Betterment Data Breach: 1.4 Million Accounts Exposed [2025]
You probably heard the headlines by now: 1.4 million Betterment users got caught in a data breach. But here's what's important to understand right out of the gate—nobody's trading accounts were actually compromised. No passwords were stolen. No one's investments were liquidated. This isn't one of those "your money's gone" situations.
That said, it's still serious. Attackers got names, email addresses, phone numbers, physical addresses, and birthdates for over a million people. And that's the kind of information that sets you up for a lifetime of phishing, social engineering, and identity theft if you're not careful.
I've been tracking data breaches for years, and what makes Betterment's situation particularly interesting is how it happened. This wasn't some sophisticated hack into their servers. It was way simpler and, honestly, way scarier: social engineering. A bad actor tricked a Betterment employee, gained access to a third-party platform, and used that access to send fraudulent crypto scam messages to unsuspecting customers.
Let me walk you through exactly what went down, what data was exposed, what Betterment's actually doing about it, and most importantly, what you should do if you're affected.
TL; DR
- 1.4 million Betterment accounts exposed through a social engineering attack against an employee
- No trading accounts compromised, no financial transactions affected, no credentials stolen
- Exposed data includes: email addresses, names, physical addresses, phone numbers, birthdates
- Attack method: Phishing emails sent to customers promoting fake crypto investments
- Immediate actions: Enable two-factor authentication, monitor accounts for fraud alerts, watch for phishing emails
- Bottom line: Your account is safe, but your personal information is now out there—treat phishing attempts seriously
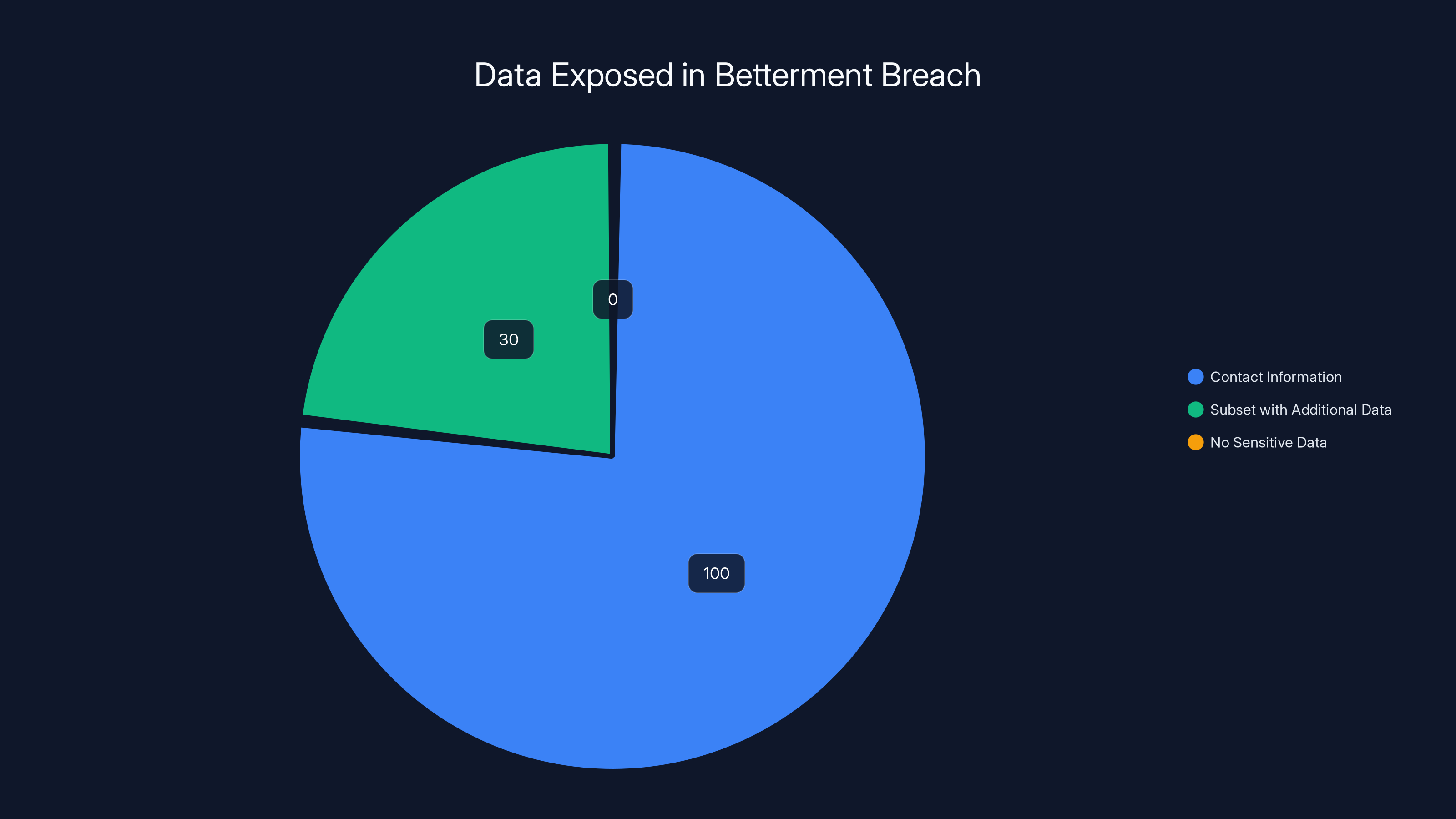
The breach exposed contact information for all 1.4 million users, with a subset also having additional data exposed. No sensitive financial data was compromised.
What Actually Happened: The Complete Timeline
The breach itself isn't complicated to understand once you break it down. In mid-January 2026, Betterment discovered that an attacker had used social engineering to compromise an employee. Let me emphasize this: it wasn't a technical hack. Nobody bypassed firewalls or exploited zero-day vulnerabilities. Instead, someone got tricked.
