Odido Telco Breach Exposes 6.2 Million Users: Complete Analysis [2025]
In February 2025, one of Europe's largest telecommunications companies discovered something every telecom company dreads: hackers had breached their systems and stolen sensitive personal information on millions of customers. Dutch telecom giant Odido confirmed the incident publicly, revealing that 6.2 million customers had their data exposed in what's become one of the largest telecom breaches in recent European history.
This wasn't a typical data breach either. The attackers grabbed a comprehensive package of personal information including names, home addresses, phone numbers, IBAN bank account numbers, and identification document details like passport and driver's license numbers. For context, that's the kind of data that makes identity theft easier than ever for criminals with access to it.
What makes this breach particularly significant is the scale combined with the sensitive nature of the data. Telecom companies sit on goldmines of personal information. They know who you are, where you live, how you communicate, and increasingly, your banking details for bill payments. When attackers compromise this data, they're not just grabbing random information. They're collecting tools for large-scale identity theft, fraud, and potentially worse.
Here's what makes this situation worth understanding: if you're a customer in the Netherlands, or even if you're thinking about telecom security more broadly, this breach highlights critical vulnerabilities that have existed in the telecom industry for years. Major telecom companies around the world face similar risks, and as we'll explore, the reasons why these breaches happen are both technical and organizational.
The Odido breach also raises uncomfortable questions about cybersecurity incident response. The breach apparently occurred on February 7, 2025, but the company didn't immediately disclose it publicly. That gap between discovery and public notification matters enormously to customers trying to protect themselves from fraud.
TL; DR
- 6.2 million Dutch customers affected: Odido confirmed the February 2025 breach impacted millions of users with stolen personal and financial data
- What was stolen: Names, home addresses, phone numbers, IBAN numbers, and ID document information (passport/driver's license numbers and validity dates)
- What was NOT stolen: Passwords, call records, location data, billing information, or ID document scans remain secure
- Services stayed online: Odido's mobile, fiber, and TV services remained uninterrupted during and after the breach
- Attackers remain unknown: No group has claimed responsibility and the stolen data hasn't yet appeared on the dark web
- Why it matters: Telecom companies are prime targets for state-sponsored and criminal actors due to the sensitive data they hold

