Coinbase Insider Breach: What You Need to Know About the Data Exposure [2025]
In mid-2025, cryptocurrency exchange Coinbase confirmed what many suspected: an insider had accessed customer data without authorization. The breach wasn't massive by modern standards, but it exposed a critical vulnerability that affects everyone holding crypto on major platforms.
Here's the thing: insider threats are arguably more dangerous than external hacks. An employee or contractor already has access. They don't need to find a zero-day vulnerability or brute-force passwords. They just walk out the door with what they shouldn't have.
This incident affects roughly 30 customers, but the real story is what it reveals about how cryptocurrency exchanges operate, where their security actually breaks down, and what you should do if you use platforms like Coinbase.
TL; DR
- The Breach: A Coinbase contractor accessed data on approximately 30 customers without authorization
- What Was Exposed: Names, email addresses, dates of birth, phone numbers, KYC information, wallet balances, and transaction history
- Company Response: The contractor was fired, affected customers were notified, and free identity theft protection was offered
- Security Context: This echoes a 2025 incident where cybercriminals bribed support agents to steal $400 million worth of customer data
- Bottom Line: Insider threats at crypto exchanges remain a persistent risk, despite increased security measures
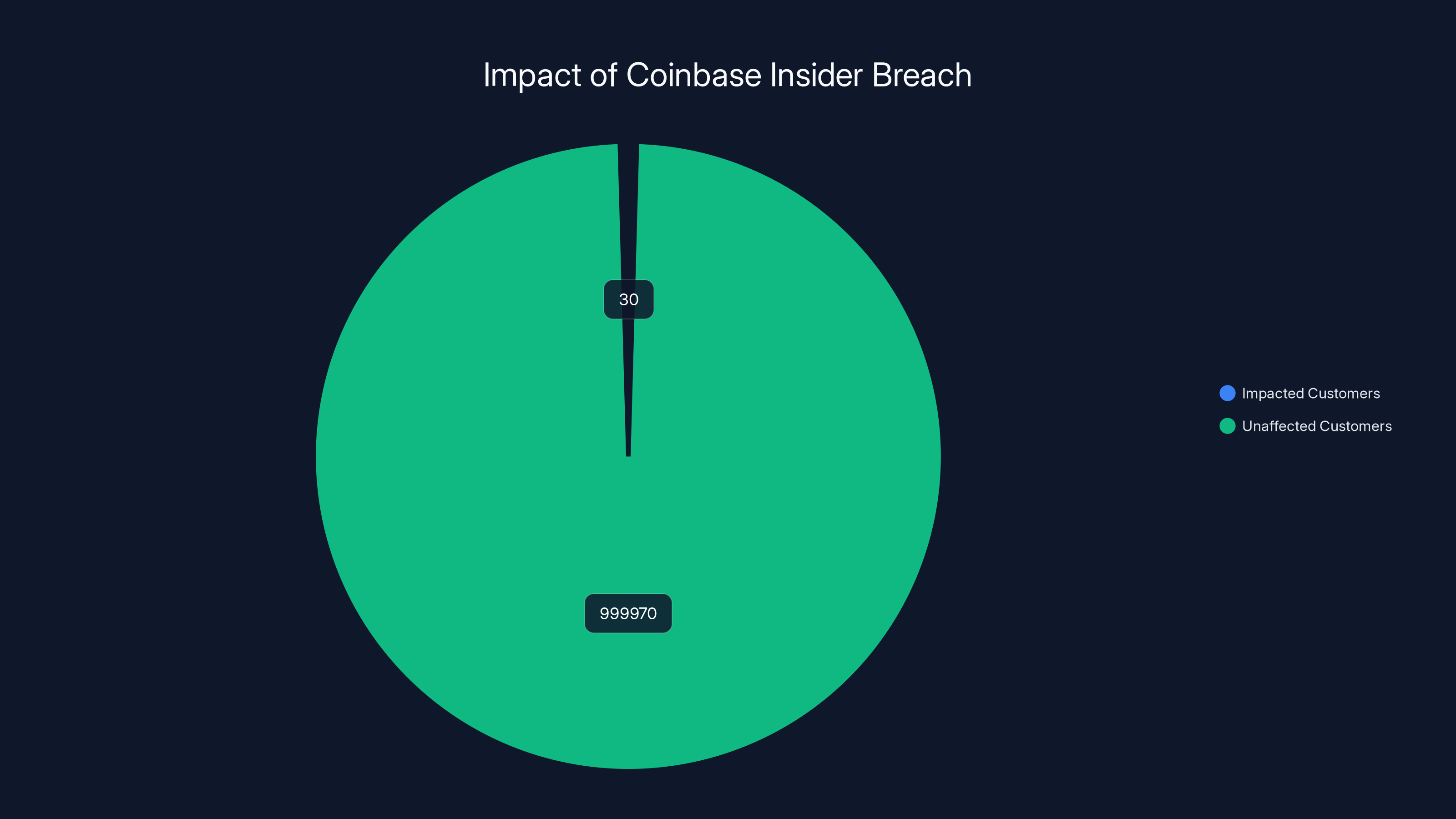
The breach affected approximately 30 customers, a minuscule fraction of Coinbase's millions of users. Estimated data based on reported figures.
Understanding the Coinbase Insider Breach Details
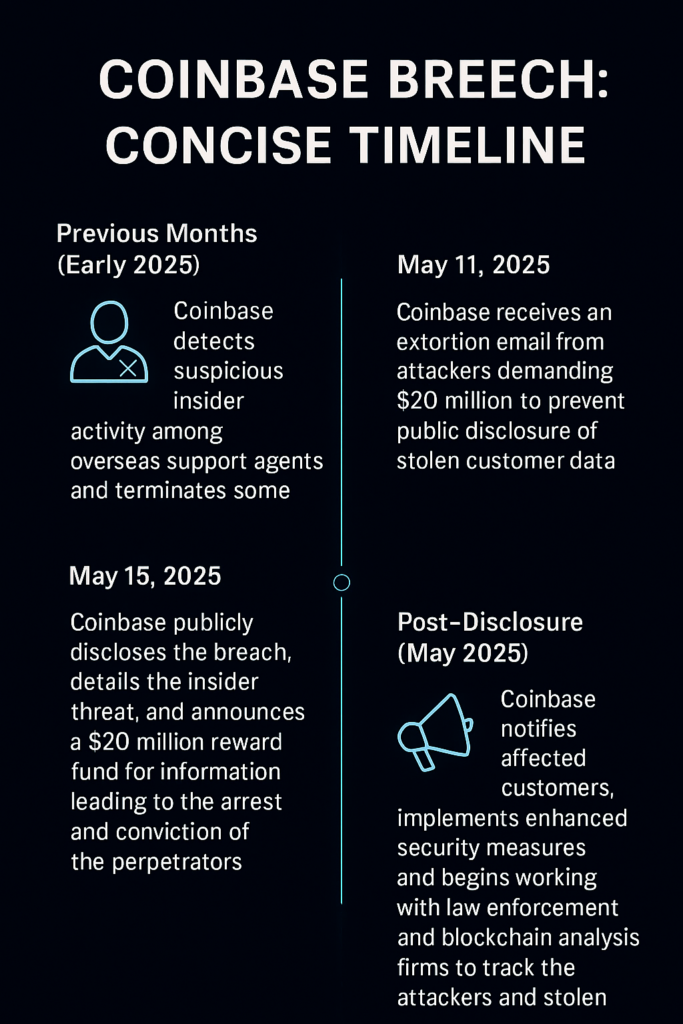
Let me be clear about what actually happened here. In mid-2025, Coinbase's security team detected that a single contractor had improperly accessed customer information. The company waited some time before publicly disclosing this, which immediately raises questions about transparency and when customers should have been notified.
