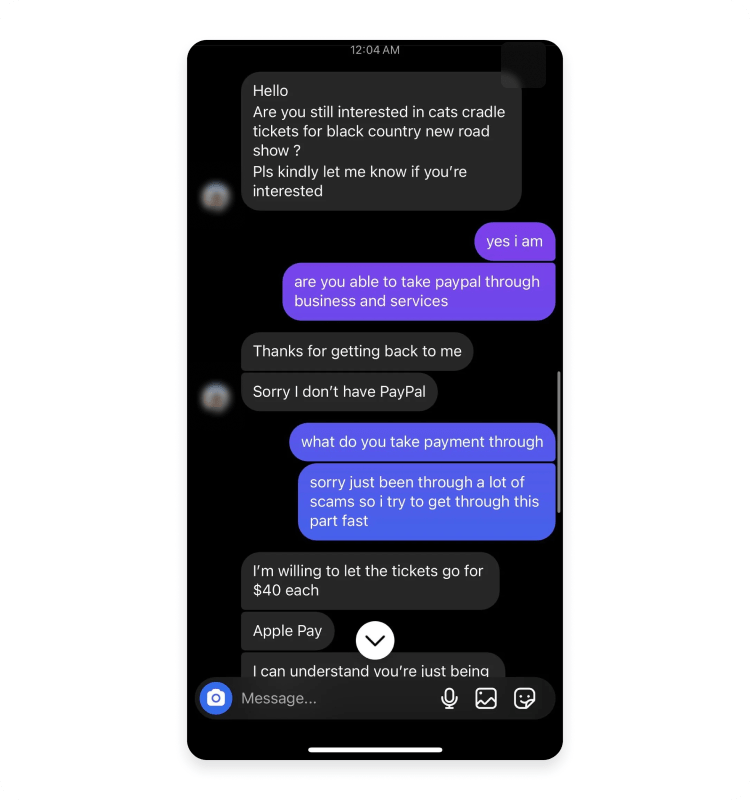
Apple Pay Unusual Activity Scam: How to Spot Fake Messages [2025]
Your phone buzzes. A notification from Apple Pay appears on your screen: "Unusual Activity Detected. Verify your identity immediately." Your heart rate spikes. You've been careful with your account. What happened?
You're probably looking at a scam.
This isn't paranoia. It's the reality right now. Millions of iPhone users are receiving these fake alerts, and they're incredibly convincing. They look exactly like legitimate Apple notifications. The formatting matches. The urgency feels real. And that's precisely what makes them dangerous.
Here's what's happening: Scammers have weaponized our trust in Apple's security systems. They've created fake notification designs that mimic the real thing so closely that most people can't tell the difference without looking very carefully. When you tap the link in these messages, you're not verifying your account. You're handing over your Apple ID credentials, payment information, and two-factor authentication codes directly to criminals.
The sophistication of these scams has evolved dramatically over the past 18 months. Early phishing attempts were obvious. Misspellings. Weird formatting. Sketchy links. You could spot them a mile away. But these new Apple Pay scams? They're designed by people who understand exactly how Apple communicates with users. The language is precise. The visual design is pixel-perfect. The timing often seems deliberate, hitting you right after you've made a large purchase or added a new card.
This article walks you through everything you need to know about these scams. How they work. Why they're so effective. And most importantly, how to protect yourself before you become another statistic.
TL; DR
- Apple Pay scams use fake "unusual activity" alerts that look nearly identical to real Apple notifications, tricking millions into revealing credentials
- Real Apple never asks for passwords in notifications – legitimate alerts direct you to Settings or direct action without requiring verification links
- Check the sender carefully – real Apple notifications come from official channels, never from email links or random SMS messages
- Enable two-factor authentication immediately if you've already clicked a suspicious link; change your Apple ID password from a different device
- Report suspicious messages to Apple (forward to reportphishing@apple.com) and your carrier to help protect others from the same scam

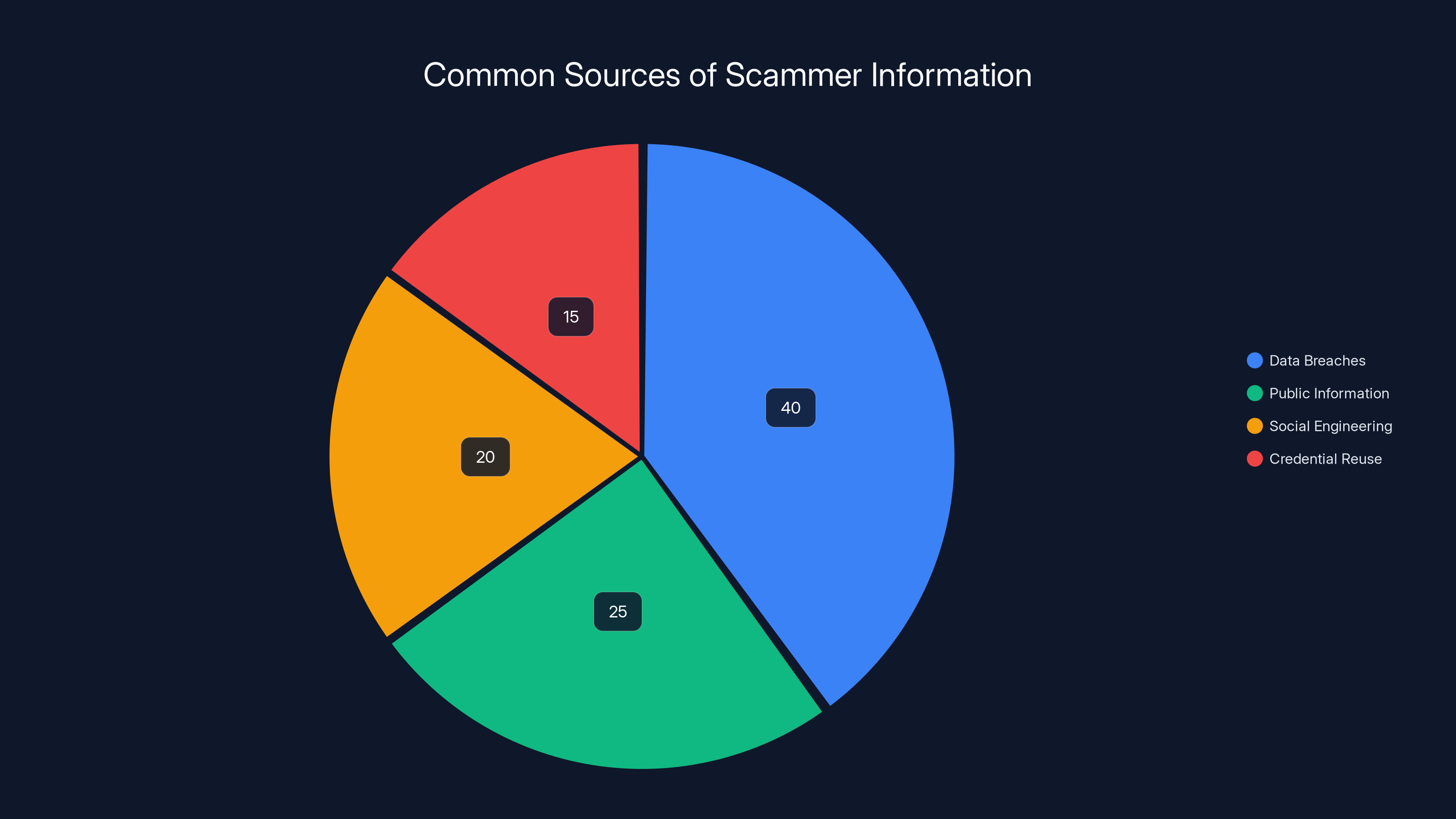
Data breaches are estimated to be the largest source of information for scammers, accounting for 40% of cases, followed by public information aggregation at 25%. (Estimated data)
Understanding the Apple Pay Scam Ecosystem
Scammers didn't invent fake Apple notifications overnight. This threat evolved gradually, building on years of phishing tactics that refined themselves through trial and error.
The earliest versions of these scams were crude. They'd copy Apple's logo, throw in some generic security language, and hope people panicked enough to click without thinking. The click-through rate was probably terrible, but when you're sending millions of messages, even a 0.1% success rate generates serious money.
But scammers learned from their failures. They studied what actually works. They analyzed which messages got responses. They discovered that urgency matters more than accuracy. Fear sells better than logic. And they realized that Apple Pay, specifically, creates a unique psychological pressure because it touches your money directly.
So they evolved.
The current generation of scams targets the intersection of two psychological vulnerabilities: the trust we place in Apple's security systems, and the panic that emerges when we're told something unusual happened with our accounts.
What makes these scams work is deceptively simple. Most of us don't read notifications carefully. We skim them. We see the Apple logo, we see the word "security," we see urgent language about account protection, and we act. The scammers know this. They design their fake alerts to exploit this skimming behavior.
