WPvivid Plugin Security Flaw: The Critical Vulnerability Affecting Nearly 1 Million WordPress Sites
Last January, security researchers at Defiant uncovered a critical vulnerability in one of the most popular WordPress backup plugins on the market. The WPvivid Backup & Migration plugin, trusted by over 900,000 active installations, contained a flaw that could allow attackers to execute arbitrary code on affected websites, as detailed in Bleeping Computer's report.
Here's what makes this particularly worrying: the plugin had been vulnerable for years, and nobody caught it until researchers dug deeper into how it handled file uploads and encryption. The vulnerability, officially tracked as CVE-2026-1357 with a severity score of 9.8 out of 10, doesn't just put individual websites at risk. It threatens the stability of entire hosting environments, client databases, and the trust businesses place in WordPress as a platform, as noted by CyberPress.
But before you panic and disable every backup plugin you own, let's break down what actually happened, who's truly at risk, and what you need to do right now to protect your site.
TL; DR
- The Vulnerability: WPvivid Backup & Migration (versions up to 0.9.122) contained improper error handling in RSA decryption plus missing path sanitization, allowing unauthenticated file uploads, as explained by SC World.
- Impact Scope: Nearly 900,000 active installations, though only sites with "receive backup from another site" enabled are vulnerable.
- The Attack Window: Attackers have only 24 hours to exploit the flaw before encryption keys expire, significantly limiting real-world exploitation.
- The Fix: Update to version 0.9.123 released January 28 immediately; this is a critical patch, not optional.
- Real Risk Level: High severity, but exploitation requires specific conditions (backup reception enabled + 24-hour window), making it less of a mass exploitation risk than the CVSS score suggests.
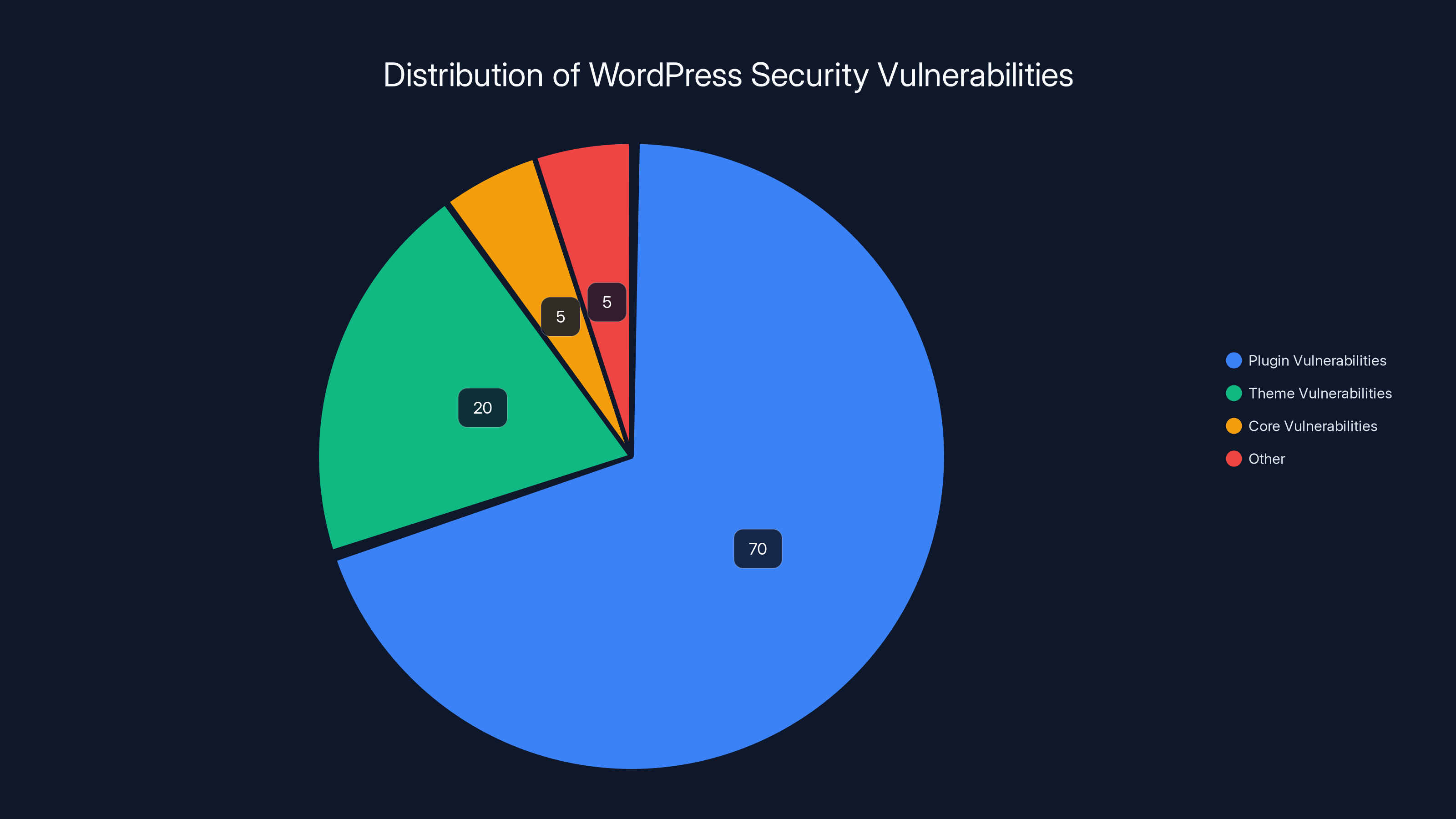
Estimated data shows that plugin vulnerabilities account for the majority of WordPress security issues, highlighting the need for better plugin management and security practices.
What Is WPvivid and Why Is It So Popular?
WPvivid Backup & Migration isn't just another backup plugin. It's become the default choice for WordPress administrators who need to move sites between hosts, create reliable backups without breaking the bank, or manage multiple WordPress installations from a single dashboard.
The plugin solves a real problem. Standard WordPress backups through hosting panels are clunky. Manual backups take hours. WPvivid automates the entire process, letting you schedule daily backups, store them in cloud services like Google Drive or AWS S3, and restore your entire site with a few clicks. The free version includes core backup functionality, while premium tiers add advanced features like scheduled migrations and cloud storage integration.
With 900,000+ active installations and over 20,000 paying customers, WPvivid has become a critical piece of the WordPress security infrastructure. Small businesses rely on it for disaster recovery. Agencies use it to manage client sites at scale. Developers trust it for staging environments.
That's why a critical vulnerability in this plugin hits so hard. It's not an obscure tool that nobody uses. It's the kind of plugin that, if exploited at scale, could compromise hundreds of thousands of WordPress installations simultaneously, as highlighted by Forbes.

