DHS Subpoenas for Anti-ICE Accounts: What You Need to Know About Government Surveillance [2025]
It started quietly. A few subpoenas here and there to major tech companies asking for user information. Nothing outrageous. But somewhere between last year and now, something shifted. The Department of Homeland Security didn't just send a handful of requests to unmask anonymous accounts critical of Immigration and Customs Enforcement. They sent hundreds.
This isn't about privacy in the abstract anymore. This is about what happens when government agencies decide they want to know who's saying what online, and they have the legal tools to make it happen. And here's the uncomfortable part: most tech companies are complying, at least some of the time.
The trend represents a significant escalation in how federal agencies approach digital surveillance of political speech. What was once a rare occurrence has become routine. What required judicial oversight in the past now operates under administrative subpoenas that don't need a judge's approval. The implications ripple through our digital ecosystem in ways that most people don't fully understand yet.
You might be thinking this doesn't affect you. You're not posting about ICE locations. You're not running an anti-enforcement account. But the infrastructure being built here doesn't stay confined to one issue or one agency. Once it exists, it gets reused. Once the precedent is set, others follow. This article breaks down what's happening, why it matters, and what you should know about your own digital presence.
TL; DR
- Hundreds of subpoenas: DHS has dramatically escalated requests to identify owners of anonymous accounts criticizing ICE operations, as reported by The New York Times.
- Administrative tool: These subpoenas don't require court approval, giving the department broad authority to demand user information, according to The Washington Post.
- Tech company compliance: Google, Meta, and Reddit have complied with at least some requests, though they claim to push back on overly broad demands, as noted by TechCrunch.
- Legal precedent: Some account holders have fought back in court and won, forcing the agency to withdraw subpoenas, as highlighted by EFF.
- Broader implications: This infrastructure will likely expand beyond ICE criticism to other forms of political speech and activism, as discussed in ACLU's analysis.
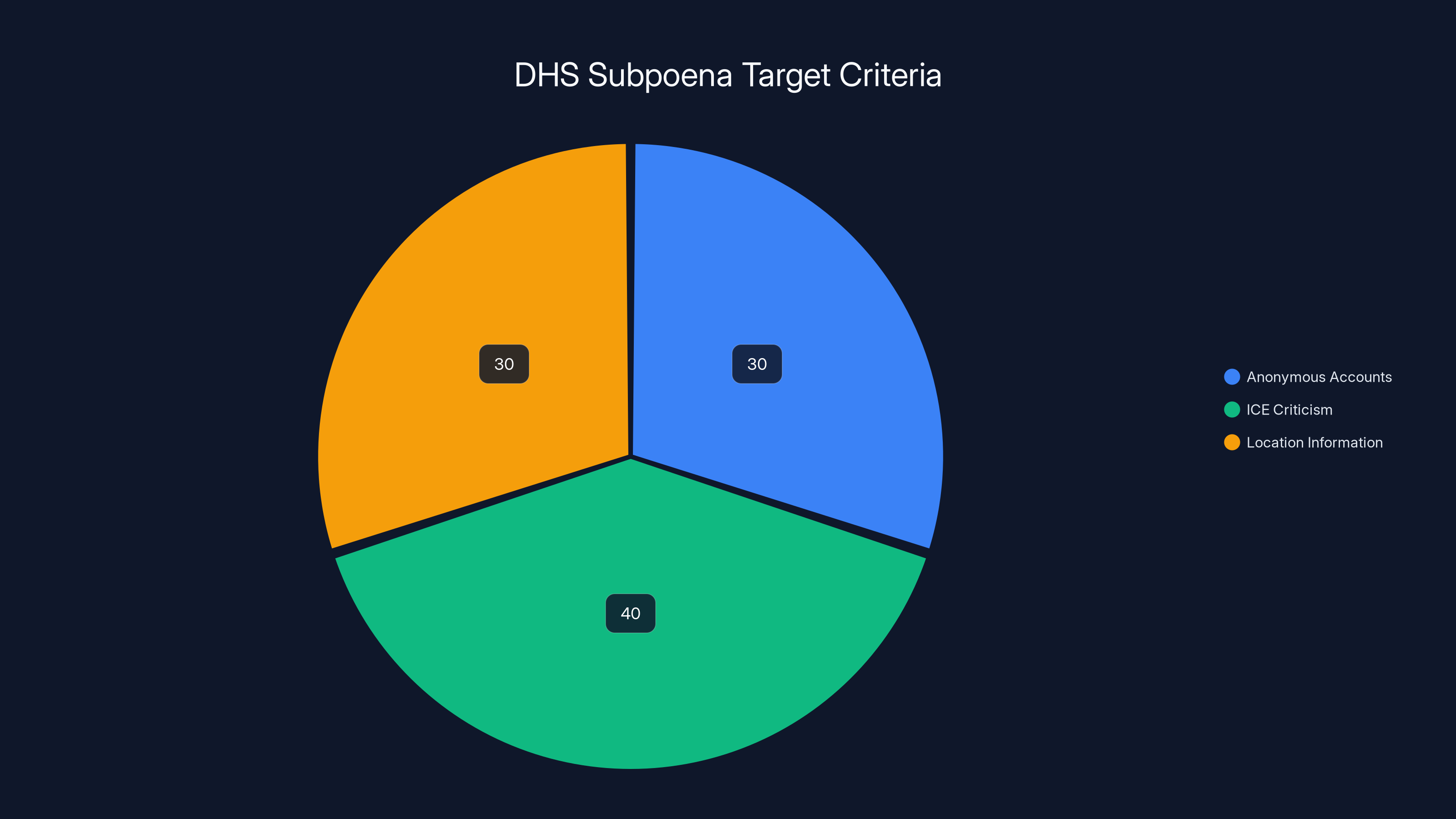
Estimated data suggests that DHS subpoenas are distributed among anonymous accounts, ICE criticism, and location information posts, each contributing significantly to the targeting criteria.
The Escalation: From Rare to Routine
Let's establish the baseline here. Government agencies requesting user information from tech companies isn't new. But there's a massive difference between occasional requests and what's happening now.
