LinkedIn Comment Phishing: How to Spot and Stop Malware Scams
LinkedIn used to be a relatively safe space for professionals. You'd scroll through posts about career wins, industry insights, and the occasional humble-brag about promotions. But like every platform with millions of users, it's become a hunting ground for scammers.
Recently, security researchers uncovered a new phishing campaign spreading across LinkedIn comments. Attackers are posting fake messages claiming user accounts have been locked or banned, then directing people to malicious links. The scary part? If you're not paying attention, these scams can look legitimate.
This isn't just annoying noise in your feed. We're talking about credential theft, malware infections, and potential identity fraud. One wrong click and a hacker could access your professional network, impersonate you to your contacts, or steal sensitive company information.
In this guide, I'll break down exactly how these scams work, show you the red flags you need to catch, and walk through concrete steps to protect yourself and your organization. Whether you're a job seeker, an executive, or just someone trying to use LinkedIn without getting hacked, you need to understand this threat.
TL; DR
- LinkedIn comment phishing is spreading: Attackers post fake account suspension notices in comments with malicious links
- Red flags are visible if you look: Fake profiles with zero followers, suspicious domains like netlify.app, and unnatural comment placement
- LinkedIn doesn't use comments for policy violations: The platform only communicates account issues through official notifications in your account settings
- Your job is to be skeptical: Never click links in comments, verify through official channels, and report suspicious activity immediately
- Bottom line: A 30-second verification step saves you from credential theft and malware infections


Estimated data shows that professional networks and employment information are prime targets for phishing on LinkedIn, each accounting for around 20-25% of attacks.
How LinkedIn Comment Phishing Actually Works
The mechanics of this scam are straightforward, which is partly why it's effective. Here's the playbook attackers are using:
First, they create a fake LinkedIn account. Nothing fancy—just a name that sounds official and a stolen profile picture, often pulled directly from LinkedIn's own design assets or employee directories. The account name might be something like "LinkedIn Compliance," "LinkedIn Security Team," or even just "LinkedIn Very." These accounts have zero followers, zero activity, and nothing that connects them to the actual platform except the name.
Next, they find popular posts in their target audience's feed. This could be anything: job postings, career advice, industry news, or motivational content. The more engagement a post has, the better. Thousands of comments mean thousands of eyes on whatever message they inject.
Then comes the malicious comment. The attacker posts something like:
"Your account has been flagged for suspicious activity and locked for security violations. Please verify your identity immediately at [MALICIOUS LINK]. If you don't verify within 48 hours, your account will be permanently suspended."
It's urgency and authority rolled into one. Most people's threat detection systems immediately trigger: account locked? Security violation? You start panicking. And that's exactly what they want.
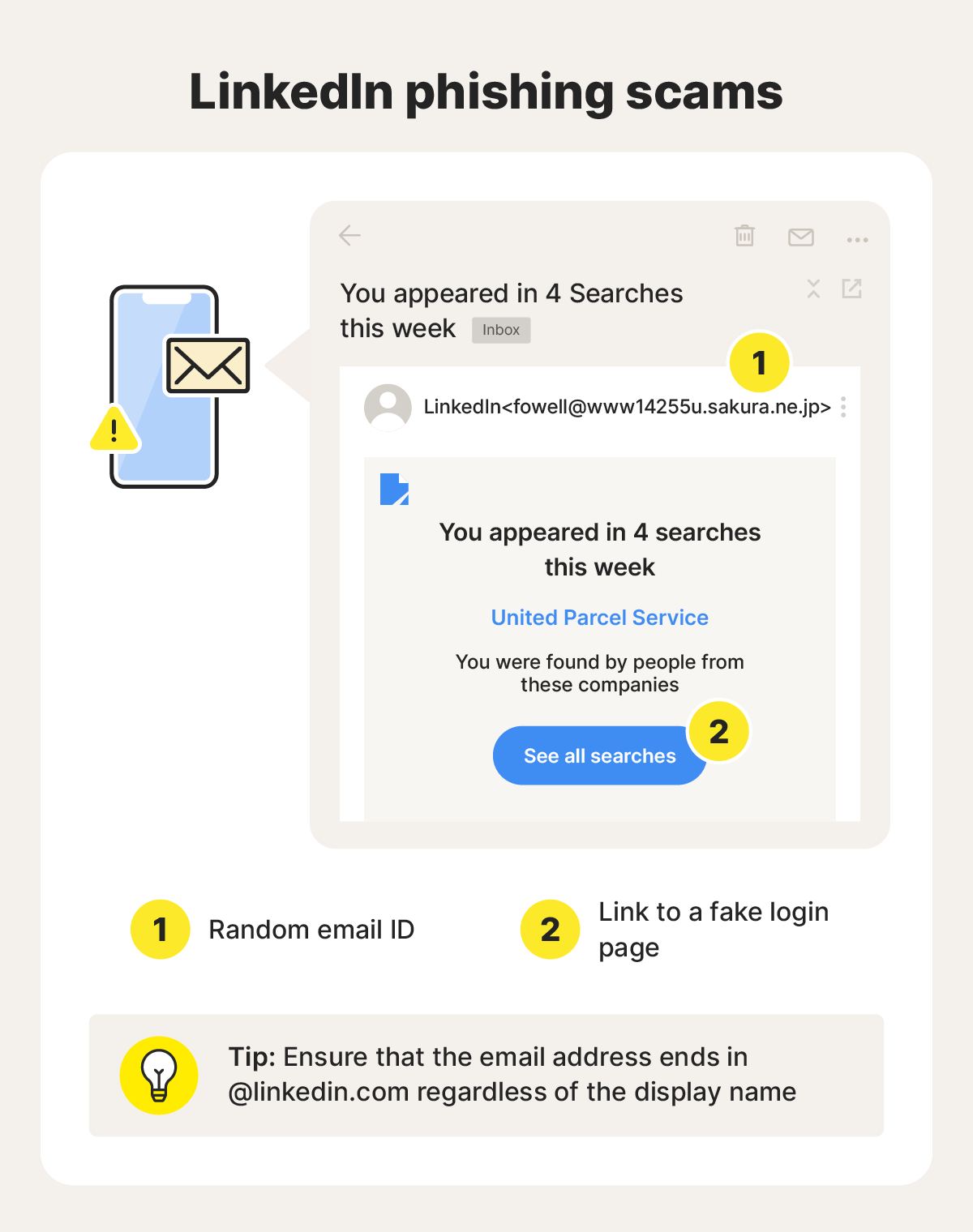
The link itself is the trap. It might point to a fake LinkedIn login page hosted on netlify.app, AWS, or another free hosting platform. Some attackers use LinkedIn's official URL shortener, which gives the link a veneer of legitimacy. Either way, when you click it, you're taken to a site that looks exactly like LinkedIn's login page—same colors, same layout, same typography.
You enter your email and password, thinking you're fixing a security issue. Instead, you've just handed your credentials to a criminal. Within minutes, they're logged into your account, changing your password, accessing your messages, and potentially accessing sensitive company information or your contacts' data.
The scary part is how passive this attack is. There's no need for the attacker to be particularly technical. They don't need to exploit zero-day vulnerabilities or break through firewalls. They just need your password, and they can access everything.
What makes this campaign particularly insidious is the scale and coordination. It's not one attacker with one fake account. Security researchers have identified multiple coordinated accounts all running the same phishing operation, which suggests this is likely an organized criminal ring with infrastructure, resources, and motivation to refine their tactics.