According to Coinbase's official statement to Bleeping Computer, roughly 30 customers were impacted. That's a tiny fraction of Coinbase's user base, which numbers in the millions. But numbers don't tell the whole story. Each of those 30 people had their most sensitive financial and personal information exposed.
The contractor's access wasn't some one-off incident. This was systematic access to customer support systems. The person could pull up account information, view KYC (Know Your Customer) documentation, see wallet balances, and review transaction histories. That's not a minor data exposure. That's a complete window into someone's financial life.
What makes this breach particularly interesting is the timing. It happened amid a broader pattern of insider threats in the crypto space. Just weeks earlier, Coinbase had dealt with an even more serious incident where overseas support agents were actively bribed to steal customer data.
How the Contractor Gained Access
The details about exactly how this contractor could access customer data aren't fully public, but we can infer from what happened. Coinbase customer support systems contain sensitive information by design. Support agents need access to help customers recover accounts, verify transactions, and handle disputes.
Here's the security problem: when you give someone legitimate access to handle customer support, that same access can be abused. There's no easy way around this without making customer support completely useless. You need some level of access, but that access becomes a vulnerability if someone decides to abuse it.
The contractor was able to access internal support interfaces that contained names, email addresses, dates of birth, phone numbers, KYC information, wallet balances, and complete transaction histories. Screenshots allegedly showing this information later appeared on ransomware operator Telegram channels, though the company noted those could have been obtained by other means.
This suggests the contractor probably extracted data and shared it with someone else, or the data was accessed through some secondary channel. Either way, the information got out.
The Timeline of Discovery and Response
Coinbase's security team detected the unauthorized access and acted relatively quickly to contain it. The contractor was fired. Affected customers were notified. The company offered free identity theft protection services and reported the incident to regulators.
But here's where it gets murky: how long between when the access occurred and when it was detected? The company hasn't said. Days? Weeks? Months? That gap matters enormously. The longer data sits outside of secure systems, the more time someone has to monetize it.
The fact that screenshots of internal Coinbase support interfaces appeared on Telegram channels suggests the data made it pretty far. Whether the contractor directly shared it or whether they sold access to someone else remains unclear. Either way, the genie was out of the bottle.
Coinbase's response included:
- Immediate Termination: The contractor was fired as soon as the unauthorized access was discovered
- Customer Notification: All 30 affected individuals were contacted directly
- Free Identity Theft Protection: Coinbase covered the cost of identity theft protection services for one year
- Regulatory Reporting: The incident was reported to appropriate financial regulators
- No Funds Lost: Cryptocurrency holdings and funds were not compromised
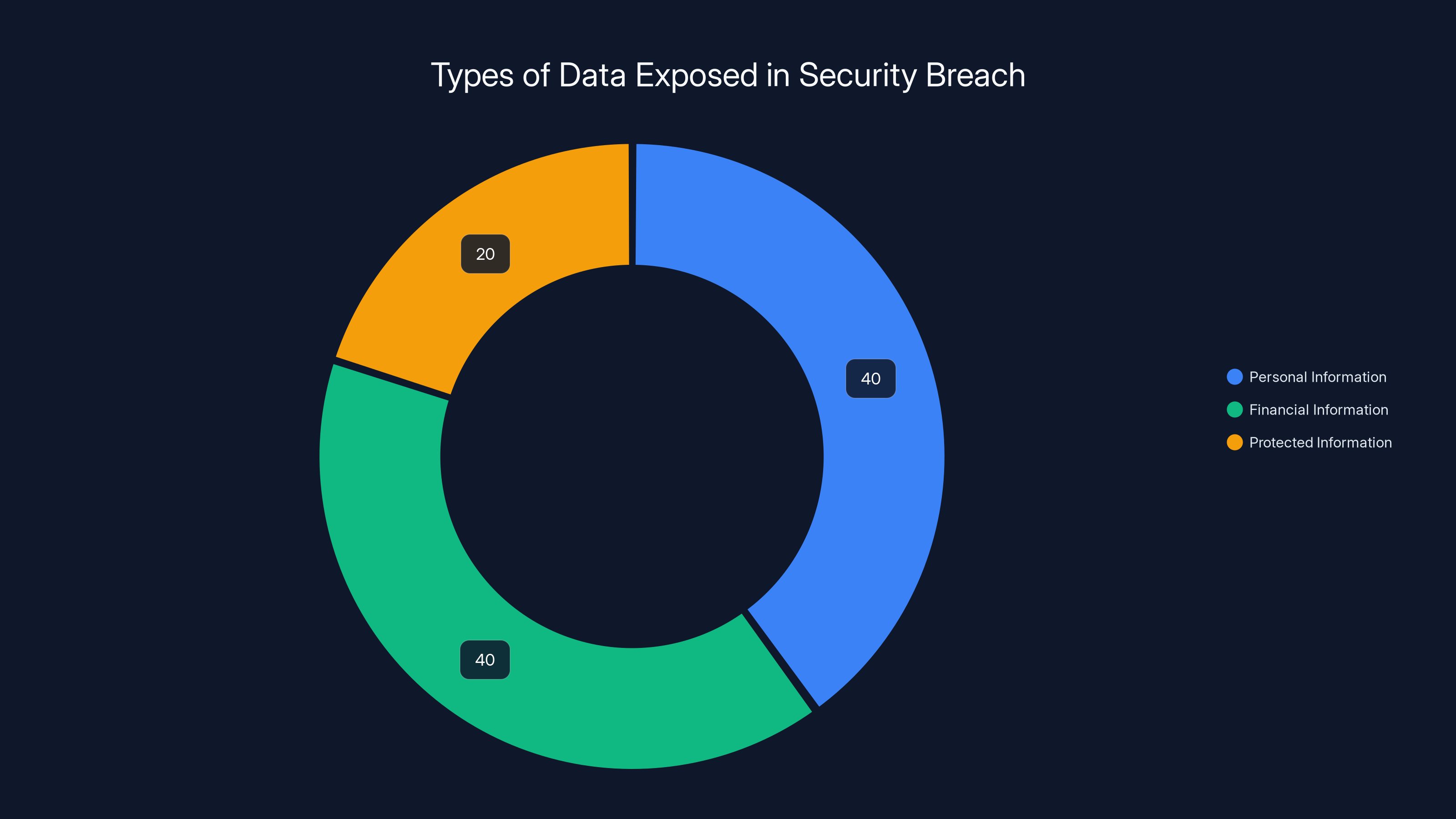
The breach exposed 40% personal and 40% financial information, while 20% of the data remained protected, including passwords and private keys. Estimated data.
The Broader Pattern: Insider Threats in Crypto
This incident doesn't exist in a vacuum. Just weeks before this contractor breach, Coinbase experienced something far more serious: a coordinated attack where cybercriminals bribed overseas support agents to steal customer data.
