything publicly available.
Then they make the phone call. But they don't call asking for the password. That would be immediately obvious. Instead, they impersonate someone internal. "Hi, this is IT Support. We're seeing unusual login attempts from your account from different locations. We need to verify your access." Or: "This is the Security Team. We're rolling out mandatory multi-factor authentication updates. Can you confirm your current MFA settings so we can register your new device?"
The social engineering portion—the actual conversation—is designed to build trust and create urgency. The attacker asks casual, work-related questions that the real employee can answer. "What project are you working on?" "Which tools do you use most?" This establishes credibility. Then the urgency: "We need to do this now before your account gets locked." Or: "If we don't update this in the next hour, you'll lose access."
At the critical moment, the attacker directs the employee to a phishing landing page. "Visit this link to verify your credentials." Or: "We'll call you back in two minutes, but we need you to log in first to verify your session." The employee, now believing the attacker is legitimate IT support, enters their username and password.
But here's where it gets worse. In SLH's current campaign, the phishing page isn't just capturing credentials. It's simultaneously logging the employee into the real Okta system. The employee sees what looks like a successful login. Their browser redirects to what appears to be normal corporate systems. Meanwhile, the attacker now has valid credentials and is watching the MFA prompt in real-time.
When the MFA notification appears on the employee's phone—either a push notification or a text message code—the attacker uses social engineering again. "I'm seeing the MFA prompt on my end. What code does it show?" The well-meaning employee, still believing they're talking to IT, reads off the six-digit code.
Now the attacker has both factors. Username. Password. Multi-factor authentication. They can log into Okta from anywhere, from any device, and they'll appear as a completely legitimate session from the employee's actual location (because the attacker used a proxy to mask their own IP address).
The beauty of this attack—from the attacker's perspective—is that it bypasses almost everything except hardware-based authentication. It defeats knowledge-based answers. It defeats code-based MFA. It defeats email-based MFA. It works because it exploits the weakest link: human trust.

Why Okta Is the Perfect Target: The Crown Jewel of Identity Infrastructure
Okta isn't just another Saa S application. Okta is the identity infrastructure for thousands of enterprises. When you sign in to Okta, you're not just accessing one app. You're gaining access to hundreds of connected applications and internal systems through single sign-on.
Here's the architecture that makes it so valuable to attackers. Your company configures Okta as the central identity provider. Then you connect everything to it. Salesforce uses Okta. Git Hub uses Okta. AWS uses Okta. Slack uses Okta. Confluence, Jira, Google Workspace, Microsoft 365—all integrated with Okta as the authentication broker.
When an employee logs into Okta once in the morning, they get an authentication token. That token grants access to every connected application. No additional login prompts. No additional MFA challenges. They click a link in Okta and they're automatically authenticated to Salesforce. They click another and they're in Git Hub. Another and they're in AWS. All from one session.
Now imagine an attacker with that same token. They don't need to breach Git Hub separately. They don't need to steal AWS credentials. They don't need to crack passwords for 50 different systems. One Okta session token. One compromise. Instant access to the entire castle.
This is what researchers mean by calling it a "skeleton key." In medieval castles, the skeleton key—a master key with a simple, universal design—could open almost every door. One Okta session works the same way. It doesn't open every door (some systems require additional authentication), but it opens most of them.
The lateral movement possibilities are enormous. An attacker with compromised Okta access could:
- Export customer data from Salesforce
- Push malicious code to Git Hub repositories
- Create administrative users in AWS
- Access financial records in accounting systems
- Download intellectual property from document repositories
- Access employee data from HR systems
- Monitor all communications through Slack
- Modify DNS records or network configurations
Each of these steps creates different data exfiltration opportunities and different blackmail angles. Financial data. Customer information. Intellectual property. Trade secrets. Source code. Employee records. Any of these can be leveraged for extortion.
This is why targeting Okta is so much more valuable than targeting any individual application. You're not breaching one system. You're breaching the entire infrastructure in a single move.
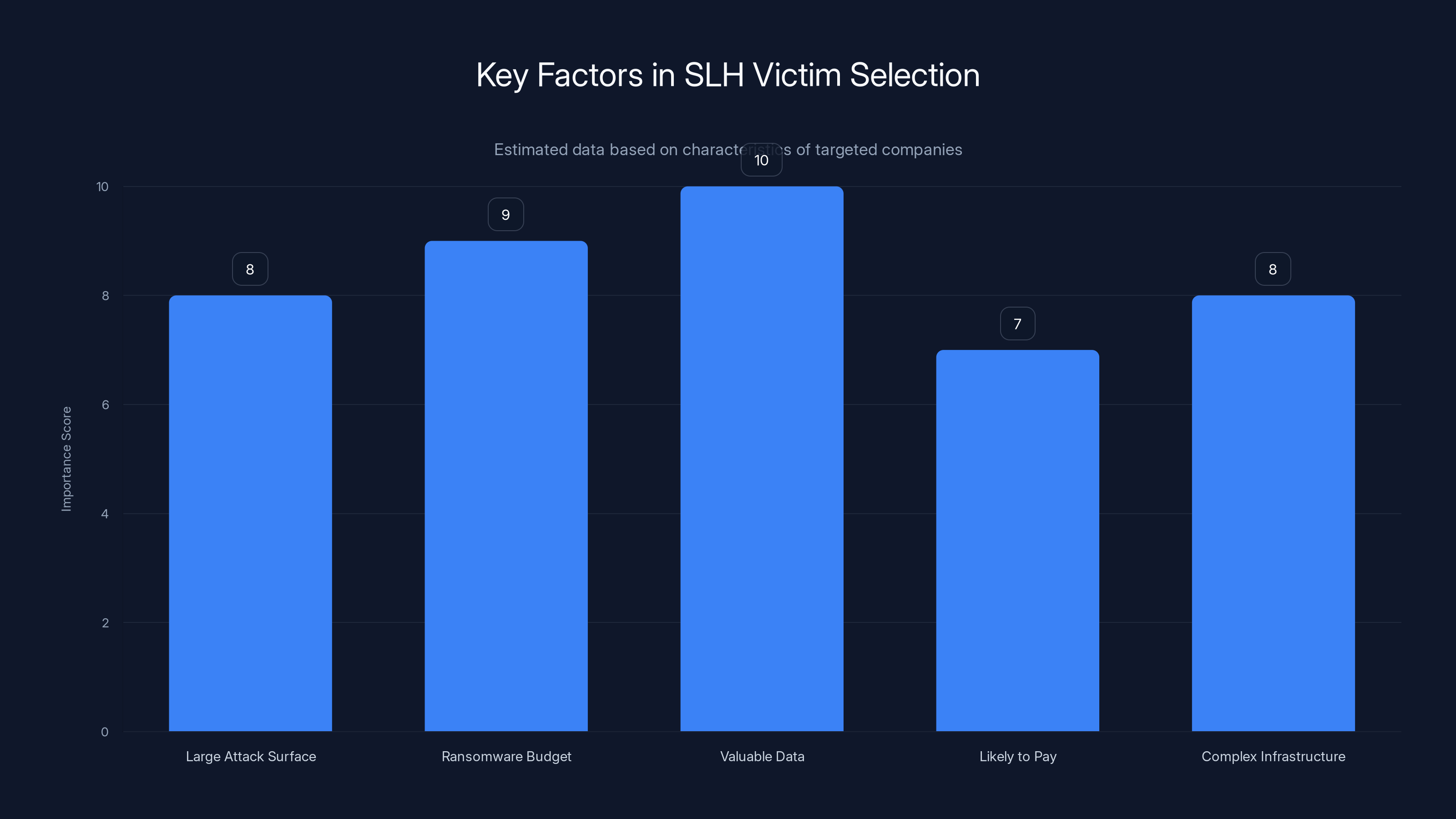
SLH targets companies based on strategic factors such as valuable data and complex infrastructure. Estimated data reflects the importance of each factor in victim selection.
