Odido's Massive Data Breach: What Happened and Why It Matters
When millions of people wake up to discover their personal information has been stolen, it's not just a tech story anymore. It's a privacy catastrophe that touches lives, bank accounts, and a sense of security that takes years to rebuild.
That's exactly what happened when Dutch telecommunications giant Odido confirmed in February 2025 that hackers had breached its systems and stolen sensitive data from over 6.2 million customers. For context, that's roughly one-third of the entire Dutch population. The scale alone should make your stomach drop.
But here's what really matters: this wasn't a random attack or a sophisticated zero-day exploit that nobody could have prevented. This was what security experts call a "foreseeable vulnerability" in a system that handles some of the most sensitive personal information humans generate.
The Odido breach is the latest domino to fall in a disturbing pattern of telecommunications companies getting hacked. Over the past 18 months, telcos across Singapore, Canada, Norway, the United Kingdom, and the United States have all experienced similar breaches. Some were attributed to nation-state actors conducting espionage. Others came from financially motivated criminal gangs. What's consistent is the target: your personal data.
In this article, we're going to break down exactly what happened with Odido, why telecommunications companies have become prime targets for hackers, what data was actually stolen, and most importantly, what you can do to protect yourself if you're one of the affected customers.
The Timeline: When the Breach Happened and How It Was Discovered
According to Odido's official statement, unidentified hackers gained unauthorized access to the company's customer contact system. The breach wasn't discovered immediately. In fact, there's a meaningful time gap between when the breach actually occurred and when Odido detected it.
This is a critical detail because it means the attackers had unfettered access to customer data for an unknown period. They were downloading files, copying databases, and extracting personal information without anyone knowing. That window of vulnerability is where the real damage happens.
The company didn't announce the breach until Thursday morning, which suggests they'd been investigating for some time before going public. This is standard practice, but it also raises questions. How long did they actually know? When did they first detect unusual activity? Were there warning signs they missed?
Odido has been less transparent about these specifics, focusing instead on what was stolen and assurances that they've "secured their systems." That language matters because it suggests the breach has been contained, but the reality is more complicated.
The timeline matters because it shows a fundamental vulnerability in how telecommunications companies monitor their networks. If a breach can go undetected long enough for millions of customer records to be exfiltrated, the monitoring systems themselves need serious reassessment.
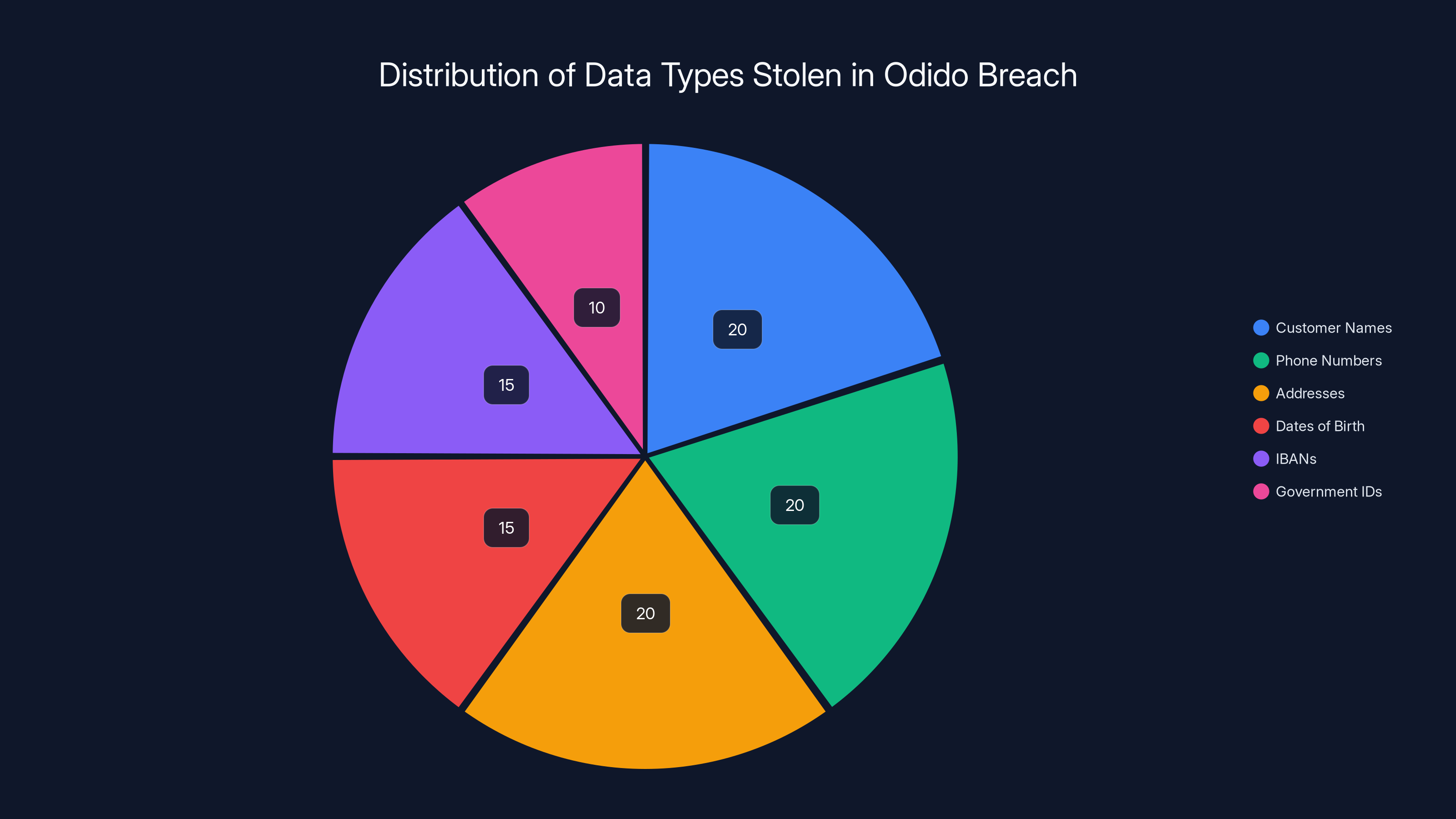
The Odido breach exposed various types of sensitive data, with customer names, phone numbers, and addresses being the most common. The inclusion of IBANs and government IDs poses significant risks for identity theft and financial fraud. Estimated data.
What Data Was Actually Stolen?
This is where things get genuinely alarming. Odido confirmed that hackers obtained the following customer information:
Confirmed stolen data:
- Full names
- Phone numbers
- Postal addresses
- Email addresses
- Dates of birth
- Bank account numbers (IBAN)
- Government-issued ID details (passport or driver's license numbers and expiration dates)
That's a comprehensive identity theft toolkit. When someone has your name, address, date of birth, bank account number, and government ID information, they have nearly everything required to open fraudulent accounts, take out loans, or impersonate you in financial transactions.
What's particularly concerning is the IBAN inclusion. Unlike credit card numbers with built-in fraud detection systems, IBANs are relatively static and don't have the same level of protection. Once a criminal has your IBAN, they can attempt direct transfers, set up automatic payments, or sell the information to other criminals who specialize in wire fraud.
The government ID details are equally dangerous. Your passport or driver's license number combined with your date of birth creates a strong foundation for identity fraud. Criminals can use this information to apply for credit, file tax returns, or even create synthetic identities that are more valuable than your actual identity.
What was NOT stolen (according to Odido):
- Call records and metadata
- Location data
- Billing information
- Image scans of government IDs
- Business customer data
Those exemptions are somewhat reassuring, but they also raise eyebrows. How do you breach a customer contact system but not access call records if they're stored in adjacent databases? The answer likely involves database architecture and access controls, but it suggests the hackers were either selective about what they took or were interrupted before they could access everything.
Why Telecommunications Companies Are Prime Targets
You need to understand why hackers and nation-states keep targeting telecom companies. It's not random. It's strategic.
