Android Privacy Tips: Protect Your Device From Prying Eyes [2025]
Your Android phone isn't just a communication device anymore. It's a digital vault holding your passwords, financial information, location history, intimate photos, and conversations with people you care about. The problem? Most people don't realize how exposed they actually are.
I'll be honest: Android privacy isn't a set-it-and-forget-it situation. It requires deliberate action, regular maintenance, and understanding what you're actually protecting against. There's online surveillance from apps, data brokers, and advertisers. Then there's physical security: what happens when someone grabs your phone off a table, or your partner wants to snoop?
This guide covers the practical, specific steps you need to take right now to lock down your Android device. Not the theoretical stuff that sounds good in marketing materials. Real security measures that actually work and won't require a PhD to understand.
I've tested these methods across multiple Android phones and versions. Some take five minutes. Others require ongoing vigilance. All of them matter.
TL; DR
- Enable biometric authentication: Use fingerprint or facial recognition as your primary unlock method, not just PIN codes
- Control app permissions: Disable location, camera, and microphone access for apps that don't legitimately need them
- Encrypt sensitive communications: Use encrypted messaging apps for conversations you want to keep private
- Review privacy settings: Android's built-in privacy controls let you see what apps access and restrict data sharing
- Use a VPN selectively: A quality VPN masks your IP address, but choose carefully since VPN providers can see all traffic
- Lock down Google account settings: Your Google account is the master key to your Android device, so protect it aggressively
- Disable default sharing features: Turn off automatic photo backup, location sharing, and crash reporting that send data to cloud services
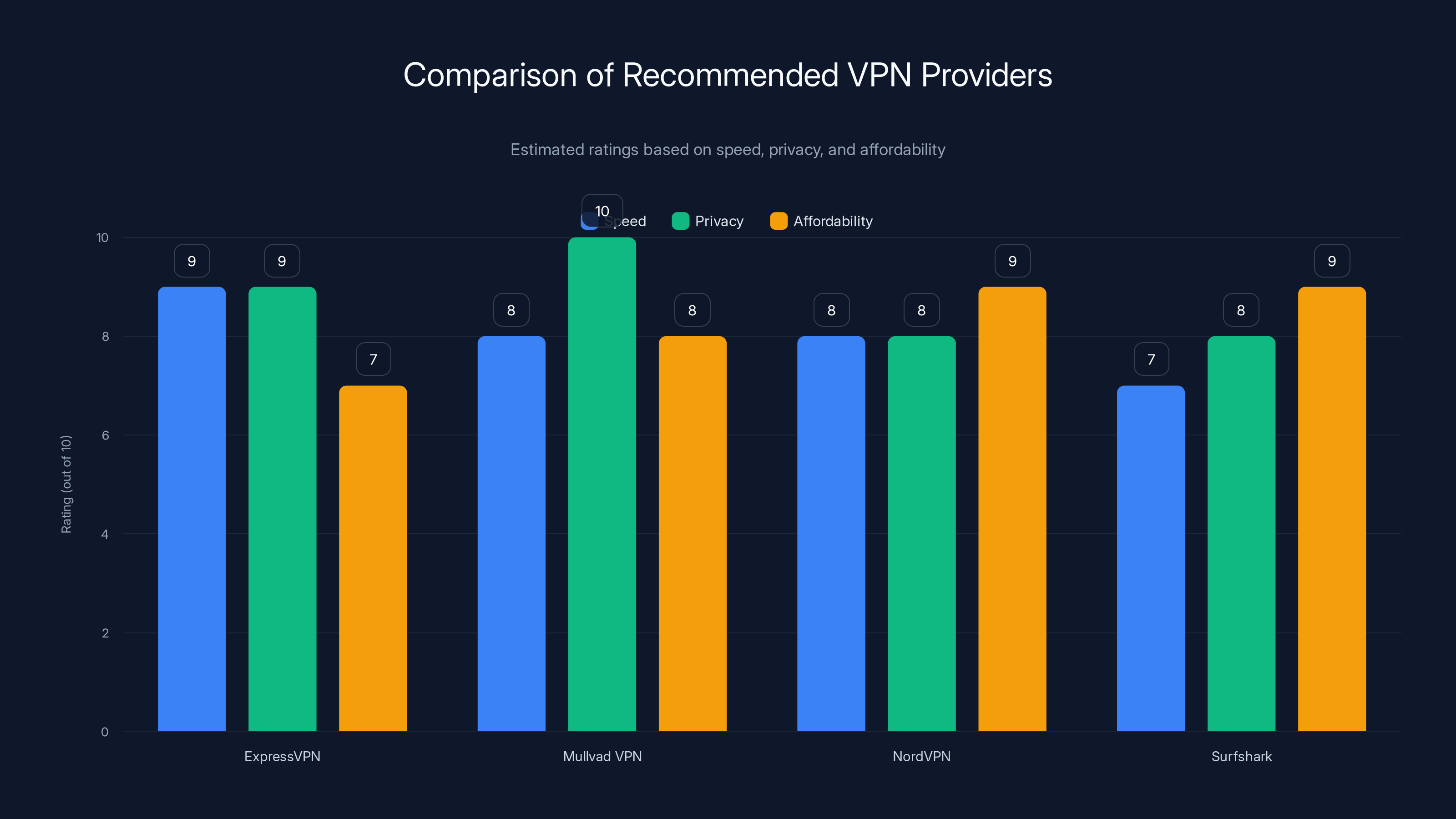
ExpressVPN and Mullvad VPN lead in privacy, while NordVPN and Surfshark offer better affordability. Estimated data based on typical VPN features.
Understanding the Android Privacy Landscape
Android powers over 3 billion devices worldwide, making it the most-used operating system on Earth. That scale attracts attention from governments, corporations, and criminals. Google collects staggering amounts of data about Android users, and that's before third-party apps get involved.
The architecture of Android actually gives you more privacy control than iPhone in some ways. You can disable Google services, use alternative app stores, and modify system-level settings. But that power comes with responsibility. Default Android configurations leak more data than most users realize.
Here's what's typically happening in the background without your knowledge. Apps send location data to advertisers through location APIs. Your phone pings Google's servers constantly with information about your location, apps you use, and devices on your network. Google Analytics tracks your behavior across websites. Photo backups go to Google Photos automatically. Your search history feeds Google's advertising machine.
None of this is necessarily malicious in intent, but it's definitely invasive. Google's privacy policy technically discloses all of this, but most people skip straight past 47-page terms of service documents.
The second privacy concern is physical security. Someone with direct access to your phone can bypass encryption if you're using a weak PIN code. They can enable USB debugging to pull files off your device. They can watch you type your password. These aren't theoretical risks. Relationship surveillance is a real problem affecting millions of people annually.
Then there's the app ecosystem. Android's app store hosts 3.6 million apps, and not all of them are trustworthy. Even legitimate apps often request permissions they don't actually need. A flashlight app requesting access to your contacts? That's real behavior. A weather app wanting to enable your microphone? It happens.
The good news is that modern Android (version 12 and later) has substantially improved privacy controls. You're not helpless. You just need to know which settings to change and why they matter.
