Last Pass Phishing Scam: How to Spot Fake Support Messages [2025]
Your password manager is supposed to be your safety net. But what happens when criminals weaponize trust against you?
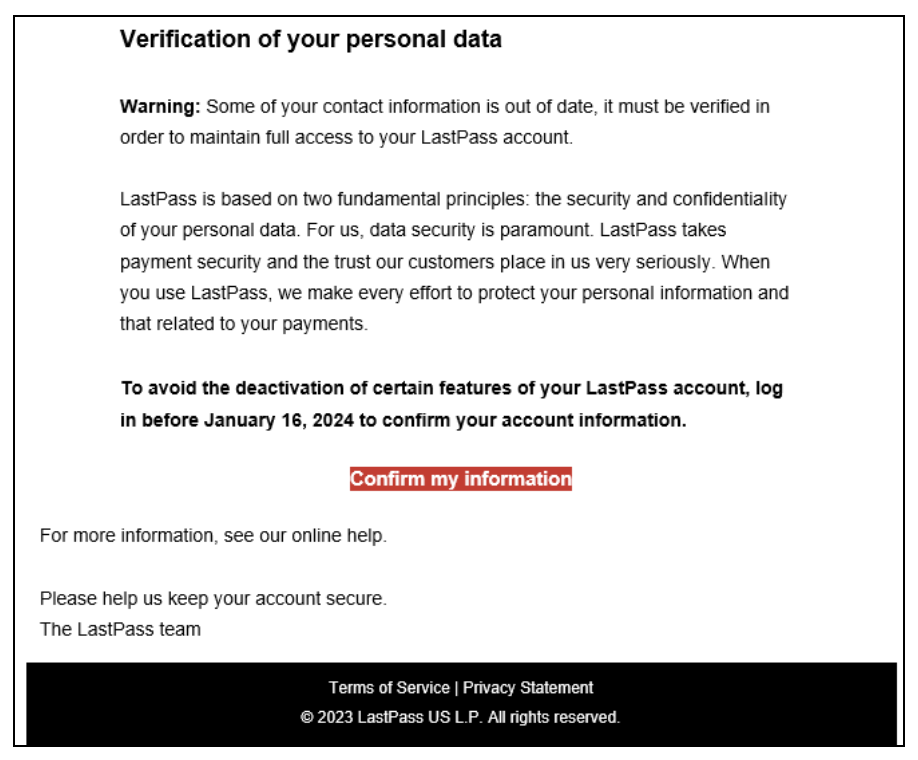
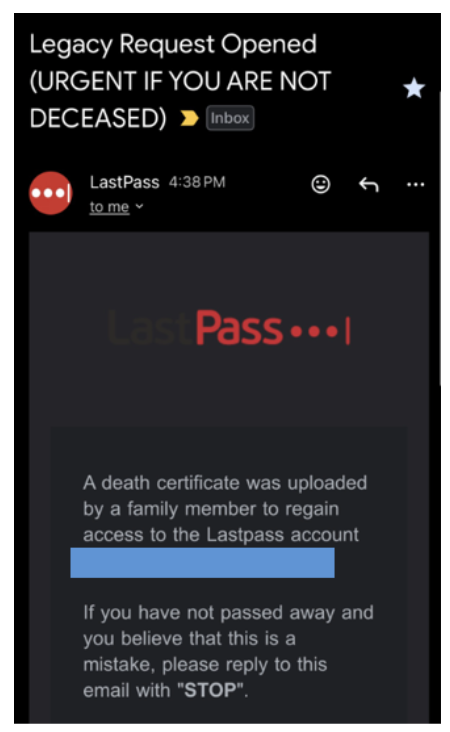
Last month, a new phishing campaign started circulating, targeting Last Pass users with emails that look almost identical to legitimate company communications. The premise is simple but devious: fake emails warn of "scheduled maintenance" and demand urgent action within 24 hours to backup your vault. Click the link, enter your credentials, and boom—attackers have your master password. Everything you've protected in your password manager is now exposed.
This isn't a hypothetical threat. Last Pass confirmed the campaign is active and widespread. And here's the terrifying part: the emails are convincing. They include official-looking branding, proper terminology, and a sense of urgency that makes people act before thinking.
In this guide, we're going to walk you through exactly what this scam looks like, why it works, how to protect yourself, and what to do if you've already fallen for it. We'll also explore the broader landscape of password manager security threats and why phishing remains one of the most effective attack vectors in 2025.
TL; DR
- Last Pass never asks for your master password via email or support messages—period
- Fake sender domains include support@sr 22vegas[.]com, support@lastpass[.]server 8, and similar variations
- The 24-hour urgency is a classic social engineering tactic designed to bypass your critical thinking
- Check sender email addresses carefully and hover over links before clicking (don't trust display names)
- If compromised, change your master password immediately and enable two-factor authentication if you haven't already
- Report suspicious emails to abuse@lastpass.com and your email provider
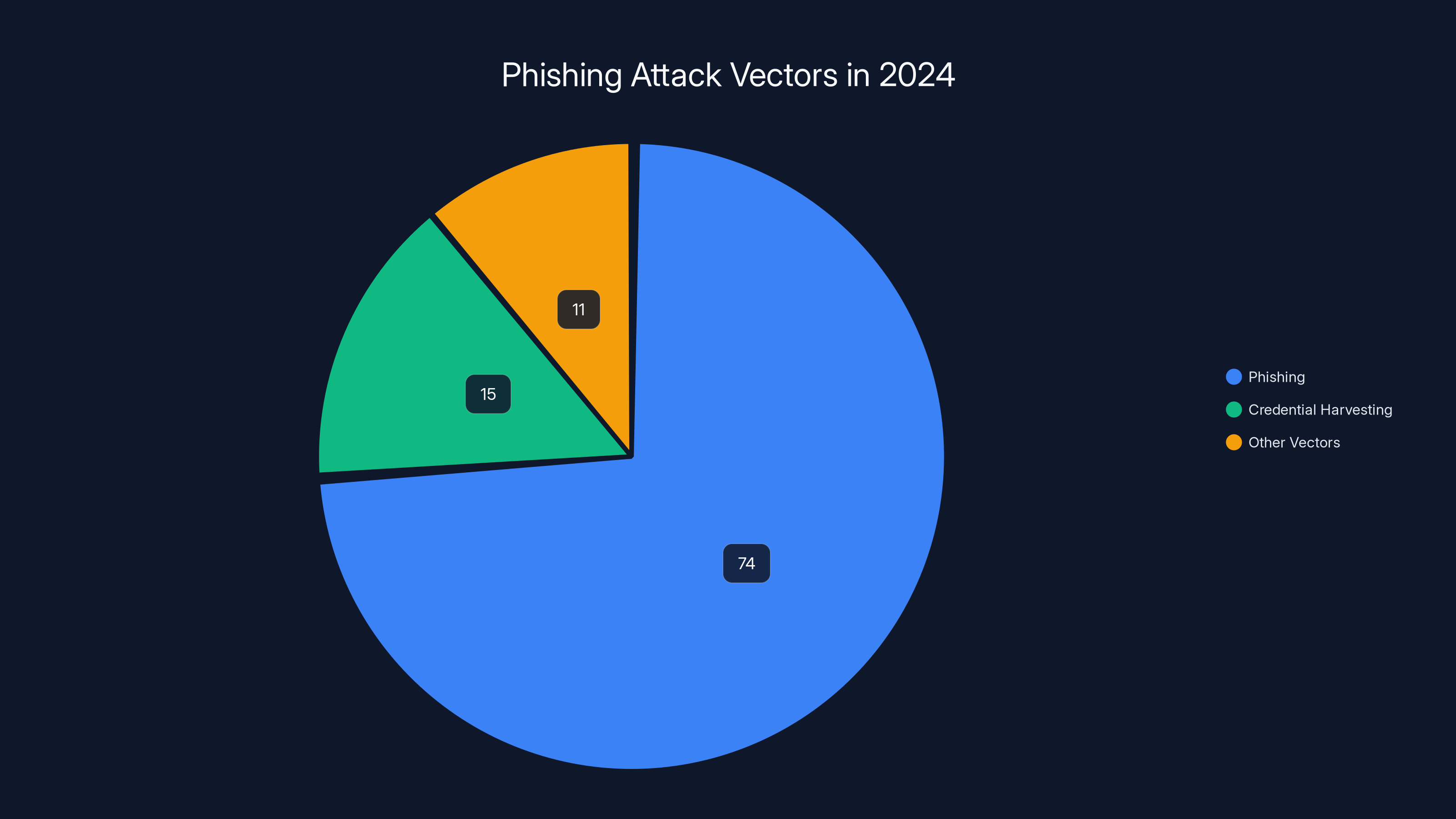
Phishing accounted for 74% of all breach classifications in 2024, highlighting its prevalence as a primary attack vector.
