Fake Chrome AI Extensions: How 300K+ Users Got Compromised [2025]
It sounds like a nightmare scenario that shouldn't happen in 2025, but it did. Security researchers discovered that over 300,000 people unknowingly downloaded what they thought were helpful AI assistants—only to realize these "tools" were actually sophisticated spyware. The extensions were sitting right there in the official Google Chrome Web Store, stealing everything from Gmail content to passwords to browsing history.
What makes this particularly unsettling is how it happened. The attackers didn't need to be tech geniuses or operate from some shadowy corner of the dark web. They simply uploaded fake AI tools to Google's official extension store, watched hundreds of thousands of people install them, and methodically harvested their data in the background.
The discovery came from Layer X, a Japanese security research firm that uncovered 30 separate malicious extensions masquerading as legitimate AI assistants. Among the most popular were tools with names like "AI Sidebar," "AI Assistant," and "Chat GPT Translate"—all designed to look legitimate and helpful while silently exfiltrating sensitive data.
This wasn't a small-time operation. The sheer number of installations (over 300,000) suggests these extensions operated for a significant period before being discovered. Users in multiple countries downloaded them, trusting that Google's Web Store vetting process had already done the security legwork. It turns out that wasn't necessarily true.
In this guide, we'll break down exactly what happened, how the attackers pulled it off, which extensions were involved, and most importantly, what you need to do right now to protect yourself and your data.
TL; DR
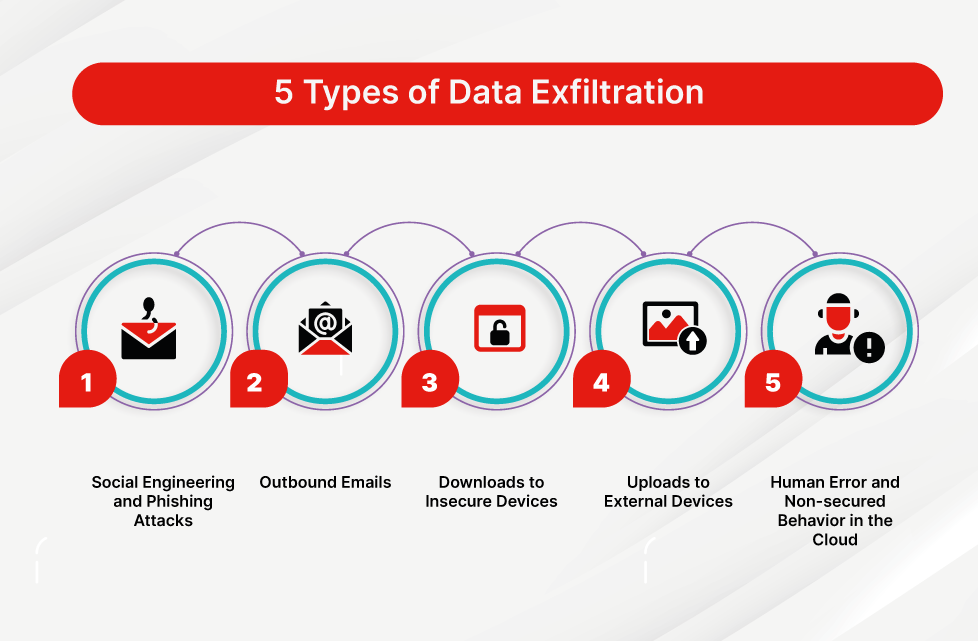
- 30 malicious Chrome extensions were discovered posing as legitimate AI tools with over 300,000 combined downloads
- The extensions used Mozilla's Readability library to steal page text, metadata, emails, and draft messages from Gmail
- Attackers used full-screen iframes to load malicious content remotely, allowing them to change extension behavior without triggering Web Store reviews
- Most popular compromised extensions included AI Sidebar (70K users), AI Assistant (60K users), and Chat GPT Translate (30K users)
- Victims should immediately uninstall suspicious extensions, change all passwords, enable two-factor authentication, and monitor accounts for unusual activity
- Google has since removed these extensions, but new variants continue to emerge regularly

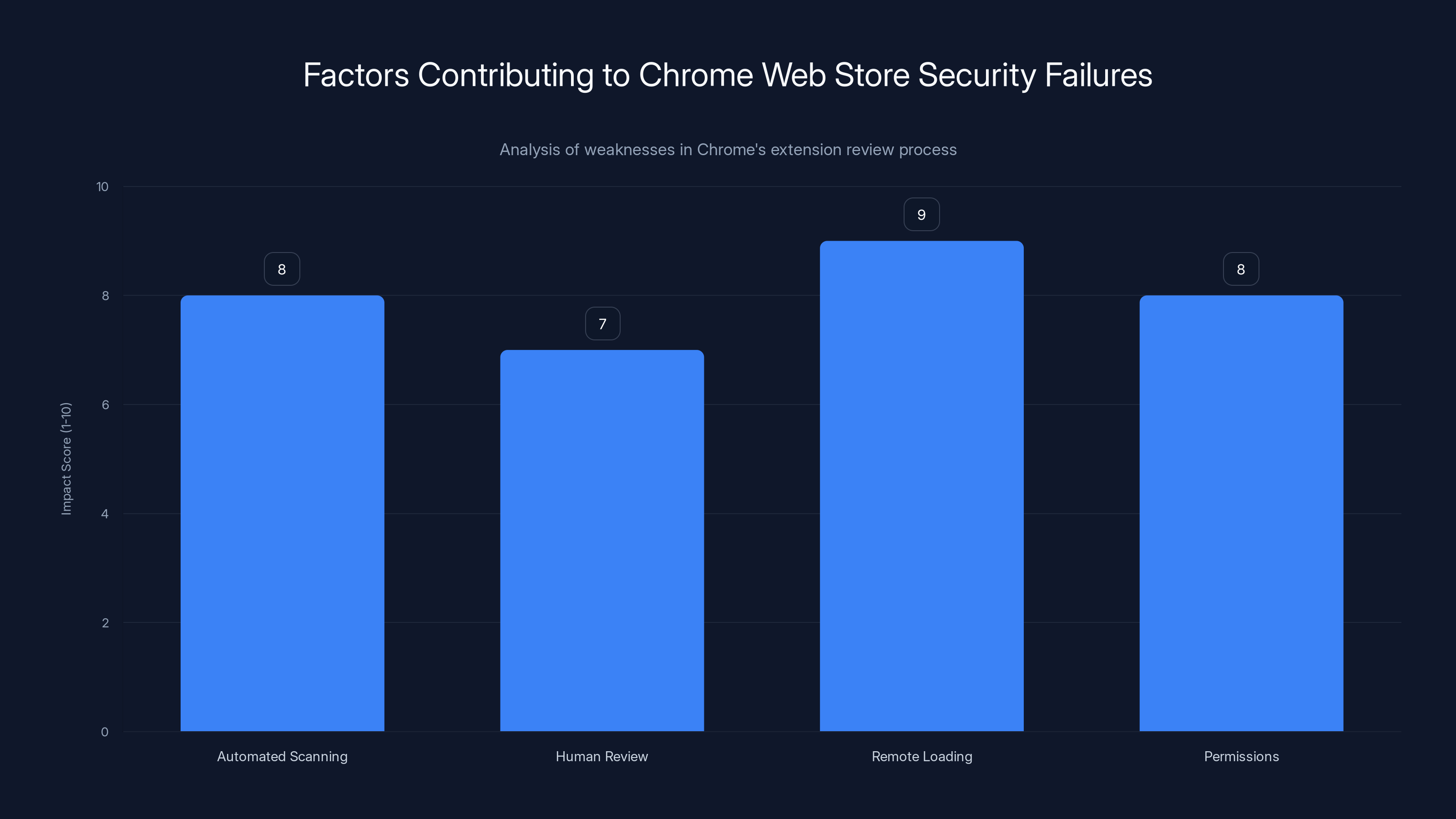
Remote loading and broad permissions were the most significant weaknesses, scoring 9 and 8 respectively, in Chrome's Web Store security review process. Estimated data.
