WinRAR's Critical Security Crisis: What You Need to Know Right Now
It's 2025, and one of the oldest, most trusted file compression tools on Windows just became weaponized by some of the world's most dangerous hackers.
I'm talking about WinRAR. You know it. You've probably used it for two decades without thinking twice. It's been sitting in your Program Files folder since the Windows XP days, quietly compressing files while you moved on to other tasks.
But here's what changed: a path traversal vulnerability tracked as CVE-2025-8088 was discovered, and it's not theoretical. This isn't a "might happen someday" situation. Security researchers documented actual exploitation in the wild by Russian state actors, Chinese government-backed groups, and financially motivated cybercriminals, as reported by The Hacker News.
So if you're still running WinRAR version 7.12 or older, your computer is potentially vulnerable to arbitrary code execution. That means attackers can install malware, steal credentials, deploy ransomware, or worse—all through a simple archive file, as detailed in Google Cloud's threat intelligence blog.
This isn't a blog post about best practices. This is a practical guide to understanding what went wrong, who's exploiting it, and exactly what you need to do to stay protected.
TL; DR
- CVE-2025-8088 is a high-severity path traversal flaw in WinRAR versions 7.12 and older with an 8.4/10 CVSS score, according to CyberPress.
- Nation-states and criminal groups are actively exploiting it to deploy NESTPACKER, POISONIVY, XWorm, and Async RAT malware, as noted by SocPrime.
- Exploitation uses the Alternate Data Streams (ADS) feature to hide malicious payloads inside RAR archives, as explained by Google Cloud's threat intelligence blog.
- Update to version 7.13 immediately (no uninstall needed—install over existing version), as recommended by ExpressVPN.
- This has been weaponized since mid-July 2025 by at least six major threat groups, as reported by The Hacker News.
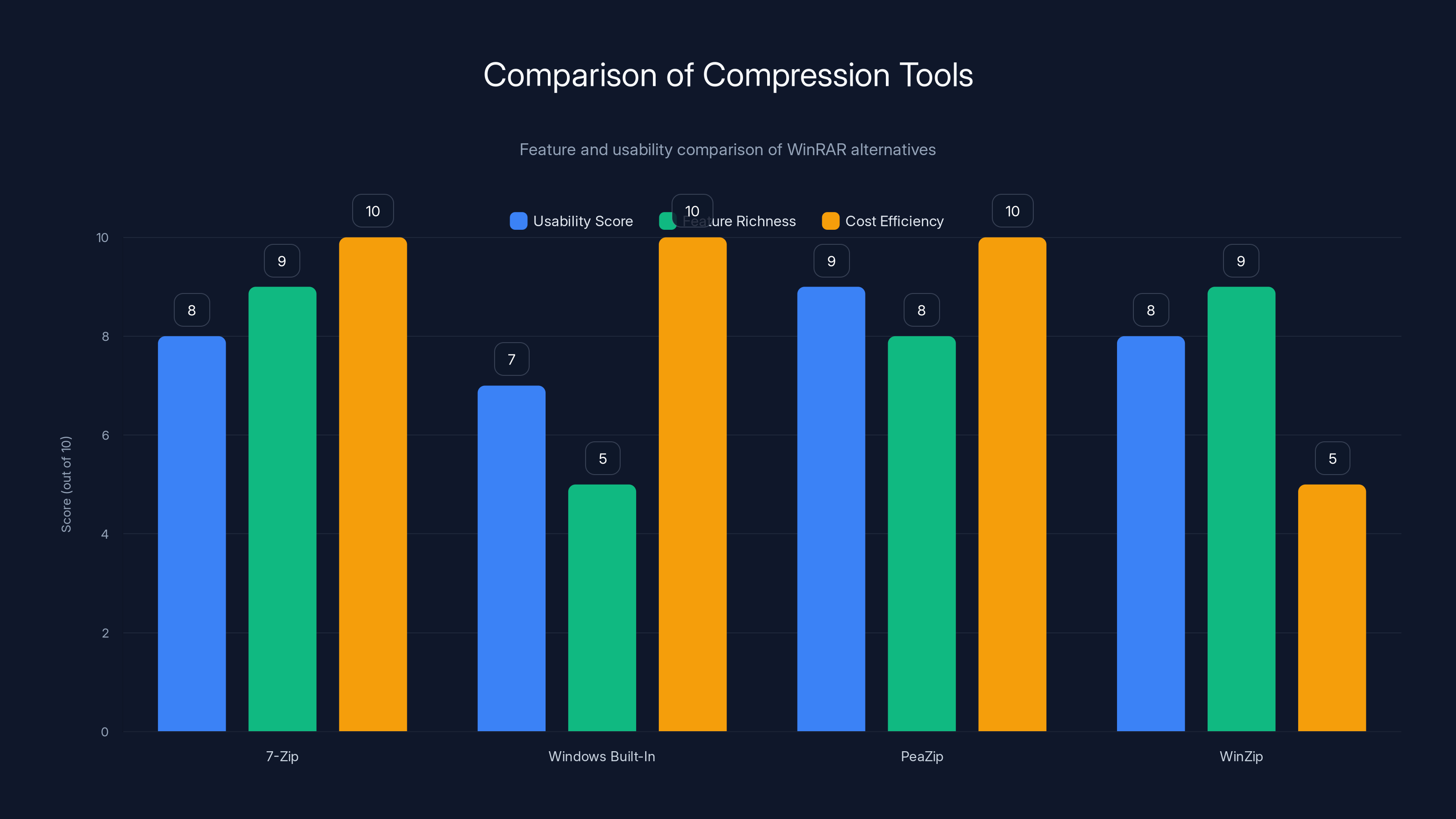
7-Zip and PeaZip offer excellent feature richness and cost efficiency, making them strong alternatives to WinRAR. Estimated data based on typical user feedback.
Understanding CVE-2025-8088: The Vulnerability Breakdown
What Is a Path Traversal Vulnerability?