Prior to recent months, these kinds of requests were handled sparingly. They were exceptions. Serious criminal investigations warranted subpoenas. The system was built with friction. You needed probable cause. You needed judicial review. You needed to justify why you couldn't investigate any other way.
That friction has largely disappeared.
The New York Times reported that DHS has fundamentally changed how it operates. Instead of targeting specific criminal investigations, the department is now using administrative subpoenas as a primary investigative tool. The scale is staggering: hundreds of subpoenas going to Google, Reddit, Discord, and Meta specifically targeting accounts that criticize ICE or describe the location of ICE agents.
Why does this matter? Because administrative subpoenas operate in a completely different legal universe than court-ordered warrants. They don't require judicial approval. They don't require showing probable cause. They don't require demonstrating that the information sought is actually relevant to an ongoing criminal investigation. An administrative official can simply issue one, and the tech company receives it.
Google and Meta have stated they challenge overbroad requests and try to notify users when they can. Reddit has been less public about its practices. Discord received a significant number of these subpoenas, though the full scope remains unclear. The key question nobody's asking is this: how many times are these companies choosing not to push back?
Compliance rates are important here, but they're also largely invisible. We only hear about cases where:
- The company refuses and it becomes public knowledge
- The account holder sues after being identified
- A journalist reports on the practice
For every case we know about, there are likely dozens we don't.
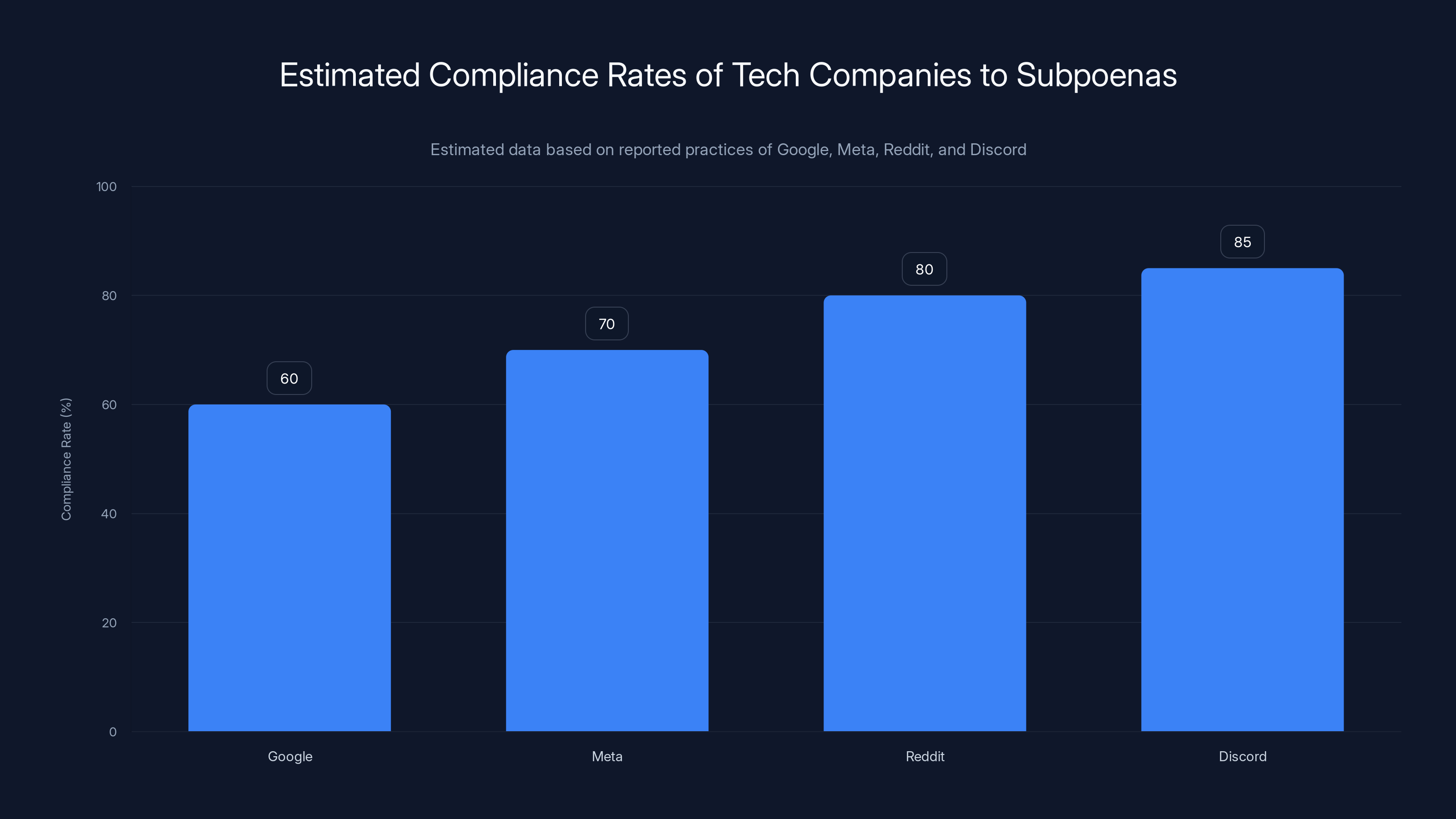
Estimated data suggests varying compliance rates among tech companies, with Discord potentially having the highest compliance rate. Estimated data.
The Legal Framework: Administrative Subpoenas Explained
Here's where things get technical, but stick with me because this is crucial to understanding why this matters.
Under federal law, government agencies have the authority to issue administrative subpoenas. These are subpoenas issued directly by an agency official without going through a court. DHS has this authority under its enabling statute, and the agency has used it for decades.
But there's supposed to be a catch. Administrative subpoenas must still be limited. They can only request information relevant to a lawful investigation. They must comply with established limitations. The subpoena can't be unduly burdensome.
In practice, these limitations are incredibly weak.
