Windows 10 Secure Boot Certificates Are Expiring: Here's What Actually Happens
Last week, Microsoft dropped a quiet but significant announcement that caught a lot of people off guard. The company is rolling out updated Secure Boot certificates across millions of devices worldwide. Sounds technical and boring, right? But here's the thing: if you're still running Windows 10 without paying for Extended Security Updates (ESU), your machine is about to enter what Microsoft calls a "degraded security state."
I get it. Most people don't think about Secure Boot certificates until something breaks. You turn on your computer, Windows loads, life goes on. But this update changes that equation, especially for Windows 10 users who've been holding out on upgrading to Windows 11.
The certificates that have protected your system for the past 15 years are about to expire. Microsoft isn't waiting for them to fail catastrophically. Instead, the company is proactively pushing out new certificates to devices running Windows 11 and newer. Windows 10? That's where things get complicated.
Here's what's happening: devices that don't receive the new certificates will gradually lose boot-level protections. Your PC will still technically work, but you're looking at increased exposure to threats that target the firmware layer. Plus, you might start seeing compatibility issues down the road as hardware and software vendors assume everyone has the new certificates.
The real tension here is obvious. Microsoft is using this certificate expiration as a gentle (and not-so-gentle) push to drive Windows 11 adoption. Windows 10 still commands roughly 36% of the market as of early 2025, which is frankly embarrassing for Microsoft given that the operating system reached end of life in October 2025. But the company can't just pull the plug overnight without facing massive pushback. So instead, they're letting security infrastructure slowly decay on older systems.
Let me walk you through what's actually happening, why it matters, and what your options really are.
TL; DR
- Secure Boot certificates expire after 15 years: Microsoft is replacing these certificates as the original batch reaches expiration
- Windows 10 users get limited support: Only devices with paid ESU subscriptions receive the new certificates; regular Windows 10 devices enter degraded security mode
- Boot-level protections diminish: Devices without updated certificates lose advanced firmware protections and face increased malware exposure
- Compatibility issues emerging: Hardware and software vendors increasingly assume new certificates, creating future incompatibilities for older systems
- It's a push toward Windows 11: This is arguably Microsoft's most elegant way yet of forcing upgrades without mandatory update policies

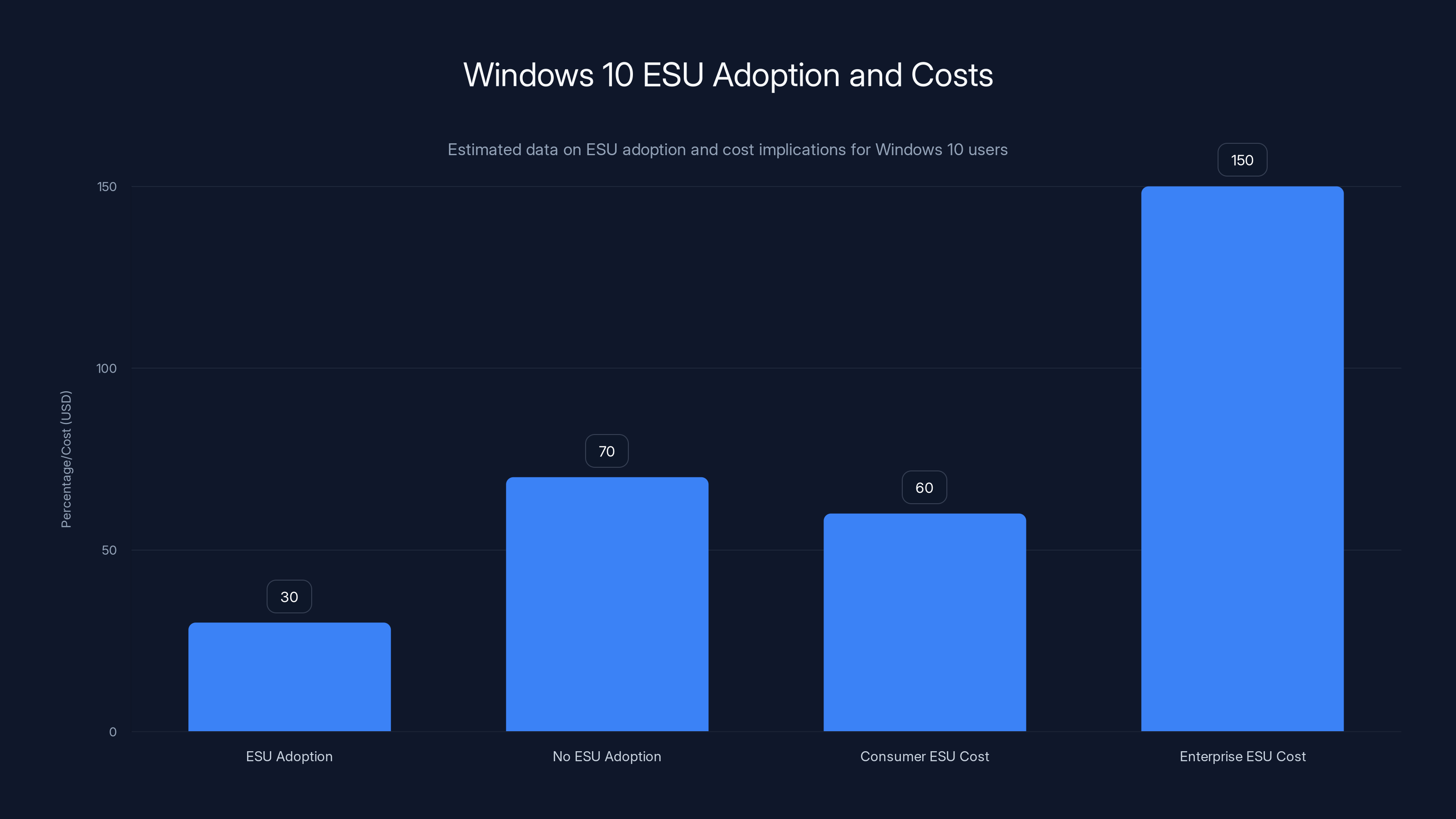
Estimated data suggests that 70% of Windows 10 users do not adopt ESU, facing security risks. ESU costs are approximately
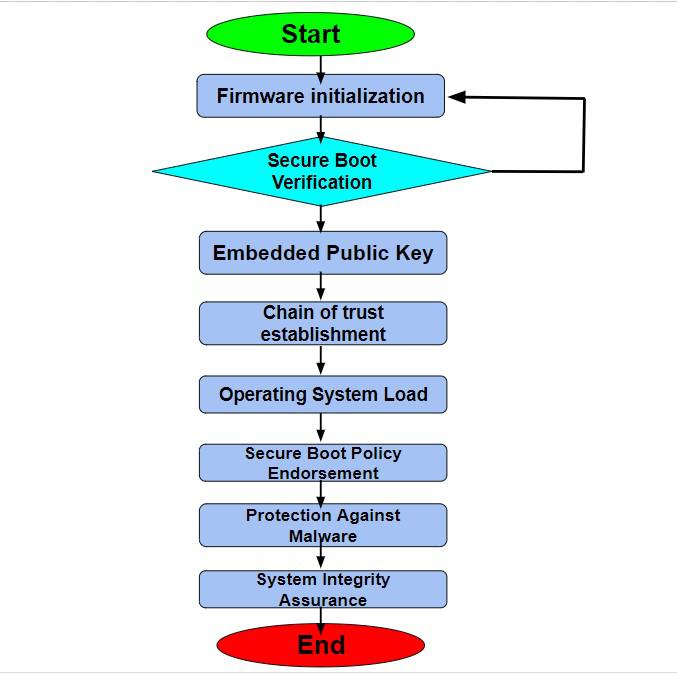
What Secure Boot Actually Does (And Why It Matters)
Secure Boot isn't new technology. It's been around since 2012, quietly running in the background on virtually every modern PC. But most people have no idea what it does or why it exists.
