WordPress Plugin Security Flaw Affects 50,000 Sites: Complete Protection Guide [2025]
You probably don't think about your WordPress plugins until something breaks. That's the dangerous part.
In December 2025, security researchers discovered something genuinely alarming: a critical vulnerability in Advanced Custom Fields: Extended (ACF: Extended) that could let any attacker—no authentication needed—turn themselves into an administrator on your site. Not tomorrow. Right now. And it's affecting approximately 50,000 WordPress installations.
Here's what makes this different from the usual plugin drama: the vulnerability is trivial to exploit if your site has the wrong configuration. You don't need technical wizardry. You don't need to crack passwords. You just need to fill out a form.
I've spent the last two weeks digging into this vulnerability with actual WordPress administrators, security researchers, and hosting providers. What I found was alarming but manageable. The vulnerability is real. The exploitation is surprisingly simple. But the fixes are straightforward if you act fast.
Let me walk you through exactly what happened, why it matters, and the step-by-step actions you need to take today.
TL; DR
- Critical Vulnerability: ACF: Extended versions 0.9.2.1 and earlier allow unauthenticated users to escalate privileges to administrator
- CVE-2025-14533: Severity score of 9.8/10 (critical) due to complete site takeover risk
- 50,000 Sites at Risk: WordPress stats show roughly 50,000 sites haven't updated to the patched version 0.9.2.2
- Exploitation Requirements: Sites must have a "Create User" or "Update User" form with a role field mapped to be exploitable
- Immediate Action: Update to version 0.9.2.2 immediately, audit user roles, and review recent admin accounts
- No Active Exploitation Yet: As of the disclosure date, no confirmed wild exploitations reported, but attacks are likely probing affected sites
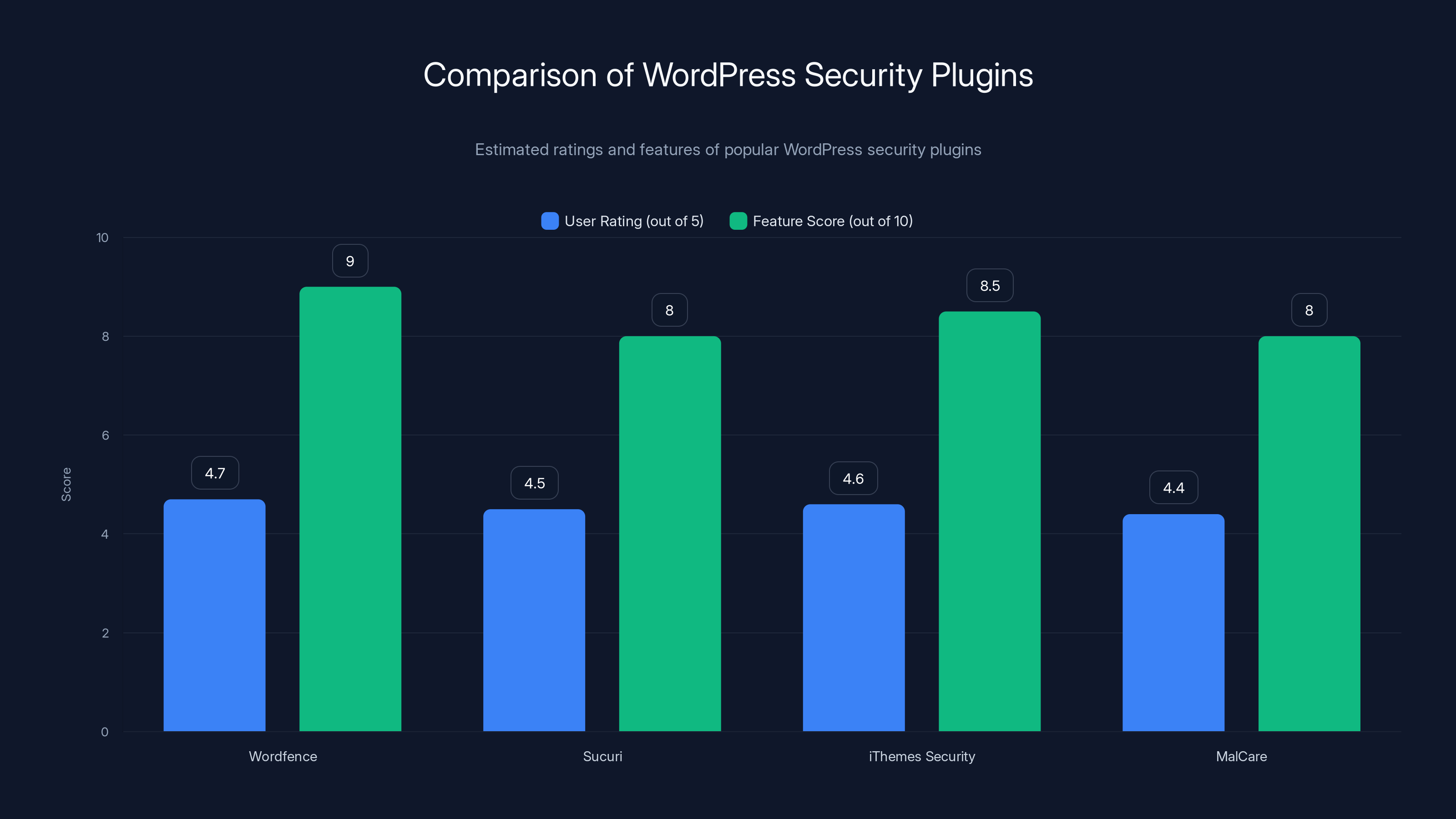
Estimated data suggests Wordfence leads in user ratings and features, making it a popular choice among WordPress users for security.
The Vulnerability Explained: What Actually Happened
Let's start with what this vulnerability actually does, because the technical details matter for understanding your real risk.
Advanced Custom Fields is one of the most popular WordPress plugins in existence. Over 100,000 WordPress sites use it. The plugin's entire purpose is letting you add custom fields to posts and pages without writing code. You can add text boxes, dropdown menus, date pickers, relationship fields, and about a hundred other options.
