ATM Jackpotting Attacks: The Physical Threat That's Draining Millions [2025]
It's 2 AM at a convenience store in a major US city. A van pulls up. Someone walks to the ATM with nothing but a screwdriver, a hard drive, and a flash of a generic key. Thirty minutes later, they're gone—and so is $10,000 in cash that the ATM can't explain.
This isn't a heist movie. It's ATM jackpotting, and it's exploding.
The FBI has been sounding the alarm for months now. Criminals have stolen over $20 million through physical ATM breaches in recent years, and 2025 is shaping up to be the worst year on record. Out of 1,900 documented cases since 2020, roughly 700 of them happened in 2025 alone. That's 37% of all incidents in a single year, as reported by SecurityWeek.
Here's what makes jackpotting different from every other type of ATM fraud you've heard about. It's not some elaborate card cloning scheme or a sophisticated digital attack from halfway around the world. It's low-tech meets high-tech. It's someone physically breaking into a machine, installing malware, and forcing it to hand over cash without authorization.
And the scary part? It's getting easier.
Most people think ATM security is untouchable. There are cameras everywhere, guards monitoring transactions, encryption protecting your card data. But jackpotting exploits a completely different vulnerability—the physical machine itself. The attackers aren't trying to steal your money. They're stealing the bank's money. And unlike traditional fraud, you might never even notice it happened.
In this guide, we're breaking down exactly what ATM jackpotting is, how criminals pull it off, why it's accelerating, and what you actually need to know to stay safe. We'll cover the technical side, the real-world tactics, the financial impact, and the defenses that actually work.
TL; DR
- **20 million through ATM jackpotting since 2020, with 700 incidents reported in 2025 alone, according to BleepingComputer.
- Generic keys are the problem: Attackers use widely available generic keys to open ATM fascias without triggering alarms or leaving evidence, as highlighted by The Record.
- Ploutus malware is the weapon: The malware bypasses XFS authorization entirely, forcing ATMs to dispense cash on demand, as detailed by The Hacker News.
- Banks are the victims: Customer accounts and funds remain protected because attackers never access card data or account numbers.
- Detection is rare: Many jackpotting attacks go unnoticed for days or weeks, meaning the actual loss could be significantly higher than reported.

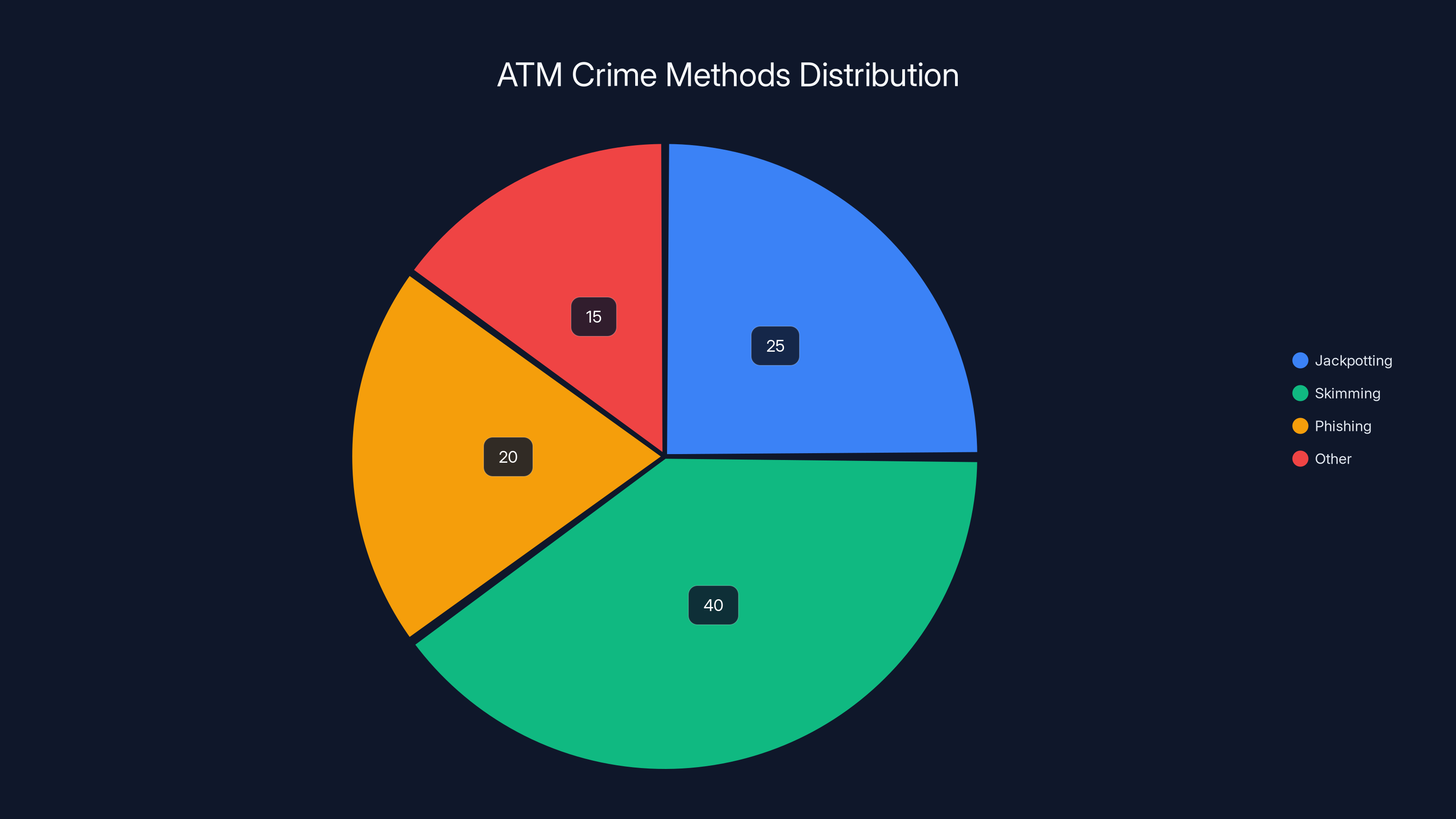
Jackpotting accounts for 25% of ATM crimes, focusing on direct cash theft, while skimming is more common at 40%, targeting card data. Estimated data.
What Exactly Is ATM Jackpotting?
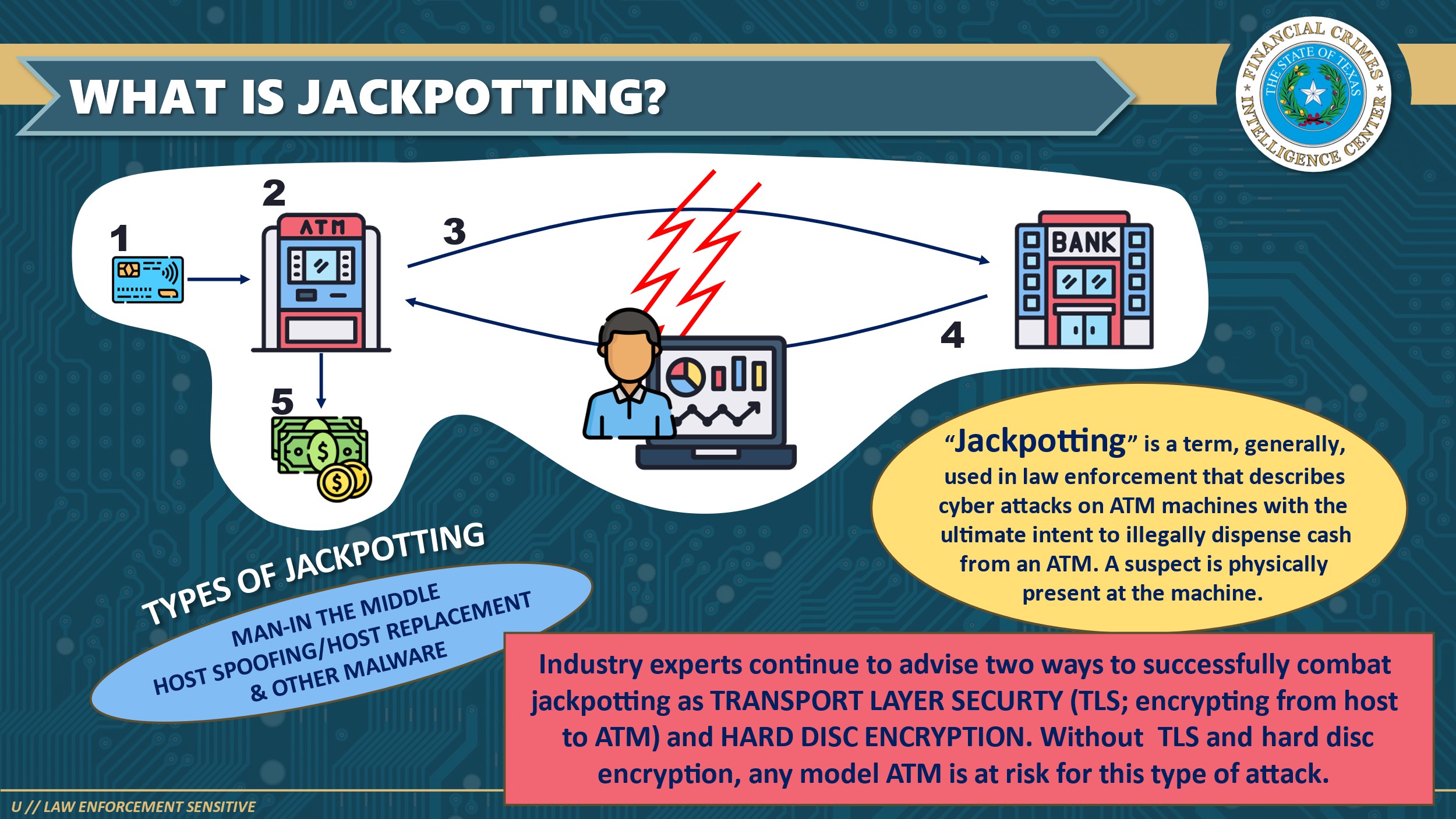
ATM jackpotting isn't a new concept, but it's been weaponized in ways that weren't possible five years ago. At its core, jackpotting is the physical compromise of an ATM machine to force it to dispense cash without authorization.
