Introduction: When ATMs Become Thieves
Imagine walking past your local bank branch and noticing something odd. An ATM is quietly dispensing cash on its own, bills spilling out like a broken fountain. No customer is present. No card was inserted. Yet the machine is working exactly as someone programmed it to.
This isn't science fiction anymore. It's happening right now, in banks across the country, and it's costing the financial system tens of millions of dollars annually.
ATM jackpotting, the term for attacks that force cash dispensers to automatically spit out money without authorization, has evolved from theoretical security research into a genuine criminal enterprise. What started as a dramatic demonstration at a security conference has become a sophisticated, organized crime operation that law enforcement is scrambling to understand and stop.
The problem has reached a critical inflection point. The FBI's recent security bulletin reveals a sobering reality: more than 700 jackpotting attacks occurred during 2025 alone, with hackers netting at least $20 million in stolen cash. That's not just a number on a spreadsheet. That's real money disappearing from financial institutions. That's security vulnerabilities transforming from academic curiosities into active weapons.
What makes this particularly concerning is the speed at which these attacks have escalated. A decade ago, ATM jackpotting was the exclusive domain of elite security researchers willing to spend months analyzing ATM internals. Today, criminal gangs are executing attacks in minutes, using readily available tools and techniques that spread across underground forums and dark web marketplaces.
The attackers aren't trying to break into customer accounts or steal personal financial information. Instead, they're taking a more direct approach: bypassing the entire security infrastructure and instructing the machine to simply hand over cash. It's a different threat model entirely, one that traditional banking security wasn't designed to defend against.
This comprehensive guide examines the ATM jackpotting crisis from every angle. We'll explore how these attacks work, why they're becoming more prevalent, what specific malware families are being deployed, and what solutions financial institutions are implementing. Whether you're a security professional, bank executive, IT manager, or simply someone concerned about the safety of financial systems, understanding this threat is essential.
TL; DR
- Over 700 jackpotting attacks occurred in 2025, stealing at least $20 million in cash
- Attackers use physical access and malware (like Ploutus) to force ATMs to dispense cash without authorization
- Ploutus exploits XFS software vulnerabilities that many ATM manufacturers rely on
- Attacks can complete in minutes and are often not detected until cash is already gone
- Financial institutions are responding with multi-factor authentication, firmware updates, and physical security improvements
- The threat continues to evolve as criminal networks share techniques across international borders

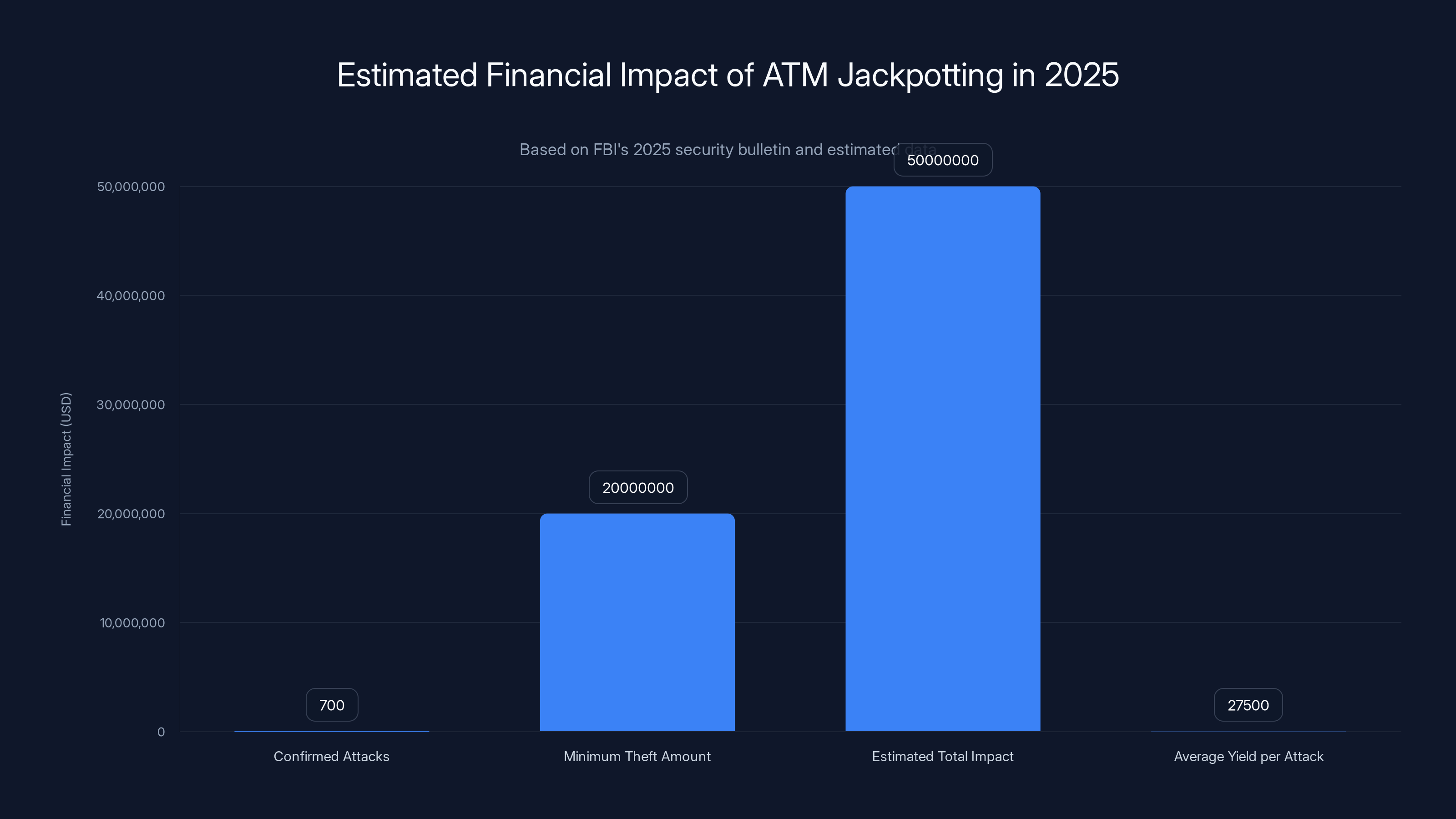
The FBI reported over 700 jackpotting attacks in 2025, with a minimum theft amount of
Understanding ATM Jackpotting: From Theory to Crime
The Birth of ATM Hacking: Barnaby Jack's Legacy
In 2010, security researcher Barnaby Jack took the stage at the Black Hat security conference with a simple device and an audacious plan. What he demonstrated that day would fundamentally change how the security community viewed automated teller machines. Standing before a crowd of industry professionals, Jack plugged a laptop into an ATM and executed a series of commands. The machine responded exactly as his code instructed: it began dispensing cash rapidly, bill after bill cascading into the cash tray below.
The audience sat in stunned silence. Nobody had seriously considered that ATMs could be hacked in this manner. These machines were supposed to be impregnable. Banks had invested heavily in their security. Yet here was proof that the security was merely theater.
Jack's demonstration revealed a fundamental flaw in how ATM manufacturers approached security. They focused on protecting the connection between the ATM and the bank's central servers, assuming that as long as transactions were authenticated and encrypted, the machines were safe. What Jack proved was that the weakness didn't lie in communications security. It lay in the physical and firmware security of the machine itself.
The implications were staggering. If someone could gain physical access to an ATM's internal components, they could potentially bypass all the security measures the banks had put in place. The entire trust model was undermined.
The Evolution from Academic Exercise to Criminal Reality
For several years after Jack's presentation, ATM jackpotting remained largely in the realm of theoretical security research. Academic papers were published. Security conferences featured discussions about potential defenses. Manufacturers were notified of vulnerabilities. The process followed the traditional responsible disclosure model.
But something shifted around 2015-2016. Criminal organizations began systematically studying the publicly available research on ATM vulnerabilities. They realized that the techniques Jack had demonstrated weren't just impressive academic exercises. They were blueprints for theft.
What happened next was inevitable: the criminal underworld started developing commercial-grade jackpotting tools. These weren't cobbled-together scripts or one-off attacks. These were sophisticated malware packages engineered for reliability, speed, and stealth. Underground forums and dark web marketplaces began offering jackpotting services. Criminal gangs established specialized teams dedicated to identifying vulnerable ATM models and developing exploits for them.
The transition from theory to practice accelerated significantly. By 2017, law enforcement agencies worldwide were reporting organized jackpotting attacks. By 2020, it had become a significant concern for financial institutions. By 2025, it's become a full-blown epidemic that requires coordinated international law enforcement response.
What's particularly troubling is that the criminals adapted faster than the defenders. While manufacturers slowly deployed security patches and updates, the attackers evolved their techniques, developed new exploits, and established reliable supply chains for attack tools and components.