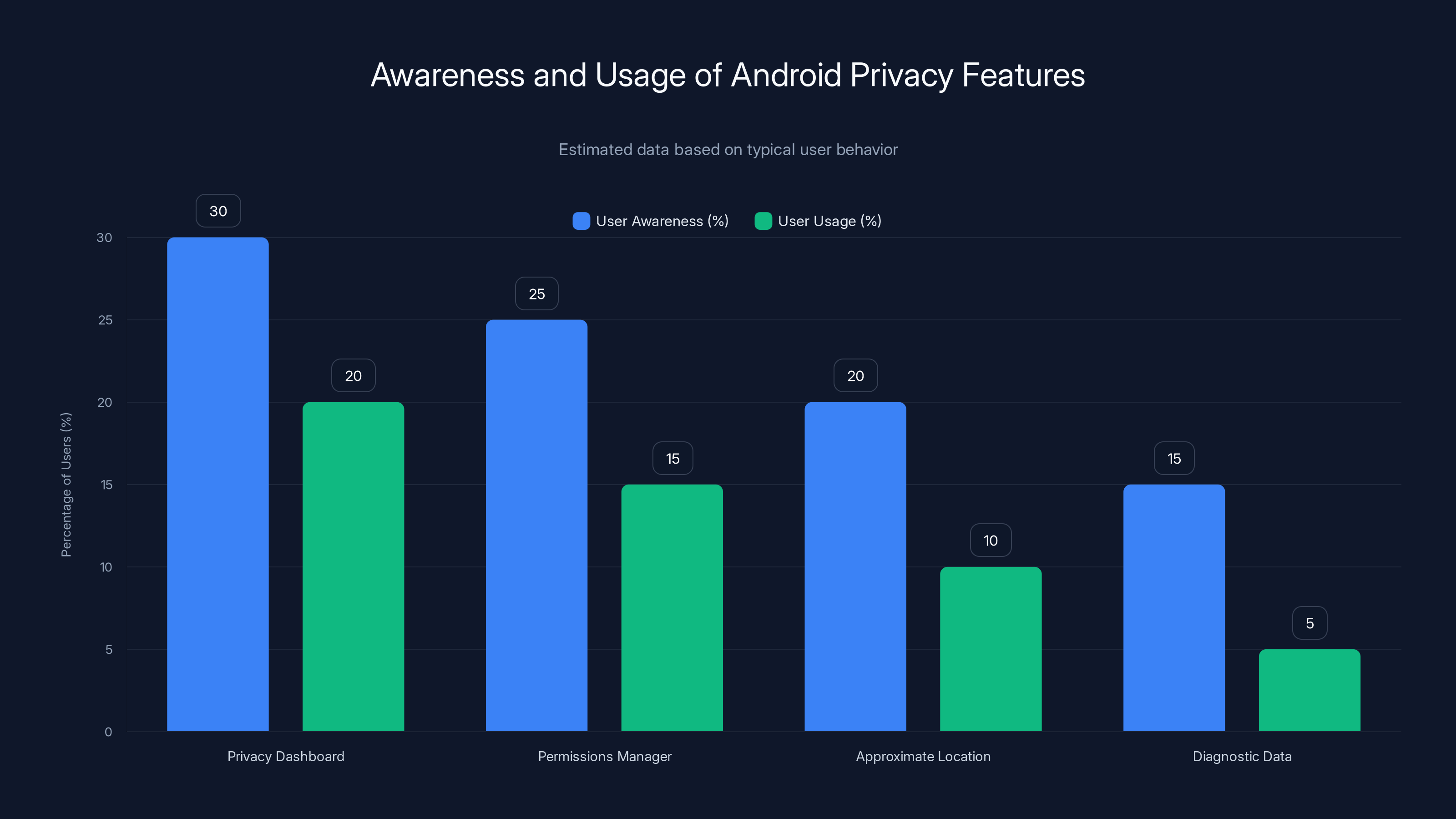
Estimated data suggests that while awareness of Android's privacy features is relatively low, actual usage is even lower. Increasing awareness could enhance user privacy.
Lock Down Your Device With Strong Authentication
Authentication is your first line of defense. If someone gets past your unlock screen, they have access to everything: encrypted messages, banking apps, social media accounts, photos, and sensitive documents.
Most people still use PIN codes as their primary unlock method. A four-digit PIN has 10,000 possible combinations, which sounds secure until you realize someone watching you unlock your phone can memorize it instantly. If your phone is stolen, attackers can crack a four-digit PIN in seconds. A six-digit PIN is barely better.
Biometric authentication changes the game entirely. Your fingerprint is unique, can't be guessed, and isn't easily copied. Facial recognition on modern phones uses infrared scanning that defeats most spoofing attempts, though not all.
First, enable fingerprint authentication. Go to Settings > Security and Privacy > Fingerprint. Register at least four fingers—this gives you redundancy if one finger is injured and makes unlocking faster since you have more options. When registering each fingerprint, scan it from multiple angles and with varying pressure. This trains the system to recognize your finger in different conditions.
Optional but worthwhile: set up facial recognition as a secondary option. Don't disable PIN-based unlock entirely. You'll need it if your phone doesn't recognize you (wet fingers, dirt on the camera, poor lighting, or when you're wearing masks).
Here's where most people miss an important detail: configure what happens when your biometric fails. Go to Settings > Security > Lock Screen. Turn on "Require PIN after failed biometric attempts." Set it to require a PIN after just 5 failed attempts. This prevents someone from repeatedly trying different fingerprints or angles on your phone.
Also critical: enable "Show notification on lock screen" to off. By default, Android displays notification previews on your lock screen where anyone can see them. Disable this. You want notifications to be invisible until you actually unlock the phone. Go to Settings > Notifications and toggle "Show notifications on lock screen" to off.
For the paranoid: consider disabling "Smart Lock" features that automatically unlock your phone when connected to trusted Bluetooth devices or recognized locations. These are convenience features that reduce security. If you use them, at minimum disable location-based Smart Lock. Someone who knows you visit the same coffee shop every morning can unlock your phone there.
Master App Permissions and Control What Apps Can Access
App permissions are the biggest privacy leak on most Android phones. Users grant permissions in bulk during installation and never review them again. Most apps request far more permissions than they actually need.
Android's permission system works on a granular level starting with Android 6.0 (2015). Instead of an all-or-nothing approach, you can grant permission to access location to one app and deny it to another. You can allow an app to access your camera only while the app is open. These granular controls exist, but they're buried in settings.
Start here: open Settings > Apps > App Permissions. You'll see categories like Location, Camera, Microphone, Contacts, Photos and Videos, etc. Tap each category and review which apps have access.
Location permissions deserve special attention. Any app with location access can build a detailed map of your movements over time. They know where you sleep (your home), where you work, and everywhere you go between. Advertisers love this data because it reveals your habits and preferences with precision. A dating app knowing your location makes sense. Your banking app? No. Your calculator app? Absolutely not.
Here's the process: go to Settings > Location. First, toggle Location Services completely off if you don't actively need it. Most people think they need it always on, but you can toggle it back on when you actually need maps or location-based apps.
If you keep Location on, go to Settings > Location > Location Services and review the list. Disable it for any app that doesn't have a legitimate reason. Then go to Settings > Apps > App Permissions > Location and check both "Allow all the time" and "Allow only while using the app" sections. Remove apps that don't need constant access.
Camera and microphone permissions follow the same principle. Go to Settings > Apps > App Permissions > Camera. Most apps shouldn't have this. A video calling app? Yes. A note-taking app? No. Social media apps often request camera access to let you take photos, but they don't need it enabled when you're just scrolling your feed.
Here's something unsettling: even with permission denied, some apps can still detect whether a camera or microphone is present on your device. They can't activate it without permission, but they know it exists. For microphone specifically, there's no real way to prevent this detection, but you can ensure the app can't actually record.
Contacts and calendar permissions are similarly often abused. Apps request contact access to "improve your experience" which usually means they want to upload your entire address book for marketing purposes. If you give a fitness app access to your contacts, it might use that data to build social graphs and recommend friends. Disable this aggressively.
One more thing: go to Settings > Apps > App Permissions > Nearby Devices. This controls Bluetooth access. Many apps request this permission but don't actually need it. Disabling it prevents apps from scanning for Bluetooth devices near you.