Telecommunications companies are, by definition, the infrastructure layer of modern society. They know where people are, who they're calling, what they're talking about (sometimes), and how they pay. That's intelligence gold.
For nation-states conducting espionage, telecom breaches are extraordinarily valuable. If you can access a telecom company's systems, you can identify government officials and diplomats based on their call patterns. You can see who's meeting with whom. You can establish communication networks. That's why Chinese threat groups have been systematically hacking telecom companies across the globe.
For financially motivated criminals, telecom breaches offer access to financial information, identity documents, and contact information. They can sell this data on dark web markets, use it for direct fraud, or even use it as a foundation for social engineering attacks against other targets.
There's also a structural problem: many telecom companies were built during an era when security wasn't the priority it is today. Legacy systems are often patched rather than redesigned. Security is treated as a cost center rather than a core business function. And the sheer complexity of telecom networks makes comprehensive security exceptionally difficult.
Compare this to banks, which operate under strict regulatory frameworks with mandatory security standards and regular audits. Telecom companies have regulations, but they're often more focused on service availability than data protection.
Another factor: telecom companies operate in a highly competitive environment where costs matter. Investing in world-class security infrastructure is expensive, and it doesn't directly generate revenue. The incentive structure is misaligned with actual security outcomes.
The Global Pattern: Odido Isn't Alone
When Odido made its announcement, it wasn't headlines-grabbing because of its uniqueness. It was headlines-grabbing because of its predictability.
Just days before the Odido breach became public, Singapore's government confirmed that Chinese-linked hackers had compromised four of the country's major telecom companies. While those particular breaches didn't involve direct access to customer personal information, the attempt alone is significant. It suggests a sustained campaign.
And this is where the bigger picture becomes unsettling. Across the Northern Hemisphere, a threat group known as Salt Typhoon has been conducting an extensive campaign against telecommunications companies. This group, widely attributed to Chinese government interests, has successfully breached hundreds of phone companies in Canada, Norway, the United Kingdom, and the United States.
The objectives are clear: surveillance and espionage. These aren't attacks aimed at stealing customer data for financial gain. They're attacks aimed at identifying and monitoring government officials, diplomats, and other high-value intelligence targets. The fact that customer data sometimes gets stolen in the process is almost incidental.
Here's what makes this pattern terrifying: if government-level threat actors want access to a telecom company, they're going to get it eventually. The question isn't whether breaches will happen. The question is whether companies and governments are prepared for the inevitable when it does.
The Odido breach sits at the intersection of these two threat vectors. It could be financially motivated criminals looking to monetize customer data. It could be nation-state actors who got what they wanted and left other data behind. We don't know yet because the investigation is ongoing.
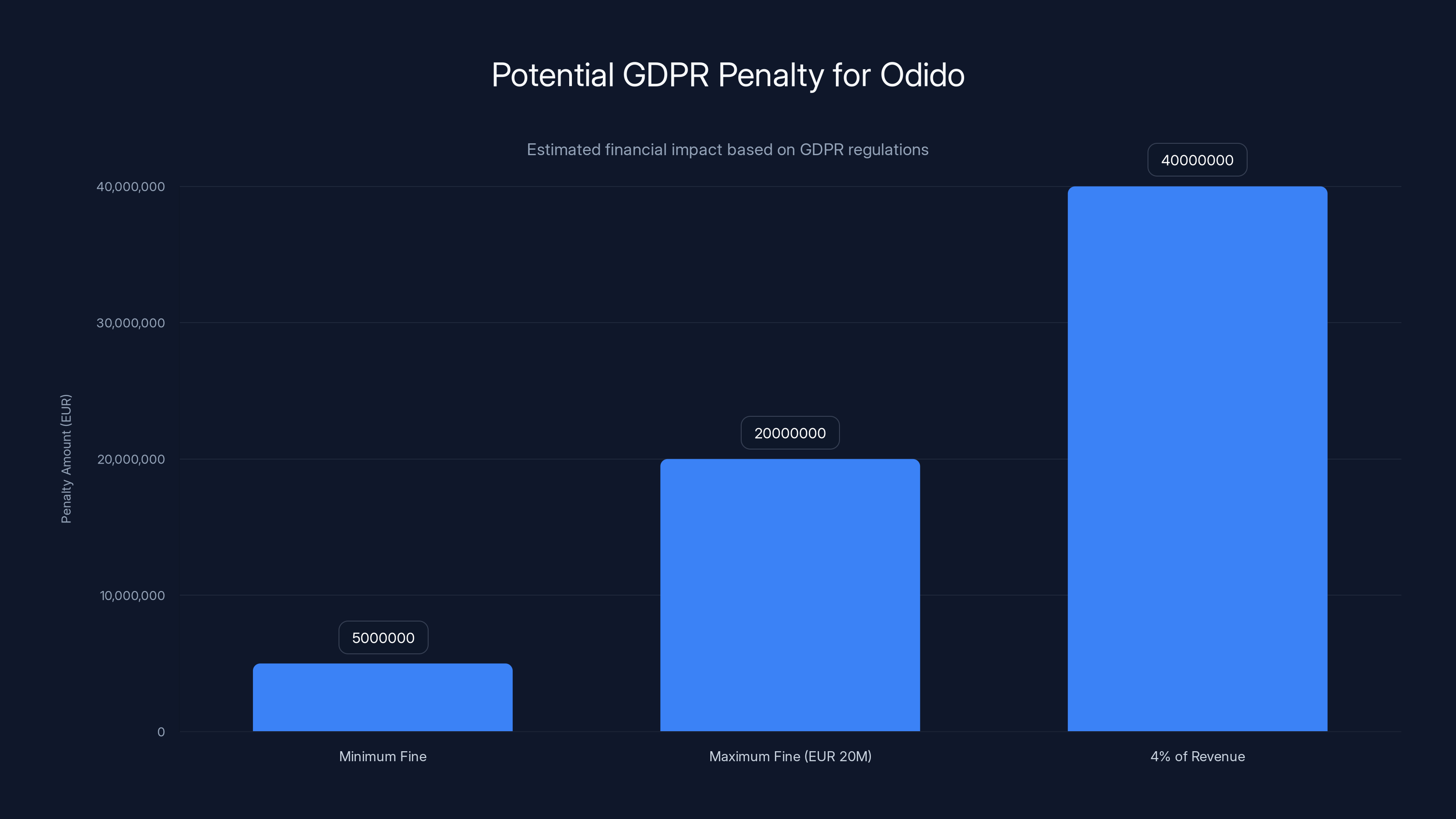
Estimated data shows that Odido could face fines ranging from EUR 5 million to EUR 40 million, depending on the severity of the breach and compliance with GDPR regulations.
The Scope: 6.2 Million Affected Customers
Let's put this number in perspective. 6.2 million people represents approximately 36% of the entire Dutch population. If you're Dutch, there's a roughly one-in-three chance your personal information was stolen in this breach.
For comparison, when a major US telecom company experiences a breach, it typically affects 1-3 million customers. The Odido breach is more than double that. It's not just a large breach. It's a nation-altering breach.
Odido also noted that former customers who had service within the past two years might be affected. This expands the potential victim pool even further. Anyone who's switched providers recently should assume their data is compromised.
The scope creates cascading problems. Investigation becomes more complex. Notification becomes more complicated. Fraud prevention becomes more resource-intensive. When you're dealing with millions of affected individuals, the infrastructure required to support them becomes strained.
Odido has set up support channels and is offering credit monitoring services to affected customers. But here's the reality: no amount of after-the-fact monitoring can reverse the fact that criminals now have comprehensive identity information on millions of people. The damage is permanent.

What About Business Customers?
One of the more surprising details from Odido's announcement is that business customers were not affected by the breach. The attackers specifically targeted the consumer customer contact system.
This distinction is important because it suggests a level of specificity in the attack. The hackers didn't just dump everything they could access. They went after the consumer database specifically. This could indicate either careful planning (they knew exactly what they wanted) or fortunate circumstance (they were interrupted before expanding laterally).