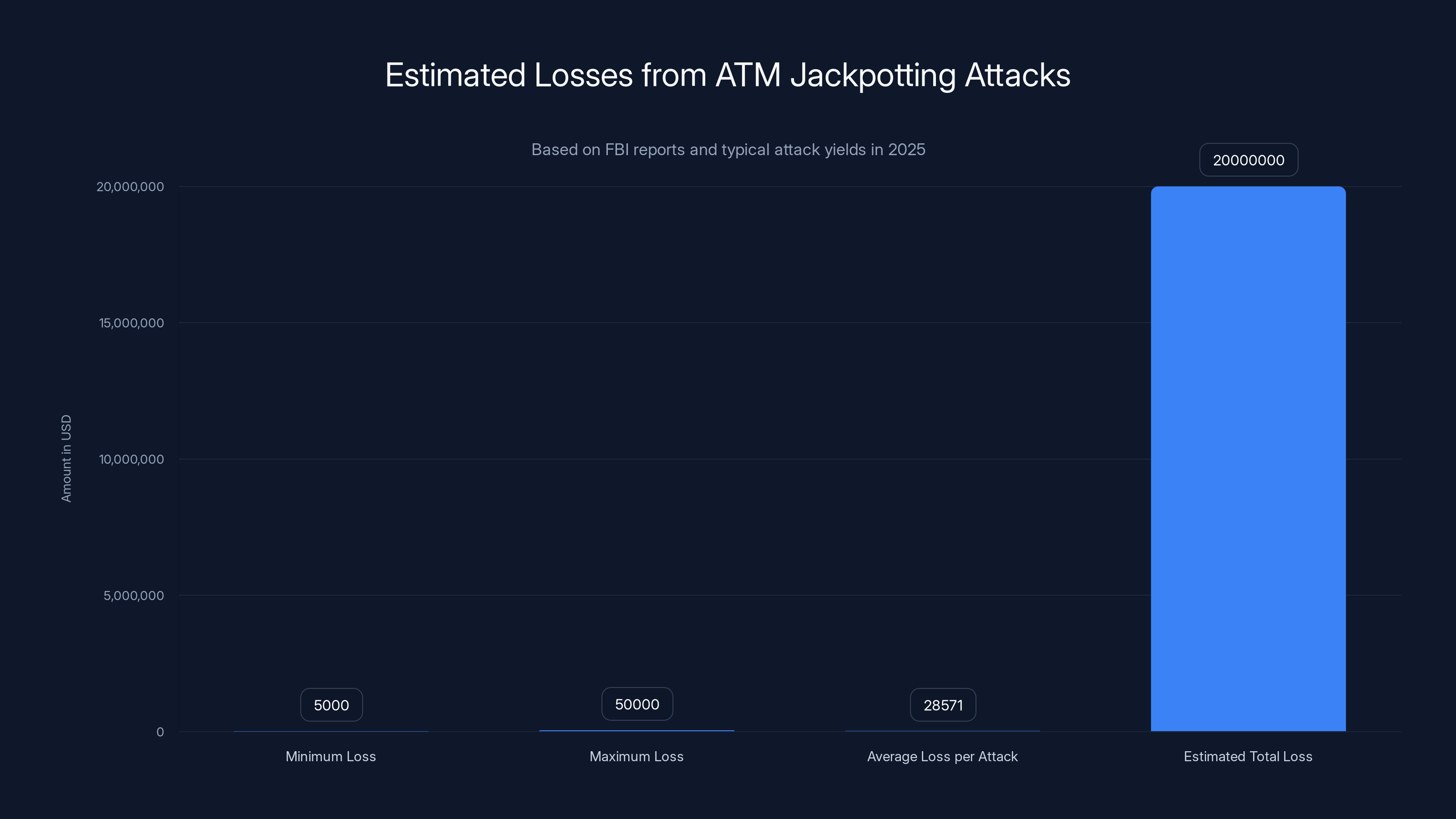
In 2025, ATM jackpotting attacks resulted in estimated losses of at least
The FBI's 2025 Alert: What We Know About the Current Threat
Key Statistics and Attack Metrics
The FBI's security bulletin released in early 2025 provides the most comprehensive public assessment of the jackpotting threat landscape to date. The numbers are staggering enough to grab attention, but it's the trends they reveal that should concern financial institutions most.
Over 700 confirmed jackpotting attacks occurred during 2025. That's nearly two attacks per day. The minimum confirmed theft amount stands at $20 million, though law enforcement suspects the actual figure is considerably higher given that many attacks go undetected for days or weeks after they occur.
To put this in perspective, $20 million annually represents just one vector of ATM-related fraud. When combined with other ATM attacks like card skimming, PIN interception, and theft of components, the total impact on the financial system is staggering. Multiply that by the fact that many smaller institutions don't report attacks to the FBI, and the true scale becomes genuinely alarming.
What's particularly striking is the concentration of attacks. Certain ATM models are targeted repeatedly. Specific geographic regions show elevated attack frequencies. This pattern suggests that criminal organizations have identified the most vulnerable systems and are systematically exploiting them. They're not attacking randomly. They're operating with specific intelligence about which machines are vulnerable and where they're located.
The average jackpotting incident yields between
Attack Timing and Detection Gaps
One of the most concerning aspects of jackpotting attacks is the detection lag. The FBI's bulletin emphasizes that attacks can occur in minutes, and often aren't discovered until hours or days later. This window of opportunity is crucial for attackers. They can be gone long before anyone realizes what happened.
Typical attack scenarios play out like this: A criminal (or team of criminals) gains physical access to an ATM. This might happen during night hours, or in locations with minimal surveillance. They unlock the machine using generic keys that are readily available or easily obtained. They connect a laptop or specialized device to the ATM's internal components. They upload malware or execute commands that override the normal dispensing controls. Within minutes, they've extracted thousands of dollars in cash.
The brilliance of the attack from the criminal's perspective is its simplicity. No need to compromise the bank's servers. No need to intercept customer authentication credentials. No need to execute complex fraud schemes that leave a detailed digital trail. Just take direct control of the machine and tell it to dispense cash.
Detection happens through multiple pathways, and the delays vary. Some attacks are discovered when bank staff arrive for morning operations and notice the cash tray is empty. Others are detected through automated auditing systems that flag reconciliation discrepancies. The most sophisticated detection involves analyzing transaction logs and identifying anomalies: cash dispensed without corresponding transactions, or transactions that don't match actual cash movements.
But by the time these detection mechanisms trigger, the attackers are long gone, and the evidence at the scene might be minimal. No stolen cards. No compromised customer accounts. Just an empty cash tray and a mystery.
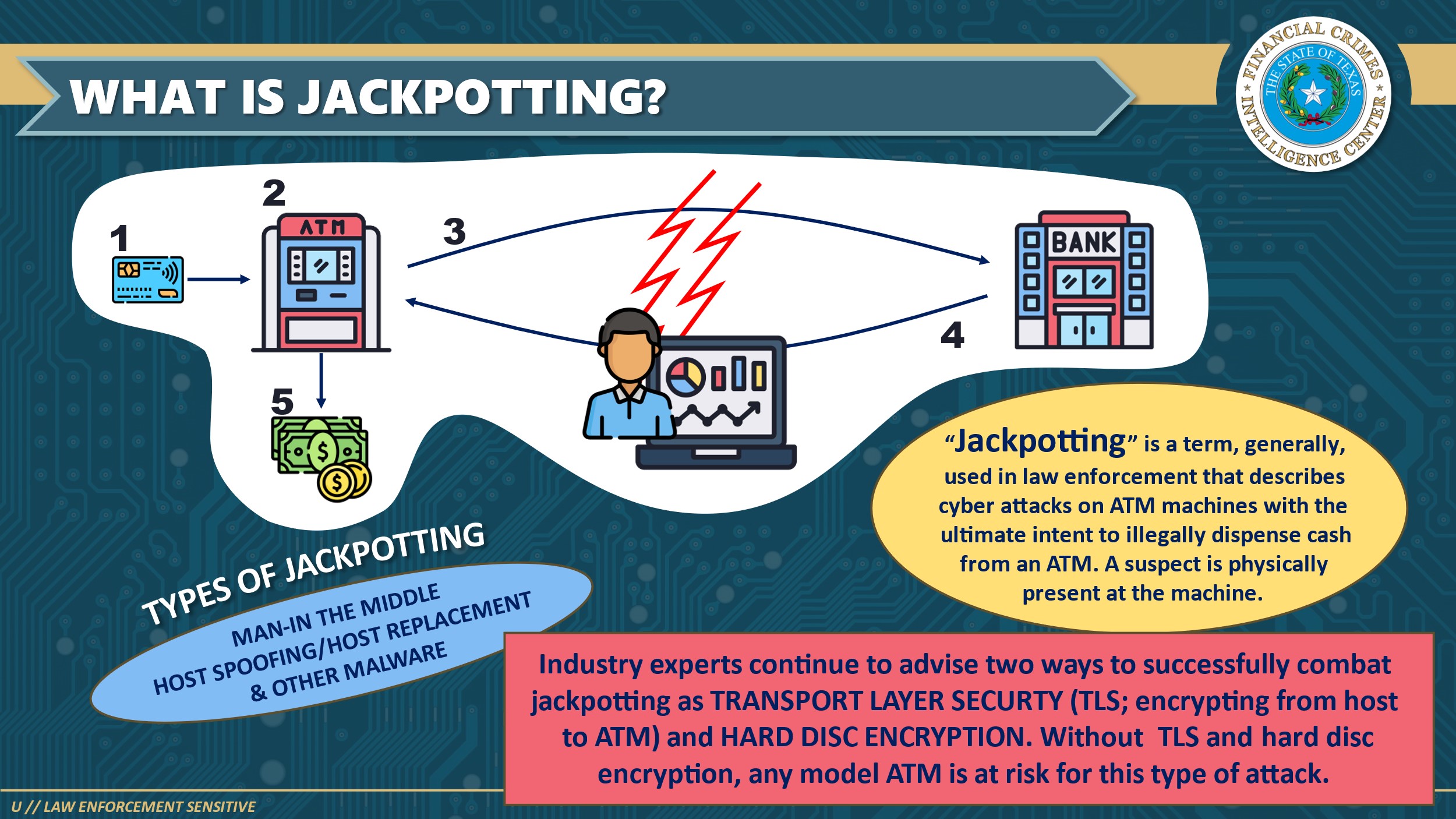
How ATM Jackpotting Attacks Work: The Technical Reality
Physical Access: The First Barrier
Every jackpotting attack begins with one fundamental requirement: physical access to the ATM. The attacker must be able to open the machine and reach its internal components. This isn't as difficult as it might sound.
ATM manufacturers use standardized locking mechanisms for security reasons. They want service technicians to be able to easily access internal components when maintenance is needed. What this means in practice is that ATMs typically use the same type of keys, or keys similar enough that they can be obtained through various channels. Security research has demonstrated that generic keys matching common ATM lock types can be purchased online from industrial supply companies for under $50.
Alternatively, attackers might use physical force. ATM front panels aren't necessarily reinforced against determined individuals with the right tools. Or they might wait for a service technician to open the machine and observe the access method.
Once inside the machine, the attacker has access to the ATM's internal architecture. Modern ATMs are essentially specialized computers running operating systems like Windows. They have hard drives, RAM, network connections, and various peripheral devices. To an informed attacker, an open ATM is like an unlocked computer sitting in a public space.
The Software Side: XFS and the Operating System
Here's where the technical sophistication comes in. ATMs rely on standardized software interfaces to manage the various hardware components. The primary interface standard is called XFS, which stands for e Xtensions for Financial Services.
XFS is a mature standard that's been around for decades. It allows software developers to write applications that communicate with ATM hardware without needing to understand the specific details of each manufacturer's implementation. A bank's ATM software can work across machines from different vendors because they all implement the XFS standard.
The problem is that XFS was designed with the assumption that the ATM would be running in a secure environment. The standard includes APIs that allow programs to command the cash dispenser to operate. It includes functions for controlling the PIN pad, the card reader, the display, and critically, the cash dispensing unit.
Now, consider what happens if someone gains control of the operating system running underneath XFS. If they can execute arbitrary code at the operating system level, they can invoke any XFS function they want. They can instruct the dispenser to operate without any of the normal safeguards. There's nothing preventing them from calling the cash dispensing function repeatedly, from bypassing the normal transaction authorization, from making the machine think it's performing a legitimate operation when it's actually just handing out cash.
Ploutus: The Malware Game-Changer
This is where specific malware families enter the picture. Ploutus is one of the most notorious jackpotting malware families. It represents the state of the art in ATM exploitation.
Ploutus works by targeting the Windows operating system that powers many ATMs. Once installed on an ATM, either through physical USB connection or through network compromise, Ploutus takes control of the machine. It doesn't just dispense money randomly. It's designed to be operated by an attacker who can interact with a command interface, either locally or potentially remotely.
Ploutus executes instructions that cause the ATM to dispense cash rapidly. Depending on the variant and the attacker's skill, the malware might also disable logging, prevent alarms, or erase evidence of the transaction. The attacker can control the dispense rate, the total amount dispensed, and various operational parameters.
What makes Ploutus particularly dangerous is its versatility. It's been discovered affecting ATMs from multiple manufacturers. The malware is regularly updated as researchers identify new vulnerabilities and attackers develop new techniques. Underground forums share modified versions of Ploutus, each tailored to exploit specific ATM models.
The malware represents the marriage of old-school security vulnerabilities with modern exploit development. It takes advantage of the fact that many ATMs still run Windows operating systems that aren't regularly patched, that haven't been updated in years, that exist in a state of perpetual vulnerability.
Hybrid Attack Models: Physical Plus Digital
The most effective jackpotting attacks combine physical access with digital exploitation. An attacker might gain physical access to the machine, connect a device that loads malware onto the ATM's hard drive, and then walk away. The malware persists on the machine, potentially activating at a predetermined time or waiting for a signal from the attacker.
Alternatively, an attacker might identify an ATM with network vulnerability and compromise it remotely, installing jackpotting malware without ever needing physical access. This remote approach is less common but particularly dangerous because it's harder to detect and can affect many machines simultaneously.
Some attacks use a man-in-the-middle approach, intercepting communications between the ATM and the bank's central systems and instructing the ATM to dispense cash while obscuring the transaction from the bank's records. Other approaches focus on compromising the ATM's firmware, making the attack persistent even if the operating system is reinstalled.
The sophistication level varies enormously depending on the attacker's resources and skill. Street-level criminals might use generic jackpotting tools they purchased from underground forums. Professional criminal organizations might employ specialized malware developers who create custom exploits for specific ATM models. Nation-state actors, if they were interested in this vector (which most aren't, given the limited financial return), could presumably develop highly sophisticated attacks.