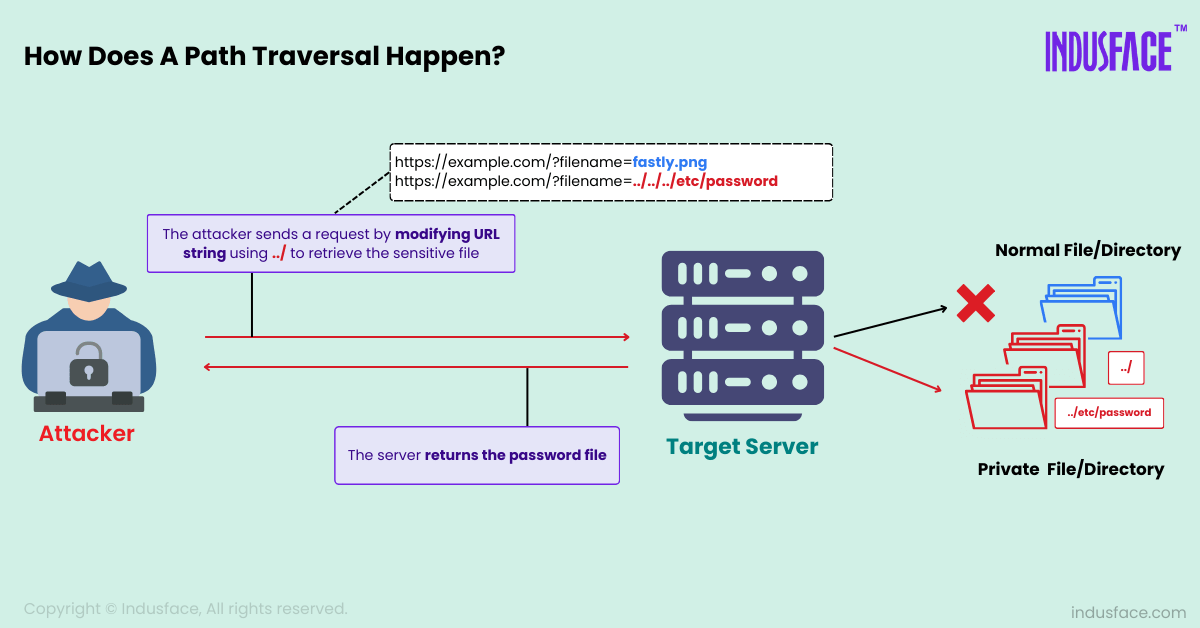
A path traversal vulnerability is a security flaw that allows attackers to access files or directories outside the intended location on a system. Think of it like this: when you extract a file from a RAR archive, the software is supposed to put it in your Downloads folder (or wherever you specify). A path traversal bug allows a malicious archive to say "actually, put this in System 32" or "write this to the startup folder."
In technical terms, the vulnerability occurs when an application fails to properly validate or sanitize file paths. Instead of checking whether a path tries to escape the intended extraction directory using sequences like ../ or absolute paths, the software trusts the archive and executes the extraction blindly.
With WinRAR's CVE-2025-8088, attackers abuse the Alternate Data Streams (ADS) feature, a Windows-specific capability that allows multiple data streams to attach to a single file. It's a legitimate feature, but in malicious hands, it becomes invisible.
The CVSS Score Explained
CVE-2025-8088 received a severity score of 8.4 out of 10 on the Common Vulnerability Scoring System (CVSS). Here's what that means:
Scores are calculated based on multiple factors: attack vector (how easily the attack can be performed), attack complexity (whether special conditions are needed), privileges required (does the attacker need admin access), and user interaction (does someone have to click something).
An 8.4 rating means this is high severity. It's not critical (9.0+), but it's serious. The attack requires minimal user interaction—just opening an archive file. No admin privileges needed. No complex setup. A user opens what looks like a normal RAR file, and malware deploys.
For comparison, the National Vulnerability Database tracks thousands of vulnerabilities weekly. Most fall in the 5-7 range. An 8.4 gets security teams moving fast.
Why Alternate Data Streams Make This Worse
Alternate Data Streams are a Windows feature that most users don't know exists. When you create a file on NTFS (Windows' file system), you're actually creating a "main" data stream. You can also attach additional, hidden data streams to the same file.
For example, you could create a file called document.pdf with a hidden .exe attached. When you open the file, you see a PDF. The executable? Invisible. The file system sees it, but Windows Explorer doesn't show it.
WinRAR's vulnerability allows attackers to embed these hidden streams inside compressed archives. When extraction happens, the path traversal bug lets them write these streams to system directories.
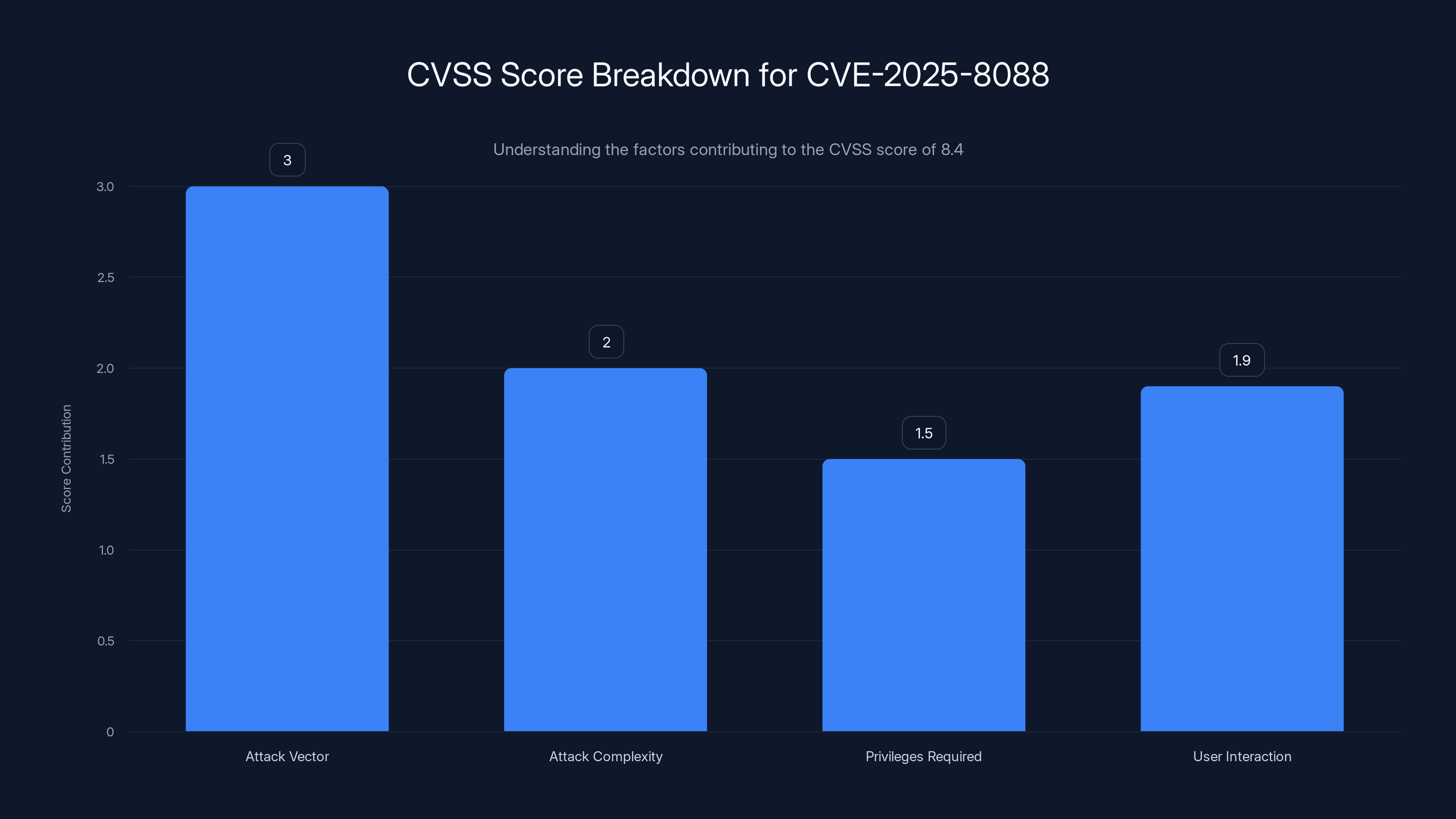
The CVSS score of 8.4 for CVE-2025-8088 is driven by a high attack vector score and minimal user interaction requirement, indicating a high severity vulnerability.
