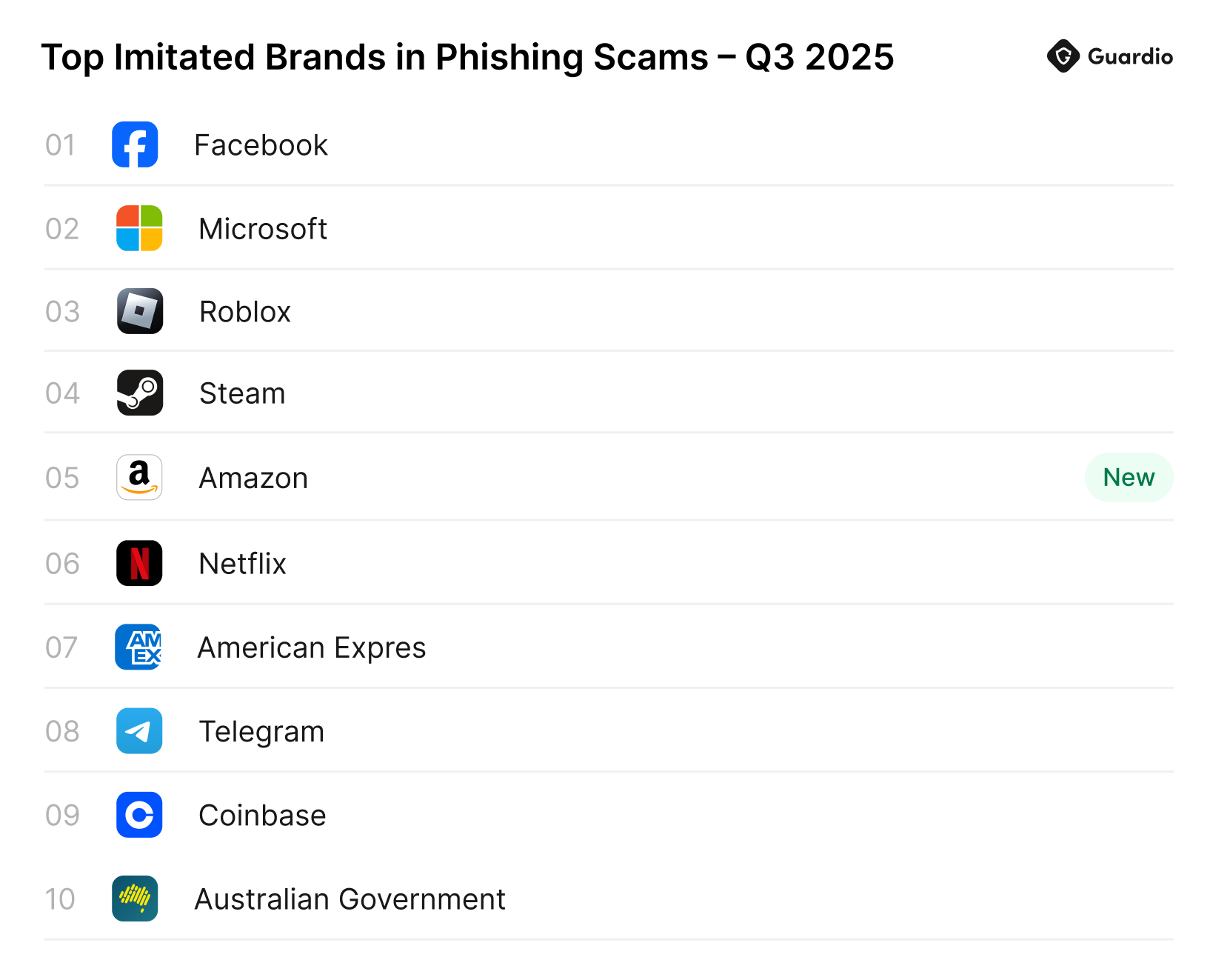
Most Spoofed Brands in Phishing Scams [2025]: The Definitive Guide
You've probably gotten one. That email that looks exactly like it came from Microsoft, asking you to verify your account. The logo's perfect, the formatting's right, and the urgency feels real.
Here's the thing: you weren't picked at random. You were targeted because you're using a service that attackers have figured out how to impersonate better than almost any other brand on the internet.
Phishing isn't some random spray-and-pray attack anymore. It's surgical. It's targeted. And it's working at scale. The latest data shows that certain brands get impersonated over and over again, and there's actually a pretty clear pattern to who the worst offenders are targeting.
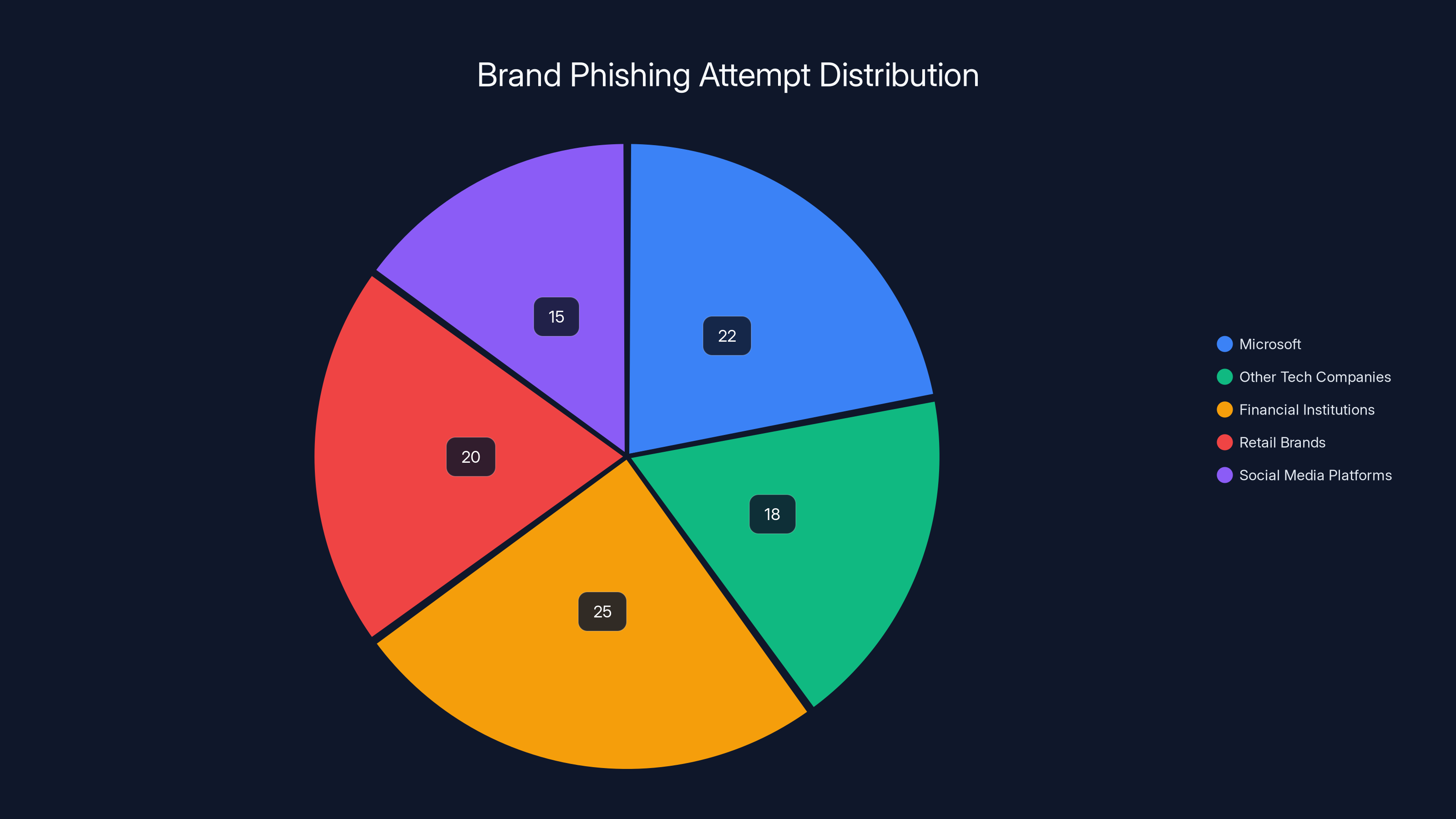
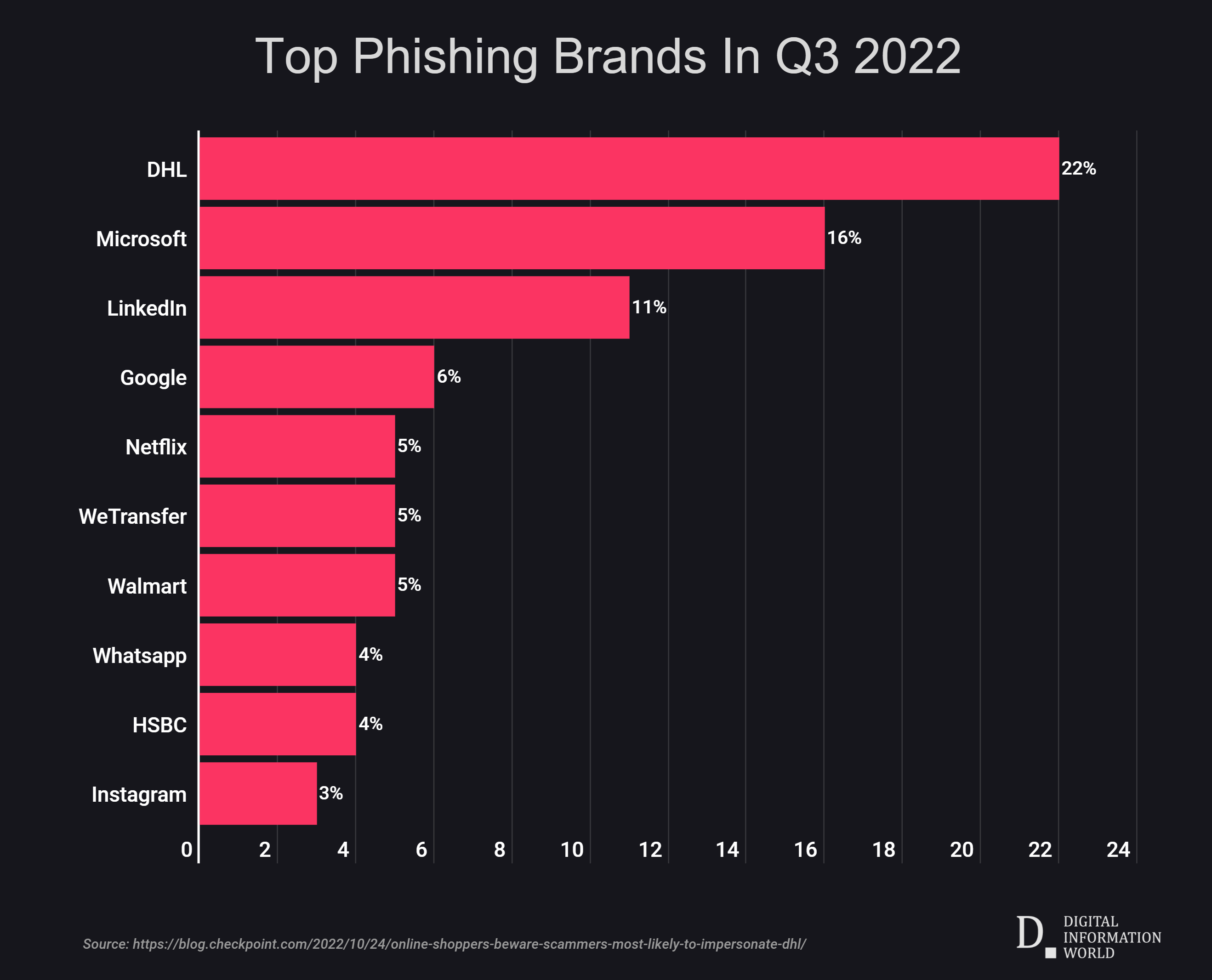
The statistics are sobering. 22% of all brand phishing attempts in the last quarter of 2025 tried to spoof Microsoft. That's not a typo. Nearly one in four. Google follows at 13%, Amazon at 9%, and Apple at 8% according to Check Point Research. But here's what might surprise you: the brand impersonation landscape is shifting, and some of the new players entering the top 10 most-spoofed list tell a different story about how attackers are evolving their tactics.
