6.8 Billion Email Addresses Leaked: What You Need to Know [2025]
Imagine waking up to find your email address—along with nearly 7 billion others—sitting on the dark web, ready to be bought and sold by anyone with a few cryptocurrency tokens. That's not hypothetical anymore.
A hacker going by the alias Adkka 72424 recently posted one of the largest email data leaks in history: 6.8 billion unique email addresses packaged into a 150GB archive on a popular dark web forum. What's worse? Researchers at Cybernews verified that roughly 3 billion of those emails are actually usable and functional, making this breach an absolute goldmine for attackers.
This isn't just a privacy violation. It's a toolbox for criminals. When threat actors have your email address, they don't just spam you with generic phishing emails. They profile you. They research your workplace, your job title, your likely salary range, your industry connections. Then they craft highly targeted social engineering attacks designed specifically to trick you into compromising your credentials or transferring money.
Business email compromise (BEC) attacks—where hackers impersonate executives or trusted vendors to steal money—have cost organizations over $2 billion in losses over the past few years. A leak like this one accelerates that timeline considerably.
TL; DR
- The Scale: 6.8 billion emails leaked in 150GB archive; approximately 3 billion verified as real and usable
- The Threat: Emails are weaponized for phishing, BEC attacks, credential harvesting, and identity theft through targeted social engineering
- The Timeline: Hacker claims 2-month extraction process from combos, ULP collections, logs, and compromised databases
- The Action: Check if your email was compromised, enable two-factor authentication, monitor financial accounts, and treat all unsolicited emails as suspicious
- The Reality: This is now the third major email breach in recent memory, signaling a disturbing trend in data security
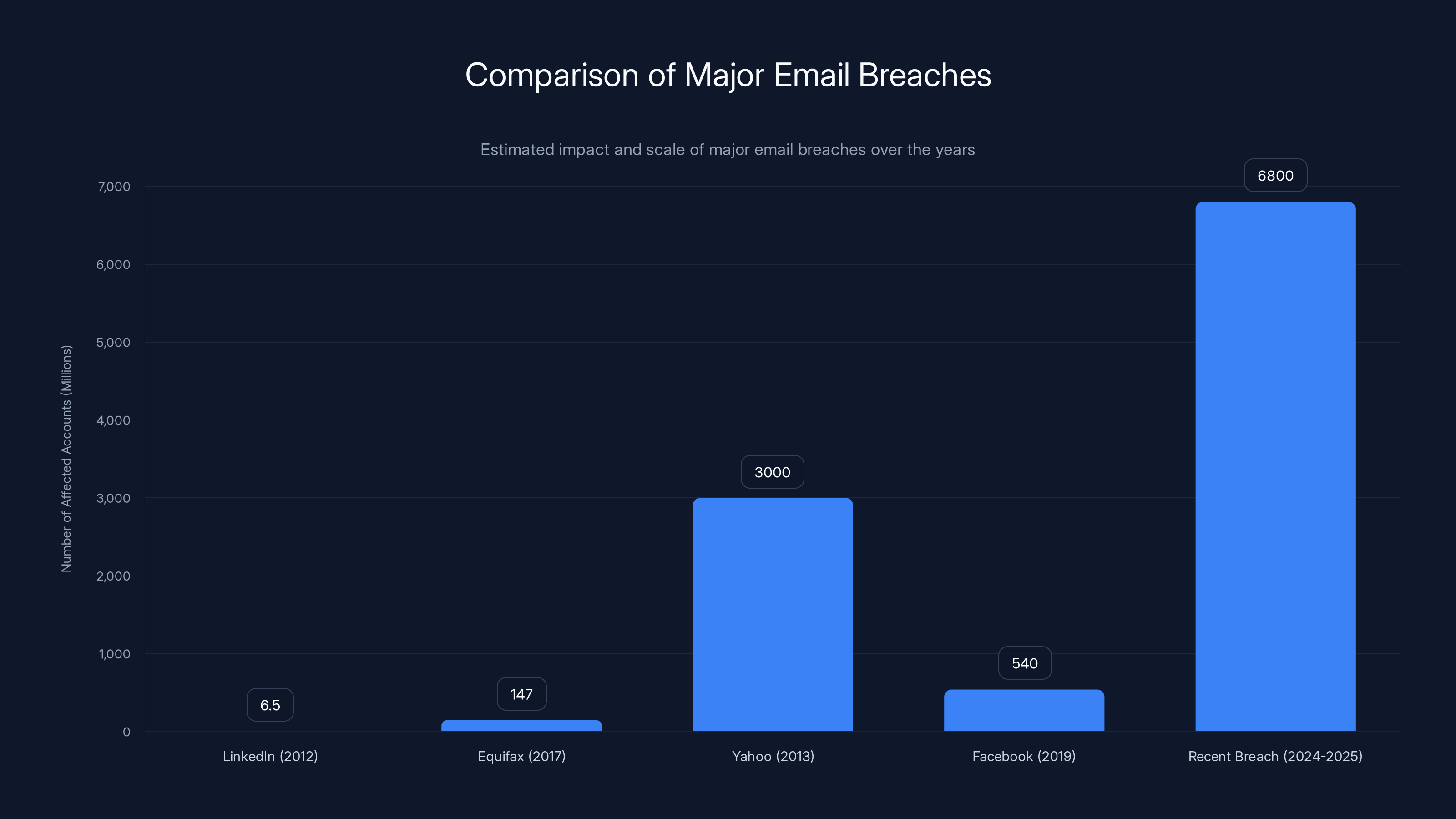
The recent 6.8 billion email breach surpasses previous major breaches like Yahoo and Equifax, highlighting the growing scale of data vulnerabilities. Estimated data for recent breach.
Understanding the Scale of This Breach
The Numbers That Matter
Let's be clear about what "6.8 billion emails" actually means in context. The global population is roughly 8 billion people. This leak represents approximately 85% of all humanity's email addresses. That's staggering.
But here's the critical detail: not all 6.8 billion are equally useful. When Cybernews analyzed the archive, they removed invalid addresses, duplicates, and unusable entries. What remained was approximately 3 billion functional, current email addresses. That's still enough to make this one of the largest email breaches ever recorded.
For context, the Equifax breach of 2017 affected 147 million people across multiple data types. This email leak is orders of magnitude larger than both.
How the Hacker Obtained These Addresses
The hacker claims to have obtained the emails through "different channels, some of which were obtained illegally." Translation: stolen data from multiple sources. Specifically, they mentioned extracting emails from:
Combos are pre-compiled lists of stolen usernames and passwords, typically sold on dark web markets. These are goldmines for attackers because they often contain validated, active credentials.
ULP collections refer to "Unlinked Passwords"—databases that contain usernames and passwords that haven't yet been matched to specific breaches. They're often compiled from leaked databases, scraped websites, or credential-stuffing attacks.
Logs and databases suggest the hacker had access to server logs or misconfigured databases that weren't properly secured. This could include anything from improperly protected Mongo DB instances to exposed backup files.
