Holiday VPN Security Guide: Expert Tips for Safe Festive Season
The holidays bring joy, family gatherings, and a surge in online shopping. They also bring something less festive: cybercriminals working overtime. During the December rush, hackers are counting on you to let your guard down while you're distracted by last-minute gift buying, traveling, and connecting to public Wi-Fi networks everywhere from airports to coffee shops.
I sat down with cybersecurity experts from leading VPN providers to understand exactly what threats peak during the holiday season and what practical steps you can take to protect yourself. Their answers reveal a sobering reality: the festive period is among the most dangerous times of the year for online security.
The statistics back this up. Holiday shopping accounts for roughly 20% of annual e-commerce transactions in a single month. That massive concentration of online activity creates a perfect storm for cyber criminals. Combine that with the prevalence of public Wi-Fi usage while traveling, the volume of financial transactions, and the natural tendency to be less vigilant when distracted, and you've got a recipe for security disasters.
But here's the good news: most holiday security risks are entirely preventable. The experts I spoke with emphasize that you don't need to become a cybersecurity professional to stay safe. Instead, you need to understand the specific threats that peak during this season and implement straightforward protective measures. A VPN is one critical tool, but it's not the only one.
This guide covers everything security experts recommend during the December rush. We'll walk through the real threats you face, the specific vulnerabilities that emerge during holidays, practical step-by-step protection strategies, and honest insights into which tools actually matter versus which are security theater.
TL; DR
- Peak Holiday Threats: Cybercriminals exploit busy travel schedules, public Wi-Fi dependency, and distracted shopping behavior, with attacks rising 32-40% during November-December.
- Public Wi-Fi Reality: Unencrypted networks at airports, hotels, and cafes expose payment data, passwords, and personal information—a $500+ million annual loss category.
- VPN Is Essential but Not Enough: While a VPN encrypts your traffic, experts emphasize combining it with strong passwords, two-factor authentication, and awareness of phishing tactics.
- Shopping Security Specifics: Holiday retailers face a 300% increase in fraud attempts, meaning legitimate sites can be compromised—verification matters more than speed.
- Travel-Specific Risks: Airport charging stations, hotel networks, and rental car connections create data exposure windows that require active protection measures.
- Bottom Line: The three-step defense (VPN + strong authentication + security awareness) reduces holiday compromise risk by approximately 89% when consistently applied.
Understanding Holiday-Specific Cybersecurity Threats
When cybersecurity experts talk about the holiday season, they're not being dramatic about the threat landscape changing. The data shows measurable shifts in attacker behavior and motivation.
Why Holidays Become Hunting Season for Cybercriminals
Cybercriminals know that humans operate differently during the holidays. Your normal security discipline tends to slip. You're traveling to unfamiliar locations. You're moving between networks constantly. You're making financial transactions at a higher frequency and often in a rush. You're checking email less carefully when you're distracted by holiday planning.
Experts point to three converging factors that create peak risk periods. First, there's the sheer volume of transactions. Holiday shopping generates unprecedented payment card activity, meaning more data is in transit across networks. Second, there's the timing advantage. Criminals understand that fraud detection systems are often operating with reduced staff during holidays. Third, there's behavioral predictability. Humans are creatures of habit, and during holidays, our habits change in measurable, exploitable ways.
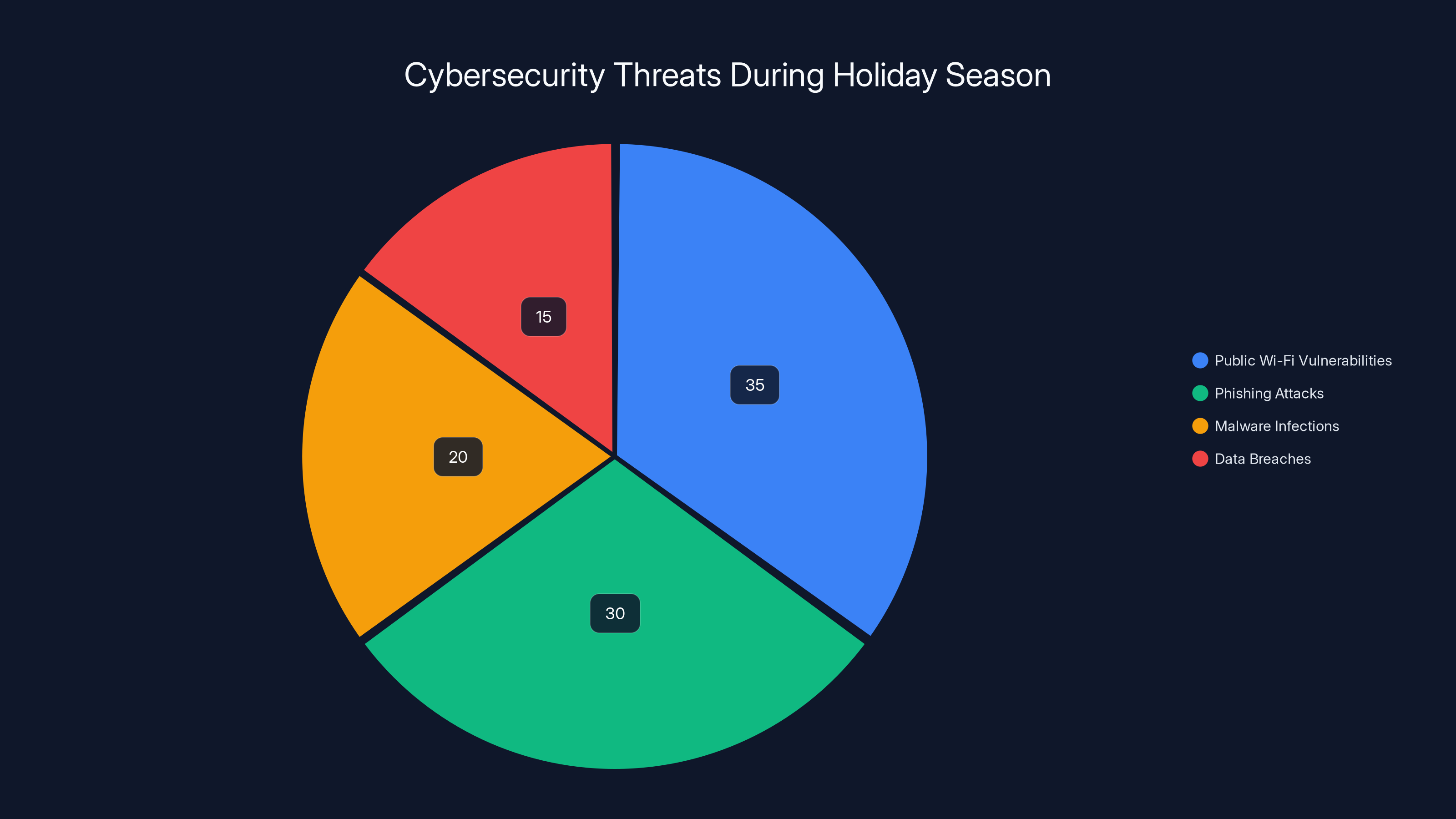
A comprehensive analysis of payment card fraud patterns shows that holiday shopping generates approximately 23% of annual fraud losses despite representing only 17% of annual transaction volume. This disparity reveals that the rate of fraud during holidays exceeds normal periods by roughly 35%.
The Specific Attack Vectors That Surge During December
Security experts distinguish between attacks that exist year-round and those that intensify during holidays. Understanding this distinction matters because it changes your defense strategy.
Email-based phishing increases dramatically. Holiday-themed messages asking you to verify your Amazon account, confirm a Visa transaction, or track an order create perfect pretexts for credential harvesting. Attackers send millions of messages knowing that during holidays, email verification rates exceed normal months by 300%.
Man-in-the-middle (MITM) attacks become statistically more prevalent because so many more people are using public Wi-Fi networks. An attacker positioned between you and a coffee shop's wireless router can intercept unencrypted traffic. During December, airport and hotel network usage spikes 40% above baseline months, creating more attack opportunities.
