Gogs CVE-2025-8110 RCE Vulnerability: What Federal Agencies Must Know
Last month, the cybersecurity world got a harsh reminder about the risks lurking in self-hosted git platforms. The US Cybersecurity and Infrastructure Security Agency (CISA) added a critical vulnerability to its Known Exploited Vulnerabilities catalog, and now federal agencies are under a hard deadline to fix it.
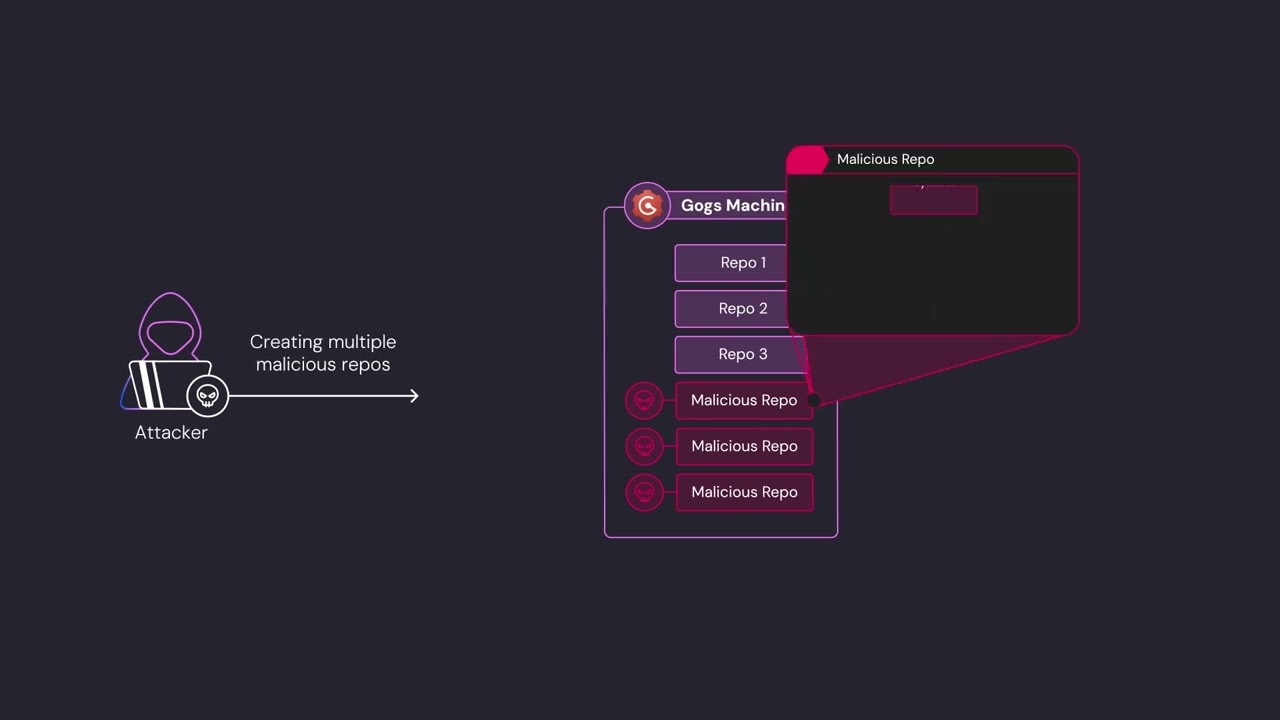
Here's the thing: this isn't some theoretical bug discovered in a lab. It's actively being weaponized. Over 700 Gogs servers are already compromised, and attackers are having a field day with it.
Let's break down what happened, why it matters, and what organizations need to do right now.
TL; DR
- Critical vulnerability: CVE-2025-8110 is a symlink bypass in Gogs that allows unauthenticated attackers to achieve remote code execution
- Federal deadline: CISA ordered Federal Civilian Executive Branch agencies to patch by February 2, 2026
- Active exploitation: Over 700 Gogs instances already compromised, two separate attack waves documented as of November 2025
- Severity score: 8.7/10 (high severity) with CVSS metrics indicating practical, widespread exploitation
- Attack vector: Unauthenticated access to the Put Contents API enables arbitrary file writes and RCE
- Exposure: More than 1,400 Gogs servers exposed online; organizations using self-hosted git services are at elevated risk

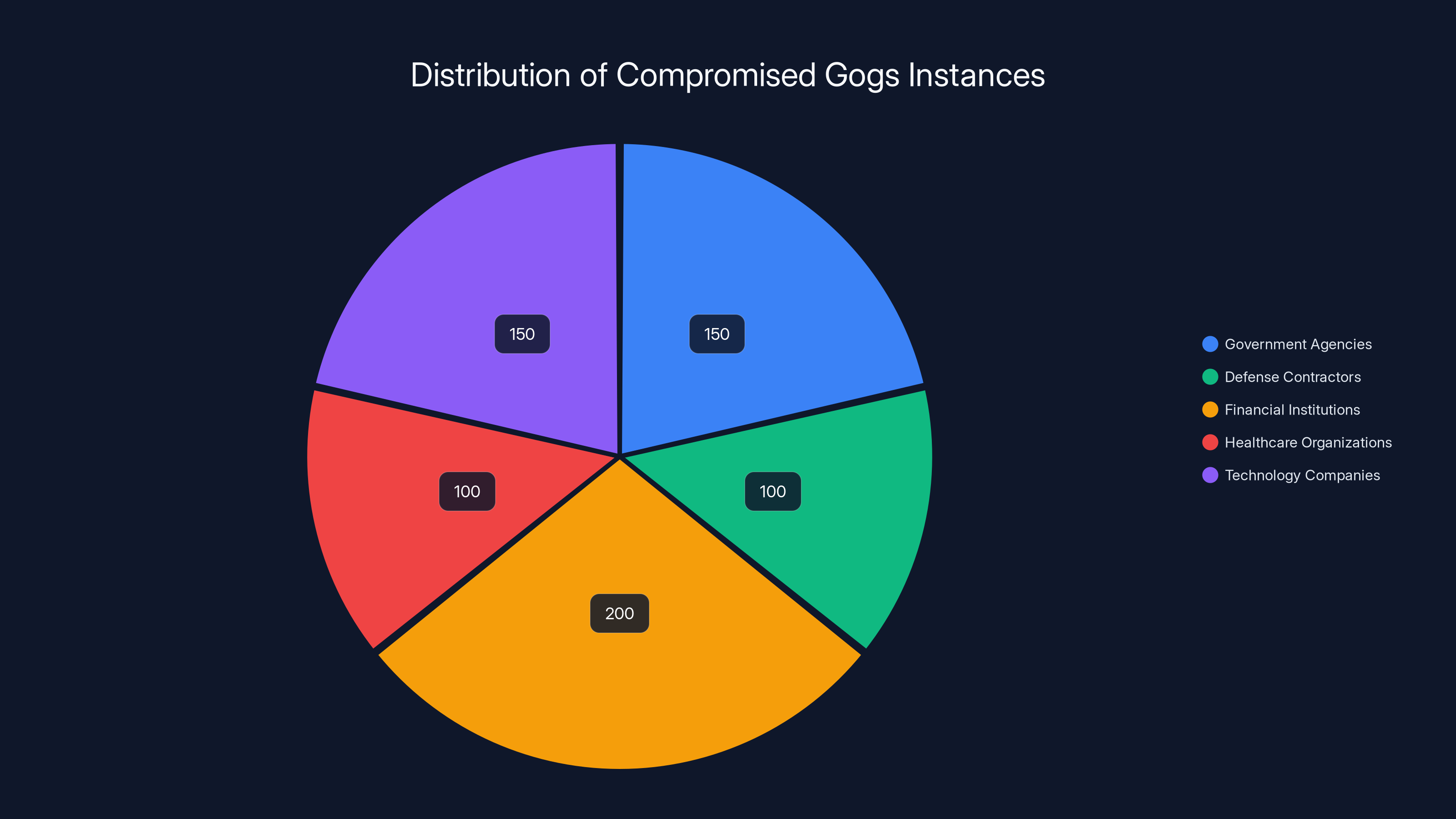
Estimated data shows financial institutions and technology companies are most affected by CVE-2025-8110, with 200 and 150 compromised instances respectively.