The hacker spent approximately 2 months aggregating and deduplifying these sources into a single dataset. That's a significant time investment, which suggests they had consistent access to multiple breach databases or were actively harvesting from live sources.
Why 150GB Is a Red Flag
A 150GB file doesn't sound massive in the age of cloud storage, but in the context of email addresses, it's enormous. Each email address is typically 20-100 bytes of data when stored efficiently. This suggests the archive includes far more than just email addresses.
It likely contains associated metadata: username handles, phone numbers, passwords (even if hashed), IP addresses, registration dates, and other profile information tied to those emails. That metadata is what makes a leak truly dangerous, because it enables attackers to build detailed profiles of victims before launching targeted attacks.
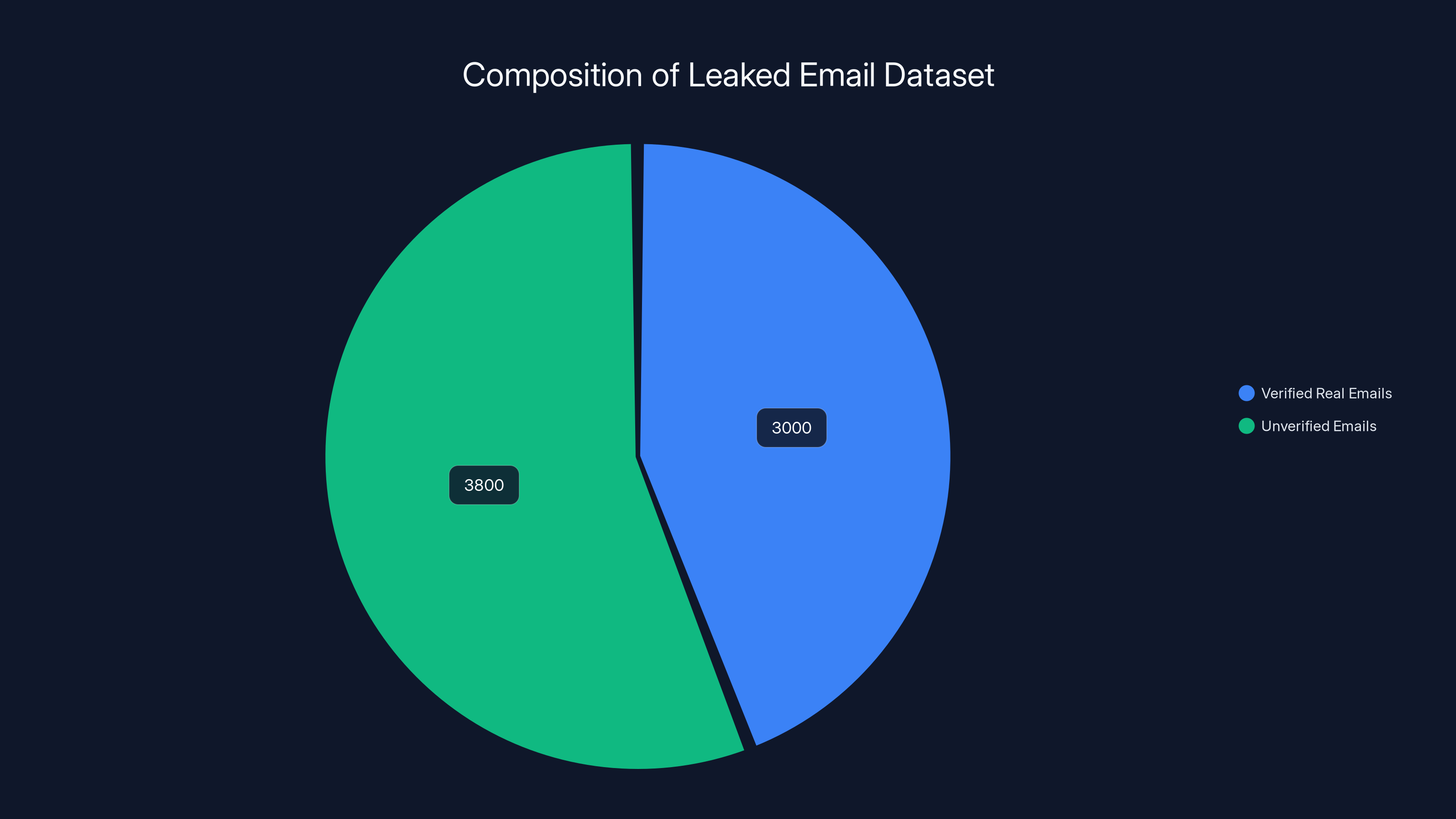
The dataset includes 3 billion verified real emails and 3.8 billion unverified emails, highlighting the massive scale of the breach. Estimated data.
The Real Danger: How Attackers Use This Data
From Email Address to Targeted Attack
Here's where most people misunderstand the threat. It's not about receiving spam emails. It's about receiving emails that are specifically tailored to you, crafted by someone who knows your real name, job title, company, industry, and likely your salary range.
A generic phishing email has a response rate of maybe 3-5%. A targeted spear-phishing email—one personalized to the victim—has a response rate of 20-30%. That's a massive difference in terms of success rate for attackers.
The workflow looks like this:
- Reconnaissance: Attacker pulls your email from the leaked database
- Profiling: They research you on Linked In, company websites, and public records
- Targeting: They identify something valuable about your position (access to finances, sensitive data, decision-making authority)
- Crafting: They write a highly believable email pretending to be someone you trust
- Delivery: They send it from a spoofed email address that looks nearly identical to a legitimate sender
- Exploitation: You click the link or download the attachment, and they've gained access
This process happens thousands of times daily. The difference with this leak is the sheer volume—attackers now have 3 billion starting points instead of having to guess or purchase smaller datasets.
Business Email Compromise (BEC) Attacks
BEC is where the real money is. These aren't attacks aimed at individuals—they're attacks aimed at employees with access to company finances. Here's how they work:
An attacker sends an email that appears to come from the CEO or CFO. The subject line is urgent: "Wire transfer needed immediately for acquisition." The body includes specifics about a vendor the company works with, a project that's underway, or a deadline that's looming.
The employee, feeling the time pressure and seeing what appears to be a legitimate request from senior leadership, authorizes a wire transfer. By the time anyone realizes it's fraudulent, the money is gone—often moved through multiple accounts and converted to cryptocurrency.
Average BEC losses per incident? Between
Why does this leak amplify BEC risk? Because attackers can now research your company's financial processes, identify key employees by title, and understand your organizational structure—all from publicly available information combined with the leaked emails.
Credential Harvesting and Account Takeover
If your email is in this database, attackers will attempt to use it to break into your accounts. They'll start with password-spraying attacks—trying common passwords like "Password 123!" or "Company 2024!" across all 3 billion emails.
They'll build credential spraying lists combining the leaked emails with passwords from previous breaches. If you reuse passwords across multiple accounts (and statistically, 80% of people do), they might get lucky on your email, banking, or corporate account.