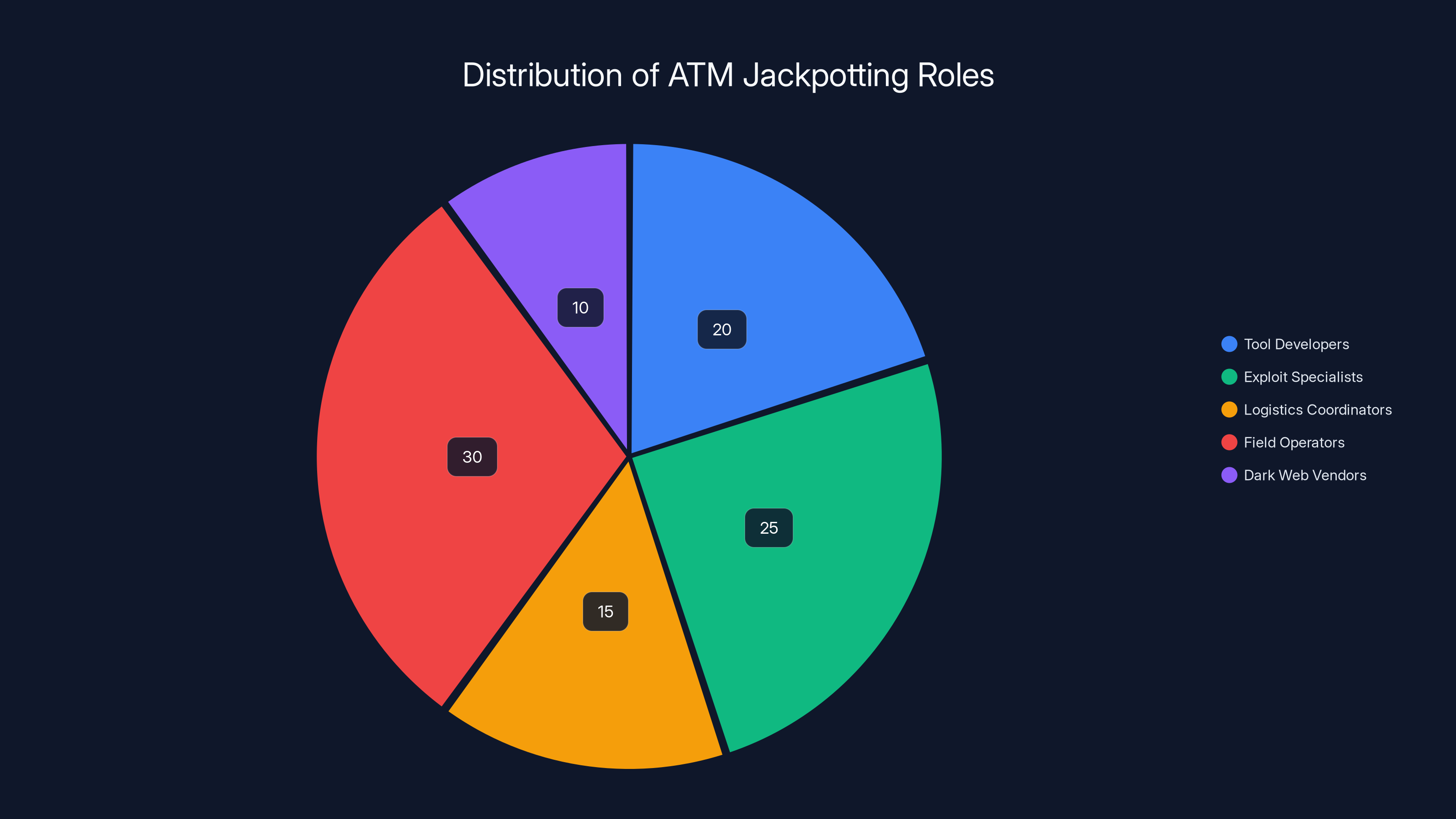
Organized crime networks involved in ATM jackpotting have distinct roles, with field operators and exploit specialists making up the largest portions. Estimated data.
The Attack Landscape: Who's Behind ATM Jackpotting?
Organized Crime Networks and International Syndicates
ATM jackpotting has become a highly organized criminal enterprise. This isn't a handful of hobbyists or script kiddies trying to make a quick buck. This is organized crime at scale, with specialized roles, supply chains, and distribution networks.
FBI investigations have traced jackpotting operations to sophisticated criminal networks operating across borders. These organizations have the capital to invest in developing custom tools, the expertise to identify and exploit vulnerabilities, and the logistics infrastructure to fence stolen cash and distribute proceeds across jurisdictions where law enforcement coordination is difficult.
These networks operate with surprising transparency in underground forums and dark web marketplaces. You can actually purchase jackpotting services. Criminal entrepreneurs offer to target specific ATM models for a percentage of the take. They sell pre-made malware packages that come with instructions and support. They offer training to help less sophisticated criminals execute attacks successfully.
The economics work in the criminals' favor. A successful jackpotting attack might net
The Skills and Knowledge Divide
What's interesting is the democratization of jackpotting knowledge. A decade ago, only elite security researchers understood how to exploit ATMs. Today, anyone with moderate technical skills can access detailed information about vulnerabilities, download malware, obtain access tools, and join criminal networks.
This democratization has two implications. First, it means more people can attempt jackpotting, lowering the barrier to entry for amateur criminals. Second, it means that the talent pool of attackers has expanded, including people with varying levels of sophistication and criminality.
You have everything from street-level criminals who use purchased malware with minimal customization, to professional groups who employ specialized developers, to experienced operators who understand multiple attack vectors and can adapt when defenses are deployed.

