8.7 Billion Records Exposed: Inside the Massive Chinese Data Breach [2025]
Someone left the front door wide open. For three weeks, one of the largest data aggregation operations ever discovered sat completely exposed on the internet. No password. No encryption. Just billions of personal records waiting to be stolen.
In 2024, security researchers from Cybernews stumbled across an unsecured Elasticsearch database hosted on a bulletproof provider. What they found was staggering: 8.7 billion records belonging to Chinese individuals and businesses. The database contained everything a criminal would need to steal identities, commit fraud, or launch sophisticated social engineering attacks.
This wasn't a single breach of one company's servers. This was something far worse. This was someone hoarding data, aggregating records from multiple sources over years, organizing them meticulously, and then completely forgetting to lock the door.
Let's walk through what actually happened, what data was exposed, who it affects, and what you should do if you might be among the victims.
TL; DR
- Scale of the breach: An unsecured Elasticsearch cluster exposed 8.7 billion records belonging to Chinese individuals and businesses
- What was exposed: Names, addresses, phone numbers, birth dates, social media IDs, plaintext passwords, company registration details, and business intelligence data
- Duration of exposure: The database remained publicly accessible for at least three weeks before being locked down
- Data aggregation: Evidence suggests this was a long-running data broker operation, not a single historical breach
- Your action items: Check if your information was included, change passwords immediately, monitor financial accounts, and enable multi-factor authentication
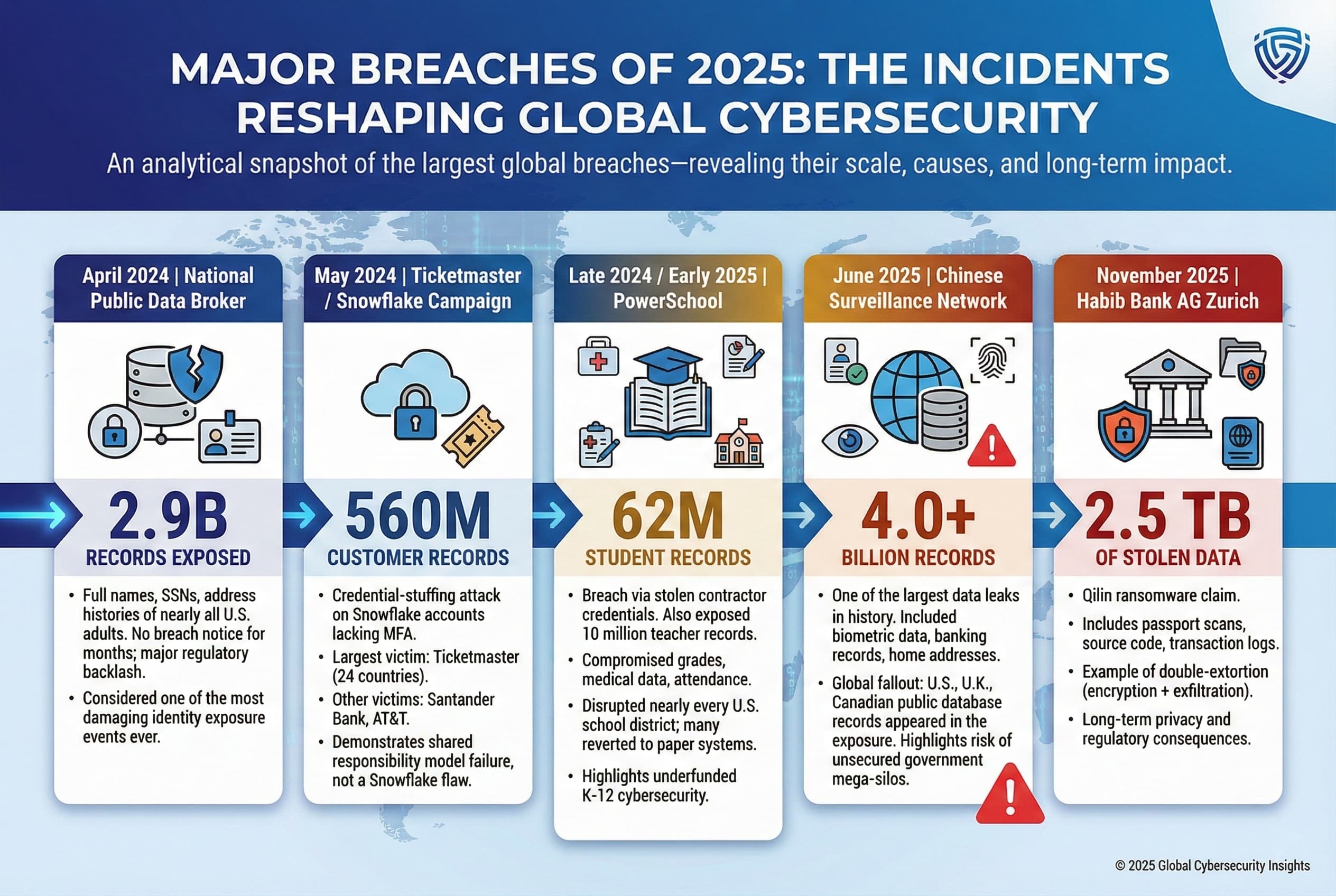
The breach exposed a variety of data types, with personal information making up the largest portion, followed by business information. Estimated data.
What Actually Got Exposed: A Breakdown of the Records
The 8.7 billion records weren't all the same type of data. This was a carefully organized operation with distinct categories of information.
For individuals, the database contained personal identifiable information (PII) that's perfect for identity theft. Names, residential addresses, phone numbers, and birth dates were all there. Social media usernames and identifiers meant your online presence was mapped to your real-world identity. But here's the part that keeps security experts up at night: plaintext passwords. Not hashed. Not salted. Just raw passwords sitting in plain text, ready to be used for credential stuffing attacks across other platforms.
The corporate records were equally devastating. Company registration details, legal representatives' information, business contact data, licensing metadata, and registration addresses created a comprehensive map of China's business landscape. This kind of corporate intelligence is worth serious money to competitors, and it was all sitting there unprotected.