The attacker used identity impersonation and deception—basically convincing an employee they were who they claimed to be—to gain access to a third-party platform. Betterment never publicly named which platform this was, but it was clearly something that had legitimately authorized access to Betterment's systems or customer data.
Once inside, the attacker didn't go looking for customer account credentials or financial information. Instead, they used the compromised access to send fraudulent messages to customers. These weren't generic phishing emails sent from an attacker's own email account. They looked like they came directly from Betterment, because the attacker was using Betterment's infrastructure to send them.
The emails promoted crypto-related scams. This is important because it's not some random attempt to get people to click a malicious link. It's a sophisticated social engineering attack designed to make people think Betterment was offering them crypto investment opportunities. Customers who fell for it might've provided their credentials, additional personal information, or even sent money to fraudulent crypto addresses.
Betterment caught this relatively quickly and shut down the unauthorized access. The company then initiated an investigation with Crowd Strike, a major incident response firm, to figure out exactly what happened and what data had been accessed.
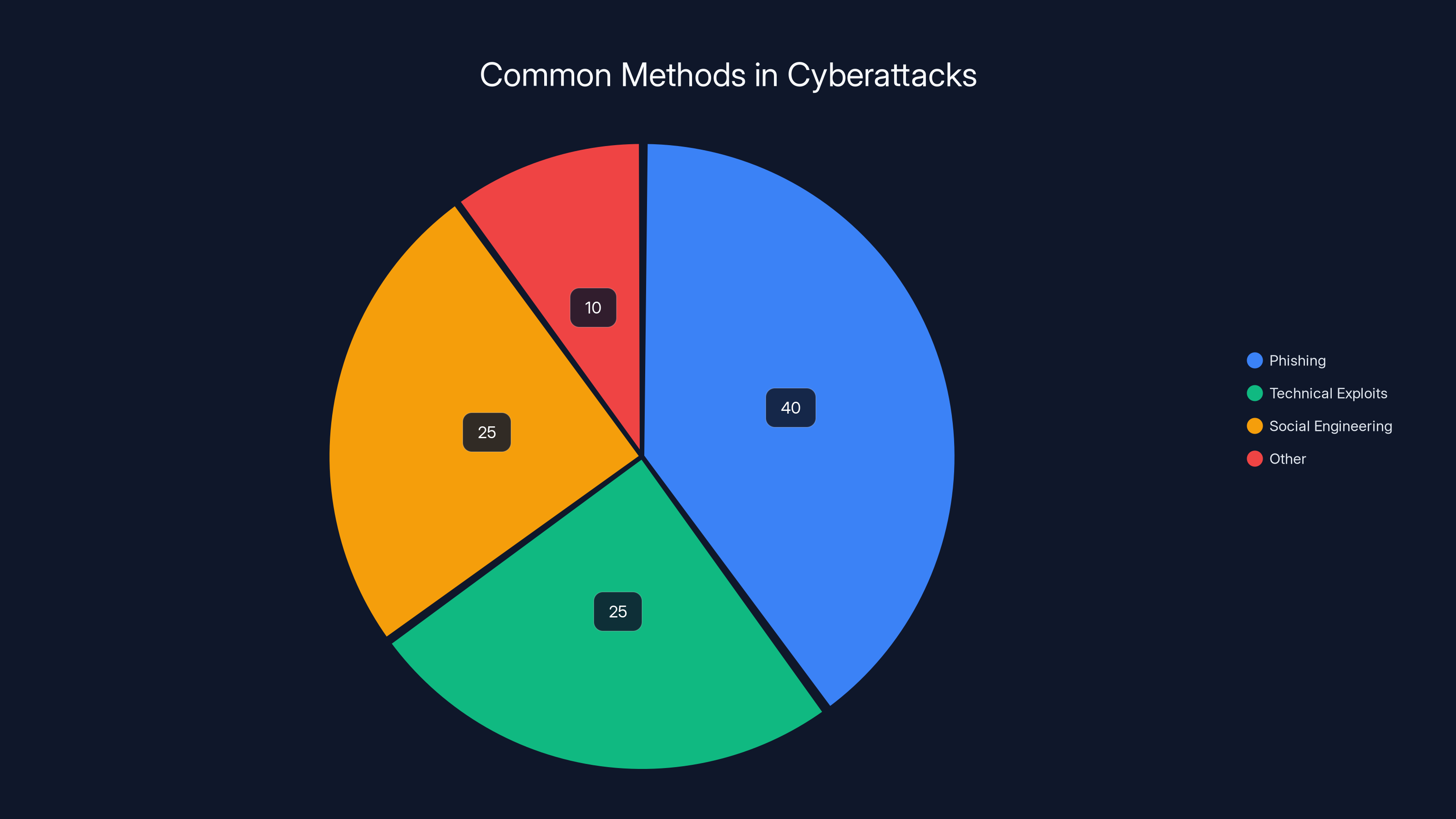
Phishing and social engineering account for a significant portion of cyberattacks, highlighting the human factor as a critical vulnerability. (Estimated data)
The Scope: 1.4 Million Exposed Records Confirmed
The exact number of affected individuals was confirmed by Have I Been Pwned, an aggregation service that collects data from publicly disclosed breaches and helps people figure out if their information's been compromised. The number came in at 1,435,174 individuals.
Now, here's where scale matters. Betterment has roughly 2.5 million active users. So we're talking about something like 57% of their user base affected. That's not a narrow, targeted breach. That's massive.
But again—and I can't stress this enough—this doesn't mean 1.4 million people's accounts were "hacked" in the way people usually think. Nobody lost money. Nobody's investments were touched. The exposed data was contact information and personal identifiers, not financial information or account credentials.