Understanding the Attack: How 30 Extensions Compromised 300,000 Users
The scale of this operation was staggering. Think about the math: if even one of these extensions accumulated 70,000 downloads (which "AI Sidebar" did), that's 70,000 people who explicitly trusted this tool enough to grant it permissions to view and modify everything they do on the web.
What makes this particularly clever is the psychological element. People were installing these extensions during the AI boom of 2024 and early 2025. AI tools were everywhere, everyone was trying them, and seemingly legitimate "AI assistants" popping up in the Chrome Web Store felt completely normal. The attackers rode this wave of AI enthusiasm and converted it into massive reach.
The extensions themselves were functional. That's the insidious part. They actually did what they claimed to do—at least on the surface. "AI Sidebar" genuinely worked as a sidebar. "Chat GPT Translate" actually translated text. They weren't completely broken tools that would immediately raise suspicion. Instead, they performed their advertised functions while silently running malicious code in the background.
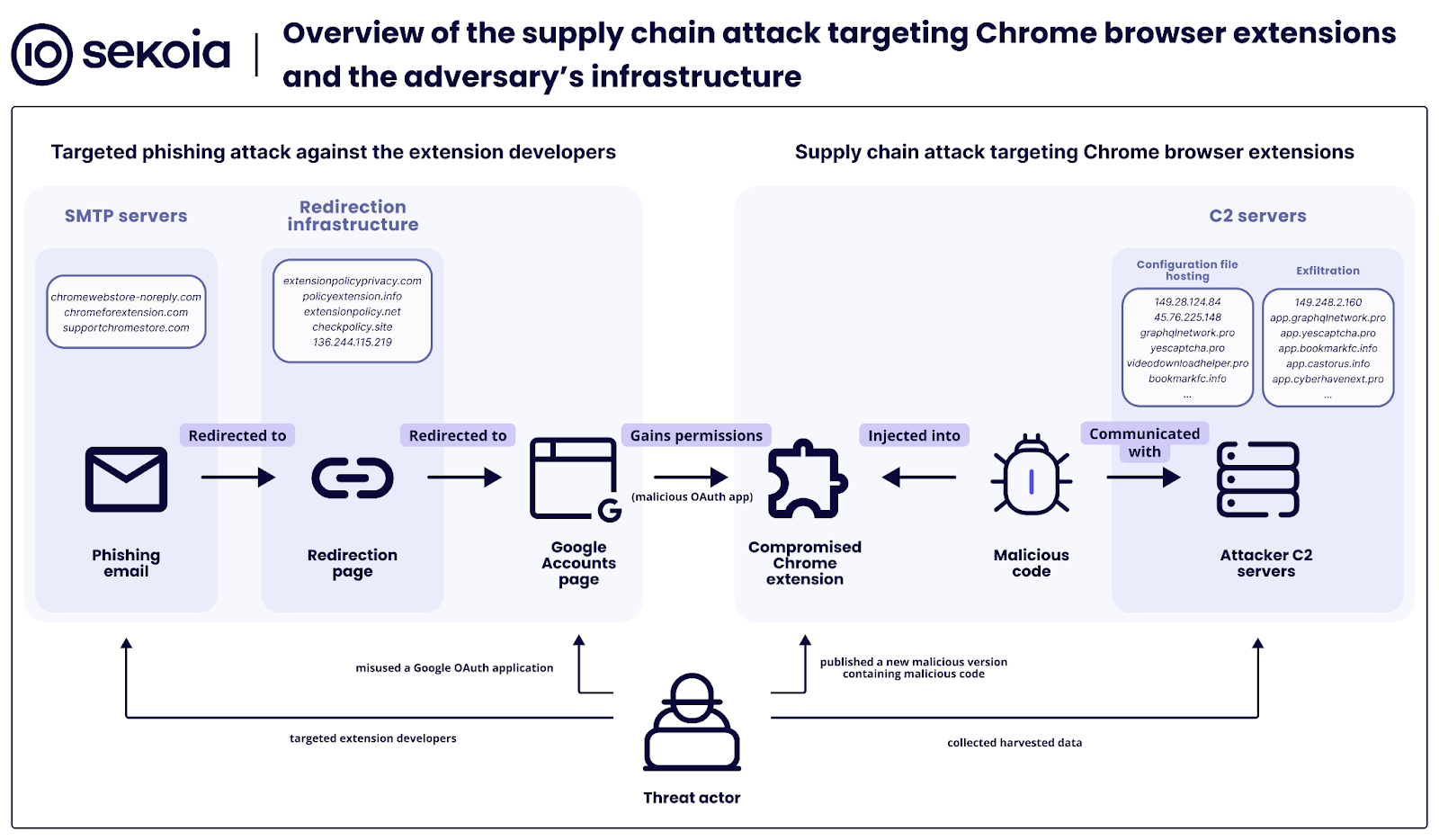
The Technical Architecture Behind the Theft
Here's where it gets technical. The attackers used a clever approach called Mozilla's Readability library. If you're not familiar with this, Readability is a legitimate, open-source tool that extracts the main text content from web pages, stripping away navigation, ads, and other noise. It's used by legitimate apps like Pocket and Instapaper to improve reading experiences.
But in the hands of bad actors, it became a data extraction tool. When you visited any webpage, the malicious extension would use Readability to pull out all the meaningful text, metadata (page titles, descriptions), and structured content. On regular websites, that's bad enough—your browsing data was being harvested. But the real nightmare scenario happened when you used Gmail.
The attackers discovered that a subset of 15 extensions included specific code targeting Gmail's interface. These extensions could read email subject lines, sender information, email body text, and even draft messages you were composing but hadn't sent yet. Imagine having someone read your emails—both the ones you received and the ones you were still writing. That's essentially what happened to tens of thousands of Gmail users.
How Data Was Exfiltrated Without Detection
The most sophisticated part of this attack wasn't the stealing—it was avoiding detection. Google reviews extensions before they appear in the Web Store, and it has automated systems monitoring extension behavior. How did these 30 extensions slip through?
The answer involves something called full-screen iframes. An iframe is like a window within a webpage that loads content from a different source. Normally, when an extension requests permissions or wants to run code, it does so locally—the code sits on your computer and runs there. Google's review systems can scan this code, identify malicious behavior, and block it.
But if an extension loads its functionality from a remote server using an iframe, the actual malicious code never gets directly reviewed during the approval process. It's hidden inside what appears to be a harmless container. Once the extension is approved and installed on users' machines, the attacker can update the remote server content at any time—change how it behaves, what it steals, how it exfiltrates data—all without pushing a new version through the Chrome Web Store that would trigger another review.
This is an incredibly clever loophole. It's like having your house pass an inspection with nothing illegal inside, and then after the inspector leaves, bringing in whatever you want because it's behind closed doors.