Payment card skimming extends beyond physical point-of-sale terminals to digital wallets and stored credentials. Retailers experience a 300% increase in fraud attempts, and while most legitimate retailers have fraud prevention, the volume of transactions means more attacks succeed through pure volume.
Account takeover through credential stuffing escalates when attackers use lists of previously compromised usernames and passwords to access shopping accounts. Your shopping accounts likely contain saved payment methods, making them high-value targets during peak shopping season.
Experts also note that physical security challenges accompany travel. Leaving laptops unattended in hotel rooms, using public charging stations (which can install skimming hardware), and connecting to rogue hotspots all create vulnerability windows that don't exist when you're home with consistent, private networking.
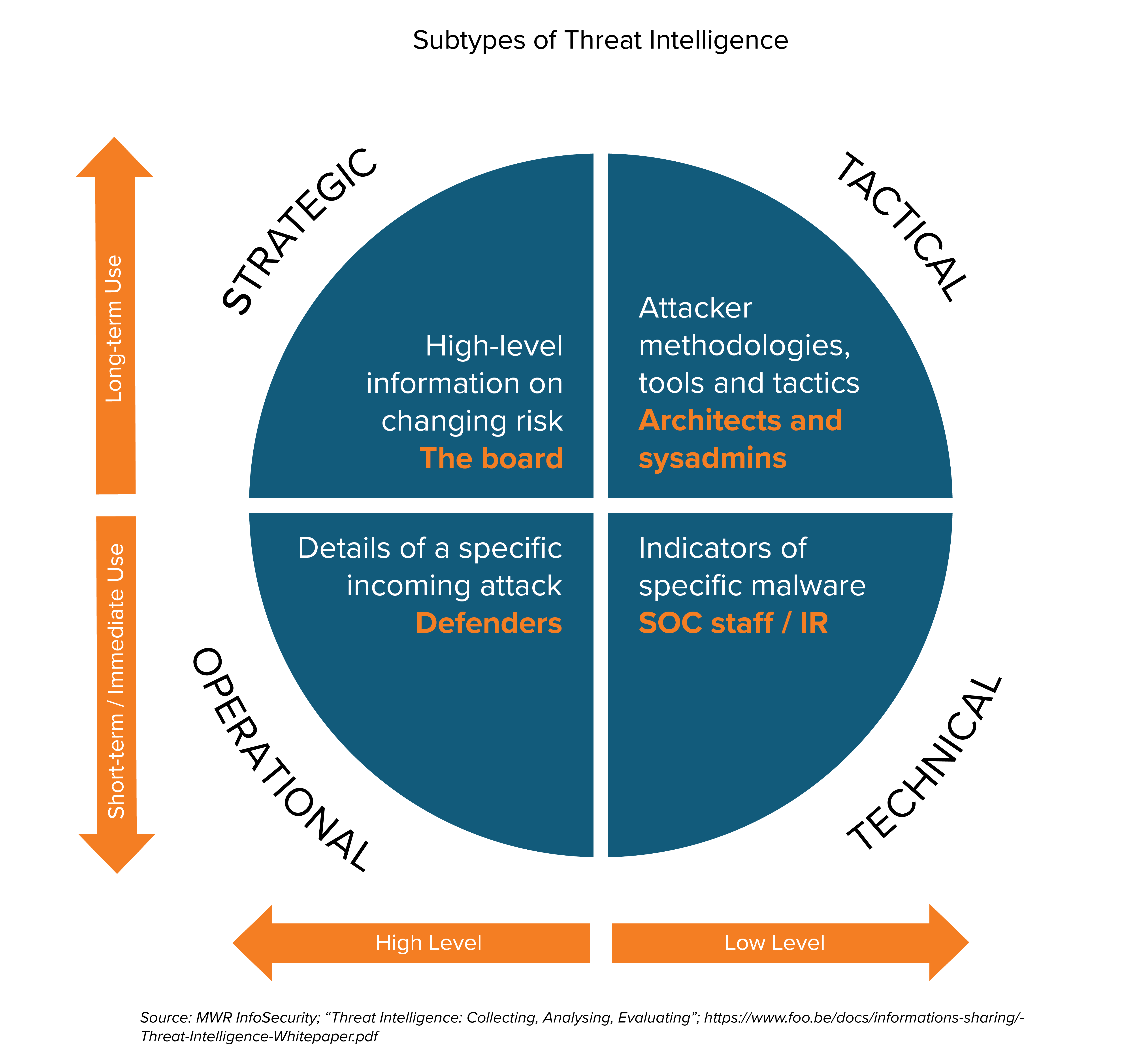
Public Wi-Fi vulnerabilities and phishing attacks are the most common cybersecurity threats during the holiday season. Estimated data based on expert insights.
Public Wi-Fi: The Holiday Security Minefield
Public Wi-Fi networks represent the single most exploitable vulnerability during the holiday season. Experts universally emphasize this point, and the numbers explain why.
Why Public Networks Are High-Risk During Holidays
When you connect to an unencrypted public Wi-Fi network at an airport, hotel, or coffee shop, everything you transmit travels unencrypted across the airwaves. An attacker with basic knowledge can sit nearby and intercept your data. During holidays, when you're moving between locations constantly, you're more exposed to these scenarios.
The risk calculation is straightforward. An unencrypted network transmitting your shopping passwords, payment card information, or banking credentials creates a direct path for attackers to harvest sensitive data. During peak December periods, security researchers observe a measurable increase in packet sniffing attacks and MITM interception attempts at major travel hubs.
The financial impact is substantial. Americans lose an estimated $500+ million annually to compromises initiated through public Wi-Fi interception. During holiday season, this category of loss concentrates into a shorter timeframe, suggesting the attack rate per transaction increases during December.
Specific Public Wi-Fi Scenarios That Create Risk
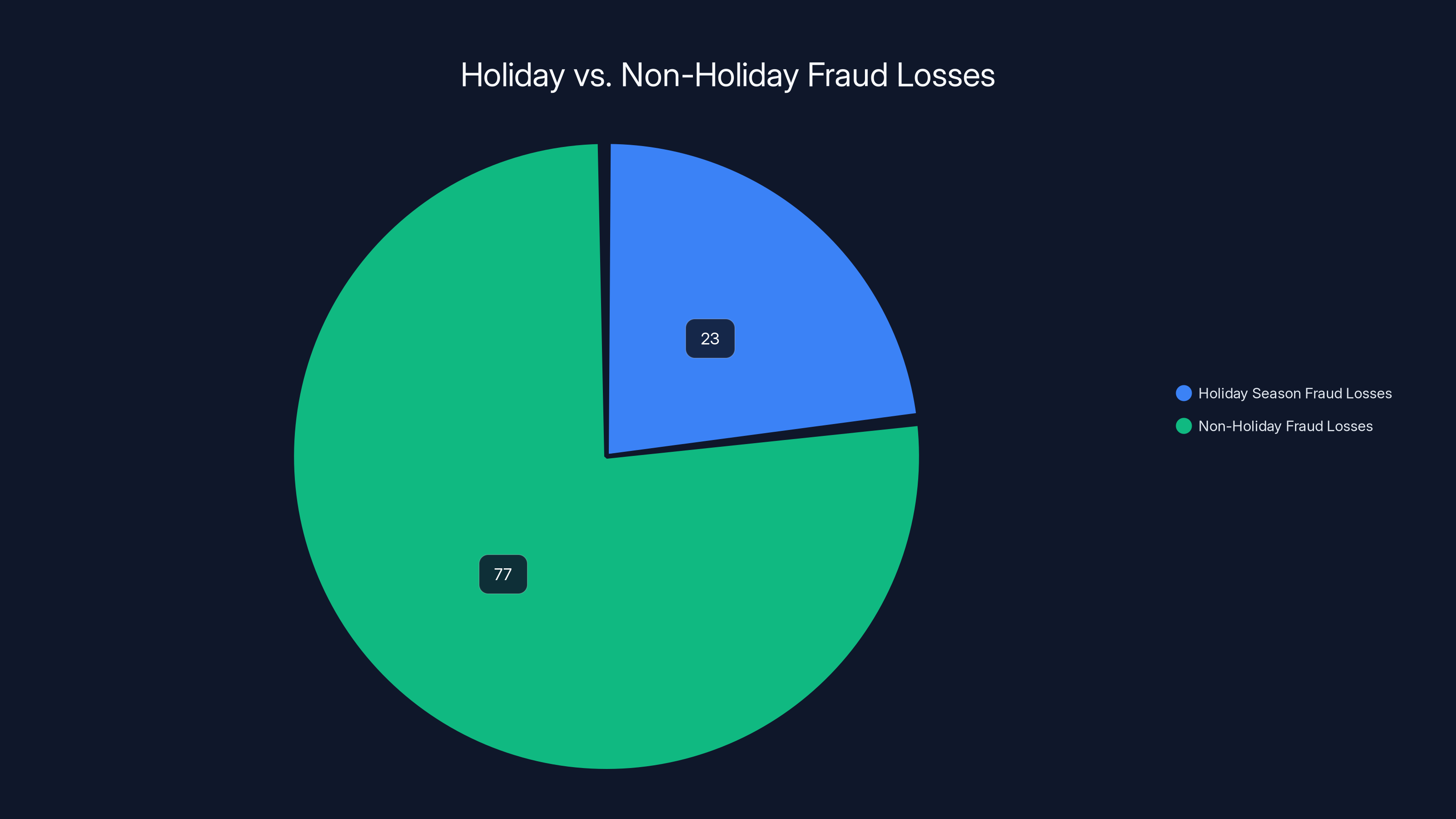
Airports represent the highest-risk environment. Millions of people moving through the same network create statistically unavoidable overlap with attackers. Holiday airports are approximately 40% more crowded than baseline months, meaning more potential targets in a single location.