Understanding the Last Pass Phishing Campaign
Let's start with what we know about this specific threat. In January 2026, Last Pass issued an official warning about a coordinated phishing campaign targeting its user base. The attackers created a fake maintenance scenario, claiming that users needed to backup their vaults urgently to prevent data loss during system upgrades.
This tactic preys on a fundamental human behavior: when someone believes a service they trust is about to lose their data, they act fast. They don't read carefully. They don't verify. They just want to protect their stuff.
The phishing emails include several telltale elements that make them appear legitimate at first glance. They reference real Last Pass features, use professional formatting, include links that appear to go to Last Pass, and create artificial time pressure. The attackers even spoofed sender addresses to look like they came from Last Pass support domains.
What makes this campaign particularly dangerous is that it targets a specific vulnerability in human psychology: we're more likely to trust communications about security and maintenance. When someone claims there's an urgent backup needed, we assume the sender has our best interests in mind. That assumption is the entire hook.
The campaign uses multiple variations of fake sender addresses to increase the probability that at least some emails slip past spam filters. These include support@sr 22vegas[.]com (which has no obvious connection to Last Pass), support@lastpass[.]server 8, support@lastpass[.]server 7, and support@lastpass[.]server 3. The server variations are particularly insidious because they use "lastpass" in the domain, creating plausible deniability.

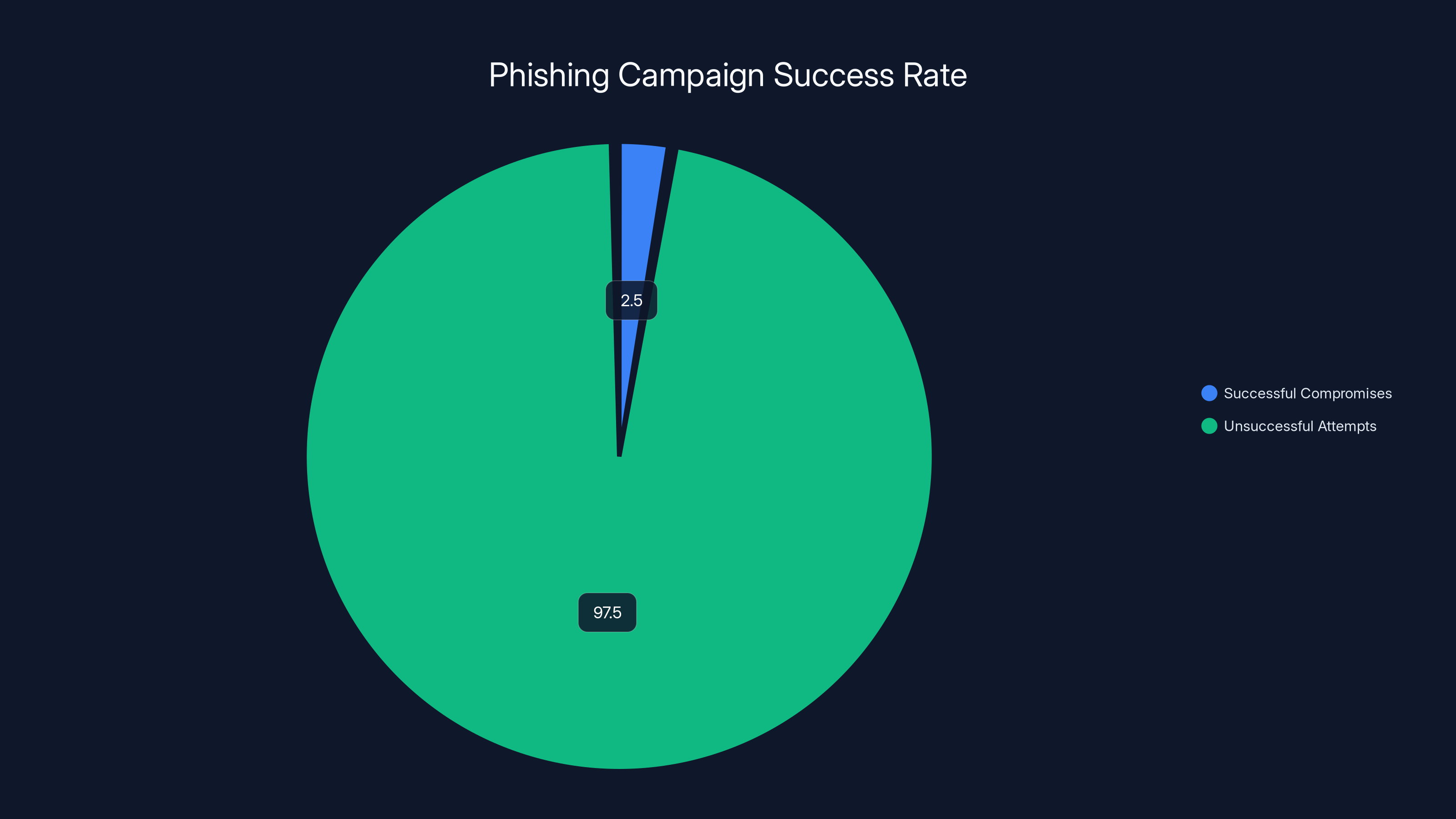
Estimated data shows that even a 2-3% success rate in phishing campaigns can lead to hundreds of compromised accounts, highlighting the effectiveness of these attacks.
How These Fake Support Messages Actually Work
To understand how to protect yourself, you need to understand the mechanics of the attack. It's not magic—it's basic social engineering applied systematically.
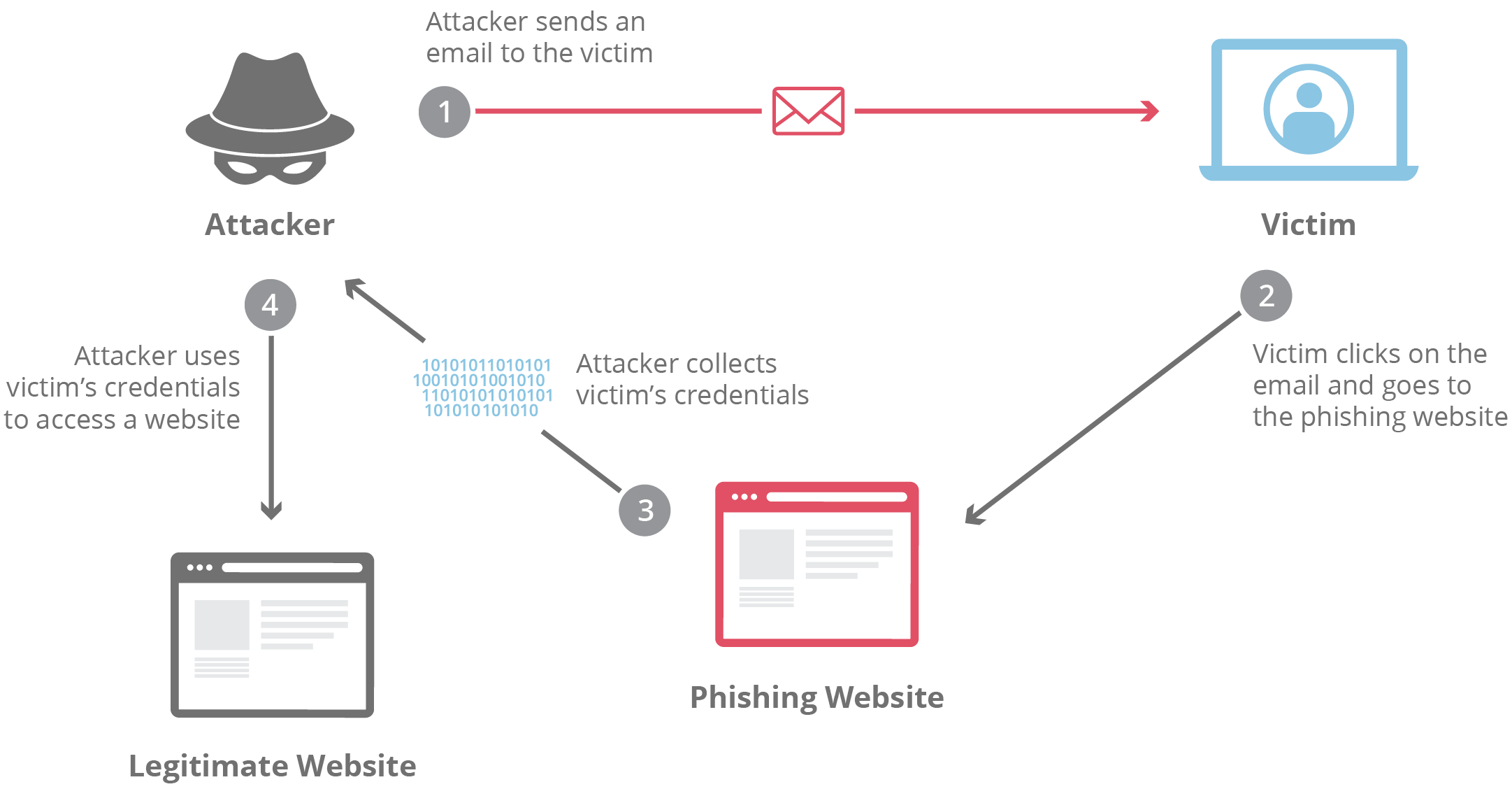
The campaign follows a predictable but effective pattern. First, attackers send thousands of emails at scale, knowing that even a 2-3% click-through rate represents hundreds of compromised accounts. Second, they create a sense of urgency by claiming maintenance is happening in 24 hours. This time pressure is crucial—it prevents people from verifying the email through normal channels.