The database contained over 160 distinct indices, each organized around different types of data. Some focused on specific geographic regions. Others targeted particular industries or business types. This wasn't chaos. This was deliberate organization.
The Scale Is Almost Incomprehensible
Let's put 8.7 billion records into perspective, because it's genuinely hard to grasp that number.
China's population is approximately 1.4 billion people. This database contained roughly six records for every single person in the entire country. That means multiple entries per person—different sources, different data collection points, different timestamps.
The database was 16 terabytes in total size. If you tried to print all of it on paper, at 500 pages per ream, you'd have roughly 8 million reams of paper. Stacked. That's a stack about 2,000 kilometers tall.
For context on breaches, this makes the largest publicly known data breaches look almost quaint. Yahoo's breach in 2013 exposed 3 billion accounts. Facebook's Cambridge Analytica scandal involved 87 million profiles. Even the massive Equifax breach of 2017, which affected 147 million people, is dwarfed by this single exposed database.
This isn't just a number. This is a surveillance infrastructure. This is years of data collection, aggregation, and consolidation by someone with resources, intent, and access to multiple information sources.
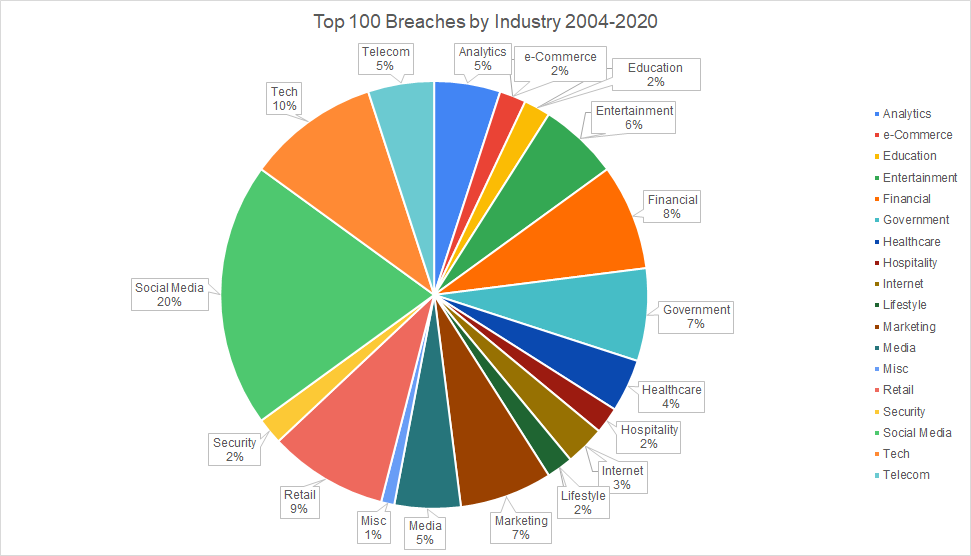
The pie chart illustrates the estimated contribution of various methods to the long-term data collection operation. Data broker partnerships and public records scraping are likely the most significant contributors. Estimated data.
Who's Behind This? The Data Broker Theory
Here's what's genuinely unclear: who actually ran this operation?
The researchers couldn't definitively identify the database owner. No obvious branding. No internal documentation pointing to a specific company or individual. But the structure of the data tells a story.
Evidence strongly suggests this was not a single breach of one company's systems. Instead, this looks like the work of a professional data broker—someone or some organization whose entire business model is collecting, aggregating, and selling personal information.
How do we know? Look at the organization. The data wasn't random or corrupted. It was meticulously segmented into 160+ indices. It was cross-referenced between different data sources. It had timestamps showing when records were imported from different places. It was timestamped across different dates, suggesting ongoing collection efforts.
Data brokers operate in a gray zone, sometimes legal and sometimes very much not. They buy records from public sources, scrape data from websites, license information from other brokers, and aggregate it all into comprehensive databases. They then sell this information to businesses, marketers, investigators, and yes, sometimes to criminals.
The fact that this database was hosted on a bulletproof hosting provider strongly supports this theory. Bulletproof hosters are known for hosting high-risk operations—ransomware infrastructure, stolen data sales, fraud operations, and so on. They deliberately avoid taking down content and don't cooperate with law enforcement. It's where people go when they don't want their infrastructure shut down.
But here's the thing: even bulletproof hosters eventually respond to pressure. After Cybernews reported the discovery, the hosting provider locked down the database. Whether this was voluntary compliance, pressure from higher-ups, or something else isn't clear. But it happened.
The Timeline: How Long Was It Actually Exposed?
The immediate answer is three weeks. That's what researchers confirmed.
But here's the problem: that's probably just when the researchers found it. This database could have been sitting there for much longer. There's no way to definitively determine when it was first exposed or when the bulletproof host originally set it up.
More important is the question of who else found it before the researchers did. In the world of data discovery, security researchers aren't usually first. Script kiddies, enterprising criminals, and automated scanning tools often find exposed databases before ethical security researchers report them.
The researchers themselves acknowledged this: "Despite the short exposure window, the scale of the dataset means that automated scraping during this period could have resulted in widespread secondary dissemination."
Translate that to English: someone probably already copied large portions of this data. Maybe multiple someones. Cybercriminal groups work fast when they find something this valuable. Database scraping tools can pull terabytes of data quickly if they're optimized.
That means even though the database is now locked down, the damage is permanent. The data is out there. How widely it's been distributed is impossible to know.
Not One Breach, but Years of Data Collection
This is perhaps the most important detail.
The researchers found timestamps and import dates throughout the database. These weren't random. They showed a clear pattern: data had been collected and added to this database over an extended period. Not weeks. Not months. Possibly years.
"The presence of timestamps and import dates points to a long-running aggregation effort rather than a single historical breach," the researchers explained in their report.
This changes the narrative completely. This wasn't someone hacking into one company and stealing their customer database in a single night. This was systematic, organized data collection from multiple sources over time.
How would someone collect data at this scale across so many sources? Several methods:
Public records scraping: Government registration databases, business licenses, and other public information can be automatically scraped from official sources. Much of this data is technically public but legally protected by terms of service.
Data broker partnerships: Buying existing datasets from other brokers. The data broker industry is complex and interconnected. Large aggregators often purchase data from smaller collectors.