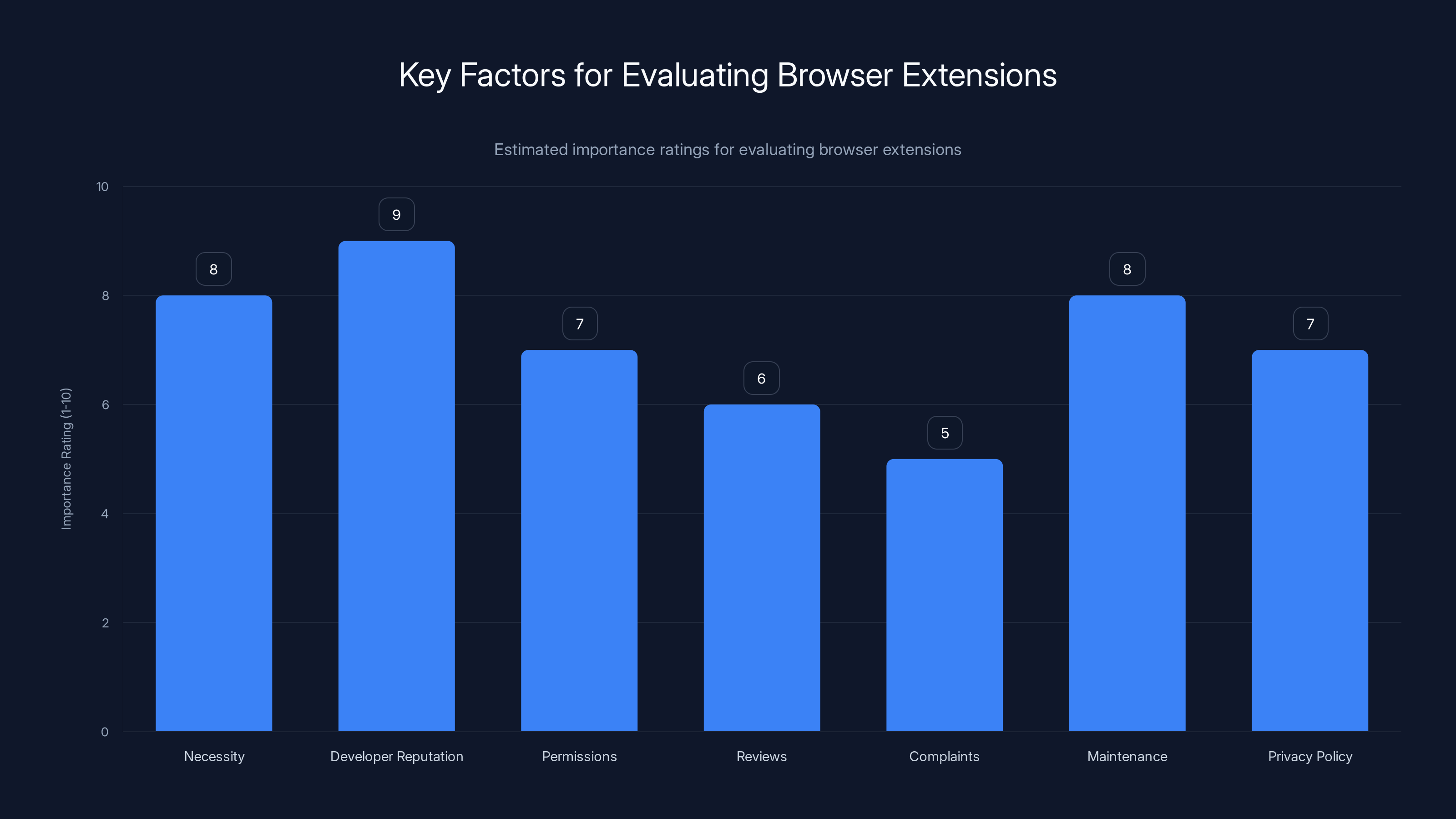
Developer reputation and necessity are the most critical factors when evaluating browser extensions for security. Estimated data.
The Complete List: Which Extensions Were Compromised
Layer X and subsequent security researchers have documented dozens of malicious extensions. The most critical ones to know about are listed below, along with their installation numbers at the time of discovery. If you installed any of these, you need to take immediate action.
Most Downloaded Malicious Extensions
AI Sidebar (ID: gghdfkafnhfpaooiolhncejnlgglhkhe) was the king of this malicious ecosystem. With 70,000 installations, it wasn't even the most recognizable name, but it was the most downloaded. People installed it thinking they were getting a helpful AI copilot for their browsing. Instead, they got a silent spy.
AI Assistant (ID: nlhpidbjmmffhoogcennoiopekbiglbp) came in second with 60,000 installations. The name is so generic it could describe a dozen legitimate tools. That anonymity might have been intentional.
Chat GPT Translate (ID: acaeafediijmccnjlokgcdiojiljfpbe) leveraged the massive brand recognition of Chat GPT with 30,000 installations. People probably figured this was either an official tool or at least something related to Chat GPT. It wasn't.
AI GPT (ID: kblengdlefjpjkekanpoidgoghdngdgl) had 20,000 installations, riding on GPT's reputation.
Chat GPT (ID: llojfncgbabajmdglnkbhmiebiinohek) was another Chat GPT impersonator with 20,000 installations. The straightforward naming convention probably made people think it was official.
AI Sidebar (ID: djhjckkfgancelbmgcamjimgphaphjdl) (note: different ID from the first one) racked up 10,000 installations. It's notable that multiple extensions had virtually identical names but different internal IDs.
Google Gemini (ID: fdlagfnfaheppaigholhoojabfaapnhb) leveraged Google's own AI product with 10,000 installations.
All told, these 30+ extensions accumulated over 300,000 downloads. For perspective, that's more users than the population of entire cities.
Why These Names Worked
Notice a pattern? The names are almost aggressively generic. "AI Sidebar." "AI Assistant." "Chat GPT." They're names that could describe thousands of legitimate tools. They leverage existing brand recognition (Chat GPT, Google Gemini) without explicitly claiming to be official products.
This is intentional obfuscation. An extension called "Super Secret Data Stealer" would never get approved and nobody would download it. But something called "Chat GPT Translate"? People assume Google's security team already vetted it. People assume it's either official or at least trustworthy. And by the time they realize something's wrong, months have passed and their data is already gone.
The Technical Deep Dive: How the Stealing Actually Worked
Understanding the mechanics of how these extensions stole data helps you understand why they were so effective—and why similar attacks will keep happening.
Step 1: Requested Permissions
When you install a Chrome extension, it asks for permissions. These aren't subtle. Chrome explicitly tells you what an extension can do: "This extension can read and change all your data on the websites you visit." That's a permission called <all_urls> and it's basically a skeleton key to your entire web experience.
For these malicious extensions, users granted those permissions willingly. They read "This AI assistant needs to access web pages to provide helpful features" and thought that was reasonable. Which, in a legitimate extension, it would be.
Step 2: Content Extraction
Once installed with full permissions, the extension ran its malicious code every time you visited a webpage. Here's what happened:
The extension would intercept the webpage content. Using Mozilla's Readability library, it would parse out the meaningful text and metadata. Readability is particularly effective because it's designed to identify the main content of a page—filtering out ads, navigation menus, and other clutter. So if you visited a news article, a social media feed, an online banking site, or your email, Readability would extract the essence of that content.
For most websites, this meant extracting article text, headlines, user comments, product information, etc. The extension would compile this extracted data into a structured format.
Step 3: Gmail-Specific Harvesting
The 15 extensions with Gmail-targeting code went further. They included additional logic specifically designed to parse Gmail's HTML interface. When you logged into Gmail, the extension would:
- Extract sender names and email addresses from your inbox
- Extract subject lines
- Extract the full body text of emails you were reading
- Extract draft text from emails you were composing but hadn't sent
- Extract recipient information from emails you were preparing to send
This is remarkably invasive. Someone could intercept your passwords if they were contained in email recovery messages. They could see sensitive conversations you had with doctors, lawyers, employers, or family members. They could read private drafts before you even decided whether to send them.
Step 4: Data Transmission
Once extracted, the data had to go somewhere. The extension would send this harvested information to attacker-controlled servers. The attackers used hidden windows (background frames) within the extension to transmit data, reducing the chance users would notice unusual network activity.
The transmission method was camouflaged. Instead of sending data with obvious labels like "user_email=bob@gmail.com", the attackers wrapped the data in legitimate-looking requests that mimicked normal browser traffic. To anyone casually monitoring their internet connection, it would look like normal web browsing.
Step 5: Remote Control and Updates
Here's the part that makes this attack nearly unstoppable: the attackers didn't hardcode the stealing logic directly into the extension. Instead, they made the extension fetch its instructions from a remote server they controlled.
This meant that even after an extension was approved by Google and installed on thousands of machines, the attackers could change what it did without pushing an update. If Google started investigating one extension for suspicious behavior, the attackers could change that extension's functionality overnight—making it legitimate-looking while still executing malicious commands on a subset of targets.
This remote control capability also meant the attackers could fine-tune their operation. If they noticed certain types of data were more valuable than others, they could adjust. If they found a new vulnerability in Gmail's interface, they could add code to exploit it. The installed extension became a zombie—the attacker's puppet that could be controlled and reprogrammed at will.
