TL; DR
- Fake extensions spread fast: Attackers created multiple extensions impersonating Proton VPN that bypassed Google's review process and remained live for weeks.
- Authentication targeted: These fake extensions harvested user credentials, tracking data, and browsing activity, storing everything on attacker-controlled servers.
- Google's gaps exposed: The Chrome Web Store's manual review process failed to catch obvious impersonation, raising questions about vetting rigor.
- Simple checks save you: Verify developer names, check official websites, review actual user comments, and look for telltale signs like poor grammar or suspicious permissions.
- Better tools exist: Using VPN apps instead of extensions, enabling 2FA, and choosing audited VPN providers significantly reduces your risk.
Introduction: When Trust Gets Weaponized
Imagine clicking what looks like your trusted VPN extension, entering your password, and then waiting. Everything seems normal. Pages load. Videos play. But in the background, someone else is collecting your login credentials, your IP address history, and a complete map of every website you visit.
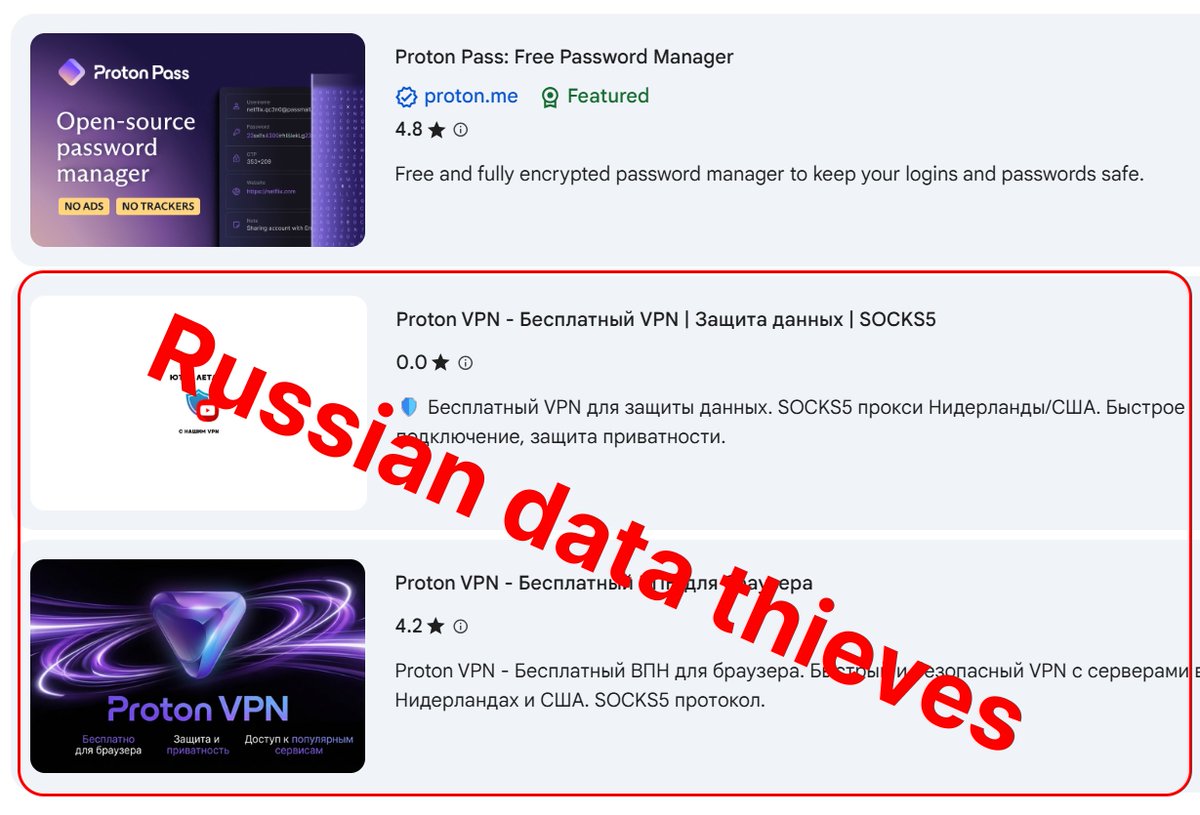
This isn't hypothetical. It happened to thousands of users in 2024 when attackers created fake Proton VPN extensions on the Chrome Web Store. These weren't subtle knock-offs. They had nearly identical names, similar icons, and convincing descriptions. Yet they slipped past Google's security reviewers and stayed live long enough to compromise users.
What's particularly unsettling is how this reveals a massive gap in security infrastructure. The Chrome Web Store processes millions of extensions yearly. Firefox, Edge, and other browsers face the same problem. Extensions are powerful. They can intercept network traffic, access your browsing history, read your passwords, and modify what you see on screen. They're trusted with intimate digital access.
Yet the vetting process treats them like simple apps. Someone downloads what they think is Proton VPN, not realizing it's a credential harvester. They trust it because Google supposedly approved it. They trust it because it looks legitimate. And by the time they realize something's wrong, damage is done.
This isn't just about one fake extension or one VPN provider. It's about how browser extension ecosystems have become profitable targets for criminals, and how trust itself has become a vulnerability. Whether you use VPNs, password managers, ad blockers, or any other extension, this matters to you.
In this guide, I'll walk you through exactly what happened, why it happened, and more importantly, how to protect yourself and your data. We'll cover identifying fake extensions, understanding the risks, choosing safer alternatives, and building better security habits around the tools you trust.
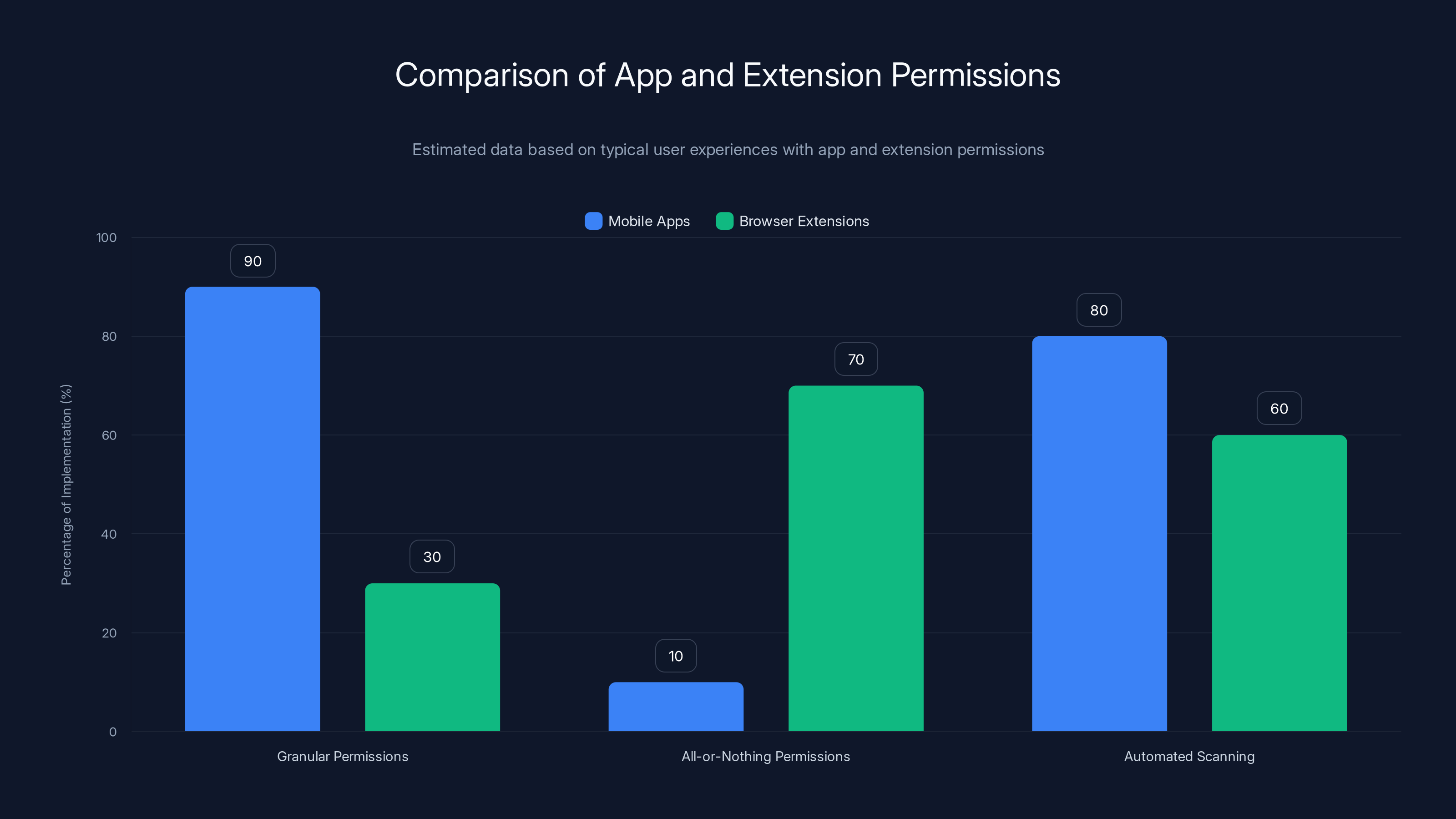
Mobile apps typically offer more granular permissions compared to browser extensions, which often use an all-or-nothing model. Automated scanning is prevalent in both, but extensions are more vulnerable due to less granular control. Estimated data.