In May 2025, Coinbase disclosed that criminals had actively recruited and bribed a group of rogue overseas support agents. These insiders used their legitimate access to customer support systems to steal account data for a subset of customers. The goal was to facilitate social engineering attacks, where bad actors would take over accounts and transfer cryptocurrency to themselves.
How much data was at risk? The criminals demanded
The key difference between that incident and the contractor breach: the May attack was financially motivated and coordinated. These were criminal networks actively targeting Coinbase and its customers. The contractor situation might have been similar, or it might have been opportunistic. We don't have enough information to know for sure.
What's concerning is that Coinbase's business model inherently creates insider threat risks. Cryptocurrency exchanges handle customer funds and maintain detailed KYC documentation. Employees and contractors have access to this information because they need it to do their jobs. You can't run a crypto exchange without some people having access to sensitive systems.
But you can improve how you manage that access. You can implement:
- Multi-person approval processes for sensitive data access
- Detailed audit trails that log who accessed what and when
- Behavioral monitoring to detect unusual access patterns
- Regular background checks and ongoing vetting of contractors
- Role-based access control that limits each person to only the data they absolutely need
- Time-limited access that requires re-approval for ongoing access
The May 2025 Bribery Incident: A Deeper Look
Let's zoom in on the May incident because it reveals something critical about cryptocurrency exchange security. Cybercriminals didn't need to compromise Coinbase's infrastructure. They didn't need to find vulnerabilities in code or APIs. They just needed money.
They recruited overseas support agents and bribed them to abuse their legitimate access. The agents pulled customer account data, and the criminals used that data to run social engineering attacks. They'd contact customers pretending to be support staff, convince them to transfer cryptocurrency, or simply take over accounts outright.
When this happens, there's no way to recover the stolen cryptocurrency. Unlike bank transfers, crypto transactions are permanent and irreversible. A customer loses their funds, and there's no clearing house to reverse the transaction.
Coinbase's response was both smart and unusual. Rather than trying to hide the incident or minimize the damage, they went on offense. They:
- Publicly disclosed the incident to warn customers and the industry
- Offered reimbursement to customers who were defrauded as a result
- Placed a bounty on information leading to arrests
- Improved their security by presumably increasing oversight of overseas support operations
But the fundamental vulnerability remains: somewhere, someone has access to customer data. Whether that access is abused is partly a human character issue and partly a structural security issue.
What Data Was Actually Exposed?
Let's be specific about what information the contractor accessed. This matters because different types of data have different risks.
Personal Information Exposed:
- Full legal names
- Email addresses
- Dates of birth
- Phone numbers
Financial Information Exposed:
- KYC documentation (government-issued ID scans, proof of address, etc.)
- Cryptocurrency wallet balances
- Complete transaction history
What Was NOT Exposed:
- Passwords
- Private keys
- Two-factor authentication codes
- Seed phrases
Notably Protected:
- Coinbase Prime accounts were untouched
- No actual cryptocurrency funds were stolen
- No password or authentication credentials were compromised
Here's what this means practically. If you were one of the 30 affected customers, someone knows:
- How much cryptocurrency you own - This makes you a target for ransom attacks, sophisticated phishing, and physical theft
- Your identity - This can be used for synthetic identity fraud, account takeover on other platforms, or SIM swapping attacks
- Your transaction history - This reveals your trading patterns and investment thesis
- Your KYC documentation - This can be used to open fraudulent accounts elsewhere or for identity theft
The good news: the attacker didn't get your private keys or passwords. If they had, they could have simply stolen your cryptocurrency directly. That didn't happen.

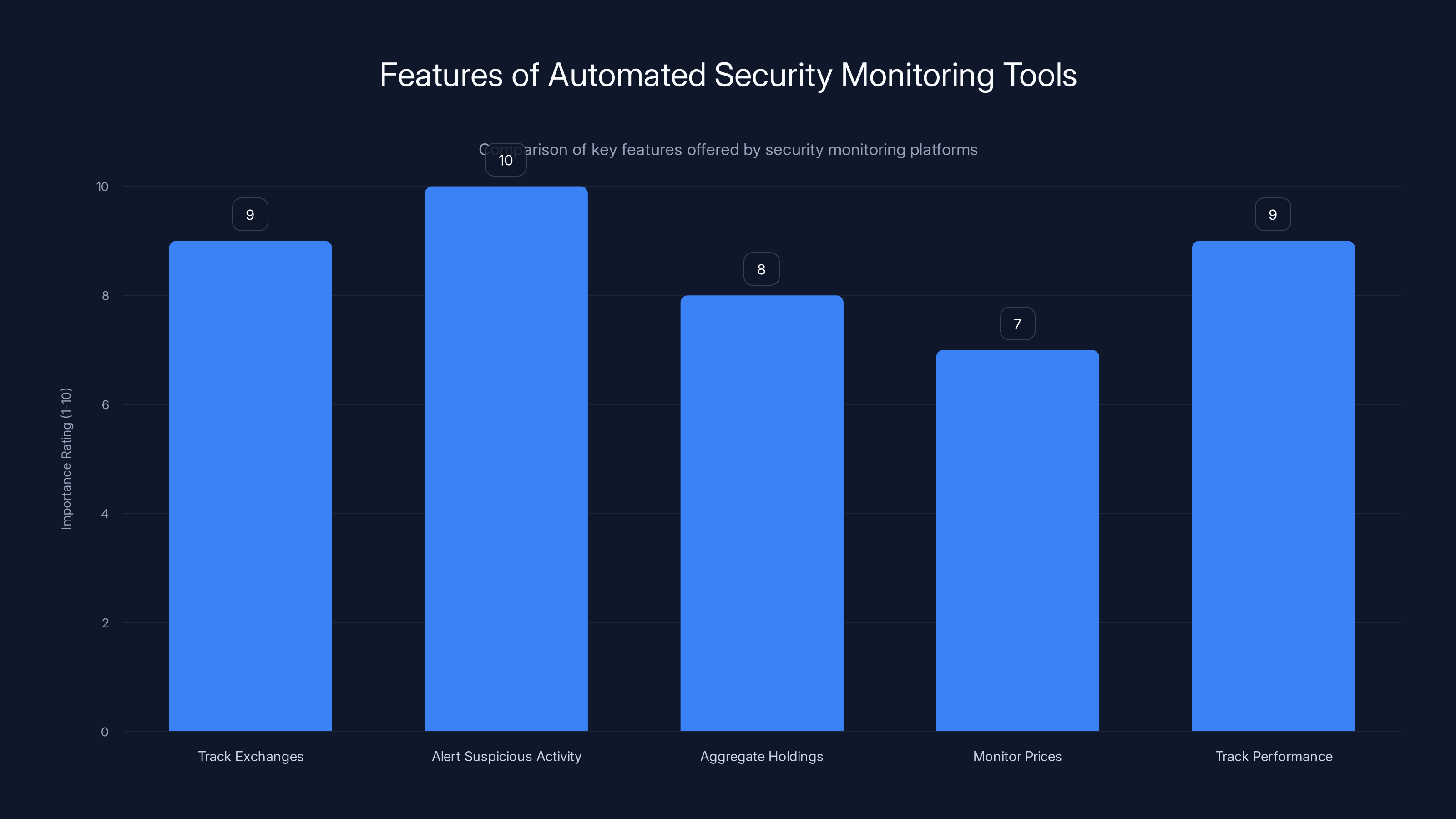
Automated security monitoring tools are highly valued for their ability to alert on suspicious activity and track multiple exchanges, with importance ratings of 10 and 9 respectively. Estimated data.
