The WordPress QSM Plugin Crisis: 40,000 Sites at Risk
Last week, something quietly landed in the WordPress security community that should have everyone's attention. A popular quiz plugin called Quiz and Survey Master—or QSM if you're in the know—was found to have a gaping SQL injection vulnerability that affects over 40,000 active installations. This isn't some obscure plugin nobody uses. This is software that helps websites create interactive quizzes, surveys, and forms without touching a line of code.
Here's what makes this scary: the flaw doesn't require any sophisticated hacking. Any user with a basic "subscriber" account—which most WordPress sites hand out like candy—can weaponize it to steal databases, modify content, or worse. And the kicker? Nearly half of all sites running this plugin haven't patched it yet.
I spent the last few days digging into the technical details, checking vulnerability databases, and talking to security researchers. What I found is a masterclass in how WordPress plugins become security nightmares and why updating immediately isn't optional anymore.
Why This Matters More Than You Think
WordPress powers over 43% of all websites on the internet. That's not hyperbole—it's reality. And because WordPress is open source, the entire plugin ecosystem lives on a foundation of trust. Developers create plugins, submit them to the official repository, and thousands of website owners install them. When a flaw shows up in a popular plugin, it's not just one site at risk. It's thousands.
The QSM plugin sits at the intersection of convenience and vulnerability. Website owners love it because it requires zero coding. Marketing teams use it for lead generation. Publishers use it for engagement. But that ease-of-use also means many site owners aren't security-conscious enough to notice when a vulnerability drops.
According to security researchers, approximately 47.9% of QSM users are running version 10.3.1 or older—that's roughly 19,160 confirmed vulnerable sites. But that number only reflects sites actively reporting their version to WordPress.org. The real number could be significantly higher. Some estimates suggest the total vulnerable install base could exceed 25,000 sites.
Understanding the SQL Injection Vulnerability
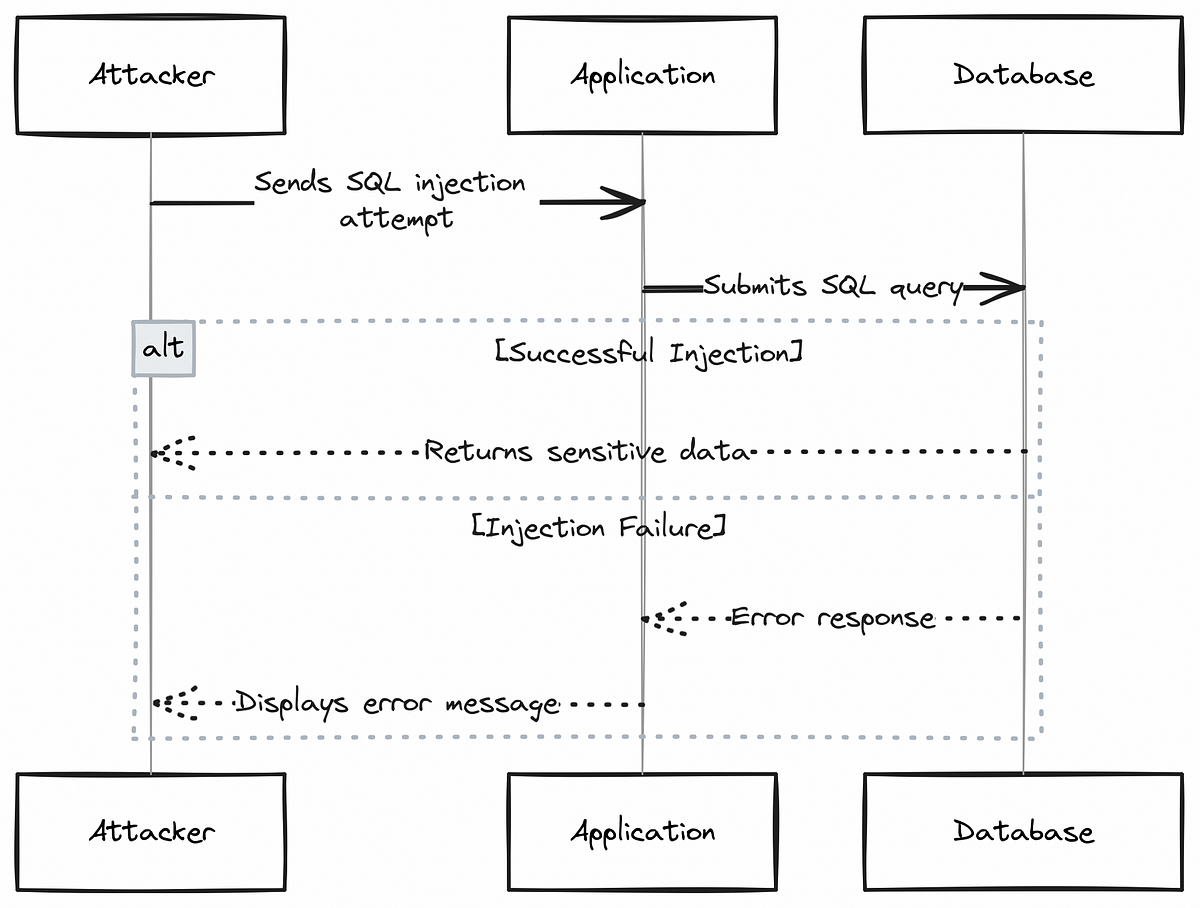
Let me break down what's actually happening here, because SQL injection sounds scary but it's worth understanding.
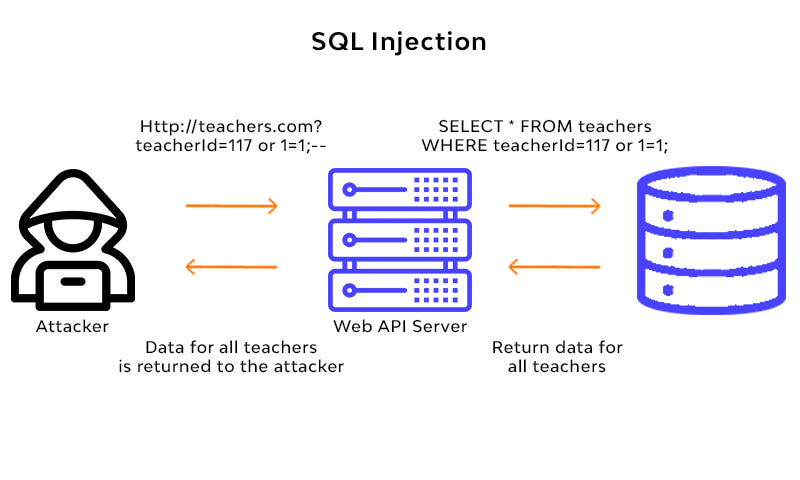
SQL is the language that talks to databases. When you submit a form on a website, the information you type gets converted into SQL commands that ask the database to store or retrieve data. The problem is, if that form doesn't "sanitize" your input—meaning it doesn't clean up what you type—attackers can inject their own SQL commands into your text.
Imagine a login form that asks for your username. Normally you'd type "john" or "jane." But what if someone types: ' OR '1'='1. If the site doesn't sanitize this, the database reads it as "show me all users where username is blank OR 1 equals 1" (and 1 always equals 1, so it shows everyone). That's the basic concept.
In the QSM vulnerability, attackers can inject SQL commands through form fields meant for survey responses. Since logged-in users can access this feature, they essentially get free reign to talk directly to the database. They can extract user credentials, see customer data, modify settings, or even upload malicious code.
The vulnerability was tracked as CVE-2025-67987 and affects all versions 10.3.1 and earlier. It was patched in version 10.3.2, released when the security advisory went public.
How the Vulnerability Actually Works in Practice
The QSM plugin creates survey and quiz forms that users fill out. Behind the scenes, those responses get stored in the WordPress database. The vulnerability exists in how QSM processes and stores these responses.
When a logged-in user submits a quiz response, they can manipulate the form data being sent to the server. Instead of submitting something harmless like "My answer is option C," they can inject SQL commands. Because QSM doesn't properly validate or escape this input before passing it to the database, the malicious SQL executes.