Hacking and breaches: Likely bought access to stolen databases from other breaches or directly compromised some systems themselves. When companies get breached, their data gets sold and resold multiple times on dark web marketplaces.
Social engineering: Some data might have been obtained by convincing people or employees to hand it over.
Phone number databases: Collections of phone numbers are easier to obtain than you'd think. They're often leaked from telecommunications companies or sold by less scrupulous carriers.
The timestamps in the database suggest this operation was ongoing. New data was being added continuously. This wasn't someone hoarding old information. This was an active intelligence gathering operation.
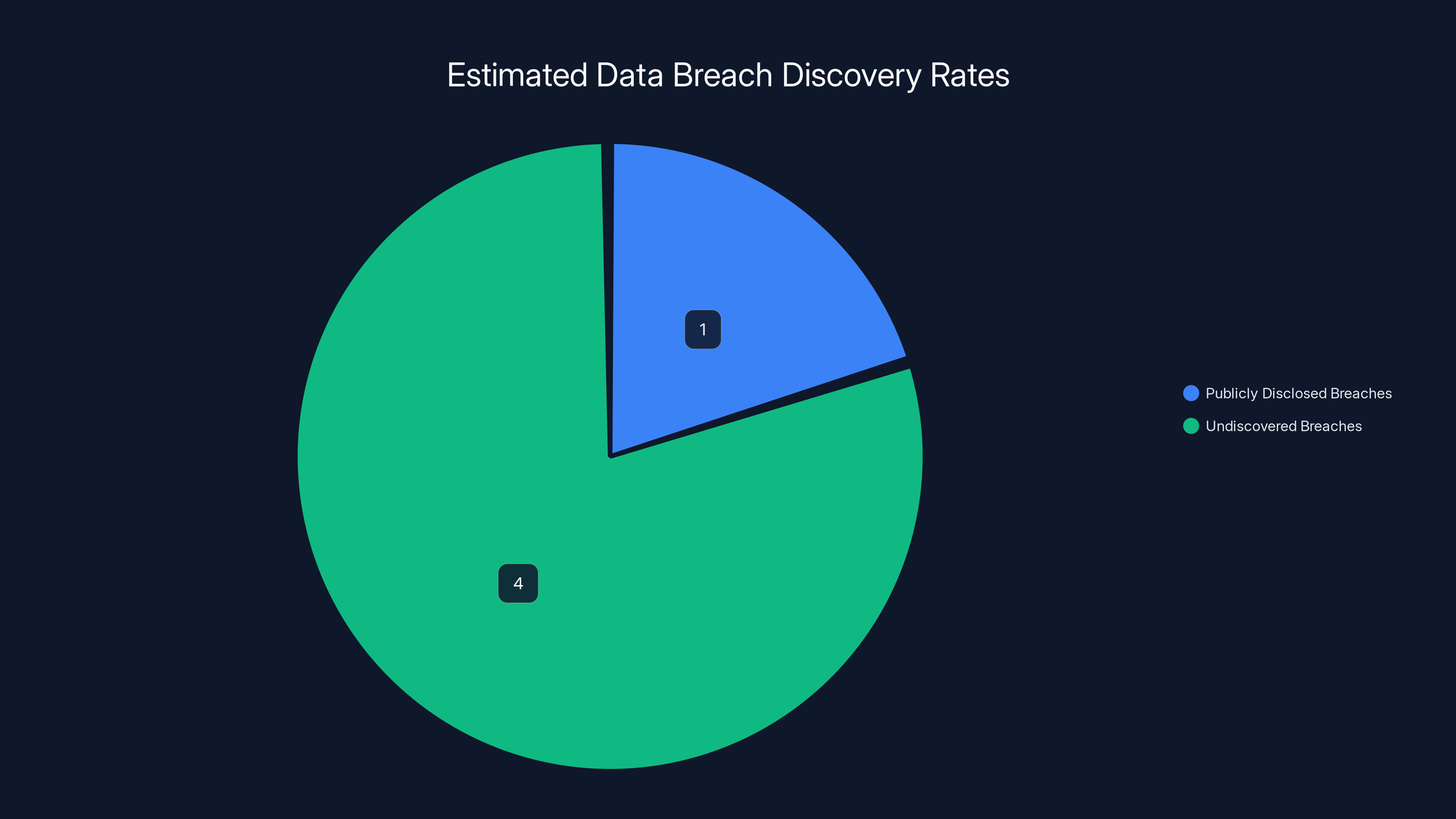
Security researchers estimate that for every data breach publicly disclosed, there are 3-5 breaches that remain undiscovered. This highlights the significant risk of undetected data exposure. (Estimated data)
What This Means if You're Affected
If you have any connection to China—you were born there, you have family there, you have a business registration, you've traveled extensively in China—you should assume your data is in this database.
This is serious because the information exposed enables multiple attack vectors:
Identity theft: Criminals now have enough information to impersonate you. Your name, address, birth date, and phone number are already in their hands. Depending on what they do with it, they could open credit accounts, file tax returns in your name, or commit fraud.
Credential stuffing: Your plaintext passwords mean attackers can immediately try those passwords on your email, financial accounts, social media, and anywhere else you might have used the same password. This is why password reuse is so dangerous.
Social engineering: Combined with your personal information, a criminal can craft highly convincing phishing emails, impersonation attempts, or scams. They know your real address, they know your phone number, they can pretend to be from companies you actually use.
Targeted phishing: Your social media identifiers mean you can be contacted through multiple channels with convincing-looking offers, scams, or malware links.
Financial fraud: Your phone number makes SIM swapping attacks possible. Criminals call your mobile provider, convince them they're you, and redirect your phone number to a device they control. Then they reset passwords to your financial accounts.
Location tracking and physical threats: In rare cases, your address information could enable stalking, home invasion, or other physical crimes.

The Corporate Records Problem
If you operate a business registered in China, or you have financial investments in Chinese companies, the corporate records exposure is equally concerning.
Business registration details, legal representative information, and contact data create a complete picture of business structure and decision-makers. This is intelligence that competitors would pay for, that criminals can use to conduct business email compromise attacks, and that foreign intelligence agencies find valuable.
