Infostealer Malware Now Targets Mac as Threats Expand Beyond Windows [2025]
The security landscape just shifted. For years, cybercriminals focused relentlessly on Windows systems. It made sense logically, economically, and strategically. But that's changed. And honestly, it's caught a lot of people off guard.
Mac OS users thought they were safer. Turns out, they weren't.
Recent threat intelligence from major security vendors reveals something uncomfortable: the malware ecosystem targeting Apple devices has grown to rival—and in some cases, exceed—traditional Windows-focused campaigns. We're not talking about theoretical risks or niche vulnerabilities anymore. This is active, ongoing, sophisticated, and expanding rapidly across the globe.
What makes this shift particularly alarming is the mechanism. Attackers aren't using complex zero-day exploits. They're using the oldest trick in the book: social engineering. Fake software, compromised advertising networks, weaponized legitimate tools. They're using psychology before code.
The variants matter too. Digit Stealer, Mac Sync, and Atomic mac OS Stealer (AMOS) aren't just crude password grabbers. They're targeting browser sessions, cloud tokens, developer credentials, and keystroke logs. They're stealing the keys to everything—not just the front door, but the master access to your digital life.
Here's what you need to know about this threat, why it's happening now, and what actually works to defend against it.
TL; DR
- The shift is real: Infostealer malware targeting mac OS has expanded dramatically, rivaling Windows-focused campaigns in sophistication and scale
- Top variants emerge: Digit Stealer, Mac Sync, and AMOS represent a new generation of mac OS threats designed to steal credentials, cloud tokens, and developer secrets
- Social engineering wins: Attackers use Click Fix scams, fake software, and malicious ads rather than technical exploits to deliver malware
- Cross-platform risk: Python-based malware accelerates threat adaptation across both Windows and mac OS environments simultaneously
- Defense requires vigilance: Employee education, network monitoring, EDR deployment, and cloud-delivered protection provide the strongest mitigation strategies
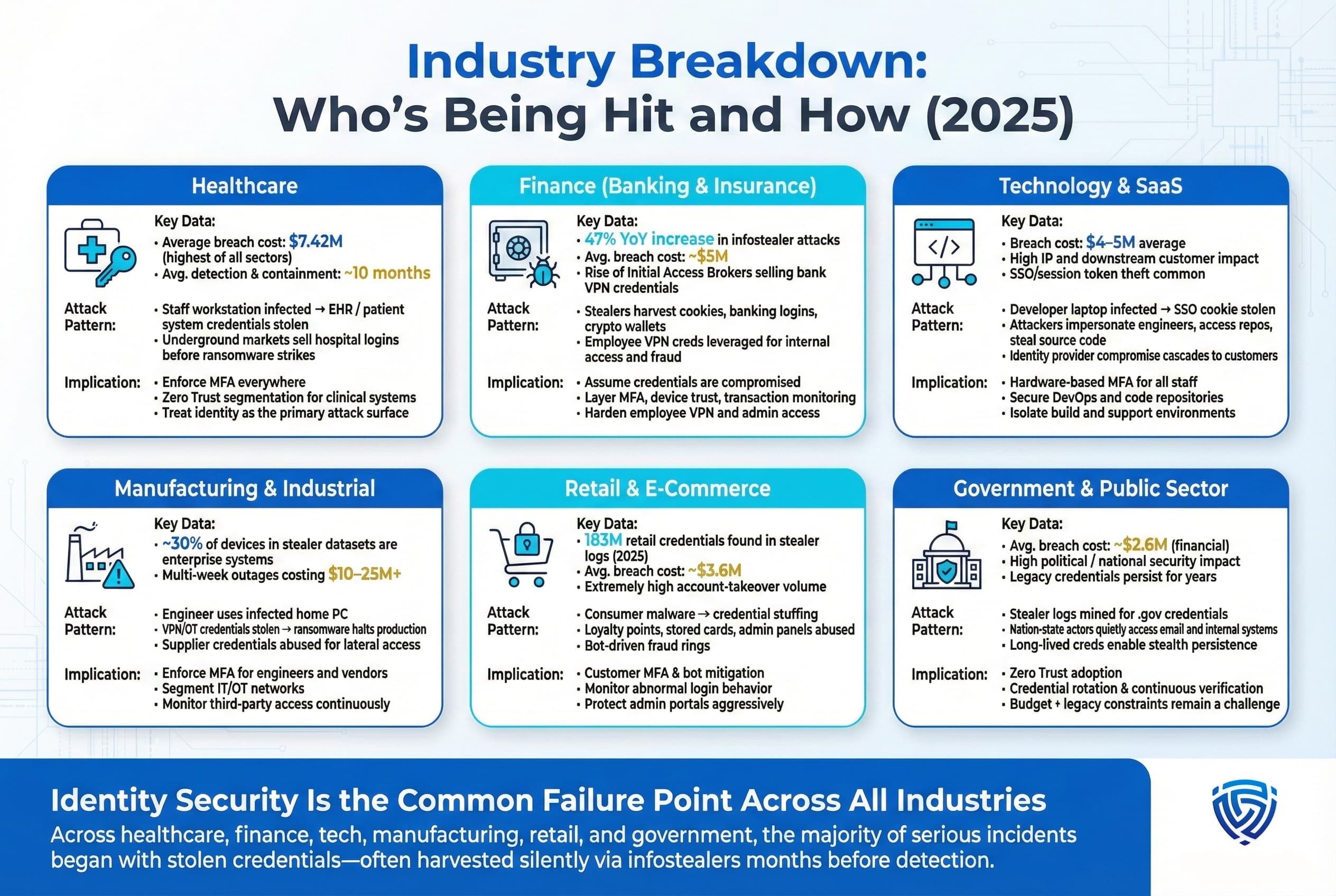
The End of the Windows-Only Era
For nearly three decades, Windows dominated the malware landscape. When you thought of cybercrime, you thought of Windows security. The math was simple: Windows had massive market share, lower security barriers, and a proven infrastructure for malware distribution.
Mac OS represented maybe 15-20% of desktop users, and the common wisdom held that Apple's closed ecosystem, code signing requirements, and reputation for security made it a harder target. Why would a criminal spend weeks developing mac OS malware when they could spend an hour modifying existing Windows malware and hitting millions of targets?
But the economics shifted.
Mac users—particularly those in technology, finance, and creative industries—tend to have higher account values. A compromised developer's credentials don't just expose their personal email. They expose entire CI/CD pipelines, Git repositories, cloud infrastructure keys, and production environments. A stolen token from a finance professional could grant access to wire transfer systems, accounting software, and banking platforms.