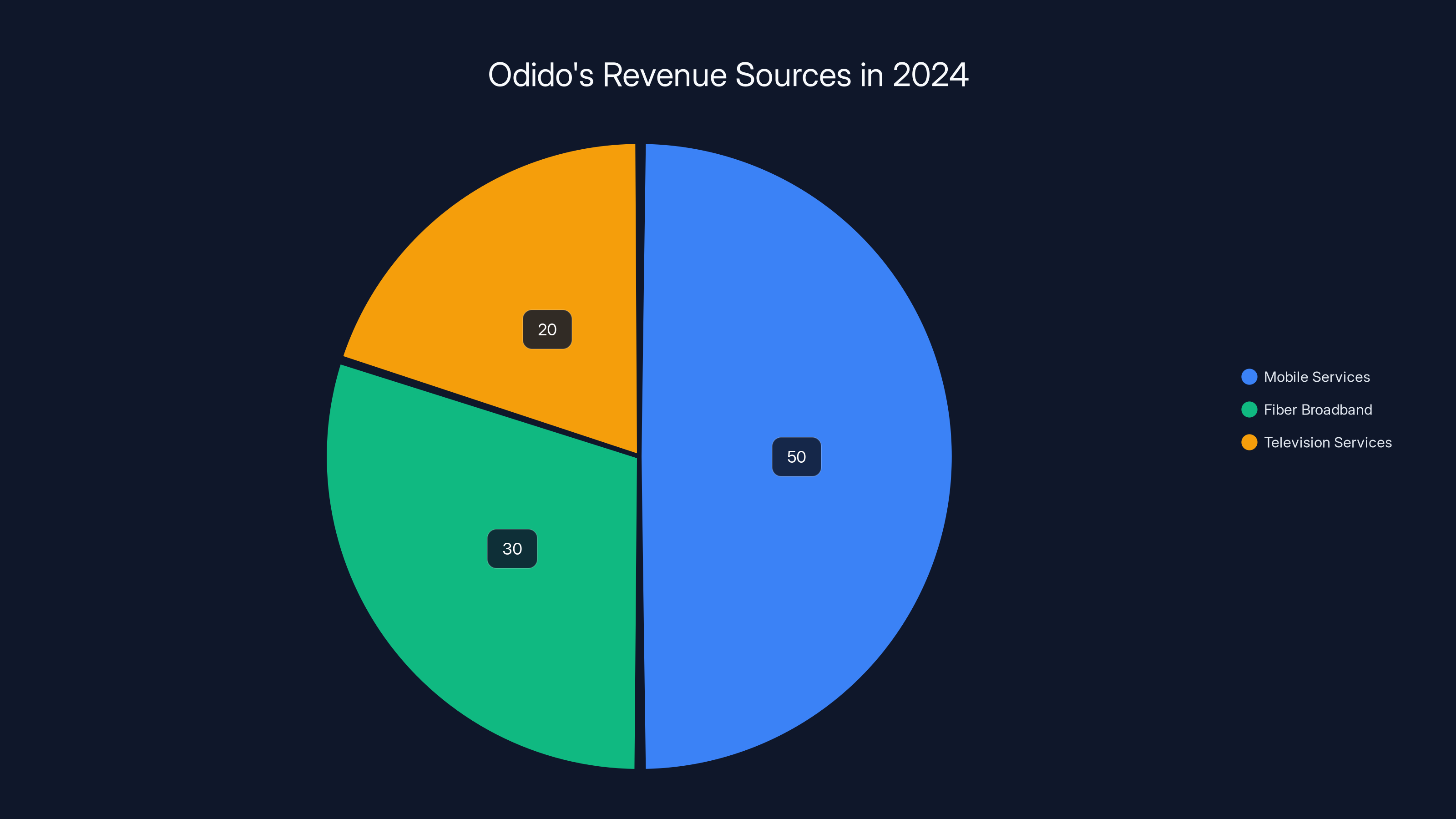
Estimated data suggests that mobile services contribute the largest share to Odido's €2.3 billion revenue in 2024, followed by fiber broadband and television services.
The Odido Breach: What Actually Happened
Odido, one of the Netherlands' largest telecommunications providers, made a public disclosure that it had suffered an unauthorized data access incident. The company released a statement saying it "deeply regrets" the situation and is "fully committed" to limiting the impact. But the timeline and specific technical details remain murky in what's a common pattern with major breaches.
According to the company's investigation, unauthorized parties gained access to "personal data from a customer contact system used by Odido." That's a critical detail because it tells us the attackers didn't breach Odido's entire infrastructure. They specifically targeted and compromised a customer contact database, which is exactly the kind of system where personal information gets stored and managed.
The breach exposure includes a disturbing amount of personally identifiable information. We're talking about the core data points that criminals need to commit identity fraud at scale. Names paired with home addresses and phone numbers form the basis for social engineering attacks. Add in IBAN numbers (essentially European bank account identifiers), and suddenly criminals have what they need to attempt unauthorized bank transfers or open fraudulent accounts.
The inclusion of identification document numbers is perhaps the most concerning element. Having someone's passport or driver's license number, combined with their name and address, dramatically increases the risk of synthetic identity fraud. Criminals can use this information to apply for credit, open new accounts, or facilitate other forms of identity theft.
What makes this breach less catastrophic than it could have been is what didn't get compromised. Passwords weren't included, which means attackers can't directly access customer accounts on Odido's network or other services where people reuse credentials. Call records and location data weren't accessed, so the detailed log of who called whom and where people were when they made calls remains secure. Billing information stayed protected, which limits financial exposure from invoice data. And critically, actual scans or images of ID documents weren't stolen, only the numbers.
The company also revealed that services remained completely uninterrupted. Customers could still make calls, use their mobile data, and access their fiber broadband throughout the incident. The unauthorized access was terminated "as soon as possible" once discovered, though the company didn't specify how long the attackers had active access before being removed.
Odido's response included bringing in third-party cybersecurity experts to investigate and notifying affected customers. This is the standard playbook for major breaches in Europe, where regulations like GDPR mandate that companies notify affected individuals within specific timeframes if there's risk to their personal data.
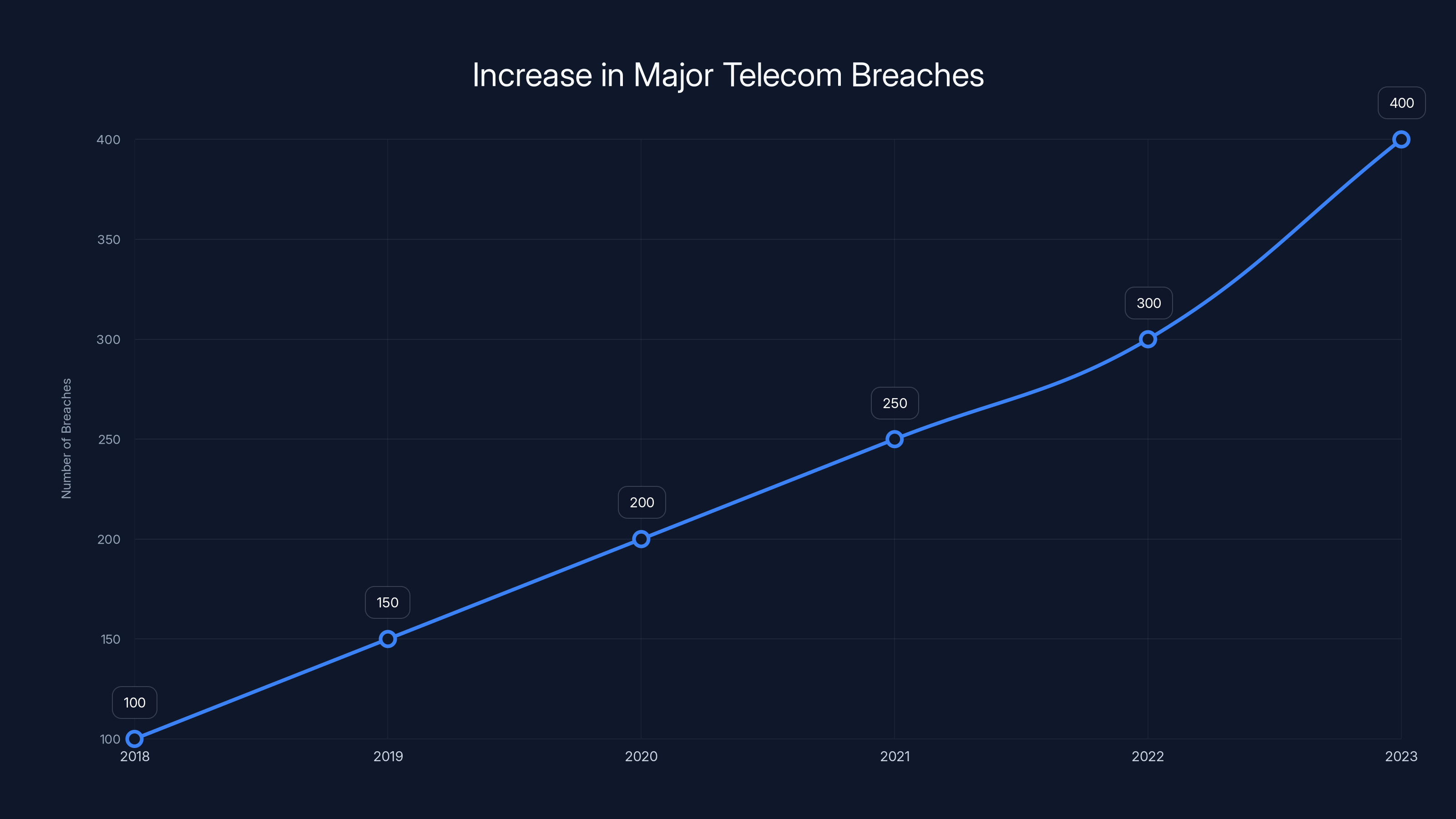
Major telecom breaches have increased by over 300% since 2018, highlighting the growing threat to companies handling sensitive data. Estimated data.
Why Telecom Companies Are Prime Targets
Telecom companies aren't targeted by hackers because their security is particularly weak. They're targeted because they're sitting on exactly the kind of data that matters most to threat actors. This is an important distinction because it means the problem isn't just about Odido making a mistake. It's about an entire industry being strategically valuable to adversaries.
Consider what a telecom company knows about you. They know your name, address, and phone number. They know which phone numbers you communicate with and how frequently. They have billing information including your financial details. They manage the infrastructure through which you send emails, make video calls, and access the internet. Some telecom companies even offer TV and home security services, expanding their visibility into your life even further.
For criminal organizations, this information is tremendously valuable. It enables fraud, identity theft, and blackmail at scale. For state-sponsored threat actors, telecom networks are critical infrastructure that can be exploited for surveillance, espionage, and disruptive attacks.
Historically, telecom breaches have been attributed to sophisticated threat actors. In 2023, the Clop ransomware gang claimed responsibility for multiple telecom breaches across different countries. Other attacks have been linked to nation-state actors attempting to gather intelligence or establish persistent access to critical infrastructure. The nature of telecom data makes these systems attractive to adversaries with significant resources and capability.
What makes telecom systems particularly challenging to secure is their sheer complexity. Modern telecom infrastructure involves thousands of interconnected systems, legacy equipment running outdated software, and the need to maintain service availability 24/7. These constraints make it harder to implement security updates and patches quickly. When vendors discover vulnerabilities, telecom companies often face the choice between taking systems offline for updates or continuing to operate with known security gaps.
Additionally, the telecom industry operates under aging security models in many cases. Much of the infrastructure was built decades ago when different threat models were relevant. While companies have added modern security layers, retrofitting comprehensive security onto legacy systems is perpetually challenging.
The Data That Was Compromised: A Detailed Breakdown
Understanding exactly what was exposed is crucial because it determines what kind of fraud risk you face if you were affected. Different data points enable different types of attacks, and knowing what was stolen helps you prioritize your protective actions.
Names and Address Information
Your name and home address in the hands of criminals becomes the foundation for a range of attacks. Paired with your phone number, this information is sufficient for social engineering attacks. A criminal calling your bank and claiming to be you, citing your address as verification, might convince customer service to reset your password or authorize a transfer.
Your address also enables physical security risks. Criminals with your home address might attempt package interception, mail theft, or even physical intrusion. In cases of high-value identity theft, criminals sometimes show up at your actual residence pretending to be service technicians or delivery personnel.
This is why the breach of address information matters so much more than a breach of, say, your browsing history. It's actionable information that facilitates real-world crime.
Phone Numbers
Your phone number in the wrong hands represents a significant security risk, especially if criminals know it's associated with your other accounts. Phone number-based attacks, including SIM swapping and SMS interception, have become increasingly common. A criminal with your name, address, and phone number can attempt to convince your mobile provider that they're you and request a SIM swap, transferring your number to a device they control.
Once they control your phone number, they can intercept two-factor authentication codes, reset passwords on important accounts, and gain access to your email and financial accounts. The security of two-factor authentication via SMS has been questionable for years, but it remains the default for many banks and services. Having your phone number publicly available in a breach removes a critical barrier to account takeover.
IBAN Numbers (Bank Account Identifiers)
IBAN numbers are the European equivalent of bank account numbers. Having an IBAN is essentially having someone's bank account identifier. While you can't directly withdraw money with just an IBAN, it enables a variety of attacks. Criminals can attempt to set up unauthorized standing orders or direct debits to transfer money out of the account. They can use the IBAN to open false accounts or apply for credit, assuming the victim's identity.
The IBAN is often visible on checks and invoices anyway, but having millions of valid IBANs in a single database is valuable to criminals because they can quickly identify active accounts and begin targeting them at scale.
Identification Document Numbers
Possibly the most serious component of the breach is the exposure of ID document numbers including passport numbers, driver's license numbers, and validity dates. This information is typically reserved for government agencies, financial institutions under strict compliance, and a limited set of other trusted entities.
With your ID document number, criminals can apply for credit in your name, create synthetic identities (mixing real and fake information), or attempt to gain access to government services. In some cases, criminals use ID numbers to request replacement documents from government agencies, essentially taking over your official identity.
The fact that the actual scans or images of these documents weren't stolen is fortunate. The data itself is sufficient to cause significant damage, but actual document images are even more valuable because they can be used for convincing impersonation across more contexts.