This isn't just about clicking a bad link. Identity theft via phishing has become the single biggest attack surface for both consumer fraud and enterprise breaches. When an attacker steals your credentials for a Microsoft account, they're not just getting access to your email. They're getting access to your entire digital life: your documents, your files, your backup codes, potentially your work systems if you use your personal account anywhere.
In this guide, we're going to break down exactly which brands are being impersonated the most, why attackers are targeting them, what new trends are emerging, and most importantly, how you can actually protect yourself against these increasingly sophisticated attacks.
TL; DR
- Microsoft dominates phishing targets with 22% of all brand impersonation attempts, followed by Google (13%) and Amazon (9%) as reported by TechRadar.
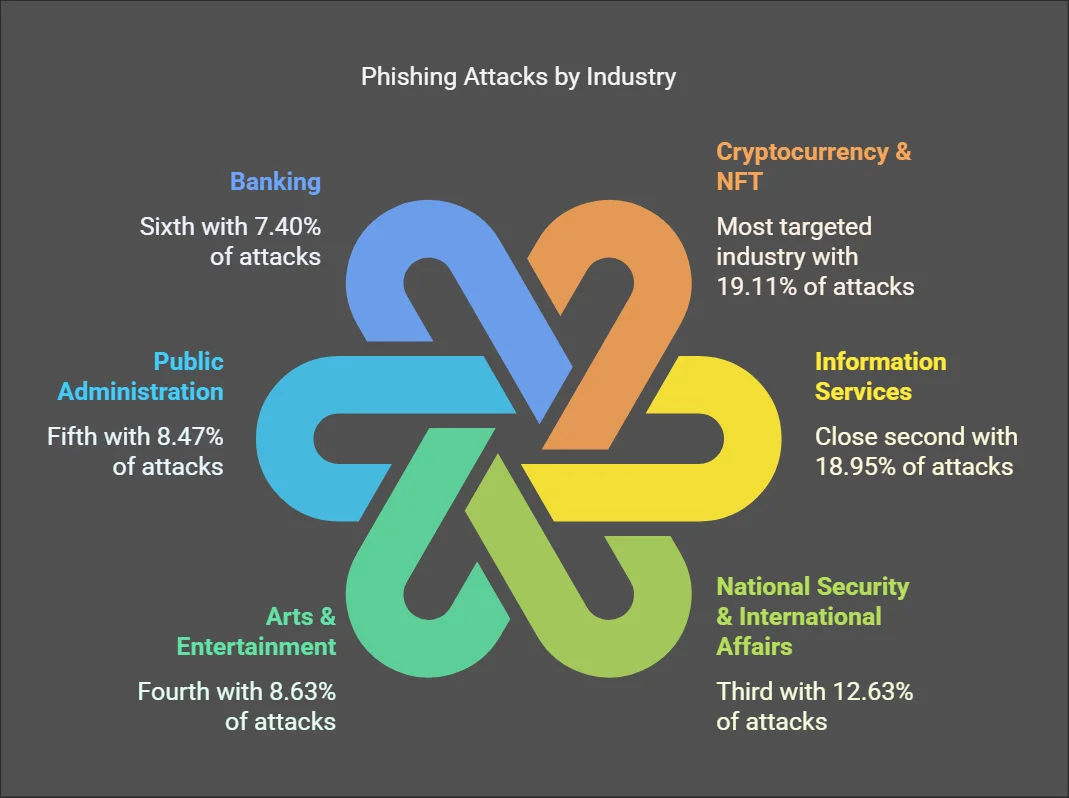
- Tech firms account for 90%+ of top 10 most-spoofed brands, with DHL as the only non-tech company in the rankings according to KnowBe4.
- Seasonal patterns matter: Amazon impersonations spike during Q4 holiday shopping when purchase volumes are highest.
- Credentials are the goal: Attackers prioritize brands that control identity and authentication, making stolen passwords incredibly valuable.
- AI is making phishing more convincing: Modern attacks now use deepfake emails, personalized content, and near-perfect brand mimicry as noted by ESET.
- Basic hygiene still works: Two-factor authentication, official website navigation (not via links), and skepticism of urgency remain your best defenses.
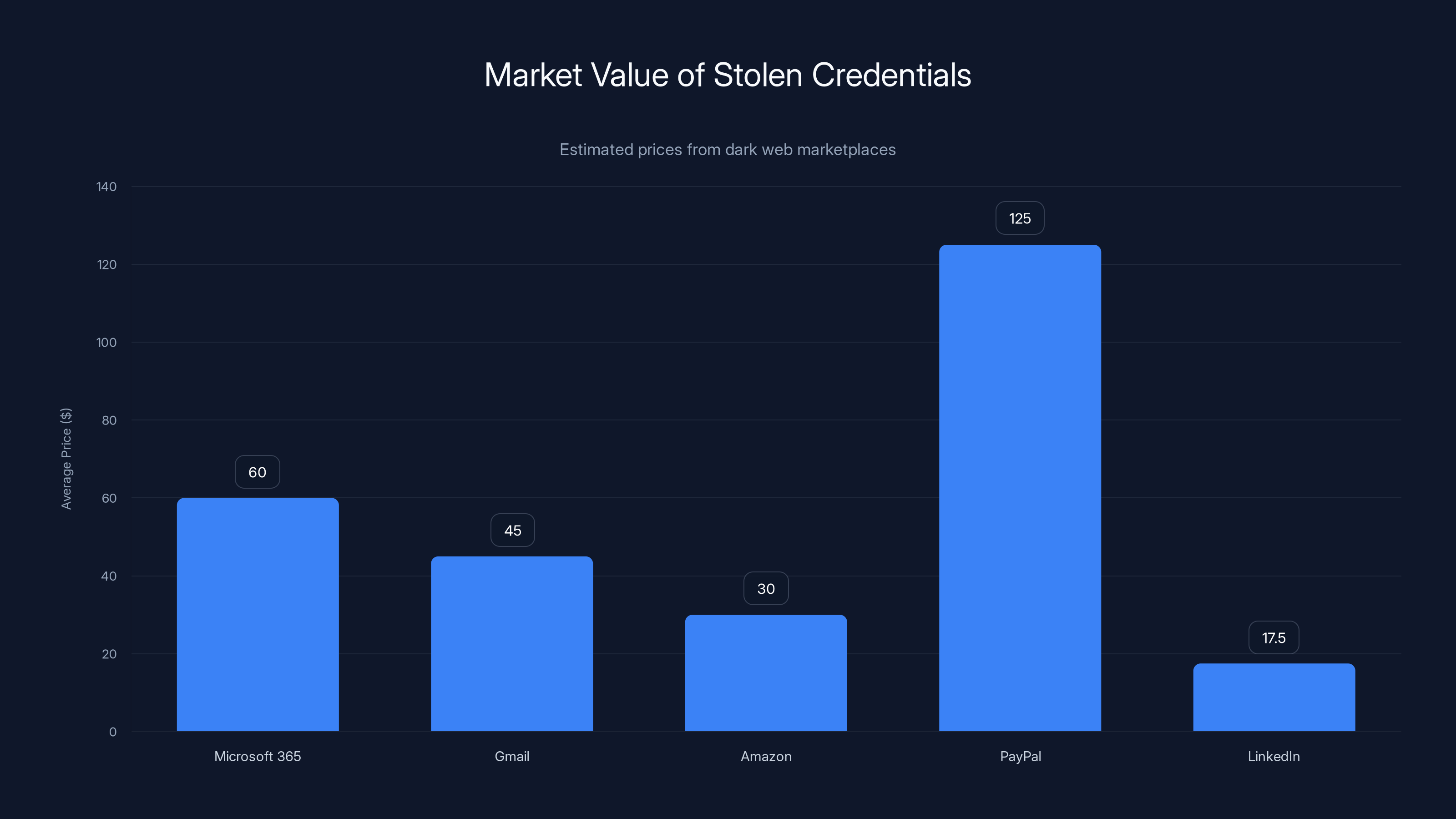
Stolen credentials have significant market value, with PayPal accounts fetching the highest average price due to linked banking information. Estimated data based on reported dark web prices.
Why Microsoft Dominates the Phishing Charts
Microsoft isn't just the most-spoofed brand by accident. There's a specific reason it sits at the top of the list with 22% of all brand phishing attempts, and understanding that reason is key to understanding why you might be targeted.
Think about what Microsoft owns. It's not just an email provider. Microsoft is identity. If you have a Windows account, you probably have a Microsoft account. If you use Office, you have a Microsoft account. If you use One Drive, Teams, Outlook, Xbox, or literally dozens of other services, you're authenticated through Microsoft infrastructure.