The Live Phishing Panel: Real-Time Credential and MFA Interception
What Silent Push discovered that's particularly concerning is that SLH isn't just collecting credentials through basic phishing forms. They've built what's called a Live Phishing Panel—a sophisticated infrastructure that captures credentials and MFA tokens in real-time, showing attackers exactly what the victim is entering as they enter it.
Here's how this system works. The attacker sets up a reverse proxy—essentially a man-in-the-middle infrastructure that sits between the phishing victim and the real Okta login endpoint. When the victim visits the phishing domain and enters their username and password, the system doesn't just store the credentials. It forwards them to the real Okta system. Okta processes the login attempt and prompts for MFA. The system captures that MFA prompt and displays it to the attacker in real-time through the panel.
So on the attacker's screen, they see:
- Username: [victim's actual username]
- Password: [victim's actual password]
- MFA type: Push notification / SMS code / TOTP
- Status: Waiting for MFA response
The attacker now asks the victim over the phone: "I'm sending you an MFA prompt, please approve it on your phone." The victim approves it on their phone. The attacker's panel lights up with the same confirmation. The victim then hears: "Great, now I also need you to tell me the code for our security verification. What six-digit code is showing on your screen?"
The victim, now in a heightened state of trust (the attackers sometimes even pretend there's a technical issue: "Our system is having trouble reading that code, can you just tell me what it shows?"), reads off the code. The attacker enters it into the panel. Session authenticated.
This is significantly more sophisticated than basic phishing because it defeats token-based MFA through social engineering rather than technical attack. It also maintains the appearance of legitimacy because the victim actually completes a successful authentication—they see the real Okta system, their real applications load, everything appears normal.
The victim never realizes they've been compromised. They go about their day. Attackers now have active, validated session tokens. These tokens work immediately and appear completely legitimate because they are—they were generated through actual authentication flows.
Silent Push also identified that SLH has built custom domain infrastructure specifically for this campaign. They registered domains that closely mimic Okta's legitimate domains, using variations like:
- okta-auth-verify[.]com
- okta-sso-verify[.]com
- okta-identity-check[.]com
- okta-secure-auth[.]com
These aren't trying to be perfect imitations. They're relying on the social engineering component (the phone call) to make the victim believe the domain is legitimate. The attacker says: "Go to okta-auth-verify to complete the update," and the victim goes there. The domain name sounds right. The login form looks right. The process feels right.
Reconnaissance and Targeting: How SLH Selects Victims
Scattered LAPSUS$ Hunters doesn't target randomly. Their victim selection shows clear strategic thinking. They're not after the easiest breach. They're after the most valuable targets—companies with:
- Large attack surfaces (many employees to target)
- Significant ransomware negotiation budgets (companies that have paid ransomware demands before)
- Valuable data (financial information, customer data, trade secrets)
- Likely to pay extortion (companies with regulatory obligations, public companies under pressure from investors)
- Complex infrastructure (more potential exfiltration targets)
Looking at the confirmed target list—Atlassian (software), Morningstar (financial data), American Water (critical infrastructure), Game Stop (retail), Telstra (telecommunications)—these companies share specific characteristics.
Atlassian is a prime target because its products (Jira, Confluence) are used internally by thousands of other companies. A compromise of Atlassian could potentially yield information about clients, infrastructure patterns, and business intelligence from dozens of upstream customers.
Morningstar is a target because it manages investment data, fund performance information, and wealth management records. That data has direct financial value. Competitors would pay for competitive intelligence. Individuals affected might face identity theft consequences.
American Water is infrastructure. Utilities are high-value targets because a compromise could be leveraged for regulatory action, publicity, and significant ransom demands. Critical infrastructure companies typically have insurance, regulatory requirements, and budgets to handle breaches.
Game Stop's selection might seem unusual—the company has financial difficulties—but it's actually strategic. Game Stop is a publicly traded company with significant social media presence. Any breach creates immediate publicity. The company has reputational damage concerns beyond just financial impact.
Telstra is a national telecommunications provider. Access to Telstra's systems could reveal customer data, infrastructure configuration, and potentially allow for follow-on attacks against Telstra's customers.
The pattern: SLH is targeting companies where the combination of data value, operational impact, and willingness to pay creates the best extortion scenario.
Recruitment methodology also shows sophistication. Silent Push identified that SLH members are actively recruiting others to participate in the campaign. They advertise access to the phishing panel and stolen credentials on underground forums. New recruits receive:
- Training on vishing scripts
- Lists of target employees
- Phishing domain infrastructure
- Access to the live phishing panel
- Instructions on credential validation
- Guidance on timing and persistence
This isn't a small team operation. This is a distributed campaign with multiple actors, likely across different time zones, enabling 24/7 targeting capability.

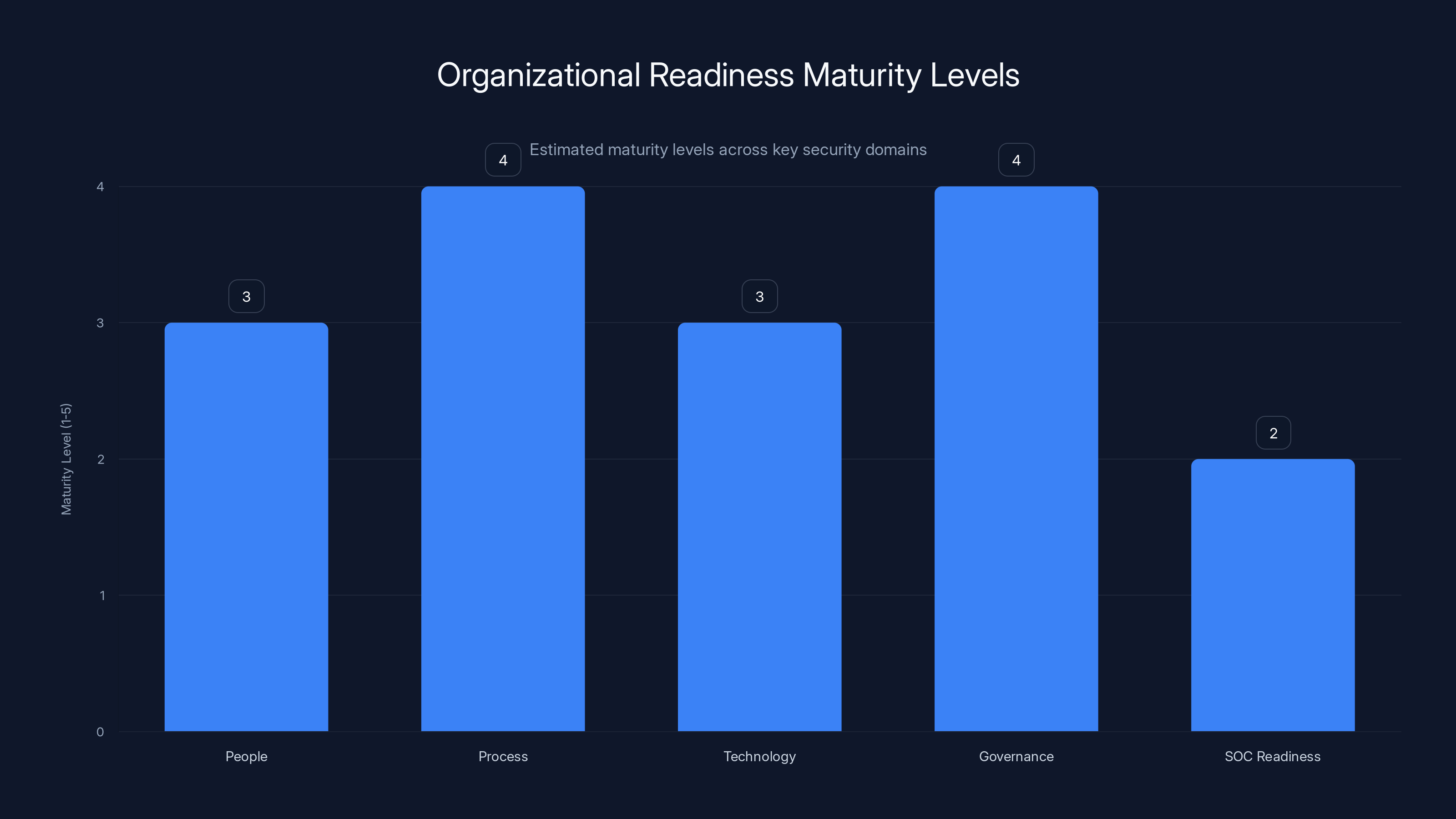
Estimated data suggests that Process and Governance are more mature than SOC Readiness in many organizations. Estimated data.
