Office 365 Zero-Day Exploit: What You Need to Know [2025]
Introduction: A Critical Moment for Office Security
Here's what happened in late January 2025: Microsoft released an emergency patch for a serious vulnerability in Office 365. Three days later—just 72 hours—Ukrainian government agencies started getting hit with sophisticated phishing emails weaponizing that exact flaw. The attackers? Russian state-sponsored hackers known as APT28, also called Fancy Bear.
This isn't theoretical. This isn't "might happen someday." This is happening right now, and if your organization uses Microsoft Office, you need to understand what's going on.
The vulnerability in question is CVE-2026-21509, a high-severity flaw that lets attackers bypass Office security features locally. A severity score of 7.6 out of 10 doesn't sound like the worst thing ever until you realize that's high enough to get on every security team's emergency list. The real kicker: the attackers had already figured out how to exploit it before the patch even existed. That's what "zero-day" means. The company had zero days to prepare.
What makes this particularly frightening is the speed. Most zero-days stay hidden for months or even years. Attackers usually keep them quiet because the longer they stay secret, the longer they can use them. But APT28 burned through this one in 72 hours. That tells you either they found a better exploit, or they're confident enough in their capabilities that they don't care who knows about it. Neither option is reassuring.
We're going to walk through everything you need to know: what the vulnerability actually is, how the attacks work, who's behind it, and most importantly, what you need to do right now to protect yourself. This isn't clickbait security theater. This is the real threat landscape in 2025.

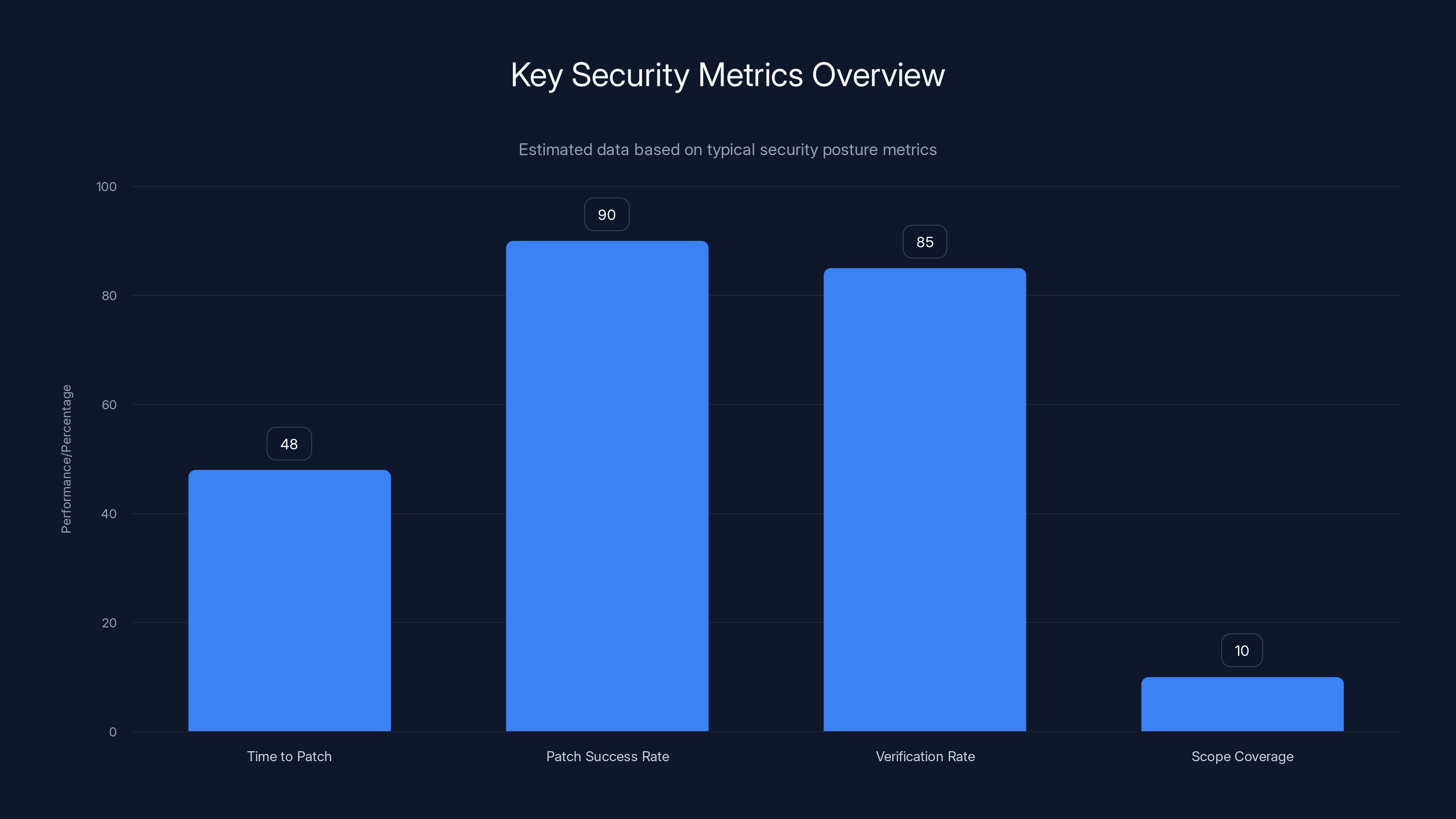
Estimated data shows typical performance in patching metrics, highlighting areas for improvement in scope coverage and verification rate. Estimated data.
TL; DR
- Critical Office vulnerability: CVE-2026-21509 allows attackers to bypass Microsoft Office security features with a severity rating of 7.6/10
- Active exploitation: Russian state actor APT28 deployed this zero-day against Ukrainian government agencies just 3 days after patch release
- Attack method: Malicious Word documents disguised as legitimate government communications via phishing
- Immediate action required: Update Office 2016, 2019, LTSC 2021, LTSC 2024, and Microsoft 365 Apps immediately
- No patch alternative: If you can't patch immediately, apply Windows Registry mitigation steps provided by Microsoft
The Vulnerability Explained: CVE-2026-21509
What Makes This Vulnerability Dangerous
Let's break down what CVE-2026-21509 actually does. The official description calls it "reliance on untrusted inputs in a security decision vulnerability." That corporate speak translates to something simpler: Microsoft Office trusts information it shouldn't, and attackers exploit that trust.
Here's the technical reality: Office documents can contain embedded objects, macros, and external content. For years, Office had built-in security features to prevent malicious code execution. Office would ask users permission, show warning dialogs, or restrict certain behaviors outright. These are the security decisions that protect you.
CVE-2026-21509 lets attackers circumvent those decisions. Instead of seeing a warning banner that says "This document tried to do something dangerous—do you want to allow it?", users see nothing. The malicious code runs silently. No prompts. No warnings. No chance to back out.
The vulnerability affects specific versions of Office, but if you're using anything modern, you're in scope. We're talking Office 2016 (yes, really), Office 2019, LTSC 2021, LTSC 2024, and Microsoft 365 Apps. That covers millions of organizations worldwide.
Why Office Vulnerabilities Matter More Than Other Software
Office isn't just another application. It's the document platform. Somewhere between 1.2 and 1.5 billion people use Microsoft Office. Governments use it. Banks use it. Healthcare systems use it. If Office gets compromised, the supply chain of trust collapses.
Think about your daily workflow. Someone sends you a document. You open it. You don't think twice. That trust is the target. Attackers know that if they can hijack Office, they can get the document onto a trusted system, execute code with the user's privileges, and pivot from there.
Zero-days in Office are particularly prized because Office documents travel. They're emailed, shared via collaboration tools, stored in cloud services, backed up, archived. If someone compromises a file you received, it stays compromised everywhere it's been copied. That's not true for, say, a vulnerability in an obscure web service.
The Timeline That Matters
On January 26, 2026, Microsoft released the patch. This was an emergency out-of-cycle patch, not part of the normal monthly update schedule. That alone signals urgency. Microsoft doesn't break its regular cadence unless something is really wrong.
On January 29, 2026—just three days later—Ukraine's Computer Emergency Response Team (CERT-UA) reported active attacks. Not "we suspect attacks might be happening." Not "based on threat intelligence, be aware." Actual, observed, confirmed attacks against government systems.
That 72-hour window is critical. If your organization didn't apply the patch on January 26 or 27, you had just days before adversaries started attacking. In the real world, many organizations take weeks or months to patch anything. That's the vulnerability gap. The patch exists, but not everyone has applied it.