Companies can be targeted with highly specific phishing emails to financial decision-makers. "Your business license renewal is due" emails that look official because they reference real company details. Invoice fraud. Wire transfer redirection.
For international companies with Chinese subsidiaries, this exposure means detailed organizational information about your China operations is now in criminal hands.
Response From Authorities and Hosting Providers
After Cybernews reported the discovery, action was relatively quick—at least by internet standards.
The bulletproof hosting provider locked down the database. No formal statement was issued about why. They didn't apologize or acknowledge the security failure. They just closed access to it.
What about official responses from Chinese authorities? Silence. No acknowledgment from the government, no official investigation announced, no statement about tracking down those responsible. This could mean several things:
- The Chinese government is investigating quietly behind the scenes
- The government is not prioritizing this investigation
- The government knows who's behind it and is taking internal action
- The government doesn't want to draw attention to how much data brokers have collected
None of these are comforting possibilities.
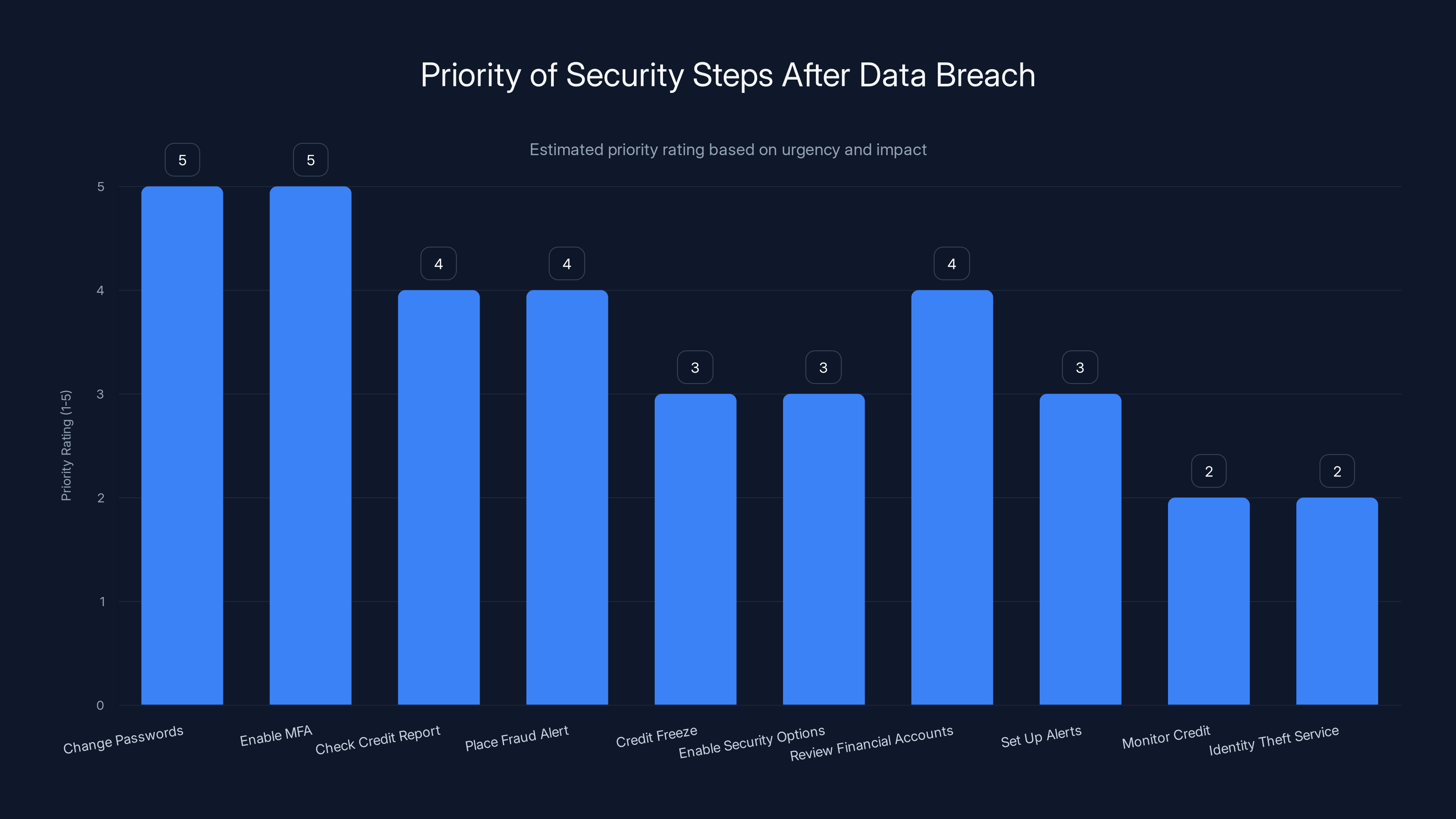
Changing passwords and enabling MFA are top priorities with a rating of 5, as they offer immediate protection. Monitoring credit and considering an identity theft service are ongoing steps with lower immediate priority.
Similar Breaches and Data Broker Operations
This isn't the first massive data broker database exposed. It's not even the first one from China.
In 2024, another massive breach leaked 45 million French records from a data broker operation, including demographic, healthcare, and financial data. The patterns were similar: organized database, multiple data sources, extended collection period.
Before that, an exposed database from a mysterious Chinese firm revealed state-owned cyber weapons and targeting lists, suggesting even government entities were involved in data collection operations.
The difference with this 8.7 billion record database is the sheer scale. This is by far the largest publicly confirmed data aggregation database exposed. The fact that it was so massive yet remained unencrypted and exposed for weeks suggests either:
- The operator got careless and assumed they were too obscure to be noticed
- The infrastructure was genuinely that poorly managed
- They prioritized speed and functionality over security
All of these point to the same conclusion: this wasn't some sophisticated nation-state operation. This was a commercial data broker who knew how to collect and organize data but didn't invest in basic security.
How Data Brokers Actually Operate
Understanding how this database came to exist in the first place requires understanding the data broker industry.
Data brokers are businesses that collect, aggregate, and sell personal information. In the United States, they're somewhat regulated (though still operate in gray areas). In China, regulation is even less clear.