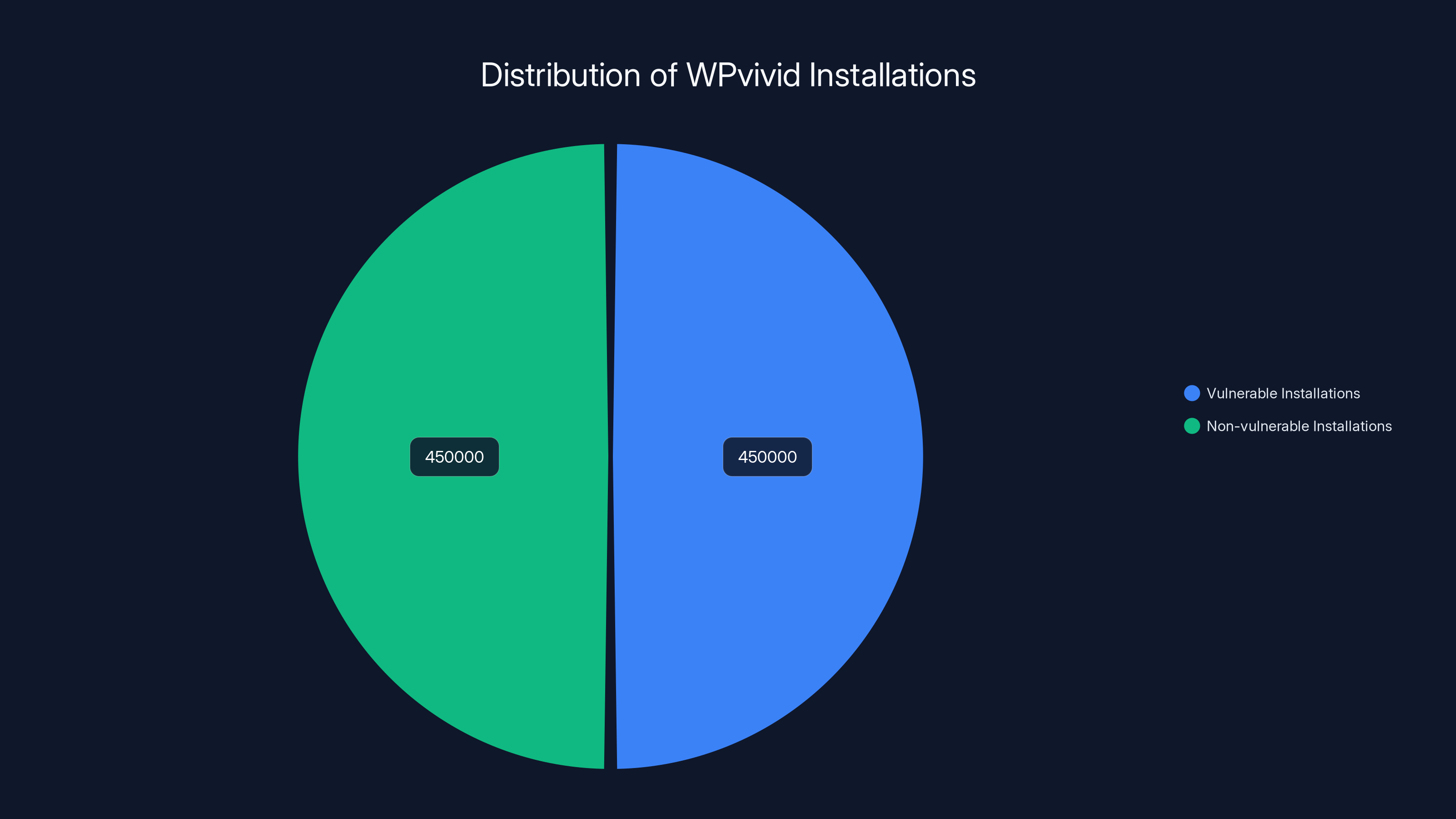
Estimated data shows that approximately half of WPvivid installations might be vulnerable if not updated, highlighting the importance of patching to version 0.9.123.
Understanding CVE-2026-1357: The Technical Breakdown
Let's talk about what actually went wrong under the hood. This isn't a simple security lapse. It's a combination of two related vulnerabilities that, together, create a perfect storm for remote code execution.
The RSA Decryption Flaw
WPvivid uses RSA encryption to secure backup files when transferring them between sites. RSA is military-grade encryption, widely considered secure. The problem wasn't with RSA itself. It was with how WPvivid handled errors during the decryption process.
When the plugin received an encrypted file and something went wrong during decryption, it didn't fail gracefully. Instead, it exposed information about what went wrong through error messages. This is called improper error handling, and it's a classic security anti-pattern, as detailed by CyberPress.
Think of it like a bank teller who, when they can't read your check, doesn't just say "sorry, I can't process this." Instead, they say "your signature doesn't match because the first letter is too tall and your account number is 12345678." They've just leaked information that shouldn't be public.
Here's the formula for cryptographic security:
WPvivid nailed the first part (RSA is solid), but failed on the other two. The improper error handling gave attackers a roadmap to how the encryption was structured and where it was failing.
The Path Sanitization Gap
The second vulnerability is about file paths. When you upload a file through WPvivid's backup restoration process, the plugin needs to know where to put it on the server. It takes a file path and saves it to that location.
Path sanitization means checking that the file path is safe before using it. A developer should verify that the path doesn't contain malicious instructions like ../../../ (which moves up the directory structure) or absolute paths that point to sensitive areas of the server.
WPvivid didn't do this properly. An attacker could craft a specially formed file path that would bypass these checks, allowing them to upload files anywhere on the server, not just in the intended backup directory.
Combined with the RSA decryption error handling issue, an attacker could:
- Send a malformed encrypted file that exploits the error handling flaw
- Include a malicious file path that bypasses sanitization
- Upload a PHP file containing malicious code to an executable location
- Execute that code and gain full control over the WordPress installation
This is remote code execution (RCE), and it's about as bad as it gets for web security, as emphasized by Bleeping Computer.

The Vulnerability Timeline: From Discovery to Patch
Understanding when this vulnerability was discovered and how long it's been in the wild is critical for assessing actual risk.
Before the Patch (Years Unknown)
The exact discovery date of this vulnerability isn't publicly documented, but based on the timeline and how CVSS scoring works, security researchers likely found it sometime in late 2024. The vulnerability affects "all versions up to 0.9.123," which is a pretty broad statement. This means the flaw could have existed for years without detection, as reported by SC World.
This is actually the scariest part. We don't know if attackers discovered this vulnerability independently and silently exploited it before researchers made it public. The best practice in security research is to assume the worst: that any vulnerability with a high CVSS score may have been exploited in the wild for some time before public disclosure.
The Patch: January 28, 2025
WPvivid released version 0.9.123 on January 28 with a patch for CVE-2026-1357. This patch addresses both the improper error handling and the path sanitization issues. If you're running this version or later, you're protected, as confirmed by CyberPress.
However, here's the problem with any security patch: adoption is slow. According to the data available, the plugin was downloaded approximately 200,000 times between January 28 and the time of publication. That's a decent number, but it represents a tiny fraction of the 900,000 active installations. Many site owners haven't updated yet, and some may never update if they've abandoned their sites.