What Exactly Were These Fake Extensions?
The fake Proton VPN extensions that appeared on Chrome's Web Store in early 2024 were disturbingly convincing. They didn't announce themselves as malware. They didn't come with scary warnings. They presented themselves as legitimate alternatives to the real Proton VPN service.
Here's what made them effective: they had actual VPN functionality. Users who installed them could browse through a VPN. Websites got masked IP addresses. The browsing was encrypted. From the user's perspective, the extension worked. The problem was everything it did in addition to providing VPN service.
The fake extensions captured login credentials when users tried to authenticate. They logged which websites users visited and when. They tracked IP addresses before and after the VPN connection. Some versions even attempted to inject code into banking websites and other sensitive pages, looking for additional data to harvest.
What's particularly clever about this attack is that the extensions didn't immediately malfunction or raise obvious suspicions. A user might install one, use it for weeks, and never realize their data was being harvested. The extension didn't crash. It didn't demand money. It didn't show pop-up ads. It just quietly collected information while appearing to provide the service the user expected.
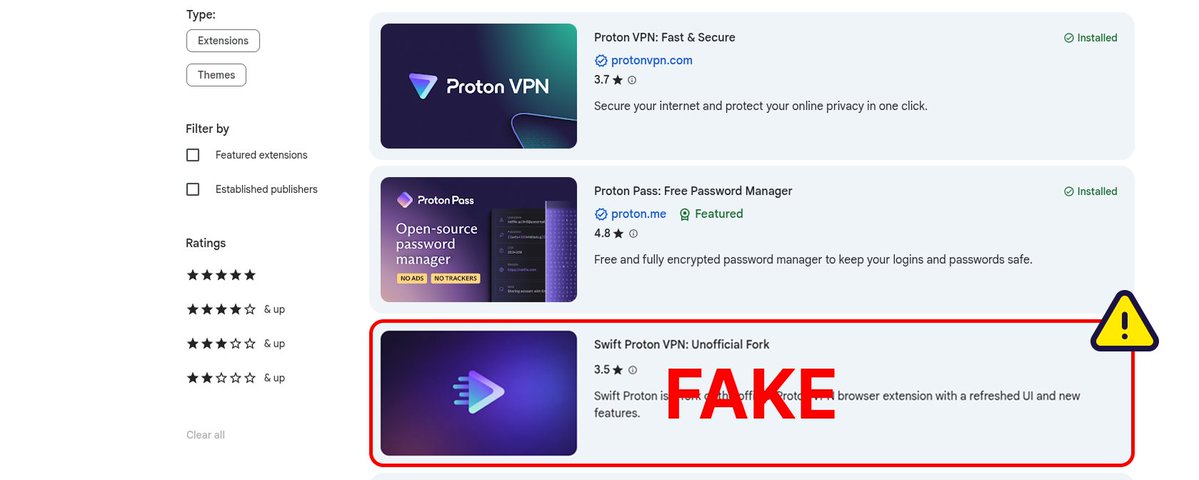
Multiple fake extensions operated simultaneously on the Chrome Web Store. Some had names like "Proton VPN Pro," "Proton VPN Plus," or "Proton VPN Ultra." The names mimicked legitimate tiering strategies that real VPN companies use, making them seem plausible to users unfamiliar with the official Proton naming conventions.
According to security researchers who analyzed these extensions, each one had between 100 and 3,000 active installations before being removed. That means between 100 and 3,000 individual users downloaded what they believed was a legitimate VPN service. Even if the number on the lower end is accurate, that's hundreds of compromised users, each potentially exposing financial data, password information, and browsing activity.
The extensions remained live for weeks despite Google's purported security review process. This timeline is crucial. It shows that the vetting process, which includes both automated scanning and manual human review, failed to catch obvious red flags.

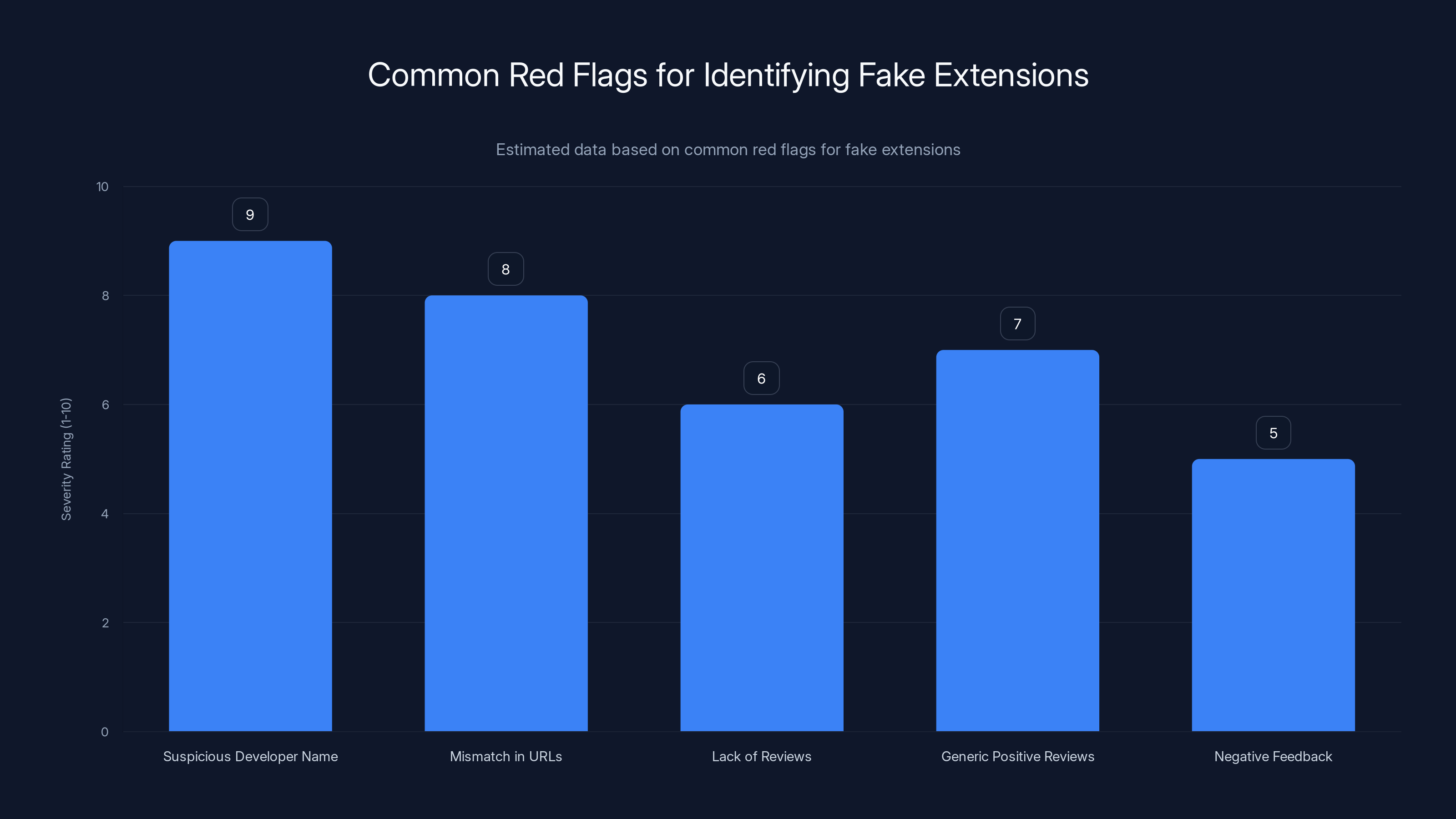
Suspicious developer names and mismatched URLs are the most severe red flags for fake extensions. Estimated data based on common indicators.