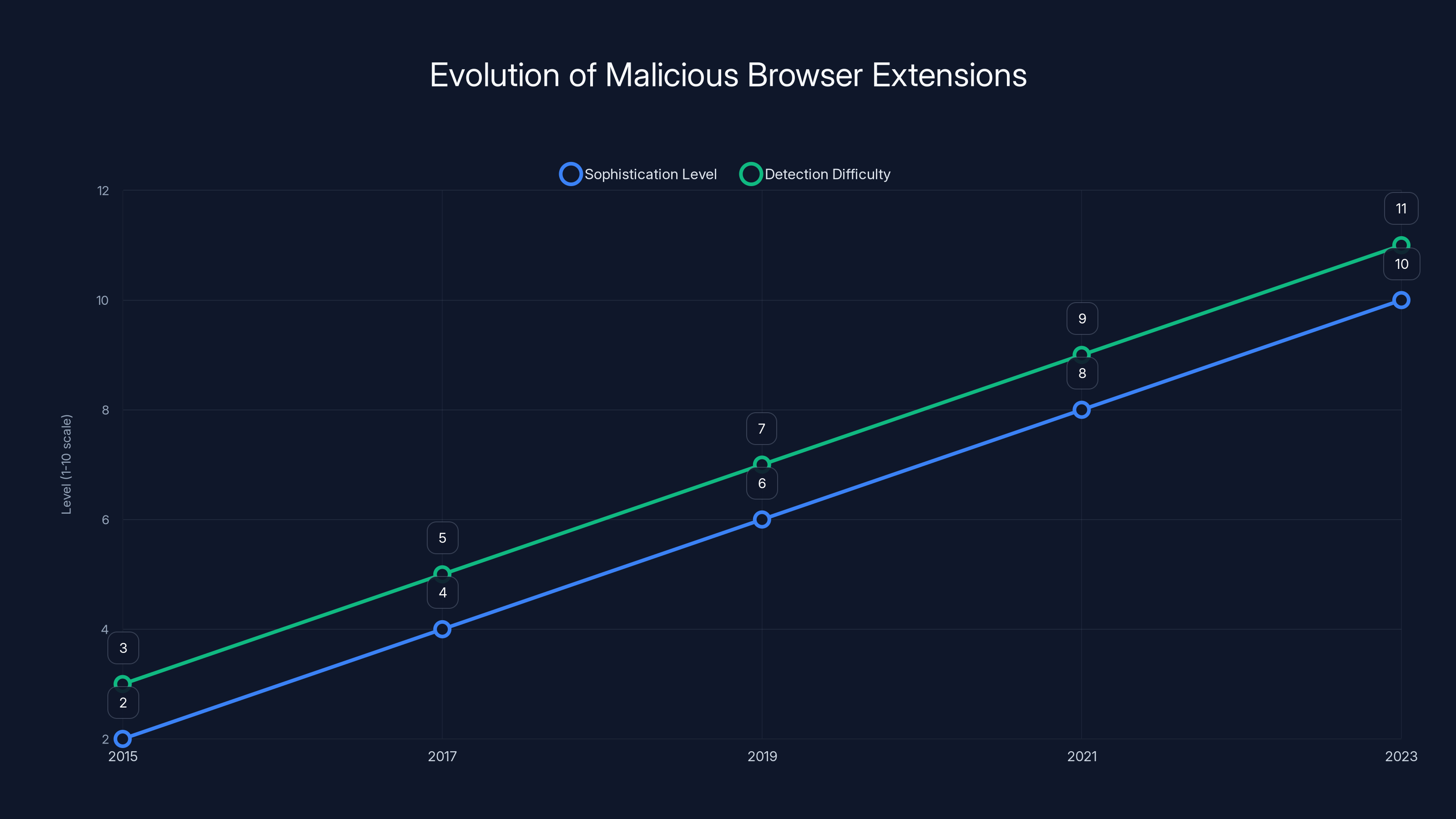
The sophistication of malicious browser extensions has increased significantly over the years, making them harder to detect. Estimated data.
The Detection and Removal: How Researchers Found What Google Missed
Here's the uncomfortable truth: Layer X, a private security research firm, discovered these extensions—not Google. The extensions were sitting in the Chrome Web Store for months, accumulating hundreds of thousands of installations, while Google's automated and manual review systems failed to catch them.
How did researchers finally discover them? Through behavioral analysis. Instead of looking at the extension code (which Google supposedly reviews), they monitored what the extensions actually did when installed and running. They watched the network traffic. They observed what APIs were being called. They tracked data exfiltration in real-time.
This is called "dynamic analysis" as opposed to "static analysis." Static analysis (which Google likely relies on) examines code without running it. Dynamic analysis runs the code in a sandboxed environment and watches what it does. The malicious extensions likely passed static analysis because their harmful code was loaded remotely or obscured, but they failed spectacularly at dynamic analysis because they actually behaved maliciously when running.
Once discovered, Google removed these extensions from the Web Store and pushed Chrome updates to disable them on users' machines. But this happened weeks after the extensions had already stolen data from hundreds of thousands of people. The damage was already done.
What About Extensions Already Removed?
One critical detail: even after Google removes an extension from the Web Store, users who already installed it will still have it on their computer unless they manually uninstall it. An extension doesn't just disappear from your system because it disappeared from the store. You have to actively remove it.
This means that even after Layer X's exposure, users who hadn't been paying attention to security news still had these extensions running, continuing to steal data.
Who Was Targeted: Geographic and Demographic Patterns
The malicious extensions weren't spread randomly. Analysis showed concentrated installations in specific countries and among specific user demographics.
Geographic Distribution
The extensions saw particularly high installation rates in the United States, Singapore, Denmark, Finland, Norway, Sweden, United Kingdom, Italy, Netherlands, Belgium, France, Germany, Spain, Canada, Mexico, Australia, and New Zealand. This geographic clustering suggests either:
- The attackers were targeting English-speaking countries specifically
- They were pushing the extensions through English-language communities
- They had specific motivations for targeting these regions (higher income, more valuable data)
The concentration in developed nations with high internet penetration suggests this wasn't random malware. The attackers were being strategic about who they targeted.
Demographic Targeting
While less data is publicly available about demographics, the types of extensions (AI tools) suggest the attackers were targeting a tech-savvy audience. People who actively use Chrome, who follow trends like AI, who install new tools to stay current—these are people more likely to have:
- Multiple email accounts
- Sensitive information in their browsers
- Higher net worth (and thus more attractive to criminals)
- Access to corporate systems (if using work email)
Some of the compromised users likely had corporate email addresses accessed through these extensions. Imagine an employee at a tech company installing "Chat GPT Translate" to improve their workflow, not realizing they're giving attackers access to their company email, internal documents sent through email, and potentially sensitive corporate information.