The Current Situation (Post-Patch)
As of now (early 2025), the vulnerability is public knowledge. Attackers have the technical details they need to exploit it. The patch exists and is available. But a significant portion of installations remain vulnerable because site owners either haven't updated yet, don't know about the vulnerability, or have simply forgotten about the plugin running on their older sites.

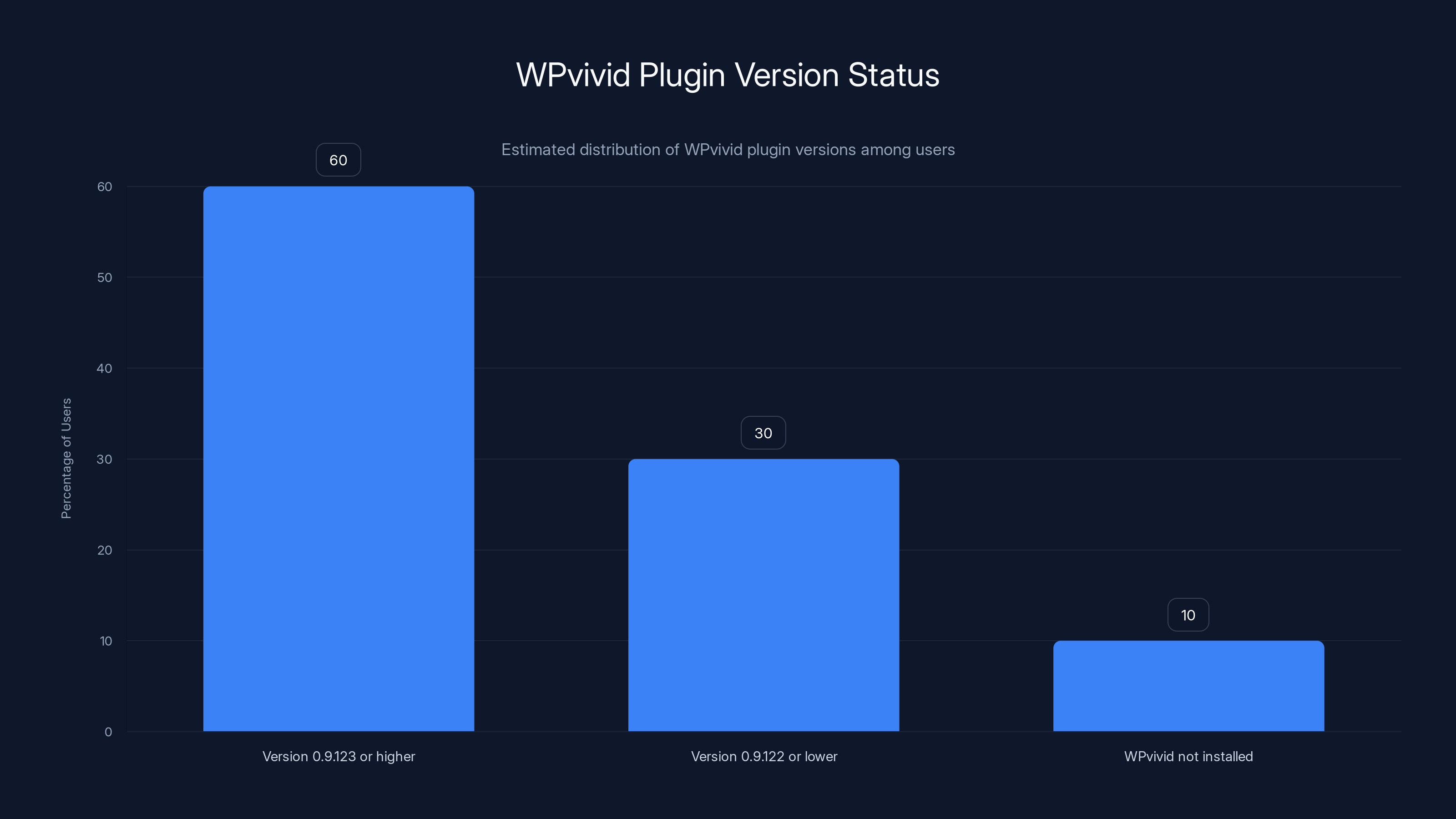
Estimated data suggests that 60% of users have the patched version of WPvivid, while 30% are still vulnerable and 10% do not have the plugin installed.
Who's Actually at Risk? The Real Attack Surface
Here's where the story gets more complicated than the headline suggests. Not every site running WPvivid is equally vulnerable.
The "Receive Backup from Another Site" Requirement
Exploiting this vulnerability requires a very specific condition: the target site must have the "Receive backup from another site" feature enabled. This is not the default setting. Most WordPress site owners use WPvivid in the conventional way: they create backups of their own site and store them on cloud services or local storage.
The "receive backup from another site" feature is designed for a specific use case: when you're running multiple sites and want to distribute backup responsibilities or consolidate backups from several installations into one central location. It's a more advanced feature that requires explicit configuration.
According to security researchers, this feature is not enabled by default. This immediately reduces the actual attack surface from 900,000 sites down to a much smaller subset—likely somewhere between 100,000 and 500,000 based on typical feature adoption rates. We don't have exact numbers, but the limitation is significant, as noted by Search Engine Journal.
The 24-Hour Encryption Key Expiration Window
Here's another critical limitation that the headlines don't emphasize enough: attackers only have 24 hours to exploit this vulnerability against any given target.
When one WPvivid installation sends a backup to another, it encrypts the transmission using RSA keys. These keys expire after 24 hours. After that window closes, the encrypted backup files become useless. An attacker can't take an old encrypted backup file from weeks ago and exploit the vulnerability with it. The key would have expired.
This 24-hour window significantly complicates attacks. An attacker would need to:
- Identify a target site running vulnerable WPvivid
- Confirm that "receive backup from another site" is enabled
- Prepare the malicious payload
- Execute the attack
- All within a 24-hour window after detecting the vulnerability window is open
It's not impossible, but it's far more difficult than simply uploading a malicious file to an unauthenticated endpoint that's always available.

Attack Scenario: How Would an Attacker Actually Exploit This?
Let's walk through a realistic attack scenario. Understanding how the vulnerability would actually be exploited helps you understand whether your site is truly at risk.
Step 1: Reconnaissance
An attacker scanning the internet for vulnerable targets would need to identify WordPress sites running WPvivid. This is easy—they can check the wp-content/plugins/ directory or look for WPvivid-specific URLs. Finding that a site runs WPvivid takes seconds.
But here's where it gets harder: they also need to determine if that site has "receive backup from another site" enabled. This isn't something that's publicly advertised in headers or easily detectable from the outside. An attacker would likely need to probe the plugin's endpoints to discover this configuration, or they'd need to get lucky and find a site that explicitly has this feature enabled.
Step 2: Preparation
Once a target is identified, the attacker needs to prepare a malicious payload. This would typically be a PHP file containing code that creates a backdoor or steals data. The attacker crafts this payload specifically to exploit the path sanitization gap, ensuring it ends up in an executable directory (like wp-content/uploads/ or the root directory).
The payload would use the RSA decryption error to bypass validation checks. This requires understanding the exact error handling behavior of the WPvivid version running on the target—not all vulnerable versions necessarily handle errors identically.