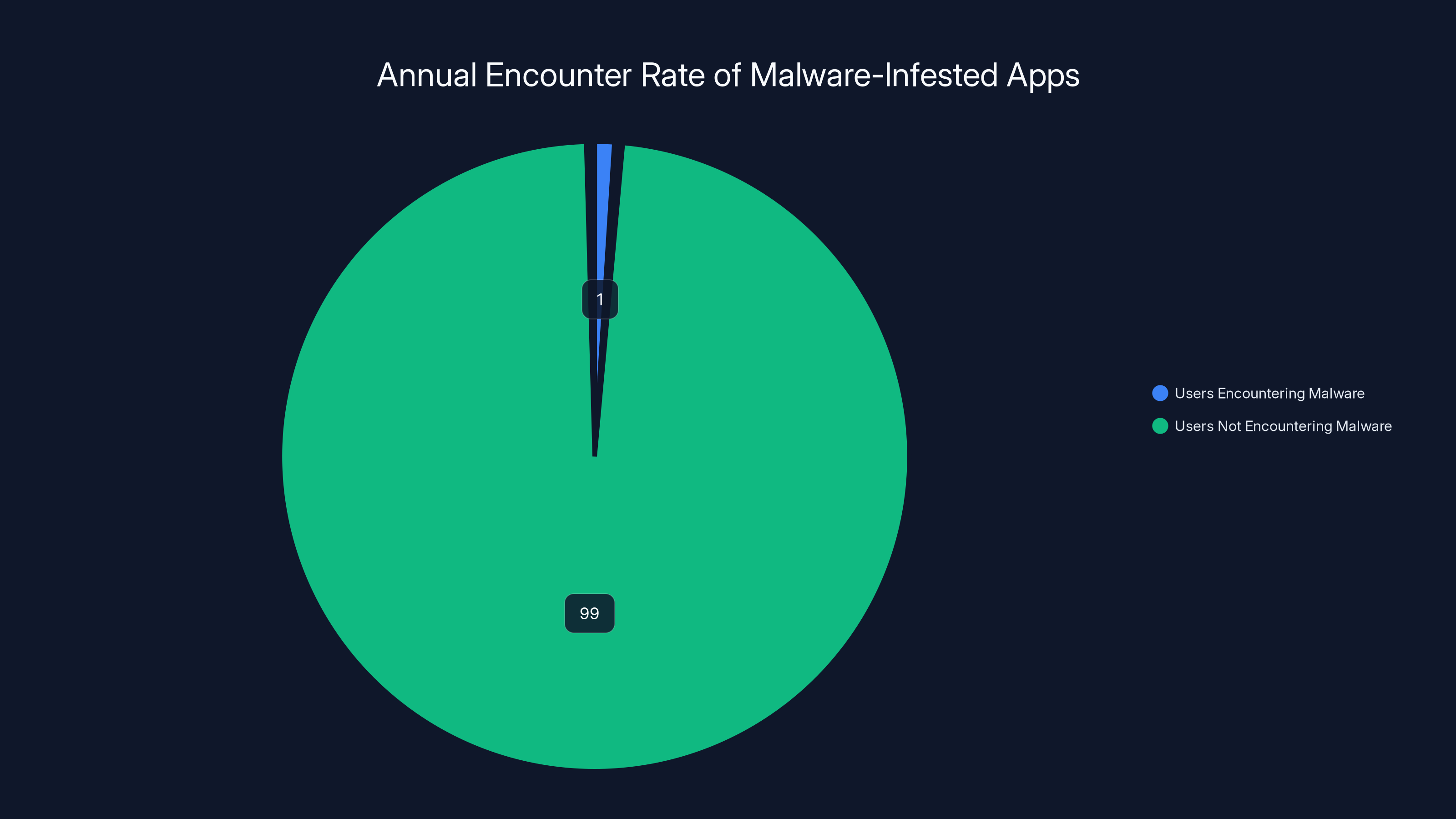
An estimated 1% of Android users encounter malware-infected apps annually, equating to about 30 million people. Estimated data.
Use Android's Built-In Privacy Controls and Diagnostic Options
Google added substantial privacy controls to Android starting with version 12. Many users don't know they exist. These controls let you see exactly what data is being collected and shut it down.
First, the Privacy Dashboard. Go to Settings > Privacy > Privacy Dashboard. This shows you a history of which apps accessed sensitive data in the last 24 hours. You'll see that the Maps app accessed location (expected), but you might also see that a music streaming app accessed your microphone (unexpected). This dashboard is your surveillance detector.
Click on any app to see more details. If something looks wrong, you can revoke that app's permissions immediately. The dashboard makes permission abuse visible, which is the first step toward fixing it.
Second, go to Settings > Privacy > Permissions Manager. This is where you can manage permissions by category. Unlike the dashboard, this shows you all apps with specific permissions, not just recent access. You can set default permissions for new apps here. I recommend setting the default for Location, Camera, and Microphone to "Don't allow," then manually enabling them only for apps that need them.
Third, enable the Approximate Location feature if you're concerned about precise tracking. Go to Settings > Privacy > Permissions > Location and toggle "Use approximate location" on for specific apps. This gives an app your general vicinity (within several kilometers) instead of exact coordinates. It's useful enough for most location-based services but insufficient for tracking your exact movements.
Next, disable Diagnostic Data. Go to Settings > Google > Manage your Google Account > Data & Privacy. Look for "Android diagnostics." Google collects diagnostic data about your device's performance, battery usage, app crashes, and more. This data is ostensibly used to improve Android, but it's also connected to your Google account. Toggle this off. Doing so prevents diagnostic reports from being automatically sent to Google.
Similarly, go to Settings > Google > Manage your Google Account > Data & Privacy and look for "Web & App Activity." This setting controls whether Google logs your search history, YouTube history, and app activity. Disable it. If it's already on, click "Turn off Web & App Activity." This is one of the most significant privacy controls available, and it's usually left enabled by default.
Go further: Settings > Google > Manage your Google Account > Data & Privacy > Location Settings. You'll see "Location History" which records everywhere you go. Disable it. Even if Location Services are off on your device, if Location History is enabled, Google has a record of your movements.
One more critical setting: Settings > Google > Manage your Google Account > Data & Privacy > Ads Settings. Here you can disable Personalized ads. Even with this disabled, you'll still see ads, but Google won't target them based on your browsing history, location, and app usage. The ads become random instead of targeted. This is a meaningful privacy win.
For paranoid users, consider disabling Backup and Restore. Go to Settings > System > Backup and Restore and toggle both "Backup to Google One" and "Restore from Google account" off. This prevents your device's data from being backed up to Google's servers automatically. Note: this makes it harder to restore your device if you lose it, so it's a trade-off between privacy and convenience.
Secure Your Communication With Encryption
Private communication is foundational to privacy overall. If someone can read your messages, they know everything: your relationships, your thoughts, your secrets, your plans, your vulnerabilities.
Android's default SMS text messages aren't encrypted. They're plain text transmitted through telecom networks and stored on servers you don't control. Assume anyone with access to your carrier's infrastructure could read them. If someone steals your phone, they can read all your SMS history instantly.
The solution is encrypted messaging. Encryption transforms your message into an unreadable format using mathematical keys. Only the person with the matching key can decrypt it. Even the company operating the messaging service can't read your messages because they don't have the keys.
WhatsApp is the most popular encrypted messaging app globally. It uses end-to-end encryption by default, which means your messages are encrypted on your phone, transmitted in encrypted form, and only decrypted on the recipient's phone. WhatsApp's servers never have access to your unencrypted messages. Go to Settings > Chats > Enable automatically delete messages and set it to 90 days. This prevents your entire conversation history from being stored indefinitely.
Signal is more privacy-focused than WhatsApp. Signal is open-source, meaning security researchers can audit the code. It's operated by a nonprofit organization (Signal Foundation) rather than a for-profit company, which removes advertising incentives. Signal doesn't collect metadata like WhatsApp does. The Signal app itself doesn't require a phone number in newer versions, letting you use it pseudonymously.
Telegram is popular but technically less secure for private conversations. Telegram uses optional encryption ("Secret Chats") rather than default encryption. In a Secret Chat, messages are end-to-end encrypted and disappear automatically. But regular Telegram chats are only encrypted in transit to Telegram's servers, not end-to-end. Telegram could theoretically read your messages, though they claim not to. Use Secret Chats for sensitive conversations on Telegram.
For even more paranoia: use a combination of encrypted messaging + disappearing messages. In WhatsApp, go to a specific chat > View Contact > Disappearing Messages > set to 24 hours. Messages automatically delete after 24 hours on both phones. This limits the window of exposure if your phone is ever compromised.
Here's something to know about Signal specifically: it requires a phone number to set up, but it doesn't require your real name. You can keep your Signal account pseudonymous. You also can't search your entire Signal chat history by keyword the way you can on WhatsApp, which means law enforcement can't subpoena your Signal account and get a searchable archive of conversations. WhatsApp stores everything, making it more discoverable in legal proceedings.
Final note on emails: Gmail is encrypted in transit but Google can read the content. For truly sensitive emails, use ProtonMail or Tutanota, which offer end-to-end encryption. Compose sensitive emails on those platforms instead of Gmail. Note that this only protects content from Google, not from the recipient or email servers they use.