The return on investment changed.
Additionally, mac OS users became complacent. After years of relative safety, the security posture atrophied. Companies stopped enforcing strict security policies on Mac devices. Employees installed software from less trustworthy sources. The psychological shield—the belief that "Macs don't get viruses"—became a liability rather than an asset.
Now, attackers have noticed.
What we're seeing in 2025 is the natural evolution of the threat landscape. As Windows security hardened (better built-in antivirus, EDR adoption, code signing enforcement), criminals diversified. They're following the money and the path of least resistance.
The result? A mac OS threat ecosystem that's no longer an afterthought. It's a primary target.
The Three Dominant mac OS Infostealer Variants
Security researchers have identified three major infostealer families that dominate mac OS exploitation campaigns. Understanding what each one does—and how it operates—helps clarify why they're so dangerous.
Digit Stealer: The Credential Hunter
Digit Stealer represents one of the first truly sophisticated mac OS infostealers designed with Mac-specific targets in mind. Unlike early malware that simply ported Windows code to mac OS, Digit Stealer was built by people who understood the mac OS ecosystem intimately.
The malware focuses on extracting:
- Browser credentials: Passwords stored in Safari, Chrome, Brave, and other browsers
- Keychain data: Stored passwords, SSH keys, and authentication tokens
- Cookie files: Session cookies that can be replayed to bypass authentication
- Auto-fill information: Credit card data, addresses, and personal information stored in browser profiles
- Email credentials: IMAP, SMTP, and OAuth tokens from Mail.app and other clients
What makes Digit Stealer particularly effective is its precision. It doesn't just dump the entire keychain. It extracts specific high-value targets with surgical accuracy. Developers get their Git Hub tokens stolen. Security professionals have their AWS credentials exfiltrated. Finance workers lose access to banking systems.
The distribution method varies, but the most common vector involves fake software—often positioned as productivity tools, browser extensions, or utility applications. A user downloads what they think is a legitimate PDF editor or screen recording tool, and instead gets Digit Stealer bundled into the installer.
Mac Sync: The Persistence Specialist
Mac Sync takes a different approach. Rather than focusing purely on credential theft, Mac Sync emphasizes persistence and expansion. Once installed, Mac Sync works to establish long-term presence on the system.
The malware typically performs these actions:
- Persistence establishment: Creates scheduled tasks, login items, or launch daemons to survive reboots
- Lateral movement preparation: Enumerates network shares, connected devices, and accessible systems
- Privilege escalation attempts: Tries to gain administrative access through various techniques
- Secondary payload delivery: Opens the door for additional malware, ransomware, or remote access tools
- Data exfiltration: Systematically uploads sensitive files to attacker-controlled servers
Mac Sync represents a shift in malware philosophy on mac OS. Early threats were quick hit-and-run operations: grab the credentials, exfiltrate, disappear. Mac Sync is designed for long-term occupancy.