The Timeline: How This Vulnerability Became Weaponized
When the Bug Was First Discovered
The earliest documented evidence of CVE-2025-8088 exploitation appeared in mid-July 2025, according to security researchers at Google's Threat Intelligence Group. That's about six months before public disclosure in some cases—a dangerous window where only attackers knew about it.
But here's the critical part: this wasn't a simultaneous discovery. Different threat groups found and began exploiting this flaw independently. Within weeks, at least six major attackers were using it.
The Initial Victims
The first confirmed targets were Ukrainian military units. Security researchers reported that Rom Com, a Russian-aligned threat group, was using the vulnerability to deploy NESTPACKER malware against Ukrainian defenders. Timing-wise, this aligns with ongoing cyber operations in the region.
APT44 and Turla, both Russian state-sponsored groups, were also leveraging the flaw with malware specifically designed for military networks. These aren't amateur hackers—these are groups with budgets, organization, and direct government backing.
The Spread to Criminal Groups
Once nation-states started using it, financially motivated threat actors noticed. Within weeks, criminal groups adapted the exploit for their own purposes: deploying infostealers like XWorm and Async RAT.
XWorm is an open-source remote access trojan that criminals rent out. Async RAT works similarly—it's a commodity malware available on dark web markets. Once attackers added WinRAR exploitation to their toolkit, they could send thousands of phishing emails with malicious RAR attachments, and each one carried a hidden payload.
The Chinese State Actors Enter the Game
Chinese government-sponsored groups also began using the vulnerability, specifically to deploy POISONIVY malware. POISONIVY is a sophisticated spyware tool with capabilities for stealing credentials, monitoring communications, and maintaining persistent access.
The fact that multiple Chinese groups adopted it independently suggests this wasn't a random find—they likely tracked the vulnerability through their own intelligence networks and weaponized it as part of broader cyber espionage campaigns.
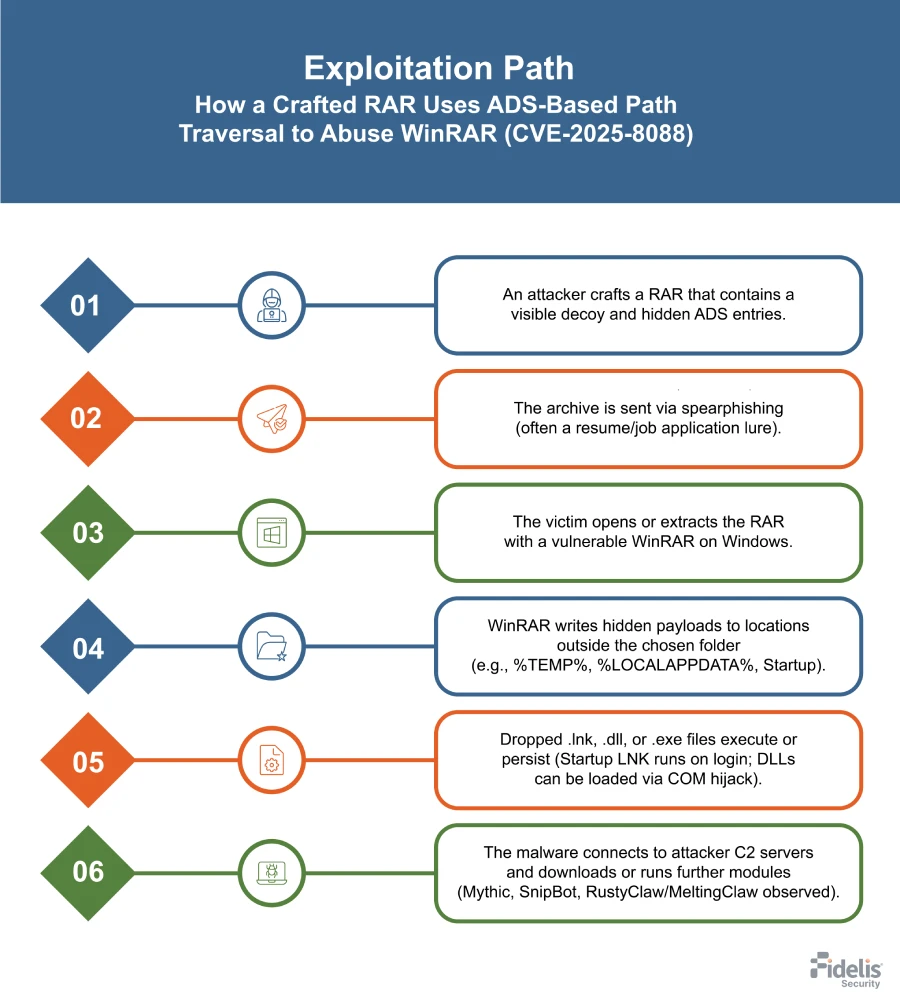
How the Attack Actually Works: Step by Step
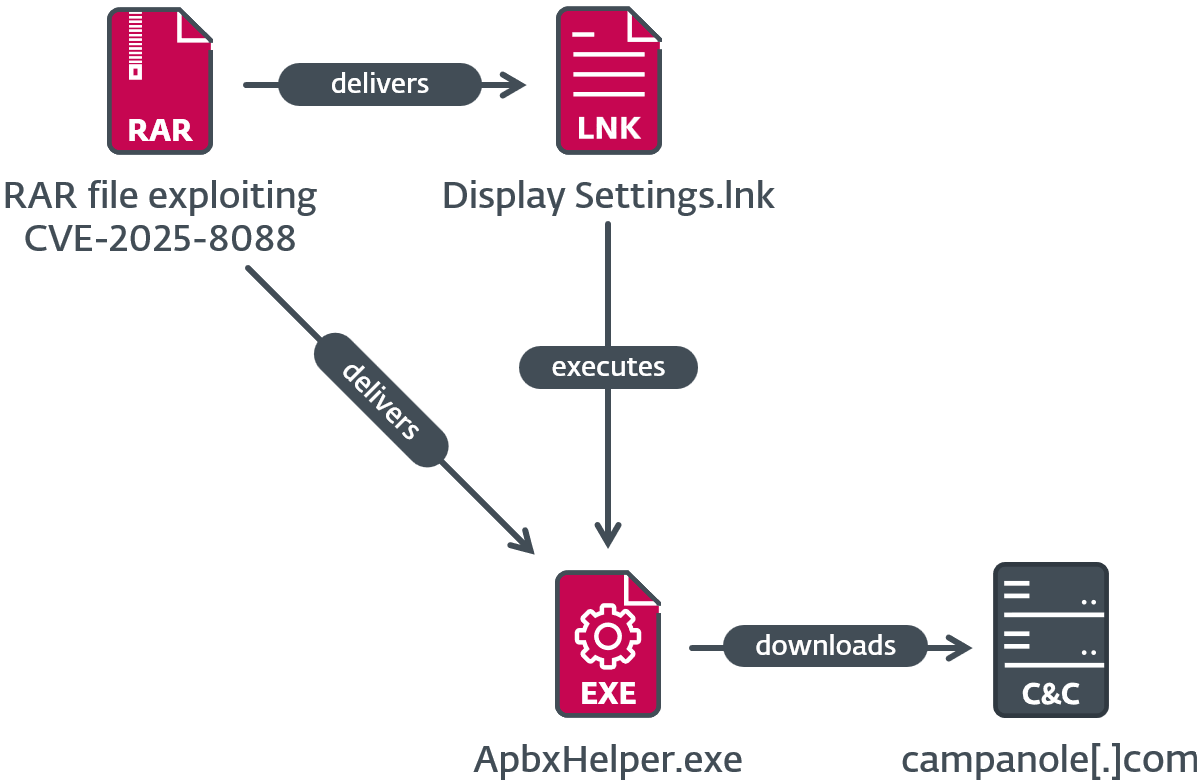
Step 1: The Malicious Archive Creation
An attacker creates a RAR file with two components: a decoy document (legitimate-looking PDF or Word file) and hidden malicious ADS entries. To the user, the archive appears to contain only the innocent document.