There's no judge involved. There's no neutral third party evaluating whether the request is reasonable. The company receiving the subpoena can challenge it, but that requires resources and legal expertise. Small tech companies do this. Large ones sometimes do. But the default, the path of least resistance, is compliance.
When Bloomberg investigated this issue, they found five specific cases where DHS sought to identify anonymous Instagram account owners. In those cases, the account holders actually sued when they discovered their information had been demanded. The legal pressure worked. DHS withdrew the subpoenas.
But that only happened because people fought back. How many others never realized they'd been targeted?
The Washington Post subsequently reported on DHS's growing reliance on these administrative subpoenas as a general investigative tool. The agency isn't just using them for serious criminal investigations. They're using them to map networks of activists, to identify who's organizing resistance, to create profiles of people engaged in political speech.
There's a legal question embedded here: Does describing the location of ICE agents constitute criminal activity? Is criticizing ICE enforcement policies something that requires covert investigation? These questions matter because they determine whether the subpoenas are even lawful, let alone proportionate.

The Target: What Gets You on DHS's Radar
According to reporting, the subpoenas targeted accounts that met specific criteria. They weren't random fishing expeditions (or at least not entirely). DHS was looking for:
- Anonymous accounts: Accounts without real names attached, making identification difficult through normal means
- ICE criticism: Posts that criticized ICE policies, operations, or tactics
- Location information: Posts that described where ICE agents were operating, when they were conducting enforcement actions, or how to identify enforcement vehicles
This third category is where the legal argument gets interesting. DHS could argue (and probably does internally) that posting ICE agent locations is akin to posting police officer locations. It's information that could be used to interfere with law enforcement operations. It could potentially constitute obstruction.
But here's the wrinkle: the First Amendment protects speech about government activities. It especially protects speech criticizing government agencies. You can criticize ICE. You can post about ICE operations. You can describe encounters with ICE agents.
The question of whether you can post real-time location information about federal agents is more complicated. Courts have been relatively protective of this kind of speech, but it's not an absolute right. The analysis gets into questions of intent, impact, and whether the speech is directly inciting illegal activity.
What concerns civil liberties advocates is that DHS doesn't seem to be distinguishing carefully between these categories. They're not just targeting people posting real-time tactical information. They're targeting anyone criticizing the agency.
And here's the thing about targeting: it changes behavior. If you know that criticizing ICE might result in a subpoena to reveal your identity, you become cautious. You self-censor. You stop posting. The government doesn't need to arrest you or threaten you. The mere possibility of identification does the work.
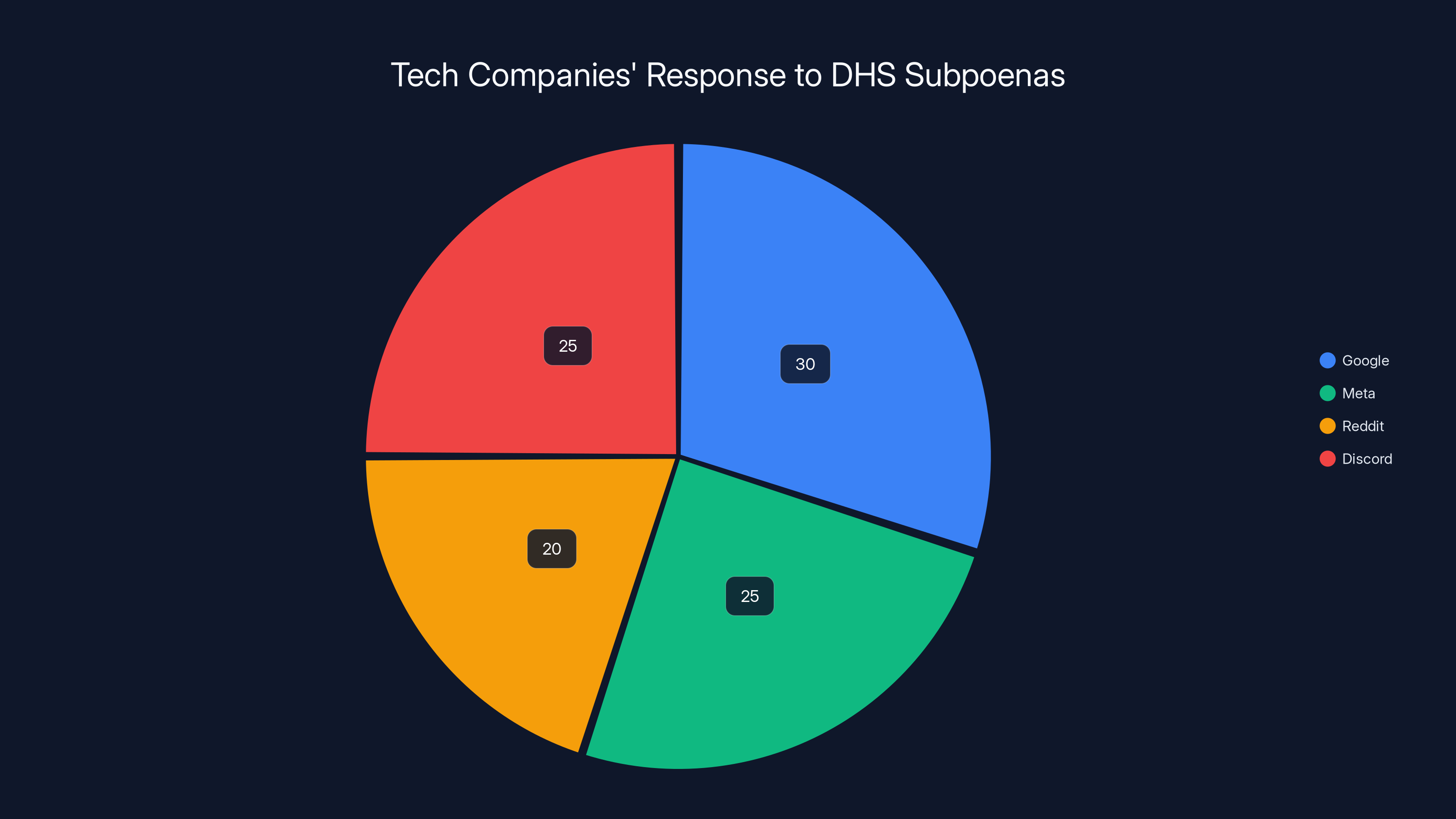
Estimated data suggests Google, Meta, and Reddit complied with some subpoenas, while Discord's response is less clear. Estimated data.