This creates problems for defense. A user might find and remove Digit Stealer relatively quickly. Mac Sync, by design, hides better, communicates more subtly, and re-installs itself if removed carelessly.
The distribution vectors include compromised websites, trojanized applications, and malicious advertisements. In several documented cases, attackers compromised legitimate Mac software update servers and used them to distribute Mac Sync to users expecting security patches. The irony is brutal.
AMOS (Atomic mac OS Stealer): The All-in-One Threat
AMOS is perhaps the most comprehensive threat. It combines credential theft, persistence, information gathering, and lateral movement into a single package. Security researchers often call it the "full-featured" infostealer because it does everything.
AMOS capabilities include:
- Complete credential extraction: Browsers, email, cloud services, messaging apps, crypto wallets
- System information gathering: Hardware specs, network configuration, installed software inventory
- File system enumeration: Searches for sensitive files, documents, and database files
- Process monitoring: Watches running applications and reports back to operators
- Network reconnaissance: Maps available network resources and accessible shares
- Cryptocurrency wallet targeting: Specifically searches for and extracts wallet files and seed phrases
- Two-factor authentication bypass: Attempts to exfiltrate backup codes and recovery keys
What distinguishes AMOS is its modular design. Operators can customize what each infected system steals. A developer's machine gets asked for Git credentials and SSH keys. A finance worker's machine gets targeted for banking data. A cryptocurrency enthusiast gets their wallet extracted.
AMOS is available for purchase on underground forums. This means the barrier to entry for running AMOS campaigns is remarkably low. You don't need to be technically sophisticated to deploy it. You just need money and delivery capability.
The pricing is astonishing. A single AMOS license runs somewhere between $100-500. Infection campaigns can generate that investment back in stolen cryptocurrency alone within hours.
How Attackers Actually Deliver This Malware
Here's the disappointing truth: most people get infected through methods that no technical security control can stop. The vulnerability isn't in mac OS. It's in human judgment.
Click Fix: The Deception That Works
Click Fix is brutally simple, yet remarkably effective. An attacker buys display advertising on a popular website. When someone visits, they see a fake system warning pop-up.
The warning looks official. It has Apple's logo. It says something like "Your Mac is at risk" or "Update required immediately." It's terrifying. And it's designed to be.
The victim clicks the warning. They're taken to a download page for a "Mac Security Tool" or "System Update." They download it. They run it. And within seconds, malware is installed.
What makes Click Fix so effective is psychological. Fear overrides caution. The sense of urgency—the false warning, the official-looking interface—triggers panic. The victim doesn't think. They just act.
Security vendors have reported Click Fix campaigns reaching hundreds of thousands of impressions daily. The cost to run these campaigns is minimal. The conversion rate is surprisingly high. If even 2% of people who see the fake warning actually download and install the malware, that's still enormous scale.
Malicious Advertising Networks
Attackers are running sophisticated ad campaigns on legitimate platforms like Google Ads. The ads promote fake versions of popular software.
Example real-world scenario: Someone searches for "PDF editor Mac." They see an advertisement for a "PDF Editor Pro" tool. The ad looks legitimate. It has a legitimate-looking website. Customer reviews. Pricing information.
The victim downloads it. Installs it. Moments later, Digit Stealer or AMOS is running in the background, harvesting credentials.
Google and other ad platforms do implement protections against malicious ads. But the cat-and-mouse game never stops. Attackers constantly create new domains, new ad accounts, new variations. By the time ads are removed, millions of impressions have occurred.
Compromised Software Distribution Channels
In several documented attacks, malware was distributed through legitimate channels that attackers compromised:
- Unofficial mirrors of popular applications
- Compromised developer websites
- Trojanized versions of legitimate software posted on forums
- Malicious updates to outdated applications
- Compromised podcasting apps, download managers, and utility software
The most insidious variant: attackers compromise a legitimate mac OS application's build or distribution infrastructure, then release updates that include malware. Users who trust the developer and install automatic updates get infected without realizing it.
Weaponized Legitimate Tools
Some of the most sophisticated distribution methods don't involve new malware at all. Instead, attackers compromise legitimate services and use them to distribute payloads.
Documented examples include:
- Whats App compromise: Attackers gain access to someone's Whats App account, then send malware links to their entire contact list with messages like "Check out this app" or "You need to see this video."