LinkedIn is aware of the campaign and has publicly acknowledged it, stating they're working to stop it. But the platform's moderation can't catch everything in real-time. New accounts pop up faster than moderators can review them. It's a game of whack-a-mole, and attackers are creating moles faster than LinkedIn can swing the hammer.
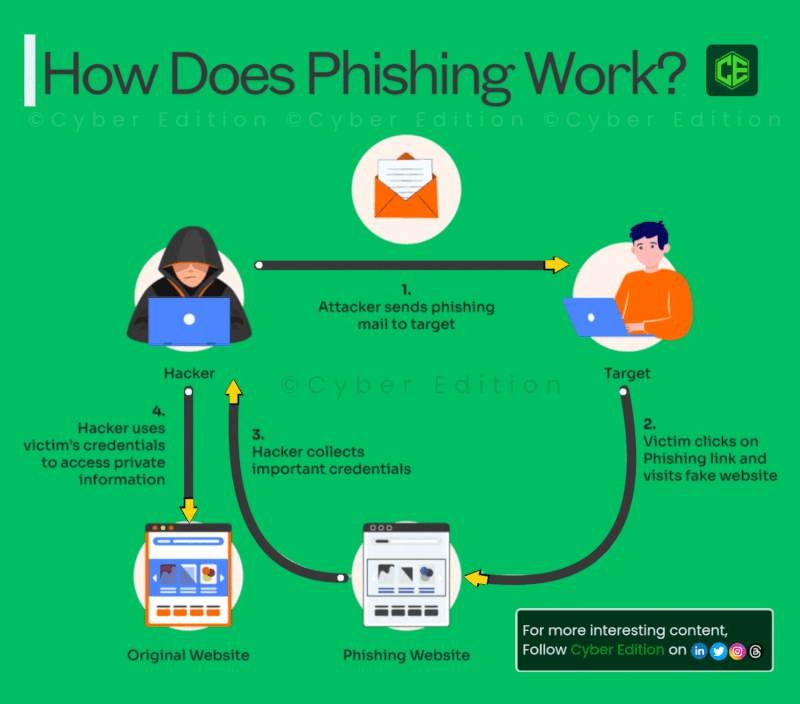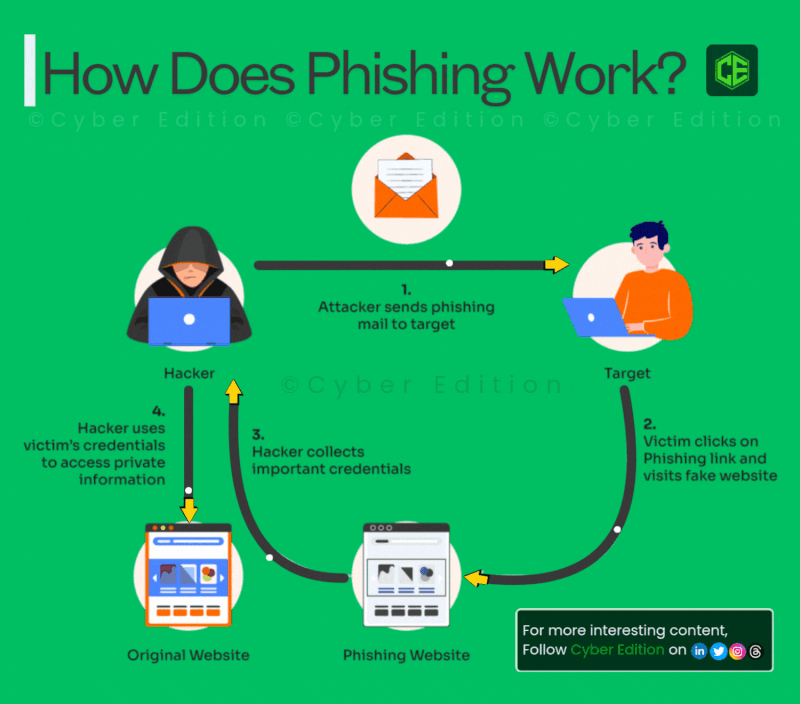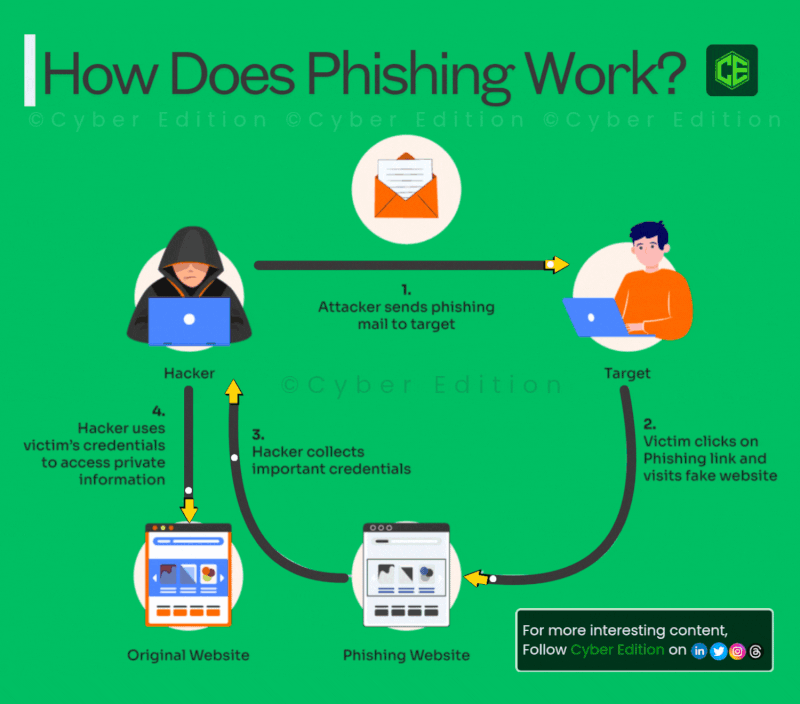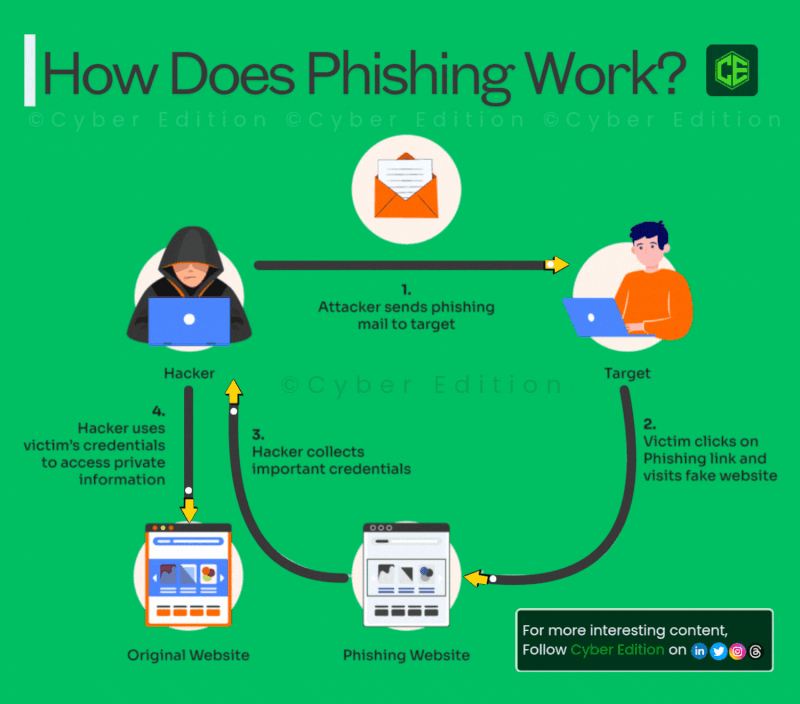
Estimated data shows an equal distribution of tactics used in LinkedIn comment phishing, highlighting the multi-step approach attackers use.