Understanding Gogs: The Self-Hosted Git Alternative Nobody Expects to Break
Before diving into the vulnerability itself, it's worth understanding why Gogs exists and why organizations choose it over GitHub or GitLab.
Gogs is a lightweight, self-hosted Git service written in Go. Think of it as running your own GitHub instance on your own infrastructure. It provides a web interface for hosting Git repositories, managing users and teams, handling pull requests, code reviews, issues tracking, and basic project documentation, all under your control.
The appeal is obvious. You get complete sovereignty over your source code. No third-party cloud provider. No questions about data residency. No reliance on someone else's uptime. For regulated industries, air-gapped networks, or organizations with extreme security requirements, Gogs becomes essential infrastructure.
It's also lightweight. Gogs doesn't require massive server resources. Many organizations run it on modest hardware, sometimes on internal networks, sometimes exposed to specific trusted networks. The Go language makes it fast and efficient. It's designed for teams that want simplicity without sacrificing functionality.
The problem? Security gets overlooked when you're running software in-house. You become responsible for patches, updates, security monitoring, and incident response. Miss an update, and you're now holding a loaded gun pointed at your own infrastructure.
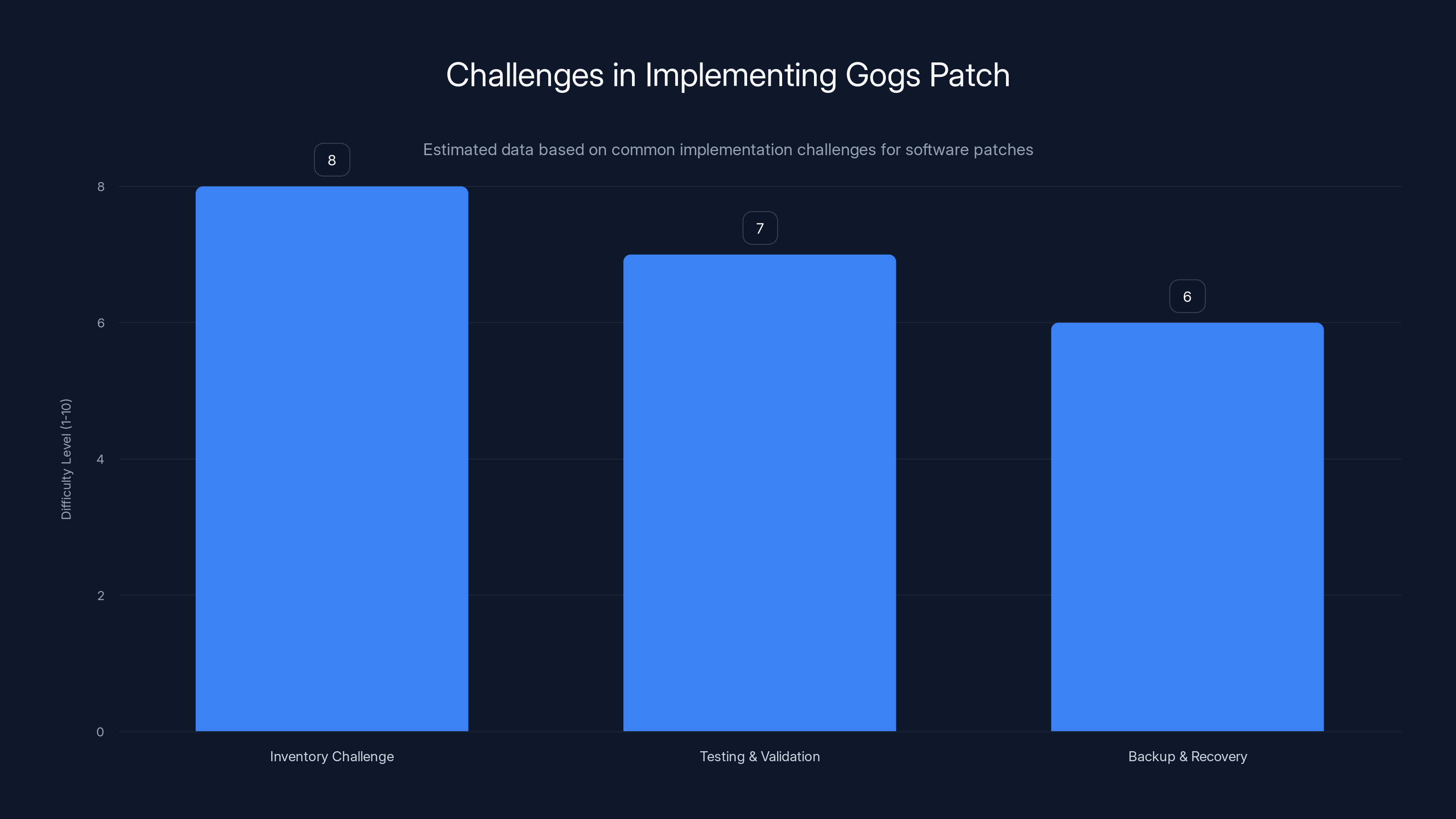
Inventory management poses the greatest challenge in implementing the Gogs patch, followed by testing and validation. Estimated data.
The Vulnerability Explained: Symlink Bypass and Remote Code Execution
CVE-2025-8110 is a symlink bypass vulnerability discovered by researchers at Wiz Research. Let's break down what this means in practical terms.
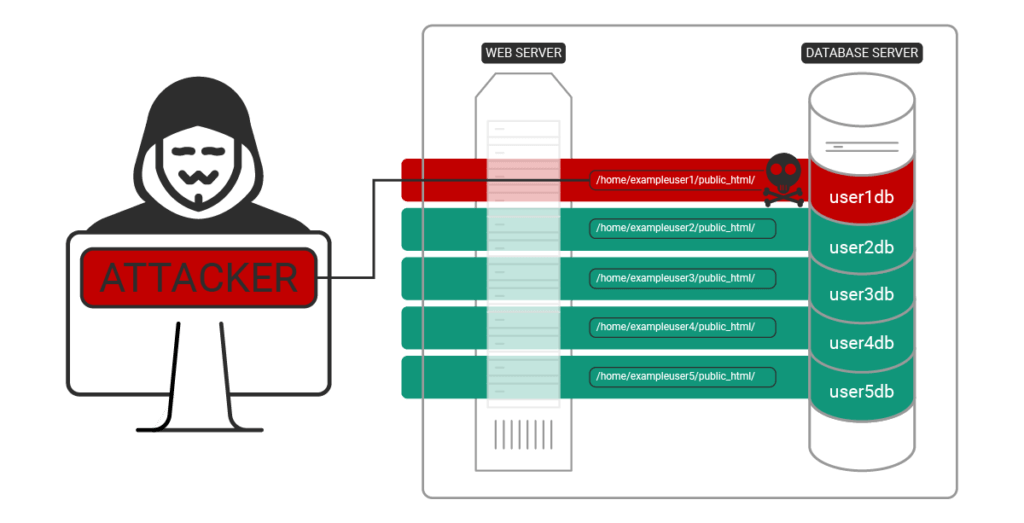
A symlink (symbolic link) is a file system feature that acts like a shortcut or pointer to another file or directory. Instead of storing data directly, a symlink references another location on the file system. This is useful for many legitimate purposes, but it creates security risks if not handled carefully.