When an attacker steals a Microsoft account credential, they're not just getting your email. They're potentially getting access to:
- All Microsoft 365 applications (Word, Excel, Power Point, Access)
- One Drive cloud storage with potentially years of personal documents
- Backup and recovery codes for your other accounts
- Authentication history showing what other services you've linked
- Payment information associated with Game Pass, Office subscriptions, or Azure credits
- Two-factor authentication recovery options (phone numbers, backup emails)
The economics of credential theft work heavily in the attacker's favor. A stolen Microsoft credential is worth money. These accounts get sold on dark web marketplaces, traded between criminal groups, or used immediately for corporate espionage, ransomware deployment, or mass mailing list harvesting.
What makes Microsoft particularly vulnerable to phishing isn't a weakness in their security. It's their scale. Over 400 million people use Microsoft 365 according to Microsoft. That's a massive target pool. An attacker can send phishing emails to 100,000 random email addresses claiming to be from Microsoft, and statistically, a significant percentage will have Microsoft accounts. Even if the click rate is only 2-3%, that's thousands of people.
Microsoft also has complex, multi-layered authentication systems that make the attack surface larger. They have multiple login pages (live.com, account.microsoft.com, portal.office.com), multiple services that require re-authentication, and various recovery flows. Each of these is an opportunity for an attacker to build a convincing fake.
The reason Microsoft phishing works so well is also about trust and urgency. When you get an email saying "Unusual activity detected on your Microsoft account," you actually feel something. Your heart rate goes up a little. You think about the data you have backed up. You might not stop to check whether the sender address is actually from Microsoft because you're in a state of mild panic.
Attackers have learned to exploit this psychological pressure. They'll craft messages like "Confirm your identity immediately" or "Your account will be suspended in 24 hours" not because there's any actual threat, but because urgency bypasses careful analysis. When you're rushing, you make mistakes.
The Google and Amazon Close Second
Google holds the number two position at 13% of brand phishing attempts, and there's a different set of reasons why Google is such a valuable target compared to Microsoft.
Google's vulnerability isn't about complexity. It's about ubiquity and integration. A Google account is often the master key to someone's digital life. Here's why:
Gmail is still the world's largest email provider with over 1.8 billion active users. That's your primary inbound communication channel. Gain control of someone's Gmail, and you can:
- Reset passwords for any service using "Forgot password? Send reset link to your email"
- Access Google Drive, which often contains sensitive personal documents
- Retrieve two-factor authentication codes if they're sent via email
- Potentially access You Tube watch history and linked accounts
- See which services are connected to your Google account (which tells attackers what else to target)
Google phishing attacks often use two vectors simultaneously. First, they get you to a fake Gmail login page and capture your password. Then, they use that password to attempt access to your actual Google account, which often triggers a "new location login detected" notification. But here's the trick: they've just sent you a notification saying that they're trying to log in from somewhere, and they ask you to confirm or deny it.
Most people, seeing this notification, either approve it (thinking it's them on a different device) or try to change their password (which requires them to go through the recovery flow controlled by the attacker).
Amazon at 9% follows a different pattern. Amazon phishing spikes dramatically during certain times of year, particularly during Q4 holiday shopping when transaction volumes are highest. Here's why this matters:
During holiday shopping, people are distracted and making rapid purchasing decisions. An email claiming to be from Amazon saying "Your package failed to deliver, update your payment information" gets a much higher click rate in November and December than it would in March. Attackers know this, so they time their campaigns accordingly.
Amazon phishing is particularly dangerous because it often captures not just login credentials, but also payment information. A fake Amazon login page might ask you to "verify your payment method" before allowing you to track your package. You enter your credit card information, thinking it's legitimate, and now attackers have both your account credentials and your payment data.
What's interesting about Google and Amazon compared to Microsoft is that the attacks are often more sophisticated because they're more specialized. Microsoft phishing tends to be broad and generic ("verify your account"), while Google and Amazon attacks are more personalized ("We couldn't deliver your package", "Unusual activity in your Google Photos").
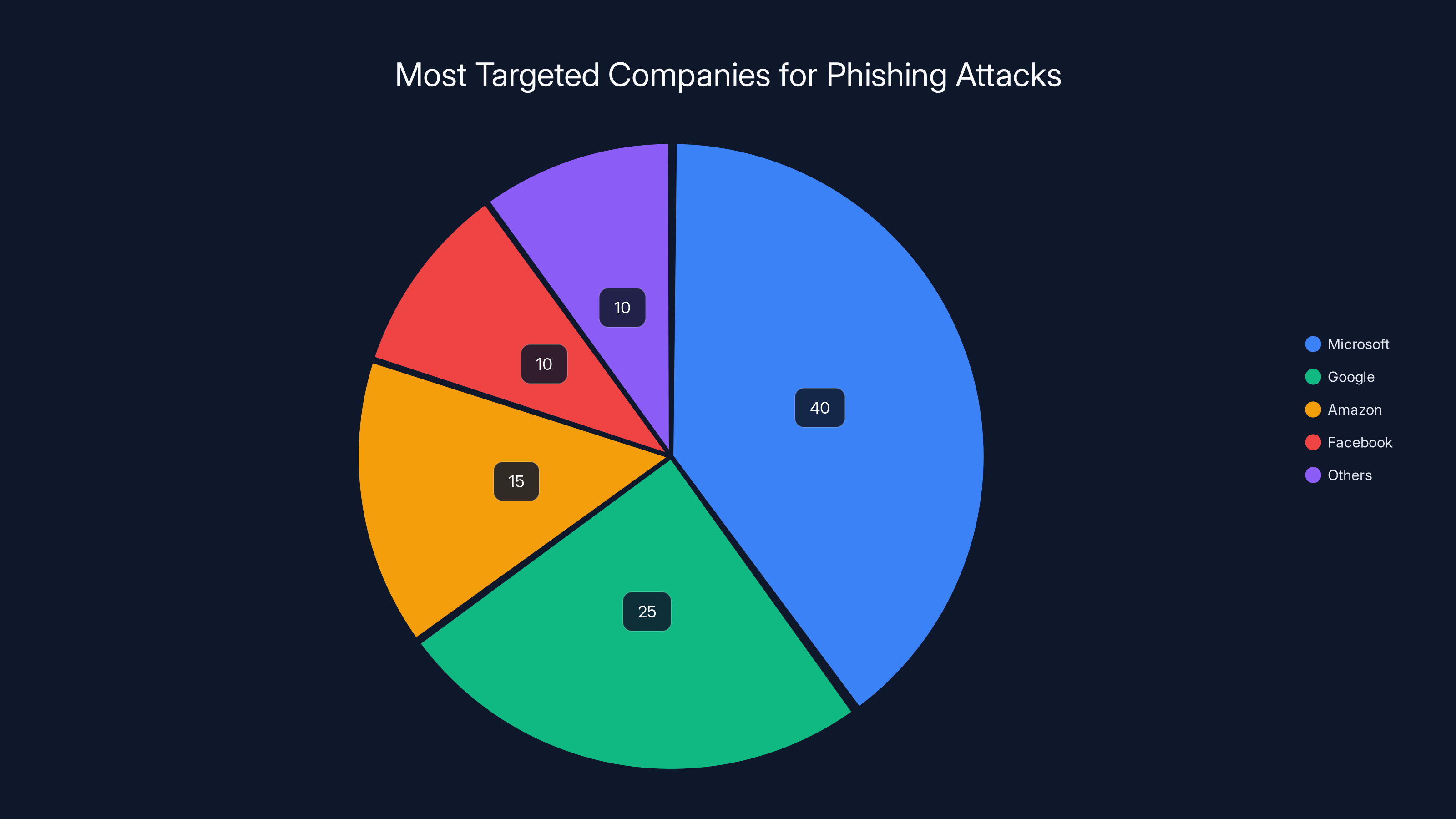
Microsoft is the most targeted company for phishing attacks, accounting for an estimated 40% of such incidents. This is due to its widespread use and the high value of its credentials on the dark web. (Estimated data)
The Unexpected Players: Why DHL Stands Out
Here's where the surprise comes in. DHL is the only non-technology company in the top 10 most-spoofed brands, sitting at just 1% of attacks. But its presence in the rankings tells you something important about how attackers think.
DHL isn't an identity provider. DHL doesn't authenticate you into systems. DHL doesn't store your files or manage your digital life. So why would attackers bother spoofing DHL?
The answer is logistics and financial urgency. When you order something expensive online, you need it to arrive. If you get an email from DHL saying "Package delivery failed, click here to reschedule," you're suddenly motivated to act quickly. You don't want your expensive purchase sitting in a warehouse somewhere.
DHL phishing attacks work not by stealing identity credentials, but by stealing payment information or redirecting shipments. Some attacks try to get you to pay a "customs fee" or "redelivery charge." Others direct you to a fake tracking page that asks you to update your address and payment method to "ensure delivery."
The presence of DHL in the top 10, even at just 1%, suggests a shift in attacker strategy. Historically, phishing was almost entirely about identity theft. But as companies have gotten better at detecting credential compromise, attackers are diversifying. They're now also targeting logistics providers, payment processors, and financial services.
The Apple and Meta Story: Consumer Targets vs. Enterprise Targets
Apple sits at 8% of brand phishing attempts, and Meta at 3%. These two companies represent an interesting divergence in how different attackers operate.
Apple phishing is often consumer-focused and device-oriented. Attackers spoof Apple ID login pages, try to get you to "verify your payment method," or claim your account has been locked due to suspicious activity. The goal is usually financial: they want to either steal your payment information or lock you out of your i Cloud account (which then becomes leverage for extortion).
What's particularly insidious about Apple phishing is how integrated Apple services are with your device. If someone gains control of your Apple ID, they can potentially:
- Remotely lock your Mac or i Phone through Find My
- Access your i Cloud backup, which contains photos, messages, and contacts
- Access your Keychain, which stores passwords and sensitive information
- Drain Apple Pay wallets associated with your account
- Use Apple Business Manager to alter device management settings if you have an enterprise account
Meta phishing is lower on the list partly because Meta's business model is different. Meta doesn't authenticate you into anything critical in the way Microsoft does. Your Facebook account is valuable for social engineering and harassment, but it's not the master key to your digital life.
