Introduction: When a Phone Becomes Impenetrable
A federal raid on a journalist's home in October 2024 revealed something remarkable. The FBI agents arrived with forensic tools, legal authority, and standard operating procedures. But they walked away empty-handed. Why? The reporter's iPhone was running Lockdown Mode, Apple's most aggressive security setting, and nothing the bureau's equipment could do made a dent.
This wasn't a glitch or an oversight. Lockdown Mode exists specifically for this scenario. It's Apple's answer to a fundamental question: what happens when your device becomes a target? Not because you've done something wrong, but because you're someone whose information matters—to governments, to threats, to powerful people.
The story sparked legitimate conversation about device security, government access, and the limits of law enforcement in a digital age. But behind the headlines is something more nuanced. Lockdown Mode isn't a magic shield that makes phones invulnerable. It's a carefully designed set of restrictions that trades convenience for security, and it only works for people who need it most.
This article breaks down exactly how Lockdown Mode works, why the FBI couldn't access that journalist's phone, what gets disabled when you activate it, and whether you actually need it. We'll walk through the technical architecture, examine real-world implications, and separate hype from reality. By the end, you'll understand one of the most sophisticated security features ever shipped in a consumer device.
TL; DR
- Lockdown Mode blocks remote exploits: It disables features that hackers and state-sponsored actors use to gain access without your knowledge
- The FBI raid proves it works: Even with legal authority and specialized tools, law enforcement couldn't bypass the protection in October 2024
- It's designed for high-risk targets: Journalists, activists, dissidents, and others facing sophisticated threats gain maximum protection
- Real security comes with real costs: Lockdown Mode disables FaceTime, limits attachments, blocks USB accessories, and prevents some cloud features
- Not everyone needs it: Most people are safer with standard iOS security, which is already far stronger than Android alternatives
- Bottom line: Lockdown Mode is the most secure consumer device setting ever released, but it's a tool for specific threats, not everyday users
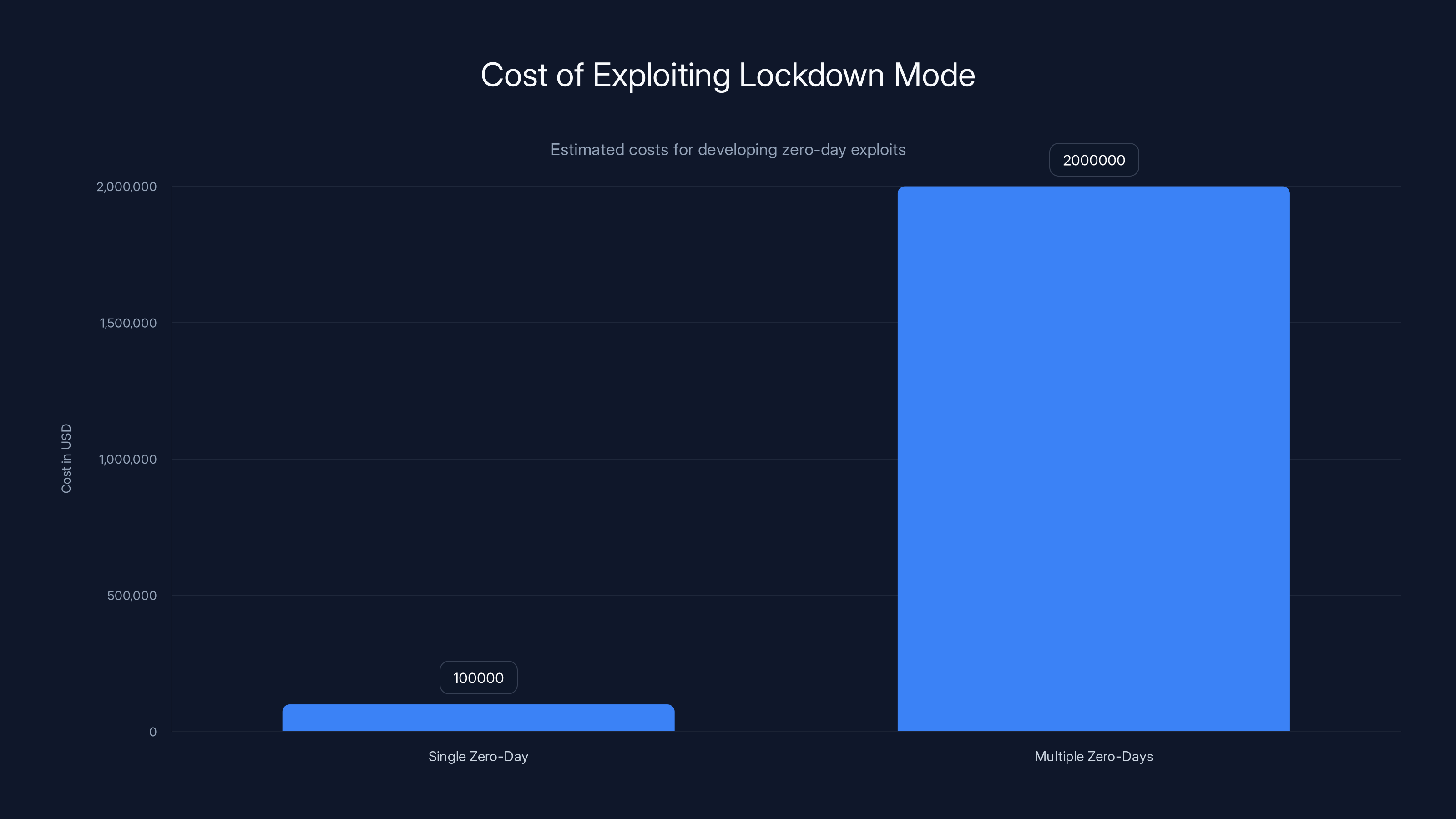
Lockdown Mode increases the cost of exploitation by requiring multiple zero-day exploits, making attacks impractical for most adversaries. Estimated data.
What Exactly Is Lockdown Mode?
Lockdown Mode is Apple's most extreme security setting, introduced in 2022 with iOS 16. Think of it as putting your iPhone in a bunker. The moment you enable it, the device fundamentally changes how it operates. Features get disabled. Connections get restricted. Third-party integrations get severed. Everything is calculated to eliminate attack vectors that hackers, criminals, and nation-states use to break into phones.
Apple didn't build Lockdown Mode because they suddenly realized iPhones were insecure. iOS has always been bulletproof compared to alternatives. What changed was the threat landscape. Security researchers began documenting zero-day exploits—vulnerabilities that even Apple didn't know about—being weaponized against journalists, activists, and dissidents. Companies like NSO Group were selling tools to governments that could turn an iPhone into a surveillance device without the owner knowing.
Lockdown Mode is Apple's response. It's not a feature for everyone. It's not a setting you enable to feel safer while scrolling Twitter. It's a tool for people facing targeted threats. People whose devices could be compromised not by a phishing email or a weak password, but by a sophisticated, nation-state-level attack.
The 2024 FBI raid perfectly illustrated this distinction. The reporter wasn't hiding illegal activity. The device contained source material, notes, and communications crucial to journalism. With standard iOS security, the FBI could theoretically attempt certain forensic techniques. With Lockdown Mode active, those techniques don't exist.