They operate by:
-
Buying data from other brokers: There's a whole secondary market of data sales between brokers. A small broker might scrape phone numbers, then sell those to a larger aggregator.
-
Licensing government records: Public records like vehicle registrations, property ownership, business licenses, and court filings can be licensed in bulk.
-
Scraping websites: Automated tools systematically download public data from websites, directories, and databases.
-
Purchasing from data harbors: Dark web marketplaces where stolen data is bought and sold.
-
Direct sales to clients: Brokers maintain databases and sell access or data exports to whoever will pay.
The biggest brokers operate massive databases with billions of records. They make their money by selling this data to businesses for marketing, credit bureaus for risk assessment, private investigators, and yes, sometimes to criminals.
The data broker industry is a pillar of modern data-driven marketing and risk assessment. But it only works if someone is willing to collect and aggregate data at massive scale. This exposed database is what the data broker industry looks like when security doesn't exist.

What Passwords Were Exposed?
The fact that the database contained plaintext passwords deserves special attention.
If this was merely a data collection operation drawing from public sources, why would there be plaintext passwords? Public government databases don't contain passwords. Business registration records don't have passwords.
This suggests the data came from direct breaches of systems, or from purchased breach data. The passwords were collected alongside other compromised credentials.
Plaintext passwords are extremely dangerous because most people reuse passwords across multiple sites. A criminal finds your password in this database and immediately tries it on:
- Your email account (the master key to everything else)
- Your banking login
- Your PayPal or Stripe account
- Your social media accounts
- Your work accounts if the company was careless about password policies
Even if you've since changed your passwords, if you changed them to something predictable or similar to your old passwords, you're still at risk. Many people increment numbers or add symbols to old passwords instead of creating entirely new ones.
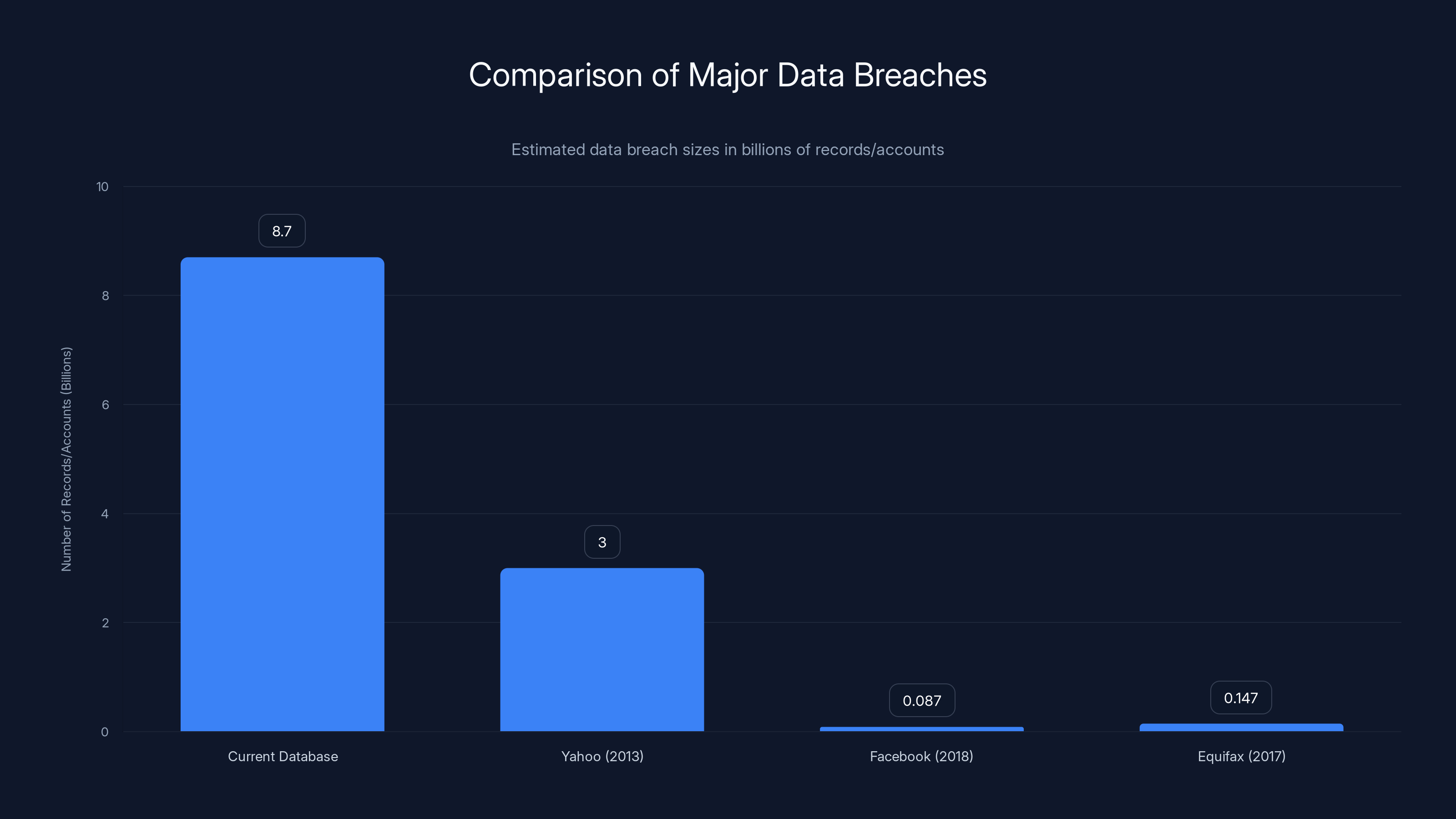
The current database breach exposed 8.7 billion records, significantly surpassing previous major breaches like Yahoo's 3 billion accounts in 2013. Estimated data.
The Corporate Intelligence Angle
The 16 terabytes of corporate intelligence data represents something different from personal data.
Company registration details are often public, but having them compiled into a single searchable database makes them far more valuable. A competitor can query "all manufacturers in this region," pull up 500 companies with their legal representatives and contact details, and start a targeted outreach campaign.
For business email compromise (BEC) attacks, this database is a goldmine. Criminals look up a target company, find the CEO and CFO names, create lookalike email accounts, and send fraudulent wire transfer requests. With organization details already gathered, these attacks become much more convincing.