The distribution networks have also become more sophisticated. These messages arrive through multiple channels simultaneously: SMS text messages, iMessage, email, and even push notifications that appear to come from Apple's own systems. Some arrive on devices that show the message originating from Apple's notification server (a trick involving spoofed headers and carrier network vulnerabilities). Others come through more traditional phishing routes but with such perfect mimicry that the delivery mechanism doesn't matter.
What's particularly clever is how scammers handle the timing. They often send these alerts during times when users are most likely to be shopping: late evening, weekends, during major retail events. They also sometimes target users right after legitimate Apple notifications, banking on notification fatigue and the assumption that if you just got a real Apple alert two minutes ago, the next one might be real too.

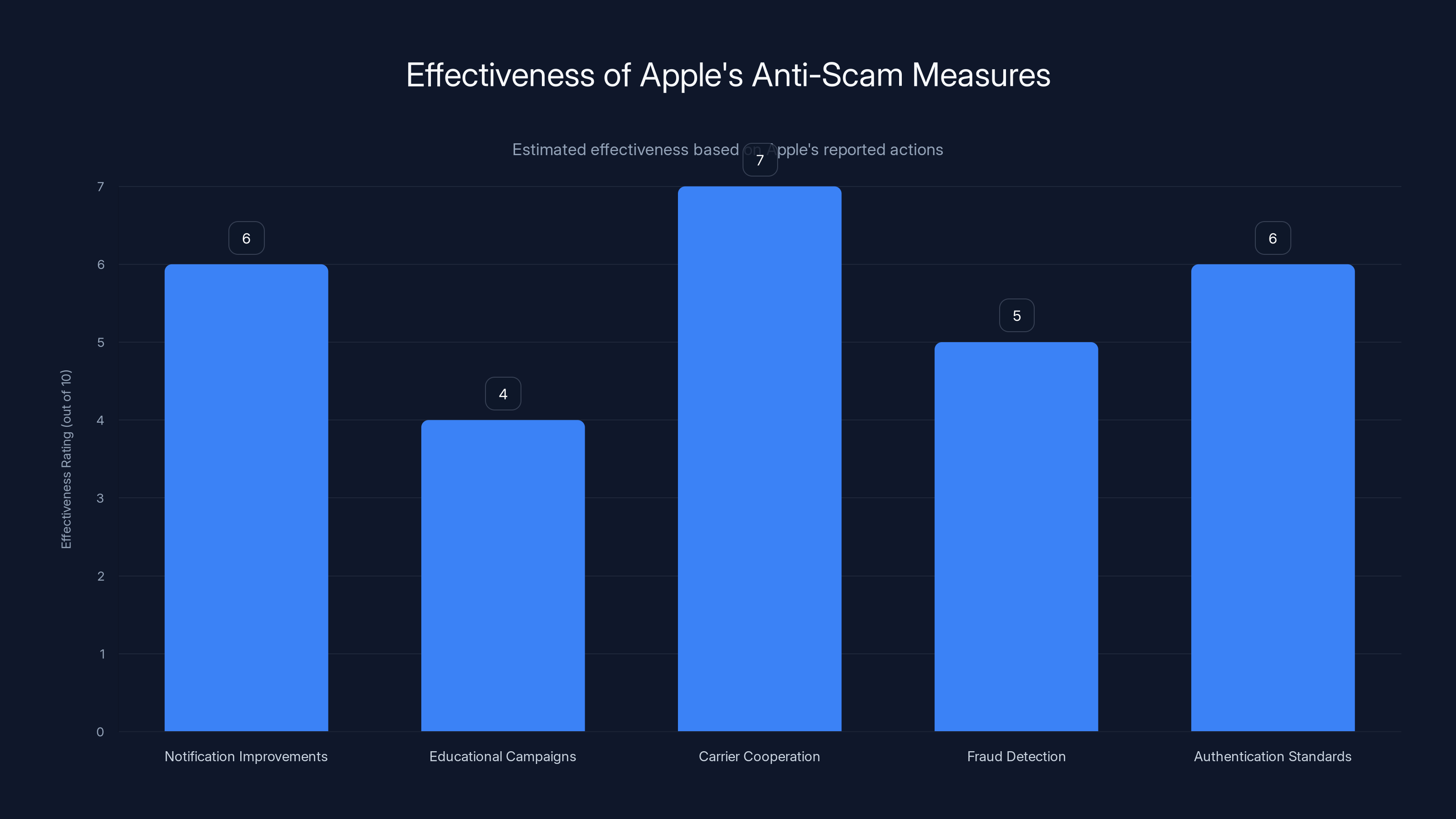
Apple's efforts to combat scams show varying effectiveness, with carrier cooperation rated highest. Estimated data.
How to Identify Fake "Unusual Activity" Notifications
Learning to spot these scams requires understanding how legitimate Apple security alerts actually look and behave.
First, let's talk about what a real Apple notification does and doesn't do. Apple's security team has been clear about this for years: Apple will never ask you to verify your identity, enter your password, or confirm payment information through a notification, email, or text message. If Apple detects unusual activity, they have direct access to your account. They don't need you to provide information they already have.
Real Apple security alerts do one of two things: they either describe what happened ("Your Apple ID was just used to sign in from a new device in New York") without asking you to do anything, or they direct you to open the Settings app on your device and handle it there. That's it. No links. No urgent verification requests. Just information and native app navigation.
Fake alerts do the opposite. They create urgency, they include links, and they request information.
Let's break down the specific red flags:
The Language Red Flags
Real Apple notifications use precise, specific language. Fake ones use vague, urgent language. Compare these:
Fake: "Unusual activity detected on your Apple Pay account. Click here immediately to verify your identity."
Real: "Your Apple ID password was just changed on an iPhone at 3:42 PM. If this wasn't you, you can reset it now."
Notice the difference? The fake one is vague and demanding. The real one is specific and informative. Scammers write in broad strokes because they don't have real data about your account. They can't say "Your Apple Pay card ending in 4729 was declined from a new location" because they don't know those details.
Listen for these phrases in fake alerts:
- "Click here immediately"
- "Verify your identity right now"
- "Confirm your information within 24 hours"
- "Your account will be locked"
- "Update your payment method now"
- "Unusual activity has been detected"
- "Click the link below to secure your account"
Real Apple alerts use phrases like:
- "Your Apple ID password was changed"
- "A new device signed in to your account"
- "Your payment method was declined"
- "You can change this in Settings"
The Visual Red Flags
Scammers have gotten scarily good at copying Apple's design language. But there are still tells.
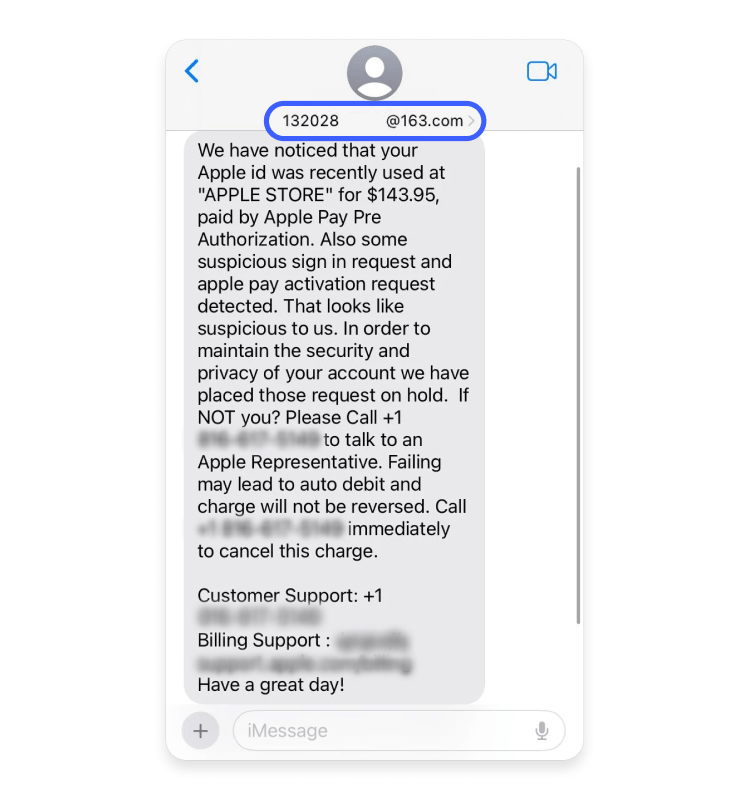
Look at the sender information. In iMessage or SMS, real Apple notifications come from specific numbers or appear in the Notifications section of Settings. Scammers often use numbers that look like they could be Apple's (1-888-275-3775 is actually Apple Support, so scammers sometimes use variations like 1-888-275-3776). They might also use email addresses like "apple-security@appleid.com" or "security@apple-id.net" (note the hyphens and variations in domain structure).
Real Apple notifications from the company use precise domain names: apple.com, icloud.com, and a few others. If it says anything else, it's fake.