- Social media accounts: Compromised Facebook, Instagram, or Twitter accounts spread malicious links to networks of friends and followers
- Legitimate file sharing: Files hosted on Google Drive, Dropbox, or i Cloud, then shared with social engineering tactics ("I found these templates you wanted...")
These methods work because they bypass technical security controls. The message comes from someone the victim trusts. The delivery mechanism is legitimate. The victim's guard is down.

Organizations with monthly security training experience significantly fewer successful phishing attacks, with an estimated 30% success rate compared to 90% for those with no training. Estimated data.
The Cross-Platform Acceleration Problem
Here's where things get more complex. Modern infostealer malware increasingly runs on multiple platforms simultaneously.
Python-based malware is a game changer for attackers. Why? Because Python code runs on Windows, mac OS, and Linux with minimal modifications. An attacker develops malware once, in Python, and suddenly it targets three operating systems.
This is fundamentally different from the old model where attackers wrote separate malware variants for each platform. That took time, money, and expertise. The cross-platform approach dramatically lowers barriers to entry.
What we're seeing is malware development becoming more efficient. Attackers spend less time on platform-specific code and more time on stealing tactics, evasion, and persistence. They iterate faster. They adapt quicker.
The second-order effect is terrifying: if a new exploitation technique is discovered on Windows, attackers port it to mac OS within weeks. Security researchers have to maintain expertise across multiple platforms. Defense becomes exponentially more complex.
For enterprises, this means a single APT group can now compromise both your Windows and mac OS infrastructure simultaneously. The lateral movement possibilities expand dramatically. Your secure Mac device sitting next to a compromised Windows laptop? That's no longer comfortable.

What Attackers Actually Want to Steal
Infostealers don't just grab passwords randomly. They're targeting specific high-value data. Understanding what they're after helps clarify the real risk.
Browser Sessions and Cookies
When someone logs into their bank's website, they receive a session cookie. That cookie proves to the bank's server that they're authenticated. Normally, the cookie expires after a certain period.
But attackers don't care about expiration. They steal the cookie immediately. Then they can access that person's banking system, transfer funds, and disappear.
The same principle applies to email, cloud storage, social media, and cryptocurrency exchanges. A stolen session cookie is often as valuable as a password—sometimes more valuable, because it bypasses multi-factor authentication.
Cloud and API Tokens
Developers and Dev Ops professionals often have tokens stored on their systems. AWS access keys. Git Hub personal access tokens. Slack API tokens. Database passwords.
These tokens are the master keys to infrastructure. A stolen AWS token could allow an attacker to:
- Access all stored data in S3 buckets
- Spin up expensive computing resources
- Modify or delete critical infrastructure
- Extract environment variables containing other secrets
- Pivot to connected cloud services
A single developer's token can be worth thousands of dollars in terms of attack capability.
Developer Credentials
For companies in the software space, developer compromises are particularly catastrophic. A stolen Git Hub token, combined with SSH keys, gives attackers:
- Access to code repositories
- Ability to commit malicious code
- Access to CI/CD pipelines
- Ability to modify production deployments
- Access to secrets stored in repositories
This enables supply chain attacks. Malicious code committed to a popular open-source project can affect millions of downstream users. It's not just the individual developer that's compromised—it's everyone who relies on their work.
Cryptocurrency Wallets and Keys
AMOS specifically targets cryptocurrency. It searches for wallet files, seed phrases, and private keys. If found, the attacker gains direct access to all funds in those wallets.
Unlike a stolen bank account (which can be recovered), cryptocurrency theft is typically permanent. The blockchain is immutable. Once coins are transferred to an attacker's wallet, they're gone.
The scale is staggering. A single developer with Bitcoin holdings could have thousands of dollars extracted instantly.
Business Email Compromise
Email is the nervous system of most businesses. A compromised executive's email account enables:
- Impersonation of that executive
- Interception of sensitive communications
- Fake wire transfer requests
- Manipulation of business processes
- Lateral movement to other accounts
Attackers use compromised email to execute Business Email Compromise (BEC) scams, where they request wire transfers from finance departments, posing as executives. These attacks generate millions of dollars annually.

Defense Framework: What Actually Works
Now, the practical part. If you're responsible for security—whether for yourself, a small business, or an enterprise—here's what actually provides protection against these threats.
Employee Education as Foundational Defense
No technical control stops someone from downloading malware voluntarily. Education is the first line of defense.
Effective security training includes:
- Recognizing Click Fix scams: Teaching people that system warnings from ads are never real. Apple, Microsoft, and other vendors never warn you through display ads.