Here's what's critical: this requires someone with at least a "subscriber" account on your WordPress site. On some sites, that means customers, newsletter subscribers, or anyone who's registered. On other sites, registration might be closed. But many WordPress sites allow public registration specifically because they want users to participate in quizzes and surveys.
So the attack chain looks like this:
- Attacker creates a free account on a vulnerable site (or finds an existing subscriber account)
- They navigate to a quiz or survey form
- They intercept the form data being sent (using browser developer tools or a proxy)
- They inject SQL commands into the response fields
- The vulnerable QSM code sends this directly to the database without sanitization
- The attacker's SQL commands execute, giving them access to the database
From there, they could:
- Extract user tables containing email addresses and passwords
- Modify administrator accounts to create backdoors
- Access customer data, payment information, or sensitive business data
- Inject malicious code into pages that affects all site visitors
- Alter plugin settings to install ransomware or cryptominers
The scary part? This doesn't require any special tools or advanced hacking knowledge. It's something a moderately skilled attacker can execute in minutes.
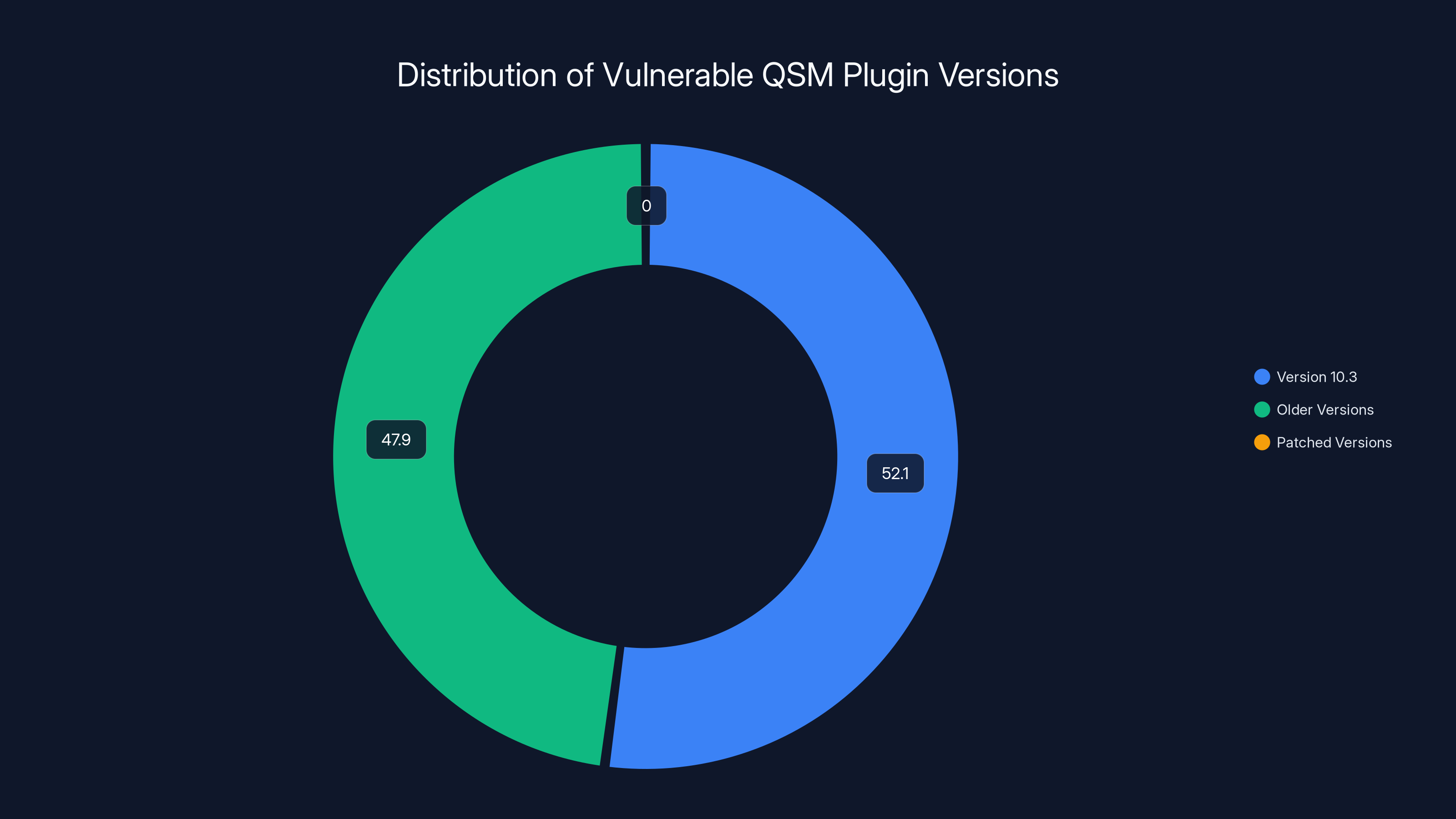
Approximately 52.1% of active QSM plugin users run version 10.3, which includes vulnerable versions, while 47.9% run older, also vulnerable versions. Estimated data suggests 25,000-30,000 sites may be affected.
The Scope: Which Sites Are Actually Vulnerable?
Let's talk numbers. The WordPress plugin repository shows that QSM has been installed over 1 million times. But "active installs" is different from "currently installed." The repository shows that approximately 40,000 sites actively use QSM right now.
Of those 40,000, here's the breakdown:
- 52.1% run version 10.3 (which includes the vulnerable 10.3.1)
- 47.9% run older versions—definitely vulnerable
- Remaining sites run version 10.3.2 or newer—patched
This means at minimum, 19,160 sites are confirmed vulnerable. But here's the problem: this data is incomplete. Many sites don't report their plugin versions, or they've disabled the plugin entirely and left it installed. The actual vulnerable population is probably closer to 25,000-30,000 sites.
Geographically, the vulnerable sites are spread globally. The affected plugin users span across the US, UK, Germany, Australia, Canada, and dozens of other countries. There's no concentration in any particular region, which makes this a truly international problem.
Industry-wise, these sites range from small business websites to media outlets to educational institutions. Anywhere that uses interactive quizzes or surveys becomes a target.
What Types of Data Are at Risk?
The actual data exposed depends on what each WordPress site stores. For a basic blog with minimal user data, the risk is lower. But for e-commerce sites, SaaS platforms, or membership sites, the exposure is severe:
- User credentials: Email addresses, usernames, password hashes
- Personal information: Names, addresses, phone numbers from user profiles
- Customer data: Purchase history, preferences, payment information
- Business data: Client lists, transaction records, internal communications
- Admin accounts: Credentials for WordPress administrators and editors
- Plugin settings: Database connection details, API keys, authentication tokens
Once attackers have this data, they can use it for identity theft, selling on dark web marketplaces, targeted phishing campaigns, or leveraging admin access for further attacks.
