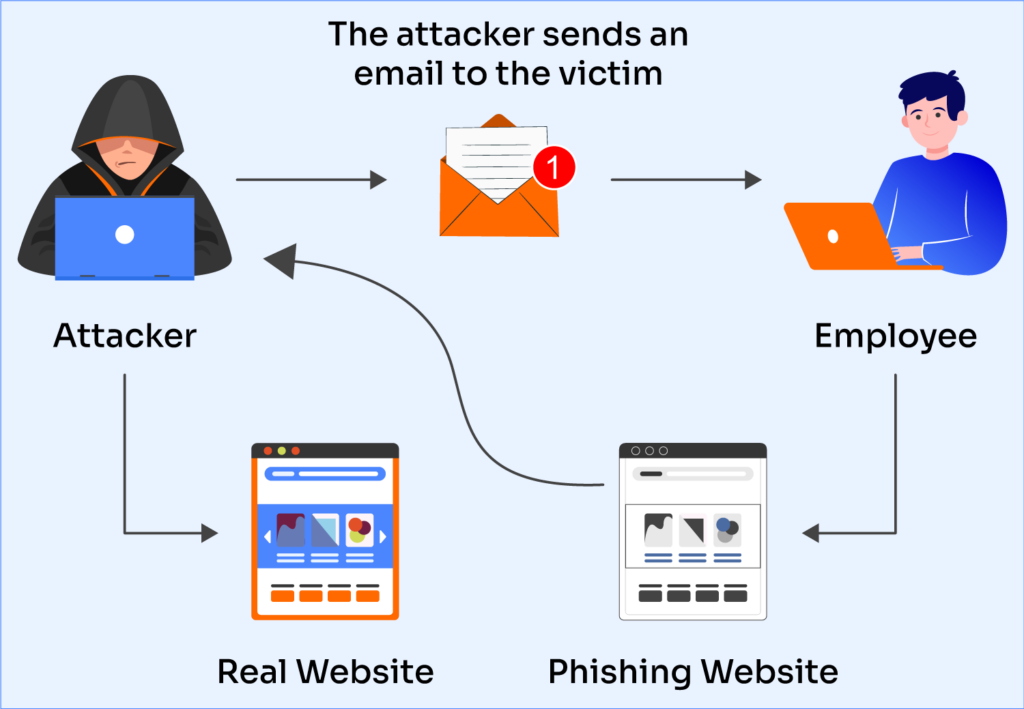
Internal Message Spoofing Phishing Campaign: How to Stop It
You get a message that looks like it came from your IT department. The sender address checks out. The tone matches other internal emails you've seen. But it's not from IT. It's from a criminal sitting in another country, and they're about to steal your credentials.
This isn't theoretical. It's happening right now, and it's working with terrifying efficiency.
A sophisticated phishing campaign is exploiting a fundamental weakness in how many organizations configure their email systems. By abusing misconfigured servers and weak email authentication protocols, attackers are sending emails that appear to come from inside your company. They're using legitimate-looking spoofed domains, familiar sender names like HR or IT, and themed lures around voicemail notifications, password resets, and shared documents. The victims don't see a red flag. The email looks internal. So they click.
What makes this campaign particularly dangerous is its scale and sophistication. We're not talking about a handful of poorly crafted emails. This is a broad, non-targeted campaign distributing thousands of phishing attempts through misconfigured infrastructure. And once attackers steal credentials through these initial phishing attacks, they don't stop there. They launch secondary Business Email Compromise (BEC) attacks, targeting the entire organization with well-researched, personalized social engineering.
The scary part? Your organization might already be vulnerable right now. Most companies don't realize their email infrastructure has these weaknesses until it's too late.
In this guide, we'll walk through exactly how this phishing campaign works, why traditional email authentication is failing, and what you need to do immediately to protect your organization. We'll also show you the specific attack tactics, the tools attackers are using, and the remediation steps your security team needs to implement today.
TL; DR
- The Core Vulnerability: Misconfigured email servers allow attackers to spoof your company's domain, bypassing SPF, DKIM, and DMARC authentication checks entirely
- The Attack Scale: Thousands of phishing emails are sent through legitimate-looking internal sender addresses using the Tycoon 2FA kit and similar phishing frameworks
- The Credential Theft: Victims receive emails about voicemails, password resets, HR communications, or shared documents, then enter credentials on fake login pages
- The Secondary Wave: Stolen credentials trigger Business Email Compromise attacks that target executives, finance teams, and other high-value targets
- The Fix Required: Strict DMARC enforcement, SPF hardening, DKIM implementation, and email gateway monitoring are non-negotiable
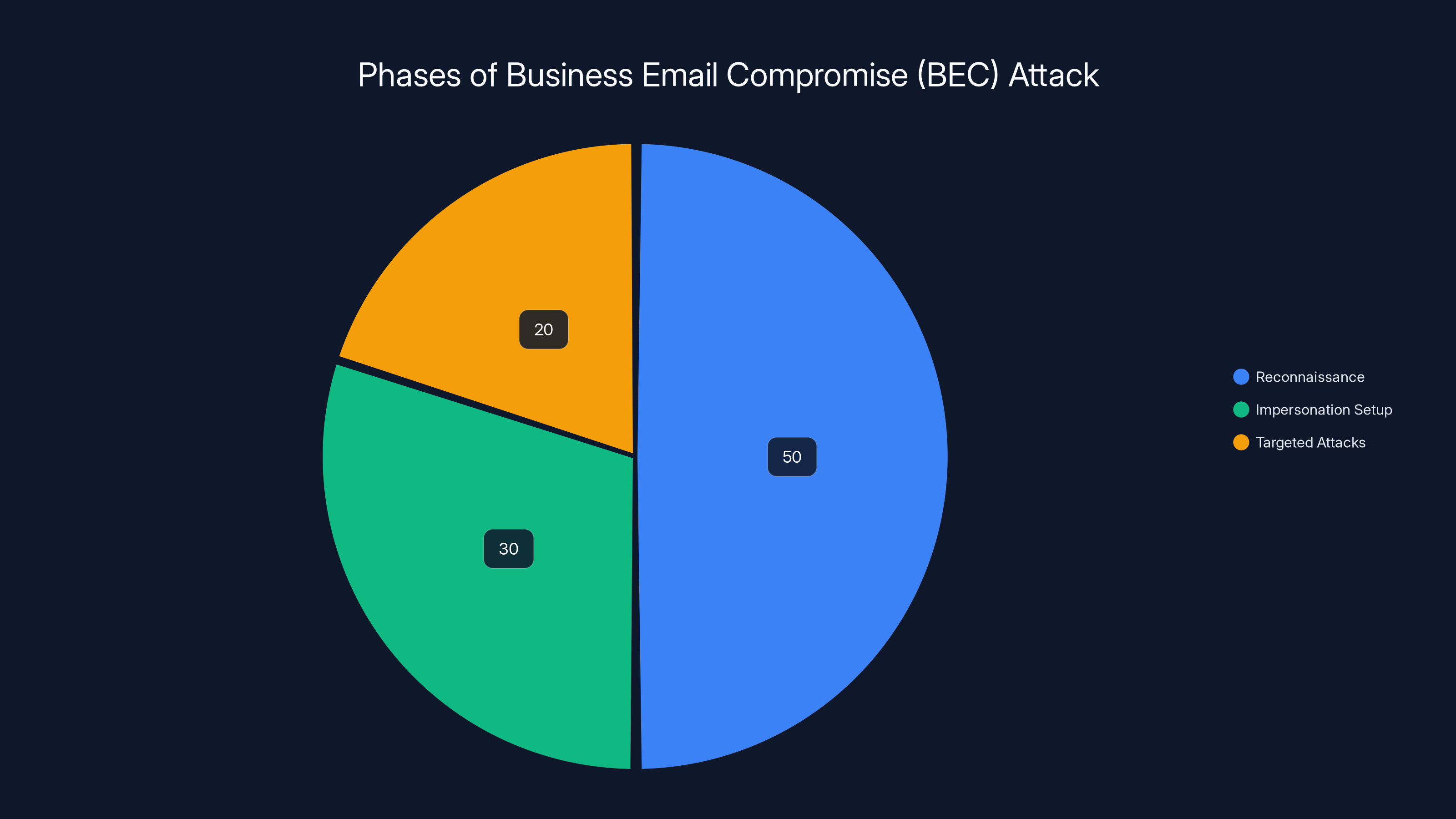
Estimated data: Reconnaissance is the most time-consuming phase, requiring 50% of the effort, followed by Impersonation Setup at 30%, and Targeted Attacks at 20%.