For business customers, this is a small mercy. But it also raises questions about database segmentation. If consumer and business customer data are stored separately with different access controls, that's actually a reasonable security practice. But if they were on the same network and the attackers simply chose not to access them, that's more concerning. It suggests they had broader access than they exercised.
Business customers should still assume that if someone was inside Odido's network long enough to steal 6.2 million consumer records, they probably identified and catalogued business customer information as well.
The Services That Remained Operational
Odido emphasized that phone, internet, and television services were not affected by the breach. This is reassuring from an operational perspective, but it requires some skepticism.
When hackers break into a telecommunications company, they typically target specific systems. They might focus on the customer relationship management system, the billing system, the provisioning system, or the data warehouse. The fact that operational systems remained unaffected suggests either that the attackers were specifically targeting customer data (not infrastructure disruption) or that Odido's network architecture kept operational systems isolated from customer-facing systems.
Given that the attackers successfully extracted 6.2 million customer records, operational continuity is actually the less impressive part of Odido's response. What matters is the forensics: understanding how the breach happened, what vulnerabilities were exploited, and how to prevent it from happening again.
The fact that phone, internet, and TV services continued uninterrupted also suggests that Odido detected and contained the breach before it could spread to more critical systems. That's a silver lining, but only barely.
How Did the Hackers Get In?
Odido hasn't publicly disclosed the specific attack vector that allowed hackers to access the customer contact system. This is understandable from a security perspective (you don't want to tip off copycat attacks), but it also leaves customers wondering: was this a known vulnerability? Could it have been prevented?
Common attack vectors for this type of breach include:
External attacks:
- Exploiting unpatched vulnerabilities in public-facing systems
- Credential stuffing (reusing leaked passwords from other breaches)
- SQL injection attacks against web interfaces
- API abuse or authentication bypass
Internal attacks:
- Compromised employee credentials
- Insider threats
- Lateral movement from a different compromised system
Supply chain attacks:
- Compromised third-party vendor with network access
- Software supply chain compromise
For a company of Odido's size, the breach likely involved one of the more sophisticated categories. Simple vulnerabilities usually get caught by security researchers or bug bounty programs before they can be exploited at scale.
The pattern of telecom breaches globally suggests that these companies are facing attacks from well-resourced adversaries (nation-states or advanced criminal groups) who have time to conduct reconnaissance, find vulnerabilities, and execute carefully planned attacks.
The Odido database, with 6.2 million records, could be sold for between USD
The Subsidiary Impact: Ben NL
Odido owns a subsidiary called Ben NL, which also had customers affected by the same breach. Both companies shared the same customer contact system, which explains why both were impacted simultaneously.
Ben NL is a smaller player in the Dutch telecom market, but the subsidiary structure is interesting because it shows how corporate ownership can create shared vulnerabilities. When you own multiple brands that share underlying infrastructure, a single breach can cascade across all of them.
For Ben NL customers, the impact is identical to Odido customers. The same data was stolen. The same notifications were sent. The same support services were made available.
But there's a business angle here worth noting. When subsidiaries share data infrastructure, it reduces operational costs and improves efficiency. But it also concentrates risk. A single vulnerability affects every brand that uses the shared system.
This is a trade-off that most companies make willingly because the operational benefits are immediate and the security risks are theoretical. Until the theoretical becomes real, and suddenly you're dealing with millions of affected customers across multiple brands.

The Response: Credit Monitoring and Support Services
Odido's immediate response included offering credit monitoring services to affected customers and establishing dedicated support channels for breach-related inquiries.
Credit monitoring is the standard response in breach situations because it can alert customers to fraudulent accounts being opened in their name. If someone uses your identity to apply for a credit card or loan, credit monitoring services will typically flag that activity.
However, credit monitoring is reactive, not preventive. It's helpful for catching fraud after it happens, but it doesn't stop criminals from having your information in the first place.
Moreover, credit monitoring only covers traditional credit products. It doesn't help if someone uses your IBAN and bank details to wire money directly from your account. It doesn't protect against sophisticated identity fraud schemes that don't immediately trigger credit checks.
For a company at Odido's scale, offering credit monitoring is also economically rational. It's cheaper to provide credit monitoring than to pay out fraud claims. It's a loss-mitigation strategy, not a customer protection strategy.
What would truly protect customers is a combination of approaches: fraud insurance, identity theft protection, and potentially cash compensation. Some companies have gone further, offering flat payments to affected customers as acknowledgment of the breach and the actual harm it causes (beyond just the theoretical fraud risk).
Regulatory Implications and Legal Exposure
The Odido breach triggers several regulatory frameworks that will affect how the company handles the aftermath and what penalties they might face.
In the European Union, all companies holding personal data of EU residents must comply with the GDPR (General Data Protection Regulation). The GDPR includes strict requirements for data protection, mandatory breach notification, and significant penalties for violations. The maximum fine is EUR 20 million or 4% of annual global revenue, whichever is higher.
For Odido, a company with billions in annual revenue, the GDPR fine calculation is complex. But 4% of revenue is a serious threat. Beyond the financial penalties, GDPR also requires companies to demonstrate that they implemented appropriate technical and organizational measures to protect personal data.
In the Netherlands specifically, there's also the Dutch Data Protection Authority (APG) which enforces GDPR compliance and can conduct independent investigations into breaches.
Odido likely faces investigations from these regulatory bodies that will examine whether the company's security practices were adequate. The investigation will focus on things like:
- What security controls were in place?
- Were they regularly tested and updated?
- Was there a security incident response plan?
- How quickly was the breach detected and reported?
- What documentation exists about security practices?
The answers to these questions will determine whether Odido is seen as negligent (high penalties) or merely unfortunate (lower penalties). In reality, most large breaches result in meaningful fines because regulators have increasingly adopted the position that companies of a certain size have a responsibility to maintain world-class security.
There's also potential for class action lawsuits from affected customers, particularly in jurisdictions that allow private rights of action for data breaches. Dutch law has been expanding consumer protection, so class actions are increasingly viable.

The Insurance Question
Companies like Odido often carry cyber liability insurance that covers costs associated with data breaches, including incident response, notification, credit monitoring, and regulatory fines up to certain limits.
However, cyber insurance typically includes exclusions for breaches resulting from certain types of negligence or failure to maintain basic security controls. If investigators find that Odido failed to apply critical security patches, didn't implement industry-standard encryption, or had other egregious failures, the insurance company might deny coverage or limit it significantly.
The details of Odido's insurance coverage are confidential, but given the size of this breach, the company is likely working closely with their insurance broker and legal team to understand what costs are covered and what might fall to the company itself.
This is another hidden cost of the breach that most customers never see. The money spent on legal fees, investigation, remediation, and insurance deductibles can sometimes exceed the cost of the breach notification and credit monitoring services.
