Notepad++ Supply Chain Attack: Chinese State Hackers Explained
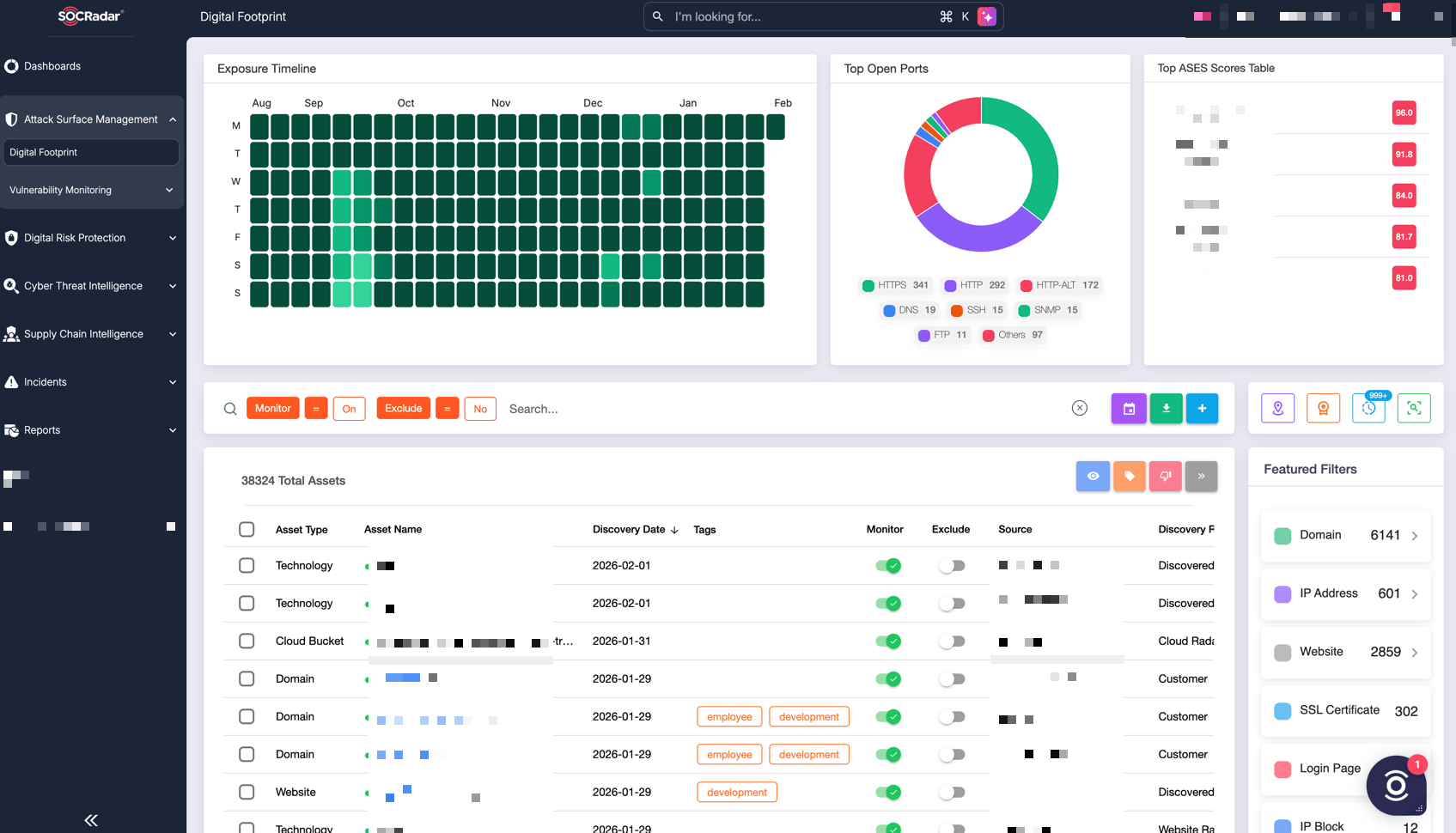
In June 2025, one of the world's most widely used text editors became the target of a sophisticated cyberattack that exposed critical vulnerabilities in software supply chains. The attackers weren't after Notepad++'s source code or user data. Instead, they compromised a shared hosting provider's server and weaponized it to deliver malicious updates to carefully selected victims, as detailed by Dark Reading.
What makes this incident particularly alarming isn't just the technical sophistication of the attack. It's what it reveals about the state of software security infrastructure and how nation-state actors are increasingly targeting the tools developers rely on every single day. According to The New York Times, this attack is part of a broader trend of cyberwarfare tactics employed by state-sponsored actors.
Notepad++ isn't some obscure utility. Millions of developers, system administrators, and regular users depend on it for basic text editing tasks. When attackers can compromise the update mechanism of such a widely trusted tool, the potential blast radius becomes exponentially larger. This attack represents a fundamental shift in how state-sponsored threat actors approach cyberwarfare: instead of targeting individual organizations, they're going after the infrastructure that connects entire ecosystems, as reported by The Record.
In this comprehensive analysis, we'll walk through exactly what happened, why it matters, how Notepad++ responded, and what this means for the future of software security. By the end, you'll understand not just the technical details of this attack, but the broader implications for everyone who relies on open-source or third-party software.
TL; DR
- Timeline: Attack began in June 2025, attackers retained access until December 2025, spanning six months of potential exposure, as noted by Ars Technica.
- Method: Compromised shared hosting server used to deliver tainted updates to select targets, exploiting weak update verification controls, according to Infosecurity Magazine.
- Attribution: Suspected Chinese state-sponsored threat actors based on targeting patterns and sophistication level, as discussed in Forrester's analysis.
- Impact: Carefully selected victims received malicious updates, but full scope of affected users remains undisclosed, as reported by Rescana.
- Response: Notepad++ migrated to new hosting, implemented certificate and signature verification, and upgraded update mechanisms, as detailed by CyberPress.
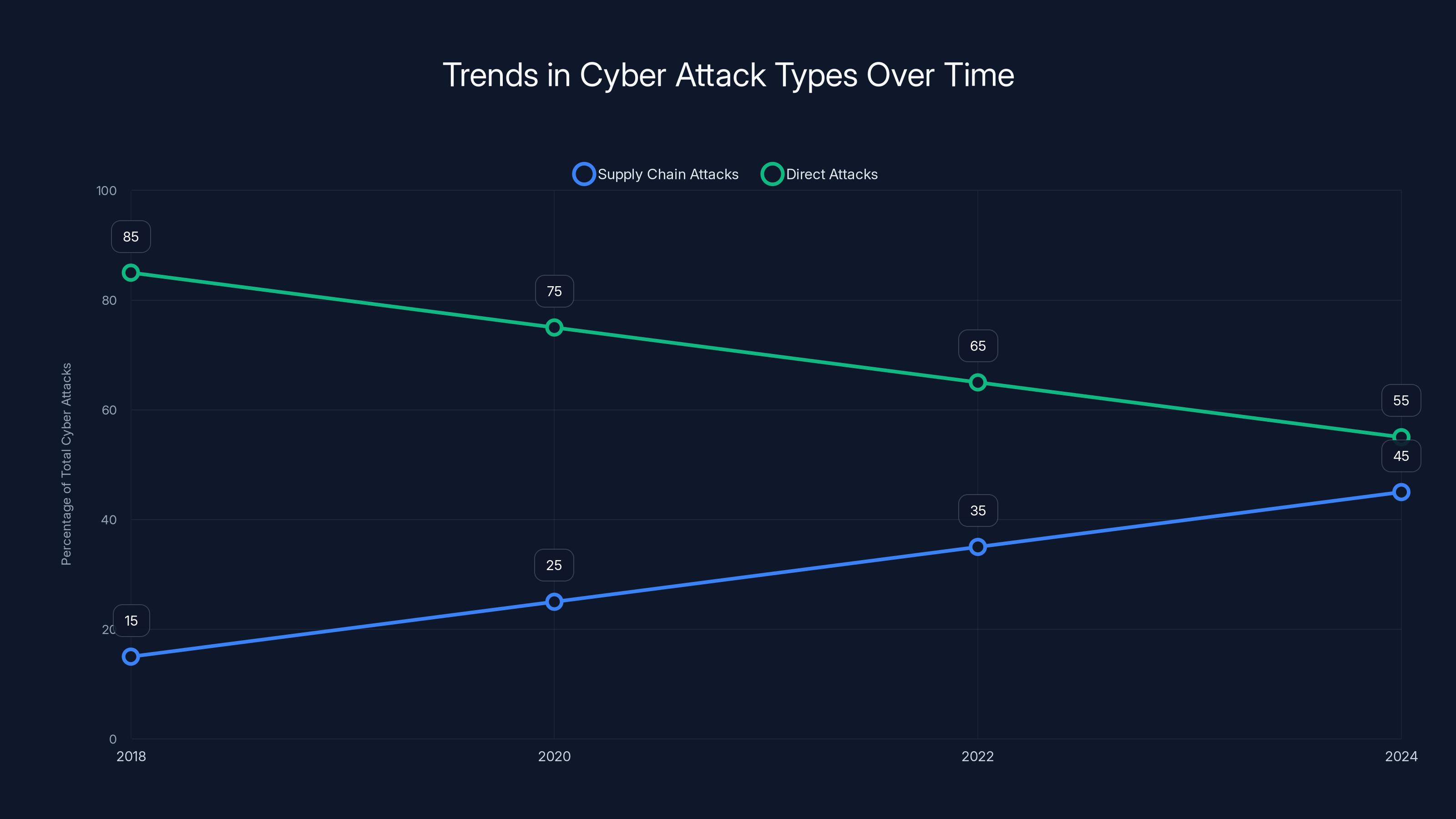
The proportion of supply chain attacks has increased significantly from 15% in 2018 to an estimated 45% in 2024, highlighting a shift in attack strategies. Estimated data.