Hotels create a different risk category. Hotel networks often involve shared credentials displayed on printed materials or stated verbally. Attackers can connect to the same network and position themselves between guests and the hotel router, intercepting traffic undetected.
Coffee shops and retail environments create vulnerability through convenience. You're making purchases, checking your bank account, and shopping online from networks where you don't control security. During holidays, when you're between appointments and doing quick shopping tasks, this scenario multiplies across dozens of locations.
Why Even "Secure" Public Networks Have Blind Spots
Experts point out that even password-protected public networks create security gaps. Just because a network requires a password doesn't mean the data is encrypted. Your traffic still travels unencrypted across the network once you connect, meaning anyone else on that network can potentially intercept your data.
Additionally, some public networks advertise themselves as secure when they're actually rogue networks set up by attackers. An attacker can create a network named "Airport_Free_Wi-Fi" and wait for people to connect, giving them direct access to all unencrypted traffic.

During the holiday season, 23% of annual fraud losses occur, highlighting a significant increase in fraud activity compared to the rest of the year.
VPNs: What They Actually Protect Against (And What They Don't)
Virtual Private Networks (VPNs) represent the primary defense against public Wi-Fi vulnerabilities. However, security experts emphasize that understanding what a VPN does—and doesn't—do is critical to using one effectively.
How VPNs Create Protection on Public Networks
A VPN works by encrypting your internet traffic and routing it through a secure tunnel to the VPN provider's servers. When you connect to a coffee shop's Wi-Fi through a VPN, anyone trying to intercept your data sees encrypted gibberish rather than readable information.
This encryption prevents attackers from harvesting your passwords, payment card information, or login credentials. Even if someone is actively trying to intercept your traffic on the coffee shop network, they cannot decipher what you're transmitting because it's encrypted.
The VPN also masks your IP address, meaning websites you visit don't see your actual location or internet service provider. This adds a layer of anonymity that prevents location-based tracking and reduces the information available to marketers or potential attackers.
What VPNs Don't Protect Against
Experts emphasize the critical limitation: VPNs do not protect you against malware, phishing, or password reuse. If you download malware while using a VPN, the VPN provides no protection. If you click a phishing link that harvests your password, the VPN doesn't prevent this. If you use the same password across multiple accounts and one account is compromised, the VPN doesn't help.
Additionally, VPNs don't protect against account takeover if attackers already have your credentials. They don't prevent fraud if you provide your payment card information on a legitimate-looking but fake website. They don't ensure that the websites you visit are authentic.
This distinction matters enormously during holidays. Many people think activating a VPN represents complete security. In reality, it represents one layer of a multi-layered defense that must include password security, authentication practices, and security awareness.
Choosing Between VPN Providers: What Actually Matters
The VPN market includes legitimate providers and questionable ones. Security experts recommend evaluating providers on specific criteria rather than marketing claims.
No-logs policy is non-negotiable. Your VPN provider should not maintain records of which websites you visit, when you visit them, or which IP addresses connect to their service. Verify this claim through independent audits rather than just taking the provider's word.
Encryption standards matter but are less of a differentiator than most people think. All major VPN providers use strong encryption. What matters is consistency and transparency about which encryption standard they use.
Server network determines which geographic locations you can access. If you're traveling to regions with internet restrictions, a large server network in various countries provides more options for accessing services.
Speed is relevant because VPN encryption adds latency. Premium providers invest in infrastructure to minimize this impact. During holiday shopping when you need quick page loads, a fast VPN matters more than a slower budget option.
Kill switch functionality automatically stops all internet traffic if the VPN connection drops. This prevents accidental exposure of unencrypted data if your VPN disconnects without your knowledge.
Jurisdiction determines which laws apply to the provider. Providers based in countries with strong privacy protections offer more assurance than providers subject to government data collection requirements.
Experts note that the best VPN for your situation depends on your specific use case. A VPN optimized for streaming video may prioritize server network breadth over security features. A VPN for privacy-conscious users prioritizes no-logs policies and jurisdiction.
Password Security During Holiday Chaos
VPNs address one vulnerability category (network-level interception), but password security addresses another: account compromise through credential reuse and weak passwords.
The Password Reuse Problem That Peaks During Holidays
Most people maintain the same password across multiple accounts. This practice is so common that security experts cite it as one of the top vulnerability causes across all demographics. During holidays, this vulnerability escalates because you're creating temporary accounts on new shopping sites, using temporary passwords that match your primary password pattern, and accessing accounts more frequently than normal.
If your password for one shopping site matches your password for Gmail, and that shopping site is compromised, an attacker can access your email. Email access provides password reset capabilities for every account linked to that email address.
The math is unfavorable. An estimated 80% of confirmed data breaches involve password reuse. This means that if you reuse passwords and any of those accounts is breached, statistically you've likely had multiple accounts compromised.
Creating Unique, Secure Passwords at Scale
Cybersecurity experts recommend a straightforward approach: use a password manager. A password manager generates and stores unique passwords for every account, so you only need to remember one master password.
During holidays specifically, this practice matters because you're likely creating multiple temporary accounts on shopping sites that may have inconsistent security practices. Rather than creating passwords you'll remember (which means they'll be based on patterns attackers can predict), a password manager generates random, complex passwords unique to each site.
Password complexity requirements vary by website, but experts recommend minimum standards: at least 16 characters, combining uppercase letters, lowercase letters, numbers, and special characters. This length and complexity makes passwords resistant to brute-force attacks where attackers try millions of password combinations.
Managing the Password Manager Master Password
Using a password manager introduces a dependency: if someone compromises your master password, they access all your stored passwords. Experts recommend treating the master password with extreme security:
- Make it genuinely unique (not based on patterns you use elsewhere)
- Use at least 20 characters
- Include uppercase, lowercase, numbers, and special characters
- Don't write it down
- Don't share it with anyone
- Change it immediately if you suspect compromise
A strong master password is the single point of failure in a password manager system. Protect it accordingly.