Once they have access to your email, they own you. Email is the master key to everything else—password resets, two-factor authentication codes, recovery options. With email access, attackers can reset your passwords on banking apps, cryptocurrency wallets, and corporate systems.
Identity Theft and Long-Term Exploitation
A leaked email isn't a one-time risk. Attackers file it away and use it for years. They might not contact you immediately. Instead, they might wait until you've changed jobs, moved companies, or changed your security posture—then strike.
Identity theft using leaked email addresses typically involves opening new accounts in your name, applying for loans, or selling your information to other criminals. The damage compounds over time.
Historical Context: Is This Becoming the Norm?
A Pattern of Massive Email Breaches
This isn't the first time we've seen a billions-scale email breach. It's becoming almost routine.
In 2019, a database containing 763 million email addresses was discovered exposed on a misconfigured server. In 2021, an even larger collection of 1.4 billion unique email addresses was compiled from previous breaches and leaked online. And now, in 2024-2025, we're seeing leaks that dwarf those numbers.
The frequency and scale of these breaches suggest a few disturbing trends:
First, data breaches are accelerating. Hackers are getting better at extracting data from poorly secured systems. Companies are collecting more data, and that data is often sitting in databases without proper encryption or access controls.
Second, there's an active marketplace for stolen data. Hackers wouldn't bother compiling and leaking 6.8 billion emails if there wasn't demand for it. The dark web has entire forums dedicated to buying, selling, and trading stolen databases. Prices are laughably cheap—bulk email lists often sell for fractions of a cent per address.
Third, the tools and techniques for mass data extraction have improved. A decade ago, extracting billions of records would have required significant technical skill. Today, there are readily available tools for accessing misconfigured cloud databases, scraping websites, and deduplicating massive datasets.
Comparison to Previous Major Leaks
To understand how severe this is, let's compare it to other major breaches:
Linked In (2012): 6.5 million emails, ~
This 6.8 billion email breach is now in the conversation with Yahoo and Equifax—massive breaches that had real financial and reputational consequences. But unlike those, this one is specifically designed for immediate exploitation by criminals.
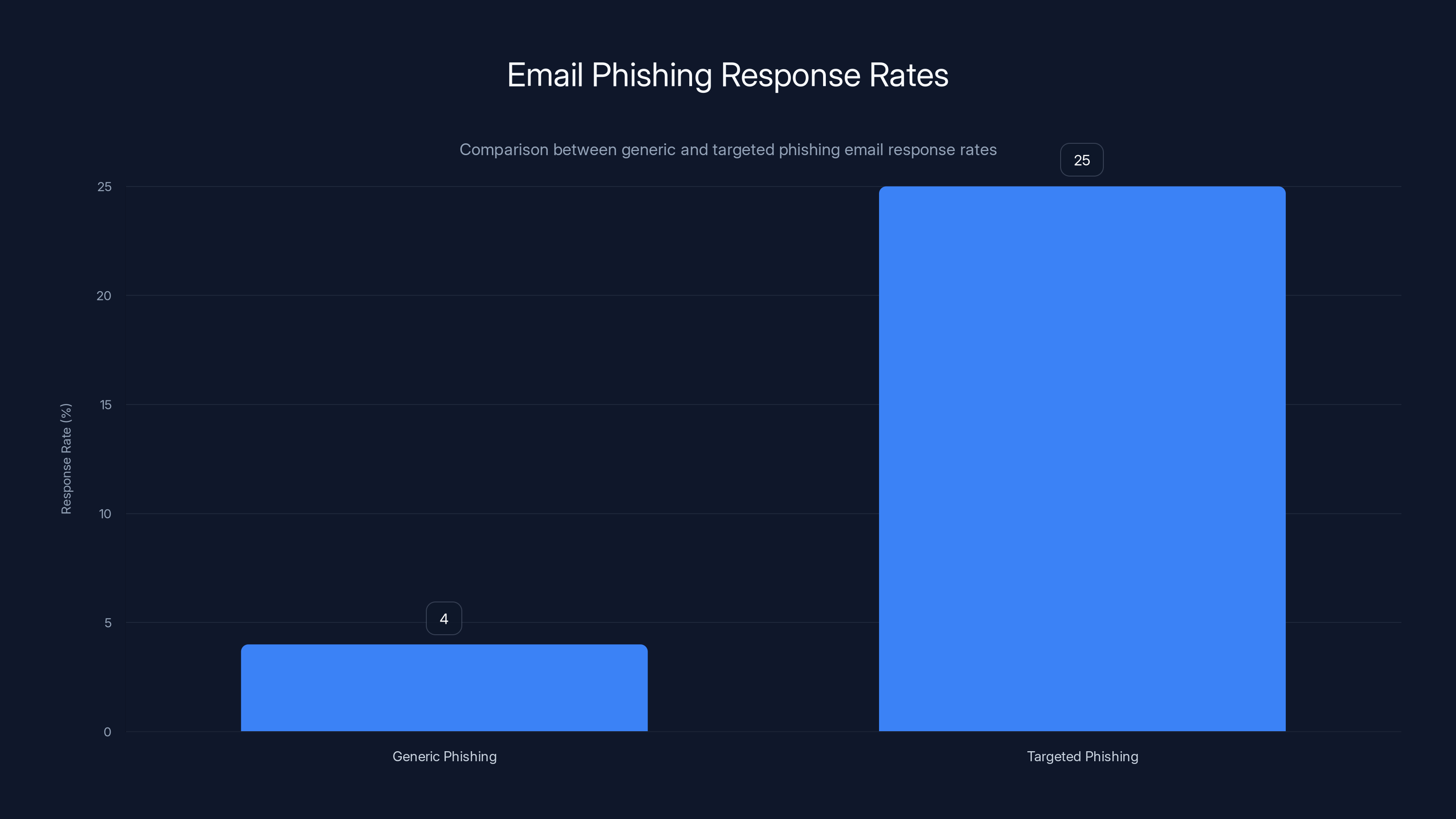
Targeted spear-phishing emails have a significantly higher response rate (20-30%) compared to generic phishing emails (3-5%). This highlights the increased effectiveness of personalized attacks. Estimated data.
Why Email Addresses Are So Valuable
Email as the Master Key
Your email address is more valuable to a criminal than your password. Here's why:
Passwords can be changed. Email addresses are permanent identifiers. Every account you have—banking, email, social media, cryptocurrency, corporate—uses your email as the recovery mechanism. If someone has your email, they can reset your passwords and take over those accounts.
Your email is also a trail. It's connected to every transaction you've made, every service you've used, every subscription you've subscribed to. It's the single point of entry to your entire digital life.
The Email-to-Money Pipeline
Here's the economics of email theft from a criminal's perspective:
-
Acquisition: Bulk email lists cost fractions of a cent per address. Even at
3 million in revenue. -
Exploitation: With 3 billion emails, attackers can run targeted campaigns with expected conversion rates of 2-5%. Even at 2%, that's 60 million people who fall for phishing or credential-harvesting attacks.