Why Traditional Security Controls Fail: The Human Factor
Here's the uncomfortable truth that every security leader knows: your technical defenses are only as strong as your least security-aware employee. And this campaign is specifically designed to exploit exactly that vulnerability.
Consider typical security defenses and why this attack bypasses them:
Firewalls and Network Security: These protect against network-based attacks. They're useless against someone who has valid credentials. Once authenticated, an attacker appears to the network as a legitimate user. Firewalls say: "Is this traffic from a known internal device? Yes? Then it's allowed." The attacker, authenticated through Okta, appears to be exactly that.
Intrusion Detection Systems (IDS): These look for suspicious network patterns. But an attacker with stolen Okta credentials isn't being suspicious. They're using the same applications in the same patterns that the legitimate employee would use. They access Salesforce because the employee's role has Salesforce access. They check Gmail because everyone checks Gmail. From a network perspective, everything looks completely normal.
Data Loss Prevention (DLP): These systems try to prevent sensitive data from leaving the network. They detect when someone tries to email out customer data, or attach files to Slack, or download large batches of documents. But SLH doesn't care about your DLP rules. They have time. They'll exfiltrate data slowly. A few customer records here. A few sales contracts there. Over weeks or months, they'll assemble enough data to use for extortion. And they'll do it in patterns that your DLP sees as normal behavior.
Email Filtering: This works great for phishing emails. But this attack doesn't primarily use email phishing. It uses phone calls. Your email filter can't block a vishing attack. It's voice communication. It's social engineering. It's trust being exploited.
Password Managers: These prevent users from reusing passwords or entering credentials on fake sites. But here's the problem: when an attacker impersonates IT support and tells you to enter your credentials into a system, many users bypass their password managers. "IT said to use the web form, so I'll type it in manually." The social engineering component overrides the technical safeguard.
Knowledge-Based Authentication: Security questions like "What's your mother's maiden name?" can be researched on social media, Linked In, or public records. Threat actors conducting reconnaissance on high-value targets will literally spend hours researching personal information about their targets.
Time-Based One-Time Passwords (TOTP): Authenticator apps that generate six-digit codes every 30 seconds. These are excellent security controls. But SLH's vishing approach defeats them through real-time interception and social engineering. The attacker doesn't need to crack the TOTP algorithm. They just need to ask the victim to read them the code while the attacker forwards the same code to the real system.
Push-Based MFA: Notification-based approvals on phones. These are even better than TOTP. But they suffer from the same social engineering vulnerability. "You should see a push notification right now. Can you approve it?" The employee approves it. The attacker is simultaneously validating their own session using the exact same approval.
The fundamental issue: every one of these controls assumes that the person authenticating is the legitimate user. They don't assume that a legitimate user, through social engineering, might voluntarily give attackers the authentication factors.
It's not a failure of technology. It's a limitation of what technology can address. Technology can't make humans un-manipulatable. Technology can't prevent someone from being called by someone who sounds authoritative and asking for their MFA code.

The Risk Calculus: Why Okta Compromise Is Worse Than Most Breaches
Let's be specific about the damage potential of a compromised Okta session. Unlike most data breaches, an Okta compromise isn't a single incident. It's the beginning of a weeks-long reconnaissance operation.
Day 1: Attacker gains Okta access. They're now logged in as the victim. They explore. They check what applications they have access to. They identify high-value systems. They check who else in the organization has administrative rights. They're mapping the infrastructure.
Days 2-3: The attacker establishes persistence. They create additional accounts—sometimes legitimate-appearing accounts that look like service accounts, sometimes spare accounts under names like "test.user" or "admin.backup". They assign these accounts to high-privilege groups. They enable password authentication in addition to SSO, giving them multiple ways to access these accounts even if the original Okta compromise is discovered.
Days 4-7: The attacker begins lateral movement. They've identified systems of interest—Salesforce for customer data, Git Hub for source code, AWS for infrastructure, Slack for internal communications, Service Now for IT records. They use their legitimate-appearing privileged accounts to access these systems. They don't exfiltrate everything immediately. They're selective. They're testing detection. They're understanding what will and won't trigger alerts.
Weeks 2-4: The attacker knows what data exists and where. They begin steady exfiltration. They use legitimate business processes to access and download data. A Salesforce report that includes customer contact information. A Git Hub repo clone that includes entire source code history. An AWS export of database records. They do this slowly, in patterns that match legitimate employee behavior.
Weeks 4-8: The attacker has assembled a significant cache of valuable data. Customer lists. Financial records. Source code. Employee information. Depending on the organization, they might have gigabytes to terabytes of information. Now they reach out with an extortion demand: "We have your data. Pay us $X or we release it." They might be specific: "We have contracts with your 500 largest customers. We have your proprietary algorithms. We have employee SSNs."
Throughout this process, the organization might have no idea they've been compromised. Why? Because the attacker is doing everything as a legitimate user. Their activity looks indistinguishable from actual employees. They access systems during business hours. They use legitimate credentials. They follow normal workflows.
This is why Okta compromise is so dangerous. It doesn't immediately trigger "ALERT: System Breached." It triggers gradual data exfiltration over weeks. By the time the organization discovers the compromise—usually when the attacker sends the extortion demand—the attacker has already obtained whatever data they wanted.