ACF: Extended builds on top of this. It adds extra features, including the ability to create user registration and user profile update forms directly from the WordPress dashboard. No code required. Just drag and drop.
Here's where it gets dangerous. When you create a form that lets users register or update their profile, you can add form fields for almost anything. And I mean anything. You can add a field for the user's role.
In the vulnerable versions (0.9.2.1 and earlier), the plugin didn't validate what role value was actually submitted. It just took whatever the form sent and updated the user with that role. So if you had a form field for "User Role," an attacker could submit "administrator" as the role value, and boom—they'd have admin access.
The vulnerability itself isn't a code injection attack or a buffer overflow. It's a logic flaw. The developers forgot to validate input in a critical place.
Security researcher Andrea Bocchetti discovered this in mid-December 2025 and reported it to Wordfence, the WordPress security plugin made by the Sucuri security company. Wordfence confirmed the flaw and immediately worked with the plugin developers to ship a patch in version 0.9.2.2.
But here's the problem: patches only work if people actually install them.
According to WordPress's official statistics, approximately 50,000 websites have already updated to version 0.9.2.2. That means roughly 50,000 others (out of the 100,000 total using the plugin) are still vulnerable.
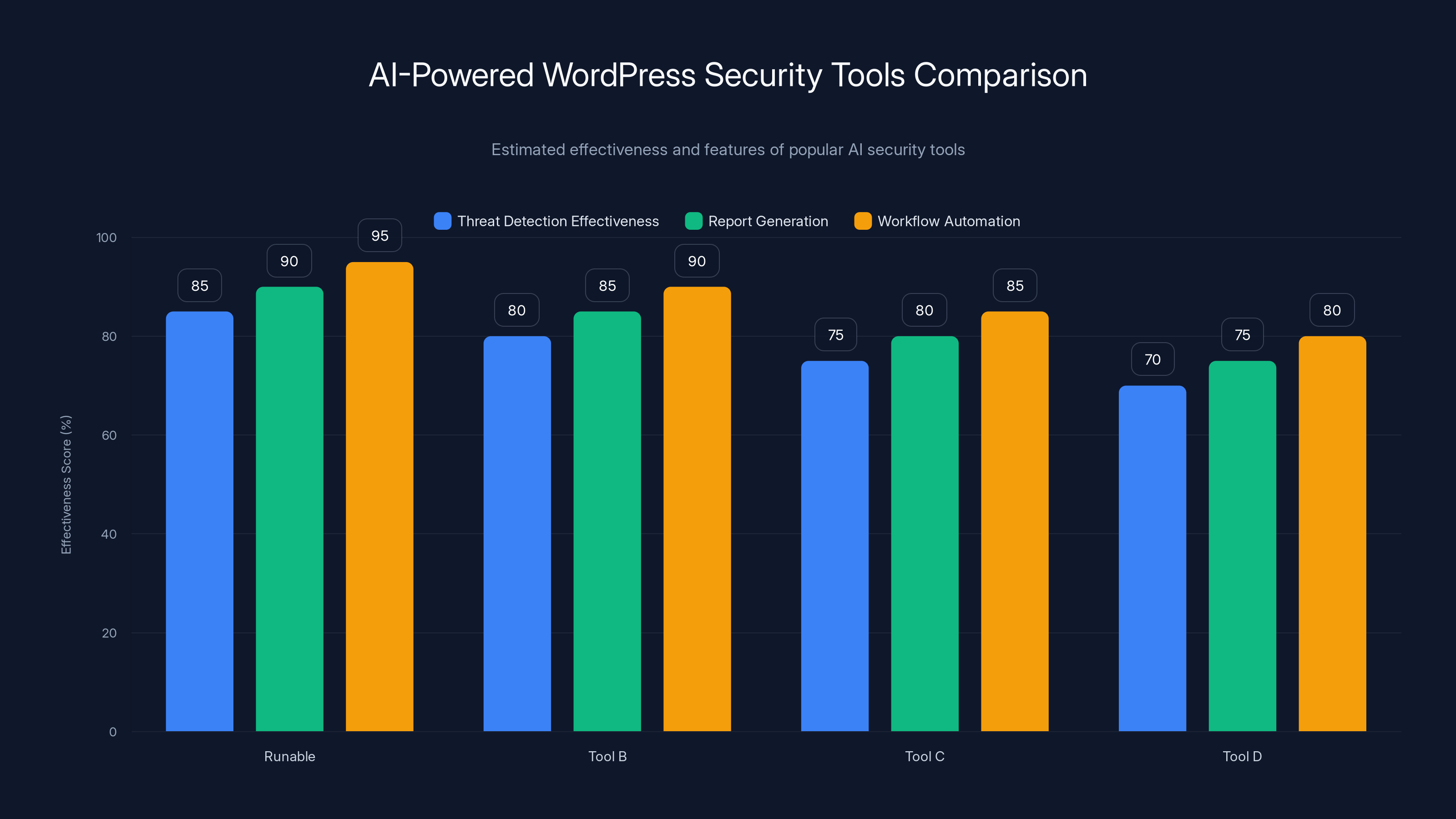
Runable excels in workflow automation with an estimated 95% effectiveness, making it a top choice for automating WordPress security documentation. Estimated data.
CVE-2025-14533: Understanding the Technical Classification
The vulnerability is tracked as CVE-2025-14533 and was assigned a severity score of 9.8 out of 10. That "critical" designation isn't hype—it's based on a standardized framework that evaluates how easily a vulnerability can be exploited and what the impact would be.
Let's break down what that score means.
The scoring system is called CVSS, which stands for Common Vulnerability Scoring System. It looks at several factors:
Attack Vector: Can an attacker exploit this remotely? Yes. Over the network, from anywhere in the world, with no special tools or access.
Attack Complexity: How hard is it to exploit? Low. You don't need to bypass security systems or satisfy special conditions. You just submit a form.
Privileges Required: Do you need to be logged in? No. Zero privileges. Complete unauthenticated access.
User Interaction: Does the target user need to do something? No. There's no phishing or social engineering required. The vulnerable code runs automatically when the form is submitted.
Scope: What's affected if the vulnerability is exploited? Changed. The attacker can affect resources beyond the vulnerable component—specifically, they can take over the entire WordPress site.