Insider Threats vs. External Hacks: Why Contractors Are High-Risk
There's a critical difference between insider threats and external hacks, and the Coinbase situation highlights why contractors amplify this risk.
External Hacks require:
- Finding a vulnerability in your systems
- Developing an exploit
- Breaking through defensive measures
- Exfiltrating data without being noticed
Insider Threats from employees require:
- Access they already have
- A decision to abuse that access
- Moving data from inside the firewall to outside
Insider Threats from Contractors add complexity:
- The contractor is not an employee, so standard HR oversight might be lighter
- The contractor might have been onboarded quickly without deep background checks
- The contractor often has time-limited access but might have longer privileges than necessary
- The contractor relationship is less stable, making them more vulnerable to bribery or coercion
In the Coinbase case, we're talking about a contractor. Contractors often have the same access as employees but with less institutional loyalty, less oversight, and sometimes less thorough vetting. They're a higher-risk category.
The cryptocurrency industry has a particular problem here. Building crypto platforms requires specialized engineers and security professionals. There aren't enough of them to hire full-time at every company, so extensive contractor networks exist. More contractors equals more access points that need monitoring.
Access Control Fundamentals
Proper insider threat mitigation requires multiple layers:
Layer 1: Least Privilege - Every person gets only the minimum access needed to do their job, no more. A support agent helping customers shouldn't have access to private keys or administrative functions.
Layer 2: Audit Trails - Every access to sensitive data is logged with timestamps, user IDs, and what was accessed. If someone pulls 30 customer records in one afternoon, that looks suspicious and should trigger alerts.
Layer 3: Anomaly Detection - Systems monitor for unusual access patterns. A contractor who normally accesses 2-3 customer records per day suddenly pulling 50? That's a red flag.
Layer 4: Separation of Duties - No single person can approve and execute sensitive actions. You need multiple people involved in critical decisions.
Layer 5: Regular Audits - You don't wait for someone to report a problem. You regularly audit access logs, check that access controls are working, and verify that people only have the permissions they should have.
The Coinbase incident suggests one or more of these layers wasn't working properly. Either the contractor had more access than they needed, the audit trail didn't catch unusual activity, or anomaly detection wasn't in place.
Identity Theft Protection: What It Actually Covers
Coinbase offered free identity theft protection to affected customers. That sounds good, but what does it actually mean?
Identity theft protection services typically include:
- Credit monitoring - Watches your credit report for unauthorized accounts or inquiries
- Dark web monitoring - Scans criminal forums and databases for your personal information
- Identity theft insurance - Covers some costs if you become a victim (up to a limit)
- Fraud resolution assistance - Helps you fix things if fraudulent accounts are opened in your name
- Public records monitoring - Alerts you if someone tries to open utilities or take out loans in your name
What it doesn't do:
- Prevent identity theft - It detects it, not prevents it
- Protect your cryptocurrency - Identity theft protection doesn't recover stolen crypto
- Reverse fraudulent transactions - If someone uses your information to open a credit card account, you can dispute it, but the process is tedious and stressful
- Guarantee compensation - Insurance has limits and exclusions
For the 30 affected Coinbase customers, this protection is valuable but not a complete solution. Someone has their personal information and knows they own cryptocurrency. That makes them a target going forward.

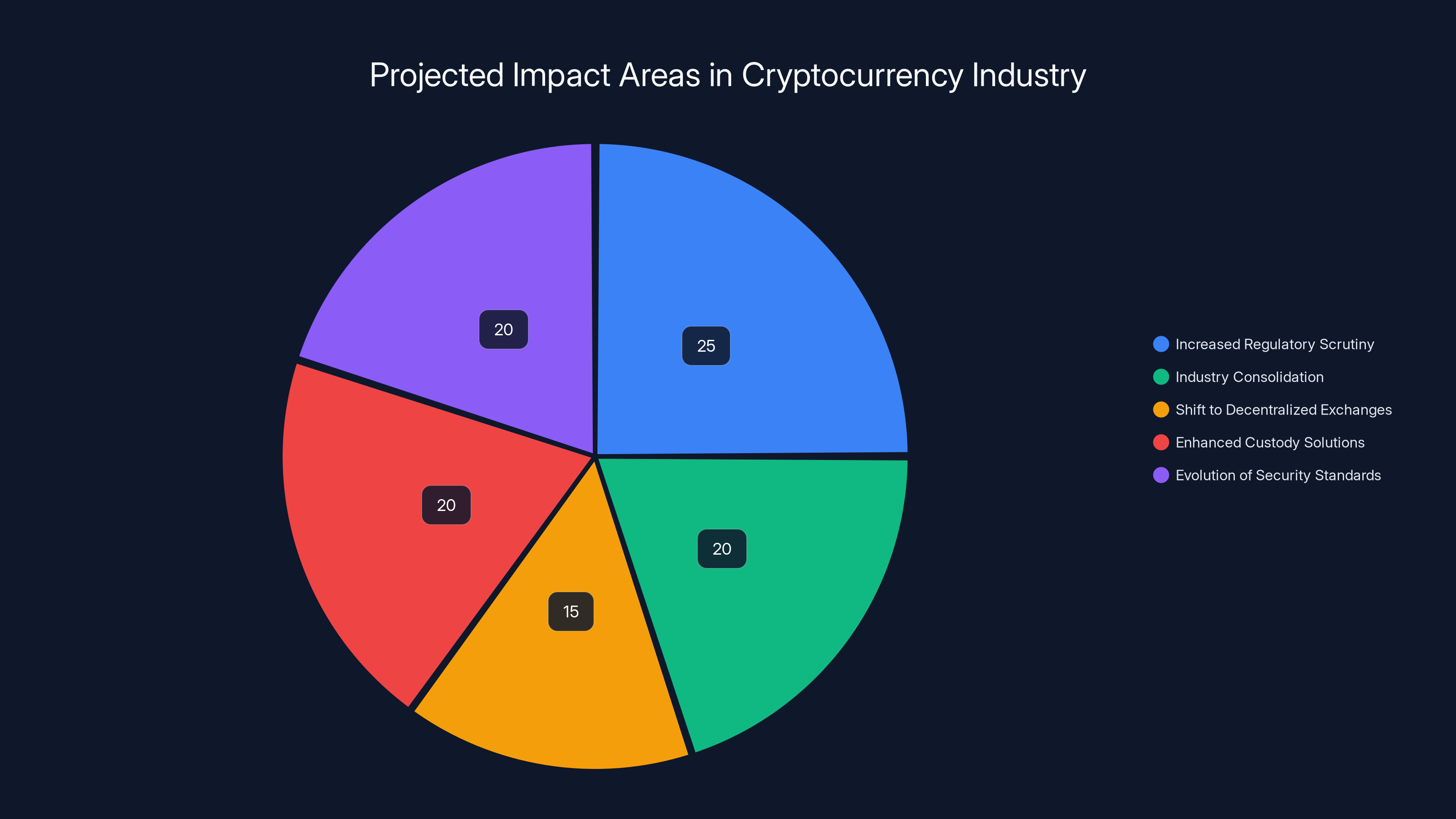
Estimated data suggests that increased regulatory scrutiny and the evolution of security standards will be the primary focus areas in the cryptocurrency industry post-incident, each accounting for about 25% of the focus.