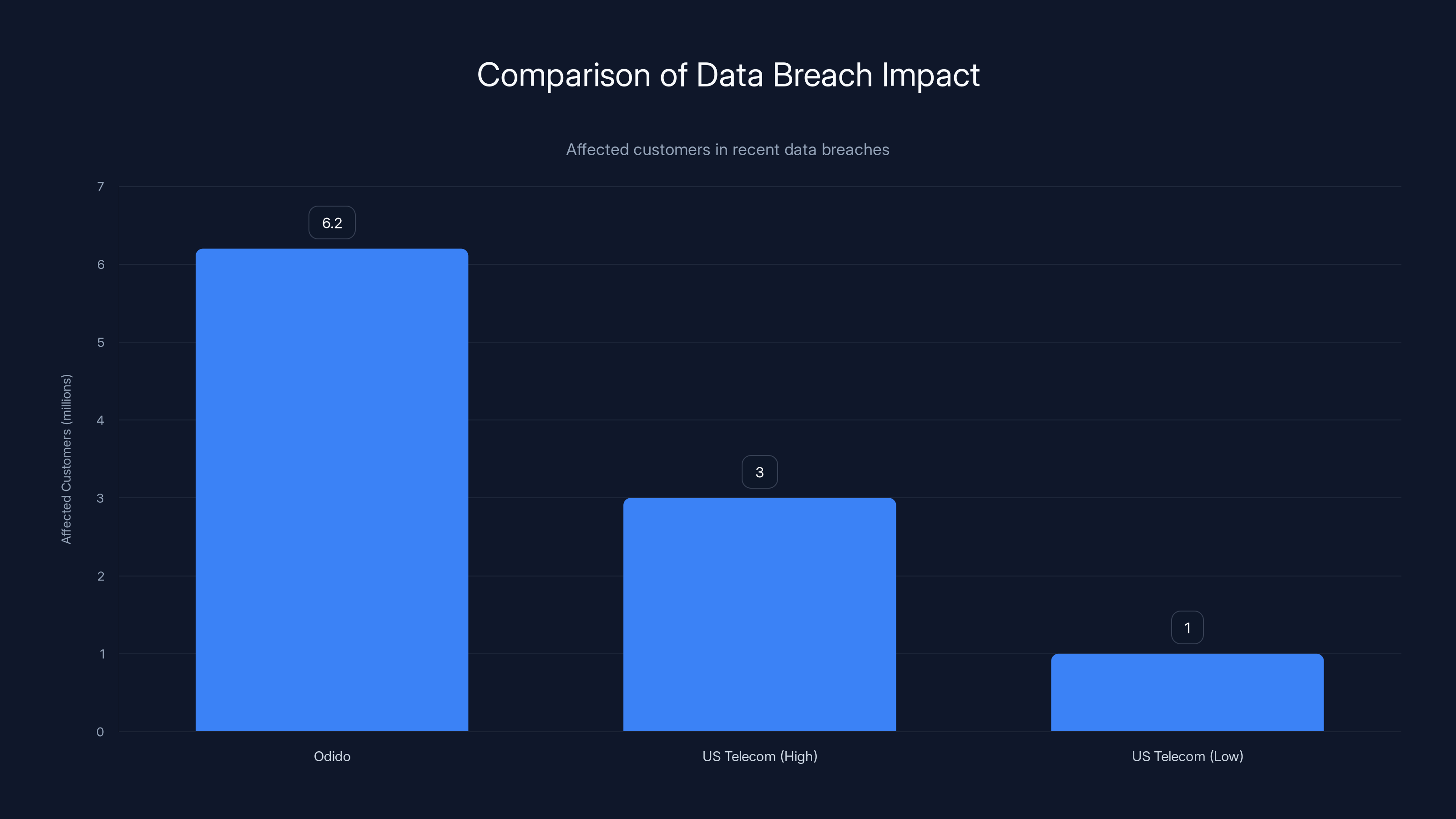
Odido's breach affected 6.2 million customers, more than double the typical high of 3 million seen in major US telecom breaches. Estimated data for US Telecom breaches.
Lessons for Other Telecommunications Companies
The Odido breach, combined with the global pattern of telecom breaches, sends a clear message to every other telecommunications company: you're next unless you fundamentally rethink your security.
For CTOs and CISOs at telecom companies, the Odido breach highlights several critical lessons:
First: Database segmentation matters. If customer data is isolated from operational systems, a breach in customer data doesn't immediately threaten service availability. This requires thoughtful architecture and clear data classification.
Second: Access controls need continuous validation. How did hackers get access to the customer contact system? If internal investigations find that access controls were too permissive or weren't properly maintained, that's a systemic problem affecting other systems too.
Third: Detection speed is critical. The longer a breach goes undetected, the more data is stolen. Implementing real-time alerting for unusual data access patterns could have limited the damage.
Fourth: Third-party risk management is essential. If the breach came through a vendor or supply chain compromise, other telecom companies need to audit their third-party vendor security practices.
Fifth: Incident response readiness matters. How fast can you disconnect compromised systems? How quickly can you identify what data was accessed? How efficiently can you notify millions of customers? These operational capabilities separate companies that handle breaches well from companies that create additional damage through poor response.
For CISOs across the telecom industry, the Odido breach is both a warning and a roadmap for identifying similar vulnerabilities in their own organizations.

What Should Affected Customers Do Immediately?
If you're one of the 6.2 million affected customers (or a Ben NL customer), here are the steps you should take right now:
Contact your bank immediately:
- Inform them about the IBAN breach
- Ask about setting up transaction limits for transfers
- Request additional authentication requirements for suspicious transactions
- Review recent account statements for unauthorized activity
Place fraud alerts:
- Contact your credit bureau and place a fraud alert on your credit file
- This makes it harder for fraudsters to open accounts in your name
- You can usually do this online or by phone
Freeze your credit if possible:
- If your jurisdiction allows it, place a credit freeze
- This locks your credit and prevents new accounts from being opened without your explicit permission
- It requires thieves to unfreeze your credit to commit identity fraud, significantly raising their effort
Monitor credit reports obsessively:
- Get a free credit report from the Dutch credit bureau
- Review it for accounts you don't recognize
- Check it regularly (not just once)
Be suspicious of unexpected communications:
- Fraudsters often use stolen identity information to call banks, government agencies, or other organizations
- If you receive an unexpected call claiming to be from your bank or government, hang up and call them directly
- Don't provide personal information over unexpected calls
Change your passwords if they were involved:
- If you used the same password for your Odido account and other services, change those passwords immediately
- Use unique, strong passwords for important accounts
Document everything:
- Keep records of calls to banks, credit bureaus, and Odido
- Document any fraudulent activity you discover
- These records are important if you need to prove fraud later
Consider identity theft insurance:
- Beyond credit monitoring, identity theft insurance can help cover costs if you become a victim
- Some policies cover legal fees, lost wages, and other associated costs
The Dark Web: Where Your Data Might End Up
Within days or weeks of the Odido breach becoming known, the stolen data will likely be offered for sale on dark web marketplaces. This is the standard playbook for financially motivated threat actors.
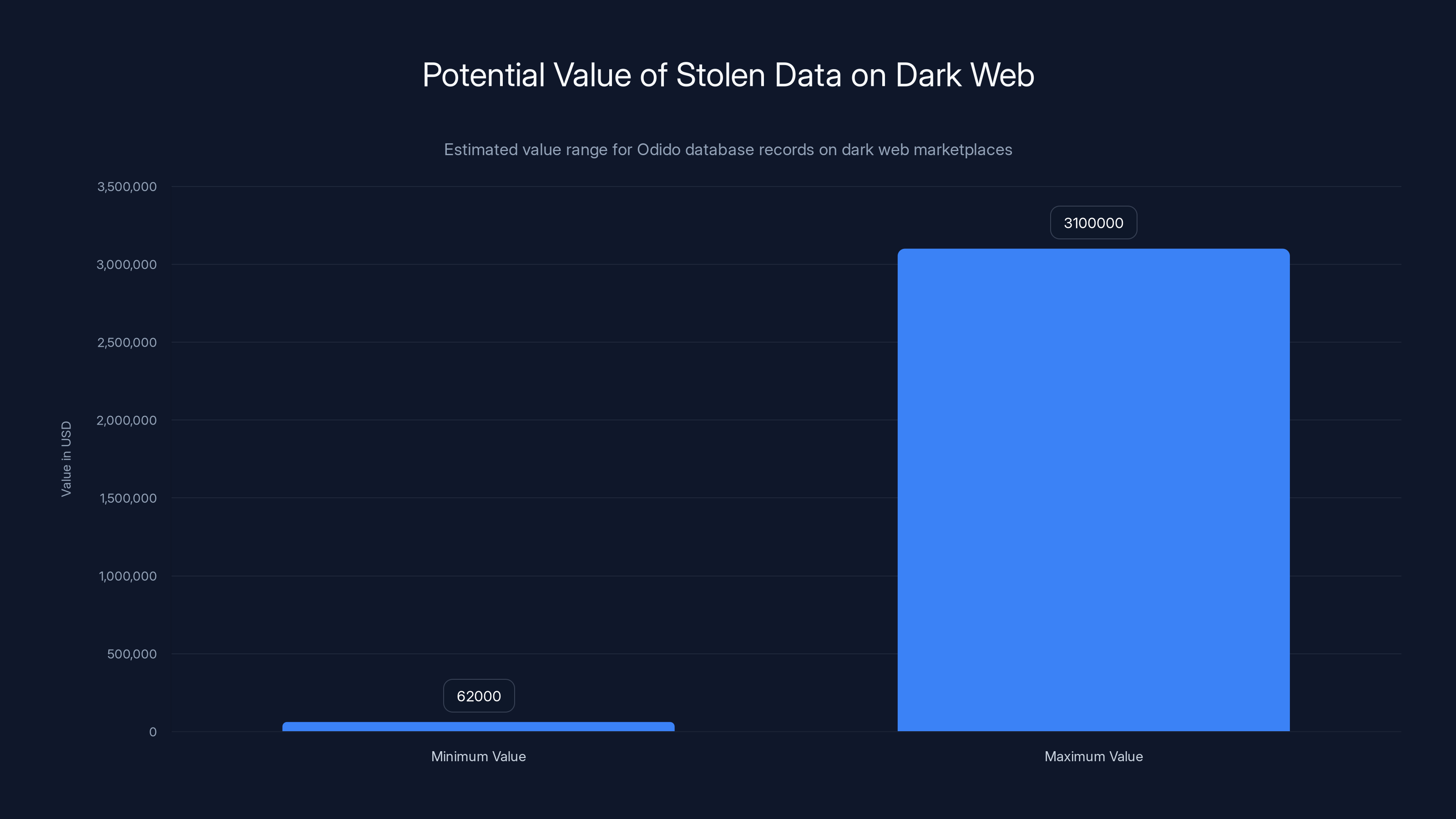
On dark web markets, customer databases are typically sold by the record count. A database with 6.2 million records containing full identity information (name, address, phone, email, date of birth, IBAN, ID numbers) would typically sell for anywhere from USD
At those prices, the Odido database could be worth USD
Once the data is on dark web markets, it becomes a commodity. It gets bought, bundled with other breaches, cross-referenced with other datasets, and potentially used as a foundation for much larger fraud schemes.