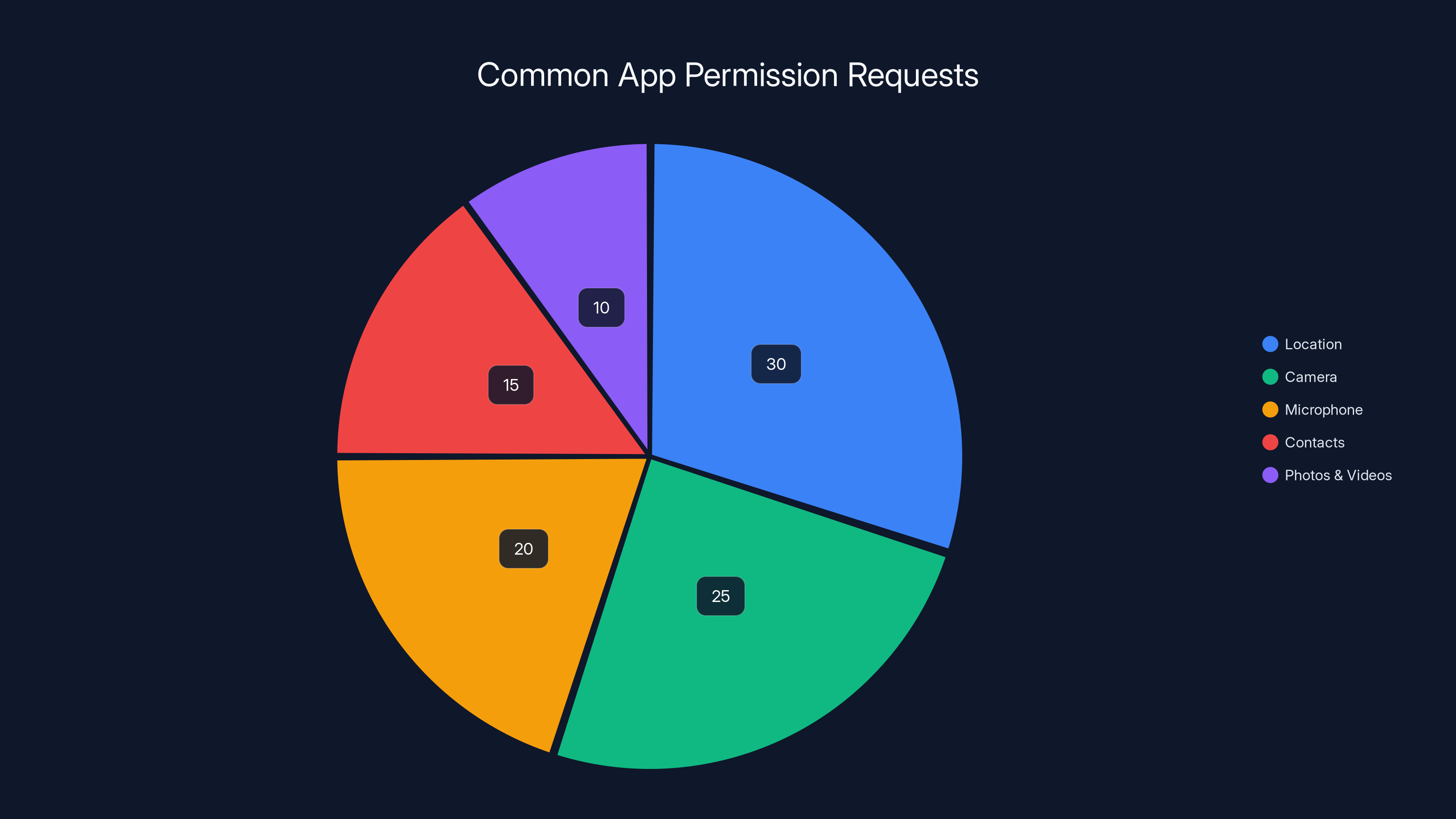
Estimated data shows that location permissions are the most requested, followed by camera and microphone. This highlights the importance of reviewing app permissions regularly.
Manage Your Google Account As Your Master Security Key
Your Google account is the master key to your entire Android ecosystem. It controls your Play Store access, your backup data, your location history, your payment methods, and much more. If someone compromises your Google account, they can lock you out of your own phone, access your entire email history, steal your payment information, and impersonate you to your contacts.
Securing your Google account is therefore essential to securing your Android device.
Start with a strong password. Your Google password should be at least 16 characters, use uppercase and lowercase letters, numbers, and symbols. Make it unique—don't reuse it for other accounts. If you reuse passwords and one service gets breached, attackers have your Google account password. Use a password manager (like Bitwarden, 1Password, or KeePassXC) to generate and store strong unique passwords.
Next, enable two-factor authentication. Go to Google account > Security > 2-Step Verification. Google will send you a code via text message or authenticator app when you sign in from a new device. This prevents someone from accessing your account even if they have your password. Use an authenticator app like Google Authenticator or Authy instead of SMS-based codes when possible. SMS codes can be intercepted or redirected through SIM swapping attacks.
Set up passkeys if your phone supports it. Passkeys are passwordless authentication that uses cryptographic keys stored on your phone. They're faster and more secure than passwords and 2FA combined. Go to Google account > Security > Passkeys and follow the prompts to set up your first passkey.
Review your Trusted Devices regularly. Go to Google account > Security > Your devices and look for unknown devices. If you see a device you don't recognize, click on it and select "Remove." This is crucial because a compromised device on your account can access all your data.
Check Security Checkup to identify vulnerabilities in your account. Google provides a guided tour through your security settings. Go to Google account > Security > Security Checkup. It flags things like accounts with your password, apps with access to your account, recovery phone numbers and emails, etc.
Review Connected Apps & Services. Go to Google account > Security > Apps with account access. Many apps ask for permission to access your Google account. This allows them to see your email, calendar, or other Google data. Remove apps you no longer use. For apps you keep, click on them to see exactly what data they can access. Remove unnecessary permissions.
Enable Advanced Protection Program if you're at high risk. This feature is designed for journalists, activists, and people who are targeted by sophisticated attackers. It requires physical security keys for sign-in instead of passwords and 2FA. It's inconvenient but extremely secure. Go to Google account > Security > Advanced Protection Program.
Finally, create a recovery email and phone number. If your account gets compromised, Google will use these to verify your identity for recovery. Go to Google account > Personal info > Email and phone. Set up a recovery email separate from your primary Gmail and a recovery phone number.

Deploy a VPN to Mask Your Online Activity
A Virtual Private Network encrypts all traffic leaving your phone and routes it through a server elsewhere, masking your IP address and location from websites and internet service providers. It's a powerful privacy tool, but with important caveats.
First, what a VPN does: when you visit a website or use an app without a VPN, your ISP sees everything. They see every website you visit, every app you use, every server you connect to. Your ISP is legally required to keep this data in the US for one year, and they sell it to data brokers. A VPN encrypts this traffic so your ISP sees only that you're connected to a VPN server, not what you're doing through it.
Second, what a VPN doesn't do: it doesn't hide you from the website itself. If you visit Google.com through a VPN, Google knows you're there. They can't see your IP address, but they can see your searches and browsing behavior based on your Google account. Similarly, apps still know who you are if you're logged in. A VPN hides your network-level activity, not your identity.
Third and most important: you're trusting a VPN provider with all your traffic. If you use a trustworthy VPN provider, great. If you use a shady one that logs your activity and sells it to advertisers, you've just made your privacy worse. VPN providers can see all your traffic (though it's encrypted so websites can't). Never use free VPNs because if the service is free, you're the product.
Recommended VPN providers balance speed, privacy, and affordability:
ExpressVPN operates servers in 105 countries, maintains zero-log policies, and uses strong encryption. It costs about $13/month if you commit annually. Their apps are user-friendly, and they explicitly don't share data with third parties.
Mullvad VPN is open-source and operates with extreme privacy focus. They don't require email addresses, supporting anonymous account creation using random 16-digit numbers. They explicitly don't keep logs. It costs about $5/month.