- Identifying suspicious downloads: Training on how legitimate software distributions work, where to find official downloads, how to verify authenticity
- Email phishing recognition: Teaching people to spot impersonation, urgent language, suspicious links, and requests for credentials
- Credential hygiene: Explaining why sharing passwords is dangerous, why unique passwords matter, how password managers work
- Reporting procedures: Making it easy to report suspicious activity without shame or penalty
The most effective training is frequent and specific. Annual security training is pointless. Monthly reminders about actual threats—with specific examples from recent attacks—actually change behavior.
Behavioral Monitoring: Detecting the Suspicious
Even with education, some people will get infected. The question becomes: how quickly can you detect and respond?
Terminal activity monitoring is crucial on mac OS. Infostealers typically need to run various commands to extract data. Monitoring for unusual terminal execution can catch infections early.
Suspicious patterns include:
- Unexpected script execution
- Commands accessing sensitive directories
- SSH key enumeration
- Credential file access
- Network traffic to unusual destinations
- Process spawning outside normal patterns
Network monitoring catches the exfiltration phase. Even if malware runs successfully, it needs to send stolen data somewhere. Monitoring for POST requests to newly registered domains, unusual geographic connection patterns, or high-volume data transfers can identify infections.
Tools that perform this monitoring include:
- EDR (Endpoint Detection and Response) solutions
- Network intrusion detection systems
- DNS monitoring and filtering
- Firewall log analysis
- Cloud-native security services
Endpoint Detection and Response (EDR)
EDR is now the industry standard for comprehensive endpoint security. Rather than relying on signature-based detection (which is useless against new malware), EDR uses behavioral analysis and machine learning to identify suspicious activity.
EDR systems:
- Monitor process execution: Track what programs run, what they do, and what they communicate with
- Analyze system calls: Detect when software tries to do something suspicious at the kernel level
- Learn normal behavior: Establish baselines for each system, then flag deviations
- Enable rapid response: When suspicious activity is detected, EDR can block execution, isolate systems, or quarantine files
- Provide forensics: Complete audit trails of what happened during an infection
Running EDR in "block mode" means it automatically responds to threats rather than just alerting. This requires careful tuning to avoid false positives, but it dramatically improves response time.
Cloud-Delivered Protection and Machine Learning
Cloud-based security services have advantages over traditional endpoint antivirus:
- Instant global threat intelligence: When a new malware variant is detected anywhere, the protection updates globally within minutes
- Behavioral analysis at scale: Machine learning models trained on billions of files can identify suspicious behavior in new malware
- No performance impact: Processing happens in the cloud, not on your device
- Zero-day protection: Models can identify suspicious behavior even in completely new malware variants
Major security vendors now offer cloud-delivered protection as a core component of their offerings.
Credential Management Infrastructure
Even if malware steals credentials, you can limit the damage:
- Enforce multi-factor authentication: Even with stolen passwords, attackers can't access accounts protected by MFA
- Use temporary credentials and tokens: For services like AWS, use temporary credentials with explicit expiration times
- Rotate credentials regularly: If a credential is compromised, regular rotation limits how long it's useful
- Monitor for credential misuse: Track failed login attempts, unusual access patterns, and access from unexpected locations
- Separate credentials by purpose: Don't reuse the same password across multiple services
Account Access Controls and Monitoring
For critical accounts (email, cloud infrastructure, financial systems):
- IP allow-listing: Only allow access from known geographic locations or networks
- Unusual access alerts: Monitor for login attempts at odd times, from unfamiliar locations, or in unusual patterns
- Session management: Enforce session timeouts and require re-authentication for sensitive operations
- Audit logging: Maintain comprehensive logs of who accessed what, when, and from where
Organizational Implementation Strategy
For businesses deploying these defenses, a phased approach works best.
Phase 1: Visibility and Assessment (Weeks 1-2)
Before you can defend against threats, you need to understand your current state:
- Asset inventory: Document all devices, especially Macs. Know what exists before you protect it
- Credential audit: Understand where sensitive credentials are stored. Are developers using password managers? Are there hardcoded credentials?
- Software audit: Identify installed applications, update status, and potential risks
- Network documentation: Map network segments, external connections, and data flows
Phase 2: Foundation Building (Weeks 3-6)
Establish fundamental security controls:
- Deploy endpoint protection: Install antivirus/EDR across all systems
- Enable MFA: Enforce multi-factor authentication on all critical accounts
- Implement credential management: Deploy password managers organization-wide
- Establish baseline monitoring: Begin collecting data on normal system behavior
Phase 3: Detection and Response (Weeks 7-12)
Add layers that detect and respond to threats:
- Configure EDR alerting: Set up rules to identify suspicious behavior
- Implement response procedures: Define what happens when malware is detected
- Train incident response team: Ensure people know how to respond to alerts
- Deploy network monitoring: Monitor for suspicious outbound communications
Phase 4: Hardening and Optimization (Weeks 13+)
Continuously improve and adapt:
- Tune detection rules: Reduce false positives, improve accuracy
- Update threat intelligence: Keep up with new malware variants and attack techniques
- Regular testing: Conduct red team exercises and penetration tests
- Security culture: Evolve from compliance-based to security-aware culture

Specific mac OS Security Hardening
Beyond general endpoint security, mac OS has specific features worth leveraging.