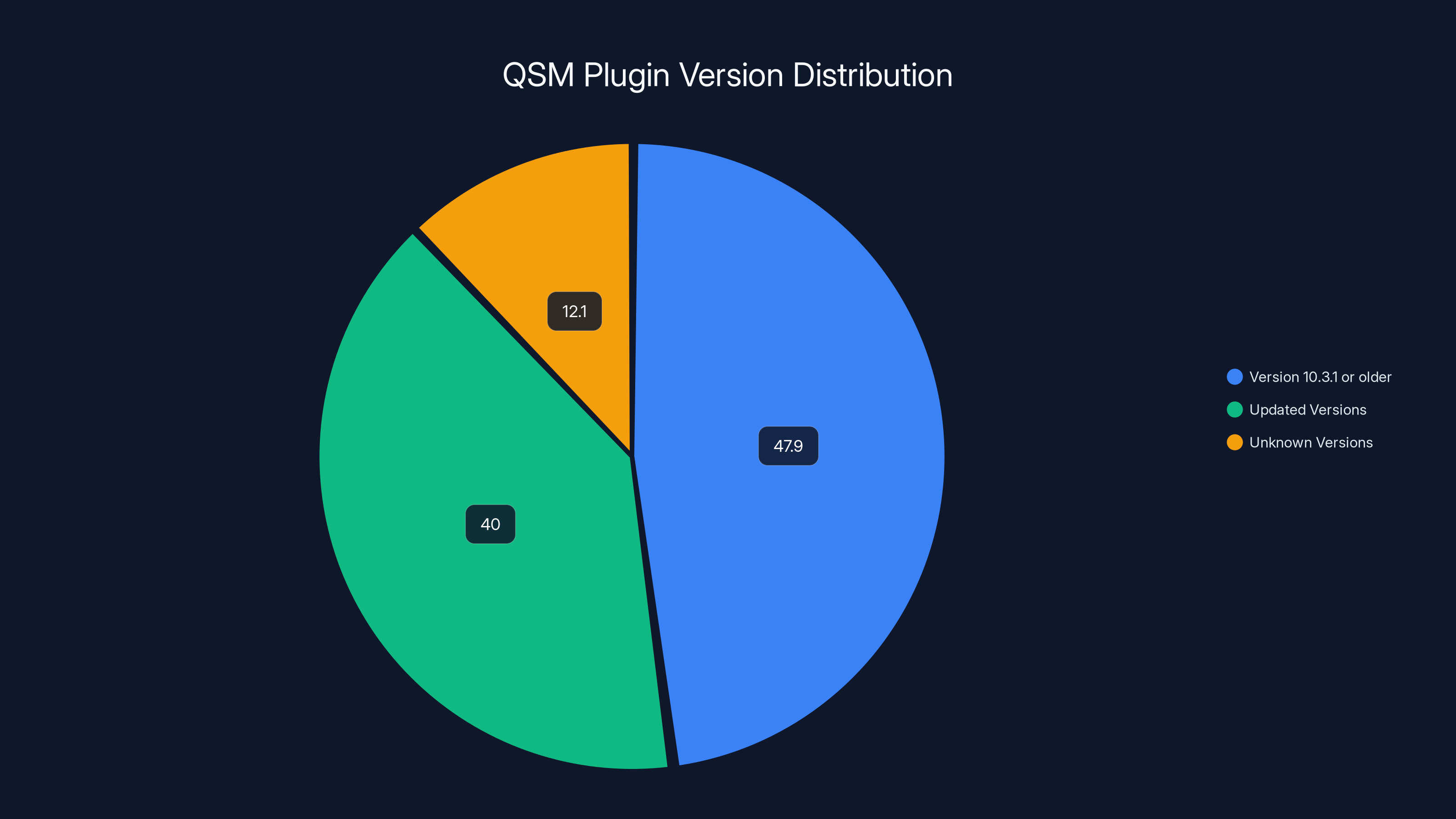
Nearly half of the QSM plugin users (47.9%) are running vulnerable versions, highlighting the critical need for updates. Estimated data.
The Timeline: How This Vulnerability Was Discovered and Disclosed
Security vulnerabilities don't just appear out of nowhere. They're either discovered by security researchers proactively hunting for bugs, or they're found when attackers exploit them in the wild.
In this case, the vulnerability was discovered by security researchers at Patchstack, a WordPress security platform that scans plugins for flaws. Patchstack follows responsible disclosure practices, which means they notify the plugin developers before going public with the details.
Here's how the process worked:
- Discovery phase: Patchstack identified the SQL injection flaw in QSM version 10.3.1
- Private notification: The research team contacted QSM developers with technical details
- Patch development: QSM developers created a fix (version 10.3.2) and prepared it for release
- Coordinated disclosure: After confirming the patch works, they released it publicly
- Public advisory: A security advisory was published warning site owners about the vulnerability
- Media coverage: Security news outlets picked up the story
This is the ideal process. Responsible disclosure gives site owners a window to patch before attackers can widely exploit the vulnerability. However, there's always a risk period—the time between when a patch is released and when site owners actually install it. During this window, attackers can see the patch, reverse-engineer what was fixed, and create exploits.
Why No One Noticed It Earlier
You might wonder why this vulnerability existed for so long without being caught. The answer reveals a fundamental weakness in the WordPress plugin ecosystem.
WordPress plugins are submitted to the official repository and reviewed by volunteer moderators. The review process looks for obvious security issues, but it's not as rigorous as professional security audits. Reviewers look for things like: Are files being uploaded safely? Are database queries using prepared statements? Are user permissions being checked?
The QSM vulnerability slipped through because:
- Complexity: The vulnerable code path isn't obvious on first glance. It's buried in survey response processing logic
- Limited scope: The vulnerability only triggers if specific conditions are met (logged-in user with certain permissions, specific form submission)
- Trust assumption: Reviewers assume that quiz/survey data isn't sensitive, so they don't scrutinize it as heavily
- Resource constraints: With over 58,000 plugins in the repository and limited volunteer reviewers, they can't check everything with forensic precision
This is why security researchers like Patchstack exist. They use automated scanning tools and manual code review to find flaws that slip through the official review process.
How to Check If Your Site Is Vulnerable
Okay, enough doom and gloom. Let's get practical. Here's how to determine if your WordPress site is affected.
Step 1: Check If You Have QSM Installed
First, you need to know if you're running the QSM plugin at all. Log into your WordPress admin dashboard and navigate to Plugins. Search for "Quiz and Survey Master" or "QSM." If it's not listed, you're safe from this particular vulnerability (but check your other plugins).
If you find it, note the version number displayed next to the plugin name. This is critical information.
Step 2: Identify Your Current Version
The vulnerable versions are 10.3.1 and all versions below it. So if you're running:
- Version 10.3.1 or earlier: YOU ARE VULNERABLE
- Version 10.3.2 or newer: YOU ARE PATCHED
- Version 10.3.5 (current as of early 2025): YOU ARE SAFE
If you're unsure, click the "View details" link on the plugin, and it will show you the exact version and changelog.
Step 3: Check Your User Permissions
While you're in the admin panel, check who has access to your site. Go to Users and look at the user list. If you have many users with "Subscriber" or "Contributor" roles, your attack surface is larger. Each of these users is a potential entry point for exploiting the QSM vulnerability.
Write down how many subscriber accounts you have. This helps you understand your risk level.
Step 4: Review Recent Database Activity
If you're paranoid (and you should be), check if the vulnerability has already been exploited. This requires some technical knowledge, but here's what to look for:
- Log into your hosting control panel (cPanel, Plesk, etc.)
- Access your database using phpMyAdmin or a similar tool
- Look at the QSM plugin tables—they usually start with
wp_qsm_ - Check the quiz responses table for suspicious entries with special characters like single quotes, dashes, or SQL keywords
- Look at WordPress user table (
wp_users) for unexpected admin accounts you didn't create
If you see suspicious data or new admin accounts you didn't authorize, you may have been compromised. This means you need to take immediate action (see the next section).
However, if this sounds too technical, you can hire a WordPress security company to do this audit for you. It typically costs $100-500 depending on your site size.