Step 3: Attack Execution
The attacker sends the malicious encrypted backup file to the target's WPvivid endpoint. If everything aligns—the vulnerable version, the enabled feature, the error handling behaving as expected, the 24-hour window still open—the attack succeeds. The malicious file gets uploaded and executed.
If any piece doesn't align, the attack fails. The attacker gets no error messages (if WPvivid was properly handling errors) and no indication of what went wrong.
Step 4: Post-Exploitation
Once the PHP file is executed, the attacker can:
- Create admin accounts in WordPress
- Install backdoors for persistent access
- Steal the site's database
- Inject malware that targets site visitors
- Redirect traffic to phishing sites
- Use the compromised server for crypto mining or botnet participation
Essentially, the game is over. The attacker owns the site.

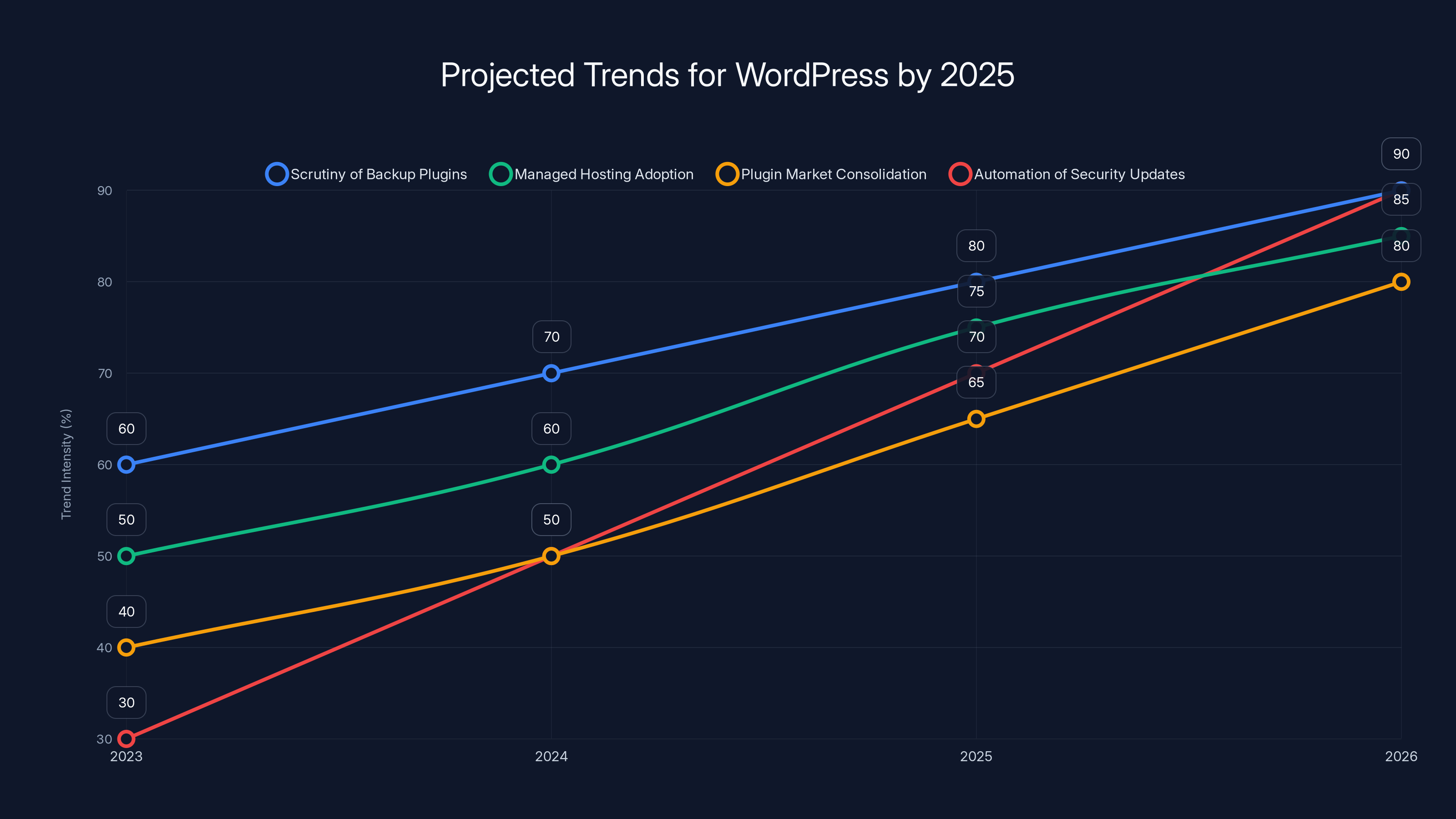
By 2025, increased scrutiny of backup plugins and the adoption of managed hosting are expected to rise significantly, alongside market consolidation and automation of security updates. (Estimated data)
Real-World Impact: What Does This Mean for Different Site Owners?
The severity of this vulnerability varies dramatically based on what kind of site you're running.
For Small Business Owners
If you're running a small business site with WPvivid and you haven't enabled "receive backup from another site," your risk is extremely low. You should still update immediately (it's a critical patch), but the odds of being targeted for this specific exploit are minimal. Attackers typically go for easier targets or sites with more valuable data.
If you ARE using the "receive backup from another site" feature for some reason, your risk is moderate. You should treat this as a security emergency and update within hours, not days.
For Web Agencies and Developers
This is where the vulnerability becomes more concerning. Agencies often manage dozens or hundreds of client sites. If an agency administrator has enabled backup syncing across client sites for easier management, multiple client sites could be vulnerable simultaneously from a single attack.
Even if the feature isn't enabled, a compromised agency server could be used as a launching point for attacks against client sites. The 24-hour window becomes less restrictive if the attacker has access to the agency's infrastructure to facilitate the attack.
For agencies, this vulnerability is a wake-up call about inventory management. Do you know exactly which versions of which plugins are running on which client sites? If you can't answer that question immediately, you have a bigger problem than WPvivid.
For Enterprise WordPress Deployments
Enterprises running WordPress at scale often have different backup strategies. They might use enterprise-grade backup solutions instead of plugins, or they have strict version control and testing policies that prevent running unpatched software.
However, enterprises that do use WPvivid face a different kind of risk: operational complexity. Updating a WordPress plugin on one site is straightforward. Coordinating updates across hundreds or thousands of sites requires change management processes, testing, and staged rollouts. During the transition period, sites remain vulnerable.

The Broader Security Lesson: Plugin Vulnerabilities Are the Norm, Not the Exception
WPvivid's vulnerability is shocking in its severity, but it's not unusual in its frequency. Let's look at the bigger picture of WordPress security.
WordPress Security Statistics
99% of WordPress security breaches involve plugin or theme vulnerabilities, according to WordPress security experts. This isn't because WordPress Core is insecure—WordPress Core development is actually quite rigorous. It's because the plugin ecosystem is enormous, distributed, and has highly variable quality standards.