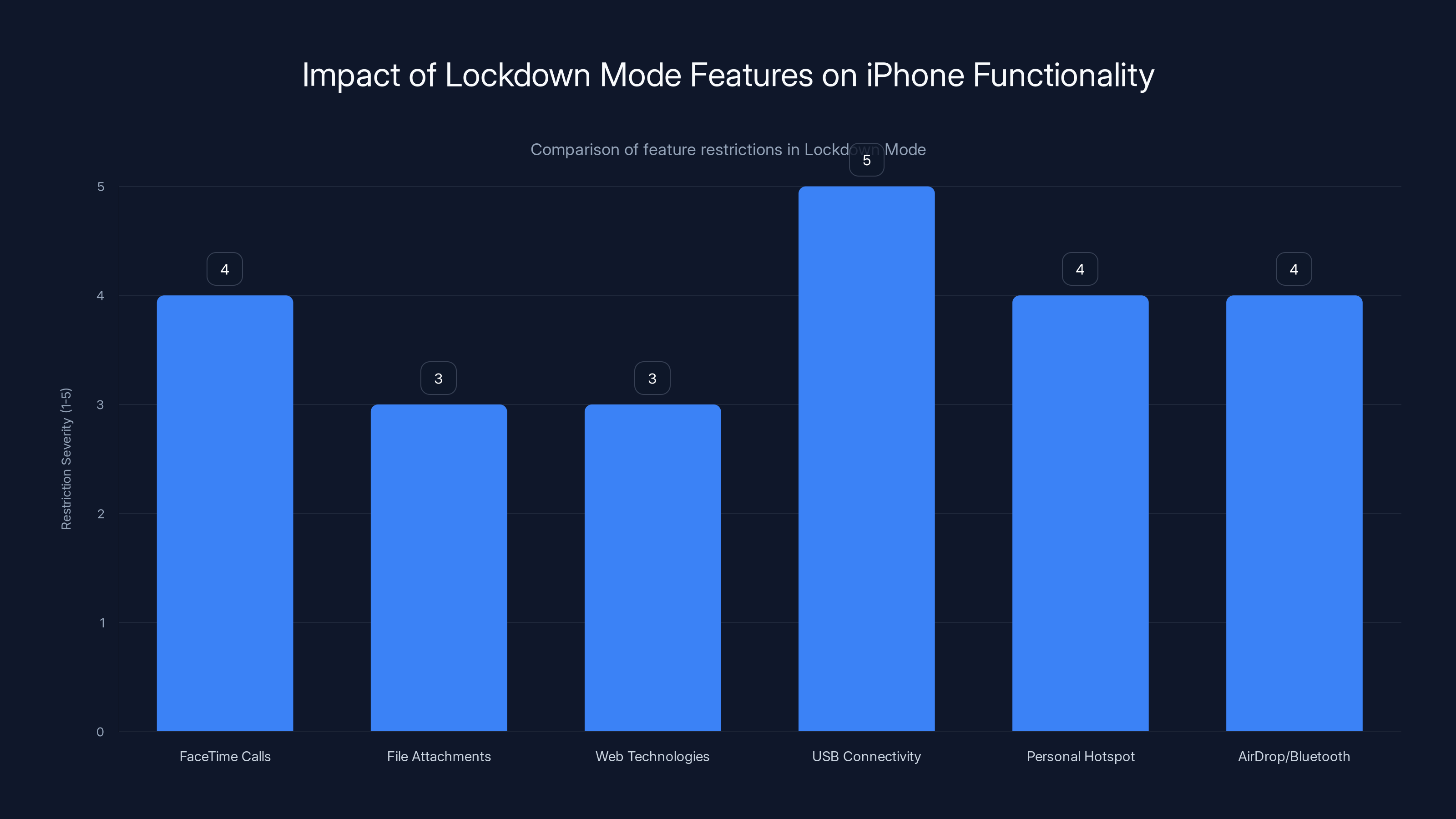
Lockdown Mode significantly restricts various iPhone features, with USB connectivity and communication tools like FaceTime and AirDrop being most affected. Estimated data based on feature descriptions.
How Apple Designs Lockdown Mode: The Threat Model
Understanding Lockdown Mode requires understanding the threats it's designed to stop. Apple's security team works from a specific threat model: sophisticated attackers with unlimited resources who are specifically targeting you.
These aren't script kiddies trying to guess your password. They're threat actors with access to zero-day exploits, which are vulnerabilities Apple doesn't know about yet. They might work for a government, an authoritarian regime, a criminal syndicate, or a wealthy individual willing to spend hundreds of thousands of dollars to compromise your device.
Zero-day exploits are the nuclear weapons of the cyber world. They work because no patch exists. Apple can't have fixed something they don't know is broken. A sophisticated attacker might chain multiple zero-days together, creating an attack pathway that looks inevitable to traditional security measures.
Lockdown Mode works by eliminating the attack surface. It doesn't make iPhones unbreakable—nothing is unbreakable with unlimited resources—but it makes attacks so difficult and expensive that they're not worth the effort for most targets.
The design philosophy is ruthless: if a feature could possibly be exploited, disable it. If a connection could be manipulated, block it. If a third-party app could create a vulnerability, restrict it. Accept massive inconvenience in exchange for near-total security.
The FBI Raid: What Actually Happened
In October 2024, federal agents executed a search warrant on the home of a journalist investigating government activities. They had legal authority. They had the device in their possession. They had forensic tools specifically designed to extract data from iPhones. And they couldn't access anything.
This wasn't because they didn't try hard enough or lack technical skill. The FBI has some of the most sophisticated forensic equipment on the planet. They've broken into iPhones before. They have relationships with security researchers who've been compensated for finding exploits. But none of that mattered because Lockdown Mode had already closed every door they might walk through.
Here's what likely happened: the agent connected the iPhone to a forensic device. The standard attack vectors—the exploits and techniques that work on most iPhones—failed immediately because Lockdown Mode had disabled them. They tried methods that rely on USB connectivity. Those don't work when Lockdown Mode restricts what can happen over USB. They attempted to use cloud backups as an entry point. Lockdown Mode had prevented cloud backups from completing in certain ways.
With each attempt, they hit the same wall. The device was encrypted. The passcode couldn't be bypassed. The attack vectors were gone. This isn't a dramatic story of good versus evil. It's a technical reality: Lockdown Mode makes forensic access impossible without the passcode.
The FBI could theoretically still access the device if they cracked the passcode, but that's a different problem. That requires guessing or brute-forcing security, not exploiting hidden vulnerabilities. It's the difference between finding a secret passage into a fortress and trying to knock down the front gate.