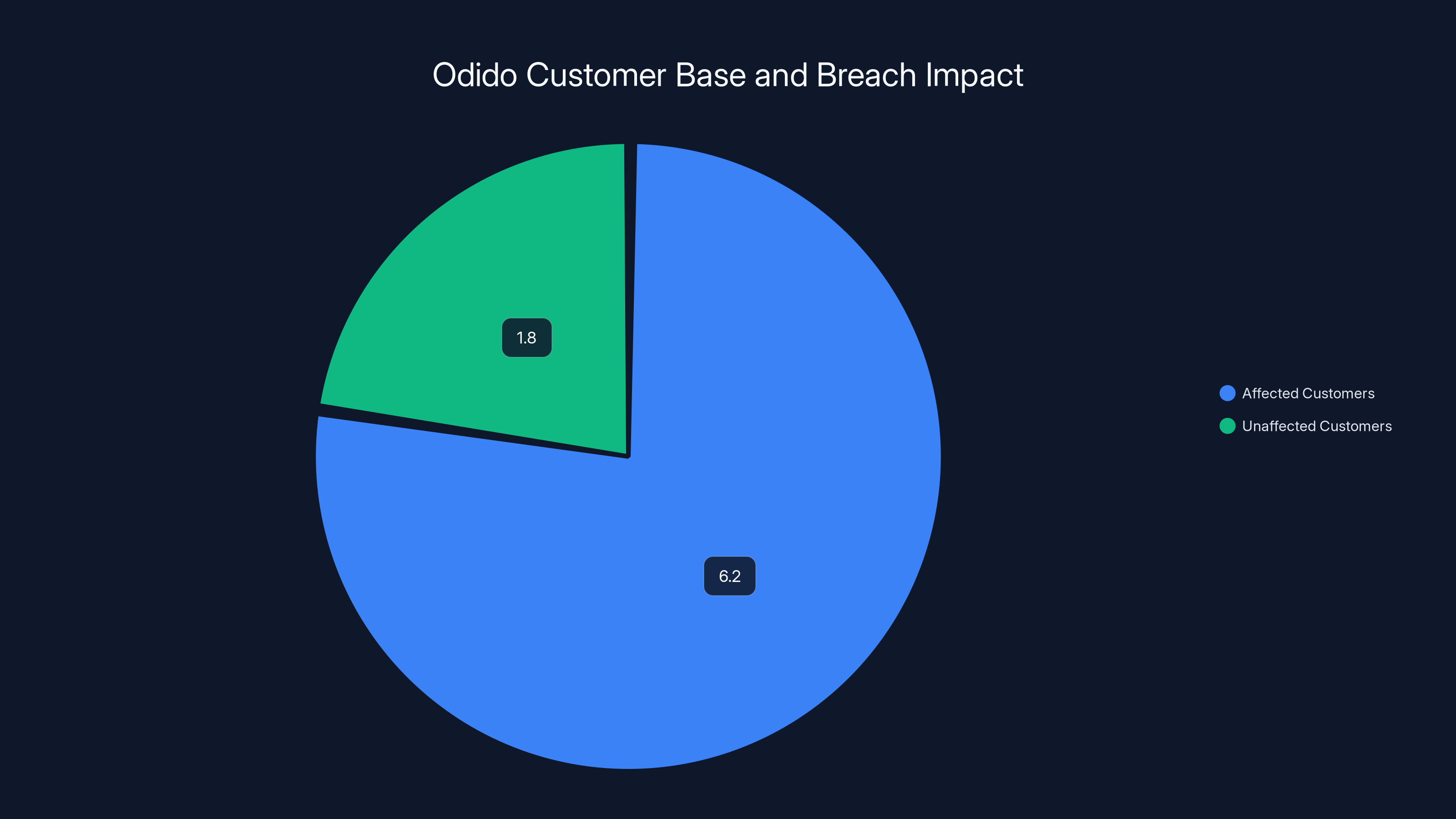
Odido serves 8 million customers, with 6.2 million affected by the breach, highlighting the significant impact on their customer base. Estimated data.
What Wasn't Compromised and Why That Matters
In breach analysis, understanding what wasn't stolen is as important as understanding what was. The fact that certain data types remained protected tells us something about how the attackers accessed the system and what their constraints were.
Passwords and Authentication Credentials
The fact that passwords weren't included in the breach is genuinely good news. It means that attackers can't directly log into customer accounts using stolen credentials. You don't need to panic about your Odido account being compromised in the sense of someone accessing it directly.
However, this doesn't mean your accounts are necessarily safe. If you reused passwords across multiple services (which many people do), criminals with other data points can use social engineering or other attack vectors to reset your passwords through account recovery mechanisms.
Call Records and Location Data
Call records reveal an enormous amount of information about a person. They show who you communicate with, when you communicate with them, and potentially the duration of those communications. Combined with location data from when calls were made or mobile data was used, this creates a detailed map of someone's movements and relationships.
For activists, journalists, dissidents, or anyone involved in sensitive activities, phone call records can be devastating if exposed. The fact that this data remained protected in the Odido breach means those privacy dimensions are intact.
Billing Information
Billing records contain detailed information about what services you use, which can reveal things about your personal circumstances. The fact that this wasn't compromised means criminals don't have detailed records of your service usage patterns or payment history.
Document Scans
While ID document numbers were exposed, the actual image files of documents weren't. This is significant because document images are far more useful for impersonation. An actual photo of a driver's license or passport is much more valuable for fraud than just the number.