Check the link destination. A real Apple link will start with "https://" followed by an official Apple domain. Fake ones often use:
- Bit.ly or Tiny URL shortened links (legitimate Apple almost never uses these)
- Domains that look similar but are slightly different (appleid-verification.com instead of appleid.apple.com)
- Links hidden behind button text that doesn't match the actual URL
On most phones, you can see the real URL by pressing and holding the link. Do this. Actually see where it goes. If it's not an official Apple domain, don't tap it.
The Behavioral Red Flags
How does the notification make you feel? That's actually important information.
Scammers engineer their messages to trigger specific emotional responses: panic, urgency, confusion. Real security alerts are usually calmer. They inform more than they alarm. They give you options rather than demanding immediate action.
Fake alerts often use:
- Multiple exclamation marks ("Verify immediately!!!")
- ALL CAPS for emphasis
- Countdown timers ("You have 24 hours to verify")
- Threats ("Your account will be locked")
- Flattery ("Protect your valued account")
Real Apple notifications are typically:
- Calm and factual
- Specific about what happened
- Clear about what you should do
- Never threatening
- Often include timestamps or device information
If a notification makes your stomach drop and you feel like you have to act right now, pause. That's a designed response. Take 30 seconds to verify it before doing anything.
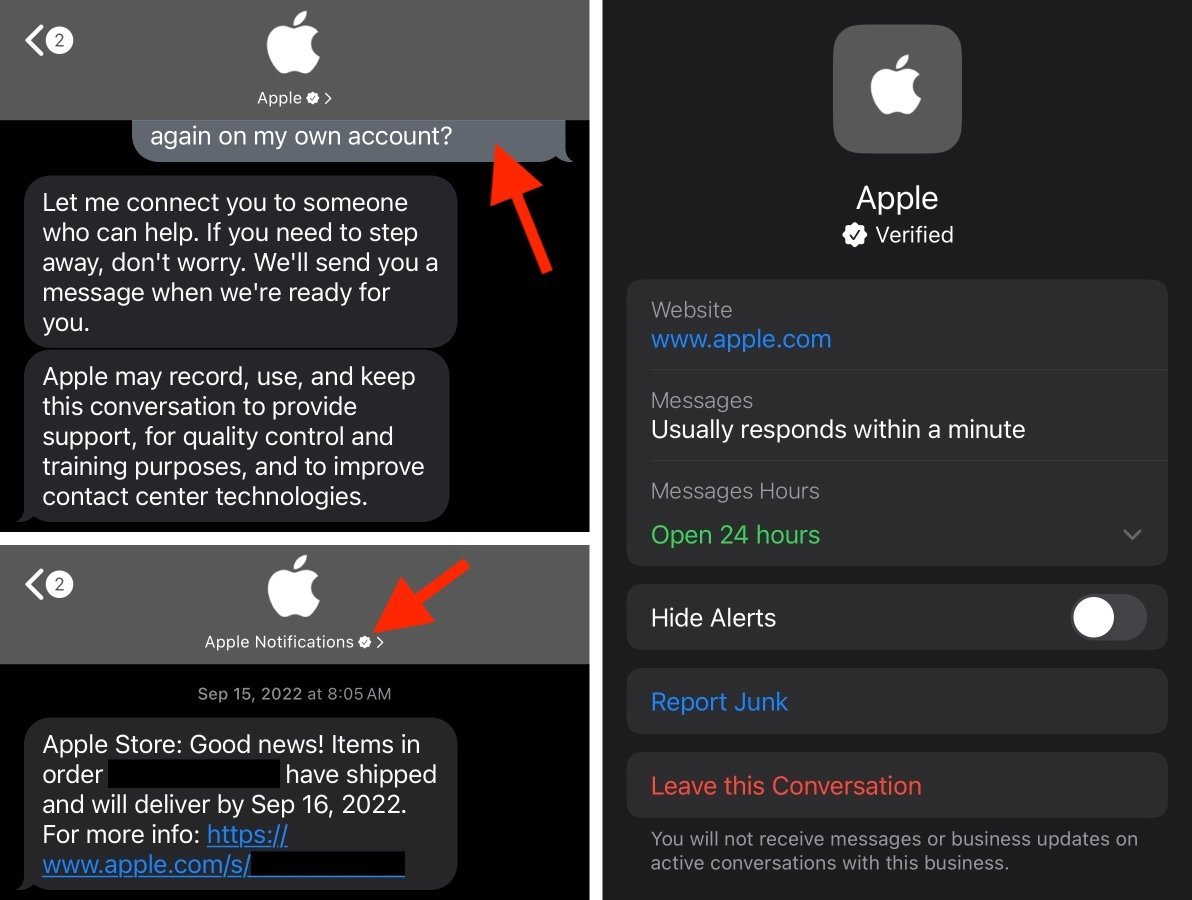
The Psychology Behind Why These Scams Work
Understanding why you might fall for one of these scams isn't a character flaw. It's psychology. Scammers exploit specific vulnerabilities that exist in all of us.
Authority and Trust
Apple has spent decades building trust. Their products "just work." Their security is generally solid. When you see an Apple notification, there's an immediate assumption that it's legitimate. You don't question it the way you might question a notification from an unfamiliar company.
Scammers weaponize this. By impersonating Apple, they inherit decades of trust instantly. You don't perform the same skepticism checks you would with other sources because the source feels official.
The Urgency Trap
Our brains are wired to respond to urgency. In actual emergencies, quick thinking saves lives. But this same mechanism is exploitable. When a notification says your account will be locked in 24 hours, your rational brain shuts down a bit. You move from thinking mode to action mode.
Scammers know this. They deliberately create false time pressure. "Verify immediately." "Act now." "Within 24 hours." None of this is based on real deadlines. But it works because it bypasses your critical thinking.
The solution? When you feel urgency, that's your signal to slow down, not speed up. Real security issues give you time to verify them properly.
Normalization of Notifications
We receive hundreds of notifications daily. Most of us develop notification fatigue. We see a notification and our brain processes it faster than our conscious mind can properly evaluate it. We've trained ourselves to respond quickly.
Scammers exploit this by making fake notifications look exactly like the legitimate ones you ignore every day. Your skimming brain treats it as routine. By the time you realize what happened, you've already clicked the link.
The Specificity Illusion
Even vague scam messages feel specific because they're about your account. The message says "Your Apple Pay account has unusual activity." Your brain fills in the blanks. "Oh, it must be that transaction I made earlier. Or maybe I forgot I used it somewhere." The scammer didn't have to be specific. Your own brain provided specificity.
Loss Aversion
The fear of losing access to your account, or losing money, is more powerful than the desire to gain something. Psychologists call this loss aversion. Scammers exploit it by framing their messages around what you might lose: "Account will be locked," "Payment failed," "Unusual activity detected."
The prospect of losing access to Apple Pay, which is connected to your money and your identity, triggers a protective response. You want to fix it immediately. This emotional state is exactly where scammers want you.

Scammers often exploit trust (30%) and urgency (25%) to manipulate victims. Notification fatigue (25%) and specificity illusion (20%) are also common tactics. Estimated data.
Real vs. Fake: A Detailed Comparison
Let's walk through some actual examples side by side. I'm building these based on common variations that millions have reported, showing exactly how to distinguish them.
Example 1: The Classic Verification Scam
FAKE MESSAGE: "Apple Pay Alert: Unusual activity detected on your account. To protect your information, verify your identity by clicking the link below within 24 hours. Verify Now → [link to fake site]"
WHY IT'S FAKE:
- Demands verification through a link
- Creates artificial time pressure (24 hours)
- Uses generic "unusual activity" language
- The link goes to a fake domain designed to capture credentials
REAL EQUIVALENT: "Your Apple ID password was changed on an iPhone in New York at 3:42 PM today. If this wasn't you, go to Settings > [Your Name] > Password & Security to change it."
WHY IT'S REAL:
- Specific about what happened (password change)
- Specific about when and where (time, location, device type)
- Directs to Settings, not an external link
- No urgency language or threats
Example 2: The Payment Method Scam
FAKE MESSAGE: "Your Apple Pay payment method has expired. Update your information now to keep using Apple Pay: https://applepay-secure-verify.com/update"
WHY IT'S FAKE:
- The domain is obviously fake (not an Apple domain)
- Real Apple would handle this in Settings, not via a link
- No legitimate reason to use a third-party URL
- Doesn't mention which payment method or account
REAL EQUIVALENT: "Your payment method on file will expire soon. Update it in Settings > [Your Name] > Payment & Shipping."
WHY IT'S REAL:
- Directs to native Settings app
- No external links
- Clear about the issue (expiring payment method)
- Specific instruction path
Example 3: The Two-Factor Scam
FAKE MESSAGE: "We detected a sign-in attempt to your Apple ID from an unfamiliar location. Confirm it was you by entering your 2FA code below: [input field]"
WHY IT'S FAKE:
- Asks for 2FA code via message (Apple never does this)
- 2FA codes are only supposed to appear in specific contexts
- Real Apple never asks you to enter codes into unknown fields
- This is collecting codes that could be used to access your account
REAL EQUIVALENT: "A sign-in attempt to your Apple ID was just made from a Safari browser on a Mac in London at 9:23 PM. If this was you, no action is needed. If not, go to Settings > [Your Name] > Password & Security to review."