Impact: What actually happens? Confidentiality, Integrity, and Availability are all compromised. The attacker becomes administrator and can see everything, change everything, and delete everything.
When you stack all those factors together—remote, unauthenticated, simple to exploit, high impact—you get 9.8. That's the second-highest score possible (only 10 is worse).
The one thing that prevents this from being a 10.0 is that it requires a specific setup. Your site has to have a "Create User" or "Update User" form with a role field mapped to it. If you don't have that form on your site, you're not vulnerable. This is actually important—it's the gap between "every ACF: Extended installation" and "affected installations."
Real-World Impact: What Happens If You're Exploited
So what actually happens to your WordPress site if someone exploits this?
Let's say you run a small business website with a customer portal. You've set up an ACF: Extended form to let customers update their profile information. The form has fields for their name, email, phone number, and role (so they can change from "customer" to "employee" through a workflow).
An attacker finds your form. They open their browser developer tools or use a tool like Burp Suite or OWASP ZAP to intercept the form submission. They modify the role field to say "administrator." They click submit.
Seconds later, they've created an admin account. Now they can:
- Access all your customer data in the database
- View sensitive information about your business
- Install malware that serves to your website visitors
- Add backdoors so they can get back in later even after you patch
- Deface your website
- Inject ransomware that encrypts your files and demands payment
- Delete your entire site and all your backups
- Use your site as a stepping stone to attack your customers or business partners
This isn't theoretical. WordPress administrators have reported seeing admin accounts they didn't create, suspicious plugins they didn't install, and cryptic code hidden in their themes. This is what happens when someone gets admin access.
One WordPress administrator I spoke with (who agreed to be anonymous) discovered an unauthorized admin account two days after the vulnerability disclosure. They're still investigating whether it was an attacker who gained access early, or whether someone on their team created an account without telling them.
The window between disclosure and exploitation is usually narrow. Security researchers publish details so website owners can patch. But bad actors are watching too. They're reading the same advisories and probing affected sites within hours.
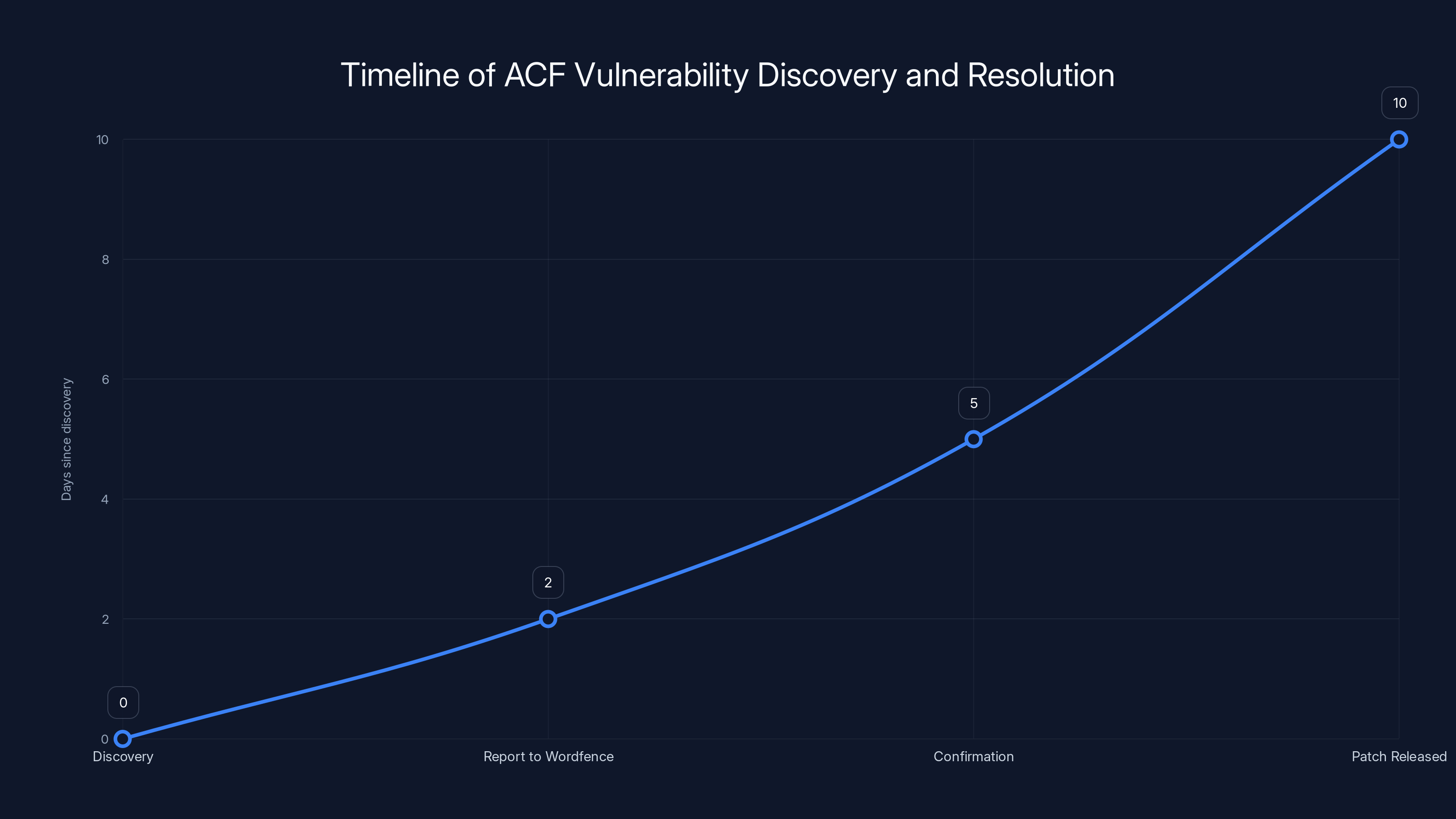
Estimated timeline shows that the ACF vulnerability was patched within 10 days of discovery, highlighting a swift response by Wordfence and developers.
Who's Actually Vulnerable: The Specific Conditions
Not every ACF: Extended installation is vulnerable in the same way. The vulnerability requires a specific setup, which is important to understand because it determines your actual risk level.