Understanding Email Spoofing: The Foundation of the Attack
Before we get into how this specific campaign works, you need to understand email spoofing at a fundamental level. Most people think email authentication is simple: a server checks the sender, verifies the domain, and either accepts or rejects the message. In reality, email authentication is a patchwork of older protocols that were designed decades ago and have been bolted together in ways that create security gaps.
Here's the basic problem: SMTP (Simple Mail Transfer Protocol), which moves email across the internet, has almost no built-in security. When an email leaves a server, it doesn't inherently prove where it came from. The "From" header can say literally anything. Any attacker with access to an email server (their own or a compromised one) can send a message claiming to be from anyone.
This is where SPF, DKIM, and DMARC come in. These are email authentication mechanisms designed to verify that an email actually came from the organization it claims to represent. But here's where it gets complicated: they only work if implemented correctly, and many organizations implement them incorrectly.
The critical vulnerability: many organizations set DMARC policy to "none" instead of "reject." This means when an email fails authentication, the server still accepts it and delivers it to the inbox. The victim never knows the email failed verification.
Why do organizations do this? Because they have complex email infrastructure. They route emails through third-party services. They have multiple mail servers. They use cloud email services alongside on-premises systems. Adding legitimate business partners to their email flow. In these complex setups, strict authentication can accidentally block legitimate internal emails. So security teams set DMARC to "none" or "quarantine" just to keep the system running.
Attackers exploit this misconfiguration ruthlessly.
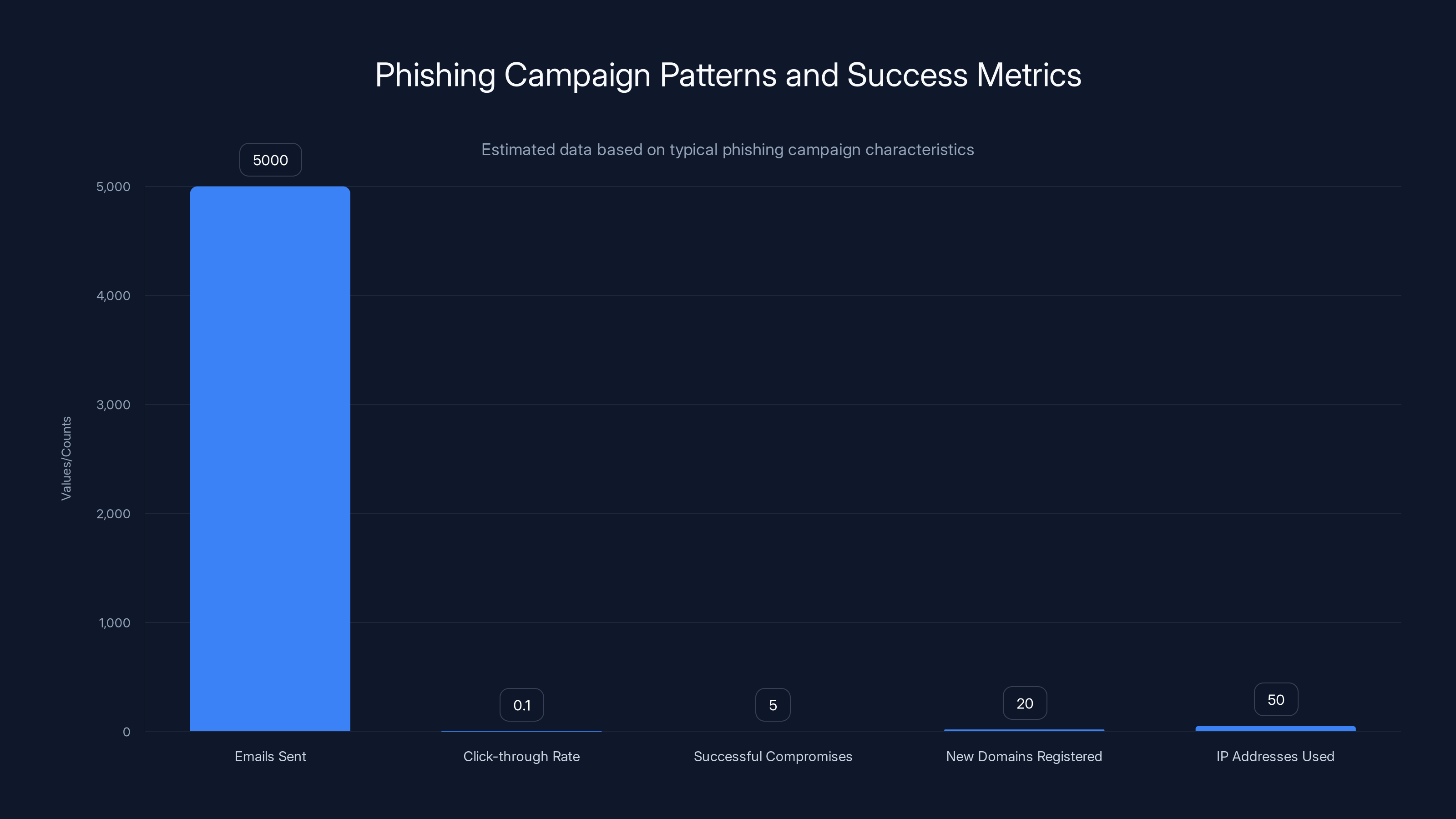
This bar chart illustrates key aspects of a broad-based phishing campaign. Despite a low click-through rate of 0.1%, the high volume of emails sent results in multiple successful compromises. Estimated data based on typical patterns.
How Email Infrastructure Misconfigurations Create Attack Surface
Let's talk about why so many organizations have weak email authentication in the first place. It's not usually because security teams don't understand the risks. It's because modern email infrastructure is absurdly complex.
A typical enterprise email setup might include:
- On-premises Microsoft Exchange servers handling internal routing
- Microsoft 365 cloud-hosted email for hybrid workers
- Third-party email security gateways (like Proofpoint, Mimecast, or similar services) for filtering and DLP
- Saa S applications that send transactional emails (Salesforce, Hub Spot, etc.) using your domain
- Managed service providers (MSPs) that handle backup or archival
- Business partners who send emails using your domain for joint projects
- Email forwarding rules that route messages to multiple systems
Each of these systems needs to be authorized in your SPF record. Your SPF record might look something like this:
v=spf 1 include:_spf.microsoft.com include: sendgrid.net include: mimecast.com ip 4:192.168.1.5 ~all
Now here's the problem: if even one of those included services is misconfigured, or if one service is compromised, attackers can exploit it. And if you don't have DKIM signatures being verified, or if your DMARC policy doesn't enforce strict rejection, an attacker can send emails from an unauthorized server that still pass through your gateway.
This is exactly what's happening in the current campaign. Attackers are identifying organizations with:
- Complex email routing through multiple third-party services
- Weak DMARC enforcement (set to "none" or "quarantine")
- Missing DKIM verification on inbound messages
- Email gateways that don't verify authentication strictly
Once they've identified a target with these weaknesses, they route phishing emails through legitimate email infrastructure (sometimes their own compromised servers, sometimes compromised third-party services) that passes the target's SPF check. The email shows the company's domain as the sender. The gateway doesn't strictly reject it. And it lands in the victim's inbox looking like an internal message.
The Tycoon 2FA Phishing Kit: The Attacker's Toolkit
Now that we understand the vulnerability, let's talk about the tools attackers use to exploit it. The primary phishing kit being used in this campaign is called Tycoon 2FA, though variations and similar kits are also in circulation.
Tycoon 2FA isn't new technology. It's a known phishing-as-a-service kit that's been circulating in underground forums for years. But it's effective because it automates the entire phishing campaign: sending emails, hosting fake login pages, capturing credentials, and logging successful attacks.
The kit includes pre-built phishing email templates themed around:
- Voicemail notifications: "You have a new voicemail message waiting. Click here to listen." These prey on the natural urgency of checking messages.
- Password reset notifications: "Your password will expire in 24 hours. Click here to reset it." This triggers compliance-conscious employees who don't want to break policy.
- HR communications: "New benefits package update. Click here to review your options." These target employees during benefits enrollment periods.
- Shared document notifications: "A colleague has shared a document with you. Click here to view." This exploits collaboration workflows.
- Two-factor authentication failures: "Your login attempt failed. Verify your identity here." This is particularly effective after legitimate login failures.