The damage calculation also includes incident response costs. A typical Okta compromise investigation requires:
- Forensic analysis of every login for the compromised account(s): potentially millions of log entries
- Review of every file accessed during the compromise window
- Assessment of every system the compromised account touched
- Credential reset across entire organization (not just the compromised account)
- Review of access logs for all potentially exposed systems
- Notification to customers if customer data was accessed
- Potential regulatory fines and penalties
- Business interruption and incident response team costs
- Potential ransomware payment if extortion demands escalate
A conservative estimate for incident response to an Okta compromise:
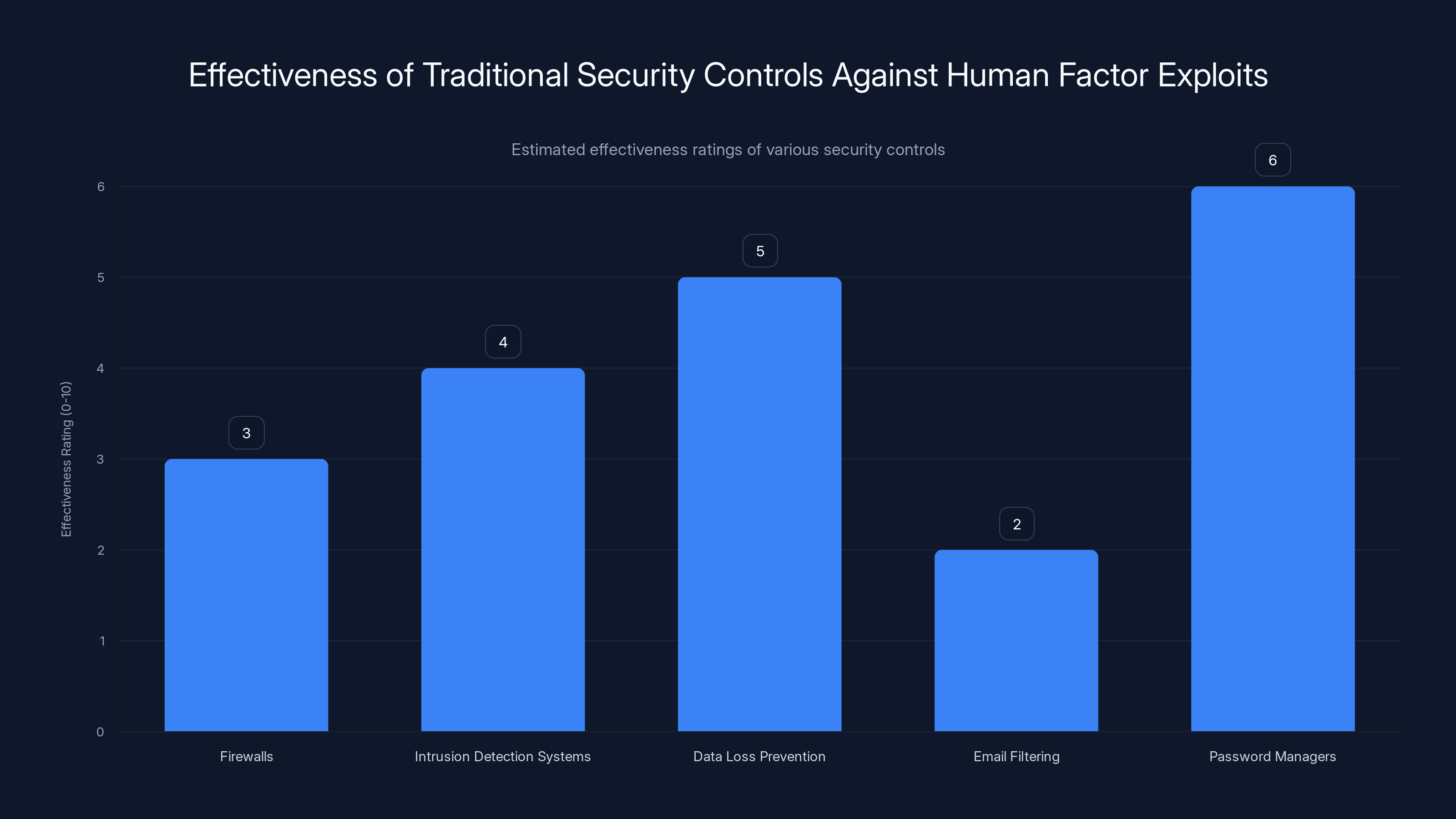
Traditional security controls show varying effectiveness against human factor exploits, with password managers being relatively more effective. Estimated data.
Who's Actually at Risk: Organizational Impact Assessment
The target list released by Silent Push includes over 100 organizations. But it's important to understand that this list represents organizations where SLH has specifically identified and begun targeting. It doesn't represent all organizations at risk.
In reality, any organization that:
- Uses Okta SSO (which includes most enterprises with 500+ employees)
- Has employees who work from outside office (remote workers, traveling sales teams, field offices)
- Has valuable data (customer information, financial records, intellectual property)
- Handles regulated information (healthcare, financial, personal information)
- Is a public company or significant private company
...is at risk from this campaign.
Small to medium businesses (100-500 employees) might think they're safe because they're not on the target list. Don't assume that. SLH's public target list represents Phase 1 of the campaign. Phase 2 will likely include mid-market targets. Phase 3, smaller targets. The initial focus is on high-profile companies—the ones where a successful breach generates news coverage and provides a credibility demonstration to potential extortion victims.
Specific high-risk industries include:
Financial Services: Banks, investment firms, insurance companies, payment processors. These organizations have regulatory obligations, significant cybersecurity budgets (meaning they've handled breaches before and likely have ransom budgets), and customer data that's directly monetizable.
Technology and Software: Saa S companies, cloud providers, software development firms. These organizations have substantial intellectual property in the form of source code. The competitive value of source code, algorithm implementations, and product roadmaps can be enormous.
Healthcare: Health systems, medical device manufacturers, pharmaceutical companies. Healthcare data is among the most valuable on the dark web. A single patient medical record can sell for
Manufacturing and Engineering: Companies with proprietary designs, manufacturing processes, or industrial secrets. Competitors in the same industry would pay significant money for access to product designs or manufacturing techniques.
Retail and E-Commerce: Companies with large customer databases. Customer lists with purchase history, browsing patterns, and contact information can be leveraged for follow-on attacks, sold to competitors, or used for targeted extortion (threatening to release customer data unless the company pays).
Critical Infrastructure: Energy, utilities, water systems, telecommunications. These organizations are often regulated, have insurance specifically for cyber incidents, and have significant budgets. They also face regulatory pressure—a major breach can result in fines from regulators, which provides another leverage point for extortion.
Legal and Professional Services: Law firms, consulting firms, accounting firms. These organizations often handle confidential information from multiple clients. A single breach can expose information about dozens of client organizations and individuals.
Geographically, the initial targets suggest SLH has particular focus on North America, Europe, and APAC, particularly Australia. But this is likely just Phase 1. As the campaign matures, expect targeting to expand to virtually every region and industry.

Immediate Technical Mitigations: What to Implement This Week
If your organization uses Okta, there are specific, technical steps you should implement immediately. These won't prevent all attacks—no single control can—but they will significantly reduce your risk.
1. Implement Hardware-Based MFA for All Administrative Access
Hardware security keys (Yubi Key, Titan Security Key, etc.) cannot be socially engineered. They cannot be captured by phishing proxies. They require physical possession of a device and a legitimate connection to the real authentication endpoint. SLH's vishing attacks are specifically designed to defeat software-based MFA. They don't work against hardware keys.
Implementation steps:
- Identify all users with Okta administrative rights
- Provision hardware security keys for these users immediately
- Configure Okta to require hardware MFA for any administrative actions
- Test the setup with a few users first
- Roll out to all administrators within 2 weeks
2. Enable Passwordless Authentication Where Possible
Passwordless authentication eliminates the first component of the attack chain. If there's no password to steal, the attacker can't use a password to log in.
Okta supports multiple passwordless options:
- Okta Verify with biometric authentication
- Windows Hello for Business
- FIDO2 security keys
- Push notifications to registered devices
The most secure approach is a combination: passwordless authentication for initial login, plus hardware MFA for sensitive actions. Attackers who can't get a password can't even complete the first step of the vishing attack.