At any given moment, there are thousands of actively maintained WordPress plugins and thousands more that are abandoned but still installed on millions of sites. Some plugins are maintained by large companies with dedicated security teams. Others are maintained by single developers in their spare time.
When a vulnerability is discovered in a critical plugin like WPvivid, it exposes the structural weakness of the WordPress ecosystem: there's no reliable way to force updates or verify that vulnerable software has been patched.
Why Plugin Vulnerabilities Slip Through
Understanding why WPvivid's vulnerability existed for so long (and how similar vulnerabilities keep appearing) requires understanding the plugin development environment:
1. Security Isn't Profitable
Developing plugins is often done at low margins. Adding security features, conducting code reviews, and hiring security experts costs money. Many plugin developers operate on thin budgets and prioritize features over security.
2. Complexity Breeds Vulnerability
Backup and migration functionality is inherently complex. You're dealing with file operations, database access, encryption, and data transfer. More complexity means more surface area for bugs. More bugs means more potential security issues.
3. Third-Party Dependencies
Many plugins rely on third-party libraries for encryption, cloud storage, and other functionality. If those dependencies have vulnerabilities, the plugin inherits them. Managing these dependencies at scale is a constant challenge.
4. Legacy Code Burden
Plugins that have existed for years accumulate legacy code. Developers add features on top of old code, creating technical debt. Eventually, nobody fully understands how the code works, and bugs hide in the complexity.
5. Testing Gaps
Security testing requires specific expertise. Many plugin developers focus on functional testing (does it work?) rather than security testing (can it be broken?). Dedicated security researchers and penetration testers find bugs that automated testing misses.

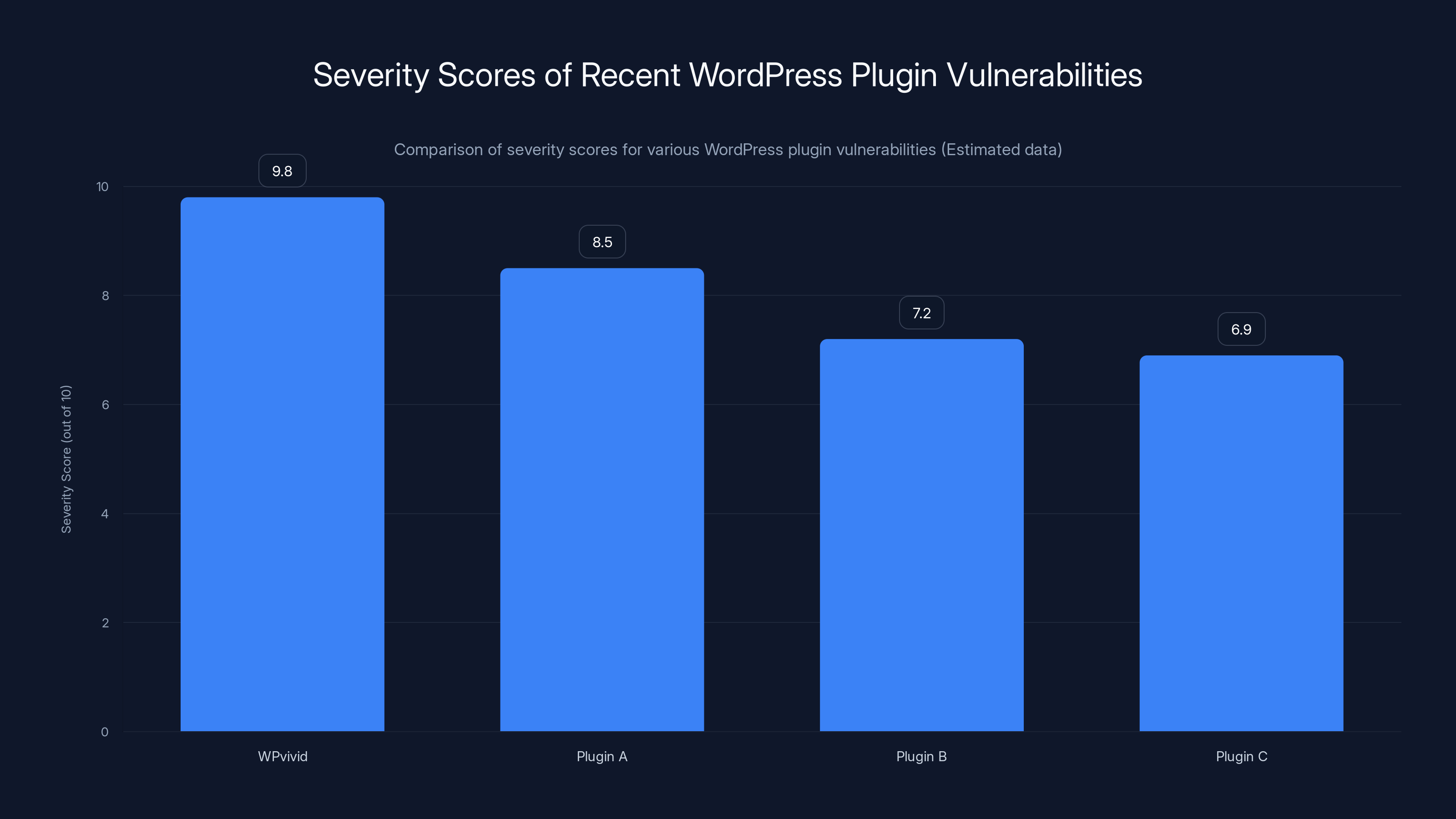
The WPvivid plugin has one of the highest severity scores at 9.8, indicating a critical vulnerability compared to other recent plugin issues. Estimated data for comparison.
What You Should Do Right Now: The Action Plan
If you're running WPvivid, here's your step-by-step remediation plan.
Step 1: Check Your Version (Do This First)
Log into your WordPress admin dashboard. Go to Plugins > Installed Plugins and find WPvivid Backup & Migration. Look at the version number displayed next to the plugin name.
- Version 0.9.123 or higher: You're patched. No action needed, but verify in your next security audit.
- Version 0.9.122 or lower: You're vulnerable. Proceed to Step 2 immediately.
- WPvivid not installed: Skip to Step 3 to ensure it isn't running elsewhere.
Step 2: Update Immediately
Don't wait for your scheduled maintenance window. This is a critical security patch. Go to Plugins > Installed Plugins, find WPvivid, and click Update now. Wait for the update to complete.
If you can't update through the dashboard for some reason (permission issues, hosting restrictions), contact your hosting provider or access your site via FTP/SFTP to manually update the plugin folder.
The update should take less than a minute. Your site will stay online during the update.
Step 3: Audit Your WPvivid Settings
After updating, review your WPvivid configuration:
- Open WPvivid dashboard (usually under Tools or Settings)
- Check if "Receive backup from another site" is enabled
- If enabled and you don't actively use this feature, disable it
- Review your backup schedule—ensure backups are running regularly
- Verify cloud storage credentials are current and valid
Disabling unused features reduces your attack surface. If you don't need inter-site backup syncing, turning it off adds an extra layer of protection.