The Red Flags You Need to Spot Immediately
The good news: if you know what to look for, these scams are actually pretty easy to spot. The attackers are relying on panic and speed to bypass your critical thinking. Slow down, and the deception falls apart.
Here are the concrete red flags:
Red Flag #1: The Profile Is Completely Fake
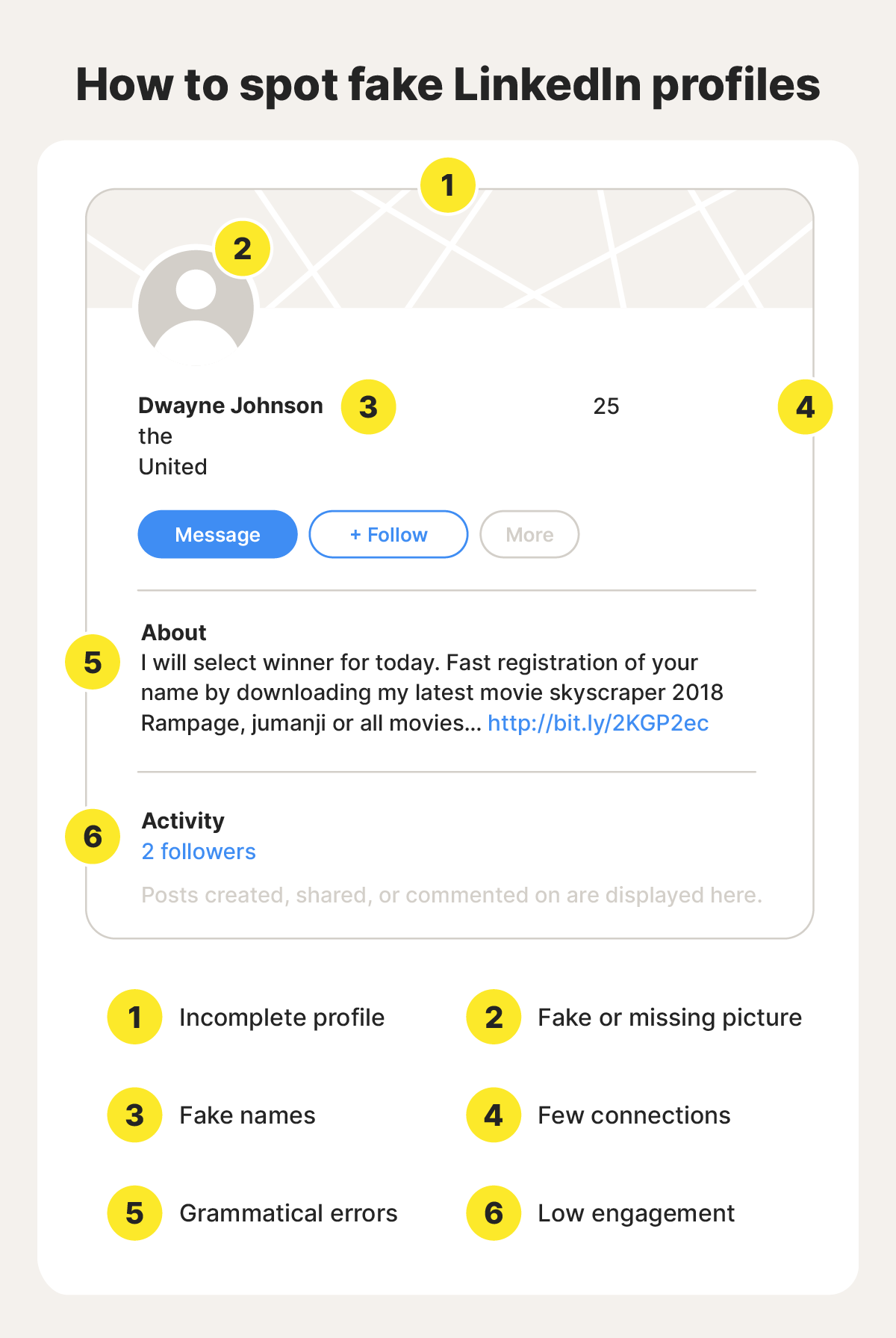
Click on the profile of anyone posting account suspension notices in comments. A legitimate LinkedIn representative would have a verified account with the official LinkedIn badge, thousands of followers, and a history of legitimate activity. These fake accounts have literally nothing. Zero followers. Zero posts. A profile picture that's obviously stolen. One account was literally named "LinkedIn Very," with a LinkedIn-branded image as the profile photo.
Real LinkedIn support staff would have verified accounts with clear branding. They wouldn't look like they were created five minutes ago.
Red Flag #2: The Link Isn't Actually From LinkedIn
Hover over (don't click) any link in a suspicious comment. Check where it actually goes. Does it point to linkedin.com? Or does it point to netlify.app, herokuapp.com, vercel.app, or some other random domain? That's your smoking gun.
LinkedIn's official URL shortener uses the domain linkedin.com/comm/... or similar. But even then, a legitimate account issue notification would never come through a comment. It would come through your account settings.
Some attackers have gotten slightly more sophisticated and use LinkedIn's official URL shortener, which can make the link appear more credible at first glance. This is why you need to click the "expand" button next to shortened URLs to see the full destination before clicking.
Red Flag #3: LinkedIn Never Communicates Policy Violations Through Comments
This is the biggest red flag, and LinkedIn has explicitly confirmed it. The platform does not and will not communicate account issues, policy violations, or security concerns through public comments on posts. Ever. Not in your feed, not in your messages, not anywhere except your official account settings.
If there's a legitimate issue with your account, LinkedIn will send you a notification directly in your account, along with options to appeal or fix the problem. It will never direct you to a random link.
Red Flag #4: The Grammar and Tone Aren't Quite Right
These attacks are often automated or templated. While some phishing attempts use perfect English, many have subtle grammar issues, awkward phrasing, or a tone that doesn't match how LinkedIn actually communicates. Real LinkedIn messages are usually conversational and professional. Phishing messages often feel robotic or overly urgent.
Don't rely solely on grammar as your defense, but it's another data point. If the message feels off, your instinct is probably right.
Red Flag #5: The Timing Doesn't Make Sense
Why would LinkedIn comment on someone else's post to notify you about your account? It doesn't. If your account had a security issue, LinkedIn would reach out to you directly through your account or via email associated with that account. A public comment is the least effective way to reach someone.
Think about it logically: if your account was actually locked, why would LinkedIn post about it on a random person's post? That's inefficient and doesn't make sense from a support perspective.
Red Flag #6: The Sense of Urgency Is Manufactured
Phishing attacks almost always create artificial urgency: "Your account will be suspended in 48 hours." "Verify immediately." "Act now." This is a classic manipulation tactic. It's designed to bypass your rational decision-making and push you into acting fast.
Legitimate security issues are handled with actual urgency, but LinkedIn would give you time to respond and would provide clear support options. They wouldn't threaten immediate action based on a comment from a random account.