3. Implement Okta Adaptive MFA Rules
Okta includes adaptive MFA, which increases authentication requirements based on risk signals. Configure rules that trigger stricter MFA when:
- Login occurs from an unusual geographic location
- Login occurs from an IP address not previously used by the user
- Login occurs during unusual hours
- Multiple failed login attempts occur
- Login occurs from a VPN or proxy
These rules won't catch all compromises (attackers can use proxies to mask location), but they will flag suspicious patterns. Couple this with monitoring and alerting, and you'll catch some attacks before data exfiltration begins.
4. Deploy Okta Device Trust and Okta Identity Governance
Device Trust ensures that authentication only succeeds from company-approved devices. An attacker logging in from their own computer—even with valid credentials—would fail because their device isn't registered as a legitimate corporate device.
This doesn't solve the vishing problem (the attacker is authenticating through the victim's device), but it does prevent attackers from immediately pivoting to their own devices for reconnaissance. If the attacker must stay on victim devices to maintain access, their activity is more easily detectable.
5. Implement Impossible Travel Detection
If an authenticated user logs in from New York at 2 PM, then logs in from London at 3 PM, that's physically impossible. A human can't travel that distance in one hour.
Configure your SIEM or Okta rules to detect and alert on these scenarios. Alert your security team immediately. Require step-up authentication if impossible travel is detected.
Again, attackers can use this against sophisticated organizations (they'll use time zones and spacing to avoid suspicious patterns), but it catches less sophisticated attacks.
6. Monitor for Suspicious Okta API Activity
If an attacker has Okta credentials and wants to maintain persistence, they might use the Okta API to create additional accounts, assign administrative roles, or configure additional authentication methods. Monitor for:
- API calls creating new users or accounts
- API calls modifying user permissions or roles
- API calls creating or modifying authentication methods
- API calls disabling or modifying security policies
- Bulk API operations (hundreds or thousands of API calls from a single user)
Configurable via Okta System Log monitoring or forwarded to your SIEM.
7. Segment Your Applications and Implement Zero Trust Access
If attackers compromise Okta, they shouldn't automatically have access to all connected applications. Implement zero trust access patterns where:
- Each application requires additional verification beyond Okta SSO
- High-value applications (database access, financial systems, source code repositories) require step-up authentication
- Application-level access logs are monitored separately from Okta logs
- Application-specific roles are used rather than relying purely on Okta group membership
This doesn't prevent Okta compromise, but it limits what attackers can access with a single compromised session.
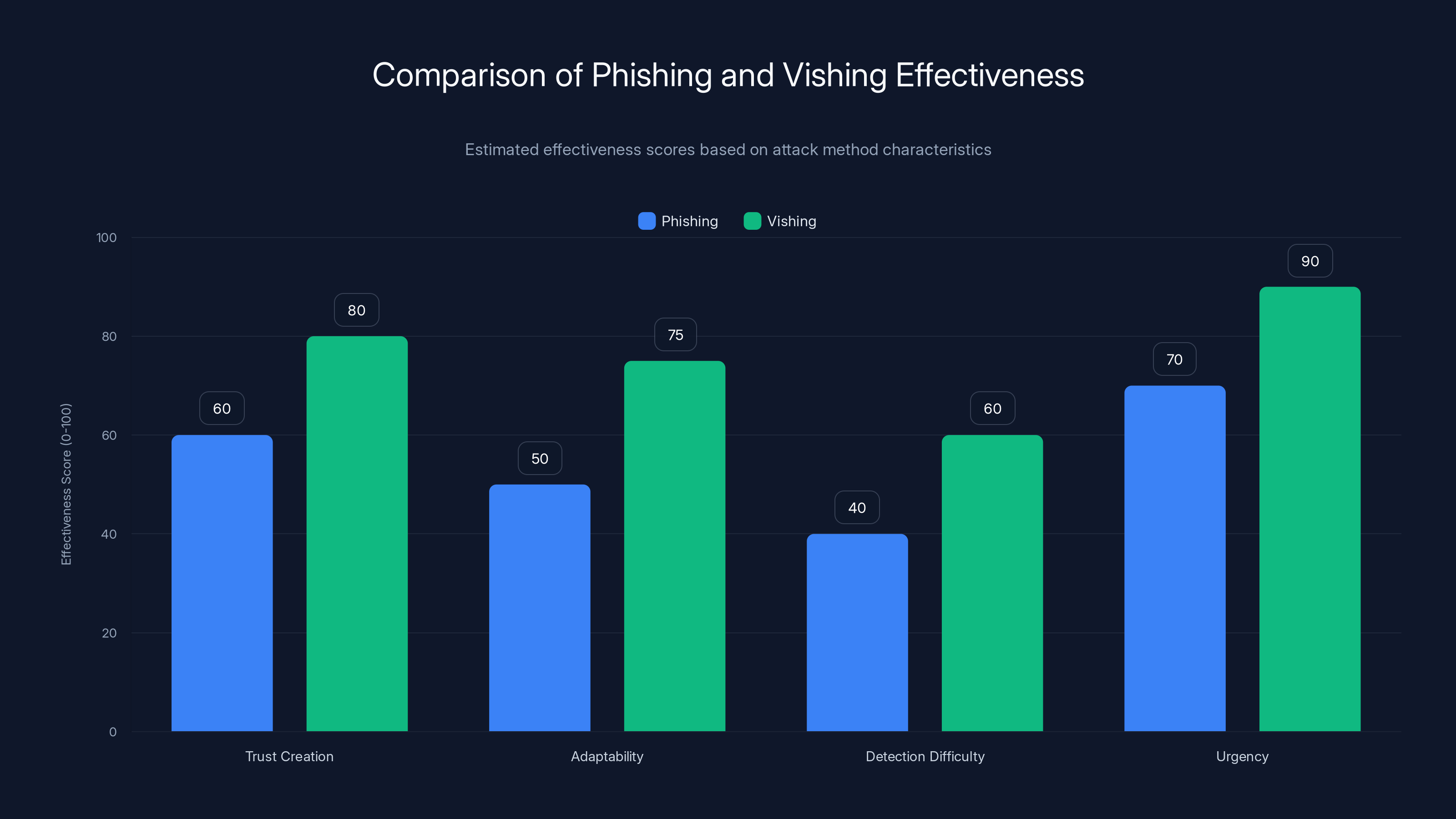
Vishing generally scores higher in trust creation and adaptability due to real-time interaction, making it more effective than phishing in these areas. Estimated data.
Behavioral and Operational Responses: Protecting Against Social Engineering
Technical controls are important, but they're insufficient against sophisticated social engineering. Your employees are the strongest link or the weakest link depending on how they're trained and supported.
Security Awareness Training Specifically for Vishing
Generic phishing awareness training doesn't prepare employees for vishing attacks. You need specific training that:
- Explains that legitimate IT support will never ask for passwords or MFA codes over the phone
- Provides specific scripts for how attackers will approach ("We're seeing unusual activity on your account," "We need to verify your identity for a security update," etc.)
- Gives employees permission to hang up and call back IT support through known numbers
- Explains the social engineering tactics (urgency, authority, trust-building through detailed knowledge)
- Provides reporting mechanisms and rewards for employees who report suspicious calls
Frustratingly, most security training is generic and doesn't address vishing specifically. Work with your security team to develop vishing-specific training.