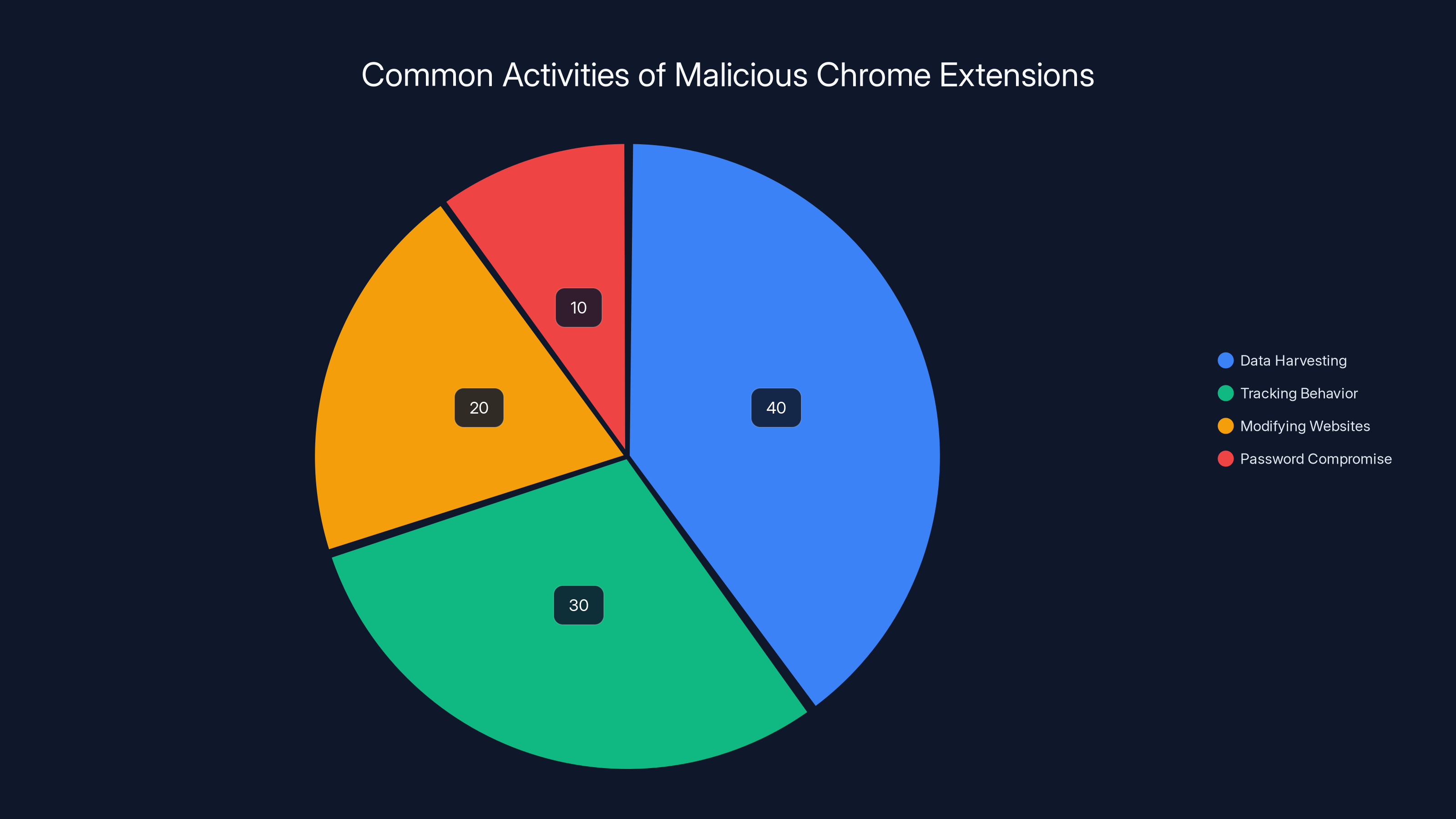
Estimated data shows that data harvesting is the most common activity of malicious Chrome extensions, followed by tracking user behavior.
The Data Stolen: What Actually Happened to Your Information
When researchers examined what was exfiltrated, the scope became clear: these weren't targeted, surgical attacks. They were indiscriminate data vacuums.
Types of Data Compromised
The extensions captured:
Email Content and Metadata: For Gmail users, this meant complete email bodies, subject lines, sender information, recipient information, and draft messages. The attackers could read everything in your inbox and everything you were writing.
Browsing History: Every webpage you visited while the extension was active was captured and sent to attackers. Your complete browsing history, essentially, became visible to criminals.
Form Data: When you filled out forms on websites—including login forms—the extracted text would include whatever you typed. This could capture usernames, partial passwords, credit card numbers, social security numbers, and personal information submitted to various services.
Authenticated Session Data: If you were logged into various websites, the extension would capture page content from those authenticated sessions. This could include banking information, e-commerce account details, social media content, and cloud storage information.
Metadata and Page Structure: Even information you didn't explicitly see, like page titles, meta descriptions, and hidden metadata, was captured and transmitted.
The Real-World Impact
For an individual user, here's what this meant:
Email Compromise: If your Gmail was compromised, attackers had access to all your emails and could reconstruct password reset flows. Many people use email as their "recovery" method for other accounts. If attackers could read your emails, they could potentially reset passwords for your bank, social media, cloud storage, and other services.
Identity Theft: Personal information extracted from emails, filled forms, and authenticated sessions could be used for identity theft. Attackers would have names, email addresses, birthdates, sometimes social security numbers, and other PII (Personally Identifiable Information).
Financial Fraud: If users visited banking websites while the extension was active, transaction history and account information would be harvested. Some users might have entered credit card information on vulnerable forms—which would be captured.
Credential Harvesting: Even if full passwords weren't captured, usernames, email addresses, and security questions could be extracted. This information could be used in credential stuffing attacks (trying the same passwords across multiple services) or for targeted social engineering.
Corporate Espionage: For users with corporate email accessed through their browsers, this could expose proprietary information, client lists, project details, and strategic information.
The Human Cost
Beyond the technical details, real people were harmed. Victims likely experienced:
- Account takeovers and fraudulent activity
- Identity theft requiring months to resolve
- Financial losses from fraudulent transactions
- The psychological stress of knowing their private communications were read
- Time spent contacting banks, credit bureaus, and support services
- Exposure of sensitive personal or professional information
Many victims probably never knew they were compromised. They installed what seemed like a helpful tool and went about their day, completely unaware that someone was reading their emails.
Why Chrome's Web Store Security Failed
Google has invested billions in security infrastructure. The Chrome Web Store is supposed to be a curated marketplace where users can install extensions with confidence. So how did 30 malicious extensions accumulate over 300,000 installations?
The Review Process Limitations
Google's extension review process involves both automated scanning and human review. But here's what researchers have discovered about the weaknesses:
Automated scanning is signature-based: Google's automated systems look for known malware signatures. If your malicious code doesn't match patterns Google has seen before, it passes. The attackers in this case likely obfuscated their code or used novel techniques that didn't match any known signatures.
Human reviewers have limited time: With millions of extensions submitted to the Chrome Web Store, Google can't spend hours deeply analyzing every single one. Reviewers look for obvious red flags: does the extension do what it claims? Are the descriptions truthful? Are there obviously suspicious permissions? These extensions passed this basic check because they actually did function as advertised.
Remote loading wasn't flagged: The critical vulnerability in this case—using iframes to load content from remote servers—should have been a red flag. But Chrome's review process apparently didn't flag this as suspicious. A legitimate extension might load UI elements from a CDN for performance reasons, so remote loading isn't inherently malicious.
Permissions are too broad: Chrome's permission system is binary for many powerful permissions. An extension either can access all websites and your data, or it can't. There's no middle ground. "AI Sidebar" needs to access webpages to function properly, which is a legitimate need. But that same broad permission also enables malicious data theft.
The Trust Problem
Ultimately, Chrome's Web Store suffers from a fundamental trust problem. Users assume Google has vetted extensions. Google has a responsibility to secure the store, but it also has incentives to approve extensions quickly (keeping the user experience smooth and selection broad). These incentives conflict.
Google is improving its security review process, but like all security measures, it's a perpetual arms race. As soon as Google adds detection for one attack method, criminals invent another.