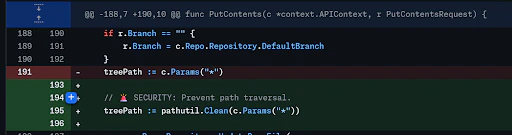
The vulnerability exists in Gogs' Put Contents API endpoint. This endpoint is meant to allow authenticated users to write file contents. The problem? The validation logic doesn't properly check for symlinks when validating file paths. Here's how the attack works:
An unauthenticated attacker sends a request to the Put Contents API targeting what appears to be a normal file path. Behind the scenes, that path contains a symlink pointing to a critical system file or location. Because the validation doesn't resolve and check symlinks, the API writes the attacker's malicious content to the symlink target instead of the intended location. This allows arbitrary file writes to any location on the server.
Once an attacker can write arbitrary files, achieving remote code execution becomes straightforward. Write a malicious script to a web-accessible directory, trigger its execution, and you own the server. Write a cron job, modify system files, or deploy a backdoor. The possibilities are endless.
The vulnerability impacts the authentication layer too. You don't need valid credentials to exploit this. An attacker can target any exposed Gogs instance from the internet and start compromising it immediately.
CISA's KEV Catalog: Why This Matters for Federal Agencies
When CISA adds a vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, it sends a clear signal. This bug isn't theoretical. It's being actively exploited by real threat actors right now.
For federal agencies, inclusion in KEV comes with mandatory requirements. The Cybersecurity Executive Order and federal security directives require FCEB (Federal Civilian Executive Branch) agencies to patch known exploited vulnerabilities within specific timeframes. For CVE-2025-8110, the deadline is February 2, 2026, giving organizations roughly three weeks from the January 12, 2026 addition date.
But here's where it gets serious. If an agency hasn't patched by the deadline, CISA's guidance is to stop using the software entirely. No exceptions. No grace periods. That means air-gapping systems, decommissioning services, or migrating to alternatives.
For many federal agencies, this creates an immediate crisis. Gogs instances that have been running silently for years suddenly become critical infrastructure requiring urgent attention. Teams need to inventory every Gogs deployment, assess which ones are exposed, test patches in lab environments, and deploy updates across their infrastructure.
The KEV listing also signals something else: attackers worldwide are now aware this vulnerability is particularly valuable. Why? Because federal systems are high-value targets. If CISA cared enough to mandate patching, foreign intelligence agencies and criminal groups took notice.

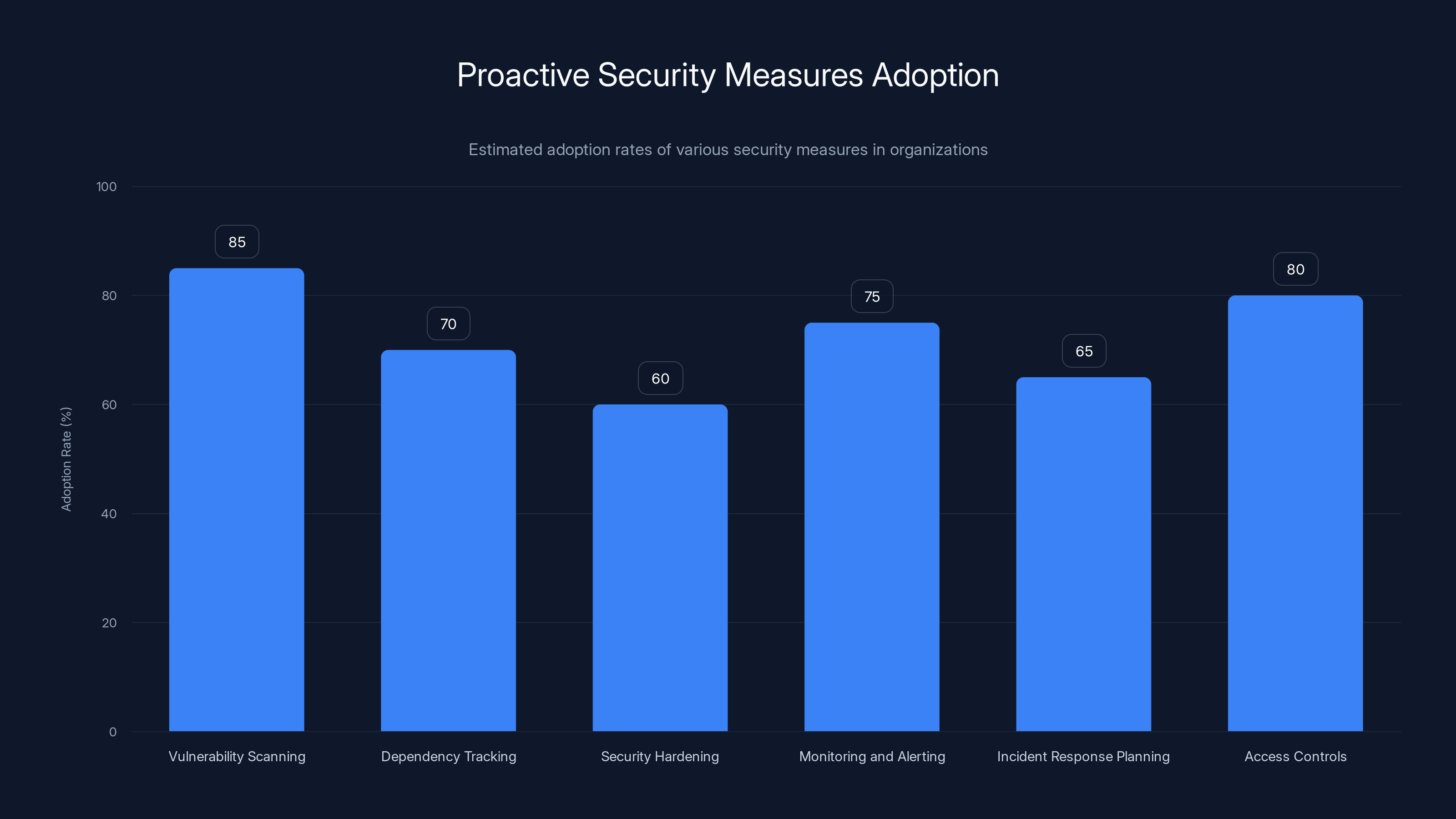
Vulnerability scanning and access controls are the most widely adopted proactive security measures, with over 80% adoption. Security hardening shows the lowest adoption at 60%. (Estimated data)
Attack Timeline: From Zero-Day to Mass Compromise
According to threat research, the timeline of this vulnerability's exploitation is concerning.
By November 1, 2025, Wiz Research and other security firms documented two separate waves of attacks exploiting CVE-2025-8110 as a zero-day vulnerability. This means attackers discovered and weaponized the vulnerability before Gogs maintainers released a patch. Organizations were exposed for an extended period with no fix available.
First wave attacks typically focus on reconnaissance. Attackers probe networks, identify Gogs instances, and confirm the vulnerability exists. They might leave minimal traces, gather information about the network, and establish beachheads for future access.
Second wave attacks tend to be more aggressive. Once attackers understand the vulnerability's impact across multiple targets, they launch broader campaigns. This is where you see mass compromise, malware deployment, and data exfiltration.
By the time Wiz Research published their findings and CISA added CVE-2025-8110 to KEV in mid-January 2026, over 700 Gogs instances were already compromised. These aren't hypothetical numbers. These are real servers with real data that real attackers now control.
The compromise statistics raise hard questions. How many of those 700 instances belong to government agencies? How many run financial systems, healthcare applications, or critical infrastructure? How much sensitive data has been exfiltrated?
For organizations that patched quickly, the situation is manageable. For those still running vulnerable versions, the risk is severe. Your Gogs instance is likely already known to attackers. Your source code, API keys stored in repositories, deployment credentials, and everything else in your git history is potentially compromised.