However, Meta phishing is becoming more sophisticated. Attackers now create fake Meta Business Manager login pages targeting small business owners. Business Manager accounts often have access to Facebook Ads accounts, Instagram accounts, and payment information for ad spending. A compromised Business Manager account doesn't just hurt the owner; it can be used to run scams and phishing campaigns directly from their legitimate business pages.

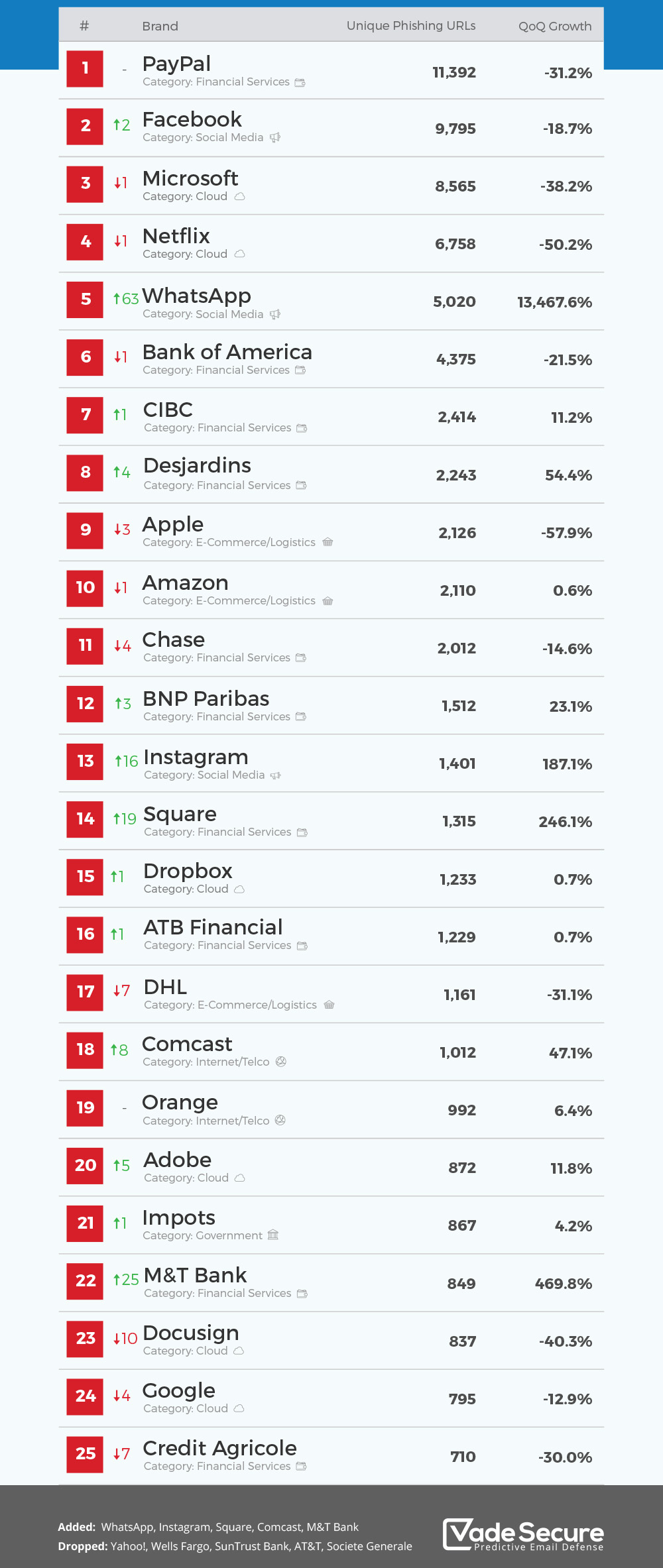
Pay Pal, Adobe, Booking, and Linked In: The Mid-Tier Targets
The tier of companies sitting at 2%, 2%, 2%, and 1% respectively—Pay Pal, Adobe, Booking, and Linked In—tells a different story. These aren't the most targeted brands, but their presence in the rankings reveals how attackers have specialized niches.
Pay Pal at 2% is targeted specifically for financial reasons. Pay Pal isn't just an email account; it's a payment processor connected to bank accounts and credit cards. A compromised Pay Pal account might have:
- Linked bank accounts
- Saved credit card information
- Transaction history showing spending patterns
- Connected accounts to e Bay and other services
- Access to Pay Pal's dispute system
Pay Pal phishing attacks often claim suspicious activity on your account or ask you to update your billing information. They're highly effective because Pay Pal actually does have legitimate security alerts, so it's easier to make fake ones seem real.
Adobe at 2% is targeted for two reasons. First, Adobe accounts often have payment information stored for Creative Cloud subscriptions. Second, Adobe applications like Acrobat Reader are so universally used that attackers can sometimes get you to open a fake Adobe login inside a legitimate-looking PDF document.
Adobe phishing is particularly dangerous in enterprise environments because Adobe software is often used by designers, marketers, and creative professionals who might have access to valuable company files and intellectual property.
Booking.com at 2% is seasonal, much like Amazon. When people are booking vacations, they're in a rush and not paying close attention to details. Fake emails claiming your reservation is at risk or you need to update your payment method get much higher click rates during travel season.
Linked In at 1% targets a professional audience. Linked In phishing attacks often impersonate recruiters or claim someone wants to connect with you professionally. Once you click the link and log in, attackers have access to your professional network, your work history, and potentially your real-time location and professional email address (which they can then use to target you at your employer).
Linked In is also valuable for social engineering. If an attacker compromises your Linked In account, they can send connection requests to everyone in your network and run scams (fake job offers, investment opportunities, etc.) while appearing to come from you.
![Most Spoofed Brands in Phishing Scams [2025]](https://c3wkfomnkm9nz5lc.public.blob.vercel-storage.com/charts/chart-1768844241356-euzbpnle1u.png)
Microsoft leads as the most spoofed brand in phishing scams, accounting for 22% of attempts, followed by Google at 13%. Estimated data shows a significant portion of attempts targeting other brands.
The Seasonal Patterns and Attack Timing
One of the most important things to understand about phishing is that it's not random. Attackers aren't sending out the same attacks year-round. They're timing their campaigns to match behavior patterns, shopping seasons, and organizational cycles.
The data shows clear seasonal trends:
Q4 (October-December): Amazon and Booking phishing spikes dramatically. People are shopping for the holidays, booking travel for family visits, and generally making high-value purchases. They're also distracted and in a rush.
Q1 (January-March): Microsoft and Google phishing increases. This is when organizations are evaluating their security, implementing new policies, and sending out compliance training. Phishing emails claiming to be from IT departments asking to "verify credentials" or "re-authenticate in new system" get better click rates.
April-June: Tax season in North America means phishing targeting financial services and tax software spike. Attackers also target Linked In more heavily as hiring season picks up and recruiters are more active.
July-September: Back-to-school season means Apple, Microsoft (for school accounts), and Google phishing increases. Also, many companies' fiscal years reset in Q3, leading to reorganizations and potential security awareness gaps.
Why does this matter? Because the timing tells you when you should be most paranoid. During holiday shopping season, be extra skeptical of shipping notifications. During tax season, be extra careful about tax-related emails. During back-to-school season, check that educational logins are legitimate.
Attackers study these patterns. They use data science and AI to predict which types of emails will get the highest click rates, and they time their campaigns accordingly. They might send out 1 million phishing emails during Black Friday knowing that 2-3% will click (20,000-30,000 people), but they might send out only 100,000 emails during February when shopping traffic is lower.

How AI Is Making Phishing Exponentially More Dangerous
Phishing in 2025 isn't what it was in 2015. Back then, phishing emails were often obviously fake. The grammar was poor, the logos were slightly off, the sender address didn't quite match.
Now? AI has completely changed the game.
Large language models can now generate phishing emails that are indistinguishable from legitimate company communications. An AI-written email claiming to be from Microsoft about unusual account activity is grammatically perfect, uses proper terminology, includes the right kind of urgency and detail, and generally looks more professional than many real company emails.
But it gets worse. Modern phishing attacks now combine several AI-powered techniques:
Deepfake and synthetic media: Attackers can now create convincing but fake screenshots or even short video clips that show your supposed account activity. A video of "your" login history from "unusual" locations is incredibly persuasive, even though it's completely synthetic.
Personalization at scale: AI can analyze your social media profiles, job history, previous data breaches, and behavioral patterns to create hyper-personalized phishing emails. Instead of a generic "verify your account," you might get something like "John, we noticed your Twitter account accessed your Google Drive yesterday from an unfamiliar location. Please verify this wasn't you."
This is targeted, it mentions specific services you actually use, and it uses your real name. Your brain recognizes these details and thinks the email must be legitimate.
Adaptive response: Some phishing attacks now use AI to respond to your actions. If you click a link and get skeptical, seeing suspicious elements, the AI might adapt the page in real-time or serve you a different landing page. If you start to type a skeptical question, some advanced systems might even respond with answers that seem to confirm legitimacy.
The most dangerous aspect of AI-powered phishing is that it eliminates the traditional defense of "look for obvious errors." When phishing emails are grammatically perfect, contextually appropriate, and visually authentic, the only remaining defense is user behavior: not clicking suspicious links, verifying independently, and using multi-factor authentication.
The Role of Stolen Data and Past Breaches
One reason certain brands are more heavily targeted is because attackers have massive datasets of stolen credentials from past breaches. When you include a real username or email address in a phishing email, the click rate goes way up.
Here's how this works in practice:
In 2023, a major data breach exposed 100 million email addresses and associated passwords. Those credentials are now in criminal databases. An attacker doesn't need to guess your email address or try to convince you blind. They can send you an email that mentions your actual email address, your first name, and potentially even references to actual passwords you've used (without your current password, which hopefully is different).
This is sometimes called password-stuffing phishing. They're essentially saying "We have information about you, and we're using it to prove we're legitimate." The presence of that personal information makes you more likely to trust the message.
Microsoft, Google, and Amazon are the most heavily targeted brands partly because attackers have the most stolen credentials for these services from past breaches. There are massive credential databases circulating on dark web forums containing millions of real Microsoft accounts that have been compromised at some point.
When an attacker sends phishing emails trying to spoof Microsoft, they're often not trying to get your password blind. They're trying to catch people who've already had their credentials compromised elsewhere and are using the same password. When you click the link and log in, they're attempting password-stuffing attacks against your real Microsoft account.

Microsoft leads with 22% of brand phishing attempts due to its wide range of services and large user base. Estimated data.
Credentials as the New Currency
There's a fundamental economic reality driving the focus on these specific brands: stolen credentials are a commodity with real, measurable market value.