Create a Secure Callback Process
Establish a policy and process where:
- If an employee receives an unexpected call from "IT Support" asking for credentials, they should immediately hang up (without rude, just "I'll call you back through the main line")
- They should call the IT Help Desk through a known, verified phone number (posted in the employee directory, on the company intranet, etc.)
- They should ask: "I received a call about unusual account activity. Can you verify if that came from IT?"
- IT should always be able to confirm or deny that they initiated contact
This simple process defeats a huge portion of vishing attacks. The attacker can't prove they're legitimate IT because they're not. The real IT can confirm they're not.
Implement a Phishing and Social Engineering Reporting System
Your employees are your sensors. Create a simple mechanism where they can report suspicious communications—emails, calls, texts—with a single action. Provide a dedicated email address (report-phishing@company.com) or integrate with security tools.
When an employee reports a vishing attempt, immediately:
- Verify the employee's account for recent suspicious activity
- Check if other employees received similar calls
- Attempt to identify the attacker's phone number and infrastructure
- Share intel with the employee's team so others are prepared
- Investigate and document the incident
Reward the reporting. Recognize the employee. Emphasize that reporting is valued, not punished. You want employees reporting suspicious activity before they're compromised, not hiding it after.
Require Identity Verification Before Granting Access
When your IT support or any support function (HR, Finance, etc.) receives a request that seems unusual—a request to change access, reset a credential, modify authentication settings—require identity verification beyond what the person already has.
If someone calls claiming to be from IT asking to reset your credentials, ask them questions that you and IT use to verify your identity. "What's the last project I completed for the company?" "What's the name of the development tool we use for version control?" These are questions an attacker wouldn't know.
Create an Incident Response Plan Specific to Credential Compromise
When (not if) this happens, you need a rapid response plan:
-
Immediate (0-30 minutes): Confirm the suspected compromise. Check access logs. Identify the compromised credentials. Notify all relevant teams.
-
Short-term (30 minutes - 2 hours): Force password reset for the compromised account(s). Revoke all active sessions. Revoke all active MFA registrations. Monitor for attempts to re-authenticate with the compromised credentials. Begin forensic analysis of what systems the compromised credentials accessed.
-
Medium-term (2 hours - 24 hours): Expand analysis to all connected systems. Identify all data potentially accessed by compromised accounts. Notify senior management. Contact legal. Prepare for potential notification obligations.
-
Long-term (24 hours - weeks): Full forensic investigation. Damage assessment. Notification to customers if required. Incident reporting to regulators if required. Communication to employees. Root cause analysis and remediation of the underlying vulnerability that allowed the compromise.
Document this plan. Test it regularly. Update it based on lessons from incidents at other organizations.

Detection and Response: Finding Compromised Sessions
The reality is that prevention will fail at some organizations. Some employees will be socially engineered. Some credentials will be compromised. Your detection and response capability is what prevents a compromise from becoming a catastrophe.
Log Analysis and Behavioral Baselines
Establish baselines for normal Okta activity:
- What time do individual employees typically log in?
- From which geographic locations?
- From which devices?
- Which applications do they access?
- How frequently do they perform actions?
- Which IP addresses are typical?
Once you have baselines, alert on significant deviations:
- Login from a new geographic location
- Login at an unusual time
- Access to applications the user doesn't typically use
- Bulk user creation or modification
- Authentication policy changes
- New MFA enrollment from an unusual device
This requires integrating Okta logs into a SIEM (Splunk, Elastic, Sumo Logic, etc.) with correlation rules and alerting.
Privileged Access Monitoring
Administrative accounts deserve special attention. Monitor every action by administrators in Okta:
- Login to Okta admin console
- Any changes to security policies
- Any changes to user permissions
- Any changes to integration settings
- Any API access
With administrative activity, you want real-time alerting, not delayed detection. If an attacker logs in to an administrative account, you want to know within minutes, not hours.
Credential Theft Pattern Detection
Scattered LAPSUS$ Hunters have a pattern: they compromise a user account, they confirm access works by logging in and accessing a few known applications, then they start creating additional accounts for persistence. Look for patterns like:
- Multiple failed login attempts followed by a successful login from a new device
- Successful login followed by immediate changes to authentication settings
- Successful login followed by creation of a new user account
- Creation of multiple user accounts in a short time period
- Bulk changes to group membership or role assignments
These patterns suggest credential compromise followed by persistence activities.
Session Analysis and Anomaly Detection
Look at individual sessions:
- How long is the session active?
- How many applications does the user access?
- What data is accessed during the session?
- Is there file download activity? How much data?
- Are there API calls? What kind?
- Are there administrative actions?
An attacker session often looks different from a normal employee session. Employees typically log in, work with a few applications, then log off. Attackers might have longer sessions, access more applications, perform administrative actions they're not authorized for.
Tools like Okta's own analytics, combined with SIEM analysis, can flag these patterns.
Data Exfiltration Detection
Regardless of Okta compromise detection, monitor for data exfiltration from your key systems:
- Salesforce: Monitor for bulk exports, report downloads, unusual queries
- Git Hub: Monitor for repository clones, large file downloads, new SSH keys
- AWS: Monitor for console access from unusual locations, API calls to list or export resources, database dumps
- Slack: Monitor for bulk message export, channel backups, integration creation
- Email: Monitor for unusual folder access, bulk mail export, forwarding rules
SLH doesn't exfiltrate everything at once. They do it slowly over weeks. But they will eventually need to export the data. Catching that export prevents the extortion demand—the attacker can't force you to pay for data they haven't collected.

Organizational Readiness: Assessment and Improvement
Beyond immediate technical mitigations, assess your organization's overall security posture and readiness to handle a potential compromise.
Identity and Access Management Maturity Assessment
Evaluate your current state:
- People: Do you have dedicated identity and access management staff? Do they have clear processes and procedures? Are they trained on security incidents?
- Process: Do you have documented procedures for credential compromise response? For user onboarding and offboarding? For access reviews? For privileged access management?
- Technology: Do you have a SIEM? Do you have endpoint detection and response (EDR)? Do you have privileged access management (PAM) tools? Are they all integrated and logging?
- Governance: Do you have regular access reviews? Do you audit privileged access? Do you have compliance requirements for access controls?
Highly mature organizations can detect and respond to a credential compromise within hours. Less mature organizations might not detect it for months.
Security Operations Center (SOC) Readiness
If you have a SOC (internal or outsourced), ensure they're prepared for a credential compromise incident:
- Have they run tabletop exercises simulating an Okta compromise?
- Do they know how to correlate logs across multiple systems?
- Do they have playbooks for credential compromise response?
- Do they have tools and access to terminate sessions, revoke credentials, and analyze logs across your environment?
- Do they have the authority to immediately disable accounts or force password resets without approval from business units?
Incident Response Plan for Okta Compromise
Develop a specific incident response plan for what happens if Okta is compromised:
-
Immediate actions (first 15 minutes): Notification tree (who gets called), initial investigation steps, decision point on whether to escalate
-
First hour: Containment (disable accounts, revoke sessions), communication (legal, PR, executive leadership), initial forensics
-
First 24 hours: Full scope determination (which systems were accessed, which data was viewed), damage assessment, notification to affected parties
-
One week: Remediation (updated security controls, credential resets, access reviews), communication (to customers if required, to employees, to board/investors)
-
Ongoing: Investigation completion, root cause analysis, security improvements, lessons learned documentation
Document this plan. Make sure the relevant people know it exists and understand their role. Test it at least annually.