The attacker's goal is straightforward: access the ATM's internal hardware, install malware, and command the machine to dump its cash. But the execution is what makes it dangerous.
Unlike skimming attacks that rely on capturing card data or phishing schemes that target login credentials, jackpotting requires direct physical access to the machine. The criminal needs to open the ATM's protective casing, access the hard drive, and deploy code that can intercept and override the normal transaction flow.
What changed in recent years is the availability of the tools needed to do this. Generic keys that unlock ATM fascias are sold on the dark web for under $100. Ploutus malware—the primary tool used in these attacks—is readily available in criminal forums. The knowledge needed to execute an attack has become commoditized.
The FBI's warning specifically highlights the use of these generic keys. An attacker can walk up to virtually any ATM from certain manufacturers and open the face panel in seconds. No drilling required. No alarms triggered. No evidence left behind, as noted by The Register.
Once inside, the attacker has two primary attack vectors. First, they can remove the ATM's hard drive, infect it with malware on an external device, and reinstall it. Second, they can replace the original hard drive with a pre-loaded one that already contains the malicious code. Both approaches achieve the same result: an ATM running compromised firmware that obeys unauthorized commands.
What makes jackpotting particularly insidious is the targeting. These aren't random attacks. Criminal networks scout ATM locations, identify models with known vulnerabilities, observe cash replenishment schedules, and time their attacks accordingly. They hit machines in areas with minimal security, grab the cash, and move on before anyone realizes what happened.
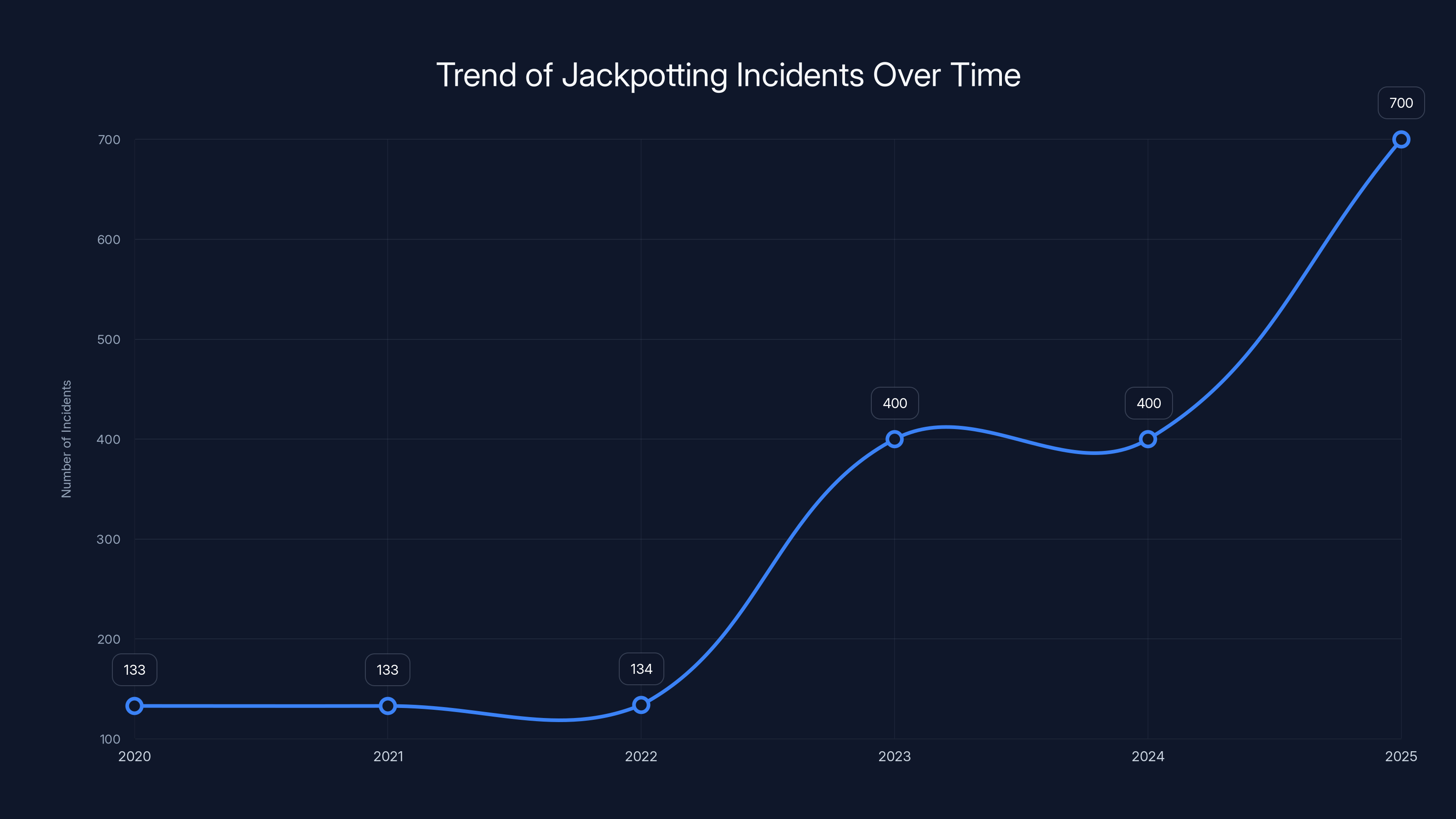
Reported jackpotting incidents have increased significantly, with a sharp rise in 2025, indicating a growing trend. Estimated data based on reported figures.
How the Attack Works: A Technical Breakdown
Understanding how jackpotting actually works requires understanding the architecture of modern ATMs. These machines aren't simple vending machines. They're specialized computers running proprietary operating systems, communicating with banking networks, and managing millions of dollars in transactions daily.
Every ATM uses an industry-standard API called XFS (e Xtensions for Financial Services). XFS is the common language that ATM software uses to communicate with the hardware components—the card reader, the cash dispenser, the display, the keypad. It's designed to be open and flexible, allowing different manufacturers and software developers to build compatible systems.
But flexibility creates vulnerability.
When you insert your card and request cash, the XFS layer handles the request. It talks to the main ATM application, which talks to the bank's backend systems for authorization. The bank approves the transaction. The XFS layer then instructs the cash dispenser to release bills. It's a multi-step process with multiple authorization checks at each stage.
Ploutus malware short-circuits this entire chain.
Once installed, Ploutus intercepts the normal command flow and injects its own XFS commands directly. It doesn't need your card. It doesn't need your PIN. It doesn't need authorization from your bank. It simply tells the ATM's cash dispenser to open and start spitting out money.