Tech Company Responses: Pushback and Compliance
Google's statement on this issue is instructive. The company says it informs users of subpoenas when it legally can, and it pushes back on requests that are overbroad. That's good. It's also incomplete.
When a subpoena comes in, Google receives a legal notice. If there's no gag order preventing notification, Google can tell the user. But if DHS includes a gag order in the subpoena, Google must comply with the demand for information without notifying the user.
Gag orders are a standard tool in these requests.
Meta's approach is similar. The company has a public transparency report. They disclose when they receive government requests. But the reports come with lag time. By the time Meta acknowledges receiving a subpoena, months have passed. The identification has already happened.
Reddit's response has been notably quieter. The platform received subpoenas but hasn't been as vocal about resisting them or about their scope. This could reflect Reddit's different corporate structure or risk tolerance. It could also reflect the fact that Reddit users are less likely to have legal resources to sue if they discover they've been identified.
Discord received hundreds of these subpoenas. The platform is used heavily by organizing communities, activists, and people discussing sensitive topics. The revelation that DHS was targeting Discord users sparked significant discussion in privacy communities.
Here's what's notable about tech company compliance: none of these companies are claiming they didn't comply. They're claiming they push back sometimes. They inform users when they can. But the baseline is cooperation.
Why? Several reasons:
First, legal obligation: Once a valid subpoena arrives, companies face legal consequences for refusing to comply. They have to comply or file a motion to quash the subpoena in court. That's expensive and time-consuming.
Second, business reality: Maintaining good relationships with law enforcement benefits companies. If DHS views you as cooperative, you get better treatment when disputes arise. If you're seen as obstructionist, you get scrutinized more carefully.
Third, liability exposure: If a company refuses to comply with a subpoena and law enforcement claims that obstruction caused harm, the company could face liability. The legal risk of compliance is lower than the legal risk of refusal.
The Domino Effect: Why This Matters Beyond ICE
One of the most important aspects of this story isn't being discussed enough: the infrastructure precedent.
When DHS successfully uses administrative subpoenas to identify anonymous account holders at scale, they're proving that this approach works. It's effective. It's efficient. It's legally viable (at least so far). What do you think happens next?
Other agencies are paying attention.
The FBI has long been interested in identifying anonymous online speech. Local law enforcement agencies have been requesting location data and user information from platforms for years. DEA, ATF, Secret Service, and other federal agencies all have investigative needs.
Once DHS demonstrates that you can issue hundreds of subpoenas targeting political speech and actually get results, those other agencies think: why aren't we doing this?
The infrastructure being built now isn't just about ICE criticism. It's about mapping networks. It's about understanding which citizens are engaged in activism, organizing, or political opposition. It's about creating databases of who said what, when, and from where.
That's powerful information. It's precisely the kind of information that gets reused in ways the original requestor never imagined.
Consider how surveillance infrastructure gets repurposed:
- Tools built to fight terrorism get used against drug dealers
- Investigative techniques developed for organized crime get applied to protest movements
- Data collected for one purpose gets accessed by agencies with completely different mandates
- Authorities expand the scope of what they consider a legitimate investigative target
The subpoena infrastructure for ICE criticism could easily become the subpoena infrastructure for climate activism, anti-war organizing, election observation, or any other form of political speech the current or future administration decides deserves investigation.
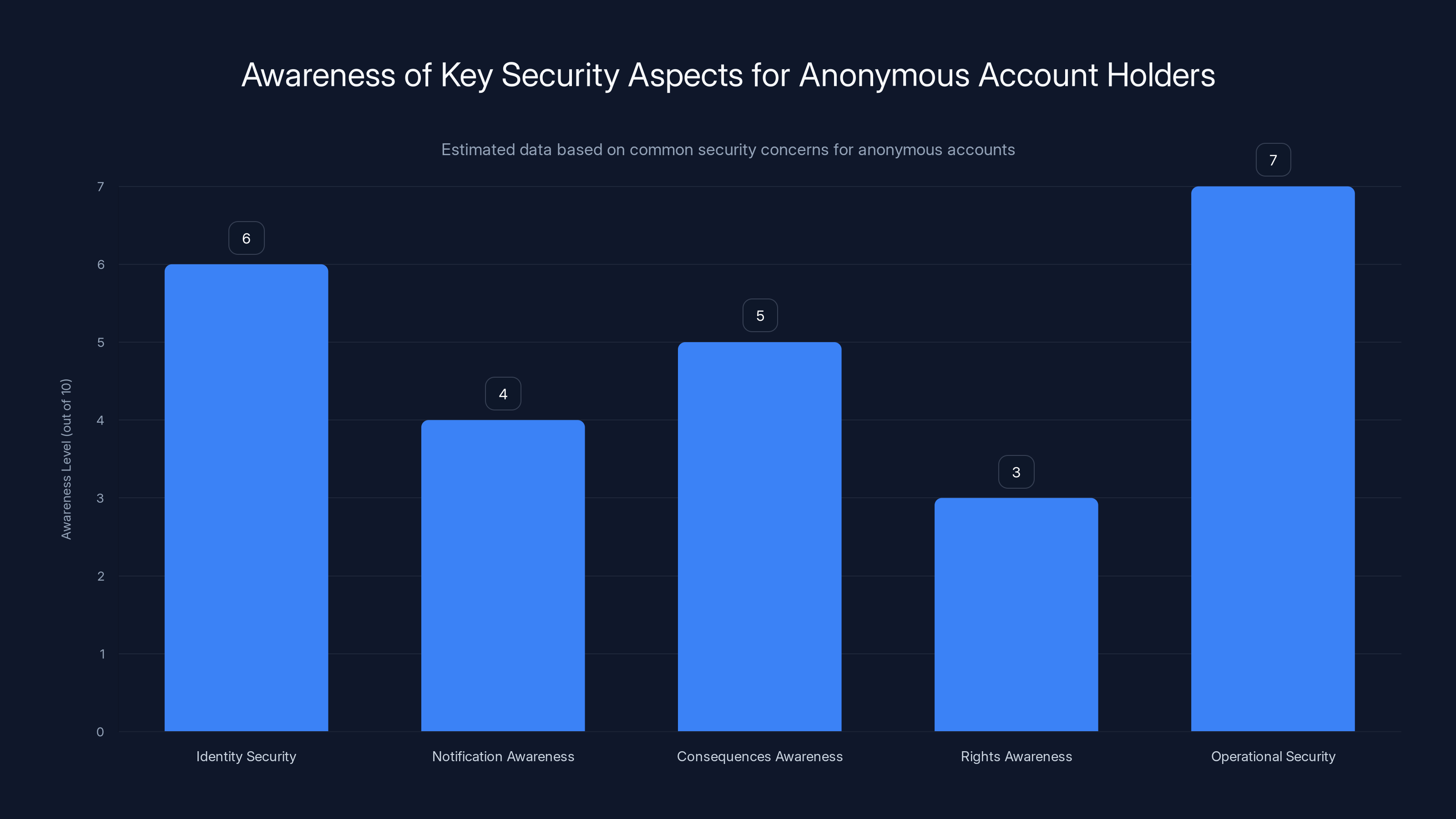
Estimated data suggests varying levels of awareness among anonymous account holders, with operational security being the most understood aspect.