How Did They Get Past Google's Security?
This is the question that keeps security professionals awake at night. Google claims to review all extensions before they appear on the Chrome Web Store. The company publishes security guidelines, enforces policies against impersonation, and maintains a team dedicated to hunting malicious extensions.
Yet these fake Proton VPN extensions passed every check.
Several factors likely contributed to this failure. First, Google's review process relies on both automated scanning and human reviewers. The automated tools scan for obvious malware signatures, suspicious permissions requests, and known attack patterns. But attackers increasingly write code specifically designed to bypass these automated checks. They use obfuscation techniques, packing, encryption, and other methods to hide malicious behavior from scanners.
Second, the manual review process involves human reviewers checking extensions for policy violations. But these reviewers can't possibly test every extension thoroughly. They might check whether an extension has excessive permissions, whether its description matches its functionality, and whether its branding appears legitimate. For something like a VPN extension, a reviewer might spend five to ten minutes looking at the code, reading the description, and checking the store listing.
In five to ten minutes, it's easy to miss credential harvesting code buried deep in a minified Java Script file. It's easy to believe that "Proton VPN Plus" is a legitimate variant if you're not familiar with Proton's actual naming conventions. It's easy to see a professional-looking icon and assume legitimacy.
Third, Proton VPN itself isn't a well-known brand to everyone. Proton Mail is more recognizable, and casual users might not realize these are part of the same company. When a reviewer checks whether an extension is impersonating a known brand, they're thinking of mega-brands like Google, Facebook, or Netflix. A mid-tier VPN provider might not trigger the same level of scrutiny.
Fourth, the attackers likely staged their extensions carefully. They probably monitored how long they could stay live before being detected. They might have released them slowly, testing different names and descriptions to see which ones took longer to get caught. This iterative approach, combined with the lag in Google's response system, meant extensions could gain users for weeks before removal.
Google eventually removed the fake extensions, but only after security researchers reported them. The company issued statements about its commitment to user safety and its ongoing efforts to improve vetting. But the damage was already done. Users who installed the extensions were exposed. Their data was harvested. And the incident exposed a structural weakness in how browser extension ecosystems handle trust and verification.
The Risks: What Data Could They Actually Access?
Understanding what these fake extensions could access is crucial to understanding why they're so dangerous. Browser extensions exist in a privileged position on your computer. They run with your user account's permissions. They can see and modify network traffic. They can access your browser's stored data. They can even monitor everything you type in certain contexts.
When you install a Proton VPN extension, you're granting it permission to intercept and modify all your network traffic. That's necessary for a VPN to work. It needs to route all your data through encrypted tunnels. It needs to replace your visible IP address with a VPN server's address. These capabilities are legitimate when the extension is trustworthy, but catastrophic when it's malicious.
The fake Proton VPN extensions were particularly effective because users expected them to access broad network permissions. A legitimate VPN extension needs those same permissions. So when users saw permission requests for "modify network requests" or "access all sites," they didn't second-guess them. Why would they? They were installing a VPN.
With these permissions, the fake extensions could:
-
Intercept login credentials: When you enter your password on any website, the extension can see it. Even if the website uses HTTPS encryption, the extension sits between your browser and the encrypted connection, so it sees plaintext passwords before encryption happens.
-
Monitor all websites visited: Every URL you navigate to, every search query you type, every link you click flows through the extension's code. The attackers maintained logs of where each user browsed and when.
-
Capture browsing history: Combined with the URL monitoring, attackers built complete maps of user behavior. They could see patterns: when you check email, what you search for, what news sites you read, what shopping you do.
-
Collect IP address information: Even though the extension supposedly provided a VPN, it logged your real IP address before routing traffic through its servers. This defeats the entire privacy purpose of using a VPN.
-
Modify page content: Extensions can inject code into webpages. This means attackers could add fake login forms, change prices, redirect clicks, or harvest form data before users submitted it.
-
Access stored passwords: Depending on how the browser stores passwords (Chrome, Firefox, Edge, etc.), extensions might be able to access or export stored credentials, though modern browsers have improved protections here.
One of the most insidious risks is credential harvesting. If you use the same password across multiple services (which many people do), losing it to an extension means attackers can try that password on email, banking, social media, and work systems. One compromised extension becomes a skeleton key to your digital life.
Another risk is tracking. Services like Google and Facebook pay billions for tracking data. They know where you browse, what you buy, what interests you. An extension harvesting this data for criminals is essentially giving them valuable market research intelligence. Some might be sold to advertisers, data brokers, or other criminal operations.
The financial damage is also significant. If credentials for banking or payment services are harvested, attackers might commit fraud directly. They might drain accounts, make unauthorized purchases, or steal identity information to open new accounts in your name. The average cost of identity theft to victims exceeds $3,000 in direct financial loss, not counting the time spent fixing the damage.
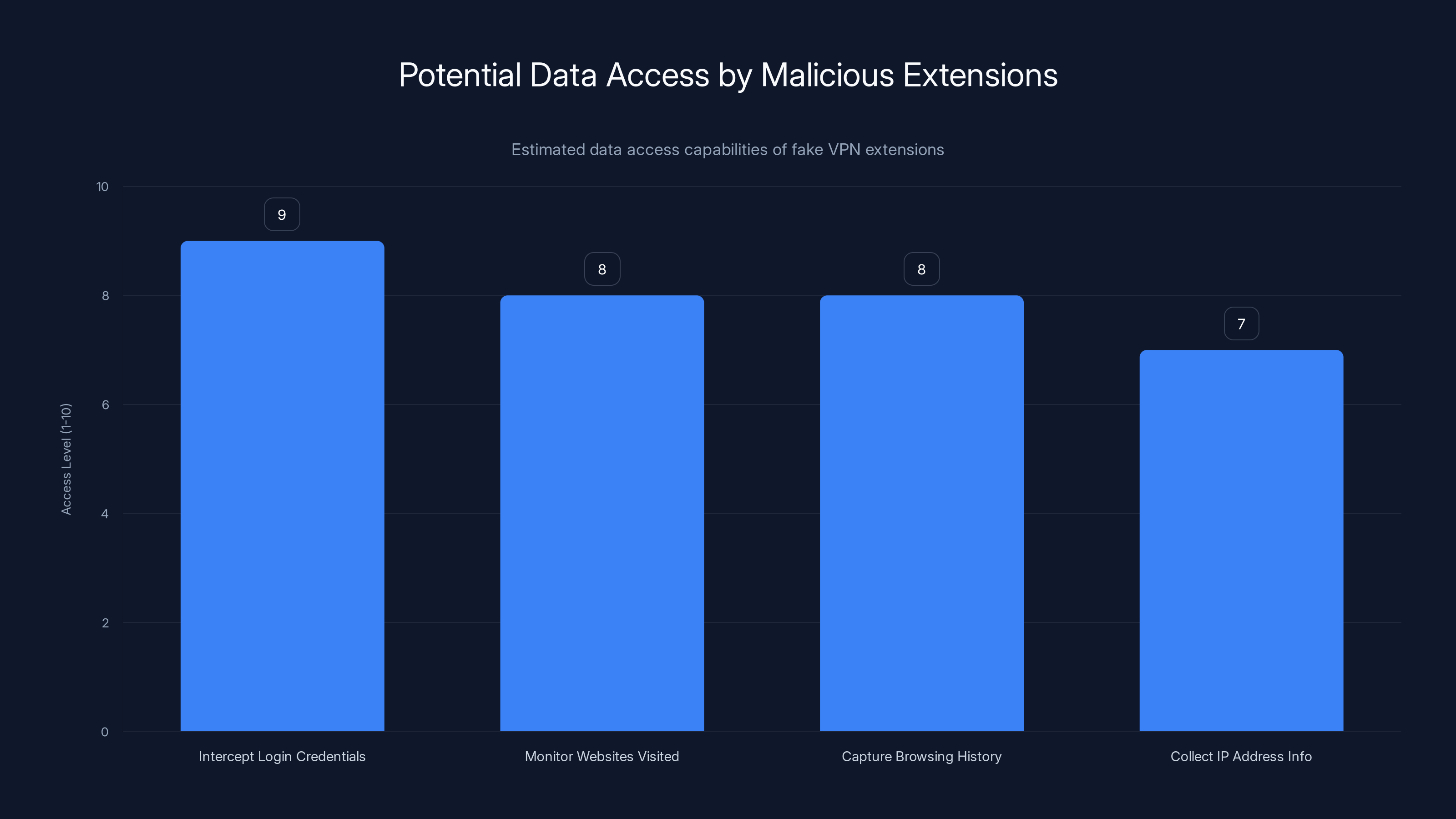
Fake VPN extensions can severely compromise user privacy by intercepting login credentials and monitoring browsing activities. Estimated data.