Here's how the FBI describes the mechanism: "When a legitimate transaction occurs, the ATM application sends instructions through XFS for bank authorization. If a threat actor can issue their own commands to XFS, they can bypass bank authorization entirely and instruct the ATM to dispense cash on demand," as detailed in The Record.
The malware doesn't just grab
But there's a critical detail that most people miss: the attack requires physical access. The attacker needs to open the machine, access the hard drive, and install the malware. This isn't a remote attack. It's not happening from a server farm in Russia. It's happening in person, in real time, at a physical location.
The Generic Key Problem
The generic key issue is what's driving the explosion in jackpotting attacks. For decades, ATM manufacturers relied on proprietary keys to secure the machine fascia. A bank employee would have the key, and the ATM was considered physically secure.
Then someone realized that many ATM manufacturers used the same key designs or similar designs across multiple models and years. Security researchers discovered that generic keys—keys that worked on multiple ATM models from different manufacturers—could be obtained.
These keys aren't something you need to be a master locksmith to use. They work like any other key. You insert it, turn it, and the fascia opens. No drilling. No cutting. No evidence. An attacker can open an ATM in under 30 seconds without drawing suspicion.
The availability of generic keys on the dark web has fundamentally changed the cost-benefit analysis of jackpotting. Instead of requiring specialized tools and expertise, an attack now requires a
Bank security teams are aware of this. Many banks have added supplementary locks or changed ATM models to address the generic key vulnerability. But there are thousands of ATMs still in service that use the older, vulnerable designs.
The Malware Delivery Vector
Once the attacker has access to the hard drive, they need to get malware onto it. This can happen in two ways.
First, they can remove the hard drive, take it to a location where they have a laptop and tools, infect it with Ploutus or a variant, and reinstall it. This is the more careful approach. It reduces the time spent at the ATM location and allows the attacker to test the malware before reinstalling it.
Second, they can come prepared with a hard drive that's already preloaded with Ploutus malware. They simply swap the original drive for the infected one, close up the machine, and leave. This is faster but riskier if the malware has bugs or if the hardware doesn't match expectations.
Ploutus variants are the primary malware used in these attacks. The malware has been around since at least 2014, and different versions have been discovered targeting different ATM models and operating systems. Some variants are designed for ATMs running Windows XP. Others target more modern systems. The malware is modular, allowing criminals to customize it for specific hardware configurations.
Once Ploutus is running, the attacker uses a specialized PIN or command sequence to interface with the malware and issue commands. In some cases, they use a physical device or USB stick to inject commands. In others, the malware includes a basic interface accessible through the ATM's emergency keypad.
The malware then stays on the machine until it's detected and removed. In some cases, this has taken weeks. Banks don't monitor their ATMs in real time for hardware-level compromises. If an ATM isn't reporting abnormal dispensing activity, it can look normal to the banking network even if it's been compromised.

The Ploutus Malware Variant: The Core Weapon
Ploutus is the malware that makes jackpotting possible. Without it, even if an attacker had physical access to an ATM, they'd have to understand the proprietary code and rebuild significant portions of the software. Ploutus eliminates that requirement.
The malware's name comes from the Greek god of wealth, and its design is elegant in its simplicity. It doesn't need to be sophisticated. It just needs to intercept XFS calls and issue unauthorized dispensing commands.
Different variants of Ploutus have emerged since the original discovery:
Ploutus. A was first documented around 2014 and targeted ATMs running Windows XP. It was relatively unsophisticated, requiring direct interaction through the ATM's keypad or an external device.
Ploutus. B and Ploutus. C were more modular and targeted different ATM models and configurations. These variants added features like time-based activation, remote communication capabilities, and better obfuscation.
Ploutus. D represented a significant evolution, including network communication features that allowed remote operators to trigger dispensing commands. This variant was particularly dangerous because an attacker didn't have to be physically present at the machine during the attack.
In 2025, security researchers have identified multiple new variants that incorporate anti-analysis features, making them harder to detect and reverse-engineer. Some variants hide their malicious functionality in legitimate system processes. Others use encryption to hide the XFS commands being issued.
The malware's primary functionality remains constant: intercept the XFS API, listen for commands, and issue dispensing instructions to the cash dispenser module. The sophistication has increased, but the core concept hasn't changed.
What's particularly worrying is the commoditization of Ploutus variants. Criminal forums sell customized versions tailored to specific ATM models. This means even attackers with minimal technical expertise can purchase a ready-to-use variant that will work on their target machine.
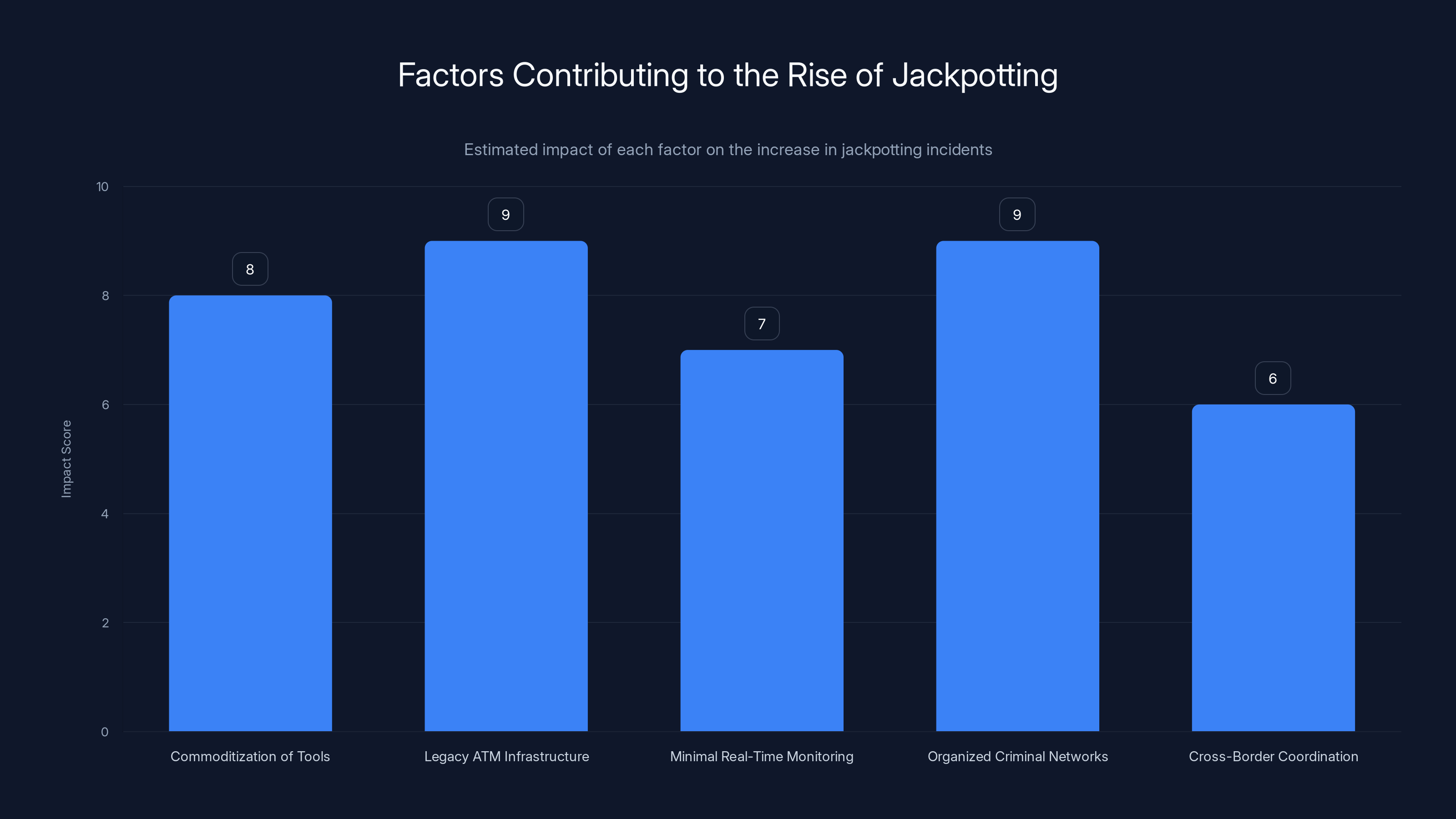
The rise in jackpotting incidents is significantly influenced by legacy ATM infrastructure and organized criminal networks, each scoring 9 out of 10 in impact. Estimated data.