Here's the exact breakdown of what was exposed, according to Betterment's official statements:
Primary exposure across all affected records:
- Email addresses
- Names
- Geographic location data
Secondary exposure (in a subset of cases):
- Physical addresses
- Phone numbers
- Birthdates
So the bad news is that attackers now have a treasure trove of personal information that can be used for identity theft, targeted phishing, and social engineering attacks. The good news is they don't have your Betterment password, your account PIN, or any financial information.
How Social Engineering Beats Technical Security
This breach highlights something security professionals have been screaming about for years: humans are the weakest link in security. And it's not because people are stupid. It's because social engineering works, and it's incredibly hard to defend against at scale.
Think about it from the attacker's perspective. To breach Betterment's infrastructure, they'd need to:
- Find unpatched vulnerabilities
- Bypass firewalls
- Evade intrusion detection systems
- Avoid triggering security alerts
- Maintain access without being noticed
That's hard, expensive, and requires significant expertise.
Or, they could:
- Research employees on Linked In
- Craft a convincing story
- Cold call someone
- Get them to click a link or provide credentials
- Gain access to a platform the company actually uses
The second path is so much easier it's almost laughable. And once you're inside a platform with legitimate access, you can do a lot of damage before anyone realizes something's wrong.
This is why every major company spends millions on employee security awareness training. It's why phishing emails are still used in 90% of cyberattacks despite being one of the oldest tricks in the book. It's why business email compromise is consistently cited as one of the costliest cybercrimes for organizations.
Betterment likely has excellent technical security. But no amount of firewalls and encryption stops someone who's legitimately supposed to be inside your system.

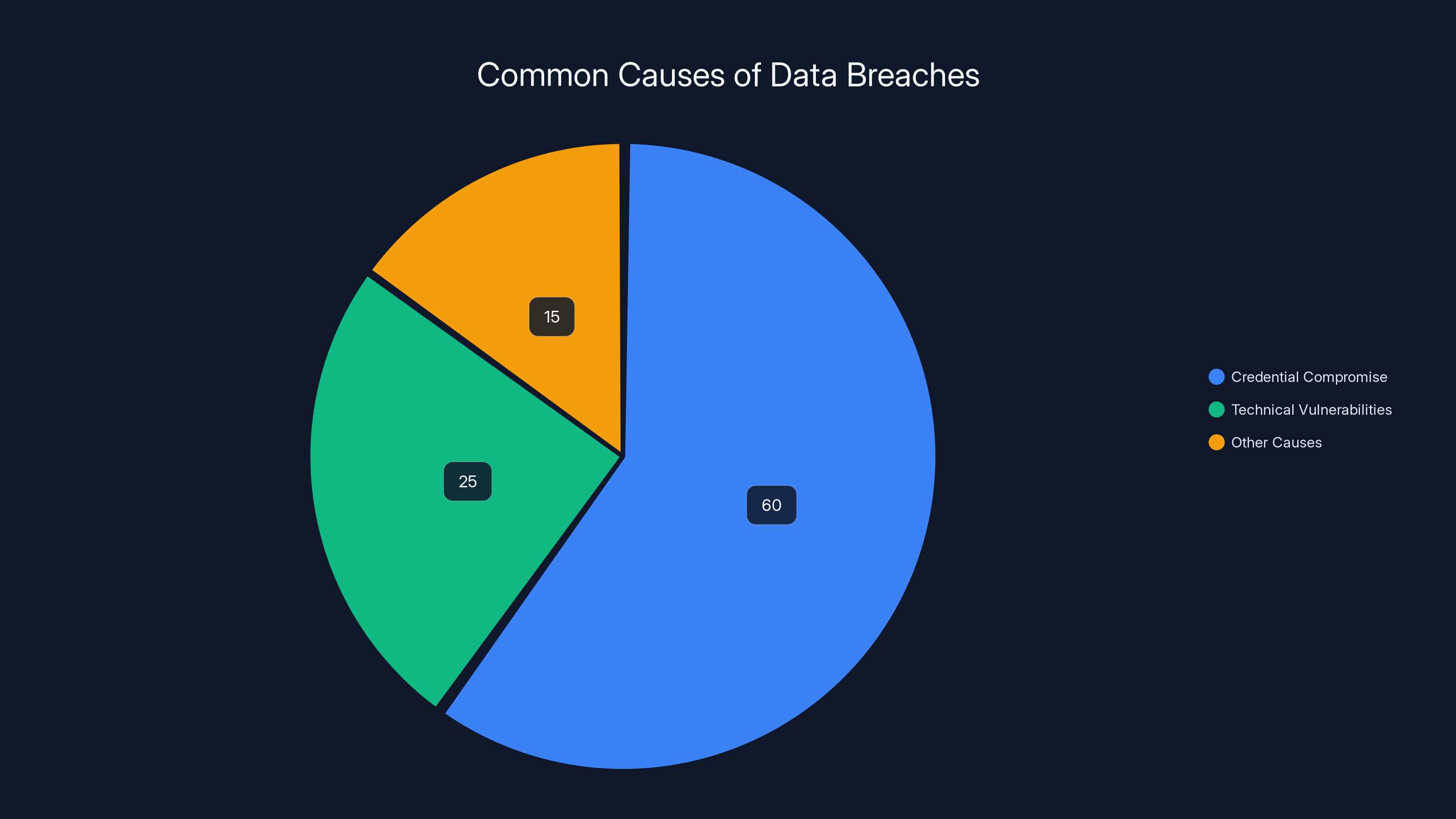
Credential compromise, including phishing and social engineering, accounts for 60% of data breaches, highlighting the need for improved human-focused security measures. Estimated data.
Crowd Strike's Investigation: What Wasn't Compromised
One of the most important parts of Betterment's response was bringing in Crowd Strike to conduct an independent investigation. This is important because it's not Betterment investigating itself—it's a third party that has no incentive to downplay what happened.
Crowd Strike's findings were clear: user accounts were not compromised. This is the key distinction everyone needs to understand.