International companies face additional risks. If your Chinese subsidiary is in this database, competitors, intelligence agencies, and criminals all now have a comprehensive org chart and contact information.
For venture capital firms, this data could expose their portfolio company details. For supply chain operations, it reveals supplier relationships and contact points for disruption.
The corporate intelligence aspect means this breach affects not just individuals but entire business ecosystems.

Automation, Scraping, and Secondary Dissemination
Here's where the situation gets worse than it initially appears.
The researchers noted that automated scraping during the three-week exposure period could have resulted in widespread secondary dissemination. Translation: the bad guys probably already made copies.
It doesn't take sophisticated tools to copy a database. Any decent programmer can write a script to download all 16 terabytes in under a day if they have decent bandwidth. Criminals and intelligence agencies have much better tools and infrastructure.
Once copied, the data gets resold. It gets uploaded to dark web marketplaces. It gets used for targeted attacks. It gets incorporated into other databases. The damage spreads geometrically.
The three-week exposure window is only relevant if we assume:
- The database was actually public the whole time (it was)
- Someone with scanning tools didn't find it earlier (unlikely)
- No automated data scraping occurred before discovery (very unlikely)
- The database owner immediately took it down after discovery (they did)
In reality, multiple threat actors probably discovered this database independently. The fact that Cybernews found it doesn't mean they were the first. They just happened to be the ones who reported it responsibly.
Implications for Personal Security
If your data is in this breach, what does that mean for your security going forward?
Immediate risks:
- Your accounts are vulnerable to password-based attacks immediately
- Phishing emails using your personal information will be more convincing
- SIM swapping attacks become easier if they have your phone number
- Credential stuffing attacks will target every account you've used
Medium-term risks:
- Your information will be resold multiple times
- You'll likely see an increase in spam, phishing, and fraud attempts
- Criminals might use your data to commit fraud that affects your credit score
- You could receive calls or emails targeting you specifically
Long-term risks:
- Your data will exist in criminal databases for years
- You'll be a target for future scams and social engineering
- Identity theft could affect you indefinitely
- Your information might be used without your knowledge
The privacy damage is permanent. You can't un-expose data.
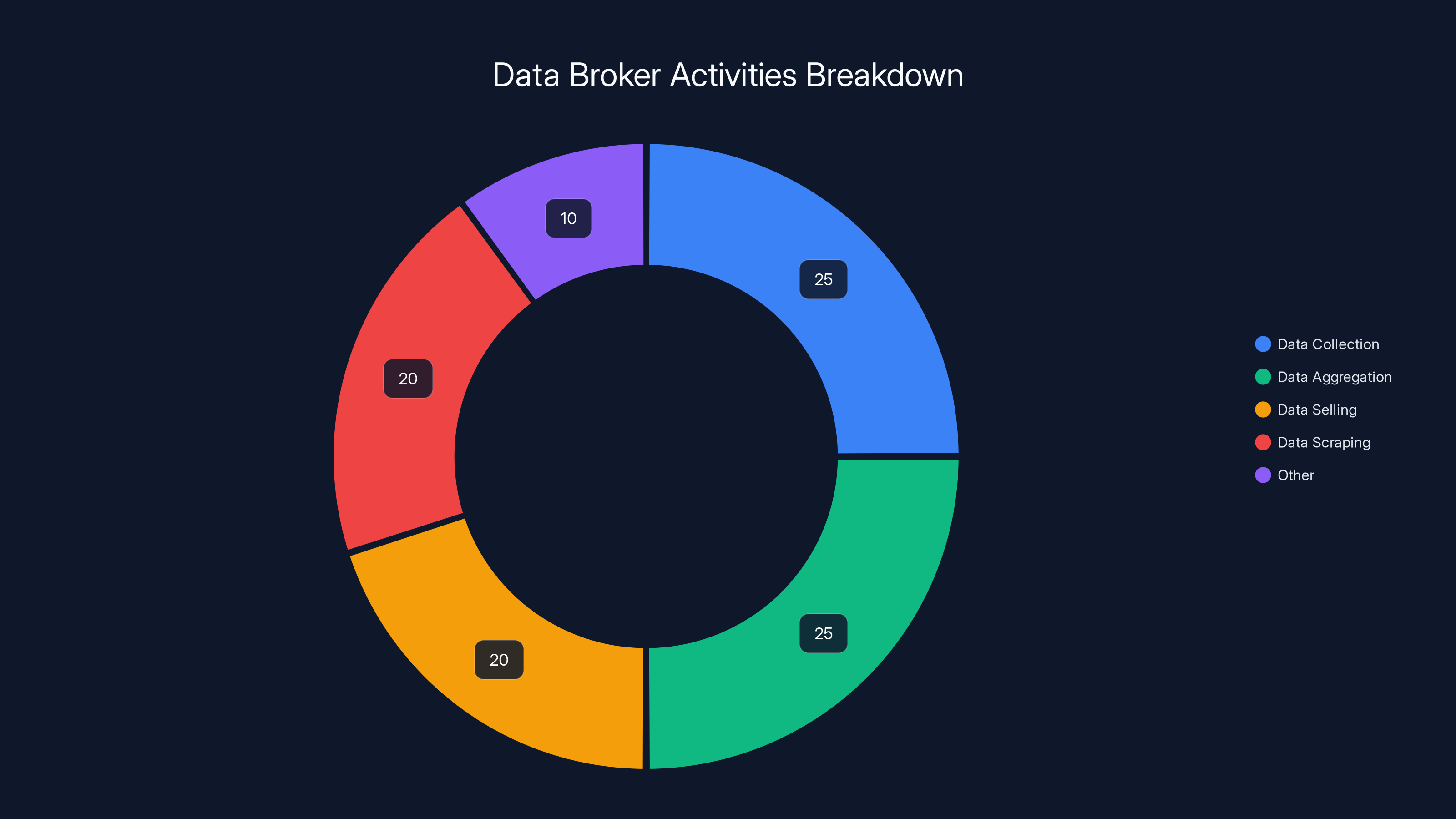
Estimated data shows that data brokers primarily focus on collecting and aggregating data, with significant activities in selling and scraping data. Estimated data.