On dark web marketplaces, you can literally buy accounts. The pricing structure is remarkably public:
- A compromised Microsoft 365 account with One Drive data might sell for $20-100 depending on how much data is in the account
- A Gmail account with linked payment information might sell for $15-75
- An Amazon account with payment methods might go for $10-50
- A Pay Pal account with linked banking might fetch $50-200
- A Linked In account with a large professional network might sell for $5-30
These aren't theoretical prices. These are actual transactions happening on real marketplaces. The price variations depend on factors like:
- Account age (older accounts with more history are more valuable)
- Data volume (accounts with lots of backed-up data are worth more)
- Financial connections (accounts linked to payment methods or bank accounts are premium)
- Professional value (Linked In accounts with large networks or in specific industries are more valuable)
- Access level (administrator or business accounts are worth significantly more)
When an attacker successfully phishes Microsoft credentials at scale, they're not stealing from individuals for fun. They're engaging in a business transaction. If they get 1,000 valid credentials and sell them for an average of
This is why the attack concentrates on identity providers like Microsoft and Google. These accounts are the master key to someone's digital life. A stolen Microsoft credential is valuable because it potentially gives access to email, documents, backup codes, and recovery options for other accounts.
The economics of phishing have shifted from individual targeted attacks to mass production and sale of credentials. That's why the same brands keep appearing at the top of the list: they're not just being targeted once, they're being targeted continuously by different criminal groups all trying to accumulate credentials to sell.
Enterprise vs. Consumer: Different Threats, Same Brands
It's important to understand that phishing targets operate on two levels: consumer phishing and enterprise phishing. The same brands appear in both categories, but the attacks work differently.
Consumer-level phishing (attacking you as an individual) aims for:
- Personal email accounts and cloud storage
- Payment information and financial access
- Identity theft
- Account takeover and potential extortion
- Access to accounts of professional value (Linked In, Git Hub, etc.)
Enterprise-level phishing (attacking you as an employee) aims for:
- Company email and network access
- Corporate cloud storage and intellectual property
- VPN credentials
- Administrative access to systems
- Ransomware deployment
- Lateral movement within corporate networks
The same Microsoft account can be valuable for both purposes. As a consumer, your Microsoft account might give someone access to your personal files and emails. As an enterprise employee, your Microsoft account might give someone access to your company's entire file structure, email systems, and potentially internal tools.
This is why employee security training is so critical in companies. An employee clicking a phishing link isn't just compromising their personal account; they're potentially compromising the entire organization. That's why organizations focus training on Microsoft, Google, and sometimes Slack (which has become increasingly important for enterprise phishing as more companies use it).
The Shift Beyond Identity: Financial and Logistics Targets
While identity providers dominate the list, there's an emerging trend of attackers targeting companies that handle financial transactions and logistics.
DHL's presence on the list, as we discussed, signals a broader shift. Attackers are realizing that stealing financial information directly can be just as valuable as stealing credentials. An email claiming your payment failed is sometimes more effective than an email asking you to verify your account.
This has led to increased phishing targeting:
- Payment processors (Pay Pal, Stripe, Square)
- Logistics companies (DHL, Fed Ex, UPS)
- Financial institutions (though these are harder to impersonate due to banking regulations)
- E-commerce platforms (Etsy, e Bay, Amazon)
These attacks often work because they create a specific, contextual urgency. You're expecting a package, so an email about delivery problems seems real. You're expecting to receive a payment, so a email about a failed transaction seems real.
The convergence of logistics and consumer targeting has also led to a rise in multi-stage attacks. The first email might be generic phishing to harvest credentials. Once someone's logged in and the attacker has access to their inbox, they can look for actual package notifications, payment notifications, or other context-specific emails. Then they can send follow-up phishing attacks that are perfectly contextualized based on that person's actual activities.
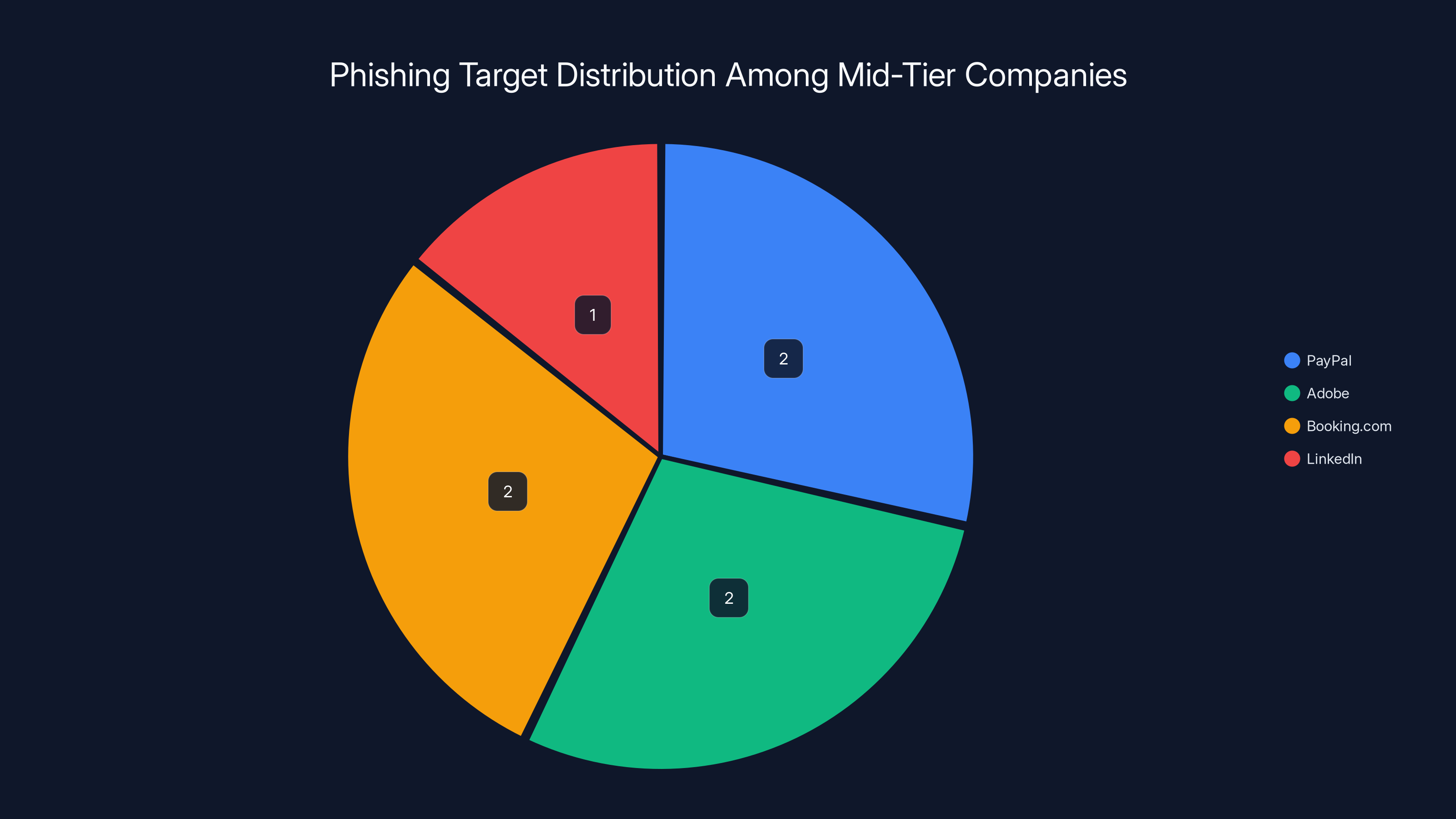
PayPal, Adobe, and Booking.com each account for 2% of phishing targets, while LinkedIn accounts for 1%. This distribution highlights the specialized niches attackers focus on, with financial and professional platforms being key targets.
Regional Variations and Language-Specific Phishing
One detail from recent data is worth highlighting: phishing isn't monolithic. Different regions get targeted differently, and attackers often customize their campaigns to language and cultural context.
For example, Check Point researchers observed a Spanish-focused Facebook phishing campaign in Q4 2025 targeting specifically Spanish-speaking users. Rather than generic phishing, the attacks were personalized to look like Spanish-language Facebook notifications asking for email, phone number, and password verification.
This is important because it shows that phishing is becoming increasingly localized and contextual. An attacker doesn't just send the same email to everyone. They segment their targets by language, region, and cultural context, then customize the message.
This creates a particular vulnerability in non-English speaking communities, where:
- Awareness campaigns are often less prevalent
- Language-specific phishing is more convincing (it's harder to notice subtle errors if you're not a native speaker of the language being used)
- Scam infrastructure might be less mature (fewer takedown efforts, fewer reporting mechanisms)
What's particularly insidious is that attackers will sometimes recruit local speakers to craft messages that are culturally appropriate and linguistically perfect. A Spanish-language Facebook phishing email crafted by a native Spanish speaker and a non-native English speaker are likely to have very different click rates.

The Role of Fake Recovery Pages and Account Recovery Flows
One specific attack pattern that's becoming increasingly sophisticated is the fake account recovery flow.
Researchers observed a specific phishing campaign where attackers created a fake domain that perfectly mimicked Netflix's official account recovery page. Here's what made it particularly dangerous:
- Users received an email claiming unusual activity on their Netflix account
- Clicking the link took them to a page that looked identical to Netflix's official password recovery page
- Users entered their current password (to "verify their identity")
- The page asked for additional verification, requesting their email address or phone number
- Then it asked to reset their password, guiding them through the recovery flow
The attack was so well-designed that even security-conscious users might fall for it because the flow was exactly what they expected to see. They were going through the legitimate recovery process, just on an attacker-controlled page.
This type of attack is particularly effective against:
- Streaming services (Netflix, Disney+, HBO Max)
- Banking services (where recovery flows have become very sophisticated)
- Cloud storage providers (Google Drive, One Drive)
- Email providers (especially recovery flows after account lockouts)
The psychology is subtle but powerful. Users expect the legitimate recovery flow to look exactly like this. When they see a page asking for their password, their email, and a new password, their brain confirms it as legitimate because it matches the pattern they expect.
Attackers now deliberately study the real recovery flows of major services and create pixel-perfect replicas. Some even go so far as to purchase expired domain names that are similar to the real service (like netflix-account-recovery.com) to make the URL seem more legitimate.
Roblox and Gaming Platform Phishing: An Emerging Trend
One specific attack observed in Q4 2025 reveals an emerging target: gaming platforms.