Cryptocurrency Exchange Security Standards and Regulations
Coinbase operates in a heavily regulated environment, at least compared to other cryptocurrency platforms. The company is licensed as a money services business in multiple jurisdictions and follows strict compliance requirements.
But here's the reality: financial regulations around cryptocurrency are still evolving. Different countries have different requirements. Some exchanges operate in jurisdictions with minimal oversight. Even for regulated exchanges like Coinbase, insider threat requirements aren't always clearly defined in regulations.
Financial institutions have long-standing practices for insider threat prevention:
- Regular background checks - Especially thorough for people with access to customer data
- Mandatory time off - Forces people to rotate out of roles, making embezzlement harder
- Restricted account access - Senior executives can't approve their own transactions
- Spouse/family conflict of interest checks - Ensures people aren't managing accounts of family members
- Detailed transaction monitoring - Flags unusual activity
The cryptocurrency industry is slowly adopting these practices, but adoption is uneven. Some platforms implement strict controls. Others operate in regulatory gray zones with minimal oversight.
For Coinbase specifically, the incident suggests:
- Contractor access wasn't properly restricted
- Unusual data access patterns weren't caught immediately
- Oversight of overseas contractors might have been lighter than oversight of US employees
Regulatory response to this incident could include:
- Stricter contractor vetting requirements for financial institutions
- Mandatory insider threat programs for crypto exchanges
- Rapid notification requirements when data breaches are discovered
- Penalties for slow disclosure of security incidents

How This Compares to Other Crypto Exchange Breaches
Coinbase isn't alone in dealing with insider threats. The cryptocurrency industry has seen multiple incidents:
Kraken (2023) - An employee allegedly moved customer data during onboarding but claims it was an error. Kraken investigated and found no actual customer harm.
Binance (Ongoing) - The platform has faced multiple security challenges and regulatory scrutiny around customer data handling.
FTX (2022) - Not technically a data breach, but executive insiders committed massive fraud, stealing customer funds. The insider threat here was the entire executive team.
What these incidents share:
- Employees and contractors with access to sensitive systems
- Sometimes inadequate monitoring or oversight
- Damage that extends beyond the immediate incident to customer trust
- Regulatory consequences and increased scrutiny
Compared to these incidents, the Coinbase contractor breach is relatively minor: 30 customers affected, no funds lost, and the company responded transparently. But it's part of a pattern showing that cryptocurrency exchanges struggle with insider threat management.

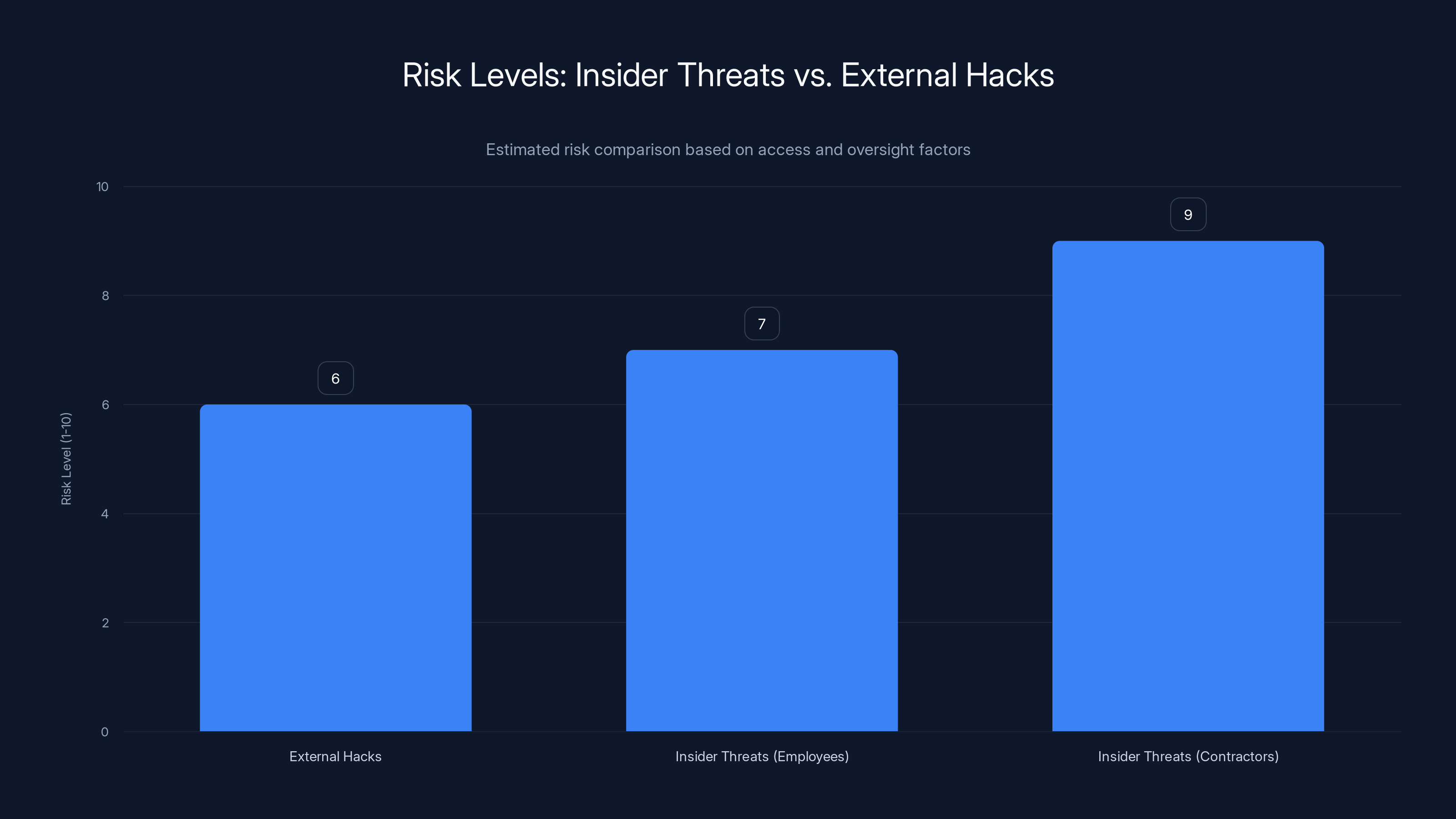
Contractors pose the highest risk due to less oversight and potential for longer access than necessary. Estimated data highlights the increased risk contractors bring compared to employees and external hacks.
The Role of Overseas Support Operations
Both the contractor breach and the May bribery incident highlight a vulnerability in crypto exchange operations: overseas support staff.
Why do exchanges use overseas support?
- Cost savings - Supporting customers across global timezones requires 24/7 operations. It's cheaper to hire support staff in countries with lower labor costs
- Timezone coverage - A support team in the Philippines can cover Asia-Pacific customers while US teams handle Americas customers
- Scaling flexibility - Contractors from overseas are often cheaper and easier to scale up or down
What's the security risk?