The Legal Fights: When Account Holders Win
For every person quietly complying with a subpoena, there are a few who fight back. Their cases matter because they establish precedent and show that pushback works.
Bloomberg's reporting focused on five cases. In each instance, DHS had sought to identify the owners of anonymous Instagram accounts. The account holders, when they discovered this, sued. The legal challenge worked. DHS withdrew its subpoenas in these cases.
This tells us something important: DHS doesn't necessarily want to fight these cases in court. When faced with a legal challenge from someone with resources, they back down. This suggests that many of the subpoenas might not hold up to judicial scrutiny.
But here's the catch: most account holders never learn they've been targeted. Most don't have lawyers ready to sue. Most don't have the time or resources to fight federal agencies. So DHS can operate confident that the vast majority of subpoenas will result in identification without resistance.
The ones that make it to court are unusual. They involve people with legal resources, or people with organizations behind them, or cases that draw media attention. For everyone else, compliance is the default.
This creates a perverse incentive structure: DHS can issue broad subpoenas knowing that most won't be challenged. Even if they're overbroad or legally questionable, they'll probably result in the desired information anyway. The legal system only constrains behavior when people actually fight back, and most people don't have the resources to do that.
Privacy in a Subpoena Age: What Anonymity Means Now
There's a philosophical question buried in this story: what does online anonymity mean in 2025?
People use anonymous accounts for all sorts of legitimate reasons. Activists operating in repressive conditions use them for safety. Marginalized people use them to avoid harassment. Whistleblowers use them to expose wrongdoing. People with medical conditions use them to discuss their situations without risking discrimination.
Anonymity serves important social functions. It enables free speech in situations where identified speech would be costly or dangerous. It creates space for thinking out loud without professional or social consequences.
But anonymity only works if it's actually anonymous. If anyone determined enough can subpoena your identity, if tech companies are cooperating with those subpoenas, if account holders don't even know they're been identified, then anonymity becomes a paper shield.
The question of how to balance government investigative needs with privacy rights isn't new. Courts have been working through these issues for years. But the scale matters. Hundreds of subpoenas isn't a security measure. It's a dragnet.
When government agencies can identify anonymous account holders at scale without judicial oversight, something fundamental changes. The space for dissent shrinks. The cost of political speech rises. People become aware that their anonymity is provisional, contingent on the government deciding they're not a priority.
That awareness changes behavior. Social scientists call this the "chilling effect." Even if DHS never targets you, the knowledge that they could is enough to make you think twice about what you post.
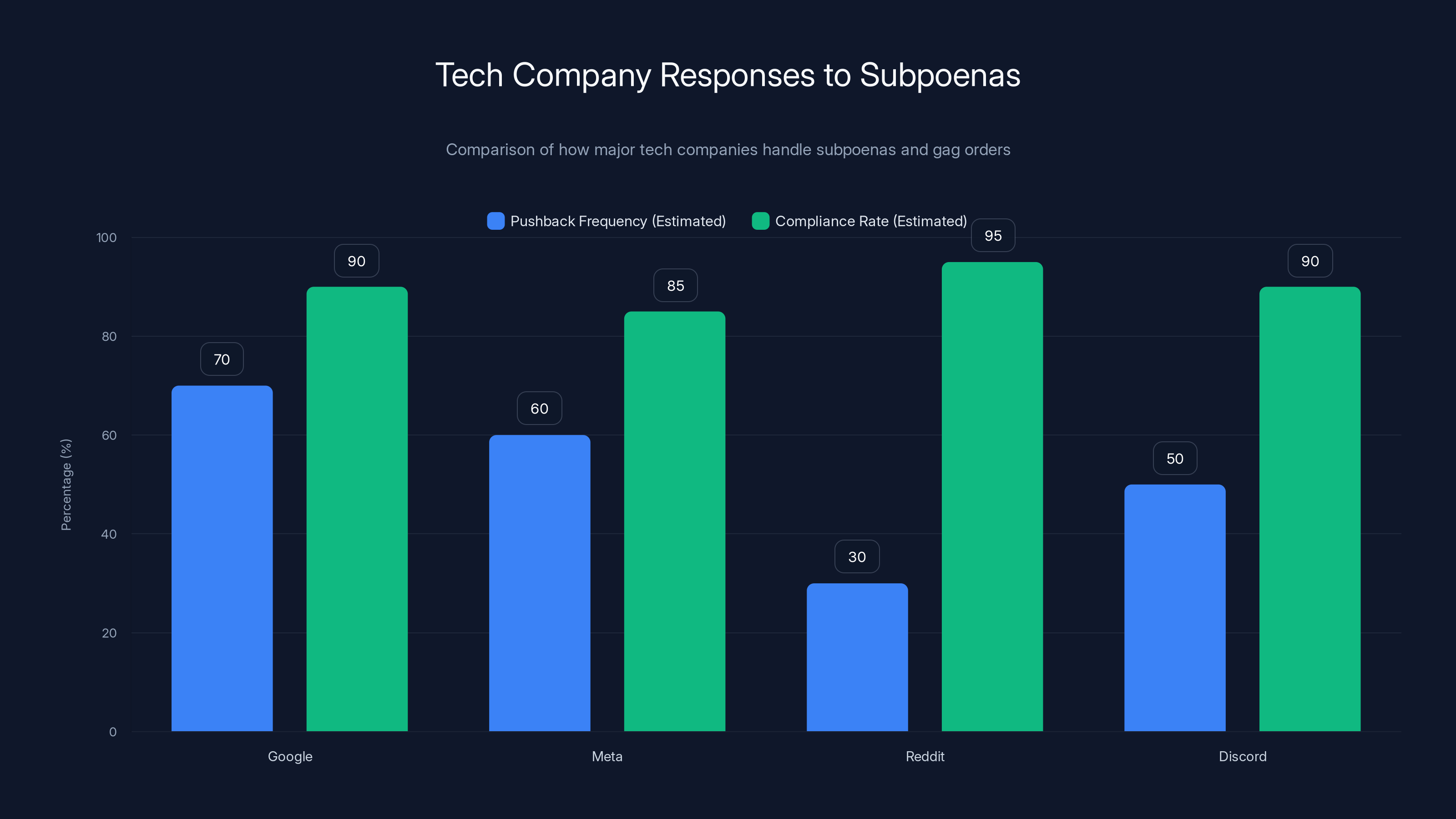
Google and Meta are more vocal about pushing back against subpoenas, while Reddit and Discord show high compliance rates. Estimated data based on narrative context.
The Infrastructure of Identification: How DHS Connects the Dots
Here's something most people don't think about: getting a name and address isn't the end of the investigation. It's the beginning.
Once DHS has identified an anonymous account holder, that person enters a database. Their information gets connected to other data points. DHS can request the person's social media history. They can get location data from the account provider. They can see who they're messaging with, what they're following, what organizations they're affiliated with.