Understanding the Attack Vector: How Supply Chain Compromises Work
Before diving into the Notepad++ incident specifically, it's crucial to understand the broader category of attack we're discussing. Supply chain attacks represent one of the most insidious threats in modern cybersecurity because they exploit trust relationships rather than brute force or user error. As SentinelOne explains, these attacks leverage trusted intermediaries to reach a wider set of targets.
Traditional direct attacks require hackers to breach your organization's defenses. Supply chain attacks work differently. They compromise a trusted intermediary, then leverage that position to reach a much wider set of targets. Think of it like poisoning a water supply instead of breaking into individual homes.
In Notepad++'s case, the attack vector involved the software update mechanism. When you install Notepad++, the application periodically checks for updates. This check connects to Notepad++'s servers to determine whether a newer version is available. If you're running version 8.4.5 and version 8.5.0 is available, the updater downloads and installs the new version.
This process requires trust. Your computer assumes that updates coming from Notepad++'s official servers are legitimate. Attackers who can intercept or manipulate this trust channel have just unlocked access to millions of machines.
The Notepad++ attack specifically targeted the hosting provider infrastructure. Shared hosting means multiple organizations host their websites and services on the same physical server infrastructure. If an attacker compromises that shared infrastructure, they can potentially reach any tenant on that server.
What makes the Notepad++ situation particularly sophisticated is that the attackers didn't just blindly inject malware into every update. They specifically searched for Notepad++'s domain within the hosting infrastructure. They were surgical about their targeting. They likely knew about existing vulnerabilities in Notepad++'s update verification systems and specifically crafted their attack to exploit those weaknesses.
The fact that investigators found no evidence of other clients on the shared hosting server being targeted suggests this wasn't opportunistic. This was intentional, pre-planned, and focused.

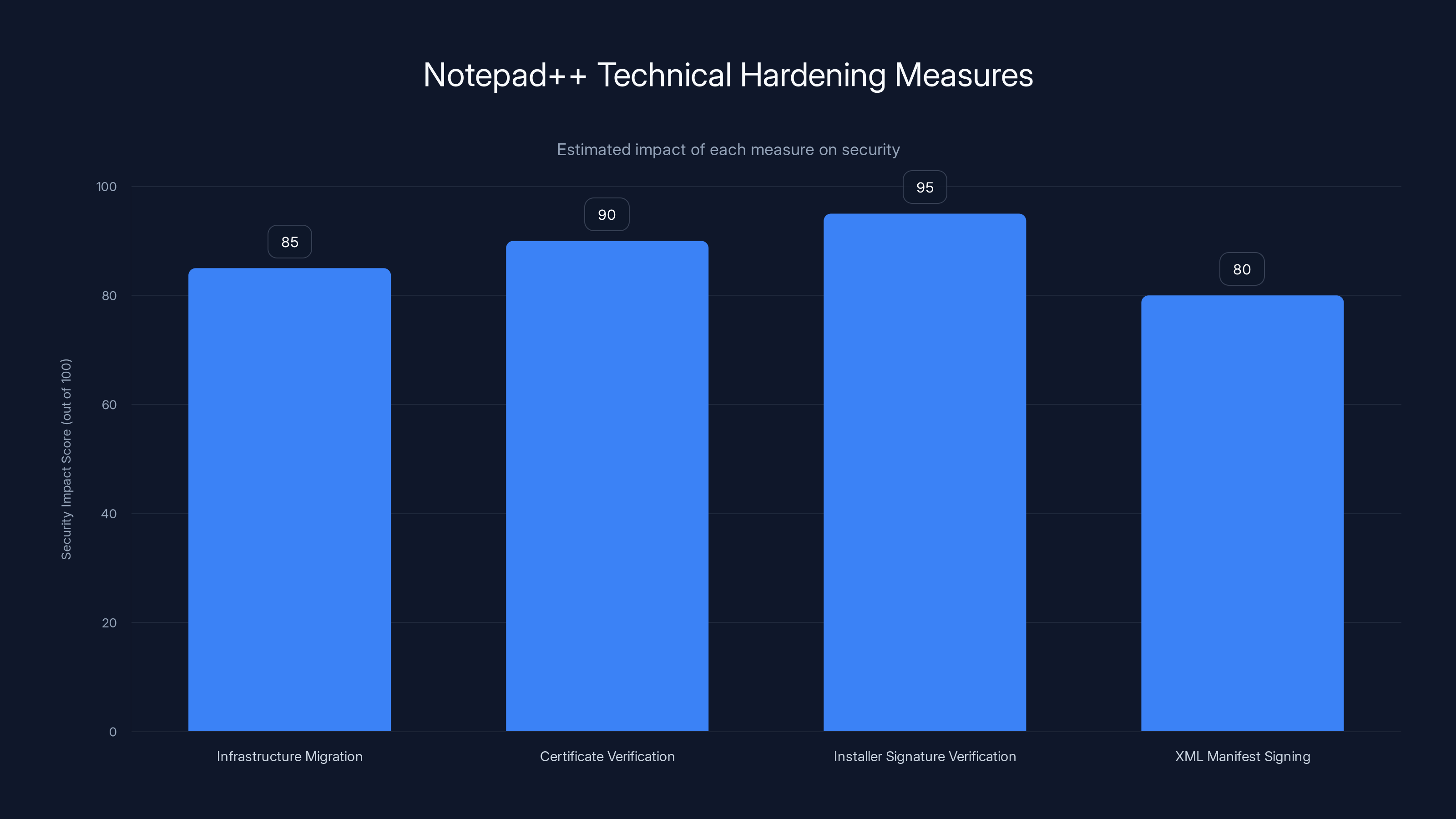
Estimated data: Each measure significantly enhances security, with Installer Signature Verification having the highest impact.
The Timeline: Six Months of Undetected Access
Understanding the attack timeline is critical because each phase reveals something different about how the attackers operated and what went wrong with Notepad++'s security monitoring.
June 2025: Initial Compromise
The attack began in June 2025 when the shared hosting provider's server was compromised. Investigators haven't publicly disclosed exactly how the initial breach occurred, but given the sophistication of what followed, it likely involved either an unpatched vulnerability in the hosting control panel or compromised administrator credentials.
Once inside the server, the attackers faced a common problem in incident response: they needed to avoid detection. Poorly executed attacks leave obvious traces. Deleted files appear in system logs. Unusual processes consume resources. Network traffic spikes attract attention.
These attackers were methodical. They likely performed reconnaissance to understand the server's configuration, identify where Notepad++'s files were stored, and determine how the update mechanism worked. Only after understanding the environment did they begin preparing their attack.
July-August 2025: Weaponization and Delivery
During this period, the attackers began delivering tainted updates to what they had identified as carefully selected targets. The term "carefully selected" is important here. It suggests the attackers weren't just randomly injecting malware into Notepad++ updates.
They had a specific target list. This could mean they were targeting specific geographic regions, specific industries (military contractors, government agencies, financial institutions), or users with certain characteristics.
The fact that the attackers delivered updates to select victims rather than everyone downloading Notepad++ suggests they either knew their targets in advance or had implemented some kind of filtering mechanism. They might have monitored which IP addresses requested updates and served malicious versions only to specific geographic regions or known target networks.
This level of precision indicates intelligence gathering. The attackers likely knew exactly which organizations they wanted to compromise and had already done the reconnaissance necessary to identify how to deliver updates specifically to those organizations.
September 2025: Patch Deployment Closes Initial Door
In September 2025, a patch was deployed that apparently invalidated whatever vulnerability or misconfiguration the attackers had been exploiting. The hosting provider released updates that changed system configurations in ways that broke the attackers' initial access mechanism.