System Integrity Protection (SIP)
SIP prevents even administrator-level processes from modifying critical system files. This limits malware's ability to establish persistence.
SIP is enabled by default on modern Macs, but disabling it is common for legitimate reasons (development, testing, legacy software). If SIP is disabled, you're accepting significantly higher risk.
Gatekeeper and Code Signing
Gatekeeper verifies that applications are signed by trusted developers. Code signing provides confidence that an app hasn't been modified since the developer released it.
Enforce the strictest Gatekeeper setting: "App Store and identified developers only." This blocks unsigned applications.
XProtect and Malware Removal Tool
XProtect is Apple's built-in malware detection. It's not perfect—it uses signature-based detection and misses new threats—but it's better than nothing.
The Malware Removal Tool (MRT) complements XProtect by removing known malware families.
Neither replaces third-party security software, but they provide baseline protection.
Firewall Configuration
mac OS includes a stateful firewall that can block incoming connections. Configure it to:
- Block incoming connections by default
- Allow only necessary services
- Log connection attempts
Secure Enclave and Encrypted Storage
Modern Macs include encrypted storage (File Vault) and secure processing (Secure Enclave). Enabling File Vault means that even if a device is stolen, data is protected.
Firmware Security
Macs include firmware protections that prevent malware from modifying the boot process. These features are enabled by default but require regular firmware updates to remain effective.

Timeline and Threat Evolution
Understanding how this threat landscape evolved helps contextualize current risks.
In 2020, mac OS infostealers were rare. Most malware targeting Macs was generic or ported from Windows with minimal optimization.
By 2022, dedicated mac OS infostealers began appearing. Digit Stealer and variants emerged, specifically designed for mac OS. Attackers were investing resources in Mac-specific code.
In 2023-2024, the landscape accelerated. AMOS emerged as a sophisticated, fully-featured threat. Distribution methods improved dramatically. Cross-platform malware became more common.
Looking at 2025 projections: expect further specialization. Attackers will likely develop malware targeting specific industries or roles. We'll see malware targeting security professionals differently than general users. Cryptocurrency-focused variants will proliferate.
The trajectory is clear: mac OS is no longer a secondary target. It's a primary focus.
Recovery and Incident Response
If you discover that a device has been infected with an infostealer, here's what needs to happen:
Immediate Actions (First Hour)
- Isolate the device: Disconnect from Wi-Fi and network. This prevents further data exfiltration.
- Preserve evidence: Don't restart or shut down. Forensics requires capturing the malware in memory.
- Notify security team: Alert your security or IT team immediately. This is not a self-service recovery.
- Change critical passwords: From another device, immediately change passwords for email, banking, and critical cloud services.
- Enable MFA: If not already enabled, immediately enable multi-factor authentication on critical accounts.
Short-term Actions (First 24 Hours)
- Full device wipe: Erase the infected Mac and restore from a known-clean backup (or clean installation)
- Credential audit: Change passwords for all services accessed from that device
- Monitor for unauthorized access: Watch email, bank accounts, cloud services for suspicious activity
- Review account activity logs: Check if attackers accessed systems after infection
- Notify relevant parties: If a developer device was compromised, notify the Dev Ops team about potential supply chain risks
Long-term Actions (First Month)
- Forensic analysis: Have security experts analyze the malware to understand exactly what was stolen
- Credential rotation: Rotate all tokens and API keys that might have been exposed
- Infrastructure review: For developer devices, review code commits and deployments during the infection period
- Threat hunting: Check other devices for similar infections
- Process improvements: Update security processes to prevent similar infections
Compliance and Regulatory Considerations
For regulated industries, infostealer infections create compliance headaches.
HIPAA (healthcare): Credential theft enables unauthorized access to patient records, triggering breach notification requirements.
PCI-DSS (payment processing): Stolen payment credentials or access to payment systems requires comprehensive incident response and forensics.
GDPR (European privacy): Data theft that includes personal information triggers notification obligations within 72 hours.
SOC 2 (service providers): Many service provider contracts require evidence of robust security controls. Infections demonstrate control failures.