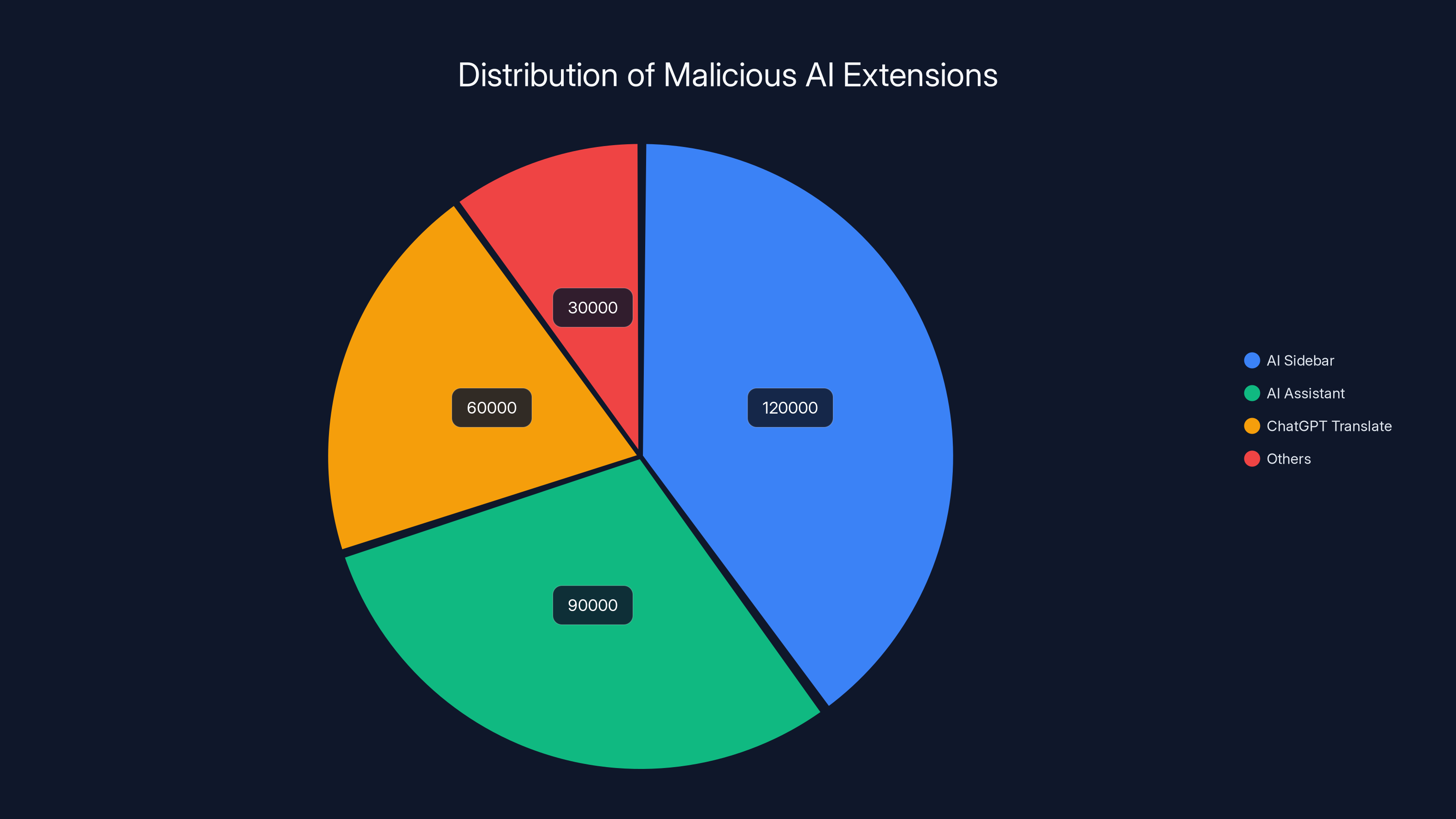
The pie chart illustrates the estimated distribution of installations among the most popular fake AI extensions. 'AI Sidebar' had the highest number of installations, followed by 'AI Assistant' and 'ChatGPT Translate'. Estimated data.
How to Check If You're Affected
Finding out whether you installed any malicious extensions is straightforward, though it requires taking action now.
Step-by-Step Detection Process
Step 1: Open Chrome and type chrome://extensions/ into the address bar. This opens your extensions dashboard.
Step 2: Review the list of installed extensions. Look for anything with "AI," "GPT," "Chat GPT," or generic AI-related names that you don't actively remember installing or using.
Step 3: Cross-reference the extension IDs with the known malicious list. The extension ID (a 32-character code) is visible in the extensions page. If you see any of these IDs, you have a problem:
- gghdfkafnhfpaooiolhncejnlgglhkhe (AI Sidebar)
- nlhpidbjmmffhoogcennoiopekbiglbp (AI Assistant)
- acaeafediijmccnjlokgcdiojiljfpbe (Chat GPT Translate)
- kblengdlefjpjkekanpoidgoghdngdgl (AI GPT)
- llojfncgbabajmdglnkbhmiebiinohek (Chat GPT)
- djhjckkfgancelbmgcamjimgphaphjdl (AI Sidebar variant)
- fdlagfnfaheppaigholhoojabfaapnhb (Google Gemini)
Step 4: If you find any of these, remove them immediately. Click the trash can icon next to the extension.
Step 5: Even if you don't find these specific extensions, review your entire extensions list. Are there extensions you don't recognize or don't actively use? If so, remove them. Keeping your extension list lean is a good security practice.
What If You Found a Malicious Extension?
If you discover you had one of these extensions installed, don't panic—but do take immediate action.
Immediately:
- Uninstall the extension
- Clear your browser cache and cookies
- Close and restart Chrome
Within the next few hours:
- Change your Gmail password from a clean device
- Change passwords for any other accounts that might have been accessed
- Check your Gmail's active sessions (in Gmail settings) and log out of any unrecognized sessions
- Enable two-factor authentication on your most important accounts if you haven't already
- Check your email recovery settings to make sure they haven't been changed
Within the next few days:
- Check your bank and credit card accounts for suspicious activity
- Review your Google Account's security settings at myaccount.google.com
- Check for password resets on social media accounts
- Consider placing a fraud alert with the major credit bureaus (Equifax, Experian, Trans Union)
Ongoing:
- Monitor your accounts for suspicious activity for at least 6 months
- Watch for phishing emails that might reference information only available from your stolen data
- Check your credit report (you're entitled to one free report annually at annualcreditreport.com)
Long-Term Protection: Browser Extension Security Best Practices
This incident highlights a critical vulnerability in how browsers handle extensions. But you can't just abandon extensions—they add legitimate value. Instead, you need a better strategy for managing them safely.
The Security Mindset for Extensions
Think of extensions like someone you're letting into your home. Would you give your house keys to a stranger? No. You'd vet them carefully. The same principle applies to extensions.
Before installing any extension, ask yourself:
-
Do I genuinely need this? Honestly, most users over-extend their browser with unnecessary tools. Fewer extensions means fewer attack surfaces.
-
Who made it? Is it from an established company with a reputation to protect? Is it open-source with active community review? Or is it from an unknown developer with minimal information?
-
What permissions does it request? Does it need access to all websites? Or could it work with limited permissions? Generic permissions that are broader than necessary are a red flag.
-
How many reviews and ratings does it have? Established extensions have thousands of reviews. Newer extensions with no reviews are riskier.
-
Are people complaining about it? Read the reviews, especially the negative ones. Do people mention suspicious behavior or privacy concerns?
-
Is it actively maintained? Check when the last update was. If an extension hasn't been updated in years, it's probably abandoned and won't receive security patches.
-
What's the privacy policy? Does the developer collect data? Do they sell it? Is their privacy policy transparent?
Specific Recommendations
Limit extensions aggressively: You probably don't need 20 extensions. Most people could get by with 3-5. Every extension you remove is an attack surface you eliminate.
Prefer official tools: If a tool offers a native app, use that instead of an extension. The Slack app, for example, is safer than a Slack extension. The Gmail website is safer than a Gmail extension.
Use privacy-focused extensions carefully: Popular privacy extensions like adblockers are generally legitimate, but they also request very broad permissions. Make sure you trust them. Stick with established options like u Block Origin (not u Block) or Ghostery from established developers.
Audit regularly: Every month or two, go back to chrome://extensions/ and review what you have installed. Remove anything you haven't actively used in the past month.
Keep Chrome updated: Use the latest version of Chrome. Updates often include security improvements for extension handling.
Consider alternative browsers: Firefox and Safari handle extension security somewhat differently. For maximum security-conscious users, Safari's more restrictive extension model may be preferable, though it limits available extensions.
Use browser profiles: Chrome allows multiple profiles. Consider using a separate profile with no extensions for sensitive browsing (banking, email, etc.) and a profile with extensions for general browsing.