The Technical Details: Symlink Validation Failures
The root cause of CVE-2025-8110 comes down to insufficient path validation in Gogs' file write operations.
Proper symlink handling requires resolving the full canonical path of any file before performing operations on it. You must follow symlinks to their target and validate that the target path is within an allowed directory. If the target is outside allowed boundaries, reject the operation.
Gogs failed to implement this validation consistently. The Put Contents API endpoint and related file write code paths didn't properly resolve symlinks before validating paths. This created a bypass where attackers could:
- Identify or create a symlink pointing to a target location outside the Gogs repository
- Send a Put Contents request targeting that symlink
- The validation checks pass because they only examine the symlink itself, not its target
- The file write operation follows the symlink and writes to the actual target location
- Arbitrary files get modified, leading to RCE
The fix, released by Gogs maintainers on GitHub, addresses this by adding symlink-aware path validation at all file write entry points. Now the code resolves symlinks and validates the canonical path against allowed directories. Symlinks pointing outside allowed locations are rejected.
This is a fundamental security control that should have been in place from day one. The fact that it wasn't reflects broader issues with self-hosted software security. When teams maintain their own infrastructure, they often focus on features and performance rather than security controls that seem unnecessary until they're exploited.
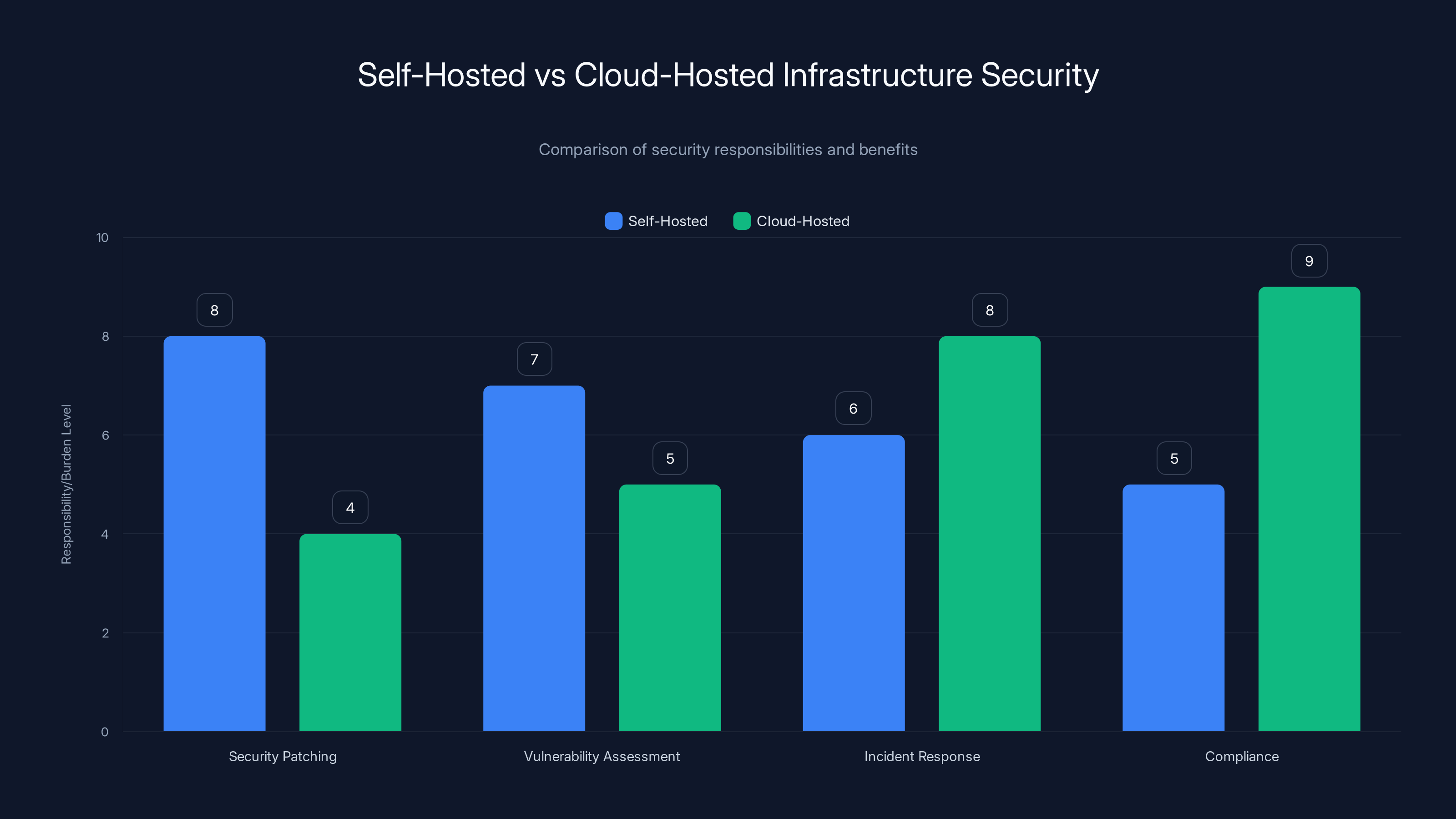
Self-hosted solutions often require more responsibility in security patching and vulnerability assessment, while cloud-hosted solutions provide better incident response and compliance support. Estimated data.
Exposure Scale: 1,400+ Gogs Servers on the Internet
Here's a sobering statistic: more than 1,400 Gogs servers are exposed online, accessible from the internet without requiring authentication or network access restrictions.
This number alone explains the severity of CVE-2025-8110. Each exposed instance represents a potential attack surface. Each server running a vulnerable version is a compromise waiting to happen.
The distribution of these servers matters. Shodan, Censys, and similar internet scanning services have indexed thousands of Gogs instances. Some belong to major corporations. Some belong to government agencies. Some belong to small startups. Some are honeypots set up by security researchers.
Why are so many Gogs instances exposed? Several reasons:
Misconfiguration: Teams set up Gogs on public IPs intending to restrict access with authentication, then forget to enable authentication on critical endpoints or assume reverse proxy security is sufficient.
Network segmentation failures: Gogs instances intended for internal networks accidentally become internet-routable due to misconfigured firewalls or cloud network policies.
Legacy deployments: Old Gogs instances running for years, forgotten until someone discovers them and realizes nobody knows what they do or who owns them.
Intentional exposure: Some teams deliberately expose Gogs to specific networks or partners, accepting risk in exchange for accessibility.
Cloud misconfigurations: Gogs containers or VMs deployed in cloud environments with overly permissive security groups.
Regardless of why they're exposed, each one is now a target. Attackers running vulnerability scans across internet-connected systems will find these servers. Exploitation takes seconds. Compromise takes minutes.
Attack Scenarios: What Happens When Gogs Gets Compromised
Let's walk through realistic attack scenarios to understand the true impact of this vulnerability.
Scenario 1: Source Code Theft An attacker exploits CVE-2025-8110 on an exposed Gogs instance. They gain RCE on the server. First, they clone every repository. They extract the entire git history, all branches, all commits, all comments, all configuration. They now possess your complete source code archive. Months or years of development work, intellectual property, proprietary algorithms, and architectural knowledge are in their hands.
They can analyze your code for additional vulnerabilities, understand your technology stack, identify supply chain dependencies, and use this knowledge for targeted attacks against downstream customers or partners.
Scenario 2: Credential Harvesting Inside repositories, developers often commit credentials accidentally. API keys, database passwords, SSH private keys, AWS access tokens. Even though developers shouldn't do this, they absolutely do. An attacker with access to your git history finds these credentials. Now they can:
Access production databases and modify data. Assume identity of service accounts. Access cloud infrastructure and deploy backdoors. Infiltrate connected systems. Pivot deeper into the network.