Here's the fundamental security problem Secure Boot solves: your computer starts up before Windows even loads. During those first few seconds, your system runs firmware code (UEFI or BIOS) that initializes hardware and loads the bootloader. If malware has infiltrated this early stage, it can do damage before your antivirus software even has a chance to scan.
Secure Boot works by cryptographically verifying that every piece of code running during boot is legitimate and hasn't been tampered with. Microsoft maintains a list of trusted certificate authorities, and during startup, your system checks that the bootloader was signed with one of these trusted certificates. If something doesn't match, the boot process halts before any malicious code can load.
Think of it like airport security. Your identity document (the certificate) gets verified before you're allowed past the gate (the bootloader). Without that verification, anyone could theoretically walk through.
The technical implementation uses public-key cryptography. Microsoft's private keys sign the bootloader code, and the public keys embedded in your UEFI firmware verify those signatures. This is mathematically secure as long as the keys themselves haven't been compromised and the signatures haven't aged beyond their validity window.
Why does this matter for the average user? Because Secure Boot is one of the primary defenses against a particularly nasty category of malware called bootkits. These are pieces of malicious code that infect your system at the firmware level, below the operating system. Once a bootkit gets in, it's nearly impossible to remove because it loads before Windows antivirus software can even start.
Rootkits and bootkits are rare but devastatingly effective. A bootkit can intercept all disk I/O operations, create hidden processes, and persist even if you completely wipe your hard drive. Secure Boot doesn't make bootkits impossible, but it makes them significantly harder. It raises the bar from something any script kiddie can deploy to something requiring genuine technical sophistication.
For enterprise environments, Secure Boot is essential. Financial institutions, government agencies, and Fortune 500 companies all rely on Secure Boot to protect systems handling sensitive data. The certificate expiration and replacement process is actually a big deal in those circles.
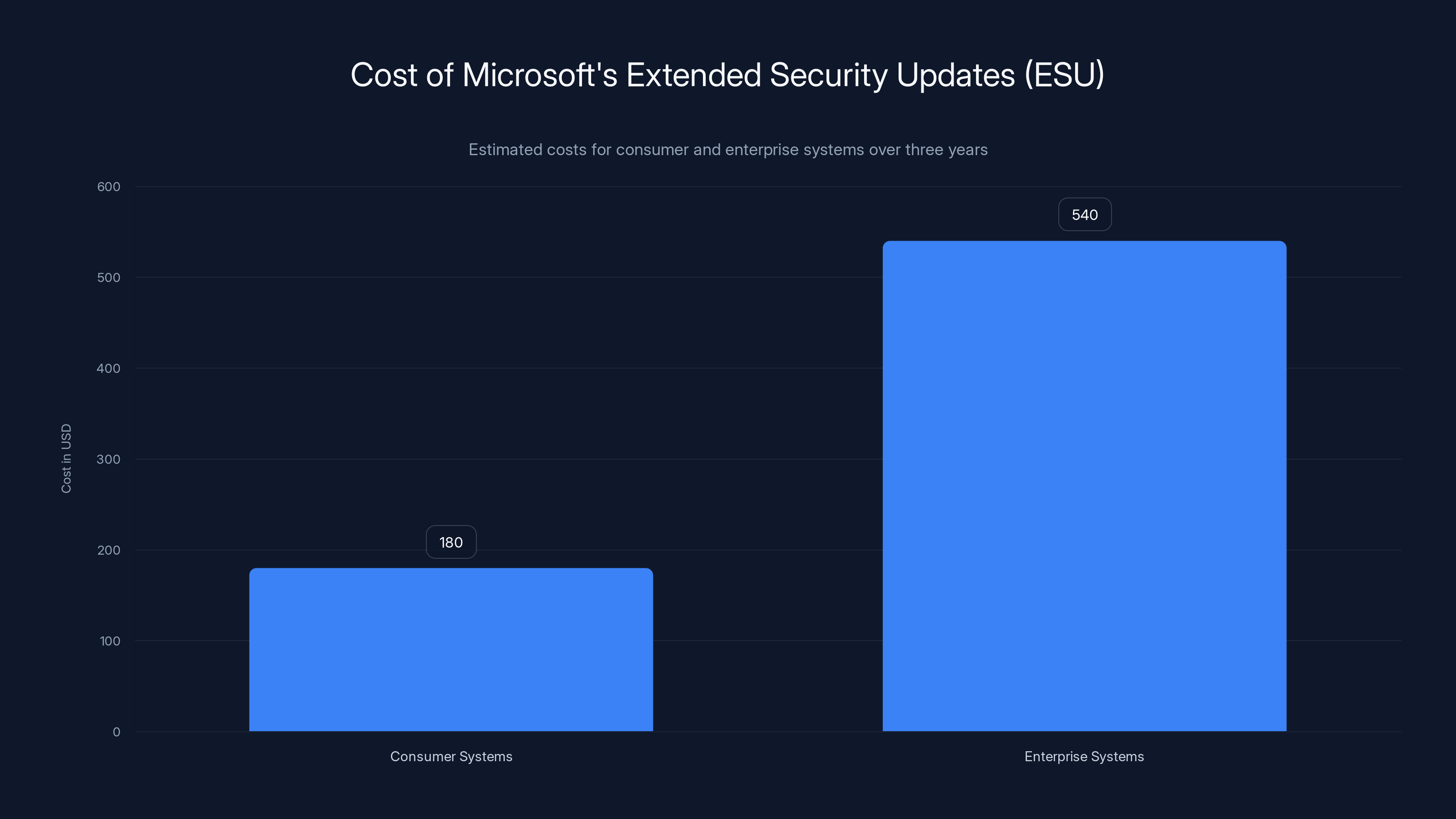
Estimated costs show that while consumers pay around $180 for three years of ESU, enterprise systems incur higher costs due to complex licensing (Estimated data).
