Understanding Windows Secure Boot Certificate Renewal
Something quiet is happening across millions of Windows devices right now. Microsoft is silently rolling out new security certificates to replace ones that have been working since 2011. If you're not paying attention, this seems like just another Windows update. But if your device doesn't get these new certificates before the originals expire, you're looking at a potential security vulnerability that could lock you out of future Windows updates entirely.
Here's the thing: most Windows users have no idea their devices are running on security certificates that are about to expire. The original Secure Boot certificates from 2011 are set to reach the end of their lifespan between June 2026 and October 2026. That's not far off. Once they expire, systems won't just "upgrade" automatically. They'll enter what Microsoft calls a "degraded security state." What does that actually mean? Your PC will continue to function, sure. But you'll lose the ability to receive boot-level security updates, which are some of the most critical patches your system needs.
Microsoft's approach here is pragmatic. Rather than waiting for certificates to expire and dealing with millions of support tickets from confused users, they're proactively distributing new certificates through regular Windows updates. It's the kind of invisible infrastructure work that most people never notice, but it's exactly the kind of thing that keeps the entire Windows ecosystem running smoothly.
The certificate renewal process started in January 2025 with Windows 11 KB5074109 update. For most Windows 11 users, this means you've probably already received the new certificates without knowing it. But there's a catch: not everyone is on the same timeline. Older devices, servers, specialized hardware, and Windows 10 systems need additional steps. Understanding what's happening, why it matters, and what you need to do about it will keep your system secure and prevent future headaches.
TL; DR
- New Secure Boot certificates are rolling out now via Windows updates (KB5074109 and later) to replace 2011-era certificates expiring June-October 2026
- Most Windows 11 users get updates automatically with no action required, but older hardware may need manufacturer firmware updates
- Windows 10 users must enroll in Extended Security Updates (ESU) to receive new certificates, or they'll lose future boot-level security patches
- Expired certificates cause a degraded security state that prevents critical boot updates and may create hardware/software compatibility issues
- The bottom line: Check your device for successful certificate installation before mid-2026 to avoid losing security support
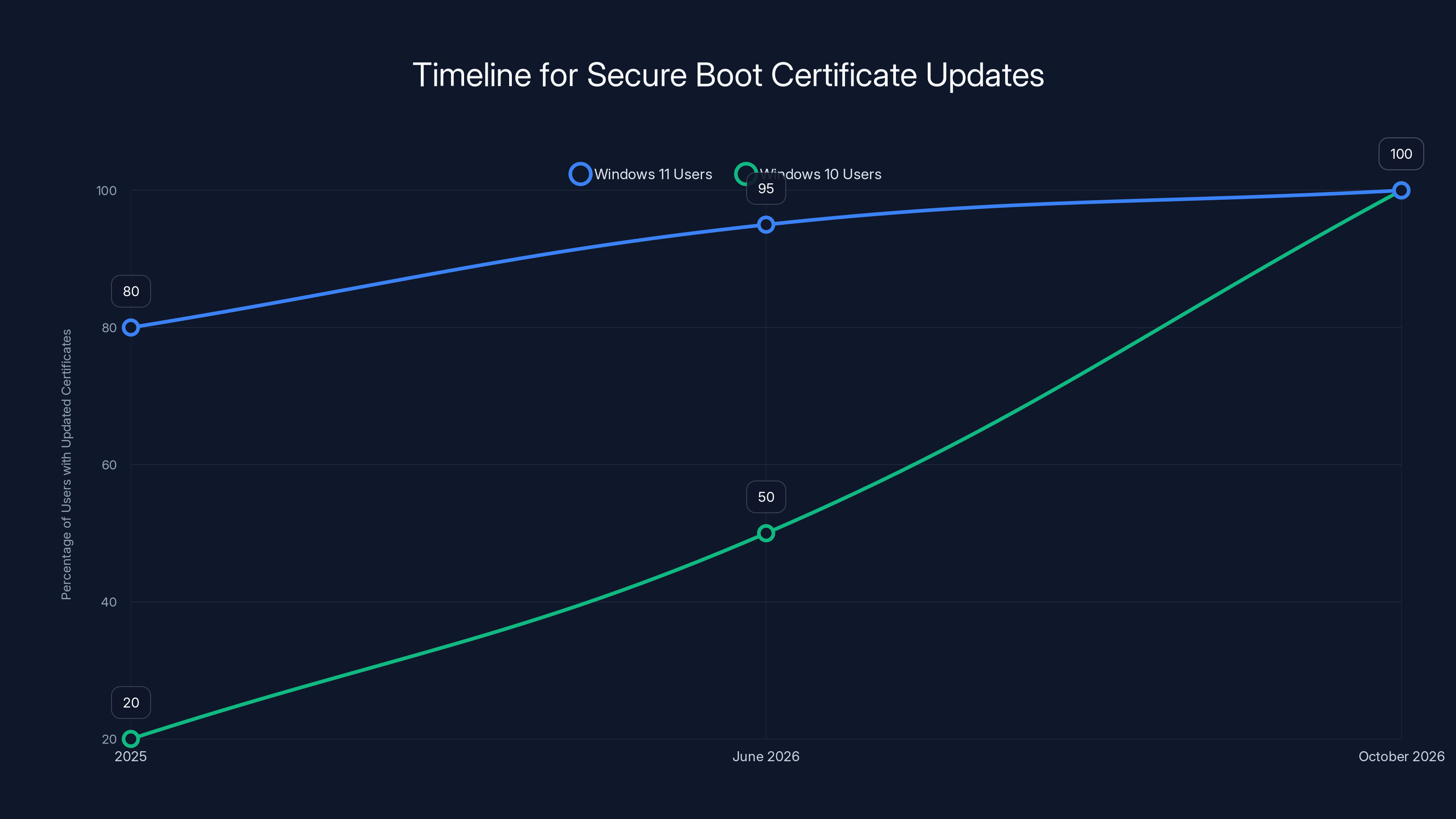
Estimated data shows that by October 2026, 100% of users should have updated Secure Boot certificates, with Windows 11 users likely updating earlier.
What Is Secure Boot and Why Does It Matter?
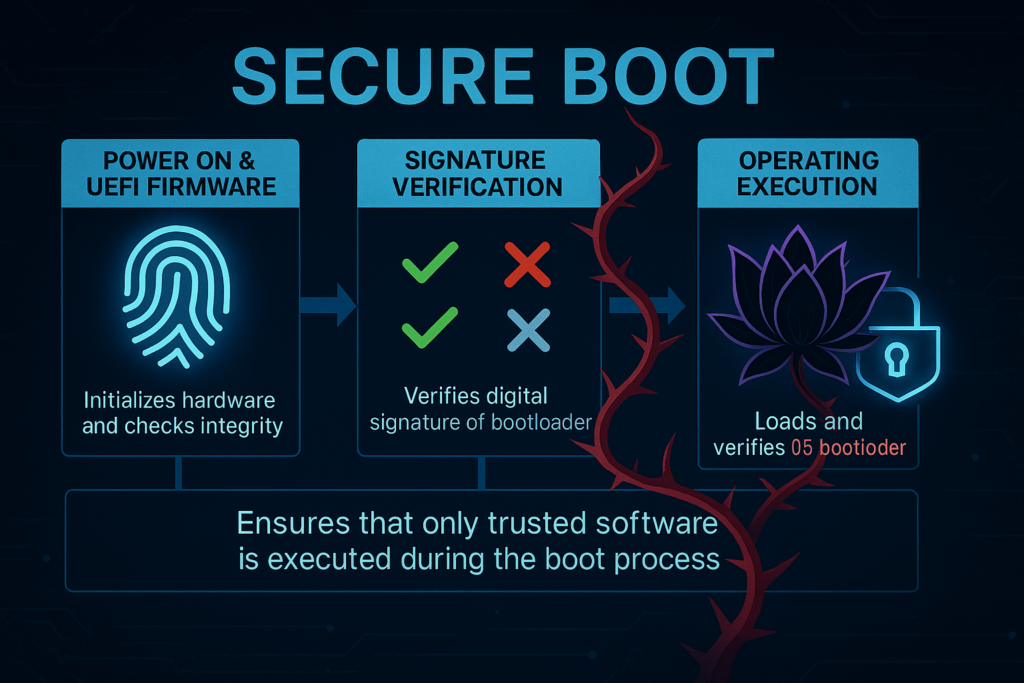
Secure Boot sounds technical, but the concept is straightforward. It's a security standard that verifies every piece of code running during your system's startup process before it actually executes. Think of it like a bouncer at a nightclub checking IDs at the door. Only approved, signed code gets to run. Everything else gets blocked.