Why ATM Jackpotting Is Accelerating: The Perfect Storm
Aging Infrastructure and Delayed Patching
One primary reason jackpotting attacks have become so prevalent is the state of ATM infrastructure in many financial institutions. These machines are expensive. Replacing an entire fleet of ATMs takes years and millions of dollars. So banks keep machines operational for 10, 15, even 20 years.
When machines are that old, they're often running outdated operating systems. Windows XP, Windows 7, sometimes even older versions. These operating systems have hundreds of known vulnerabilities. They're no longer receiving security updates. Attackers know exactly which exploits will work against them.
Even machines running more modern operating systems often don't receive regular security patches. Banks might apply patches infrequently, or only when mandated by corporate policy, or only after a security incident. The typical scenario is that security researchers identify a vulnerability in a widely-used ATM model, disclose it to the manufacturer, and then wait months for a patch to be developed, tested, and deployed across thousands of machines.
During that window, criminals know about the vulnerability too. They start developing exploits, refining techniques, and preparing to execute attacks. By the time patches are deployed, they've already tested their methods on dozens of machines.
Weak Physical Security in Some Locations
ATM placement varies dramatically. Some machines are located in secure bank branches with 24-hour security staff, security cameras, and alarms. Others are in remote convenience stores, gas stations, or standalone kiosks with minimal monitoring.
An attacker can target machines based on their assessment of security. A machine in a low-surveillance location, accessible at night, in an area where someone tampering with an ATM might not immediately draw attention, becomes an attractive target. Attackers can spend time studying a location, understanding patrol patterns, identifying the optimal time window for access.
The ease of physical access varies, but at many locations, it's substantially easier than banks would like to admit. A person standing next to an ATM for 5-10 minutes, ostensibly using it, could actually be attempting to access the internal mechanisms or connecting a device to extract information or load malware.
Limited Detection and Response Capabilities
Most banks don't have real-time monitoring that would detect an ATM jackpotting attack in progress. They have transaction logs that might reveal anomalies later, but by that time the attacker is long gone.
Some jackpotting incidents go undetected for days. The attacker makes a withdrawal of
Respective capabilities also lag. Even when an attack is detected, banks might not immediately have the forensic expertise to determine what happened. Was it a jackpotting attack? A simple cash handling error? A mechanical malfunction? Understanding the true nature of incidents requires specialized knowledge that many institutions don't possess internally.
International Criminal Networks and Information Sharing
Another factor accelerating attacks is information sharing among criminal organizations. When one group develops a successful exploit for a particular ATM model, that information spreads through underground forums and dark web communities. Other criminals benefit from the research and development work, adapting and modifying the techniques.
This creates a network effect that favors attackers. Defensive information (security patches, best practices, detection methods) spreads much more slowly than offensive information (working exploits, attack code, vulnerability details).
Criminal organizations operating across different continents can coordinate attacks. One group in Eastern Europe develops the malware, another group in Asia performs reconnaissance on specific machines, a third group in South America executes the physical attacks. The proceeds get funneled through money laundering networks and distributed across jurisdictions where law enforcement coordination is minimal.