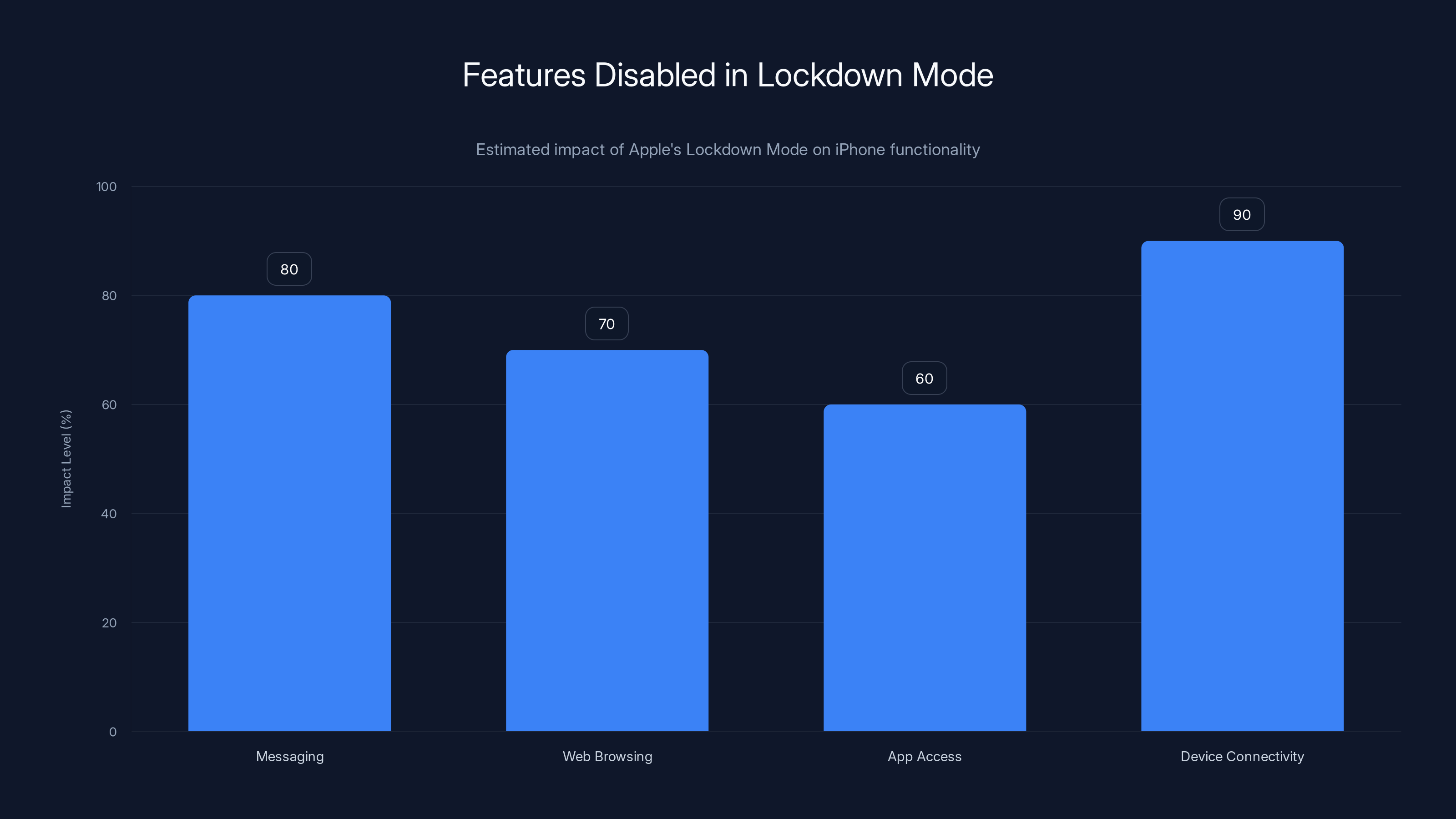
Lockdown Mode significantly restricts various functionalities to enhance security, with connectivity being most affected. (Estimated data)
What Lockdown Mode Actually Disables: The Feature List
When you enable Lockdown Mode, here's what stops working:
Attachments and Messaging: FaceTime stops accepting incoming calls from unknown numbers. Messages can't load certain attachment types. This blocks attacks that use multimedia files to trigger vulnerabilities. A sophisticated attacker might craft a specially designed image or video file that exploits a parsing vulnerability when the device tries to display it. Lockdown Mode prevents this by restricting what attachments the system will process.
USB Connectivity: When your phone is locked, USB connections are basically shut down. You can't plug into a computer and have it recognized normally. This eliminates an entire attack surface. Researchers have long used USB connections to access device internals. Lockdown Mode forces USB to operate only when the device is unlocked.
Web Technologies: Lockdown Mode restricts advanced web technologies that attackers use for exploitation. JavaScript, web plugins, and certain web standards get disabled or restricted. These technologies, while normally safe, can be weaponized through zero-day exploits in browsers or Safari.
Sideloading Restrictions: Apple already prevents sideloading on iOS, but Lockdown Mode ensures that if someone physically controls your device, they can't force-install an app through any method. It closes every possible avenue for installing malicious software.
iCloud Restrictions: Lockdown Mode limits what iCloud can do, preventing cloud-based attacks. Sophisticated attackers might compromise cloud backups to insert malicious data that gets synchronized back to the device. Lockdown Mode prevents this.
Tethering Restrictions: Personal Hotspot is disabled, preventing attackers from using network-level attacks through the wireless connection. This sounds minor but eliminates a sophisticated attack vector.
Device Connectivity: AirDrop, Bluetooth, and certain wireless connections face restrictions. These connection points could theoretically be used for attacks. Lockdown Mode makes them much harder to exploit.
The Technical Architecture: How It Actually Works Under the Hood
Lockdown Mode isn't one feature. It's a coordinated set of changes across iOS's kernel, security framework, and app sandbox that work together to eliminate attack vectors.
Sandbox Hardening: Every app on iOS runs in a sandbox, meaning it can only access resources Apple explicitly permits. Lockdown Mode tightens the sandbox even more, preventing apps from accessing certain system features that could be exploited. This makes it impossible for a compromised app to leverage system vulnerabilities.
Code Execution Prevention: Modern iPhones have specialized hardware called the Secure Enclave that protects the most sensitive operations. Lockdown Mode ensures that even if an attacker manages to execute code on the main CPU, that code can't reach the Secure Enclave. It's like a fort within a fort.
Memory Protection: Advanced memory protection features work overtime in Lockdown Mode. If an attacker tries to write to certain areas of memory, the protection mechanism stops them. This prevents return-oriented programming attacks and other techniques that manipulate memory to achieve code execution.
Cryptographic Isolation: Lockdown Mode ensures that even if someone breaks into one part of the system, they can't use that foothold to compromise other parts. Each component is cryptographically isolated, preventing lateral movement.
Process Isolation: Unlike traditional computers where one compromised process might lead to system compromise, iOS processes run isolated from each other. Lockdown Mode ensures that even a completely broken process can't interact with other processes in ways that could lead to privilege escalation.
The genius of this architecture is that it doesn't require new hardware or entirely new software. It's a careful reconfiguration of existing security mechanisms, turning up the dial everywhere simultaneously.