Microsoft introduced Secure Boot to Windows 8 back in 2011, and it became mandatory for Windows 11 systems. The security threat it protects against is the boot-level malware, which is the nastiest kind. Regular antivirus software runs after Windows has already loaded. Bootkit malware runs before Windows even starts, hiding itself in the firmware or the early boot process where traditional security tools can't see it. By the time your antivirus engine fires up, the malware is already in control of everything underneath it.
Secure Boot prevents this by establishing a "chain of trust" during startup. The system's firmware is signed with a certificate. The bootloader is signed. The Windows kernel is signed. Each layer verifies the signatures of the layer it's about to load. If any signature is invalid or missing, the boot process stops dead. A compromised bootloader can't load, so even if malware has infiltrated your system, it can't hijack the startup sequence.
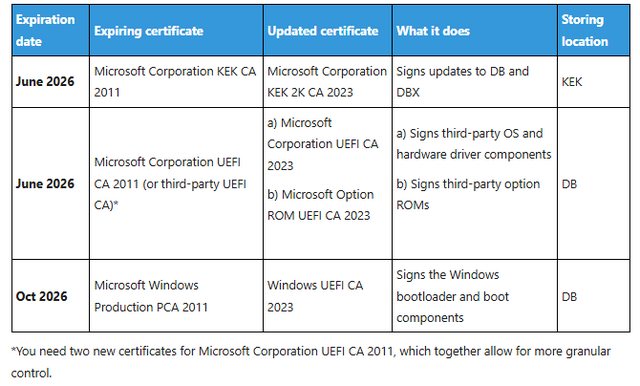
The certificates used in this verification process don't last forever. Like all cryptographic certificates, they have expiration dates. Microsoft issued the current generation of Secure Boot certificates in 2011. That's 14 years of continuous use on potentially billions of systems worldwide. The original Certificate Authority (CA) certificates that signed the bootloaders for Windows 8, Windows 8.1, Windows 10, and Windows 11 are now nearing retirement.
The 2026 Expiration Timeline Explained
Microsoft didn't set these expiration dates randomly. Cryptographic standards evolve. What was considered an acceptable security strength in 2011 isn't necessarily adequate for 2026 and beyond. By retiring older certificates on a planned schedule, Microsoft ensures that the security infrastructure supporting millions of Windows systems stays current with modern security expectations.
The expiration window runs from June 2026 through October 2026. Different certificate chains expire on different dates depending on when they were issued and their assigned lifespan. This staggered expiration prevents a single point of catastrophic failure. If every certificate expired on the same day, we'd see a coordinated global incident where older systems suddenly couldn't boot properly. Instead, Microsoft is managing this transition gradually.
What happens when a certificate expires? The system doesn't lock you out immediately. Windows will keep running on an expired certificate, but it enters a "degraded security state." Microsoft's Nuno Costa, who oversees this transition, explained that expired credentials become potential weak points. They're more susceptible to cryptographic attacks because research into breaking those specific algorithms has progressed over the decades. An algorithm that was secure in 2011 is substantially weaker in 2026.
Moreover, future security updates from Microsoft will require the new certificates. If you're running on an expired certificate, your system won't accept those updates. This doesn't mean immediate danger, but it creates a security debt that compounds over time. Your system will gradually drift further behind the security curve as new threats emerge and Microsoft releases patches for them.
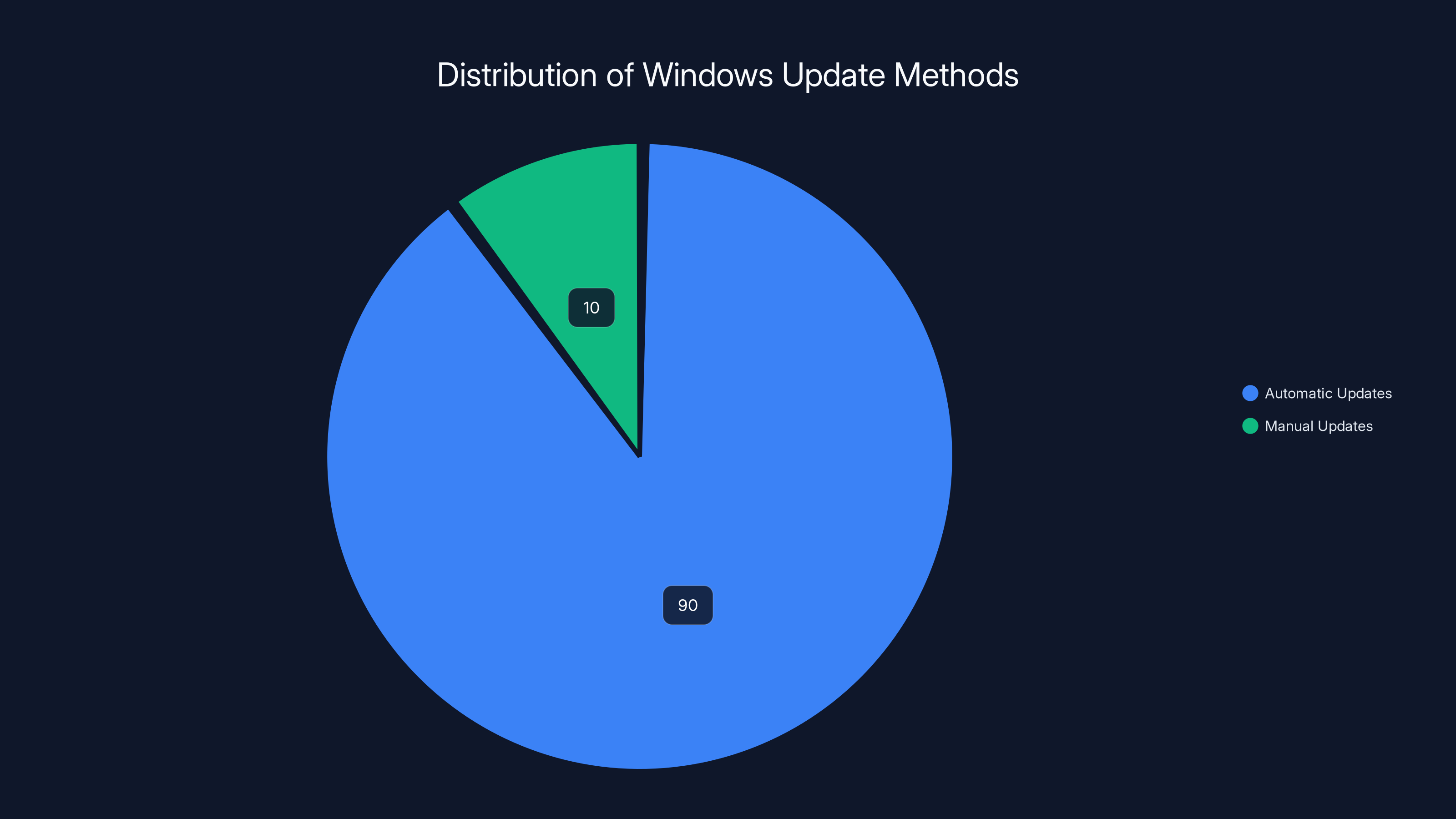
An estimated 90% of Windows 11 systems receive automatic updates, while 10% require manual intervention due to specialized hardware or firmware constraints.
How Certificate Authority Infrastructure Works
Understanding the certificate replacement requires understanding how certificate hierarchies work. It's not just one certificate expiring. It's an entire chain.