Why LinkedIn Is a Phishing Gold Mine
Understanding why LinkedIn has become a target helps you understand the broader threat. It's not random.
LinkedIn has over 900 million users, with a heavy concentration of professionals, executives, and people in decision-making positions. For attackers, this is jackpot. A successful phishing attack here doesn't just give you access to someone's social profile. It potentially gives you access to:
- Professional networks and contacts that can be exploited for business email compromise scams
- Employment information that can be used to impersonate you at your workplace
- Email addresses and phone numbers for additional social engineering attacks
- Confidential information from private messages or connections
- Company data if you've shared details about your workplace, clients, or projects
LinkedIn's entire value proposition—that it's a trusted professional network where people share real information—is exactly what makes it attractive to attackers. There's genuine, verifiable professional data on LinkedIn that's worth money on the dark web.
Furthermore, LinkedIn's open comment system means attackers can post to millions of feeds without requiring any approval or verification. Unlike email phishing, which requires sending thousands of individual emails (and risks getting flagged as spam), a single comment on a viral post reaches millions of people instantly.
The comment section also adds a layer of pseudo-legitimacy. If someone sees a comment from what appears to be "LinkedIn," they're more likely to trust it than an unsolicited email. It's social proof. Other people can see it too. That's the trap.
Lastly, LinkedIn's own growth and prominence mean attackers are increasingly focused on it. As the platform's security matures to stop some threats, attackers shift tactics. Comment phishing is just the latest evolution.

Estimated data showing the progression of a phishing attack over four days, highlighting key stages from initial phishing to incident response.
What Happens If You Click the Malicious Link
Let's walk through the worst-case scenario so you understand what's actually at stake.
You see a comment, panic, click the link. You're taken to a fake LinkedIn login page. It looks perfect. Same blue color scheme, same logo, same layout. You enter your email address and password. You hit login.
The page might show an error: "Invalid login" or "Please try again." This is intentional. It gives you the impression that something went wrong, when really, the attacker has already captured your credentials. You might even be redirected to the real LinkedIn homepage, which reinforces your belief that you successfully logged in.
Now the attacker has your email and password. What happens next?
Immediate compromise (minutes to hours): They log into your actual LinkedIn account. If you used the same password elsewhere—and statistically, 66% of people reuse passwords—they can now try that password on other sites. Your email account, your banking app, your work systems. This is called credential stuffing, and it's automated. Attacker software tries your credentials against thousands of common services.
They change your LinkedIn password, locking you out. They might update your profile information, making it look like you're in a different country, have a different job, or are looking for employment in a specific sector. This is preparation for the next stage of the attack.
Short-term exploitation (hours to days): With access to your account, they can browse your professional connections and see who you're connected to. They might impersonate you in private messages: "Hey, I'm starting a consulting business and need some advice. Can you do a quick call?" This is a spear-phishing attack, using your credibility to target your network.
They might create a fake job posting impersonating your company, targeting your competitors or other industry professionals. They might scrape data from your profile and your connections to build a more targeted attack list.
For executives and people in sensitive positions, they can gather information about company structure, ongoing projects, and important contacts—all the intelligence an attacker needs for more sophisticated business email compromise (BEC) scams.
Medium-term damage (days to weeks): If this was part of a larger coordinated attack, your compromised account becomes part of an attack infrastructure. Your profile might be added to a network of hacked accounts used for mass phishing, malware distribution, or social engineering campaigns.
Your connections might receive invitations from your account to view a "malicious document" or "resign confirmation form" that actually contains malware. Lateral movement. Your trust extends to your network, and attackers exploit that.
Long-term consequences: You might not even realize your account was compromised if the attackers are subtle about it. They might simply monitor your account for sensitive information you share with clients or colleagues. They might track job changes at your company to identify when new executives join, then target those people with targeted phishing attacks.
If your company has significant intellectual property or you work in a regulated industry, credential theft on your LinkedIn account could be a foothold for industrial espionage or data theft.
The Sophisticated Variants: When Scammers Get Clever
While the basic phishing scam is straightforward, attackers have developed more sophisticated variants. Understanding these helps you catch even the harder-to-spot attacks.
Variant 1: The False LinkedIn Admin Account
Instead of naming their account something obvious like "LinkedIn Security," attackers now create accounts that impersonate real LinkedIn employees or executives. They might use a name similar to actual LinkedIn staff, with a stolen profile photo and slightly modified branding.
They'll comment on industry-relevant posts, making legitimate-sounding contributions to build credibility. Then, when they post the phishing message, it carries the weight of apparent authority. Someone with a few hundred followers looks more credible than an account with zero followers.
Variant 2: The Partnered Service Scam
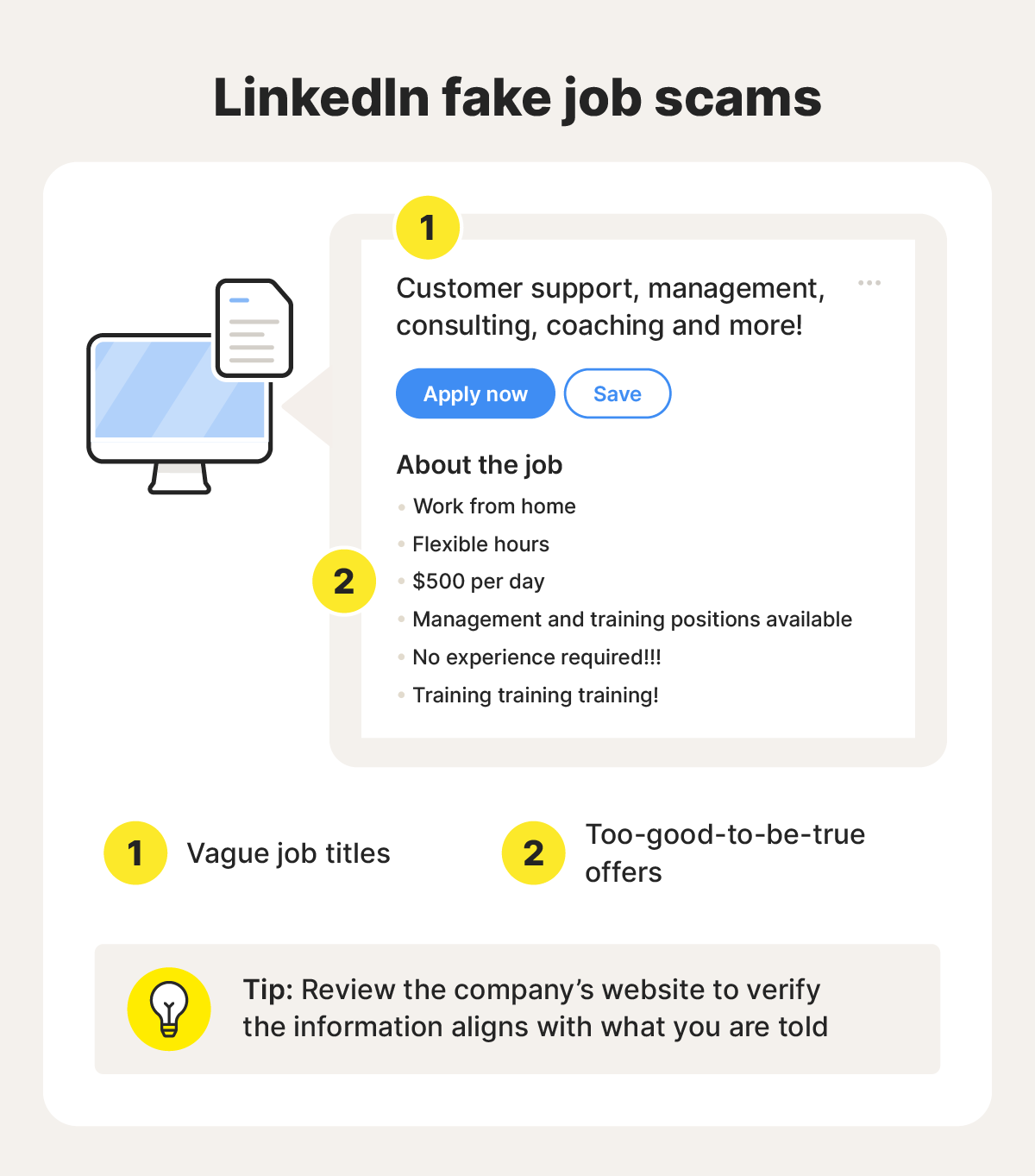
Instead of impersonating LinkedIn directly, attackers claim to represent LinkedIn's security partners or third-party services. "LinkedIn has contracted with us to verify your identity. Please confirm your details at [LINK]." This exploits the fact that LinkedIn does use third-party services, making the claim seem plausible.