The attacker uses tools that can craft RAR files with specific directory traversal sequences. These sequences use relative paths like ..\..\Windows\System 32 to tell WinRAR exactly where to extract the hidden payload.
Some of these hidden entries are actual malware. Others are dummy data designed to blend in and confuse analysis. It's misdirection at the file level.
Step 2: Social Engineering and Delivery
The malicious RAR gets sent via email, messengers, or uploaded to file-sharing sites. The filename matters: Invoice_2025.rar, Security_Update.rar, Tax_Form_Scan.rar. Something that makes sense to open.
Many of these campaigns target specific organizations. A phishing email to a finance department looks like an invoice. To military networks, it might look like an official bulletin.
Step 3: User Opens the Archive
The victim opens the file with WinRAR. The application displays the decoy document—a PDF that opens in their PDF reader. The user sees exactly what they expect: a legitimate-looking file.
Meanwhile, in the background, WinRAR is extracting the hidden ADS entries. Because of the path traversal flaw, these entries write to system directories: Startup folders, System 32, App Data, or other sensitive locations.
Step 4: Malware Execution
The payload doesn't need the user to do anything else. If it was written to a startup folder, it executes on the next reboot. If it was written to a directory that auto-executes scripts, it runs immediately.
Depending on the malware, this might establish a reverse shell (giving attackers remote access), install a credential stealer (harvesting passwords and session tokens), or deploy additional payloads like ransomware.
The whole process takes seconds. By the time the user closes the PDF, the malware is already running.
Step 5: Persistence and Escalation
Once inside, the malware establishes persistence—mechanisms to survive reboots and system cleanup. Common tactics include:
- Registry modifications that load malware on startup
- Scheduled task creation
- DLL injection into system processes
- Creating new user accounts for backdoor access
If the initial payload is a remote access trojan, an attacker is now inside the network. For nation-states and organized crime, this is the foothold they need to escalate privileges, move laterally to other systems, and achieve their objectives.
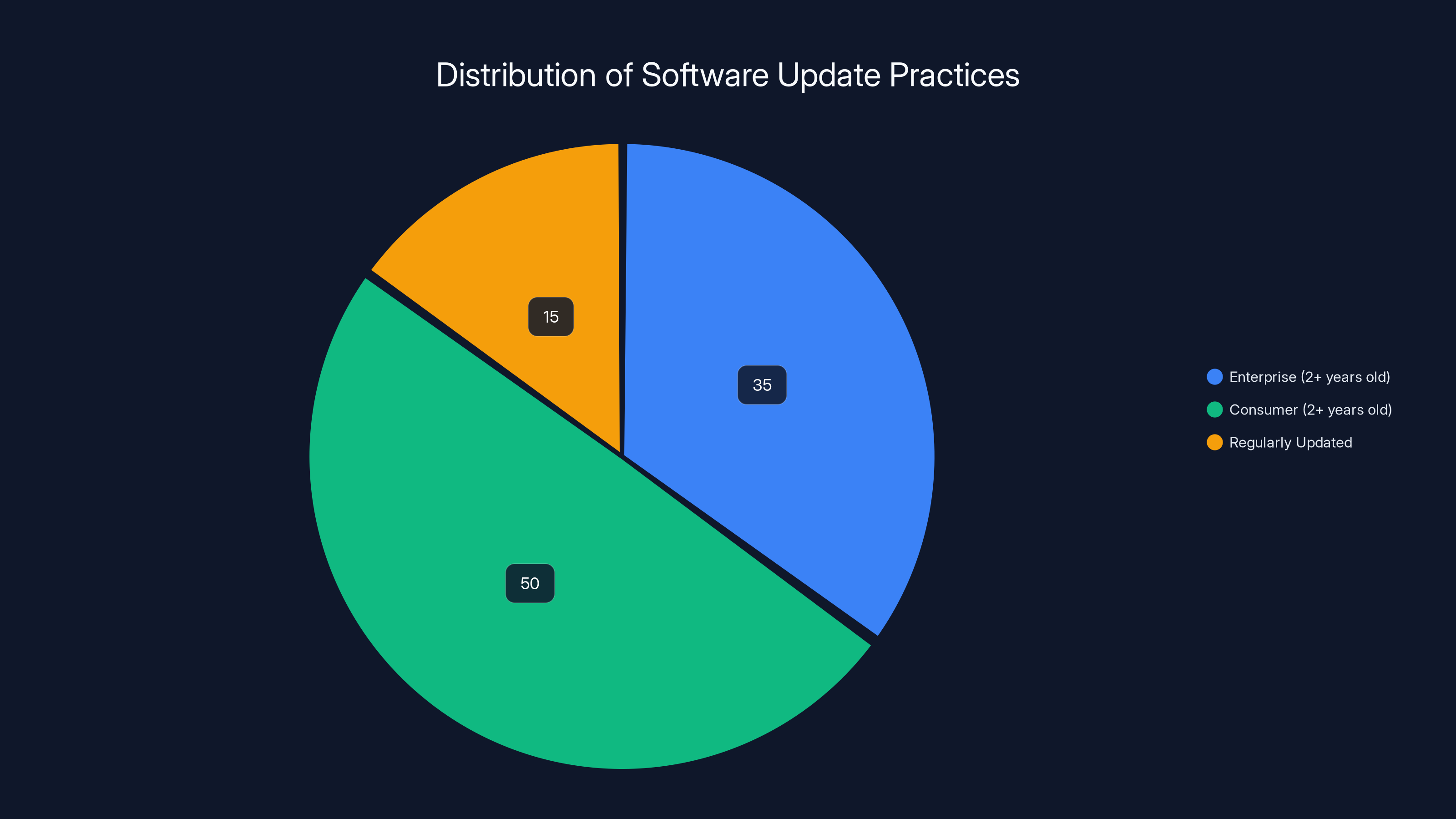
Estimated data suggests that a significant portion of both enterprise (35%) and consumer (50%) machines run outdated software, highlighting a major risk in supply chain security.