Red Flags: How to Spot Fake Extensions
Now we get to practical protection. You can't rely entirely on Google, Apple, Mozilla, or other app store operators to catch all fake extensions. You need to develop your own verification skills. Here are the red flags that should make you pause before installing any extension, not just VPN tools.
Check the developer name carefully. Legitimate companies have official developer accounts. Proton VPN extensions come from a developer account literally named "Proton Technologies" or similar. If an extension claims to be from Proton but the developer name is "John Smith" or "Tech Solutions LLC," that's a massive red flag. Look at the developer's other extensions. Real companies have multiple tools. A developer with only one extension, and that extension is supposedly from a major company, is suspicious.
Visit the official website before installing. Before clicking install, go to the official Proton website and find their extension. Click the link from their site, not from your browser search results. This ensures you're getting the legitimate version. Check that the Chrome Web Store URL matches what the official site links to. Attackers sometimes create near-duplicate URLs like "chromewebstore-security.com" that look official but aren't.
Read the actual user reviews carefully. Fake extensions often have suspiciously positive reviews or no reviews at all. But if they do have reviews, look for red flags. Do reviewers mention authentication problems? Do they complain about the extension not working? Do they mention suspicious behavior like unusual data usage or crashes? Real user feedback often includes constructive criticism. If every review is glowing and generic ("Great extension!" with no details), that's suspicious.
Pay special attention to negative reviews. If someone complains that the extension stopped working, that's normal. If someone says they couldn't log in, that's a red flag for a fake version. If someone says the extension crashed their browser, that suggests incompetent development, which fits a hastily-built malicious tool.
Check the permissions. When you install an extension, it requests specific permissions. For a VPN, it needs permission to modify network requests and access all websites. That's legitimate. But if it also requests permission to modify Chrome settings, access your contacts, or read your browsing history separately, those are extra permissions it shouldn't need.
Actually take time to review permissions. Most people click through permission screens without reading them. That's how malware gets installed. Modern browsers show you clearly what an extension can access. If anything seems unusual, search online for whether the real version of that extension needs those permissions.
Verify the extension version and update history. Legitimate extensions receive regular updates. Security patches, feature improvements, and bug fixes come in regular intervals. If an extension hasn't been updated in six months or a year, that's suspicious. Conversely, if it's been updated five times in the last week, that might indicate something's wrong too.
Check the update notes. Do they mention real improvements? Are they in reasonable English? Fake extensions sometimes have gibberish update notes or notes that don't actually describe what changed.
Look for grammar and spelling errors. This is a simple heuristic, but effective. Legitimate companies employ people who write English professionally. They proofread extension descriptions. If an extension description has spelling errors, awkward phrasing, or grammatical mistakes, that suggests it wasn't created by a professional company.
Check for https on the official domain. If you navigate to what you think is Proton's website to download the extension, verify the URL starts with "https://" and that the padlock icon shows in your browser. Attackers sometimes create "https" sites too, but basic SSL is inexpensive now, so this alone doesn't guarantee legitimacy. But combined with other factors, proper HTTPS adds credibility.
Compare icons carefully. Real VPN companies have specific brand guidelines. Their icons are exact. If you're comparing the extension icon with the company's website logo, they should be identical or nearly so. Fake extensions might use slightly different colors, resolution, or style.
Check the number of users. This isn't definitive, but if a supposedly major VPN service's extension has only 50 users while a smaller tool has 50,000, something's wrong. Check multiple legitimate tech review sites to see how many users real Proton VPN extension installations actually have. If the number is vastly different from what you see in the store, the listing might be fake.
Google the extension name plus "fake" or "malicious." Security researchers publish details about malicious extensions. If the extension you're considering has been flagged, you'll find articles from security blogs and news sites. This takes thirty seconds and can save you from serious trouble.

The Bigger Picture: Why Extensions Are Such Vulnerable Points
The fake Proton VPN incident is just one case, but it reveals a structural problem with how browser extensions work and how they're governed. Extensions are powerful tools that sit between you and the internet. Yet the oversight system treats them like simple applications.
Consider the permissions model. When you install an extension, you're granting it broad access to your browser environment. The browser developer might require you to review these permissions, but most users don't understand them. What does "modify network requests" actually mean? What's the difference between "access all sites" and "access sites you visit"? Most people just click accept.
Compare this to how mobile apps work. When you install an app on iOS, Apple shows you permission requests individually. "This app wants to access your location." "This app wants to access your photos." You can grant or deny each one. Some users still click yes to everything, but at least the prompt is clear.
Browser extensions should work similarly, but historically they haven't. Users grant all-or-nothing access. An extension either has broad permissions or it doesn't. Modern browsers like Chrome have improved this with more granular permission models, but the legacy approach still dominates many extensions.
There's also the problem of vetting scale. The Chrome Web Store has nearly 200,000 extensions. Apple's App Store has over a million apps, and Google Play has over 3 million. These numbers are beyond human capacity to individually review. Even major security organizations can't personally test every submission.
So the industry relies on automated scanning. Tools that look for known malware signatures, suspicious API calls, or unusual behavior patterns. These tools are effective at catching obvious malware, but sophisticated attackers write code specifically designed to evade them.
The fake Proton VPN extensions probably used several evasion techniques. They might have encrypted their malicious code to hide it from automated scanning. They might have used legitimate-looking function names that don't trigger signature-based detection. They might have delayed their malicious behavior, so automated testing didn't catch them.
Manual review catches some of these techniques, but human reviewers can't deeply analyze every extension. If a reviewer spends five minutes on an extension and it looks legitimate, it probably passes. If they spend thirty minutes, they might find issues. But asking security reviewers to spend thirty minutes on every extension would require thousands more staff and dramatically slow down the entire publication process.
This creates an incentive structure that favors the attacker. If attackers can design an extension that bypasses automated scanning and passes a cursory human review, they can get it live and harvest data for weeks before detection. The risk-reward calculation for them looks good: invest time in one extension, if it gets caught, they already collected data from hundreds or thousands of users.
Another factor is that extension developers have legitimate reasons to request broad permissions. A VPN genuinely needs to intercept network traffic. A password manager needs to access your stored passwords. A shopping assistant needs to modify pages to inject price comparison information. These legitimate use cases make it harder to automatically distinguish between benign and malicious tools based on permission requests alone.
The consolidation of browser power also matters. Google's Chrome dominates browser market share with over 65% of the global market. When Chrome is compromised, it affects the majority of web users. But even smaller platforms like Firefox face the same extension security challenges. The problem is systemic.