At the top sits the Root Certificate Authority (Root CA). This certificate is baked into the firmware of every Windows system and virtually every computer running UEFI firmware. It's the ultimate source of trust. If the Root CA is compromised, everything downstream is compromised. So Root CAs are protected like the crown jewels. They're kept offline, in secure vaults, accessed only under extreme security protocols.
Underneath the Root CA sit intermediate CAs. These are certificates issued by the Root CA that can themselves issue certificates to other entities. They have more limited scope and shorter lifespans than Root CAs. For Secure Boot, Microsoft's intermediate CAs are what actually verify and sign the bootloaders and kernels that run on your system.
When a certificate expires, you can't simply revoke it and issue a new one with the same key. The key material itself needs to be rotated. New certificates require new cryptographic keys. That means new Root CAs, new intermediate CAs, and ultimately new bootloaders and kernels signed with these new certificates.
Microsoft issued new Secure Boot Root CA certificates in 2023 and started shipping them with new systems in 2024. These new certificates have a lifespan extending well into the 2030s. Systems need both the old certificates (to verify existing code) and the new certificates (to verify future code) during the transition period. This is why the rollout is phased and why it's being done through Windows updates.
The New Certificates: What Changed and Why
Microsoft's new Secure Boot certificates represent a meaningful upgrade in cryptographic strength. The older certificates used NIST P-256 elliptic curves. The new ones use stronger algorithms that are resistant to newer attack methods discovered over the past decade.
The asymmetric cryptography protecting these certificates also improved. Longer key sizes, more robust padding schemes, and updated hash algorithms form the foundation of the new certificates. These aren't just cosmetic improvements. They're the difference between algorithms that could theoretically be broken with sufficient computing power in 2011 versus algorithms that would require computational resources that don't exist in 2026.
The distribution strategy also changed. In 2011, certificate updates required BIOS firmware updates from the original equipment manufacturers (OEMs). Those updates were (and still are) risky propositions. If a firmware update fails halfway through, you have a "bricked" system that won't boot at all. Microsoft couldn't mandate them. Too many users would be left with dead machines.
Now, with Windows Update acting as the distribution channel, Microsoft can push certificate updates to virtually every system automatically. The new certificates are part of the normal Windows update process. They're installed into the firmware by the Windows bootloader, which is far safer than pushing firmware updates directly.
For systems sold since 2024, this is seamless. They shipped with both old and new certificates already installed. Their systems will continue functioning through the entire transition period with zero issues.
Windows 11 Users: The Automatic Update Path
If you're running Windows 11 and you've installed updates since January 2025, you've already received the new Secure Boot certificates. For most users, that's the entire story. The update happened silently. Your system is now prepared for the certificate expiration.
The rollout happens through regular Windows updates. KB5074109 (released in January 2025) was the first monthly update to include the new certificates. Every subsequent monthly update also carries them. If you've installed any Windows 11 updates in the past few months, you have them.
Microsoft designed this to be transparent. You won't see a notification. You won't see a security alert. Your system won't restart any differently than it normally would. The certificates are installed into your firmware during the normal boot process as Windows loads. By the time you sit down at your computer, the update is complete.
The beauty of this approach is that it's immune to user negligence. Even if you ignore Windows Update notifications, you'll eventually get the new certificates just from normal security patching. Even if you actively delay updates, the new certificates will be installed the next time you allow updates to run.
However, there are exceptions. Some specialized systems don't follow this path. Servers, Io T devices, and systems in highly controlled enterprise environments might have different update processes. These environments often disable automatic updates to prevent unexpected reboots. Administrators managing these systems need to manually verify that the new certificates have been installed and ensure firmware updates are applied if the OEM requires them.

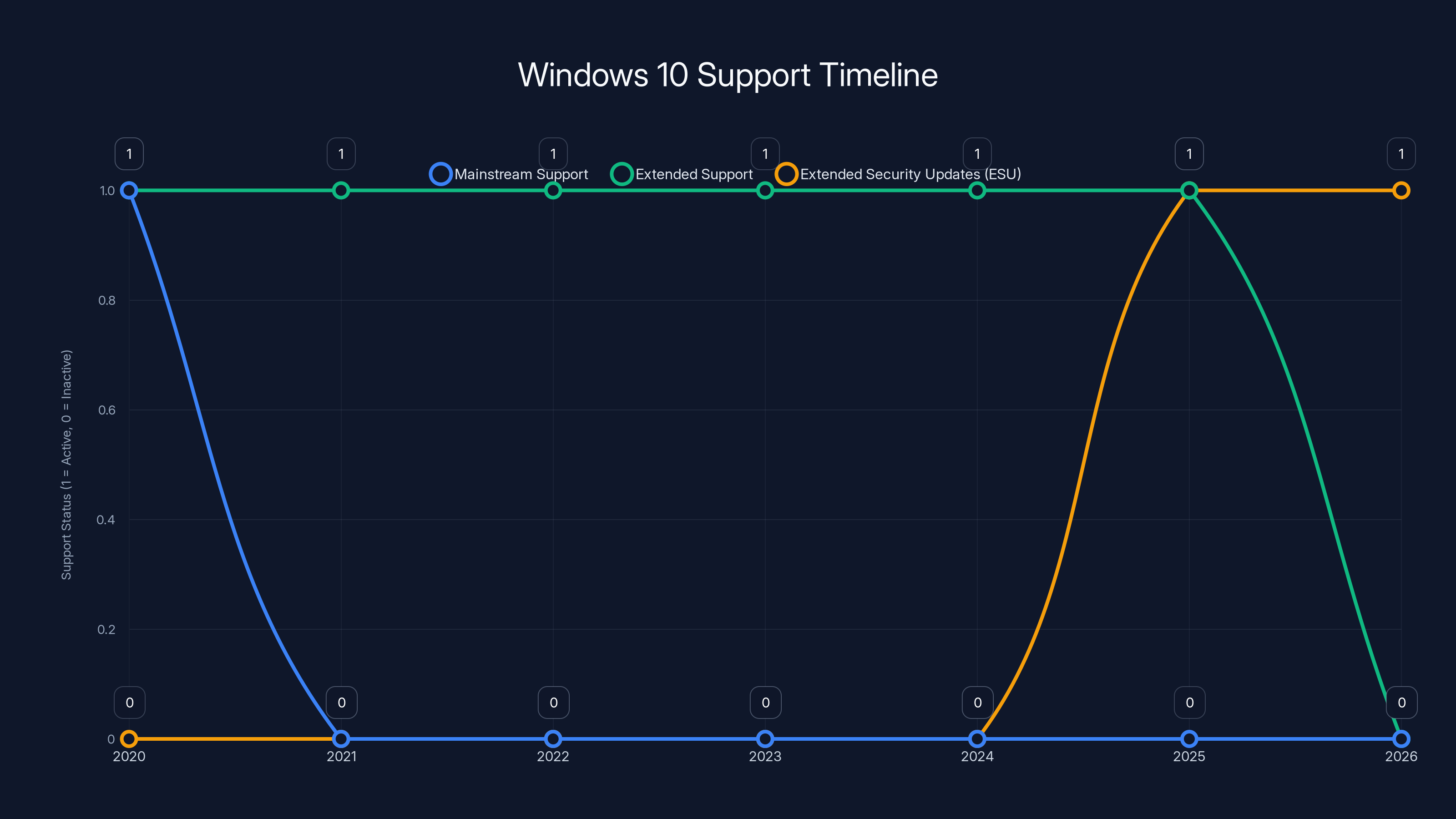
Windows 10 entered Extended Support in 2020, which will last until 2025. Users can opt for Extended Security Updates to maintain security until mid-2026.
The Catch: Specialized Systems and Firmware Updates
Not all Windows devices follow the same update path. Microsoft acknowledges that "a fraction of devices" will need additional steps. This fraction includes a variety of hardware categories that account for far more than 1% of Windows devices when you add them all together.
Servers are one category. Windows Server systems often run in data centers where reboots are extremely disruptive. Many server environments disable automatic Windows updates entirely. Instead, administrators schedule maintenance windows and apply updates on their own timeline. These systems won't automatically receive the new certificates unless someone manually triggers Windows Update.