Scenario 3: Supply Chain Attack If your Gogs instance hosts libraries, SDKs, or packages that other organizations depend on, an attacker can modify source code to inject backdoors. When downstream users build and deploy your compromised code, they unknowingly distribute the malware to their own customers and infrastructure.
This is particularly dangerous for component libraries, infrastructure automation code, or any code that gets packaged and distributed.
Scenario 4: Persistent Backdoor Installation After gaining RCE, an attacker doesn't immediately cover their tracks. They install persistent backdoors. They add cron jobs that maintain access. They modify system files to establish long-term presence. They set up data exfiltration pipelines that slowly siphon information over time.
Months later, when your organization finally patches CVE-2025-8110, you think you're secure. But the attacker maintained persistence through other means. Your incident response efforts focus on the wrong indicators of compromise.
Scenario 5: Development Environment Compromise Unlike production systems that get monitored heavily, development infrastructure often flies under the radar. A Gogs instance is development infrastructure. An attacker using RCE can inject malicious code into build systems, deployment pipelines, and development tooling. Developers unknowingly build and test backdoored software. Over time, that compromised code makes its way to production through normal release processes.
By the time security teams detect the compromise, months of development work is tainted.

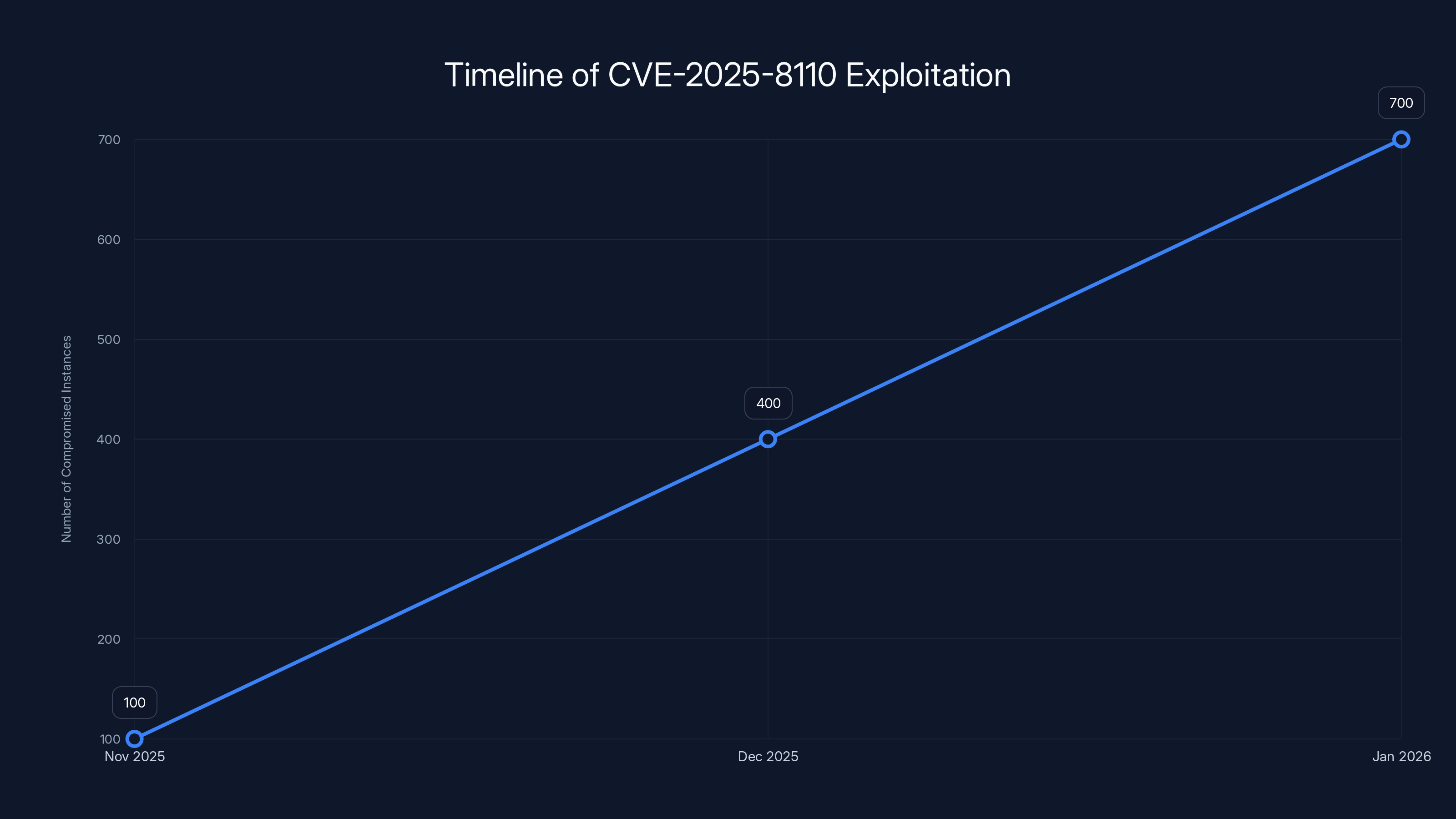
The number of compromised Gogs instances increased from 100 in November 2025 to over 700 by mid-January 2026, highlighting the rapid spread of the CVE-2025-8110 exploitation.
The Broader Context: Self-Hosted Git Services and Security
Gogs isn't alone in facing security challenges. The entire self-hosted git service landscape carries inherent risks that organizations often underestimate.
Git itself is powerful but not designed with security as the primary concern. It's designed for distributed version control and collaboration. Security features exist, but they're optional. Many teams running self-hosted git services use them in ways that prioritize ease of use over security.
Gitea, another self-hosted git option, has faced similar vulnerabilities. GitLab's self-hosted offering carries the weight of GitLab's complexity, making security misconfiguration likely. Even GitHub Enterprise, while more mature, requires careful configuration to avoid exposing sensitive data.
The pattern is consistent: when organizations run their own git infrastructure, security falls to teams that are primarily developers or DevOps engineers. They're not security specialists. They focus on reliability and feature availability. Security controls get implemented when requirements force them, not proactively.
This explains why vulnerabilities like CVE-2025-8110 achieve such high compromise rates. The organizations running Gogs are often exactly the ones without mature security operations, incident response capabilities, or vulnerability management processes.
Further, git services tend to live on the boundary between development and production systems. Developers interact with them daily. CI/CD systems depend on them. Change management processes interact with them. This high traffic and multiple integration points make them attractive targets. Compromise a git service and you influence everything downstream.

Remediation: The Technical Fix and Implementation Challenges
Gogs maintainers released a patch for CVE-2025-8110. The fix is available on their GitHub repository and involves adding symlink-aware path validation at all file write entry points.
Technically, the fix is straightforward. For organizations, implementation is where challenges emerge.
Inventory Challenge Many organizations don't maintain accurate inventories of self-hosted git services. Gogs instances run on development servers, integration machines, and isolated networks. Teams might not know exactly which versions are deployed. Some instances might have been forgotten entirely.
Creating a complete inventory is step one. Use network scanning tools to identify Gogs instances. Interview development teams about systems they use. Check infrastructure-as-code repositories for deployment configurations. Document every instance, its purpose, what data it holds, and its criticality.
Testing and Validation Before deploying patches to production, organizations need testing environments. If your Gogs instance holds critical data or serves integration functions, you can't just patch and hope. You need to:
Set up a staging instance mirroring production. Deploy the patch to staging. Run smoke tests of normal operations. Verify authentication still works. Confirm repositories are accessible. Test pull requests, issues, and collaboration features. Verify integrations with other systems still function.
For organizations with multiple Gogs instances across teams, this becomes time-consuming.
Backup and Recovery Before making changes to systems holding source code, backups matter. Can you recover if the patch introduces unexpected issues? Do you have clean repository backups? Can you roll back if necessary?