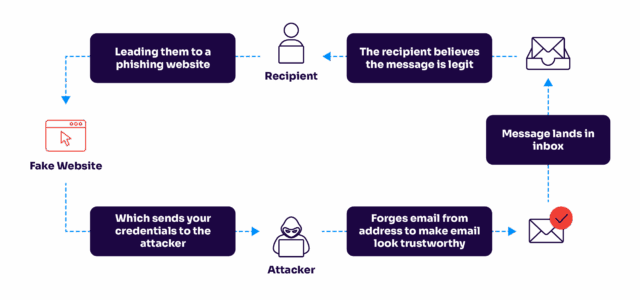
Each template includes the spoofed company domain as the sender. Each includes authentic-looking company branding (logos, colors, fonts) that the attacker has scraped from the company website. Each includes a legitimate-looking subject line. And each includes a link to a fake login page controlled by the attacker.
When a victim clicks the link, they're taken to a fake Microsoft 365 login page, a fake Gmail login, or a spoofed company portal. The page looks authentic because it's a pixel-perfect copy of the real thing. The victim enters their credentials. The attacker captures them. And then the fake page redirects to the real login page, so the victim doesn't realize anything went wrong.
Here's where it gets worse: the attacker now has the victim's credentials. If the victim uses the same password elsewhere, that's one more compromise. But more importantly, those credentials grant the attacker access to the victim's email account, which is the gateway to everything else in the organization.

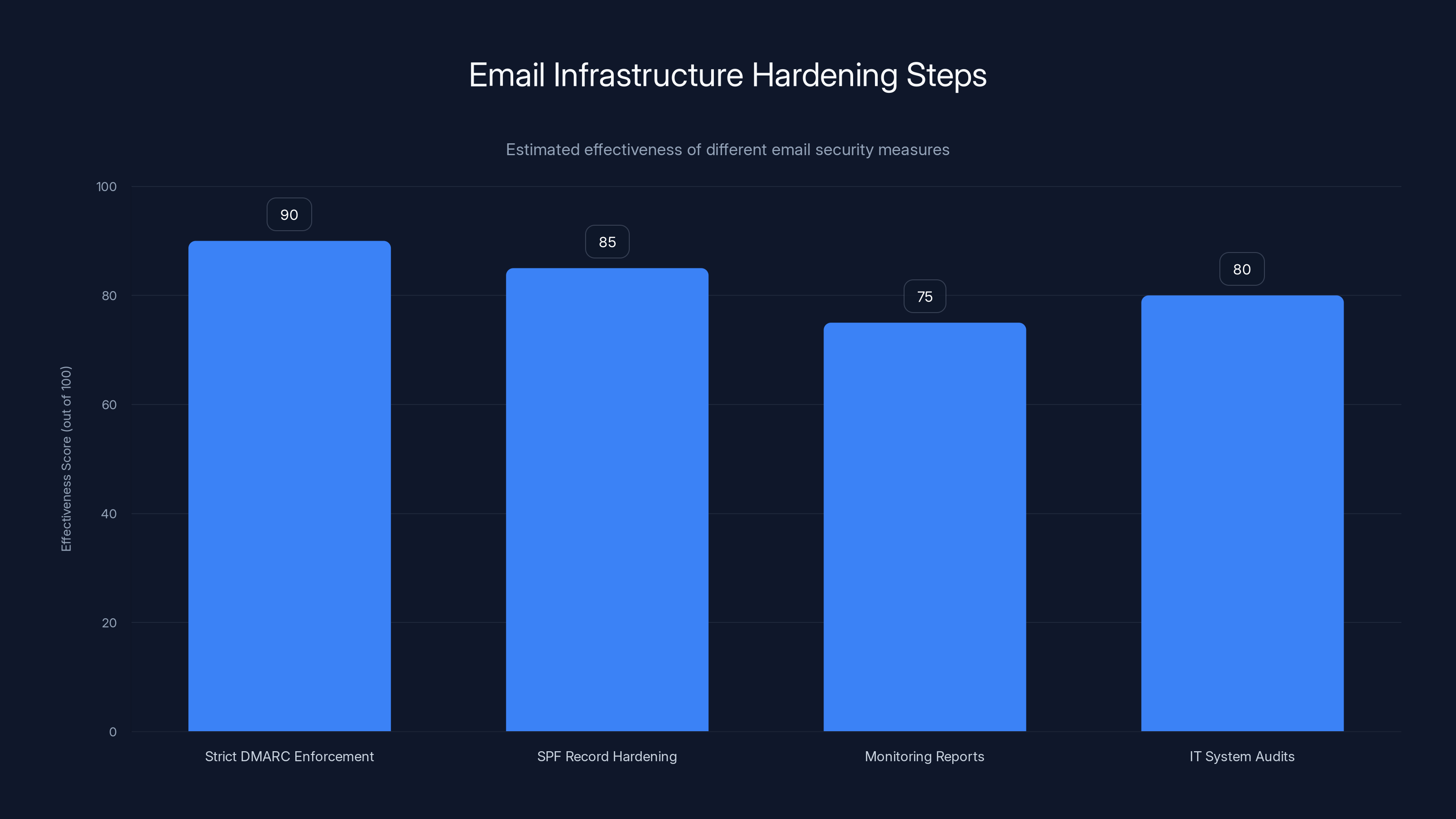
Implementing strict DMARC enforcement is estimated to be the most effective measure in hardening email infrastructure, followed closely by SPF record hardening. (Estimated data)
The Secondary Attack: Business Email Compromise
Once attackers have stolen credentials through the initial phishing attack, the campaign doesn't end. This is where it becomes a serious threat to the entire organization.
The stolen credentials are used to launch Business Email Compromise (BEC) attacks, also called Email Account Takeover (EAT) attacks. Unlike the initial broad phishing campaign, these attacks are highly targeted, research-intensive, and personalized.
Here's how it works:
Phase 1: Reconnaissance
Attackers study the compromised email account. They read through existing emails to understand the company's organizational structure, communication patterns, project timelines, and relationships. They identify who reports to whom. They find out which executives have budget authority. They discover ongoing projects and partnerships. They learn how the company's finance team works, who approves expenses, and what thresholds require different levels of approval.
This intelligence gathering is thorough and time-consuming, but it's necessary to make the attack believable.
Phase 2: Impersonation Setup
Attackers create email accounts that look similar to real accounts. Instead of using compromised accounts directly (which might alert the real user when they try to log in), they create lookalike accounts. An executive's account might be "j.smith@company.com", but the attacker creates "j.smith@companyw.com" or uses a display name like "James Smith" while the actual email address is different.
They also create rules to forward emails. If a subordinate's account has been compromised, attackers set up forwarding rules to send copies of incoming emails to an attacker-controlled account. This lets them monitor responses in real-time and respond quickly to questions.
Phase 3: Targeted Attacks
With their research complete and their infrastructure set up, attackers launch highly targeted BEC attacks against specific individuals:
- Finance team: "I need a wire transfer approved immediately for an urgent vendor payment. Please process this invoice for $50,000 and send me confirmation." The email includes spoofed vendor invoices with the attacker's wire instructions.
- HR department: "We have a new executive joining next week. Please process their onboarding. Their salary should be wired to this account starting next Friday." Complete with forged offer letters and banking details.
- Procurement: "Update our payment details with this vendor. All future invoices should go to this account." Subsequent legitimate invoices then get rerouted to the attacker.
- Executive requests: "Can you wire $100,000 to complete this acquisition? This is confidential, so don't discuss it with anyone else." This exploits the natural reluctance of subordinates to question executive authority.
Each of these attacks is researched, personalized, and designed to trigger immediate action. The attacker isn't blasting out thousands of emails hoping for a few hits. They're targeting specific people with specific requests, and they've done their homework.
These attacks work with alarming frequency. According to industry reports, BEC attack success rates exceed 50% when the attackers have done proper reconnaissance. Some organizations have lost hundreds of thousands or even millions of dollars to a single BEC campaign.
Campaign Scope: Scale and Targeting Patterns
Now let's talk about the actual scope of this phishing campaign. This isn't a boutique attack targeting a few organizations. This is a broad-based, high-volume campaign sending thousands of phishing emails.
Research has identified patterns in the campaign:
Non-Targeted Approach: Unlike many sophisticated phishing campaigns that carefully select targets, this campaign appears to target entire industries at once. Organizations receive thousands of phishing emails with the same template, just adjusted for their specific domain. The attacker isn't doing extensive research on each target before the initial phishing wave. They're using a spray-and-pray approach, accepting that most emails will be caught or ignored.
Why? Because volume compensates for low conversion rates. If you send 5,000 phishing emails to employees of 50 different organizations, and only 0.1% click through to the fake login page, that's still 5 successful credential compromises. Multiply that across dozens of organizations, and you have dozens of valid email accounts to weaponize for BEC attacks.