For example, a criminal might buy the Odido database and cross-reference it with other breaches to find individuals with significant assets. They then use the identity information to apply for loans or credit cards. Or they sell the data in bundles to other criminals who specialize in different types of fraud.
This is the downstream effect of breaches that's often invisible to victims. Your data doesn't just disappear. It becomes a permanent asset in the underground economy.
One emerging service in dark web markets is "data enrichment," where brokers take existing data (like the Odido database) and combine it with other sources (leaked credit reports, public records, other breaches) to create even more valuable datasets. A criminal might buy your IBAN from the Odido breach, cross-reference it with other data sources to find your current employer and income level, and then use that enriched dataset to target you for a specific fraud scheme.

How Governments Should Respond
The Odido breach puts pressure on Dutch and European governments to strengthen regulations and oversight of telecommunications companies. The pattern of breaches globally suggests that the current regulatory framework isn't sufficient to prevent these incidents.
Possible policy responses could include:
Mandatory security standards: Rather than relying on companies to self-assess their security, governments could mandate specific security controls, testing schedules, and verification requirements. Similar to how hospitals must comply with healthcare regulations.
Data minimization requirements: Governments could require telecommunications companies to collect and retain only the minimum customer data necessary to provide services. Fewer data stored means smaller breach impact.
Encryption mandates: All customer data should be encrypted at rest and in transit. This wouldn't prevent breaches, but it would make stolen data less usable.
Rapid notification requirements: Some jurisdictions now require breach notification within a specific timeframe (e.g., 72 hours). Faster notification means companies can't hide breaches or delay investigations.
Breach liability insurance: Governments could require telecommunications companies to carry insurance for breach costs, creating a financial incentive for better security.
Enhanced penalties: Current fines aren't proportionate to the damage caused by mass breaches. Higher penalties would incentivize better security practices.
Executive accountability: Tying executive compensation to security metrics could align incentives between company leadership and actual security outcomes.
These policy responses require balancing competing interests: strengthening security without placing impossible burdens on companies, protecting privacy without stifling innovation, and creating accountability without creating perverse incentives.
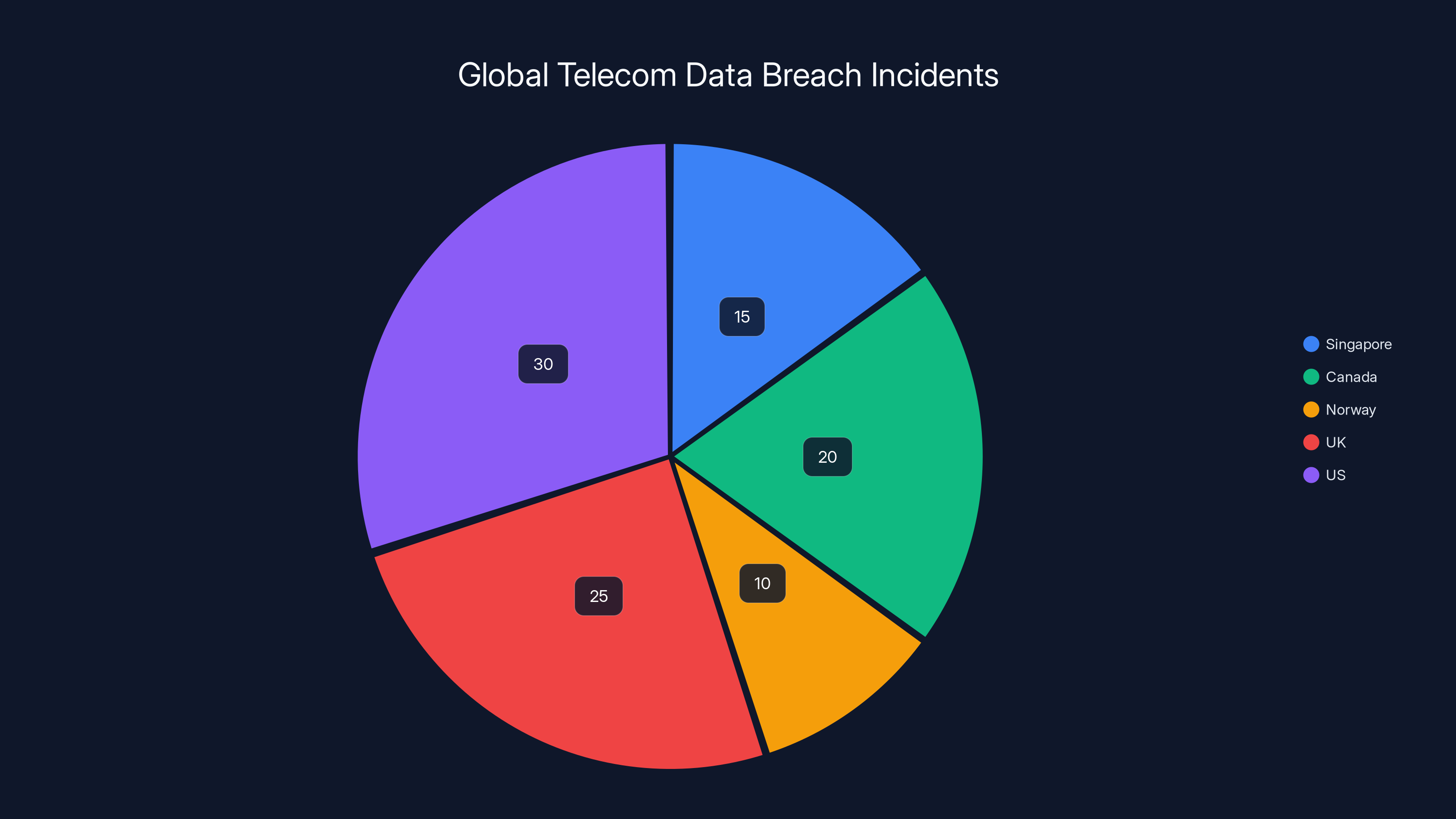
Estimated data shows the US and UK leading in telecom data breaches, highlighting a global pattern of vulnerability. Estimated data.