At this point, many attacks would end. The initial vulnerability is fixed. The attackers have been shut out. Investigation begins, remediations are implemented, and life returns to normal.
But these attackers had planned ahead. They still had credentials.
October-November 2025: Credential-Based Persistence
During the September patch deployment, the attackers retained administrative credentials they had obtained during the initial compromise. Instead of being locked out, they simply logged back in using their stolen credentials.
This is a fundamental principle of advanced persistent threats (APTs). Attackers don't just exploit one vulnerability and hope for the best. They establish multiple access points, often called "persistence mechanisms." If the primary attack vector gets patched, they have backup methods to maintain access.
For six additional weeks, the attackers continued to deliver tainted updates using their legitimate credentials. From the server's perspective, an authorized administrator was initiating the update delivery. Nothing appeared suspicious in the logs because they were using valid authentication.
This highlights a critical security principle: even if you patch vulnerabilities, you still need to monitor what authenticated users do. In this case, the attackers had legitimate access to the system. The problem wasn't their credentials being invalid. The problem was that their behavior wasn't questioned.
December 2025: Credential Rotation Ends Access
Finally, in December 2025, the hosting provider forced a complete password rotation across all administrative accounts. This invalidated the stolen credentials the attackers had been using.
For the first time since June, the attackers lost access to the system. They couldn't log back in. They couldn't deliver further updates. The compromise was finally truly ended.
But by this point, the attackers had maintained persistent access for six months. In the world of cyberattacks, six months is an eternity. That's enough time to establish additional backdoors, exfiltrate massive amounts of data, or plant logic bombs that execute at some future date.
The Weakness Exploited: Insufficient Update Verification
The attackers could deliver tainted updates only because Notepad++'s update verification controls were insufficient. This is the technical core of the vulnerability that made the supply chain attack possible.
How Secure Update Mechanisms Should Work
When software updates reach your computer, there needs to be a way for your system to verify that the update is genuinely from the legitimate publisher and hasn't been modified by an attacker.
Modern software signing works through digital certificates and cryptographic signatures. Here's the basic process:
- The software publisher creates a private key (never shared, kept secret)
- The publisher uses this private key to digitally sign updates before publishing them
- When the update reaches your computer, your system uses the publisher's public certificate (available publicly) to verify the signature
- If the signature is valid, you know the update came from someone who has the private key (presumably the legitimate publisher)
- If the signature is invalid or missing, your system rejects the update
This cryptographic chain of trust ensures that even if an attacker intercepts the update, they can't modify it without breaking the signature. And they can't forge a valid signature without the private key.
Additionally, updates should be delivered over secure HTTPS connections that verify the server's SSL/TLS certificate. This prevents attackers from intercepting updates at the network level.
Notepad++ in older versions had gaps in this defense. The specification from Notepad++ mentioned that updates weren't sufficiently verifying certificates and signatures. Attackers who could control the delivery point could potentially serve modified installers that the older verification mechanisms wouldn't catch.
The Specific Vulnerability in Notepad++
The exact nature of Notepad++'s update verification weakness wasn't disclosed in full detail, likely to prevent immediate exploitation before users could update. However, several possibilities exist based on common update mechanism flaws:
Incomplete Certificate Validation: The system might have checked that an SSL certificate existed but not verified that the certificate matched the domain or that it was signed by a trusted certificate authority.
Missing Signature Verification: The update installer might have lacked digital signature validation entirely. The system checked that a file was present but didn't cryptographically verify that it came from the legitimate publisher.
Hash Verification Without Signature: Some systems verify that downloaded files match expected hashes but don't verify those hashes through a cryptographically signed manifest. If the attacker controls the download source and the hash source, this provides no actual protection.
Improper Chain of Trust: The update mechanism might have trusted intermediate files or configurations that weren't themselves properly signed or verified.
Real-World Examples of Similar Vulnerabilities
Notepad++ wasn't the first to experience this class of vulnerability. Understanding previous incidents illuminates why update verification is so critical.
In 2016, a major code signing issue affected multiple software vendors. Several companies were issuing signed certificates without properly verifying ownership of the domains they were signing. This allowed attackers to obtain certificates for domains they didn't actually control, enabling them to sign malware that systems would trust as legitimate.
The CCleaner supply chain attack in 2017 exploited a company's build infrastructure. Attackers modified the software during compilation, before it was signed. The final signed executable contained malware. The signature was valid, the certificate was legitimate, but the software was weaponized.
These incidents show that update security isn't just about cryptography. It's also about controlling who can access the build and distribution infrastructure, securing the private keys used for signing, and verifying the integrity of each step in the update pipeline.
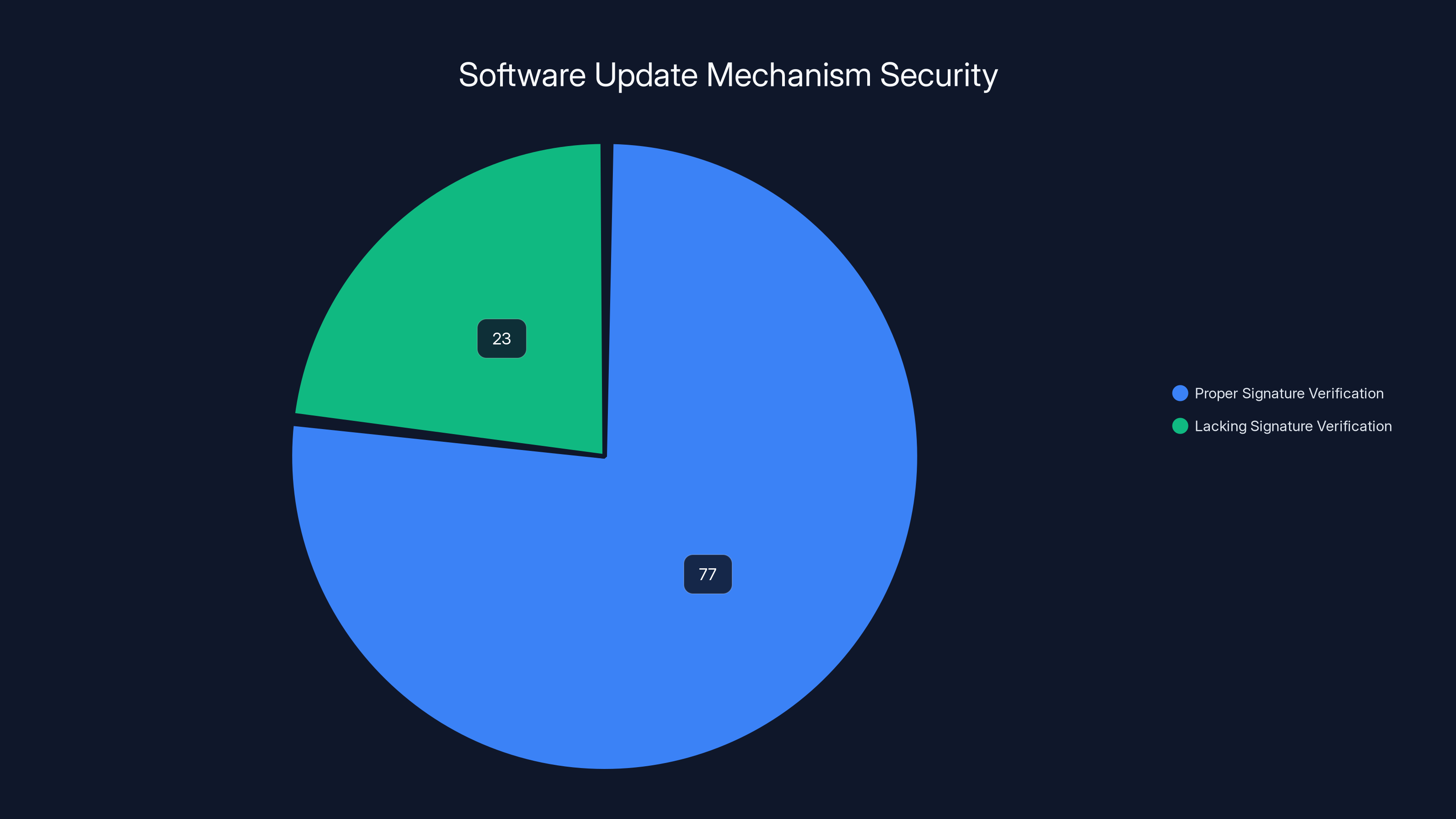
A 2024 study found that 23% of software lacks proper signature verification for updates, posing significant security risks.
Attribution: Why Researchers Believe This Was Chinese State-Sponsored
The advisory notes that investigators determined the attackers were "most likely" Chinese state-sponsored actors. This conclusion didn't come from assumptions or speculation. It came from specific indicators of compromise and attack patterns.