-
Monetization: Of those 60 million compromised accounts, maybe 5-10% have financial value (banking access, cryptocurrency wallets, business accounts). That's 3-6 million accounts with direct financial access.
-
Return: If each compromised financial account yields an average of
1.5-6 billion in direct theft.
Those numbers are rough estimates, but they illustrate why criminals invest so heavily in obtaining email lists. The return on investment is tremendous.
Red Flags: How to Recognize You're Being Targeted
Warning Signs of Spear-Phishing Attacks
If your email is in this breach, attackers will be coming for you. Here's what to watch for:
Emails from "colleagues" you don't recognize asking for urgent action—clicking a link, downloading a file, or confirming credentials. Legitimate colleagues typically communicate through established channels.
Emails from your bank asking you to "verify" information. Real banks never ask for credentials via email. This is a classic phishing tactic.
Urgency and pressure. Spear-phishing emails often create artificial time pressure: "Your account will be locked in 24 hours," or "Immediate action required." Legitimate companies give you time to act.
Slightly off email addresses. An email from "support@yourbank.co" instead of "support@yourbank.com". These homoglyphic attacks are common because the difference is often invisible to casual reading.
Generic greetings like "Dear Customer" instead of your actual name. Spear-phishing attempts are usually more personalized, but generic greetings are a red flag that it's automated.
Links that don't match the sender. Hover over any link before clicking. If it says it's from your bank but the link points to a random domain, that's a phishing attempt.

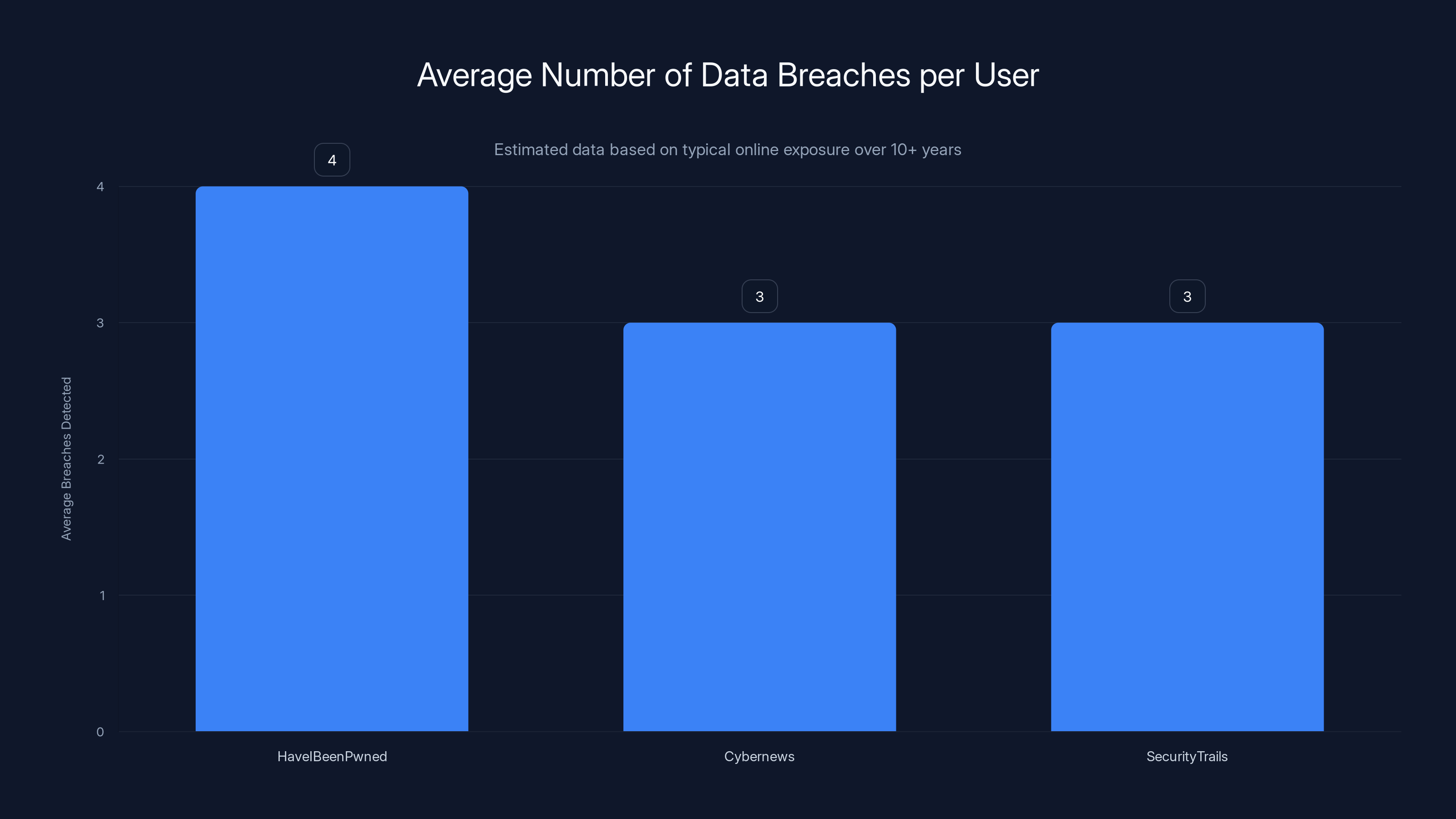
Users typically find their email in 3-4 major data breaches using these tools. Estimated data based on common online exposure.
Immediate Steps: What to Do Right Now
Step 1: Check If Your Email Is Compromised
First, determine whether your email is actually in this leaked database. Several tools can help:
Have IBeen Pwned.com (haveibeenpwned.com) is the most reliable resource. Enter your email address and the site will tell you which breaches have exposed your information. It updates regularly as new breaches are discovered.
Cybernews (cybernews.com/exposed-data/) also maintains a database of major breaches and offers a free checker.
Security Trails provides exposure checking and historical breach data.
Don't be shocked if your email appears in multiple breaches. The average person who's been online for 10+ years has probably been exposed in at least 3-4 major data breaches.
Step 2: Change Your Passwords Everywhere
If you used the same password across multiple accounts (and statistically, you probably did), now's the time to change that habit.
Start with your most critical accounts:
-
Email account first. Your email is the master key. If an attacker takes your email, they can reset every other password you have. Make it strong, unique, and memorable only to you.
-
Banking and financial accounts. Credit cards, investment accounts, cryptocurrency wallets, payment apps—anything with direct access to money.
-
Work/corporate accounts. If you have company email, VPN access, or corporate systems, change those passwords immediately.
-
Social media and entertainment. These are lower priority but still important.
For password creation, use a password manager like Bitwarden, 1 Password, or Last Pass. Let it generate 16+ character passwords with mixed case, numbers, and symbols. The goal is to make each password completely unique and impossible to remember (but the password manager remembers it).