WHY IT'S REAL:
- Provides specific technical details (browser, OS, location, time)
- Doesn't request codes or credentials
- Offers optional action but doesn't demand it
- Directs to Settings for any account changes
Step-by-Step: What to Do If You Receive a Suspicious Message
You've just received a message that looks like it might be from Apple. It could be real or fake. Here's exactly what to do:
Step 1: Don't Click Anything Yet
This is the hardest step because everything in the message screams urgency. Force yourself to pause. Your account isn't going to be locked in the next 30 seconds. Take a breath.
Step 2: Examine the Sender Information
If it's a text message, look at the phone number it came from. Real Apple alerts come from specific numbers. If you're unsure, don't trust your memory. Look up Apple's official contact numbers on a different device or a printed statement. Compare carefully. Scammers often use numbers that are close but not quite right.
If it's an email, check the sender address carefully. Hover over it (don't click) to see the full email address. Real Apple emails come from @apple.com, @icloud.com, or a few other official domains. Anything else is fake.
If it's an iMessage, check whether it shows "From Apple Inc." or similar official designation. Scammers can sometimes spoof this, but legitimate Apple messages have official identifiers.
Step 3: Check for Links and Requests for Information
Scroll through the message. Does it ask you to:
- Click a link?
- Enter your password?
- Provide your Apple ID?
- Verify your payment information?
- Enter a two-factor authentication code?
- Confirm personal information?
If it asks any of these, it's almost certainly fake. Real Apple never asks for this information via notification.
Does it contain a clickable link? Press and hold it (don't tap) to see the real URL destination. If it's not from an official Apple domain, don't tap it.
Step 4: Verify Through Official Channels
This is how you actually confirm whether there's a real issue. Don't use any information from the suspicious message. Instead:
Open the Settings app on your iPhone manually (not by tapping anything in the message). Go to [Your Name] > [appropriate section: Password & Security, Payment & Shipping, etc.]. Check whether there's actually an issue.
Alternatively, go directly to iCloud.com, sign in (from your device's browser, not by tapping anything in the message), and check your account status.
Or call Apple directly using the number from your iPhone's settings or a trusted source. When you call, you can ask about the specific alert you received.
Step 5: If It's Fake, Report It
Forward the message to Apple at reportphishing@apple.com. Include the full message and any context (when you received it, which app it came through, etc.). This helps Apple track new scam variations.
Also report it to your carrier. Most carriers have a way to report spam/phishing SMS messages.
If it was in iMessage, you can right-click the message and select "Report Junk."
Step 6: If You Already Clicked It, Act Immediately
If you already tapped the link or entered information, don't panic. But act quickly.
First, change your Apple ID password. Go to Settings > [Your Name] > Password & Security > Change Password. Use a strong, unique password that you haven't used anywhere else.
Second, enable two-factor authentication if you haven't already. This prevents anyone from accessing your account even if they have your password.
Third, review your account activity. Go to Settings > [Your Name] > Password & Security > Review your recent account activity. Check for any unauthorized access attempts or changes to your account.
Fourth, check your payment methods. Go to Settings > [Your Name] > Payment & Shipping. Make sure no unauthorized cards have been added.
Fifth, consider contacting your bank or card issuer to let them know your information may have been compromised. They can flag accounts for suspicious activity.

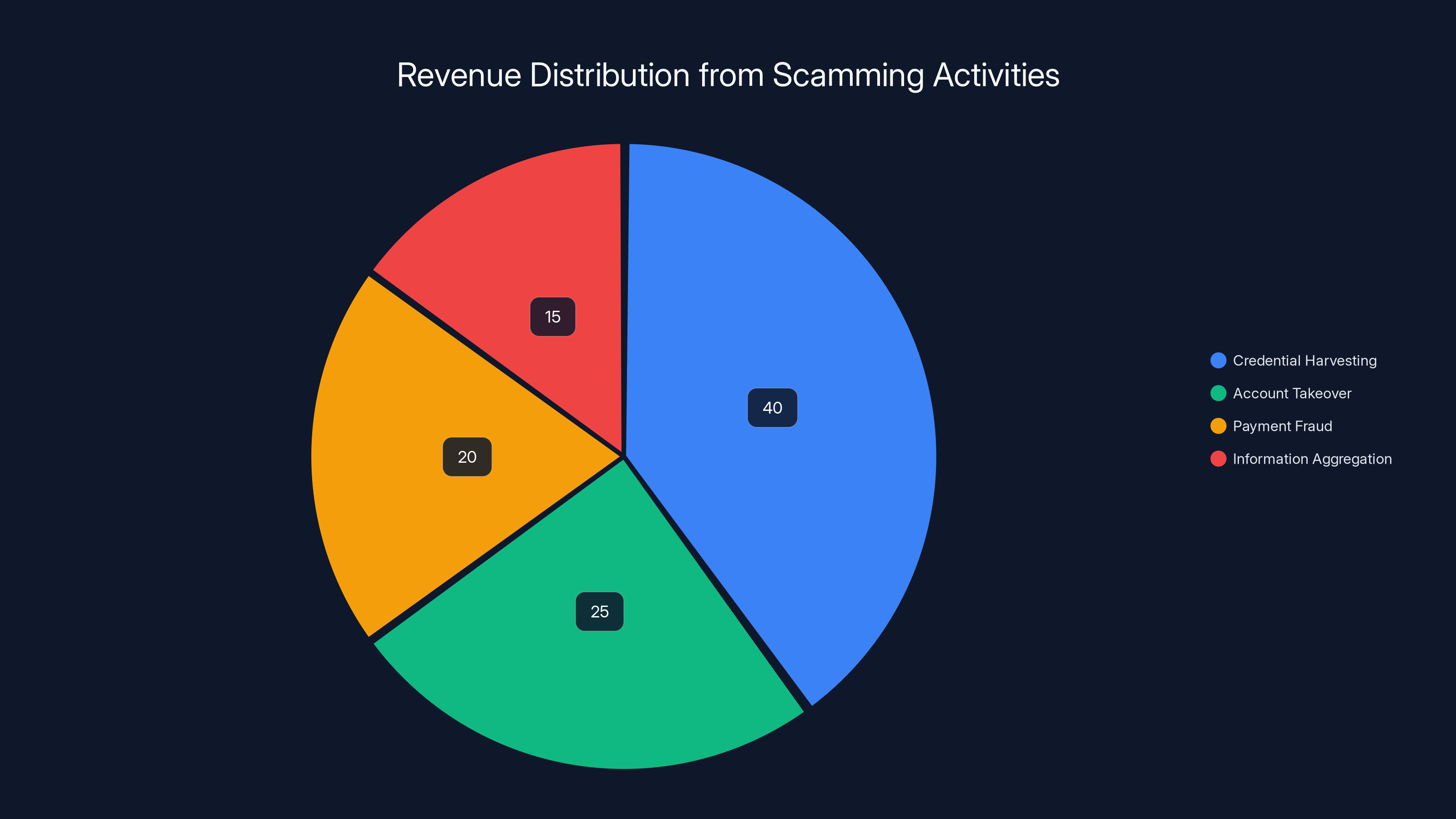
Estimated data shows that credential harvesting is the most lucrative scamming method, contributing to 40% of the revenue. Account takeover and payment fraud follow, with information aggregation being the least profitable.
How These Scammers Obtain Your Information
Understanding where scammers get your phone number or email address is actually important for protecting yourself going forward.
They don't always have your information beforehand. Many scammers use random number generators or purchased lists, sending the same message to millions of numbers or addresses. They know that a certain percentage will result in clicks, and they're fine with that math.
But sometimes they do have specific information about you, which is scarier. Here's how:
Data Breaches
Every few months, another major company gets hacked. Your personal information leaks: name, email, phone number, sometimes payment information or Apple ID. Scammers buy these lists from dark web marketplaces. They might know your real name, your phone number, and that you use Apple products. They use this to make their scams feel more personalized.
Public Information Aggregation
Your phone number and email are probably more public than you realize. They might be in old forum posts, mentioned in comments sections, included in a LinkedIn profile, or linked to other accounts you've forgotten about. Scammers use tools to scrape and aggregate this information, building profiles about people.
Social Engineering
Sometimes a scammer calls your bank pretending to be you, or they social engineer support staff at Apple by pretending to be a user with your details. They collect more information this way, using what they already know to seem legitimate.
Account Hijacking and Credential Reuse
If you've been a victim of a previous phishing attack and used the same password across multiple services, scammers might have access to multiple accounts including Apple. They can see your payment information and email address associated with your Apple account.
This is why using unique passwords for every important account matters so much.