You're vulnerable if all of these are true:
You're running Advanced Custom Fields: Extended version 0.9.2.1 or earlier. (Check your Plugins page to see your version.)
You have created at least one form that includes "Create User" or "Update User" functionality. This form appears publicly on your website, not hidden behind an admin panel.
That form has a field mapped to the user's role. This is the critical piece. If you never added a role field to your user forms, you're not vulnerable even if you haven't updated.
The form is accessible without authentication. If your form is behind a login page or restricted to certain user roles, your risk is lower (but not zero).
Let me explain why the form needs to be public. The vulnerability requires unauthenticated access. If your form requires you to be logged in, then you're already a known user in the system. The attacker would need to escalate from a lower privilege (like "subscriber" or "contributor") to administrator. That's still bad, but it's a different threat model than a complete stranger taking over your site.
So what if you don't have a user role field in your forms? You're probably safe from this specific vulnerability. But you should still update, because the developers wouldn't have patched it if there wasn't a real problem.
What if you have a user form, but no role field? You're definitely safe from this vulnerability. Again, update anyway. There might be other bugs.
What if your user forms are behind a login page? Your risk is significantly lower, because the attacker needs to already have access to your site. But if someone has compromised a low-privilege account (like a subscriber or contributor), this vulnerability could let them escalate to admin. That's still a serious problem.
The Patch Explained: What Version 0.9.2.2 Actually Fixed
The developers behind ACF: Extended didn't sit around. Once Wordfence notified them of the vulnerability, they worked fast to ship a patch.
Version 0.9.2.2 introduced input validation for user role fields. Now, when a form is submitted with a role value, the plugin checks whether that role is actually valid and whether the current user has permission to assign that role. If they don't, the form doesn't process.
It's a simple fix conceptually, but it's a critical one. The code now enforces what should have been enforced from the start.
But here's the thing: the patch only protects you if you actually install it.
WordPress plugins have two ways updates can happen. Either you have automatic updates turned on, in which case the patch installs itself when you're not looking, or you have to manually update by clicking the "Update" button in your Plugins page.
Many WordPress administrators disable automatic updates because they're worried about plugins breaking their site. That's a legitimate concern—updates do sometimes cause compatibility issues. But it creates a security risk. You're trading update convenience for security vulnerability.
The patch itself doesn't require any configuration changes on your part. You don't need to reconfigure your forms. You don't need to change your database. You just update the plugin version, and you're protected.
If you've already installed version 0.9.2.2 or later, you're done with this particular vulnerability. But you should still audit your site for any damage that might have occurred before you patched.

Updating the plugin, auditing admin users, checking plugins/themes, and using a security scanner are equally important steps to secure your WordPress site. Estimated data based on typical security recommendations.
Checking Your Installation: Step-by-Step Audit Process
Let me walk you through exactly how to check whether you're vulnerable and whether you've been exploited.
Step 1: Check Your Plugin Version
Log into your WordPress dashboard. Go to Plugins on the left sidebar. Find "Advanced Custom Fields: Extended." Look at the version number displayed next to it. If it says 0.9.2.2 or higher, you're patched. If it says 0.9.2.1 or lower, you need to update immediately.
If you don't see ACF: Extended at all, you probably don't use it, so this vulnerability doesn't affect you. (Though you might use the regular Advanced Custom Fields plugin, which is different.)
Step 2: Check Your Forms
If you are on a vulnerable version, check whether you actually have any public user creation or user update forms. In your WordPress dashboard, look for the ACF: Extended settings (usually under Custom Fields or a dedicated menu). Look for forms. Check whether any of them are marked as "public" or "enabled on frontend." Check whether any of them have a field mapped to "User Role."
If you don't have this specific form configuration, you're probably not vulnerable even on an old version. But update anyway—security updates exist for a reason.
Step 3: Review Your Admin Accounts
This is the most important step. Even if you've patched, you need to check whether anyone exploited the vulnerability before you patched.
Go to Users in your WordPress dashboard. Look at your list of administrator accounts. Do you recognize all of them? When were they created? If you see an admin account you didn't create, with a creation date that coincides with when you were running the vulnerable version, that's a red flag.
Click on each suspicious admin account to see more details. Check the email address. Check when they last logged in. Check whether they changed any settings.
If you find a suspicious account, don't delete it yet. First, take a screenshot. Check your server logs to see what IP address the account was created from. Preserve evidence. Then delete the account and change your admin password immediately.
Step 4: Check Your Theme and Plugins
If someone had admin access, they could install malware in your theme or plugins. Go to Themes in your dashboard and check whether you recognize the theme. If you see an unfamiliar theme, that's suspicious. Go to Plugins and look for any plugins you didn't install. Delete anything that looks wrong.
Be careful, though. Sometimes plugins are installed automatically by other plugins or by hosting providers. When in doubt, check your hosting provider's documentation.
Step 5: Scan Your Site
Use a WordPress security plugin to scan your site for malware. Wordfence has a free version that scans for known malware. Sucuri has a free malware scanner. MalCare, iThemes Security, and others all have scanning capabilities. These tools look at your files and database for known malicious code.
Note that these scanners aren't perfect. They can miss sophisticated malware. But they'll catch most common attacks.
Step 6: Check Your File Modification Dates
This is more technical, but if you have access to your server via FTP or SSH, look at the modification dates on your theme files and plugin files. If core files were modified on a date that coincides with when the vulnerability was active on your site, something is wrong.
Most WordPress themes and plugins get updated pretty regularly, so modified dates move around. But if you see a suspicious pattern—like all your theme files modified on the same date when you weren't updating anything—that's worth investigating.

Updating to the Patched Version: Detailed Instructions
Okay, so you've checked and you're on a vulnerable version. Here's exactly how to update.
For WordPress Dashboard Updates
Log into your WordPress dashboard. Go to Plugins. You should see a notification on the ACF: Extended plugin saying "There is a new version available." Click "Update now."
WordPress will download the new version, back up your current version, and activate the new code. This usually takes less than a minute.
After the update completes, verify that ACF: Extended is still activated (you'll see "Deactivate" button if it is). Go back to the Plugins page and confirm the version number now shows 0.9.2.2 or higher.