The Numbers: How Much Money Are We Talking About?
The FBI's public statements on jackpotting losses have been consistent but alarming. Over
But here's the critical asterisk: that number is only based on reported incidents. Many jackpotting attacks go undetected for days or weeks. Some ATMs don't get checked regularly enough to notice the cash shortage immediately. Some banks don't report incidents if they believe it reflects poorly on their security. The actual losses could be significantly higher.
The 2025 numbers are particularly striking. Out of approximately 1,900 documented jackpotting incidents since 2020, around 700 occurred in 2025. That's more than one-third of all incidents in a single year. The trend is accelerating.
Breaking this down further:
- 2020-2022: Roughly 400 total incidents (averaging 133 per year)
- 2023-2024: Roughly 800 total incidents (averaging 400 per year)
- 2025: 700 incidents (on pace for 700+ by year's end)
The trajectory is clear. Jackpotting attacks are doubling year-over-year in many regions.
As for the per-incident losses, they vary significantly based on the ATM model and how much cash was in the machine at the time of the attack. A small convenience store ATM might hold
When you multiply that by 700 incidents in a single year, you're looking at potential losses in the

Geographic and Sectoral Hotspots
Jackpotting attacks aren't evenly distributed across the US. Certain regions and sectors are hit disproportionately harder than others.
The FBI has documented significant clustering in metropolitan areas with major financial hubs. Cities like New York, Los Angeles, Chicago, and Miami have experienced higher concentrations of attacks. This makes sense from a criminal perspective: more ATMs, more cash, more places to blend in.
But there are also hotspots in smaller cities and rural areas where ATMs are less frequently monitored. A convenience store in a smaller town might only have someone check the ATM weekly or bi-weekly. An attacker hitting that machine could have days before the shortage is noticed.
Certain industries are also disproportionately targeted. Casino ATMs, which typically hold larger amounts of cash, are attractive targets. ATMs in truck stops and gas stations have also seen elevated attack rates. These locations often operate 24/7 with minimal security presence, making them ideal for jackpotting.
Convenience stores and grocery stores with independent ATMs (not connected to a larger banking network) are particularly vulnerable. These machines are often managed by third-party ATM operators who may have less sophisticated monitoring and security protocols.
The geographic pattern suggests that jackpotting is being executed by organized criminal networks with localized knowledge and resources. They're not random attacks. They're targeted, planned, and executed by individuals with knowledge of ATM locations, cash schedules, and security gaps.
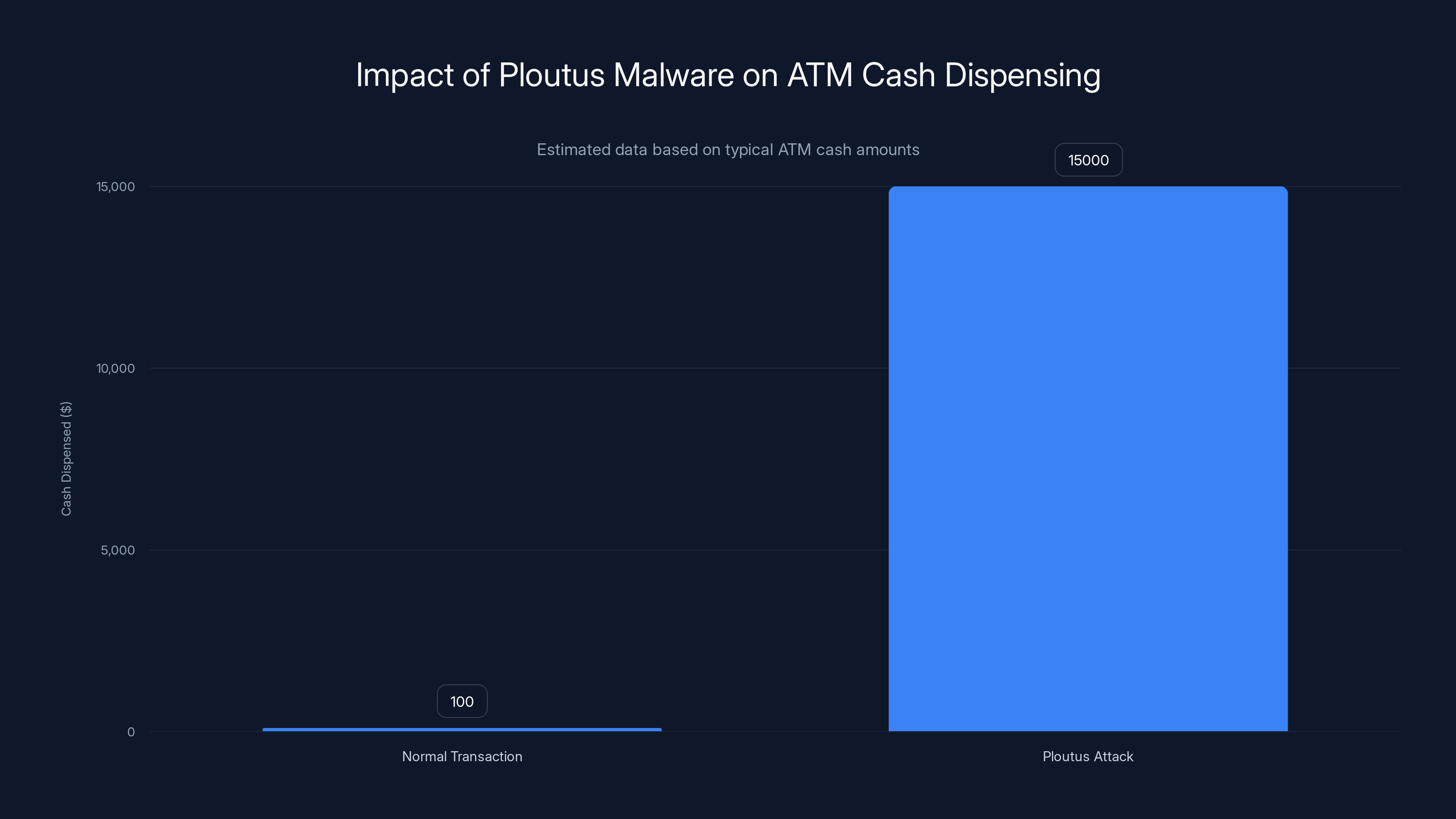
Ploutus malware can force an ATM to dispense its entire cash cassette, potentially releasing
Why Now? The Perfect Storm of Factors
Jackpotting isn't new, but the explosion in 2025 didn't happen randomly. Several factors have converged to create an environment where jackpotting thrives.
Factor 1: The Commoditization of Tools
Generic keys and Ploutus variants are now accessible to anyone with internet access and cryptocurrency. The barrier to entry has collapsed. Ten years ago, executing a jackpotting attack required specialized knowledge and custom tools. Today, it requires
Factor 2: Legacy ATM Infrastructure
Many ATMs in service today were deployed 10-15 years ago or longer. They run outdated operating systems, use vulnerable authentication mechanisms, and haven't received the security hardening that modern systems have. Banks have been slow to replace the entire fleet, partly due to cost and partly due to complacency. This creates a massive vulnerable attack surface.
Factor 3: Minimal Real-Time Monitoring
Banks monitor their ATM networks for transaction anomalies and connectivity issues, but they don't monitor for hardware-level compromises in real time. If an ATM is dispensing cash on demand but reporting normal operations to the backend, the bank's systems might not flag anything suspicious. By the time a physical inspection happens and the compromise is discovered, days or weeks may have passed.
Factor 4: Organized Criminal Networks
Jackpotting has transitioned from being the work of independent hackers to being coordinated by organized criminal networks. These networks have resources to scout locations, coordinate multiple simultaneous attacks, fence cash, and operate with relative impunity. They treat jackpotting as a business model, not a one-off heist.
Factor 5: Cross-Border Coordination
There's evidence that some jackpotting networks include international actors. The tools and malware are developed in certain countries, while the physical attacks are executed by different groups in other countries. This geographical distribution makes law enforcement response more challenging.
Factor 6: Limited Enforcement
While the FBI is actively investigating jackpotting cases, prosecutions have been relatively rare. Many attackers operate in ways that make attribution difficult. The use of cryptocurrency for purchasing tools and money laundering through ATM networks further complicates enforcement.
Customer Safety: The Good News and the Reality Check
Here's something important to understand about jackpotting: it doesn't directly threaten your personal finances. At all.