The Threat Groups Weaponizing This Vulnerability
Rom Com: Russian-Aligned Operators
Rom Com is a Russian-speaking threat group with a history of targeting military and energy sectors. The group has been active since at least 2021, but their capabilities have evolved significantly.
When security researchers first documented Rom Com's use of CVE-2025-8088, they were deploying NESTPACKER, a modular backdoor designed specifically for lateral movement in networked environments. Ukrainian military units were the primary targets, suggesting direct government backing and coordination with information warfare operations.
What's notable about Rom Com's operations is sophistication—their reconnaissance is thorough, their payloads are custom, and their command and control infrastructure is resilient. They're not a script-kiddie group.
APT44 and Turla: Russian State Sponsors
APT44 is another Russian state-sponsored group, widely believed to be affiliated with Russian military intelligence (GRU). Turla is similarly state-backed, with operations spanning two decades.
Both groups used CVE-2025-8088 against Ukrainian military networks, which aligns with known information warfare activities. The malware deployed—customized backdoors and credential theft tools—indicates these weren't opportunistic attacks but targeted campaigns with specific objectives.
What's concerning about APT44 and Turla adopting this exploit is that they have significant resources and can integrate it into broader cyber campaigns targeting NATO-aligned nations. It's not just about Ukraine—it's about establishing footholds in multiple countries' security infrastructure.
Chinese State-Sponsored Groups
Multiple Chinese government-backed threat actors began using CVE-2025-8088 to deploy POISONIVY. POISONIVY is sophisticated malware with capabilities for:
- Credential harvesting from browsers and email clients
- Real-time screen monitoring and keystroke logging
- File exfiltration
- Network reconnaissance
- Persistence mechanisms
Chinese state actors using this against US and allied organizations suggests espionage objectives—stealing intellectual property, monitoring communications, or establishing long-term access for future operations.
Criminal Groups: XWorm and Async RAT Operators
Beyond state actors, financially motivated cybercriminals quickly adapted the exploit. Groups using XWorm and Async RAT target:
- Cryptocurrency exchange accounts
- Banking credentials
- Corporate email accounts
- VPN access credentials
- Confidential business files
These groups operate more like a business. They send thousands of emails, compromising anyone willing to open an attachment. Mass exploitation with commodity malware is their model—volume over precision.
Carpathian, another mentioned threat group, operates in the cybercrime space and has been linked to ransomware distribution, credential theft, and botnet operations.
Why WinRAR? Why Now? Understanding the Attack Surface
The Installed Base Problem
WinRAR has been around since 1995. It's installed on an estimated 500 million computers worldwide. Not every Windows machine has it, but enough do that the attack surface is enormous.
Many corporate environments have WinRAR pre-installed or allow users to install it. System administrators might not have comprehensive tracking of which machines have it. Users installed it years ago and forget it's there.
For attackers, that's ideal. You're targeting a tool that:
- Millions of people trust
- Has been around forever (people don't suspect it)
- Isn't always centrally managed
- Processes files automatically without obvious warnings
The RAR Archive Format Itself
RAR files are still commonly used, especially for large files, multi-part archives, and legacy systems. ZIP became standard for modern Windows, but RAR persists in certain circles: software distribution, archive preservation, and older workflows.
An attacker sending malicious RAR files blends better than sending EXE files directly. A RAR attachment with a PDF inside is less suspicious than an executable.
Compound This With Email Delivery
Email security has improved, but it's not perfect. Advanced email gateways can detect known malware signatures, but a brand-new exploit weaponization bypasses those signatures entirely. Email is still one of the most effective attack vectors because of human factors: urgency, authority, relevance.
A phishing email claiming to be an invoice, security update, or official notice works because the decoy document inside looks legitimate. By the time email security catches the broader campaign pattern, thousands of people might already be infected.
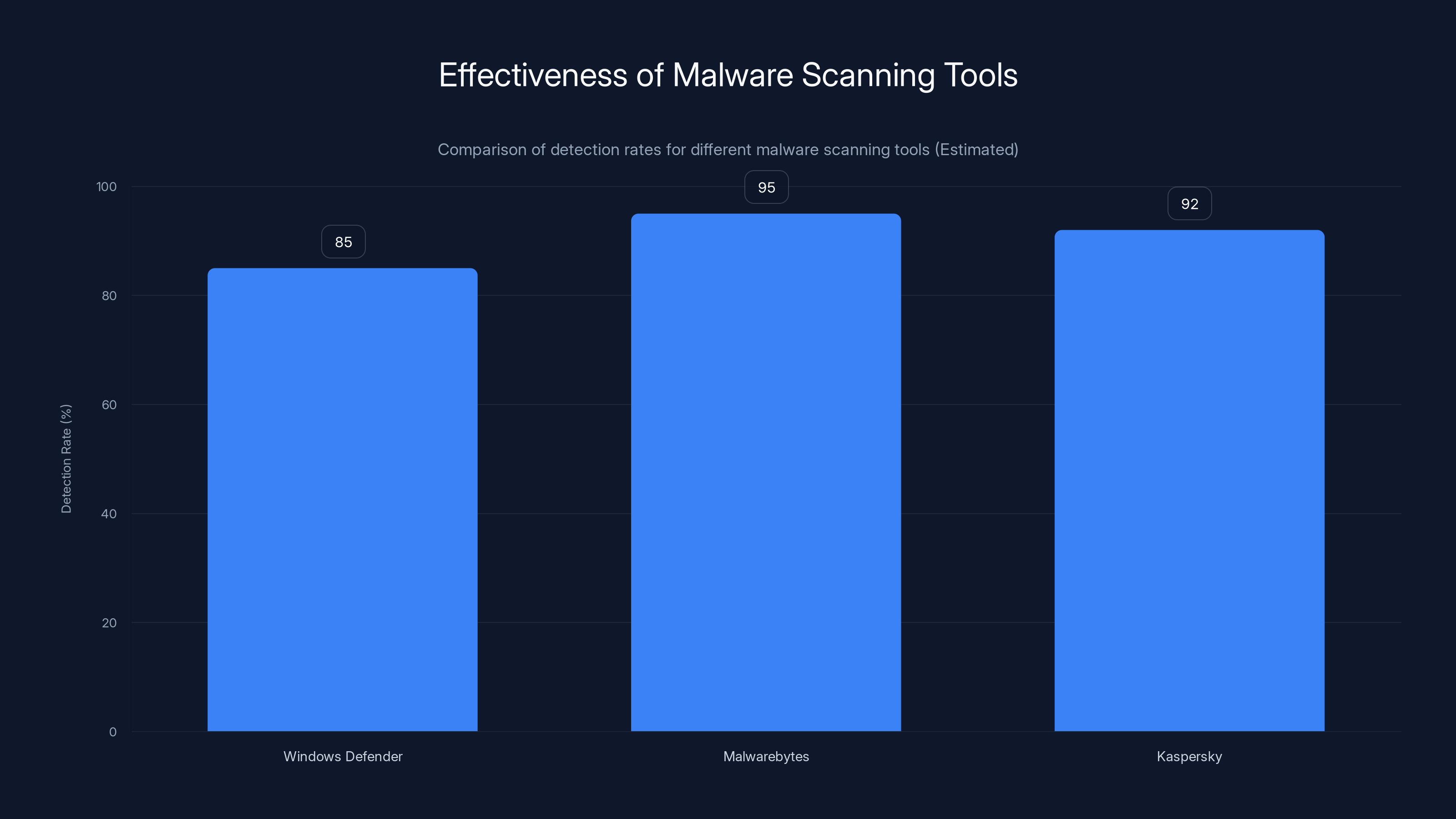
Malwarebytes shows the highest estimated detection rate at 95%, followed by Kaspersky at 92%, and Windows Defender at 85%. Estimated data based on typical performance reviews.