Io T (Internet of Things) devices are another category. These are Windows systems embedded in everything from ATMs to car infotainment systems to medical devices. They're often locked down more tightly than consumer PCs. Updates might be controlled by the device manufacturer rather than Microsoft. A fitness tracker running a minimal Windows version might never receive standard Windows Update notifications.
Specialized enterprise hardware like point-of-sale systems, manufacturing equipment, and industrial control systems often run on custom-configured Windows installations. These devices might have firmware that's years old and isn't compatible with receiving certificates through Windows Update.
For these systems, a firmware update from the device manufacturer (OEM) might be required. Firmware updates are the scariest type of update. If they fail, the system doesn't boot at all. Older systems might not have received firmware updates in years. The manufacturer might not even provide new firmware versions for legacy hardware.
Microsoft says that for "the vast majority" of Windows 11 users, automatic updates are sufficient. Industry estimates suggest automatic updates cover 85-95% of consumer and business Windows 11 systems. The remaining 5-15% requires manual intervention or OEM firmware updates.
Where do you find out if your specific hardware needs a firmware update? Check your OEM's support pages. HP, Lenovo, Dell, ASUS, Acer, and other major manufacturers have started publishing Secure Boot certificate information. A quick search for "[Your OEM] Secure Boot certificate update 2025" should point you to whatever steps your specific system needs.
Windows 10 and Extended Security Updates
Windows 10 is at the end of its life. Microsoft stopped mainstream support on October 13, 2020. The system is currently in Extended Support, which continues through October 13, 2025. After that date, it's game over. No more security updates, no more bug fixes, nothing.
Since Windows 10 is essentially a legacy system, Microsoft isn't rolling out the new Secure Boot certificates to it through normal Windows Update. Instead, users have an option: enroll in Extended Security Updates (ESU).
Extended Security Updates is a paid program that extends Windows 10 support for three more years beyond the normal end date. Microsoft charges for ESU because it requires maintaining security patches for aging infrastructure. For individuals, ESU costs $55 per year. For small businesses, the cost scales based on the number of systems. For enterprises, it's part of licensing agreements.
If you enroll in ESU, you'll receive the new Secure Boot certificates alongside other security patches. If you don't enroll, you won't get the new certificates. When the original certificates expire in mid-2026, your system will enter a degraded security state.
This creates a practical decision point for Windows 10 users. If you're running Windows 10 and you want your system to remain secure after June 2026, you have a few months to decide. Either enroll in ESU, or plan to upgrade to Windows 11 before the certificates expire.
Migrating from Windows 10 to Windows 11 is straightforward if your hardware supports it. Most Windows 10 systems can run Windows 11. The hardware requirements are minimal: a processor from roughly 2015 or newer, TPM 2.0 (which is standard on all newer systems), and UEFI firmware with Secure Boot support (which is standard on anything built in the last decade).

What "Degraded Security State" Actually Means
Microsoft's terminology can be vague. When they say a system enters a "degraded security state" after certificates expire, what specifically happens?
First, the system continues to boot normally. Windows doesn't refuse to start if your Secure Boot certificate is expired. Bootkit malware isn't suddenly going to be able to hijack your system just because a certificate expired. The security architecture is still in place and still functional.
Second, the system can't receive future boot-level security updates. This is the real problem. Any new security patches that require signed bootloader changes need to be validated against valid certificates. If your system's certificates are expired, Windows Update will refuse to apply them. Your Secure Boot infrastructure is frozen in time.
Third, future hardware and software might not work with your system. As new devices and software are released, they'll be signed and verified against the new certificates. Older systems running on expired certificates might reject them as invalid. A graphics card driver, a firmware update from a peripheral manufacturer, or a Windows component update all rely on Secure Boot signatures. If those signatures can't be verified, the component won't load.
Fourth, there's a potential compatibility issue with future Windows versions. Windows 12 (or whatever the next major version is called) will likely require the new certificates. Systems running on expired certificates might have trouble upgrading.
None of this happens catastrophically. It's not like your system suddenly stops working. It's more like you're slowly losing the ability to patch security vulnerabilities. Your system remains functional but increasingly isolated from the security ecosystem that supports it.
The practical impact varies by use case. A system that never connects to the internet and runs the same applications forever might be fine with expired certificates. A system regularly installing new software, updating hardware, and patching security vulnerabilities will eventually hit incompatibilities.

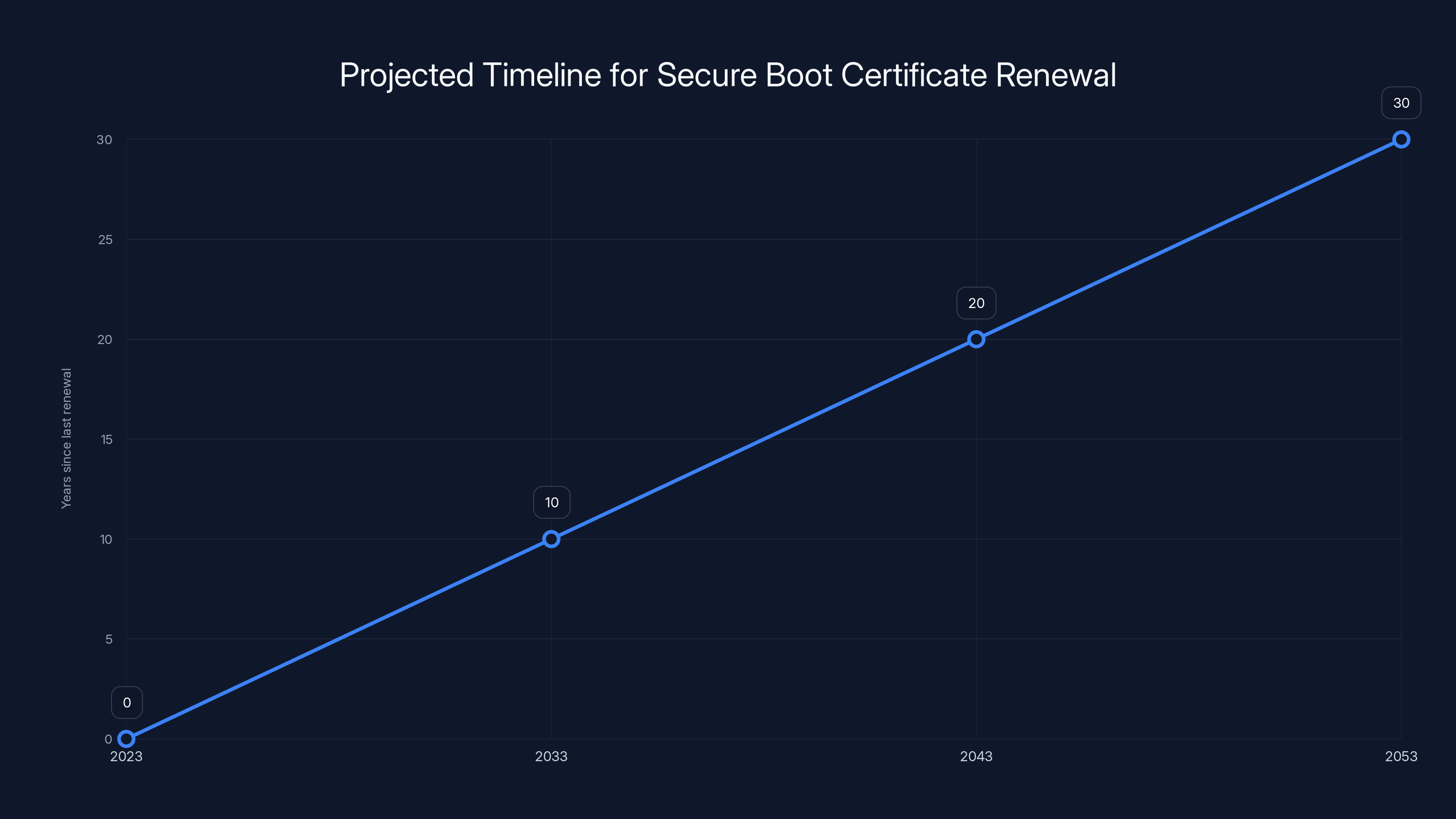
Secure Boot certificates are projected to be renewed every 10-15 years, ensuring ongoing adaptation to cryptographic advancements. Estimated data.