The Targeting Strategy
Once scammers have a list of numbers and emails, they might segment it. People who've made recent purchases are more likely to have working Apple IDs and active payment methods, so they get hit with payment-related scams. People with older accounts get general verification scams.
They also test different messages and track which ones generate the highest click-through rates. They're running experiments, constantly refining their approach. A message that works 0.5% of the time gets used more broadly. A message that only works 0.1% of the time gets abandoned.
This is why scam messages seem to evolve. They're getting better at what they do because only the effective variations survive.
Protecting Your Apple ID: Advanced Settings and Features
Apple has built several security features that can help protect you, but you have to enable and use them correctly.
Two-Factor Authentication (2FA)
This is non-negotiable. If you don't have 2FA enabled on your Apple ID, enable it right now. Go to Settings > [Your Name] > Password & Security > Two-Factor Authentication.
How it works: When someone tries to sign into your Apple ID from a new device, they need your password AND a code that only you have access to (usually sent to your iPhone). A scammer who has your password still can't get in.
The catch: Make sure your trusted devices are actually trusted. Go to Password & Security and review which devices are listed. If you see a device you don't recognize, remove it immediately.
Recovery Contact and Key
Apple offers two additional recovery options beyond your phone number:
A recovery contact is another person you trust (usually a close friend or family member) who can help you regain access to your account if you get locked out. Apple doesn't have to give you any information; they'll ask your recovery contact to confirm your identity.
A recovery key is a unique code that can unlock your account if you lose access to your phone and security questions. Write this down, memorize it, or store it securely (not on your computer, not in cloud storage). If a scammer gets it, they can access your account more easily. So protect it accordingly.
Device Trusted Contacts
This is different from recovery contacts but serves a similar purpose. If you're trying to sign in on a new device and you're away from home, you can ask a trusted contact to approve the sign-in. This prevents someone with your password from accessing your account from an unknown location without your approval.
App-Specific Passwords
For any app that needs your Apple ID (older mail clients, some third-party apps), never give it your actual Apple ID password. Instead, generate an app-specific password. Go to Settings > [Your Name] > Password & Security > App-Specific Passwords.
These passwords only work for that specific app. If a scammer gets an app-specific password, they can only access that particular application, not your entire Apple ID.
Payment Method Verification
Go to Settings > [Your Name] > Payment & Shipping and review every payment method on file. You should recognize every single one. If you see a card you don't remember adding, remove it immediately and notify your bank.
Also, enable purchase notifications. Go to Settings > [Your Name] > Notifications and enable App Store & iTunes notifications. You'll be notified of every download, purchase, or subscription change on your account.
Address and Contact Information
Scammers sometimes change your recovery email or phone number to lock you out of your own account. Regularly verify that your contact information is correct and only includes addresses and numbers you recognize.
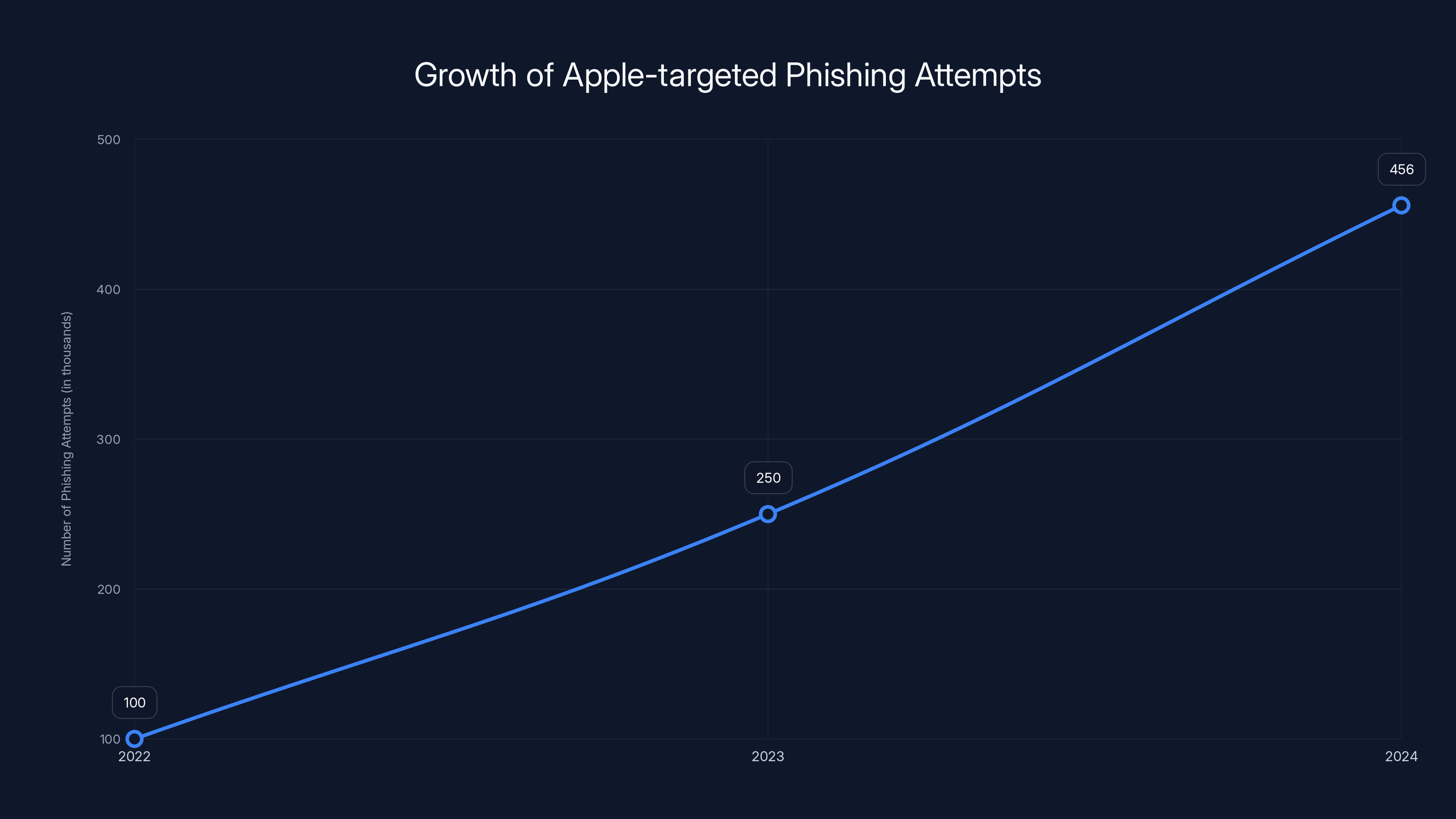
Apple-targeted phishing attempts surged by 356% from 2022 to 2024, with Apple Pay scams as the fastest-growing variant.
What Apple Is Doing About This Problem
Apple has publicly acknowledged these scams and says they're working on solutions. Here's what they've actually done:
Notification System Improvements
Apple has updated iOS to make it harder for scammers to spoof their notifications. The notification system now verifies that alerts claiming to be from Apple actually come from Apple's servers. This prevents some (but not all) of the most obvious spoofing attacks.
However, scammers still get through by using different delivery methods (SMS, email, web links) rather than native iOS notifications.
Educational Campaigns
Apple has created educational materials warning about phishing, published them on Apple Support, and worked with carriers to distribute warnings. The problem is that the people most vulnerable to these scams often don't read the warnings.
Carrier Cooperation
Apple has worked with carriers to implement better SMS filtering. Carriers now use AI to identify likely phishing messages and filter them before they reach users. This works reasonably well, but determined scammers find workarounds.
Fraud Detection Systems
When someone with a compromised password tries to sign in, Apple's systems sometimes detect it as unusual and require additional verification. This is helpful but creates a false sense of security for people who think Apple's systems will catch everything.
Authentication Standards
Apple has been pushing industry standards for better email authentication (SPF, DKIM, DMARC) that make it harder to spoof their email addresses. This has helped, but email spoofing is still possible.
The Limitations of Apple's Response
Here's the uncomfortable truth: Apple can't stop these scams through technology alone. The vulnerability isn't really a technical flaw in Apple's systems. The vulnerability is in human psychology. And you can't patch that with an iOS update.
Apple would need to:
- Completely redesign how security alerts work (radical change, lots of user confusion)
- Implement mandatory biometric verification for sensitive changes (privacy concerns, accessibility issues)
- Partner with law enforcement globally to prosecute scammers (jurisdiction issues, limited resources)
- Somehow prevent people from clicking suspicious links (impossible)
So instead, they're doing what they can: making their systems more secure, educating users, and cooperating with carriers and law enforcement. It helps, but it doesn't solve the fundamental problem.
The real defense is you: knowing how to identify these scams and refusing to click the links.