Timing and Frequency: The campaign shows evidence of being automated. Emails are sent in waves, often during business hours when employees are actively using email. Phishing templates are updated regularly, sometimes daily, to evade email filters. New domains are registered constantly, cycling through them to avoid domain reputation blacklisting.
Geographic Distribution: The phishing emails appear to originate from compromised mail servers, botnets, and bulletproof hosting providers across multiple countries. This makes attribution difficult and allows attackers to rotate through IP addresses that haven't yet been blacklisted.
Success Metrics: While we don't know the exact success rate, the fact that the campaign is continuing at scale suggests it's profitable. Phishing campaigns are resource-intensive: registering domains, maintaining phishing infrastructure, managing stolen credentials. Attackers only continue campaigns that work. The fact that this campaign persists suggests it's successfully stealing credentials from at least a few targets per day.
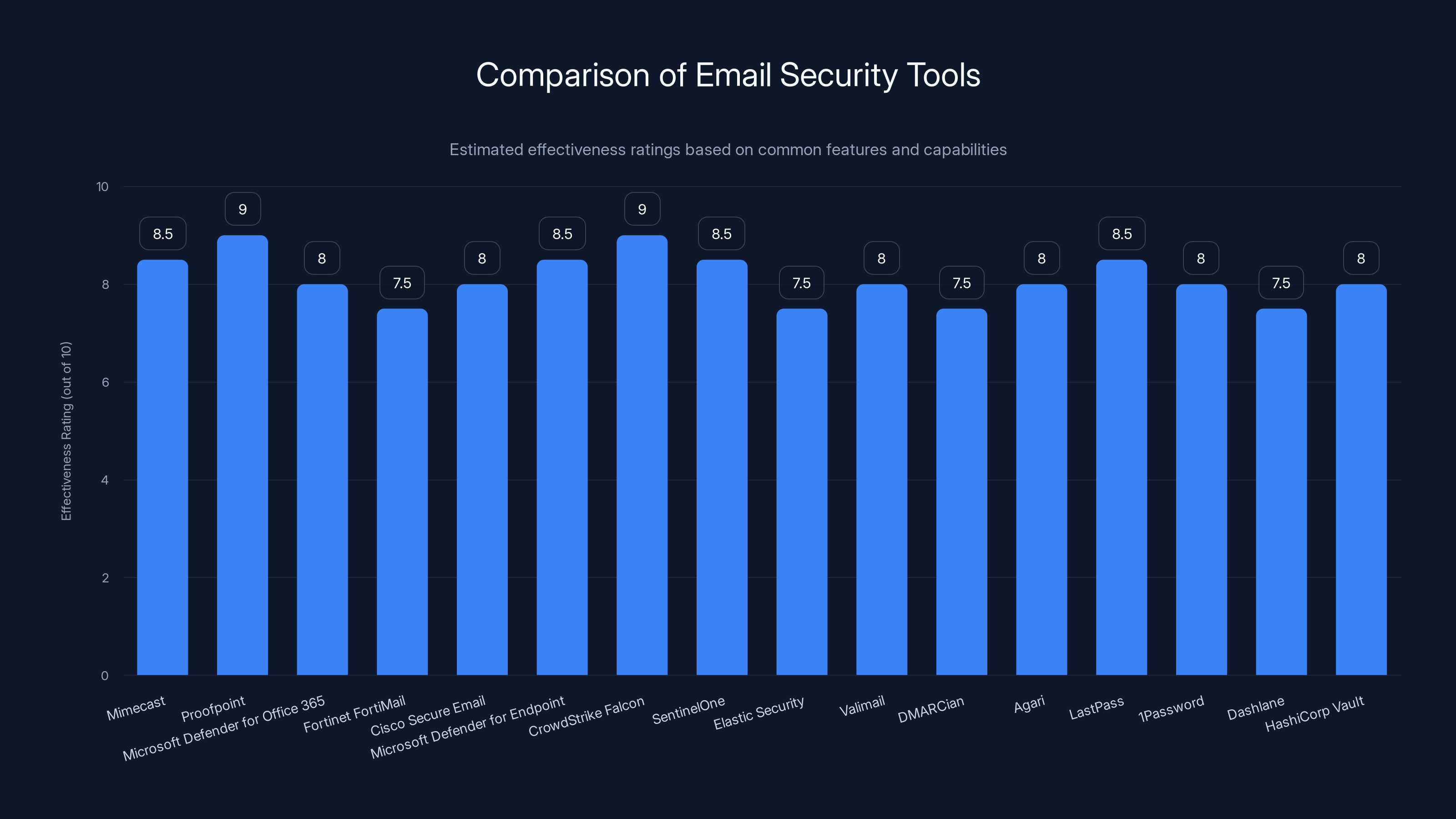
Estimated effectiveness ratings show Proofpoint and CrowdStrike Falcon as leading tools in their categories. Estimated data based on feature capabilities.
Email Gateway Weaknesses: How Phishing Slips Through
If your organization has email security tools like Mimecast, Proofpoint, or similar gateways, you might think you're protected. And you might be. But these tools only work if they're configured correctly, and the current campaign is specifically targeting their weaknesses.
Here's how phishing emails bypass even sophisticated email gateways:
Weak Authentication Verification
Many email gateways don't perform strict DMARC, SPF, or DKIM verification by default. They're configured to filter for malicious content, suspicious links, and known phishing domains. But they're not configured to reject emails that fail domain authentication. So an email from an unauthorized server that claims to be from your domain passes through because it doesn't contain malware or suspicious links.
The gateway sees: an email with your company's domain as the sender, no malicious payload, no known malicious links. It passes through. The fact that SPF verification failed? The gateway isn't configured to care.
Legitimate Service Exceptions
Most organizations add legitimate exceptions to their email filtering rules. Transactional emails from Salesforce, Hub Spot, and other Saa S tools use your domain as the sender. Marketing emails from Mailchimp might use your domain. HR emails from ADP might use your domain. So security teams whitelist these services.
But sometimes the whitelisting is too broad. If a gateway is configured to accept emails from "anyone who claims to be from our domain, as long as it comes through our trusted email security provider," that's an invitation for attackers to send phishing emails through the same provider.
Display Name Spoofing
While domain spoofing (sending from someone@company.com) is the main attack vector, display name spoofing is an additional trick. The actual email address might be "malicious.attacker@compromised-provider.com", but the display name shows "IT Support it-support@company.com". Many email gateways don't flag this because the actual sender domain is allowed.
Victims don't pay attention to the actual email address in the header. They see "IT Support" and assume the email is internal.
Link Reputation and TLS Certificates
Fake login pages are hosted on legitimate-looking domains. Attackers don't use obviously malicious URLs. Instead, they register domains like "microsoft-account-verify.com" or "office 365-security-check.com". They purchase TLS certificates for these domains (they're inexpensive). From a technical perspective, the link is "secure" (HTTPS). Email gateways that check link reputation might flag it, but they're checking against known malicious domain lists, not against the domain's actual purpose.
Bypass technique: if a phishing link is brand new, it hasn't been added to blacklists yet. The gateway sees a new, legitimate-looking domain with a valid certificate. It passes the link through. By the time the domain is blacklisted, thousands of phishing emails have already been sent.

Recognizing Spoofed Internal Messages: What to Look For
Ultimately, your human defense is your strongest layer. Email filters fail. But if your employees can recognize phishing emails, they can report them and avoid clicking. So let's talk about what a spoofed internal message actually looks like, and what red flags employees should watch for.
The Good Spoofing: What Makes It Believable
First, understand what makes a spoofed internal message effective:
- Correct domain name: The email comes from @company.com, not @compan-y.com or @company-inc.com. No typo. No obvious misdirection.
- Authentic branding: The email includes your company's actual logo, color scheme, and formatting. It doesn't look like it was created by amateurs. It looks professional.
- Realistic sender names: The sender is "IT Help Desk" or "HR Benefits" or "IT Security", not "Friendly Hacker" or "Customer Service Admin".
- Familiar templates: The email mimics real templates you've seen before. It has the same structure, tone, and formality as actual internal communications.
- Contextual relevance: The email is timely. It arrives when you might actually expect an IT security notification, or during benefits enrollment season, or after a failed login attempt.
- No obvious grammatical errors: The email is written professionally. No Nigerian prince offering. No obvious ESL mistakes. It reads like a native English speaker wrote it.