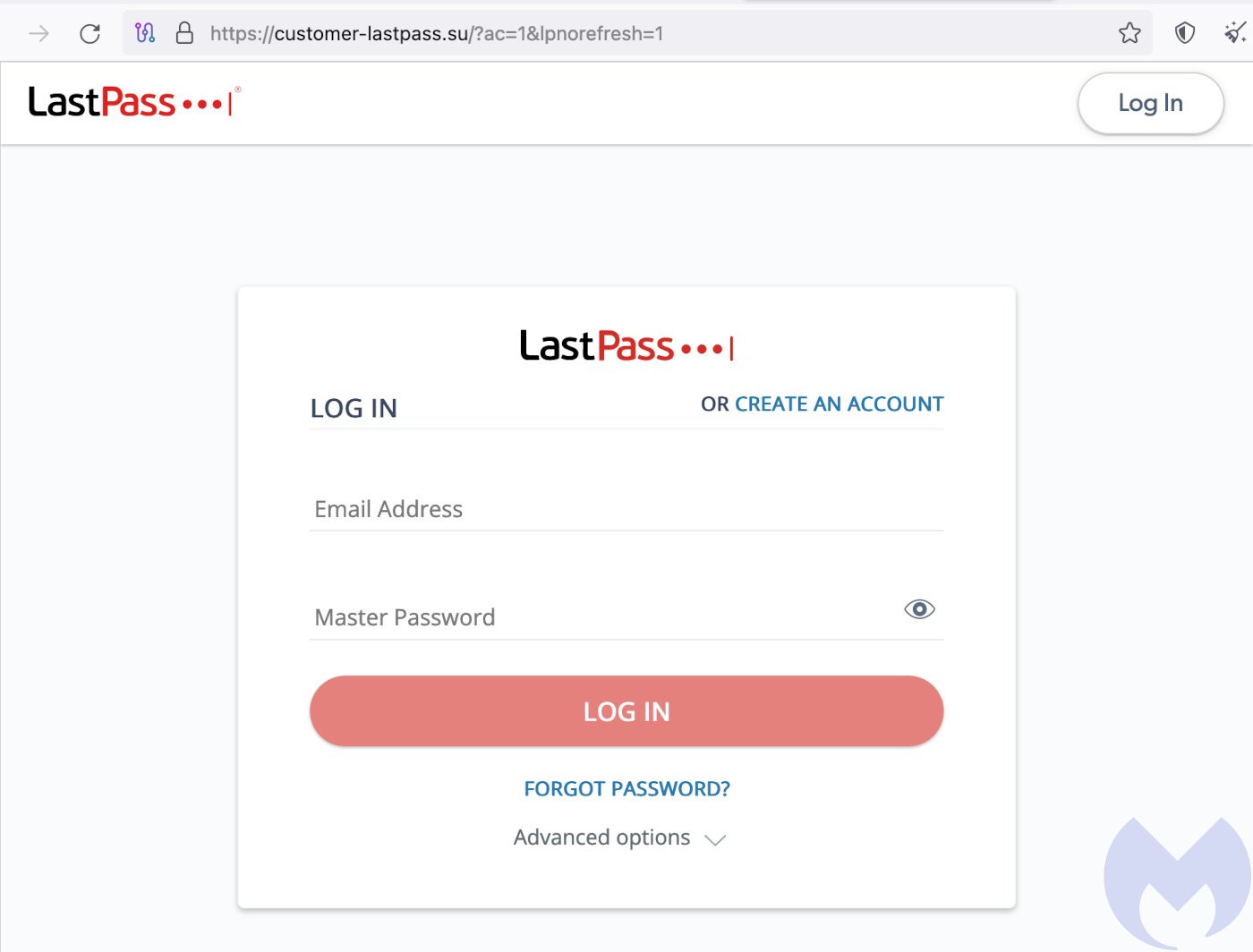
Third, the email includes a link that appears to lead to Last Pass. When you click it, you're taken to a fake login page that looks almost identical to the real one. It might have slight differences in spacing, font, or color, but the average person won't notice. You enter your master password and email address, assuming you're logging into the legitimate backup system. The scammers capture this information and immediately test it against the real Last Pass servers.
If your password is correct, they have access to your entire vault. Depending on what you store there—credit cards, banking credentials, two-factor authentication recovery codes, cryptocurrency wallets—the damage can be catastrophic.
What's particularly clever about this campaign is that it doesn't always trigger immediately. Some attackers will harvest credentials and wait weeks or months before accessing accounts. This gives them time to avoid raising suspicion while the phishing emails fade from your memory.
The psychology is sophisticated too. Last Pass is, by definition, a service that manages security. So when someone gets an email claiming there's a security issue, the target's guard is actually down—they assume the sender must be trustworthy because they're managing something that matters. Attackers exploit this meta-level trust.
Why Phishing Still Works in 2025
You'd think that after decades of phishing scams, people would be immune. Yet here we are in 2025, and phishing is still the most effective attack vector. Why?
First, the human brain hasn't evolved to handle digital environments. We have instincts for reading faces, understanding tone, and detecting lies in person. Online, those instincts are useless. An email can be crafted by a person halfway around the world, and there's no way to tell it's fake without deliberate verification.
Second, phishing works at scale. An attacker doesn't need to fool everyone—they just need to fool enough people. If they send 10,000 emails and 0.1% of recipients fall for it, that's still 10 compromised accounts. At a 1% success rate, they have 100. Scale up to millions of emails, and the numbers become staggering.
Third, password managers have become high-value targets. They're not like stealing someone's email password, which gives you access to one service. Stealing someone's master password gives you access to everything—every bank account, every cryptocurrency wallet, every sensitive account they've ever created. From an attacker's perspective, password managers are jackpots.
Fourth, the tools for creating convincing phishing emails have become democratized. You don't need to be a programmer or designer—you can buy templates, use AI tools to generate convincing copy, and deploy campaigns through rented infrastructure. The barrier to entry has never been lower.
Finally, phishing works because legitimate companies sometimes do send urgent security messages. Last Pass has, in the past, sent emails about security updates and account issues. So when an attacker sends a fake email claiming there's an urgent security issue, it's plausible. It fits the pattern of real communications you've received before.