Researchers found a sophisticated phishing campaign targeting Roblox users. The attack created a fake game page (a clicker game or some simple browser game) and directed Roblox users to it. Once they tried to play, they got a prompt saying "You must be logged in to Robux." This prompted them to enter their Roblox credentials.
Why target Roblox specifically?
- Roblox users are increasingly young, and younger users are less likely to recognize phishing
- Roblox accounts often have real-money spending connected to them (Robux is a virtual currency you can buy with real money)
- Roblox credentials can be valuable for account takeover, as compromised accounts can be used to scam other players or manipulate games
- Many Roblox users reuse passwords, so credentials stolen from Roblox might work on their email, Discord, or other services
This pattern suggests that attackers are increasingly targeting younger user bases and gaming platforms, recognizing that these users might be less aware of phishing risks but often have real financial value attached to their accounts.
The emergence of gaming platform phishing as a distinct category also signals something broader: phishing is becoming vertically specialized. Rather than broad, generic attacks against everyone with a Microsoft account, attackers are increasingly creating specialized campaigns for specific user bases.

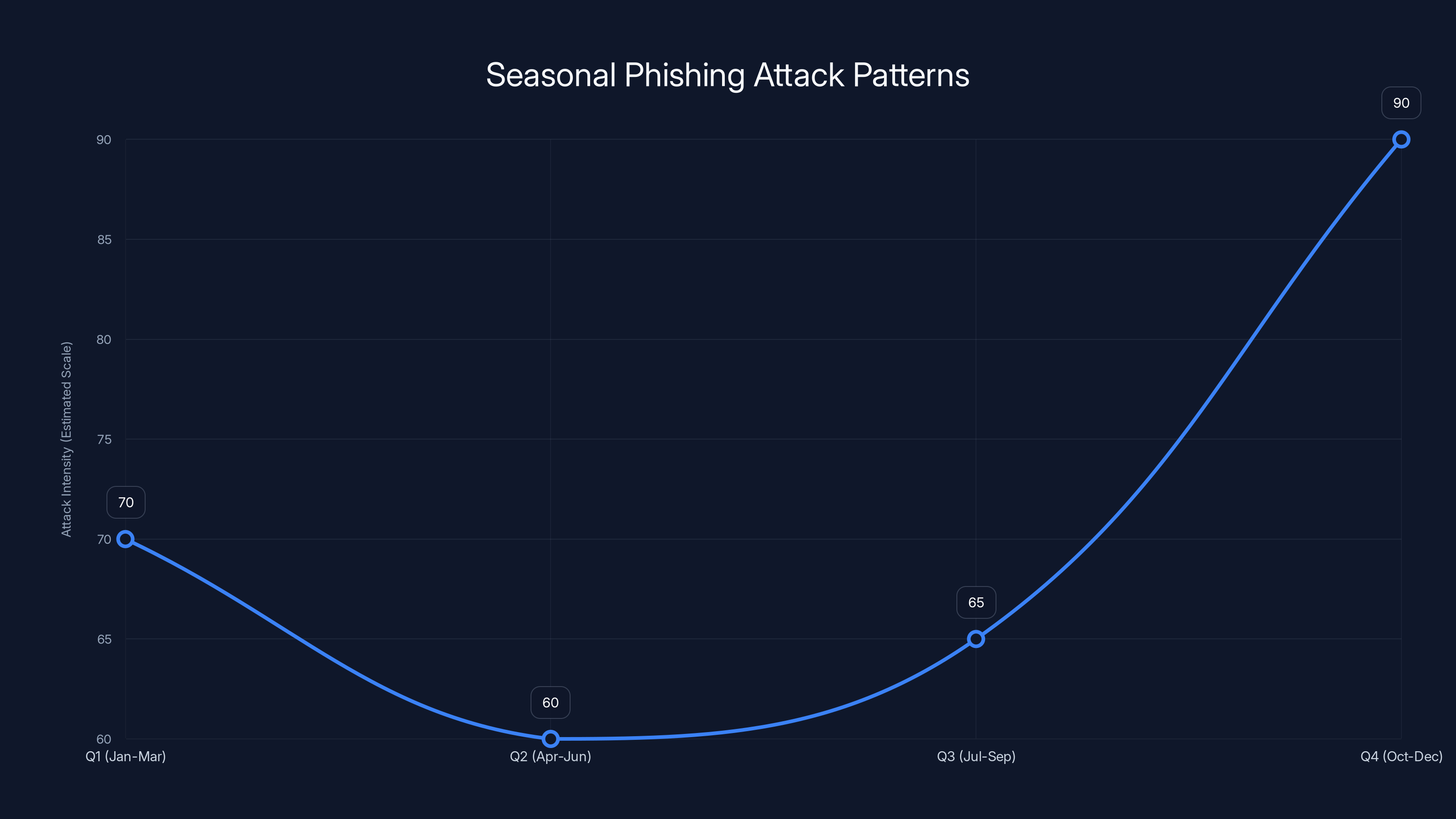
Phishing attacks peak in Q4 due to holiday shopping and travel, while Q1 sees a rise in attacks targeting organizational security changes. Estimated data based on typical seasonal trends.
How Attackers Choose Which Fake Domains to Register
One technical aspect that's worth understanding is how phishing campaigns create fake websites. The domain name is often the dead giveaway, but attackers have become increasingly sophisticated about domain selection.
Common strategies include:
Typosquatting: Registering domains similar to legitimate ones, like:
microsft.com(missing an 'o')amazn.com(missing an 'o')goog 1e.com(using '1' instead of 'l')
Adding trustworthy suffixes:
verify-microsoft-account.compaypal-security.comamazon-account-services.com
Using subdomains of compromised legitimate sites:
- An attacker might compromise a small business website and create
microsoft.authentic-business.comto make it seem like a legitimate subdomain
Registering domains that match what users expect to see:
- When you're in a panicked state (your account might be compromised!), you're not carefully examining URLs. You might see
account-microsoft.secure.comand your brain recognizes the pattern without carefully checking it's legitimate.
Attackers often use artificial urgency and emotional triggers to make you not carefully examine the URL. By the time you realize something's wrong, you've already entered your password.
Why Multiple Brands in a Single Campaign Matter
One sophisticated attack pattern is using multiple brand impersonations in sequence. Here's how it works:
You might get an email claiming to be from Amazon about a package delivery problem. You click it (or if you're cautious, you go to Amazon.com directly). But while you're trying to track your package, you get another notification saying your Amazon account requires additional verification.
This second notification actually impersonates Google (your email provider), asking you to re-authenticate your email because unusual activity was detected. You log in to Google, and your credentials are captured. Then you get directed back to Amazon to complete the package tracking process.
You're now compromised twice over (Amazon credentials captured from the first page, Google credentials captured from the second), and you might not even realize it because the entire experience felt seamless and legitimate.
This multi-brand attack vector works because:
- It uses the context of a real problem (your package)
- It chains the experience across multiple trusted companies
- Each step feels individually legitimate
- The attacker is harvesting credentials from multiple accounts
- Users often don't realize they've been compromised because everything appeared to work as expected
It's becoming increasingly common for sophisticated phishing campaigns to target multiple brands in a single attack chain, maximizing the value of credentials stolen and increasing the likelihood that at least one part of the attack succeeds.
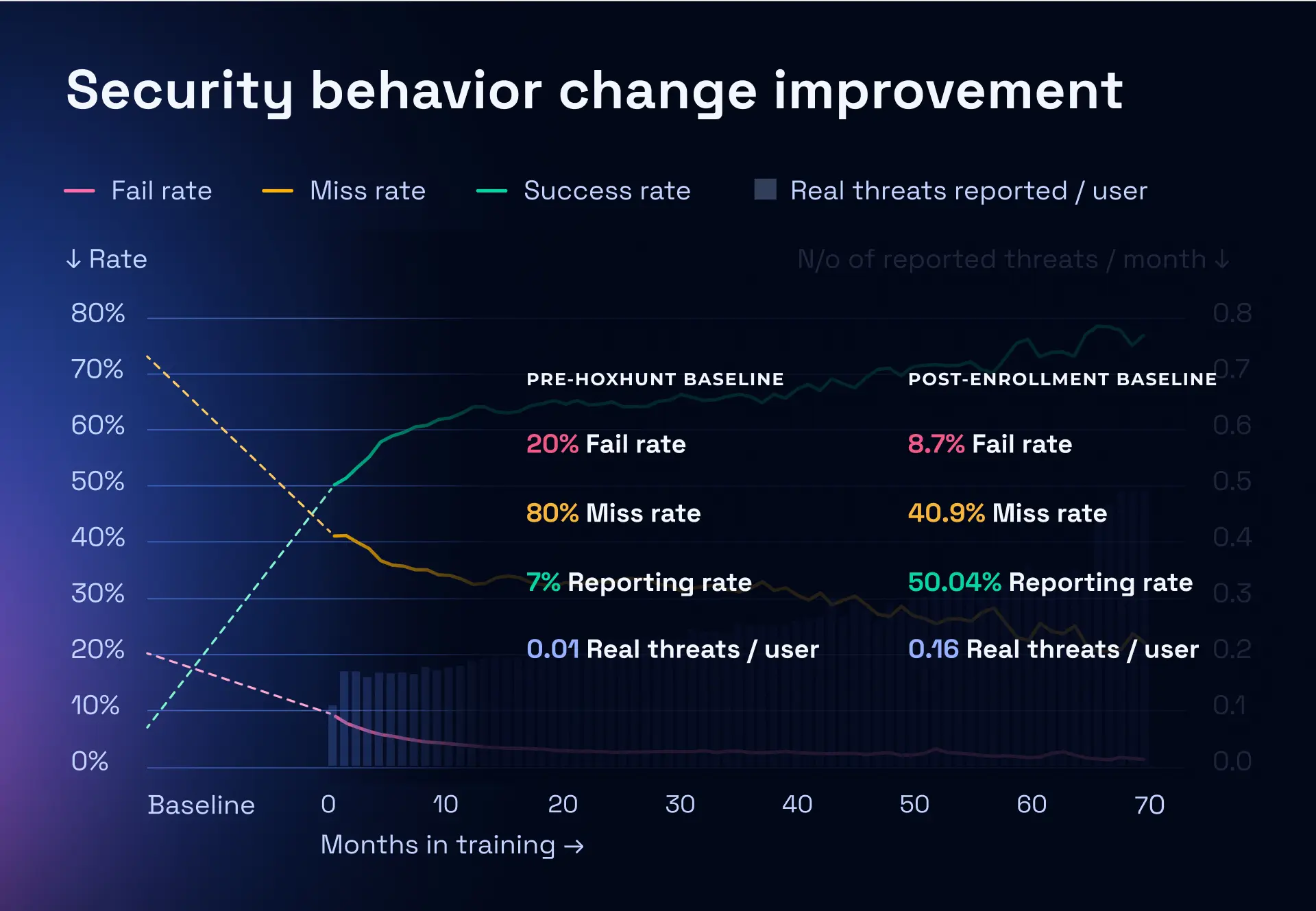
The Effectiveness of Two-Factor Authentication
Here's where the data gets encouraging. While phishing is becoming more sophisticated, two-factor authentication (2FA) remains incredibly effective at preventing account takeover, even when credentials have been compromised.