The Original Certificates Are Aging Out
Secure Boot certificates, like all cryptographic certificates, have a lifespan. They're not valid forever. Microsoft issued the original set of Secure Boot certificates back around 2010-2011, as the technology was being formalized and implemented across the industry.
Those original certificates were issued with a 15-year validity window. If you do the math, that means they're expiring right around now in 2025. Microsoft saw this deadline coming years ago and started planning the replacement process.
Why 15 years? Mostly because in 2011, predicting technology needs beyond 15 years seemed unreasonable. Cryptographic standards evolve. Hardware changes. Threat landscapes shift. A 15-year window seemed reasonable for an infrastructure technology.
But here's where it gets interesting: Microsoft didn't just let the certificates expire silently. Instead, they did something unusual. They started provisioning new certificates years in advance, making sure the transition would be smooth. Starting with Windows 11 and certain supported builds of Windows 10, Microsoft began distributing the replacement certificates through monthly Windows updates.
The old certificates didn't disappear overnight. They're still valid. They'll continue to be valid for a while. But newer hardware is increasingly shipping with only the new certificates in their firmware. Some OEMs have even removed the old certificates from the UEFI firmware of new systems, betting that customers will be on updated operating systems by the time the old certificates actually expire.
This is where Windows 10 becomes a problem. Windows 10 officially reached end of support in October 2024, with extended support ending in October 2025. Devices running standard Windows 10 (without paid ESU subscriptions) stop receiving monthly updates. No monthly updates means no new certificate distribution. No new certificates means that when hardware vendors strip the old certificates from their firmware, Windows 10 systems without ESU subscriptions will no longer be able to boot properly on those systems.

Windows 10 Without ESU Gets Left Behind
Here's where Microsoft's strategy becomes clear, and honestly, a bit ruthless.
Windows 11 users automatically receive the new certificates as part of monthly updates. It's automatic, transparent, and users don't need to do anything. The transition is happening behind the scenes.
Windows 10 users have two paths:
Path 1: Extended Security Updates (ESU) If you've paid for ESU, your system continues receiving monthly updates, which means the new certificates get distributed. Your device stays fully secure and compatible. But ESU isn't cheap. For consumer systems, it's roughly $60 per year for three years. For enterprise systems, the pricing tiers are more complex, but you're looking at annual costs per device.
Path 2: No ESU If you haven't paid for ESU (and most people haven't), your Windows 10 system stops receiving updates once official support ends. New certificates never arrive. Eventually, as hardware vendors update their firmware and remove old certificates, your system will be unable to boot on newer hardware.
Microsoft describes this as entering a "degraded security state." That's actually a bit of an understatement. Here's what actually happens:
Devices that don't get the new certificates lose access to the latest root CA chains. They can no longer verify boot code signed with newer keys. This means new drivers, new firmware updates, and new hardware components might fail verification.
Boot-level protections erode. Your system becomes more vulnerable to firmware-level attacks because you're not validating against the latest threat intelligence and security standards.
Compatibility issues emerge. Gradually, hardware vendors update their firmware. New laptops and desktops ship with the new certificates only. If you try to run an old Windows 10 system without the new certificates on brand new hardware, you'll hit boot failures.
Is this an intentional pressure campaign to force Windows 11 adoption? Yeah, it absolutely is. Microsoft won't frame it that way, but that's what it is.
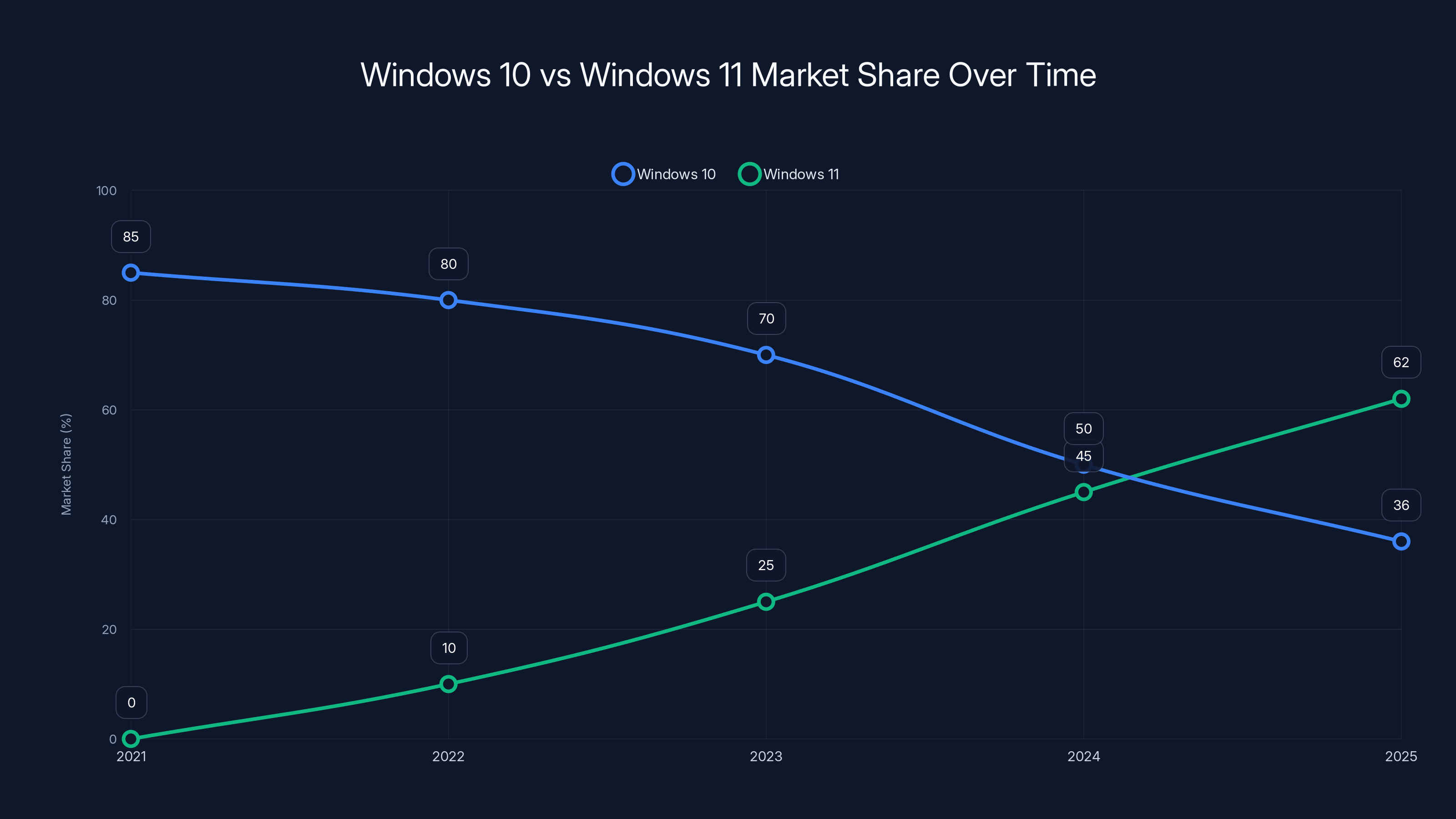
By mid-2025, Windows 11 surpassed Windows 10 with a 62% market share, driven by infrastructure changes like Secure Boot. Estimated data.