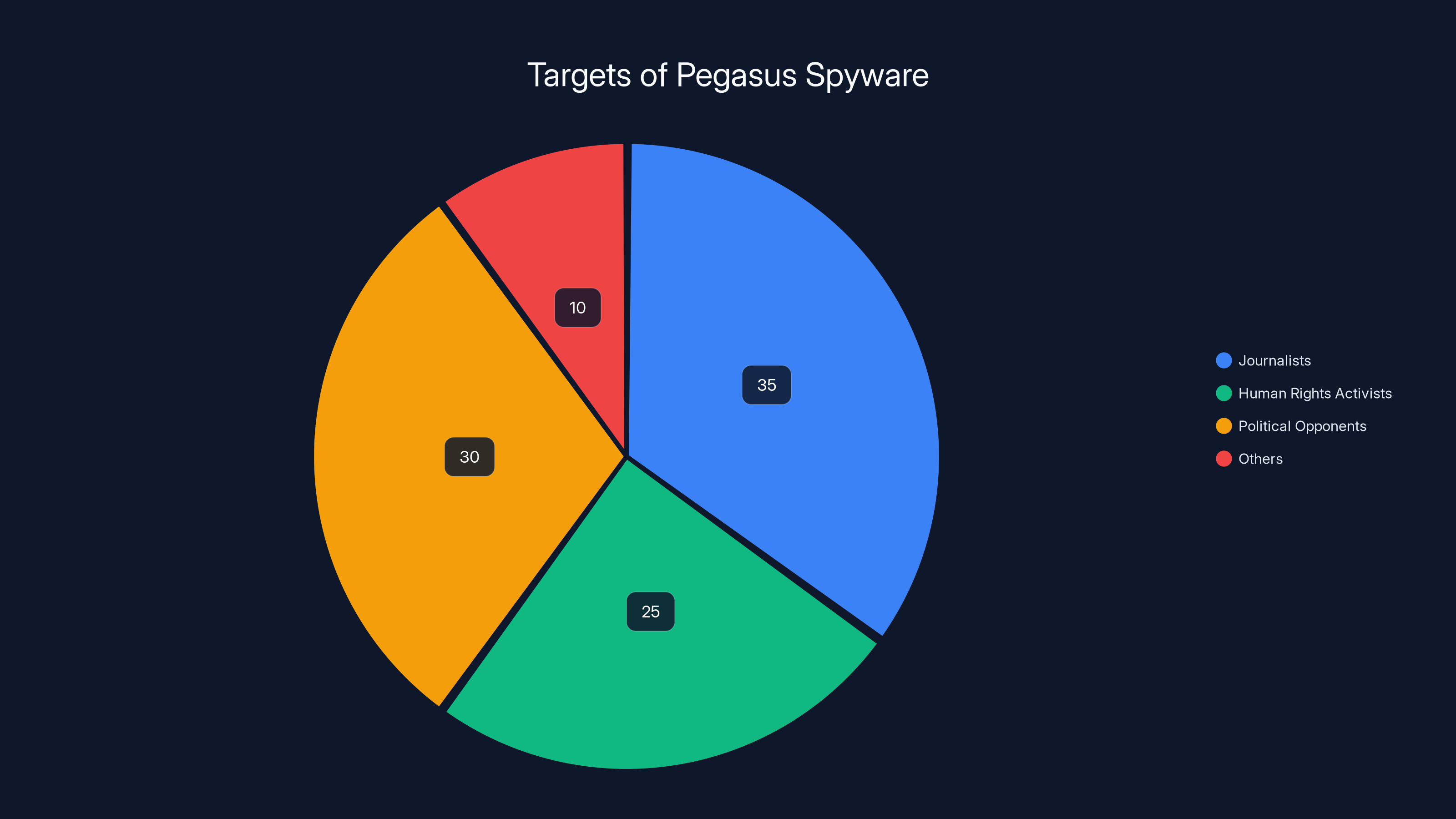
Estimated data suggests that journalists and political opponents were the primary targets of Pegasus spyware, highlighting the need for enhanced security measures like Lockdown Mode.
Why Journalists and Activists Need Lockdown Mode
Not everyone needs Lockdown Mode, but some people genuinely can't live without it. Journalists, especially those covering government corruption or national security issues, face systematic targeting. Activists challenging authoritarian regimes risk having their devices compromised by the very governments they're challenging.
The threat isn't theoretical. Security researchers have documented sophisticated malware specifically designed to target human rights defenders, journalists, and political opponents. Tools like Pegasus spyware can turn a phone into a remote surveillance device, recording conversations, accessing messages, and exfiltrating files without the owner knowing anything happened.
For these targets, Lockdown Mode is the difference between safety and exposure. It's not paranoia. It's protection against documented threats.
In the 2024 FBI raid situation, the journalist wasn't doing anything illegal. But they were investigating government activities and protecting sources. Without Lockdown Mode, an aggressive forensic attack might have compromised those sources, put people at risk, and violated journalistic ethics about protecting sources. Lockdown Mode prevented that.
This is why the implications matter beyond the specific case. When governments can't access phones even with legal authority and physical possession of the device, it changes the dynamics of power. It means you can't be forced to reveal information through a device seizure.
The Privacy vs. Law Enforcement Debate: Complex and Legitimate
The FBI's inability to access that journalist's iPhone sparked a fascinating policy debate. And it's not as simple as "privacy good, law enforcement bad" or vice versa.
Law enforcement has legitimate needs. Criminal investigations sometimes require accessing devices. Serious crimes—human trafficking, terrorism, child exploitation—often leave digital evidence. Without the ability to access phones, some investigations become impossible.
But there's also a legitimate concern about overreach. History shows that surveillance powers, once granted, expand beyond their original intent. What's justified for terrorism investigations becomes ordinary tools for investigating ordinary crimes, then for investigating people the government simply wants to monitor.
Lockdown Mode doesn't solve this debate. It makes it sharper. The technology now exists to make devices unbreakable even with legal authority and physical possession. This has real consequences for law enforcement, national security, and criminal investigation.
The journalist's case exemplifies the tension. The FBI had legal authority to search for evidence of crime. But the device was designed to resist that search. Both positions are defensible. The journalist's right to protect sources against government overreach is legitimate. The FBI's need to investigate actual crimes is also legitimate. Technology has created a scenario where only one can win.
This isn't a technology problem with a technology solution. It's a policy problem that societies need to address collectively. Some countries have decided that encryption is a public safety threat and tried to ban it. Others have decided that privacy is fundamental and protected encrypted communications. The United States hasn't fully decided, which creates tension.
Lockdown Mode forces that decision. You can't unsee technology once it exists. You can't pretend inaccessible devices aren't possible. The question is whether you want them to exist.