Severity Scoring: What 7.6/10 Actually Means
You'll see references to CVSS score 7.6. The Common Vulnerability Scoring System (CVSS) rates vulnerabilities from 0 (low) to 10 (critical). Here's the practical translation:
7.6 = High severity. This is in the tier where security teams escalate to executives, where CISOs start asking questions, where patches become mandatory rather than optional. On the CVSS scale, this sits above most regular vulnerabilities but below the absolute worst-case scenarios.
What pushes it to 7.6 rather than, say, 8.5? The attack requires local access. You can't exploit this remotely through the internet. An attacker can't magically compromise your Office installation from thousands of miles away. They need to trick you into opening a malicious document. But that's not a huge barrier. People open documents every day.
The severity also reflects that while this is serious, it's not a worm. It doesn't propagate by itself. It doesn't jump from computer to computer without user interaction. It requires the victim to do something—open a document, grant permission, interact with the attack. That's what keeps it from being a 9 or 10.

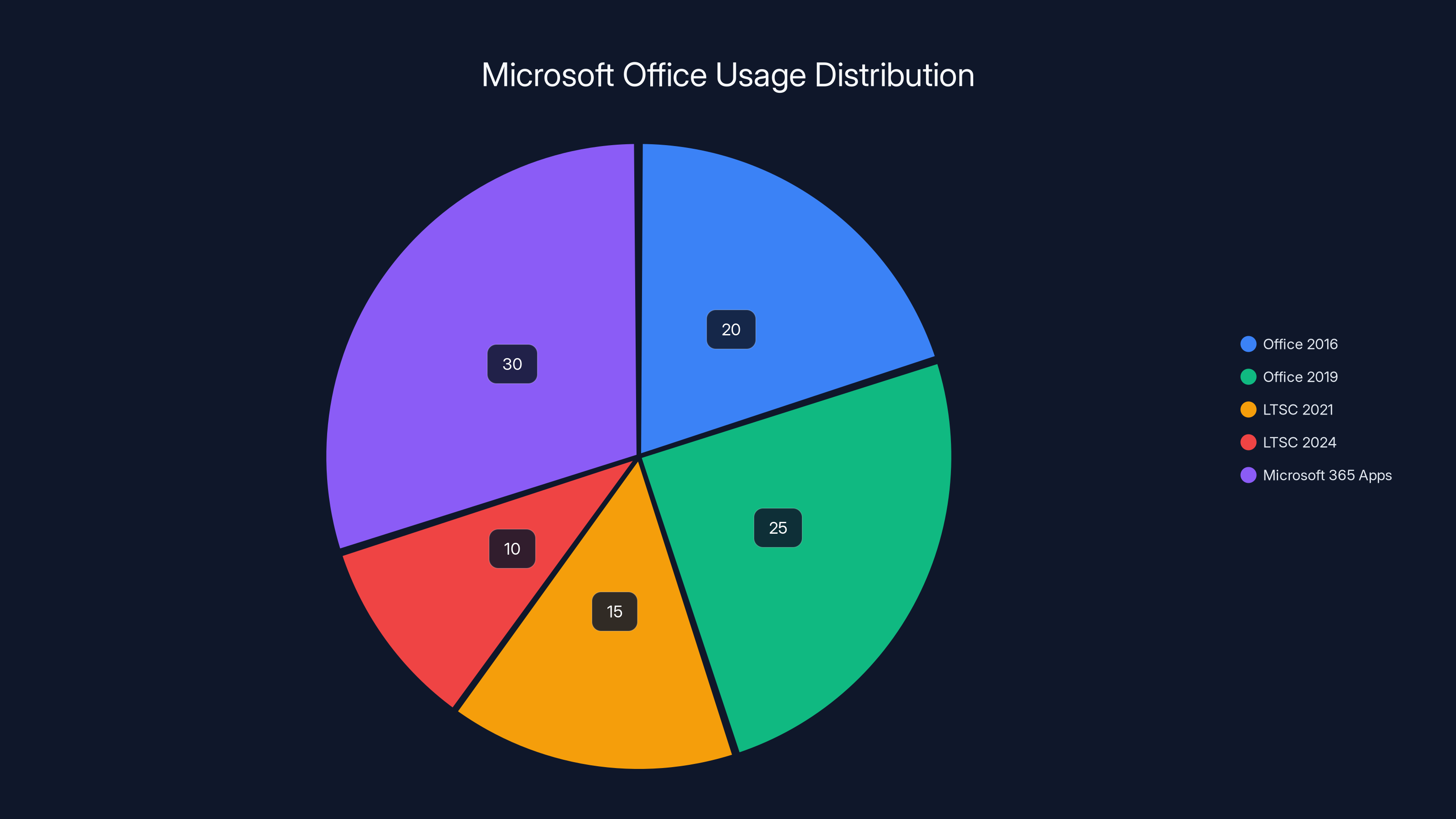
Estimated data shows Microsoft 365 Apps has the largest share of users affected by CVE-2026-21509, highlighting the widespread impact of the vulnerability.
APT28: The Threat Actor Behind the Attacks
Who Is APT28?
APT28 has been around since at least 2008. The acronym stands for "Advanced Persistent Threat 28," which is cybersecurity's way of saying "really sophisticated, dangerous attackers." They're also known as Fancy Bear or Sofacy, depending on which security firm is naming them.
Here's what matters: APT28 is linked to Russia's GRU, specifically the General Staff Main Intelligence Directorate. That's not speculation or inference. Ukrainian security researchers traced the malware they found back to code and tools that APT28 has used in previous, confirmed operations. This is state-sponsored hacking with high confidence.
APT28 has a history of targeting government entities, military systems, and critical infrastructure. They were involved in the hack of the Democratic National Committee in 2016. They've targeted NATO countries. They've targeted Ukraine repeatedly over the past decade. This isn't some random criminal group trying to steal credit cards. This is a nation-state with resources, persistence, and strategic objectives.
How Researchers Identified APT28
CERT-UA analyzed the malware loader used in the January 2026 attacks. They compared it against known APT28 malware from previous campaigns. The similarities were too close to be coincidental. Same code patterns. Same techniques. Same tooling.
Specifically, the researchers linked it back to attacks from June 2025 where APT28 used Signal messaging to distribute malware called Beard Shell and Slim Agent to Ukrainian government employees. Same actors. Same methods. Same targets.
This type of attribution isn't perfect—some of the best security researchers in the world debate threat actor attribution constantly—but when you see the same tools, the same techniques, the same targeting, and the same timing as a previously confirmed state actor, the confidence level is high.
Why APT28 Cares About Ukrainian Government
Ukraine isn't a random target. The country has been under sustained cyberattack for over a decade, accelerating dramatically after Russia's 2022 invasion. Ukrainian government agencies are under constant pressure from coordinated Russian cyber operations.
APT28's interest in Ukrainian government makes strategic sense. They want to access government communications, decision-making processes, military information, diplomatic cables—anything that gives Russia an information advantage. Office documents are the communication medium for government work. Compromise Office, and you've got access to the lifeblood of government operations.
The phishing lures are particularly clever. Some pretended to be about EU COREPER consultations (European Council working group discussions). Others spoofed Ukraine's Hydrometeorological Center. Both are plausible documents that government employees would open without suspicion. Whoever planned these attacks understood Ukrainian government workflows, the types of documents officials receive, and what would look legitimate.
The Attack Method: Phishing with Malicious Documents
How the Attack Actually Works
Step one: Attacker sends an email to government officials. The email looks like it's from a legitimate source—a government colleague, an EU agency, a weather service. It includes a Word document attachment with a relevant-sounding name.
Step two: Official opens the document. Normally, Office would show security warnings. Not this time. The document contains code that exploits CVE-2026-21509, bypassing those security warnings completely.
Step three: Once the warning mechanisms are bypassed, the malicious code executes. This code is the "malware loader"—it doesn't do the actual damage itself, but it downloads and installs the real payload.
Step four: The payload is deployed. In this case, security researchers found Beard Shell and Slim Agent, both tools that give APT28 remote access to the compromised system. From there, they can steal files, access other networked systems, monitor communications, or maintain persistent access for future operations.
The entire process happens in seconds. By the time the user realizes something is wrong, the malicious code has already executed and downloaded the backdoor. Even if they close the document, the damage is done.
Why Phishing Is Still So Effective
Cyber security has advanced tremendously. We have firewalls, antivirus, endpoint detection and response, user education, multi-factor authentication. Yet phishing with malicious documents still works.
Why? Because it exploits the gap between security and usability. A government official needs to receive and open documents. That's their job. They can't refuse to open documents from colleagues. They can't treat every email as suspicious. The system requires some level of trust.
Phishing targets that trust. By making the document look legitimate, using the right context, and hitting the right people (targeted spear-phishing is more effective than mass phishing), attackers can achieve opening rates between 20% and 40% on well-crafted campaigns. If your organization has 500 government employees, a 25% click rate means 125 compromised systems.