The Red Flags: What Doesn't Add Up
But even the best spoofing has tells. Train your employees to look for:
- Urgency without context: "Click here immediately" without explaining why. Real internal communications usually explain what's happening.
- Requests for credentials in unusual ways: Your IT department will never ask you to confirm your password via email. Ever. If an email asks you to re-enter credentials, verify the request through another channel before complying.
- Generic greetings: "Dear User" or "Hello" instead of your name. Many internal systems personalize emails.
- Suspicious link URLs: Hover over links before clicking. Does the link match where the email says it goes? If the email claims to be from Microsoft but the link goes to office 365security.net, that's a red flag.
- Requests for unusual information: Your IT department doesn't need to ask you for your employee ID, your manager's name, or your salary information. BEC attackers sometimes ask questions to verify they have the right person in the right role.
- Unusual sender address in the header: Check the actual "From" email address, not just the display name. If it says "HR Benefits benefits@company.com" that looks legitimate. But if the actual address is "hr.benefits@secure-update-verify.com", that's an attacker.
- Reply-to address mismatch: Sometimes the "From" address and the "Reply-to" address don't match. This is a common phishing tell.
The most important rule: when in doubt, verify through another channel. If you get an email claiming to be from IT asking you to verify your password, call the IT help desk. If you get an email from HR about a benefits update, log into the HR portal directly instead of clicking the email link. Legitimate internal communications will never be compromised by you taking an extra minute to verify.
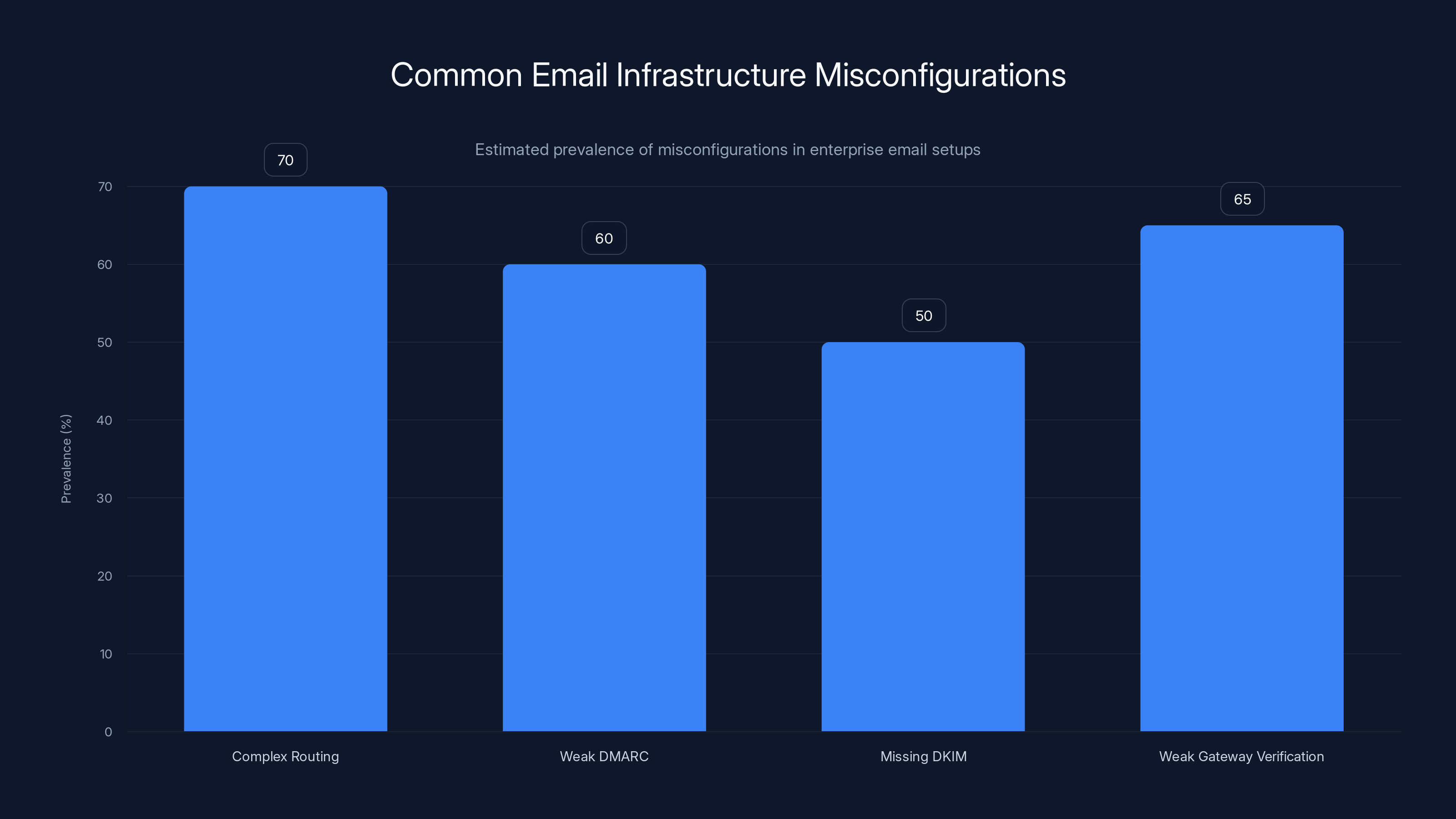
Estimated data shows that complex routing and weak gateway verification are the most common email misconfigurations, affecting over 60% of enterprises.
Organizational Defense: Hardening Your Email Infrastructure
Now let's talk about what your organization needs to do immediately. These aren't theoretical best practices. These are the specific configurations and policies that prevent this attack from working against your organization.
Step 1: Implement Strict DMARC Enforcement
This is the most critical step. Go to your DNS records and change your DMARC policy to "p=reject".
Your DMARC record should look something like this:
v=DMARC1; p=reject; rua=mailto: dmarc-reports@company.com; ruf=mailto: dmarc-forensics@company.com; fo=1
Breakdown of this record:
- v=DMARC1: DMARC version 1
- p=reject: Reject emails that fail authentication (this is the critical part)
- rua=mailto: dmarc-reports@company.com: Send aggregated reports to this address so you can monitor what's happening
- ruf=mailto: dmarc-forensics@company.com: Send forensic reports on failed authentications
- fo=1: Generate reports for both SPF and DKIM failures
Before you make this change, you absolutely must audit your entire email infrastructure. Set DMARC to "p=quarantine" for 2-4 weeks first. Monitor the reports to see what legitimate emails are failing authentication. Work with your IT team to fix any legitimate systems that aren't properly authenticated. Only after you're confident that legitimate emails will pass should you move to "p=reject".
Once you implement strict rejection, any email claiming to be from your domain that doesn't pass SPF or DKIM verification will be rejected outright.
Step 2: Harden Your SPF Record
Your SPF record should be as restrictive as possible. It should specify exactly which systems are allowed to send emails on behalf of your domain, and nothing else.
Example of a hardened SPF record:
v=spf 1 include:_spf.microsoft.com include: sendgrid.net ip 4:203.0.113.50 -all
The critical part is the "-all" at the end. This means "if the sending server isn't in the list above, reject it." Some organizations use "~all" (softfail), which means "maybe reject it," but that's not strict enough. Use "-all" (hardfail).
Audit every system that sends emails using your domain: cloud email providers, Saa S applications, transactional email providers, backup systems, monitoring tools, everything. Add them all to your SPF record. Anything not explicitly allowed should be denied.
Step 3: Implement DKIM Signing on All Outbound Systems
Every system that sends emails on behalf of your organization should have DKIM signing enabled and configured. DKIM adds a cryptographic signature to outbound emails, proving they came from your domain and haven't been altered.
This requires working with your email administrators and every Saa S provider or service that sends emails using your domain. Each needs to be configured with your DKIM keys and signing preferences.
Once DKIM is configured, your receiving email gateway should verify DKIM signatures on inbound emails. Any email claiming to be from your domain without a valid DKIM signature is suspect.
Step 4: Configure Email Gateway to Enforce Authentication Strictly
If you use Mimecast, Proofpoint, Microsoft 365 Email Security, or another gateway, configure it to:
- Enforce strict SPF verification (reject or quarantine emails that fail SPF)
- Enforce strict DKIM verification (reject or quarantine emails without valid signatures)
- Enforce DMARC policies (respect the DMARC policy in DNS records)
- Enable display name spoofing detection (flag emails where the display name claims to be internal but the actual sender is external)
- Require TLS for connections from trusted partners
- Implement external email tagging (add a banner to emails from external senders, so recipients know they're not internal)
Step 5: Implement External Email Tagging
One of the most effective defenses is making external emails visually distinct. Configure your email system to add a banner to every email from outside your organization:
⚠️ CAUTION: This email originated outside your organization. Do not click links or open attachments unless you recognize the sender and expected the email.