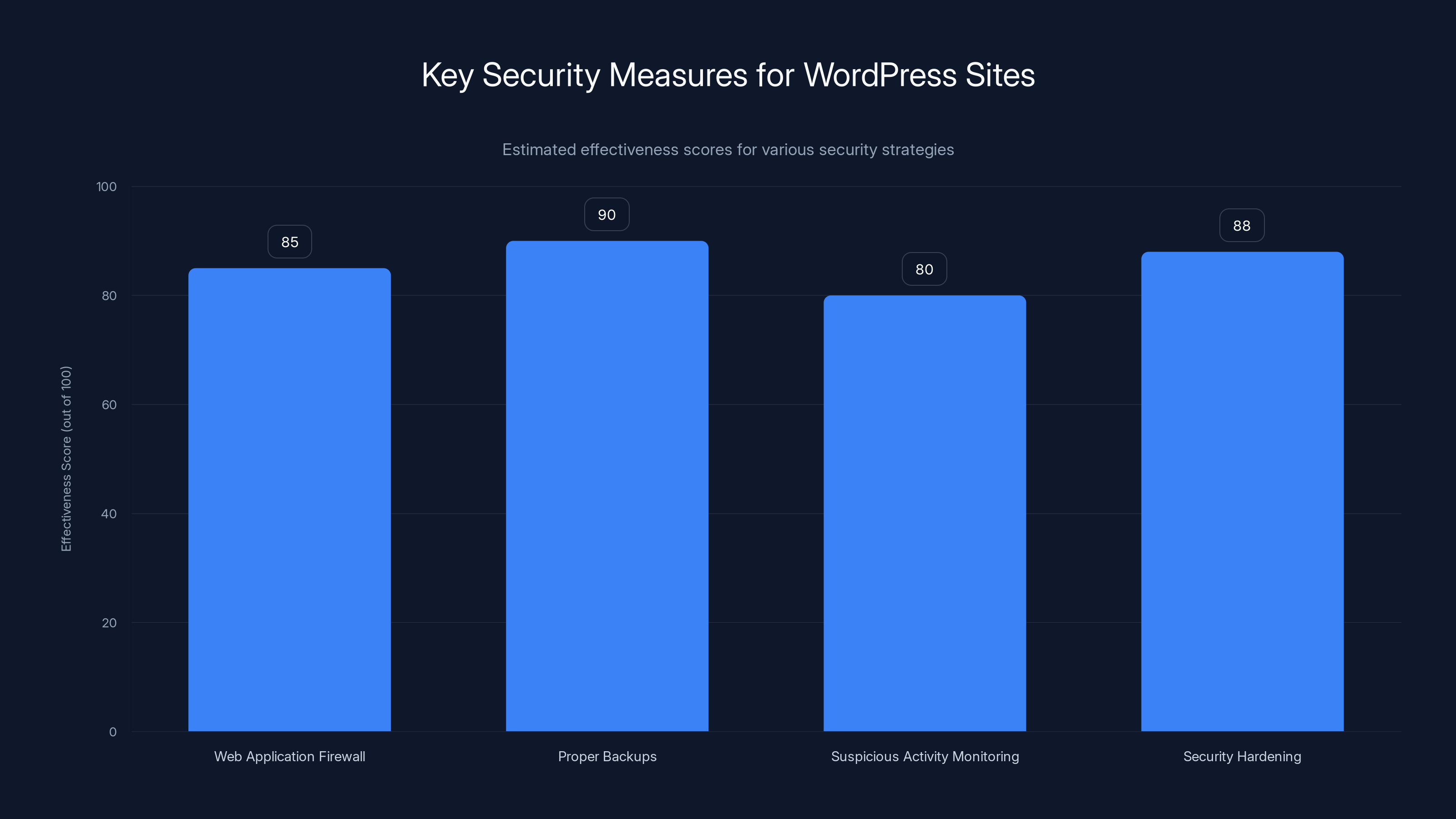
Implementing a combination of these security measures can significantly enhance the security posture of a WordPress site. Estimated data based on typical security assessments.
Immediate Actions: Patch Your Site Now
If you determined that your site is vulnerable, here's the step-by-step process to fix it. Don't delay on this.
Step 1: Backup Your Database and Files
Before touching anything, create a complete backup of your WordPress site. This includes your database and all files. If the patching process goes wrong, you need a rollback point.
Most hosting providers offer one-click backups. If yours doesn't, use a backup plugin like UpdraftPlus (free version is fine). Download a copy locally.
Step 2: Update QSM to the Latest Version
Go to Dashboard > Plugins > Installed Plugins. Find the QSM plugin and look for an update notification. If an update is available, click the "Update Now" link.
WordPress will automatically download version 10.3.2 or newer and update the plugin. The entire process usually takes under 60 seconds.
If no update appears, try:
- Click "View details" on the QSM plugin
- Go to the official QSM page to check the current version
- If they've released a newer version, you might have a caching issue. Clear your WordPress cache and refresh
- If still stuck, you can manually upload the latest version via FTP
Step 3: Verify the Update
After updating, verify the new version is installed. Go back to the Plugins page and confirm you're now running version 10.3.2 or higher.
Step 4: Change All Passwords
Important: Change your WordPress admin password immediately. If attackers exploited this vulnerability before the patch, they may have compromised your admin account.
- Go to Users > Your Profile
- Scroll to "Account Management"
- Click "Generate Password"
- Copy the new password, paste it somewhere safe, then click "Update Profile"
- Log out and log back in with the new password
Also change passwords for any administrator and editor accounts on your site. If you share admin access with others, notify them to change their passwords too.
Step 5: Run a Security Scan
Now run a comprehensive security scan using a plugin like Wordfence:
- Install Wordfence (free from the plugin repository)
- Go to Wordfence > Scan
- Click "Start a new scan"
- Wait for it to complete (usually 10-30 minutes depending on site size)
- Review any threats it finds and follow the remediation steps
Wordfence will scan for malware, suspicious files, database anomalies, and other security issues that may have resulted from the vulnerability.
Step 6: Check User Accounts
Go to Users and look for any accounts you don't recognize. Attackers sometimes create new admin accounts to maintain access. Delete any suspicious accounts immediately.
While you're there, consider disabling "Anyone can register" unless you specifically need it. This reduces your attack surface.
Broader WordPress Security: Why This Keeps Happening
The QSM vulnerability isn't unique. It's part of a pattern. WordPress has this weird dichotomy where it powers massive Fortune 500 websites and also powers hobby blogs. The same ecosystem serves both.
This creates an incentive problem. Plugin developers often prioritize features over security. They race to add new functionality, launch faster than competitors, and rush code to production. Security reviews and penetration testing cost money and slow down releases.
For free plugins especially, there's no revenue stream to fund rigorous security practices. Developers are often working part-time or maintaining plugins as side projects. They do the best they can, but best-effort security isn't good enough when you're protecting 40,000 websites.
The Plugin Vetting Problem
WordPress allows anyone to submit a plugin to the official repository. The review process filters out obvious malware and checks for some security patterns, but it's not a comprehensive audit. Once a plugin is approved, it can receive updates without the same level of scrutiny.
This is intentional. WordPress wants a low barrier to entry so developers can contribute. But it creates a security risk.
Compare this to Apple's App Store, where every app gets reviewed before release. Or Microsoft's Windows Store, where applications are scanned and verified. WordPress volunteers don't have the resources for that level of vetting.
The Update Adoption Problem
Even when security patches are released, many site owners don't install them immediately. Some sites are automated to update plugins, but others require manual updates. Site owners forget, or they're worried updates will break something.
The QSM vulnerability shows this in action: nearly 48% of users are running outdated versions weeks after a patch was released.
This is why WordPress has been moving toward automatic security updates. But even with automation enabled, some sites use configurations where automatic updates don't work. Websites using custom code, heavily modified themes, or older server environments sometimes can't update safely.
The Credential Sprawl Problem
Here's something that compounds the issue: WordPress sites often have too many user accounts with too much permission. A typical WordPress site might have:
- 1-2 administrators
- 3-5 editors
- 10-50 contributors
- 100+ subscribers
Each of these subscribers is a potential attack vector. They don't need to be malicious—their account just needs to be compromised. An attacker can use a subscriber account the same way the legitimate subscriber would, except they're injecting SQL instead of answering quizzes.
Best practice is to minimize user accounts. Delete accounts for people who no longer need access. Use "Contributor" roles instead of "Editor" when possible. Reserve "Administrator" for only those who truly need it.