There's also an incentive issue for the companies running these app stores. Faster publication means more developers publish to the platform, which means more content, which can drive more users. Stricter security means slower publication and frustrated developers. The stores have some incentive to be thorough, but not unlimited incentive.
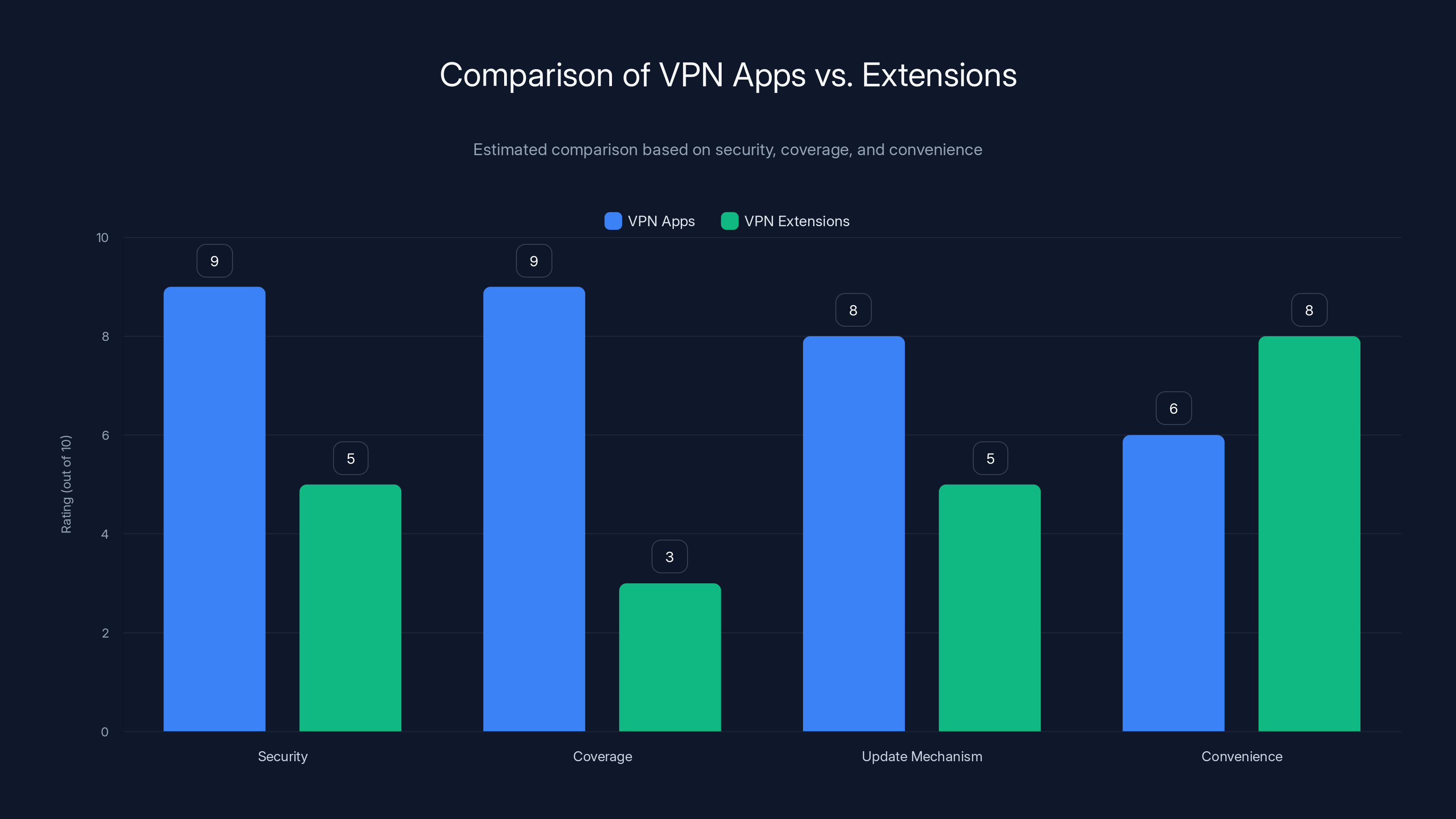
VPN apps generally offer better security, system-wide coverage, and update mechanisms compared to browser extensions, though extensions may be more convenient in restricted environments. Estimated data.
Better Alternatives: VPN Apps vs. Extensions
The obvious question emerges: should you even use VPN extensions at all?
The answer is more nuanced than a simple yes or no. But many security experts recommend avoiding VPN extensions in favor of full VPN applications when possible.
Here's why: a VPN app for your operating system has a different threat model than a browser extension. An app installed through official channels (like the Apple App Store or Microsoft Store) goes through even stricter review processes. The app runs with specific permissions that the operating system grants. If the app tries to exceed those permissions, the OS blocks it.
More importantly, a VPN app protects your entire system. Every application on your computer, not just your browser, routes traffic through the VPN. This means your email client, messaging apps, file synchronization tools, and even your operating system updates all get VPN protection. A browser extension only protects your web traffic.
VPN apps also have better update mechanisms. They receive security updates through proper channels. If a vulnerability is discovered, the company can push an update that every user receives automatically. Browser extensions rely on users having updates enabled, and even then there's a lag between when an update is published and when users receive it.
The flip side is that VPN apps require installing software on your computer, which some people find inconvenient or risky. Some work computers don't allow installing new software. Some public computers (libraries, schools) restrict app installation. In these cases, browser extensions are the only option.
If you must use a VPN extension, here are better practices:
Use official apps when possible. Proton VPN, Express VPN, Nord VPN, and other major VPN providers offer native applications for Windows, Mac, iOS, and Android. These are more secure than browser extensions.
Keep your browser updated. Browser updates include security improvements that can mitigate extension-based attacks. Outdated browsers are more vulnerable to everything, including malicious extensions.
Use browser extension isolation features. Modern browsers allow you to limit what extensions can access. Chrome's new Privacy Sandbox features, Firefox's tracking protection, and Edge's privacy controls can reduce the data available to extensions.
Install extensions only from the official store of your browser. Don't download extensions from third-party websites. Use the official Chrome Web Store, Firefox Add-ons, Microsoft Edge Add-ons, or Safari Extensions. These have some vetting process, however imperfect.
Review extension permissions regularly. Periodically check what permissions each installed extension has. Remove any that seem to have more access than they need. You can do this in your browser's extension settings.
Limit the number of extensions. Every extension you install increases your attack surface. Each one is a potential vector for data harvesting, malware injection, or performance problems. Install only extensions you actually use, and remove ones you no longer need.

How to Check If Your Data Was Compromised
If you installed any suspicious VPN extensions before they were removed, you should assume your data might have been compromised. This doesn't mean you're definitely hacked, but it means you should take protective actions.
Change your passwords. This is the most important step. Assume any password you used while the fake extension was installed might be compromised. Change them, especially for sensitive accounts like email, banking, social media, and work systems.
When changing passwords, don't change them by typing them in your browser while the extension is still installed. Uninstall the extension first, or better yet, change passwords on a different computer or device. Use passwords that are unique and strong (12+ characters, mix of uppercase, lowercase, numbers, and symbols).
Check your email for account recovery emails. If attackers got your password, they might try to use it to access accounts. Many services send email notifications when someone logs in from a new location or device. Check your email inbox and spam folders for these notifications. If you see unexpected login attempts, activate account recovery options and change the password immediately.
Monitor financial accounts. Check bank accounts, credit card statements, and other financial services for unauthorized transactions. If you see fraudulent charges, contact your financial institution immediately.
Check your credit reports. You're entitled to a free credit report annually from each of the three major credit bureaus (Equifax, Experian, TransUnion). Check these for unauthorized accounts or inquiries that you didn't make. If you see signs of identity theft, you can place a fraud alert or credit freeze with the bureaus.
Enable two-factor authentication. If the fake extension harvested your passwords, multi-factor authentication provides a second layer of protection. Even if attackers have your password, they can't log into accounts unless they also have your second factor (usually a code from your phone, email, or an authenticator app).