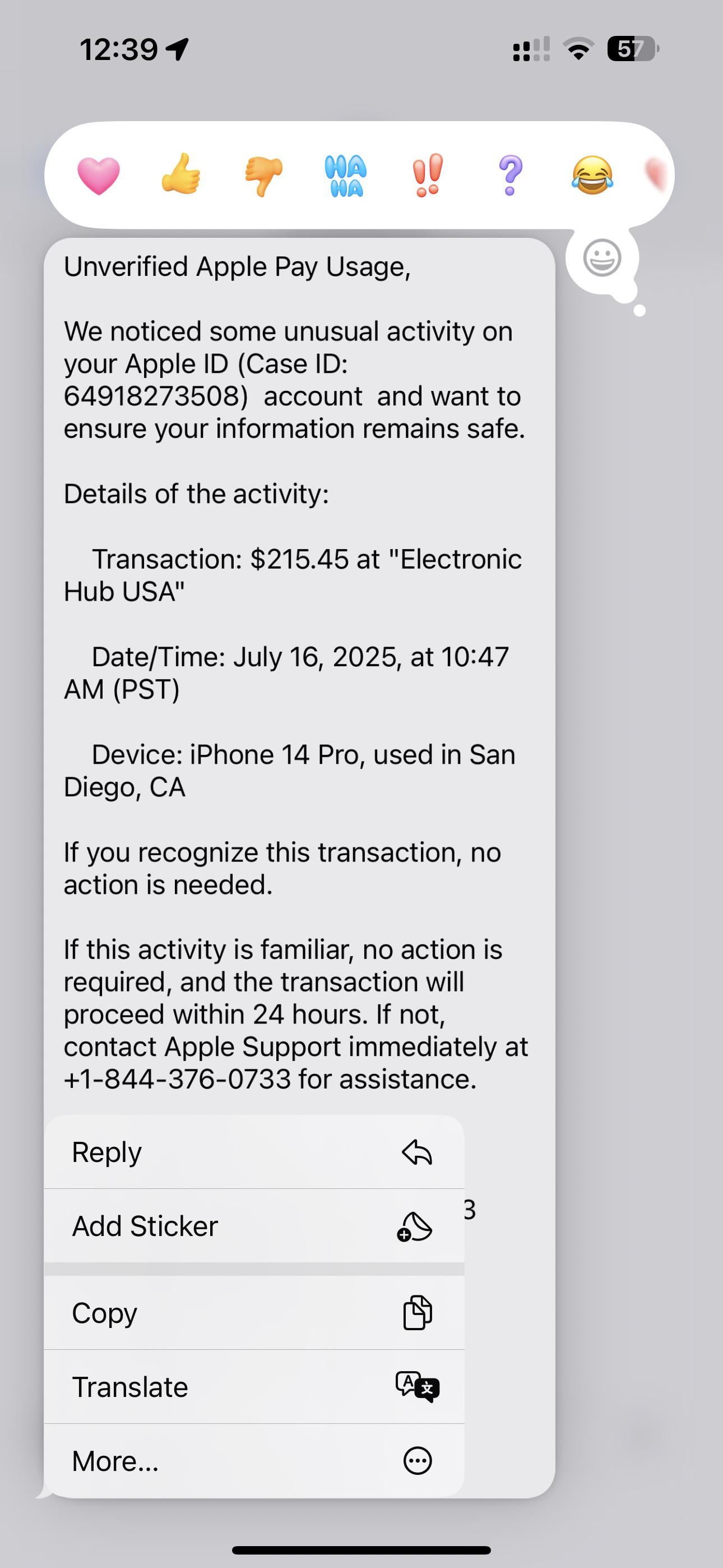
The Business Model Behind These Scams
Understanding how scammers make money from these attacks helps explain why they're so persistent and sophisticated.
Credential Harvesting
The simplest model: Scammer sends phishing message. You click link. You enter your Apple ID and password. Scammer immediately tests the credentials by trying to sign in to your account. Once confirmed as working, they sell the credentials on the dark web to other criminals.
A working Apple ID with payment information attached sells for anywhere from
Scammers might sell thousands of credentials daily. At even $5 each, that's serious money. And they're not paying for infrastructure (they use compromised servers or free services), so their profit margin is enormous.
Account Takeover and Resale
Some scammers use harvested credentials to take over accounts completely. They:
- Change the password
- Remove the legitimate owner's trusted devices
- Update recovery contact information
- Update payment methods
- Change the associated email address
Now they own the account. They can use it to purchase apps, store credit, or sell it to someone else. They might hold it for ransom ("Pay $500 to get your account back") or just milk it for value.
Payment Fraud
With your Apple ID and payment information, scammers can:
- Buy app store credit and sell it at a discount
- Purchase apps and software and resell them
- Use it to sign up for subscriptions and immediately sell the access
- Charge purchases to your linked credit cards
They're not usually trying to steal a large amount from one person. They're distributing the fraud across thousands of victims, taking small amounts from each. This makes it harder to detect and less likely to trigger fraud detection systems.
Information Aggregation and Resale
Other criminals buy harvested credentials not to use the accounts directly, but to build profiles. They combine your Apple ID information with data from other breaches, creating detailed dossiers that are valuable to identity thieves or corporate spies.
Malware Distribution
Some phishing pages don't just harvest credentials. They also distribute malware. You click the link, enter your password, and a malicious script runs on your device or downloads something to it. This might install keylogging software or other spyware.
The Economics of Scale
Here's why these scams are so hard to stop: the numbers work brilliantly for scammers.
Assume a scammer sends 10 million messages. The delivery cost (if any) is minimal. They use bulk SMS services or compromised email servers.
Of those 10 million messages, maybe 0.05% result in clicks. That's 5,000 clicks.
Of those 5,000 clicks, maybe 20% result in actual credential entry. That's 1,000 credentials harvested.
Those 1,000 credentials might generate $5,000 in value (either direct sales or fraudulent charges).
The scammer's investment? Maybe
That's a 9x return on investment. And it scales. They can run this same campaign every week.
Compare this to traditional crime. Robbing a bank requires significant planning, carries serious legal risk, and generates maybe $10,000-50,000 for an enormous amount of work. Cybercrime generates similar returns with virtually no risk (scammers operate from countries without extradition treaties) and minimal effort.
That's why these scams aren't going away. The economics are too favorable.

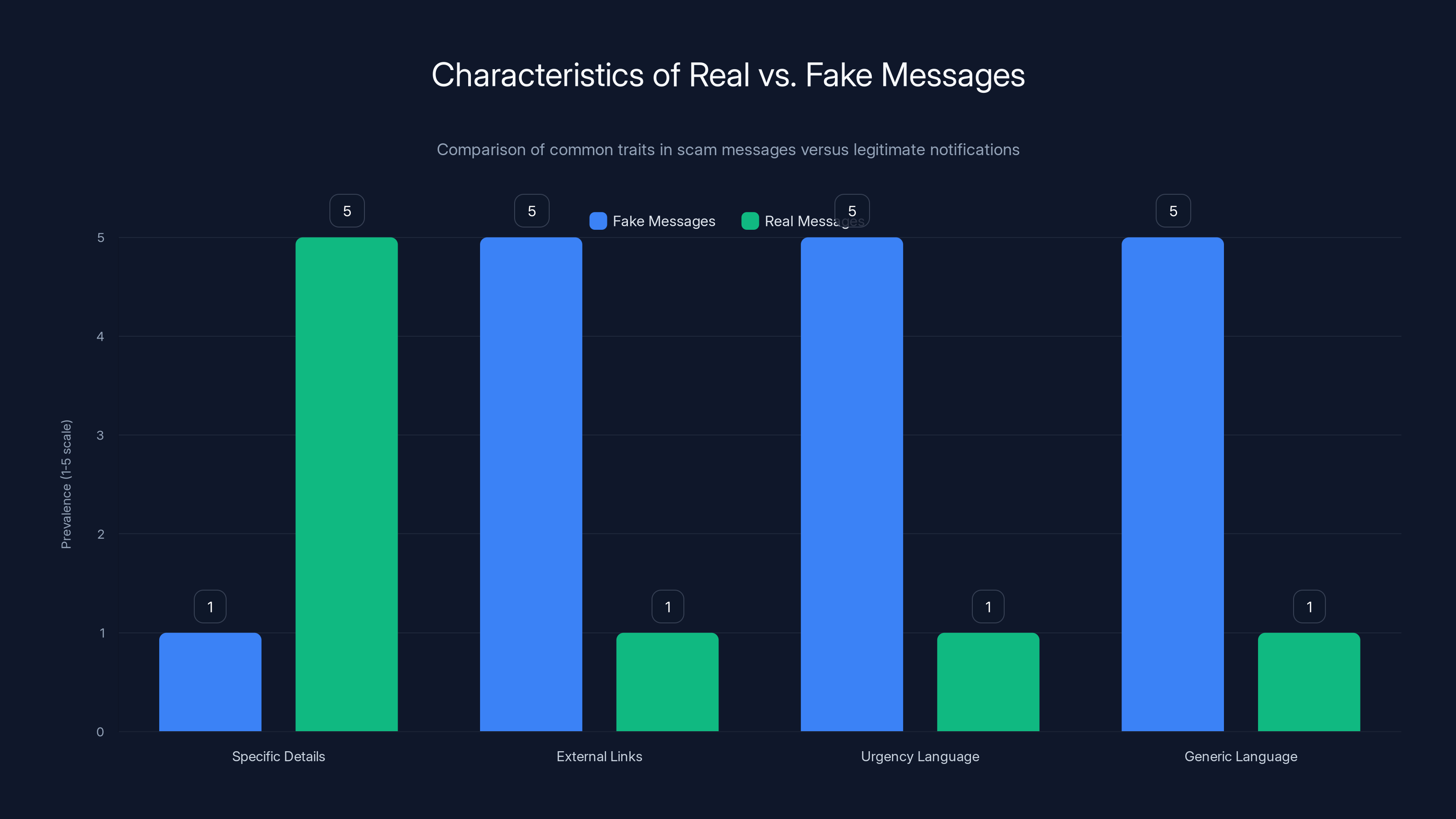
Fake messages often use external links, urgency, and generic language, while real messages provide specific details and avoid external links. Estimated data.