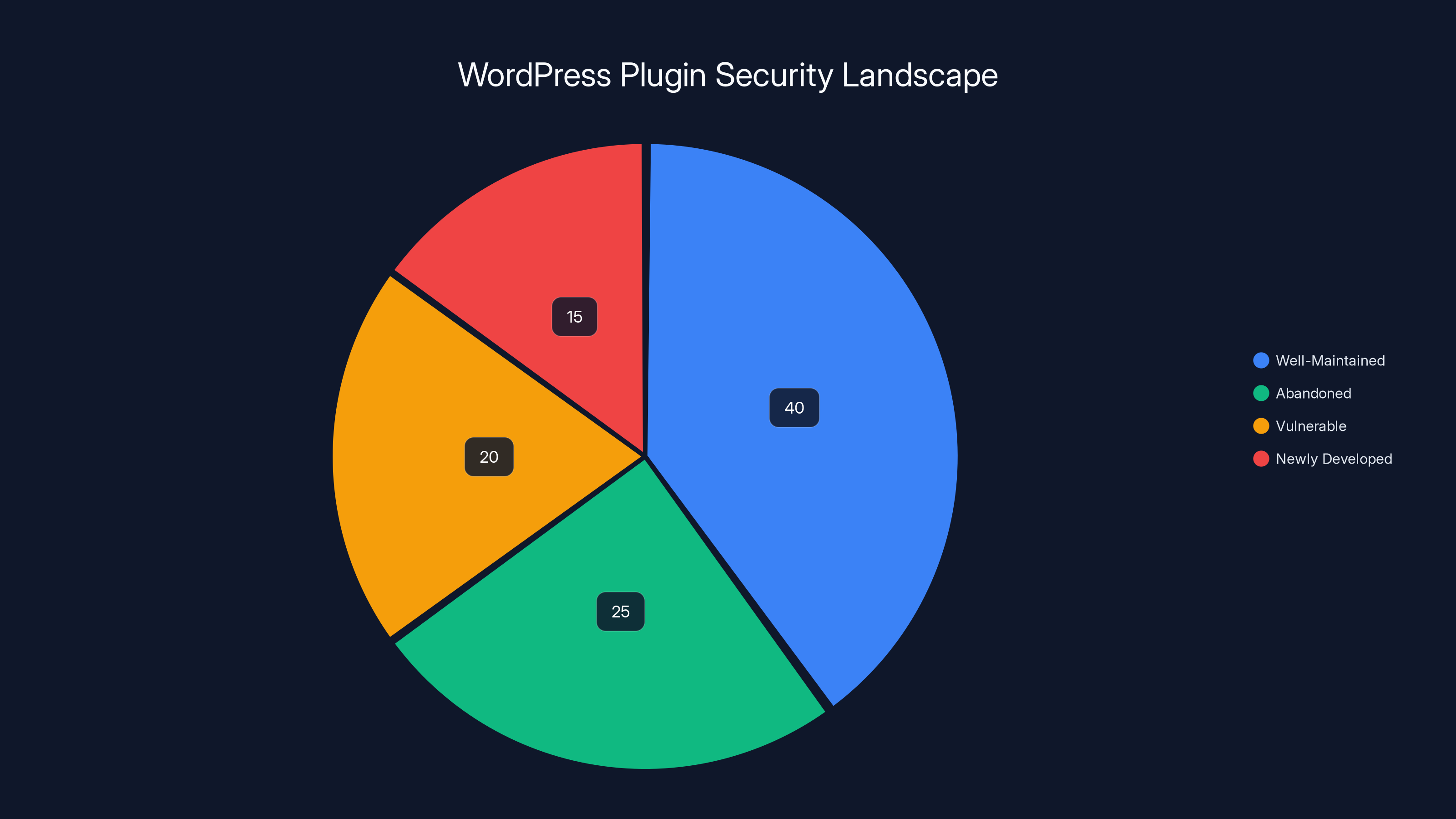
Estimated data shows that a significant portion of WordPress plugins may be abandoned or vulnerable by 2025, highlighting ongoing security challenges.
Long-Term Security Improvements: Beyond Just Patching
Patching is the immediate fix, but it's not a comprehensive security strategy. Here's what WordPress site owners should be doing to prevent future vulnerabilities from turning into disasters.
Use a Web Application Firewall (WAF)
A WAF sits between your site and the internet, filtering malicious traffic. It catches SQL injection attempts before they reach your WordPress installation. Services like Cloudflare, Wordfence Premium, or Sucuri offer WAF protection.
A WAF would have blocked the QSM SQL injection attempts by detecting the suspicious SQL commands in form submissions. Even if the plugin was vulnerable, the WAF would prevent exploitation.
Cost: $10-50/month depending on the provider and features.
Implement Proper Backups with Testing
Backups are your insurance policy. You should have:
- Daily backups stored off-site (not on the same server)
- Multiple backup versions (keep the last 30 days minimum)
- Regular restore tests to confirm backups actually work
If your site gets compromised, you can restore from a clean backup and get back online quickly. Without backups, you're looking at total data loss or paying ransoms.
Services like UpdraftPlus, BackWPup, or hosting-provided backups are good options.
Monitor for Suspicious Activity
Enable security monitoring that alerts you to suspicious activity like:
- Unexpected admin account creation
- Large database queries
- Unusual login patterns
- File modifications
- Failed login attempts
Wordfence and Sucuri provide these alerts automatically. Some send email notifications within minutes of detecting issues.
Security Hardening: The Layers Approach
Security experts talk about "defense in depth"—multiple layers of protection so if one layer fails, others catch the attack. For WordPress:
Layer 1: Updates
- Automatically update WordPress core, plugins, and themes
- Set up automatic update checks weekly
Layer 2: Access Control
- Change default admin username (not "admin")
- Use strong passwords (16+ characters, random)
- Enable two-factor authentication for admins
- Disable user registration if not needed
Layer 3: Monitoring
- Install security plugin (Wordfence, Sucuri, iThemes Security)
- Enable login attempt logging
- Get alerts for suspicious activity
Layer 4: Firewall
- Use Cloudflare or similar WAF service
- Block known malicious IP ranges
- Rate limit suspicious requests
Layer 5: Regular Audits
- Scan for malware weekly
- Review user accounts monthly
- Check plugin list quarterly (remove unused plugins)
If an attacker gets past layer 1 (updates), layer 2 blocks them. If they bypass that, layer 3 detects them. And so on.
The QSM Plugin's Response and Future Updates
QSM developers released version 10.3.2 to patch the SQL injection vulnerability. But what about the underlying security culture?
In responsible plugin development, fixing a vulnerability isn't the end of the story. Smart developers then audit similar code, implement automated security testing, and adjust their development process to prevent similar issues.
The ideal scenario would be if QSM developers:
- Conduct a full security audit of the codebase
- Implement prepared statements for all database queries (not just the vulnerable ones)
- Add automated security scanning to their build pipeline
- Hire a third-party security firm for annual penetration testing
- Document their security practices so users know they're taking it seriously
Some plugin developers do this. Others patch and move on. Without visibility into QSM's internal processes, we can't know which approach they're taking.
For users, this uncertainty means relying on third-party monitoring. Services like WPScan, Patchstack, and Sucuri continuously scan plugins for new vulnerabilities. If QSM develops another security issue, these services will catch it and alert site owners.
Version Management Going Forward
QSM continues releasing updates. As of early 2025, version 10.3.5 is the latest. Each subsequent version likely includes bug fixes and minor improvements on top of the security patch.
If you've updated to 10.3.2 or newer, you're protected from this specific vulnerability. But you should continue updating to newer versions as they're released. Staying on the latest version ensures you get all patches, not just security ones.
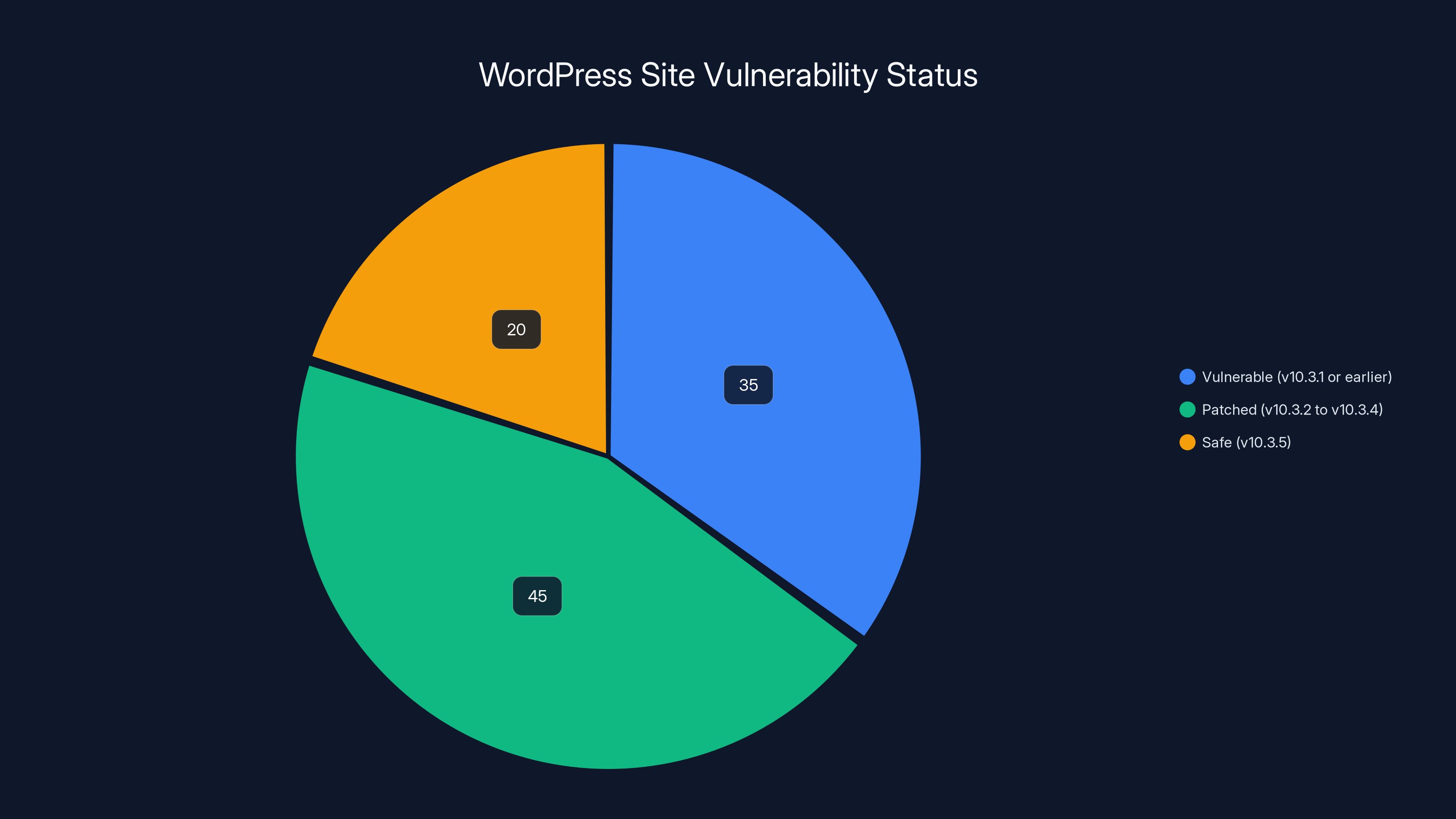
Estimated data suggests that 35% of WordPress sites using the QSM plugin are vulnerable, while 45% are patched, and 20% are fully safe with the latest version.