The Broader Implications: What This Reveals About Supply Chain Risk
One Tool, Multiple Attack Vectors
WinRAR wasn't a zero-day for long. Once the initial vulnerability was discovered, multiple threat groups found ways to weaponize it independently. This pattern repeats across the threat landscape:
- A vulnerability is discovered in widely-deployed software
- Nation-states find it and exploit it quietly
- Criminal groups notice and adapt it
- Within weeks, there are dozens of variants in active use
The vulnerability window isn't measured in days anymore—it's sometimes weeks or months between discovery and public patching, with attackers operating in that gap.
Software We Depend On, Software We Don't Update
WinRAR doesn't auto-update. This is intentional—the developers want users to control when updates happen. But human nature means many people never update anything unless forced to do so.
Research suggests that 30-40% of enterprise Windows machines are running software versions more than 2 years old. For consumer machines, the number is higher. Patch deployment is a distributed, messy problem.
Asymmetric Advantage
Attackers only need to find one vulnerability. Defenders need to patch every one. Attackers can target outdated software on machines you might forget about. One old WinRAR installation on one employee's machine can compromise an entire network.
This is the fundamental asymmetry: the attacker's job is reconnaissance and patience. The defender's job is perfection at scale.
Immediate Actions: How to Protect Yourself
Step 1: Update WinRAR Immediately
Update to version 7.13 or newer. This is non-negotiable. WinRAR doesn't require an uninstall before updating—the new version installs over the old one.
To check your current version:
- Open WinRAR
- Click Help → About WinRAR
- Look for the version number
If you're on 7.12 or older, update now. The fix is straightforward.
Download the latest version from the official WinRAR website.
Step 2: Verify the Download Source
Only download from the official WinRAR website or your organization's approved software repository. Don't use third-party download sites—they might host infected versions.
Once downloaded, verify the file checksum if you're paranoid:
- Get the official SHA256 hash from the WinRAR download page
- In Power Shell, run:
Get-File Hash -Path "C:\path\to\WinRAR.exe" -Algorithm SHA256 - Compare the output to the official value
If they match, the file is legitimate.
Step 3: Scan Your System for Malware
If you've been running vulnerable WinRAR and opening untrusted RAR files, your system might already be infected. Run a full malware scan:
- Windows Defender Offline Scan (built into Windows)
- Malwarebytes Premium (third-party, reputable)
- Kaspersky Rescue Disk (for serious infections)
Don't rely on a single scan. Run multiple tools—malware detection isn't 100% consistent across vendors.
Step 4: Monitor for Suspicious Activity
After patching and scanning, watch for signs of compromise:
- Unexpected network traffic (check Task Manager → Performance → Open Resource Monitor)
- New user accounts (Control Panel → User Accounts)
- Unexpected scheduled tasks (Task Scheduler → Task Scheduler Library)
- Unusual processes running (Task Manager → Details tab)
If you find anything suspicious, consider this a serious breach and involve your IT department or a cybersecurity firm.
Step 5: Educate Your Users or Family
If you manage IT or have family who uses computers, explain the risk:
- Don't open RAR files from unknown sources
- Verify sender identity before opening attachments
- Keep software updated
- Use email cautiously
One infected machine can compromise an entire network. Prevention is vastly easier than remediation.

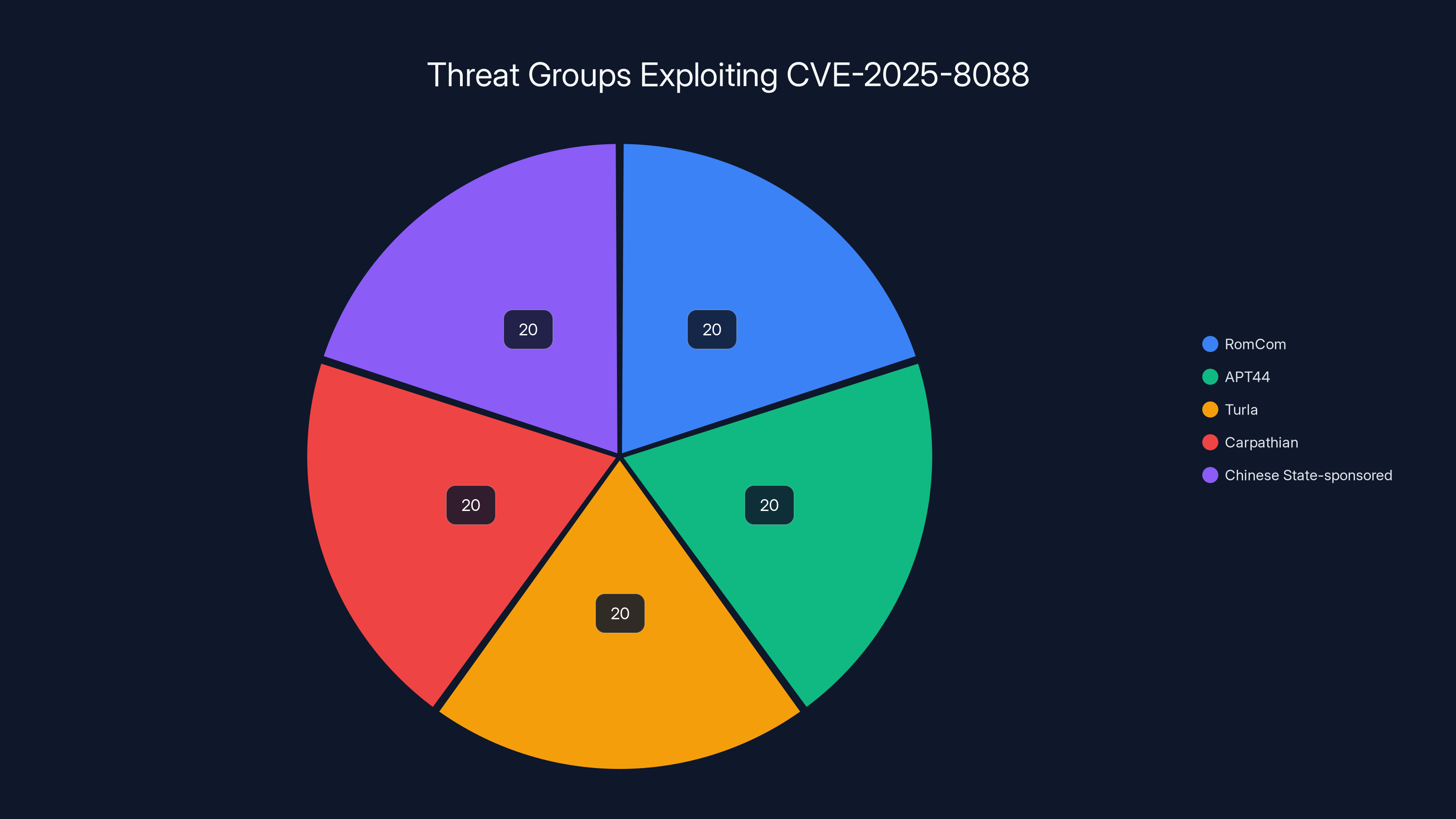
The pie chart shows an equal distribution among the six major threat groups exploiting CVE-2025-8088, indicating diverse actor involvement. Estimated data.