One identification becomes a network map.
This is especially relevant for organizing communities. If DHS identifies people organizing actions, they can map the entire network. They can see who talks to whom. They can identify people playing coordinator roles. They can understand the structure of activist groups.
That's incredibly valuable information to a law enforcement agency. And it flows directly from the subpoena power.
Even if no charges are ever filed, even if no criminal investigation ever happens, the government now has comprehensive intelligence on who's organizing what. They have databases of activists. They have relationship maps. They have patterns of behavior.
Historically, this kind of intelligence work required much more legal process. Police would need to develop probable cause. They'd need to go through courts. They'd need to justify why surveillance was necessary.
Administrative subpoenas short-circuit that process. They allow intelligence gathering without traditional oversight. And they do it at scale.

International Implications: How US Practices Spread
There's a broader pattern worth noting. When the United States develops new surveillance capabilities or new legal tools for identifying people, other countries pay attention.
Authoritarian governments actively study how democracies rationalize surveillance. They use our legal precedents to justify their own practices. They point to American techniques and say: if the US government does this, why can't we?
The subpoena infrastructure for identifying anonymous account holders will eventually be cited by governments around the world to justify their own identification programs. Countries that want to suppress dissent can point to US precedent and claim they're following established democratic practices.
This isn't hypothetical. We've already seen it happen with encryption backdoors, with data retention requirements, with facial recognition tools. Surveillance infrastructure built in the US becomes a template that gets replicated globally.
Activists in countries with less robust legal protections are watching this. They're seeing that even in the United States, anonymity is no longer reliable. If US government can identify you, Chinese government can too. If it's legal here, it becomes harder to argue against it elsewhere.
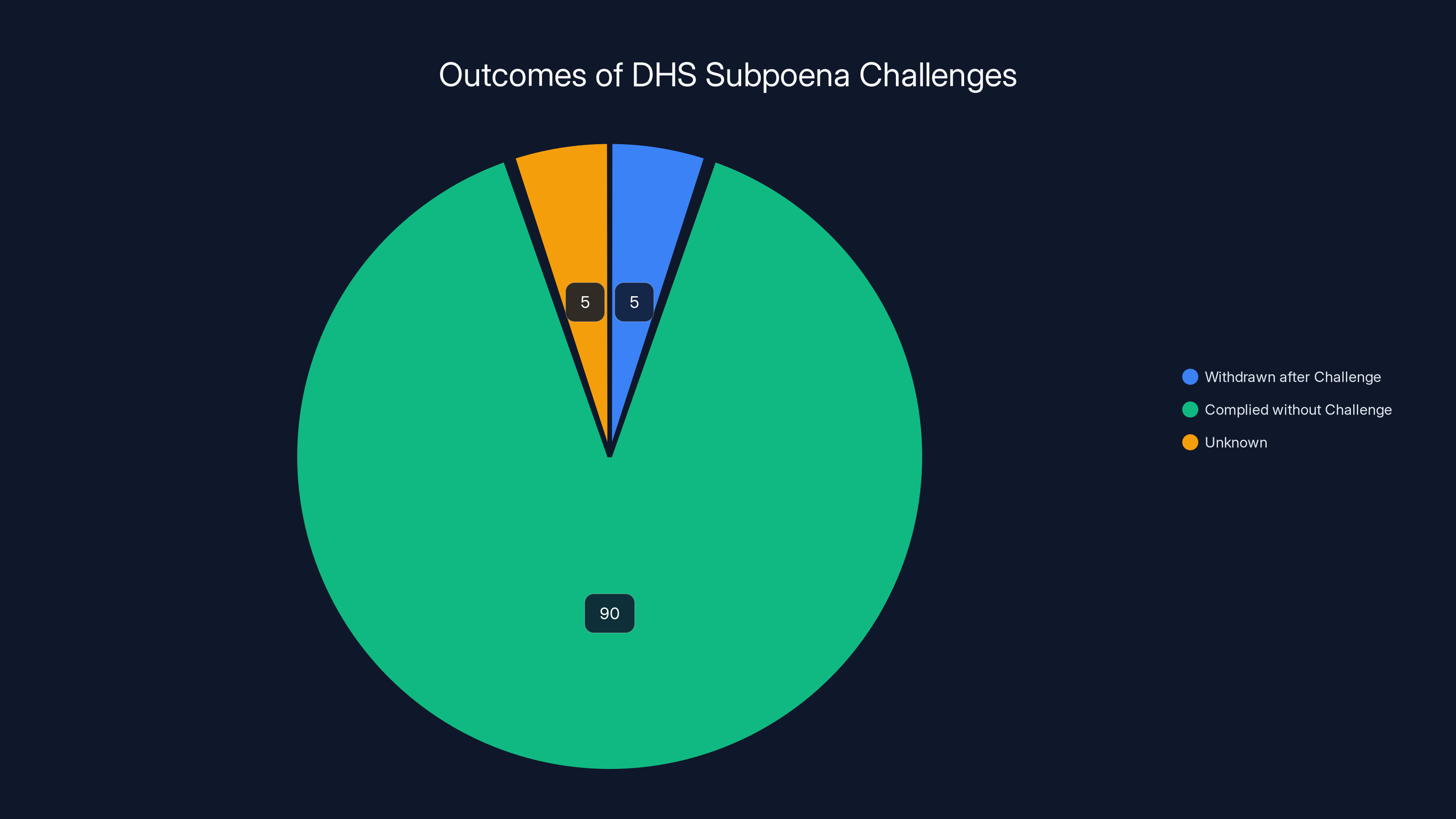
Estimated data suggests most DHS subpoenas go unchallenged, with only a small percentage resulting in withdrawal after legal pushback. Estimated data.
The First Amendment Question: Political Speech and Government Power
Underlying all of this is a constitutional question: can the government use administrative subpoenas to identify people engaged in protected political speech?
The First Amendment doesn't protect all speech. It protects most speech, but there are categories of unprotected speech: true threats, incitement to imminent lawless action, obscenity, fraud, and a few others. The question is whether describing ICE agent locations or criticizing ICE policies falls into those categories.
Most First Amendment scholars would say no. Criticism of government agencies is core protected speech. Describing government activities is protected speech. Even posting location information about government officials might be protected depending on context and intent.
But there's a gap between what's constitutionally protected and what law enforcement can actually do.
Even if the speech is protected, the government can still conduct investigations. Even if the subpoenas are legally questionable, they can still be issued. By the time the question gets to a court, the identification has already happened. The harm has already been done.
This is partly why the system is so effective from a law enforcement perspective: the cost of pushback is high, but the cost of compliance is low. Even when legally questionable, most subpoenas succeed in their purpose before they're ever challenged.