When they say "accounts were not compromised," they mean:
- Attackers did not steal login credentials
- Attackers could not access individual user accounts
- No trades were executed without authorization
- No funds were transferred
- No account settings were changed
- Two-factor authentication keys were not obtained
What happened instead was that attackers used Betterment's infrastructure to send fraudulent messages. Think of it like someone stealing the keys to a company's mail room and using it to send out fraudulent letters that look like they're from the company. The mail room security wasn't breached—the attacker just used it as a tool.
This distinction matters enormously for customers. Your money is safe. Your investments are untouched. Your account is secure. What you do need to worry about is your personal information being used for phishing, identity theft, and social engineering going forward.

The Crypto Scam Angle: Why This Matters
The fraudulent messages that were sent promoted crypto-related scams. This is a deliberate targeting choice, and it's worth understanding why.
Betterment's user base is largely retail investors—people interested in building wealth, learning about investing, and potentially diversifying into alternative assets. Crypto appeals to exactly this demographic. They're educated enough to understand blockchain concepts but sometimes not experienced enough to recognize sophisticated scams.
An email from what appears to be Betterment promoting a new crypto investment opportunity would look legitimate to most people. Some percentage of recipients would click links, provide credentials, or follow instructions to transfer money.
Betterment did warn customers about these emails and advised them not to trust any unsolicited crypto-related offers. But the damage was already done for however many people got tricked before the warning went out.
The crypto angle also reflects a broader trend in cybercrime. Attackers increasingly target users with phishing emails that offer legitimate-seeming investment opportunities, job offers, or financial rewards. This is called spear phishing when it's targeted at specific individuals or companies.
By using Betterment's actual infrastructure to send these emails, the attackers achieved a level of legitimacy that's nearly impossible to replicate. Email authentication systems would pass checks. The message would land in the inbox instead of spam. It would pass cursory inspection as genuine.

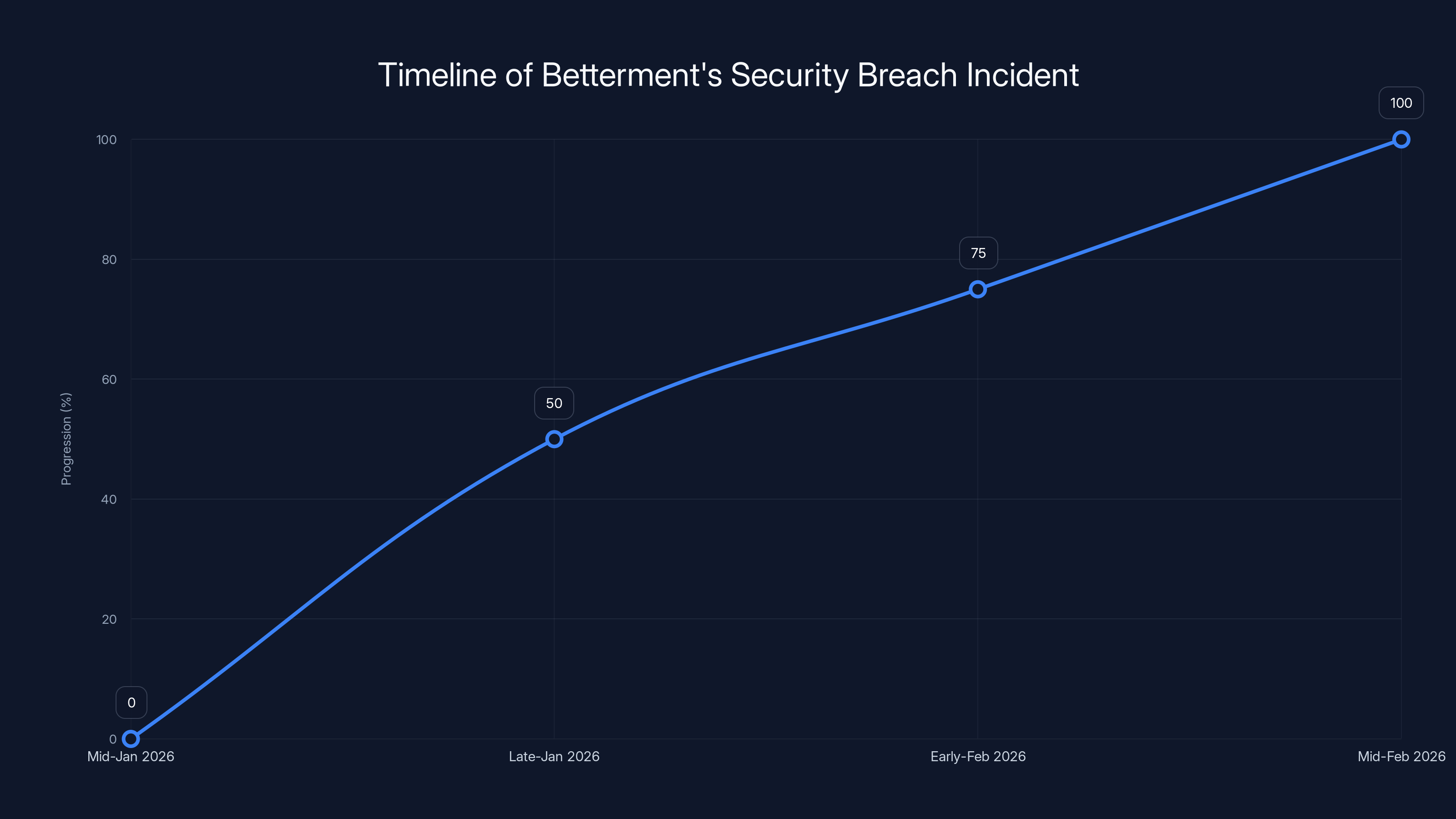
The breach was identified in mid-January 2026, with Betterment taking steps to shut down access and investigate by mid-February. Estimated data.