Git repositories themselves are somewhat self-healing (git is distributed, every clone is a backup), but backing up the entire Gogs system state including configuration, user accounts, and repository metadata is important.
Deployment and Verification Once testing is complete, deployment must happen carefully. Plan maintenance windows. Notify users. Deploy to less critical instances first. Monitor for issues. Verify the patch was applied correctly.
Confirm that the vulnerable endpoint now rejects symlink-based requests. Verify that legitimate operations still function. Check logs for any unusual activity.
Post-Patch Analysis After patching, organizations should investigate whether they were compromised during the vulnerability window. Check access logs for unusual requests to the Put Contents API. Look for unexplained file modifications. Review git commits for suspicious activity. If you find evidence of compromise, escalate to incident response and assume credentials are stolen.

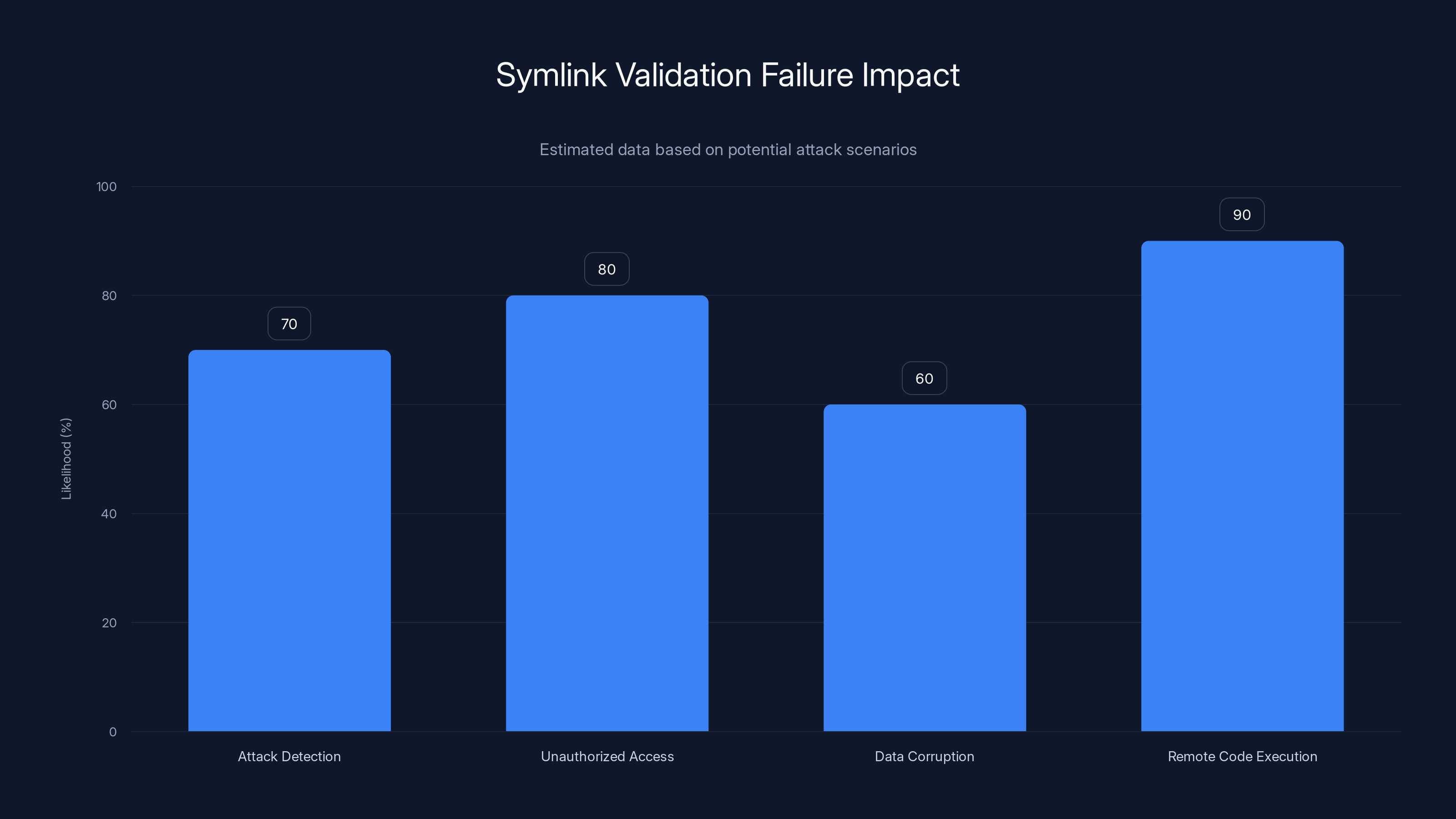
Estimated data shows that remote code execution (RCE) is the most likely impact of symlink validation failures, with an estimated likelihood of 90%.
Federal Compliance and the February 2 Deadline
For organizations operating under federal contracts or subject to federal compliance requirements, the February 2, 2026 patch deadline isn't optional.
The Cybersecurity Executive Order and federal security directives require FCEB agencies to identify and patch known exploited vulnerabilities within 6 business days of CISA notification for the most critical vulnerabilities, and within longer timeframes for lower severity issues.
For CVE-2025-8110, CISA granted approximately 21 days (January 12 to February 2). This seems generous until you consider the work involved in identifying vulnerable instances, testing patches, and coordinating deployment across multiple departments.
Missing the deadline carries consequences. Federal agencies face compliance violations, potential suspension of IT contracts, and security reviews. Contractors risk losing clearances or certifications required for federal work.
Beyond federal requirements, many private organizations maintain compliance frameworks that mandate patch management. SOC 2, ISO 27001, and other standards require organizations to identify and remediate known vulnerabilities in timely manner.
The deadline creates urgency. It forces prioritization. Gogs instances that were deprioritized suddenly become critical. Patch management processes that were informal suddenly require documentation. Infrastructure that was largely ignored suddenly demands attention.
Detection: Identifying Compromise and Exploitation Attempts
Organizations need to know whether their Gogs instances were exploited during the vulnerability window.
Log Analysis Gogs maintains access logs, API logs, and system logs. Look for:
- Requests to the Put Contents API endpoint
- Requests containing path traversal patterns or unusual characters
- Requests with symlink references
- Failed authentication followed by successful API calls
- API requests from unexpected geographic locations
- Unusual request patterns or volumes
These indicators suggest exploitation attempts.
Repository Integrity Review recent commits and file changes:
- Commits made by unknown authors
- Commits with timestamps during off-hours or unusual times
- Changes to sensitive files (build scripts, deployment configs, access control files)
- Addition of new SSH keys or user accounts
- Modifications to git hooks
File System Changes Check for unauthorized modifications:
- New files in web-accessible directories
- Modified executable files
- Changes to cron jobs or system initialization scripts
- New user accounts
- Modified sudoers or SSH configuration
Network Behavior Look for signs of data exfiltration:
- Unusual outbound connections from the Gogs server
- Large data transfers to unknown destinations
- DNS queries to suspicious domains
- Port scanning or network reconnaissance from the Gogs server
Application Behavior Monitor Gogs runtime behavior:
- Unexpected errors or crashes
- Memory or CPU usage spikes
- New processes spawned from Gogs
- Changes to application configuration

Broader Implications: Rethinking Self-Hosted Infrastructure Security
CVE-2025-8110 reveals deeper issues with how organizations approach self-hosted software security.
The Illusion of Control Organizations choose self-hosted solutions for control. They want to own their data. They want complete visibility and governance. They want to avoid vendor lock-in. These are legitimate desires.
But ownership comes with responsibility. You're not just running software. You're now responsible for security patching, vulnerability assessment, security hardening, monitoring, incident response, and compliance.
Many organizations underestimate this responsibility. They assume that because they control the infrastructure, they're more secure. This often leads to the opposite. Overconfidence in internal security combined with insufficient security operations creates vulnerability.