Variant 3: The Verification-Before-Feature Unlock
Attackers claim you need to verify your identity to unlock a new LinkedIn feature, access a job opportunity, or participate in a recruiter's request. "Premium recruiters require verification. Verify here to apply." This preys on FOMO (fear of missing out) and professional ambition.
Variant 4: The Account Recovery Scam
Instead of claiming suspension, attackers claim your account might have been compromised and you should reset your password immediately. "We detected unusual activity. Reset your password now." This feels like you're being protected, when really you're giving up control.
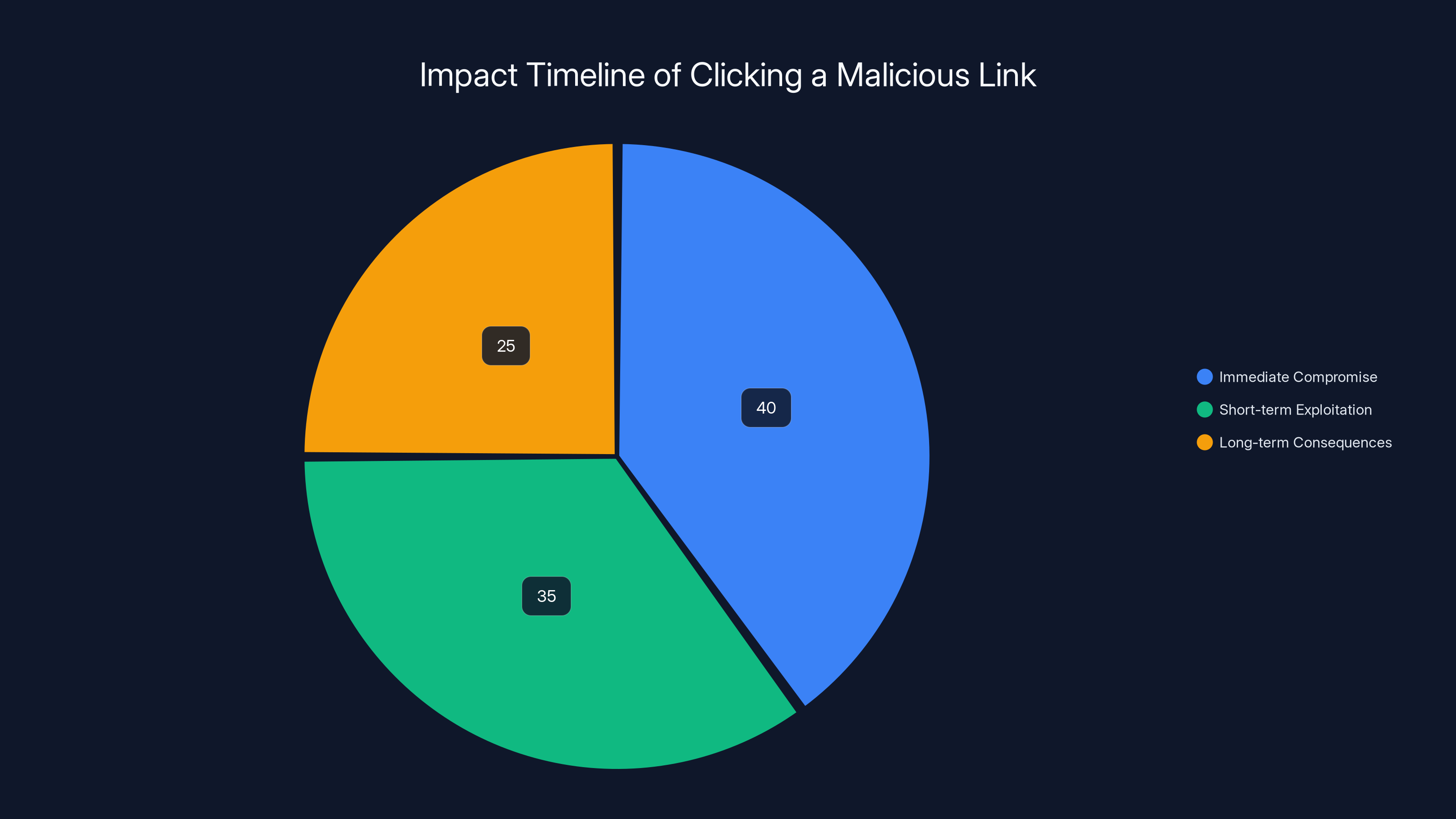
Estimated data shows that immediate compromise accounts for 40% of the impact, with short-term exploitation at 35% and long-term consequences at 25%.
Multi-Vector Attacks: When LinkedIn Phishing Is Just the Beginning
LinkedIn phishing attacks rarely exist in isolation. Smart attackers use a multi-vector approach.
They might target you on LinkedIn with a comment phishing attempt, knowing most people will ignore it. But simultaneously, they're sending similar phishing emails to addresses they've scraped from LinkedIn profiles. They're creating fake job postings on other platforms to capture resumes with personal information.
They're monitoring your LinkedIn activity to identify when you're actively job searching or changing roles. They're watching your public posts for information about your industry, your pain points, your professional interests. Then they craft targeted spear-phishing emails that reference specific conversations or interests you've shared publicly.
This is coordinated, sophisticated, and intentional. It's not just one attack vector. It's a campaign designed to eventually break through your defenses through sheer variety and persistence.
The most successful attacks aren't always the most technical. They're the most patient and persistent.

How to Verify Your Account Status Without Clicking Links
If you're concerned that your account might actually have an issue, here's the safe way to verify it.
Step 1: Open a new browser tab. Don't click any links from comments or messages. Type linkedin.com directly into your browser address bar. This ensures you're going to the real LinkedIn, not a fake login page.
Step 2: Log in as normal. If your account is truly locked or suspended, you'll find out immediately. LinkedIn won't let you log in. You might see a message in your account saying what the issue is.
Step 3: Check your account settings. Click on your profile picture, then "Settings & privacy"> "Account access"> "Login and security." This is where LinkedIn displays any account issues that need your attention. If there's nothing there, your account is fine.