Step 3: Enable Two-Factor Authentication (2FA)
Even if an attacker has your password, they can't access your account without the second factor. Most services offer multiple 2FA options:
Authenticator apps (Google Authenticator, Authy, Microsoft Authenticator) generate time-based codes that change every 30 seconds. These are more secure than SMS because they can't be intercepted by SIM-jacking attacks.
Hardware security keys (Yubi Keys, Titan keys) are the most secure option. They're physical devices that you plug into your computer or tap to your phone. Even if an attacker has your password, they can't use it without the physical key.
SMS codes are the least secure option (vulnerable to SIM-jacking) but better than nothing.
Prioritize 2FA for:
- Email account (absolutely critical)
- Banking and financial accounts
- Cryptocurrency wallets
- Work/corporate accounts
- Social media where you have personal information
Step 4: Monitor Your Accounts and Credit
Set up alerts on your financial accounts. Most banks allow you to configure alerts for:
- Login attempts from new devices
- Large transactions
- Password changes
- New beneficiaries added
For credit monitoring, consider:
Credit freezes through the three major credit bureaus (Equifax, Experian, Trans Union). A freeze prevents anyone from opening new credit in your name without your explicit permission.
Credit monitoring services that alert you when someone tries to open an account in your name. Many are free (included with some email providers) or cost $10-20/month.
Identity theft insurance offers coverage if your identity is stolen, though it's somewhat controversial since the protection is limited.
Step 5: Be Paranoid About Email
Given that your email is now in a database used by attackers, adopt a defensive posture:
Never click links in emails, even from trusted senders. If a sender claims urgent action is needed, go directly to their website by typing the URL yourself, rather than clicking their email link.
Verify unexpected requests through a second channel. If you receive an email from your "boss" asking to wire money, call them directly to verify. Don't use a phone number from the email—use a number you already have.
Use email aliases for less-trusted services. Gmail's "plus addressing" (+) lets you create multiple identifiers from one account: yourname+amazon@gmail.com, yourname+sketchy-service@gmail.com. This helps you identify which service leaked your data if you later see compromises.
Turn on advanced protection if available. Gmail, Outlook, and other providers offer enhanced security modes for high-risk users.

The Business Impact: Why Companies Should Care
Enterprise Risk Assessment
If you're a business leader or security professional reading this, here's what you need to understand: this breach puts every employee at risk, and every employee is a potential entry point for attackers.
A single employee who falls for a phishing email can compromise your entire company. An attacker who gains access to one email account can:
- Move laterally through your network
- Access shared drives and sensitive documents
- Impersonate executives in BEC attacks
- Steal customer data or proprietary information
- Deploy ransomware
- Establish persistent access for future exploitation
The financial and reputational damage of a breach can be catastrophic. Companies typically spend:
- $4.29 million average cost per data breach (IBM's 2023 data breach report)
- 18 months to detect and respond to a breach
- Years to rebuild reputation and customer trust
What Companies Should Do
Immediate actions:
- Assume all employee emails are now in attackers' hands
- Implement mandatory 2FA across all critical systems
- Monitor for suspicious login attempts and unusual network activity
- Brief employees on phishing and social engineering threats
- Review email security policies and implement DMARC/SPF/DKIM to prevent email spoofing
Medium-term improvements:
- Implement advanced email security with AI-based threat detection
- Deploy EDR (Endpoint Detection and Response) tools
- Conduct security awareness training and phishing simulations
- Segment networks to limit lateral movement if one account is compromised
- Implement zero-trust architecture
Long-term strategy:
- Move toward passwordless authentication
- Implement continuous monitoring and threat intelligence
- Develop incident response plans and conduct regular tabletop exercises
- Maintain cyber insurance coverage
- Regular security audits and penetration testing

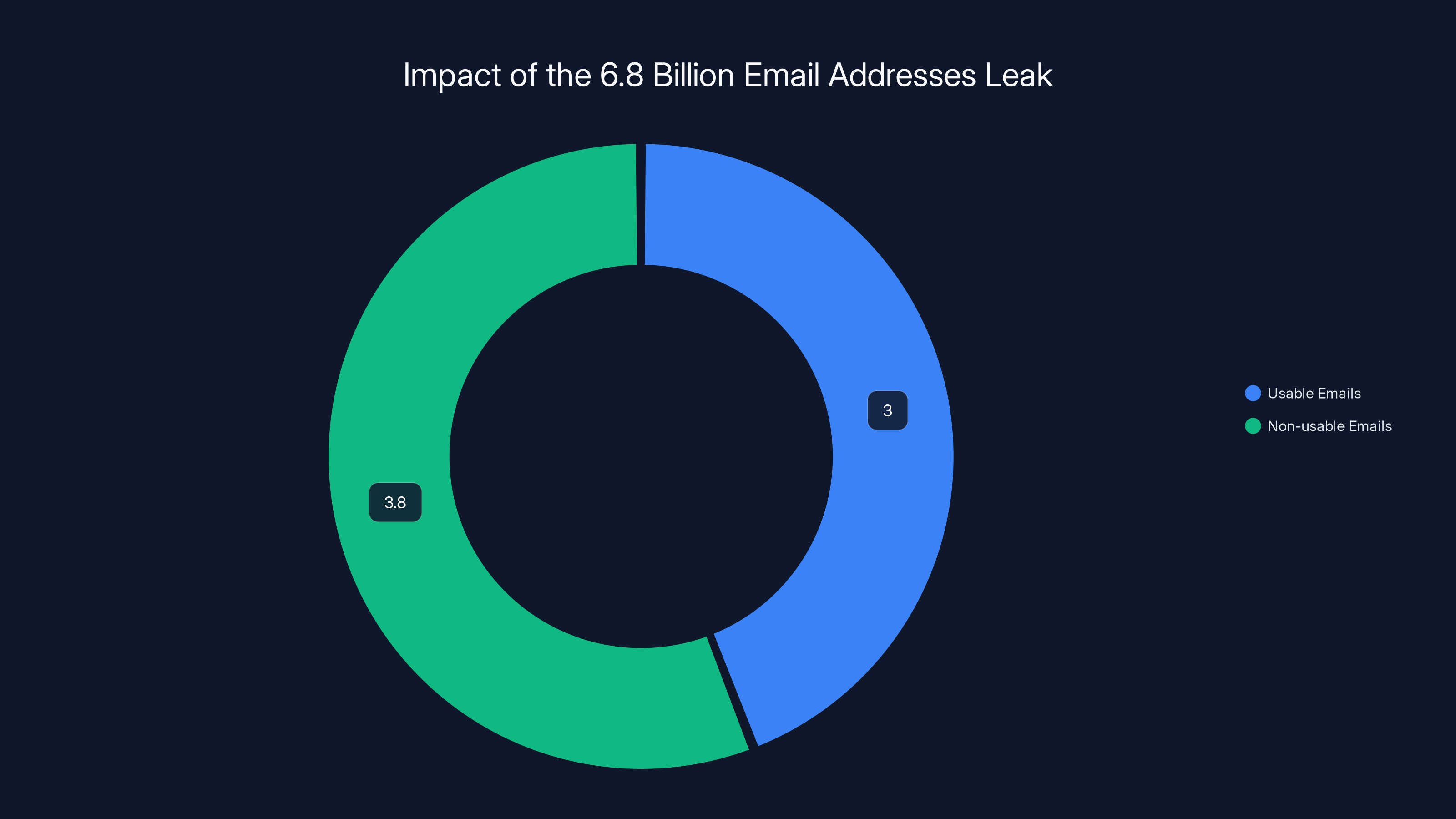
Out of 6.8 billion leaked email addresses, approximately 3 billion are verified as usable, posing significant risks for targeted attacks. Estimated data.