Jackpotting attacks target the bank's cash supply, not customer account balances. The attacker never accesses your card data, your PIN, or your account information. They're stealing the bank's money, not yours.
This is fundamentally different from skimming, phishing, or account takeover attacks. When a skimmer steals your card number, your bank account is at risk. When a phisher gets your credentials, your money is at risk. But when a criminal jackpots an ATM, only the bank's cash is at risk.
The secondary effects are more interesting to consider. If ATM networks become less secure, banks might reduce the cash available at certain locations or increase security measures that affect user experience. You might encounter longer waits at ATMs due to enhanced verification procedures. You might see fewer ATMs in certain areas as banks consolidate operations.
But your actual account balance is protected by FDIC insurance and the banking system's authorization and audit procedures. Even if an ATM is compromised, the bank can trace what happened through its logs and recover the losses without charging customers.
That said, there are precautions you should take to minimize your exposure to ATM-related risks:
1. Use ATMs in secure locations: Prioritize ATMs inside bank branches, secured areas, or well-lit, heavily monitored locations. Avoid ATMs in isolated areas or in locations with minimal security presence.
2. Inspect the machine before use: Look for signs of physical tampering, loose panels, unfamiliar stickers, or anything that seems out of place. If something seems off, don't use that ATM.
3. Cover the keypad: When entering your PIN, cover the keypad with your hand. Modern ATMs can have hidden cameras or overlay devices, and covering the keypad is a basic precaution.
4. Limit cash withdrawals: The less cash you carry, the less exposure you have to loss or theft. Consider using debit cards or mobile payment systems instead of cash when possible.
5. Monitor your accounts regularly: Check your bank account and credit regularly for unauthorized activity. While jackpotting doesn't directly threaten you, other ATM-related fraud might.
6. Use your bank's ATM network: Your own bank's ATM network is typically better secured and monitored than third-party ATMs in convenience stores or other locations. Expect to pay out-of-network fees if necessary.
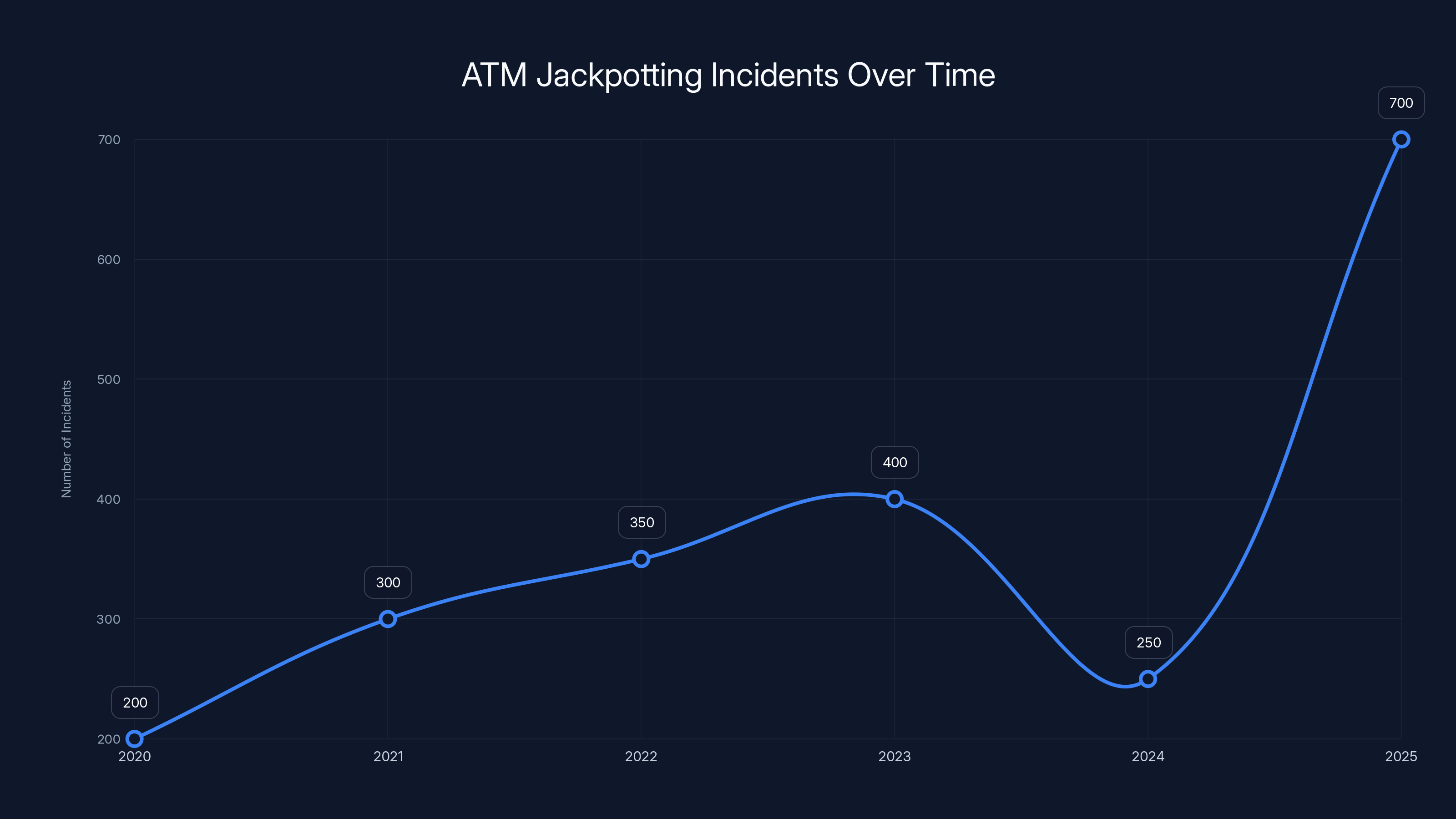
ATM jackpotting incidents have surged in 2025, accounting for 37% of all cases since 2020. Estimated data highlights the growing threat.
What Banks Are Doing (and Not Doing) About It
Banks have known about jackpotting for years. The FBI's warnings aren't new information to financial institutions. But the response has been spotty and inconsistent.
Hardware Upgrades: Major banks have been gradually replacing aging ATM fleets with newer models that incorporate better security. Modern ATMs include secure boot mechanisms, encrypted hard drives, and hardware-based integrity checks that make Ploutus installation much more difficult. But the replacement process is expensive and slow. Banks are prioritizing high-traffic locations while leaving older, smaller-branch ATMs vulnerable.
Software Hardening: Some manufacturers have released firmware updates that add additional verification checks and make it harder for unauthorized malware to function. But banks are inconsistent about deploying these updates. Some keep ATMs on months-old firmware versions, while others update regularly.
Physical Security Enhancements: Banks have added supplementary locks, replaced vulnerable locks with newer designs, and increased the frequency of physical inspections at ATM locations. But this is labor-intensive and expensive, so many smaller regional banks and third-party ATM operators haven't fully implemented these measures.
Monitoring Improvements: Some banks have enhanced their monitoring systems to detect unusual dispensing patterns or hardware anomalies. But most banks still lack real-time hardware integrity checks. Detection typically happens after the fact, during routine audits.
Industry Coordination: The banking industry has established information-sharing channels to alert each other about known vulnerabilities and attack patterns. But information sharing is often slow, and there's no unified standard for ATM security across all manufacturers and institutions.
The reality is that banks have financial incentives to absorb jackpotting losses rather than invest heavily in prevention. The cost of replacing an entire ATM fleet with modern, secure hardware could exceed the current losses from jackpotting attacks. From a purely economic standpoint, many banks view jackpotting as an acceptable cost of doing business.
This calculation will likely change if jackpotting losses continue to escalate. At some point, the cumulative losses will exceed the cost of comprehensive hardware replacement, and banks will be forced to act more decisively.
Law Enforcement Response and Investigation Challenges
The FBI, Secret Service, and local law enforcement agencies have been investigating jackpotting cases, but the results have been mixed.
Investigation Challenges:
-
Attribution difficulty: Jackpotting attacks leave minimal digital evidence. A compromised ATM might log unusual activity, but the logs could be deleted or modified by the malware. Investigators can't easily determine who performed the attack or where they're based.
-
Cash trail: Once cash is removed from an ATM, it's nearly impossible to trace. Criminals can spend or exchange the cash immediately, and there's no digital record of where it went.
-
Cross-jurisdictional complexity: An attacker might operate in one state while the ATM's owning bank is headquartered in another. Different law enforcement agencies have different protocols and resources, making coordination challenging.