The Security Implications of Degraded Boot Protection
Let's talk about what "degraded security state" actually means in practice.
Secure Boot works by validating signatures on code that runs during the boot process. If a system doesn't have the latest certificates, it can't validate against the latest cryptographic standards or certificate chains. This creates a security gap.
Bootkits and firmware-level malware specifically target these gaps. They're designed to slip in below the operating system's security defenses. Once installed, they're nearly impossible to remove without specialized tools.
The threats are real, though still relatively uncommon. Equation Group, the NSA-linked hacking collective, famously used firmware-level exploits as part of their attack toolkit. Stuxnet, the famous worm that targeted Iranian nuclear facilities, included firmware-level components. More recently, the Hacking Team, a surveillance software company, developed tools that operated at the firmware level.
But here's the thing: you're not going to get hit by a Stuxnet-level attack just because your Windows 10 system doesn't have the latest Secure Boot certificates. These are nation-state and sophisticated criminal tools. The average person running Windows 10 without updated certificates faces a very low individual risk.
The aggregate risk is different, though. If millions of systems lack updated certificates, they become a more attractive target. Adversaries look at the attack surface and think, "That's a big pool of vulnerable systems. Worth developing an exploit for." From a security engineering perspective, having a large population of systems running with degraded protections is not ideal.
Pour yourself a coffee if you need one here, because I'm about to explain the cryptography.
Secure Boot uses PKCS#1 v 1.5 padding in the implementation details, though the high-level concept is straightforward. The signature verification algorithm has evolved. Older systems might not properly validate against newer certificate standards or longer key lengths. This becomes a problem as cryptographic standards evolve and older algorithms are deprecated.
Certificate pinning also comes into play. Systems are provisioned with a specific set of trusted root certificates. New threats and new attack vectors might require trust in additional certificate chains that older systems simply don't have.
For enterprise environments and government systems, this is genuinely concerning. A military contractor running Windows 10 without the latest certificates is running a system with known security gaps. Security compliance frameworks like Fed RAMP, NIST SP 800-53, and ISO 27001 all have requirements around firmware security and validated boot processes. Systems without updated certificates might fail compliance audits.
Hardware Compatibility Issues on the Horizon
Let's look forward a bit. What happens over the next 12-24 months?
Hardware manufacturers are gradually removing support for older cryptographic standards and older certificate chains. It's a gradual process, but it's happening. BIOS updates, UEFI firmware updates, and new hardware all assume that systems will have modern certificate support.
Laptop manufacturers like Dell, HP, and Lenovo have started testing new hardware against Windows 11 specifically. Some have even dropped official Windows 10 support. If you buy a brand new Think Pad or Elite Book in late 2025 or 2026, there's a decent chance it ships with firmware that only recognizes the new Secure Boot certificates.
Try installing Windows 10 on that hardware? Boot failure. The firmware won't recognize the old certificates and won't complete the boot sequence.
This isn't malicious per se, but it's strategic. Hardware manufacturers are using this certificate transition as a pivot point to deprecate Windows 10 support. It's the natural consequence of a certificate expiration meeting an operating system that's officially out of support.
Serverware is different. Enterprise servers running Windows Server 2019 (which is still supported through 2024) will continue receiving updates and new certificates. But consumer and commercial PC hardware is definitely moving toward Windows 11-only configurations.
Storage controllers, network drivers, and chipset firmware all might have their own firmware update processes that assume new certificates. If a firmware update fails verification because of outdated certificates, you could be looking at a bricked storage controller.
Is this dramatic? A bit. But it's also a realistic consequence of certificate deprecation on legacy operating systems.