Regional Variations: How the Scam Changes by Location
The Apple Pay unusual activity scam isn't uniform globally. It adapts to regional circumstances, payment systems, and user behaviors.
United States Variations
In the US, the scam focuses heavily on Apple Pay because it's deeply integrated with banking. Scammers also target the broader Apple ID because US users tend to have significant payment information and subscription services linked to their accounts.
They often use SMS as the primary delivery method because SMS penetration is high and most Americans read their texts quickly without scrutiny.
The threat model mentions account lockouts and payment failure because these are fears that resonate with American users.
European Variations
European users tend to be more skeptical of unsolicited communications. GDPR regulations have also made email-based phishing less effective (fewer harvested email lists are sold legally).
So European scammers have shifted toward SMS and iMessage. They also sometimes use local language variations and references to European banks or payment systems (Revolut, N26, etc.) alongside Apple Pay.
The messaging tends to be more sophisticated in English-speaking European countries, where users are more likely to spot obvious grammatical errors.
Asian Market Variations
In markets like Singapore and Hong Kong where digital payments are ubiquitous, Apple Pay scams compete with scams targeting local payment systems like Alipay and WeChat Pay.
Scammers often use WhatsApp as the delivery method here rather than SMS, and they frequently include verification codes as part of the scam (asking you to provide 2FA codes you've received).
Emerging Markets
In countries with lower smartphone penetration, phishing tends to target web-based platforms and emails rather than SMS. Scammers also more often target Gmail and other email accounts that might be linked to payment information.
One particularly insidious variation in some markets involves scammers posing as Apple support staff and offering to "help" victims resolve problems with fake Apple messages that have already successfully tricked them.
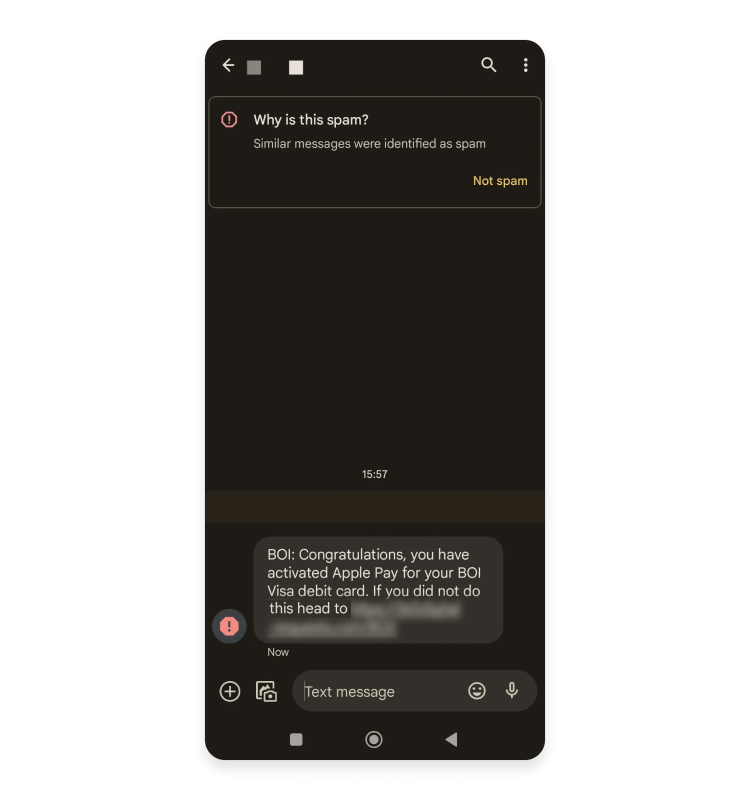
What to Do If You've Already Been Compromised
If you've fallen for one of these scams, the damage might be done, but you can still limit the harm. Time matters here—the faster you act, the better your outcome.
Immediate Actions (Do These Now)
First, change your Apple ID password from a different device. Don't use the compromised device if possible. Go to appleid.apple.com from a computer or another phone and change your password immediately.
Second, enable two-factor authentication if you haven't already. This prevents someone from signing into your account even with your new password.
Third, sign out of iCloud on your current device and sign back in with your new password. This forces any existing sessions with the old password to terminate.
Fourth, check your trusted devices. Go to Settings > [Your Name] > Password & Security > Devices. Remove any device you don't recognize.
Fifth, review your recovery information. Make sure your recovery email and phone number are only addresses and numbers you control. If the scammer changed these, change them back.
Sixth, check your payment methods. Go to Settings > [Your Name] > Payment & Shipping and examine every payment method. Remove anything you don't recognize.
Secondary Actions (Do These Within 24 Hours)
Contact your bank or credit card company. Let them know your payment information may have been compromised. They can:
- Monitor for suspicious charges
- Cancel your existing card and issue a new one
- Flag your account for unusual activity
- Lock your account temporarily while they investigate
Also contact your phone service provider. Let them know your Apple ID was compromised, and ask if they can help identify any unauthorized access or changes to your account.
Checking for Damage
Review your iTunes/App Store purchase history. Go to Settings > [Your Name] > Media & Purchases > Purchase History. Look for any purchases you didn't make. If you see unauthorized charges, report them immediately to Apple.
Check your Apple iCloud storage. Scammers sometimes upload files to compromised accounts as a way to store information or distribute malware. If you see files in your iCloud that you didn't upload, delete them and consider scanning your devices for malware.
Review your subscriptions. Some scammers subscribe compromised accounts to expensive services. Go to Settings > [Your Name] > Subscriptions and cancel anything you didn't authorize.
Check your email forwarding. Scammers sometimes set up email forwarding on compromised accounts to continue receiving communications. Go to iCloud.com, check Mail settings, and ensure no forwarding rules are active.
Long-Term Protection
Once the immediate crisis is handled, focus on preventing future compromises:
- Use a password manager to ensure your Apple ID password is unique and strong
- Enable notifications for all account activity
- Check your security settings quarterly
- Use security keys for important accounts if possible
- Consider enabling account notifications for any new devices added
If the scammer made changes to your account and you can't undo them yourself, contact Apple Support. They can help restore your account if you can verify your identity.

The Future of Apple Pay Scams
These attacks are evolving, and understanding where they're headed helps you stay ahead of them.
AI-Generated Phishing
Scammers are starting to use AI to generate highly personalized phishing messages. Instead of sending the same message to millions, they could generate millions of unique variations, each slightly tailored to the recipient based on available information.
An AI might know that you're a Mac user, that you make frequent purchases from the App Store, and that you last signed in from California. It could generate a message that references Mac specifically and mentions California.
This would make phishing significantly harder to detect. You can't just spot a generic message anymore; you'd need to recognize psychological manipulation even when it's perfectly personalized.
Deepfake Verification Attempts
Some security researchers are concerned about scammers using deepfakes—AI-generated audio or video of Apple representatives—to convince victims to complete compromising actions.
Imagine receiving an email from someone claiming to be Apple Support, with an attached video of an "Apple representative" explaining that your account needs verification. The video looks perfect, sounds perfect, and is entirely fake.
This hasn't reached mainstream phishing yet, but it's technically possible and getting easier to do.
Compromised Device Integration
As IoT and smart devices proliferate, scammers will try to use compromised devices as distribution vectors. They might compromise a smart TV or smart home hub, have it display a fake Apple Pay alert on your device's main screen.
Or they might compromise your Mac and have Safari show a fake Apple alert that looks exactly like a native system notification because it's being injected into the browser at a low level.
Multi-Stage Attacks
The future likely involves more sophisticated multi-stage attacks. Stage 1 is the phishing message. Stage 2 might be a phone call from someone claiming to be Apple, using information harvested from Stage 1 to seem legitimate. Stage 3 might be malware that was hidden on a webpage you visited.
Scammers are becoming more patient and more thorough. They're willing to invest more effort per victim if the payoff is larger.