Steps You Should Take Right Now
If there's any chance your data was in this breach, here's what to do:
Within the next 24 hours:
- Change your passwords for critical accounts—especially email, banking, and financial services
- Use a password manager to generate completely new, random passwords
- Enable multi-factor authentication (MFA) on every account that supports it
- Check your credit report at all three bureaus (Equifax, Experian, Trans Union) for suspicious activity
- Place a fraud alert on your credit if you find anything suspicious
Within the next week: 6. Consider a credit freeze if you're concerned about identity theft 7. Enable additional security options like requiring a PIN for account changes 8. Review your financial accounts for unauthorized activity 9. Set up alerts on your bank and credit cards for unusual activity 10. Check your email account for suspicious recovery options or forwarding rules
Ongoing: 11. Monitor your credit and financial accounts monthly for the next year minimum 12. Be extremely cautious about unexpected emails, calls, or messages 13. Never verify personal information when someone contacts you—call the organization directly 14. Consider an identity theft monitoring service 15. Keep all software and devices updated
The Broader Pattern of Data Aggregation
This breach is a symptom of a much larger problem: the existence of massive data aggregation operations that nobody adequately regulates.
Data brokers exist in a regulatory gray zone almost everywhere. In the EU, GDPR provides some protections, but enforcement is minimal. In the US, the FTC has started paying attention, but regulation is incomplete. In China, legitimate regulation barely exists.
The incentives are clear: collect as much data as possible, because data is valuable. Sell it to whoever will pay. Don't invest in security because it's expensive and nobody's enforcing it anyway.
Until governments implement serious consequences—not just fines, but criminal liability—this pattern will continue. We'll keep seeing massive exposed databases because the operators have calculated that the risk of exposure is worth the profit from selling the data.
Even more concerning, this particular database might have been one of many. If this broker had 8.7 billion records in a single database, they might have similar operations elsewhere. This might be just one piece of a larger intelligence apparatus.

What Companies Should Do
If you're a business and you think your company records might be in this database, here's what matters:
Assessment: Find out if your company is in there. Security researchers might be able to help, or you can try searching underground marketplaces or asking security firms to investigate.
Notification: You're probably not legally required to notify customers (depending on jurisdiction), but consider it anyway. You should definitely notify employees and business partners.
Investigation: Work with security firms to understand what data was taken and what's now at risk.
Defense: Implement harder defenses for executive and financial systems. Assumption of breach applies—act as though criminals have detailed knowledge of your organization.
Relationships: Alert your supply chain partners, investors, and anyone else who might be affected.
For companies operating in China or dealing with Chinese partners, this database represents a legitimate counter-intelligence threat. Competitors and foreign intelligence agencies now have detailed information about your operations, structure, and decision-makers.
The Future of Data Privacy in China
This breach raises questions about the future of data privacy in China specifically and in authoritarian countries more generally.
Data privacy regulation in China is contradictory. On one hand, the government has implemented data protection laws like the Personal Information Protection Law (PIPL). On the other hand, the same government demands access to data for surveillance and control purposes.
Data brokers operate in this environment knowing that:
- Law enforcement won't aggressively investigate them
- The government might actually want them to collect this data
- International cooperation on prosecution is unlikely
- Penalties, if they exist, are manageable
This creates a permissive environment for massive data aggregation operations. Why would a broker invest in security if the government arguably benefits from their data collection?
For individuals, privacy protection is mostly up to you. Technology solutions like VPNs, encrypted messaging, and privacy-focused services help. But it's a losing battle against determined adversaries with infrastructure resources.
International Implications
This breach matters beyond China's borders.
For anyone who:
- Has family or business connections in China
- Does business with Chinese companies
- Has traveled to China
- Has Chinese phone numbers or email accounts
- Invests in Chinese companies
Your data is likely in this database alongside millions of others.
International corporations should be concerned about their China operations. Competitors, intelligence agencies, and criminals now have detailed information about who works there and how it's organized.
For researchers, activists, journalists, and anyone with sensitive reasons for connecting to China, this database represents a security nightmare. Your identity is tied to your activities.
For government officials and military personnel with connections to China, the implications are serious. Intelligence agencies worldwide are probably already examining what's in this database.
The fact that this data was hosted on a bulletproof provider suggests it might have been explicitly set up for international customers. Non-Chinese brokers buying Chinese intelligence. Foreign companies buying competitive information. Intelligence agencies acquiring information about international targets in China.
Learning From This: Security Lessons
What should we learn from this breach?
First: Massive databases without encryption and access controls shouldn't exist. This is basic security. Any database containing sensitive personal information should have authentication, encryption at rest, encryption in transit, and audit logging. The fact that this database had none of these is negligence on the part of its operator.
Second: Data minimization matters. The database aggregated information that didn't need to be in a single place. If this had been broken into multiple smaller, encrypted databases with access controls, the breach would have been far less catastrophic.
Third: Security by obscurity doesn't work. The operator apparently assumed their database was obscure enough that nobody would find it. But Elasticsearch instances are trivially easy to scan for on the internet. Any script that checks port 9200 (the default Elasticsearch port) finds them immediately.
Fourth: Regulatory pressure matters, but it's insufficient. China has data protection laws. They just don't enforce them against operations like this.
Fifth: Consumer awareness is limited. Most people don't know that massive data brokers exist and own their information. Privacy is an afterthought until a breach happens.

What Happens to Exposed Data?
Now that this database is locked down, what happens to the data that was already copied?
Historically, massive datasets like this get:
- Resold on dark web marketplaces: Complete database sales for cryptocurrency
- Incorporated into other databases: Merged with other stolen data to create even more comprehensive profiles
- Used for targeted attacks: Criminals match phone numbers with real people and execute fraud campaigns
- Purchased by intelligence agencies: Foreign governments buy access to this data
- Traded among cybercriminal groups: Shared as a resource for other operations
- Used for social engineering: Phishing campaigns built on accurate personal information
- Leveraged for deepfakes and fraud: Personal information used to create convincing false identities
The data has a long shelf life. A password stolen today might not be used for months or years. A phone number sold today could enable SIM swapping next year. A home address could be used for physical threats much later.