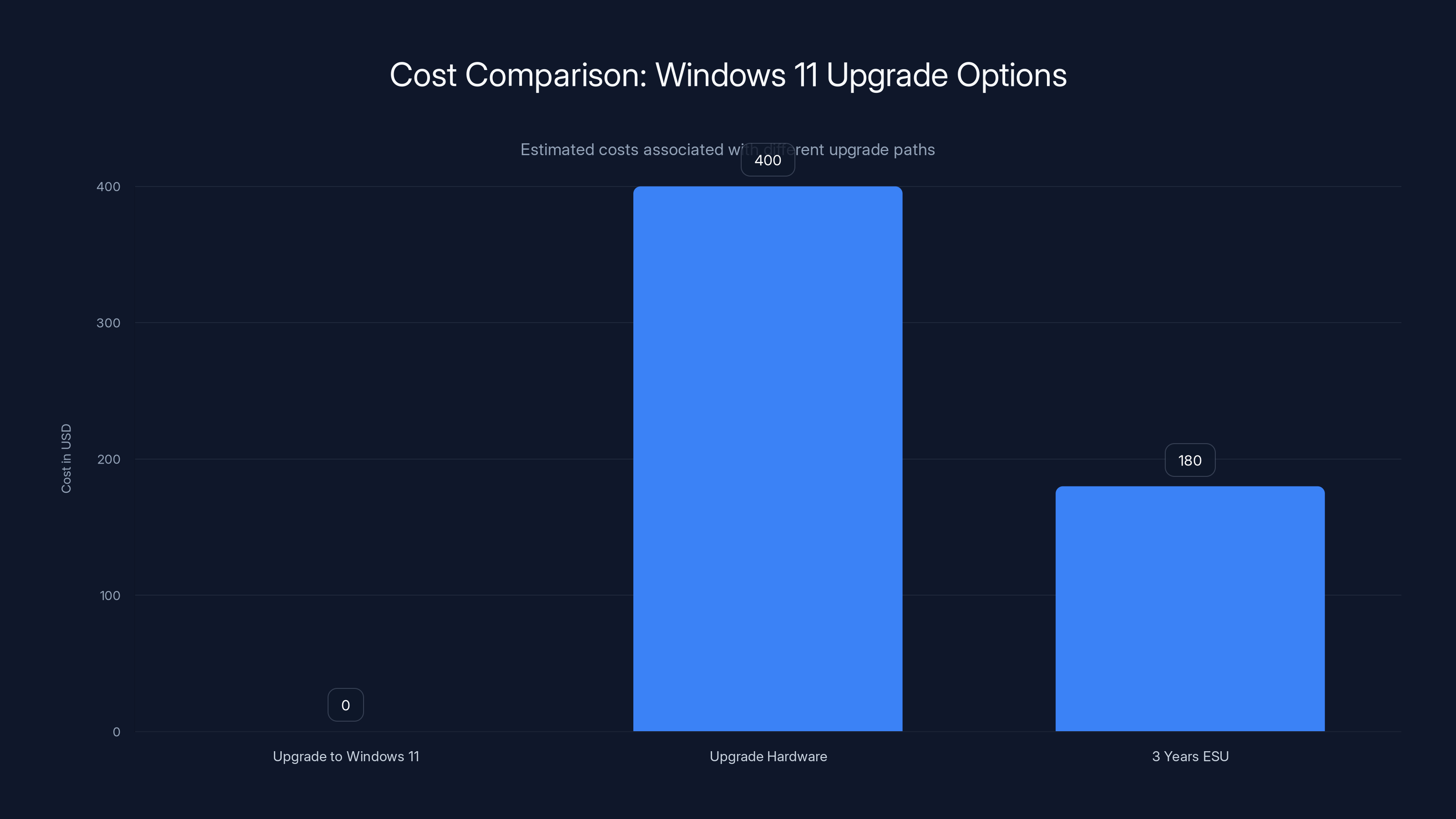
Upgrading to Windows 11 is cost-effective if hardware is compatible. Hardware upgrades average
Microsoft's Extended Security Updates (ESU): The Expensive Escape Hatch
If you really don't want to upgrade to Windows 11, Microsoft does provide an option: Extended Security Updates.
ESU is Microsoft's program for keeping older operating systems on life support beyond their official support end dates. For Windows 10, ESU is available for three years after mainstream support ends (so until October 2028, in theory).
Here's what ESU actually includes:
Security patches continue flowing. Every Patch Tuesday, systems with ESU subscriptions still receive critical security updates. That includes Secure Boot certificate distributions.
No feature updates. ESU doesn't include new features or functionality. You won't get new copilot integrations or UI improvements. Just security patches.
Gradual performance degradation. Patches for older operating systems increasingly target narrow security issues rather than performance. You might see edge cases where patches make things slightly slower as they add safety checks.
Pricing starts at around
Here's my honest take: ESU is Microsoft's way of saying, "You can delay upgrading to Windows 11 if you're willing to pay for it." For most people, that's not a compelling deal. You're paying money to not upgrade, rather than just biting the bullet and upgrading to Windows 11.
For enterprises with millions of devices, the math is different. Some organizations have justified the ESU cost for specific systems that can't migrate to Windows 11 due to legacy software or hardware incompatibilities. But for typical consumers and small businesses? It rarely makes financial sense.

Why Upgrading to Windows 11 Is Complicated
Now, you might be thinking: "Fine, I'll just upgrade to Windows 11. Problem solved."
Not so fast. The upgrade path is more complicated than most people realize.
Windows 11 has minimum hardware requirements that actually matter. You need a TPM 2.0 chip, UEFI firmware, Secure Boot support, and a compatible processor. Most systems from the last five years meet these requirements, but some don't.
If your system doesn't have a TPM 2.0 chip (common on business-grade laptops from 2019-2020), you're stuck. You can't upgrade. Well, you can use workarounds and registry edits, but those aren't supported configurations.
Second, there are legitimate software incompatibilities. Some enterprise applications haven't been updated for Windows 11. Some older hardware drivers never received Windows 11 versions. Organizations with legacy software can't just upgrade without testing extensively.
Third, there's the data migration piece. Upgrading an existing Windows 10 installation to Windows 11 works most of the time, but it's not risk-free. Some users encounter boot issues, driver problems, or application crashes after upgrading. A clean Windows 11 installation is more reliable but requires backing up data, wiping the drive, and reconfiguring everything.
For home users with simple setups? The upgrade is usually painless. For anyone with legacy software, special hardware configurations, or critical business systems? It's a much bigger undertaking.
So the realistic situation for a lot of Windows 10 users is: you can't upgrade because of hardware limitations, you won't upgrade because of software incompatibilities, or the upgrade process carries enough risk that you're hesitant to attempt it.
Microsoft's Secure Boot certificate expiration is basically a way of saying, "Okay, you've had five years. Time to move on." But it's doing so in a way that's frustrating for people with legitimate reasons to stay on Windows 10.