Enterprise Considerations: Managing Risk at Scale
Patching Strategy
For organizations, CVE-2025-8088 requires prioritized patching:
- Inventory: Scan your network for WinRAR installations. Many corporate environments have it on machines nobody tracks.
- Prioritize: Machines with high-value data or network access get patched first.
- Test: Deploy to a test group before pushing organization-wide.
- Enforce: Set policies to prevent downgrade to vulnerable versions.
- Verify: Confirm patches are applied across your fleet.
Tools like Microsoft Endpoint Manager or Tanium can automate much of this.
Email Gateway Hardening
Configure email filters to:
- Block RAR file attachments (or at least flag them)
- Scan archives at the gateway for suspicious content
- Implement DMARC/SPF/DKIM to prevent spoofing
- Require user authentication for external attachments
No single control catches everything, but layered defenses reduce risk.
Endpoint Detection and Response (EDR)
Deploy EDR tools that monitor suspicious behavior:
- Process execution from unusual locations
- Registry modifications linked to persistence
- Network connections to known command and control servers
- Credential access attempts
Microsoft Defender for Endpoint, CrowdStrike Falcon, and VMware Carbon Black are industry-leading options.
EDR might not prevent the initial infection, but it can catch it before attackers achieve their objectives.
Incident Response Planning
Assume you will get infected at some point. Have a plan:
- Detection: Alerting mechanisms for suspicious activity
- Containment: Isolating affected machines from the network
- Eradication: Removing malware completely
- Recovery: Restoring systems from clean backups
- Communication: Notifying relevant stakeholders
A documented incident response plan dramatically reduces the damage from successful attacks.

Alternative Tools: Should You Replace WinRAR?
7-Zip: Open Source and Free
7-Zip is an open-source compression tool that handles RAR, ZIP, 7z, and other formats. It's free, has no ads, and the source code is publicly auditable.
Pros:
- Free and open source
- Excellent compression ratios
- Handles modern and legacy formats
- No update nags or licensing questions
Cons:
- UI isn't as polished as WinRAR
- Smaller development team means slower vulnerability fixes
- Less corporate polish
Windows Built-In ZIP Support
Windows 10 and 11 have built-in ZIP compression and extraction. For most users, this handles 90% of use cases. You don't need third-party tools if you're only working with ZIP files.
Pros:
- Already installed
- No security maintenance burden
- Simple and reliable
Cons:
- ZIP only (not RAR, 7z, etc.)
- Limited compression options
- Can't create archives with advanced features
PeaZip: Feature-Rich and Lightweight
PeaZip is another open-source option with a more intuitive interface than 7-Zip. It supports RAR, ZIP, 7z, ISO, and dozens of other formats.
Pros:
- Open source and free
- Clean, intuitive interface
- Excellent format support
- Active development
Cons:
- Less known than 7-Zip or WinRAR
- Smaller user base
- Less corporate adoption
WinZip: Commercial Alternative
WinZip is the commercial alternative to WinRAR. Similar capabilities, different pricing model.
Pros:
- Well-established company
- Supports RAR and other formats
- Active security updates
- Cloud integration options
Cons:
- Not free (49.95 lifetime)
- Less popular than WinRAR in some regions
- Proprietary source code
My recommendation? If you only work with ZIP files, use Windows' built-in support or 7-Zip. If you need RAR support, upgrade to WinRAR 7.13+. The patch is simple and WinRAR is still solid software. Switching tools entirely is unnecessary if you patch promptly.
The Bigger Picture: What CVE-2025-8088 Tells Us About Cybersecurity in 2025
Zero-Day Exploitation Is Now the Norm
WinRAR's vulnerability was exploited by at least six threat groups before public disclosure. This isn't exceptional anymore—it's standard practice. Nation-states maintain portfolios of zero-days, criminal groups buy them, and vulnerability brokers profit from the market.
The implication: patching after a vulnerability is disclosed is often too late. By the time you see a CVE, attackers have already moved through thousands of networks.
Supply Chain Attacks Multiply the Impact
WinRAR is a supply chain component. It's not your primary business application—it's a tool your employees use to work with files. Attacking it is like attacking the pipes in a building instead of the doors. It's indirect, but it works.
Expect more attacks targeting widely-deployed, trusted utilities. The ROI is enormous—one vulnerability affects millions of machines.
Patching at Scale Is Still Broken
For all our advances in patch management, millions of people still run vulnerable software. Patch management is process-intensive, requires testing, and people procrastinate.
We need:
- Better automated patching with fewer reboots
- Software that updates securely by default
- Better visibility into what's installed where
- Risk-based patch prioritization
The Human Element Remains the Weakness
CVE-2025-8088 works because users open files they receive. Better security literacy helps, but not everyone will remember to be suspicious of every attachment.
The most effective defense isn't perfect patching—it's defense in depth. Email filtering, endpoint detection, network segmentation, and incident response plans catch what patching misses.

Long-Term Risk Management: Beyond WinRAR
Build a Vulnerability Management Program
Don't wait for crises. Build a systematic approach to finding and fixing vulnerabilities:
- Asset inventory: Know what software you have and where
- Vulnerability scanning: Regularly scan for known vulnerabilities
- Risk prioritization: Focus on high-impact, easily-exploitable vulnerabilities first
- Patch management: Systematic testing and deployment
- Verification: Confirm patches are actually applied
Tools like Qualys and Tenable automate much of this.
Implement Least Privilege Access
Even if malware gets in, it shouldn't have unlimited permissions. Run as standard user, not admin. Use UAC (User Account Control) to restrict what applications can do.
If WinRAR extraction malware ran with limited privileges, it couldn't write to System 32. Simple containment strategy.
Maintain Offline Backups
When ransomware or destructive malware strikes (and it will), offline backups are your lifeline. Implement 3-2-1 backup strategy:
- 3 copies of data
- 2 different storage types
- 1 offsite copy
Test restores regularly. Backups that can't be restored are just digital theater.
Monitor the Threat Landscape
Subscribe to threat intelligence feeds, follow security researchers on social media, and read incident reports. Understanding what attackers are doing gives you strategic foresight.
CISA (Cybersecurity and Infrastructure Security Agency) publishes advisories on actively exploited vulnerabilities. Worth reviewing weekly.