Backup and Recovery Capability
Assume that if attackers get access to Okta and can move laterally, they might also be able to compromise backup systems. Ensure your critical data has immutable backups—backups that can't be deleted or encrypted by attackers even if they compromise your administrative systems.
Test restoration from these backups regularly. Know how long recovery takes. Know which data is critical for business continuity and prioritize recovery of that data.
Supply Chain Risk and Third-Party Implications
One often-overlooked aspect of Okta compromise risk is the supply chain impact. If your organization uses Okta and provides services to other organizations, a compromise of your Okta could potentially compromise your customers' access to your systems.
Okta Tenant Isolation
If you're a Saa S provider using Okta to authenticate your customers' employees, you need to understand Okta's multi-tenancy model:
- Each customer (tenant) has their own Okta org
- Compromise of one tenant should not affect other tenants
- But if your organization's Okta is compromised and you use that Okta to manage customer access, attackers could potentially modify customer authentication settings
If you're a Saa S provider, verify with Okta how tenant isolation works in your specific implementation.
Third-Party Audit of Identity Controls
If your organization is large enough to be audited by customers (SOC2, ISO27001, HITRUST, etc.), your identity controls are likely part of the audit scope. A compromise event would be a finding. Be prepared for:
- Customer audits asking for additional evidence of control effectiveness
- Potential contract implications (customers might demand increased security or reduced pricing)
- Regulatory audits if you handle regulated data
Communication with Customers and Partners
If your organization is targeted by SLH and the targeting becomes public (either through news coverage of the attack group or through your own disclosure), you should proactively communicate with customers:
- Explain what happened
- Explain what data was and wasn't accessed
- Explain what you're doing to prevent recurrence
- Provide guidance on what customers should do
Proactive, transparent communication builds trust and prevents customers from learning about the incident from news media.

Okta's Response and Vendor Security Improvements
Okta, as the target of this campaign, has a significant interest in improving their own security and helping customers defend against these attacks.
Okta's Published Guidance
Okta has published detailed guidance on defending against vishing attacks and securing Okta implementations. Review this guidance:
- Best practices for MFA configuration
- Recommendations for authentication policy implementation
- Guidance on detecting compromised sessions
- Information on security enhancements in newer Okta versions
Okta Customer Security Notifications
Okta notifies customers about threat intelligence related to attacks targeting Okta or authentication generally. Subscribe to these notifications and read them when they arrive. Sometimes Okta will provide indicators of compromise (IOCs) that customers can use to check their own logs.
Okta's Roadmap for Security Enhancements
Okta continues to invest in security features specifically designed to prevent these types of attacks:
- Improved adaptive MFA rules and anomaly detection
- Better logging and visibility into authentication events
- Enhanced passwordless authentication options
- Integration with device security providers for device-based authentication
- Threat analytics and automated response capabilities
Understanding the roadmap helps with planning security improvements in your own organization.
Okta Alternatives and Comparative Risk Assessment
Some organizations might consider switching away from Okta as a response to this threat. Before doing so, understand that similar attacks are possible against any major identity provider—Ping Identity, Microsoft Entra ID (formerly Azure AD), One Login, etc.
The characteristics that make Okta a target (enterprise adoption, central role in infrastructure, valuable data accessible through SSO) apply to other identity platforms as well.
Instead of switching vendors (which is expensive and disruptive), focus on:
- Implementing comprehensive MFA with hardware-based options
- Reducing reliance on password-based authentication by moving to passwordless
- Monitoring identity infrastructure with specific attention to credential compromise detection
- Training employees on social engineering awareness
- Segmenting applications so a single compromised identity doesn't grant universal access
These approaches work regardless of which identity provider you use.

Future Threat Evolution: What's Next
This Scattered LAPSUS$ Hunters campaign is unlikely to be the last attack on identity infrastructure. Expect to see evolution:
AI-Enhanced Social Engineering
Attackers are beginning to use AI-generated voice to conduct vishing attacks. Instead of a human calling and conducting social engineering, an AI-generated voice that sounds convincing and natural conducts the call. This could potentially scale vishing attacks from hundreds of targets per group to thousands, all automated.
Defense: Require callback verification (employee hangs up, calls back through known number). AI voice might sound natural, but it can't respond to unexpected verification questions in real time.
Compromised Identity as a Service
As attacks become more successful, some threat groups might begin selling compromised credentials as a service. "We'll compromise an Okta account for your competitor for $10,000. Here's proof of access." This creates a marketplace where attackers and their customers don't need to do the social engineering themselves.
Defense: Session monitoring that detects when credentials are being used from unusual locations or patterns, even if the initial compromise isn't detected.
Hardware Spoofing
Advanced threat actors might begin developing ways to spoof or compromise hardware security keys. This is technically difficult and expensive but not impossible. As passwordless authentication and hardware MFA become standard, well-funded attackers will invest in defeating it.
Defense: Layered authentication where MFA is just one component. Use MFA plus device trust plus location analysis plus user behavior analysis. No single factor is perfect; combinations are much harder to defeat.
Supply Chain Attacks on Identity Infrastructure
Instead of directly targeting Okta, attackers might compromise Okta's software supply chain, its plugins, or its integrations. A compromised Okta plugin could gain access to every organization that uses that plugin.
Defense: Software supply chain security, regular audits of installed plugins and integrations, code signing verification, and rapid patching processes.
The Bottom Line: Preparation Over Prevention
Here's the uncomfortable truth: no organization can perfectly prevent sophisticated credential-based attacks. Humans are vulnerable to social engineering. That's not a failure of technology. That's a feature of human cognition.
What organizations can do is:
-
Reduce the probability of compromise through technical controls (passwordless, hardware MFA) and organizational controls (training, secure callback processes)
-
Reduce the impact if compromise occurs through segmentation (not all credentials grant access to all systems) and monitoring (detecting compromises quickly)
-
Prepare for rapid response through incident response plans, backup systems, and tested procedures
The organizations that suffer the most from attacks like this are those that assume it won't happen to them and therefore have no detection or response capability. By the time they detect a compromise, the attacker has been in their environment for months.
The organizations that suffer the least are those that assume compromise is inevitable and therefore prepare for it. They detect attacks quickly. They limit the damage. They recover rapidly.
SLH's campaign against Okta SSO is sophisticated and effective. But it's not inevitable. It's preventable, detectable, and survivable with the right preparation.
FAQ
What is vishing and how does it differ from phishing?
Vishing (voice phishing) is a social engineering attack conducted over the phone, while phishing typically occurs through emails or text messages. Vishing is often more effective because voice communication creates immediate trust and psychological pressure. Attackers impersonate authority figures like IT support, making urgent requests that bypass normal verification processes. The real-time interaction also allows attackers to adapt their social engineering approach based on victim responses, making it harder to detect than written phishing attempts.
How does Scattered LAPSUS$ Hunters actually compromise Okta credentials?
SLH uses a multi-step process combining social engineering and technical infrastructure. First, they research target employees on Linked In or public sources. Then they call impersonating IT support, creating urgency around account security or mandatory updates. They direct victims to phishing domains they control that closely mimic Okta login pages. Using a "Live Phishing Panel" (a man-in-the-middle proxy), they capture credentials as entered and simultaneously forward them to the real Okta system. When Okta prompts for multi-factor authentication, they use social engineering to convince the victim to read them the MFA code. With both credentials and MFA, they now have complete access.
Why is Okta compromise more dangerous than compromising a single application?