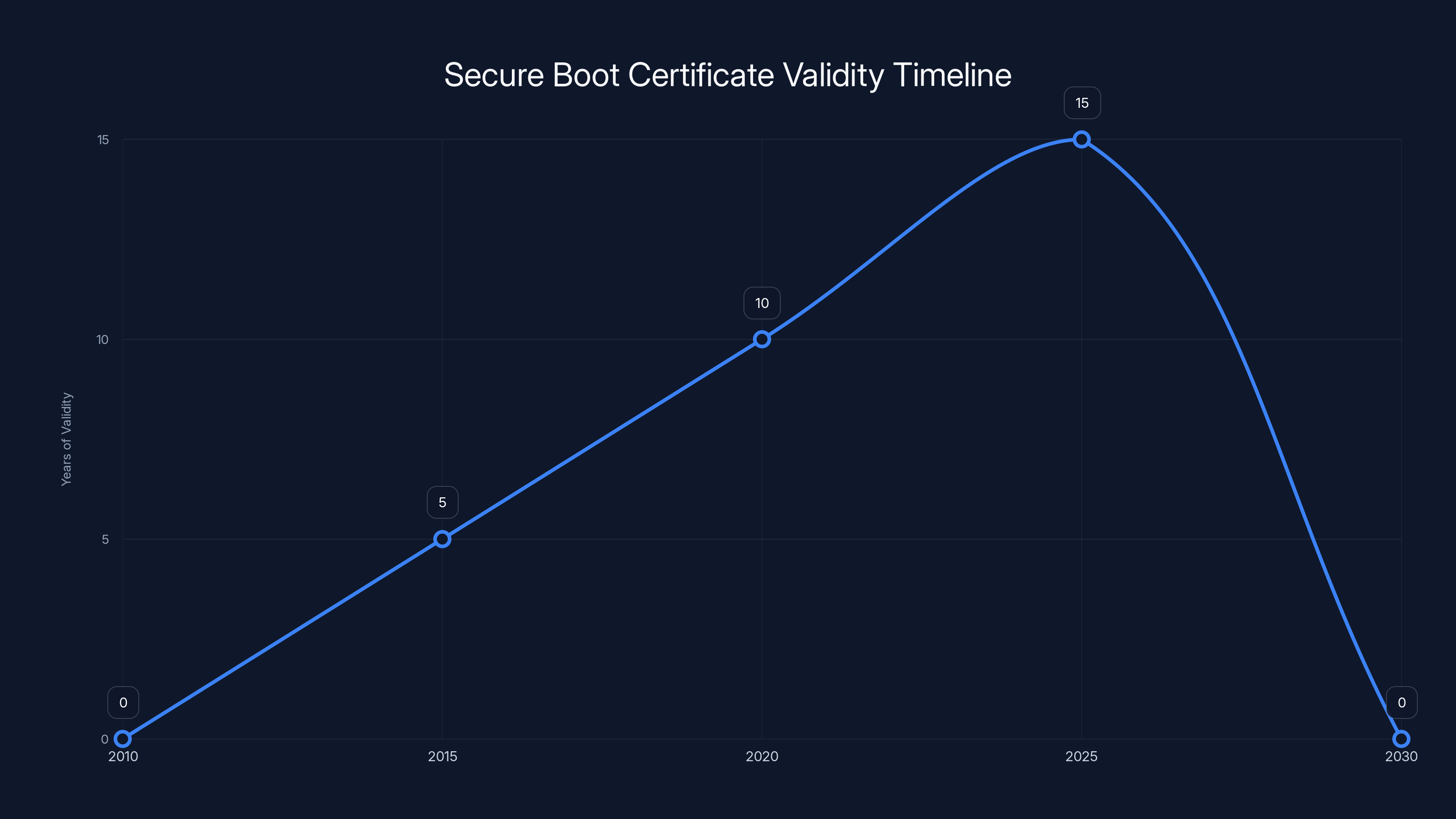
Secure Boot certificates issued in 2010-2011 have a 15-year validity, expiring in 2025. Estimated data.
The Enterprise Perspective: Compliance and Risk Management
If you're managing IT infrastructure for an organization, this certificate transition is a significant issue.
Compliance frameworks like PCI DSS, HIPAA, and SOC 2 all have requirements around secure boot configurations. An auditor reviewing your systems might flag Windows 10 machines without updated Secure Boot certificates as non-compliant.
Insurance policies also factor in. If your organization experiences a breach, insurers will examine your security controls. Systems running with degraded boot protection might result in denied claims or increased premiums.
Patch management becomes more complex. Enterprises have to decide: do we invest in ESU for thousands of devices, or do we accelerate Windows 11 migrations? The financial and operational implications are significant.
Virtualized environments add another layer. If you're running Windows 10 in virtual machines, the certificate issue is less critical since you control the virtual hardware. But physical device support is a real concern.
For healthcare organizations, government agencies, and financial institutions, the pressure to migrate away from Windows 10 is genuine. These sectors have the strictest compliance requirements and the highest costs associated with security failures.

Market Share Shifts: Windows 11 Finally Takes the Lead
Let's look at the actual adoption numbers.
For years, Windows 10 completely dominated. Even after Windows 11 launched in late 2021, adoption was glacial. People didn't see a compelling reason to upgrade, and hardware requirements created friction.
But by mid-2025, Windows 11 finally overtook Windows 10 in global market share. Windows 11 hit roughly 62% market share, while Windows 10 dropped to 36% as of January 2025. It took a while, but Microsoft's various upgrade pressures finally worked.
The Secure Boot certificate transition is interesting because it's one of the few technical reasons (rather than marketing reasons) that legitimately pushes people toward Windows 11.
Prior upgrade pressure mostly came from Microsoft's messaging and feature comparisons. "Windows 11 is faster." "Windows 11 has better AI features." Most people didn't care. Windows 10 was stable, functional, and familiar.
But Secure Boot certificate degradation is different. It's not marketing. It's infrastructure. You can't argue with it or ignore it forever. Eventually, hardware won't boot, drivers won't install, and functionality will degrade.
It's subtle pressure, but it's effective.
The geographic differences are interesting too. In developed markets with strong IT infrastructure (US, Western Europe, Australia), Windows 11 adoption is higher and Windows 10 adoption lower. In developing markets and regions with older hardware, Windows 10 is still dominant. That's because upgrading infrastructure costs money, and not every organization has it.