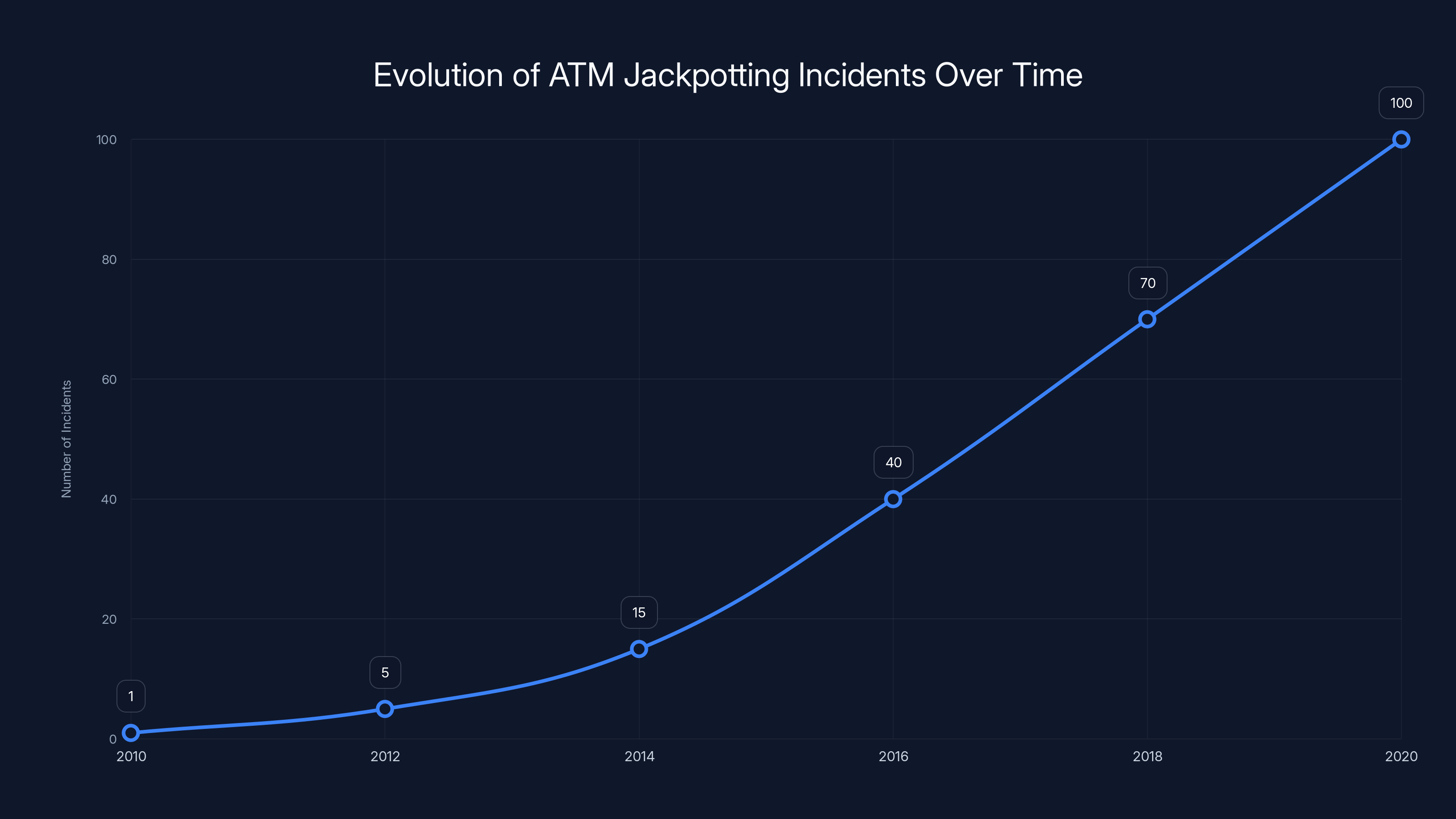
Following Barnaby Jack's 2010 demonstration, ATM jackpotting incidents increased significantly, highlighting growing exploitation of ATM vulnerabilities (Estimated data).
The Technical Arsenal: Malware and Attack Tools
Ploutus Family Variants and Evolution
Ploutus has evolved significantly since it first appeared. The original Ploutus variants were relatively simple: they targeted specific ATM models and provided basic dispensing capabilities. Subsequent versions, including Ploutus-D and Ploutus-M, became more sophisticated.
Ploutus-D added functionality for faster operation and better evasion. Ploutus-M included components for bypassing PIN entry mechanisms and other advanced features. Researchers have identified at least a dozen distinct variants, each one incorporating refinements based on previous versions and emerging defensive measures.
The malware landscape continues to evolve. New variants appear regularly, each one optimized for specific vulnerabilities, specific ATM models, or specific operating environments. Criminal organizations invest in malware development the way legitimate software companies do. They hire developers, conduct testing, iterate on designs, and release updates.
Custom Exploit Tools and Attack Frameworks
Beyond generic malware, criminals have developed specialized tools for executing jackpotting attacks. Some tools are designed specifically for loading malware onto ATMs through physical access. Others are remote administration tools that allow attackers to control compromised ATMs from a distance.
These tools range from simple scripts that automate the attack process, to sophisticated frameworks that provide multiple exploitation vectors and include anti-forensics capabilities that erase logs and evidence.
The tools also reflect specialization. Different tools target different ATM manufacturers. Some focus on exploiting network vulnerabilities, others on physical access vectors. The diversity of tools means that attackers can choose the optimal approach for their situation.
Detection Evasion and Anti-Forensics
Sophisticated attackers don't just steal cash. They also cover their tracks. Advanced malware variants include components that disable logging, erase transaction records, disable security alarms, and remove evidence of the attack from the machine's storage.
Some variants are designed to operate in a "live off the RAM" mode, where they load into memory but don't write to disk, making forensic recovery more difficult. Others encrypt their malware payload so that even if security researchers get access to the machine, analyzing the attack is more challenging.
The cat-and-mouse game between attackers and forensic investigators continues. As investigators develop better techniques for recovering evidence from compromised ATMs, attackers develop new evasion and anti-forensics methods.
Impact on Financial Institutions and Customers
Direct Financial Losses
The most obvious impact is the theft itself. $20 million in confirmed losses during 2025 represents real money that has to be absorbed somewhere in the financial system. For large institutions, this might be distributed across the network and barely noticeable. For smaller regional banks or credit unions, jackpotting attacks can represent significant losses.
These direct losses trigger cascading expenses. Banks must investigate attacks, conduct forensic analysis, implement remediation measures, deploy security patches, upgrade equipment, and enhance physical security. The cost of recovery often exceeds the value of the stolen cash.
Reputational and Customer Confidence Impact
When customers learn that their local bank's ATMs have been compromised, confidence erodes. Even if the customers' accounts were never directly compromised, the knowledge that an attacker was able to gain access to a bank machine raises questions about security in general.
Large-scale jackpotting incidents that make news coverage amplify this effect. When a single attack against a major bank hits the headlines, it can trigger broader concerns about ATM security across the entire sector.
Operational Disruptions
Institutions that have experienced jackpotting attacks often must take machines offline for forensic investigation, patching, and security hardening. If a machine is a primary ATM for a location, this disrupts service to customers. Multiple machines going offline simultaneously can create visible service degradation.
Some banks have responded to jackpotting threats by increasing the frequency of physical inspections and maintenance of ATMs, which also creates operational overhead and disrupts service.
Regulatory and Compliance Burden
Regulators are increasingly focused on ATM security. Banks must document their security practices, incident response procedures, and vulnerability management processes. Regulatory examinations now include specific questions about ATM security.
FAIL to meet regulatory expectations, and you face enforcement actions, fines, and requirements to implement expensive security upgrades. The regulatory burden is becoming one of the significant costs associated with maintaining secure ATM networks.