The Boot Process and Certificate Verification
To understand why Secure Boot certificates matter, it helps to walk through what actually happens when your computer starts up.
Your system's firmware (also called BIOS or UEFI, depending on age) is the first code that runs. It's stored in read-only memory on your motherboard. When you press the power button, the firmware wakes up and starts executing.
The firmware's first job is to initialize the hardware: the CPU, RAM, disk controllers, and everything else. Once basic hardware is ready, the firmware needs to load the operating system. It does this by reading the boot sector from your disk. The boot sector contains the Windows bootloader.
But how does the firmware know the bootloader is genuine and hasn't been modified by malware? This is where Secure Boot certificates enter the picture. The bootloader is digitally signed with a certificate. The firmware verifies this signature using the public key stored in its Secure Boot database.
If the signature is valid, the bootloader is allowed to run. If the signature is invalid or missing, the boot process stops. The system won't load Windows at all.
Once the bootloader is running, it loads the Windows kernel. The kernel also has a digital signature. The bootloader verifies this signature before executing the kernel. Again, if the signature is invalid, the boot stops.
This chain continues through each layer of the boot process. Every component that runs before Windows is fully loaded goes through this verification. Any component with an invalid signature gets blocked.
The certificates used in this verification chain have specific lifespans. When a certificate expires, the signatures it created are no longer considered valid. This doesn't mean bootloaders or kernels suddenly become malicious. It means the verification process fails because the certificate that signed them is out of date.
Microsoft's new certificates extend this chain of trust into the future. Systems need both old and new certificates during the transition because some code is still signed with old certificates. Once the transition is complete and all bootable code uses the new certificates, the old certificates can be phased out entirely.
The Enterprise and Server Implications
For large organizations, the Secure Boot certificate renewal presents a different challenge than it does for individual consumers.
Enterprise IT departments typically maintain strict control over Windows updates. They test updates in lab environments before deploying them to production systems. They schedule update deployments carefully to avoid disrupting critical services. Some enterprises stagger updates across weeks or months to distribute the load on infrastructure.
This means enterprise systems might not receive the new certificates through automatic updates. The IT department might deliberately delay January 2025 updates until they've thoroughly tested them. Systems might not receive the new certificates until March, April, or even later.
For server environments, this becomes critical. A Windows Server running a critical application might not be rebooted for months. Applying updates in such environments is like changing the oil in an airplane while it's still flying. The stakes are high, and downtime is expensive.
Microsoft's phased rollout gives enterprises time to plan. January 2025 saw the first update containing new certificates. Now enterprises have until June 2026 to ensure all their systems have received the new certificates. That's an 18-month window. Most enterprise IT departments will complete their deployments in the first 6-9 months.
The critical insight for enterprises is that they can't delay the transition indefinitely. June 2026 is a hard deadline. Any system that hasn't received the new certificates by then will enter a degraded security state. Large enterprises with thousands or tens of thousands of systems need to start planning their certificate rollout schedules now.
For Microsoft's Software as a Service (Saa S) offerings (like Microsoft 365, Azure, and Dynamics 365), the certificate transition is essentially invisible. Microsoft manages the infrastructure and handles all certificate updates automatically.
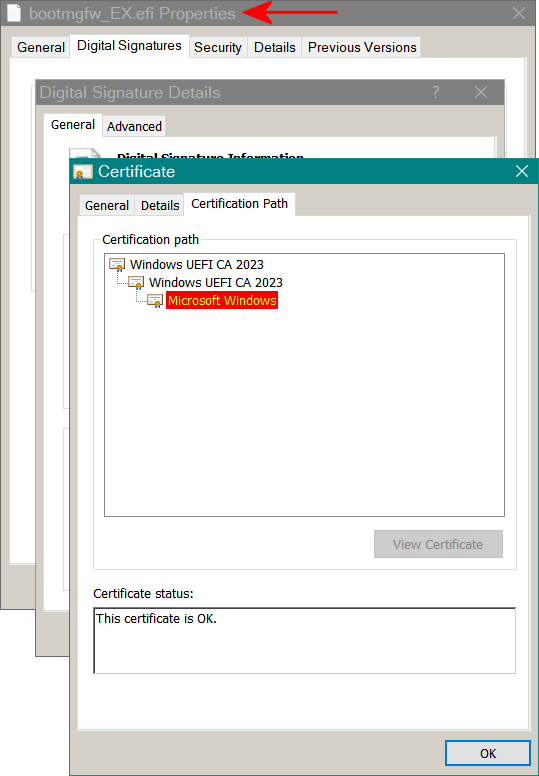
Checking Your System's Certificate Status
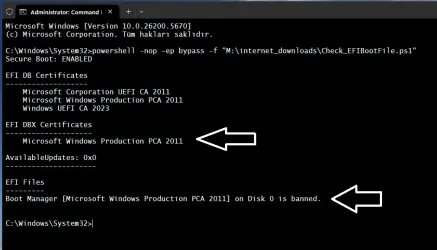
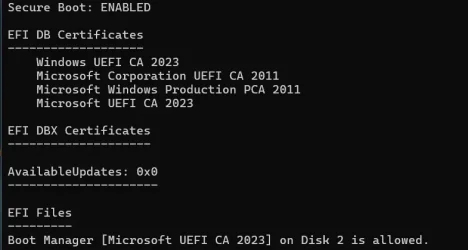
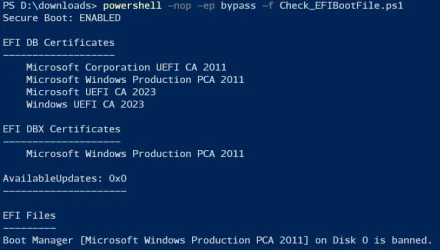
How do you verify that your system has actually received the new Secure Boot certificates? For most users, checking Windows Update is sufficient. But if you want to dig deeper, you can inspect the Secure Boot configuration directly.
On Windows 11, open Settings > System > System Information. Look for your Windows build number. If it's build 23607 or later (released in January 2025 or after), you almost certainly have the new certificates.
For a more technical verification, use Power Shell. Open Power Shell as Administrator and run:
powershellConfirm-Secure Boot UEFI
This command returns a simple True/False indicating whether Secure Boot is currently enabled. But it doesn't tell you which certificates are installed. For deeper inspection, you'd need to use firmware utilities specific to your hardware manufacturer.
On many systems, you can access the UEFI firmware settings by restarting and pressing a key during startup (usually Delete, F2, F10, or F12, depending on your manufacturer). Inside the firmware settings, there's typically a Secure Boot menu that shows installed certificates. However, decoding the certificate information requires technical knowledge.
For practical purposes, the easiest check is confirming that Windows Update has delivered KB5074109 or a later monthly update to your system. If it has, the new certificates were installed.
For enterprise and server environments, check your Windows Update logs and your IT department's deployment records. Large organizations track update deployments carefully.