The Maintenance Burden Self-hosted Gogs requires ongoing maintenance. New versions are released regularly. Security patches need deployment. Compatibility with other systems must be verified. Configuration needs periodic review.
For organizations without dedicated infrastructure teams, this burden becomes unsustainable. Systems fall behind on updates. Security patches don't get deployed in timely manner. Monitoring doesn't happen because nobody is assigned the responsibility.
This isn't a failure of individual teams. It's a structural problem. The security value of owning infrastructure comes with costs that many organizations can't bear.
The Cost-Benefit Question After a vulnerability like CVE-2025-8110 hits, organizations should reassess whether self-hosted git infrastructure is worth the security costs and operational overhead.
Cloud-hosted alternatives like GitHub, GitLab, or Bitbucket handle patching automatically. They employ dedicated security teams. They benefit from centralized security updates deployed across millions of instances. They maintain professional incident response capabilities.
For most organizations, the marginal control gained by self-hosting doesn't justify the security risks and operational costs. There are exceptions: organizations with extreme data sensitivity, regulated industries with specific requirements, companies in countries with internet restrictions.
But the general trend should be toward consolidating git infrastructure on managed platforms rather than proliferating self-hosted instances.
The Maturity Question Organizations should assess their security maturity before running self-hosted services. Do you have:
- Dedicated infrastructure team?
- Formal patch management process?
- Vulnerability scanning and assessment capabilities?
- Security monitoring and incident response?
- Compliance framework and audit trails?
- Backup and disaster recovery procedures?
If any answer is "no," self-hosting critical infrastructure like git services is risky.

Lessons for Developers: Secure Coding Practices
From a software engineering perspective, CVE-2025-8110 illustrates important lessons about secure file handling.
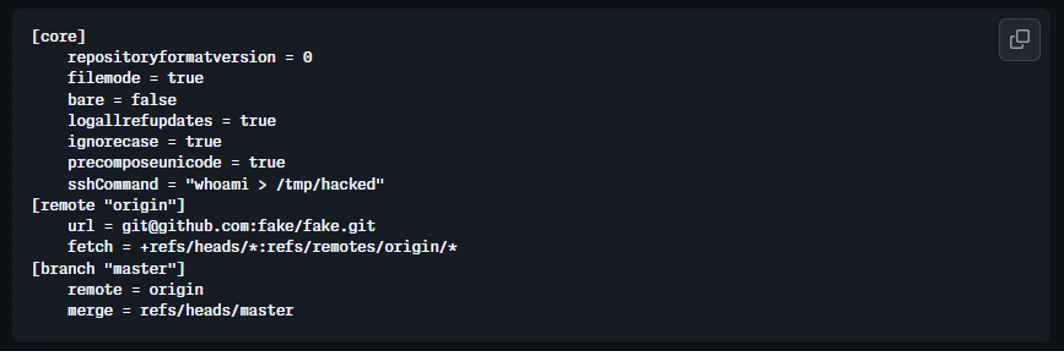
Validate Paths Canonically Never validate file paths based on the path string. Always resolve the full canonical path (following symlinks) and validate the resolved path. Attackers can use symlinks to bypass string-based validation.
Use Allowlists, Not Denylists Instead of checking paths against a list of forbidden locations, check against a list of allowed locations. This is more secure because you only allow what's explicitly permitted.
Separate Concerns Path validation should happen before any file operations. Separate the validation logic from the file operation logic. Don't interleave them.
Test With Malicious Input Unit tests should include malicious inputs: symlinks, path traversal attempts, unusual characters. Don't just test happy paths.
Use Security Libraries
When possible, use libraries designed for secure file operations rather than implementing path handling from scratch. Libraries like os.path.realpath in Python resolve symlinks. Use them.
Document Assumptions If file operations assume files exist in specific locations, document this assumption clearly. Future maintainers won't introduce vulnerabilities if they understand the security model.
Response Strategies: What Organizations Should Do Now
Organizations should implement a multi-phase response to CVE-2025-8110.
Phase 1: Immediate (Days 1-3) Identify all Gogs instances. Scan your network for Gogs services. Ask teams about systems they operate. Check DNS records and SSL certificates for Gogs servers.
Determine which instances are exposed to the internet. Use network scanning tools. Check firewall rules and security group configurations.
If exposed instances exist, consider whether they should remain accessible from the internet. If not, restrict access immediately using firewall rules or VPN requirements.
Phase 2: Assessment (Days 3-7) For each instance, determine the current version and whether it's vulnerable. Check the installed Gogs version against patch availability.
Assess the criticality of each instance. What data does it hold? How many users depend on it? How would disruption impact operations?
Review access logs for signs of exploitation. Look for unusual API requests, failed authentication followed by successful access, or requests from unexpected locations.
Phase 3: Testing (Days 7-14) Set up testing environments mirroring production. Deploy patches to testing environments. Verify normal operations still work. Test integrations with other systems.
Document the patch process. Create runbooks for deployment. Identify who needs to be notified and when.
Phase 4: Deployment (Days 14-30) Deploy patches to all vulnerable instances according to criticality. Critical instances first, then less critical systems. Maintain backup and rollback procedures.
Monitor systems carefully after patching. Watch for unexpected behavior or errors.
Phase 5: Verification (Days 30+) Confirm all instances have been patched. Verify vulnerable endpoints now reject symlink-based attacks. Review access logs post-patch for any suspicious activity.
If compromise evidence exists, initiate incident response. Assume credentials are compromised. Rotate secrets. Audit what attackers accessed.

Preventing Future Vulnerabilities: Proactive Security Measures
Beyond addressing CVE-2025-8110, organizations should implement proactive measures to reduce risk of similar vulnerabilities.
Vulnerability Scanning Implement regular vulnerability scanning of all self-hosted infrastructure. Tools like Nessus, OpenVAS, or Qualys can identify known vulnerabilities. Integrate scanning into your CI/CD pipeline. Scan new systems before production deployment.
Dependency Tracking Maintain accurate inventory of software versions running in your environment. Use software composition analysis tools to identify vulnerable dependencies. Subscribe to security advisories for software you depend on.
Security Hardening Beyond patching, harden Gogs instances by:
- Disabling unnecessary features
- Restricting API access to trusted networks
- Implementing rate limiting on API endpoints
- Adding authentication requirements to sensitive endpoints
- Using reverse proxy to hide internal details
- Implementing request signing or API tokens
Monitoring and Alerting Implement monitoring of Gogs instances:
- Alert on unusual API access patterns
- Monitor CPU, memory, and disk usage for anomalies
- Alert on failed authentication attempts
- Monitor outbound network connections
- Alert on file modifications in critical directories
Incident Response Planning Develop an incident response plan specific to git service compromise:
- Identify who needs to be contacted
- Document escalation procedures
- Plan how to preserve evidence
- Plan how to identify what data was accessed
- Plan credential rotation procedures
- Plan communication with users and stakeholders
Access Controls Limit who can access Gogs:
- Use strong authentication (MFA when possible)
- Limit API token scope
- Implement role-based access control
- Regularly audit user accounts
- Remove access for departed employees
- Require VPN or specific network access

Looking Forward: The Evolving Threat Landscape
CVE-2025-8110 is one of an increasing number of critical infrastructure vulnerabilities. As development tools become more integrated into core business operations, they become increasingly attractive targets.
The future will likely see:
More Git Service Vulnerabilities As organizations continue self-hosting git services, vulnerabilities will be discovered. Each year brings new CVEs affecting Gogs, Gitea, and other platforms.
Increased Supply Chain Attacks Git services will continue being entry points for supply chain attacks. Attackers will focus on compromising development infrastructure to inject backdoors into software.
Regulatory Pressure Governments will impose stricter requirements on how organizations manage development infrastructure. Compliance requirements will force investment in security.