This simple visual cue makes users think twice before clicking. It breaks the illusion that the email is internal. When users see this banner on an email claiming to be from IT, they immediately know something is wrong.
User Training: The Human Firewall
Technology alone won't stop this attack. Your employees need to be trained to recognize and report phishing emails.
Security Awareness Training
Your organization should require regular security awareness training that includes:
- How to recognize phishing emails
- How to verify suspicious requests through alternate channels
- What to do if they suspect they've clicked a phishing link
- How to report phishing emails to the security team
- The specific risks of Business Email Compromise attacks
Training should be mandatory, annual at minimum, and should include real examples relevant to your organization. Generic training about Nigerian princes doesn't help. Training about actual attacks your organization has received, actual email templates used, actual social engineering tactics targeting your industry, is much more effective.
Simulated Phishing Campaigns
Regularly send simulated phishing emails to your employees. Not as a gotcha to punish people, but as a learning opportunity. When employees click a simulated phishing link, they should be redirected to training content, not shamed or disciplined.
Track click rates and improve your training based on who's clicking. Offer additional training to employees who are clicking at high rates. Celebrate teams that maintain low click rates.
Simulated phishing campaigns also give your security team real data about which users might be at higher risk of social engineering and which departments might need additional training.
Credential Verification Workflows
Train employees that legitimate IT requests will never ask for credentials via email. If an email asks them to verify their password, reset their credentials, or confirm their identity, they should:
- Do not click the link in the email
- Call the IT help desk directly using a phone number they know
- Go directly to a known login page (by typing the URL in the browser, not clicking an email link)
- Verify the request before proceeding
Many organizations have IT policies that employees should know by heart. "Our IT department will never ask for your password. Ever." Simple, clear, and remembered.
Incident Reporting and Response
Make it easy for employees to report phishing emails. Create a simple report process:
- Forward suspicious emails to a dedicated security mailbox
- Or click a button in the email client that reports the email directly
- Or fill out a simple form in the employee portal
When employees report phishing, the security team should:
- Confirm it's phishing
- Block the sender or domain
- If the email was sent to many employees, send a company-wide alert
- Update any automated filters based on the new threats
Most importantly, thank the employee for reporting. Make it clear that reporting phishing helps protect the entire organization. Employees who report threats are helping, not causing trouble.
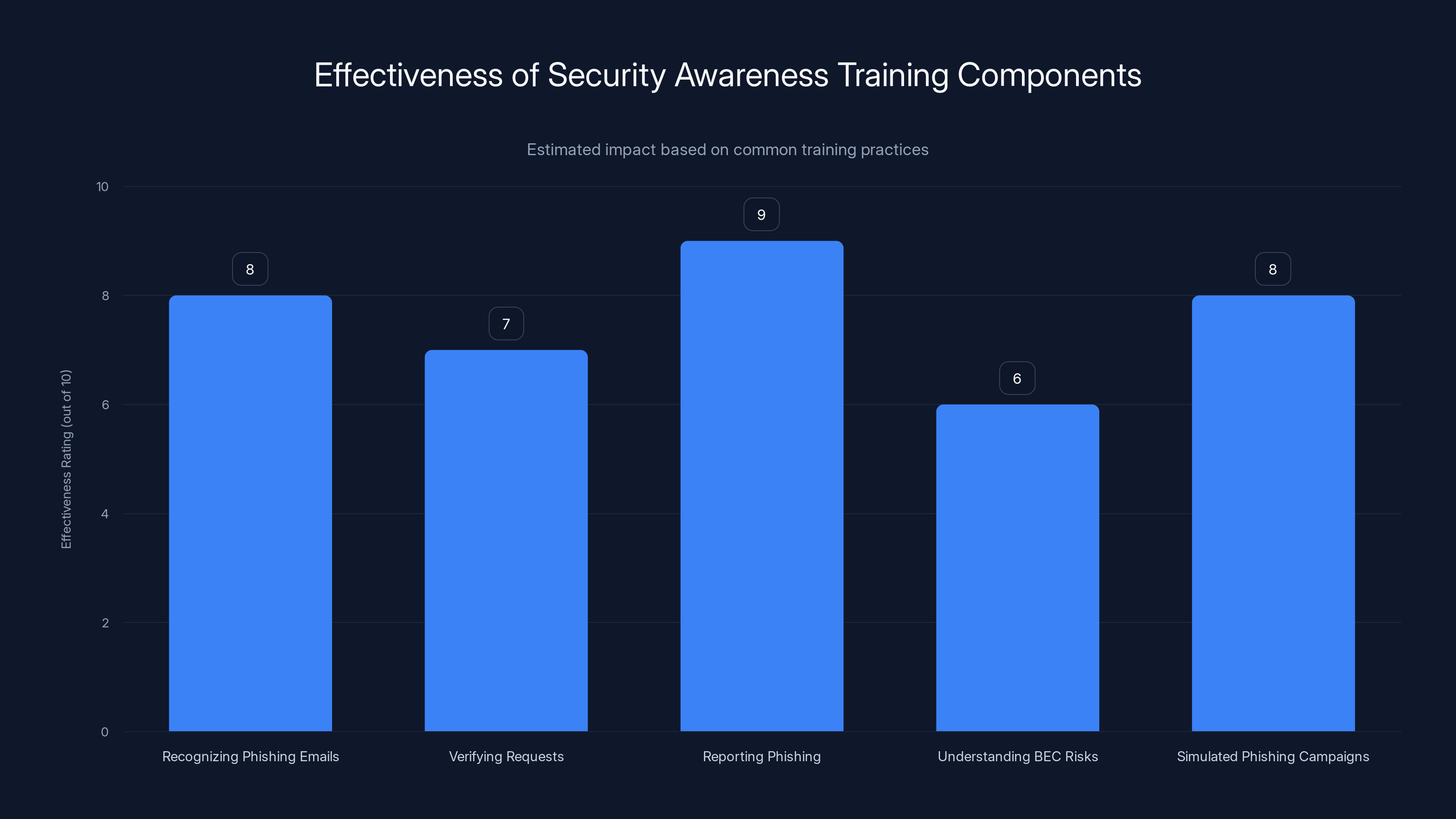
Training on recognizing phishing emails and reporting them are highly effective components, with ratings of 8 and 9 out of 10 respectively. Simulated phishing campaigns also score well, highlighting their importance in training. (Estimated data)
Detection and Monitoring: Catching Attacks in Progress
Even with great defenses, some attacks will get through. Your security team needs to detect them quickly and respond before significant damage occurs.
Email Log Analysis and Anomaly Detection
Monitor your email logs for patterns that indicate attacks:
- Emails claiming to be from your domain coming from external IP addresses
- Emails with spoofed display names but unusual sender addresses
- Bulk emails from new addresses claiming to be internal
- Emails requesting credential verification
- Emails requesting unusual wire transfers or banking information
- Emails using your company's domain but arriving from unusual geographic locations
Modern email security platforms can detect these patterns automatically. If you're not already using anomaly detection in your email security solution, enable it now.
Endpoint Detection and Response (EDR)
If an employee enters their credentials on a fake login page, the attacker can potentially use those credentials to access their email and other systems. EDR (Endpoint Detection and Response) tools running on employee computers can detect:
- Credential harvesting attempts
- Unusual login patterns or geographic anomalies
- Email forwarding rules being created
- Sensitive files being accessed
- Data being exfiltrated
If an EDR tool detects that an employee's credentials have been compromised, your security team can immediately reset the password and investigate what the attacker accessed.
Business Email Compromise Indicators
Watch for specific indicators that BEC attacks are occurring:
- Wire transfer requests from unusual senders
- Requests to update payment information for vendors
- Requests to process urgent payments outside normal procedures
- Emails from executives requesting confidential actions
- Unusual email forwarding or delegation rules being created
- Email activity from compromised accounts at unusual times of day or from unusual locations
Your finance team should have clear procedures for handling wire transfer requests. Ideally, all requests should be verified through multiple channels (not just email) before being processed. Some organizations require that wire transfers be approved in person or through a phone call, not email alone.
Threat Intelligence and OSINT
Your security team should subscribe to threat intelligence feeds that identify phishing domains, malware distribution sites, and other attack infrastructure. When phishing campaigns are detected in the wild, threat intelligence providers identify the domains being used, the infrastructure, and the patterns.
Subscribing to these feeds lets your organization block malicious domains at the gateway level before employees even receive the phishing emails.