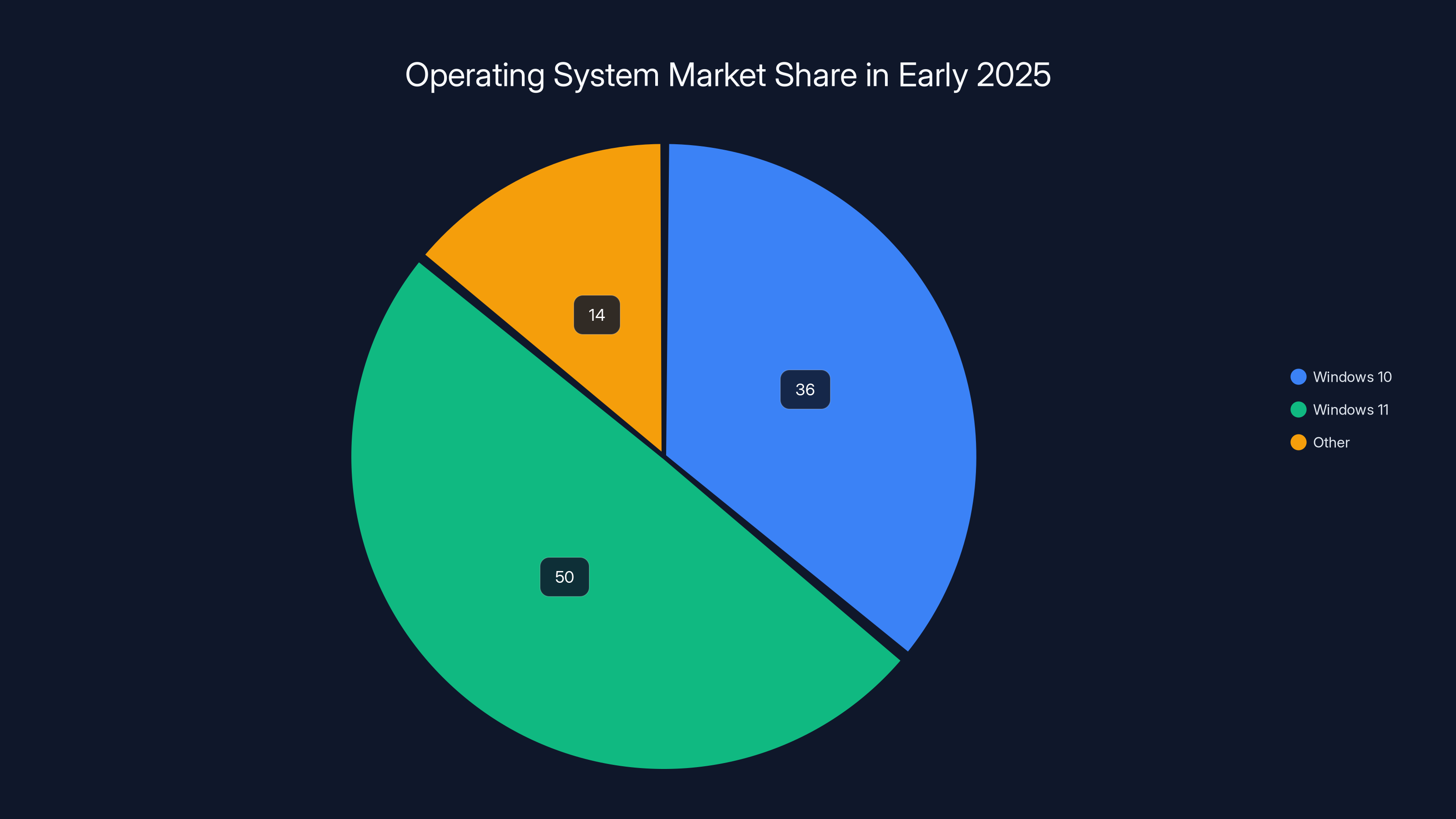
Windows 10 still holds a significant 36% market share in early 2025, despite Microsoft's push for Windows 11 adoption. Estimated data.
Security Risks If You Do Nothing
Let's be direct: what are the actual risks if you ignore this and keep running Windows 10 without upgrading?
Short-term (Next 12 months): Very minimal personal risk. If you're not a high-value target, you're unlikely to encounter firmware-level malware. Your system will continue to work normally. Antivirus and security software will still protect you at the OS level.
Medium-term (1-2 years): Compatibility issues emerge. New hardware might not boot with your system. Firmware updates might fail. You might not be able to connect certain devices due to driver incompatibilities.
Long-term (2+ years): Boot-level protections effectively disappear as support infrastructure erodes. Your system becomes increasingly isolated from the modern hardware and software ecosystem. Eventually, you'll face a forced migration.
Is this catastrophic? Not immediately. But it's death by a thousand cuts. Each firmware update, each driver incompatibility, each new requirement chips away at your system's viability.
For most people, the migration path to Windows 11 is simpler and faster than dealing with years of degradation.

What Should You Actually Do?
Here's my practical recommendation:
If your hardware is compatible with Windows 11: Just upgrade. Yes, there's risk in the migration process, but it's lower than the risk of running an unsupported operating system with degraded boot protections for years. Plan the upgrade for a day when you can back everything up. Run the upgrade. If something breaks, you have your backup.
For most people with reasonably recent systems (2018 or later), Windows 11 compatibility shouldn't be an issue.
If your hardware isn't compatible: You have a few options. First, check whether you actually have a blocker or whether you're just perceiving one. TPM 2.0 is more common than people realize. Second, consider upgrading your hardware rather than paying three years of ESU. A budget laptop costs
If you're running legacy software that won't work on Windows 11: This is the legitimate scenario. Test thoroughly. Check compatibility. See if vendors have released Windows 11 versions. If not, you're in a tough spot. ESU becomes a more defensible choice, but consider whether you really need to keep running that software. Can it be replaced? Can it run in a virtual machine? Are there cloud-based alternatives?
If you're an IT administrator: Start planning now. Do an inventory of systems and their Windows 11 compatibility. Identify hardware that needs replacing. Test your critical applications on Windows 11 in a lab. Create a migration timeline. Don't wait until boot failures force you to migrate under pressure.

The Bigger Picture: Infrastructure Lifecycle Management
Zoom out for a moment. This certificate situation is a lens for understanding how technology infrastructure works.
Nothing lasts forever. Operating systems have lifecycles. Hardware becomes obsolete. Standards evolve. Security threats change. The companies maintaining these systems have to make decisions about when to deprecate old technologies and push adoption of new ones.
Microsoft's approach with Windows 10 is actually pretty reasonable. They didn't just turn off Windows 10 overnight. They gave users 15 years of Secure Boot protection. They gave consumers until 2025 to migrate. They offered ESU for those who needed more time.
Could they have handled this better? Sure. They could have made Windows 11 hardware requirements less restrictive. They could have offered cheaper upgrade paths. They could have been more transparent about the certificate expiration timeline.
But the core principle is sound: old infrastructure eventually has to be retired and replaced.
This is true for everything. Your router. Your phone. Your car. Your house's electrical wiring. Everything has a lifecycle. The question is whether you manage that lifecycle proactively or reactively.
For Windows 10 users, the time for proactive management is now. The certificate expiration gives you a concrete deadline. Use it to plan your upgrade strategy rather than waiting for failures to force your hand.