Targeting Patterns and Intelligence
The most compelling evidence of state sponsorship is the surgical targeting of Notepad++ users. The attackers didn't compromise the update system and serve malicious code to everyone. They specifically identified their targets and served tainted updates only to them.
This kind of precision requires intelligence gathering. The attackers needed to know which organizations they wanted to target, which networks they operated from, and how to filter update requests accordingly. State actors have access to network intelligence, signals intelligence (SIGINT), and human intelligence (HUMINT) that private criminals typically don't have.
The fact that the attackers specifically searched for Notepad++'s domain within the hosting infrastructure suggests they had prior knowledge of where Notepad++ was hosted. They weren't just randomly compromising servers and hoping to find interesting targets. They targeted this specific server because they knew Notepad++ was there.
Technical Sophistication
The technical execution of the attack demonstrates sophisticated operational security. The attackers:
- Identified and exploited an unpatched vulnerability in the hosting infrastructure
- Avoided obvious detection for six months
- Established credential-based persistence after the initial access vector was patched
- Implemented selective targeting that limited visibility into the attack
- Maintained operational security throughout the six-month period
This level of sophistication isn't typical of financially motivated cybercriminals. They generally prioritize speed and scale (hit as many targets as possible for financial gain). This attack prioritizes precision and stealth (target specific victims while avoiding detection).
The operational tradecraft suggests experience with multi-stage attacks and understanding of how target organizations would respond to compromise. State-sponsored threat actors conduct operations over months and years, not days and weeks. They're comfortable with slow, methodical progress toward long-term objectives.
Timing and Geopolitical Context
The 2025 timeframe is significant. Tensions between Western nations and China regarding cybersecurity, intellectual property theft, and espionage have been escalating consistently. Intelligence assessments from the U. S., Australia, Canada, and European nations have repeatedly identified China as a primary threat actor conducting sophisticated cyber operations against government, military, and private sector targets.
Notepad++'s user base includes government contractors, military organizations, defense companies, and intelligence agencies. These are exactly the types of organizations that Chinese intelligence would want to target for cyber espionage.
The 2020 Volt Typhoon operation, attributed to Chinese state actors, demonstrated a nearly identical operational pattern: accessing critical infrastructure, establishing persistent presence, maintaining access for extended periods, and moving laterally through networks with careful operational security. The Notepad++ attack follows similar patterns.
What Remains Unknown
Several critical details weren't disclosed, presumably to avoid tipping off the threat actors:
-
The specific Chinese intelligence agency or military unit: Attributing attacks to "Chinese state-sponsored actors" is accurate but broad. Actual attribution to specific units (MSS, PLA Unit 61398, etc.) requires additional evidence not publicly released.
-
The identity of targeted organizations: While the attack was highly selective, the advisory doesn't specify which organizations received tainted updates.
-
The malware payload: The specific capabilities of the malware delivered through the tainted updates weren't disclosed publicly.
-
The initial vulnerability: How the hosting provider's server was initially compromised wasn't disclosed.
The Source Code Was Never Compromised: Understanding What This Means
One of the most important details in the Notepad++ advisory is a statement that often gets overlooked: the attackers' goal was not to compromise the source code itself. This distinction is crucial because it illustrates the difference between two entirely different types of attack objectives.
Why Source Code Compromise Wasn't the Goal
If attackers successfully compromise source code, they can inject backdoors that persist in every future version of the software forever. This is the most dangerous kind of supply chain attack because it's nearly impossible to detect or remediate completely.
The Solar Winds breach is the classic example. Attackers compromised Solar Winds' source code repository and build infrastructure, injecting a backdoor into a library used by the monitoring software. This backdoor was included in legitimate, signed Solar Winds updates and distributed to approximately 18,000 customers.
If Notepad++ attackers had compromised source code, they could have injected a backdoor into version 8.5.0, version 8.6.0, and every future version. Even if the current compromise was discovered and fixed, the backdoor would persist in older versions and potentially in future versions if they failed to detect it.
The fact that the Notepad++ attackers didn't attempt source code compromise suggests several possibilities:
- They lacked the capability to escalate from hosting infrastructure access to source code repository access
- They had specific short-term objectives that didn't require persistence in source code
- Hosting infrastructure compromise was sufficient to accomplish their actual intelligence collection goals
- They intended to avoid detection and source code compromise is more likely to be discovered during code review
What Delivering Tainted Updates Actually Accomplishes
Instead, the attackers focused on delivering tainted updates to carefully selected targets. This accomplishes several operational objectives:
Direct System Compromise: Delivering malware to systems allows immediate execution of reconnaissance, data exfiltration, or establishment of backdoors.
Targeted Intelligence Collection: By controlling which victims receive the tainted updates, attackers can specifically target organizations of interest without burning their access on less important targets.
Reversibility: If attacks through one tainted update are discovered, the attacker can claim it was a one-time incident while maintaining their underlying access to the update infrastructure.
Deniability: Delivering malware through tainted updates is more deniable than modifying source code. Attackers can blame a system compromise without admitting to source code tampering.
For espionage operations (the likely objective of a state-sponsored actor), direct system compromise to targeted organizations is often sufficient. The goal isn't to permanently alter the software. The goal is to gain access to specific systems to steal information, establish persistence for long-term monitoring, or conduct lateral movement into connected networks.
Implications for Remediation
The fact that source code wasn't compromised means the fundamental security of Notepad++ wasn't undermined. Users don't need to distrust the Notepad++ project itself. They don't need to assume that future versions will contain hidden backdoors.
What they need to ensure is that they're running recent versions with proper update verification enabled. This shifts the responsibility to both users (keeping systems updated) and to Notepad++ (ensuring updates are properly verified).

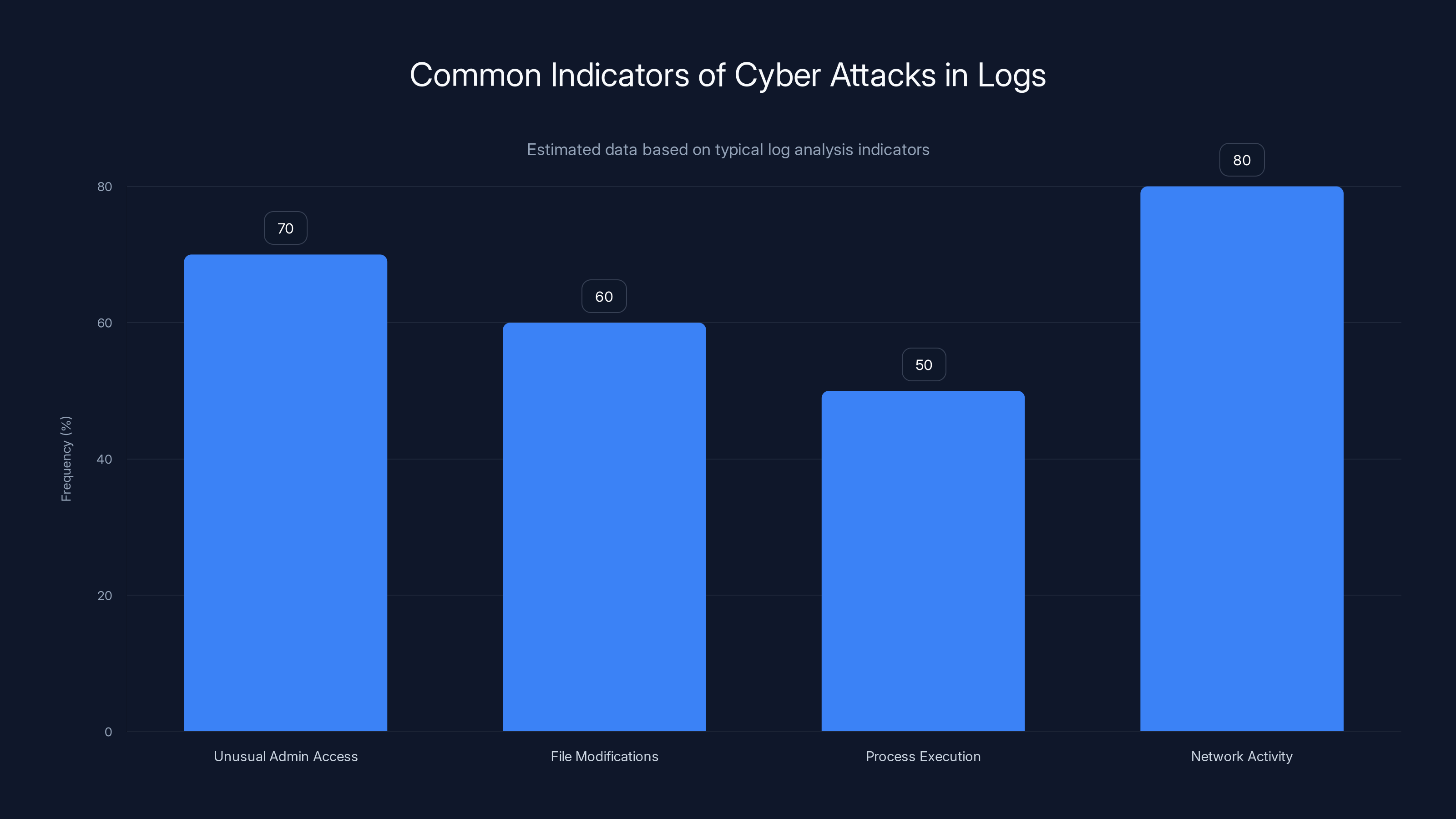
Estimated data shows that network activity and unusual administrative access are the most common indicators detected in logs during cyber attacks.