Organizations in regulated industries need incident response plans that address regulatory obligations, not just technical recovery.
The Competitive Advantage of Proactive Security
While this threat landscape is genuinely concerning, organizations that take proactive steps gain significant advantages.
Competitors that lag on security spend incident response budget. Proactive organizations spend on prevention. Prevention is cheaper, faster, and less disruptive.
Proactive security also provides business confidence. When customers know that you take security seriously—that you monitor for threats, educate employees, and maintain strong controls—they're more likely to trust you with sensitive data.
For developers, a compromised device could cost your career. A single stolen Git Hub token could result in your commits appearing to include malicious code. An employer might question your judgment. Clients might distance themselves.
Proactive personal security is career insurance.
Industry Trends and Future Threats
Where is this threat landscape heading?
Increased targeting of remote work infrastructure: As VPN, SSH, and remote access tools become standard, attackers will focus more on extracting credentials that grant remote access. A stolen VPN credential could give attackers months of undetected access.
Supply chain focus: We'll see more attacks targeting developers and development infrastructure. One compromised developer affects thousands of downstream users.
AI-powered malware: Machine learning will enable malware to adapt in real-time. Malware that learns your typing patterns and exfiltrates data when defenses are lowest. Malware that communicates using your normal traffic patterns to avoid detection.
Increased cryptocurrency targeting: As cryptocurrency becomes more mainstream, expect sophisticated attacks targeting crypto wallets and exchanges.
mac OS ecosystem expansion: As enterprises adopt more Macs, attackers will invest proportionally more. The threat won't plateau until mac OS security reaches parity with hardened Windows infrastructure.
The key insight: the threat landscape is dynamic. Static defenses fail. Successful defense requires continuous assessment, adaptation, and learning.
FAQ
What is an infostealer?
An infostealer is malware specifically designed to extract sensitive information from a compromised device without necessarily disrupting the system's operation. Rather than encrypting files (ransomware) or destroying data, infostealers silently harvest credentials, browser sessions, tokens, and files, then send them to attacker-controlled servers. What makes infostealers particularly dangerous is that victims often don't realize they're infected until significant damage has occurred.
How does malware like Digit Stealer, Mac Sync, and AMOS actually work?
These malware variants typically use different mechanisms. Digit Stealer focuses on extracting credentials from browsers and system keystores with surgical precision. Mac Sync emphasizes establishing long-term persistence on a system and creating backdoors for future access. AMOS combines both approaches, adding specialized targeting for cryptocurrency wallets, developer credentials, and cloud tokens. All three work by running in the background, hiding from the user's view, and periodically exfiltrating stolen data to attacker infrastructure.
Why are mac OS devices suddenly being targeted more heavily?
Mac OS users in technology, finance, and creative industries have high-value credentials and access. A stolen developer's Git Hub token or an architect's AWS access key is worth thousands of dollars in terms of attack capability. Additionally, mac OS users historically had lower security vigilance—the belief that "Macs don't get viruses" led to weaker defenses. As Windows security hardened, attackers diversified to softer targets.
How do attackers deliver this malware to mac OS devices?
Attackers use several methods: Click Fix scams with fake system warnings, malicious advertisements promoting fake software, compromised software distribution channels, and weaponized legitimate tools like Whats App. The most successful methods exploit psychology rather than technical vulnerabilities—they create urgency and fear that makes users act without thinking. This means technical security controls alone can't stop malware delivery; user awareness is essential.
What specific data do these infostealers target and steal?
Infostealers target high-value data: browser credentials and session cookies (which bypass authentication), cloud and API tokens (which provide infrastructure access), developer credentials like Git Hub tokens and SSH keys (which enable code compromise), cryptocurrency wallet files and seed phrases (which grant direct access to funds), and business email credentials (which enable fraud and lateral movement). A single compromised credential can lead to account takeovers, supply chain attacks, or direct financial loss.
What's the most effective defense against infostealer malware?
No single defense works alone. A layered approach is necessary: employee education to prevent infection in the first place, multi-factor authentication to limit damage even if credentials are stolen, endpoint detection and response (EDR) to identify infections quickly, credential rotation to limit exposure windows, and cloud-delivered security with machine learning to catch new malware variants. For organizations, implementing EDR in block mode provides the strongest automated response capability.
How can I tell if my Mac is infected with an infostealer?
Infostealers are designed to hide. Users rarely notice obvious symptoms. The best approach is to watch for behavioral anomalies: unexpected fans running continuously (indicating background processing), battery draining faster than normal, network activity when you're not using the system, or unexpected prompts for credentials you've already provided. For businesses, detection requires monitoring systems: watching for unusual Terminal execution, suspicious network connections, or unexpected process creation.