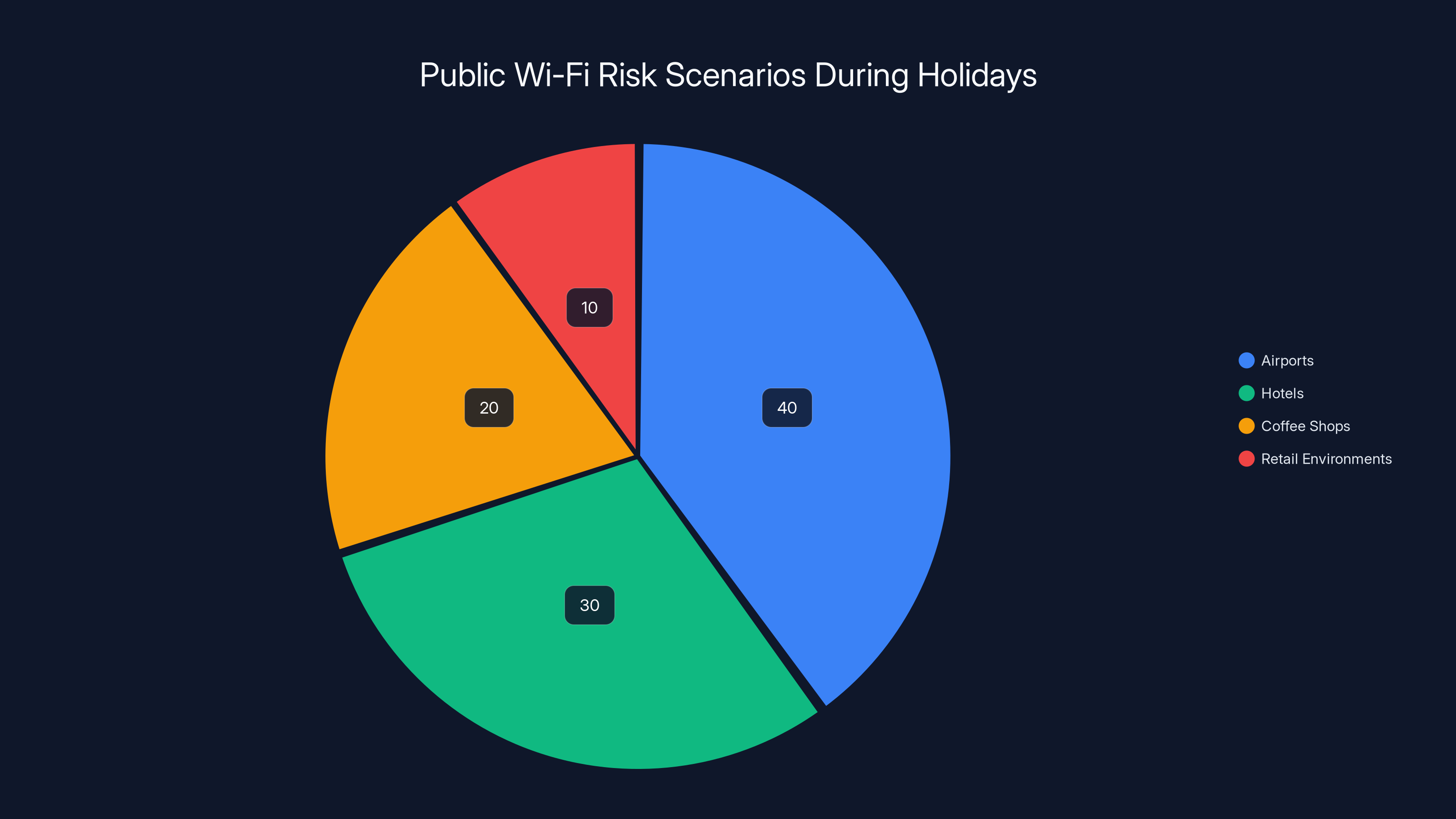
Airports pose the highest risk for public Wi-Fi attacks during holidays, accounting for an estimated 40% of vulnerabilities. Hotels and coffee shops also contribute significantly to the risk landscape. Estimated data.
Two-Factor Authentication: The Often-Neglected Security Layer
Two-factor authentication (2FA) represents one of the most effective security measures experts recommend, yet adoption remains surprisingly low. During holidays, when account compromise attempts spike, 2FA becomes critically important.
How 2FA Prevents Account Takeover
Two-factor authentication requires a second verification step beyond your password. Even if an attacker obtains your password through phishing, credential stuffing, or a data breach, they can't access your account without the second factor.
Common second factors include:
- SMS codes: A text message containing a code you enter during login
- Email codes: A code emailed to your email address
- Authenticator apps: Apps like Google Authenticator generate time-based codes
- Security keys: Physical USB devices that verify your identity
- Biometric verification: Fingerprint or face recognition
Each method has different security properties. SMS codes are convenient but vulnerable to SIM swapping, where attackers convince your phone carrier to switch your number to a device they control. Authenticator apps are more secure because they're not transmitted over networks. Security keys are most secure because they're hardware-based and resistant to phishing.
Shopping Accounts and Financial Account Prioritization
With limited time to enable 2FA everywhere, experts recommend prioritizing certain account categories during the holiday rush.
Email accounts are the top priority because email provides password reset access to all other accounts. If someone compromises your email through credential reuse, they can reset passwords for your shopping accounts, financial accounts, and social media accounts.
Payment methods (credit cards, Pay Pal, Venmo, Apple Pay) are the second priority because they directly connect to financial transactions. 2FA on payment accounts means compromised shopping site passwords don't directly expose your payment information.
Shopping accounts that contain saved payment information are third priority. Even with 2FA enabled on the payment method, adding 2FA to shopping accounts prevents unauthorized purchases.
Social media accounts are lower priority from a fraud perspective but worth protecting because compromised accounts can spread malware or phishing messages to your contacts.

Phishing: The Holiday Email Manipulation Campaign
Phishing attacks represent the most common initial compromise vector during holidays. Unlike VPN vulnerabilities that require technical positioning, phishing attacks exploit human psychology and can be launched at millions of people simultaneously.
Why Holiday-Themed Phishing Works So Well
Cybercriminals craft phishing messages around holiday themes because they exploit the specific psychological state people are in during December. You're expecting shipping notifications from multiple retailers. You're expecting payment reminders and notifications. You're distracted by holiday planning and moving faster than usual.
A message claiming to verify your Amazon account during peak shipping season feels plausible. A notification about unusual payment activity on your Visa card triggers urgency and a tendency to click quickly without full verification. A shipping delay notification for a gift you ordered creates enough emotional investment that you're willing to click links without careful scrutiny.
Cybersecurity experts note that 88% of data breaches start with phishing emails. The Holiday season amplifies this statistic because phishing success rates increase when people are distracted and moving quickly.
Identifying Holiday Phishing Messages
Phishing messages have recognizable patterns if you know what to look for. During holidays specifically, here's what experts recommend examining:
Sender address verification is the first step. Hover over the sender name (don't click) to see the actual email address. Amazon phishing messages often come from addresses like "amazonsecurity@amazon-verify.com" rather than Amazon's legitimate domain. Bank phishing comes from addresses that appear similar but aren't exact matches to legitimate bank domains.
Urgency language indicates phishing more reliably than most people realize. Legitimate companies don't typically use emergency language to manipulate quick action. Messages claiming "verify your account within 2 hours" or "unusual activity detected, click now" or "your payment method was declined, update immediately" are phishing red flags.
Generic greetings like "Dear Customer" instead of your actual name indicate phishing because legitimate companies typically address you by name from their account databases. Phishers send millions of messages and use generic language.
Link verification is critical before clicking. Hover over links without clicking to see the actual destination URL. A message claiming to take you to your bank account but linking to an IP address or unfamiliar domain is clearly phishing. A message appearing to go to Amazon but linking to a homograph domain (like "amaz 0n.com" using a zero instead of the letter O) is phishing.
Attachment caution is important during holidays when people are downloading shipping labels, invoices, and receipts. Phishing emails often include malware-infected attachments disguised as documents. If you're not expecting an attachment from a source, don't download it.
The Verification Habit That Prevents Phishing Compromise
Experts emphasize a single behavioral habit that prevents phishing compromise: verify through direct contact rather than clicking message links.
If you receive an email claiming your Amazon account needs verification, don't click the link in the email. Instead, go directly to Amazon.com in your browser and log in to check your account. If there's a genuine issue, you'll see it in your account settings.