Odido: Understanding the Affected Company
To understand the scope and impact of this breach, it's helpful to know who Odido is and why they hold so much customer data. Odido is one of the largest telecommunications providers in the Netherlands, and the company serves a significant portion of the Dutch population.
Odido operates across mobile, broadband, and television services. They run multiple brand names including Ben, Simpel, and Tele 2 Thuis, each targeting different market segments. The company operates nationwide 5G and fiber networks across the Netherlands, meaning their infrastructure reaches into millions of homes and businesses.
The scale of their operations is substantial. Odido serves around 8 million customers. To put that in perspective, the Netherlands has a population of about 17.5 million people, meaning Odido reaches nearly half the country's population. The company employs over 2,000 people and generated roughly €2.3 billion (about $2.5 billion USD) in revenue in 2024.
This scale is important because it explains why the breach affected 6.2 million people. That's not everyone who subscribes to Odido services, but it's the subset of their customer base whose information was stored in the compromised customer contact system. This suggests that not all customer data was in that particular system, or that the breach occurred before certain customers were migrated to the system.
Odido's infrastructure also means they manage critical telecommunications services for millions of people. The breach didn't interrupt these services, which is good for business continuity but concerning from a security perspective. It suggests the attackers had access to customer data systems without triggering sufficient alarm to force service interruptions.

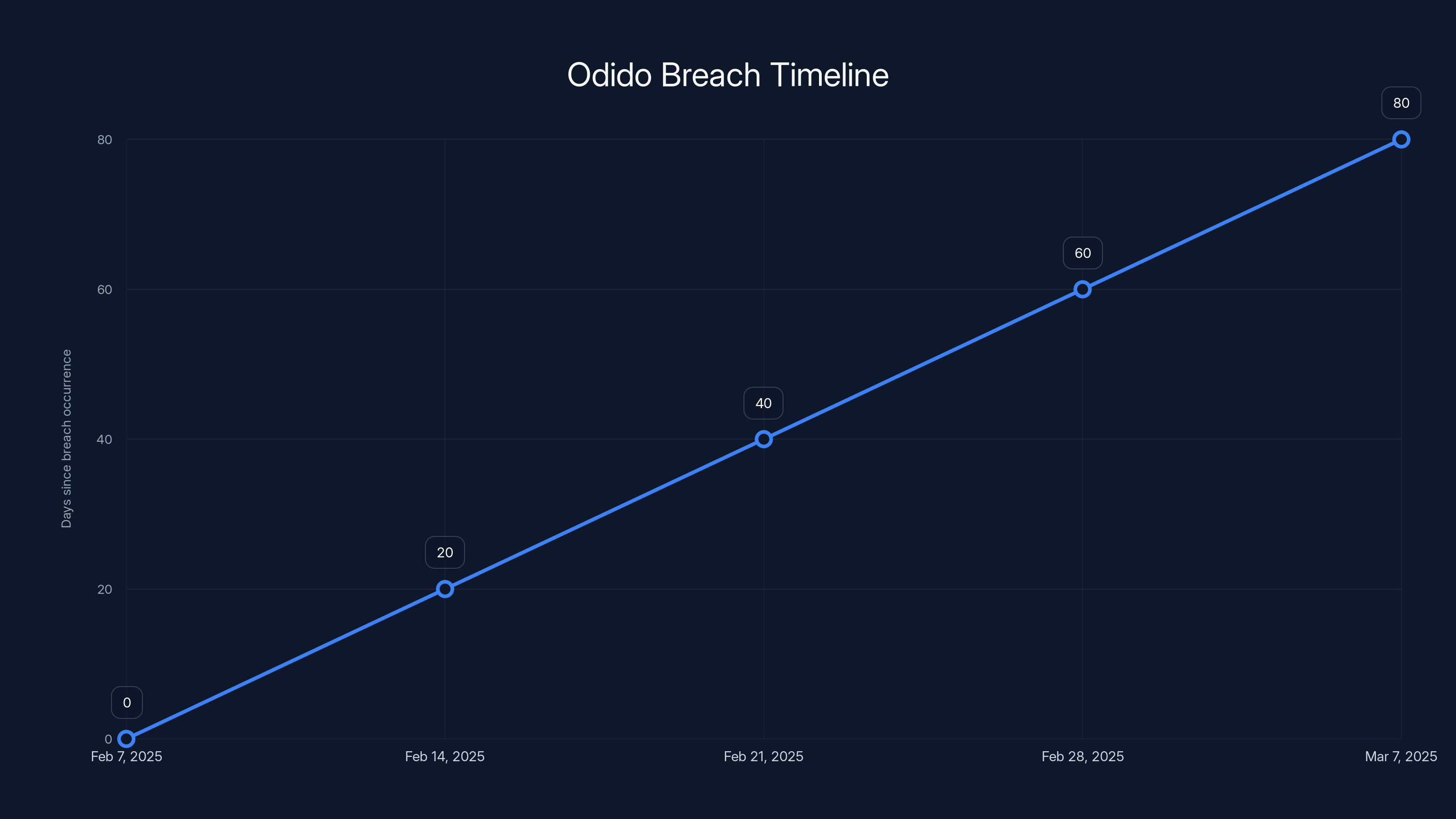
Estimated data shows a potential gap between breach occurrence and public disclosure, highlighting the risk exposure period. Estimated data.
The Breach Timeline: What We Know
Timing matters tremendously in breach response. The faster a company identifies a breach and notifies customers, the faster affected individuals can take protective action. In the Odido case, we have some information about the timeline, though like many breaches, the complete picture remains somewhat unclear.
The breach apparently occurred on February 7, 2025. That's the date Odido identified as when the unauthorized access took place. However, the breach wasn't necessarily discovered immediately. There's often a gap between when access occurs and when the company detects it.
Odido's public disclosure came later, with the company releasing a notice on its website confirming the incident. The company notified affected customers, though the timing and method of that notification remain unclear from the public information available.
This timeline matters because it affects customer risk exposure. If the attackers had access from February 7 through the detection date, every day of that window represents a potential opportunity for them to exfiltrate data, explore the system for additional vulnerabilities, or set up persistent access mechanisms.
The fact that the company engaged third-party cybersecurity experts is standard practice and sensible. These external experts can provide fresh perspective and expertise that internal teams might lack. However, bringing in external experts typically extends the investigation timeline, which means the gap between the breach and public disclosure increases.