The vulnerability makes it even worse because it removes the last line of defense—the security warnings in Office. Even technically savvy users who know to look for those warnings won't see them.
Document-Based Attack History
This isn't APT28's first rodeo with malicious documents. They've been doing this for years. The evolution is clear:
2015: Macro-based attacks, easily stopped by Office security policies
2017: Leveraging Office vulnerabilities to bypass macro restrictions
2020: Supply chain attacks through document templates and add-ins
2025: Zero-day vulnerabilities that bypass all warning mechanisms
Each generation requires defenders to stay ahead, and each generation makes the attacker's job harder. Zero-days level the playing field because defenders have no advance warning.
The Specific Targets: Ukrainian Government Agencies
Which Organizations Were Hit?
CERT-UA reported attacks against multiple Ukrainian government entities. While the agency didn't name every target (classified information, operational security), the scope suggests broad targeting across government.
The phishing lures give hints. Messages about EU COREPER consultations would target foreign ministry and EU affairs officials. Messages about the Hydrometeorological Center would target environmental and emergency services officials. The attacks were tailored to different agencies, suggesting APT28 had prior intelligence about organizational structure and communication patterns.
This level of targeting sophistication indicates that someone—probably Russian intelligence—spent time researching Ukrainian government before launching the attack. They understood which agencies to target, which officials to contact, and what topics would convince them to open documents.
Why Government Agencies Are Priority Targets
Government systems are the prize. They contain:
- Classified information: Military plans, diplomatic communications, intelligence assessments
- Decision-making processes: How leaders discuss strategy, options, and threats
- Personal information: Names, addresses, phone numbers of officials and their families
- Infrastructure details: How critical systems work, their vulnerabilities, their interdependencies
Compromising government systems gives strategic advantage. It's not about stealing money (though that matters). It's about information advantage. In conflicts—and the US-Ukraine-Russia situation is a conflict—information is force multiplier. Knowing what your enemy knows, what they're planning, what they're worried about—that's invaluable.
That's why state actors invest in attacks like this. APT28 didn't spend months developing this attack, getting the phishing lures right, and coordinating with Russian intelligence because they wanted to steal someone's identity. They did it for strategic intelligence.
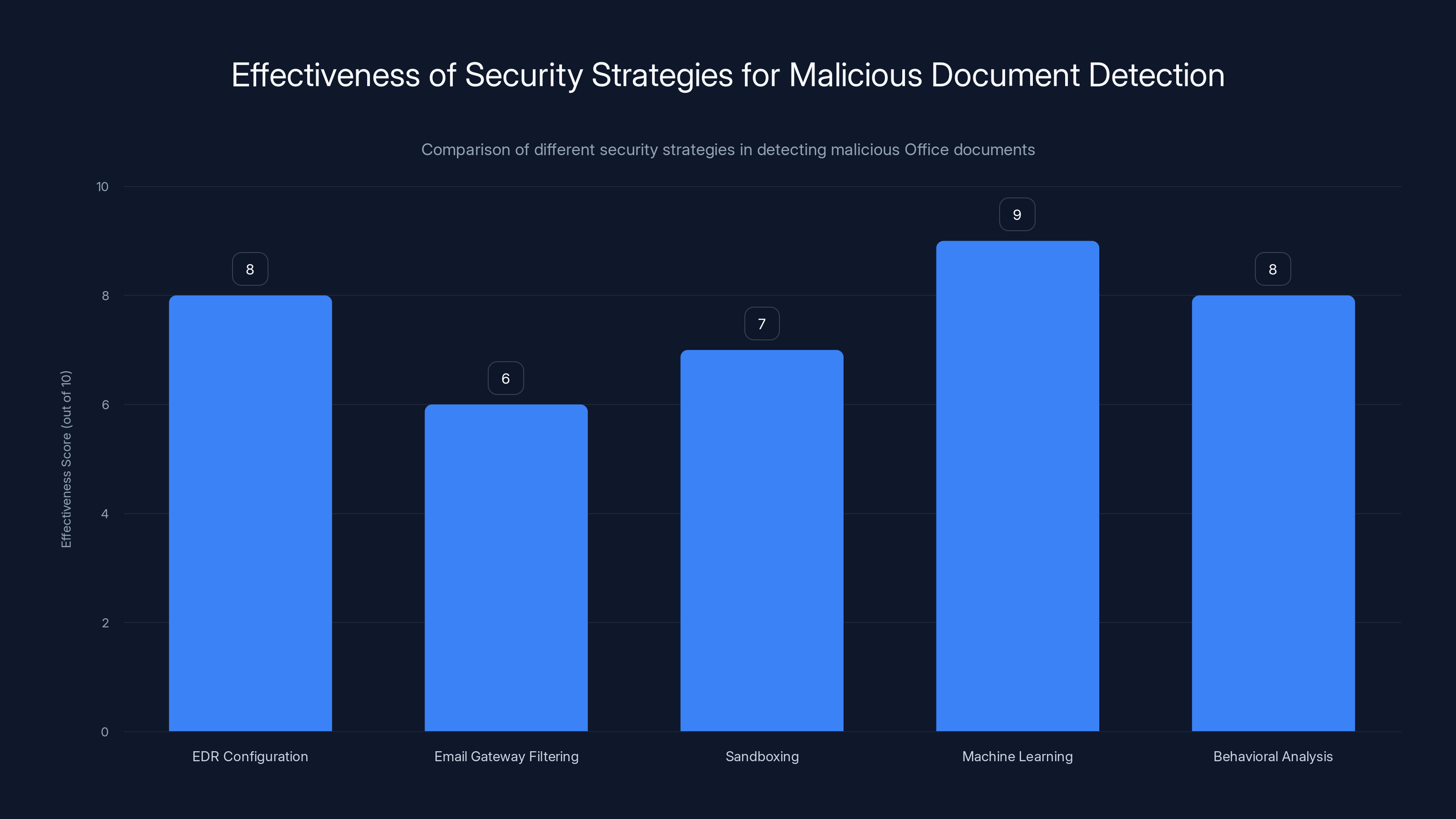
Machine learning and behavioral analysis are highly effective in detecting malicious Office documents, scoring 9 and 8 respectively. EDR configuration is also crucial, scoring 8.
Immediate Mitigation: What You Must Do Now
Priority 1: Apply the Patch Immediately
If your organization hasn't patched yet, stop reading this and go do it. Seriously. Click away. Come back when you're done.
Here's what you need to patch:
- Microsoft Office 2016
- Microsoft Office 2019
- Microsoft Office LTSC 2021
- Microsoft Office LTSC 2024
- Microsoft 365 Apps (what used to be Office 365)
For most organizations, this means going to Windows Update and checking for updates. If you're on Microsoft 365 Apps, the patches typically deploy automatically, but verify in File > Account > Update Options that you're on the latest version.
If you're using older versions—say, Office 2013—you're out of luck. Microsoft doesn't patch those anymore. Your mitigation is to not use those versions, or apply the registry fix detailed below.
Priority 2: Verify Patches Are Installed
Don't just assume patches worked. Verify them. Open Word. Go to File > Account. Look for "Office Updates" or similar. It should say you're up to date. If it says "updates available," click the update button and wait for it to finish.
For LTSC versions, the process is different. LTSC stands for Long Term Servicing Channel, which basically means annual updates instead of monthly. If you're on LTSC 2021 or LTSC 2024, make sure you've installed the latest cumulative update for January 2026.
Additionally—and this is important—after updating, restart your Office applications. Don't just close and reopen. Restart your machine. Some patches require a full reboot to take effect properly.
Priority 3: Apply Registry Mitigation for Unpatched Systems
If you absolutely cannot patch immediately (legacy systems, compatibility concerns, testing windows), Microsoft provides a registry workaround. This isn't as good as the patch—it's a temporary measure—but it's better than nothing.
Microsoft's official security bulletin provides step-by-step instructions for applying the registry fix. The process involves:
- Opening Registry Editor (type "regedit" in Windows search)
- Navigating to a specific registry key
- Creating or modifying a DWORD value
- Restarting your application
The exact steps depend on your Office version and Windows version. Microsoft's security page (the official bulletin, not some third-party guide) has the definitive instructions. Don't improvise or try to copy-paste random registry edits you find online. Registry changes can break Windows if done wrong.