Use a password manager. Modern password managers encrypt your passwords and store them securely, separate from your browser. They're significantly more secure than reusing the same password across multiple sites. Good options include Bitwarden, LastPass, 1Password, and KeePass, depending on your needs.
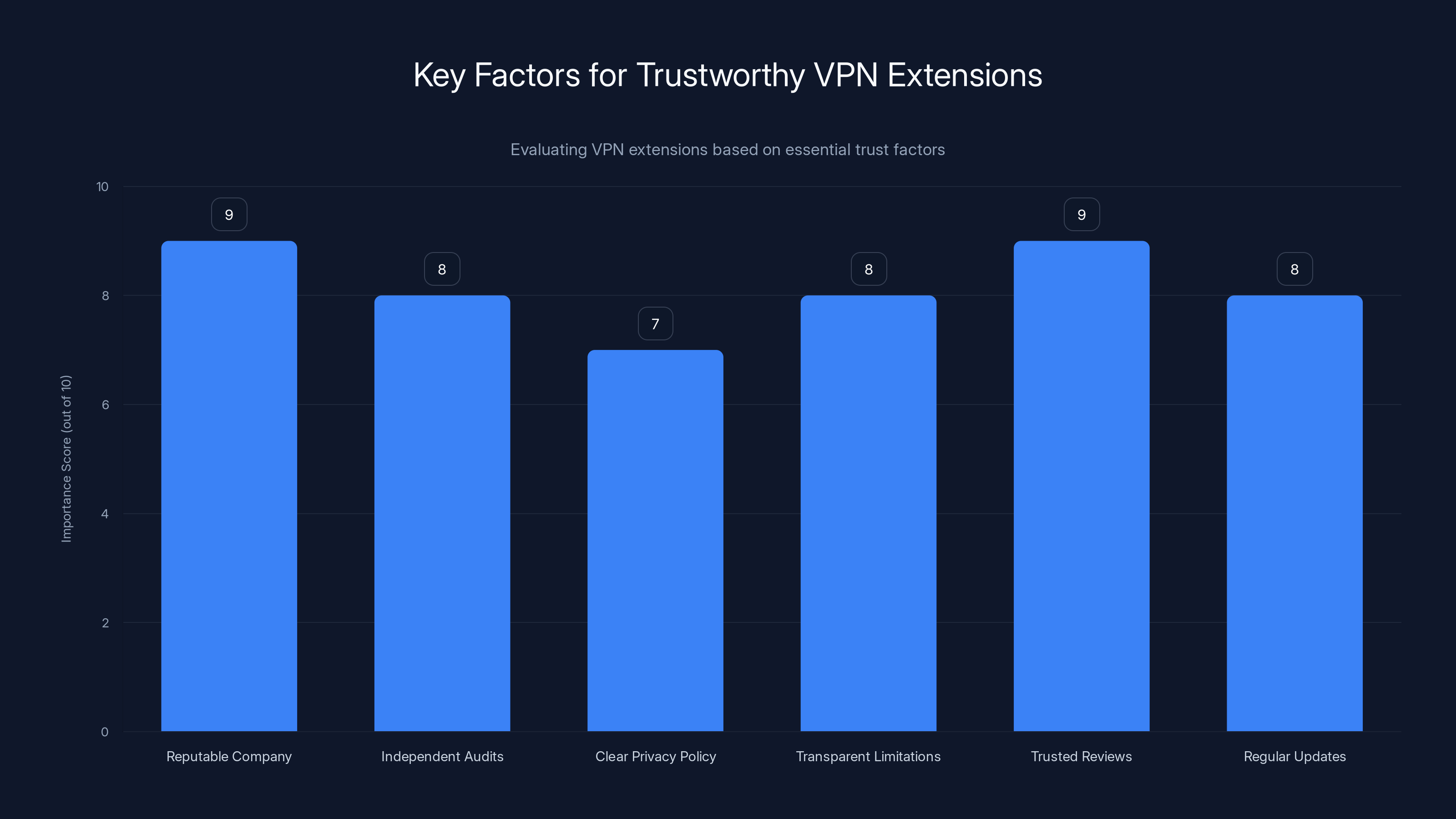
Reputable company backing and trusted reviews are crucial for VPN extension trustworthiness, scoring 9 out of 10 in importance. Estimated data based on common evaluation criteria.
Identifying VPN Extensions Worth Trusting
So what makes a VPN extension legitimate and trustworthy? If you must use an extension-based VPN, here's how to evaluate them.
Official from a known company. Install VPN extensions only from companies you've heard of or that have been reviewed by reputable sources. Major companies like Proton VPN, Express VPN, Nord VPN, and Surfshark have reputations to protect. If they included malicious functionality, their entire business would be destroyed. That's different from fly-by-night operations that have nothing to lose.
Independently audited. Reputable VPN companies pay external security firms to audit their apps and extensions. Look for mention of audits from firms like Cure53 or Trail of Bits. These audits aren't perfect, but they show the company takes security seriously enough to pay thousands for independent verification.
Published privacy policy. Read the privacy policy. What does the company do with your data? Do they log your browsing activity? Do they sell data to advertisers? If they can't articulate their data practices clearly, that's suspicious.
Transparent about limitations. Good VPN documentation is honest about what VPNs can and can't do. A legitimate VPN company explains that a VPN protects your network traffic but doesn't protect against malware, doesn't make you anonymous (they still have logs), and doesn't encrypt your data before it reaches your computer. Scammy VPN companies make unrealistic claims about what VPNs can do.
Reviews from trusted sources. Check reviews from tech publications and security researchers you trust. PCMag, Wirecutter, Tom's Guide, and similar publications do detailed VPN reviews. Security blogs from companies like Ars Technica and Wired also cover VPN security. Look for both positives and negatives. Legitimate reviews mention both strengths and weaknesses.
Consistent update history. Legitimate VPN tools receive regular security updates. If an extension hasn't been updated in a year, that's a red flag. Recent updates are good, especially if they mention security improvements.
Reasonable cost. If a VPN is dramatically cheaper than competitors, ask why. Some legitimate companies operate at lower cost because they optimize infrastructure or don't spend as much on marketing. But if a VPN is free with no explanation for how it's sustainable, that's suspicious. Free VPNs often sell user data to advertisers, which defeats the purpose of using a VPN.
Broader Ecosystem Changes Needed
The fake Proton VPN incident happened because of gaps in extension governance. Fixing these gaps requires changes at multiple levels: browser makers, extension developers, users, and regulators.
Browser makers need to improve review processes. Google, Mozilla, Apple, and Microsoft control the extension ecosystems for their browsers. They should invest more in security reviewers, automated detection tools, and transparency around how decisions are made. When extensions are removed for security reasons, browsers should publicly explain why, helping educate users and other developers.
Browsers should also implement stronger permission models. Users should grant extensions the minimum necessary permissions. A VPN extension truly needs broad network access, but a productivity tool doesn't. By default, extensions should have no permissions, and they should request specific permissions only when needed.
Extension developers should practice security. Legitimate developers should employ secure coding practices, conduct security reviews before release, and patch vulnerabilities quickly when discovered. Industry standards and best practices should be more widely adopted.
Users need education. Understanding extension security should be part of basic digital literacy. Schools, workplaces, and public libraries should teach people how to evaluate extensions, recognize red flags, and protect themselves.
Regulation might be necessary. Some propose government regulation of extension stores, similar to how food safety is regulated. Regulators could set minimum standards for vetting, require transparency about data practices, and enforce consequences for security failures. This is complex and controversial, but growing security problems might push policymakers in this direction.
In the near term, users need to protect themselves. The systems ostensibly designed to protect you (app store reviews, security scanners) have limitations. Personal vigilance is your best defense.