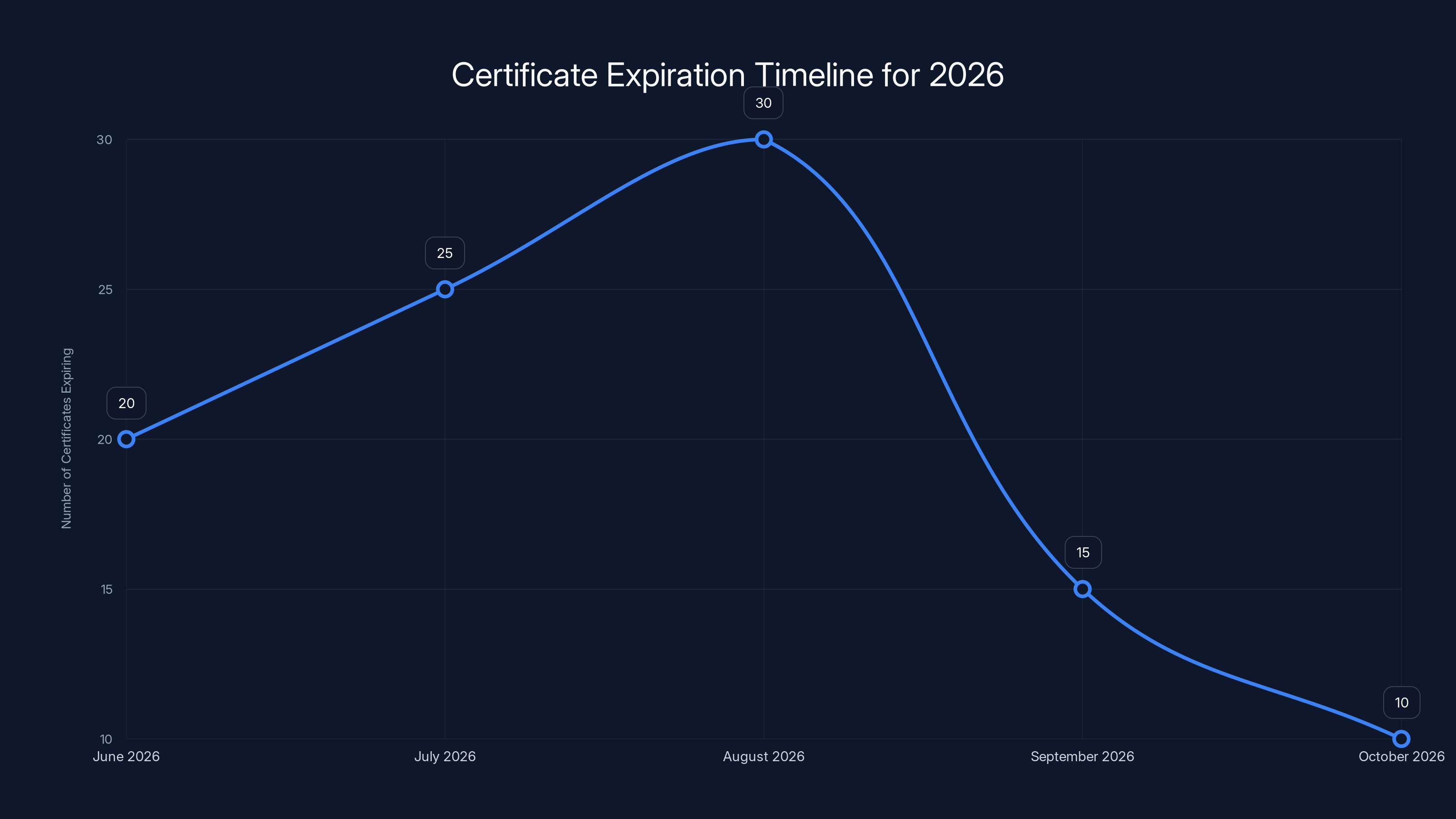
The expiration of certificates is staggered over several months in 2026 to prevent a single point of failure. Estimated data shows a peak in expirations around August.
Manufacturer-Specific Firmware Updates
While Windows Update handles certificate installation for most systems, some hardware requires manufacturer firmware updates. This is where things get complicated.
Different OEMs have different requirements. Some manufacturers are pushing firmware updates proactively. Others are providing them on-demand. Some haven't announced their plans yet.
HP has published Secure Boot guidance for its systems, with firmware updates available on a model-by-model basis. Lenovo is doing similar outreach to its enterprise customers. Dell has issued communications through its IT support channels. Smaller manufacturers are slower to respond.
The safest approach is to check your system manufacturer's support website directly. Search for "Secure Boot 2026" or "Secure Boot certificate renewal" on their support pages. If they have firmware updates available, they'll be listed there.
If your manufacturer doesn't have guidance yet, check back periodically through 2025. Most manufacturers will eventually publish their Secure Boot plans. The deadline is June 2026, so manufacturers have until then to release any necessary firmware updates.
Don't rush into firmware updates for systems that don't need them. Firmware updates are risky. If something goes wrong, your system might not boot at all. Only apply firmware updates if your manufacturer specifically recommends them for Secure Boot certificate support.

Why This Matters: The Broader Security Picture
Secure Boot certificate renewal isn't just about maintaining an existing security infrastructure. It's about staying ahead of evolving threats and adapting to changing cryptographic standards.
The bootkit malware threat is real. Rootkits that operate at the firmware level have been discovered targeting everything from enterprise servers to consumer systems. The Hacking Team APT (advanced persistent threat) used firmware-level exploits. Nation-state actors have access to bootkit capabilities. These threats exist, and they're dangerous.
Secure Boot doesn't make these threats impossible. But it significantly raises the barrier to entry. An attacker needs to either compromise the bootloader or modify boot code in ways that don't match the signed certificates. This requires much deeper technical sophistication than typical malware.
By maintaining a current certificate infrastructure, Microsoft makes it progressively harder for attackers to launch bootkit attacks. Each new generation of certificates incorporates lessons learned from cryptographic research over the preceding years.
Moreover, the certificate renewal represents a process that will repeat every 10-15 years indefinitely. This is the new normal for security infrastructure. Systems need to anticipate and plan for regular cryptographic refresh cycles. Organizations that do this well stay secure. Those that treat security as "set it and forget it" gradually become vulnerable.
The transition also demonstrates something important about Windows: it's evolving. Some people perceive Windows 11 as a static OS, but infrastructure like Secure Boot is constantly being refreshed and improved. These changes aren't flashy. You don't see them in marketing materials. But they're happening, and they matter.
Timeline for Action: What You Should Do Now
The certificate expiration window runs from June 2026 to October 2026. That's your hard deadline. But waiting until June 2026 to start paying attention is a mistake.
Now (early 2025): Check that your system has received Windows Update KB5074109 or later. If you're running Windows 11 and your system updated since January 2025, you're fine. If you're running Windows 10, start planning your migration to Windows 11 or your Extended Security Updates enrollment.
Spring 2025: If you're managing enterprise systems, create a deployment plan for ensuring all systems have the new certificates installed. Test the certificate installation process in your lab environment. Document which systems need firmware updates from manufacturers.
Summer 2025: Begin rolling out new certificates to enterprise systems if you haven't already. Start coordinating with your hardware manufacturers about any firmware updates. Create a tracking system to identify which systems have successfully received the new certificates.
Fall 2025: Complete the certificate rollout for systems you control. Verify that all critical systems are running on the new certificates. Identify any systems that are problematic and plan mitigation strategies.
Winter 2025-2026: Final verification pass. Ensure every system is prepared. For any systems that can't be updated, plan for eventual replacement or disconnection from the network.
Spring 2026: Final preparation. Handle any remaining stragglers. Test that systems can still boot after the expiration date (even though they should).
This timeline seems conservative. You could theoretically wait until May 2026 and start addressing Secure Boot certificates. But that's cutting it extremely close. Hardware manufacturers need time to develop and test firmware updates. Enterprise IT departments need time to plan deployments. Waiting too long compresses the timeline into a crisis situation.
The smart approach is to view the certificate renewal as a six-month initiative, not a last-minute scramble.