Priority 4: Check for Compromise Indicators
If your organization has already been attacked—if someone opened a malicious document before you patched—you need to know. Look for these indicators:
In Office files:
- Recently modified Office documents from suspicious senders
- Documents with unusual file properties or metadata
- Multiple documents opened in rapid succession from the same sender
On the system:
- New user accounts or administrative access grants
- Unusual network connections, especially to non-US IP addresses
- Processes spawned from Word or Excel that aren't normal (like powershell.exe or cmd.exe)
- New files in Windows Temp directories or App Data folders
In logs:
- Security Event Viewer showing failed authentication attempts
- Application logs with errors around the time the document was opened
- Registry changes to security settings
If you find any of these indicators, your system may be compromised. This is the time to escalate to security teams or external incident responders. Don't try to clean it up yourself. Sophisticated malware often has multiple backdoors and persistence mechanisms. A partial cleanup can alert the attacker that you've discovered them while leaving other access points intact.
Organizational Response: Beyond Patching
Incident Response Planning
If you're in government, defense, critical infrastructure, or handle sensitive information, you should have an incident response plan for this exact scenario. If you don't, now is the time to create one.
Your incident response plan should cover:
-
Detection: How will we know if we've been compromised? What systems, logs, and monitoring will we watch?
-
Containment: If we find a compromised system, how do we isolate it without alerting the attacker? How do we prevent lateral movement?
-
Investigation: Who leads the investigation? What tools will we use? What data do we preserve?
-
Recovery: How do we restore from clean backups? How do we verify the backups are clean? How long will it take?
-
Communication: Who do we notify? When? How do we handle public disclosure if required?
Incident response planning should involve security teams, IT operations, legal, communications, and executive leadership. It shouldn't be written by security alone and filed away. It should be practiced. Run tabletop exercises. Walk through scenarios. The first time you deal with a real incident is not the time to figure out your process.
Threat Hunting for APT28 Infrastructure
APT28 doesn't attack randomly. They scout targets first. They establish infrastructure. They do reconnaissance.
Your security team should look for signs of reconnaissance:
- Port scanning: Did anyone scan your network ports recently? Check firewall logs.
- Credential testing: Did someone try to log in with valid usernames but wrong passwords repeatedly? Check authentication logs.
- Network reconnaissance: Did someone enumerate your network shares, try to access them, or map your network structure? Check network logs.
- Phishing attempts: Did you receive earlier phishing emails that seemed less sophisticated than the final attack? Keep those for analysis.
APT28 is professional. They won't leave obvious footprints. But they will leave some footprints. If you find reconnaissance activity that correlates with when this vulnerability was released, you've got evidence that someone was targeting your organization.
Communication Security Review
If you work in government or critical infrastructure, consider the security of your communication channels. APT28 focuses on intelligence gathering. One vector is compromising communication systems or eavesdropping on communications.
Review:
- Email security: Is your email encrypted? Are you using STARTTLS or TLS? Are sensitive discussions happening over plain email?
- Document security: Are sensitive documents encrypted? Are you using password-protected versions?
- External communication: If you communicate with international partners, are those channels secure?
- Metadata: Even if documents are encrypted, metadata (who, when, what's discussed) can be sensitive.
The goal isn't perfect security (that's impossible). The goal is to make the attacker's job harder. If all your sensitive communications are encrypted and authenticated, attackers can't easily eavesdrop. That forces them to try other vectors.
CISA's Known Exploited Vulnerabilities Catalog
What Is the KEV Catalog?
CISA, the US Cybersecurity and Infrastructure Security Agency, maintains a catalog called Known Exploited Vulnerabilities (KEV). This is a list of security flaws that have been actively exploited by adversaries. If your vulnerability is on the KEV catalog, it means it's not theoretical. Real attackers are using it right now.
When a vulnerability gets added to the KEV catalog, it becomes a priority for:
- Federal agencies: US government agencies are required by executive order to patch known exploited vulnerabilities within specific timeframes
- Critical infrastructure operators: Power plants, water systems, hospitals, telecommunications—these organizations are required to prioritize KEV patches
- Security teams worldwide: If CISA says it's being exploited, every security team pays attention
CVE-2026-21509 was added to the KEV catalog shortly after the Ukrainian attacks were disclosed. This elevates it from "important" to "critical." Organizations can no longer treat this as a normal patch cycle item. It's urgent.
The Compliance Angle
For government contractors, healthcare organizations, and financial institutions, patching KEV vulnerabilities often becomes a compliance requirement. Your contracts may explicitly require patching known exploited vulnerabilities within 30 days or similar timeframes.
If you're not patched and an auditor asks, "Are you patched against known exploited vulnerabilities?" and you say "No, we're planning to patch in Q2," you've just admitted to non-compliance. That becomes a finding, which escalates to your executive leadership, which becomes a bigger problem.
The time to patch is now, not in Q2 or "after testing." Yes, you should test. But test quickly. The longer the vulnerability sits unpatched, the longer your organization is at risk, and the worse your compliance posture looks.
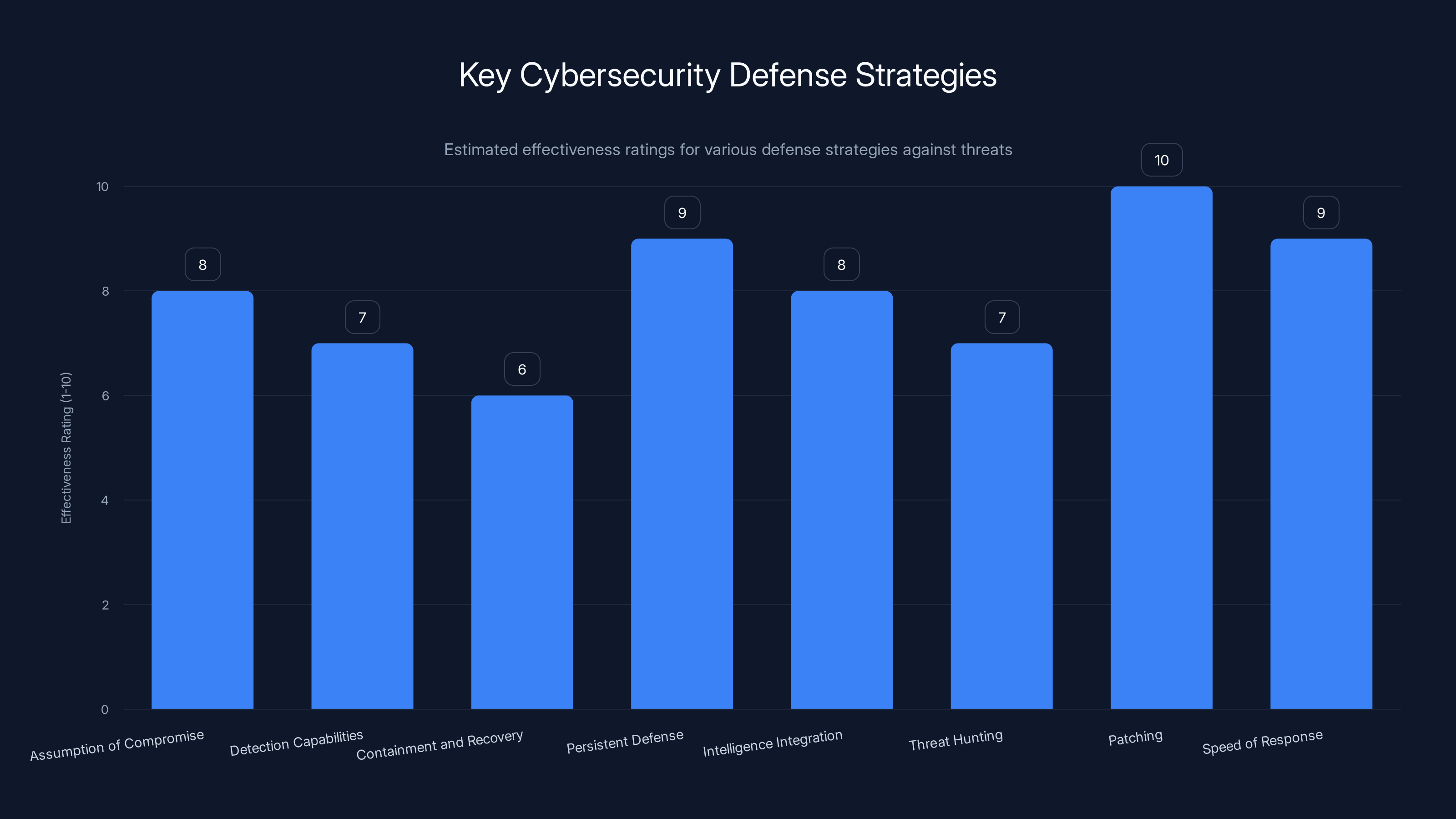
Patching and speed of response are rated as the most effective strategies against cybersecurity threats, highlighting their critical role in defense. Estimated data.