- Weaker vetting - Background checks are harder to conduct thoroughly in some countries
- Weaker enforcement - If an overseas contractor violates agreements, enforcement is difficult
- Language barriers - Security training and expectations can be harder to communicate
- Regulatory differences - Different countries have different laws about data protection and employee monitoring
- Corruption/bribery vulnerability - In some regions, government officials or criminals can pressure or bribe people more easily
The May Coinbase incident showed exactly this risk. Cybercriminals actively recruited overseas support agents because they knew those agents were more vulnerable to bribery.
Other exchanges have had similar issues. The pattern is clear: if you operate a global support function with cheaper overseas labor, you're introducing insider threat risks.
The solution isn't to eliminate overseas support (that would make the service too expensive). The solution is:
- Strict access controls that limit what overseas staff can see
- Aggressive monitoring of overseas access to customer data
- Regular audits of overseas operations
- Elevated vetting for overseas staff with sensitive access
- Clear communication of consequences for breaking rules

Protecting Yourself on Cryptocurrency Exchanges
If you use Coinbase or any cryptocurrency exchange, what can you do to protect yourself given these insider threats?
First, understand the risk: Using any centralized exchange means trusting that platform with your personal information and, temporarily, your cryptocurrency. No matter how good their security is, there's always some risk of insider threats, hacks, or collapse.
Second, minimize what you expose: Don't keep more cryptocurrency on an exchange than you're actively trading or planning to use. Move long-term holdings to a self-custody wallet where only you have the keys.
For self-custody:
- Hardware wallets like Ledger or Trezor store keys offline
- They require multiple confirmations to send cryptocurrency
- They're much harder for insiders to compromise because the insider doesn't have network access
- You can't lose funds to hacks if you're the only person with access
Third, enable all security features: Every exchange offers security tools. Use them:
- Two-factor authentication - Preferably with an authenticator app, not SMS
- Withdrawal address whitelist - Only allow cryptocurrency transfers to pre-approved addresses
- IP whitelist - Only allow logins from specific IP addresses
- Login notifications - Get alerted anytime someone logs into your account
Fourth, monitor your accounts actively: Check your account history regularly. Look for:
- Logins you don't recognize
- Withdrawals you didn't authorize
- Changes to security settings
- New addresses added to your whitelist
Fifth, separate your exchange account from your identity: Don't reuse passwords. Don't use the same email address you use for banking or other critical accounts. If the exchange is breached, you don't want attackers to have the keys to your entire digital life.
Sixth, protect your information offline: Even if you weren't affected by this Coinbase incident, your information might be out there:
- Check haveibeenpwned.com to see if your email has been in known breaches
- Monitor your credit reports at annualcreditreport.com (free, official source)
- Consider a credit freeze if you're concerned about identity theft

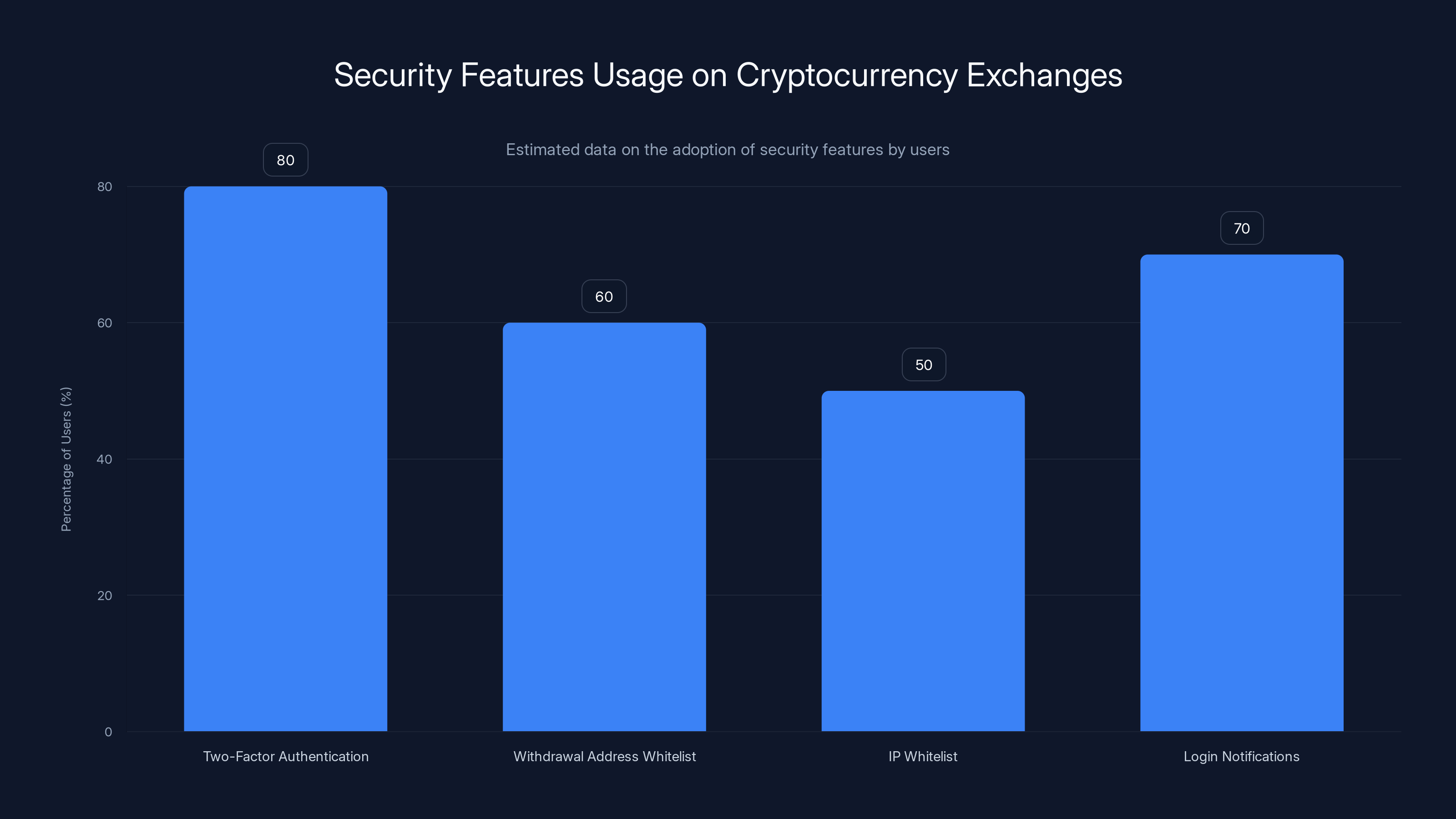
Estimated data suggests that two-factor authentication is the most commonly used security feature among cryptocurrency exchange users, while IP whitelisting is the least adopted.
Automated Security Monitoring for Your Digital Assets
If you're managing cryptocurrency or digital assets across multiple platforms, manual monitoring becomes impractical. This is where automated security tools become valuable.
Platforms that aggregate account monitoring can:
- Track multiple exchanges - Monitor all your accounts from one dashboard
- Alert on suspicious activity - Notify you instantly if unusual transactions or logins occur
- Aggregate holdings - Show total cryptocurrency across all platforms
- Monitor prices - Alert you to price movements
- Track portfolio performance - See gains and losses in real-time
For teams managing cryptocurrency operations or for individuals with substantial holdings across multiple platforms, this kind of aggregation tool is worth considering. The automation handles the tedious daily checking, leaving you to focus on strategy.