Personal Data Exposure: The Real Risk
Here's the thing people often miss when they hear about data breaches. The immediate risk—your account being compromised—is usually manageable. The long-term risk—having your personal information on the dark web—lasts years.
With names, email addresses, phone numbers, physical addresses, and birthdates, attackers can now:
Targeted Phishing: They know you're a Betterment customer, they have your email and phone number, and they can craft extremely convincing phishing emails and texts specifically designed for investors.
Identity Theft: With your name, address, birthdate, and possibly SSN (if it was in their systems), attackers can attempt to open fraudulent accounts, apply for credit, or file false tax returns. While they don't have your SSN from this particular breach, the combination of data makes them much better at social engineering their way to getting it.
Account Takeover on Other Platforms: If you reused your email address and password across multiple sites (which 60% of people do), attackers can attempt to gain access to your other accounts. Betterment clarified they don't have passwords, but people might have used the same credentials elsewhere.
SIM Swapping: With your name, address, and phone number, sophisticated attackers can call your mobile carrier, convince them they're you, and have your phone number transferred to a SIM card the attacker controls. Once they do that, they can reset passwords, bypass two-factor authentication, and take over your accounts.
Social Engineering: Your personal information is now in the attacker's toolkit. They can use it to impersonate you, contact your other service providers, and gain access to accounts or information.
This is why the usual advice—"just change your password and enable two-factor authentication"—is necessary but insufficient. You need to be permanently more vigilant about suspicious requests, unexpected calls, and phishing attempts.

Betterment's Response: What They Did (and What They're Still Doing)
Betterment's response to this breach has been relatively swift and transparent. Let me break down what happened:
Immediate Actions:
- They discovered the unauthorized access
- They shut down the attacker's access
- They brought in Crowd Strike for investigation
- They notified affected customers
- They warned customers about the phishing emails and crypto scams
Ongoing Actions:
- They're monitoring for any signs of additional compromise
- They're working with Have I Been Pwned to confirm the scope
- They're offering credit monitoring to affected users
- They're increasing focus on employee security training
The credit monitoring piece is worth noting. Some breaches force you to pay for credit monitoring. Betterment appears to be offering it for free to affected users, which is the standard practice for breaches of this severity.
However, free credit monitoring has limitations. It's usually limited to a set period (often 2-3 years), but the risk from this breach persists far longer. Many security experts recommend either paying for longer-term credit monitoring or using a service like My Identity Shield or Life Lock (now part of Norton 360) for continuous monitoring.
One thing Betterment hasn't publicly committed to is whether they'll be changing their third-party access policies or implementing additional authentication requirements for accessing customer data platforms. This is something customers should ask about, because it directly addresses how this breach happened.

1Password, Dashlane, and Bitwarden are all highly rated password managers, with 1Password slightly leading due to its user-friendly interface and robust security features. Estimated data based on typical user reviews.
What You Should Do If You're Affected
If you use Betterment, here's your immediate action plan:
Step 1: Confirm You Were Affected Go to Have I Been Pwned and search your email address. This will tell you definitively whether you were in this breach or others. It takes 30 seconds and costs nothing.
Step 2: Change Your Password (Just in Case) Betterment says passwords weren't compromised, but security best practice says change it anyway. Use a unique, strong password (12+ characters with uppercase, lowercase, numbers, and symbols). Don't reuse this password anywhere else.
Step 3: Enable Two-Factor Authentication If you haven't already, enable two-factor authentication on your Betterment account. Use an authenticator app (Google Authenticator, Authy) rather than SMS if possible, because SMS can be intercepted via SIM swapping.
Step 4: Review Your Account Activity Log into Betterment and review your recent account activity. Look for any trades, transfers, or settings changes you didn't make. If you see anything suspicious, contact Betterment's support immediately.
Step 5: Monitor Your Credit Check your credit reports at Annual Credit Report.com (the official free service). Look for any accounts you didn't open or inquiries from lenders you didn't apply to. You're entitled to one free report per bureau per year.
Step 6: Place a Credit Freeze Contact Equifax, Experian, and Trans Union to place a credit freeze. This prevents anyone from opening new accounts in your name. It's free and takes about 15 minutes of phone calls or 30 minutes online.
Step 7: Be Suspicious of Unsolicited Communications Expect to see increased phishing attempts. Don't click links in unexpected emails or texts claiming to be from Betterment, your bank, or other financial institutions. Instead, go directly to the official website or app.
Step 8: Monitor for Fraud Alerts Watch for unexpected bills, credit cards arriving in the mail that you didn't request, or calls from debt collectors about accounts you didn't open. These are signs of identity theft.

The Broader Pattern: Why This Keeps Happening
Betterment isn't the first company to suffer a major breach, and it won't be the last. When you look at recent breaches affecting millions of users—Sound Cloud, Equifax, T-Mobile, Yahoo—there's a pattern: human error or social engineering is involved in most of them.
Companies spend billions on technical security. They hire the best security engineers. They implement the latest technologies. But they struggle with employee security awareness, third-party access management, and the simple fact that humans are vulnerable to manipulation.
According to Verizon's Data Breach Investigations Report, roughly 60% of breaches involve credentials. That's usually phishing, weak passwords, or social engineering. Technical vulnerabilities account for a much smaller percentage.
This suggests that the most impactful investments companies could make aren't cutting-edge security technology. They're things like:
- Mandatory security training that actually teaches people how to recognize social engineering attempts
- Zero-trust architecture that doesn't automatically trust anyone once they're inside
- Stricter access controls on who can access what data and why
- Regular security audits of third-party platforms and integrations
- Incident response plans that are tested and practiced regularly
Betterment likely has some of these in place, but clearly not enough to prevent a social engineering attack from giving attackers access to customer data.