Windows Registry Mitigation: Technical Details
Understanding the Registry Workaround
Microsoft's registry mitigation doesn't fix the underlying vulnerability. Instead, it disables the specific feature that the vulnerability exploits. It's a security-over-functionality trade-off.
Here's the principle: the vulnerability exists in a specific Office feature that processes certain types of objects in documents. By disabling that feature at the registry level, you prevent the malicious code from executing, even if a document tries to exploit the vulnerability.
The downside? Some legitimate documents that rely on that feature will stop working. Malicious documents that tried to exploit it will stop executing. That's the intended behavior.
How to Apply the Mitigation
Applying registry changes requires administrative access and comfort with Windows internals. If you're not confident, escalate to your IT security team.
The process typically involves:
- Opening Registry Editor: Press Windows + R, type "regedit", press Enter
- Navigating to the key: Use the left sidebar to navigate to the correct registry path (provided by Microsoft)
- Creating or modifying values: Right-click, create new DWORD, set appropriate values
- Restarting: Close all Office applications and restart them for changes to take effect
Microsoft's official security bulletin provides exact registry paths and values. Don't guess. Use the official documentation.
Group Policy Alternative
If you manage multiple machines, applying registry changes one by one is inefficient. Group Policy allows you to push registry changes across all domain-joined machines simultaneously.
Your IT operations team can create a Group Policy Object (GPO) that applies the registry mitigation to all computers in your domain. This is much faster than manual changes and ensures consistency.
The process involves:
- Opening Group Policy Editor on your domain controller
- Creating a new GPO
- Adding registry preferences that deploy the mitigation values
- Linking the GPO to organizational units
- Running gpupdate on client machines to apply the changes
This is technical work that typically requires Active Directory and Group Policy experience. If you don't have that expertise in-house, contact your IT vendor or a managed security services provider.
Detection and Prevention: Security Tools and Strategies
Endpoint Detection and Response (EDR)
If your organization uses Endpoint Detection and Response (EDR) software, make sure it's configured to detect malicious Office behavior. EDR tools work by:
- Monitoring process behavior: Watching what processes Office applications spawn and what they do
- Analyzing file access: Monitoring what files Office applications try to access
- Tracking network activity: Recording what network connections Office applications make
- Correlating events: Connecting individual events into larger attack patterns
Malicious Office documents typically exhibit abnormal patterns:
- Word spawning Power Shell or Command Prompt
- Office applications accessing the Windows registry
- Office applications downloading files from the internet
- Office applications making network connections to suspicious IP addresses
A properly configured EDR should catch these behaviors. If you have EDR installed but don't have it configured for Office detection, fix that now. If you don't have EDR at all, this vulnerability is a good business case for acquiring it.
Email Gateway Filtering
Most malicious documents arrive via email. Email security gateways can scan attachments and block known malicious files.
The challenge: CVE-2026-21509 is new. Malicious files leveraging it might not be in signature databases yet. Signature-based detection looks for known patterns. For new exploits, signature detection lags behind.
Better protection involves:
- Sandboxing: Send suspicious attachments to a sandboxed environment, open them, and watch for malicious behavior
- Machine learning: Train models on known malicious Office documents to identify suspicious characteristics in new documents
- Behavioral analysis: Check for Office features that are rarely used legitimately but commonly exploited
Email gateways that use these techniques catch more attacks, including zero-days, than traditional signature-based detection.
User Education (The Reality)
Phishing succeeds because users open documents. No amount of technology fixes that fundamental human behavior. Education helps, but it's not a silver bullet.
Effective user education involves:
- Specific threat awareness: "APT28 is sending documents about EU meetings. Be suspicious of unexpected documents about EU consultations."
- Reporting mechanisms: Make it easy for users to report suspicious emails without judgment
- Feedback loops: When someone reports a phishing email, analyze it and share results with the organization
- Simulated phishing: Run red team exercises to identify vulnerable users and target them for additional training
- Metrics that matter: Track email reporting rates, click rates, and improve based on data
The goal isn't to make users paranoid or unable to do their jobs. It's to create a security culture where people think before opening unexpected documents and report suspicious activity.

Long-Term Defense: Building Resilience
Zero-Trust Architecture
Traditional security assumes that if you're inside the network, you're trusted. That's broken when insiders can be compromised or when sophisticated attackers operate inside your perimeter.
Zero-Trust means never trust, always verify. Every user, every device, every connection, every application is verified before accessing resources.
For Office security specifically, Zero-Trust means:
- Device verification: Check that the device accessing Office is legitimate, updated, and secure
- User verification: Verify the user's identity, location, and behavioral patterns
- Application verification: Check that Office itself is legitimate and hasn't been modified
- Content verification: Scan and analyze documents before they're opened
Implementing full Zero-Trust is complex and takes time. But starting with Office is reasonable. Many Zero-Trust frameworks prioritize document security because documents are such a high-value target.
Segmentation and Micro-Segmentation
If APT28 compromises one machine, can they move laterally across your entire network? If yes, your segmentation is poor.
Network segmentation divides your network into zones. Users in one zone have restricted access to other zones. If an attacker compromises a user's machine, they're confined to that zone instead of having free access to the entire network.
Micro-segmentation takes it further: restricting not just network access but also what applications can access what resources, what data a particular application can process, etc.
For government agencies at risk of APT28 attacks, segmentation is critical. Separate your sensitive decision-making networks from your routine operational networks. Separate your classified networks from unclassified networks. Don't route everything through a single gateway.
This is expensive and complex. But if an attacker can move freely from a compromised Office machine to critical systems, the attack surface explodes. Segmentation contains that damage.
Backup and Recovery
If you do get compromised—if an attacker deploys ransomware or data exfiltration—clean recovery depends on good backups.
Backup requirements for defending against APT28:
- Immutable backups: Backups that attackers cannot modify or delete, even with administrative access
- Offline backups: At least some backups that aren't connected to the network, so attackers can't encrypt or destroy them
- Frequent backups: Daily or more frequent, so you don't lose too much data if recovery is needed
- Verified recovery: Test restoring from backups regularly to ensure they actually work
- Isolated recovery: Have a recovery environment separate from production so you can verify backups are clean before restoring
Many organizations have backups that sound good in theory but fail in practice. They back up to network storage that's accessible from compromised machines. They test recovery once a year. They don't have isolated recovery environments.
APT28 and other sophisticated attackers know this. They spend time in your network, figure out your backup strategy, and destroy or encrypt backups before you even know you've been hit. Good backup security means thinking like an attacker and defending accordingly.
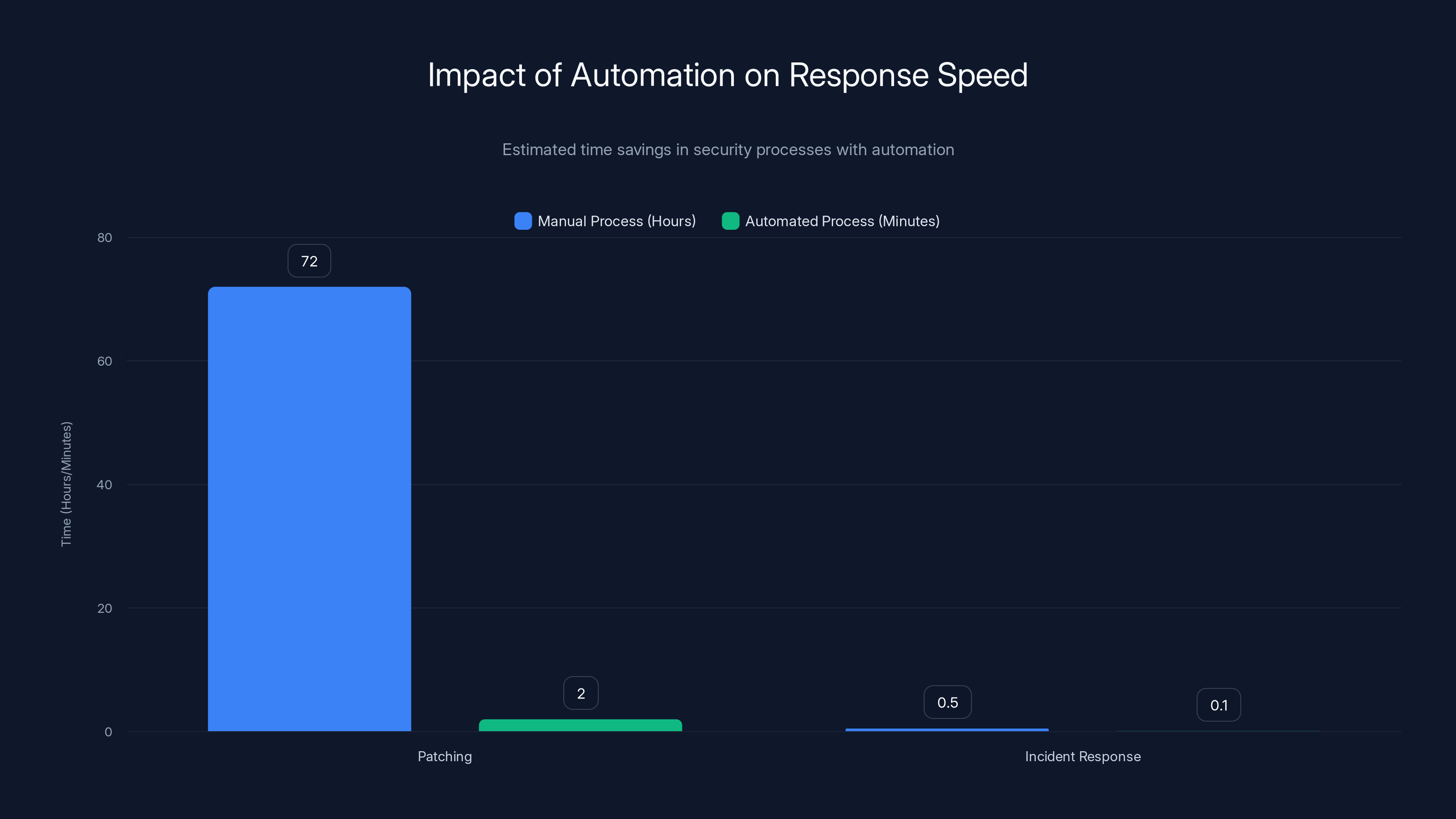
Automation significantly reduces response times, with patching dropping from days to hours and incident response from 30 minutes to seconds. Estimated data.