Tools in this space handle document generation, reporting, and analytics - essentially turning raw transaction data into insights you can actually use. Think of it like having a dedicated analyst watching your accounts 24/7 and flagging anything unusual.

Regulatory and Legal Implications
The Coinbase contractor breach raises multiple regulatory questions:
Data Protection Compliance: Under GDPR (Europe), CCPA (California), and similar laws, companies must notify individuals about data breaches without undue delay. Coinbase appears to have done this, but the timeline remains somewhat unclear.
Financial Services Regulation: Cryptocurrency exchanges are increasingly regulated as financial institutions. This means they need to maintain customer data security standards equivalent to banks. Insider threat incidents trigger regulatory investigations.
Incident Reporting Requirements: Securities regulators, financial regulators, and state attorneys general all have requirements for breach notification. Failing to report breaches properly can result in fines exceeding the value of the data exposed.
Restitution and Compensation: Companies are often required to offer free monitoring or credit protection to affected individuals. This is standard practice but can be expensive at scale.
For the 30 affected Coinbase customers, potential legal avenues include:
- Class action lawsuits if they can prove financial harm
- Regulatory complaints to the SEC, CFTC, or state authorities
- Claims against identity theft insurance (though coverage and limits vary)
For Coinbase as a company, potential consequences include:
- Regulatory fines from federal and state agencies
- Enhanced oversight and requirements for improved security programs
- Mandatory public disclosure of security incidents
- Reputational damage affecting user acquisition and retention
- Class action settlements if customers can prove damages
The cryptocurrency industry is increasingly subject to financial services regulations worldwide. Insider threat incidents are viewed seriously by regulators because they directly undermine customer trust in the financial system.

Future Security Improvements for Exchanges
How can Coinbase and similar platforms prevent future insider threats?
Zero Trust Architecture: Rather than assuming employees are trustworthy, implement systems where every access request is verified regardless of who's asking. This means:
- Multi-factor authentication for all data access
- Continuous verification of user identity
- Access to sensitive data requires approval from multiple people
- All access is logged and monitored
Advanced Anomaly Detection: Machine learning systems that understand normal behavior and flag anything unusual:
- Unusual data access patterns
- Access at unusual times
- Access from unusual locations
- Combinations of activities that seem suspicious
Compartmentalized Access: Break up data so no single person can access everything:
- A support agent might see customer name and transaction history but not KYC documents
- An engineer might have access to technical systems but not customer data
- A compliance person might see aggregate data but not individual customer information
Hardware-based Security Keys: Rather than relying on passwords or even authenticator apps, require physical security keys for sensitive access. These can't be phished or compromised remotely.
Blockchain-based Audit Trails: Store access logs on a blockchain so they can't be modified or deleted. Every access to customer data creates an immutable record.
Contractor Restrictions: Limit contractor access to essential functions only:
- Shorter permission periods that require re-approval
- More frequent background checks
- Restrictions on what contractors can see
- Separate systems for contractors that don't have access to full customer data
Employee Training: The human element remains critical. Regular security awareness training focused on insider threats, recognizing social engineering, and reporting suspicious behavior.
The Cryptocurrency Industry's Broader Security Challenges
The Coinbase incidents are just the most visible examples of a broader industry challenge. Cryptocurrency exchanges face unique security pressures:
High-value targets: Exchanges hold billions in customer cryptocurrency. This makes them attractive targets for hackers, criminals, and even nation-states.
Immutable transactions: Unlike traditional banking where fraudulent transfers can be reversed, cryptocurrency transactions are permanent. This makes every security incident potentially catastrophic for customers.
Global operations: To serve customers worldwide, exchanges operate across multiple jurisdictions with different regulatory requirements and security standards.
Rapid growth: The cryptocurrency industry is growing faster than security practices can mature. Many exchanges are relatively young companies that scaled quickly without time to implement robust security practices.
Technical complexity: Cryptocurrency systems are inherently more complex than traditional financial systems. More complexity means more potential vulnerabilities.
Recruiting security talent: The best security professionals often prefer working at established tech companies or financial institutions with higher pay and better benefits than crypto startups.
These factors combine to create an environment where insider threats are a persistent risk. The Coinbase incidents are likely not isolated. Other exchanges probably have similar vulnerabilities; they just haven't been disclosed yet.

Long-term Implications and Industry Evolution
What will this incident mean for the cryptocurrency industry long-term?
Increased Regulatory Scrutiny: Regulators worldwide will likely require exchanges to implement stronger insider threat programs. Expect:
- Mandatory background checks
- Regular security audits
- Specific technical controls
- Incident reporting timelines
- Minimum insurance or financial requirements
Industry Consolidation: Smaller exchanges that can't afford robust security programs will fail or be acquired by larger platforms. This reduces the number of places where user funds sit.
Shift to Decentralized Exchanges: As regulatory and security burdens on centralized exchanges increase, decentralized exchanges that don't hold customer funds might gain market share. However, they come with their own security risks (smart contract vulnerabilities, for example).
Enhanced Custody Solutions: More sophisticated custody solutions will emerge for institutional investors and high-net-worth individuals who want the security of crypto with professional safeguards:
- Institutional-grade security practices
- Insurance against theft
- Multi-signature storage
- Separate legal entities holding customer assets
Evolution of Security Standards: The industry will develop and adopt security standards similar to those in traditional finance:
- Regular penetration testing
- Third-party security audits
- Continuous monitoring and incident response plans
- Employee and contractor vetting standards

What Coinbase Has Done Right (And What It Hasn't)
Let's be fair: Coinbase's response to the contractor breach was reasonably transparent. The company:
- Disclosed the incident publicly rather than trying to hide it
- Provided clear details about what happened and how many people were affected
- Took responsibility rather than blaming the contractor entirely
- Offered remediation to affected customers
- Reported to regulators as required
But there are gaps:
- Timing of disclosure - How long between discovering the breach and announcing it? The public still doesn't know
- Contractor vetting - What processes allowed this person to have this much access?
- Access controls - Why could one person pull 30 customer records without triggering alerts?
- Frequency - Is this the first incident, or are there others not yet disclosed?
- Root cause analysis - What specific security controls failed?
The May 2025 bribery incident is particularly concerning because it suggests Coinbase's overseas support operations had serious security gaps. You don't accidentally bribe support agents; criminals specifically targeted them because they knew those agents were vulnerable.
For a company handling billions in customer funds, these incidents suggest security practices aren't yet industry-leading. They're adequate, but not exceptional.
Lessons for Other Platforms and Users
What should other cryptocurrency platforms learn from Coinbase's experience?
For Exchanges:
- Treat insider threats with the same seriousness as external hacks
- Implement strict access controls and monitoring
- Focus on overseas operations where oversight is hardest
- Communicate security practices transparently with users
- Invest in security as heavily as you invest in features
For Users:
- Don't trust any single platform with your entire portfolio
- Use hardware wallets for long-term holdings
- Treat exchange accounts like you treat online banking - actively monitor them
- Understand that centralized exchanges always carry counterparty risk
- Be skeptical of platforms that downplay security incidents
For Regulators:
- Establish clear insider threat prevention requirements
- Require regular security audits and penetration testing
- Impose penalties for delayed breach disclosure
- Mandate insurance or financial reserves to cover potential losses
- Require platforms to demonstrate they're not holding customer funds in a way that enables fraud

FAQ
What exactly is an insider threat?