If You Don't See an Update Available
Sometimes WordPress doesn't check for updates immediately. You can force it. Go to Dashboard > Updates. You should see an "Update Plugins" button. Click it. WordPress will fetch the latest information about available updates and show you what's available.
If you still don't see ACF: Extended in the updates list, you might be on a very old version that's no longer supported, or you might not actually have the plugin installed. Double-check your Plugins page.
For Manual Updates via FTP/SFTP
If you can't update through the dashboard (sometimes happens with custom hosting setups), you can update manually.
Download the latest version of ACF: Extended from the official WordPress plugin repository or from the plugin developer's website. Extract the ZIP file on your computer. Using FTP or SFTP (ask your hosting provider which one to use), connect to your server. Navigate to /wp-content/plugins/ and delete the "acf-extended" or "advanced-custom-fields-extended" folder. Upload the new version's folder to the same location. That's it.
Then log into WordPress and verify the plugin still shows as activated and the version is correct.
After You Update
Once the update is complete, test your forms to make sure they still work. If you have user creation or update forms on your site, submit a test form. Make sure the form processes correctly and creates/updates the user as expected.
If something breaks after the update, you can downgrade. But you absolutely need to be on 0.9.2.2 or later for security. If the update breaks something critical, contact your hosting provider or the plugin developer for help.

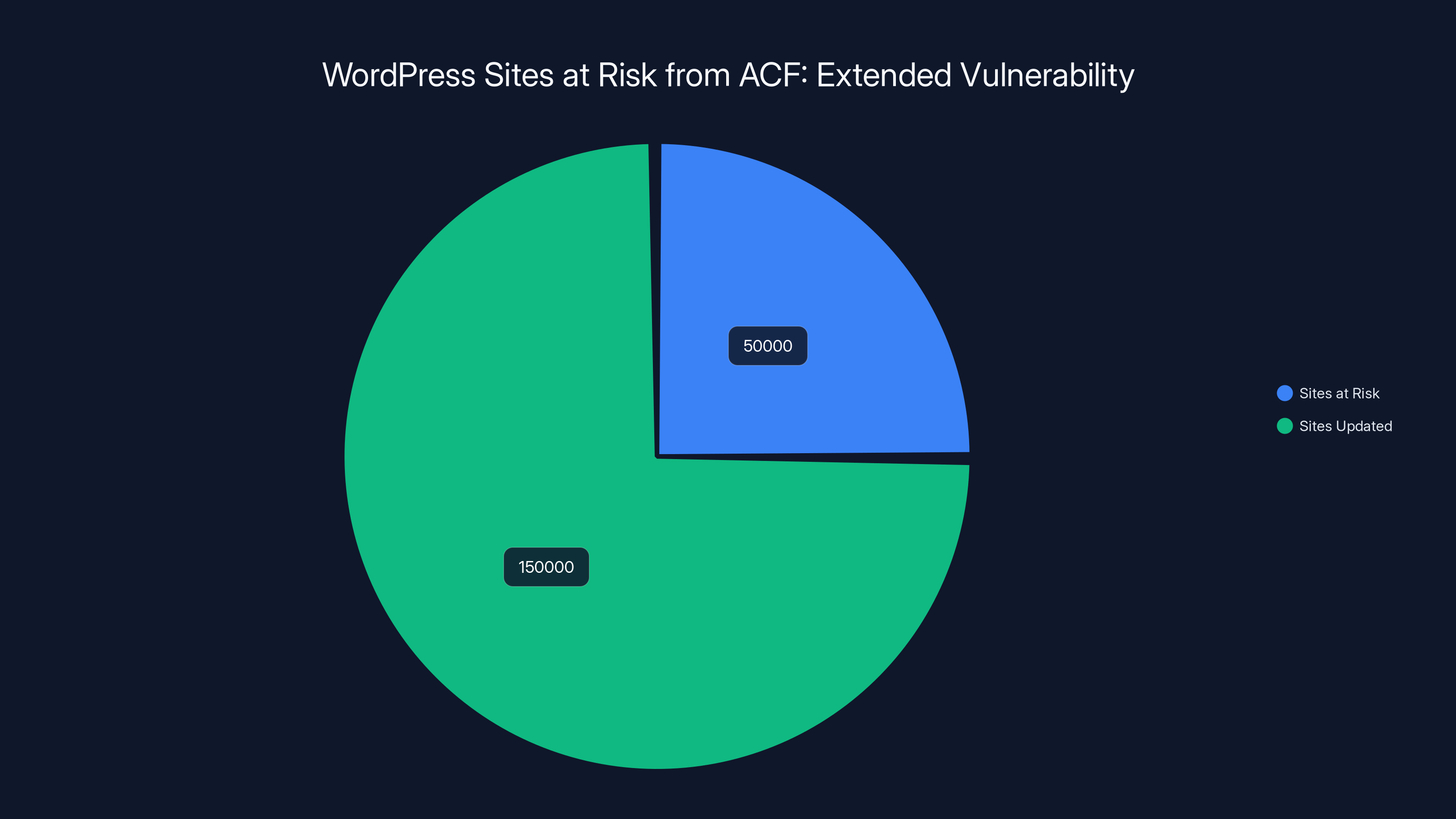
Approximately 50,000 WordPress sites remain at risk due to not updating to the patched version, representing a significant portion of the user base.
Preventing Similar Vulnerabilities: Best Practices
This vulnerability highlights a broader problem: WordPress plugins are often developed by individuals or small teams with limited security resources. Not every developer follows security best practices. That means you need to protect yourself by choosing plugins carefully and staying vigilant.
Choose Trusted Plugins
When you're evaluating a WordPress plugin, check its download count and user ratings on the WordPress plugin repository. A plugin with 100,000+ active installations and 4.5+ stars has a lot of eyes on it. That doesn't guarantee security, but it's a good sign.
Check the plugin's support forum on WordPress.org. Are developers responding to reported bugs? Do they seem to care about security?
Check the "active installs" count. If a plugin suddenly shows a huge drop in active installs after a security vulnerability, that's a red flag. It might mean the developer abandoned it.