Why the Data Hasn't Appeared on Dark Web Markets (Yet)
One notable aspect of the Odido breach is that the stolen data hasn't appeared on the dark web or in criminal markets as of the time of reporting. This is unusual enough to be worth examining because it tells us something about the attackers' intentions.
When criminal organizations steal data, they typically monetize it quickly. Data markets on the dark web allow criminals to sell stolen information to other criminals. A dataset containing 6.2 million people's personal information would typically be worth significant money in these underground markets.
The fact that the data hasn't appeared in such markets suggests a few possibilities. First, the attackers might be sitting on the data waiting for a specific buyer, particularly if this is a nation-state or organized crime group with sophisticated plans for the data. Second, the attackers might be using the data themselves rather than selling it, which would explain the delay in public appearance. Third, law enforcement or cybersecurity researchers might have disrupted the usual distribution channels.
It's also possible that the attackers have leveraged the data for direct attacks that haven't yet surfaced publicly. If they're using the information for targeted fraud, identity theft, or other crimes that don't require mass distribution, the data would remain private and valuable only to them.
This uncertainty about the attackers' intentions and capabilities is one of the most frustrating aspects of breach investigation for affected customers. Without knowing what the attackers plan to do with the data, it's harder to know what protective measures are most important.

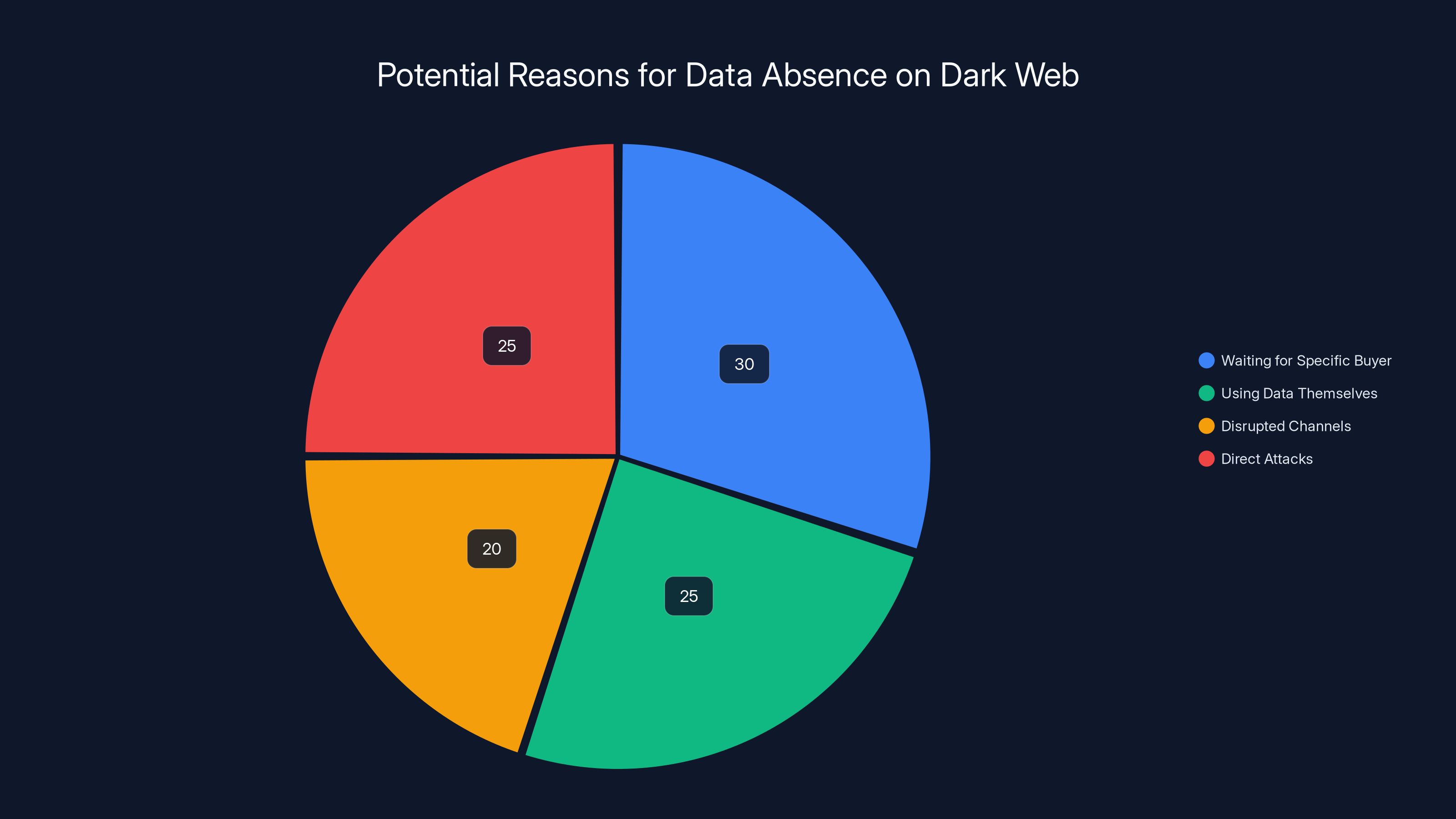
Estimated data suggests multiple reasons for the absence of stolen data on dark web markets, with waiting for a specific buyer and direct attacks being equally likely.
Attacker Identification: Still Unknown
Odido's statement explicitly says nothing about the identity of the attackers. No group has claimed responsibility for the breach. In the modern threat landscape, this is somewhat unusual. Many major breach groups maintain profiles on the dark web and claim their attacks as part of their brand building and intimidation efforts.
The fact that no one has claimed responsibility could mean several things. If the attackers are sophisticated nation-state actors, they might not want to draw attention to the breach. Public attribution could trigger government response, diplomatic incidents, or increased law enforcement scrutiny. State-sponsored attackers often prefer to operate quietly, maintaining access and collecting intelligence without drawing attention.
Alternatively, if this is a criminal group, they might be keeping quiet because they're negotiating with Odido over ransom, or they're planning to use the data themselves rather than sell it. Some criminal organizations have also become more cautious about public claims after increased law enforcement focus on ransomware and data theft operations.
The investigation by third-party cybersecurity experts might eventually determine the attackers' identity, but that information is often withheld from public disclosure to avoid tipping off the attackers or compromising ongoing law enforcement investigations.