Step 4: Contact LinkedIn support through official channels. If you do see an issue, click the help or support link within your LinkedIn account settings. Don't search for "LinkedIn support" and click random links. Use the support options available within your account.
Step 5: Verify through alternative communication. If you're really concerned, call LinkedIn's support number (which you can find by logging into your account and navigating to help) or email them through your registered email address. Legitimate support will reach out to you through channels they can verify.
The key principle: always initiate contact through official channels, never through links provided by a stranger in a comment.
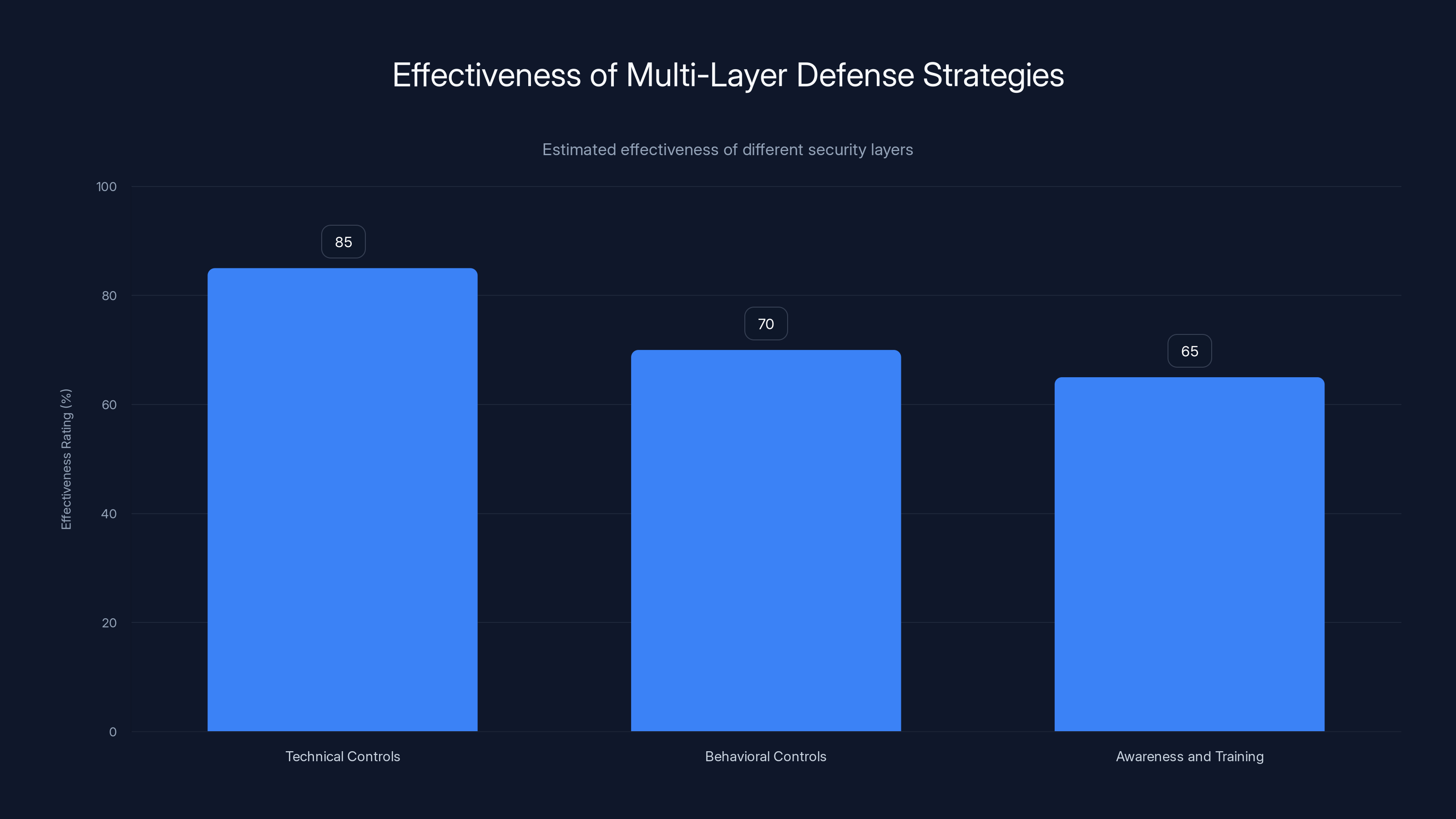
Technical controls, such as 2FA and strong passwords, are estimated to be the most effective layer, followed by behavioral controls and awareness training. Estimated data.
Protecting Yourself: A Multi-Layer Defense Strategy
No single defense is perfect. Security works best when you layer multiple protections.
Layer 1: Technical Controls
Enable two-factor authentication (2FA): This is the most important step. Even if attackers get your password, they can't log in without your phone. Go to Settings > Account > Login and security > Two-step verification. LinkedIn offers 2FA via authenticator app, SMS, or security keys. The authenticator app or security key is more secure than SMS.
Use a unique, strong password: Your LinkedIn password should be unique (not used anywhere else) and strong (at least 16 characters, mixing uppercase, lowercase, numbers, and symbols). Use a password manager like Bitwarden or 1Password to generate and store unique passwords.
Set up account recovery options: Add a recovery phone number and backup email address to your account. This helps you regain access if your account is compromised.
Enable login notifications: LinkedIn can notify you every time someone logs into your account from a new location or device. Check these notifications regularly and report any unrecognized logins immediately.
Layer 2: Behavioral Controls
Treat all unsolicited links as suspicious: If you didn't expect someone to send you a link, don't click it. Instead, navigate to the service manually through your browser.
Hover before you click: On desktop, hover over links to see where they actually go. On mobile, long-press the link to see the URL.
Verify unusual requests: If someone messages you with an urgent request ("Can you send me the project files?"), verify it's really them. Call them. Use a communication channel you trust.
Be skeptical of authority claims: Just because someone claims to represent LinkedIn (or any company) doesn't mean they do. Scammers impersonate authority figures all the time.
Layer 3: Awareness and Training
Learn what phishing looks like: The more you see phishing attempts, the better you get at spotting them. Read security articles, take training courses, and stay updated on new attack tactics.
Understand social engineering: Most successful attacks exploit psychology, not technology. Understand how manipulation works so you can recognize it.
Stay informed about LinkedIn-specific threats: Follow cybersecurity news outlets that cover LinkedIn threats. Subscribe to LinkedIn's official security blog. Know what attacks are currently active.

What Organizations Need to Do
If you manage a team or work in a security role, you need to address this at an organizational level.
Employee Training
Run regular phishing simulations. Send your employees fake phishing emails (with IT's approval) to see who clicks. Track results. Train the people who fail. Make security training part of onboarding and ongoing professional development.
Teach employees about LinkedIn-specific threats. Host lunch-and-learns about phishing. Create internal documentation about safe LinkedIn practices.
Policy Updates
Update your security policies to specifically address phishing on social media platforms. Make it clear that employees should never click links in unsolicited comments or messages. Define the official channels through which company policies or security notices will be communicated.
Create a policy about what information employees can share on LinkedIn. Many companies now restrict employees from publicly listing the names of clients, specific project details, or advanced knowledge of upcoming announcements.
Technical Controls
If your organization uses Microsoft 365 or Google Workspace, leverage their phishing detection and reporting tools. Both platforms can flag suspicious emails and provide one-click reporting.