Notepad++'s Response: Technical Hardening Measures
After discovering the attack, Notepad++'s developers didn't just patch the vulnerability and move on. They implemented comprehensive hardening measures across multiple layers of the update infrastructure.
Infrastructure Migration
The first major step was migrating to new hosting infrastructure entirely. This removed the attackers' foothold and ensured they couldn't maintain access through remaining backdoors or credential reuse.
Migrating hosting infrastructure sounds straightforward but involves significant complexity:
- Provisioning new servers and configuring them from scratch
- Transferring all website files and configurations
- Updating DNS records to point to new servers
- Ensuring SSL/TLS certificates are properly configured for the new infrastructure
- Testing that all functionality works identically on the new infrastructure
- Maintaining uptime and service availability during the transition
The fact that this was completed by early December demonstrates that Notepad++ took the threat seriously and prioritized security over convenience.
Update Mechanism Overhaul
The updater was updated to version 8.8.9 with hardened verification controls. The specific improvements included:
Certificate Verification: The update system now verifies that the server's SSL/TLS certificate is valid, signed by a trusted certificate authority, and matches the expected domain. This prevents man-in-the-middle attacks where attackers intercept connection and serve their own certificates.
Installer Signature Verification: The downloaded installer file itself is now digitally signed. Before execution, the system verifies that the signature is valid and made by the legitimate Notepad++ publisher. This prevents attackers from modifying the installer even if they control the delivery point.
XML Manifest Signing: The XML file returned by the update server (which lists available versions and their properties) is now also digitally signed. This prevents attackers from manipulating update information.
Future Enforcement
Version 8.9.2 (expected approximately one month after the advisory) will enforce certificate and signature verification as mandatory requirements, not optional features. This means systems will refuse to install updates unless proper verification succeeds.
This enforcement was likely phased to give users time to update. If verification was enforced immediately for all users, older systems that hadn't updated would suddenly fail to receive updates, creating a security problem in a different way.
By making enforcement mandatory in a new version, Notepad++ ensures that users who update to 8.9.2 will have the enhanced protections active. Users on older versions remain protected by the improved update server and certificate verification, even if they haven't upgraded yet.
Comparison with Industry Best Practices
Notepad++'s response aligns with recommendations from cybersecurity authorities:
NIST Cybersecurity Framework: Recommends implementing secure development practices including code signing, secure distribution mechanisms, and integrity verification.
Microsoft Security Development Lifecycle (SDL): Emphasizes securing the build and distribution pipeline as a critical component of software security.
CISA Supply Chain Risk Management Guidance: Specifically recommends verifying software authenticity through digital signatures and establishing secure distribution mechanisms.
Notepad++'s response covered all these bases: new infrastructure (addresses environment security), certificate verification (addresses transport security), installer signing (addresses software integrity), and XML signing (addresses complete chain of trust).

Industry-Wide Implications: Why This Attack Matters Beyond Notepad++
The Notepad++ incident isn't just a problem for Notepad++ users. It's a signal about the state of software supply chain security across the entire industry and reveals systemic vulnerabilities that affect millions of software developers and end users.
Shared Hosting as a Single Point of Failure
Notepad++ being hosted on shared hosting infrastructure alongside other tenants created vulnerability exposure. If the shared hosting provider was breached, any tenant on that server became a potential target.
Many open-source projects and small software publishers use shared hosting because it's cost-effective and straightforward. This creates a systematic risk: attackers can compromise one hosting provider and potentially reach many software projects simultaneously.
The distinction between dedicated hosting (where you control an entire server) and shared hosting (where you share infrastructure with others) becomes critically important from a security perspective. When one tenant is compromised, other tenants become collateral damage.
Update Mechanism Security Across the Industry
The Notepad++ vulnerability specifically involved insufficient update verification. This isn't unique to Notepad++. Many legacy software projects implemented update mechanisms before modern security practices became standard.
A 2024 study of software update mechanisms found that approximately 23% of software tested lacked proper signature verification of updates. This means hundreds of millions of devices worldwide are running software with insufficient update security.
These legacy systems are attractive targets for attackers. The barriers to successful exploitation are lower than for modern systems with hardened security controls.
Nation-State Targeting of Developer Tools
Targeting Notepad++ is strategic because Notepad++ users include many security professionals, system administrators, software developers, and IT staff. These are exactly the people a state actor would want to compromise to gain access to critical infrastructure, military systems, or government networks.
Developer tools are attractive because they're often installed on systems with elevated privileges and have access to sensitive source code repositories and build infrastructure. Compromising a developer's machine can provide a foothold into an entire organization's development and deployment pipeline.
This trend is likely to continue. As attackers mature their tactics, we'll see increasing focus on supply chain attacks targeting the tools, libraries, and infrastructure that the security community itself relies upon.
The False Sense of Security
Many users assume that software from well-established, reputable open-source projects is inherently secure because it's open-source. The logic is that the source code is visible to thousands of security researchers, so backdoors would be quickly discovered.
The Notepad++ incident shows a critical gap in this thinking. The source code might be open and trustworthy. The problem can be entirely in the distribution mechanism. You could have the most secure source code in the world, but if an attacker can modify the installer after compilation, the final product delivered to users is compromised.
This requires users and organizations to trust not just the software project, but also the entire infrastructure around it: hosting providers, update servers, certificate authorities, and build systems.

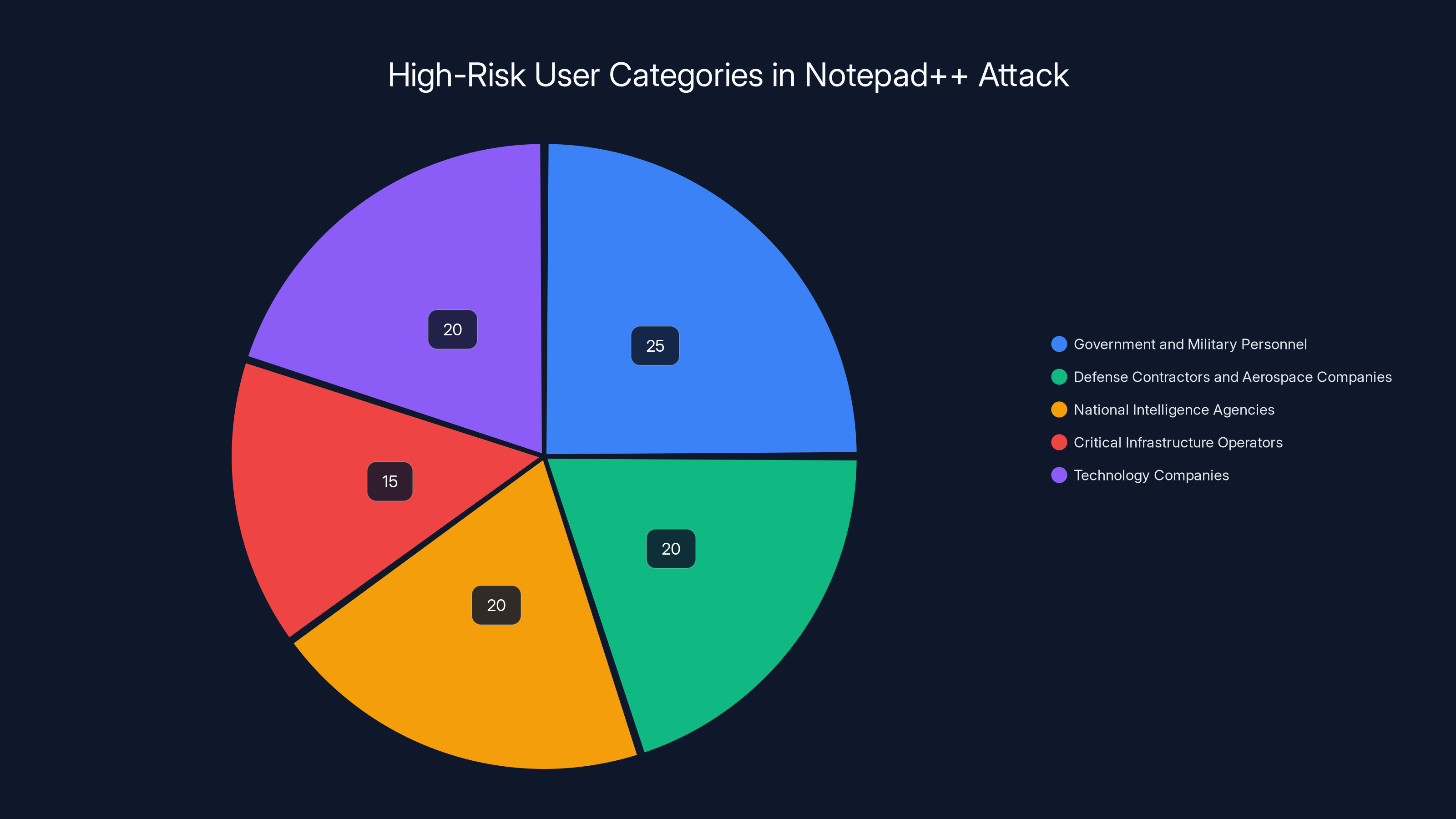
Estimated data shows that government and military personnel were the most targeted group, followed closely by defense contractors and technology companies. Estimated data.