Responding to the Breach: What Affected Customers Should Do
If you're an Odido customer, particularly if you've been notified that your data was included in the breach, you need to take specific protective actions. These aren't overactions or paranoid responses. They're sensible steps given what was compromised.
Immediately: Monitor Your Financial Accounts
Start monitoring your bank and credit card accounts for unauthorized transactions. Set up alerts on your accounts that notify you of any transactions over a certain amount, any international transactions, or any new cards being requested.
Call your bank proactively and let them know your information was in a data breach. Ask them to place a fraud alert on your account or enable additional verification for sensitive transactions. Many banks are willing to add manual verification steps for accounts whose information has been compromised.
Short Term: Credit Freeze and Monitoring
Consider placing a credit freeze on your accounts with the major credit bureaus. In most countries, this is free and prevents new credit from being opened in your name without your explicit permission. It's one of the strongest protections against identity theft because it stops criminals at the source.
If a freeze feels too restrictive, a fraud alert is a lighter touch that still triggers additional verification when someone tries to open new credit in your name.
Sign up for credit monitoring services that will alert you if new accounts are opened or inquiries are made about your credit. Many of these services are free in the aftermath of a major breach, and they provide valuable early warning of attempted fraud.
Ongoing: Credential and Account Hygiene
Change your passwords for all important accounts, especially if you reuse passwords. This is a good opportunity to implement unique, complex passwords managed through a password manager. While attackers didn't directly access Odido customer accounts in this breach, criminals have your address and phone number, which they can use for account recovery attacks on other services.
Enable multi-factor authentication (MFA) on important accounts, particularly your email and financial accounts. MFA adds an extra layer of protection beyond just passwords. However, be aware that SMS-based MFA isn't as secure as app-based authentication. If available, use authentication apps like Google Authenticator or Authy instead of SMS codes.
Be extra cautious about unexpected communications claiming to be from financial institutions or government agencies. Criminals with your personal information will attempt social engineering attacks, including phishing emails and phone calls pretending to represent your bank or tax authority.
Legal and Regulatory: Know Your Rights
In the European Union, the General Data Protection Regulation (GDPR) provides specific rights and protections for people whose data has been breached. Odido has obligations under GDPR to notify you, provide information about the breach, and take steps to mitigate harm.
You have the right to request compensation for damages caused by the breach. You also have the right to request deletion of your data from Odido's systems (subject to certain exceptions where they have legal obligations to retain it).
If you're affected and suffer direct losses from fraud or identity theft related to this breach, document everything. You may be able to pursue legal claims against Odido if you can establish that the company failed to implement adequate security measures.

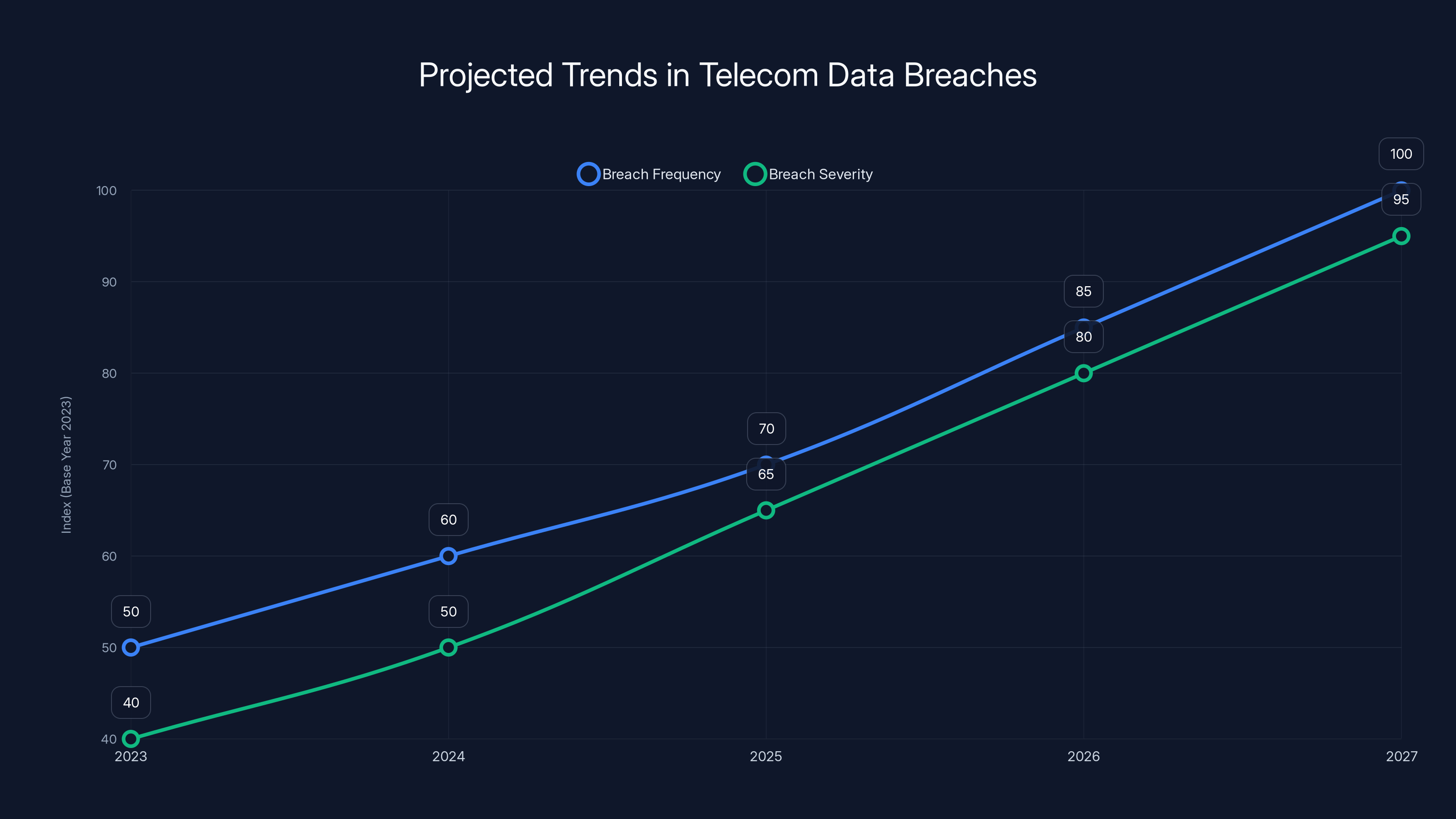
Estimated data suggests both the frequency and severity of telecom data breaches will increase over the next five years, driven by new technologies and more sophisticated threats.
The Broader Telecom Security Landscape
The Odido breach isn't an isolated incident. It's part of a pattern of major telecom breaches that have occurred globally in recent years. Understanding this broader context helps explain why telecom companies are such attractive targets and what systemic vulnerabilities exist.
Telecom companies across Europe, Asia, and North America have experienced major breaches in recent years. These breaches have exposed call records, location data, billing information, and customer personal data at massive scales. The common thread across these incidents is that telecom companies hold data that's simultaneously valuable to criminals and difficult to protect at the scale these companies operate.
The reasons telecom companies remain vulnerable despite being aware of these threats are worth exploring. First, legacy systems remain in place. Telecom infrastructure includes equipment installed decades ago, some running software that's no longer receiving security updates. Replacing this equipment is expensive and disruptive. Second, the need for service availability means telecom companies can't easily take systems offline for security updates or maintenance.
Third, telecom companies have become targets for nation-states attempting to maintain access to communication infrastructure for surveillance or espionage purposes. These sophisticated threat actors are persistent and resourceful. They might spend months or years developing exploits and identifying vulnerabilities specific to telecom systems. This level of sustained effort is hard to defend against without equally sophisticated security operations.