Step 4: Change Admin Passwords (Best Practice)
While the 24-hour window likely means your site wasn't compromised if you weren't actively being attacked during that window, it's good security hygiene to change admin passwords after a critical vulnerability disclosure.
Change:
- All WordPress admin user passwords
- Hosting control panel (cPanel, Plesk, etc.) password
- Database passwords if you have direct access
- Credentials for any cloud storage connected to WPvivid
This breaks any potential compromised credentials an attacker may have obtained before the patch was released.
Step 5: Monitor Your Site for Suspicious Activity
After patching, monitor these indicators of compromise:
- Unexpected admin users: Check Users > All Users for unfamiliar accounts
- Modified core files: Use a security plugin like Wordfence or Sucuri to scan for file changes
- Strange cron jobs: Check Tools > Site Health > Debug Information for unfamiliar scheduled tasks
- Server logs: If you have access, check your web server logs for suspicious file uploads or PHP execution attempts
- Performance issues: Degraded site speed could indicate crypto mining or other background attacks
- Security plugin alerts: If you use Wordfence, Sucuri, or similar, check their activity logs
Prevention: Building a Resilient WordPress Security Strategy
The WPvivid vulnerability is a symptom of deeper issues in how we manage WordPress security. Here's how to build a more resilient approach.
Implement a Plugin Inventory System
You can't protect what you don't know exists. Maintain a master inventory of all plugins running on all your sites, including:
- Plugin name and slug
- Currently installed version
- Last update date
- Security patch status
- Number of active installations using this plugin
- Developer reputation and update frequency
Use this inventory to track vulnerabilities as they're disclosed. Tools like WordPress.com's security tools or third-party plugin monitoring services can help automate this.
Establish Update Policies
Create clear policies for how quickly you update plugins based on severity:
- Critical severity (CVSS 9.0+): Update within 24 hours
- High severity (CVSS 7.0-8.9): Update within 3-7 days
- Medium severity (CVSS 4.0-6.9): Update within 2-4 weeks
- Low severity (CVSS 0-3.9): Update within 1-2 months
For single sites, you might update everything immediately. For agencies managing many sites, staged updates reduce risk.
Use a Web Application Firewall (WAF)
A WAF (Web Application Firewall) like Sucuri, Wordfence, or Cloudflare can block common attack patterns even if vulnerabilities exist in your plugins. A WAF would have likely blocked the WPvivid attack by:
- Detecting suspicious file upload attempts
- Blocking requests with malicious path traversal sequences
- Identifying unusual POST/PUT requests to plugin directories
Regular Security Audits
Schedule quarterly security reviews that include:
- Plugin vulnerability scanning
- File integrity checking
- Database access monitoring
- User account audit (remove unused accounts)
- Change log review (what was modified and when?)
- Backup verification (can you actually restore from backups?)
These audits catch problems before they become crises.
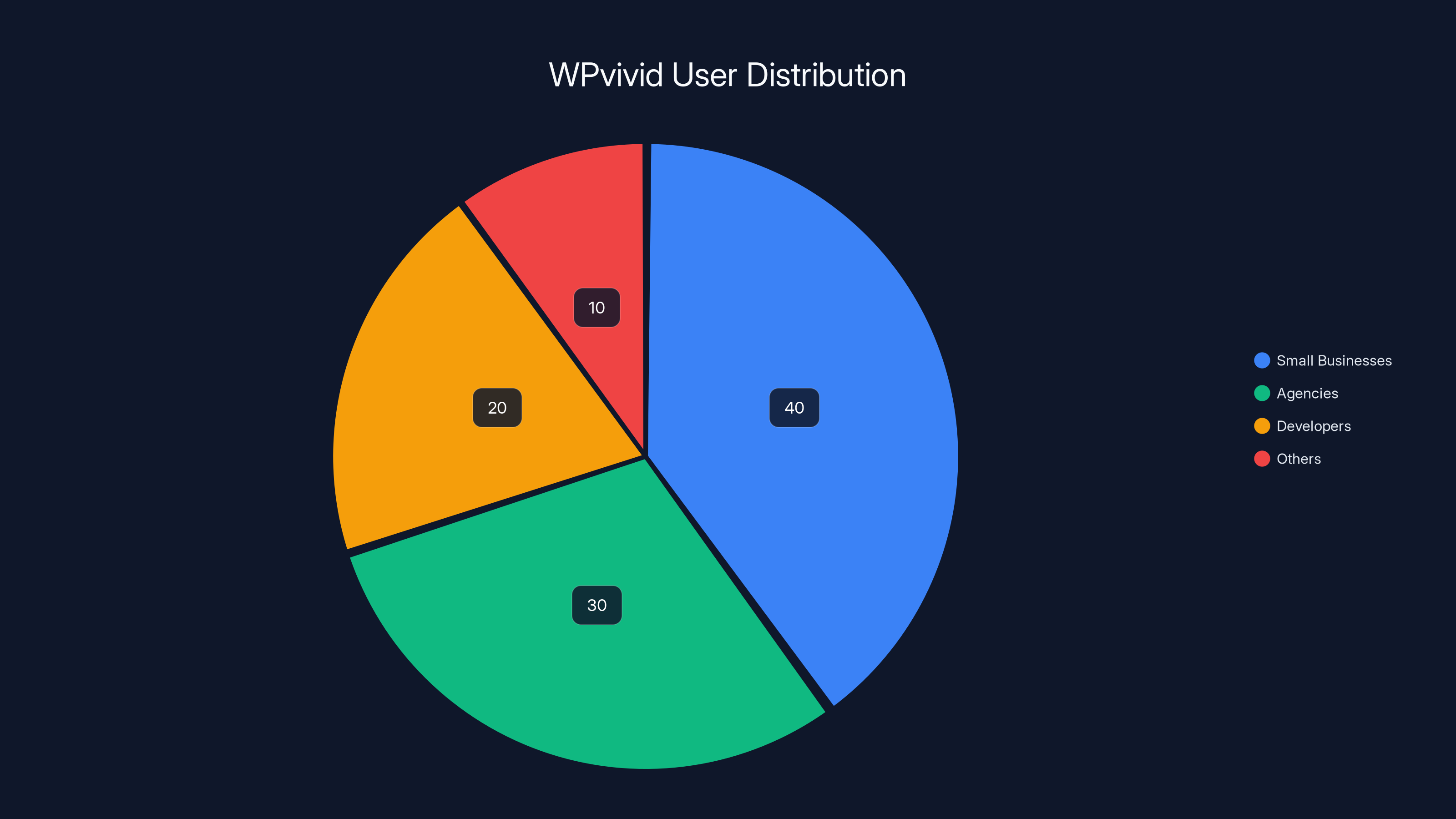
WPvivid is widely used by small businesses (40%), agencies (30%), and developers (20%) for site management and backup solutions. Estimated data based on user context.
The Backup Paradox: When Your Safety Net Has Holes
There's a dark irony here worth discussing. WPvivid is a backup and migration plugin—it's supposed to be your safety net when things go wrong. Yet this vulnerability in the backup plugin itself could be the thing that goes wrong.