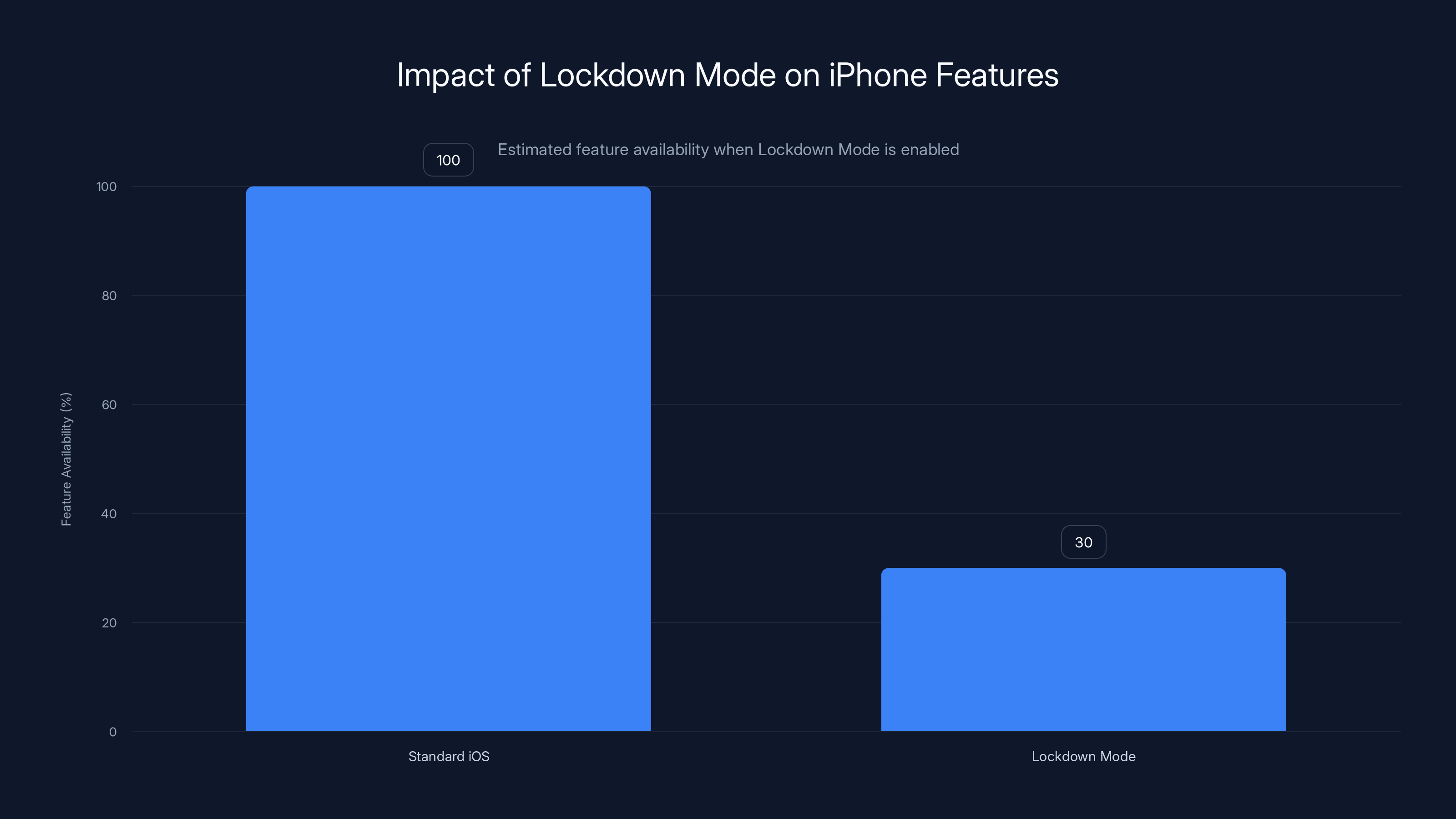
Lockdown Mode significantly reduces feature availability to enhance security, limiting potential attack vectors. Estimated data.
Real-World Usability: What Changes When You Enable It
Lockdown Mode provides exceptional security, but the cost is genuine inconvenience. This isn't theoretical—here's what actually happens when you enable it:
FaceTime Gets Weird: Incoming FaceTime calls from unknown numbers don't ring through. You won't know someone's trying to call until much later, if you check the Recents list. This alone makes Lockdown Mode impractical for most people. But for targets of sophisticated attackers, this tiny inconvenience is a worthwhile trade for blocking attacks that use video calls as exploit vectors.
Attachments Become Restricted: Certain file types won't load in Messages. Some emails won't display properly if they contain embedded media. Forget about complex PDF attachments or rich document formats. This prevents zero-day exploits in document parsers, but it means collaborative work becomes harder.
Web Browsing Gets Limited: Websites that rely on advanced JavaScript functionality might not work properly. Complex web applications could behave unpredictably. This blocks browser-based exploits but sacrifices modern web functionality.
Third-Party Accessories Don't Work: USB-connected devices, external storage, and accessory hardware don't function when the device is locked. Need to use a scanner or card reader? Lockdown Mode prevents that. This is intentional—the more hardware you can plug into your phone, the more attack vectors exist.
Cloud Features Get Restricted: iCloud features work differently. Certain backup options aren't available. This prevents cloud-based attacks but makes data recovery more complicated.
Hotspot Is Disabled: You can't share your mobile connection with other devices. For business travelers and people who rely on tethering, this is genuinely limiting.
These aren't bugs or oversights. They're deliberate security choices. Every disabled feature represents an attack vector that's been eliminated. The trade-off is straightforward: maximum security for severe inconvenience.
For someone facing the level of threats Lockdown Mode is designed to address, that trade makes sense. For most people, it doesn't. A journalist investigating government corruption might accept that their phone is less convenient in exchange for being virtually uncompromisable. A business executive might not make that same choice. A teenager definitely shouldn't.
Comparing Lockdown Mode to Standard iOS Security: Threat Model Matters
Standard iOS security is already exceptional compared to Android and other platforms. iPhones are encrypted by default. The operating system is locked down. Apps run in sandboxes. Updates roll out frequently. Hardware-level protections like the Secure Enclave provide additional safety.
For most people, this is sufficient. The probability of being targeted by sophisticated zero-day exploits is essentially zero if you're not someone important or interesting to threat actors.
But for high-value targets, standard iOS security has limitations. A sophisticated attacker with enough resources might find zero-day exploits that iOS's standard protections don't address. They might discover new attack vectors by chaining together multiple vulnerabilities. They might find weaknesses in peripheral features that aren't hardened because most users don't need them hardened.
Lockdown Mode eliminates these possibilities by making the attack surface microscopic. It's not just more secure. It's categorically more secure for high-risk targets.
The difference is threat-model dependent. Here's how to think about it:
Standard iOS: Protects against common threats. Stolen phones, malware downloaded from the App Store, hacking attempts using weak passwords. Effective for 99.9% of users.
Lockdown Mode: Protects against sophisticated nation-state attackers with zero-day exploits. Effective for journalists, activists, political prisoners, and people facing extreme threats.
One isn't better than the other. They're optimized for different threat models. Standard iOS is optimized for convenience and reasonable security. Lockdown Mode is optimized for maximum security regardless of convenience.