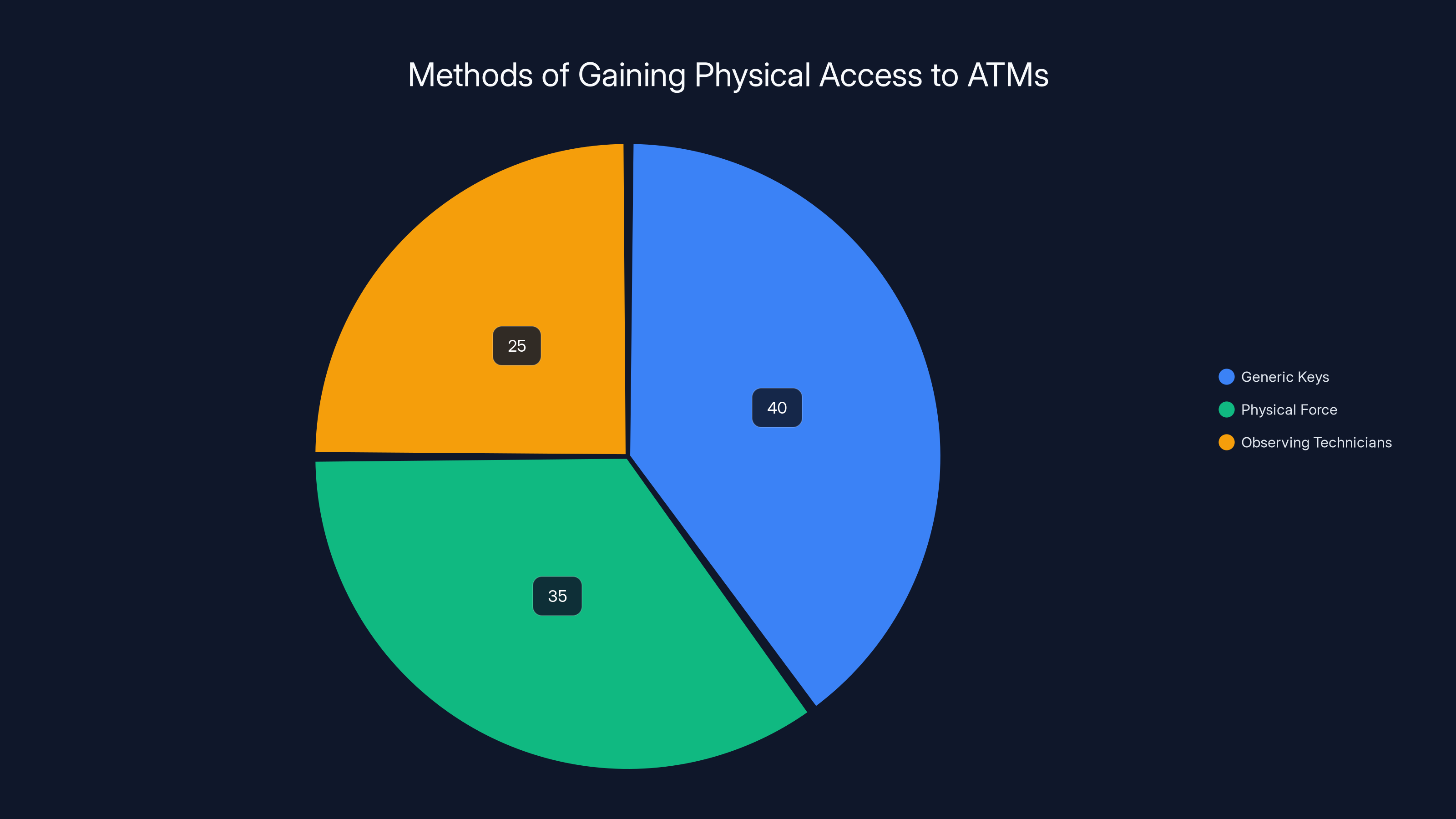
Estimated data suggests that generic keys are the most common method for gaining physical access to ATMs, followed by physical force and observing technicians.
Defensive Measures: How Banks Are Fighting Back
Multi-Factor Authentication and Transaction Authorization
One effective defensive approach is to add additional layers of authentication before allowing the ATM to dispense cash. This might include requiring multiple forms of authentication, time-based restrictions on cash dispensing, or additional verification steps that would make it harder for malware to simply issue a dispense command.
Some manufacturers are implementing real-time transaction authorization where the ATM must verify with the bank's central systems before dispensing any cash. This prevents malware from simply overriding the normal authorization process.
Firmware Security and Integrity Verification
ATM manufacturers are increasingly implementing firmware signing and verification mechanisms. The idea is that the ATM will verify the integrity of its firmware before executing it. If malware attempts to modify the firmware, the verification will fail and the machine won't execute the suspicious code.
This approach is effective but requires careful implementation. The verification mechanisms themselves must be secure and tamper-proof. The cryptographic keys used for verification must be protected. And legacy machines might require firmware upgrades to support this capability.
Physical Security Enhancements
Banks are investing in better physical security for ATMs. This includes more tamper-evident seals that make it obvious when someone has accessed the internal components, improved locking mechanisms that are harder to defeat, and surveillance equipment that provides better visibility of ATM activity.
Some institutions have moved ATMs to higher-security locations or removed them from locations with minimal surveillance. Others have implemented facial recognition and movement detection that alerts security when someone spends too long interacting with an ATM in suspicious ways.
Real-Time Monitoring and Anomaly Detection
Institutions are deploying monitoring systems that analyze ATM behavior in real-time. These systems learn the normal pattern of activity for each machine and alert when anomalies occur: unusual dispense operations, communication with unexpected external systems, machines accessing functions they normally don't use.
This monitoring is challenging to implement because ATMs are diverse, behave differently depending on location and configuration, and generate enormous volumes of log data. But it's gradually becoming more sophisticated as banks invest in better analytics capabilities.
Rapid Incident Response and Isolation
Banks are also improving their incident response capabilities. When a jackpotting attack is detected or suspected, response teams can now isolate the machine from the network, disable remote functions, physically secure the machine for forensic investigation, and prevent potential lateral movement to other systems.
Some institutions have established specialized teams focused specifically on ATM security incidents. These teams have the expertise to quickly determine what happened and implement containment measures.
Collaborative Information Sharing
The financial sector has established information sharing groups where banks and ATM manufacturers share threat intelligence. When a new attack variant emerges, this information is shared across the industry quickly, allowing other institutions to prepare defenses or check if their systems are affected.
Government agencies, particularly the FBI and Secret Service, also participate in these information sharing networks, helping accelerate the distribution of threat intelligence.

The Global Perspective: Jackpotting Around the World
Regional Variations in Attack Patterns
Jackpotting attacks aren't distributed evenly across the globe. Certain regions experience higher concentrations of attacks. Europe, particularly Eastern Europe, has been a significant hub of jackpotting activity. Africa has seen dramatic increases in attacks in recent years. Parts of Asia are experiencing growing problems.
The regional variations reflect different factors: the prevalence of vulnerable ATM models, the presence of organized crime networks with the expertise to execute attacks, the strength of local law enforcement, and the profitability relative to other criminal activities.
Some regions have ATM fleets that are newer and better maintained, making them harder targets. Others rely heavily on older machines that are trivial to exploit. The economics of crime differ by region, affecting which criminal groups invest resources in jackpotting versus other illicit activities.
International Law Enforcement Challenges
Criminal networks exploit jurisdictional boundaries. An attack might be executed in one country, the stolen cash funneled through another country, and the proceeds laundered in a third country. Coordinating law enforcement across international borders is time-consuming and often ineffective.
Different countries have different legal frameworks, different priority levels for investigating financial crimes, and different technical capabilities. A well-resourced FBI might investigate jackpotting attacks aggressively, while other national law enforcement agencies might lack the expertise or budget.
Criminal organizations exploit these disparities intentionally. They conduct operations where they know law enforcement coordination is weak. They move stolen cash through money laundering networks that span continents.
Some countries have made jackpotting a priority. Others treat it as a minor property crime not worthy of significant investigative resources. This patchwork of enforcement creates opportunities for criminals.