An insider threat is when someone with legitimate access to a system (an employee, contractor, or partner) abuses that access to cause harm. In the Coinbase case, the contractor had legitimate access to customer support systems but used it to view customer data without authorization. Insider threats are particularly dangerous because the person already has access, so they don't need to find vulnerabilities or break into systems.
Why do cryptocurrency exchanges use contractors with access to customer data?
Cryptocurrency exchanges need 24/7 global support to help customers across all timezones. Hiring full-time employees for all these roles would be extremely expensive. Contractors from countries with lower labor costs make the economics work. The trade-off is accepting higher security risk because contractors are often less vetted, less committed to the company, and sometimes more vulnerable to bribery or coercion than employees. This is a cost-benefit decision that every exchange makes.
What should I do if I was affected by the Coinbase breach?
If Coinbase notified you that your data was exposed, activate the free identity theft protection service they offered, place a credit freeze with Equifax, Experian, and Trans Union immediately, monitor your accounts for suspicious activity, and consider moving your cryptocurrency holdings to a hardware wallet that you control. The most important step is preventing someone from using your information to open accounts in your name. A credit freeze makes this dramatically harder.
How is this different from other cryptocurrency breaches?
The Coinbase contractor breach is relatively small (30 customers) and didn't result in theft of cryptocurrency. However, it's part of a pattern where cryptocurrency exchanges have multiple insider threat incidents within a short period. The May bribery incident was much more serious because cybercriminals actively targeted overseas support staff. Together, these incidents suggest Coinbase's security practices around insider threats have gaps. Other exchanges probably have similar vulnerabilities.
Can I recover cryptocurrency if my account is compromised?
Generally no. If an attacker takes over your account and transfers your cryptocurrency, that transaction is permanent and irreversible. You could potentially:
- Open a case with the exchange if the attacker is still identifiable
- Pursue legal action if you can prove negligence on the exchange's part
- Try to recover funds if the attacker's wallet is frozen (if regulators cooperate)
But in most cases, stolen cryptocurrency is simply gone. This is why security practices like hardware wallets and withdrawal address whitelists are so critical. You need to prevent access in the first place because recovery is rarely possible.
Should I move my cryptocurrency off Coinbase after this breach?
Not necessarily because of this specific breach (which affected only 30 people), but the broader pattern of insider threats is worth considering. If you're holding cryptocurrency on any centralized exchange, you're assuming some risk:
- The exchange itself could be hacked
- Employees or contractors could steal customer data or funds
- The exchange could collapse or be seized by regulators
- The exchange could face a technical failure
A prudent approach is keeping only what you actively trade on the exchange and moving everything else to a hardware wallet that only you control. This limits your exposure to exchange risk.
How does a hardware wallet protect against insider threats?
A hardware wallet like Ledger or Trezor stores your private keys offline on a physical device. To transfer cryptocurrency, you must physically authorize the transaction on the device. An insider at a cryptocurrency exchange can't steal your funds because they don't have access to your private keys. They could potentially steal your personal information (which is still serious), but they can't take your cryptocurrency. This is why hardware wallets are considered the gold standard for long-term cryptocurrency storage.
What laws apply to data breaches in cryptocurrency?
It depends on the jurisdiction. In the US, each state has different data breach notification laws. California's CCPA is particularly strict. In Europe, the GDPR applies and requires notification within 72 hours in most cases. Internationally, data protection laws are becoming stricter. Cryptocurrency exchanges that operate globally must comply with the strictest standards in the jurisdictions where they have customers. Coinbase, for example, must comply with GDPR in Europe, CCPA in California, and various other regulations in other jurisdictions.
How can exchanges prevent future insider threats?
The most effective approaches involve:
- Strict access controls - Each person gets only the minimum access needed
- Continuous monitoring - Systems watch for unusual access patterns
- Audit trails - Every access to sensitive data is logged
- Separation of duties - No single person can approve and execute sensitive actions
- Regular background checks - Especially for contractors
- Employee training - Help staff recognize social engineering and insider threat attempts
- Hardware security keys - Require physical verification for sensitive access
- Restricted contractor access - Limit what contractors can see and how long they can keep access
No single approach solves the problem. It requires multiple layers working together.

Conclusion
The Coinbase insider breach affecting roughly 30 customers is significant not because of its size, but because it reveals structural vulnerabilities in how cryptocurrency exchanges manage access to sensitive data. Combined with the May 2025 bribery incident affecting a much larger group of customers, these incidents suggest that even one of the most professional exchanges in the industry has gaps in insider threat prevention.
Here's what matters: cryptocurrency exchanges hold customer funds and personal information. That makes them attractive targets. Employees and contractors need access to customer data to provide support and run the business. But that same access becomes a vulnerability if someone decides to abuse it.
Coinbase's response has been reasonably transparent. The company notified customers, offered remediation, and reported the incident to regulators. But the real question is whether the company's security practices have fundamentally changed to prevent future incidents or whether this is just damage control.
For users, the lesson is clear: don't trust any centralized platform with more than you're willing to lose. Use hardware wallets for long-term holdings, monitor your accounts actively, and understand that using cryptocurrency means accepting certain risks. No platform is perfectly secure. The key is managing your risk intelligently.
The cryptocurrency industry is maturing. Regulations are tightening. Security practices are improving. But insider threats will remain a persistent challenge as long as humans have access to valuable systems. The best defense is defense in depth: multiple layers of security, active monitoring, user vigilance, and maintaining assets you control yourself.
Coinbase will likely emerge from these incidents with stronger insider threat controls. The broader industry will adopt similar practices. Regulatory scrutiny will increase. Over time, cryptocurrency platforms will look more like traditional financial institutions in terms of security practices. That's probably healthy for the industry and good for users.
But in the near term, treat every cryptocurrency exchange with appropriate skepticism. The incidents at Coinbase could happen anywhere. Your responsibility is protecting your own information and assets using every tool available.

Key Takeaways
- Coinbase confirmed a contractor improperly accessed customer data on ~30 users, exposing personal and financial information
- Insider threats are more dangerous than external hacks because insiders already have legitimate system access
- A May 2025 incident showed cybercriminals actively bribed overseas support agents to steal customer data worth $400 million
- Effective insider threat prevention requires multiple layers: access controls, audit trails, anomaly detection, and strict contractor vetting
- Users should keep only active trading funds on exchanges and store long-term cryptocurrency holdings in self-custody hardware wallets
Related Articles
- Canada Computers Data Breach 2025: Timeline, Impact, Protection [2025]
- TriZetto Provider Solutions Breach: 700K+ Affected [2025]
- Bumble & Match Cyberattack: What Happened & How to Protect Your Data [2025]
- Moltbook Security Disaster: How AI Agents Exposed 1.5M Credentials [2025]
- Malwarebytes and ChatGPT: The AI Scam Detection Game-Changer [2025]
- Notepad++ Server Hijacking: Inside the Six-Month Supply Chain Attack [2025]
![Coinbase Insider Breach Exposed 30 Customers' Data [2025]](https://tryrunable.com/blog/coinbase-insider-breach-exposed-30-customers-data-2025/image-1-1770215903444.jpg)