The Long-Term Impact on Consumer Trust
The Odido breach, along with the pattern of telecom breaches globally, has a cumulative effect on consumer trust. When your telecommunications company—a service provider you depend on daily—gets hacked and your most sensitive personal information is stolen, it changes how you view that company's competence and trustworthiness.
For Odido, the immediate impacts are customer churn (people switching to other providers), brand damage, and potential legal liability. But the longer-term impact is on the entire category of telecommunications companies in the Netherlands.
Consumers learn from this breach. They learn that telecom companies might not adequately protect their data. They learn that breaches affecting millions of people are possible and maybe even inevitable. They learn that the companies' response is credit monitoring and support services, not accountability and meaningful compensation.
Over time, this erodes the social contract between service providers and customers. Customers become more skeptical. They share less information. They're more likely to switch providers. They're more likely to demand stronger privacy protections.
For companies, this creates a long-term problem: trust takes years to build and minutes to destroy. Odido and other breached telecom companies will spend years rebuilding their reputation and proving that they've actually improved security. Some customers will never come back.

Looking Forward: Will This Happen Again?
Yes. Absolutely. Unless there's a fundamental shift in how telecommunications companies approach security, we'll see more breaches like Odido.
Here's why: the economic incentives don't align. For a telecom company, investing in world-class security is expensive and doesn't directly generate revenue. It's treated as a cost center. The alternative—accepting the risk of breaches and managing the aftermath—is often cheaper than preventing every possible breach.
That changes only when the cost of breaches exceeds the cost of prevention. We're not there yet. A breach affecting 6 million customers results in regulatory fines of tens of millions of euros, but for a multi-billion dollar company, that's a manageable cost.
Second, the threat landscape is getting worse, not better. Nation-states continue to target telecom companies for espionage purposes. Criminal groups continue to target them for financial gain. As long as the incentives exist, the attacks will continue.
Third, there's an asymmetry in cybersecurity. Defenders have to protect against all possible attacks. Attackers only need to find one vulnerability. As systems get more complex, the surface area for vulnerabilities grows. It's a fundamental asymmetry that suggests breaches are not just likely but inevitable.
The realistic question isn't whether Odido or other telecom companies will experience breaches. The realistic question is how quickly they can detect breaches and limit the damage.
The Responsibility Distribution Problem
Here's something that doesn't get discussed enough: the responsibility for the Odido breach is actually distributed across multiple parties, and that distribution affects how we should think about the problem.
Odido's responsibility: The company is responsible for maintaining reasonable security practices, detecting breaches, and responding appropriately. They failed at detection (how long did it go undetected?) and their preventive security was insufficient.
Regulatory responsibility: Governments set standards and enforce compliance. But standards are often written in vague language like "appropriate security measures" rather than specific technical requirements. This gives companies wiggle room to under-invest.
Industry responsibility: The telecom industry could voluntarily establish higher security standards and share threat intelligence more actively. Instead, companies often treat security as competitive advantage and guard information carefully.
Customer responsibility: At a certain level, customers need to assume their data might be compromised and take defensive actions. This isn't fair, but it's realistic.
Attacker responsibility: Nation-state actors conducting espionage and criminal groups conducting fraud bear responsibility for the actual data theft. But they also understand that the risk-reward is favorable.
The Odido breach is ultimately a failure across all these layers. It's not a single responsible party. It's a system-wide failure of security, regulation, transparency, and incentive alignment.
Fix requires action at multiple levels simultaneously. Companies need to invest in security. Governments need to strengthen standards and enforcement. Customers need to protect themselves. Industry needs to cooperate more on threat intelligence.
The breach happened anyway, which suggests the system isn't working as well as it should.

Alternative Perspectives: Was the Breach Preventable?
Here's the uncomfortable question: Could Odido have prevented this breach?
The honest answer is: probably, but not certainly.
If the breach resulted from an unpatched known vulnerability, then yes, it was preventable. Applying security patches is table stakes for security. Any company not doing that has failed at basic security.
If the breach resulted from insufficient access controls (e.g., administrative credentials that weren't properly protected), then yes, it was preventable. Access control is fundamental.
If the breach resulted from a sophisticated supply chain attack through a third-party vendor, it's more complicated. These attacks are designed to evade detection and exploit trust relationships that are hard to fully secure.
If the breach resulted from a nation-state actor using zero-day exploits (previously unknown vulnerabilities), then prevention becomes much harder. No company can defend against threats they don't know exist.
The reality is probably somewhere in the middle. There were likely preventable factors combined with sophisticated attack techniques that no reasonable company would have stopped.
But here's what's clear: Odido's security was not sufficient for the sensitive data they were storing. Whether the vulnerability was preventable or not, the overall security architecture failed to detect and stop the breach.
That's the accountability question that matters. Not "could you prevent every possible attack?" but "did you maintain security practices sufficient to detect and stop attacks before massive data theft occurred?"
Odido's answer appears to be no.
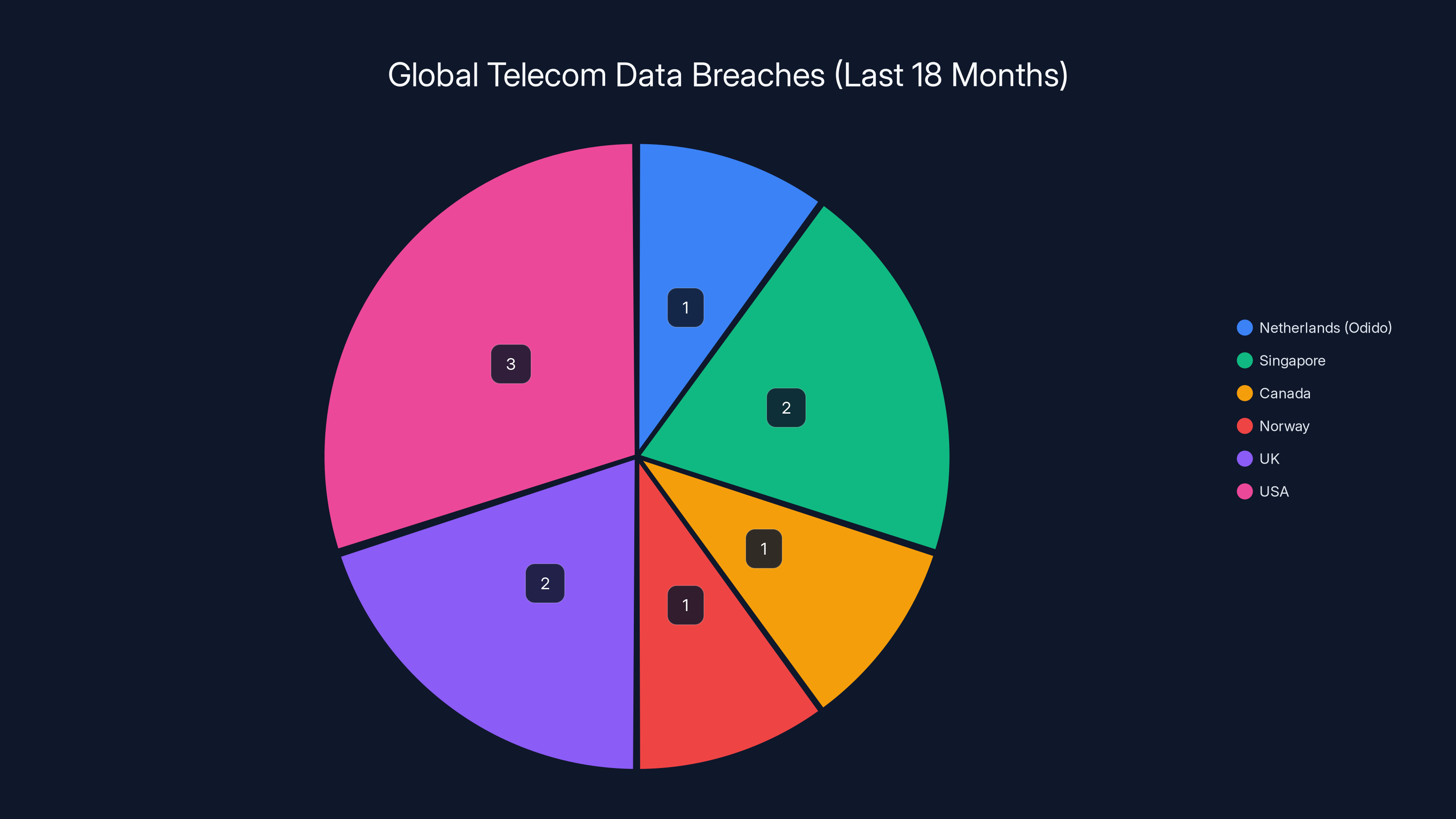
Estimated data shows the distribution of telecom data breaches over the last 18 months, highlighting the global nature of these security incidents.