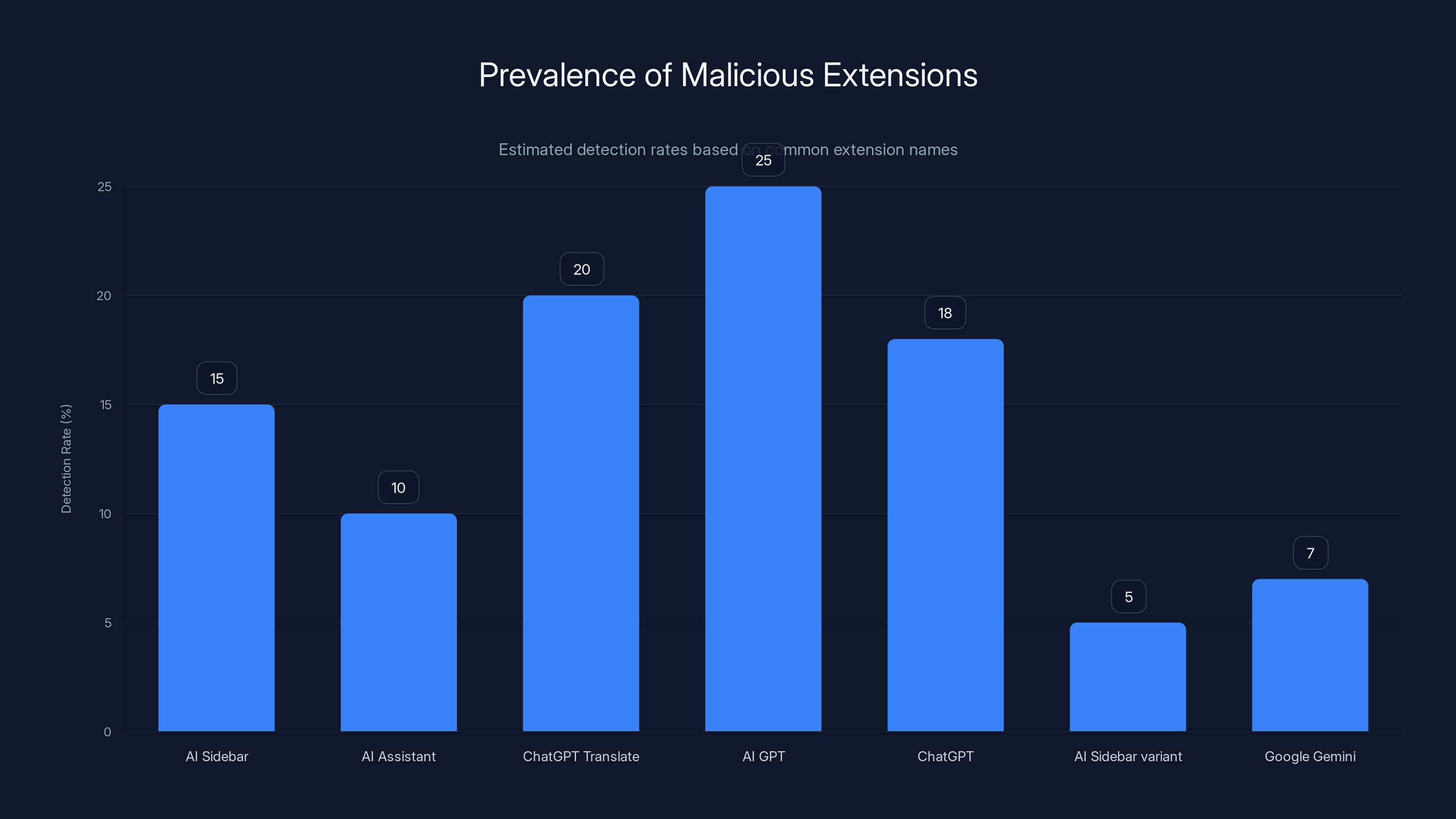
Estimated data suggests 'AI GPT' and 'ChatGPT Translate' have higher detection rates among users checking for malicious extensions. Estimated data.
The Broader Picture: Why Browser Extensions Are a Persistent Security Problem
This incident didn't happen in isolation. It's part of a troubling pattern that security researchers have been documenting for years.
The Extension Ecosystem Problem
Browser extensions occupy a unique position in computing. They have deep access to your browsing data and can run code on every website you visit. This power is necessary for legitimate extensions to work—an adblocker needs to see all webpage content to block ads. But that same power enables malicious behavior.
Meanwhile, extension stores (Chrome Web Store, Firefox Add-ons, Edge Add-ons) operate under inherent constraints. They can't thoroughly analyze every extension submitted. They rely partly on automated scanning and partly on human review, both of which have limitations.
The result: a persistent security vulnerability. The attackers don't need sophisticated zero-days or rare exploits. They just need to create an extension that looks legitimate, passes basic review, and functions as advertised while doing malicious things in the background. This is achievable with standard web development skills.
The Evolution of Malicious Extensions
Malicious extensions have become increasingly sophisticated. Early versions were obvious about their intentions—they would obviously break browsers or make it clear something was wrong. Modern malicious extensions are indistinguishable from legitimate ones from a user perspective.
The trend is toward:
Legitimate functionality + hidden malice: Extensions that work exactly as advertised while secretly exfiltrating data
Remote control: Using cloud servers to change extension behavior without pushing updates
Obfuscated code: Making the malicious code hard to detect through static analysis
Patience: Instead of creating obvious damage, modern malicious extensions quietly harvest data for months before being discovered
The Economic Motivation
Why do attackers bother? Because stolen data is valuable. Email access alone can be sold for money. Personal information can be used for identity theft, which is profitable. Corporate data stolen from employees' browsers can be sold to competitors or used for extortion.
A single successful malicious extension that infects 100,000 users could generate hundreds of thousands of dollars in revenue for the attacker. The cost to develop and distribute the extension is minimal—mostly just time. For attackers, the economics are compelling.
Similar Attacks: It's Happening Again
This specific campaign may have been discovered and shut down, but similar attacks continue constantly. Security researchers are regularly discovering new waves of malicious extensions.
Recent Examples
In early 2025, security teams identified a new variant targeting users in specific countries with similar tactics: create an AI-themed extension, get it approved, start harvesting data. The names change ("AI Writer," "Code Copilot," "Smart Assistant") but the methodology remains the same.
Outside the Chrome ecosystem, similar attacks have hit Firefox users and Edge users. Extension stores across browsers are targeted because they're lucrative attack vectors.
Why New Attacks Work
Each time a new malicious extension campaign launches, thousands of people install it before it's discovered. Why? Because:
- People forget previous attacks: Each new campaign targets users who don't remember previous incidents
- Extension names are generic: "Code Copilot" could describe dozens of legitimate tools
- Reviews are slow to accumulate: In the first weeks, a malicious extension might have zero negative reviews because nobody's noticed yet
- Security researchers have limited bandwidth: Only a few organizations actively hunt for malicious extensions
What Google and Browser Vendors Should Do
This incident raises questions about browser vendor responsibility. What should they do differently?
Potential Improvements
Stricter permission models: Instead of broad "access all websites" permissions, extensions could request specific permissions like "access email.google.com" or "read Gmail emails." This would limit the blast radius of compromises.
Dynamic analysis by default: Every extension should be run in a sandbox and monitored for suspicious behavior before approval. This costs more but catches techniques that static analysis misses.
Content security policy enforcement: Blocking remote code loading unless explicitly permitted and justified would close the iframe loophole used in this attack.
Mandatory disclosure: When malicious extensions are discovered, browser vendors should notify affected users directly, not rely on users to find out through news articles.
Regular re-review: Extensions should be periodically re-reviewed to catch behavior changes. If an extension was legitimately reviewed 2 years ago, code running today on the same extension should still be verified.
Automatic killing of confirmed malicious extensions: Instead of just removing from the store, browsers should actively disable known malicious extensions on users' machines.
Google has implemented some improvements, but none are comprehensive enough to prevent all attacks.

The Future of Extension Security
Looking ahead, the extension ecosystem faces existential questions.
Emerging Threats
As AI tools become more sophisticated, attackers will likely create more convincing fake AI extensions. Generative AI could help attackers create extensions with convincing fake reviews, descriptions, and even slightly different code for each user (personalized malware).
The attack surface also expands with the adoption of new extension capabilities. Manifest V3, Chrome's new extension architecture, was designed partly with security in mind, but it's still being debugged. New vulnerabilities will likely emerge.
Potential Solutions
Some researchers are exploring alternative models:
Capability-based security: Instead of extensions having blanket access to websites, they'd request specific capabilities like "modify forms" or "read email addresses." Users would grant granular permissions.
Decentralized review: Instead of centralized stores, extensions could be reviewed by community members, creating redundancy in the review process.
Reproducible builds: Requiring extensions to be reproducible from source code would make it harder to hide malicious code.