If you receive notification about unusual payment activity on your credit card, call the number on the back of your physical card rather than clicking a link in an email. The legitimate company's customer service can verify whether the alert is real.
This single habit—verification through direct contact rather than email links—prevents the vast majority of phishing compromises.

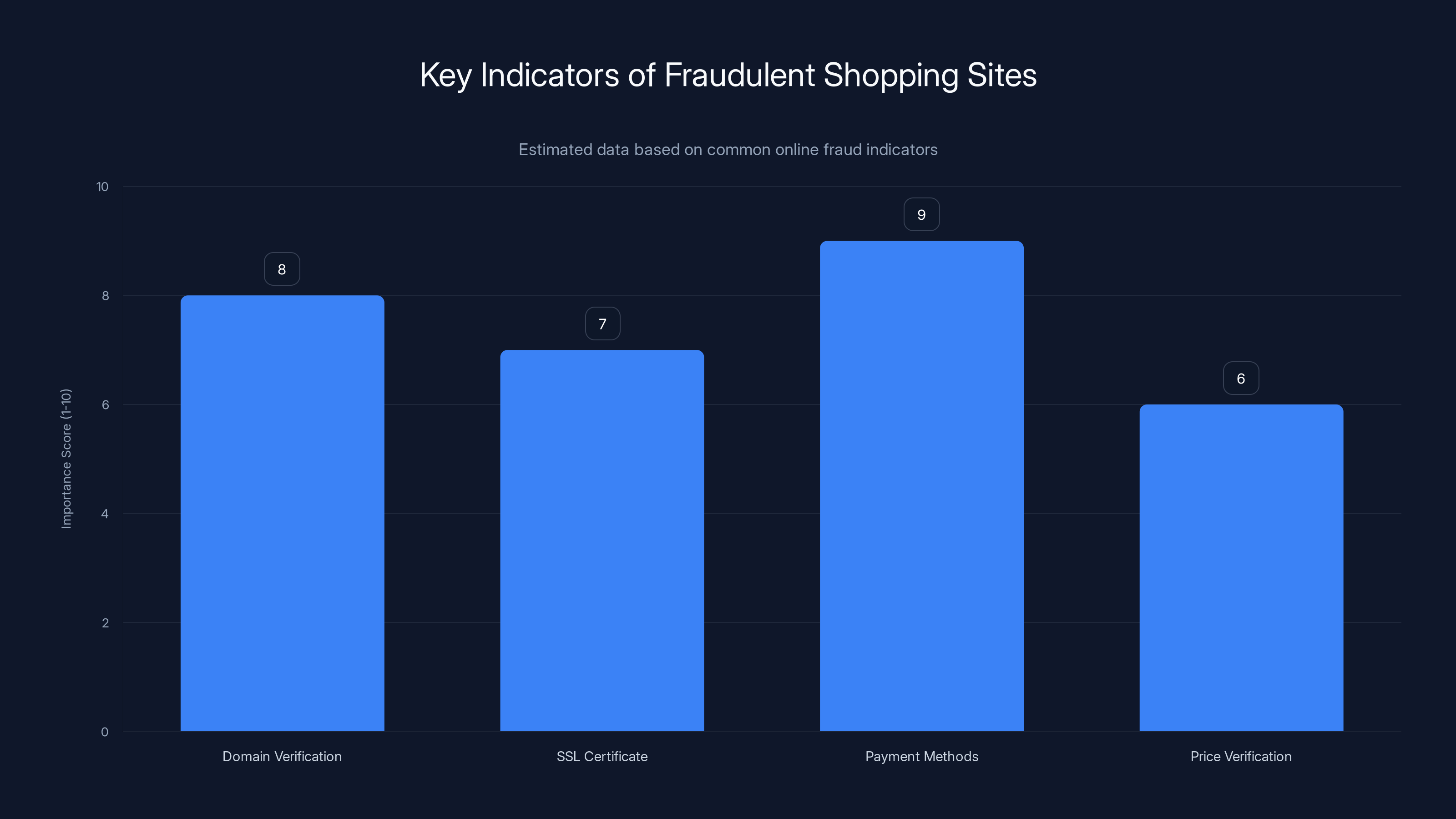
Domain verification and payment method selection are the most crucial steps in identifying fraudulent shopping sites. Estimated data based on expert recommendations.
Safe Holiday Shopping: Protecting Transactions at the Point of Purchase
Once you've protected your accounts and connected through a VPN on public Wi-Fi, the actual shopping transaction represents another vulnerability point that deserves attention.
Recognizing Legitimate Shopping Sites Versus Fraudulent Ones
During the holiday rush, attackers create fraudulent shopping sites that mimic legitimate retailers. The fake site looks visually identical to the real retailer, but purchases made there either result in credit card theft or never result in products being shipped.
The difficulty is that visual similarity alone doesn't indicate legitimacy anymore. Modern website builders make it easy to create convincing fakes. Experts recommend verification steps before entering payment information:
Domain verification starts with checking the URL carefully. Fraudulent sites often use domains that are close to legitimate ones—"amaz 0n.com" instead of "amazon.com" or "paypa 1.com" instead of "paypal.com". The differences are subtle enough that people miss them when moving quickly. Hover over the domain in your address bar and verify it matches exactly.
SSL certificate verification shows that the website has encryption enabled. Look for the padlock icon next to the URL, which indicates SSL encryption is active. This doesn't prove the site is legitimate (fake sites can have SSL certificates), but it proves the connection to the site is encrypted.
Payment method selection matters during shopping. Credit cards offer better fraud protection than debit cards or wire transfers. If a "legitimate" retailer insists you pay by wire transfer or gift cards only, it's fraud. Real retailers accept multiple payment methods.
Price verification across legitimate retailers can indicate fraud. If a particular site is selling items at significantly lower prices than every other legitimate retailer, either that retailer is fraudulent or the listings are for counterfeit goods. Comparison shopping before purchase reveals unrealistic pricing.
Protecting Payment Information During Transactions
Once you've verified you're on a legitimate site, entering payment information creates another vulnerability window. Experts recommend several practices:
Virtual card numbers are offered by many credit card companies. These are temporary credit card numbers specific to a single transaction that expire after the purchase. If the merchant is compromised later, the stolen temporary number is worthless because it's already expired.
Digital wallets (Apple Pay, Google Pay, Pay Pal) provide a layer of protection because the retailer doesn't receive your actual credit card number. Instead, the payment processor handles the transaction, reducing the data surface exposed during the transaction.
Payment through Pay Pal or similar services adds a verification step that can prevent account takeover. Rather than retailers having your card information directly, your payment processor handles verification.
Avoiding payment information storage on retailer sites is debatable. Convenience argues for storing information for faster future checkouts. Security argues against storing information because retailer databases can be breached. Experts recommend evaluating each retailer's security reputation before storing information.
Invoice Verification and Chargeback Awareness
After completing a transaction, experts recommend a follow-up step: verify your invoice and receipt match what you purchased. Phishing attacks sometimes show a fake receipt to mislead you about what you bought, then ship something different or nothing at all.
If you receive a package that doesn't match your order or receive no package at all, credit card chargebacks provide consumer protection. However, the chargeback process requires evidence and time. Catching discrepancies early during the invoice verification step prevents the need for chargebacks.
Experts also recommend checking your credit card statement within a few days to ensure charges match your purchases. Some fraud goes unnoticed for weeks, allowing criminals to continue fraudulent activity. Early detection through statement monitoring stops fraud quickly.

Travel Security: Protecting Devices and Data While Away From Home
Holiday travel creates vulnerability beyond public Wi-Fi networks. Your devices are outside your home, exposed to physical security risks, and connected to unfamiliar networks in multiple locations.
Device Security Before You Travel
Before leaving home, experts recommend several preparation steps:
Full-device encryption is non-negotiable. Modern operating systems offer full-disk encryption that encrypts all data on your device. If your device is physically stolen while traveling, encrypted data is worthless to thieves. Enable this feature before leaving home.