ProtonVPN is operated by the same company that makes ProtonMail encrypted email. They're based in Switzerland, which has strong privacy laws. They maintain no-log policies and offer a free tier with limited bandwidth, starting at $10/month for premium.
IVPN is another open-source, privacy-first option. They're based in Gibraltar and don't keep logs. They cost about $10/month.
How to set up a VPN on Android: go to Settings > Network & Internet > VPN. Click "Add VPN" and follow the app's instructions. Most VPN apps walk you through this. Configure the VPN to auto-connect when you open a particular app. Some VPN services allow "killswitch" functionality that blocks internet entirely if the VPN disconnects, preventing data leaks.
Here's the reality check: using a VPN adds latency to your connection because traffic has to route through additional servers. Video streaming might buffer. Online gaming might have slightly higher ping. It's a trade-off between privacy and performance. Most people don't notice it, but streaming 4K video on a VPN might noticeably buffer depending on your internet speed.
Also, some websites block VPN traffic. Netflix, Disney+, and other streaming services actively block VPN access because they want to enforce regional content restrictions. Banking websites sometimes block VPN traffic for security reasons. You might need to disable your VPN to access certain services.
Best practice: use a VPN all the time on public Wi-Fi networks (coffee shops, hotels, airports). These networks are completely unencrypted by default, meaning anyone with a laptop can eavesdrop on all the traffic. On your home network with a secure password, VPN is less critical since the connection is already encrypted. But using a VPN all the time doesn't hurt much and provides consistent privacy.

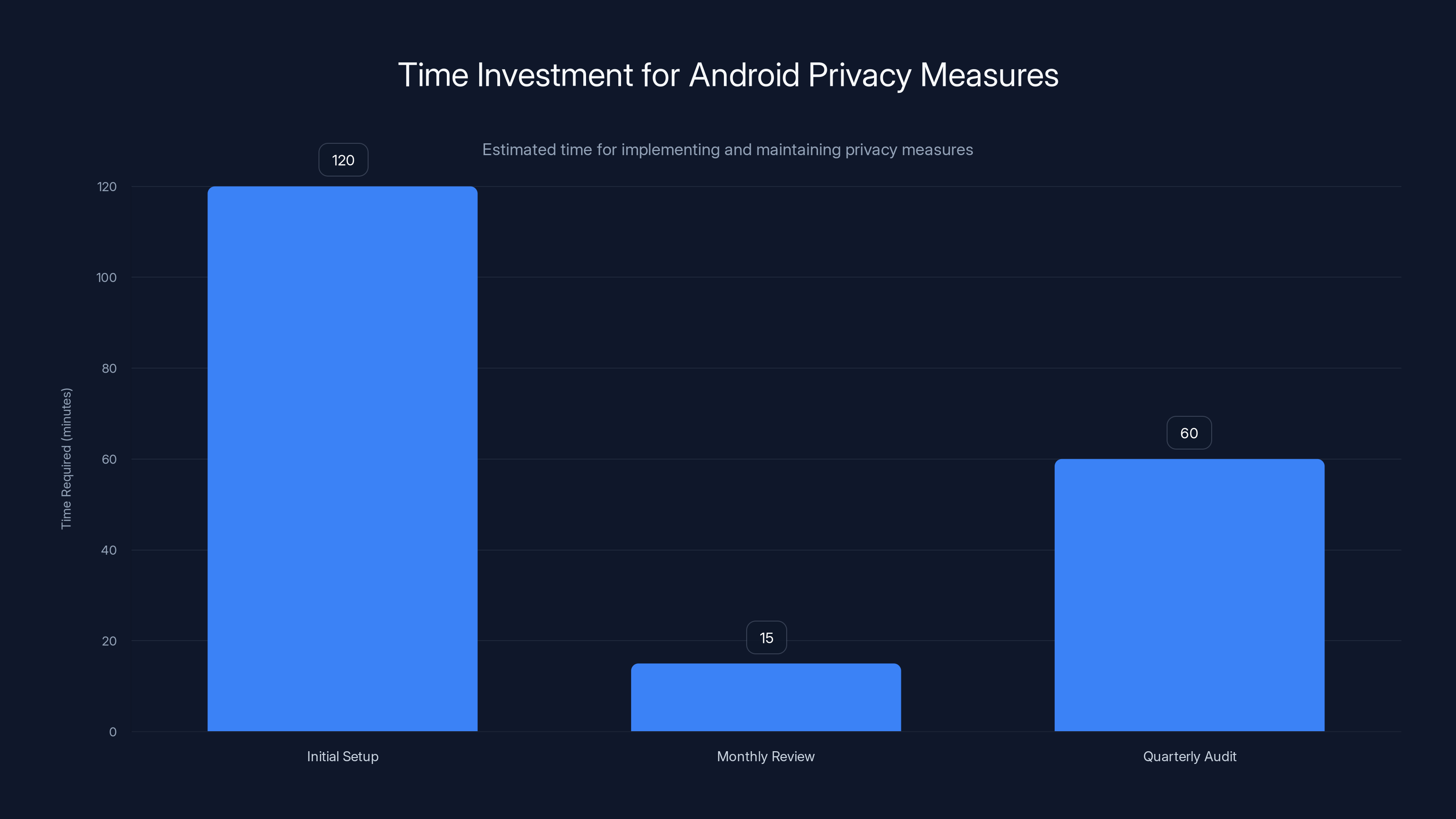
Initial setup of core privacy measures takes about 2 hours, with minimal ongoing maintenance of 15 minutes monthly and 1 hour quarterly. Estimated data.
Disable Location Sharing and Reduce Location Tracking
Location data is simultaneously one of the most valuable and most invasive data types. Advertisers pay enormous amounts for precise location history because it reveals your habits, income level, relationships, and routines.
Google, Apple, and dozens of apps collect location data continuously. Some do it obviously (Maps needs location to give you directions). Others do it secretly (why does your flashlight app need location?). Over time, they build a complete map of everywhere you go.
Start by disabling the most aggressive location tracking: Google's Location History. Go to Settings > Google > Manage your Google Account > Data & Privacy > Location Settings. Toggle off "Location History." This tells Google to stop recording a timeline of your physical location.
Then disable Timeline itself. Go to Settings > Google Maps > Settings > About > Location Services > Manage all > Location Services > Google Location Accuracy. Turn this off too. This prevents Google from requesting location from your phone specifically.
Next, review which apps have location permissions. Go to Settings > Privacy > Permissions > Location and look at both "Allow all the time" and "Allow only while using the app." Remove location permission from apps that don't need it. The default weather app? Sure. Your banking app? No.
Use approximate location for apps that need general position but not exact coordinates. In Android 12+, you can grant "approximate location" instead of "precise location." This gives an app your general area (within several kilometers) instead of your exact coordinates. Go to Settings > Apps > Permissions > Location and toggle "Approximate location" for specific apps.
Disable Google Timeline completely. Timeline is a chronological map of your physical movements. Even with Location History disabled, Timeline can still exist if you have Google Photos enabled or Google Calendar events with locations. Go to Google Maps, open Settings > Timeline and select "Delete all Location History." This purges the entire timeline.
Then go to Settings > Google > Manage your Google Account > Data & Privacy > Manage your Google Timeline and toggle the option to disable Timeline entirely.
For communication apps that offer location sharing features (Google Maps' location sharing, WhatsApp's live location), disable these by default. They should be opt-in for specific conversations, not always-on features.
One more advanced technique: on newer Android versions, you can randomly spoof your GPS location using privacy apps. This confuses apps that request location. Search for "Mock Location" or "Fake GPS" apps in the Play Store. These let you set a fake location that apps see instead of your real location. Set a random location in a major city near you and enable it when you don't want apps tracking your real position.

Control Cloud Backup and Automatic Data Synchronization
Cloud backups are convenient for disaster recovery. They're also a massive privacy vulnerability because they move your data to Google's servers where it can be accessed by Google, law enforcement with a warrant, or anyone who compromises your account.
Google automatically backs up certain data to your account if you enable it. This includes app data, contacts, calendar, SMS messages, settings, and more. Convenient for restoring a new phone? Yes. But it also means your entire digital life is copied to a remote server.