Enable Automatic Updates for Security Patches
I mentioned this before, but it's worth repeating. Configure your WordPress installation to automatically update plugins when security patches are available. If you're worried about compatibility issues, test updates on a staging site first. But definitely get patches installed.
Most WordPress hosting providers (like WP Engine, Kinsta, SiteGround) allow you to configure this in their dashboard. If you're self-hosting, you can configure WordPress directly by adding this to your wp-config.php file:
php// Enable automatic updates for plugins, only security patches
define( 'AUTOMATIC_UPDATER_DISABLED', false );
define( 'WP_AUTO_UPDATE_CORE', 'minor' );
Use a WordPress Security Plugin
A dedicated security plugin can help catch exploitation attempts and scan for malware. Wordfence, Sucuri, iThemes Security, and MalCare all have free versions with useful features. The paid versions offer advanced protection like firewalls and activity logging.
I'd recommend at least using the free version of Wordfence or Sucuri. It gives you peace of mind and catches obvious problems.
Keep WordPress Core Updated Too
Don't just update plugins. Keep WordPress core (the main WordPress software) updated as well. Enable automatic updates for WordPress minor and major versions. Critical security fixes in WordPress core are released regularly.
Minimize Plugin Count
Every plugin is potential attack surface. Install plugins because you need them, not because they sound cool. If you have plugins you're not actively using, deactivate them. If you're sure you won't need them, delete them.
I've seen WordPress sites running 30+ plugins. That's excessive. Most sites should need 8-12 plugins maximum. Keep it lean.
Use a Web Application Firewall (WAF)
A WAF sits between your website and the internet, filtering malicious requests before they reach your WordPress installation. Cloudflare, Wordfence Premium, and other services offer WAF protection. They can block known attack patterns and protect against common vulnerabilities.
For basic protection, Cloudflare's free tier is solid. For WordPress-specific protection, Wordfence Premium is worth the $200/year cost if you're running a business-critical site.
Regular Backups Are Non-Negotiable
If you do get exploited and don't catch it immediately, a good backup lets you roll back to before the compromise. Most hosting providers include automatic backups. Make sure your backups are:
- Automated (daily minimum)
- Offsite (not on the same server as your website)
- Tested (actually verify you can restore from a backup)
- Retained for at least 30 days
Monitor Your Admin Users
Set up alerts for new admin accounts being created. Check your admin user list monthly. If you find a user you don't recognize, delete them immediately.
Some security plugins can log all user management changes, which helps if you're investigating an attack.

Timeline: What Happened and When
Understanding the timeline helps you assess your risk level based on when you updated.
Mid-December 2025: Security researcher Andrea Bocchetti discovers the vulnerability in ACF: Extended and reports it to Wordfence for responsible disclosure.
The researcher and Wordfence work with the plugin developers to create a fix.
Patch released: Version 0.9.2.2 is released with the vulnerability fix.
Disclosure date: Wordfence publishes a public advisory explaining the vulnerability. This is the moment the problem becomes widely known.
Post-disclosure window: The period when the vulnerability is public but not widely exploited. This is the most critical window—patches are available, but many site owners haven't installed them yet. Attackers are probing for vulnerable sites.
Current status: At the time of this article, approximately 50,000 sites have updated. Approximately 50,000 have not. No confirmed wild exploitations have been reported, but that doesn't mean attempts haven't been made.
If you're reading this article weeks after the vulnerability was disclosed, the risk is lower than it is right now. More people have updated. Automated scanners have likely found most vulnerable sites. But the risk is still real if you haven't patched.

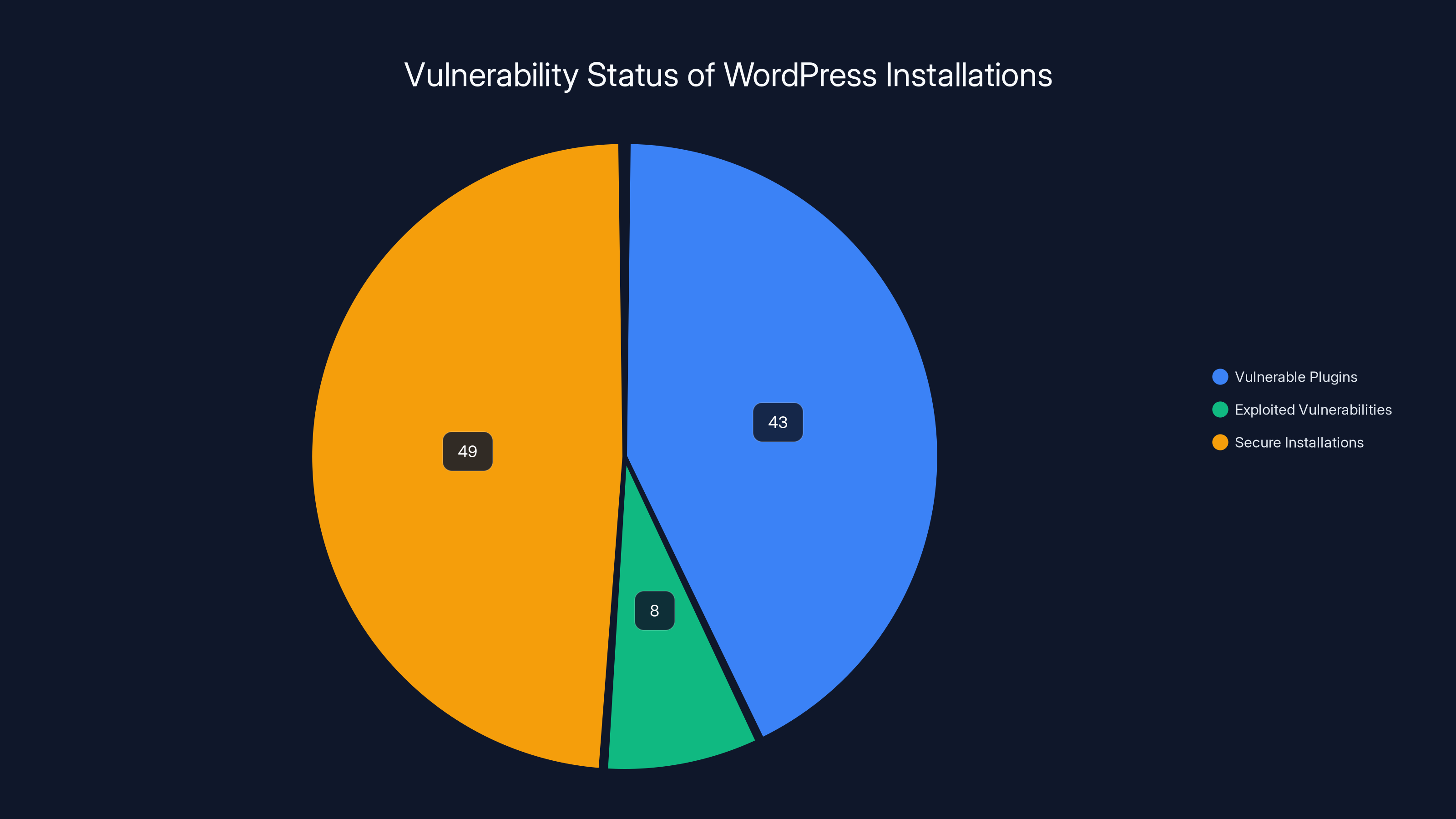
Approximately 43% of WordPress installations have at least one vulnerable plugin, but only 8% have vulnerabilities actively being exploited. Estimated data.