First Amendment advocates argue that identifying people based on their political speech requires much higher legal barriers. They argue that the government shouldn't be able to subpoena user information for someone engaged in protected speech without going through courts, without showing probable cause of a crime, without meeting rigorous standards.
DHS essentially argues that describing ICE agent locations or organizing activities that interfere with ICE operations crosses the line from protected speech into obstruction or other crimes. From that perspective, identifying the people involved is just standard investigative work.
This debate isn't resolved. Cases are still working through courts. But the practical reality is that DHS is operating as if the subpoena power is legitimate and broadly applicable, and they're doing it at scale.

What Account Holders Should Know: Practical Implications
If you maintain anonymous accounts that discuss ICE activities, immigration enforcement, or related topics, you should understand the situation you're operating in.
First, understand that your identity is not secure. Tech companies can be subpoenaed. They will cooperate. Your IP address, device information, and account creation data can be requested and provided. Using VPNs helps, but it's not a complete solution. Tech-savvy investigators can often trace beyond VPN usage.
Second, understand the notification situation. If you receive notification from a tech company that your information was subpoenaed, you've been lucky. It means the subpoena didn't include a gag order. Many subpoenas do include gag orders. You might never know you've been identified.
Third, understand the consequences that might follow. Identification doesn't automatically mean charges will be filed. But it does mean you're now in databases. You're connected to networks of interest to federal law enforcement. Future interactions with authorities will happen with that knowledge.
Fourth, understand your rights. If you learn you've been subpoenaed, you can file a motion to quash the subpoena. You can hire a lawyer to challenge it. You can go public with the information, which sometimes creates pressure on agencies to back down. Some organizations have legal resources to help with this kind of case.
Fifth, understand operational security. If anonymity is important to your safety, consider how you access your anonymous accounts. Consider what information you're sharing. Consider whether your online activity could be correlated with your offline identity through metadata patterns.
The Regulatory Response: What's Missing
One striking aspect of this situation is that there's been remarkably little legislative response.
Congress hasn't passed laws limiting DHS's subpoena authority. They haven't required judicial approval for administrative subpoenas seeking to identify people engaged in political speech. They haven't imposed transparency requirements that would let us understand the scope of this practice.
Part of that reflects the fact that surveillance tends to be bipartisan when it targets the other side's activists. Republicans worried about antifa threats might not mind tools targeting left-wing activism. Democrats might not mind tools targeting right-wing organizing. It's easier to support broad surveillance powers when you believe you won't be targeted.
But silence from Congress is de facto approval. Without legislative constraints, DHS can continue expanding this practice.
Some civil liberties organizations have called for legislation requiring judicial approval for subpoenas seeking to identify anonymous speakers. They've called for transparency reports showing how many subpoenas are issued and what they target. They've called for limitations preventing identification solely based on political speech.
None of that has happened yet.
Some states have passed stronger privacy laws. California's privacy legislation includes some provisions relevant to this. But state laws can't constrain federal agencies, and DHS can simply argue federal authority preempts state law.