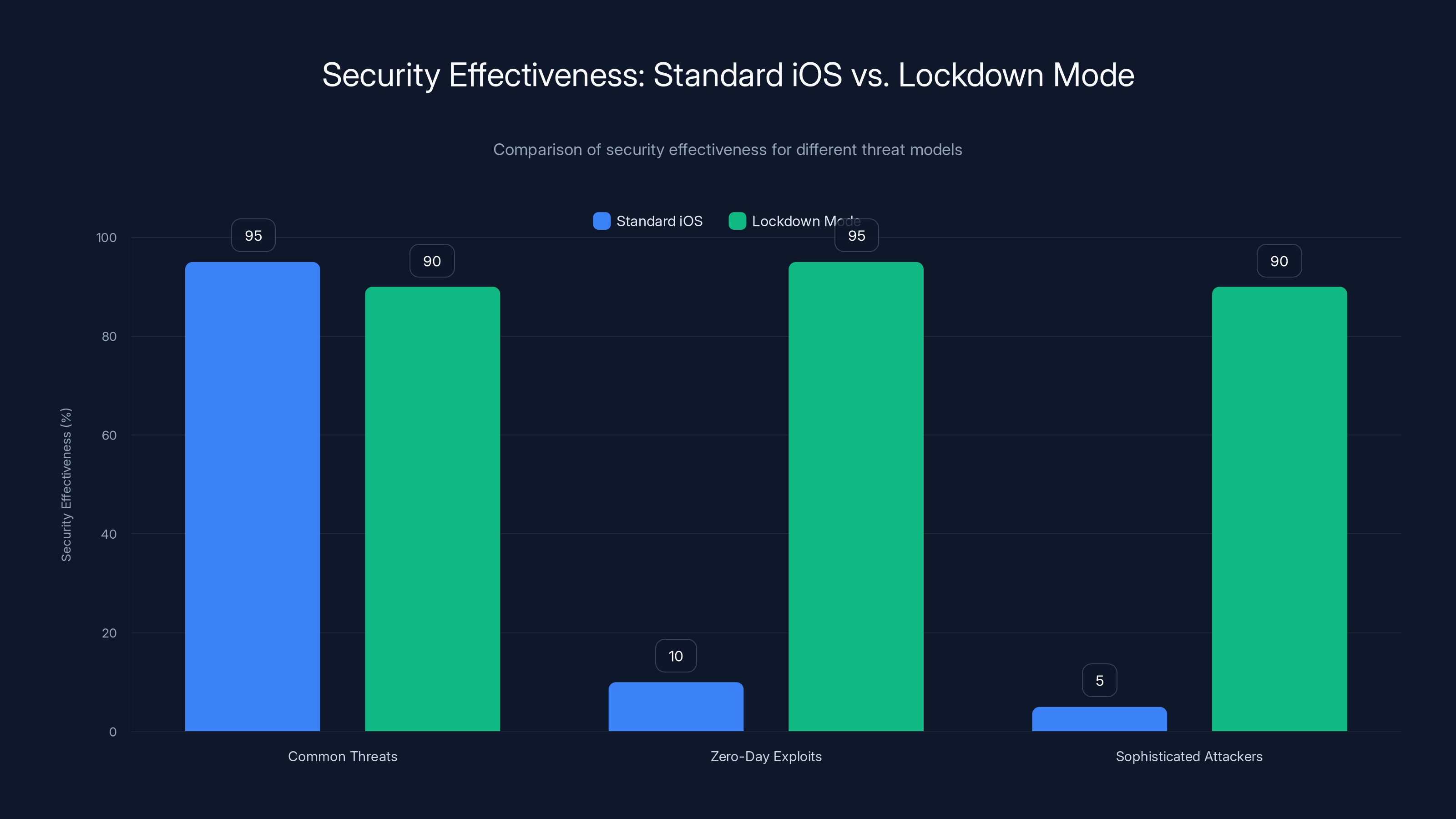
Standard iOS provides excellent protection against common threats, but Lockdown Mode significantly enhances security against sophisticated attackers and zero-day exploits. Estimated data.
The Pegasus Problem: Why Lockdown Mode Was Necessary
Lockdown Mode exists because of Pegasus. Understanding Pegasus helps explain why Apple felt compelled to create such an extreme security mode.
Pegasus is spyware created by NSO Group, an Israeli company that sells surveillance tools to governments. It's not malware in the traditional sense. You don't download it. You're not tricked into running it. It installs through zero-day exploits that are so sophisticated and so well-hidden that the victim never knows they've been compromised.
Once installed, Pegasus gives the operator total control. They can read all your messages, access photos and videos, monitor your location in real-time, listen to calls, and capture keystrokes. It's the most invasive form of surveillance possible through a phone.
The nightmare scenario for a dissident journalist or human rights activist in an authoritarian country: their device is compromised by Pegasus, probably through a zero-day exploit in a text message or email that exploited a vulnerability they didn't know existed. They have no indication they've been compromised. Every secret is exposed to the government. Every source is identifiable.
Pegasus was used extensively against activists, journalists, and political opponents. The Pegasus Project (an investigation by dozens of news organizations) documented its use against thousands of targets, including political opponents of various governments, human rights defenders, and journalists.
Standard iOS security couldn't stop Pegasus because Pegasus used zero-day exploits that iOS didn't know about. You can't patch something you don't know is broken. Pegasus demonstrated that even the world's most secure consumer operating system was vulnerable to well-resourced attackers.
Lockdown Mode's entire purpose is preventing Pegasus-like attacks. By eliminating the attack surface so severely, it makes it impractical to develop and deploy spyware. An attacker with a zero-day exploit can only use it if the feature it exploits is available. Lockdown Mode disables so many features that the odds of having a useful zero-day are drastically reduced.

Can Lockdown Mode Be Hacked? The Practical Reality
No security is absolute. Given unlimited resources and time, an attacker with zero-day exploits might theoretically break through Lockdown Mode. But the cost-benefit ratio changes dramatically.
Before Lockdown Mode, if you were a target of sophisticated attackers and they found a zero-day exploit, they could deploy it and compromise your device. The exploit would likely work because your device runs all the normal features that the exploit was designed to attack.
With Lockdown Mode, an attacker might still find a zero-day, but the feature that vulnerability exploits is probably disabled. They need a different zero-day. And another. They might need to chain together multiple zero-days, each one harder to find and more expensive to acquire.
At some point, the cost exceeds the benefit. For most targets—even valuable ones—Lockdown Mode makes exploitation impractical. You'd need to spend millions developing exploits for a target whose information isn't worth millions.
For state-sponsored attackers targeting the most important people? Lockdown Mode increases costs but doesn't make exploitation impossible. But that's the point. Lockdown Mode isn't designed to be unbreakable. It's designed to be unbreakable for the vast majority of threats while accepting that an adversary with unlimited resources might eventually break through.
The FBI raid in 2024 demonstrates this practical reality. The FBI had legal authority, physical possession of the device, and sophisticated forensic equipment. They still couldn't get in. This shows that Lockdown Mode is effective against even powerful institutional adversaries.
Should You Enable Lockdown Mode? Making the Decision
Honest answer: probably not.
Lockdown Mode is designed for a specific set of people facing specific threats. If you're not in that category, standard iOS security provides plenty of protection while remaining convenient.
Here's how to assess your threat model:
You might need Lockdown Mode if: You're a journalist investigating government or corporate wrongdoing. You're an activist challenging authoritarian regimes. You work in human rights. You're a political opposition figure. You've received credible threats. You handle sensitive information about public figures or governments. Your work makes you a valuable espionage target.
Standard iOS is sufficient if: You're protecting against theft and casual hacking. You want security against malware and compromised apps. You're concerned about privacy from advertisers and data brokers. You value your data but aren't facing sophisticated targeted attacks. Your threat model involves common crimes, not nation-state surveillance.
The honest assessment for most people: standard iOS is excellent. It's secure enough. It's more secure than any Android device. It's more secure than Windows or Mac. It's only insufficient if you're a specific type of target facing specific types of threats.
If you do enable Lockdown Mode, have a backup communication plan. Since FaceTime stops working from unknown numbers, make sure people can reach you through alternative methods. Since attachments are restricted, make sure collaborators know to use simple file formats. The inconvenience is real and requires planning.