Consider URL filtering solutions that block known phishing domains. Solutions like Cisco Umbrella or Zscaler can prevent employees from even reaching phishing pages.
Implement DMARC, SPF, and DKIM email authentication protocols. This prevents attackers from spoofing your company domain.
Incident Response
Create a clear process for employees to report suspected phishing. Make it easy. One-click reporting is better than requiring employees to email security team screenshots and explanations.
If an employee does get phished, have a rapid response plan. Reset their password immediately. Force a logout of all sessions. Check for lateral movement (did the attacker move from their account to other systems?). Monitor their account for suspicious activity.
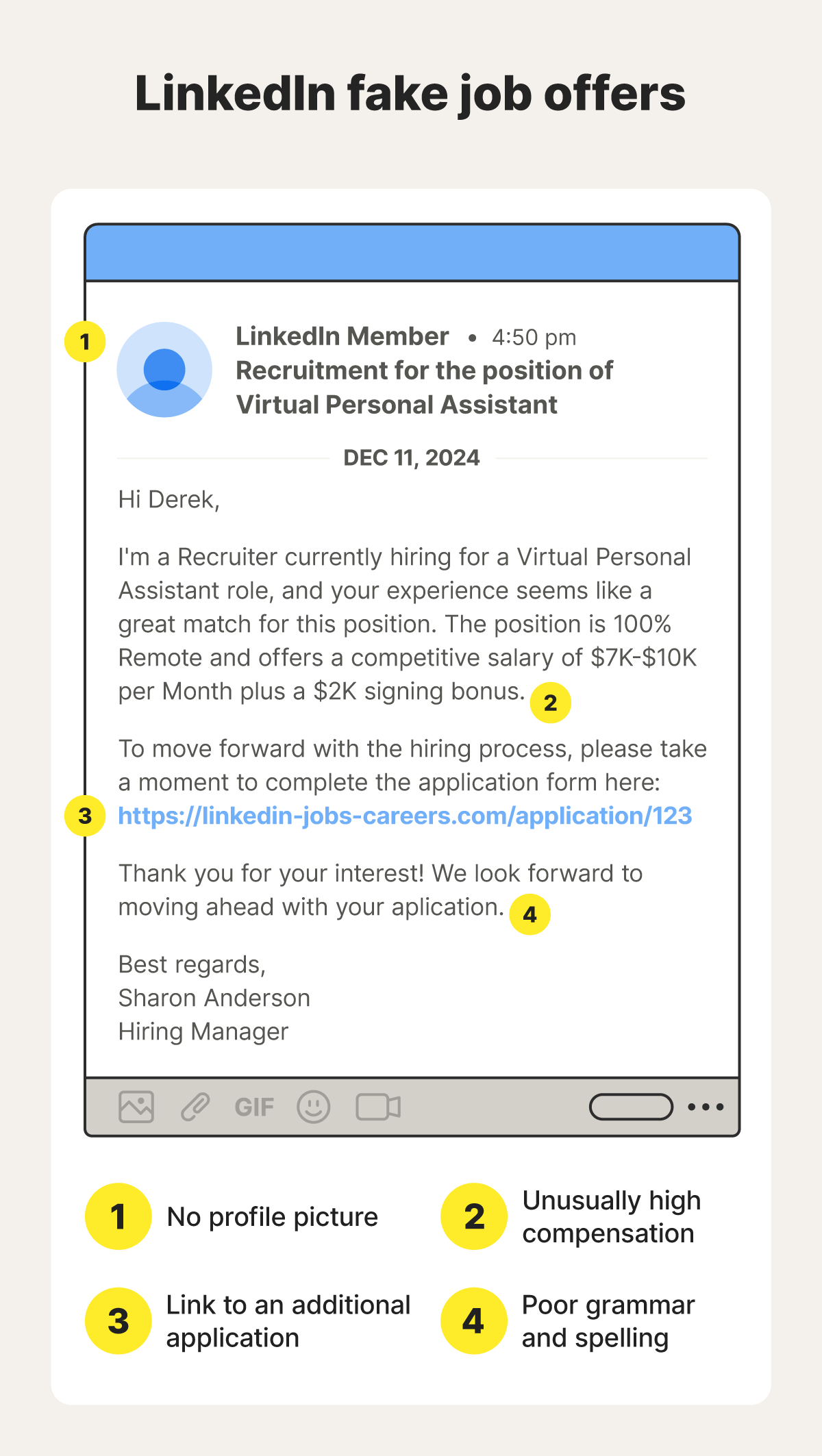
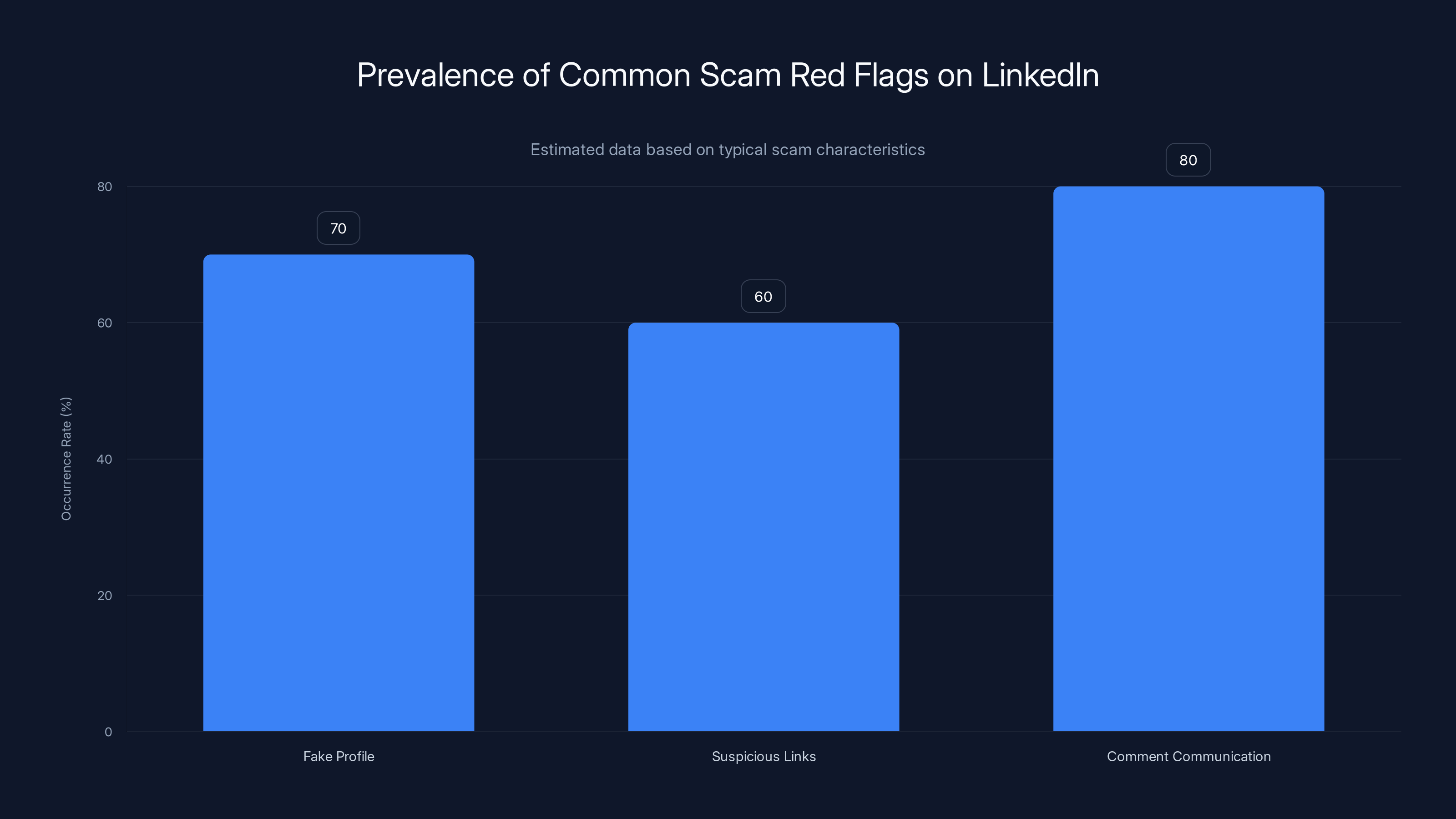
Estimated data suggests that 'Comment Communication' is the most prevalent red flag, occurring in 80% of scams, followed by 'Fake Profile' and 'Suspicious Links'.