What About Site Owners Who Can't Update?
Some WordPress sites run on older servers, use heavily customized code, or have configurations where automatic updates don't work. If you're in this position, you have limited options.
Option 1: Manually Test Updates in a Staging Environment
Create a clone of your site in a staging environment (your hosting provider can usually help with this). Update the QSM plugin there first. Test everything to make sure it doesn't break anything. If it works, then update your live site.
This takes more time but eliminates surprise breakages.
Option 2: Use a WAF and Monitoring
If updating is truly impossible, use a WAF to block SQL injection attempts. This isn't as good as patching (WAF rules can be bypassed), but it's better than no protection.
Also enable aggressive monitoring so you detect breaches quickly. Daily security scans and intrusion alerts give you a chance to respond before attackers do significant damage.
Option 3: Disable the QSM Plugin
If you're not actively using QSM quizzes or surveys, disable the plugin. Don't just deactivate it—delete it entirely from your server. This eliminates the vulnerability completely.
If you need the quiz functionality, you might be able to switch to a newer, actively maintained plugin that handles security better.
Option 4: Migrate to a Managed WordPress Host
Some hosting providers (like Kinsta, WP Engine, or Flywheel) automatically update plugins and manage security for you. If you're stuck on outdated infrastructure, migrating to a managed host solves the update problem permanently.
It's more expensive than shared hosting, but the security benefits often justify the cost.

The Bigger Picture: WordPress Security Landscape in 2025
The QSM vulnerability is one of dozens of WordPress security incidents that occur annually. Understanding this single vulnerability teaches us about the broader security challenges WordPress faces.
The Plugin Explosion
WordPress has over 58,000 plugins in the official repository, with thousands more on third-party marketplaces and GitHub. Not all of them are well-maintained. Some are abandoned by their original developers, living on in zombie state, eventually accumulating security vulnerabilities as WordPress core evolves around them.
The WordPress team has been pushing developers to adopt better security practices. They've released security guidelines, tools for developers, and increased automated scanning. But with so many plugins to monitor, the ecosystem will always have vulnerabilities.
The Open Source Trade-off
WordPress being open source is both a strength and a weakness. It's a strength because hundreds of developers can audit the code, security researchers can find vulnerabilities, and the community rapidly patches issues.
But it's also a weakness because attackers can read the same code and find the same vulnerabilities. When a patch is released, attackers reverse-engineer it to understand what was fixed, then scan the internet for unpatched sites still running vulnerable versions.
This is why rapid patching matters so much. The window between patch release and site owner update is when attackers strike.
The Economics of Security
At the core of WordPress's security problem is economics. Plugin developers often aren't well-compensated. Free plugins earn no revenue. Paid plugins might charge $20-50 one-time, which doesn't generate enough revenue to fund ongoing security work.
Compare this to commercial software vendors who have security teams, regular audits, and bug bounty programs. WordPress plugin developers mostly work alone or in tiny teams, usually part-time.
Improving this requires either:
- Plugin developers charging more (which reduces adoption)
- WordPress ecosystem companies funding security (like Automattic does for Jetpack)
- WordPress.org providing more security support (which requires more donations/funding)
- Site owners paying for managed WordPress hosting that handles security (which increases their costs)
There's no easy solution. Each option has trade-offs.
The Enterprise Problem
WordPress dominates in the SMB and mid-market space. But enterprises often struggle with WordPress security because enterprise IT departments want guarantees that plugins meet security standards.
WordPress plugins don't have an official security certification or audit process. Enterprises end up either:
- Not using WordPress (choosing proprietary alternatives)
- Building their own "enterprise WordPress" with locked-down plugin lists and regular audits
- Paying for premium managed services that handle security for them
This gap means large enterprises rarely benefit from WordPress's flexibility and low cost. They sacrifice it for perceived security.
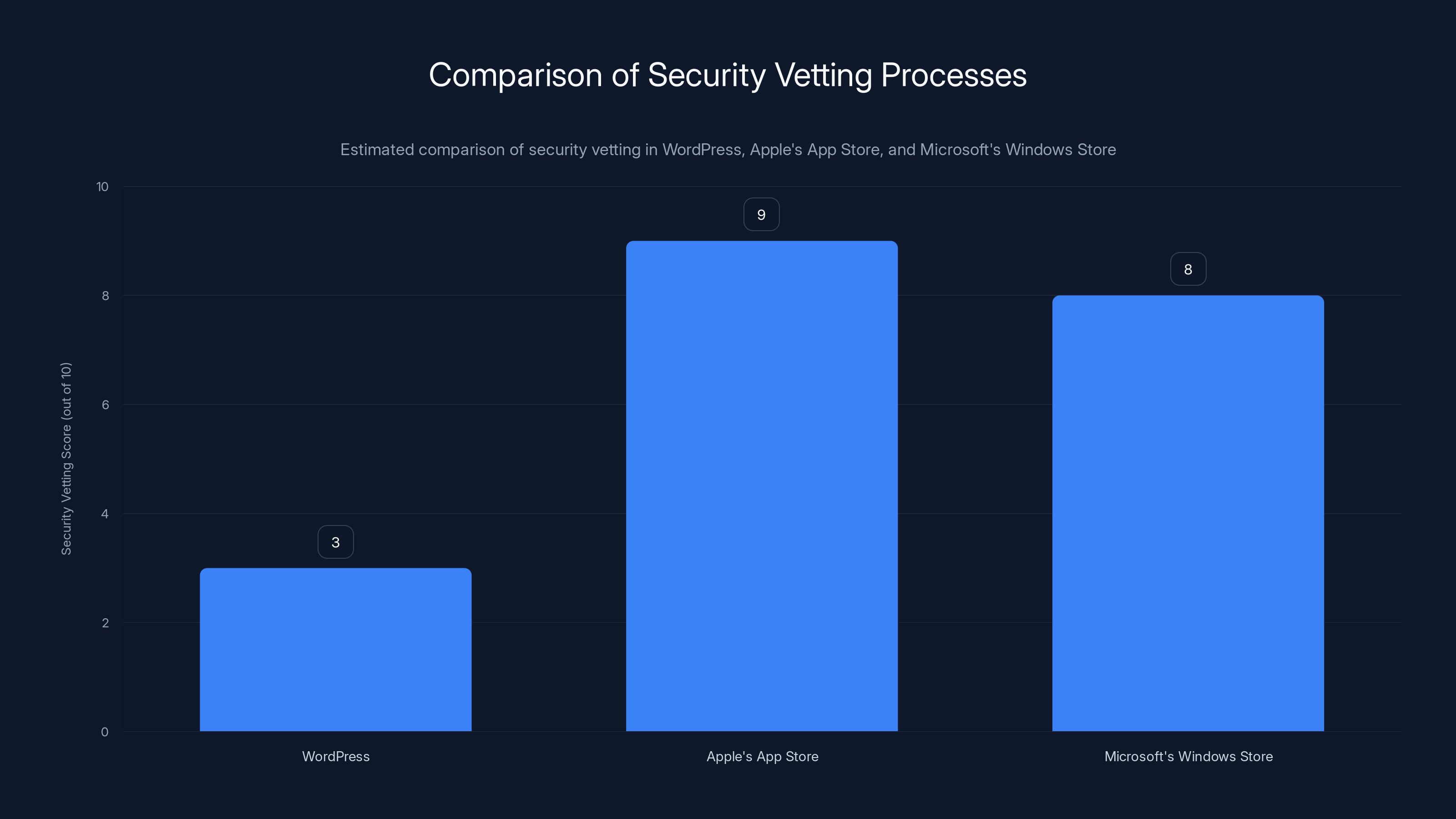
Estimated data shows WordPress has a lower security vetting score compared to Apple's App Store and Microsoft's Windows Store, highlighting the need for improved security measures.