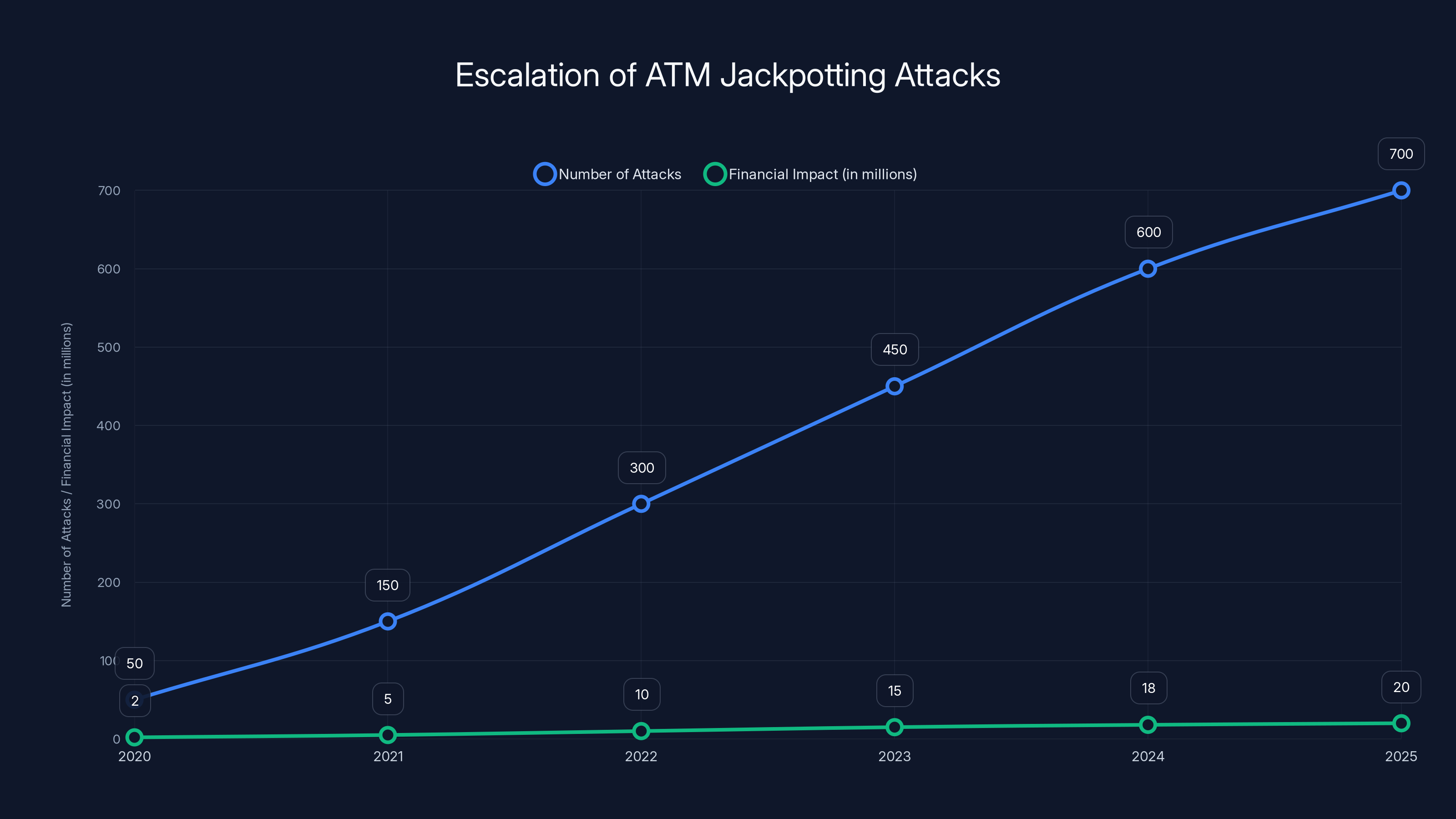
The number of ATM jackpotting attacks has sharply increased from 50 in 2020 to 700 in 2025, with financial losses growing from
The Future of ATM Security: Emerging Technologies and Approaches
Biometric Authentication and Advanced Verification
The future of ATM security likely includes more advanced authentication mechanisms. Facial recognition, fingerprint scanning, and behavioral biometrics could make it much harder for malware to authorize transactions without legitimate user interaction.
However, implementing these technologies across millions of existing ATMs is a slow and expensive process. Not all customers appreciate additional security measures that slow down transactions. And biometrics introduce their own security challenges if not implemented carefully.
Blockchain and Distributed Ledger Verification
Some researchers propose using blockchain or other distributed ledger technologies to create tamper-proof records of ATM transactions and machine state. The idea is that any unauthorized modifications to the machine or its records would be immediately detectable.
While theoretically sound, practical implementation would require significant changes to ATM architecture and would likely slow down transaction processing. The technology is still in the research phase.
AI-Powered Behavioral Analysis
Machine learning and artificial intelligence could enable more sophisticated real-time detection of jackpotting attacks. Systems could learn the normal operational patterns of each ATM model, location, and time period, then flag anomalies that might indicate an attack in progress.
The challenge is reducing false positives while maintaining high detection accuracy. ATMs behave variably depending on legitimate factors, and distinguishing attack-related anomalies from normal variance is difficult.
Hardware-Based Security and Secure Enclaves
ATM manufacturers are beginning to incorporate hardware-based security mechanisms, including secure processors and trusted execution environments. The idea is that the most critical functions, particularly cash dispensing authorization, run in a protected area that's resistant to malware and physical attacks.
Implementing this across the installed base of ATMs will take years, but it represents the long-term direction for the industry.

Regulatory Response and Government Action
FBI Guidance and Recommendations
The FBI's security bulletins on jackpotting provide specific guidance to financial institutions. Recommendations include regular security assessments, firmware patching, physical security upgrades, monitoring for suspicious activity, and coordination with law enforcement.
These recommendations are based on field experience and investigation of actual attacks. They represent the current best practices for defending against jackpotting threats.
Legislation and Enforcement
Government agencies are working to enhance their ability to investigate and prosecute jackpotting attacks. Federal charges can include violations of the Computer Fraud and Abuse Act, the Economic Espionage Act, and money laundering statutes.
Some jurisdictions are considering specific legislation focused on ATM attacks to create enhanced penalties and clearer legal frameworks for prosecution.
International Cooperation
Law enforcement agencies from multiple countries have established joint task forces to investigate international jackpotting networks. Information sharing agreements allow agencies to work together on cases that cross borders.
However, cooperation is limited by differing legal systems, extradition treaties, and political considerations. True international coordination remains challenging.
Best Practices for Banks and Financial Institutions
Comprehensive Security Assessment
Institutions should conduct thorough security assessments of their entire ATM fleet. This includes identifying which machines run vulnerable operating systems, which machines have unpatched security vulnerabilities, which machines have weak physical security, and which machines are in high-risk locations.
These assessments should be updated regularly as new vulnerabilities are discovered and the threat landscape evolves.
Prioritized Remediation Strategy
Based on assessment results, institutions should develop a prioritized remediation strategy. The machines that pose the highest risk should be addressed first. Remediation might include patching, firmware updates, physical security improvements, or complete replacement.
Institutions should also establish timelines for remediation and commit resources to meet those timelines. Security should not be perpetually deferred in favor of operational priorities.
Employee Training and Awareness
Staff who service and maintain ATMs should understand the risks of physical tampering and know what to look for. Branch staff who interact with customers should know how to respond if someone reports suspicious ATM activity.
Security-conscious employees are an important line of defense against jackpotting attacks.
Monitoring and Detection Infrastructure
Institutions should invest in monitoring systems that provide real-time visibility into ATM activity. These systems should generate alerts when suspicious activity is detected, enabling rapid response.
Monitoring should be tailored to each institution's specific environment and needs. One-size-fits-all solutions are unlikely to be effective.
Incident Response Planning
Institutions should have documented procedures for responding to suspected jackpotting attacks. These procedures should include steps for isolating machines, preserving evidence, contacting law enforcement, and conducting forensic analysis.
Regular drills and testing of these procedures help ensure that when a real incident occurs, the response is swift and effective.

Looking Ahead: The Evolving Threat Landscape
Predictions and Trends
Security researchers and FBI analysts predict that jackpotting attacks will continue to evolve and potentially increase in frequency. Several factors support this prediction.
First, the barrier to entry continues to lower. As more detailed information about vulnerabilities becomes public, as tools become more readily available, and as criminals develop more user-friendly exploit packages, more actors will attempt jackpotting.
Second, the profitability remains high. Even with law enforcement increasingly focused on the problem, jackpotting offers attractive returns for relatively low risk compared to other crimes.
Third, defenders are struggling to keep pace. The diversity of ATM models, the slow pace of security updates, and the prevalence of legacy systems that can't easily be patched create a massive installed base of vulnerable machines.
Potential Game-Changing Developments
The threat landscape could shift dramatically if certain developments occur. For example, if a significant percentage of ATMs are upgraded to include modern hardware-based security features, the attack surface would shrink considerably. If law enforcement significantly escalates prosecution and incarceration of jackpotting operators, the risk-reward calculation might change for some criminals. If major ATM manufacturers establish requirement or incentives for regularly updated security firmware, the prevalence of unpatched vulnerabilities would decrease.
However, none of these developments are guaranteed to occur quickly. The financial sector moves slowly. Large-scale replacement of ATM infrastructure takes years. Regulatory and legislative changes happen gradually.
Meanwhile, criminal organizations continue to innovate, adapt, and refine their techniques.