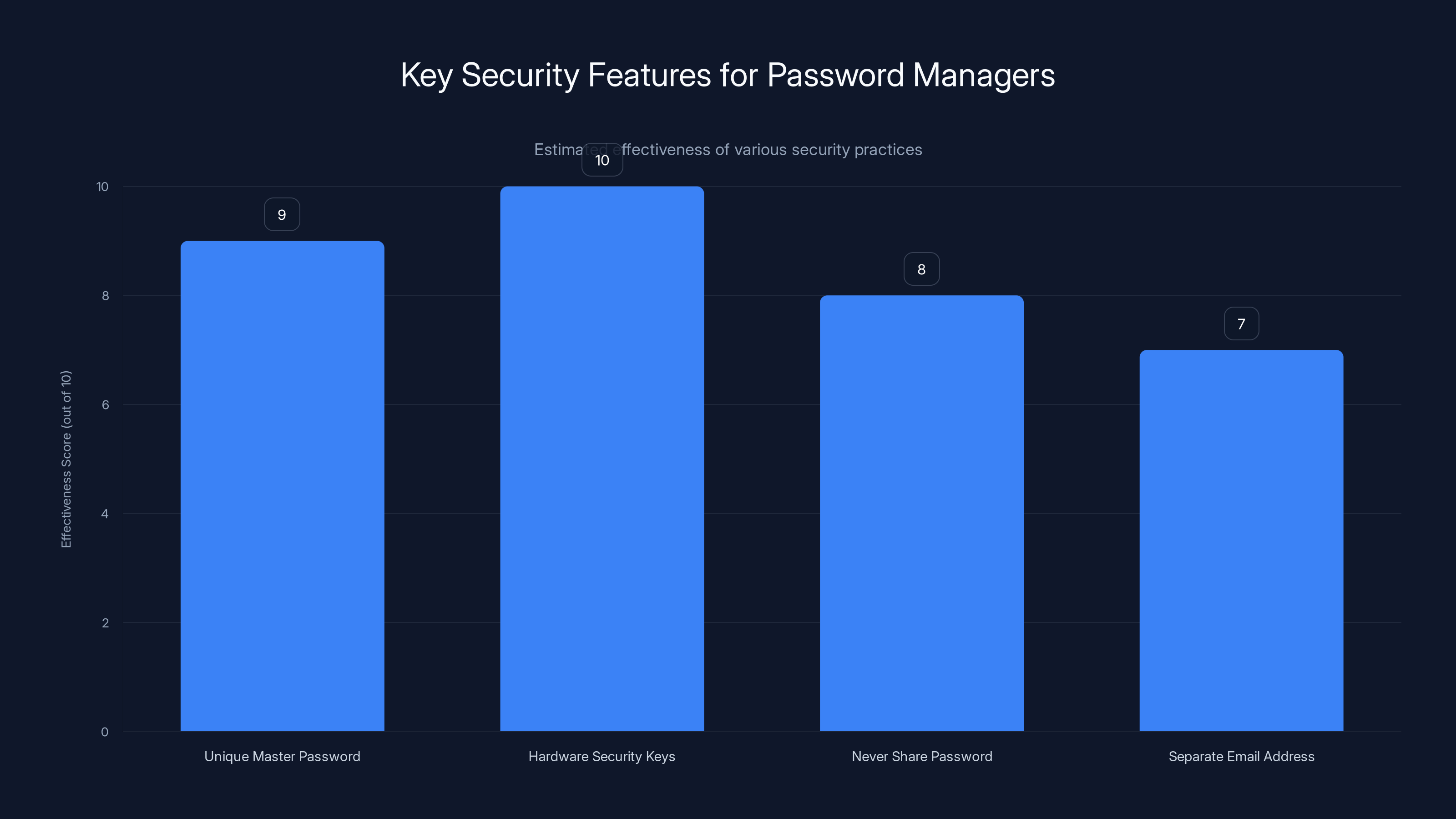
Hardware security keys offer the highest level of protection, closely followed by using a unique master password. Estimated data based on security best practices.
Red Flags That Expose Fake Last Pass Emails
Now let's talk about defense. There are specific things you can check to determine whether an email claiming to be from Last Pass is legitimate.
Sender Address Is Paramount
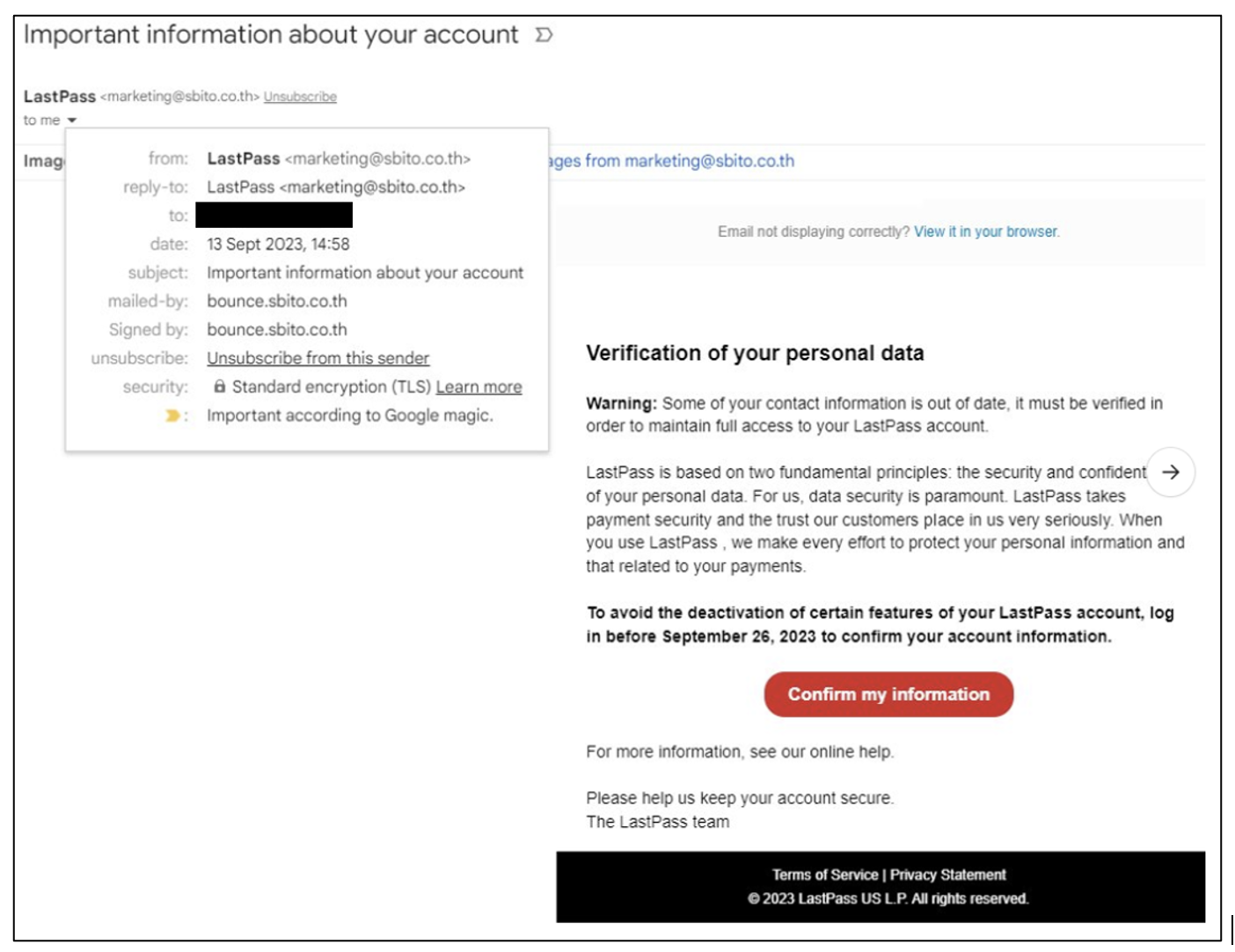
The most reliable indicator is the sender's email address. Last Pass support communications should come from @lastpass.com or a verified Last Pass domain. Anything else is suspicious. The fake campaign uses addresses like support@sr 22vegas[.]com, support@lastpass[.]server 8, or support@lastpass[.]server 7.
Notice how the "server" variations try to appear legitimate? They use "lastpass" in the domain name, betting that you'll see it and assume it's official. But Last Pass doesn't use subdomains like server 7 or server 8 for communications. When you see something like support@lastpass[.]server 3, it's a tell-tale sign of a spoofed email.
To verify the sender address, don't just look at the display name. An attacker can set the display name to "Last Pass Support" while using a completely different email address. In most email clients, you need to click on the sender's name or open the full header to see the actual email address.
Link URLs Don't Match the Display Text
Hover over any links in the email. The link text might say "Go to Last Pass," but where does it actually lead? If it doesn't go to lastpass.com or a verified Last Pass subdomain, it's fake.
Attackers often use text that says something like "Verify Your Account" or "Complete Backup," but the actual URL is something completely different. Your email client should show you the true destination when you hover over the link. If it doesn't, that's a red flag in itself.
The Urgency Language
Legitimate security communications sometimes do include time-sensitive information. But real password manager companies know that urgency is a classic phishing tactic, so they usually phrase things carefully. The Last Pass phishing campaign uses language like "you must backup your vault within 24 hours" or "action required immediately."
Compare this to how legitimate companies usually phrase things: "We recommend updating your password" or "Please review your recent account activity." There's a difference between urgent phrasing and pressure phrasing. Real companies are careful to avoid language that mimics known phishing tactics.
Email Design and Formatting
Last Pass and other professional companies maintain consistent design standards in their emails. If an email looks slightly off—different fonts, weird spacing, pixelated logos—it might be a clue. Attackers sometimes use free templates that don't perfectly match the real brand guidelines.
That said, this is a weak indicator. Scammers are getting better at design every year, and legitimate emails sometimes get mangled by email clients anyway. Don't rely solely on appearance.
Generic Greetings Instead of Personalization
Legitimate companies often personalize emails with your name or account information. Phishing emails frequently use generic greetings like "Dear User" or "Dear Valued Last Pass Customer." If an email about your account doesn't mention your name or account details, it's worth being suspicious.