The regulatory gap remains. Government agencies have powerful tools. Tech companies have weak incentives to resist. Users have limited information and limited resources. It's a system that heavily favors government surveillance.

International Precedent: Surveillance Creep Elsewhere
This isn't uniquely American, though the Constitution provides some protections that don't exist elsewhere.
European governments have also been pressuring tech companies for user information. The UK government has been increasingly aggressive about identifying anonymous online speakers, especially in cases involving threats or harassment. The Australian government has been pushing tech companies for user information to combat extremism.
In less democratic countries, the situation is much worse. Chinese authorities pressure tech companies constantly for user information. Russian authorities are increasingly aggressive about identifying dissidents online. Middle Eastern governments use subpoena-like mechanisms to suppress political speech.
The US system matters because it sets precedent. When American law enforcement develops new surveillance tools or new legal theories about when they can identify users, that becomes a template. It becomes a justification that other governments use.
Conversely, European privacy protections sometimes impose standards that American companies have to follow globally. If European law requires much higher bars for identification, that sometimes protects people in other countries too.
But overall, the trend is toward more surveillance, more identification, more mapping of networks. The infrastructure keeps expanding.
The Future: How This Escalates
If current trends continue, we should expect:
-
Expansion to other targets: Administrative subpoenas that started with ICE criticism will expand to other topics. Climate activists, election observers, drug policy reformers, immigration advocates, and many others will eventually be in the crosshairs.
-
Increased technical sophistication: As DHS gets better at identification, they'll build more sophisticated profiles. They'll combine subpoena data with other data sources. They'll use AI to find connections between accounts and people.
-
More tech company cooperation: Without legal barriers, tech companies will continue complying. They might push back on the most egregious requests, but the baseline will be cooperation.
-
Network mapping at scale: Instead of targeting individual accounts, government will use subpoena data to map entire networks of activism and organizing.
-
Normalization of surveillance: As more people experience or learn about subpoenas, the knowledge that anonymity isn't protected will become common sense. People will stop trusting that anonymous accounts are actually anonymous.
-
Spillover to other countries: US precedent will justify similar surveillance in other countries. Democratic countries will cite US practices. Authoritarian countries will use them as cover for more aggressive surveillance.
These aren't certain predictions. They're reasonable extrapolations from current trends. They could be prevented through legislation, through tech company resistance, through court decisions, or through public pressure.
But without intervention, the trajectory is clear. Surveillance expands. Anonymity shrinks. The infrastructure of identification becomes more sophisticated. Government gets more powerful.
What You Can Do: Individual and Collective Action
This isn't just a problem for other people to solve. It affects everyone who cares about privacy, about freedom of speech, about limits on government power.
Individual actions:
- Support digital privacy tools: Use VPNs, encrypted messaging, and other privacy-protecting technologies.
- Be thoughtful about what you post and where: Even if you're using a real name, consider the implications of what you're sharing.
- Support organizations working on these issues: Civil liberties groups, privacy organizations, and internet freedom advocates need resources.
- Tell your representatives: Contact Congress members and let them know you care about privacy rights and limits on government surveillance.
Collective actions:
- Push for transparency: Demand that tech companies publish transparency reports showing how many subpoenas they receive and how they respond.
- Support legal challenges: Organizations fighting these subpoenas need public support and sometimes crowdfunding.
- Build political pressure: When governments overreach, public attention and outcry sometimes creates constraints.
- Support technical solutions: Fund and use technologies that make identification harder without enabling criminal activity.
The Bottom Line
What's happening with DHS subpoenas for anonymous accounts represents a significant shift in how government relates to online speech. The scale is new. The mechanism is powerful. The oversight is weak.
It's not a crisis yet, in the sense that we're not seeing mass arrests of people based on their online speech. But the infrastructure is being built. The precedent is being established. The norm is shifting toward the idea that government should be able to identify anyone saying anything if they determine there's sufficient reason.
That's worth paying attention to. That's worth understanding. That's worth pushing back against if you believe online anonymity serves important social purposes.
The question isn't really about ICE. It's about whether there should be space for anonymous political speech in the United States. It's about whether government can identify people based on their political activities without going through courts. It's about whether the infrastructure of surveillance and identification is expanding appropriately or whether it's outpacing our ability to manage it democratically.
Those are questions worth grappling with now, before the infrastructure becomes so entrenched that changing it becomes nearly impossible.

Key Takeaways
- DHS issued hundreds of administrative subpoenas to identify owners of anonymous accounts criticizing ICE operations, representing a dramatic escalation from prior rare use, as reported by The New York Times.
- Administrative subpoenas don't require judicial approval or showing probable cause, making them a powerful tool with minimal legal oversight, according to The Washington Post.
- Major tech companies including Google, Meta, and Reddit have complied with these subpoenas, though some claim to push back on overbroad requests, as noted by TechCrunch.
- Account holders who discovered they were targeted have successfully challenged subpoenas in court, but most people never learn they've been identified, as highlighted by EFF.
- This surveillance infrastructure will likely expand beyond ICE to target other forms of political activism and dissent, as discussed in ACLU's analysis.
- The practice creates a chilling effect on anonymous political speech even for people never directly targeted, as noted by The New York Times.
- International governments are watching US surveillance practices and will likely replicate similar approaches, as reported by The Washington Post.
Related Articles
- DHS Subpoenas to Identify ICE Critics Online [2025]
- Digital Resistance: How Video Evidence Challenges Government Power [2025]
- Ring Cancels Flock Safety Partnership Amid Surveillance Backlash [2025]
- How to Remove Big Tech from Your Life: Complete Guide [2025]
- Ring Cancels Flock Deal After Super Bowl Ad Sparks Mass Privacy Outrage [2025]
- Social Security Data Handover to ICE: A Dangerous Precedent [2025]
![DHS Subpoenas for Anti-ICE Accounts: Impact on Digital Privacy [2025]](https://tryrunable.com/blog/dhs-subpoenas-for-anti-ice-accounts-impact-on-digital-privac/image-1-1771110332884.jpg)