Detection: How Was the Attack Discovered?
One detail the advisory doesn't fully explain is how the attack was actually discovered. Understanding detection mechanisms is crucial because many attacks go undetected for years.
Log Analysis and Anomaly Detection
The advisory mentions that "suspicious events in our logs" indicated the server could have been compromised. This suggests that Notepad++ (or the hosting provider on their behalf) was monitoring server logs for suspicious activity.
Common indicators that would appear in logs include:
- Unusual Administrative Access: Logins from unexpected IP addresses, logins at unusual times, administrative actions without corresponding tickets or change requests
- File Modifications: Changes to update distribution files, configuration files, or web content without corresponding authorized modifications
- Process Execution: Execution of unexpected processes, particularly processes known to be associated with common attack tools
- Network Activity: Outbound connections to known malicious IP addresses, data exfiltration patterns, connections to known command-and-control servers
Security teams typically use Security Information and Event Management (SIEM) systems to correlate these indicators across multiple data sources. A single log entry might seem innocent, but correlating multiple indicators can reveal attack patterns that wouldn't be obvious from individual data points.
Third-Party Investigation
The advisory mentions that an external investigation was conducted. This likely involved forensic analysis of the compromised systems, examining:
- File Integrity: Comparing files on the compromised system to known-good versions to identify modifications
- Timeline Reconstruction: Using file timestamps, log entries, and system artifacts to establish when compromise occurred and what was done during the compromise
- Artifact Analysis: Examining malware samples, configuration files, and tools left behind by attackers
- Network Traffic Analysis: Reviewing network logs to understand communication patterns
External investigations by professional incident response teams are often more thorough than internal investigations because they bring specialized expertise and can maintain objectivity.
User Reports
Users might have reported unusual behavior in Notepad++ (though this wasn't mentioned in the advisory). Users who received malicious updates might have noticed:
- System performance degradation
- Unexpected network connections
- Security software alerts
- Unusual system behavior
User reports, when correlated with other indicators, can help narrow down the timeframe of when malicious updates were delivered.

Risk Assessment: Who Was Actually at Risk?
The advisory states that attackers delivered tainted updates to a "handful of carefully selected victims." This phrasing is important because it means not every Notepad++ user who updated during the compromise period received malicious code.
High-Risk User Categories
Based on the attack's selectivity, certain user categories were likely at higher risk:
Government and Military Personnel: State-sponsored actors typically target government and military systems for intelligence gathering. Notepad++ users in government agencies would be high-value targets.
Defense Contractors and Aerospace Companies: Organizations working on classified or sensitive defense projects would be valuable intelligence targets.
National Intelligence Agencies: Intelligence agencies themselves would be targeted by foreign intelligence services.
Critical Infrastructure Operators: Organizations operating power grids, water treatment, telecommunications, and other critical systems would be valuable targets for gathering intelligence or establishing backdoors.
Technology Companies: Tech companies are often targeted for intellectual property theft and to establish presence in supply chains.
Lower-Risk User Categories
Casual users, students, and small businesses running Notepad++ faced lower risk because they would generally not be individually targeted by a state-sponsored intelligence operation. The targeting was selective and focused on specific high-value organizations.
However, even lower-risk users shouldn't dismiss the incident. If an organization they work for was targeted, their systems might have been compromised. Additionally, if update verification was weak enough for attackers to exploit, other threats might also be able to exploit the same weakness.
Mitigation for Potentially Affected Users
Users who might have received malicious updates during the June-December 2025 period should consider:
System Scanning: Running comprehensive antivirus and anti-malware scans. This won't detect all advanced malware, but it will catch common threats.
Credential Rotation: Changing passwords for sensitive accounts, particularly for systems that had recent Notepad++ updates. If attackers gained initial access through tainted updates, they might have used system access to harvest credentials.
Behavioral Analysis: Looking for signs of compromise: unexpected network connections, system performance degradation, new user accounts, scheduled tasks, or unusual administrative activity.
Update to Latest Version: Ensuring Notepad++ is updated to version 8.8.9 or later, which includes hardened update verification.
Assume Breach Mentality: For organizations with high security requirements, treating the potential compromise as a given and conducting defensive investigation accordingly. This is more thorough than hoping compromise didn't occur.

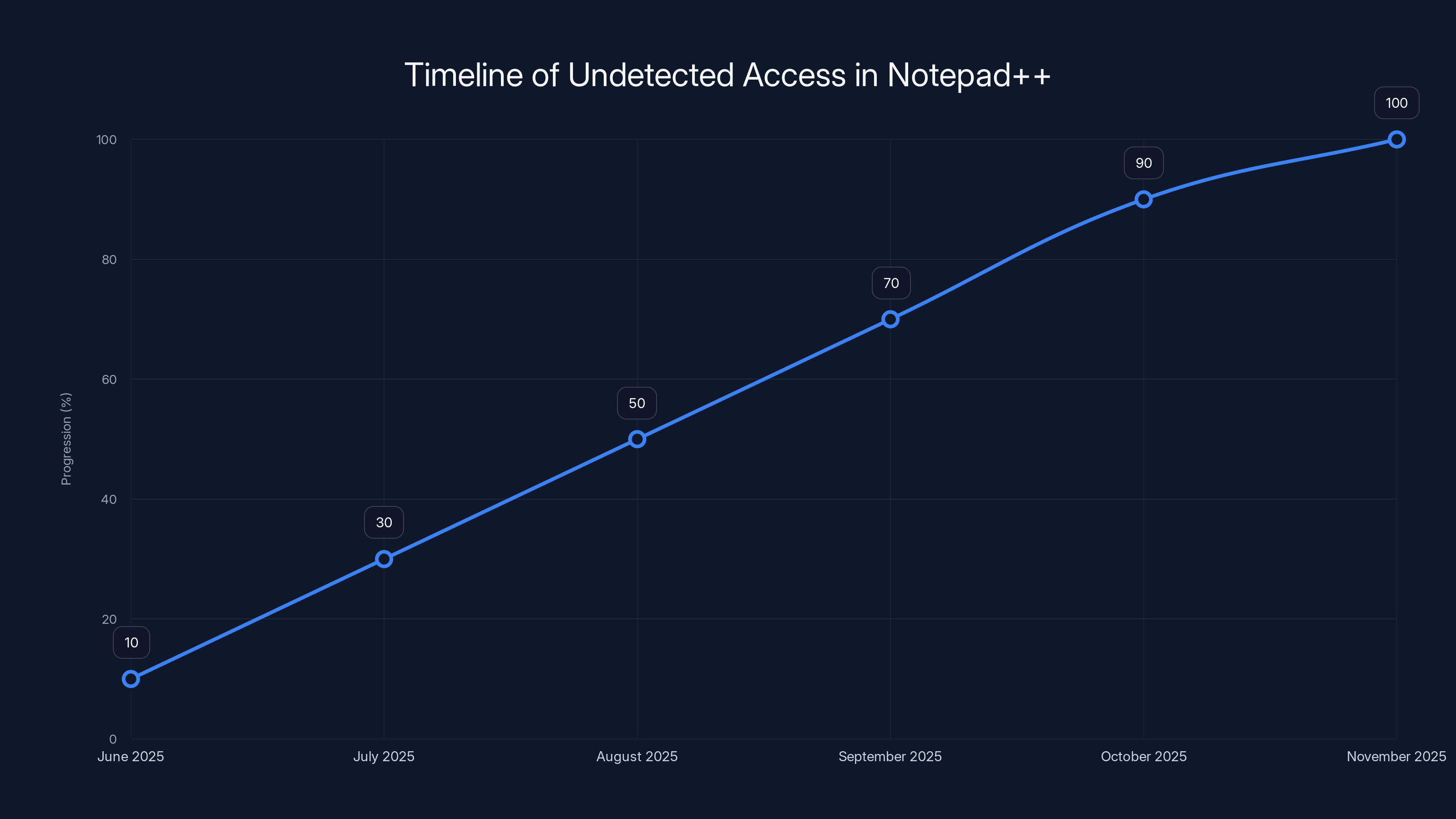
The attack on Notepad++ progressed methodically over six months, with key phases including initial compromise, weaponization, and delivery. Estimated data.