Requesting Sensitive Information
This is the most important red flag: Last Pass will never ask for your master password via email, text, or phone. Period. If an email asks for your master password, 2FA codes, recovery codes, or other sensitive credentials, it's a phishing email. Don't even consider responding.
Legitimate companies have systems for password resets that never require them to see your actual password. If someone is asking for it, they're not who they claim to be.
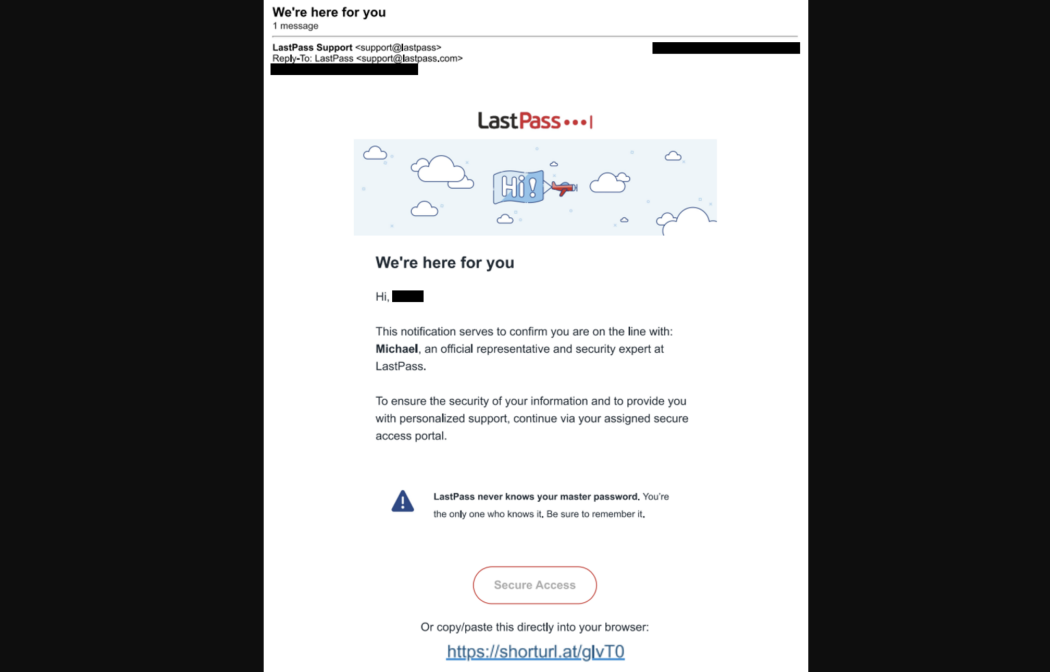
Immediate Steps If You've Clicked a Phishing Link
Let's say you received one of these emails and clicked the link. You may have even started entering your credentials. What now?
First, don't panic. You have options, and the damage isn't necessarily catastrophic if you act quickly.
Step 1: Stop What You're Doing
If you realize mid-way through entering your password that something feels wrong, stop immediately. Don't finish entering information. Close the tab or window.
Step 2: Go Directly to Last Pass
Don't click any more links from the suspicious email. Instead, go directly to lastpass.com by typing the URL into your browser address bar. Log into your account using your legitimate master password.
If you didn't realize the email was fake until later, you still want to do this. Go to the official Last Pass website and log in.
Step 3: Check Your Account Activity
Once you're logged in to your real Last Pass account, look for any unauthorized access logs or suspicious activity. Most password managers have an "Account Activity" or "Security" section where you can see login attempts and access history.
If you see logins from locations you don't recognize, or at times when you weren't using the service, someone has accessed your account.
Step 4: Change Your Master Password Immediately
This is crucial. Change your master password to something completely new. Make it strong, at least 16 characters, with uppercase, lowercase, numbers, and special characters.
Changing your master password does multiple things:
- It locks out anyone who obtained the old password
- It forces a re-encryption of all your stored credentials
- It changes the decryption key needed to access your vault
If an attacker has your old master password, having the old password doesn't help them anymore once you've changed it. The encryption scheme in Last Pass means that changing your master password is essentially like changing all of your security at once.
Step 5: Enable or Strengthen Two-Factor Authentication
If you haven't already enabled two-factor authentication (2FA) on your Last Pass account, do it now. Even if someone has your master password, they won't be able to access your account without passing the second factor.
Last Pass supports multiple 2FA methods:
- Authenticator apps (Google Authenticator, Microsoft Authenticator, Authy)
- Hardware security keys (Yubi Key, Titan Security Key)
- SMS or email codes
- Biometric authentication (where available)
The strongest option is a hardware security key, but authenticator apps are solid middle ground between security and convenience.
Step 6: Review and Update Passwords for Critical Accounts
If your Last Pass vault was compromised, the attacker has access to all your stored passwords. Your banking passwords, email passwords, cryptocurrency wallets—everything.
Prioritize the most critical accounts:
- Email account - This is the gateway to everything else. If someone has your email password, they can reset passwords for any service that uses email for recovery.
- Banking and financial accounts - Update these immediately.
- Cryptocurrency and investment accounts - These are high-value targets.
- Work accounts - Depending on what you access, these could be sensitive.
- Social media and other services - Lower priority, but still worth updating.
This is tedious, but necessary. You can't trust that a single password change will protect you if the attacker accessed your vault.
Step 7: Monitor Your Accounts for Suspicious Activity
Set up alerts on your banking accounts, credit cards, and email. Watch for unauthorized transactions or access attempts.
Consider placing a fraud alert or credit freeze with the major credit bureaus (Equifax, Experian, Trans Union) if you're concerned about identity theft. A credit freeze prevents anyone from opening new accounts in your name without unfreezing it first.
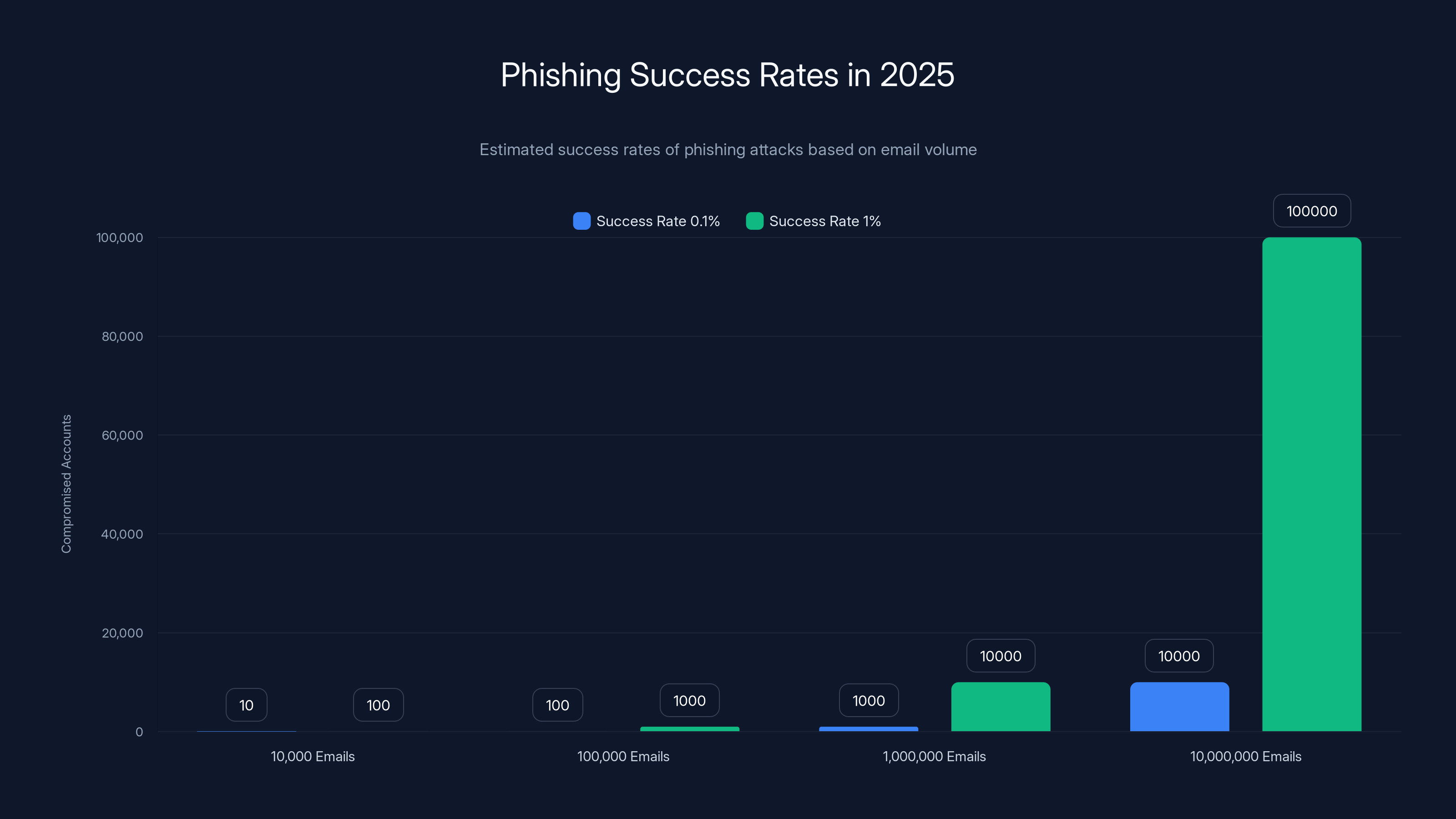
Even with low success rates, phishing can compromise thousands of accounts due to the sheer volume of emails sent. Estimated data.