Go to Settings > System > Backup & Restore and review what's being backed up. You'll see options like "Backup to Google One," "Restore from Google account," and "Automatic System Update." If any of these are enabled and you value privacy, disable them.
Be specific about what you actually need backed up. If you care about recovering your contacts and calendar after a device failure, that's worth the privacy trade-off. If you don't, disable all backup.
Google Photos is another major culprit. Photos are automatically uploaded to Google's servers if you have Google Photos installed and enabled. Google can then analyze your photos (facial recognition, object detection, location analysis). If you must use Google Photos, go to Settings > Backup & Sync and disable it. Use another app like Proton Drive or Nextcloud instead.
Disable Nearby Share on your device. This feature uses Bluetooth and internet to transfer files between nearby devices. While convenient, it creates additional attack surface. Go to Settings > Connected devices > Nearby Share and toggle it off.
Review Continuity features that sync activity between devices. If you have a tablet, watch, or Chromebook, Android automatically syncs certain data. Go to Settings > Google > Manage your Google Account > Data & Privacy and review each service's settings. Disable syncing for apps you don't use across devices.
For sensitive files (financial documents, medical records, intimate photos), don't store them in Google Drive. Use end-to-end encrypted storage like Proton Drive or Tresorit. These services can't access your files even if law enforcement requests them because you hold the encryption keys.
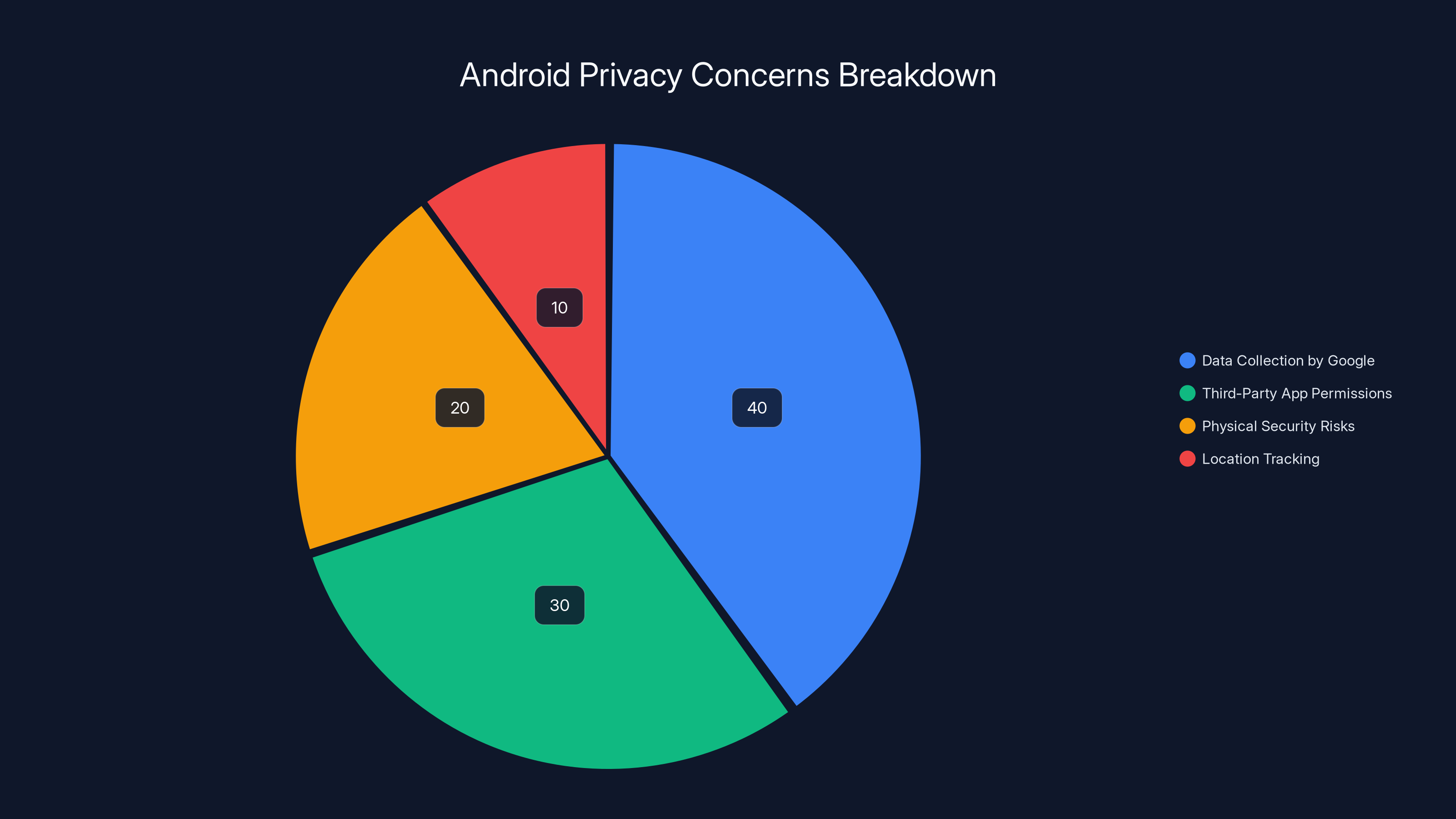
Estimated data shows that data collection by Google accounts for the largest share of privacy concerns, followed by third-party app permissions. Estimated data.
Review and Restrict Ad Personalization
Google's advertising business depends on knowing as much about you as possible. They use everything: your location history, search history, YouTube history, apps you use, websites you visit (through Google Analytics), your contacts, your calendar events, your purchase history. All of this feeds into their ad targeting system.
You can't opt out of advertising entirely on Android without extreme measures. But you can opt out of personalized advertising, which substantially reduces the profiling.
Go to Settings > Google > Manage your Google Account > Data & Privacy > Ads Settings. You'll see your Ad ID, a unique identifier Google uses to track you across apps. You can reset this ID, which severs the connection to your previous tracking history. Click "Reset" to get a new ID.
Then toggle "Personalized ads" off. With this disabled, you'll still see ads, but Google won't target them based on your location, search history, apps, or behavior. Ads become randomly selected instead of targeted. It's not perfect privacy, but it's substantially better.
Note that disabling personalized ads in Google's settings doesn't affect Facebook's ad targeting, TikTok's targeting, or any other ad network's targeting. You need to opt out of each platform individually.
For Facebook: go to Settings > Apps > Facebook > Permissions and disable Location, Camera, Microphone, Contacts, and Calendar. Then go to Settings > Google > Manage your Google Account > Data & Privacy > Manage apps you've authorized and revoke Facebook's access to your Google data.
For most other apps: find their privacy settings and look for ad personalization controls. Not all apps have them, which is another reason to avoid installing apps you don't actually use.
Use a DNS-level ad blocker on Android. Services like Adguard or NextDNS block ads at the DNS level, preventing them from loading entirely. This blocks ads in apps and websites. Install the app, enable DNS protection, and ads are blocked system-wide. This is more effective than browser-based ad blockers.

Secure Your Device Against Physical Access
You can have perfect encryption and privacy settings, but if someone steals your phone or gains physical access, they can bypass everything given enough time and expertise.
The first line of defense is a strong lock screen. We covered biometric authentication earlier. But also set a strong PIN as a fallback. Go to Settings > Security and Privacy > PIN to set a PIN of at least 8 digits. Don't use obvious sequences (1234, 5678, your birth year, etc.). Use a random sequence like 47382916.
For additional security, enable Timeout Lock. Go to Settings > Security > Lock screen settings > Lock after 30 seconds of inactivity. This ensures your phone is locked quickly if you set it down. If someone grabs it, they have only the time it took you to lock it.
Disable Lock Screen Information. By default, Android shows notifications on your lock screen. This leaks information before someone even unlocks your phone. Go to Settings > Notifications and toggle "Show notifications on lock screen" off. Now notifications only appear after unlock.
Disable Emergency SOS. On modern Android phones, a quick press of volume up + power button triggers Emergency SOS. An attacker can trigger this without unlocking your phone to access emergency calling. Go to Settings > Advanced features and disable Emergency SOS if available on your device.
Enhance security further by disabling USB Debugging. This allows computers to access your device via USB cable. An attacker with USB access and USB debugging enabled can pull files, install apps, and modify settings. Go to Settings > Developer Options and toggle off USB Debugging.