Incident Response: What to Do If You've Been Hit
Despite your best efforts, you might get hit with this phishing campaign. If employees have clicked phishing links and entered credentials, here's your response plan:
Immediate Actions (First Hour)
- Identify affected users: Review your email gateway logs to see who received the phishing email. Check which employees opened it. Check your email security platform for click logs.
- Check webserver logs: The phishing email linked to a fake login page. Check your webserver logs and your email gateway logs to see how many times the fake login page was accessed.
- Reset credentials: For every employee who accessed the fake login page (or every employee whose credentials you're not confident about), reset their password immediately.
- Enable MFA: If the affected users don't already have multi-factor authentication enabled, enable it immediately. Even if an attacker has the password, they can't access the account without the second factor.
- Alert affected users: Send a message to affected employees letting them know they should reset their passwords and be alert for unusual account activity.
Longer-Term Actions (First Day)
- Block the malicious domain: Work with your DNS provider and email gateway to block the phishing domain and any related infrastructure.
- Monitor affected accounts: Enable extra logging and monitoring on affected email accounts. Watch for forwarding rules, delegation changes, or unusual access patterns.
- Review email logs: Search the email system for any emails sent from the affected accounts after the phishing attack. These might be BEC emails sent by the attacker using the compromised account.
- Investigate for secondary attacks: Check if the attacker has already launched BEC attacks using the compromised accounts. Look through email and financial records for unusual wire transfers or payment changes.
- Scan endpoints: If employees accessed the fake login page from their computers, scan those computers for malware. The attacker might have done more than just steal credentials.
Post-Incident Actions (First Week)
- Post-mortem analysis: Understand how the phishing email got through your defenses. Did your email gateway fail to detect it? Was there a configuration weakness? Was the DMARC policy not set to reject? Use this to improve your defenses.
- Update security training: Use this attack as a real example in your security awareness training. Show employees what the actual phishing email looked like. Train them on what to look for.
- Review and harden email security: Implement the hardening steps discussed earlier if you haven't already. Update your DMARC policy, harden your SPF record, implement DKIM, configure your gateway to enforce strict authentication.
- Incident report: Document the incident, the response, and what you've learned. Share lessons learned with the broader organization.
Advanced Defensive Strategies: Going Beyond Basics
If your organization wants to go beyond the basics, there are additional strategies that dramatically increase your security posture:
BIMI (Brand Indicators for Message Identification)
BIMI is a newer email authentication standard that displays your company's logo next to your emails in receiving email clients (like Gmail). If an attacker sends an email claiming to be from your domain, they can't include your logo because they haven't authenticated as your domain.
Implementing BIMI requires:
- A strict DMARC policy set to "p=reject"
- Your company's official logo in SVG format
- A BIMI TXT record in your DNS
Once implemented, all emails from your domain that pass DMARC will display your logo. Emails claiming to be from your domain that don't have your logo are instantly suspect.
Conditional Access and Zero Trust
Instead of trusting that an employee is who they claim to be based on a password, implement zero-trust principles:
- Require multi-factor authentication for all email access
- Require known device access (employees can only access email from registered devices)
- Implement location-based access controls (flag or block access from unusual countries)
- Require continuous verification (not just at login, but throughout the session)
Even if an attacker has stolen credentials, they can't access the email account without the second factor. This dramatically reduces the impact of credential compromise.
API-Level Protections
Many email breaches happen at the API level, not just through traditional login. If you use Microsoft Graph API or Gmail API to integrate with email systems:
- Implement strict API authentication and rate limiting
- Monitor for unusual API access patterns
- Restrict API access to only the minimum required permissions
- Regularly rotate API credentials
Email Route Protection
Some organizations implement custom email routing rules that add additional verification steps. For example:
- Emails requesting wire transfers are sent to a separate mailbox where they're verified by the finance team
- Emails claiming to be from executives requesting unusual actions are quarantined for manual review
- Any email from a new external sender to a group like "finance@company.com" is held for approval before delivery
These rules increase friction for legitimate emails but significantly reduce the risk of BEC attacks succeeding.

Tools and Technologies for Email Security
While no single tool eliminates this risk, certain tools significantly improve your defense:
Email Security Gateways
These are critical. They sit between your organization and the internet, filtering emails before they reach employee inboxes:
- Mimecast
- Proofpoint
- Microsoft Defender for Office 365
- Fortinet Forti Mail
- Cisco Secure Email
Each has different strengths, but the key is that they enforce authentication, scan for malware and phishing, and integrate with your DMARC/SPF/DKIM policies.
Endpoint Detection and Response (EDR)
These tools run on employee computers and detect when compromised credentials are being used:
- Microsoft Defender for Endpoint
- Crowd Strike Falcon
- Sentinel One
- Elastic Security
Email Authentication Monitoring
These tools specifically monitor and report on email authentication:
- Valimail (now part of Proofpoint)
- DMARCian
- Agari
They provide detailed insights into what's happening with your email authentication and where vulnerabilities exist.
Credential Access Management
Password managers and privileged access management (PAM) tools reduce credential exposure:
- Last Pass
- 1 Password
- Dashlane
- Hashi Corp Vault
When credentials are stored securely and never typed or copied manually, they're much harder for attackers to steal.
Workflow Automation Tools for Verification
If your organization uses workflow automation platforms, you can automate credential verification for sensitive requests:
- Runable and similar platforms can automate the process of verifying high-risk requests
- Create automated workflows that flag wire transfer requests for manual verification
- Implement approval workflows that require multiple confirmations for sensitive actions
- Use AI-powered tools to detect unusual patterns in business communications
Use Case: Automate verification workflows for wire transfers and sensitive business requests to prevent BEC attacks from succeeding, even if credentials are compromised.
Try Runable For Free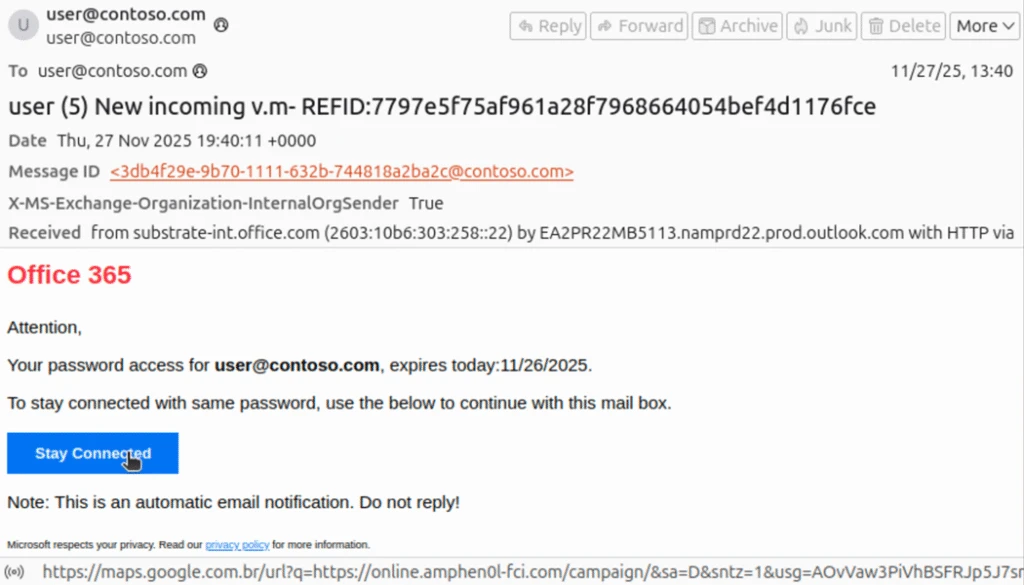
Building a Security Culture Around Email
Ultimately, the strongest defense is an organization where security is everyone's job, not just the security team's job.
Executive Buy-In
Executives need to understand that phishing and BEC attacks can cost the organization millions. They need to allocate budget for email security tools, training, and incident response. And they need to model good security behavior themselves: using strong passwords, enabling MFA, reporting phishing emails, and not bypassing security controls.
Cross-Department Coordination
Security isn't just IT's responsibility. Finance needs to understand BEC attack risks and implement verification procedures. HR needs to understand how phishing targets employees. Management needs to understand why not clicking suspicious links is more important than responding to emails instantly.
When a phishing email arrives, the entire organization needs to be aligned in treating it as a threat, not a nuisance.
Continuous Improvement
Email threats evolve constantly. This specific phishing campaign using spoofed internal messages will eventually be replaced by other attacks. Your email security posture needs to evolve with the threat landscape.