Threat Intelligence: Understanding APT28's Operations
How APT28 Operates
APT28 isn't a crime gang trying to maximize profit. They're a military intelligence service trying to maximize strategic advantage. That changes their risk calculus.
A criminal attacker might steal a vulnerability and use it quietly for months, extracting maximum value. APT28 burned through this vulnerability in 72 hours. That suggests they either:
- Had multiple vulnerabilities and chose to use this one first
- Believed it would be quickly discovered and patched anyway
- Valued speed over stealth—they need intelligence now
- Wanted to demonstrate capability or test defenses
APT28's typical operational pattern involves:
- Long reconnaissance: Weeks or months of studying the target, understanding their systems, their people, their workflows
- Initial access: Phishing, watering holes, supply chain compromises, or zero-day exploits
- Persistence: Installing backdoors and ensuring multiple ways to regain access
- Privilege escalation: Moving from user access to administrative access
- Lateral movement: Spreading throughout the network to reach high-value targets
- Intelligence gathering: Stealing documents, monitoring communications, exfiltrating data
- Persistence maintenance: Updating backdoors, ensuring they remain undetected
The timeline from initial access to full network compromise typically runs weeks to months for APT28. They're patient. They're thorough. They don't hurry.
TTPs: Tactics, Techniques, and Procedures
Security researchers track APT28's TTP (Tactics, Techniques, and Procedures)—their preferred methods, tools, and approaches. Knowing these helps defenders prepare.
APT28's known TTPs include:
- Spear phishing: Highly targeted phishing with researched context
- Office exploits: Repeated use of Office vulnerabilities
- Custom malware: Beard Shell, Slim Agent, Sofacy malware family
- Living off the land: Using legitimate tools like Power Shell for attacks
- C2 infrastructure: Command and control servers in Russia, former Soviet states
- OPSEC: Careful operational security, rotating infrastructure, covering tracks
If your organization's security monitoring is looking for these specific TTPs, you're more likely to catch APT28 activity early.
Intelligence Sharing
CISA, the FBI, and other agencies share threat intelligence about APT28. Organizations can subscribe to threat feeds that include IOCs (Indicators of Compromise): IP addresses, domains, file hashes, and behavioral signatures associated with APT28.
Using these feeds means your security tools automatically flag suspicious activity associated with known APT28 infrastructure. It's a force multiplier. You get the benefit of collective intelligence from hundreds of organizations defending against the same threat.

Industry Impact and Sector-Specific Concerns
Government and Defense
Government agencies are primary targets for CVE-2026-21509 exploitation. Every government agency in a NATO country, every government allied with Ukraine, and every government with geopolitical interests in Eastern Europe should be treating this as a critical incident.
Defense-specific considerations:
- Classified networks: Are these connected to unclassified networks in ways that could spread a compromise?
- Supply chain security: Do contractors have secure ways to exchange classified information? Are they patched?
- Military systems: Some military systems run older Office versions. These need special attention.
Critical Infrastructure
Critical infrastructure operators—energy, water, transportation, communications—aren't the initial targets, but APT28 could pivot to them if defending against government attacks.
Critical infrastructure considerations:
- Operational technology (OT): Do your OT systems use Office? Often they shouldn't, but some do.
- Business networks: Even if OT is separate, business networks often connect to operational networks
- Supply chain: Vendors and partners often have access to critical infrastructure networks
Finance and Healthcare
While these sectors aren't currently targets in the Ukraine-Russia context, they could be if APT28 expands operations or if similar vulnerabilities are discovered.
Both sectors use Office heavily and have mature security practices. Their incident response and patching processes should be well-developed. The challenge is scale—banks and healthcare systems often manage thousands of machines across geographically distributed locations.
Private Sector
Private companies in defense, energy, telecommunications, and technology sectors often have government customers or government contracts. If the government is being targeted, supply chain partners might be too.
Additionally, APT28 sometimes attacks private companies to gather competitive intelligence or to set up infrastructure for future government attacks.
Metrics and Measurement: How to Track Your Security Posture
Patching Metrics
You should track:
- Time to patch: How long from vulnerability release to patches deployed? For zero-days, can you do it in hours? Days? Weeks?
- Patch success rate: What percentage of machines successfully installed the patch?
- Verification rate: What percentage of patches did you verify actually took effect?
- Scope coverage: What percentage of your organization is running vulnerable software? (Should be 0% after patching)
These metrics tell you how fast you can respond to critical vulnerabilities. APT28 gave the world 72 hours. Did your organization patch in that window? If not, why not, and how can you improve?
Detection Metrics
- Mean time to detect (MTTD): How long does it take you to discover a security incident?
- Phishing reporting rate: What percentage of employees report suspicious emails?
- EDR alert volume: How many alerts is your EDR generating, and what percentage are false positives?
- Threat hunting findings: When security teams hunt for APT28 indicators, what do they find?
These metrics tell you how visible attacks are. If you can't see attacks, you can't stop them.
Resilience Metrics
- Backup success rate: What percentage of backups complete successfully?
- Recovery time objective (RTO): How long to restore from backup if needed?
- Recovery point objective (RPO): How much data loss is acceptable if you have to restore from backup?
- Segmentation effectiveness: If one zone is compromised, can the attacker reach other zones?
These metrics tell you how quickly you can recover if defense fails.