Authentication Bypasses
As 2FA becomes more common, scammers are developing techniques to bypass it. Some phishing pages now include real-time authentication bypass, where they capture your 2FA code as you enter it and use it simultaneously with your password to sign into your account.
Apple will continue adding security features. Scammers will continue finding ways around them. It's an arms race with no permanent winner.
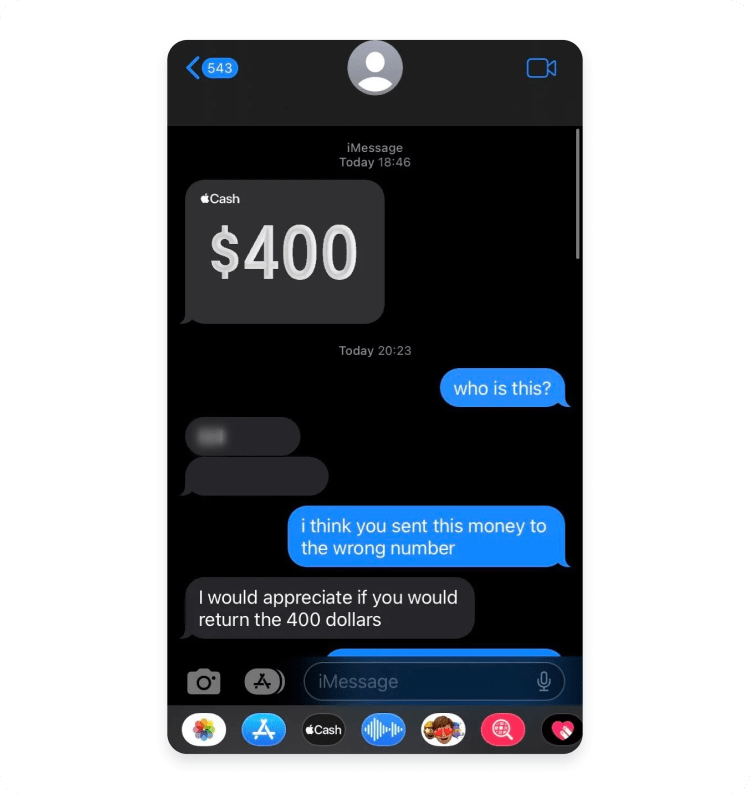
FAQ
What does Apple consider "unusual activity" on an account?
Apple classifies unusual activity as sign-in attempts from unfamiliar devices, locations, or times; multiple failed password attempts; or unexpected payment changes. Real Apple notifications about unusual activity will be specific about what triggered the alert, include timestamps, and describe the exact action that seemed odd. They'll never ask you to verify information or click external links to resolve the issue.
How can I tell the difference between a text from Apple and a phishing text?
Real Apple texts come from specific numbers that Apple publishes (not random numbers), contain specific information about what happened to your account, and direct you to native apps like Settings rather than external links. Phishing texts often use similar-looking but slightly different phone numbers, contain vague language about "unusual activity," and include links to external websites. When in doubt, ignore the text and manually open Settings or iCloud.com to check your account status directly.
Should I ever click a link in an Apple notification?
Rare. Apple's security alerts almost never include clickable links. If an alert does include a link, verify through official channels first (Settings app, Apple.com, or a call to Apple Support) before clicking anything. The only exceptions are notifications about actual Apple products you've installed or app updates, which might link to the App Store. Everything else is suspect.
What if I already entered my password into a phishing page?
Change your Apple ID password immediately from a different device, enable two-factor authentication if you haven't already, and review your account activity for unauthorized changes. If the phishing page was sophisticated, it might have also harvested two-factor authentication codes, so monitor your account closely and consider contacting your bank about potential fraud.
Can scammers access my iPhone if they have my Apple ID password?
Not easily, especially if you have two-factor authentication enabled. With just your password, they can sign into iCloud.com or attempt to sign into your account from a different device. But your actual iPhone would require your face/fingerprint to unlock, so they can't physically control it. However, they could potentially lock you out of your own account if they change your password and recovery information.
How do I report a phishing message to Apple?
Forward the message to reportphishing@apple.com. Include the full message content, the date and time you received it, and which app or service delivered it. Apple's security team reviews these reports and uses the information to identify new phishing variations. You should also report it to your carrier (most have phishing report mechanisms) and mark it as junk/spam in your messaging app.
Are iMessage phishing messages riskier than SMS phishing?
They can be, because iMessage appears more official and uses Apple's infrastructure. However, the fundamental scam is the same: don't click links or enter credentials based on unsolicited messages. iMessage messages are marginally more credible-looking than SMS, which is precisely why scammers prefer them, but they're equally dangerous if they contain phishing links.
Can enabling Do Not Disturb prevent phishing messages?
No. Do Not Disturb mutes notifications but doesn't prevent messages from arriving. You can still receive phishing messages while Do Not Disturb is enabled; you just won't hear about them until you unlock your phone. Using Do Not Disturb might actually make you less likely to notice and report phishing messages to Apple.
What's the difference between phishing and vishing?
Phishing is deceptive communication via email, SMS, or messages. Vishing (voice phishing) is the same concept but via phone calls. A scammer might call pretending to be Apple support, reference details from a previous phishing email you received, and ask you to verify information or disable security features. Both are social engineering attacks trying to extract credentials or money.
If I see an Apple Pay scam message, should I block the sender?
Yes, blocking the sender prevents them from reaching you again. But realize that phishing messages often come from spoofed numbers or different numbers each time, so blocking one number doesn't stop the campaign. Your best defense is still skepticism and verification rather than just blocking.
Conclusion: Your Defense Against Apple Pay Scams
These scams persist because they work. They're simple, scalable, and the payoff is significant. Millions of people have been targeted, and a percentage will click the link. As long as that percentage is profitable, scammers will keep sending these messages.
But you don't have to be that percentage.
The defense against these attacks isn't complicated. It's built on a few core principles that protect you not just from Apple Pay scams but from most phishing attacks:
First, cultivate suspicion. When you receive an unsolicited notification asking you to take action—especially action related to money or account security—pause. That instinct to act immediately is exactly what scammers want. Give yourself permission to be skeptical.
Second, verify through official channels. Never use information from a suspicious message to verify the message's legitimacy. Instead, open the Settings app yourself, call Apple directly using a number you looked up independently, or visit Apple's website directly. This takes an extra 30 seconds but eliminates 99% of phishing risk.
Third, understand that Apple's security team doesn't need your help. When you receive a notification about unusual activity, Apple already knows about it. They have your account data, your device data, your location data, your sign-in history. They don't need you to provide information via an unsecured link. If they need you to do something, the legitimate notification will direct you to the Settings app, not an external website.
Fourth, enable the security features you have available. Two-factor authentication is the single most important thing you can do. Recovery contacts and recovery keys are also valuable. These features exist specifically to prevent account takeovers when phishing succeeds.
Fifth, stay informed. These scams evolve. What works today might not work in six months. By reading articles like this and staying aware of common attack patterns, you're developing the pattern recognition skills that make you a harder target.
The reality is that no security measure will ever be 100% effective. But the combination of awareness, good security practices, and quick response to breaches will protect you in virtually all circumstances.
You'll probably receive one of these phishing messages eventually. Most active smartphone users do. The difference between victims and non-victims isn't luck. It's these practices.
Apply them. Share them with people you know. And remember: Apple's security team doesn't need your help verifying your account. Ever. If a message makes you doubt that principle, it's trying to scam you.

Key Takeaways
- Fake Apple Pay alerts use urgent language, external links, and credential requests—real Apple alerts never do this
- Check sender information carefully; scammers use phone numbers and email domains that look similar to Apple's official ones
- Two-factor authentication is your strongest defense—enable it immediately if you haven't already
- If you've clicked a suspicious link, change your Apple ID password from a different device and enable 2FA
- Report phishing messages to reportphishing@apple.com and your carrier to help protect others from the same attack
- Scammers profit from harvested credentials ($5-50 each); the economics are why these scams persist despite awareness campaigns
- Verify account issues through Settings or iCloud.com directly, never by clicking links in unsolicited notifications
- When in doubt, call Apple directly using a number you find independently—not a number from the suspicious message
Related Articles
- Malwarebytes and ChatGPT: The AI Scam Detection Game-Changer [2025]
- Minecraft Server Security Guide: Keep Your Server Safe [2025]
- Canada Computers Data Breach 2025: Timeline, Impact, Protection [2025]
- Jeffrey Epstein's 'Personal Hacker': Zero-Day Exploits & Cyber Espionage [2025]
- ExpressVPN Valentine's Day Deal Guide: Save Up to 81% [2025]
- NordVPN No-Logs Audit 2025: What Independent Verification Really Means
![Apple Pay Unusual Activity Scam: How to Spot Fake Messages [2025]](https://tryrunable.com/blog/apple-pay-unusual-activity-scam-how-to-spot-fake-messages-20/image-1-1770210440430.jpg)