What should I do immediately if I discover my Mac is infected?
First, disconnect your device from Wi-Fi and network—this prevents further data exfiltration. From another device, immediately change passwords for email, banking, and critical cloud services, and enable multi-factor authentication. Then contact your security team or an IT professional before restarting the device; shutting down disrupts forensics. Don't attempt self-recovery; a professional should wipe and rebuild the system from a known-clean state.
How does cross-platform malware written in Python change the threat landscape?
Python-based malware can run on Windows, mac OS, and Linux with minimal modifications. This means attackers develop once and attack three platforms simultaneously, dramatically reducing development costs and time. Security researchers must maintain expertise across multiple platforms. Organizations face the risk of comprehensive compromise where Windows and Mac devices in the same company are attacked by the same malware campaigns, enabling sophisticated lateral movement.
Are there mac OS-specific security features that help protect against infostealers?
Yes, several built-in mac OS features help. System Integrity Protection (SIP) prevents even administrator-level processes from modifying critical system files, limiting persistence mechanisms. Gatekeeper and code signing verification prevent execution of unsigned, untrusted applications. XProtect provides built-in malware detection. File Vault encryption protects data even if the device is stolen. Enabling all these features by default provides baseline protection, though they should be complemented by third-party EDR and security software.
How frequently should organizations update their mac OS security posture in response to this threat landscape?
Given the rapidly accelerating threat landscape, security reassessments should occur at least quarterly. At minimum, annual reviews are necessary. Organizations that haven't updated Mac security strategies since 2022 are operating under outdated threat models. The threat landscape has evolved dramatically, with dedicated mac OS malware families, sophisticated distribution methods, and cross-platform campaigns now standard.
Conclusion
The era when mac OS users could assume relative safety is over. In 2025, infostealer malware targeting Apple devices is no longer theoretical or niche. It's active, sophisticated, and expanding. Organizations and individuals that continue operating under the assumption that Macs are inherently safer are accepting unnecessary risk.
The threat landscape didn't change because mac OS became less secure. mac OS is arguably as secure as it ever was. The landscape changed because attackers discovered an opportunity. mac OS users were complacent. The return on investment shifted. The economics of targeting Macs became favorable.
But here's the encouraging part: defense is achievable. It's not mysterious. It doesn't require exotic technology or security expertise beyond what's available today.
Educate your team about Click Fix scams and phishing. Deploy endpoint protection and EDR. Enable multi-factor authentication. Monitor for suspicious activity. Rotate credentials. These are all standard practices, available through standard tools.
The organizations and individuals that implement these defenses will be fine. The ones that don't will eventually be compromised. It's not a matter of if—it's a matter of when.
Start now. Not after your next incident. Not during a compliance audit. Now. Assess your current security posture. Identify gaps. Prioritize the highest-impact mitigations. Implement them.
Your credentials, your data, and potentially your career depend on it. Don't wait until you discover that your system is infected. Don't wait until you're receiving notifications of unauthorized access to your accounts. Don't wait until attackers have already weaponized your developer credentials or stolen your cryptocurrency.
The threat is real. The defense is available. The choice is yours.
Key Takeaways
- Infostealer malware targeting macOS has expanded dramatically and now rivals Windows-focused campaigns in sophistication and scale
- DigitStealer, MacSync, and AMOS represent the dominant threat variants, each with specialized capabilities for credential and data extraction
- Social engineering through ClickFix scams and malicious advertisements remains the primary infection vector, not technical vulnerabilities
- Python-based cross-platform malware allows attackers to simultaneously target Windows and macOS infrastructure with minimal code modification
- Layered defense combining employee education, MFA, EDR deployment, and behavioral monitoring provides the strongest protection against infostealer threats
- Organizations should implement immediate EDR rollout and continuous credential rotation to detect and mitigate infostealer infections within hours rather than weeks
Related Articles
- ShinyHunters SSO Scams: How Vishing & Phishing Attacks Work [2025]
- OpenClaw AI Assistant Security Threats: How Hackers Exploit Skills to Steal Data [2025]
- Office 365 Zero-Day Exploit: What You Need to Know [2025]
- Claude Code Outage: What Happened and Why AI Tool Reliability Matters [2025]
- Notepad++ Supply Chain Attack: Chinese State Hackers Explained [2025]
- Notepad++ Supply Chain Attack: What You Need to Know [2025]
![Infostealer Malware Now Targets Mac as Threats Expand [2025]](https://tryrunable.com/blog/infostealer-malware-now-targets-mac-as-threats-expand-2025/image-1-1770223002391.jpg)