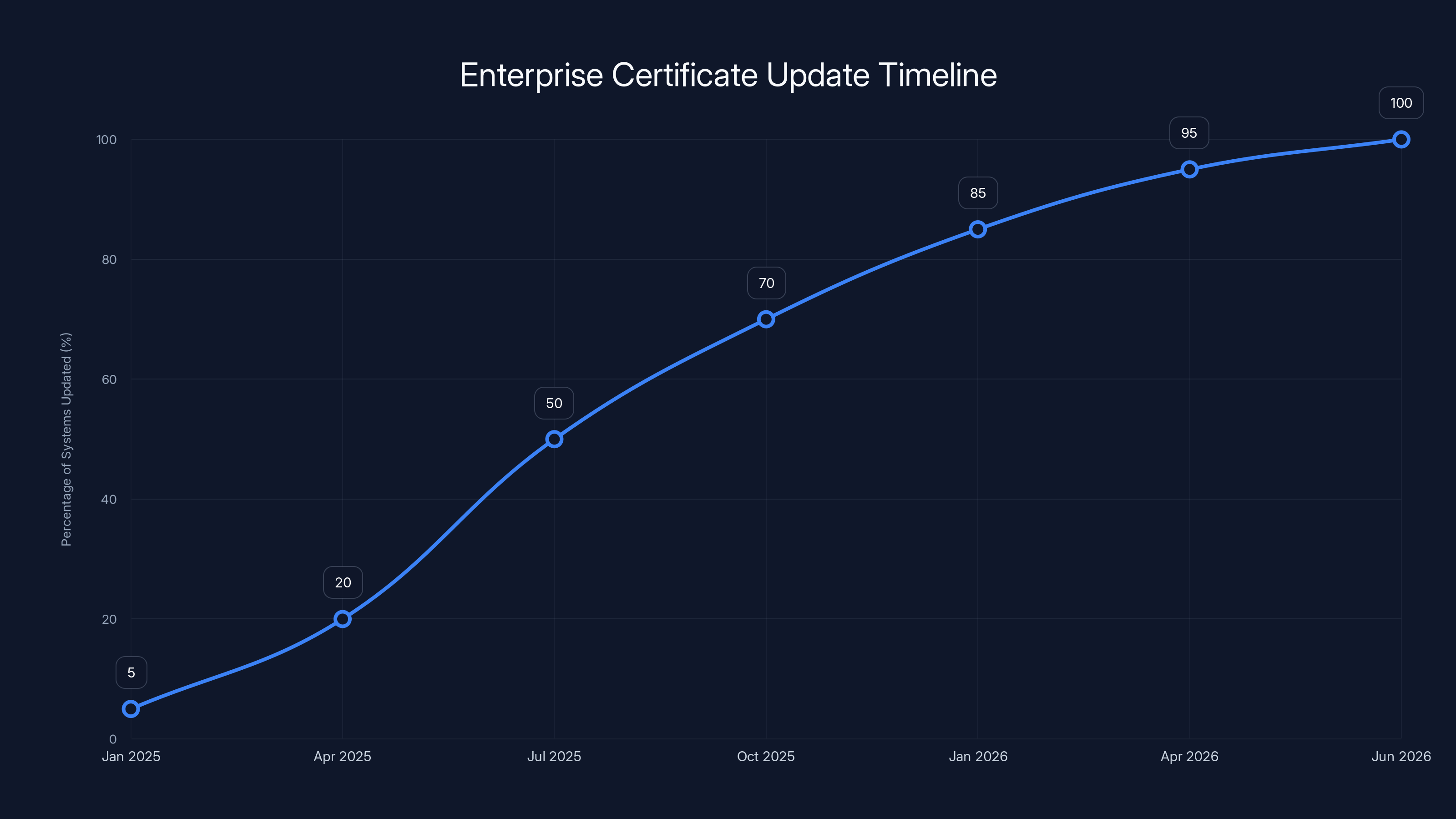
Most enterprises are expected to complete certificate updates within the first 6-9 months of the 18-month window, reaching 100% by June 2026. Estimated data.
Common Misconceptions About Secure Boot
Secure Boot has been surrounded by myths and misconceptions since its introduction. Let's clear up some of the confusion.
Misconception 1: Secure Boot prevents all malware. False. Secure Boot only prevents malware that needs to modify the bootloader or run before Windows loads. Regular application-level malware, rootkits running as Windows processes, spyware, and ransomware can still infect your system. Secure Boot is one layer of defense, not complete protection.
Misconception 2: Expired certificates mean your computer is compromised. False. An expired certificate doesn't mean your system has been attacked. It just means the cryptographic proof of the bootloader's authenticity can no longer be verified using that certificate. The bootloader itself isn't compromised just because the certificate expired.
Misconception 3: You can't boot without Secure Boot enabled. False. Secure Boot can be disabled in firmware settings. If you disable Secure Boot, your system will boot without certificate verification. You lose protection against bootkit malware, but your system will still start up. This is why Secure Boot was historically optional (it's now effectively mandatory on Windows 11, though still technically disableable).
Misconception 4: Secure Boot prevents you from installing alternative operating systems. Largely true, and it's intentional. Secure Boot was designed to make it harder for malware to boot before Windows loads. As a side effect, it prevents other operating systems from booting unless they're signed with certificates in your Secure Boot database. However, users can disable Secure Boot in firmware settings to install other OSes if they choose.
Misconception 5: Certificate renewal is a one-time event. False. This is the first major Secure Boot certificate renewal, but it won't be the last. Every 10-15 years, certificates will need renewal as they approach expiration. Organizations need to build processes to handle this recurring event.
Future-Proofing Your System
Whatever you do about this certificate renewal, think about broader patterns. Technology moves faster than we expect. Standards evolve. Security requirements change. Systems need to be designed with this in mind.
For individuals, this means staying current with Windows updates. Yes, updates are sometimes annoying. They restart your computer at inconvenient times. But they're how you receive security patches and infrastructure updates like this certificate renewal. Delaying or disabling updates creates accumulated technical debt that eventually becomes problematic.
For organizations, this means building update processes that can handle infrastructure changes without requiring constant heroic efforts. Automated update deployment, testing pipelines, and monitoring systems should be in place. These processes enable you to handle the next certificate renewal (in 2035 or so) with minimal friction.
For hardware vendors and manufacturers, this means designing systems that can receive firmware updates safely and securely. The riskiest part of this certificate renewal is systems that require firmware updates but don't have safe update mechanisms. Manufacturers that build updateability into their products from the start won't face this problem.
The certificate renewal is a good reminder that security infrastructure requires ongoing maintenance. It's not something you set up once and then ignore forever. Cryptographic standards evolve. Certificates expire. Hardware ages. The systems protecting your computer need continuous attention.

What's Next After the 2026 Transition
Once the June-October 2026 transition is complete, what happens next?
The old 2011-era certificates will still exist on many systems, but they'll be expired and non-functional. Gradually, over the following years, they'll be phased out entirely from new systems. Systems running the old certificates will enter a degraded security state and eventually become incompatible with new software.
Microsoft will likely stop supporting old certificates by 2027 or 2028. Any system that hasn't transitioned to the new certificates will be on its own.
The new certificates from 2023 have a lifespan extending well beyond 2035. They'll be sufficient for at least another decade. By the time they approach expiration, whatever comes next in the cryptographic evolution will be ready to replace them.
Microsoft might eventually use certificate renewal as an opportunity to further strengthen Secure Boot. The next generation of certificates could incorporate post-quantum cryptography, which would be resistant to attacks from quantum computers. Or they could implement different verification mechanisms entirely, moving beyond certificate-based signing.
The important thing is that this process is repeatable. Microsoft has now demonstrated how to manage a global infrastructure security transition affecting hundreds of millions of systems. They can apply these lessons to future transitions.
For users and organizations, the key is to recognize this as a new normal: periodic cryptographic refresh cycles are part of maintaining a secure system. Planning for them, budgeting time and resources for them, and executing them carefully is how you stay secure in the long term.

The Human Side: Why This Matters to You
All of this technical discussion about cryptography and certificates might feel abstract. But the implications are concrete.
If your system doesn't get the new certificates and then you're unable to receive critical security patches, you're at risk. That risk grows over time as new vulnerabilities are discovered in the boot firmware, drivers, and core Windows components.
If you're running Windows 10 and don't plan for the transition, you might wake up in July 2026 and realize your system has suddenly become incompatible with new hardware or software you want to use.
If you're managing dozens or thousands of systems in an organization, the certificate renewal is a coordination challenge. You need to track which systems have been updated, identify systems that need special attention, and create contingency plans for systems that resist updates.
The smart move is to handle this now. Check if your system has the updates. If it doesn't, run Windows Update. If you're managing other systems, make sure they're updated too. If you're running Windows 10, start planning your transition strategy. The work takes a few minutes or a few hours now. Waiting until the certificates expire and then dealing with the fallout takes far longer.
Secure Boot certificate renewal is one of those infrastructure changes that most people will never notice. It will happen silently in the background. But paying attention now, checking that your system is prepared, and planning ahead means you'll never have to think about it again.
FAQ
What exactly is a Secure Boot certificate and why do they expire?