Okta functions as a central identity hub connecting to hundreds of organizational applications. A compromised Okta session acts as a "skeleton key," providing automatic authentication to all connected systems without requiring separate compromises of each app. Attackers can access Salesforce for customer data, Git Hub for source code, AWS for infrastructure, Slack for internal communications, and dozens of other systems from a single validated session. This enables weeks-long reconnaissance and data exfiltration that would take months if each system had to be compromised separately.
What immediate steps should an organization take if they suspect credential compromise?
If you suspect Okta credentials are compromised, immediately force a password reset for the affected account(s), revoke all active sessions, revoke all registered MFA devices, and begin analyzing access logs to determine what systems the compromised credentials accessed. Within the first hour, disable the compromised account entirely and check for related suspicious activity like new account creation or permission changes. Then begin forensic analysis of all systems the compromised account touched to determine the scope of potential data access. Document everything for potential regulatory reporting requirements.
Can hardware security keys be defeated by vishing attacks?
Hardware security keys (like Yubi Keys) are much more resistant to vishing attacks than software-based MFA because they require physical possession of a unique device and cryptographic validation with the legitimate authentication endpoint. An attacker cannot use vishing to trick someone into providing a hardware key, and the key cannot be used remotely without the attacker having physical access to it. However, no single security control is perfect—layered defenses combining hardware keys with device trust, location monitoring, and behavioral analysis provide much better protection than relying on any single factor.
How can organizations detect if their Okta session has been compromised?
Look for suspicious patterns in your Okta audit logs: logins from unusual geographic locations or IP addresses, access to applications you don't typically use, unusual timing of logins, creation of new user accounts you didn't authorize, changes to authentication policies, or bulk API activity. Many organizations miss these signals because they're not actively monitoring. If you have a SIEM (Splunk, Elastic, etc.), configure correlation rules to alert on these patterns. Real-time alerting is crucial—if you wait for a daily report and a compromise occurred yesterday, the damage has already been done.
What role does employee training play in preventing vishing attacks?
Employee training is critical but must be specific to vishing, not generic phishing awareness. Employees need to understand that legitimate IT support will never ask for passwords or MFA codes over the phone, and they should always hang up and call back IT through a known phone number to verify requests. Training should include specific examples of social engineering tactics attackers use (urgency, authority, technical complexity) and permission for employees to verify requests through alternate channels. However, even well-trained employees can be socially engineered by sophisticated actors. Training is necessary but insufficient—it must be combined with technical controls like secure callback procedures and anomaly detection.
Is switching away from Okta a viable response to this threat?
Switching identity providers would be expensive and disruptive, but similar vishing attacks could target any major identity provider (Ping Identity, Microsoft Entra ID, One Login, etc.). The characteristics that make Okta valuable to attackers—enterprise adoption, central role in infrastructure, broad access to multiple applications—apply to all major identity platforms. Instead of switching, focus on hardening your current identity infrastructure through passwordless authentication, hardware MFA for sensitive access, anomaly detection, and employee training. These defensive measures work regardless of which identity provider you use and are significantly less disruptive than a vendor migration.
How does "impossible travel detection" work as a security control against Okta compromise?
Impossible travel detection looks for authentication attempts from locations that would be physically impossible to travel between in the time elapsed. For example, if an employee logs in from New York at 2 PM and then logs in from London at 2:15 PM, that's physically impossible without a private jet. Security systems alert on these patterns. However, sophisticated attackers can defeat this by using time zones and spacing their access to avoid suspicious patterns (login from New York, then 8 hours later from London). Still, it catches less sophisticated attacks and forces well-funded attackers to be more careful about their patterns, which can make their activity more detectable through other means.
What should organizations do if they appear on SLH's target list?
Being on a target list doesn't mean your organization has been compromised—it means you've been identified as a potential target. Assume attackers are currently or will soon be attempting vishing attacks against your employees. Implement heightened identity monitoring immediately, increase employee security awareness training focused specifically on vishing, enforce hardware MFA for all administrative access, and establish incident response procedures. Notify your security team and executive leadership, and consider briefing your board if this organization is public. Most importantly, begin detecting attempts now rather than waiting until the campaign succeeds.
Conclusion: From Awareness to Action
The Scattered LAPSUS$ Hunters campaign targeting Okta SSO represents a sophisticated, coordinated, and active threat to major enterprises globally. This isn't a theoretical attack or a vendor-specific vulnerability. It's a real campaign happening right now, with real attackers actively attempting to compromise real organizations.
The organizations most at risk are those that understand this threat and have prepared for it. They've implemented passwordless authentication and hardware MFA. They've deployed monitoring to detect compromised sessions. They've trained employees on vishing tactics. They've prepared incident response procedures. They've segmented their applications to limit the blast radius of a compromise.
Organizations that ignore this threat because they "haven't been targeted yet" are making a critical mistake. The targeting lists are not public. You only discover you've been targeted when the attack succeeds or when your security team happens to detect the vishing attempts.
If you haven't already taken action, here are the priorities:
This week: Deploy hardware MFA for all administrative access to Okta. Configure adaptive MFA rules based on risk signals. Brief your security team on the threat and begin monitoring for indicators of compromise.
This month: Implement vishing-specific security awareness training. Establish secure callback procedures for sensitive requests. Deploy logging and monitoring for all identity infrastructure.
This quarter: Complete migration to passwordless authentication for all users. Implement device trust and location-based rules. Conduct a full security assessment of your identity infrastructure and third-party integrations.
Ongoing: Regular detection and response testing. Employee security training updates. Monitoring of Okta security advisories and threat intelligence.
The good news: these controls don't just protect against this specific campaign. They make your entire identity infrastructure more secure against credential-based attacks generally. They're investments in baseline security, not overreactions to a single threat.
The reality: credential-based attacks are becoming the primary attack vector for sophisticated threat actors. The attackers understand that controlling identity is more valuable than deploying malware or ransomware. The organizations that invest in identity security today are the organizations that will defend themselves effectively against threats for years to come.
Your Okta SSO infrastructure is critical. Treat it that way. Defend it accordingly. Prepare for compromise even as you work to prevent it. That's not paranoia. That's professional cybersecurity.
Start today. Your organization's security depends on it.
Key Takeaways
- Scattered LAPSUS$ Hunters are actively running vishing campaigns targeting ~100 enterprises' Okta SSO credentials with real-time MFA interception capabilities
- One compromised Okta session provides complete 'skeleton key' access to all connected enterprise applications and systems, enabling rapid lateral movement and data exfiltration
- Vishing attacks defeat traditional MFA through social engineering, but hardware security keys and passwordless authentication provide significantly stronger resistance
- Organizations should implement layered defenses: hardware MFA for admins, passwordless authentication, anomaly detection, application segmentation, and employee training on social engineering
- Detection and rapid response capabilities are critical—the average time to detect credential-based breaches is 191 days, during which attackers can exfiltrate terabytes of data
Related Articles
- OpenAI Scam Emails & Vishing Attacks: How to Protect Your Business [2025]
- Browser-Based Attacks Hit 95% of Enterprises [2025]
- AI-Powered Phishing: How LLMs Enable Next-Gen Attacks [2025]
- WhatsApp's Strict Account Settings: Ultimate Cyberattack Protection [2025]
- TikTok US Outage Recovery: What Happened and What's Next [2025]
- 800,000 Telnet Servers Exposed: Complete Security Guide [2025]
![Okta SSO Under Attack: Scattered LAPSUS$ Hunters Target 100+ Firms [2025]](https://tryrunable.com/blog/okta-sso-under-attack-scattered-lapsus-hunters-target-100-fi/image-1-1769546323157.jpg)