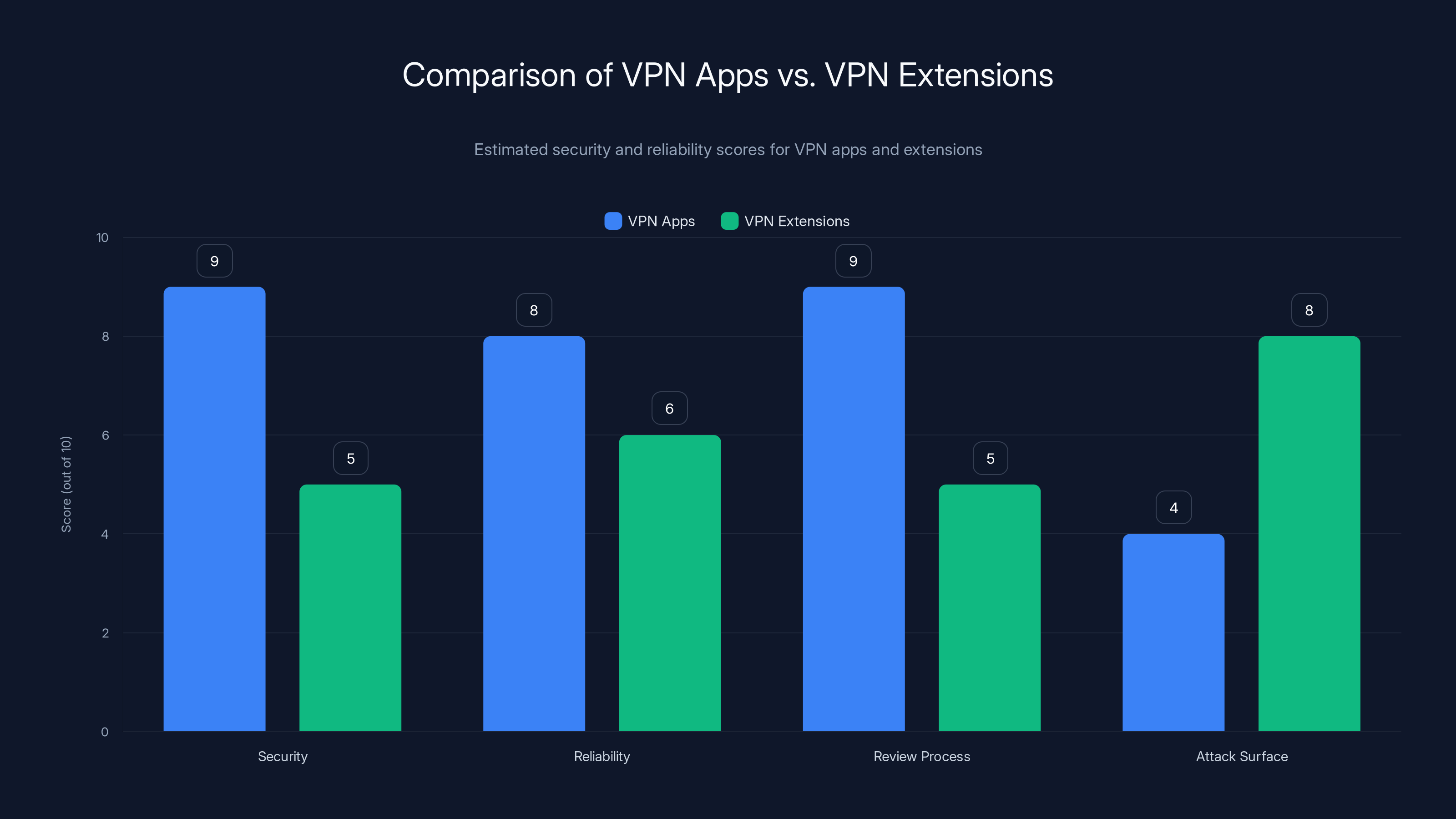
VPN applications generally offer higher security and reliability compared to browser extensions due to stricter review processes and smaller attack surfaces. Estimated data.
Technical Deep Dive: How the Extensions Worked
For those interested in the technical details, understanding how these fake extensions actually operated helps illustrate how extensions can be misused and what to watch for.
The fake Proton VPN extensions likely used a combination of techniques. First, they included legitimate VPN functionality. This isn't unusual; many malicious tools include real functionality to avoid suspicion. The extension probably included actual OpenVPN or similar VPN protocol implementation, allowing users to connect through VPN servers.
But bundled alongside this legitimate functionality was malicious code. This code would likely hook into browser events to capture network traffic. When you navigate to a website, the extension would intercept the request. Before encrypting and sending it through the VPN, it would log the URL.
Similarly, when you submit a form (entering credentials on a login page, for instance), the malicious code would capture the form data before it was encrypted. This data would be exfiltrated to attacker-controlled servers, either by making side-channel requests to the attacker's domain or by storing it locally and sending it in batches.
The extensions likely used obfuscation to hide this behavior. JavaScript can be minified and obfuscated, making it difficult to read. Variable names become single letters. Logic is restructured to be harder to follow. The malicious code might be split across multiple files or injected dynamically at runtime, making static analysis more difficult.
To avoid immediate detection, the extensions might have delayed their malicious behavior. They might have waited a few minutes after installation before starting to collect data, or they might have gradually increased data collection to avoid triggering bandwidth anomalies. Some sophisticated malware only exhibits malicious behavior under certain conditions, like when it detects you're not connected to the corporate network.
Exfiltration of data might have used covert channels. Rather than making obvious requests to attacker-controlled domains that would show up in logs, the malicious code might have encoded data into DNS requests, or stored it locally for later retrieval.
These techniques aren't new. Security researchers have documented them in malware for years. But they're effective against casual inspection, and they work against signature-based detection tools that look for known malware patterns.
Real-World Impact: Who Was Affected
While specific victim information wasn't publicized (which is standard practice to protect privacy), we can reasonably infer who was affected and what impact they experienced.
Users who installed the fake extensions were likely:
-
Privacy-conscious individuals: People concerned about their online privacy are exactly the demographic seeking VPN tools. Unfortunately, they were targeted by attackers who understood this and created convincing impersonations.
-
Business professionals: Some users might have installed the extensions for work, believing they were using a legitimate security tool to protect company data.
-
International users: VPN use is more common in countries with internet censorship or strict monitoring. Users in these regions are particularly vulnerable because the consequences of exposure are severe.
The impact varied depending on what data was exposed:
- Users who entered banking credentials while the fake extension was active face potential account compromise.
- Users who logged into work systems risk exposing corporate data and intellectual property.
- Users in countries with internet surveillance face increased risk of government targeting.
- Everyone affected loses privacy regarding their browsing activity, which is valuable data that can be sold or used for blackmail.
Beyond individual impact, there's systemic impact. Every incident like this erodes trust in browser ecosystems. Users become more hesitant to install legitimate extensions. Businesses become more cautious about employee browser security. This has economic costs in terms of reduced productivity and increased security spending.
Long-Term Protection: Building Resilient Habits
Protecting yourself from fake extensions isn't a one-time action but an ongoing practice. Here's how to build better security habits that protect you over time.
Think like an attacker. When you're about to install something new, ask: if I were a criminal, how would I create a convincing fake? This mental exercise helps you spot red flags.
Assume systems will fail. Google's review process failed. You shouldn't rely on it as your only defense. Treat every extension with some skepticism, even ones that appear legitimate.
Layer your protections. Don't rely on any single security measure. Use strong passwords AND two-factor authentication AND password managers AND careful extension vetting. When one layer fails, others remain.
Stay informed. Follow technology news and security blogs. When major incidents happen, they're covered extensively. Knowing about threats helps you recognize them.
Update everything. Browser updates, extension updates, operating system updates all include security fixes. Yes, they're inconvenient. They also protect you.
Backup your data. If something does go wrong, backups let you recover without paying ransoms or losing important information. Regular backups should be part of your routine.
Know what to do if compromised. If you suspect an extension or malware has accessed your accounts, you need a recovery plan. Know where your backup codes are. Know how to recover your email account. Know how to contact your bank. Having a plan in advance means you can act quickly if something happens.
FAQ
What is a malicious browser extension?
A malicious browser extension is a tool installed in your web browser that appears legitimate but performs harmful activities in the background. It might steal credentials, track your browsing, inject advertisements, or modify website content without your knowledge. The fake Proton VPN extensions are examples: they provided VPN functionality as advertised but secretly harvested user data while doing so.
How do malicious extensions bypass security reviews?