This is why the breach isn't a discrete event. It's a permanent change in the threat landscape.
FAQ
What is the 8.7 billion record Chinese data breach?
The breach refers to an exposed Elasticsearch database discovered in 2024 that contained approximately 8.7 billion records of Chinese individuals and businesses. The database was unsecured and publicly accessible for at least three weeks before being locked down after security researchers from Cybernews reported the discovery. It's one of the largest known data exposures ever documented.
How did the database get exposed so badly?
The Elasticsearch cluster was hosted on a bulletproof hosting provider without basic security measures like authentication, encryption, or access controls. The operator apparently relied on obscurity, assuming the database was hidden enough that it wouldn't be discovered. However, Elasticsearch instances are trivially easy to find using automated port scanning tools. The lack of basic security combined with the massive scale suggests the operator prioritized functionality over protection.
What personal information was exposed?
The database contained names, residential addresses, phone numbers, birth dates, gender information, social media identifiers, and plaintext passwords for individuals. For businesses, it included company registration details, legal representative information, business contact data, licensing metadata, and registration addresses. This combination of personal and corporate information enables identity theft, credential stuffing, phishing attacks, and business fraud.
Who is affected by this breach?
Anyone with a connection to China is potentially affected. This includes people born in China, those with family there, individuals with business registrations in China, and anyone who has traveled there extensively. The database primarily contains information about mainland Chinese residents, but the exposure affects international individuals and companies with China operations or business relationships.
How long was the database actually exposed?
The confirmed exposure period was at least three weeks before the hosting provider locked it down after Cybernews reported the discovery. However, the database could have been publicly accessible for much longer before researchers found it. Additionally, given the time required to copy 16 terabytes of data, it's likely that criminal groups discovered and copied portions of the database before responsible disclosure occurred.
What should I do if my data was exposed?
Take these immediate steps: change passwords for critical accounts (especially email and banking), enable multi-factor authentication everywhere possible, check your credit reports for fraudulent activity, place a fraud alert if needed, and monitor your financial accounts. Ongoing monitoring should include monthly credit checks, email security reviews, and caution about unsolicited contact. Consider working with identity theft monitoring services if you're particularly concerned.
Is plaintext password exposure particularly serious?
Yes, extremely serious. Plaintext passwords mean criminals can immediately attempt credential stuffing attacks on other websites. Since many people reuse passwords across multiple sites, a password stolen here could provide access to your email, banking, social media, and other critical accounts. This is why changing all your passwords to unique, complex passwords is the most critical action to take after a breach like this.
How do data brokers collect data at this scale?
Data brokers use multiple sources: scraping public data from websites and government registries, purchasing data from other brokers, buying stolen data from dark web marketplaces, licensing information from telecommunications companies and public records vendors, and sometimes directly hacking into systems. The timestamps in this database show it was actively collected over an extended period, not from a single breach event.
What makes this breach worse than previous major breaches?
The scale is significantly larger than previous known breaches. At 8.7 billion records, it dwarfs major breaches like Yahoo (3 billion accounts) and Equifax (147 million). The fact that it was a single organized database from a data broker means the records are comprehensive and cross-referenced, making them far more useful for targeted attacks than fragmented stolen data. Additionally, it includes plaintext passwords, social media identifiers, and corporate intelligence all in one place.
Could foreign governments have accessed this data?
It's very possible. The database was publicly accessible on the internet for weeks or longer. Any sophisticated actor with network scanning capabilities could have found it. Intelligence agencies from major powers likely obtained copies. The fact that it was hosted on a bulletproof provider suggests it was intentionally set up to serve international customers, which could include state actors looking to acquire intelligence on individuals and businesses.
What are the long-term implications?
The damage is permanent. Once exposed, personal data remains valuable to criminals indefinitely. You should expect an increased risk of fraud, phishing, and social engineering for years. Any system that relies on your password, phone number, address, or identity could potentially be compromised. Protection requires ongoing vigilance including password management, financial monitoring, and caution about social engineering attempts.

Staying Protected Going Forward
This breach represents a new baseline threat landscape. Massive databases of personal information exist, and they will continue to be exposed.
The only permanent solutions are systemic: governments need to enforce data protection laws, companies need to encrypt sensitive data, brokers need to be regulated, and individuals need tools and awareness to protect themselves.
Until that happens, assume your personal information has been exposed to adversaries. Protect your most critical accounts with unique, strong passwords and multi-factor authentication. Monitor your finances and credit. Be skeptical of unsolicited contact. Use password managers. Keep software updated.
The 8.7 billion records now out there won't magically disappear. But you can dramatically reduce the damage they cause by taking security seriously. Don't wait for the next breach. Act now.
The internet is not private. Your data is not secure. This breach confirms what security experts have been saying for years: assume breach, and protect yourself accordingly. The individuals and businesses in this database learned that lesson the hard way.
Key Takeaways
- An unsecured Elasticsearch database exposed 8.7 billion records of Chinese individuals and businesses—one of the largest known data breaches ever documented
- Exposed data includes personal identifiable information, plaintext passwords, corporate records, and business intelligence—all organized across 160+ indices
- Evidence suggests this was a long-running data broker operation collecting from multiple sources over years, not a single historical breach
- The database remained publicly accessible for at least three weeks before being locked down after Cybernews reported the discovery
- Assume your data was exposed if you have any connection to China, and immediately change critical passwords, enable multi-factor authentication, and monitor your credit
Related Articles
- Harvard & UPenn Data Breaches: Inside ShinyHunters' Attack [2025]
- ICE Domestic Terrorists Database: The First Amendment Crisis [2025]
- ExpressVPN 81% Off Deal: Is It Worth It? [2025]
- Switzerland's Data Retention Law: Privacy Crisis [2025]
- Coinbase Insider Breach Exposed 30 Customers' Data [2025]
- Apple Pay Unusual Activity Scam: How to Spot Fake Messages [2025]
![8.7 Billion Records Exposed: Inside the Massive Chinese Data Breach [2025]](https://tryrunable.com/blog/8-7-billion-records-exposed-inside-the-massive-chinese-data-/image-1-1770235722982.jpg)