The Psychological Impact on Customers
There's a human element to data breaches that statistics and technical details don't capture.
When millions of people learn that their personal information has been stolen, the emotional response goes beyond rational risk assessment. There's a sense of violation. Your privacy—something you assumed was protected—has been compromised. That's deeply unsettling.
For many people, the psychological impact of a breach is worse than any actual fraud that results. The knowledge that criminals somewhere have your identity information, your bank account details, and your personal information creates a lasting sense of vulnerability.
There's also the grief of broken trust. You chose Odido as your telecommunications provider. You gave them your information. You assumed they would protect it. The breach breaks that implicit contract.
For some customers, the Odido breach might be the moment they decide telecommunications companies aren't trustworthy anymore. They might become more paranoid about sharing information. They might become more willing to use privacy tools and VPNs. They might become more skeptical of corporate claims about security.
From a business perspective, that's the hidden cost of breaches. It's not just the people who experience fraud. It's the broader erosion of trust that affects customer behavior for years afterward.

Comparing Global Telecom Breaches: Odido in Context
To understand how serious the Odido breach is, let's compare it to other major telecom breaches globally.
The 2022 T-Mobile breach affected approximately 54 million customers and included names, dates of birth, phone numbers, email addresses, and social security numbers. That's nearly 9 times larger than the Odido breach in terms of customer count.
The 2021 AT&T breach affected 7.6 million customers, making it slightly larger than Odido.
The 2019 Twitter data breach exposed phone numbers and email addresses for 15 million users (though Twitter is social media, not telecom).
Based on customer count alone, Odido isn't the largest breach globally, but it's top-tier. What makes it particularly significant is the data that was stolen. The inclusion of IBANs and government ID details makes this more dangerous than some larger breaches that only exposed contact information.
The global pattern of 2024-2025 breaches, particularly those attributed to nation-state actors, suggests a coordinated campaign. Odido appears to be part of that larger pattern.
When you aggregate all these breaches together, you realize that millions of people across multiple countries have had their personal information compromised. The cumulative impact on the telecommunications industry's reputation and on consumer confidence is substantial.
What Doesn't Change: The Business Model
Here's something uncomfortable: the Odido breach probably won't fundamentally change how telecommunications companies operate.
They'll enhance security in certain areas. They'll implement additional monitoring. They'll conduct security audits. But they probably won't completely reimagine their business model or their relationship with customer data.
Because fundamentally, the business model of telecommunications depends on collecting and storing customer data. Phone companies need to know who you're calling. Internet companies need to know your usage patterns. TV companies need to know what you're watching. That data is valuable for operations, for targeted advertising, for analytics.
The Odido breach doesn't change that incentive structure. It might change the security practices around that data, but it won't eliminate the data collection.
In an ideal world, the breach would trigger a rethinking: "Maybe we're collecting too much data. Maybe we should adopt data minimization practices. Maybe we should limit what we store."
But that would require companies to voluntarily give up valuable data and competitive advantage. That's unlikely unless forced by regulation.
So we'll probably see improvements in security practice, but not fundamental changes in data strategy. Which means the fundamental risk—that massive databases of sensitive customer information are sitting in company systems waiting to be breached—remains.

The Path to Stronger Telecom Security
If you wanted to dramatically improve security in the telecommunications industry, what would you actually need to do?
First: Reduce data collection. Only collect and store the minimum customer information necessary to provide service. Delete data when it's no longer needed. This is data minimization, and it's the most direct way to reduce breach impact.
Second: Encrypt everything. All customer data should be encrypted at rest and in transit. This doesn't prevent breaches, but it makes stolen data much less useful.
Third: Implement proper access controls. Who has access to customer databases? How is that access monitored? Are there multiple layers of authentication required to access sensitive data? Are access logs reviewed for anomalies?
Fourth: Continuous security testing. Rather than annual penetration tests, companies should conduct continuous security testing and vulnerability scanning. Red teams should regularly attempt to break into systems. Results should inform security improvements.
Fifth: Faster detection and response. Invest in security operations centers that can detect unusual activity in real-time. Have incident response plans that can isolate compromised systems within minutes, not hours.
Sixth: Executive accountability. Tie compensation of senior leadership to security metrics. Make breaches costly to executives personally, not just to the company.
Seventh: Transparency. Companies should be required to publicly disclose their security practices, incident response capabilities, and breach history. Let customers make informed decisions.
Implementing all these changes would be expensive and disruptive to business operations. But it would dramatically reduce both the likelihood of breaches and the impact when they occur.
The question is whether industry competition and regulation will force these changes, or whether the status quo will persist until there's a catastrophic breach that forces change.
Lessons for Other Industries
The telecommunications industry isn't unique in storing sensitive customer data. Healthcare, financial services, insurance, and retail all store similarly sensitive information.
The Odido breach offers lessons for these other industries:
Finance: Banks and financial services should assume their systems will eventually be targeted by sophisticated attackers. Defense-in-depth is essential. Encryption, access controls, real-time monitoring, and incident response capabilities are non-negotiable.
Healthcare: Healthcare providers store some of the most sensitive data (medical records, insurance information, financial information). Healthcare breaches can have life-threatening consequences if medical information is altered. Security here requires even higher standards than telecom.
Retail: Retail companies storing payment information and customer data face similar risks. Payment card data should never be stored in plaintext. Customer data should be minimized.
Government: Government agencies storing citizen data face the highest standards of accountability. Breaches of government systems represent not just privacy violations but potential threats to national security.
The pattern of breaches across industries suggests that cybersecurity is becoming an existential risk for any company storing significant customer data. Companies that don't take it seriously will eventually pay the price.

FAQ
What exactly happened in the Odido data breach?
Odido, a major Dutch telecommunications company, experienced a breach where hackers gained unauthorized access to the customer contact system. The breach exposed data for approximately 6.2 million customers, including names, phone numbers, addresses, dates of birth, bank account numbers (IBANs), and government ID details such as passport or driver's license numbers. The breach was confirmed in February 2025, though the actual intrusion timing was not immediately disclosed. Current and former customers (those with service within the past two years) may be affected.
How many people were actually affected by the Odido breach?
Odido confirmed that more than 6.2 million customers were affected, representing approximately one-third of the entire Dutch population. This figure includes both current Odido customers and Ben NL customers (Odido's subsidiary), as well as former customers who had service within the past two years. The scope makes this one of the largest data breaches affecting a single telecommunications company in recent years, surpassed in customer count by incidents like the T-Mobile 2022 breach but comparable to the 2021 AT&T breach in terms of affected individuals.
What data was stolen in the Odido breach?
The stolen data includes full customer names, phone numbers, postal addresses, email addresses, dates of birth, bank account numbers (IBAN), and government-issued ID details such as passport numbers, driver's license numbers, and expiration dates. Notably, what was NOT stolen includes call records and metadata, location data, billing information, image scans of government IDs, and business customer data. The inclusion of IBANs and government ID information makes this breach particularly dangerous for identity theft and financial fraud, as criminals have comprehensive identity verification information.