This creates a logical problem: how do you recover from an attack that exploits your backup tool? If an attacker gains code execution through WPvivid and modifies your backups, your backups can't save you.
The Solution: Layered Backups
Don't rely on a single backup method. Implement multiple backup strategies:
1. Plugin-Based Backups (WPvivid, Updraft Plus, etc.)
Convenient for daily automated backups and easy restoration. But vulnerable to plugin-specific exploits. Update regularly and monitor carefully.
2. Hosting Provider Backups
Most hosting providers maintain server-level backups independent of WordPress. These are managed by the hosting company and aren't vulnerable to plugin exploits. Usually stored for 7-30 days.
3. Manual Backup Exports
Monthly or quarterly manual backups give you point-in-time recovery for major changes. Export your WordPress content via Tools > Export and save it somewhere safe.
4. Database Backups
SQL database dumps backed up to a separate server or cloud storage. This is the most important data to protect.
With layered backups, if one backup method is compromised, you have others to fall back on.

Evaluating Your Backup Tool: Questions to Ask Before Trusting It
After the WPvivid incident, you might be wondering: can I trust my backup plugin? Here are the questions to ask when evaluating any backup tool.
Security Questions
-
Does the developer maintain an active security update schedule? Plugins that get security patches within days of disclosure are better than those that take weeks.
-
Does the developer conduct security audits? Look for security certifications, third-party audits, or evidence of proactive security testing.
-
Is the source code visible? Open-source plugins allow security researchers to identify problems. Closed-source plugins are riskier.
-
How does the plugin handle encryption? Does it use industry-standard encryption libraries? Does it implement encryption properly?
-
What's the backup history? Has this plugin had major vulnerabilities before? One vulnerability might be bad luck. Multiple vulnerabilities suggest sloppy development practices.
Functionality Questions
-
Can you restore from backup without the plugin installed? If the plugin becomes unavailable, can you manually restore backups from files?
-
Are backups stored in standard formats? SQL databases and compressed files that any tool can read are safer than proprietary formats that only the original plugin can understand.
-
How long are backups retained? Longer retention means more points-in-time to recover from.
Support Questions
-
Is support responsive? Email the support address with a technical question. See how long it takes to get a real answer.
-
Does the developer have a responsible disclosure policy? Can you report security issues privately before they're publicly disclosed?
The Bigger Picture: Why WordPress Security Remains a Challenge in 2025
The WPvivid vulnerability is a symptom of broader issues in web security that we haven't solved despite decades of trying.
The Plugin Economy Problem
WordPress plugins are developed by independent developers or small companies who don't have the resources of major software companies. They don't have QA teams, security specialists, or CI/CD pipelines. Many are passion projects maintained in someone's spare time.
This creates an unfortunate reality: the most important security-related plugins often have the fewest resources dedicated to security. It's an economic problem disguised as a technical problem.
The Update Problem
Even when patches are available, adoption is slow. Site owners don't update because:
- They don't know an update exists
- They're worried updates will break functionality
- They've abandoned their sites and don't monitor them
- Updates require testing on staging servers first
- They don't understand why updating is important
Until we solve the update problem—making updates automatic, safe, and transparent—vulnerabilities will persist even after patches are released.
The Testing Problem
WordPress plugins aren't tested the way software that handles sensitive data should be tested. There's no standard for security testing in the WordPress community. Some developers use automated scanning tools. Others don't test for security at all.
In contrast, banks, payment processors, and healthcare software undergo rigorous security audits. Their code is reviewed by specialists. Their infrastructure is tested for vulnerabilities regularly.
WordPress plugins often get a "does it work?" test and nothing more. Security is an afterthought.
Looking Forward: What This Means for WordPress in 2025 and Beyond
The WPvivid vulnerability won't be the last critical flaw found in popular WordPress plugins. Understanding how it might lead to systemic changes is important for long-term security.
Trend 1: Increased Scrutiny of Backup Plugins
Backup plugins have elevated risk because they handle the full website and database. Expect more security researchers to focus on this category, finding more vulnerabilities. This increased scrutiny is actually good—it drives improvements.
Trend 2: Move Toward Managed WordPress Hosting
Managed WordPress hosting companies (WordPress.com, Kinsta, WP Engine) handle backups, security, and updates as a service. For non-technical site owners, this is becoming more attractive than self-hosted WordPress with manual security management.
Trend 3: Plugin Market Consolidation
As security becomes a higher bar, we'll likely see smaller, lower-quality plugins disappear. Large, well-funded plugins with dedicated security teams will consolidate the market. This is actually better for users, even if it reduces choice.
Trend 4: Automation of Security Updates
We're moving toward automatic security updates for critical vulnerabilities. WordPress Core can already be auto-updated. Plugins will follow. This dramatically reduces the window of vulnerability.

Real-World Case Studies: How Backup Plugin Vulnerabilities Have Been Exploited
WPvivid isn't the first backup plugin to have critical vulnerabilities. History provides context.
Case Study 1: Updraft Plus Vulnerability (2019)
Updraft Plus, another popular backup plugin, had a vulnerability that allowed arbitrary file uploads. Sites using older versions were compromised. Recovery required restoring from clean backups—ironically showing why backup plugins are so important.
The lesson: even mature plugins with good track records can have serious vulnerabilities. Always keep backups of backups.
Case Study 2: Back WPup Vulnerability (2021)
Back WPup, a free backup plugin with millions of installations, had a path traversal vulnerability similar to WPvivid's. It was exploited in the wild, and researchers estimated thousands of sites were compromised before the patch was released.
The lesson: free plugins get as much scrutiny as paid plugins. Popularity matters more than price when it comes to security attention.
Case Study 3: All-in-One WP Migration (2021)
This popular migration plugin had authentication bypass vulnerabilities. Researchers found active exploitation in forensic analysis of compromised sites. The plugin had been updated, but adoption of the update was slow.
The lesson: the time between vulnerability disclosure and exploit in the wild is shrinking. What used to be weeks is now days.
FAQ
What exactly is CVE-2026-1357 and why does it matter?
CVE-2026-1357 is a critical security vulnerability in WPvivid Backup & Migration plugin that combines improper error handling in RSA decryption with inadequate path sanitization, allowing unauthenticated attackers to upload arbitrary files and execute malicious code on vulnerable WordPress installations. It matters because WPvivid is installed on nearly 900,000 WordPress sites, making this potentially one of the largest-scale plugin vulnerabilities affecting the WordPress ecosystem.
How can I tell if my WordPress site is vulnerable to this attack?
You're vulnerable if three conditions are all true: you have WPvivid version 0.9.122 or earlier installed, you have enabled the "Receive backup from another site" feature in WPvivid settings, and someone has attempted to exploit the vulnerability within the 24-hour encryption key validity window. Check your WPvivid version by going to Plugins > Installed Plugins and looking for the version number next to WPvivid Backup & Migration.
Why does the attack only work within a 24-hour window?
WPvivid uses RSA encryption keys to secure backup transfers between sites. These keys expire after 24 hours for security purposes. After expiration, the encrypted backup files become worthless to attackers. An attacker would need to discover the vulnerability window, identify a target, craft a malicious payload, and execute the attack all within 24 hours of the key being valid, which significantly limits real-world exploitation.