What NOT To Do After a Phishing Attack
In your panic, you might be tempted to do things that actually make the situation worse. Let's talk about the mistakes to avoid.
Don't Ignore It and Hope
Some people realize they've been phished and then just... don't do anything about it. They hope the attacker won't access their account, or that nothing bad will happen. This is gambling with your security.
Attackers who harvest credentials test them quickly. If you don't change your password within hours, they might already have access. Taking action immediately gives you the best chance of staying ahead of them.
Don't Click Any More Links From the Suspicious Email
If an email led you to a phishing site once, it might do it again. Any link in that email is potentially malicious. Delete it or report it as spam.
Don't Share the News on Social Media or Email
It might feel like you're helping others by warning them about the phishing campaign, but broadcasting that you fell for it has downsides. You're publicly announcing that you were compromised, which might attract additional attention from scammers.
Instead, report the email to Last Pass (abuse@lastpass.com) and your email provider, and tell friends directly through trusted channels.
Don't Reuse Any Passwords
After being phished, never reuse the compromised password. This is a good general rule anyway, but it's critical after an incident. Each account should have a unique, strong password. A password manager makes this feasible.
Don't Assume You Only Need to Change Last Pass
Yes, you changed your Last Pass master password. But your vault still contains hundreds of other passwords. Those are now potentially compromised too. You need to update the critical ones.
The Broader Context: Why Password Managers Are Targeted
Password managers aren't uniquely vulnerable to phishing—email phishing works against any online service. But password managers are specifically attractive targets because of their high value.
Consider what an attacker gets from compromising a typical email account: access to that email service, plus the ability to reset passwords for services using that email for recovery. It's valuable, but limited.
Now consider what they get from compromising a Last Pass vault: access to potentially hundreds of passwords, banking credentials, cryptocurrency wallets, secure notes with sensitive information, and more. It's exponentially more valuable. One compromised password manager vault can lead to compromise of dozens of other accounts.
This is why password managers are increasingly targeted by phishing campaigns, ransomware operations, and targeted attacks. They're high-value targets, and compromising one is like hitting a jackpot.
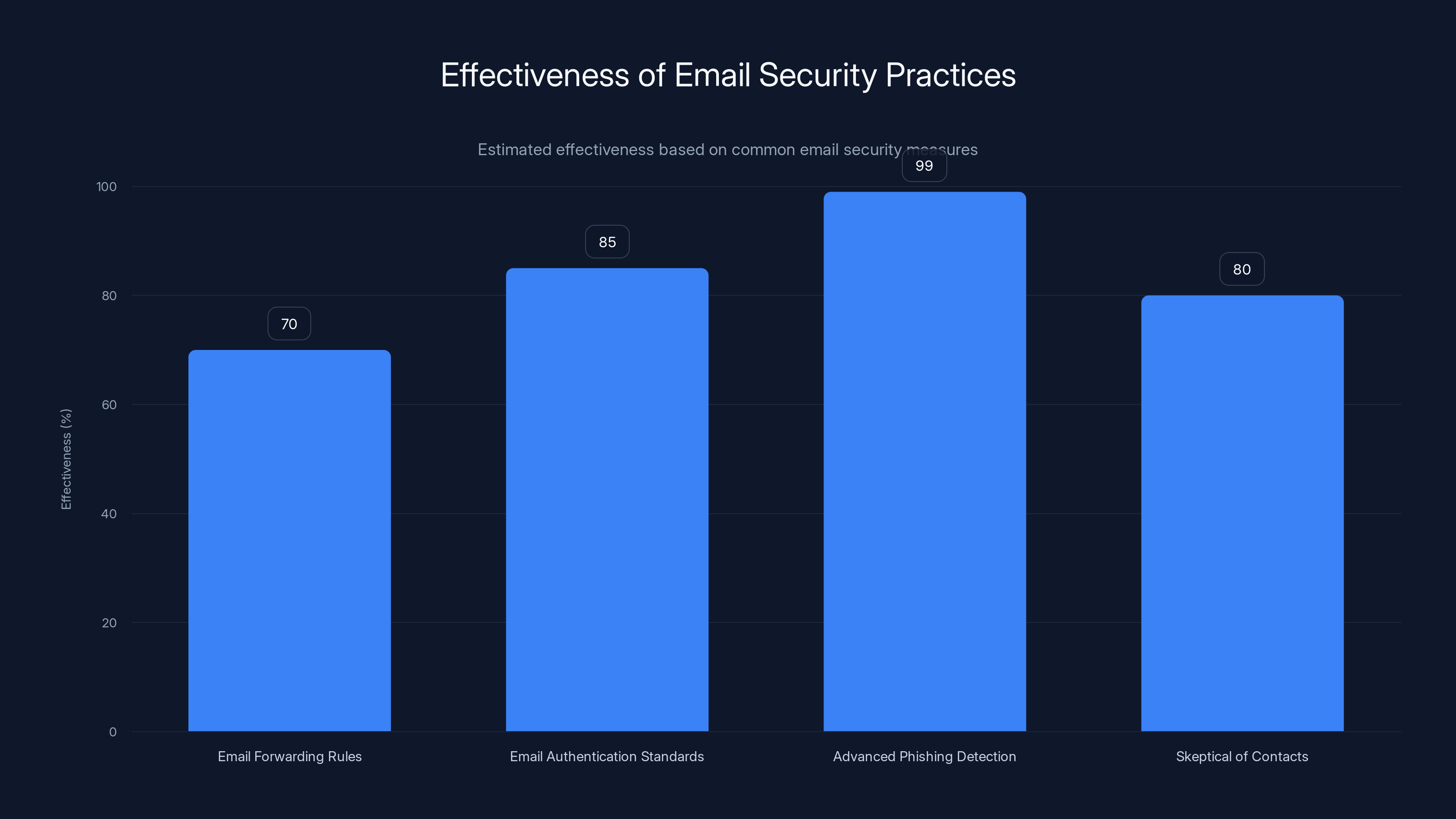
Advanced phishing detection is the most effective practice, catching up to 99% of threats. Email authentication standards also significantly enhance security. Estimated data.
How to Strengthen Your Password Manager Security
Beyond avoiding phishing, there are specific steps you can take to make your password manager account harder to compromise.
Use a Unique Master Password You'll Never Forget
Your master password should be strong and unique. Not just strong—unique to your Last Pass account. This means you can't reuse it from some other service.
A good master password is at least 16 characters and includes uppercase, lowercase, numbers, and special characters. Avoid dictionary words, birthdays, or information someone could guess about you.
One trick: use a passphrase combining random words with numbers and special characters. "Blue Penguin#42
Enable Hardware Security Keys
If Last Pass supports it (and it does), use a hardware security key for two-factor authentication. These are small devices, like a Yubi Key or Google Titan Security Key, that you physically connect to your computer when logging in.
Hardware keys are resistant to phishing because they won't authenticate unless the domain you're accessing matches the domain they were registered for. Even if you're on a convincing phishing page, the key won't generate a valid authentication code for that site.
Never Share Your Master Password
Obvious? Yes. But bear repeating. Your master password should only exist in your mind. Never write it down somewhere an attacker could find it. Never tell anyone, even if they claim to work for Last Pass.
Use a Separate Email Address (If Practical)
Some security-conscious users create a dedicated email address just for their password manager account. This email address has a strong password, two-factor authentication, and is used for nothing else.
The idea is that if an attacker compromises your primary email address, they haven't automatically compromised your password manager account, because it's registered to a different email.
This is more security theater than practical defense, but it does add a layer of separation.
Keep Your Device Secure
Last Pass runs on your device. If your device is compromised by malware, your entire vault is at risk—no amount of password strength helps if a keylogger is capturing every character you type.
Keep your operating system patched, use antivirus software, and avoid running untrusted software.