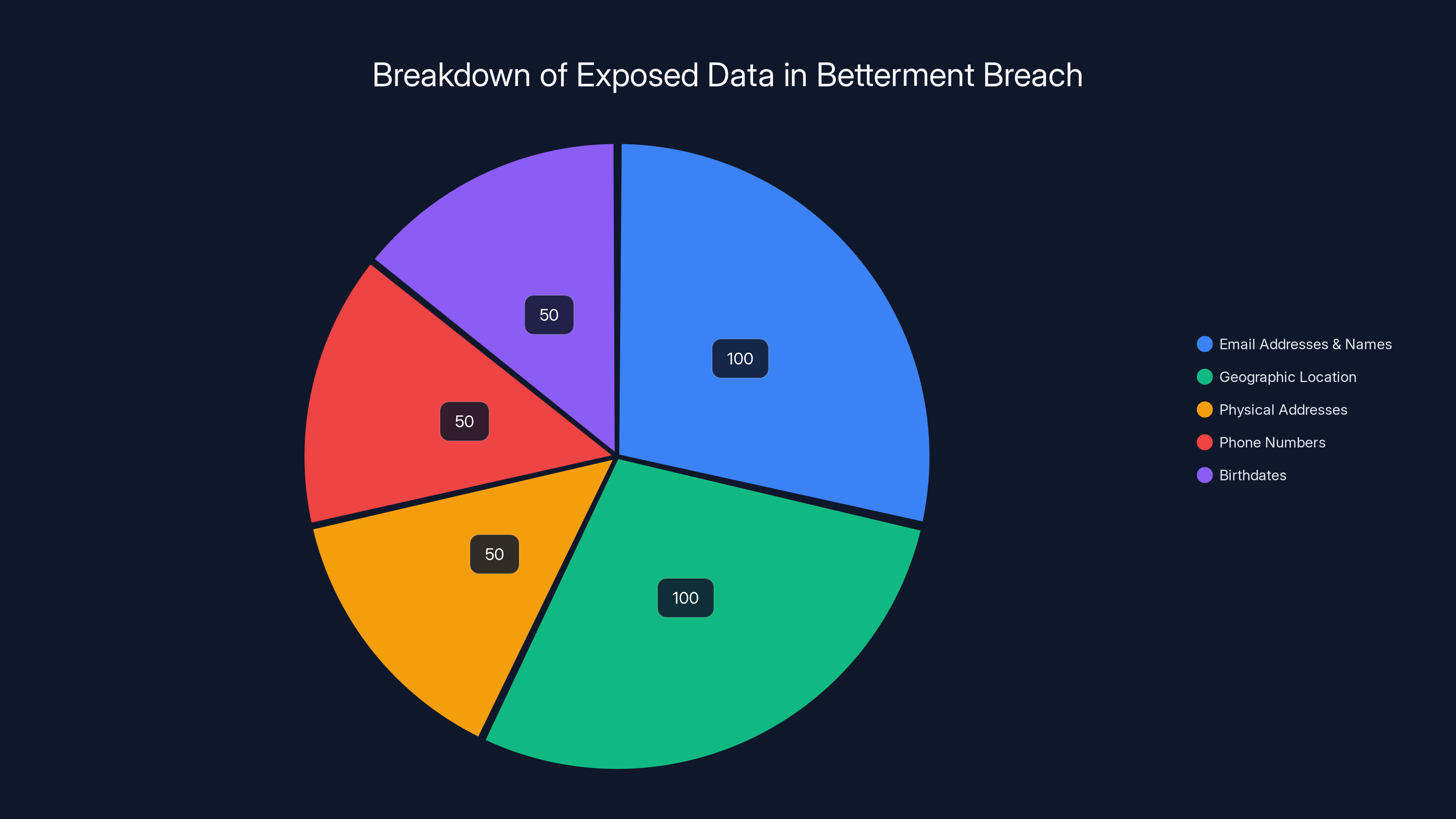
The primary exposure included email addresses, names, and geographic location data for all affected records. Secondary exposure, affecting a subset of cases, included physical addresses, phone numbers, and birthdates. Estimated data based on typical breach disclosures.
Protecting Your Financial Data Going Forward
Beyond the immediate steps for this breach, here's how to protect yourself from future compromises:
Use Unique, Strong Passwords Everywhere Password reuse is a huge vulnerability. If one site gets breached, attackers will try that password on every other site. Use a password manager like 1 Password, Dashlane, or Bitwarden to generate and store unique passwords for every account.
Enable Two-Factor Authentication on Everything Important Two-factor authentication makes it nearly impossible for someone to take over your account even if they have your password. Use an authenticator app rather than SMS when possible.
Monitor Your Accounts Actively Don't just check your credit reports once a year. Set up account alerts for:
- Large transactions
- Password changes
- Account logins from new devices
- Address changes
Most financial institutions offer these alerts for free.
Be Skeptical of Unsolicited Communications Learn to spot phishing. Real banks and companies won't ask for sensitive information via email or text. They won't send you links asking you to "confirm" your account. If you're unsure, go directly to the company's website (type the URL yourself, don't click a link) and contact them.
Limit What You Share Online Your personal information is increasingly valuable to criminals. Avoid oversharing on social media, be careful about which forms you fill out, and opt out of data brokers when possible.
Consider Identity Theft Insurance While not a substitute for vigilance, identity theft insurance can cover costs associated with fraudulent accounts, legal fees, and recovery efforts. Many homeowner's and renter's insurance policies include it.
The Crypto Scam Connection: Red Flags to Watch For
Since the fraudulent emails in this breach promoted crypto investments, here's how to spot crypto scams:
Red Flag 1: Pressure to Act Fast Legitimate investments don't require you to decide in 5 minutes. Scammers create artificial urgency: "Limited time offer," "Only 100 spots available," "Price increasing tomorrow."
Red Flag 2: Guaranteed Returns Anyone promising guaranteed returns (especially high ones like 50-100% annually) is either lying or running a Ponzi scheme. Legitimate investments have risks.