The Broader Implications: What This Means for Device Security
The FBI's failure to access that journalist's iPhone in 2024 represents a turning point in how we think about device security. For decades, the assumption was that if a government agency had legal authority and physical possession of a device, they could access it. That assumption is now demonstrably false.
This changes negotiations between law enforcement and privacy advocates. It means the debate about encryption and backdoors is no longer theoretical. Lockdown Mode proves that unbreakable devices can exist in consumer products. Now the question is whether society wants them to.
This also changes how threats evolve. Attackers will focus on compromising devices before they're locked in Lockdown Mode. They'll target cloud accounts and backup services. They'll focus on network-level attacks rather than device exploits. The security arms race just moved to a different battlefield.
For manufacturers, Lockdown Mode raises the bar. Apple has proven that you can ship a consumer device that's essentially unbreakable without the passcode. Other manufacturers will likely follow with equivalent features. This expands the reality that sophisticated security is possible in consumer products.
For governments, it creates pressure to find new approaches. Some might try to regulate encryption or require backdoors. Others might increase pressure on device manufacturers to cooperate with law enforcement. Still others might accept that some devices are inaccessible and focus on network-level surveillance or other techniques.
For users, it means that personal security is becoming a genuine option, not just a technical fantasy. You can actually protect your device against sophisticated attacks. You can make your information inaccessible to powerful adversaries. That's revolutionary when you consider how device security worked even five years ago.
Lockdown Mode and Business Security: Enterprise Implications
While Lockdown Mode is designed for individual journalists and activists, it has interesting implications for business security.
For executives handling sensitive information, Lockdown Mode provides exceptional protection for confidential data. An executive's iPhone contains merger information, strategic plans, proprietary technology details. If compromised, this information could be worth millions. Lockdown Mode makes such compromise dramatically harder.
For companies with intellectual property concerns, Lockdown Mode offers peace of mind for key personnel. Rather than managing complex mobile device management systems, companies could recommend that executives with access to critical information enable Lockdown Mode.
The tradeoff is real—Lockdown Mode disables many enterprise features like complex VPN setups, certain authentication methods, and some mobile device management capabilities. So companies need to weigh the security benefits against operational costs.
For most businesses, standard iOS security combined with strong mobile device management is sufficient. But for companies competing in extremely high-stakes environments (defense, pharmaceutical R&D, financial services with state-level threats), Lockdown Mode becomes a valuable option.
The implication is that consumer device security is becoming sophisticated enough to protect enterprise information. Historically, that required specialized hardware and software. Now it's available in a consumer phone.
Future Evolution: What's Next for Lockdown Mode and Device Security
Lockdown Mode in 2025 is impressive, but it won't remain state-of-the-art indefinitely. Apple will continue evolving it, and competitors will develop their own equivalents.
Likely improvements: better granularity in what users can disable while maintaining protection. Currently, Lockdown Mode is all-or-nothing. Future versions might allow disabling FaceTime restrictions while keeping other features locked down. This would improve usability while maintaining security.
Integration with secure communication apps: Lockdown Mode might eventually work seamlessly with encrypted messaging apps, allowing secure communication even while other features are restricted.
Hardware improvements: Apple's custom silicon gives them advantages in implementing security. Future chips might include additional hardware protections that enable Lockdown Mode without sacrificing as many features.
Cross-platform standardization: If Lockdown Mode becomes standard in iPhones, Android manufacturers might develop equivalents. The mobile security landscape could shift toward everyone having access to maximum-security modes.
Government responses: Some governments might mandate backdoors or try to restrict maximum-security modes. Others might embrace them. This regulatory uncertainty will influence how the feature evolves.
The meta-trend: device security is becoming more sophisticated faster than attack capabilities. Five years ago, sophisticated attackers had reasonable confidence in compromising phones. Today, they face much higher barriers. In five more years, the barriers might be even higher—unless regulation intervenes to require backdoors.

Lockdown Mode and Everyday Security: How It Influences Normal iPhone Use
Even if you never enable Lockdown Mode, its existence influences how you think about iPhone security. It proves that protection at this level is possible, which changes your threat perception.
You realize that your iPhone is actually quite secure by default. The features Lockdown Mode disables are disabled for a reason—they represent potential attack vectors. Knowing this, you might be more cautious about what you do with your phone. You understand the security model better.
Lockdown Mode also influences which iPhone models and iOS versions matter. Older devices running older iOS versions have more vulnerabilities. Keeping current isn't just about features—it's about security. Lockdown Mode requires iOS 16 or later, which means devices running older versions don't have this option. This creates practical pressure to update.
For most people, the practical implications are subtle. You don't enable Lockdown Mode, but you're more aware of your phone's security. You understand that encryption and privacy protection actually work. You know that if you ever did need extreme security, the option exists.
This psychological shift is important. For decades, people assumed that phones weren't truly secure. That governments could access them. That privacy was impossible. Lockdown Mode proves that assumption wrong. Your phone can actually be secure. Privacy can actually be protected. This changes how people think about digital security generally.
The Lockdown Mode Debate: Where Are We Now?
As of 2025, Lockdown Mode exists. It works. The FBI couldn't break it. That's established fact. The debate has moved from "is this possible?" to "should we allow this?"
Privacy advocates argue that Lockdown Mode protects fundamental rights. Citizens have the right to protect their communications and data from government overreach. Surveillance capabilities, once granted, expand beyond their intended scope. Lockdown Mode represents reasonable protection against that expansion.
Law enforcement argues that Lockdown Mode hampers legitimate investigation. Criminal investigations sometimes require accessing devices. Terrorism investigations need to identify threats. Child exploitation investigations need to stop criminals. Unbreakable phones make this harder, potentially allowing criminals and threats to evade detection.
National security agencies argue that strong encryption and unbreakable devices create intelligence gaps. Understanding threats requires intelligence gathering. Devices they can't access become gaps in their threat assessment.
Tech companies argue that they have the right to design secure products. Security is a legitimate feature. Users have the right to choose security. Companies shouldn't be forced to implement backdoors or weaken security.
All these arguments have merit. This isn't a simple good-versus-evil scenario. It's a genuine policy tension: individual privacy protection versus institutional needs versus design freedom.
Different countries will resolve this differently. Some will accept unbreakable devices as inevitable. Others will try to require backdoors. Others will find middle ground. The reality is that technology now makes some devices unbreakable, and that's a fact societies need to grapple with.
Lockdown Mode isn't the end of the story. It's the beginning of a very long conversation about device security, privacy, and institutional access in an age where technology makes absolute security possible.
FAQ
What is Lockdown Mode exactly?
Lockdown Mode is Apple's most extreme security setting, available on iPhone 14 and later running iOS 16 or newer. When enabled, it disables numerous features and restricts device functionality to eliminate attack vectors that sophisticated threat actors use to compromise iPhones. The setting is designed for people facing targeted, sophisticated threats like nation-state surveillance or advanced cyber attacks.
How does Lockdown Mode protect against the FBI accessing an iPhone?
Lockdown Mode eliminates the attack surfaces that forensic tools typically exploit. It disables USB connectivity when the device is locked, restricts what attachment types can be processed, hardens the sandbox, prevents sideloading, and implements multiple other protections. These changes mean forensic techniques that normally work on iPhones simply don't have the attack vectors they need. The device becomes essentially unbreakable without the passcode, which is why the FBI couldn't access the journalist's phone in the 2024 raid despite having legal authority and physical possession.