Secure Boot certificates are digital signatures that verify the authenticity of your Windows bootloader and kernel before they run. They're issued by Microsoft's Certificate Authority and function like ID cards for boot-level software. Certificates expire for security reasons: cryptographic algorithms that were secure when the certificate was issued become progressively weaker as computing power increases and research advances. The 2011 certificates are expiring now because 15 years of cryptographic research has weakened their security margins. Retiring them on a scheduled basis and replacing them with stronger certificates maintains the security of the entire boot process.
When exactly do I need to have the new certificates installed on my system?
Microsoft recommends having the new certificates installed before June 2026, when the first batch of old certificates begin expiring. The deadline extends through October 2026 for the final batch of old certificates. However, waiting until June 2026 is extremely risky because hardware manufacturers still need time to develop firmware updates, and you want buffer time to handle unexpected issues. For most Windows 11 users, the certificates are already installed if you've received updates since January 2025. Windows 10 users need to either enroll in Extended Security Updates or plan to upgrade to Windows 11 before the deadline.
What exactly happens to my computer if the certificates expire and I don't get the new ones?
Your system will continue to boot normally and function for basic tasks. However, it enters what Microsoft calls a "degraded security state." Specifically, you won't be able to receive future boot-level security patches, which are critical for protecting against firmware and bootkit malware. Additionally, future hardware drivers and software updates might refuse to load because they'll be signed with the new certificates that your system can't verify. Over time, your system will become increasingly incompatible with new hardware and software. It won't stop working immediately, but it will gradually become isolated from the security ecosystem that supports modern Windows.
Do I need to do anything manually to get the new certificates, or are they automatic?
For Windows 11 users, the new certificates are delivered automatically through Windows Update (starting with KB5074109 in January 2025). If you install regular monthly updates, you already have them or will get them with your next update. No manual action is required for the vast majority of Windows 11 users. However, some specialized hardware like servers, Io T devices, or older systems might require additional steps. Check your device manufacturer's support pages for any specific guidance. Windows 10 users must enroll in Extended Security Updates ($55/year for individuals) to receive the new certificates through a different update channel.
How can I check if my system has already received the new certificates?
The easiest check is verifying that Windows Update has delivered KB5074109 or a later monthly update to your system. Open Settings > Update & Security > Update History and search for KB5074109 or check if any updates after January 2025 are listed. Alternatively, check your Windows build number in Settings > System > About. If it's 23607 or later, released in January 2025 or after, you have the new certificates. For more technical verification, system administrators can check firmware settings through UEFI menus, though this requires specialized knowledge and varies by hardware manufacturer.
If I'm running Windows 10, what are my options?
You have three main options. First, enroll in Extended Security Updates (ESU) from Microsoft, which continues security support until October 2028 and includes the new Secure Boot certificates. This costs $55/year for individuals or varies for businesses. Second, upgrade to Windows 11 before the June 2026 deadline if your hardware supports it. Most systems from 2015 onward can run Windows 11. Third, stop using the system before June 2026 and replace it. Any other approach (ignoring the issue and continuing to use an unsupported system with expired certificates) leaves your computer vulnerable to boot-level attacks and unable to receive security patches.
Will my hardware manufacturer need to provide a firmware update for my system?
Microsoft says that a "fraction of devices" will require firmware updates from manufacturers. This varies by system. Most newer systems will receive certificates purely through Windows Update. Older systems, specialized hardware, and server equipment are more likely to need manufacturer firmware updates. Check your hardware manufacturer's support website by searching for "Secure Boot certificate 2025" or "Secure Boot firmware update." If they've published guidance, follow it. If they haven't published anything yet, check back periodically through 2025. The deadline gives manufacturers until June 2026 to release necessary firmware updates. Don't apply firmware updates unless your manufacturer specifically recommends them, as firmware updates carry higher risk than software updates.
Is Secure Boot the same as TPM 2.0? Are both required for Windows 11?
No, they're different security features, though both are required for Windows 11. Secure Boot is the certificate-based verification system for bootloaders and kernels that we've been discussing. TPM 2.0 (Trusted Platform Module) is a separate security processor that handles cryptographic functions and protects encryption keys. Both are required for Windows 11, but they're independent systems. The certificate renewal we're discussing affects only Secure Boot, not TPM. Systems that have TPM 2.0 but haven't received Secure Boot certificates will still have problems receiving boot-level security updates after June 2026.
Could this Secure Boot certificate renewal cause problems for Linux users or people who want to run alternative operating systems?
Potentially, yes. Systems that have the new Secure Boot certificates but no longer have the old 2011 certificates installed won't be able to boot Linux distributions or other operating systems that were signed with the old certificates. However, users can disable Secure Boot in firmware settings to boot unsigned operating systems. The trade-off is losing protection against bootkit malware. Linux distributions are already being updated with the new Microsoft certificates, so newer Linux versions should be compatible. However, older Linux installations might have compatibility issues. This is an area where users should verify their Linux distribution is current before the certificate transition completes.

Conclusion: Planning Ahead for Security Infrastructure Evolution
The Windows Secure Boot certificate renewal represents a significant but largely invisible infrastructure transition. For most users, it will happen in the background, and they'll never notice. But for security-conscious individuals, IT departments, and system administrators, understanding what's happening and planning accordingly is essential.
Microsoft's approach is pragmatic and well-designed. Rather than forcing a chaotic last-minute transition, they're rolling out new certificates well in advance through regular Windows updates. They're providing clear timelines and guidance. They're giving hardware manufacturers time to develop firmware updates. They're managing the transition in a way that minimizes disruption while maximizing security.
The lesson here extends beyond just this certificate renewal. Security infrastructure requires ongoing maintenance. Cryptographic standards evolve. Certificates expire. Hardware ages. Systems need to be designed with the assumption that they'll need periodic updates and refreshes. Organizations that build this mindset into their processes will handle future transitions smoothly. Those that treat security as "set it and forget it" will face crises.
For you personally, the action items are simple: Check that your Windows 11 system has received updates since January 2025. If you're running Windows 10, start planning your transition. If you manage multiple systems, create a tracking system to ensure they all receive the new certificates. Talk to your hardware vendor about any firmware updates you might need.
Doing this work now, while there's no urgency and no crisis, ensures you'll never face the situation of systems that can't receive security patches because Secure Boot certificates expired. It's the kind of boring, unglamorous infrastructure work that prevents catastrophes.
Secure Boot itself might seem like a technical detail that doesn't matter to you. But consider what would happen if bootkit malware infected your system. You'd have malware running before Windows even loaded, with root access to everything on your computer. Traditional antivirus software wouldn't see it. You couldn't remove it because it controls the boot process. Your data would be completely exposed. Secure Boot prevents this nightmare scenario. Keeping Secure Boot working correctly, with valid, current certificates, is how you prevent that attack.
The certificate renewal is happening whether you pay attention or not. Systems that don't receive new certificates will enter a degraded security state. But you don't have to be one of them. A few minutes of checking now ensures your system stays secure and supported for years to come.
Key Takeaways
- Microsoft is rolling out new Secure Boot certificates starting January 2025 to replace 2011-era certificates expiring June-October 2026
- Windows 11 users receive updates automatically through Windows Update (KB5074109+); Windows 10 users must enroll in Extended Security Updates
- Systems without new certificates enter a degraded security state that prevents boot-level security patches and may cause hardware/software incompatibility
- A small fraction of specialized systems require manufacturer firmware updates in addition to Windows Update
- The deadline is mid-2026, but planning and deployment should happen throughout 2025 to avoid last-minute complications
Related Articles
- Windows 11 Storage Security Feature Explained [2025]
- How Microchip Authentication Is Stopping Counterfeit Luxury Goods [2025]
- Humanoid Robots & Privacy: Redefining Trust in 2025
- Windows 11 Printer Support: What Microsoft Actually Changed [2025]
- I Switched From Windows 11 to Windows XP for a Week: Here's What I Learned [2025]
- iPhone Lockdown Mode Explained: How Apple's Ultimate Security Works [2025]
![Windows Secure Boot Certificate Renewal Explained [2025]](https://tryrunable.com/blog/windows-secure-boot-certificate-renewal-explained-2025/image-1-1770745119680.jpg)