FAQ
What exactly is CVE-2025-8088?
CVE-2025-8088 is a path traversal vulnerability in WinRAR versions 7.12 and older that allows attackers to write files to arbitrary locations on your system through malicious RAR archives. The flaw has a CVSS severity score of 8.4/10 (high severity) and has been actively exploited by nation-states and criminal groups since mid-July 2025.
How do attackers exploit this vulnerability?
Attackers create RAR archives containing a legitimate decoy document (like a PDF) and hidden malicious payloads in Alternate Data Streams (ADS). When a user opens the archive with vulnerable WinRAR, the path traversal flaw allows the hidden payloads to be extracted to system directories like Startup folders or System 32, where they execute without user knowledge or permission.
Which threat groups are currently exploiting this?
At least six major threat groups are confirmed to be exploiting CVE-2025-8088: Rom Com (Russian-aligned), APT44 (Russian state-sponsored), Turla (Russian state-sponsored), Carpathian (financially motivated), and multiple Chinese state-sponsored actors. They're deploying malware including NESTPACKER, POISONIVY, XWorm, and Async RAT.
Do I need to uninstall WinRAR to update?
No. WinRAR version 7.13 and newer can be installed directly over the existing vulnerable version without uninstalling first. Simply download and run the installer for version 7.13 or later from the official website.
What should I do if I've opened RAR files from unknown sources?
Immediate steps: (1) Update WinRAR to 7.13+, (2) Run a full system malware scan using Windows Defender Offline and Malwarebytes Premium, (3) Monitor your system for suspicious processes and network activity, (4) Change passwords for critical accounts (email, banking, etc.) from a clean device, (5) Consider professional incident response if you find signs of infection.
Is WinRAR still safe to use after patching?
Yes. WinRAR is safe after updating to version 7.13 or newer. The vulnerability is fixed. However, always practice caution when opening attachments from unknown sources, maintain updated security software, and keep Windows patches current as additional defense layers.
Should I switch to a different compression tool?
Not necessarily. Patching WinRAR is sufficient. However, if you prefer alternatives, 7-Zip and PeaZip are open-source options, Windows has built-in ZIP support, and WinZip is a commercial alternative. The choice depends on whether you need RAR support and your preference for open-source versus commercial software.
Can my antivirus software detect and block this exploit?
Once malware is deployed, modern antivirus and EDR solutions can detect it. However, novel or customized variants might evade detection. This is why multiple layers of defense matter: email filtering, behavior monitoring, access controls, and backups work together. Never rely on a single security tool.
What about enterprise environments with centralized software management?
Organizations should: (1) Inventory all machines with WinRAR installed, (2) Prioritize patching systems with sensitive data or network access, (3) Test updates in a test environment first, (4) Deploy via Group Policy or centralized update management, (5) Monitor compliance to ensure patches are applied, (6) Consider blocking RAR attachments in email gateways as additional protection.
Is this vulnerability exploitable remotely or only locally?
This vulnerability requires user interaction—the victim must open a malicious RAR file. So it's not remotely exploitable in the sense of being weaponizable without any user action. However, social engineering makes this practical. An email with a carefully crafted RAR attachment and convincing pretext is highly effective.
What's the difference between a path traversal and other vulnerability types?
Path traversal vulnerabilities specifically allow attackers to access files or directories outside the intended scope. Other vulnerability types might allow remote code execution directly, SQL injection, or privilege escalation. Path traversal is powerful because it works in combination with other features—in WinRAR's case, combining with ADS functionality creates a weaponizable exploit.

Conclusion: Staying Ahead of the Threat Curve
CVE-2025-8088 is serious, but it's manageable. The patch exists. The fix is simple. The guidance is clear.
What makes this vulnerability noteworthy isn't the technical details—it's what it represents. We live in an era where widely-trusted tools become attack vectors, where nation-states and criminals weaponize the same flaws, and where patching at scale remains our most imperfect defense.
The immediate action is straightforward: update WinRAR to version 7.13. Don't procrastinate. That one action eliminates your vulnerability to this specific attack.
But zoom out further, and the lesson is broader. Security isn't about perfect tools or perfect patching. It's about layered defenses, understanding your risk, and building processes that handle inevitable breaches.
Update your software. Keep your backups current. Monitor suspicious activity. Educate your team. Maintain visibility into what's installed and running on your systems.
Threat groups are sophisticated and well-funded. But they're also predictable. They look for the easiest paths. Make yourself a harder target, and they'll move on to someone else.
WinRAR got patched. That's how this particular story ends. But more vulnerabilities are coming. More exploits will be found. The cycle continues.
Your job is to stay ahead of it.

Recommended Next Steps
For Individual Users:
- Check your WinRAR version right now (Help > About)
- Visit rarlab.com and download version 7.13 or newer
- Install the update (no uninstall needed)
- Run a full system malware scan this week
- Add a reminder to check for software updates monthly
For IT Administrators:
- Scan your network for WinRAR installations
- Prioritize patching based on system criticality
- Deploy through your centralized update management
- Consider blocking RAR attachments in email gateways
- Add CVE-2025-8088 to your incident response playbooks
For Security Teams:
- Review EDR logs for signs of WinRAR exploitation
- Update detection rules for NESTPACKER, POISONIVY, XWorm, and Async RAT
- Strengthen email gateway filtering
- Conduct security awareness training on attachment risks
- Develop a formal vulnerability management program if you don't have one
The threat is real. But so is the solution. Act on it.
Key Takeaways
- CVE-2025-8088 is a high-severity path traversal vulnerability in WinRAR 7.12 and older with a CVSS score of 8.4/10
- Nation-states (RomCom, APT44, Turla) and Chinese government actors are actively exploiting this to deploy NESTPACKER, POISONIVY, and other malware
- Attackers hide malware in Alternate Data Streams within RAR archives, using path traversal to extract to system directories like Startup folders
- Update to WinRAR 7.13 or newer immediately—no uninstall required, installation happens over the existing version
- Run full malware scans with multiple tools (Windows Defender Offline + Malwarebytes Premium) to detect potential compromise
- Enterprise defenses should include email gateway RAR filtering, EDR deployment, systematic patch management, and regular backup testing
- This vulnerability represents broader cybersecurity challenges: zero-day exploitation windows, supply chain attack vectors, and imperfect patching at scale
Related Articles
- Browser-Based Attacks Hit 95% of Enterprises [2025]
- OpenAI Scam Emails & Vishing Attacks: How to Protect Your Business [2025]
- Okta SSO Under Attack: Scattered LAPSUS$ Hunters Target 100+ Firms [2025]
- SMS Sign-In Security Flaws: The Hidden Risk Exposing Millions [2025]
- Microsoft Office CVE-2026-21509 Security Flaw: What You Need to Know [2025]
- 800,000 Telnet Servers Exposed: Complete Security Guide [2025]
![WinRAR Security Flaw CVE-2025-8088: Complete Defense Guide [2025]](https://tryrunable.com/blog/winrar-security-flaw-cve-2025-8088-complete-defense-guide-20/image-1-1769629036695.jpg)