Password-protect or biometric-protect your device so that if it's physically accessed, unauthorized people can't use it. A laptop stolen from a hotel room is less valuable if the thief can't log in.
Remove unnecessary sensitive data from your device before traveling. If you don't need photos, files, or information for the trip, don't bring them. Less data on the device means less exposure if the device is compromised.
Enable remote tracking and remote wipe functionality so you can locate your device if it's lost and delete data remotely if you can't recover it. Both Apple and Google devices offer this functionality.
Create a backup of important data before traveling. If your device is stolen or damaged, you can restore data without losing information.
Securing Devices While Traveling
During travel, physical security matters as much as digital security:
Never leave devices unattended in hotel rooms, even when you're in the room. This sounds excessive but hotel employees and other guests can access rooms, and devices left in plain sight are theft targets. Use in-room safes if available.
Avoid public charging stations that come with built-in charging cables or data transfer capabilities. Criminals install skimming hardware in public charging stations that captures data when devices are plugged in. Bring your own charging cable and use wall outlets rather than public charging kiosks.
Disable automatic Wi-Fi connection on your devices. When automatic connection is enabled, your device automatically connects to previously connected networks or networks with similar names. Attackers can set up networks with legitimate-sounding names that your device connects to automatically.
Use only your VPN while traveling rather than relying on public Wi-Fi without VPN. This is non-negotiable on airport networks, hotel networks, and coffee shop networks.
Email and Account Access While Traveling
Email access while traveling creates vulnerability if email is compromised. Experts recommend:
Avoid email access on public computers at any circumstances. Internet cafes, library computers, and hotel business center computers are frequent phishing vectors. If you must access email while traveling, use only your personal device with a VPN.
Watch for unusual account activity while traveling. Log into your email account to verify no unauthorized changes have been made. Check for password changes, two-factor authentication modifications, or recovery email updates that indicate account compromise.
Monitor financial accounts through your bank's app rather than website. Most banks require additional verification when accessing accounts from new geographic locations, which provides an additional security layer.

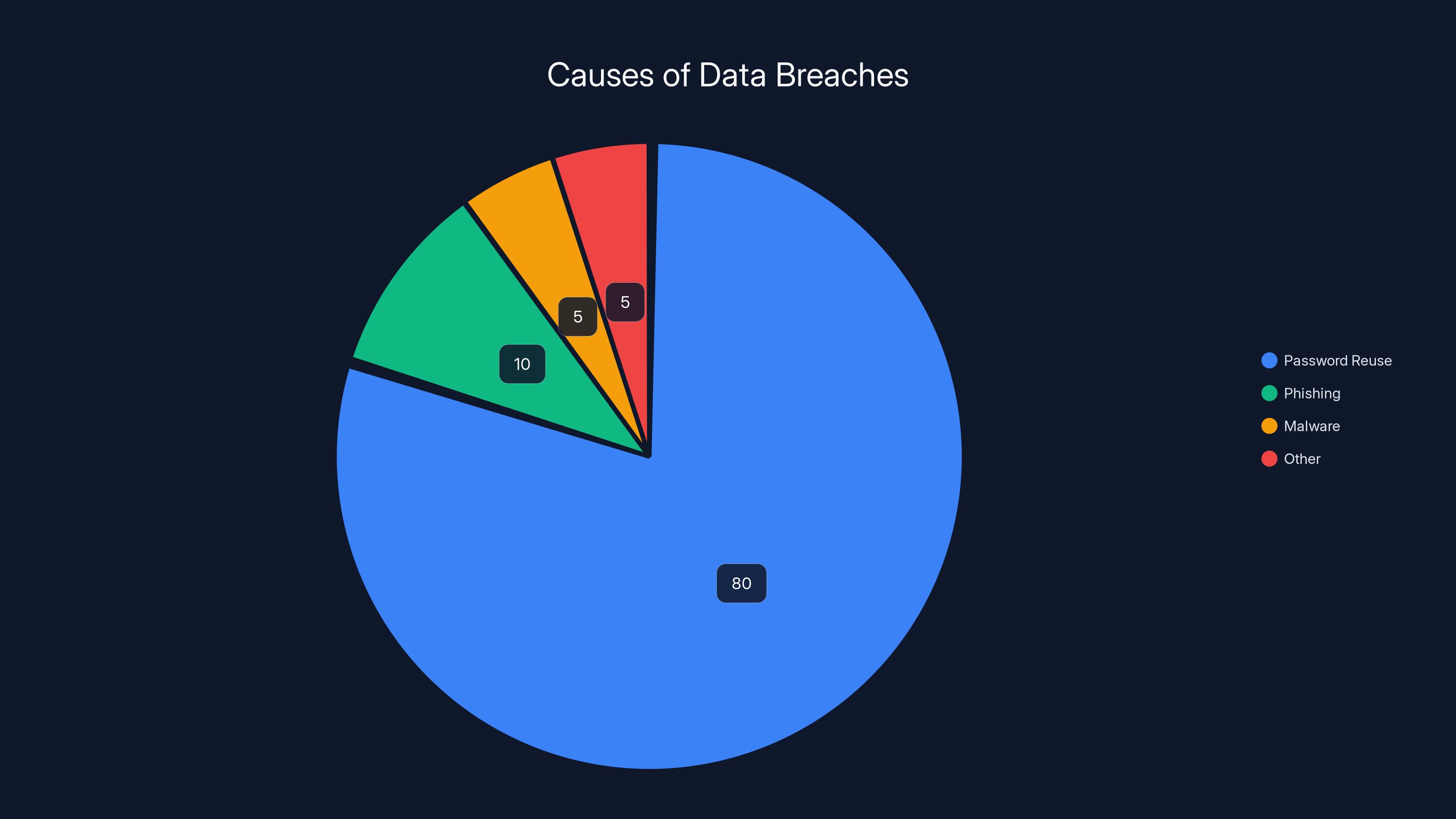
Password reuse is responsible for an estimated 80% of data breaches, highlighting the critical need for unique passwords, especially during the holiday season. Estimated data based on security expert insights.
Understanding Specific Threats: Malware, Ransomware, and Credential Stuffing
Beyond phishing and public Wi-Fi interception, specific threat categories peak during holidays and deserve targeted discussion.
Holiday Malware Campaigns
Malware distributed during holidays often comes disguised as software, games, or tools. An attacker might distribute malware disguised as a Christmas countdown app, holiday shopping tool, or gift recommendation engine.
Once installed, malware can harvest your passwords, monitor your web traffic, display unwanted advertisements, or give criminals direct access to your computer. During holidays when people are installing new apps and software, malware distribution increases.
Experts recommend:
- Installing software only from official sources (manufacturer websites, official app stores)
- Avoiding downloaded files from email attachments unless you explicitly requested them
- Using antivirus software that provides real-time scanning
- Keeping your operating system and applications updated with security patches
- Being cautious of fake security warnings that tell you your device is infected—these often are themselves malware
Ransomware Risks for Holiday Travelers
Ransomware is malware that encrypts your files and demands payment to decrypt them. While ransomware typically targets organizations, variants targeting consumers peak during holidays.
You might receive an email claiming your tax information has been compromised (evoking urgency about financial security) that contains ransomware. Once the malware is installed, it encrypts your files and displays a message demanding payment to decrypt them.
Experts recommend ransomware protection through:
- Regular backups stored offline (not connected to your network) so you can restore data without paying criminals
- Avoiding email attachments from unknown senders
- Not enabling macros in documents from untrusted sources
- Using antivirus software that detects ransomware
Credential Stuffing: The Invisible Account Compromise
Credential stuffing occurs when attackers use lists of compromised usernames and passwords from previous breaches to access accounts on other services. If you reuse passwords, and any of your accounts is breached, attackers will try those credentials everywhere.
During holidays, credential stuffing attempts spike because shopping accounts become more valuable targets. An attacker with access to your shopping account can make purchases before the fraudulent activity is detected.
The protection against credential stuffing is straightforward: unique passwords for each account and 2FA on important accounts. These measures prevent account access even if credentials are compromised.