Better transparency: Publishing detailed telemetry about extension behavior changes, permission changes, and network activity would expose suspicious patterns faster.
None of these are silver bullets, but combinations of them could significantly improve security.
If You're a Developer: Don't Build Malicious Extensions
This might sound obvious, but it needs to be said: building malicious extensions is illegal. If you're considering doing it for money, understand the risks.
Cybercrimes involving data theft typically carry federal charges including violations of the Computer Fraud and Abuse Act, which can result in years of prison time and substantial fines. International law enforcement agencies actively pursue extension-based malware creators. The operators behind this recent campaign, if identified, would face serious criminal penalties.
More pragmatically: data harvested from stolen credentials and emails is currency in dark web marketplaces, but it's hot currency with short shelf life. By the time you're making significant money, law enforcement is likely investigating. Digital forensics can trace criminal activity backwards from payment flows, server logs, and infrastructure.
The risk-reward ratio is terrible. Don't do it.
What You Can Do Right Now
If you've read this far, you're probably concerned about your own security. Here's your action plan:
Immediate (Next 15 minutes)
- Open
chrome://extensions/in your browser - Review your installed extensions
- Delete anything suspicious, unknown, or unused
- Look specifically for the malicious IDs listed earlier in this article
Short-term (Next few hours)
- If you found a malicious extension, change your Gmail password
- Check your Gmail's active sessions and log out of unknown sessions
- Enable two-factor authentication on your Gmail account if not already enabled
- Check the recovery phone number and backup email associated with your Google account
Medium-term (Next few days)
- Change passwords on other important accounts
- Check your credit report at annualcreditreport.com
- Review your email for anything unusual
- Check your browser history for websites you don't remember visiting
Long-term (Ongoing)
- Audit your extensions monthly
- Keep Chrome updated
- Only install extensions from established developers
- Read extension reviews before installing
- Monitor your accounts for unusual activity
If at any point you notice suspicious account activity, contact your bank, credit card company, or email provider immediately. Fraudulent activity is easier to dispute if caught quickly.

FAQ
What is a malicious Chrome extension?
A malicious Chrome extension is software installed in your Chrome browser that appears to be legitimate but secretly performs harmful activities. These extensions might steal data, track your behavior, modify websites you visit, or compromise your passwords. The malicious extensions in this campaign appeared to be AI assistant tools while actually harvesting emails and personal data from users' browsers and Gmail accounts.
How do malicious extensions steal data?
Malicious extensions steal data by using the permissions users grant them when installing. Once installed, they can read page content on every website you visit, extract data using tools like Mozilla's Readability library, capture form submissions, and access authenticated pages where you're logged in. The extensions then send this harvested data to attacker-controlled servers through hidden network requests that disguise the traffic as normal browser activity.
How can I tell if I have a malicious extension installed?
You can check your installed extensions by typing chrome://extensions/ into your address bar. Review the list for extensions you don't recognize or remember installing, especially those with generic AI-related names like "AI Sidebar," "AI Assistant," or "Chat GPT Translate." You can also cross-reference the extension IDs with the known malicious list provided in this article. If you installed any extension from the malicious list before Google removed them, you likely have been affected.
What should I do if I installed one of these malicious extensions?
First, uninstall the extension immediately and clear your browser cache. Then change your passwords, starting with Gmail, from a clean device. Enable two-factor authentication on important accounts, check your email's active sessions and security settings, and review your accounts for suspicious activity. Consider placing a fraud alert with credit bureaus. Monitor your accounts for at least six months for signs of identity theft or fraudulent charges.
How do malicious extensions get approved by Google?
Malicious extensions pass Google's review by appearing legitimate. They often use remote code loading through iframes—the extension code that Google reviews performs harmless functions, but once installed, it loads additional malicious code from attacker servers that Google never sees. The extensions typically demonstrate their advertised functionality while quietly running malicious code in the background. Google's review process relies partly on automated scanning for known malware signatures, which novel obfuscation techniques can evade.
Can extensions installed on other browsers do the same thing?
Yes. Malicious extensions targeting Firefox, Edge, and other chromium-based browsers using similar tactics have been discovered. The vulnerability isn't unique to Chrome—it's inherent to how browser extension ecosystems work. Any browser that allows extensions has the potential for malicious extensions to be distributed through official stores, though the specific attack vectors may differ slightly.
How can I prevent malicious extensions in the future?
Limit your extensions to only those you actively use and trust. Before installing any extension, research the developer, check reviews (especially negative ones), and verify what permissions it requests. Only install from established developers with many positive reviews. Audit your extensions monthly and remove anything unnecessary. Consider using separate browser profiles for sensitive activities like banking, keeping them extension-free.
Do I need to reinstall Windows or Chrome?
Generally no, you don't need to completely reinstall. Uninstalling the malicious extension and clearing your browser cache removes the malware. However, if the extension had access for an extended period, you should treat it as if accounts may have been compromised and change passwords as a precaution. Your operating system wasn't directly affected—only your Chrome browser data was accessed.
What about my credit card information?
If you used a credit card on websites while a malicious extension was installed, the extension could have captured your credit card number, expiration date, and CVV if you entered them. Check your credit card statements for unauthorized charges. Contact your credit card issuer to report potential compromise and request a new card. Most credit card issuers have fraud protection, so unauthorized charges can often be disputed.
Can the attackers still access my data?
After you uninstall the extension, the attackers can no longer access new data—they can't see your new emails or browsing activity. However, data they already harvested (emails, passwords, personal information) is in their possession. That's why changing passwords and enabling two-factor authentication is crucial. The attacker may have historical data, but they can't leverage it without your current passwords.
Conclusion: The Reality of Browser Security in 2025
This incident is a stark reminder that convenience and security are perpetually at odds. Chrome extensions add tremendous value—they enhance functionality, improve productivity, and extend the browser's capabilities in ways the core browser doesn't support. But that same power that makes extensions useful also makes them dangerous.
The uncomfortable truth is that browser extension security will remain imperfect. Browser vendors are improving, but so are attackers. This is an ongoing arms race with no permanent victory condition. New malicious extensions will continue to be discovered. Users will continue to be compromised. The ecosystem's incentives—speed of review, breadth of extension selection, user convenience—work against security.
But knowing these risks, you're not helpless. By limiting extensions, carefully vetting what you install, monitoring your accounts, and staying informed about threats, you can significantly reduce your risk. You can't achieve perfect security in a browser extension ecosystem, but you can achieve reasonable security through thoughtful decisions.
The 300,000+ users affected by this campaign learned a hard lesson. Don't be one of the next 300,000. Review your extensions today. Change your passwords. Enable two-factor authentication. Audit your account security settings.
Your data is valuable—to you and to criminals. Treat it accordingly.

Key Takeaways
- 30+ malicious Chrome extensions accumulated over 300,000 downloads by posing as legitimate AI tools, successfully stealing emails and personal data from hundreds of thousands of users
- Attackers used Mozilla's Readability library to extract page content and Gmail-specific code to read emails, subjects, and draft messages before they were even sent
- Remote iframe loading allowed attackers to change extension behavior without pushing updates through the Chrome Web Store, bypassing Google's security review system
- Most popular compromised extensions were AI Sidebar (70K users), AI Assistant (60K), and ChatGPT Translate (30K), leveraging recognizable AI brand names
- Immediate actions: check chrome://extensions for malicious IDs, uninstall suspicious tools, change Gmail password, enable two-factor authentication, and monitor accounts for fraud
Related Articles
- 6.8 Billion Email Addresses Leaked: What You Need to Know [2025]
- Odido Data Breach: 6.2M Customers Exposed [2025]
- Odido Telco Breach Exposes 6.2M Users: Complete Analysis [2025]
- iRobot's Chinese Acquisition: How Roomba Data Stays in the US [2025]
- Russia's DNS & DPI Blocking: YouTube, Telegram, WhatsApp & Alternatives
- AI-Powered Email Threats: How Security Economics Are Changing [2025]
![Fake Chrome AI Extensions: How 300K+ Users Got Compromised [2025]](https://tryrunable.com/blog/fake-chrome-ai-extensions-how-300k-users-got-compromised-202/image-1-1771004408790.jpg)