Protecting Your Users' Data: Privacy Considerations
If your site was exploited, you need to think about your users' privacy and legal obligations.
If an attacker had admin access to your WordPress site, they could have accessed:
- User account information (names, emails, phone numbers)
- Any personal information submitted through forms
- Customer data if you're running an e-commerce site
- Private messages or customer support conversations
- File uploads
- Any other data stored in your WordPress database
If you discover that your site was compromised, you likely have legal obligations to notify users, depending on where you operate and what data you store.
In the EU, GDPR requires notifying users if their personal data has been compromised. In California, CCPA requires notification. Many other jurisdictions have similar laws.
Here's what you should do:
- Determine exactly what data was accessed
- Assess the risk to users (was it sensitive data?)
- Consult with your legal team or a lawyer
- Send users a notification explaining what happened, what data was affected, and what they should do (like change their password)
- Document everything for regulatory purposes
This is serious business. If you discover a compromise, don't take it lightly.

Using AI-Powered Tools for WordPress Security Monitoring
Speaking of staying protected, many WordPress administrators are now using AI-powered tools to monitor their sites for unusual activity and security threats. Tools that can automate threat detection, generate security reports, and help manage your security posture are becoming increasingly valuable as WordPress environments grow more complex.
Platforms like Runable can help automate security monitoring workflows and generate detailed security reports about your WordPress installation. For instance, you could set up an automated workflow that generates daily security scans, compiles vulnerability reports, and creates documentation of your plugin inventory and versions.
While Runable isn't a security plugin itself, it can help you automate the administrative side of security management—creating reports, documenting your patch history, and maintaining records of security audits. Starting at $9/month, it's an affordable way to build automated security documentation workflows.
Use Case: Automate daily WordPress security scans and generate vulnerability reports with AI-powered documentation.
Try Runable For Free
What Happens If You Ignore This Vulnerability
Let me be blunt about what happens if you don't patch.
If you're running a vulnerable version and someone exploits it, you could lose everything. Your website gets defaced. Your customer data gets stolen. Malware gets injected so attackers can get back in later. Your site gets delisted from Google search results for distributing malware. Your reputation takes a hit. You might face legal liability.
I talked to one WordPress administrator whose site was compromised through a similar vulnerability. The attacker installed a credit card skimmer that stole customer payment information. By the time the site owner discovered it, hundreds of customers had been affected. The cleanup cost thousands of dollars. The reputational damage lasted months.
That's the real-world cost of not patching.
Compare that to the cost of updating right now: five minutes of your time. That's it. The benefit is tremendous. The effort is minimal.
There's no reason not to patch immediately.

Future Vulnerabilities: What This Teaches Us
This vulnerability is far from the first, and it won't be the last. It highlights some perennial problems in WordPress security.
First, plugins are often developed without rigorous security review. The WordPress plugin ecosystem is massive and decentralized. Anyone can publish a plugin. Most are safe, but some have basic security flaws that code review would catch immediately.
Second, site owners are slow to update. Even after a security patch is available, many sites run old versions for weeks or months. Some never update. This creates an extended window where millions of sites are vulnerable.
Third, the attack surface keeps growing. As WordPress plugins become more feature-rich, they become more complex. More complexity means more potential bugs. More bugs means more vulnerabilities.
This suggests a few takeaways for the future:
Stay proactive about security. Don't wait for a vulnerability to affect you. Implement best practices now.
Choose plugins from trusted developers with good security track records. Do your research.
Enable automatic security updates. You can't stay on top of every vulnerability manually.
Monitor your site actively. Use security plugins. Check your admin users. Review your file logs. Catch problems early.
Consider using platforms that abstract away some of the complexity. Managed WordPress hosting services like WP Engine, Kinsta, and Pressable handle many security concerns for you.
The WordPress ecosystem isn't going away. It powers about 43% of the web. But that also means it's a target. Security needs to be a constant priority, not an afterthought.
Reporting Additional Vulnerabilities: How It Works
If you discover a security vulnerability in a WordPress plugin, you have a responsibility to report it responsibly. Here's how the process works.
Don't post about it on social media or a public forum. Attackers are watching for vulnerability disclosures. If you reveal a vulnerability publicly before a patch exists, you're giving attackers a roadmap.
Instead, look for the plugin developer's security contact information. This is usually in the plugin documentation or on their website. Report the vulnerability directly to them, not publicly.
Give them reasonable time to patch. Industry standard is 90 days. If they don't respond, you can escalate to Wordfence, which helps with WordPress plugin security.
When reporting, include:
- A clear description of the vulnerability
- Steps to reproduce it
- The impact (what can an attacker do?)
- Your suggested fix (if you have one)
- Your contact information so they can follow up
Responsible disclosure protects everyone. It gives developers time to patch before attackers can exploit the vulnerability widely.