If you're developing apps, you need USB debugging. But for normal users, it's an unnecessary security hole.
Enable Full Disk Encryption. Modern Android devices encrypt data by default, but verify this is enabled. Go to Settings > Security > Encryption. Your device should show something like "Encrypted" or "Full disk encryption enabled." If you see "Not encrypted," enable it immediately.
Disable Find My Mobile or Find My Device if you don't plan to use it. These services let you remotely wipe your device if lost, which is good. But they also require cloud-stored credentials. If your account is compromised, someone could potentially remotely wipe your device maliciously. Only enable if you actively use it.
For paranoid users: enable Secure Folder (Samsung phones) or Private Space (Google Pixel phones). These create encrypted compartments for sensitive apps and files. Even if someone unlocks your phone, they can't access the secure folder without a separate PIN. Put banking apps, password managers, and sensitive photos here.
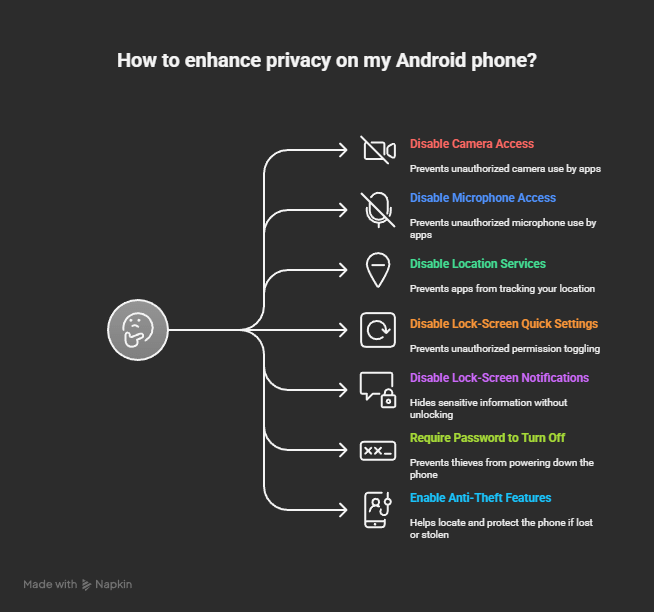
Monitor and Control Smart Device Integration
Android connects to numerous smart devices: watches, headphones, speakers, cars, and smart home devices. Each of these connections is another potential privacy vector.
Start with smartwatches. If you wear a Wear OS watch, it mirrors notifications, tracks your location, and monitors your health data. Review Wear OS app permissions: go to Wear OS app > Settings > Permissions and disable unnecessary permissions. Your watch doesn't need microphone access unless you use voice commands.
Disable Location on your watch unless you actively use it. Go to Watch Settings > Privacy and toggle Location off. Your watch is connected to your phone via Bluetooth, so your phone knows where you are anyway.
Smart speakers (Google Home, Echo) are always listening for wake words. While Amazon and Google claim they don't record until the wake word is spoken, these devices have been caught recording without permission multiple times. Consider not having them in your bedroom, bathroom, or other private areas.
If you have a smart speaker, go to its app (Google Home or Alexa) and review the microphone permissions. You can mute the microphone physically on the device. Do this when you're not actively using it.
Disable Activity Recording on smart speakers. Go to the device's app > Settings and toggle off "Record and Save Activities" or similar. This prevents a record of what you asked the device to do.
Disconnect Account Linking. Smart speakers often link to other services (Spotify, Gmail, Calendar, etc.). Go to the app > Settings > Linked Services and disconnect anything you don't actively use. Each linked service is another company with access to some of your data.
For Android Auto in your car: disable location sharing when not needed. Go to your phone's Settings > Apps > Android Auto > Permissions and toggle Location off. Your car doesn't need to know your home address. Android Auto also logs driving data. If you care about privacy, use a dumb car interface instead.
Bluetooth headphones and speakers connect without encryption by default. Someone nearby can potentially listen to the Bluetooth traffic and determine what you're listening to. For sensitive listening (therapy sessions, private calls), use wired headphones. For normal use, wireless is fine.

Implement a Security and Privacy Maintenance Routine
Security isn't a one-time setup. Threats evolve, new vulnerabilities are discovered, new privacy-invasive features are added to Android, and app permissions creep outward over time. A successful privacy strategy requires ongoing maintenance.
Set a monthly privacy review. Block one hour per month (the first Sunday, for example) to review your privacy settings. Go through Settings > Privacy > Privacy Dashboard and check what apps accessed sensitive data. Revoke permissions from apps that seem suspicious. Review your Google account security in Settings > Google > Manage your Google Account > Security.
Set a quarterly major audit. Every 3 months, perform a comprehensive review. Go through Settings > Apps > App Permissions by category and verify each app still needs the permissions you granted. Check Settings > Google > Manage your Google Account > Data & Privacy for any new data collection options you should disable. Review which apps you still actively use and uninstall the rest.
Update Android regularly when updates are released. Go to Settings > System > System Update and check for updates. Security updates patch vulnerabilities that attackers exploit. While Android updates sometimes add new privacy-invasive features, the security benefits outweigh the privacy downsides most of the time.
Update all your apps regularly as well. Apps receive security patches and sometimes add better privacy controls. Go to Play Store > Profile icon > Manage apps and devices > Updates and install available updates. Consider enabling "Auto-update" for most apps, though it's less convenient for apps you actively use frequently.
Use an app that shows permission changes when apps are updated. Some privacy apps flag when an update adds new permission requests. App names like Permissions Manager or Permission Monitor can help identify when apps request new permissions you hadn't granted before.
Subscribe to privacy newsletters. Follow privacy advocates like Electronic Frontier Foundation (EFF) or privacy researchers who highlight concerning new trends in data collection and privacy policies. Being informed about emerging threats helps you respond proactively instead of reactively.
Consider using Android Privacy Guard or similar privacy management apps that provide graphical interfaces for managing permissions. These apps make privacy management less technical and easier to maintain.
For maximum privacy maintenance, consider investing in custom Android ROMs like LineageOS, which remove Google services entirely and add extra privacy controls. This is technically complex but provides the highest level of privacy for Android users willing to sacrifice convenience.
Identify and Remove Malicious Apps
Malware is real on Android, though Google's security has substantially reduced the risk compared to years past. An estimated 1% of Android users encounter malware-infected apps annually, which sounds small until you realize that's 30 million people.
Malware typically works by requesting extensive permissions and then misusing them. A fake antivirus app requests permission to access your files, then steals sensitive documents. A game requests microphone access and records your conversations. A utility requests SMS access and sells your text messages to marketers.
The first detection method is simple: be suspicious of apps requesting permissions they don't logically need. A flashlight app doesn't need location or contacts. A calculator doesn't need camera access. A note app doesn't need the ability to send SMS. If an app's permission requests seem excessive, don't install it.
Before installing any app, read the reviews in the Play Store carefully. Look for comments about excessive permissions, unexpected behavior, or crashes. If dozens of people say the app is requesting strange permissions, believe them.
Check the developer of apps before installing. Does the developer have other legitimate apps? Do they have a professional website? Developing legitimate apps requires expertise, and most malware developers are lazy. Apps by unknown developers with no online presence are higher risk than apps by established companies.
Use Android's built-in security scanning. Go to Settings > Security > Google Play Protect. Ensure "Scan apps with Play Protect" is toggled on. Google continuously scans apps in the Play Store and on your device for known malware. This isn't foolproof but catches most obvious threats.
Use a dedicated antivirus app if you're paranoid. Apps like Kaspersky, Norton, or AVG provide additional malware detection. Note that antivirus apps are less necessary than they used to be, but they add a layer of protection for less cautious users. Just don't install a free antivirus as they often have their own privacy issues.
Monitor Data Usage. Go to Settings > Network & Internet > Data Usage. Look for apps consuming unexpectedly large amounts of data. Malware sometimes exfiltrates data constantly. If a simple app is using gigabytes of data monthly, that's suspicious.
Check Battery Usage. Go to Settings > Battery. Apps running in the background consuming abnormal battery might be malicious. Legitimate apps run efficiently. Malware often runs background processes constantly to steal data or send ads.