Preparing for the Next Vulnerability
The QSM plugin will eventually be patched for good. Site owners will update. The media coverage will fade. But there will be another vulnerability in another plugin, and another after that.
Instead of viewing security as a one-time fix, view it as an ongoing practice. Here's a framework:
Monthly Security Review Checklist
- Check for plugin and theme updates
- Review active user accounts (delete unused ones)
- Verify backup is working (test restore)
- Check for security alerts from monitoring plugins
- Update WordPress admin password
Quarterly Security Audit
- Run comprehensive malware scan
- Review database for suspicious data
- Check access logs for unusual activity
- Test website functionality (ensure updates didn't break anything)
- Document any security incidents
Annual Security Overhaul
- Perform full security audit (consider hiring professionals)
- Update disaster recovery plan
- Review all installed plugins for continued necessity
- Update password for all admin accounts
- Consider security certifications or compliance standards
This ongoing approach prevents you from getting caught off-guard by the next vulnerability.

Tools and Resources for WordPress Security
If you're looking to level up your WordPress security, here are the essential tools and services.
Free Tools
Wordfence Security (free version)
- Malware scanning
- Firewall rules
- Login security
- Activity logging
Website: wordfence.com
WPScan
- Vulnerability scanner
- Plugin/theme identification
- WordPress version detection
- Tracks CVEs
Website: wpscan.com (WPScan CLI tool is free and open source)
iThemes Security
- Two-factor authentication
- File integrity monitoring
- Security logging
- Backup scheduling
Website: ithemessecurity.com
Paid Services
Sucuri
- Malware scanning and removal
- WAF (Web Application Firewall)
- DDoS protection
- 24/7 monitoring
Starting at: $100/month
Website: sucuri.net
Cloudflare
- WAF with SQL injection protection
- DDoS mitigation
- Performance optimization
- DNS security
Starting at: Free (with paid tiers)
Website: cloudflare.com
Patchstack
- Automated patching for vulnerable plugins
- Patch management
- Vulnerability monitoring
- Security analytics
Starting at: $99/year
Website: patchstack.com
Hosting-Level Security
If you're willing to pay more for hosting, managed WordPress hosts offer built-in security:
- Kinsta ($35+/month): Automated daily backups, SSL, DDoS protection, premium support
- WP Engine ($20+/month): Automatic updates, staging environment, performance optimization
- Flywheel ($15+/month): Managed hosting with built-in staging and backups
- Bluehost ($2.95-13.95/month): Includes free SSL and WordPress pre-installed, but less premium support than other options
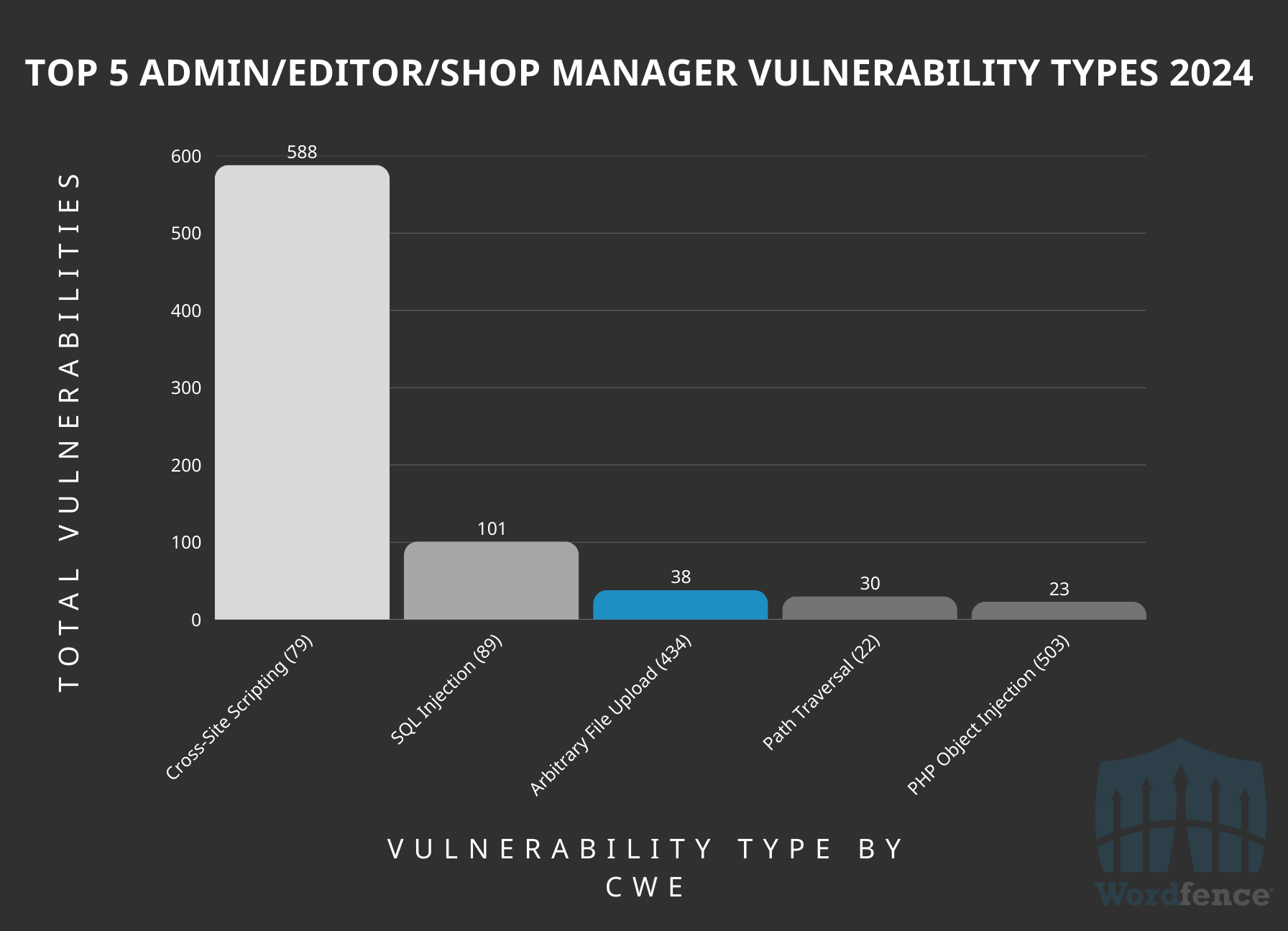
Conclusion: Your Action Plan
Let me be clear about what you need to do:
- This week: Check if you have the QSM plugin. If yes, verify your version. If vulnerable, update immediately.
- This month: Run a comprehensive security scan. Change your WordPress admin password. Review user accounts.
- Going forward: Set reminders to check for plugin updates monthly. Use a security plugin for ongoing monitoring. Keep backups current.