Consumer Protection: What Should You Know?
Recognizing Vulnerable ATMs
While the general public doesn't need to understand the technical details of jackpotting, awareness of the issue is valuable. If you notice an ATM that shows signs of physical tampering, unusual behavior, or doesn't seem to be working correctly, it's reasonable to avoid using it and report it to the institution.
Signs of potential tampering include loose panels, unusual additions or devices attached to the machine, obscured camera lenses, and machines that have been offline and recently brought back online.
Using ATMs Safely
Basic ATM safety practices are relevant: use ATMs in well-lit, visible locations, avoid machines in isolated areas, shield the PIN pad when entering your PIN to prevent skimming devices from capturing it, and check your account regularly for unauthorized transactions.
While jackpotting attacks don't directly compromise customer accounts, the general security of the ATM and the institution is relevant to the security of your money.
Staying Informed
Customers of banks that experience jackpotting attacks deserve to be informed about the incident. Responsible banks communicate with customers about security incidents, the measures being taken to prevent future attacks, and any steps customers should take to protect themselves.
If your bank has been the victim of jackpotting attacks, it's reasonable to ask about the specific steps they're taking to improve security and prevent future incidents.

Conclusion: A Problem Without Easy Answers
ATM jackpotting has evolved from academic security research into a serious criminal enterprise that costs the financial system tens of millions of dollars annually. The problem has multiple root causes: aging infrastructure, delayed patching, weak physical security in some locations, insufficient real-time monitoring, and sophisticated criminal organizations with the resources to develop and deploy specialized attack tools.
No single solution will eliminate jackpotting entirely. The problem requires a multi-layered approach involving hardware improvements, software security enhancements, physical security measures, monitoring and detection, rapid incident response, and law enforcement action.
The financial sector is responding to the threat, but the pace of response is not matching the pace of threat evolution. Criminals are innovating faster than defenders are deploying countermeasures. The installed base of vulnerable machines is enormous and grows only slowly as institutions replace aging equipment.
For individual institutions, the priority should be a comprehensive understanding of your own ATM security posture, a commitment to remediation of identified vulnerabilities, investment in monitoring and detection capabilities, and coordination with law enforcement and industry peers.
For the broader financial sector, continued investment in security infrastructure, acceleration of security updates and patches, migration away from legacy operating systems, and development of next-generation ATM security architectures is essential.
For regulators and law enforcement, sustained focus on investigating and prosecuting jackpotting operations, international coordination to disrupt criminal networks, and support for financial institutions' security efforts is critical.
The threat is real, the impact is significant, and the problem is escalating. But with coordinated effort across all stakeholders, the trend can be reversed. The challenge is ensuring that defense innovation happens faster than offense innovation—a race that, for ATM security, has not yet been won.

FAQ
What exactly is ATM jackpotting?
ATM jackpotting refers to a cyberattack where hackers gain access to an ATM's internal systems and force the machine to dispense cash automatically without processing legitimate transactions. Attackers typically use a combination of physical access (opening the machine) and digital exploitation (installing malware or executing commands) to bypass the machine's normal security controls and authorization processes.
How do attackers typically gain access to ATMs?
Attackers use several methods to gain access. They may obtain generic keys that fit standard ATM locks (available from industrial suppliers for under $50), use physical force to open machines, observe bank technicians during maintenance, or compromise ATMs remotely through network vulnerabilities. Once physically inside the machine, they can install malware, plant devices, or directly manipulate the internal components that control cash dispensing.
What is Ploutus and why is it so dangerous?
Ploutus is a family of malware specifically designed to compromise ATMs and force them to dispense cash. It works by gaining control of the Windows operating system running on many ATMs, then using XFS (e Xtensions for Financial Services) software to instruct the cash dispensing unit to operate. Ploutus is dangerous because it works on ATMs from multiple manufacturers, is regularly updated by criminals, and can be obtained on dark web forums, making it accessible to various criminal groups worldwide.
How much money are hackers stealing through jackpotting?
According to the FBI, hackers conducted over 700 jackpotting attacks in 2025 alone, stealing at least
What can banks do to protect against jackpotting attacks?
Financial institutions should implement multiple defensive layers: regular security assessments of ATM fleets, prompt application of security patches and firmware updates, enhanced physical security for machines in vulnerable locations, real-time monitoring systems that detect unusual ATM activity, comprehensive incident response procedures, and regular training for staff. Additionally, banks should coordinate with law enforcement and participate in industry information-sharing groups to stay current on emerging threats and attack techniques.
Can customers' accounts be compromised by jackpotting attacks?
No. Jackpotting attacks target the ATM machine itself, not customer accounts. Attackers instruct the machine to dispense cash without processing legitimate transactions, so there are no fraudulent charges to customer accounts. However, the fact that an ATM has been compromised might raise broader concerns about security practices at that institution, and customers deserve to be informed about incidents at their bank.
How can I protect myself from jackpotting-related risks?
While jackpotting doesn't directly threaten your account, you should use ATMs in well-lit, visible locations with good surveillance, avoid isolated machines, shield the PIN pad when entering your PIN, check your account regularly for unauthorized transactions, and report any ATM that shows signs of tampering or unusual behavior to your bank. If your institution experiences jackpotting incidents, ask about the specific steps they're taking to improve security.
What is XFS software and why is it vulnerable?
XFS (e Xtensions for Financial Services) is a standardized software interface that allows different ATM software applications to communicate with various hardware components like the cash dispenser, PIN pad, and card reader. XFS was designed assuming ATMs would operate in secure environments. However, if attackers gain control of the ATM's operating system, they can invoke any XFS function they want, including commands that force the cash dispenser to operate without legitimate authorization.
Are older ATMs more vulnerable than newer ones?
Generally yes. Older ATMs often run outdated operating systems like Windows XP or Windows 7 that no longer receive security updates and have hundreds of known vulnerabilities. Many banks keep machines operational for 10-20 years to minimize replacement costs, creating a massive installed base of vulnerable equipment. Newer machines may have better security features, though implementation varies significantly between manufacturers.
What is law enforcement doing to combat jackpotting?
Federal agencies like the FBI and Secret Service investigate jackpotting operations and have established joint task forces to target criminal networks. The FBI publishes security bulletins warning financial institutions about threats, and law enforcement agencies from multiple countries share intelligence about international criminal operations. However, prosecution remains challenging due to jurisdictional complications and the international nature of many criminal networks.

Key Takeaways
- ATM jackpotting attacks exceed 700 incidents annually, stealing $20+ million with significant undetected losses
- Ploutus malware and similar tools exploit XFS vulnerabilities to force machines to dispense cash automatically
- Attackers combine physical access (using generic keys or force) with digital exploitation (malware installation) for rapid, high-reward attacks
- Defense requires multi-layered approach: firmware updates, physical security, real-time monitoring, incident response planning, and law enforcement coordination
- Organized international criminal networks now operate jackpotting as a sophisticated enterprise with specialized roles and supply chains
- Banks must conduct comprehensive security assessments and maintain urgent remediation timelines for vulnerable ATM fleets
- The threat continues accelerating as criminal techniques democratize and legacy ATM infrastructure persists across the financial sector

Related Articles
- North Korean Job Scammers Target Developers with Fake Interviews [2025]
- Billions of Exposed Social Security Numbers: The Identity Theft Crisis [2025]
- Keenadu Android Backdoor: Firmware Malware Threat [2025]
- Why AI Models Can't Understand Security (And Why That Matters) [2025]
- N-Day Vulnerabilities: Why Patched Exploits Are Now Your Biggest Security Risk [2025]
- Odido Telco Breach Exposes 6.2M Users: Complete Analysis [2025]
![ATM Jackpotting Attacks: The Rising Threat to Cash Machines [2025]](https://tryrunable.com/blog/atm-jackpotting-attacks-the-rising-threat-to-cash-machines-2/image-1-1771542572096.jpg)