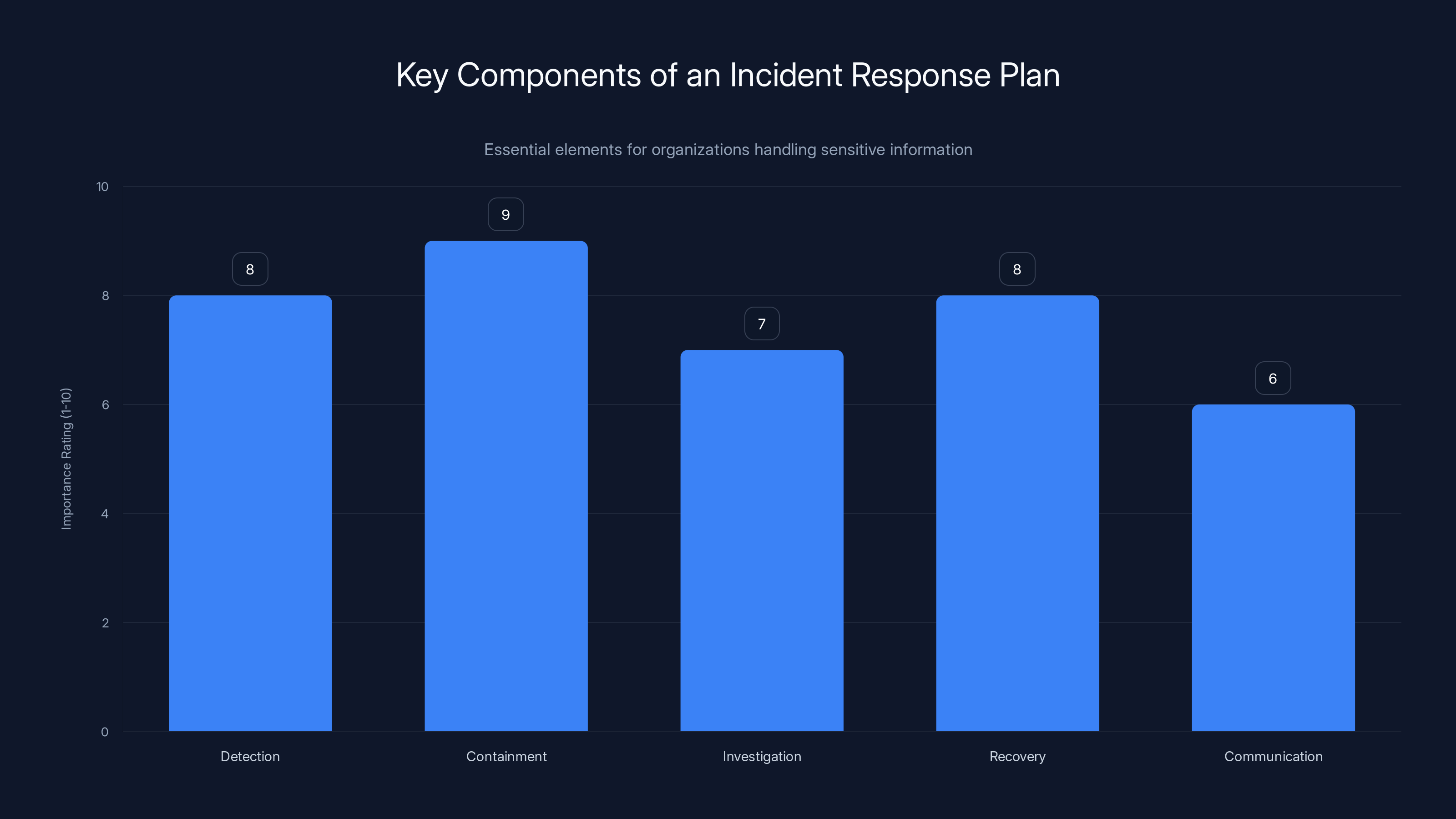
Detection and Containment are critical components of an incident response plan, each rated at 8 or above in importance. Estimated data based on typical organizational priorities.
Lessons Learned: What This Tells Us About the Threat Landscape
Zero-Days Are Common
CVE-2026-21509 is one vulnerability in one month. Zero-days are being discovered and exploited constantly. The myth that zero-days are rare or exotic is wrong. They're being actively exploited by state actors on a regular basis.
The implication: you can't defend against zero-days by waiting for patches. Defense against zero-days requires:
- Assumption of compromise: Plan for attackers getting in
- Detection capabilities: Even if you can't prevent zero-day exploitation, can you detect it?
- Containment and recovery: If an attacker gets in, can you isolate damage and recover?
State Actors Are Persistent
APT28 has been attacking Ukraine for over a decade. They're not going away. They'll keep attacking, and they'll keep developing new capabilities.
Organizations under sustained attack need:
- Persistent defense: Not one-time security improvements but continuous updating
- Intelligence integration: Understanding how the specific threat actor works
- Threat hunting: Actively searching for attacks instead of waiting for tools to alert
Patching Remains Critical
Despite zero-days and sophisticated attacks, patching is still the most important defense. It's not sexy. It's not headlines-worthy. But it blocks the vast majority of attacks.
APT28 had 72 hours before patches were available. After that, patching becomes the primary defense. Organizations that patched quickly were protected. Organizations that delayed remain at risk.
Speed Matters
In cybersecurity, speed is a competitive advantage. Attackers move fast. Defenders need to move faster.
Organizations that can:
- Patch within hours of vulnerability disclosure
- Deploy threat intelligence automatically to detection tools
- Escalate and respond to alerts within minutes
- Conduct threat hunting on a regular schedule
...are fundamentally more secure than organizations that can do these things but take weeks.
Speed requires automation, planning, and rehearsal. It's not a one-time project. It's a continuous capability.
Automation and Workflow Tools: Improving Response Speed
Why Automation Matters for Security
Security teams are understaffed. The global cybersecurity skill shortage means many organizations are trying to defend themselves with smaller teams than they really need.
Automation helps teams do more with less. It's the only way to keep up with the volume and speed of modern attacks.
For patching and vulnerability management specifically, automation can:
- Scan for vulnerabilities: Automatically scan systems for unpatched software
- Test patches: Automatically test patches on test systems before production deployment
- Deploy patches: Automatically deploy patches to production on a schedule
- Verify patches: Automatically verify patches installed successfully
- Report status: Automatically report what's patched, what's pending, what failed
When this process is automated, patching a critical vulnerability takes hours instead of weeks. Manual processes require coordination between teams, approvals, scheduling, testing—all of which adds delay.
Building Automated Incident Response Workflows
Beyond patching, automated workflows can improve incident response for detected attacks.
Example workflow: "If Office spawns Power Shell with suspicious command line, automatically quarantine the machine and alert the security team."
Without automation: Someone manually checks the alert, initiates quarantine, notifies stakeholders. This takes 30+ minutes.
With automation: The machine is quarantined in seconds. A ticket is automatically created. Stakeholders are automatically notified. Security team reviews within minutes.
Automation doesn't replace human judgment. It accelerates detection and response so humans can focus on investigation and remediation instead of triage and coordination.
Tools and Platforms
Various tools can help automate security workflows:
- SIEM (Security Information and Event Management): Collect logs from all systems and correlate events
- SOAR (Security Orchestration, Automation and Response): Define workflows that automatically respond to events
- Patch management tools: Deploy patches automatically on a defined schedule
- Vulnerability scanning tools: Automatically scan for vulnerable software
- ITSM platforms: Manage ticketing, approvals, and coordination
The specific tools matter less than the principle: find repetitive, time-consuming security tasks and automate them.

The Role of Configuration Management
Why Configuration Matters
A patched system can still be insecure if it's misconfigured. Configuration management ensures that systems are deployed consistently and configured securely.
For Office specifically, configuration management can:
- Disable dangerous features: Disable macros, disable external content loading, disable certain plugins
- Enable security features: Enable data loss prevention, enable protected view, enable external content warnings
- Deploy consistently: Ensure all machines have the same security configuration
- Update on change: When security policies change, deploy to all machines
Without configuration management, individual machines drift. One machine has macros disabled, another doesn't. One has protected view enabled, another doesn't. This creates inconsistency, which creates opportunities for attackers.
Configuration as Code
Best practices treat configuration as code:
- Version control: Track changes to configuration
- Code review: Have someone review configuration changes before deployment
- Automated testing: Test configurations before deploying to production
- Deployment automation: Deploy consistently through automation
- Audit trails: Track who made changes, when, and why
Configuration as code brings software development rigor to security configuration. It's not perfect, but it's vastly better than manual configuration on each machine.
Future Vulnerabilities and Emerging Threats
The Vulnerability Forecast
If CVE-2026-21509 taught us anything, it's that Microsoft Office remains a high-value target for attackers. Expect more Office vulnerabilities in the future.
Reasons why Office stays in the attacker's crosshairs:
- Universal usage: Office is on billions of machines
- Complex codebase: Office is massive, complex software with lots of code to hide vulnerabilities in
- High-value target: Office is the medium for exchanging documents, and documents contain valuable information
- Supply chain potential: Office compromises can lead to supply chain attacks
Microsoft has invested heavily in Office security. The pace of Office vulnerabilities has slowed compared to a decade ago. But they still happen, and when they do, they're significant.
Broader Threats: AI-Powered Attacks
Looking beyond Office, emerging threats include AI-powered attacks:
- Better phishing: AI can generate targeted phishing emails with research on specific individuals, organizations, and contexts
- Malware generation: AI can automatically generate variations of malware to evade detection
- Watering hole attacks: AI can identify high-value targets and automatically create targeted attacks
These aren't theoretical. Organizations are already seeing AI-assisted phishing that's more convincing than previous generation attacks.
Supply Chain Vulnerabilities
As organizations improve their own security, attackers increasingly target their supply chains. A vendor with weaker security might provide access to a more heavily defended customer.
Supply chain risk considerations:
- Vendor assessment: Do your vendors have security standards equivalent to your own?
- Vulnerability transparency: Do vendors quickly disclose vulnerabilities in their products?
- Incident response: If a vendor is compromised, how quickly do they notify customers?
- Contractual obligations: Does your vendor contract include security requirements and incident response procedures?