Use the Breach Alert Feature
Last Pass (and most password managers) have a breach alert feature that monitors public databases of leaked passwords and credentials. If your password shows up in a breach, they'll notify you.
This isn't perfect protection, but it does give you a heads-up if your credentials are exposed somewhere.

Comparing Last Pass to Alternatives
Some people, after hearing about this phishing campaign, might wonder if they should switch password managers. Let's put this in perspective.
Phishing campaigns target popular services because there are more potential victims. Last Pass is one of the most popular password managers, so it's a natural target. But every password manager is potentially vulnerable to phishing attacks—it's not unique to Last Pass.
Alternatives like Bitwarden, 1 Password, and Dashlane all use similar architectures, and all have their own security considerations. Switching won't eliminate the phishing threat—you'd just face different phishing emails from whoever becomes your new password manager provider.
The real protection against phishing isn't the password manager you choose—it's how carefully you verify emails before interacting with them.
What you should evaluate about your password manager:
- Is it using end-to-end encryption for your vault?
- Does it support hardware security keys for two-factor authentication?
- Does the company publish regular security audits?
- How quickly does the company respond to reported vulnerabilities?
- What's the company's history with security incidents?
Last Pass has had some security issues over the years, which is a legitimate concern. But so have other major password managers. No company with millions of users and years of operation has a perfectly clean security record.
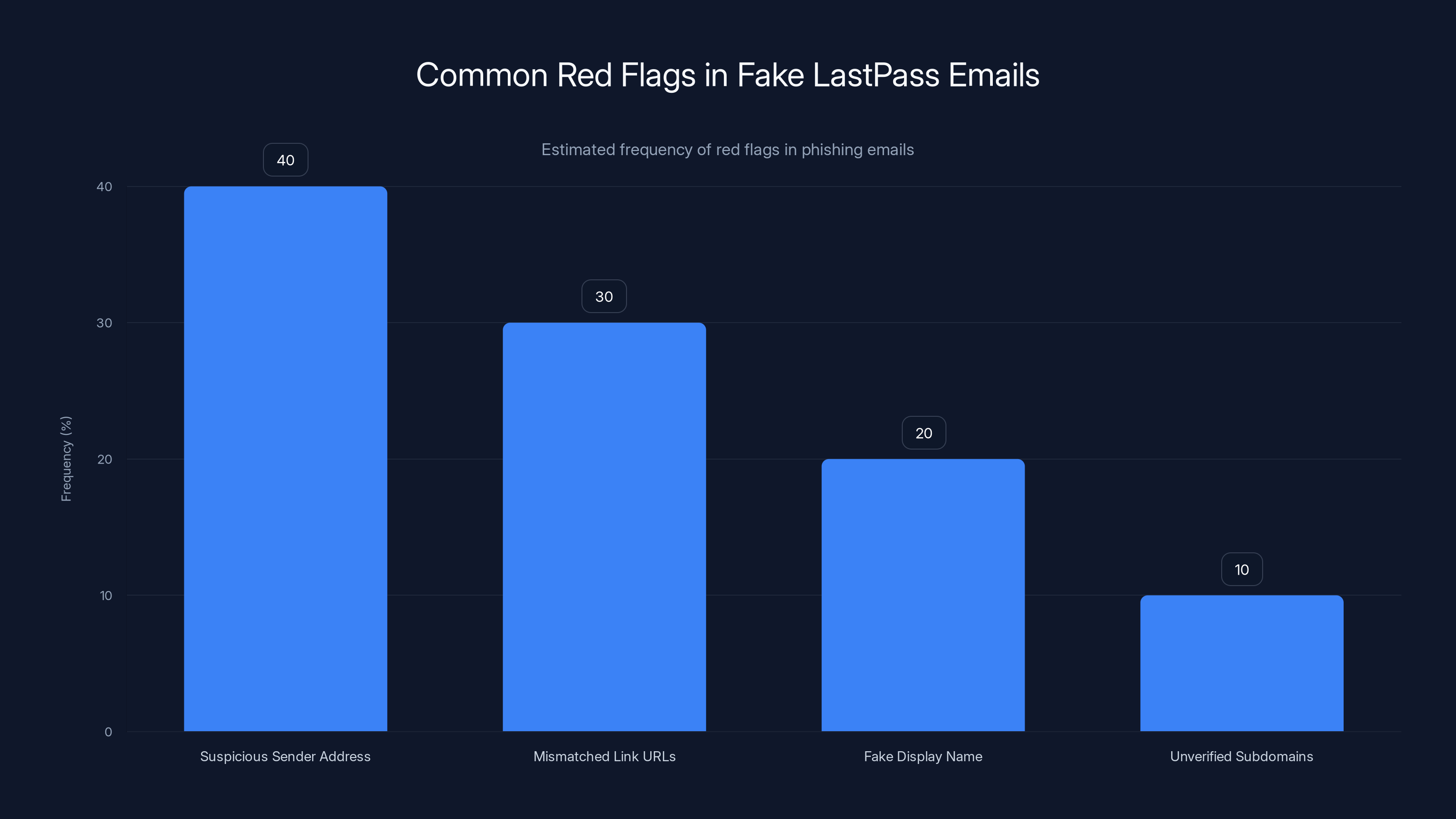
Estimated data shows that suspicious sender addresses are the most common red flag in fake LastPass emails, followed by mismatched link URLs.
Reporting and Response: What Last Pass Is Doing
Last Pass has taken the standard steps in response to this phishing campaign: they've issued a warning, provided guidance to users, and committed to working with third-party partners to take down the malicious domains.
The domains they've identified so far include support@sr 22vegas[.]com, support@lastpass[.]server 8, support@lastpass[.]server 7, and support@lastpass[.]server 3. Last Pass is working to get these domains suspended through the hosting providers and domain registrars.
But here's the reality: taking down the malicious domains doesn't fully stop the campaign. Attackers can register new domains, use different hosting providers, or move to bulletproof hosting services that are resistant to takedown requests. The game of whack-a-mole between attackers and defenders is endless.
Last Pass is also encouraging users to report suspicious emails to abuse@lastpass.com. This helps them identify new variations of the campaign that might slip past their own detection systems.
From a defense perspective, Last Pass could do more to educate users about recognizing phishing attempts. They've issued warnings, which is good, but many users don't read them or don't take them seriously until they've been compromised.

The Bigger Picture: Why Phishing Remains Effective
Let's step back and think about why phishing is such a persistent problem, even in 2025 when we've had decades to develop defenses.
Phishing is effective because it exploits fundamental weaknesses in how humans process information online. We're designed to be social creatures who trust authority figures and respond to urgency. We can't easily verify the identity of someone communicating via email. We get dozens or hundreds of emails per day and can't carefully scrutinize each one.
Meanwhile, attackers have optimized their approach. They use A/B testing to figure out what email subjects get the highest click-through rates. They use machine learning to identify which types of messages are most likely to succeed. They use social engineering research to craft messages that resonate emotionally.
Traditional security measures—firewalls, antivirus software, encryption—don't stop phishing because phishing is fundamentally a social attack, not a technical one. You can have the most secure password manager in the world, but if you voluntarily give an attacker your master password, security technology can't help you.
This is why the defense against phishing ultimately comes down to human behavior and awareness. You need to:
- Verify the sender's identity before trusting their message
- Recognize when language is creating artificial urgency
- Understand that legitimate companies have processes that don't require sensitive credentials
- Know what your trusted services' actual communication patterns look like
- Accept that you might make mistakes and have a recovery plan
No amount of technology can fully eliminate phishing risk. But awareness and careful behavior can reduce your risk significantly.
Best Practices for Email Security
Phishing isn't just a Last Pass problem—it's an email problem. Here are best practices for defending against phishing attempts across all services.
Set Up Email Forwarding Rules
If you know that a service (like Last Pass) only contacts you from specific email addresses or domains, you can set up email rules to automatically sort legitimate messages and flag anything from other addresses. This won't catch all phishing attempts, but it's a good first line of defense.
Use Email Authentication Standards
Email providers can implement authentication standards like SPF (Sender Policy Framework), DKIM (Domain Keys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting and Conformance). These standards help verify that emails actually come from the domains they claim to come from.
As a user, you can't directly implement these, but you can check if your email provider supports them and enable them for any domains you manage.
Enable Advanced Phishing Detection
Most email providers now offer advanced phishing detection that uses machine learning to identify suspicious emails. Gmail's phishing detection catches about 99.9% of phishing and spam emails before they reach your inbox.
Yet some still get through. Check if your email provider has additional security features you can enable.
Be Skeptical of Unexpected Contacts
If you get an email from a service you use, but it's asking you to do something unusual, be suspicious. Legitimate companies have established patterns for how they communicate. If an email breaks that pattern, verify it through an independent channel.