Regularly review your DMARC, SPF, and DKIM configuration. Test your defenses with simulated phishing. Update your security training based on new threat intelligence. Invest in new security tools and capabilities as they become available.
The organizations that avoid being hit by these attacks aren't the ones with the newest tools. They're the ones with strong fundamentals: strict email authentication, user training, detection and monitoring, and a culture where security is taken seriously.

FAQ
What exactly is email spoofing and how does it differ from phishing?
Email spoofing is the technical ability to make an email appear to come from a different sender than it actually does. Phishing is a social engineering attack that uses email spoofing (or other deception tactics) to trick users into revealing sensitive information. In this phishing campaign, attackers are using spoofing to make phishing emails appear to come from inside your organization, making victims more likely to trust and engage with the message.
How can an attacker spoof an email from my company's domain if I have SPF records?
Attackers exploit misconfigured SPF, DKIM, and DMARC policies. If your DMARC policy is set to "none" or "quarantine" instead of "reject", receiving email servers will still accept emails that fail authentication and deliver them to inboxes instead of blocking them. Additionally, if your SPF record is incomplete or includes too many third-party services, attackers can exploit gaps in your authentication chain to send emails that appear to pass verification.
What should I do if I clicked a phishing link and entered my credentials?
Immediately change your password to something completely new and different from any previous password. Enable multi-factor authentication on your email account if it's not already enabled. Monitor your email account for unusual forwarding rules, delegation permissions, or login activity from unusual locations. Notify your IT security team so they can monitor your account and investigate whether your credentials were used to access sensitive systems. Check your financial accounts and any other accounts that use the same password.
How does Business Email Compromise (BEC) differ from the initial phishing attack?
The initial phishing campaign is broad and non-targeted, sending thousands of emails to harvest credentials. BEC is highly targeted and research-intensive, using stolen credentials to send convincing emails to specific people asking for wire transfers, payment changes, or other valuable actions. Once attackers have stolen credentials through phishing, they have the foothold they need to launch BEC attacks against your entire organization.
What's the difference between setting DMARC to "reject", "quarantine", and "none"?
When DMARC is set to "p=reject", emails that fail authentication are completely rejected and never reach the victim's inbox. When set to "p=quarantine", emails that fail authentication are accepted but sent to spam or a quarantine folder. When set to "p=none", emails that fail authentication are still delivered to the inbox as normal, and the organization only receives reports about failures. For maximum security against spoofing, you need "p=reject". However, you should test with "p=quarantine" first to ensure legitimate emails won't be blocked.
Can I implement strict DMARC enforcement (p=reject) immediately, or do I need to prepare first?
You should definitely prepare before implementing "p=reject". Start by setting DMARC to "p=quarantine" for 2-4 weeks and carefully monitor the reports to see what legitimate emails are failing authentication. Work with your IT team to fix any systems that aren't properly authenticated. Test with your email security gateway to ensure it's configured to enforce DMARC properly. Only after you've addressed legitimate authentication issues should you move to "p=reject". Implementing "p=reject" too quickly without proper preparation could accidentally block legitimate business emails.
How can I tell if an email claiming to be internal is actually spoofed?
Check the actual sender email address, not just the display name. If the display name says "IT Support" but the actual address is from an external domain, it's spoofed. Hover over links to see the actual URL they point to, not where the email claims they go. Look for the external email banner that your organization should have implemented. Verify urgent requests through another channel before responding. Be suspicious of requests asking you to confirm your password or verify your identity, as legitimate IT teams won't ask this via email.
What are the most important email security configurations I should implement first?
In priority order: (1) Implement strict DMARC enforcement set to "p=reject" after testing, (2) Harden your SPF record to only include authorized senders and use "-all" instead of "~all", (3) Implement DKIM signing on all systems sending email from your domain, (4) Configure your email gateway to enforce strict authentication verification, (5) Implement external email tagging so users can distinguish internal from external emails, (6) Require multi-factor authentication for all email access, and (7) Deploy endpoint detection and response (EDR) tools to detect compromised credentials being used.
How often should I update my SPF, DKIM, and DMARC configuration?
You should review your email authentication configuration at least quarterly, or whenever you add new services that send emails on your behalf. Every time you implement a new Saa S application, onboard a new vendor, or change email infrastructure, you need to update your SPF record. Additionally, review your DMARC reports monthly to see if there are authentication failures you need to address. Make updates to your SPF record immediately when new senders are added, not months later.
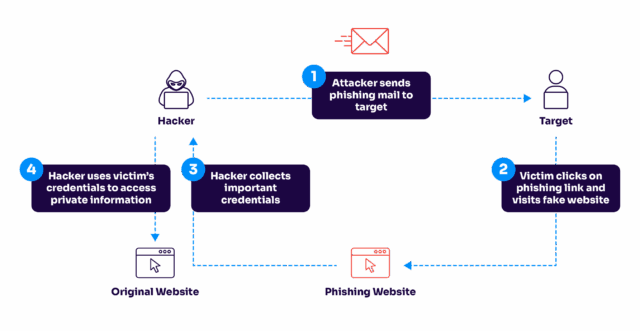
Conclusion: Taking Action Today
This phishing campaign exploiting internal message spoofing represents a real and immediate threat to organizations of all sizes. The attackers aren't using groundbreaking new techniques. They're exploiting fundamental weaknesses in email authentication that exist because many organizations haven't properly configured their email infrastructure.
The good news? These weaknesses are entirely fixable. You don't need to deploy expensive new tools or restructure your entire IT organization. You need to implement the foundational email security practices that should have been in place all along.
Start with your DMARC policy. Check it today. If it's set to "none" or "quarantine", make a plan to change it to "reject". If you're not currently using SPF, DKIM, and DMARC, implement all three. These three protocols, properly configured and strictly enforced, eliminate the primary attack vector for this phishing campaign.
Next, configure your email gateway to enforce these authentication standards. Make sure it's not making exceptions for legitimate services that haven't been properly authenticated. If you're not sure your gateway is configured correctly, have your vendor review it.
Train your employees to recognize spoofed emails and to verify unusual requests through alternate channels. A single employee who understands that their IT department will never ask for a password can prevent an entire breach.
Monitor for attacks. Watch your email logs for patterns that indicate spoofing. Check your financial systems for unusual wire transfer requests. If an attack gets through, detect it quickly and respond before real damage occurs.
Build a security culture in your organization where email security is everyone's responsibility. Make it easy for employees to report phishing. Celebrate teams that maintain low click rates on simulated phishing. Show that security isn't a burden but a priority.
This phishing campaign is real, it's active right now, and it's targeting organizations across industries. But it's not sophisticated. It's not using zero-day vulnerabilities or attacking through mysterious attack vectors. It's exploiting basic configuration mistakes that should have been corrected years ago.
The organizations that won't be hit are the ones that have already fixed these mistakes. The ones that have strict DMARC enforcement, hardened SPF records, DKIM signing, and security-conscious employees.
Your organization can be one of them. Start today. Review your email authentication configuration. Make a list of what needs to be fixed. Create a timeline for implementation. Allocate resources. And execute.
Your future security depends on it.
Key Takeaways
- Email spoofing exploits misconfigured DMARC, SPF, and DKIM policies that aren't set to strict enforcement, allowing attackers to send emails claiming to be from your organization
- The Tycoon2FA phishing kit and similar tools create authentic-looking internal emails with spoofed domains, fake login pages, and credential harvesting infrastructure
- Stolen credentials from initial phishing attacks are weaponized in secondary Business Email Compromise campaigns targeting executives and finance teams with high-value requests
- Implementing strict DMARC enforcement (p=reject), hardening SPF records, implementing DKIM signing, and configuring email gateways properly eliminates the primary attack vector
- Employee training, external email tagging, credential verification workflows, and detection monitoring create layered defenses that catch attacks in progress before major damage occurs
Related Articles
- Blue Screen of Death Malware: How ClickFix Attacks Work [2025]
- Scattered Lapsus$ Hunters Caught in Honeypot: Inside the Bust [2025]
- NordVPN Salesforce Breach Claim: What Really Happened [2025]
- ESA Cyberattack: What You Need to Know About the 200GB Breach [2025]
- Supply Chain, AI & Cloud Failures in 2025: Critical Lessons
- Cybersecurity Insiders Plead Guilty to ALPHV Ransomware Attacks [2025]
![Internal Message Spoofing Phishing Campaign: How to Stop It [2025]](https://tryrunable.com/blog/internal-message-spoofing-phishing-campaign-how-to-stop-it-2/image-1-1767821960672.jpg)