What are the real inconveniences of using Lockdown Mode?
Lockdown Mode disables FaceTime incoming calls from unknown numbers, restricts file attachments in Messages and email, limits advanced web technologies, disables USB connectivity when locked, prevents Personal Hotspot, blocks AirDrop and certain Bluetooth features, and restricts some iCloud functionality. These aren't minor tweaks—they fundamentally change how an iPhone operates. For someone relying on their phone for everyday communication and work, these restrictions can be severe. However, for journalists or activists facing sophisticated threats, these inconveniences are acceptable trade-offs for security.
Who actually needs Lockdown Mode?
Lockdown Mode is designed for journalists investigating government or corporate wrongdoing, activists in authoritarian countries, human rights defenders, political opposition figures, and others facing targeted attacks from sophisticated threat actors. People protecting against theft, malware, or ordinary hacking don't need Lockdown Mode. Standard iOS security is more than sufficient for average users. The feature is specifically optimized for high-value targets facing nation-state-level threats.
Can Lockdown Mode actually be hacked or bypassed?
Theoretically, an attacker with unlimited resources and multiple zero-day exploits might break through Lockdown Mode, but the practical difficulty increases exponentially. Before Lockdown Mode, a single zero-day exploit could compromise an iPhone. With Lockdown Mode, attackers might need multiple zero-days chaining together, each one in features that the mode didn't disable. The cost and difficulty become impractical for most targets. The 2024 FBI raid demonstrates that even law enforcement with sophisticated tools couldn't break through, suggesting Lockdown Mode is effectively secure against most real-world threats.
How does Lockdown Mode compare to encryption and privacy on Android?
Android phones offer encryption and security features, but no equivalent to Lockdown Mode. While Android's security has improved significantly, iOS remains more hardened by default. Lockdown Mode represents an extreme security posture that Android devices haven't matched. For users facing sophisticated targeted threats, iOS with Lockdown Mode offers substantially better protection than standard Android devices. However, for everyday users, both platforms offer reasonable security, with iOS maintaining advantages in consistent updates and unified hardware-software integration.
Should I enable Lockdown Mode to feel more secure?
No. If you're enabling Lockdown Mode just to feel safer while scrolling social media or checking email, you don't need it. The inconveniences far outweigh the benefits for everyday users. Standard iOS security already protects against common threats like theft, malware, and weak-password hacking. Lockdown Mode is designed for people facing actual sophisticated targeted threats. Enabling it without facing those threats means accepting significant inconvenience for protection you don't actually need.
Can Lockdown Mode help protect business or corporate information?
Lockdown Mode can help protect sensitive business information for executives handling critical data, but it requires coordination with IT departments. Some enterprise security systems assume standard iOS features and might conflict with Lockdown Mode restrictions. For most companies, standard iOS security combined with proper mobile device management is sufficient. However, for companies in high-stakes industries handling state-level threats, Lockdown Mode is worth evaluating despite the compatibility challenges.
What's the difference between Lockdown Mode and regular iPhone encryption?
Regular iPhone encryption protects your data at rest, securing what's stored on the device. Lockdown Mode goes further by protecting against active attacks, sophisticated exploits, and targeted surveillance. Encryption prevents people from reading your data if they steal the device and extract the storage. Lockdown Mode prevents people from installing spyware, executing exploits, or breaking in through zero-day vulnerabilities. They're complementary protections—encryption is standard iOS, Lockdown Mode is an extreme option for extreme threats.
Will Lockdown Mode become standard on all phones?
Android manufacturers are likely to develop equivalent features as consumer demand for privacy and security increases. However, Lockdown Mode might remain unique to iPhones for years because it relies on Apple's integration of hardware and software. Implementing equivalent protection on diverse Android devices is more challenging. In the long term, maximum-security modes might become standard across platforms, but for now, Lockdown Mode remains an iOS exclusivity that's generated significant interest from the Android security community.
Conclusion: The Future of Device Security in Your Hands
The 2024 FBI raid on a journalist's home showed something that security researchers have argued for years: truly secure devices are possible. Not theoretical. Not academic. Actual devices running actual software that federal law enforcement can't access despite having legal authority and physical possession.
Lockdown Mode is the practical embodiment of this principle. It's not perfect. It's not unbreakable. But it's effective enough against real threats that the most sophisticated forensic capabilities in the world couldn't bypass it. That's remarkable. That's important. That changes how we think about device security going forward.
For journalists, activists, and others facing targeted threats, Lockdown Mode is a genuine game-changer. It means you can use a modern smartphone and still have reasonable confidence that your communications and data won't be compromised by sophisticated attacks. That's powerful. For decades, people in these situations had to choose between having a modern phone and having security. Lockdown Mode makes that choice unnecessary.
For most people, this is interesting but not directly applicable. Standard iOS security is more than sufficient for everyday needs. But Lockdown Mode's existence changes the security landscape for everyone. It proves that extreme security is possible. It shifts the conversation about encryption, privacy, and device access. It puts pressure on other manufacturers to offer equivalent protection.
The implications are still unfolding. Governments will respond. Manufacturers will innovate. The technology will evolve. But the fundamental reality has been established: consumer devices can be made essentially unbreakable. Whether society wants them to be is a question we're still figuring out.
If you're facing genuine threats, Lockdown Mode is worth enabling despite the inconvenience. If you're not, standard iOS security is sufficient and more practical. Either way, understanding how Lockdown Mode works and what it does gives you better insight into device security generally. You understand that protection is possible. You understand the trade-offs. You understand that your phone can actually be secure if you need it to be.
That understanding matters. In a world where devices are increasingly central to how we communicate, work, and think, knowing that genuine security is possible is empowering. Lockdown Mode proves it's real.
Key Takeaways
- Lockdown Mode eliminated attack vectors that even the FBI with forensic tools couldn't overcome in a 2024 raid, proving that unbreakable consumer devices are technically feasible
- The feature works by disabling 30+ iOS functions simultaneously—FaceTime, USB connectivity, attachments, cloud features—creating such a minimal attack surface that sophisticated zero-day exploits become impractical
- Designed specifically for journalists, activists, and human rights defenders facing nation-state surveillance rather than everyday users, with real inconvenience costs that make it impractical for casual use
- Lockdown Mode emerged directly from documented campaigns against journalists and activists using Pegasus spyware, showing how real-world threats drive security innovation in consumer devices
- The feature represents a turning point in the encryption debate: governments can no longer assume they'll access devices with legal authority, forcing a genuine societal conversation about security, privacy, and institutional power
Related Articles
- Apple's Lockdown Mode Defeats FBI: What Journalists Need to Know [2025]
- ExpressVPN 81% Off Deal: Is It Worth It? [2025]
- Switzerland's Data Retention Law: Privacy Crisis [2025]
- France's VPN Ban for Minors: Digital Control or Privacy Destruction [2025]
- France's VPN Ban for Under-15s: What You Need to Know [2025]
- Major Cybersecurity Threats & Digital Crime This Week [2025]
![iPhone Lockdown Mode Explained: How Apple's Ultimate Security Works [2025]](https://tryrunable.com/blog/iphone-lockdown-mode-explained-how-apple-s-ultimate-security/image-1-1770297005382.jpg)