For example, if you get an email from your bank asking you to confirm your account details, don't click the link in the email. Instead, go to the bank's website directly (by typing the URL or using a bookmarked link) and access your account from there. If there really is an issue, you'll see it in your account.
Educate People Around You
Phishing succeeds partly because many people don't understand how these attacks work. If you have family members, friends, or coworkers using password managers or accessing sensitive accounts, teach them about phishing. Awareness is the most powerful defense.
Looking Forward: Phishing in 2025 and Beyond
As we move deeper into 2025, phishing attacks are evolving. AI tools are making it easier for attackers to generate convincing copy, create fake websites, and identify targets. Conversely, defenders are also using AI to detect suspicious emails more effectively.
The arms race continues.
One trend to watch: deepfake technology is improving rapidly. Within a few years, attackers might send video messages claiming to be from your company's CEO or your bank's security team. These will be convincing enough to fool most people. Defense against this level of sophistication requires institutional changes—companies will need to implement strong identity verification systems and change how they communicate with customers.
Another trend: attackers are getting better at identifying high-value targets. Instead of sending 10,000 generic phishing emails, they're researching specific people, learning about their interests and habits, and crafting personalized attacks. This "spearphishing" approach has much higher success rates than mass campaigns.
For now, the defense remains awareness and careful behavior. But that defense is getting weaker as attackers get smarter. At some point, we'll need new technical solutions.

FAQ
What should I do if I accidentally entered my Last Pass master password into a phishing email?
First, don't panic. Immediately go to the official Last Pass website by typing the URL in your browser (or using a bookmark), log in with your current master password, and change your master password to something completely new. This invalidates the password the attacker captured. After changing your password, enable two-factor authentication if you haven't already, and review your vault for any signs of unauthorized access. Monitor your critical accounts (email, banking, cryptocurrency) for suspicious activity over the next few weeks.
How can I tell if an email from Last Pass is legitimate?
Verify the sender's email address by looking at the full email headers, not just the display name. Legitimate Last Pass emails should come from @lastpass.com or verified Last Pass domains. Never trust the display name—attackers can set it to "Last Pass" while the actual email comes from a completely different address. Additionally, Last Pass will never ask for your master password, recovery codes, or authentication factors. If an email requests these, it's definitely a phishing email. When in doubt, go directly to lastpass.com by typing the URL, log in, and check your account settings for any genuine support messages.
Why do phishing campaigns target password managers specifically?
Password managers are high-value targets because they contain access to dozens or hundreds of other accounts. When an attacker compromises a typical email account, they get access to one service and the ability to reset passwords for others. But when they compromise a password manager vault, they potentially gain access to everything the victim has secured there: banking passwords, cryptocurrency wallets, work credentials, and more. This makes password manager accounts exponentially more valuable to attackers, so these services see disproportionate targeting.
Is Last Pass still safe to use after this phishing campaign?
Yes, but with caveats. The phishing campaign is an attack against users, not a vulnerability in Last Pass itself. Attackers are tricking people into voluntarily giving up their master passwords—they're not hacking Last Pass's systems. That said, Last Pass has had its own security incidents in the past, so it's reasonable to evaluate whether it meets your security needs. Any password manager can be targeted by phishing, so switching providers won't eliminate this threat. What matters is choosing a manager with strong encryption, regular security audits, and support for hardware security keys, then using it responsibly.
Can two-factor authentication protect me against phishing?
Two-factor authentication (2FA) provides protection against phishing in some scenarios but not all. If an attacker has your master password but not your 2FA device (like a hardware security key), they won't be able to access your account even with the correct password. However, if the phishing attack specifically targets your 2FA, such as by sending you a fake SMS or by using a credential stealing attack on your authenticator app, then 2FA can be bypassed. Hardware security keys provide the strongest protection because they require physical possession and won't authenticate unless the domain matches where they were registered.
What's the difference between phishing and spearphishing?
Phishing is a mass attack where scammers send thousands of generic emails hoping a small percentage will fall for it. Spearphishing is a targeted attack where scammers research a specific person or organization and craft personalized messages designed to manipulate them. The Last Pass campaign appears to be phishing (mass emails to many users), but more sophisticated attackers will use spearphishing techniques. Spearphishing is harder to defend against because the emails are more convincing and specifically tailored to make the target believe they're legitimate.
If I used the same master password elsewhere, am I in danger?
Yes. If you reused your Last Pass master password on other services and an attacker obtained it through a phishing email, they could attempt to access those other services. This is why password reuse is dangerous and why strong password managers (which encourage unique passwords for each service) are important. If you reused your master password, change it on all services where you used it. Going forward, make sure each service has a unique password—this is one of the core security principles password managers help enforce.
What's the best way to report a phishing email to Last Pass?
Forward the entire email (including headers) to abuse@lastpass.com. Don't just send a summary—include the complete email with all its metadata. The headers contain information about where the email actually came from, which servers it passed through, and other details that help Last Pass and email security teams identify the attack infrastructure. You should also report the phishing email to your email provider (Gmail, Outlook, etc.) as spam or phishing. This helps all of us collectively improve defenses against these campaigns.
Could this phishing campaign indicate a larger breach at Last Pass?
Not necessarily. Phishing campaigns can target users of any popular service. Attackers don't need internal access to Last Pass or breached customer data to run a mass phishing campaign—they just need to know that Last Pass is popular and guess that some percentage of email addresses belong to Last Pass users. That said, if you want to verify whether Last Pass has suffered a breach, check Have I Been Pwned (HIBP), a service that tracks known data breaches. Additionally, Last Pass publishes security updates on their blog, so you can monitor there for official announcements about any incidents.
Conclusion: Staying Safe in an Era of Sophisticated Phishing
The Last Pass phishing campaign of January 2026 is just one example of a broader trend: as the value of digital credentials increases, so does the sophistication of attacks targeting them. Password managers like Last Pass are convenient, but that convenience comes with responsibility.
The email campaign we discussed uses old techniques—artificial urgency, fake sender addresses, convincing design—but it's effective because human psychology hasn't evolved since these tactics were first developed. We still respond to urgency. We still trust authority. We still make mistakes.
The good news is that you have agency. You can reduce your risk significantly through awareness and careful behavior.
Start with the basics: verify sender email addresses, be skeptical of urgent requests for sensitive information, understand that legitimate companies won't ask for your master password. Enable two-factor authentication with hardware security keys if possible. Use strong, unique master passwords.
Beyond personal practices, advocate for better systems. Encourage services you use to implement strong authentication standards. Support companies that invest in user security and education. Report phishing emails to help defenders track emerging threats.
Phishing will continue evolving. New attack vectors will emerge. But the fundamental principle remains: verification defeats deception. Take time to verify before trusting. That single habit will protect you against the vast majority of phishing attempts.
Last Pass itself isn't uniquely vulnerable—password managers generally are well-engineered and secure. The vulnerability is in human behavior, which is actually the hardest thing to secure. But it's also the most important, because no amount of technical security can overcome the decision to voluntarily give an attacker your credentials.
Stay alert. Stay skeptical. Verify before you trust. And if you do get phished, act quickly to contain the damage. These practices will serve you well not just with Last Pass, but with every online account you maintain.
The phishing ecosystem will continue adapting. But so will we. Each phishing email we identify and report helps defenders understand the landscape better. Each person who learns to spot these attacks becomes a node of resistance in a much larger network. Together, even as threats evolve, we make the internet a little bit harder for attackers to exploit.
That's not perfect protection. But it's something. And sometimes, something is enough.
Key Takeaways
- LastPass will never ask for your master password via email, text, or phone—period. Any request for it is a scam.
- Fake phishing emails use spoofed addresses like support@sr22vegas[.]com and support@lastpass[.]server3 to appear legitimate.
- Artificial 24-hour urgency is a classic social engineering tactic designed to make you act before thinking critically.
- If compromised, change your master password immediately, enable 2FA with hardware keys, and update critical account passwords.
- Hardware security keys provide the strongest phishing defense because they verify the domain and won't authenticate to fake sites.
- Phishing remains the #1 attack vector (74% of breaches) because it exploits human psychology, not technical vulnerabilities.
- Password managers are high-value targets because compromising one vault gives access to hundreds of other accounts.
Related Articles
- Most Spoofed Brands in Phishing Scams [2025]
- Supreme Court Hacker Posted Stolen Data on Instagram [2025]
- Massive Phishing Campaign Targets Middle East Officials, Activists, Journalists [2025]
- Google Gemini Calendar Prompt Injection Attack: What You Need to Know [2025]
- UStrive Security Breach: How Mentoring Platform Exposed Student Data [2025]
- 198 iOS Apps Leaking Private Chats & Locations: The AI Slop Security Crisis [2025]