Uninstall apps you don't use. The attack surface of your phone is proportional to the number of apps you've installed. Each app is a potential vulnerability. Uninstall anything you haven't used in 3 months. Go to Settings > Apps and uninstall from the app's page or long-press and select uninstall.

When Privacy Conflicts With Functionality
There's an honest tension between privacy and convenience. Disabling all location tracking makes navigation impossible. Disabling all data backup makes device recovery impossible. Using encrypted messaging that doesn't sync across devices creates usability problems.
You don't need to choose an extreme. Privacy and usability exist on a spectrum, and the right place for you depends on your threat model.
If you're a normal person in a developed country with no reason to believe anyone is specifically targeting you, you can afford to prioritize convenience more heavily. Enable Google Photos. Use Gmail. Let Google keep your location history. The privacy trade-off is acceptable.
If you're a journalist, activist, politician, or anyone else who might be targeted by adversaries with resources, you need to prioritize privacy heavily. Use encrypted messaging exclusively. Disable all cloud backups. Use a custom ROM. Use a VPN. Accept the inconvenience.
Most people fall in the middle. You want reasonable privacy without ridiculous inconvenience. The advice in this guide aims for that balance. Implement the core measures (strong authentication, app permission controls, disabled ad personalization, encrypted messaging) and accept that this prevents some convenient features from working.
One final principle: use different tools for different threat levels. Your banking app lives in a secure folder with maximum protection. Your social media apps get fewer permissions. Your utility apps get minimal trust. Compartmentalize based on what data each app needs.
Future Privacy Features Coming to Android
Google is working on several privacy features that should land in future Android versions. These offer hope that privacy on Android will continue improving.
Generative AI Privacy Protections: Google is building local AI processing directly into Android so that some tasks don't require sending data to Google's servers. Summarizing emails, generating images, and other AI features could eventually run on-device, keeping your data off remote servers.
Enhanced Data Transparency: Future versions might provide even more granular visibility into what data apps access and when. Imagine seeing real-time notifications every single time an app accesses location or contacts. This transparency alone would pressure developers to request fewer permissions.
Hardware Security Improvements: Modern Android devices use the Titan M2 security coprocessor (Pixel devices) and Knox security platform (Samsung devices) to isolate sensitive data. Future improvements might make even stolen devices unable to extract encrypted data.
Privacy Dashboards for Apps: Rather than showing users which apps accessed sensitive data, future dashboards might show the reverse: for a specific app, show what data it has accessed historically. This would help identify misbehaving apps more easily.
Stronger Encryption Standards: As computing power increases and encryption breaks, newer standards will become standard. Quantum-resistant encryption is being researched and will eventually be deployed to protect against future decryption threats.
The point is that Android's privacy capabilities are evolving. What's hard today will be easy in future versions. Privacy won't solve itself automatically, but the trend is toward better privacy by default.
FAQ
What is Android privacy and why does it matter?
Android privacy refers to protecting your personal data from unauthorized access, whether by hackers, corporations, governments, or people with physical access to your device. It matters because your phone contains intimate information: your location history, private conversations, financial details, health records, and more. Without privacy protections, this information can be misused for surveillance, identity theft, manipulation, or embarrassment.
How can I tell if my Android device is secure?
Go to Settings > Security to check if your device is up-to-date on security patches. Look for "Security update" or "Patch level" showing a date within the last 3 months. Check Settings > Privacy > Permission Manager to ensure apps don't have unnecessary permissions. Review Settings > Google > Manage your Google Account > Security for any warning signs. If you see unknown devices in your trusted devices list or security alerts, your device might be compromised.
What's the difference between a VPN and a proxy?
A VPN encrypts all your device's traffic and routes it through remote servers, masking your IP address from websites and ISPs. A proxy is lighter-weight, typically handling only web traffic, without encryption. VPNs provide stronger privacy and security but impact performance more noticeably. For Android, use a VPN rather than a proxy for comprehensive protection.
Can Google read my encrypted messages if I use WhatsApp or Signal?
No, Google cannot read your encrypted messages on WhatsApp or Signal because the encryption happens on your device. Only the recipient can decrypt your messages. Even WhatsApp and Signal's servers cannot read your messages because they don't possess the decryption keys. However, they can see metadata like who you're communicating with and when.
Should I disable all location services if I care about privacy?
Disabling location services entirely creates inconvenience without proportional privacy gains if you trust Google with your location data. A better approach is keeping location off by default but enabling it selectively when you need maps or navigation. Alternatively, use approximate location instead of precise location for most apps. This balances privacy and functionality.
What should I do if I think my Android device has been hacked?
First, change your Google account password from a different device and enable two-factor authentication. Go to your Google account security settings and review trusted devices, removing unknown ones. Factory reset your Android phone (Settings > System > Reset Options > Erase all data) to remove any malware. Restore from a backup you know was created before the potential compromise. If you're in danger from sophisticated attackers, physically destroy the device instead of resetting it.
Are custom Android ROMs like LineageOS more private than Google's Android?
Yes, significantly. Custom ROMs like LineageOS remove Google services entirely and add features designed for privacy like restricted background access and encrypted app containers. However, they require technical expertise to install, don't receive updates as quickly as manufacturer Android, and can cause app compatibility issues. They're appropriate for privacy-focused technical users but not for most people.
Is biometric authentication on Android actually secure?
Biometric authentication (fingerprint and face recognition) is substantially more secure than PIN codes for everyday use. However, it's theoretically vulnerable to sophisticated attacks like high-quality face masks or fingerprint lifts in a forensic investigation. For absolute maximum security, use a PIN or passkey instead. For practical everyday security, biometric is excellent and should be your primary method.
Conclusion
Android privacy requires deliberate action, but it's entirely achievable. You don't need to live in a cave rejecting all technology. You don't need to become a security expert. You just need to understand your threats and implement reasonable protections.
The core measures take maybe two hours total: enabling strong authentication, reviewing app permissions, disabling location tracking, securing your Google account, and switching to encrypted messaging. After that, maintenance is minimal. Monthly reviews take 15 minutes. Quarterly audits take an hour.
Start today with these priorities:
- Enable fingerprint authentication and set a strong PIN
- Go to Settings > Privacy > Permission Manager and review app permissions
- Disable location history in your Google account
- Switch to Signal or WhatsApp for sensitive conversations
- Disable ad personalization in your Google account settings
These five actions prevent the majority of common privacy violations. Do these today, and you've solved 80% of the problem.
From there, add complexity based on your threat model. If you value privacy enough to sacrifice convenience, implement VPNs, disable cloud backups, use custom ROMs, and review settings monthly. If you just want reasonable privacy without hassle, the five core actions are sufficient.
Privacy isn't all-or-nothing. It's a spectrum. Find the balance that makes sense for you personally, not some imagined worst-case scenario. Implement what you can maintain consistently. Security that you abandon is worse than no security at all.
Your phone contains your life. Protect it accordingly.
Key Takeaways
- Enable biometric authentication and strong PIN codes to prevent unauthorized device access through either online or physical means
- Systematically review app permissions in Settings > Privacy > Permissions and disable location, camera, and microphone access for apps that don't legitimately need them
- Disable Google's location history, ad personalization, and web activity tracking in your Google account security settings to reduce profiling
- Use end-to-end encrypted messaging apps like Signal or WhatsApp for conversations you want to keep private from Google and other companies
- Implement a monthly privacy review routine checking which apps recently accessed sensitive data through Android's Privacy Dashboard to catch unauthorized behavior early
Related Articles
- Google's $135M Android Data Settlement: What You Need to Know [2025]
- Google's $135M Data Collection Settlement Explained [2025]
- How to Set Up an AirTag: Complete Step-by-Step Guide [2025]
- India's Supreme Court vs WhatsApp: Privacy Rights Under Fire [2025]
- X's Paris HQ Raided by French Prosecutors: What It Means [2025]
- StationPC PocketCloud Portable NAS Review: Complete Guide [2025]
![Android Privacy Tips: Protect Your Device From Prying Eyes [2025]](https://tryrunable.com/blog/android-privacy-tips-protect-your-device-from-prying-eyes-20/image-1-1770230547698.jpg)