Industry Response and Coordinated Disclosure
One thing that worked well with this vulnerability is the coordinated disclosure process. Wordfence was notified before public disclosure. They worked with the developers to create a patch. The patch was released before the vulnerability became widely public.
That's how the system is supposed to work. Not every vulnerability gets this treatment, but when it does, it significantly reduces the window where site owners are exposed.
Wordpress.org also plays a role. They host the official plugin repository, and they coordinate with security researchers and plugin developers to manage vulnerabilities responsibly.
If you're developing a WordPress plugin, this is worth emulating. Have a security contact email. Respond quickly to security reports. Release patches promptly. Communicate clearly with your users about what's been fixed.
If you're a site owner, appreciate that the system worked in this case. But don't rely on it. Update proactively anyway.

FAQ
What exactly is the Advanced Custom Fields: Extended plugin?
Advanced Custom Fields: Extended (ACF: Extended) is a WordPress plugin that expands the functionality of the core Advanced Custom Fields plugin. It adds features like user registration and profile forms, custom post types, and advanced field options. It's used by over 100,000 WordPress sites to create custom data structures without coding.
How do I know if my WordPress site is vulnerable?
Your site is vulnerable if you're running ACF: Extended version 0.9.2.1 or earlier AND you have a public "Create User" or "Update User" form with a role field mapped to it. Check your Plugins page in WordPress to see your version. Look at your site's frontend to see if you have such forms. If you don't have this specific form configuration, you're probably not vulnerable.
What should I do right now if I'm vulnerable?
Update ACF: Extended to version 0.9.2.2 or later immediately. Go to your WordPress dashboard, navigate to Plugins, find ACF: Extended, and click "Update now." The update takes less than a minute. After updating, audit your admin users list for any suspicious accounts you didn't create.
Can I be exploited if my user form is password-protected?
Your risk is significantly lower if your form requires authentication. The vulnerability allows unauthenticated users to escalate to admin. If users are already logged in, they might be escalating from a lower privilege like "subscriber" to "administrator," which is still bad but requires them to already have access to your site. However, you should still update because this would still be a serious privilege escalation risk.
What if I've already updated? Do I need to do anything else?
Yes. Update is step one, but not the only step. Audit your admin users to see if anyone created unauthorized accounts while you were vulnerable. Check your Plugins and Themes lists for anything unfamiliar. Use a security scanner to look for malware. Check your server logs if you have access. If you find suspicious activity, clean it up immediately.
How do I prevent vulnerabilities like this in the future?
Enable automatic updates for security patches, minimize your plugin count and choose trusted plugins, use a WordPress security plugin like Wordfence to monitor for attacks, keep regular backups so you can recover from compromise, and monitor your admin users list for unauthorized accounts. Also, consider using managed WordPress hosting if you want someone else handling security infrastructure.
Is my data safe if my site was compromised?
If an attacker had admin access, they could have accessed anything in your WordPress database: user information, customer data, file uploads, etc. If you discover you were compromised, you should notify your users (this might be legally required depending on your jurisdiction and the data you store). Consult with your legal team about notification requirements and liability.
What's the difference between the free Advanced Custom Fields plugin and ACF: Extended?
Advanced Custom Fields (ACF) is the base plugin developed by Elliot Condon that adds custom field functionality. ACF: Extended is a separate plugin by other developers that adds additional features on top of ACF, like user creation forms and more field types. Only ACF: Extended has this vulnerability. If you use regular ACF, this vulnerability doesn't affect you.
How was this vulnerability discovered?
Security researcher Andrea Bocchetti discovered the vulnerability and reported it to Wordfence, a WordPress security company, using responsible disclosure practices. Wordfence coordinated with the plugin developers to create a patch before publicly disclosing the vulnerability. This responsible process helped minimize the window where sites were vulnerable without patches available.
What should I do if I find an unauthorized admin account?
Don't delete it immediately. Take screenshots and notes. Check your server logs to see what IP address created the account and what the account has been doing. Review what posts, pages, plugins, or themes it modified. Delete the account only after you've gathered evidence. Change your admin password afterward. If you suspect active compromise, take your site offline and contact your hosting provider's security team.

Conclusion: Act Now, Stay Safe
Let's cut through the noise. This vulnerability is real, it's serious, and it's easy to fix.
You have a 50,000-site problem right now. Those sites are running outdated code that has a trivial-to-exploit privilege escalation vulnerability. If you're one of them, you need to update today. Not tomorrow. Today.
The good news: it takes five minutes. The WordPress dashboard will walk you through it. No technical skills required. No downtime necessary.
After you update, do the audit I described. Check your admin users. Look for suspicious plugins or themes. Scan with Wordfence or Sucuri. It'll take 20 minutes. That's the difference between "site that got compromised and destroyed" and "site that was fine."
Then, implement the best practices I outlined. Automatic updates. Minimal plugin count. Security plugin active. Regular backups. Monitoring. These aren't optional if you care about your WordPress site.
WordPress powers millions of websites. Small businesses, nonprofits, enterprises. All of them are potential targets. The plugin ecosystem is powerful but imperfect. You have to protect yourself.
This vulnerability won't be the last one. But you can prepare for future ones by staying vigilant now.
Update today. Audit today. Then implement the practices that keep you safe every day going forward.
Your website will thank you.

Key Takeaways
- ACF: Extended versions 0.9.2.1 and earlier have a critical privilege escalation vulnerability (CVE-2025-14533) affecting approximately 50,000 WordPress sites
- The vulnerability allows unauthenticated users to set themselves as administrators through a form submission if a role field is present, enabling complete site takeover
- Immediate action: Update to version 0.9.2.2, audit admin users for unauthorized accounts, and scan for malware using security plugins like Wordfence
- Sites need specific form configuration (Create User or Update User forms with role fields) to be exploitable, though all installations should update regardless
- Implement defensive WordPress security practices: automatic updates, minimal plugin count, security plugins, regular backups, and continuous monitoring of admin accounts
![WordPress Plugin Security Flaw Affects 50,000 Sites: Complete Protection Guide [2025]](https://tryrunable.com/blog/wordpress-plugin-security-flaw-affects-50-000-sites-complete/image-1-1769026165540.jpg)