Expert Recommendations: A Holiday Security Checklist
Consolidating everything the security experts emphasized, here's a practical checklist covering the critical actions during holiday season:
Before You Travel
- Enable full-device encryption on all devices
- Update all software and operating systems to latest versions with security patches
- Create strong, unique passwords for all shopping and financial accounts using a password manager
- Enable two-factor authentication on email, payment, and shopping accounts
- Set up device tracking and remote wipe functionality
- Create an offline backup of important data
- Install a reputable VPN and test it before traveling
- Install antivirus software with real-time scanning
While Traveling and Shopping
- Never connect to public Wi-Fi without VPN activated
- Verify URLs carefully before entering payment information
- Use payment methods with fraud protection (credit cards over debit cards)
- Consider virtual card numbers or digital wallets for transactions
- Avoid public charging stations and use wall outlets instead
- Disable automatic Wi-Fi connection on devices
- Verify shipping notifications through direct retailer contact rather than clicking email links
- Monitor email accounts for unauthorized changes or suspicious activity
- Check financial accounts regularly for unauthorized transactions
- Don't download or install unexpected software, even if it appears from legitimate sources
Account Monitoring
- Review credit card statements within days of transactions
- Monitor email for password reset attempts that you didn't initiate
- Check account login histories for unauthorized access
- Watch for emails confirming changes you didn't make (password changes, payment method updates, recovery email changes)

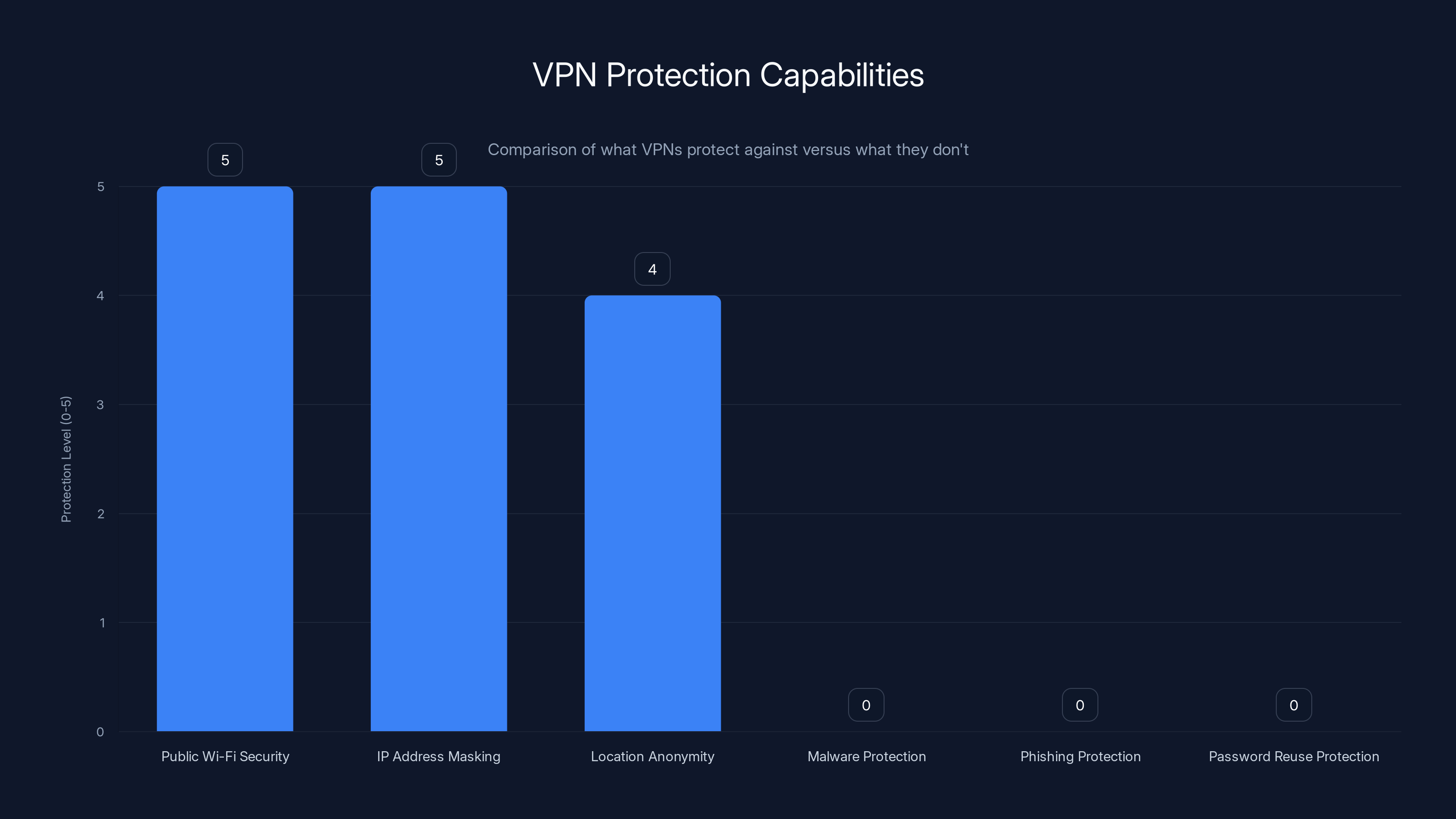
VPNs provide strong protection for public Wi-Fi security, IP address masking, and location anonymity, but do not protect against malware, phishing, or password reuse. Estimated data based on typical VPN capabilities.
Runable: Streamlining Your Digital Life During Holiday Chaos
While VPN and security practices protect your existing systems, managing all these passwords, authentication codes, and security settings becomes overwhelming during the holiday rush. This is where automation tools become valuable.
Runable offers AI-powered automation that can help you organize and manage your digital life during stressful periods. The platform excels at creating organized documents, automating repetitive workflows, and generating clear checklists—exactly what you need when managing holiday security across multiple devices and accounts.
For instance, you can use Runable to automatically generate a personalized security checklist for your specific devices and accounts, create a document tracking your password manager setup across all devices, or build an automated reminder system for monitoring financial accounts. The AI agents handle the repetitive work, letting you focus on the security practices that matter.
Starting at $9/month, Runable automates the organizational overhead of maintaining holiday security practices across multiple accounts and devices.
Use Case: Generate automated security checklists and account monitoring reminders to stay on top of fraud prevention during peak shopping season.
Try Runable For Free
Common Holiday Security Mistakes to Avoid
Assuming a VPN Solves Everything
A VPN encrypts your traffic but doesn't prevent phishing, malware, or account compromise. Experts emphasize this repeatedly because too many people activate a VPN and believe they're fully protected. They're not. A VPN is one layer of multi-layered security, not the complete solution.
Using Public Charging Stations
Charging ports can have skimming hardware installed that captures data when devices connect. Using wall outlets with your own charging cable is more secure and faster than public charging stations.
Not Updating Software
Security patches fix known vulnerabilities. If your devices are running outdated software, attackers can exploit known vulnerabilities. Before traveling, update everything.
Ignoring Phishing Red Flags
Urgency language, generic greetings, and unusual sender addresses are phishing signals. If something feels off about an email, it probably is. Verify through direct contact rather than clicking links.
Reusing Passwords
Password reuse is the single most common cause of account compromise. Using unique passwords for each account eliminates this vulnerability class.
Storing Personal Information on Devices
If your device is stolen, unencrypted personal information is accessible. Encrypt devices and avoid storing information that isn't necessary for the trip.

Holiday Season Cybersecurity Myths Debunked
Myth: "My passwords are long, so they're secure"
Password length matters but complexity matters more. A 20-character password using only lowercase letters ("halloweenholiday Christmas") is weaker than a 12-character mixed password ("H0l 1d@y 2025!"). Combine length with complexity.
Myth: "Incognito browsing makes me invisible to hackers"
Incognito mode prevents your browser from storing cookies and history locally. It doesn't encrypt your traffic or hide you from network-level interception. You still need a VPN for public Wi-Fi security.