Why are telecommunications companies such common targets for hackers?
Telecommunications companies are prime targets for both nation-state actors and financially motivated criminals because they store comprehensive personal information (names, addresses, phone numbers, financial details) and serve as infrastructure providers with access to communication patterns. For nation-states conducting espionage, breaching telecom companies provides valuable intelligence about government officials, diplomats, and other high-value targets based on their call patterns and communications. For financially motivated criminals, the data can be sold for fraud or used directly for identity theft. Additionally, many telecom companies run legacy systems that weren't designed with modern security in mind, creating vulnerabilities that sophisticated attackers can exploit.
Is this part of a larger pattern of telecom breaches?
Yes, the Odido breach is one incident in a sustained pattern of telecommunications breaches globally. In 2024-2025, telecom companies in Singapore, Canada, Norway, the United Kingdom, and the United States all experienced significant breaches. A threat group known as Salt Typhoon, widely attributed to Chinese government interests, has been conducting extensive campaigns against hundreds of phone companies across multiple countries, primarily for espionage and surveillance purposes. These pattern of attacks suggests a coordinated global campaign rather than isolated incidents, with nation-state actors being responsible for many of the most sophisticated breaches targeting telecom infrastructure.
What should affected customers do immediately?
Affected customers should take several immediate actions: contact their bank and inform them about the IBAN breach while requesting transaction limits and additional authentication requirements; place fraud alerts with credit bureaus; consider placing a credit freeze on their credit file if allowed in their jurisdiction; monitor credit reports for unauthorized accounts; be suspicious of unexpected communications, particularly unexpected calls claiming to be from banks or government agencies; change passwords on other services if the same password was used for Odido; document all communication with banks and credit bureaus; and consider identity theft insurance beyond the credit monitoring offered by Odido. While not all affected customers will experience fraud, the comprehensive nature of the stolen data justifies preventive action.
How long before customers experience fraud from the Odido breach?
Fraud attempts from major breaches typically appear within 3-6 months of the data becoming available on dark web markets. However, sophisticated identity theft schemes can take years to surface, and some victims don't discover their identity has been compromised until they apply for credit years later and find out accounts have been opened fraudulently in their name. This is why ongoing vigilance is more important than assuming the threat period has a fixed endpoint. The data stolen in the Odido breach has permanent value in the underground economy.
What are the regulatory implications of the Odido breach?
The breach triggers multiple regulatory frameworks, particularly the GDPR (General Data Protection Regulation) in the European Union, which can result in fines up to 20 million euros or 4% of annual global revenue, whichever is higher. The Dutch Data Protection Authority (APG) will conduct investigations into whether Odido maintained appropriate technical and organizational security measures. Regulatory focus will be on whether security controls were adequate, regularly tested and updated, whether incident response plans existed, and how quickly the breach was detected and reported. Additionally, affected customers in jurisdictions allowing private rights of action may pursue class action lawsuits for damages resulting from the breach.
Could Odido have prevented this breach?
Whether the specific breach was preventable depends on the attack vector and underlying vulnerabilities, which Odido hasn't publicly disclosed. If the breach resulted from unpatched known vulnerabilities, insufficient access controls, or poor credential management, then prevention was likely possible. If it resulted from sophisticated supply chain attacks through third-party vendors or zero-day exploits previously unknown to security researchers, prevention becomes significantly more challenging. However, the key accountability question isn't whether every possible attack could be prevented, but whether Odido maintained security practices sufficient to detect and stop attacks before massive data exfiltration occurred. The answer appears to be no, suggesting fundamental gaps in security architecture and monitoring capability.
What happens to stolen data on the dark web?
Within days or weeks of a breach becoming public, stolen databases are typically offered for sale on dark web marketplaces. The Odido database of 6.2 million records with comprehensive identity information could be worth tens of thousands to millions of dollars depending on data quality and verification. Once sold, the data becomes a commodity that is purchased, bundled with other breaches, cross-referenced with additional sources, and used as a foundation for fraud schemes. Criminals may use data enrichment services to combine the Odido data with other sources to create even more valuable enriched datasets for targeting specific individuals. This is the downstream effect of breaches that remains largely invisible to victims but creates years of potential fraud risk.
How does the Odido breach compare to other major telecom breaches?
The Odido breach affected 6.2 million customers, making it one of the largest but not the single largest telecom breach on record. The 2022 T-Mobile breach affected approximately 54 million customers (nearly 9 times larger in customer count). The 2021 AT&T breach affected 7.6 million customers (slightly larger than Odido). However, what makes Odido particularly severe is the type of data stolen: inclusion of IBANs and government ID details makes this breach more dangerous than some larger breaches that only exposed contact information. In the context of 2024-2025 breaches attributed to nation-state actors, Odido appears to be part of a coordinated global campaign rather than an isolated incident.
Key Takeaways
- Odido confirmed a data breach affecting 6.2 million customers in February 2025, exposing names, addresses, phone numbers, bank account numbers (IBANs), and government ID details
- Telecommunications companies are prime targets for both nation-state espionage operations and financially motivated criminal groups due to the sensitive personal information they store
- The Odido breach is part of a larger global pattern of telecom breaches, with companies in Singapore, Canada, Norway, the UK, and US experiencing similar incidents in 2024-2025
- Affected customers should take immediate preventive action including contacting banks, placing fraud alerts, freezing credit, and monitoring accounts, rather than waiting for fraud to occur
- The breach raises significant regulatory implications under GDPR and may result in substantial fines, investigations, and potential class action lawsuits against Odido

Conclusion
The Odido data breach represents far more than a single incident of corporate negligence. It's a watershed moment that exposes fundamental vulnerabilities in how we've structured modern telecommunications infrastructure and how we protect the most sensitive personal information.
When 6.2 million people—roughly one-third of an entire country—have their names, addresses, bank details, and government ID information stolen, it's not just a privacy problem anymore. It's a national security problem. It's an economic problem. It's a social trust problem.
What makes Odido significant isn't that it's unique. It's that it's a predictable repetition of a pattern we're seeing globally. Telecom companies in Singapore, Canada, Norway, the UK, and the US have all experienced similar breaches. Some attributed to nation-states conducting espionage. Others to sophisticated criminal groups. The common thread is that these attacks are working.
And until the incentive structure changes, they'll continue to work. For telecommunications companies, the cost of a major breach—even one affecting millions of customers—is often less expensive than the cost of implementing world-class security infrastructure that could prevent it.
That misalignment between cost and responsibility is the real problem. It's not that Odido's security was incompetent. It's that the entire industry optimizes for operational efficiency and shareholder returns rather than for protecting the irreplaceable personal information that customers entrust to them.
For affected customers, the path forward involves assuming the data is compromised and taking defensive action. For regulatory bodies, it involves strengthening standards and enforcement. For telecommunications companies, it involves a fundamental rethinking of security not as a cost center but as a core business responsibility.
Until that happens, expect more Odidos. Expect more millions of affected customers. Expect more breaches that could have been prevented.
The Odido breach is a failure of the system—companies, regulators, industry, and attackers operating within a set of incentives that made the breach not just possible but predictable. Understanding those systemic failures is the only way to prevent the next breach from being inevitable.
But until the incentives align, prevention will remain a noble goal rather than a consistent practice. The Odido breach proves that reality with the stolen data of 6.2 million people.
Related Articles
- Odido Telco Breach Exposes 6.2M Users: Complete Analysis [2025]
- 6.8 Billion Email Addresses Leaked: What You Need to Know [2025]
- AI Recommendation Poisoning: The Hidden Attack Reshaping AI Safety [2025]
- Why Your VPN Keeps Disconnecting: Complete Troubleshooting Guide [2025]
- NordVPN & CrowdStrike Partnership: Enterprise Security for Everyone [2025]
- Gemini Model Extraction: How Attackers Clone AI Models [2025]
![Odido Data Breach: 6.2M Customers Exposed [2025]](https://tryrunable.com/blog/odido-data-breach-6-2m-customers-exposed-2025/image-1-1770998895492.jpg)