Cloud Migration Acceleration Organizations will increasingly move git services to cloud platforms. The operational and security benefits will outweigh the perceived benefits of self-hosting.
AI-Enhanced Vulnerability Discovery Vulnerability research will become increasingly automated. Machine learning models will discover vulnerabilities faster. Time between discovery and exploitation will continue collapsing.
Shift in Threat Models The distinction between development and production systems will blur. Attacks will increasingly target development infrastructure as an entry point to production systems.

FAQ
What is CVE-2025-8110?
CVE-2025-8110 is a critical vulnerability in Gogs (a self-hosted git service) that allows unauthenticated remote code execution through a symlink bypass in the Put Contents API endpoint. The vulnerability affects Gogs versions prior to the patched release and has been actively exploited in the wild, with over 700 confirmed compromised instances as of January 2026.
How does the symlink bypass vulnerability work?
The vulnerability occurs because Gogs' file write operations don't properly validate paths after resolving symlinks. An attacker can craft a malicious request to the Put Contents API targeting a symlink that points to sensitive files or system locations. The validation checks fail to follow the symlink, allowing the attacker to write arbitrary files to any location on the server, leading to remote code execution. The fix involves implementing canonical path validation that resolves symlinks before checking if paths are within allowed directories.
Why did CISA add this vulnerability to the KEV catalog?
CISA adds vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog when there is confirmed evidence of active exploitation in the wild. CVE-2025-8110 was added to KEV on January 12, 2026, because researchers documented two separate waves of attacks exploiting the vulnerability before any patch was available. This designation mandates that federal agencies must patch by February 2, 2026, or stop using Gogs entirely.
What organizations are most at risk from this vulnerability?
Organizations running self-hosted Gogs instances without proper network restrictions and current patches are at immediate risk. This includes government agencies, defense contractors, financial institutions, healthcare organizations, and technology companies that have deployed Gogs on internet-accessible infrastructure. Organizations with development teams unaware of their Gogs instances are particularly vulnerable because they cannot respond to patch requirements.
How can I determine if my Gogs instance was compromised?
Review your Gogs access logs, git commit history, and system logs for suspicious activity. Look for API requests to the Put Contents endpoint with unusual patterns, commits made by unknown authors with unexpected timestamps, changes to sensitive files or system configuration, new user accounts, or unexpected outbound network connections from the Gogs server. If you find any evidence of compromise, assume all credentials and secrets stored in repositories are compromised and should be rotated immediately.
What is the proper way to patch Gogs for CVE-2025-8110?
Obtain the patched Gogs version from the official GitHub repository. Back up your current Gogs instance including all repositories and configuration. Test the patch in a staging environment mirroring your production setup, verifying that normal operations continue to function. Deploy the patch during a maintenance window with monitoring in place to catch any issues. After deployment, verify that the vulnerable Put Contents API endpoint now properly validates paths and rejects symlink-based requests. Review logs for any suspicious activity during and after patching.
Are there alternatives to self-hosting Gogs for source code management?
Yes, cloud-hosted alternatives like GitHub, GitLab, Bitbucket, and others handle security patching automatically and employ dedicated security teams. These platforms perform security updates across millions of instances and maintain professional incident response capabilities. For most organizations without extreme data sensitivity requirements or specific regulatory mandates requiring on-premises infrastructure, cloud-hosted solutions provide better security posture with less operational overhead than self-hosted git services.
What should federal agencies do if they cannot patch by the February 2 deadline?
Federal agencies unable to patch vulnerable Gogs instances by February 2, 2026, must immediately cease using those systems per CISA requirements. This means either air-gapping Gogs instances from networks with sensitive data, implementing alternative source control solutions, or migrating to cloud-hosted platforms. Continuing to use patched systems after the deadline violates federal cybersecurity requirements and creates compliance violations that can result in IT contract suspension.
How does Gogs compare to other self-hosted git solutions in terms of security?
Gogs, Gitea, and other lightweight self-hosted solutions share similar architectural patterns and security considerations. None are inherently more secure than others; security depends primarily on how organizations configure, maintain, and monitor their instances. Larger platforms like GitLab self-hosted come with more comprehensive security features but also increased operational complexity. Cloud-hosted platforms handled by security specialists provide superior security outcomes for most organizations compared to self-hosted alternatives.
What are the financial implications of a Gogs compromise?
Financial impacts include costs of incident response and forensics, credential rotation across all downstream systems, remediation of compromised source code or deployed backdoors, potential regulatory fines for security breaches, business disruption from compromised development infrastructure, notification costs if customer data was accessed, potential litigation if software contained injected vulnerabilities, and reputational damage from security failures in your development practices.
What monitoring and detection approaches work best for Gogs security?
Implement comprehensive logging of all API access, file operations, and authentication events. Centralize logs to a SIEM for analysis and alerting. Monitor for unusual access patterns, failed authentication followed by successful access, requests from unexpected locations, and anomalous resource usage. Set alerts on modifications to sensitive repositories, addition of new user accounts, and changes to system files. Use network monitoring to detect unusual outbound connections from Gogs servers. Combine behavioral analysis with signature-based detection for comprehensive coverage.
Conclusion: Acting Now on Critical Vulnerability
CVE-2025-8110 represents a significant and active threat to organizations running Gogs. The vulnerability is being actively exploited, over 700 instances are already compromised, and federal agencies face strict compliance deadlines.
The good news is that patches exist. The vulnerability is fixable. Organizations that act quickly can eliminate this risk.
The bad news is that many organizations won't act quickly enough. Self-hosted infrastructure lacks visibility in many organizations. Gogs instances run silently for years without formal oversight. Patch management processes are informal or nonexistent. When February 2 arrives, many organizations will face difficult choices: emergency patching campaigns, compliance violations, or infrastructure shutdown.
This vulnerability is also a wake-up call about the broader challenges of self-hosted infrastructure. Ownership comes with responsibility. That responsibility includes security patching, vulnerability assessment, monitoring, and incident response. Many organizations underestimate these responsibilities until a vulnerability like this forces them to reckon with neglected infrastructure.
Moving forward, organizations should evaluate whether self-hosted git services are worth the security costs and operational overhead. For most organizations, cloud-hosted alternatives provide better security with less operational burden. For organizations that choose self-hosting, investing in proper security operations, monitoring, and patch management is non-negotiable.
The clock is ticking for federal agencies and other organizations affected by CVE-2025-8110. Patch immediately. Monitor carefully. Assess whether you were compromised. And then think carefully about whether self-hosted git infrastructure remains the right choice for your organization.

Key Takeaways
- CVE-2025-8110 is a critical symlink bypass vulnerability in Gogs enabling unauthenticated remote code execution with a CVSS score of 8.7
- Over 700 Gogs instances show confirmed compromise from active exploitation before patches became available
- Federal agencies must patch by February 2, 2026, per CISA's Known Exploited Vulnerabilities mandate
- Organizations should assess whether self-hosted git infrastructure security costs justify the operational burden
- Proper patch validation testing, backup procedures, and post-patch compromise assessment are essential response steps
Related Articles
- CISA Retires 10 Emergency Directives: What Changed for Federal Cybersecurity [2025]
- SmarterMail CVE-2025-52691 RCE Vulnerability: Complete Guide [2025]
- Supply Chain, AI & Cloud Failures in 2025: Critical Lessons
- Condé Nast Data Breach 2025: What Happened and Why It Matters [2025]
- Oracle EBS Breach: How Korean Air Lost 30,000 Employees' Data [2025]
- AWS CISO Strategy: How AI Transforms Enterprise Security [2025]
![Gogs CVE-2025-8110 RCE Vulnerability: What Federal Agencies Must Know [2025]](https://tryrunable.com/blog/gogs-cve-2025-8110-rce-vulnerability-what-federal-agencies-m/image-1-1768318804737.jpg)