-
Technical expertise requirements: Investigating jackpotting requires law enforcement officers with specialized knowledge of ATM architecture, XFS, malware analysis, and hardware security. This expertise is relatively rare outside of federal agencies.
-
Low prosecution rates: Even when suspects are identified, proving that they were responsible for specific attacks is difficult. The connection between a generic key purchase, a malware download, and a specific ATM compromise might not hold up in court.
Enforcement Actions:
The FBI has made some progress. In recent years, they've executed search warrants targeting individuals suspected of distributing Ploutus malware. They've identified and arrested multiple individuals involved in jackpotting networks. But the volume of arrests is small compared to the volume of attacks.
The Secret Service, which has jurisdiction over financial crimes, has also been involved in investigations. They've worked with international partners to disrupt criminal networks that include jackpotting as part of their broader fraud operations.
Local law enforcement agencies often lack the resources and technical expertise to investigate jackpotting cases effectively. They typically defer to federal agencies, which means cases can take months to progress.
International Dimension:
Some jackpotting networks operate internationally. The malware might be developed in Eastern Europe, the hardware tools might be manufactured in Asia, and the physical attacks might be executed by different individuals across multiple countries. This makes law enforcement response extremely challenging and requires international cooperation and extradition agreements.
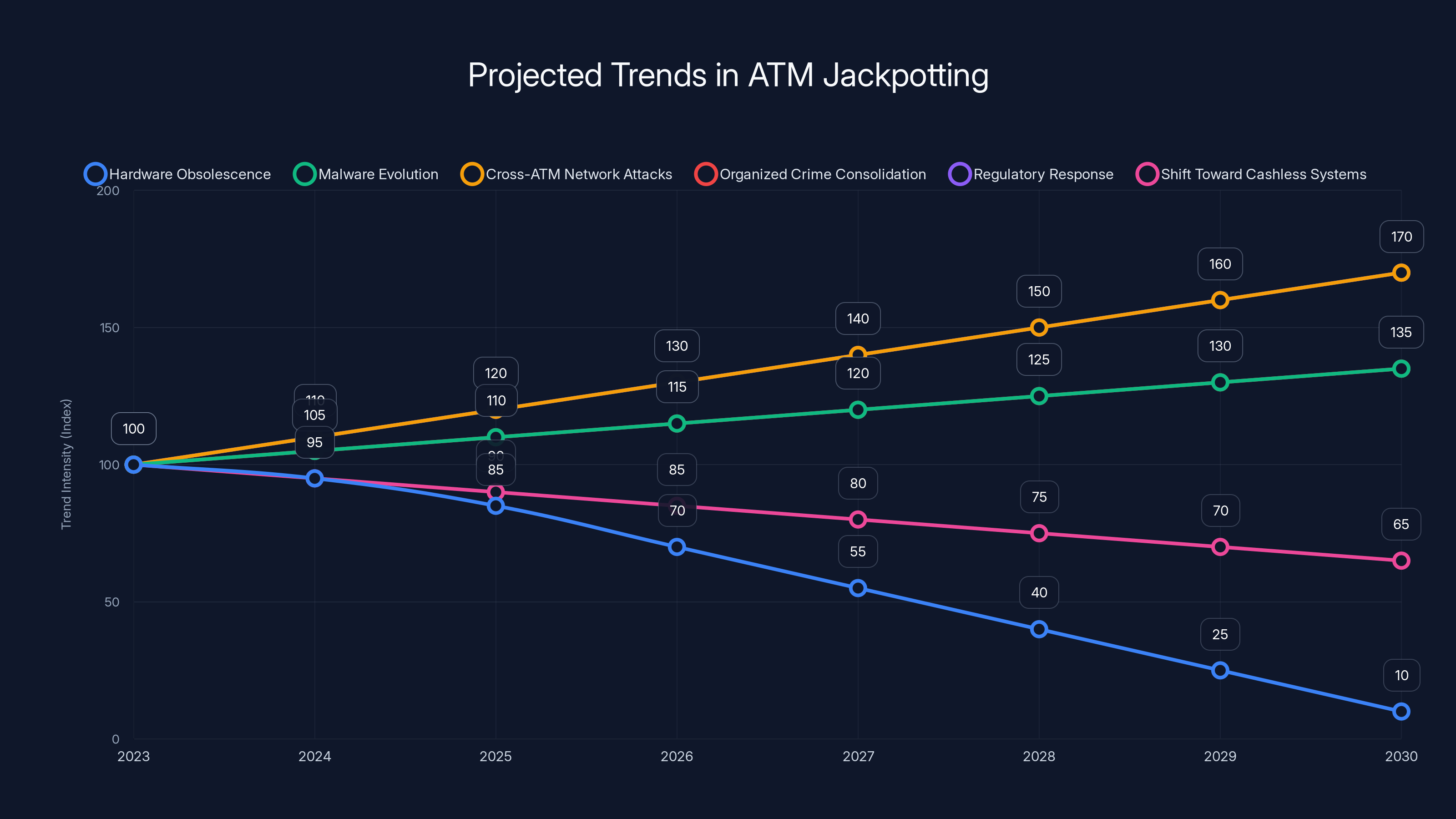
The chart illustrates projected trends in ATM jackpotting from 2023 to 2030, highlighting the decline in hardware obsolescence and cash usage, while malware evolution and network attacks are expected to rise. (Estimated data)
The XFS Vulnerability: A Fundamental Design Problem
Underlying all of jackpotting is a fundamental security problem with how XFS (e Xtensions for Financial Services) was designed and implemented.
XFS was created to provide a standardized interface between ATM software and hardware components. Before XFS, each ATM manufacturer had proprietary software that directly controlled hardware. Standardization meant that software developers could build applications that worked across different hardware platforms.
But standardization required openness. XFS had to be flexible enough to accommodate different manufacturers' hardware. It had to be well-documented so developers could build compatible applications. It had to support legacy systems while allowing for future innovation.
This flexibility created security gaps.
XFS originally relied on the assumption that the ATM's operating system would enforce security. If malware compromised the OS, it could potentially issue arbitrary XFS commands. The designers didn't anticipate that malware would become sophisticated enough to do this or that generic ATM keys would become available on the dark web.
Modern implementations of XFS have added security improvements:
1. Command whitelisting: Only certain XFS commands are permitted in certain contexts. Unauthorized commands are rejected.
2. Hardware-based enforcement: Some modern ATMs implement XFS enforcement at the hardware level, making it harder for software-based malware to override it.
3. Cryptographic signing: Commands are signed by authorized sources, making it difficult to inject arbitrary commands.
4. Secure boot: The ATM's operating system is loaded and verified before it runs, preventing unsigned code from executing.
But these improvements are only available in newer ATM models. Thousands of older machines in active service lack these protections.
The fundamental lesson here is that APIs designed without security in mind become security problems later. The ATM industry learned this lesson the hard way, but learning came years after the damage was already done.
Jackpotting vs. Other ATM Attacks: A Comparison
Jackpotting is just one of many threats facing ATM networks. Understanding how it compares to other attack types provides context for its relative risk.
Skimming
Skimming involves attaching a physical device to an ATM's card reader that captures card data as cards are inserted. The attacker later retrieves the device and uses the captured data to create counterfeit cards or conduct identity theft.
Jackpotting vs. Skimming:
- Jackpotting is faster and yields immediate cash
- Skimming creates a longer tail of fraud that can affect customers
- Jackpotting is detected faster once someone performs a physical inspection
- Skimming can go undetected for weeks if no one notices the physical device
Phishing and Social Engineering
Phishing attacks target ATM users or bank employees, not the ATMs themselves. The goal is to capture credentials or trick people into revealing sensitive information.
Jackpotting vs. Phishing:
- Jackpotting requires physical access to specific machines
- Phishing can target millions of people from a single location
- Jackpotting yields limited cash per incident
- Phishing can lead to massive account takeovers
Malware Installation (Remote)
Some malware targets ATMs remotely, trying to compromise machines through network connections or by providing infected firmware updates.
Jackpotting vs. Remote Malware:
- Jackpotting requires physical access
- Remote malware can spread across entire networks
- Jackpotting is difficult to execute at scale
- Remote malware could potentially compromise thousands of machines simultaneously
Cash Trapping
Cash trapping involves inserting a foreign object into the cash dispenser to jam it and prevent bills from being dispensed. When the bank technician comes to fix it, the attacker steals the cash from the jammed dispenser.