Prevention and Detection: What Should Telecom Companies Do Differently
While affected customers need to take protective action, the broader question is what could have prevented this breach or how similar breaches could be detected faster. This is important because customer-level protection is necessary but insufficient. We need better security at the institutional level.
Segmentation and Access Controls
One fundamental security principle that many organizations still struggle with is network and data segmentation. The customer contact system that was compromised at Odido should have been isolated from other systems using network segmentation. This prevents an attacker who compromises one system from pivoting to other systems.
Access to this system should have been restricted through strong access controls. Not every employee needs access to all customer data. Restricting access to the minimum required for job functions (a principle called least privilege) limits the damage when attackers exploit employee accounts or credentials.
Encryption and Data Protection
The data in the customer contact system should have been encrypted at rest, meaning it would be unreadable to attackers even if they gained direct access to the database. Encryption in transit (as data moves across networks) is equally important. While encryption doesn't prevent an attacker from accessing a system, it makes the stolen data less useful if the attacker actually gets it.
Additionally, sensitive fields like ID numbers should be encrypted at a higher level or tokenized, meaning they're replaced with meaningless tokens that can't be used to cause harm even if stolen.
Monitoring and Detection
A sophisticated customer contact system should have comprehensive logging and monitoring. Unusual access patterns, large data exports, or access from unexpected locations should trigger automated alerts. The Odido breach apparently wasn't discovered for some period after February 7, suggesting that detection capabilities were either absent or ineffective.
Behavioral analytics can identify when a system user is behaving differently than normal, potentially indicating account compromise. This is particularly important for access to sensitive data systems where unusual activity patterns are a red flag.
Incident Response Planning
Odido's incident response itself appeared reasonable once the breach was discovered. They engaged external cybersecurity experts, contained the breach, and notified customers. However, having a well-documented incident response plan before a breach occurs is critical. This plan should specify timelines, responsible parties, communication procedures, and escalation paths.

What Customers Can Learn From This Breach
Beyond the immediate protective actions, this breach teaches some important lessons about digital security and what to expect from companies that hold your data.
First, you should assume that any company holding significant amounts of personal data is a potential breach target. This includes not just telecom companies but banks, retailers, healthcare providers, and others. Having a standing assumption that your information might be compromised at some point is more realistic than assuming it won't be.
Second, understand what data each company holds about you. Review privacy policies and terms of service to understand what data is being collected. Request data access reports from companies holding your information. The GDPR allows you to request a copy of all data a company holds about you.
Third, implement layered security for yourself. Don't rely on a single company to keep your information safe. Use unique passwords for each account so a breach at one company doesn't compromise your other accounts. Use multi-factor authentication where available. Monitor your financial accounts and credit for signs of fraud. These personal security practices aren't perfect, but they significantly reduce your risk.

Future Risk and What to Expect
The Odido breach tells us something about future risk in the telecom industry and related sectors. We should expect more breaches. The question is whether the severity and frequency will increase or whether improved security efforts will slow the tide.
The trend lines suggest that breach frequency will continue, at least in the near term. Telecom companies are increasingly attractive targets as they adopt new technologies. 5G networks, while more secure than 4G in some respects, introduce new attack surfaces. Io T integrations and edge computing create new vulnerabilities. The expansion of telecom company services (many now offer financial services, cloud services, and other offerings) increases the scope of sensitive data they hold.
Simultaneously, we're seeing more sophisticated threat actors enter the telecom space. Nation-states are investing heavily in the capability to compromise telecom infrastructure. Criminal organizations are becoming more organized and professional. The skill gap between defenders and attackers in this space is concerning.
What should change is accountability and transparency. When breaches occur, companies should be required to disclose them quickly and completely. Regulatory agencies should have real enforcement power over companies that fail to implement adequate security. Customers should have meaningful recourse for damages caused by breaches resulting from inadequate security.

Real-World Impact: Stories From Previous Telecom Breaches
While specific names are being withheld for privacy, telecom breaches have caused documented harm to customers beyond just financial fraud. Previous major telecom breaches have resulted in identity theft affecting thousands of individuals, with victims spending years clearing their credit reports and legal records after criminal activity committed in their names.
In some cases, the exposure of call records has resulted in personal information about relationships, medical conditions, and other sensitive matters becoming public or being used for blackmail. The psychological impact of knowing that your communication records were exposed to criminals extends beyond immediate fraud risk.
Government employees and contractors have had their information exposed in telecom breaches, potentially compromising national security if attackers used the data to identify and target specific individuals. Journalists and activists have had their information exposed, potentially compromising sources and ongoing investigations.
The real-world impact of breaches is often hidden from public view because most fraud and identity theft aren't widely publicized. Affected individuals deal with fraud calls, accounts opened in their names, credit damage, and the time-consuming process of clearing up the mess. Multiply that experience across millions of people, and you get a sense of the true scale of harm caused by major breaches.

Moving Forward: Industry Changes and Standards
The telecom industry is responding to increased breach incidents with new security standards and best practices. Organizations like NIST and ENISA publish guidance specifically for telecom security. However, implementing these standards at the scale of a major telecom company is a multiyear effort involving significant investment.
Some telecom companies are implementing zero-trust security models, where no user or system is trusted by default regardless of whether they're inside or outside the network perimeter. This represents a fundamental shift from older security models that trusted anyone or anything inside the network.
Others are investing in advanced threat detection capabilities, including AI and machine learning systems that can identify anomalous behavior patterns that might indicate an ongoing breach. These systems are particularly valuable for detecting sophisticated attackers who might otherwise evade traditional intrusion detection systems.
Regulation is also evolving. The European Union's Network and Information Security (NIS) Directive requires telecom operators to implement specific security measures and report certain incidents to authorities. Similar regulations are being developed in other regions.