Red Flag 3: Anonymous Team Members If you can't find information about who's running the project, that's a problem. Legitimate companies have transparent leadership.
Red Flag 4: Request for Personal Keys No legitimate platform will ever ask for your private keys or seed phrases. If someone asks, they're trying to steal your crypto.
Red Flag 5: Fake Testimonials Scam sites are full of fake reviews from fake accounts. Real testimonials are harder to fake but still possible. Be skeptical of unusually perfect reviews.
Red Flag 6: Unsolicited Offers Betterment customers received unsolicited emails about crypto opportunities. Legitimate opportunities don't require unsolicited outreach.
Red Flag 7: Suspicious URLs Scammers use URLs that look similar to legitimate sites. Instead of "example.com," they might use "examp 1e.com" (with a 1 instead of l). Always verify URLs carefully.
What About Your Betterment Investments? Are They Safe?
Let's address the elephant in the room: Yes, your investments are completely safe.
Betterment's actual trading platform, portfolio management systems, and account access controls were not compromised. This breach affected only customer contact information that was accessible through a third-party platform. It didn't touch the financial systems that actually manage your money.
Moreover, Betterment uses industry-standard security for financial accounts:
- Encryption of all data in transit and at rest
- Multi-factor authentication for account access
- Account monitoring for suspicious activity
- Segregated customer assets (your money isn't Betterment's money)
- FDIC insurance on cash positions up to $250,000
The breach proves that Betterment's employee security training wasn't sufficient to prevent social engineering. But it doesn't prove that their financial systems are vulnerable.
That said, if this breach makes you uncomfortable using Betterment, that's understandable. Some customers will switch to competitors. Others will stay because Betterment's actual service and security infrastructure are solid—they just got caught by something incredibly common (social engineering) that affects even the most secure companies.

Comparing Betterment to Competitors: Security Implications
You might be wondering: Does Betterment's security compare to other robo-advisors or investment platforms?
The truth is, major financial platforms are all targets for the same types of attacks. Vanguard, Charles Schwab, Fidelity—they've all dealt with breaches or security incidents. It's not a Betterment-specific problem. It's an industry-wide challenge.
What matters more than any single breach is how a company responds. Did they investigate thoroughly? Did they notify customers? Are they implementing improvements?
Betterment's response has been solid on all three counts. They brought in Crowd Strike. They notified customers. They shared details about what happened and what wasn't compromised. That's the gold standard for breach response.
Few companies are perfect. What you want is a company that's good at responding when something goes wrong. Betterment appears to be that company.
The Third-Party Risk Problem
One thing worth discussing is Betterment's use of third-party platforms to access customer data. This is standard practice in tech—companies use services for email, customer support, analytics, etc.
But it creates what security professionals call supply chain risk. You're not just trusting Betterment's security. You're trusting every third-party service they use. And if one of those services gets compromised, your data is at risk.
This is actually a huge vulnerability in modern technology. The Solar Winds breach (which affected thousands of companies) happened because attackers compromised a software update from a vendor. The 3CX breach compromised supply chain security software. These vendor breaches often have much bigger consequences than direct breaches.
What Betterment should do going forward:
-
Audit third-party access: Every third-party service that touches customer data should have minimal, well-documented access. Access should be logged and monitored.
-
Implement zero-trust access: Don't assume that someone inside a legitimate platform is legitimate. Require additional authentication for sensitive data access.
-
Regular penetration testing: Hire security firms to specifically test how attackers could abuse third-party integrations.
-
Better employee training: Teach employees how social engineering works and why they should be suspicious of requests that seem legitimate.
These aren't unique to Betterment. They're industry best practices that most major financial companies are working on.

Recovery and Moving Forward
For Betterment as a company, this breach is significant but not catastrophic. Their core business—actually managing investments and providing good returns—wasn't impacted. Customer money is safe. That's what matters most.
But they will face some short-term consequences:
- Customer attrition: Some customers will leave, especially those who are privacy-conscious or don't trust the company to prevent future breaches
- Regulatory scrutiny: Financial regulators may investigate how the breach happened and whether Betterment's security practices meet standards
- Legal liability: They'll likely face class action lawsuits from customers, though these often settle for minimal damage
- Reputational damage: Trust is hard to earn and easy to lose in finance. Some customers will question whether to stay
For customers, the path forward is simpler:
-
Don't panic: Your account is secure. Your money is safe. Take the rational steps outlined above.
-
Don't overreact: Don't close your account unless you've thoroughly thought about it. Short-term moves often cost money in the long run.
-
Stay vigilant: Be extra cautious about phishing, unusual account activity, and suspicious requests for the next year or two.
-
Don't ignore it: Don't just pretend this didn't happen and move on. Actually implement the protections we discussed.
-
Hold companies accountable: If Betterment's response seems insufficient, let them know. Support other customers asking for better security practices.
This breach is a reminder that security is an ongoing process, not a one-time fix. Even large, well-funded companies with significant security investments get compromised. The question is how they respond and what they learn.
Key Takeaways for Your Financial Security
Before we wrap up, let me summarize the absolute essential points:
About This Breach:
- 1.4 million records were exposed through social engineering, not technical hacking
- Your account credentials and financial information were NOT compromised
- Your investments and trading accounts are completely safe
- Your personal information (name, email, address, phone, birthdate) was exposed
Immediate Actions:
- Check Have I Been Pwned to confirm you were affected
- Enable two-factor authentication
- Change your password (just to be safe)
- Place a credit freeze
- Monitor for phishing attempts
Long-Term Protection:
- Use unique passwords with a password manager
- Enable 2FA on all financial accounts
- Monitor accounts actively for suspicious activity
- Be skeptical of unsolicited communications
- Keep personal information private
About Your Betterment Account:
- It's secure and safe to continue using
- Your investments weren't touched
- You can stay with confidence if you implement proper security measures
- You can switch to another platform if you prefer, but they face the same risks

FAQ
What exactly was exposed in the Betterment breach?