Jackpotting vs. Cash Trapping:
- Jackpotting forces the machine to dispense on demand
- Cash trapping requires waiting for a technician
- Jackpotting is more reliable and less detectable
- Cash trapping is simpler but lower-yield
The Future of Jackpotting: Trends and Predictions
Jackpotting is unlikely to disappear anytime soon. As long as ATMs contain cash and vulnerabilities exist, attackers will target them. But the landscape will evolve.
Trend 1: Increased Hardware Obsolescence
As new, more secure ATMs are deployed, older machines will be retired. But this transition will take years. In the interim, there will be a window of vulnerability where vulnerable older machines exist alongside secure newer ones. Attackers will continue targeting the older machines until they're all gone.
Trend 2: Malware Evolution
Ploutus variants will continue to evolve, incorporating anti-analysis features, polymorphic code, and sophistication that makes them harder to detect and remove. New variants will emerge targeting newly discovered vulnerabilities in modern ATM operating systems.
Trend 3: Cross-ATM Network Attacks
As individual ATM security improves, attackers might shift toward compromising entire ATM networks rather than individual machines. A single vulnerability in a bank's ATM management software could potentially compromise hundreds or thousands of machines simultaneously.
Trend 4: Organized Crime Consolidation
Jackpotting will likely become increasingly associated with organized crime networks rather than independent attackers. These networks will develop specialized capabilities, distribute risk, and operate with more sophistication.
Trend 5: Regulatory Response
As losses accumulate, regulatory bodies will likely impose stricter security requirements on banks and ATM manufacturers. Standards for hardware authentication, firmware signing, and intrusion detection will become mandatory.
Trend 6: Shift Toward Cashless Systems
Longer-term, the financial industry's transition toward cashless systems will reduce the attractiveness of ATM jackpotting. As fewer people use cash and ATMs hold less cash, the economics of jackpotting attacks will become less favorable.

Best Practices for Banks and ATM Operators
If you work in banking or ATM operations, there are concrete steps your organization should take to reduce jackpotting risk.
Immediate Actions (0-3 months):
-
Inventory assessment: Catalog every ATM in your network, noting the model, age, operating system, and known vulnerabilities. Prioritize machines that use generic keys or run outdated operating systems.
-
Physical inspections: Increase the frequency of physical inspections at ATM locations. Look for signs of tampering, replaced components, or unauthorized modifications.
-
Security awareness training: Train employees who interact with ATMs (technicians, branch managers, security personnel) on jackpotting tactics and signs of compromise.
-
Monitoring enhancement: Implement real-time monitoring that alerts staff when an ATM dispenses cash without a corresponding transaction. This can catch some jackpotting incidents in progress.
Short-term Actions (3-12 months):
-
Supplementary lock installation: Add secondary locks to machines that only use generic keys. Implement PIN-protected access that supplements the key mechanism.
-
Firmware updates: Deploy all available security updates and patches to every ATM in the network. This closes known vulnerabilities that Ploutus variants might exploit.
-
Hardware integrity checking: Implement periodic integrity checks of critical hardware components. Some machines can automatically detect if hard drives have been replaced or tampered with.
-
Incident response plan: Develop a protocol for responding to suspected jackpotting incidents. This should include forensic preservation, investigation coordination, and customer communication.
Medium-term Actions (12-24 months):
-
Hardware modernization: Begin replacing the oldest, most vulnerable machines with modern hardware that includes secure boot, encrypted storage, and hardware-based security checks.
-
Network segmentation: Isolate ATM networks from other banking networks. Implement strong authentication and encryption for all ATM-to-bank communication.
-
Threat intelligence integration: Subscribe to threat intelligence services that track jackpotting attacks, newly discovered Ploutus variants, and emerging attack patterns.
-
Industry collaboration: Participate in banking industry information-sharing initiatives. Share intelligence about attacks you've experienced or vulnerabilities you've discovered.
The Role of Manufacturers in Security
ATM manufacturers bear significant responsibility for security vulnerabilities. They design and build the machines, decide on security mechanisms, and issue software updates.
Manufacturer Accountability Issues:
-
Legacy support: Some manufacturers have discontinued support for older ATM models, leaving users unable to install critical security updates. Machines that are 10-15 years old might never receive patches for newly discovered vulnerabilities.
-
Slow patch deployment: When vulnerabilities are discovered, manufacturers sometimes take months to develop, test, and release patches. In the interim, the vulnerability is exploitable.
-
Expensive upgrades: Security improvements often require expensive hardware replacements or major software rewrites. Manufacturers sometimes choose not to implement improvements in older models because the cost exceeds the revenue.
-
Proprietary designs: Some manufacturers make replacement parts and security modules proprietary and expensive, making it costly for banks to implement improvements.
What's Changing:
The increasing visibility of jackpotting attacks is putting pressure on manufacturers to prioritize security. New machines are being built with hardware-based security modules, secure boot firmware, and encrypted storage. But the transition is slow, and there's significant installed base of vulnerable machines.
Regulatory pressure from banking authorities and law enforcement is also pushing manufacturers to be more proactive about security disclosures and patch deployment.

Why This Matters Beyond Just Banks
Jackpotting impacts more than just the financial institutions that own ATMs. The broader security implications are significant.
Lesson 1: Physical Security Matters
In an era when we focus heavily on cybersecurity, jackpotting is a reminder that physical security remains critical. No amount of encryption or firewalls protects against an attacker with physical access to hardware.
Lesson 2: Legacy Infrastructure Is Dangerous
Thousands of ATMs in service today are running software from the 2000s with security assumptions from an era before sophisticated malware existed. This lesson applies far beyond ATMs: legacy infrastructure across critical systems (power grids, water treatment, transportation) contains similar vulnerabilities.
Lesson 3: Standards Can Create Vulnerabilities
XFS was created to solve a real problem (interoperability), but its openness created security gaps. This pattern repeats across technical standards. Designers must anticipate that standards will eventually be exploited and build in security from the beginning.
Lesson 4: Organized Crime Adapts Quickly
When jackpotting tools and techniques became available, organized crime quickly adopted them as a reliable income source. Criminal networks are more agile than legitimate organizations in adopting new attack methods.
What Individual Users Should Know and Do
While jackpotting doesn't directly threaten your personal bank account, you should still be aware of it and take precautions.
Knowledge Points:
-
Your money is protected: Jackpotting attacks don't target customer accounts. FDIC insurance and banking network authentication protect your funds.
-
Banks are responsible: Banks must absorb jackpotting losses. There's no customer liability if an ATM is compromised.
-
Attacks are increasing: The number of jackpotting incidents is rising significantly. Be aware that this type of attack is becoming more common.
-
Detection takes time: Banks might not immediately notice that an ATM has been compromised. Larger crimes often go undetected for days or weeks.
Actions You Can Take:
-
Use trusted ATMs: Prefer ATMs in bank branches or secure, well-monitored locations. Avoid isolated or poorly lit ATMs.
-
Inspect before using: Look at the ATM briefly before inserting your card. If anything seems loose, damaged, or unusual, don't use it.
-
Report concerns: If you notice an ATM that appears tampered with or damaged, report it to the bank immediately.
-
Limit cash dependence: Use debit cards, credit cards, or mobile payment systems when possible. The less cash you handle, the less exposure you have to various types of theft.
-
Check your statements: Review your bank statements regularly for unauthorized activity. While jackpotting doesn't directly affect customers, other ATM-related fraud might.
-
Protect your PIN: Cover the keypad when entering your PIN, regardless of whether you think the ATM is compromised. This is good security practice generally.

The Business Case for Security Improvement
For banks and ATM operators, the decision to invest in jackpotting prevention comes down to economics. The cost of improvements must be justified by loss reduction.
Cost Analysis:
Replacing an ATM can cost
For a bank with 1,000 ATMs, a comprehensive modernization could cost $50 million or more.
If jackpotting losses average
But if jackpotting losses accelerate to what trend data suggests could happen (500+ incidents per year across the US), the economics change dramatically. At that scale, comprehensive security improvements become cost-justified.
The Tipping Point:
The industry is approaching a tipping point where losses become significant enough to justify preventive investment. We're probably 12-18 months away from that inflection point, depending on how quickly attack rates continue to accelerate.
Conclusion: The Growing Threat and Your Options
ATM jackpotting represents a unique and growing threat to the financial system. Unlike cybercrime, which can be executed from anywhere in the world, jackpotting requires physical presence and specific knowledge of ATM architecture. Yet despite this requirement for physicality, it's becoming dramatically more common.