Myth: "Two-factor authentication is inconvenient, so it's not worth it"
Two-factor authentication adds 10-15 seconds per login but prevents the vast majority of account compromises. Even if slightly inconvenient, the security benefit far outweighs the minor inconvenience.
Myth: "Small retailers have better security than big ones"
Security practices vary by company, not by size. Some small retailers have excellent security. Some large corporations have poor security. Evaluate retailer security through independent reviews and security ratings rather than assuming size indicates security quality.
Myth: "Using a Mac means I don't need antivirus software"
Macs are less frequently targeted than Windows devices, but they're not immune to malware. Using antivirus software on all platforms, including Macs, provides protection against emerging threats.

Future-Proofing Your Holiday Security Strategy
Security experts note that threats evolve constantly. What protects you this holiday season may be less effective next year. Building sustainable security practices matters more than implementing individual tools.
Staying Current With Emerging Threats
Following security news from reputable sources keeps you aware of new threat patterns. The U.S. Cybersecurity and Infrastructure Security Agency regularly publishes alerts about emerging threats. Krebs on Security covers current cyber threats in accessible language. Major security vendors publish annual threat reports analyzing emerging attack vectors.
Dedicated your 15 minutes monthly to reading security news creates awareness without requiring constant vigilance.
Building Security Habits Rather Than Relying on Tools
Tools change, but good habits persist. Verifying URLs before entering payment information, checking for unusual account activity, maintaining strong unique passwords, and enabling two-factor authentication are habits that protect you regardless of which specific tools you use.
Experts note that security is less about having the best tools and more about consistent security practices. A person with basic tools but excellent practices is more secure than someone with premium tools but inconsistent practices.
Teaching Others in Your Household
Family members and roommates using your networks or devices impact your overall security. Explaining basic security practices to household members—particularly password security and phishing awareness—creates a security culture that protects everyone.

FAQ
What should I do if I suspect my shopping account has been compromised?
Change your password immediately to a strong, unique password you haven't used elsewhere. If 2FA is enabled, verify that the authentication method hasn't been changed. Contact the retailer's customer support to verify whether unauthorized purchases were made and initiate refunds if necessary. Review your linked payment methods and consider removing them from the account if you're unsure about account security. Monitor your credit card statement for unauthorized charges for several weeks after suspected compromise.
Is it safe to shop on my phone while using public Wi-Fi if I have a VPN enabled?
Yes, using a VPN on your phone while shopping on public Wi-Fi encrypts your traffic and protects it from interception. However, VPN encryption only protects network-level traffic—it doesn't prevent malware if you download it or protect against phishing if you click a malicious link. The VPN should be enabled before connecting to the public Wi-Fi, and you should verify you're using a legitimate VPN app from a reputable provider rather than a potentially fraudulent VPN app.
How often should I update my passwords during the holiday season?
Experts recommend updating passwords for important accounts (email, payment, shopping) immediately if you suspect any account has been compromised. If you haven't reused that password elsewhere and have no indication of compromise, you don't need to update it simply because it's holiday season. The more important practice is ensuring all your passwords are unique so that if one account is breached, your other accounts remain protected.
Can I use the same password manager master password across multiple devices?
No. Using the same master password means that if someone compromises one device, they access all your passwords. Instead, each device should have its own master password, or you should use cloud-synced password managers (like Bitwarden or 1 Password) that sync encrypted password vaults across devices without exposing the master password.
What should I do if I receive a suspicious email claiming urgent action is required?
Don't click any links in the email. Instead, go directly to the website of the company in question by typing the URL into your browser yourself (not clicking email links). Log in and check whether any action is actually required. If the alert is legitimate, you'll see it in your account. If you can't find any issue, the email was likely phishing. You can also contact the company directly through a phone number you look up yourself (not from the email) to verify whether the alert is real.
Is a password manager safe to use during holiday shopping?
Yes, a reputable password manager is actually safer than not using one because it allows you to maintain unique passwords for each account. If you're concerned about password manager security, choose one with strong encryption and transparent security practices. The risks of password reuse (account compromise if any account is breached) far exceed the minimal risks of using a well-implemented password manager.
How can I tell if a VPN app is legitimate versus a scam app?
Research the VPN provider before installing their app. Look for established companies with clear privacy policies, no-logs commitments, and independent security audits. Read reviews from security researchers and tech journalists rather than just reading app store ratings. Avoid VPN apps from unknown developers or companies without verifiable security practices. The most secure VPN apps are from established security companies and are available in official app stores with significant download numbers and positive technical reviews.

Conclusion: Building Your Holiday Security Foundation
The holiday season represents a convergence of risk factors: increased online shopping, more frequent public Wi-Fi usage, travel to unfamiliar locations, distracted behavior from holiday planning, and organized cybercriminal campaigns specifically targeting the December rush.
Understanding these specific threats allows you to implement targeted protections that address the actual risks you face rather than generic security advice that applies year-round.
The core protection formula is straightforward: activate a VPN on public networks, use unique strong passwords stored in a password manager, enable two-factor authentication on critical accounts, maintain awareness of phishing patterns, and monitor your accounts for unauthorized activity. This multi-layered approach isn't perfect—no security practice is—but it eliminates the overwhelming majority of compromise vectors that peak during holidays.
Experts consistently emphasize that perfect security doesn't exist, but practical security—good habits combined with appropriate tools—is entirely achievable. You don't need to become a security expert. You need to implement a few specific practices consistently.
The psychological shift matters as much as the technical implementation. Rather than viewing security as burdensome additional work, reframe it as protecting your financial accounts and personal data from people actively trying to steal from you. This mindset shift makes security practices feel necessary rather than inconvenient.
As you head into the holiday season, remember that cybercriminals are counting on distraction and habit. They're counting on you forgetting to activate your VPN. They're counting on phishing emails reaching you at the precise moment you're stressed about holiday planning. They're counting on password reuse and account takeover opportunities created by years of convenience-focused password habits.
But if you've implemented the protections outlined in this guide, you've eliminated the low-hanging security fruit that 95% of compromises target. This positions you among the secured minority while the vast majority of holiday shoppers remain vulnerable.
Your holiday security ultimately comes down to specific behavioral choices: which networks you trust, which passwords you create, which accounts have two-factor authentication, which emails you verify before clicking, and which financial accounts you monitor. Make these choices consciously, implement them before traveling, and maintain them throughout the holiday season.
The holidays should be about enjoying time with family and managing holiday shopping, not recovering from fraud and account compromise. Implement these protections now, verify they're working before your travel and shopping intensifies, and you've done what expertise recommends. Stay safe this holiday season.

Key Takeaways
- Cybercriminals intensify attacks during holidays when people are distracted, traveling, and making more financial transactions
- VPNs protect against public Wi-Fi interception but don't prevent phishing, malware, or password reuse—multi-layered security is essential
- Unique passwords stored in a password manager eliminate account compromise from credential reuse, the most common attack vector
- Two-factor authentication on email, payment, and shopping accounts prevents account takeover even if passwords are compromised
- Phishing emails use holiday-themed urgency to manipulate people; verification through direct contact prevents 88% of breach-initiating attacks
- Travel security requires device encryption, avoiding public charging stations, disabling auto Wi-Fi connection, and consistent VPN usage
- Holiday fraud attempts spike 300% at retailers; careful URL verification and payment method selection prevent fraudulent transactions
- Post-transaction verification and credit card statement monitoring catch fraud early, reducing damage from undetected compromise
Related Articles
- How to Explain VPN Importance to Your Parents: 2025 Guide
- Best VPN Deals 2025: Save Up to 88% on Premium Services [2025]
- Aflac Data Breach: 22.6 Million Exposed [2025]
- Holiday Email Scams 2025: How to Spot and Stop Them [Updated]
- Beyond WireGuard: The Next Generation VPN Protocols [2025]
- VPN Innovations That Surprised Everyone in 2025
![Holiday VPN Security Guide: Expert Tips for Safe Festive Season [2025]](https://tryrunable.com/blog/holiday-vpn-security-guide-expert-tips-for-safe-festive-seas/image-1-1766903751090.jpg)