The Dark Web Marketplace: Understanding the Economics
Where This Data Is Sold
The leaked emails aren't just posted on the internet. They're sold on dark web forums where criminals gather to buy and sell stolen data.
These forums operate like e Bay or Alibaba, except for illegal goods. Hackers establish reputation, offer escrow services, and rate each other based on the quality and freshness of stolen data.
XSS forum (notorious in the security community) is where major breaches are often first posted. Hackers auction off datasets, sometimes starting at thousands of dollars.
Russian Market (also called "Russian Marketplace") is a dark web site where stolen credentials, full identity packages, and other data are sold. Prices are shockingly low—stolen credit card details sometimes sell for as little as $2-5 each.
Exploit forums host discussions about new vulnerabilities and techniques, as well as sales of leaked databases.
The interesting part? Not all of these are hidden anymore. Law enforcement has shut down some of these marketplaces, and companies like Flashpoint and Recorded Future monitor dark web activity as a paid service.
The point is: once your data is leaked, it enters an economy where it's packaged, resold, combined with other datasets, and exploited repeatedly. A single data breach can have consequences for years.

Technical Deep Dive: How Email Databases Get Breached
Common Vulnerability Patterns
How do attackers extract billions of emails in the first place? The hacker who leaked this data likely exploited one or more of these common patterns:
Misconfigured cloud databases are the #1 cause of large data breaches. Engineers set up Mongo DB, Postgre SQL, or Elasticsearch instances without authentication, thinking they're safe inside a private network. They're accessible from the internet and exposed completely. Security researchers find dozens of these monthly.
SQL injection vulnerabilities allow attackers to manipulate SQL queries and extract entire databases. A vulnerability in a web form or API endpoint can give attackers access to everything.
Unencrypted backups sitting in cloud storage buckets. Companies back up their databases but don't encrypt the backups or secure the storage location. An attacker finds the bucket, downloads the backup, and has the entire database.
Weak API security. Many applications expose APIs that return user data without proper authentication. An attacker can enumerate user IDs and pull data for millions of accounts.
Employee negligence. Developers accidentally commit database credentials to Git Hub, leave production databases exposed, or use weak passwords for admin accounts.
Third-party compromises. Your data gets breached because a vendor you use got breached. This is becoming increasingly common as supply chain attacks proliferate.
The Aggregation Problem
What makes this particular leak so dangerous is the aggregation aspect. The hacker didn't just breach one company. They combined data from multiple sources:
- Data from previous major breaches (which are re-sold and re-leaked multiple times)
- Data from credential combo lists (collections of usernames and passwords from multiple sources)
- Data from misconfigured servers and databases
- Data extracted from password spraying and credential stuffing attacks
- Data scraped from public sources
By combining all these sources and deduplicating them, the hacker created a comprehensive email database that represents the "hits" from multiple data sources. This is actually more valuable than a single breach because it increases the likelihood that each email is real and active.

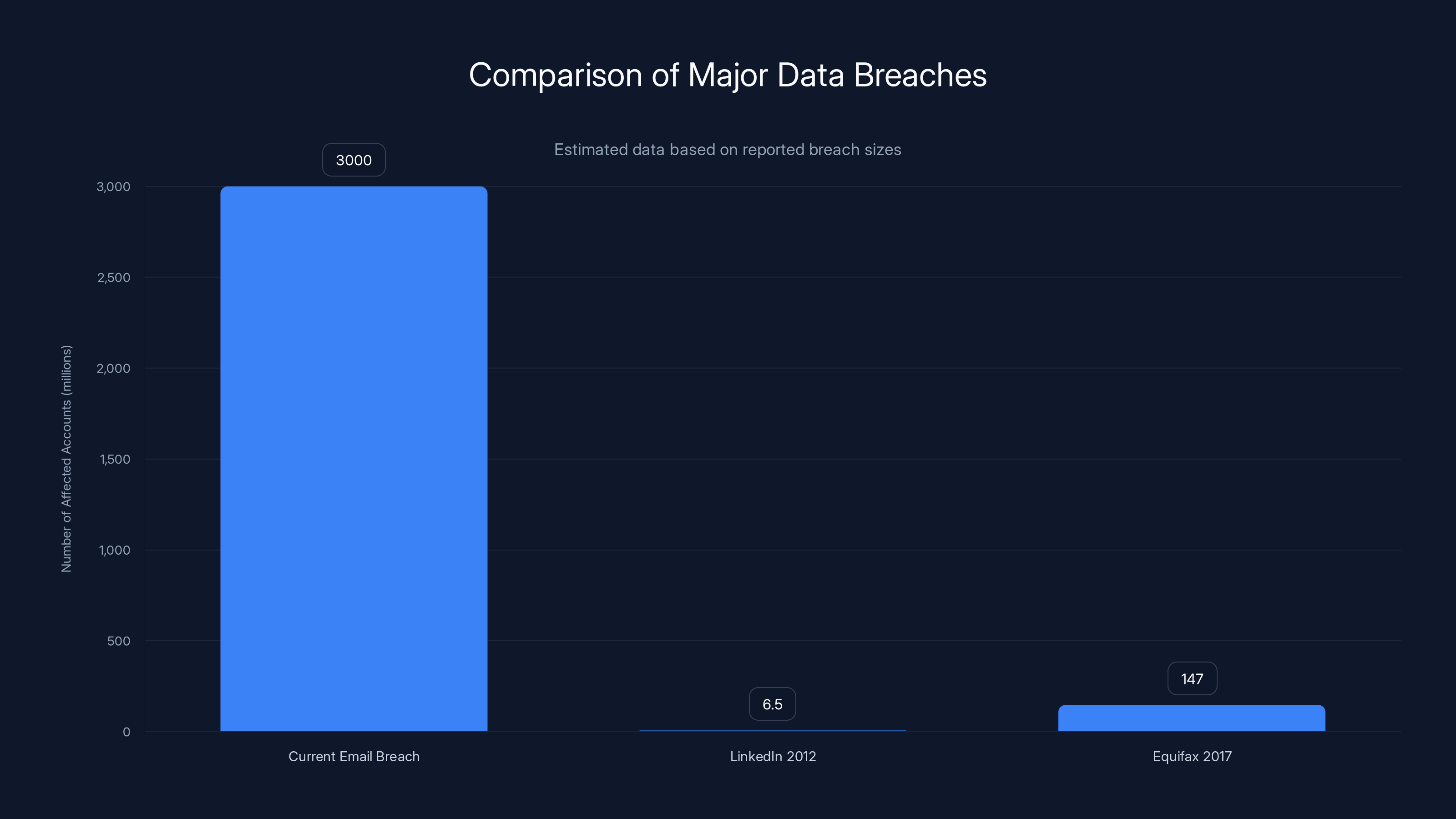
The current email breach, with 3 billion functional addresses, dwarfs previous breaches like LinkedIn (6.5 million) and Equifax (147 million). Estimated data.