FAQ
What exactly is Odido and who are they?
Odido is one of the Netherlands' largest telecommunications providers, serving approximately 8 million customers with mobile, fiber broadband, and television services. The company operates brands including Ben, Simpel, and Tele 2 Thuis and generated €2.3 billion in revenue in 2024. They're a major provider of critical communication infrastructure across the Netherlands with nationwide 5G and fiber networks.
How did the attackers gain access to the Odido systems?
Odido hasn't provided detailed technical information about how the breach occurred. The company confirmed that unauthorized parties accessed a customer contact system, but specific details about the attack vector, whether it was a known vulnerability or zero-day exploit, or how the attackers initially gained access remain unclear from publicly available information.
Can I change my IBAN number if it was exposed in the breach?
Your IBAN is tied to your specific bank account and isn't something you can simply change like a password. However, you can request to close your current account and open a new one with a new IBAN through your bank. This is a significant step that you should only consider if you notice actual fraudulent activity on the account. For most people, careful monitoring of the account and working with the bank to flag suspicious transactions is more practical than closing the account.
What are the actual chances I'll be a victim of fraud if I was affected by this breach?
The risk is real but not certain. The fact that passwords weren't exposed and the data hasn't yet appeared on dark web markets suggests that criminals don't currently have complete account takeover capabilities for most victims. However, the presence of names, addresses, phone numbers, and ID numbers does enable identity theft and social engineering attacks. Studies of past major breaches suggest that perhaps 5-15% of affected individuals experience some form of fraud, though this varies based on the types of criminals who access the data and how they choose to use it.
Should I switch away from Odido after this breach?
Whether to stay with Odido is a personal decision that depends on whether the company's service quality and pricing justify staying after the security failure. The breach itself doesn't necessarily mean Odido is uniquely insecure compared to other telecom companies. However, if you're concerned about their security practices, you have the right to switch providers. If you do stay, focus on protecting yourself through the recommended security practices rather than assuming the company will prevent all future breaches.
How long should I monitor my accounts for fraud after a breach like this?
Most fraud related to breached personal data occurs within the first 12 months, but sophisticated identity theft and fraud can occur years later. A reasonable approach is to monitor accounts actively for 12-24 months after a breach notification, then continue with normal ongoing monitoring practices indefinitely. The data exposed won't become less dangerous with time, so indefinite monitoring is really the baseline for anyone exposed in a breach of this nature.
What's the difference between a data breach and a ransomware attack?
A data breach is when attackers unauthorized access and steal information, as happened with Odido. A ransomware attack is when attackers encrypt data and demand payment to decrypt it. Some attacks are both, where attackers steal data and then encrypt systems, threatening to publicly release the data unless ransomed. The Odido incident appears to be pure data theft without the ransomware component.
Will Odido be fined for this breach under GDPR?
It's possible. Under GDPR, companies that fail to implement appropriate security measures and suffer breaches can face fines up to €20 million or 4% of global annual revenue, whichever is higher. Whether Odido faces fines depends on whether regulatory authorities determine that the company failed to implement adequate security measures proportional to the risk. The breach alone isn't automatically a violation. The company would only be fined if it's determined that the company's security practices fell below the required standard.
Should I enable two-factor authentication using SMS or is that not secure?
SMS-based two-factor authentication (2FA) is better than no 2FA but is not as secure as other methods. In a data breach like Odido's where your phone number is exposed, criminals could potentially use SIM swap attacks to intercept SMS messages. Prefer authentication apps like Google Authenticator, Microsoft Authenticator, or Authy when available. If SMS 2FA is your only option, it's still worth enabling because it's better than relying on password alone.
What can I do if my information is used for fraud despite my precautions?
If you discover fraud using your information, immediately contact your bank or credit card issuer to report unauthorized transactions. File a fraud report with your country's relevant authority (in the U. S., the FTC; in Europe, you can file with your national data protection authority). Document everything including fraudulent accounts, unauthorized transactions, and your communication with institutions. Most countries have protections against liability for fraudulent transactions if you report them promptly. You may also be entitled to compensation from Odido under GDPR if you can establish damages.
Conclusion
The Odido breach affecting 6.2 million customers represents one of the most significant telecom breaches in recent European history. The exposure of names, addresses, phone numbers, bank account identifiers, and ID document information creates real risk for millions of people. The breach is serious, but it's not unprecedented, and it's also not unexpected given the current threat landscape.
What matters now is both individual action and systemic change. For affected customers, the priority is protecting yourself through the recommended security practices: monitoring financial accounts, placing credit freezes, enabling multi-factor authentication, and being cautious about unsolicited communications. These actions won't eliminate fraud risk, but they significantly reduce it.
For the telecom industry and regulators, this breach should be a wake-up call about the fundamental importance of security for companies handling sensitive data. The technical security practices needed to prevent these breaches are well-known. The challenge is implementing them consistently at scale across complex, legacy-heavy infrastructure while maintaining service availability.
Odido will likely face regulatory scrutiny and potentially financial consequences for this breach. Customer trust will take time to rebuild. But the broader lesson applies to every company holding customer data: the breach is no longer a question of if, but when. Being prepared with robust security practices, rapid detection capabilities, and comprehensive incident response plans isn't optional for companies in this position.
For those of us as customers, the lesson is equally clear. Assume your data will be breached at some point. Take appropriate protective measures. Monitor your accounts. Stay informed about what data companies hold about you. And hold companies accountable when they fail to protect that data adequately. The Odido breach is one more data point in a growing pattern that should concern anyone who values their personal security and privacy.
The good news is that while complete prevention of breaches isn't realistic, fraud prevention and identity theft protection are entirely within your control if you're willing to implement the necessary measures. The Odido breach, while serious, also provides an opportunity to audit your own security practices and implement improvements that will benefit you regardless of what other companies do with your data.

Key Takeaways
- 6.2 million Dutch Odido customers had personal data including names, addresses, phone numbers, IBAN numbers, and ID document information exposed in a February 2025 breach
- Passwords, call records, location data, billing information, and actual ID document scans were not compromised, limiting the breach severity
- Affected customers should immediately freeze credit, enable fraud monitoring, and implement unique passwords and multi-factor authentication
- Telecom companies are consistently targeted by both criminal and state-sponsored threat actors due to the sensitive personal data they manage
- Better security practices including network segmentation, encryption, and continuous monitoring could have prevented or detected this breach faster
Related Articles
- 6.8 Billion Email Addresses Leaked: What You Need to Know [2025]
- NordVPN & CrowdStrike Partnership: Enterprise Security for Everyone [2025]
- ExpressVPN ISO Certifications & Data Security [2025]
- iRobot Acquisition Complete: How Roomba's Data Protection Strategy Evolved [2025]
- Gemini Model Extraction: How Attackers Clone AI Models [2025]
- Mysterious Bot Traffic From China Explained [2025]
![Odido Telco Breach Exposes 6.2M Users: Complete Analysis [2025]](https://tryrunable.com/blog/odido-telco-breach-exposes-6-2m-users-complete-analysis-2025/image-1-1770982557549.jpg)