Lessons for Software Publishers and Maintainers
The Notepad++ incident provides crucial lessons for anyone responsible for distributing software to users.
Prioritize Update Mechanism Security
The update mechanism is the direct line between your software and users' systems. Compromise of this channel is equivalent to complete compromise of the software from a user's perspective.
Update mechanisms should be secured with:
- Cryptographic Signature Verification: Verify that updates are digitally signed by legitimate keys
- Secure Key Storage: Store signing keys in hardware security modules (HSMs) with restricted access
- Secure Delivery: Deliver updates over HTTPS with proper certificate validation
- Integrity Verification: Verify file hashes and signatures before execution
- Staged Rollouts: Deploy updates to small percentages of users first, monitoring for problems before broad rollout
Infrastructure Security is Foundational
Regardless of how secure your application code is, if the infrastructure that hosts and distributes it is insecure, the entire system is vulnerable.
Infrastructure security includes:
- Access Controls: Restricting who can access production infrastructure and requiring multi-factor authentication
- Monitoring and Logging: Comprehensive logging of all actions in production systems and active monitoring for anomalies
- Patching and Updates: Maintaining current patches on all infrastructure components
- Incident Response Planning: Having documented procedures for responding to suspected compromises
- Regular Security Audits: Periodic security assessments of infrastructure by qualified professionals
Isolation and Least Privilege
The fact that the Notepad++ update server was on shared hosting infrastructure with other tenants created cross-contamination risk. Attackers who breached the hosting provider could reach any tenant.
For software distribution infrastructure, consider:
- Dedicated Infrastructure: Using dedicated servers rather than shared hosting for critical infrastructure
- Network Segmentation: Isolating update servers from general web infrastructure
- Minimal Services: Running only necessary services on distribution infrastructure, reducing attack surface
- Immutable Infrastructure: Using infrastructure-as-code and containerization to ensure infrastructure is consistent and reproducible
Supply Chain Risk Management
Software distribution depends on multiple third parties: hosting providers, certificate authorities, domain registrars, content delivery networks. The security of your software distribution is only as strong as the weakest link in this chain.
Manage supply chain risks by:
- Vendor Security Assessment: Evaluating security practices of all third parties involved in distribution
- Contractual Security Requirements: Including specific security requirements in contracts with third parties
- Redundancy: Having backup infrastructure and distributions channels so a single provider's compromise doesn't completely disrupt service
- Threat Intelligence: Staying informed about threats to third-party services

Broader Context: State-Sponsored Targeting of Software Infrastructure
The Notepad++ attack didn't occur in isolation. It's part of a broader trend of nation-states targeting software development and distribution infrastructure as strategic assets.
The Value of Developer Tool Compromise
Developer tools occupy a privileged position in software ecosystems. A compromised text editor, compiler, build system, or code repository affects not just the direct users of the tool, but all software produced by those users.
This creates a multiplier effect. Compromising a software tool used by 100 developers might indirectly affect 1,000 applications built by those developers, affecting millions of end users.
Different developer tools offer different value:
Text Editors and IDEs: Direct access to developers' systems, which often have elevated privileges and access to sensitive source code and credentials.
Build Systems and Compilers: The ability to inject code into compiled binaries, affecting all software built with the compromised tools.
Package Managers and Repositories: Access to distribute malware to software developers when they install dependencies.
Version Control Systems: Access to source code repositories and the ability to commit malicious code that might not be immediately noticed.
State actors pursuing long-term espionage or preparing for potential future conflicts would prioritize compromising these tools to establish infrastructure for future operations.
International Coordination Against Supply Chain Attacks
Recognizing the severity of supply chain threats, governments have begun coordinating responses:
The U. S. signed an executive order on cybersecurity that specifically addresses software supply chain security. Multiple countries have announced vendor security assessment programs. International standards bodies have published software supply chain security guidelines.
These coordinated efforts acknowledge that supply chain attacks are a strategic threat to national security, not just a technical problem for individual organizations to solve.
The Arms Race Dynamic
Supply chain security is becoming an arms race between defenders and attackers:
Defenders: Implementing stricter verification, monitoring, and incident response capabilities
Attackers: Developing more sophisticated techniques to evade detection, establish persistence, and maintain access
Historically, attackers have an advantage in this dynamic because defenders must secure every possible attack surface, while attackers only need to find one weakness. This asymmetry means defenders must continuously improve their practices even just to maintain current security levels.
Remediation Steps for Organizations and Users
If you're responsible for Notepad++ deployment in your organization or concerned about potential compromise, here are concrete remediation steps.
For IT Administrators and Organizations
Immediate Actions (Within 24 Hours):
-
Audit Notepad++ versions across your organization using endpoint management tools. Identify all systems running pre-8.8.9 versions.
-
Disable auto-update for Notepad++ until systems are updated to 8.8.9 or later. This prevents any potentially compromised systems from receiving "updates" that might be part of ongoing attacks.
-
Check firewall and proxy logs for any suspicious outbound connections from systems that had Notepad++ installed during June-December 2025. Look for connections to known malicious IP addresses or unusual destinations.
-
Review administrative access logs for systems with Notepad++ installed. Look for unusual administrative sessions, particularly from external IP addresses or at unusual times.
Short-Term Actions (1-2 Weeks):
-
Deploy Notepad++ 8.8.9 or later to all systems through controlled channels. Use your organization's software deployment mechanisms to ensure version control and install verification.
-
For systems that might have received malicious updates, consider running malware scans and system hardening procedures even if no obvious compromise is detected.
-
Implement application whitelisting on systems with Notepad++ to restrict what programs can execute. This prevents many types of malware from running even if Notepad++ was compromised.
-
Require multi-factor authentication for all sensitive systems and services accessed by developers and system administrators. This limits damage if credentials were stolen.
Long-Term Actions (Ongoing):
-
Implement software asset management to continuously monitor which versions of software are deployed across your organization.
-
Establish a vendor risk management program to assess and monitor the security practices of critical third parties, including software vendors and hosting providers.
-
Conduct security awareness training for developers and system administrators about supply chain risks and appropriate security practices.
-
Develop and test incident response procedures specifically for supply chain attacks and software compromise scenarios.
For Individual Users
Verification of Your Current Version:
- Open Notepad++
- Click "Help" menu
- Click "About Notepad++"
- Check the version number in the dialog
If your version is earlier than 8.8.9, update immediately.
Updating to the Latest Version:
- In Notepad++, click "Help" menu
- Select "Check for Update"
- Follow prompts to download and install the latest version
- Alternatively, visit the Notepad++ website and manually download version 8.8.9 or later
Verification After Update:
- After updating, verify you're running the new version using the steps above
- Check that the installation date is recent (today or very recently)
- Restart Notepad++ to ensure the new version is fully loaded
If You Suspect Compromise:
- Run a full antivirus/anti-malware scan of your system
- Change passwords for sensitive accounts, particularly email, banking, and work accounts
- Consider using a password manager if you aren't already, to detect if unauthorized password changes occur
- Enable multi-factor authentication on important accounts
- Monitor accounts for suspicious activity
What This Tells Us About Future Threats
The Notepad++ attack reveals important patterns about how cybersecurity threats are evolving and what we can expect in the future.
The Increasing Sophistication of State-Sponsored Attacks
Nation-states have essentially unlimited budgets, years of operational planning capability, and access to intelligence that private actors don't have. State-sponsored attacks are becoming increasingly sophisticated as these actors bring military and intelligence agency resources to bear on cybersecurity problems.
We can expect future attacks to:
- Target Earlier in Supply Chains: Rather than just targeting end-use software, attackers will compromise components and libraries that multiple projects depend on.
- Persist Longer: We'll see more attacks that maintain access for extended periods (months or years) while gathering intelligence rather than immediately launching visible attacks.
- Operate More Stealthily: Attacks will be designed to avoid detection through careful operational security and minimal impact on system performance.
- Use Legitimate Credentials More Often: Rather than exploiting vulnerabilities, attackers will obtain legitimate credentials (through phishing, insider threats, or previous compromises) and use normal authentication mechanisms.