The QSM vulnerability affects 40,000 sites, but it affects them unequally. Sites with good security practices—regular updates, monitoring, strong passwords—will be fine. Sites that haven't updated will likely be compromised.
You're reading this article, which means you're thinking about security. That puts you ahead of the majority of WordPress site owners. Use that advantage. Take action today, not tomorrow.
WordPress isn't going anywhere. It will continue powering massive portions of the internet. That's exactly why we need to take its security seriously. Your site, your data, and your visitors depend on it.
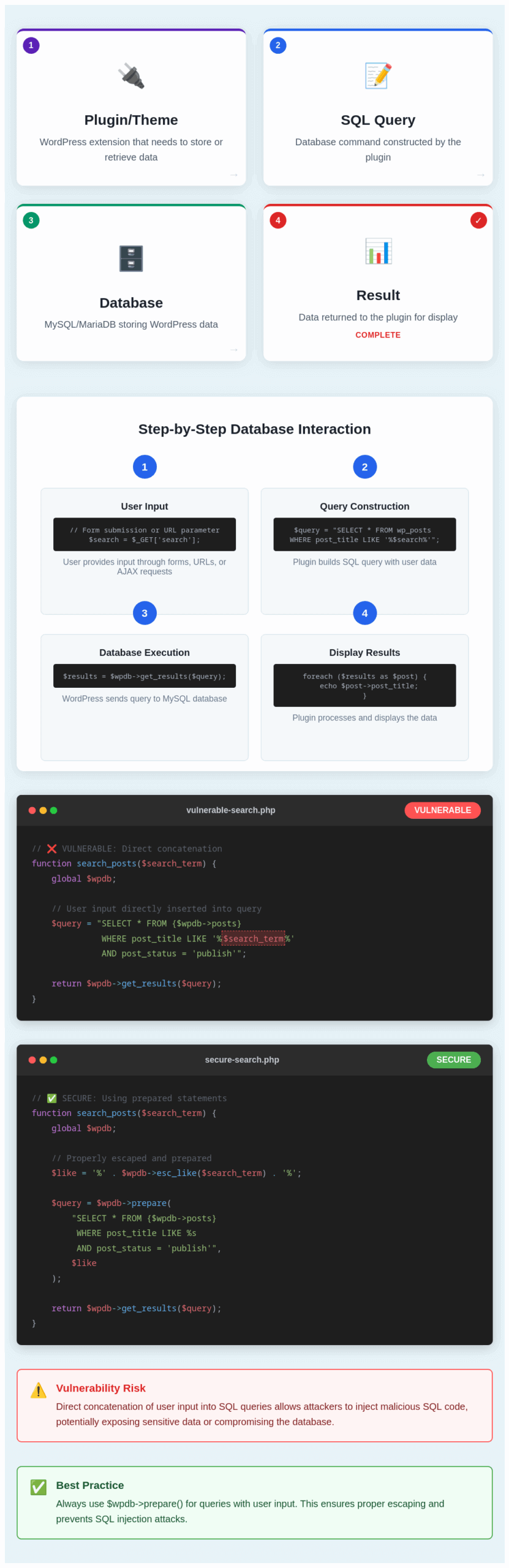
FAQ
What is QSM and why is it popular?
Quiz and Survey Master (QSM) is a WordPress plugin that allows site owners to create interactive quizzes, surveys, and forms without writing any code. It's popular because it's free, easy to use, and offers good functionality for lead generation, audience engagement, and feedback collection. Over 1 million WordPress sites have installed it at some point, with approximately 40,000 actively using it today.
How do I know if my site is vulnerable to the QSM SQL injection flaw?
You're vulnerable if you have QSM plugin version 10.3.1 or earlier installed on your WordPress site. Log into your WordPress admin dashboard, go to Plugins, find "Quiz and Survey Master," and check the version number displayed. If it's 10.3.2 or newer, you're patched. Older versions need immediate updating.
Can attackers exploit this vulnerability without a user account?
No, the vulnerability requires at least a "Subscriber" level account on the WordPress site. However, many WordPress sites allow public registration, making it easy for attackers to create a free subscriber account specifically to exploit this flaw. If your site has open registration enabled, your risk is significantly higher than if registration is closed.
What data could attackers steal through this vulnerability?
Attackers could potentially access any data in your WordPress database, including user credentials (emails and password hashes), customer personal information, purchase history, payment data, business records, admin account details, and sensitive plugin settings like API keys and authentication tokens. The extent of damage depends on what information your site stores.
How long will it take to update QSM and patch my site?
The actual update process takes less than 2 minutes. WordPress automatically downloads and installs the patch when you click "Update Now." However, we recommend you first backup your site (which takes 5-10 minutes using most backup plugins), verify the update doesn't break anything, and change your admin password afterward (5 minutes). The entire process typically takes 30-45 minutes if you do it carefully.
What should I do if I think my site has already been compromised?
If you suspect compromise, immediately change all administrator passwords, run a malware scan using Wordfence or Sucuri, check your user accounts list for suspicious additions, review database access logs if available, and consider hiring a professional WordPress security firm to conduct a forensic investigation. Restore from a clean backup if you find evidence of compromise. Do not delay on this—attackers with database access can cause significant damage.
Are there plugins that could prevent this vulnerability even without updating?
Yes, a Web Application Firewall (WAF) can block SQL injection attempts before they reach your site. Cloudflare, Sucuri, and some WordPress security plugins offer WAF protection that would have prevented exploitation of this vulnerability. However, a WAF is not a substitute for patching. You need both layers of protection for comprehensive security.
Why didn't the WordPress plugin review process catch this vulnerability?
The WordPress plugin review process is volunteer-driven and focuses on obvious security issues like hardcoded API keys or malicious code. SQL injection vulnerabilities in complex plugin logic are harder to catch without professional security audits or automated scanning. The volume of plugins (58,000+) makes comprehensive review impossible. This is why third-party security scanning services like Patchstack exist.
Should I remove the QSM plugin if I'm not using it?
Yes, absolutely. If you're not actively using QSM, delete it entirely from your server. Leaving unused plugins installed increases your attack surface even if they're deactivated. Plugins can be re-installed later if you need them again. Keeping only the plugins you actually use is a fundamental security best practice.
What's the difference between updating and simply activating an older version of QSM?
Updating installs the fixed code that patches the vulnerability. Simply reactivating an old version keeps the vulnerable code in place. You must actually update to version 10.3.2 or newer, not just reactivate an older version. Updates replace the vulnerable files with patched versions.
How often should I check for WordPress and plugin updates?
You should check for updates at least monthly, and ideally enable automatic updates for WordPress core and plugins. Automatic updates are particularly important for security patches. Many hosting providers allow you to configure automatic updates in their control panel, or you can set them up in WordPress by modifying the wp-config.php file to enable background automatic updates.
Key Takeaways
- Over 40,000 WordPress sites are affected by a critical SQL injection vulnerability in QSM plugin versions 10.3.1 and earlier
- The flaw allows any logged-in user with subscriber or higher privileges to extract sensitive database data through SQL injection attacks
- Nearly 48% of QSM users are running vulnerable versions, representing approximately 19,160 confirmed vulnerable sites
- Patching to version 10.3.2 or newer is critical, but must be paired with password changes, security scans, and ongoing monitoring for comprehensive protection
- SQL injection vulnerabilities continue to occur because WordPress plugin developers often lack resources for rigorous security testing, and the ecosystem has limited vetting beyond volunteer review
Related Articles
- Moltbook Security Disaster: How AI Agents Exposed 1.5M Credentials [2025]
- Software Integrity vs Data Sovereignty: Why Code Matters More [2025]
- OpenAI Scam Emails & Vishing Attacks: How to Protect Your Business [2025]
- LinkedIn Phishing Scam Targeting Executives: How to Protect Yourself [2025]
- How to Disable Chrome's On-Device AI Scam Detection [2025]
- Iran's Internet Shutdown: Longest Ever as Protests Escalate [2025]
![WordPress QSM Plugin SQL Injection Flaw Hits 40,000 Sites [2025]](https://tryrunable.com/blog/wordpress-qsm-plugin-sql-injection-flaw-hits-40-000-sites-20/image-1-1770232083729.jpg)