This applies to both software vendors (like Microsoft) and service vendors (like IT service providers, cloud providers, etc.).

Resources and Further Reading
Official Security Guidance
The most authoritative sources for technical details and mitigation steps come directly from Microsoft, CISA, and Ukraine's CERT-UA:
- Microsoft Security Bulletin: Microsoft publishes official patches and registry mitigation steps
- CISA Advisory: CISA provides guidance for critical vulnerabilities affecting critical infrastructure
- CERT-UA Report: Ukraine's cybersecurity team publishes technical analysis and IOCs
When implementing mitigations, refer to these official sources, not third-party summaries or guides.
Threat Intelligence Sources
For tracking APT28 and related threats:
- CISA KEV Catalog: The Known Exploited Vulnerabilities list
- US-CERT threat advisories: Government security agency guidance
- Microsoft Threat Intelligence: Microsoft publishes research on threats targeting their products
- Security vendor research: Major security firms (Crowd Strike, Mandiant, Proofpoint) publish APT28 research
Incident Response and Forensics
If you suspect compromise:
- SANS Incident Handlers Handbook: Free guide to incident response procedures
- Incident response services: Firms like Mandiant, Crowd Strike, and others offer incident response and forensics
- Digital forensics tools: En Case, FTK, and open-source tools like Autopsy
Continuing Education
Security professionals should stay current with threats and defenses:
- Security conferences: DEF CON, Black Hat, RSA Conference feature threat research
- Certifications: GIAC Security Essentials, OSCP, CEH certifications
- Training courses: Specialized training in threat hunting, incident response, vulnerability management
Conclusion: Preparing for the Next Attack
CVE-2026-21509 is serious, but it's not unique. It's one of many high-severity vulnerabilities that attackers will exploit. The specific vulnerability will be patched, but the underlying threat—sophisticated attackers with resources and persistence—won't go away.
Here's what organizations need to understand:
First, patching is non-negotiable. When a vulnerability is exploited in the wild by state actors, patching becomes a mandatory security control, not an optional IT task. Every machine running vulnerable Office needs to be updated. Every machine. No exceptions for "we're testing" or "we'll patch next quarter." Now.
Second, detection and response capabilities matter as much as prevention. You will be attacked. Assume compromise. The question is whether you can detect attacks and respond fast enough to minimize damage. EDR tools, SIEM, threat hunting, incident response planning—these aren't nice-to-have security theater. They're essential if prevention inevitably fails.
Third, organizational readiness requires planning and practice. Your incident response plan shouldn't be a document on a shelf. Run tabletop exercises. Simulate attacks. Walk through scenarios. The first time you deal with a real APT28 attack is not the time to figure out your process.
Fourth, threat intelligence should inform your defense. APT28 has particular methods, particular tools, particular infrastructure. If you're tracking those indicators, you're more likely to catch them. Threat intelligence is a force multiplier for small security teams.
Fifth, segmentation and resilience matter. You can't prevent all compromises, so design your systems for resilient recovery. Network segmentation contains damage. Good backups enable recovery. Offline backups can't be encrypted by ransomware.
The attackers are sophisticated, well-resourced, and persistent. You can't outpace them forever. But you can make yourself a harder target. You can make attacks more expensive and time-consuming. You can detect and respond faster than they expect. That's what modern cybersecurity is about.
APT28 will continue attacking Ukrainian government. They'll continue refining their tools and techniques. When the next vulnerability is discovered—and there will be a next one—they'll exploit it. The question for your organization is: will you be ready?

FAQ
What exactly is CVE-2026-21509?
CVE-2026-21509 is a high-severity security vulnerability in Microsoft Office that allows attackers to bypass Office security features. The vulnerability is caused by Office incorrectly trusting untrusted inputs when making security decisions. Attackers can exploit this by sending malicious Office documents that execute code without triggering normal security warnings.
How does APT28 exploit this vulnerability in real attacks?
APT28 sends phishing emails with malicious Word document attachments to government officials. When the document is opened, the vulnerability allows APT28's code to execute without triggering Office's normal security warnings. The code then downloads and installs malware (Beard Shell or Slim Agent) that gives APT28 remote access to the compromised system. From there, they can steal documents, monitor communications, or move laterally across the network.
What Office versions are affected by this vulnerability?
The vulnerability affects Microsoft Office 2016, Office 2019, Office LTSC 2021, Office LTSC 2024, and Microsoft 365 Apps. If you're using Office 2013 or older, those versions are no longer supported by Microsoft and won't receive patches, though they're not explicitly listed as vulnerable to this specific CVE.
How long does it take to patch the vulnerability?
The patch itself downloads and installs quickly, usually within 10-30 minutes depending on your system and internet speed. However, organizations often take longer because they test patches in lab environments first, schedule deployments during maintenance windows, and roll out updates gradually across their infrastructure. For a critical zero-day like this, organizations should compress that timeline to hours or days, not weeks.
What if I can't patch immediately?
Microsoft provides a Windows Registry workaround that disables the vulnerable feature without patching. This mitigation prevents the vulnerability from being exploited but may break legitimate functionality that relies on the vulnerable feature. The registry fix is temporary and less secure than patching, so it's intended as a short-term measure while you prepare patches.
How do I know if my organization has been compromised?
Signs of compromise include recently modified Office documents from suspicious senders, new user accounts or administrative access grants, unusual network connections to non-US IP addresses, Office applications spawning Power Shell or Command Prompt, and security event logs showing failed authentication attempts or registry changes. If you find any of these indicators, escalate immediately to your security team or external incident responders.
Why does patching take so long in most organizations?
Officially, patching requires testing to ensure the patch doesn't break legitimate applications, then scheduling deployment during maintenance windows to minimize disruption, then rolling out gradually across the organization. In reality, bureaucratic processes, change management approvals, lack of automation, and competing IT priorities all contribute to delays. For critical zero-days being actively exploited, this timeline is unacceptable.
Should I be more concerned about Office vulnerabilities than other types of attacks?
Yes, relatively. Office is ubiquitous, documents are trusted by default, and successful exploitation gives attackers code execution on your system. That combination makes Office vulnerabilities among the highest-impact security risks. However, Office is one attack vector among many. You should be concerned about patch management broadly, phishing broadly, and a defense-in-depth approach rather than focusing entirely on Office.
What is the difference between a zero-day and a regular vulnerability?
A zero-day is a vulnerability that doesn't have a patch available yet. Attackers have discovered the flaw, but the vendor hasn't released a fix. Regular vulnerabilities are known to the vendor, patches exist, and it's up to users to apply them. Zero-days are harder to defend against because you can't patch your way out of the problem—you must rely on detection, behavioral controls, or other mitigations.
How can I tell if my Word documents are malicious?
Malicious documents often exhibit unusual characteristics like embedded objects (OLE objects), suspicious macros, or external data connections. However, modern attacks can be very subtle. Your best defense is to avoid opening unexpected documents, especially from unknown senders, and to keep Office updated. If you're suspicious of a document, you can submit it to antivirus vendors (like Virus Total) for scanning before opening it.
Is the registry mitigation as good as patching?
No. The registry mitigation disables vulnerable features, which prevents exploitation but may also break legitimate functionality. Patching fixes the vulnerability without disabling features. For example, if the vulnerable feature is required for a business process, the registry mitigation will block that process. Patching allows the feature to work securely. The registry mitigation is a temporary measure while you prepare patches, not a long-term alternative to patching.
Key Takeaways
- CVE-2026-21509 is actively exploited by Russian state actor APT28 within 72 hours of patch release, making immediate patching critical
- The vulnerability affects Office 2016, 2019, LTSC 2021, LTSC 2024, and Microsoft 365 Apps by bypassing security warnings
- Phishing with malicious Office documents remains the primary attack vector; both detection and user awareness are essential
- Organizations lacking immediate patch capability can apply Windows Registry mitigations as a temporary measure
- APT28's sophisticated targeting of government agencies demonstrates state-sponsored cyberattacks require zero-trust architecture and rapid incident response
Related Articles
- Notepad++ Supply Chain Attack: What You Need to Know [2025]
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- North Korean Labyrinth Chollima Malware Splits Into Three Entities [2025]
- Claude Code Outage: What Happened and Why AI Tool Reliability Matters [2025]
- Malwarebytes and ChatGPT: The AI Scam Detection Game-Changer [2025]
- Notepad++ Supply Chain Attack: Chinese State Hackers Explained [2025]
![Office 365 Zero-Day Exploit: What You Need to Know [2025]](https://tryrunable.com/blog/office-365-zero-day-exploit-what-you-need-to-know-2025/image-1-1770140261097.jpg)