Future Prevention: What Needs to Change
The Role of Companies
Companies need to treat data security as a business priority, not an IT checkbox.
Encrypt everything at rest. Use AES-256 encryption for stored data. If an attacker accesses your database, the data is useless without the encryption key.
Implement role-based access controls. Not every employee needs access to the entire user database. Restrict access to what people need.
Audit and monitor database access. Who accessed what data, when, and from where? If access logs show someone downloading millions of rows, that's a red flag.
Use secure authentication for database access. Multi-factor authentication for database credentials, not just passwords.
Regular security testing. Penetration testing, vulnerability scanning, and security audits should be ongoing, not annual.
The Role of Regulators
Government regulations are pushing companies toward better data security, but the consequences need to be stronger.
GDPR (Europe) imposes fines up to 4% of global revenue for breaches. That's significant enough to get boardroom attention.
CCPA (California) allows consumers to sue for breaches. This creates financial accountability.
But most other jurisdictions have weak or nonexistent data breach laws. Companies operating there have no real incentive to invest in security.
Stronger regulations with meaningful penalties would force companies to prioritize data security instead of treating it as optional.
The Role of Individuals
While companies and regulators need to step up, you also need to take responsibility for your own security:
- Use unique, strong passwords for each account
- Enable 2FA on everything critical
- Stay skeptical of unsolicited emails
- Keep your software updated
- Monitor your accounts for suspicious activity
- Don't reuse credentials across sites

The Bigger Picture: Why This Matters Beyond Immediate Risk
Privacy Erosion
Every major data breach represents a small death of privacy. Your email address, once semi-private, is now public knowledge available to anyone with a few dollars.
This has broader implications. Your email is a proxy for your identity online. Companies can use leaked emails to:
- Build detailed profiles about you
- Target you with advertising
- Identify you across platforms
- Sell your information to data brokers
- Harass you
The erosion of email privacy is the erosion of digital privacy itself.
The Arms Race of Data Security
This breach highlights a fundamental imbalance: defenders have to be right 100% of the time, while attackers only need to be right once.
A company can implement perfect security practices for years. One misconfiguration, one unpatched server, one employee who falls for social engineering—and 6.8 billion records are exposed.
Meanwhile, attackers can fail 99 times and succeed once. They have asymmetric incentives and infinite resources (they don't have to pay for attacks, they profit from them).
This suggests that perfect prevention isn't realistic. Instead, the focus should be on detection and response: assuming breaches will happen and minimizing the damage when they do.
The Convergence Threat
Individual breaches are bad. But the real threat is convergence.
When you combine leaked emails with leaked passwords from another breach, with leaked phone numbers from a third breach, with home addresses from public records, with financial information from a data broker—you get a complete identity profile that can be weaponized.
This convergence is happening. Data brokers buy information from dozens of sources and combine it. Criminals do the same. Your complete identity—name, email, phone, address, company, salary range, education, family members—is likely already available for purchase somewhere.
The 6.8 billion email breach is one piece of a much larger puzzle that's being assembled without your consent.

Long-Term Strategy: Thinking Beyond This Breach
Adopting a Zero-Trust Mindset
Zero-trust security means assuming nothing is trustworthy by default. Don't trust that an email is from who it claims to be. Don't trust that a link is legitimate. Don't trust that your password is sufficient.
This applies to personal security:
- Treat every email as potentially malicious
- Verify requests through secondary channels
- Use strong authentication (2FA minimum, hardware keys ideally)
- Keep software updated
- Monitor accounts for suspicious activity
Building Resilience
Since data breaches are inevitable, focus on resilience—the ability to recover quickly if you're compromised:
- Keep backups of important data (not stored on the same system)
- Know how to recover your accounts if they're compromised
- Have contact information for your bank and other critical services
- Document your accounts and recovery options
- Test your recovery plan occasionally
Choosing Quality Over Convenience
Many convenience-focused tools (single sign-on with Google/Facebook, autofill features, cloud-synced passwords) make you more vulnerable to compromise.
Consider trading some convenience for security:
- Use a dedicated password manager instead of browser autofill
- Use hardware security keys instead of SMS 2FA
- Manually type URLs instead of clicking email links
- Keep sensitive accounts separate from your casual browsing
This is more inconvenient, but significantly more secure.

What the Industry Predicts
Emerging Threats
Security researchers predict that leaked email addresses will be weaponized in new ways:
AI-powered phishing will become more effective. Attackers are using language models to generate personalized, grammatically perfect phishing emails at scale. The combination of AI-generated emails and targeted email lists creates a perfect phishing storm.
Deepfake social engineering will become more common. Attackers will combine leaked personal information with deepfake video/audio to impersonate trusted people. Imagine receiving a video call from your "CEO" asking you to wire money—with their voice and face artificially generated.
SIM-jacking attacks will increase. With your email address and personal information, attackers can call your mobile carrier and convince them to port your number to a new phone. Then they control your 2FA codes.
Cryptocurrency theft will escalate. Attackers will use email breaches to compromise cryptocurrency exchange accounts and wallets. Given the value in crypto, this is a prime target.
Defensive Evolution
On the defensive side, companies are evolving too:
Passwordless authentication is becoming mainstream. Services like Windows Hello, Apple Face ID, and FIDO2 security keys eliminate passwords entirely, making phishing much harder.
AI-powered threat detection is improving rapidly. Machine learning models can identify spear-phishing emails, anomalous login attempts, and compromise indicators at scale.
Supply chain security is receiving more attention. Companies are realizing that their security is only as strong as their weakest vendor or dependency.
Incident response as a service is growing. Companies are outsourcing breach response to specialized firms that can react faster than in-house teams.