The mechanics are simple: even if an attacker has your password, they can't access your account without the second factor. This is why:
- SMS 2FA (where you get a code via text message) stops most phishing attacks because the attacker doesn't have your phone
- App-based 2FA (using Google Authenticator, Microsoft Authenticator, etc.) is even better because the codes are time-limited and can't be intercepted over the internet
- Hardware security keys (physical devices like Yubi Key) are essentially phishing-proof because the key won't authenticate on a fake website
But here's the thing: while 2FA is effective, it has a critical weakness that phishing exploits. Some phishing attacks use real-time 2FA interception.
Here's how it works:
- You click a phishing link and enter your password on a fake login page
- The attacker immediately uses your stolen password to attempt a real login on the actual service
- The real service sends you a 2FA prompt (text message, authenticator app notification, etc.)
- The fake website simultaneously shows you a message asking for your 2FA code ("Enter the code sent to your phone")
- You see the legitimate 2FA notification, assume it's the same login you're attempting, and enter the code on the fake website
- The attacker immediately uses that code to complete the login
The attacker has your password, they have your 2FA code, and now they have your account.
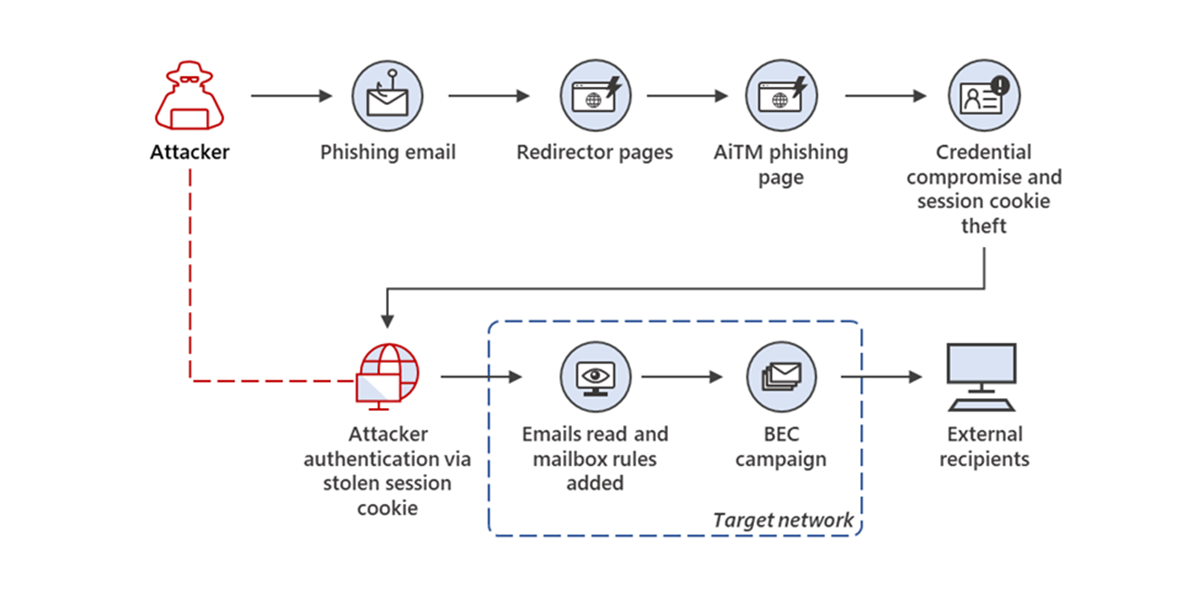
This attack is called adversary-in-the-middle (AITM) phishing or sometimes session hijacking phishing, and it's becoming increasingly common. It's why hardware security keys are so important: they won't authenticate on the attacker's domain because the key verifies that it's actually communicating with the legitimate company's servers.
Corporate Intelligence and Social Engineering Integration
One detail that's often overlooked in phishing discussions is how phishing integrates with broader social engineering.
Modern sophisticated phishing campaigns don't just send random emails. They're often combined with:
- Linked In research to identify job titles and organizational structure
- Company website information to understand departments and processes
- Social media profiles to find personal details (family members, vacation plans, recent purchases)
- Job postings and company announcements to find legitimate operational details
- Press releases and industry news to understand current priorities
An attacker might identify that your company is implementing a new Microsoft Teams deployment in Q2. They then craft a phishing email that references this specific project, mentions it by name, and claims to be from the IT department with instructions to "upgrade your Teams client" or "enable new authentication."
Because the email references a real project that's happening right now, the click rate skyrockets. It's not generic; it's specific to your situation.
This is why insider threat programs and security culture matter so much in organizations. A well-trained employee might notice that the email mentions a Teams deployment but doesn't mention specific dates or IT contacts they actually know. They might be more skeptical of urgent requests that came via email rather than official channels.
But a less-trained employee, seeing a reference to something real happening in their organization, might be much more likely to click.

The Psychological Tactics That Make Phishing Work
Beyond the technical aspects, phishing works because it exploits specific psychological principles.
Authority and legitimacy: People trust things that appear to come from trusted sources. A legitimate-looking email from "Microsoft Security Team" triggers an authority response. You assume that the sender has the right to ask for this information.
Scarcity and urgency: "Your account will be closed in 24 hours." "Limited time to update your payment information." "Unusual activity detected—act now." These create a sense that you need to do something immediately or lose something valuable. Urgency bypasses careful analysis.
Reciprocity: Some phishing emails thank you for being a customer or offer you something (a refund, a credit, a bonus). This creates an obligation to reciprocate by doing what they ask.
Social proof: "We need to verify your information because 10,000 similar accounts were compromised." This creates the impression that many people are doing this, so it must be legitimate.
Curiosity: "We found suspicious activity on your account—click to see what happened." The human brain wants to know what's going on. You click partially because you're curious, not just because you're worried.
Personalization: Using your real name, real email address, or references to services you actually use makes the email feel legitimate. It feels like it's specifically about you, not a mass mailing.
The most effective phishing campaigns use multiple psychological triggers simultaneously. They create urgency, reference real situations, use trusted brand names, and ask you to do something that seems completely normal and legitimate.
Enterprise Defense: Beyond Individual User Behavior
For organizations trying to defend against phishing, relying solely on user awareness training is insufficient. The most effective defenses use multiple layers:
Email filtering and threat detection: Tools that analyze emails for suspicious characteristics (malicious links, unexpected sender addresses, unusual request patterns, etc.) can catch many phishing attempts before they reach users.
Link rewriting and sandboxing: Some tools rewrite links in emails so that when you click them, your system verifies the destination is legitimate. Others open suspicious links in isolated environments (sandboxes) to see if they're malicious before letting users access them.
DMARC, SPF, and DKIM implementation: These email authentication standards make it much harder to spoof a company's email address. If implemented correctly, users can't receive emails claiming to be from microsoft.com unless they're actually from Microsoft.
Real-time threat intelligence: Organizations use threat feeds that know about known phishing campaigns, malicious domains, and attack patterns. Emails matching these patterns get flagged or blocked.
Endpoint detection and response (EDR): Even if a user clicks a malicious link and gets compromised, EDR tools can detect suspicious behavior on the user's computer and isolate it before the attack spreads.
Single sign-on (SSO) with monitoring: When all applications go through a central SSO system, the organization can monitor for suspicious login patterns (multiple failed attempts, logins from unusual locations, access to unusual applications) and block them in real-time.
Conditional access policies: Tools like Azure AD's Conditional Access can require additional authentication when logins appear unusual (new location, new device, unusual time of day). Even if an attacker has the password, they can't access the account without additional factors they don't have.
The reality is that you cannot phishing-proof an organization through user behavior alone. Users will always click things they shouldn't. The defense has to include technical controls that work even when users make mistakes.
What Defenders Are Getting Right (And What They're Still Missing)
Organizations that have successfully reduced phishing impact tend to do several things:
They assume breach: They operate under the assumption that phishing will happen, credentials will be stolen, and they plan for response and containment rather than just prevention.
They monitor for anomalous behavior: Rather than trying to prevent every phishing attempt, they monitor for what happens after someone's been compromised. Sudden mass forwarding of emails, unusual file access patterns, or lateral movement through the network all trigger alerts.
They implement micro-segmentation: Rather than assuming that once someone's inside the network everything is accessible, they segment the network so that compromised user accounts have limited access.
They enforce least privilege: Not every employee needs access to every system. By limiting access to only what's needed for each role, they limit the damage a compromised account can do.
However, many organizations are still struggling with:
Legacy systems that don't support modern authentication: Some applications can't use multi-factor authentication, making them perpetually vulnerable.
User friction vs. security trade-offs: The most secure authentication methods (hardware keys, physical presence requirements) are also the most inconvenient. Many organizations can't implement them because employees would bypass them.
Balancing user awareness with unrealistic expectations: You can't train your way out of phishing entirely. Some phishing attempts are just too sophisticated, and some users will always click. Expecting 100% compliance from users is unrealistic.
The Future of Phishing: What's Coming Next
Based on trends we're already seeing, phishing is likely to evolve in several directions:
Voice and video deepfakes: As deepfake technology improves, phishing might move beyond text and images into voice calls and video. Imagine a convincing video call with someone claiming to be from your bank asking you to verify information.
Real-time AI assistance: Some phishing emails are already being crafted with AI assistance. As this improves, the gap between phishing emails and legitimate company communications will narrow further.
Physical security integration: Phishing might expand into physical world attacks, where you get a phone call claiming to be from your bank, a text message from your delivery service, or even a face-to-face impersonation.
Third-party and supply chain attacks: Rather than directly phishing a company, attackers might phish their suppliers, partners, or customers to gain initial access to the target organization.