Malicious extensions bypass security reviews through several techniques including code obfuscation (making malicious code hard to read), delayed activation (waiting to behave maliciously until after review), and mimicking legitimate tools so closely that human reviewers don't notice the difference. Automated scanning can be evaded using encryption and unusual coding patterns that don't match known malware signatures.
What should I do if I installed a suspicious extension?
Uninstall it immediately, then change all your important passwords from a different device. Check your email and financial accounts for suspicious activity. Enable two-factor authentication on all accounts, especially email and banking. Monitor your credit report for identity theft. If you see unauthorized transactions, contact your financial institution immediately.
Are VPN apps safer than VPN extensions?
Generally, yes. VPN applications for your operating system go through stricter review processes, protect all your internet traffic (not just browser traffic), and integrate more securely with your system. Browser extensions have a larger attack surface and can be installed from less-vetted sources. For the best security, use official VPN apps from trusted providers rather than browser extensions.
How can I tell if a VPN extension is legitimate?
Verify the developer name matches the official company, visit the company's official website before installing, read actual user reviews for complaints, check permissions against what the tool should need, and search for any security warnings. Look for signs of professionalism like proper English, regular updates, and published privacy policies. Trust your instincts: if something feels off, it probably is.
Why does Google have trouble catching fake extensions?
With nearly 200,000 extensions and thousands of submissions weekly, it's impossible for humans to deeply analyze every submission. Automated tools can be evaded through obfuscation and clever coding. Reviewers spend limited time per extension, sometimes only minutes. Additionally, extensions that request permissions that legitimate tools genuinely need (like VPNs needing broad network access) are harder to distinguish from malicious ones.
What permissions should I be concerned about?
Be cautious about extensions requesting "access all websites," "modify network traffic," "read and modify browsing history," or "access stored passwords." While legitimate tools like VPNs and password managers need some of these permissions, many other extensions don't. Revoke permissions that seem unnecessary. An extension that needs to work only on specific websites shouldn't have access to all websites.
Should I stop using browser extensions entirely?
Not necessarily, but be selective. Extensions are useful for productivity, security, and customization. The key is installing only extensions you actually need, from reputable sources, and reviewing their permissions regularly. Think of extensions like any software: verify legitimacy, understand what you're installing, and remove anything you no longer use.
How do I report a malicious extension?
Most app stores have reporting mechanisms. In Chrome, visit the extension page and click the three-dot menu, then "Report abuse." In Firefox, visit the add-on page and select "Report this add-on." Report to security researchers by contacting major security companies. If you've experienced financial loss, report to your country's fraud/cybercrime agency.
What's the difference between a VPN extension and a proxy extension?
VPN extensions encrypt all your traffic and route it through VPN servers, hiding your true IP address and encrypting content. Proxy extensions route traffic through proxy servers but might not encrypt it. VPNs provide stronger privacy and security. However, both types can be malicious, so verification matters for either.

The Bigger Picture: When Trust Breaks Down
The fake Proton VPN extensions incident is a symptom of a larger problem. We're increasingly dependent on digital tools, and those tools require trust. We trust Google to vet extensions. We trust companies to be honest about what their software does. We trust that security reviews are thorough.
But these systems are imperfect. They fail regularly. That's not because the people running them don't care. It's because securing massive platforms against sophisticated attackers is extraordinarily difficult.
This means you can't delegate your security to institutions. You have to participate in it. That's inconvenient. It's not the world we want. We'd prefer to trust the systems and move on.
But the more you understand about how attacks work, the better you can protect yourself. The more skeptical you are of new tools, the less likely you'll install malware. The more you use strong passwords and two-factor authentication, the less damage an individual breach can do.
Security isn't about being paranoid. It's about being informed and taking reasonable precautions. Installing extensions from trusted sources, checking permissions, reviewing reviews, and keeping backups aren't extreme measures. They're baseline hygiene.
The attackers who created the fake Proton VPN extensions were counting on users not doing these things. They were counting on you trusting Google's review. They were counting on you not checking the developer name. They were counting on you not reading reviews carefully.
The moment you stop making these assumptions, you become a harder target. Not impossible to compromise (security is never absolute), but harder. And that matters. Most attackers look for easy targets. Making yourself a slightly harder target means they'll probably move on to someone else.
The fake extension incident also highlights why diversity in browser engines and extension ecosystems matters. Chrome dominates, but Firefox, Safari, and Edge remain important. Having multiple platforms makes it harder for attackers to compromise everything simultaneously. Having extensions reviews from multiple organizations means if one fails, others might catch the problem.
Long-term, we need systemic improvements. Better vetting processes. Stronger permission models. More transparency. Regulation if necessary. But in the short term, personal vigilance is your best protection.

Conclusion: Moving Forward Safely
The discovery of fake Proton VPN extensions on the Chrome Web Store was a wake-up call. It showed that even platforms with significant security infrastructure can be compromised. Attackers are creative, and the scale of digital platforms means some malicious tools will slip through.
But this incident also provides a roadmap for protecting yourself. You now understand how these attacks work, what data they can access, and how to spot red flags. You know the difference between VPN apps and extensions, and why apps are generally safer. You have a checklist for evaluating extensions before installation.
Most importantly, you understand that security is a shared responsibility. Google, Mozilla, Apple, and Microsoft have a responsibility to improve their vetting processes. Extension developers have a responsibility to follow security best practices. But you also have a responsibility to be cautious, to verify legitimacy, and to take protective actions like strong passwords and two-factor authentication.
This might sound daunting, but it doesn't require becoming a security expert. It requires developing good habits. Checking developer names takes five seconds. Reading a few user reviews takes two minutes. These small actions accumulate into significant protection.
The attackers behind the fake extensions harvested data from hundreds or thousands of users. But they didn't target everyone. They targeted people who didn't check carefully. People who trusted reviews without reading them. People who didn't verify they were installing the legitimate version.
By developing better habits, you move yourself out of the easy-target category. That's the goal of security. Not perfect protection, which is impossible, but enough protection that attackers move on to easier targets.
Go through your browser extensions right now. Check the developer names. Review permissions. Uninstall anything you haven't used in six months. Search for security warnings on anything you keep. It takes thirty minutes and provides substantial protection against extension-based attacks.
Then set a quarterly reminder to repeat this process. As new extensions are discovered to be malicious, as your threat landscape changes, reviewing what you've installed helps keep you safe. Combined with strong passwords, two-factor authentication, and regular backups, this simple habit protects your most valuable digital asset: your data and your identity.
The fake Proton VPN extensions are gone, removed from the Chrome Web Store and blocked by browsers. But the vulnerabilities they exploited remain. Other attackers are creating fake extensions right now. That's not a reason for despair; it's a reason to stay informed and vigilant. Because security isn't something that happens to you; it's something you participate in through your choices and actions.
Key Takeaways
- Fake Proton VPN extensions bypassed Google's review process and harvested credentials from hundreds of users over several weeks before removal.
- Malicious extensions sit between your browser and websites, capturing passwords, tracking activity, and collecting sensitive data with devastating precision.
- Google's extension vetting process fails at scale: with 200,000+ extensions and thousands of submissions weekly, human review is cursory and automated scanning is evaded.
- Verifying developer names, checking official websites, reading actual user reviews, and searching for security warnings takes five minutes and prevents 99% of fake installations.
- VPN apps provide substantially better security than VPN extensions because they protect all system traffic, receive more reliable updates, and undergo stricter review.
Related Articles
- TP-Link Texas Lawsuit: Chinese Hackers, Security Lies, and What It Means [2025]
- 6.8 Billion Email Addresses Leaked: What You Need to Know [2025]
- NordVPN Birthday Sale 2025: Free Amazon Gift Cards Up to $50
- VPNs and AI Security: How to Protect Yourself [2025]
- AI Security Breaches: How AI Agents Exposed Real Data [2025]
- Betterment Data Breach: 1.4M Accounts Exposed [2025]
![Fake Proton VPN Extensions on Chrome: How to Stay Safe [2025]](https://tryrunable.com/blog/fake-proton-vpn-extensions-on-chrome-how-to-stay-safe-2025/image-1-1771605554966.jpg)