Your Action Plan: A 30-Day Timeline
Days 1-3: Immediate Triage
- Check if your email is in the breach (haveibeenpwned.com)
- Change your email password if it's compromised
- Enable 2FA on your email account
- Review recent account activity for anything suspicious
- Set up fraud alerts with your bank
Days 4-10: Password Overhaul
- Set up a password manager (Bitwarden is free and good)
- Generate new, unique passwords for all financial accounts
- Generate new, unique passwords for work/corporate accounts
- Change passwords for social media and other accounts
- Delete all saved passwords from your browser
Days 11-20: Authentication Hardening
- Enable 2FA on all financial accounts
- Enable 2FA on work/corporate accounts
- Consider hardware security keys for highest-priority accounts
- Disable any backup authentication methods that are less secure (SMS, security questions)
- Test that you can log in with your new authentication setup
Days 21-30: Ongoing Monitoring
- Set up fraud monitoring on financial accounts
- Check credit reports at annualcreditreport.com (free once per year)
- Consider credit freeze if you're concerned about identity theft
- Set calendar reminders to periodically check account activity
- Review email security settings and implement advanced protection if available
FAQ
What does it mean that 6.8 billion emails were leaked?
A hacker compiled email addresses from multiple sources—previous data breaches, stolen credential lists, compromised databases, and server logs—into a single dataset containing 6.8 billion unique addresses. This represents approximately 85% of all email addresses in use globally. Of these, roughly 3 billion are verified as real and functional, making it one of the largest email breaches in history.
How do attackers use leaked email addresses?
Attackers use leaked emails as a starting point for multiple attack vectors. They conduct phishing campaigns targeting specific individuals with personalized emails. They perform credential stuffing attacks, attempting to use leaked passwords with your email address across different platforms. They research victims online to conduct spear-phishing and business email compromise attacks. They sell or trade the email lists on dark web marketplaces. They use the emails to initiate social engineering attacks or identity theft.
How can I check if my email is in this breach?
Visit haveibeenpwned.com and enter your email address. The service maintains a database of publicly known data breaches and will tell you if your email appears in any of them. You can also check Cybernews.com/exposed-data for breach information. If your email appears in multiple breaches, don't panic—it just means you've been exposed in multiple incidents. Focus on securing your most critical accounts.
What's the difference between this and previous email leaks?
Previous major email leaks involved breaches of specific companies or services. This leak aggregates data from multiple sources—including previous breaches, stolen credential lists, compromised databases, and scraped information. The combination makes it more dangerous because attackers can cross-reference data points to build detailed victim profiles. The scale (3 billion functional emails) is also unprecedented.
Should I change all my passwords immediately?
Yes, if your email is in the breach, you should change passwords for critical accounts—email, banking, financial services, and work accounts—immediately. For other accounts, change passwords within the next 7-10 days. Use a password manager to generate unique, strong passwords for each account. If you've reused passwords across multiple sites, prioritize changing those accounts first.
Is two-factor authentication really necessary?
Yes, absolutely. 2FA is the single most effective defense against unauthorized access to your accounts. Even if an attacker has your password (which is now likely if your email is in the breach), they can't access your account without the second factor. Enable 2FA on your email account first (it's the master key), then on financial and work accounts. Authenticator apps or hardware security keys are more secure than SMS codes.
What should I do if I get a suspicious email?
Do not click any links or download any attachments. Don't reply to the email. If the email claims to be from a legitimate organization (your bank, your email provider, a company you do business with), contact that organization directly using a phone number or website you already know is legitimate. Verify the sender's email address carefully—attackers often use addresses that look almost identical to legitimate ones. Report phishing emails to the organization being impersonated and to your email provider.
Can I get my email removed from the leaked database?
Unfortunately, no. Once data is public on the internet, it's essentially impossible to remove it completely. The file is now shared across dark web marketplaces and stored on multiple servers. Your focus should be on minimizing the damage through strong passwords, two-factor authentication, and monitoring.
Will companies face consequences for inadequate data security?
It depends on jurisdiction and the type of company. Companies operating under GDPR (Europe) can face fines up to 4% of global revenue for breaches. Under CCPA (California), consumers can sue for data breaches. However, many jurisdictions have weak or no data breach laws. Companies should be held accountable, but regulatory enforcement is inconsistent. Private lawsuits and negative press are sometimes the only real consequences.
Is my identity stolen if my email is in the breach?
Not necessarily. Your email being in a breach is a risk factor, not proof that your identity has been stolen. However, you should treat it as a warning sign and take precautions. Monitor your accounts for suspicious activity, check your credit reports, and set up fraud alerts. Identity theft often isn't discovered for months or years, so ongoing vigilance is important.

Conclusion: Living in a World of Breached Data
The 6.8 billion email leak isn't an anomaly—it's a symptom of a larger problem. We live in a world where data breaches have become routine, where companies profit from collecting massive amounts of personal data, and where security is often deprioritized in favor of convenience and features.
But here's the important part: while you can't control whether companies secure your data properly, you can control your own security posture.
You can use strong, unique passwords. You can enable two-factor authentication. You can be skeptical of unsolicited emails and requests. You can monitor your accounts for suspicious activity. You can take action when you discover your data has been compromised.
Are these steps inconvenient? Yes. Do they take time? Absolutely. But the alternative—becoming a victim of identity theft, losing access to your accounts, or having your money stolen—is far more costly and time-consuming.
The security landscape has changed. The old advice of "just use a strong password" is no longer sufficient. You need multiple layers of defense: strong passwords, unique passwords, two-factor authentication, regular monitoring, skepticism about email, and awareness of social engineering tactics.
This requires shifting your mindset from "trust the internet" to "trust nothing by default." It's a more paranoid way to live online, but it's increasingly necessary.
The 6.8 billion email leak is a wake-up call. It should prompt you to audit your security posture, update your most critical passwords, and enable two-factor authentication where you haven't already. It should make you more skeptical of unsolicited emails and requests. It should inspire you to think more carefully about what data you share online and with which companies.
Your email is now in a database used by criminals. That's not changing. What can change is how prepared you are when they target you.
Key Takeaways
- 6.8 billion email addresses leaked with 3 billion verified as real and functional—among largest email breaches ever
- Attackers weaponize leaked emails for phishing, business email compromise, credential harvesting, and identity theft through targeted social engineering
- Immediate actions include checking breach status, changing critical passwords, enabling 2FA, and monitoring accounts for suspicious activity
- Email is the master key to digital identity—compromised email access enables attackers to reset passwords on all connected accounts
- Business email compromise attacks cost organizations 50K-$2M when using leaked email data
Related Articles
- Lumma Stealer's Dangerous Comeback: ClickFix, CastleLoader, and Credential Theft [2025]
- Windows 11 Notepad Security Flaw: What You Need to Know [2025]
- Microsoft Zero-Day Exploits: Critical Windows & Office Vulnerabilities [2025]
- Trenchant Exploit Sale to Russian Broker: How a Defense Contractor Employee Sold Hacking Tools [2025]
- ExpressVPN Pricing Deals: Save on the Cheapest VPN [2025]
- Surfshark VPN 87% Off: Complete Deal Analysis & VPN Buyer's Guide [2025]
![6.8 Billion Email Addresses Leaked: What You Need to Know [2025]](https://tryrunable.com/blog/6-8-billion-email-addresses-leaked-what-you-need-to-know-202/image-1-1770925354179.jpg)