Credential-less authentication becoming urgent: As phishing becomes more sophisticated, the push toward authentication methods that don't rely on passwords or even traditional 2FA will accelerate.
The constant in phishing's evolution is that identity and access remain the most valuable targets. As long as that's true, Microsoft, Google, Amazon, and other identity providers will remain the most heavily impersonated brands.
Taking Control: Practical Steps You Can Take Today
For individuals, the practical defensive steps remain consistent despite phishing's evolution:
1. Use unique, strong passwords for every service: If you reuse passwords across services, a phishing attack that steals one credential compromises all services. Use a password manager to make this manageable.
2. Enable 2FA everywhere, preferably with an authenticator app or hardware key: SMS 2FA is better than nothing, but app-based or hardware-key based 2FA is significantly more secure.
3. Navigate directly to official websites: When you get an email about account activity, don't click the link. Instead, open a fresh browser, search for the official website, and navigate directly. If there's a real issue, you'll see it in your actual account.
4. Verify sender email addresses carefully: The display name in an email can be anything. The actual sender address is harder to fake. If an email claims to be from Microsoft, the sender should actually be from a @microsoft.com address, not @microsft.com or @microsoft-verify.com.
5. Check for HTTPs and legitimate certificates: When you do click a link (hopefully rarely), verify the website uses HTTPS and that the certificate is valid. Modern browsers will warn you if something is off, but you have to actually look.
6. Be suspicious of urgency and emotional appeals: Phishing works by creating a sense that you need to act now or something bad will happen. Legitimate companies are usually patient. If something creates urgency and emotional pressure, slow down and verify independently.
7. Report phishing attempts: When you see phishing, report it to the company being impersonated and to your email provider. Most companies have a way to report phishing (usually something like abuse@company.com). This helps defenders identify attacks and get malicious sites taken down.
8. Use browser security tools: Modern browsers have phishing detection built in. Keep your browser updated to get the latest protections. Browser extensions from reputable security companies can also help.
Why Identity is the New Battlefield
Ultimately, understanding why Microsoft, Google, and Amazon dominate the phishing charts comes down to understanding that identity has become the critical battle line in cybersecurity.
In the past, security was about protecting perimeters. You had a network, you protected its edges, and if you were inside, you were trusted. That model has collapsed. With cloud services, remote work, and the integration of personal and professional devices, there is no longer a clear edge to the network.
Instead, identity has become the new perimeter. Your identity—specifically, your ability to authenticate to services—is what determines what you can access, what data you can see, and what damage you can do.
By focusing on stealing identity credentials from the biggest identity providers, attackers are taking the most direct path to breaching networks and compromising data. A stolen Microsoft credential might give them access to a company's email, files, and potentially their entire network (depending on how that company has set things up).
This is also why the phishing landscape is unlikely to change dramatically. As long as identity is the new security perimeter, identity providers will remain the most valuable targets for phishing attacks.
The companies at the top of the most-spoofed list aren't there by accident. They're there because they're the gateways to everything else. Defending against phishing, then, isn't just about individual email security. It's about recognizing that your most critical resource is your digital identity, and protecting it accordingly.
FAQ
What exactly is phishing and how does it work?
Phishing is a social engineering attack where someone tries to trick you into revealing sensitive information (usually login credentials) by impersonating a trusted person or organization. It typically works by sending you an email, text message, or phone call that appears to come from a legitimate company, requesting that you "verify" information, "confirm" your account, or "update" your payment method. When you click the link and enter your information on a fake website or in a response, the attacker captures your credentials.
Why is Microsoft the most targeted company for phishing attacks?
Microsoft dominates phishing statistics for several reasons. First, it's ubiquitous—over 400 million people use Microsoft 365 for work and personal use. Second, a Microsoft account is often the master key to someone's digital life, providing access to email, cloud storage, backup codes, and recovery options for other accounts. Finally, Microsoft credentials are highly valuable on the dark web, making them economically attractive for attackers who can sell them to other criminals.
How can I tell if a phishing email is fake, especially when they look so convincing now?
Even though phishing emails are becoming more sophisticated, several red flags remain. Check the sender's actual email address (not just the display name) to verify it matches the legitimate company's domain. Hover over links without clicking to see where they actually point—legitimate companies use their official domain names. Look for generic greetings like "Dear Customer" instead of your actual name. Be suspicious of urgency and threats ("Account will be closed in 24 hours"). Most importantly, never click links in emails asking for sensitive information; instead, navigate directly to the company's official website using a search engine or your saved bookmarks.
Is two-factor authentication enough to protect against phishing?
Two-factor authentication (2FA) is significantly more effective than passwords alone, but it's not completely phishing-proof. While SMS or app-based 2FA will stop most phishing attacks, sophisticated attackers can still intercept 2FA codes through real-time interception phishing, where they immediately attempt to log into the real service while you're viewing a fake login page, and trick you into providing the 2FA code. Hardware security keys (like Yubi Key) are essentially phishing-proof because they cryptographically verify they're communicating with the legitimate service, but SMS or app-based 2FA provides a strong layer of protection for most people.
What should I do if I think I've fallen for a phishing attempt?
Immediately change your password for that account from a different device or computer (not the one where you entered your credentials). Enable or strengthen 2FA if you haven't already. Check your account activity for suspicious logins or access from unfamiliar locations, and revoke any sessions that seem unauthorized. If the compromised account is connected to other important accounts (like an email address used for password recovery on other services), change those passwords as well. Consider contacting the company's official support line to report the attack and check for any fraudulent activity. For enterprise accounts, notify your IT security team immediately.
Are certain industries or user groups more vulnerable to phishing?
Yes, several groups are disproportionately vulnerable. Younger users (under 25) fall for phishing at 3-4 times the rate of older users, partly because security awareness training has been less prevalent for them. Healthcare and financial services employees are heavily targeted because their accounts provide access to sensitive data and systems. Remote workers are more vulnerable because they're less likely to have access to company security infrastructure and less likely to have in-person security training. Non-English speakers can be more vulnerable to language-specific phishing that they might not immediately recognize as suspicious. Additionally, companies going through transitions (mergers, major system implementations, new security policies) see higher phishing click rates as employees are confused about legitimate vs. illegitimate communications.
How do I report phishing emails and get malicious websites taken down?
Most companies have a dedicated phishing report address, usually something like abuse@company.com or security@company.com. You can forward suspicious emails to these addresses. Additionally, you can report phishing to your email provider (Gmail, Outlook, etc.) by clicking "Report phishing" or a similar option in your email client. If you encountered a malicious website, you can report it to the browser you were using (Chrome, Firefox, Safari all have reporting mechanisms). Finally, organizations like the Anti-Phishing Working Group (APWG) accept phishing reports and share that intelligence with ISPs and hosting providers to get sites taken down quickly.
Why do attackers focus on specific brands when they could just randomly phish everyone?
Attackers are incredibly strategic about their targeting because resources matter. A phishing email to someone who doesn't have a Microsoft account is wasted effort. By focusing on specific brands that billions of people use, attackers dramatically increase their success rates. Additionally, credentials for certain services (like Microsoft or Google accounts with payment information linked) are worth significantly more on the dark web than random email addresses. Attackers often have databases of stolen email addresses and known password histories, so they can target people who are most likely to be vulnerable to specific brands. The economics favor specialization and targeting rather than random mass attacks.
The Bottom Line on Phishing and Brand Spoofing
The data is clear: Microsoft, Google, Amazon, Apple, and a select group of other tech giants will remain the most heavily targeted brands for phishing indefinitely. This isn't likely to change because identity and authentication are the fundamental building blocks of everything else in the digital world.
What's encouraging is that the defensive strategies remain consistent and effective. Basic cyber hygiene—strong unique passwords, two-factor authentication, careful verification of links and sender addresses, healthy skepticism of urgency—still stops the vast majority of phishing attempts.
What's concerning is that phishing is becoming more sophisticated, more personalized, and more integrated with broader social engineering and intelligence gathering. The attackers aren't random amateurs anymore. Many are part of organized crime syndicates or state-sponsored groups with significant resources, expertise, and time.
Your best defense isn't perfect vigilance (which is humanly impossible) or complete avoidance (which is unrealistic). Your best defense is defense in depth: multiple layers of protection so that when one layer fails (and it will eventually), other layers catch the attack.
For individuals, that means strong passwords, 2FA, and being thoughtfully skeptical of requests for sensitive information. For organizations, that means email filtering, link rewriting, endpoint detection, conditional access policies, and a security culture where people feel empowered to question suspicious requests.
The brands at the top of the phishing list aren't there because they have weak security. They're there because they're the keys to everything else. Protecting those keys has become the central challenge of modern cybersecurity, and it's a challenge that's becoming more urgent every year.
Microsoft, Google, and Amazon will likely remain the most spoofed brands in 2026, 2027, and beyond. But by understanding why they're targeted and implementing practical defenses, you can significantly reduce your personal and organizational risk.
Key Takeaways
- Microsoft accounts are 22% of all brand phishing attempts because they're the master key to someone's digital identity and cloud storage
- Tech firms account for 90%+ of the top 10 most-spoofed brands, with DHL's appearance signaling shift toward logistics and financial targeting
- Stolen credentials command real prices on dark web markets (200 depending on account type), creating economic incentive for phishing at scale
- Modern phishing uses AI to generate grammatically perfect emails, real-time 2FA interception, and personalized details from past breaches to defeat traditional defenses
- Two-factor authentication works for most attacks, but sophisticated AITM phishing can intercept 2FA codes; hardware security keys are essentially phishing-proof
- Basic cyber hygiene (unique passwords, 2FA, independent website verification, healthy skepticism of urgency) remains the most effective individual defense despite increasing sophistication
- Organizations need defense-in-depth strategies including email filtering, endpoint detection, conditional access, and least-privilege access rather than relying solely on user awareness
Related Articles
- 45 Million French Records Leaked: What Happened & How to Protect Yourself [2025]
- Supreme Court Hacker Posted Stolen Data on Instagram [2025]
- Massive Phishing Campaign Targets Middle East Officials, Activists, Journalists [2025]
- Tea App's Comeback: Privacy, AI, and Dating Safety [2025]
- Proton VPN Kills Legacy OpenVPN: What You Need to Know [2025]
- Best VPN Service 2026: Complete Guide & Alternatives
![Most Spoofed Brands in Phishing Scams [2025]](https://tryrunable.com/blog/most-spoofed-brands-in-phishing-scams-2025/image-1-1768844538330.jpg)