The convergence of several factors—the commoditization of attack tools, the widespread availability of Ploutus malware, the existence of millions of vulnerable legacy ATMs, and the coordination of organized criminal networks—has created an environment where jackpotting is an efficient, low-risk way to steal large amounts of cash.
Banks are beginning to respond, but the response is gradual and incomplete. Many continue to treat jackpotting as an acceptable loss rather than a crisis requiring immediate action.
For the average person, the good news is clear: your personal finances are protected. Jackpotting doesn't target customer accounts. Banks absorb the losses. Your money is insured and secured by multiple layers of protection.
But the broader trend is concerning. If jackpotting attacks continue to accelerate, we might see a shift in how banks operate. ATMs might become less common in certain areas. Access to cash might become more restricted. Verification procedures might become more burdensome.
The financial industry's response to jackpotting over the next 12-24 months will determine whether this threat becomes a minor nuisance or a major problem. If manufacturers accelerate the deployment of secure hardware and banks increase security investment, jackpotting will become increasingly difficult and less profitable. If the industry remains complacent, we'll likely see losses continue to accelerate.
The choice, ultimately, belongs to financial institutions. The technology to secure ATMs against jackpotting exists today. What's missing is the financial incentive and organizational priority to deploy it at scale. As losses grow, that incentive will eventually emerge.
Until then, jackpotting will likely remain a growing concern for banks while posing minimal direct risk to individual customers. It's a reminder that in an increasingly digital financial system, physical security remains critically important. And it's a lesson that legacy infrastructure, when not properly maintained and updated, becomes a liability that can be exploited in ways the original designers never anticipated.

FAQ
What is ATM jackpotting and how is it different from other ATM crimes?
ATM jackpotting is the physical compromise of an ATM machine to force it to dispense cash without authorization. Unlike skimming attacks that capture card data or phishing schemes that target credentials, jackpotting requires direct physical access to the machine's internal hardware. The attacker opens the ATM fascia using a generic key, accesses the hard drive, installs malware (typically Ploutus), and then forces the machine to dispense its entire cash supply. It's fundamentally different because it targets the bank's cash directly, not customer accounts or card information.
How do criminals actually open ATMs without triggering alarms?
Criminals use generic keys that are sold on the dark web for under $100. These keys were discovered to work on multiple ATM models from different manufacturers. An attacker simply inserts the key into the ATM's fascia lock, turns it, and the protective panel opens. No drilling, no damage, no alarms triggered. The process takes under 30 seconds. Once inside, they can remove the hard drive, install Ploutus malware, or swap it with a pre-loaded infected drive. The entire operation leaves minimal evidence and can happen without attracting attention in a busy location.
Is my personal bank account at risk if I use a compromised ATM?
No. Your personal bank account is completely protected. Jackpotting attacks target the bank's cash supply, not customer accounts. Attackers never access your card data, PIN, or account information. They use the malware to bypass the normal transaction authorization process and force the cash dispenser to open. Your account balance remains secure, protected by FDIC insurance and the banking system's authorization procedures. The bank absorbs the loss, not the customer.
What is Ploutus malware and why is it so dangerous?
Ploutus is malware specifically designed to exploit the XFS (e Xtensions for Financial Services) API that ATMs use to communicate with their hardware components. When installed, Ploutus intercepts XFS commands and issues unauthorized dispensing instructions. It allows attackers to bypass bank authorization entirely and force ATMs to dispense cash on demand without a valid card, PIN, or bank authorization. Ploutus is dangerous because variants are readily available on criminal forums, it's relatively simple to install on vulnerable machines, and it's difficult to detect once it's running on an ATM's hard drive.
How often are ATM jackpotting attacks detected and reported?
Detection rates are likely much lower than the actual number of attacks occurring. The FBI has documented about 1,900 jackpotting incidents since 2020, with roughly 700 in 2025 alone. However, banks often don't discover compromises until weeks after an attack, sometimes during routine audits or cash counting. Many incidents go unreported if the losses fall below certain thresholds or if banks want to avoid negative publicity. The actual number of jackpotting attacks is probably significantly higher than official statistics suggest.
What should I do if I encounter a suspicious ATM?
If an ATM appears physically damaged, has loose panels, unfamiliar stickers, or anything that seems out of place, don't use it. Report it immediately to the bank that operates the machine. Cover the keypad when entering your PIN regardless of whether you suspect compromise. Use ATMs in secure locations like bank branches or well-monitored areas rather than isolated convenience stores. Inspect the machine briefly before using it. If you notice anything unusual, walk away and report it. These precautions protect against both jackpotting and other types of ATM fraud.
Why haven't banks fixed this problem if they've known about jackpotting for years?
Banks have known about jackpotting since at least 2020, but the response has been gradual due to cost-benefit calculations. Replacing an entire ATM fleet with modern, secure hardware can cost $50 million or more for a large bank. Current jackpotting losses, while significant, are still less than the cost of comprehensive replacement in many cases. However, as attack rates accelerate and losses mount, the economics are shifting. Many banks are now beginning to upgrade security measures, deploy firmware updates, and replace vulnerable machines. The transition will likely accelerate over the next 12-24 months as losses become more significant.
How is the FBI responding to jackpotting attacks?
The FBI has established task forces dedicated to investigating jackpotting cases, identified and arrested individuals involved in jackpotting networks, and published warnings to the financial industry about emerging threats and attack patterns. However, investigation and prosecution face challenges due to the difficulty of attribution, the cross-jurisdictional nature of attacks, and the need for specialized technical expertise. The number of prosecutions remains relatively small compared to the volume of attacks, partly because many attackers operate in ways that make attribution difficult and partly due to limited law enforcement resources dedicated to financial cybercrime.
What technologies and practices can prevent or reduce jackpotting attacks?
Modern ATM security includes secure boot firmware that verifies the operating system before it runs, encrypted hard drives that prevent unauthorized access even if removed from the machine, hardware-based integrity checks that detect tampering, supplementary locks that require PIN or biometric authentication in addition to generic keys, real-time monitoring that alerts banks to unusual dispensing patterns, and firmware updates that patch known vulnerabilities in XFS and the operating system. Additionally, banks are implementing more frequent physical inspections of ATM locations and replacing vulnerable legacy machines with modern, more secure models.
Are international ATMs at higher risk of jackpotting than US ATMs?
Jackpotting attacks have been documented globally, but the highest concentration remains in the United States. Some international ATM networks have different security architectures and older machines, which could make them more vulnerable. However, US ATMs are particularly attractive targets because of the large number of vulnerable legacy machines, the availability of specialized tools and malware, and the relative sophistication of domestic criminal networks. International law enforcement coordination to address jackpotting is ongoing but faces challenges due to different regulations and extradition agreements.
What happens to banks and ATM operators that experience jackpotting attacks?
When a jackpotting attack is discovered, banks typically conduct a forensic investigation to determine the scope of the compromise, calculate losses, report the incident to law enforcement, implement corrective measures to prevent future attacks, and in some cases, report the incident to banking regulators. Banks absorb the financial losses directly, which can range from
Need more specific information about protecting your financial data? Learn more about banking security best practices and how to stay safe when using ATMs in public locations.
Key Takeaways
- ATM jackpotting attacks have stolen over $20M since 2020, with 700 incidents in 2025 representing 37% of all documented cases
- Criminals use widely available generic keys ($100) and Ploutus malware to open ATMs and force cash dispensing without authorization
- Customer accounts are completely protected because attackers never access card data, PINs, or account information—banks absorb losses
- Legacy ATMs running outdated operating systems are extremely vulnerable; modern machines with secure boot and hardware integrity checks are significantly more resistant
- Detection of jackpotting attacks often takes days or weeks, meaning actual losses are likely much higher than the $20M officially reported
Related Articles
- ATM Jackpotting Attacks: The Rising Threat to Cash Machines [2025]
- AI in Cybersecurity: Threats, Solutions & Defense Strategies [2025]
- Keenadu Android Backdoor: Firmware Malware Threat [2025]
- Why AI Models Can't Understand Security (And Why That Matters) [2025]
- North Korean Job Scammers Target Developers with Fake Interviews [2025]
- N-Day Vulnerabilities: Why Patched Exploits Are Now Your Biggest Security Risk [2025]
![ATM Jackpotting Attacks Explained [2025]](https://tryrunable.com/blog/atm-jackpotting-attacks-explained-2025/image-1-1771601865357.jpg)