The Shift From Direct Attacks to Supply Chain Attacks
Direct attacks (attacking an organization directly) are becoming harder as organizations improve security. Supply chain attacks require fewer sophisticated exploits because defenders must protect entire ecosystems, which is inherently harder than protecting a single organization.
We can expect the ratio of supply chain attacks to direct attacks to increase. A 2024 analysis found that supply chain attacks now account for approximately 45% of all reported cyber attacks, up from about 15% in 2018.
The Inadequacy of Individual Organization Security
Notepad++ demonstrates that even well-maintained open-source projects can become vehicles for attack. No organization can fully protect itself if the infrastructure it depends on is compromised.
This requires:
- Ecosystem-Level Security Thinking: Organizations need to consider not just their own security, but the security of vendors, suppliers, and infrastructure they depend on.
- Shared Threat Intelligence: Organizations need to share information about threats with peers and through industry organizations.
- Regulatory Approaches: Governments may increasingly mandate security standards for critical software and infrastructure providers.
The Growing Role of Automation and AI in Cybersecurity
As attacks become more sophisticated, human-driven security responses become insufficient. We'll see increasing automation in:
- Threat Detection: Machine learning models identifying anomalous behavior in logs and network traffic
- Incident Response: Automated responses to detected threats, such as isolating systems or blocking suspicious connections
- Vulnerability Assessment: Automated scanning identifying vulnerable components in supply chains
- Malware Analysis: Automated tools analyzing malware behavior and providing threat intelligence
The organizations most effective at cybersecurity will be those that successfully blend human expertise with automated systems.

Industry Response and Recommendations
Following the Notepad++ disclosure, cybersecurity organizations and authorities have provided guidance for improving supply chain security across the industry.
CISA Recommendations
The U. S. Cybersecurity and Infrastructure Security Agency (CISA) has emphasized:
- Software Provenance Verification: Implementing systems to verify the source and integrity of software throughout the supply chain
- Zero Trust Principles: Requiring verification at every step rather than assuming trusted sources are secure
- Secure Development Practices: Mandating security practices for organizations producing critical software
- Incident Disclosure Requirements: Requiring timely disclosure of vulnerabilities and breaches
Industry Best Practices
The Information Security Industry Association has recommended:
- Software Bill of Materials (SBOM): Maintaining detailed records of all components in software products
- Dependency Management: Tracking dependencies on third-party libraries and components
- Security Testing: Automated security testing of software at build time
- Code Signing: Requiring cryptographic signatures for all distributed software
Emerging Standards
New standards are being developed specifically for supply chain security:
- SLSA Framework (Supply chain Levels for Software Artifacts): A framework for evaluating the trustworthiness of software artifacts based on the security practices used to produce them.
- NIST Secure Software Development Framework (SSDF): Guidelines for secure software development practices.
- ISO/IEC 42010: Standards for architecture and design documentation that can improve security analysis.

FAQ
What exactly happened with Notepad++?
Notpad++ was targeted by suspected Chinese state-sponsored attackers who compromised the hosting provider's server where Notepad++ was hosted. From June to December 2025, attackers delivered tainted updates to carefully selected victims, exploiting weak update verification controls in older versions of Notepad++. The source code was never compromised. Notepad++ responded by migrating to new hosting, implementing hardened certificate and signature verification, and releasing updates with enhanced security controls.
How can I tell if my Notepad++ installation was affected?
You cannot definitively determine if your installation received a malicious update without specialized forensic analysis. However, you can check your version number (Help > About) and ensure you're running version 8.8.9 or later, which includes hardened update verification. If you're concerned about possible compromise, run antivirus scans, change important passwords, and enable multi-factor authentication on sensitive accounts.
Should I stop using Notepad++?
No. Notepad++ remains a legitimate and widely-used text editor. The vulnerability was in the update mechanism and hosting infrastructure, not in the core application itself. By updating to version 8.8.9 or later and ensuring automatic updates are enabled, you benefit from the improved security measures Notepad++ implemented in response to this incident. Switching to different software isn't necessary unless you have other reasons to change.
Why did it take so long to detect this attack?
Advanced persistent threat (APT) operations are designed to avoid detection. The attackers used legitimate credentials (after the initial access was established), limited their targeting to avoid drawing attention, and maintained careful operational security. Many sophisticated attacks go undetected for months or years. Detection often occurs through forensic analysis after a tip-off from threat intelligence, user reports, or through cooperation with hosting providers who conduct regular security reviews.
What does "supply chain attack" mean?
A supply chain attack targets an organization indirectly by compromising a trusted intermediary that the target organization depends on. Rather than attacking the target directly, attackers compromise a trusted supplier, vendor, or service provider. The Notepad++ attack was a supply chain attack because attackers compromised the hosting provider and update distribution mechanism rather than attacking users' systems directly.
How likely is my organization to be targeted?
The Notepad++ attack specifically targeted government, military, and defense-related organizations. Private sector companies in non-sensitive industries face lower risk from state-sponsored attacks. However, all organizations should assume some risk from sophisticated attackers and implement appropriate defenses. The principle of assuming breach and implementing defense-in-depth applies regardless of your assessment of targeting likelihood.
What can I do to protect against supply chain attacks?
Implement layered defenses: verify software sources and signatures, monitor for unexpected system behavior, require multi-factor authentication, implement application whitelisting to restrict what software can execute, keep systems patched and updated, monitor network traffic for suspicious connections, and maintain regular backups. At an organizational level, assess vendor security practices, require vendors to follow secure development practices, and maintain incident response procedures specifically for supply chain compromises.
Will there be charges or lawsuits against the hosting provider?
Lawsuits are possible but typically face challenges. Hosting providers generally have terms of service that limit their liability for security breaches. However, if the hosting provider failed to implement reasonable security practices (such as timely patching) or failed to disclose the breach appropriately, liability arguments become stronger. Regulatory agencies in affected countries might also investigate and potentially impose fines if specific security regulations were violated.
Conclusion: The New Reality of Software Security
The Notepad++ attack represents a turning point in how we need to think about software security. For decades, the focus has been on securing individual applications and organizations. Notepad++ demonstrates that this approach is insufficient. Software security today requires securing entire ecosystems: the infrastructure that hosts code, the systems that build applications, the mechanisms that distribute updates, and the supply chains that connect all these components.
For users, the immediate takeaway is simple: update Notepad++ to version 8.8.9 or later and ensure automatic updates remain enabled. The developers behind Notepad++ responded quickly and thoroughly to eliminate the vulnerability and harden their update mechanisms.
But the broader implications are more profound. This attack illustrates that supply chain security is now a critical concern for all organizations. Whether you use Notepad++, install open-source libraries, rely on cloud services, or use commercial software, your security depends on the security of your entire supply chain.
State-sponsored actors have demonstrated sophisticated capabilities in targeting developer tools and infrastructure. This capability will only increase as nations recognize the strategic value of compromising the tools and infrastructure that underpin digital systems.
The response requires action at multiple levels. Individual users must keep software updated and maintain good security practices. Organizations must implement vendor risk assessment programs and secure development practices. Governments must establish standards and regulations for critical software security. Industry must adopt supply chain security frameworks and share threat intelligence.
The Notepad++ incident won't be the last supply chain attack. More attacks like this will occur. But each incident that's detected and disclosed provides lessons that help the entire industry improve. The response to Notepad++ demonstrates that when developers, security researchers, and organizations work together, they can detect advanced attacks, understand how they work, and implement protections.
The future of cybersecurity depends on our collective ability to secure supply chains. Notepad++ is just one example of how that work is being done.
Quick Tips for Implementation:
Key Takeaways
- Chinese state-sponsored attackers compromised Notepad++'s hosting provider from June to December 2025, delivering tainted updates to select high-value targets
- Attack exploited weak update verification controls in older Notepad++ versions; source code was never compromised
- Update to version 8.8.9 or later immediately to benefit from hardened certificate verification, installer signatures, and XML manifest signing
- Supply chain attacks are a strategic threat tool for nation-states; expect similar attacks on other developer tools and software infrastructure
- Organizations must implement vendor risk assessment, monitor for behavioral anomalies, and assume breach mentality for potential compromise scenarios
Related Articles
- Notepad++ Supply Chain Attack: What You Need to Know [2025]
- SonicWall Breach Hits Marquis Fintech: What Banks Need to Know [2025]
- Notepad++ Supply Chain Attack: Chinese Hackers Hijack Updates [2025]
- Notepad++ Server Hijacking: Inside the Six-Month Supply Chain Attack [2025]
- ShinyHunters SSO Scams: How Vishing & Phishing Attacks Work [2025]
- Agentic AI Security Risk: What Enterprise Teams Must Know [2025]
![Notepad++ Supply Chain Attack: Chinese State Hackers Explained [2025]](https://tryrunable.com/blog/notepad-supply-chain-attack-chinese-state-hackers-explained-/image-1-1770118651660.jpg)