Looking Forward: What Windows 11 and Beyond Need to Address
The Windows 10 certificate situation reveals some legitimate friction in how Microsoft manages upgrade transitions.
For Windows 11 and whatever comes next, there are lessons:
Hardware requirement flexibility: The TPM 2.0 requirement for Windows 11 blocks upgrades on systems that are otherwise perfectly capable. Microsoft could make this requirement less strict without compromising security.
Clearer communication: Most users don't understand why they can't upgrade. Microsoft could do better explaining hardware requirements and providing detailed compatibility checking tools.
Smoother upgrade paths: The in-place upgrade from Windows 10 to Windows 11 works most of the time, but the failure cases are painful. Better testing infrastructure and rollback capabilities would help.
ESU affordability: $60 per year for security updates is a decent price, but it's positioned more as a penalty for not upgrading than as a legitimate support option. More aggressive pricing could help organizations migrate gradually.
These are things we'll likely see Microsoft adjust over time. The company is generally responsive to feedback when enough customers complain.
The Reality Check
Here's what I think is actually true: Most people don't need to worry about this.
If you're running Windows 10 on a personal computer and you have no pressing need to upgrade, you'll probably be fine for another 12-18 months. Your system will continue to work. Antivirus will still function. Updates will still install (at least for a while).
Eventually, you'll hit compatibility issues or hardware limitations that force an upgrade. That timeline is probably 2-3 years out for most casual users.
But if you do upgrade now, you avoid that eventual pain. You get access to Windows 11's improvements. You're back on a supported, actively maintained operating system.
The certificate expiration is real, but it's not an immediate crisis. It's a clock ticking toward a deadline. Smart planning means beating that clock rather than racing it.
For organizations and businesses, the timeline is tighter. Compliance requirements, security audits, and data protection standards make the Windows 10 support gap more urgent. If you're running business systems on Windows 10, you should be planning your migration now.
But for home users? You've got time. Use it wisely.
FAQ
What exactly is Secure Boot and why does my computer need it?
Secure Boot is a firmware-level security feature that verifies the authenticity of code running during your computer's startup process. It uses digital certificates and cryptographic signatures to ensure that only legitimate, unmodified code can execute before Windows loads. This protects against bootkits and firmware-level malware that could otherwise hide below your antivirus software and persist indefinitely.
Why are Secure Boot certificates expiring now?
The original Secure Boot certificates were issued in 2010-2011 with a 15-year validity window. That lifespan is expiring now in 2025. Microsoft planned this transition years in advance, but the timing creates a challenge for older operating systems like Windows 10 that are no longer receiving regular updates.
Will my Windows 10 computer stop working if I don't update the certificates?
Not immediately. Your system will continue to function normally for the near-term. However, you'll enter a degraded security state where your system can no longer verify against the latest boot security standards. Over time, as hardware vendors update firmware and remove old certificate support, you may encounter boot failures and compatibility issues with new hardware.
Do I need to pay for Extended Security Updates to stay on Windows 10?
If you want to keep receiving Secure Boot certificate updates while staying on Windows 10, yes, you need an ESU subscription (roughly $60/year). Without ESU, your Windows 10 system stops receiving all updates and never gets the new certificates. However, for most users, upgrading to Windows 11 is more cost-effective than paying multiple years of ESU fees.
Can I upgrade to Windows 11 if my hardware is older?
It depends on your specific hardware. Windows 11 requires TPM 2.0, UEFI firmware, and a compatible processor. Most systems from 2018 onward meet these requirements. You can check compatibility by running Microsoft's PC Health Check tool. If your hardware doesn't meet requirements, you have limited upgrade options without ESU.
What happens to my data if I upgrade to Windows 11?
The in-place upgrade process (upgrading Windows 10 to Windows 11 directly) preserves your files and applications. However, there's always a small risk with any major operating system upgrade. I recommend backing up all your important data before upgrading, just in case something goes wrong. A complete backup ensures you can recover if the upgrade encounters issues.
Is Windows 10 really unsafe to use after the certificates expire?
Not in the immediate sense. Windows Defender and third-party antivirus will still protect you from most threats at the operating system level. The risk is specifically at the firmware level, where bootkits and advanced malware operate. For most users, this is a theoretical risk. However, for systems handling sensitive data or in regulated industries, the degraded boot protection becomes a genuine compliance concern.
Can I still use Windows 10 after 2025 if I ignore this certificate issue?
Yes, but with caveats. Your system will continue to work, but functionality will gradually degrade as hardware and software vendors update their systems to assume new certificate support. New hardware might not boot with your system. Driver installation might fail. Eventually, you'll be forced to upgrade due to compatibility issues, not security requirements.
Key Takeaways and Next Steps
The Windows 10 Secure Boot certificate transition is happening whether you're paying attention or not. It's not a hack, not a conspiracy, just infrastructure reaching the end of its designed lifecycle.
Here's what you need to remember: Microsoft is proactively managing the replacement of security certificates that protect your computer's boot process. Windows 11 and newer systems get automatic updates with the new certificates. Windows 10 systems without paid subscriptions don't, gradually losing boot-level security protections.
For most people, this is a gentle nudge to finally upgrade from Windows 10 to Windows 11. That nudge will gradually become a shove over the next 12-24 months as hardware incompatibilities emerge.
The good news? Windows 11 is stable, functional, and increasingly mature as an operating system. The upgrade process is usually straightforward if your hardware supports it. Delaying the inevitable only extends the pain.
The best time to upgrade was three years ago when Windows 11 launched. The second best time is right now.
We are a team of technology professionals who test, analyze, and explain complex technical topics. If you need help understanding technical infrastructure changes or planning IT transitions, that's what we're here for. Clear information beats marketing spin every time.

Related Articles
- Windows Secure Boot Certificate Renewal Explained [2025]
- CISA End-of-Life Edge Device Replacement Guide [2025]
- Windows 11 Hits 1 Billion Users: What This Milestone Means [2025]
- Windows 11 Hits 1 Billion Users: The Surprising Truth Behind the Milestone [2025]
- Windows Server 2008 End of Support: Complete Migration Guide [2025]
- Windows 11 Printer Support: What Microsoft Actually Changed [2025]
![Windows 10 Secure Boot Certificates: What You Need to Know [2025]](https://tryrunable.com/blog/windows-10-secure-boot-certificates-what-you-need-to-know-20/image-1-1770831467696.jpg)