The breach exposed customer contact information including email addresses, names, and geographic location data for all 1.4 million affected users. A subset of users also had physical addresses, phone numbers, and birthdates exposed. Importantly, account credentials, passwords, and financial information were not compromised according to Crowd Strike's investigation.
How did attackers gain access to Betterment's systems?
Attackers used social engineering to trick a Betterment employee into providing access to a third-party platform that had legitimate access to Betterment's infrastructure. They didn't hack into Betterment's systems—they used identity impersonation and deception to manipulate an employee into giving them legitimate access. This highlights why employee security training is just as critical as technical security measures.
Is my Betterment account safe to use after this breach?
Yes, your Betterment account is completely safe to use. Your trading account, account credentials, and financial information were not compromised. Betterment's financial systems and security controls remained intact throughout the breach. If you implement proper security measures like two-factor authentication and monitor your account for unusual activity, you can confidently continue using Betterment.
What should I do if I received phishing emails from this breach?
Do not click any links or provide any information in suspicious emails claiming to be from Betterment. Report them as phishing (most email providers have a built-in report option). Contact Betterment directly through their official website or app if you're unsure whether a communication is legitimate. Never provide credentials or personal information via email, even if the email appears to come from a trusted company.
Can attackers access my Betterment account with just my name and email address?
No, not without significant additional effort. Betterment uses strong authentication including passwords and two-factor authentication. However, if you reused the same password across multiple platforms, attackers could attempt to access other accounts. This is why having unique passwords for every account is essential. Enable two-factor authentication to add an extra layer of protection even if your password is compromised.
Will Betterment provide compensation or free credit monitoring?
Betterment is offering credit monitoring to affected users, though details about duration and extent may vary. You should check your notification from Betterment for specifics. Beyond that, compensation may come through class action settlements, but these often result in minimal payouts. You can also place a free credit freeze with the three major bureaus and monitor your credit reports yourself at no cost.
How long should I be concerned about identity theft from this breach?
You should remain vigilant indefinitely, but especially during the first 2-3 years after the breach when your personal information is most actively being used on the dark web. Identity thieves often hold onto data and use it strategically. However, a single exposure doesn't mean identity theft will definitely occur. By implementing proper protections (credit freeze, monitoring, strong passwords), you significantly reduce your risk.
Could this breach happen to other financial companies?
Absolutely. Social engineering attacks are among the most common breach vectors and affect companies of all sizes. Vanguard, Schwab, Fidelity, and other major financial institutions have all dealt with breaches. The financial services industry is heavily targeted because it provides direct access to money. What matters is how quickly companies detect breaches and how thoroughly they respond—areas where Betterment performed relatively well.
Should I switch away from Betterment after this breach?
That's a personal decision based on your risk tolerance and trust in the company. The breach didn't compromise your financial information or investments, and Betterment's response was relatively transparent. However, if this event shakes your confidence in Betterment's security practices, switching to another platform is reasonable. Keep in mind that all financial platforms face similar security challenges and breach risks. Ensure your new platform also has strong security (two-factor authentication, encryption, account monitoring) before moving your money.
How can I check if my email was in this specific breach?
Visit Have I Been Pwned (haveibeenpwned.com) and enter your email address in the search box. The site will indicate whether your email appeared in the Betterment breach or any other publicly disclosed breaches. This is a free, legitimate service maintained by security researcher Troy Hunt and is widely trusted in the security community.
What are the long-term implications of this breach for Betterment?
Short-term, Betterment will likely experience some customer attrition, increased regulatory scrutiny, and potential legal costs from class action lawsuits. Long-term, the impact depends on their response and whether they implement meaningful security improvements. Companies that handle breaches transparently and improve their practices often recover trust over time. Betterment's prompt detection and thorough investigation (with Crowd Strike) positions them better than companies that hide or downplay breaches.

Wrapping Up: Your Action Plan
The Betterment breach is a significant data exposure, but it's not the catastrophic account compromise that headlines might suggest. Your money is safe. Your account is secure. Your personal information, however, is now in the hands of bad actors, and you need to be proactive about protecting yourself from identity theft and fraud.
Here's what I'd do right now if you're a Betterment customer:
- Check Have I Been Pwned to confirm you were affected
- Enable two-factor authentication on Betterment (if not already done)
- Place a credit freeze with the three major bureaus
- Review your recent Betterment account activity for anything suspicious
- Change your Betterment password if it's not unique
- Set up alerts on your credit card and bank accounts for unusual activity
- Be extra cautious about phishing emails for the next few months
Beyond Betterment specifically, this breach is a reminder that even large, well-resourced companies get compromised. The best defense isn't perfect security (which doesn't exist). It's layered protection: strong passwords, two-factor authentication, credit monitoring, skepticism about unsolicited requests, and a habit of checking your accounts regularly for unusual activity.
Betterment's response to this breach has been appropriate and relatively transparent. Whether you stay with the company or switch is your call. Just make sure wherever you invest, you're implementing proper security practices on your end.
Stay vigilant, stay skeptical, and stay secure.
Related Articles
- Substack Data Breach: What Happened & How to Protect Yourself [2025]
- Substack Data Breach [2025]: What Happened & How to Protect Yourself
- 8.7 Billion Records Exposed: Inside the Massive Chinese Data Breach [2025]
- Coinbase Insider Breach Exposed 30 Customers' Data [2025]
- Sapienza University Ransomware Attack: Europe's Largest Cyberincident [2025]
- Conduent Data Breach 2025: What Millions of Americans Need to Know [2026]
![Betterment Data Breach: 1.4M Accounts Exposed [2025]](https://tryrunable.com/blog/betterment-data-breach-1-4m-accounts-exposed-2025/image-1-1770395784747.jpg)