If I update WPvivid to version 0.9.123, am I completely safe?
Updating to version 0.9.123 patches this specific vulnerability, but it doesn't guarantee complete safety. You should also disable the "Receive backup from another site" feature if you're not using it, change your admin passwords as a precaution, scan your site for signs of compromise, and implement broader security practices like using a WAF and maintaining multiple backup strategies independently of WPvivid.
Should I uninstall WPvivid and use a different backup plugin?
Uninstalling WPvivid is not necessary if you update promptly to version 0.9.123 or later. WPvivid is a reputable, widely-used plugin developed by a professional team. One vulnerability doesn't mean it should be abandoned—all software has vulnerabilities. Instead, update immediately, monitor your site, and consider implementing additional backup layers for defense in depth. However, if you prefer a different backup tool, WordPress.org's plugin directory has alternatives like Updraft Plus, Duplicator, and Back WPup.
What signs should I look for to know if my site was compromised by this vulnerability?
Watch for: unexpected admin user accounts in Users > All Users, strange files in /wp-content/uploads/ directory, modifications to core WordPress files (detected by security plugins), unusual database changes, degraded site performance (potentially from crypto mining or malware), unfamiliar cron jobs in Tools > Site Health, or security plugin alerts about suspicious activity. If you suspect compromise, restore from a clean backup taken before any suspicious activity began.
Why do so many WordPress vulnerabilities involve improper file handling like path traversal?
File operations are deceptively complex. Developers need to validate file extensions, check file paths, verify permissions, and handle errors gracefully. Missing any of these steps opens security holes. Improper file handling is common because it requires specific security knowledge, and many plugin developers come from functional programming backgrounds rather than security backgrounds. Path traversal specifically has been a known vulnerability since the 1990s, yet it still appears regularly in modern code.
How does this vulnerability compare in severity to other recent WordPress plugin exploits?
With a CVSS score of 9.8 out of 10, CVE-2026-1357 is in the critical severity range, comparable to the most dangerous WordPress vulnerabilities. However, the requirement for specific conditions (backup reception enabled, 24-hour window, no default setting) makes real-world exploitation less likely than vulnerabilities with no preconditions. Vulnerabilities like the early versions of the Elementor Page Builder vulnerability (which had no preconditions) typically have higher real-world impact despite similar CVSS scores.
What should agencies managing multiple client sites do about this vulnerability?
Agencies should immediately audit which client sites have WPvivid installed and what version. Create a prioritized list: high priority for sites with backup reception enabled, medium priority for all other sites with vulnerable versions. Update critical sites first (within hours), then schedule updates for remaining sites. Maintain a change log documenting which sites were updated and when. Consider implementing automated plugin update management tools to prevent similar incidents in the future. Review your backup strategy to ensure you have independent backups not managed by any single plugin.
Conclusion: Securing WordPress Is a Continuous Process
The WPvivid vulnerability represents a critical moment for WordPress site owners to reassess their security practices. But it's important to keep this in perspective: WordPress as a platform isn't fundamentally broken, and WPvivid isn't a fundamentally insecure plugin. What we're seeing is the inevitable result of running thousands of independently developed plugins on millions of websites.
Security isn't a destination. It's a continuous process that requires vigilance, good practices, and quick response when problems arise. The WPvivid incident should serve as a reminder that:
Updates are not optional. When a critical security patch is released, treat it with urgency. The longer you wait, the longer attackers have to exploit the vulnerability. In an ideal world, security updates would be automatic. Until that becomes standard, you need processes to track and apply patches quickly.
Layered security works. No single tool—not WPvivid, not a security plugin, not a firewall—provides complete protection. Security comes from combining multiple approaches: keeping software updated, using a WAF, monitoring for suspicious activity, maintaining backups independently, and conducting regular audits.
Know your infrastructure. You can't protect what you don't know you have. If you're running multiple WordPress sites and can't immediately answer "what plugins are running on which sites and what versions are they?" then you have a more fundamental problem than any single vulnerability. Create an inventory. Document your setup. Make security visible.
Learn from incidents. Every major security incident teaches us something about the WordPress ecosystem. The WPvivid vulnerability teaches us that even mature, popular, well-intentioned plugins can have serious flaws. This should inform how you evaluate and trust your tools going forward.
If you're reading this in the weeks or months after the WPvivid vulnerability was disclosed, the most important action is simple: check your version, update if necessary, verify your settings, and move on. But take this moment to also think about the bigger picture of your WordPress security strategy. What would happen if your primary backup method was compromised? What backup layers exist below that? How quickly could you respond to a vulnerability in a critical plugin? These aren't questions to answer once and forget. They're questions to revisit regularly as your site and the WordPress ecosystem evolve.
WordPress powers nearly half the internet. That makes WordPress security everyone's responsibility. Individual site owners, developers, hosting providers, and plugin developers all have a role to play. The WPvivid vulnerability was found by security researchers working to make the ecosystem safer. Updates are available. The tools exist to protect yourself. What matters now is using them.
Additional Resources and Tools
Security Monitoring:
- Wordfence Security - Real-time security monitoring and malware scanning
- Sucuri Security - Website security platform with WAF and malware removal
- MalCare - Automated malware detection and removal
Backup Alternatives:
- Updraft Plus - Popular backup and migration alternative
- Duplicator - Migration and backup plugin
- Back WPup - Free backup scheduling plugin
Vulnerability Tracking:
- CVE Details Database - Track published vulnerabilities
- WPVuln DB - WordPress-specific vulnerability database
- CISA CVE Database - U.S. government vulnerability catalog
Key Takeaways
- CVE-2026-1357 is a critical vulnerability affecting WPvivid's 900,000+ installations, but only sites with 'receive backup from another site' enabled are truly vulnerable.
- The 24-hour encryption key expiration window significantly limits real-world exploitation, making mass attacks less likely despite the critical CVSS score.
- Update to WPvivid version 0.9.123 immediately—this is the essential first step, completed within hours rather than days.
- Implement layered backup strategies using multiple independent backup methods so no single tool compromise loses all recovery options.
- Plugin vulnerabilities represent 99% of WordPress breaches, not WordPress Core itself—this reflects broader ecosystem challenges around security quality and update adoption.
Related Articles
- Testing OpenClaw Safely: A Sandbox Approach [2025]
- Fake Chrome AI Extensions: How 300K+ Users Got Compromised [2025]
- iRobot's Chinese Acquisition: How Roomba Data Stays in the US [2025]
- Russia's DNS & DPI Blocking: YouTube, Telegram, WhatsApp & Alternatives
- Odido Data Breach: 6.2M Customers Exposed [2025]
- AI-Powered Email Threats: How Security Economics Are Changing [2025]
![WPvivid Plugin Security Flaw: Nearly 1M WordPress Sites at Risk [2025]](https://tryrunable.com/blog/wpvivid-plugin-security-flaw-nearly-1m-wordpress-sites-at-ri/image-1-1771009744786.jpg)