How to Report These Scams
Reporting matters. Every report gives LinkedIn more data to identify and shut down these scam networks faster.
Report on LinkedIn
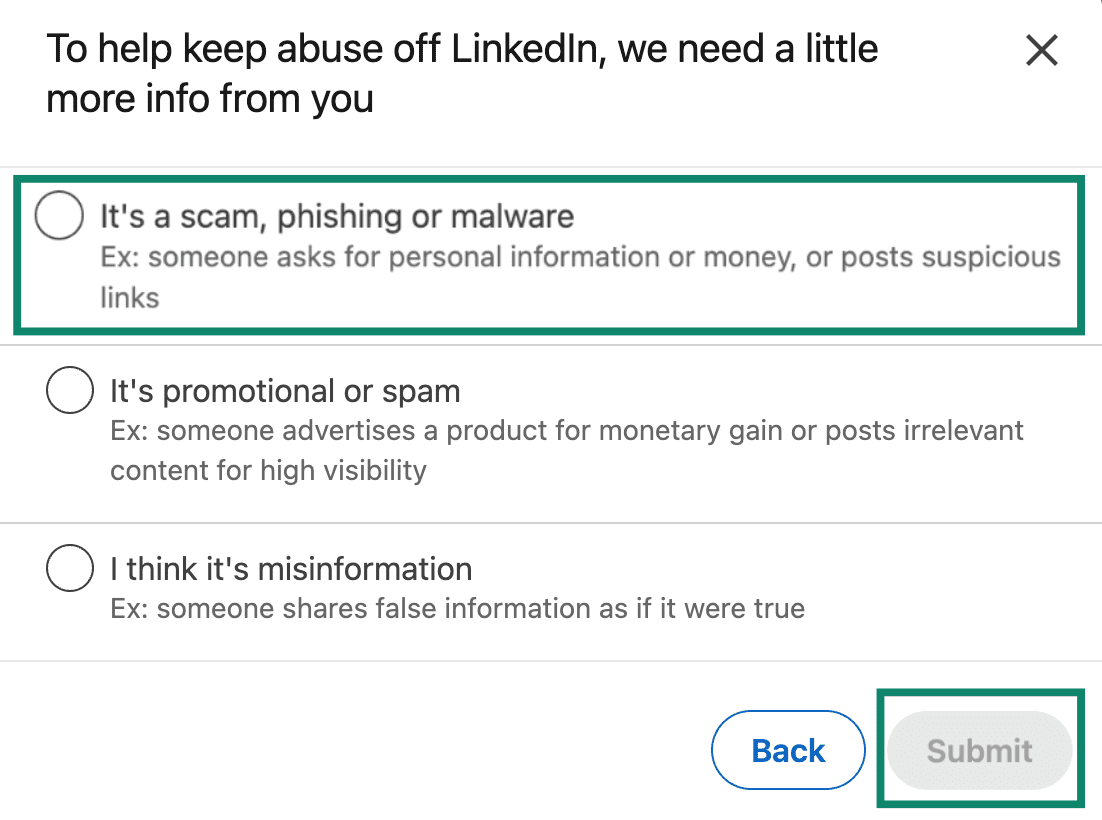
On the actual comment containing the phishing link, click the three dots (more options) > "Report comment." Choose "It's phishing, spam or abuse." LinkedIn will review it.
If you see a fake account, visit their profile and click the three dots > "Report profile." LinkedIn prioritizes reports of accounts impersonating their service.
Report to Authorities
If you've lost money or have been significantly compromised, report it to your country's cybercrime agency. In the US, that's the FBI's Internet Crime Complaint Center (IC3). In the UK, it's Action Fraud. Most countries have similar agencies.
Include details: the fake account name, the date of the phishing attempt, the link URL (if you didn't click it), and any evidence of compromise.
Report to Your Employer
If you work in a security or compliance role, report these attacks through internal channels. Aggregate data about phishing attempts can help your organization understand emerging threats.
What LinkedIn Is Doing (And What Remains Undone)
LinkedIn has acknowledged the campaign and stated they're working to stop it. Here's what that likely means in practice:
Account detection: LinkedIn's automated systems are looking for patterns associated with phishing accounts. Accounts with zero followers, accounts posting links to known phishing domains, accounts created in batches. When these patterns are detected, the accounts are suspended or limited.
Comment moderation: LinkedIn's moderation team (both automated and human) is reviewing reported comments and removing phishing content. However, this is reactive—they can only act after the comment is reported.
User notification: LinkedIn has publicly warned users about this specific campaign and reiterated their policy about never communicating account issues through comments.
Link filtering: LinkedIn is monitoring for links to known phishing pages and may automatically hide or warn about suspicious links in comments.
What remains insufficient:
Prevention: LinkedIn's moderation is still reactive. A phishing account can exist for hours and reach thousands of people before being removed. Proactive measures (like requiring new accounts to have some activity or verification before posting on large posts) could reduce this, but would also limit legitimate users.
Technical barriers: LinkedIn could add more friction to the phishing process. For example, links from accounts older than 30 days could be treated differently than links from brand new accounts. Accounts posting identical messages could be flagged. These technical measures could significantly reduce the success rate of these attacks.
User defaults: LinkedIn could default all users to the most restrictive comment privacy settings, requiring opt-in to see comments from unconnected accounts. This would be inconvenient for legitimate users, but would dramatically reduce exposure to phishing comments.
The reality is that platforms face a constant tension between user experience and security. Implementing stronger protections often means restricting functionality that legitimate users value. LinkedIn has to balance security with the openness that makes the platform useful.

The Broader Threat Landscape: LinkedIn Isn't Alone
LinkedIn comment phishing is part of a much larger trend. Professional networks and social platforms are becoming primary attack vectors.
Twitter/X: Attackers impersonate companies and individuals to direct followers to phishing pages. Verified accounts have been compromised to conduct massive phishing campaigns.
Facebook: Fake accounts run "job recruitment" scams, directing people to phishing pages or asking for upfront payments.
Instagram: Romance scams and investment scams originating from fake accounts have cost victims hundreds of millions.
TikTok: Misinformation and scam promotion spread rapidly due to the platform's algorithm.
The common thread: user trust is the vulnerability. Platforms are powerful because we trust the people and organizations on them. Attackers exploit that trust by impersonating trusted entities or creating convincing fakes.
As platforms become more central to how professionals communicate, work, and build relationships, they become increasingly valuable targets for attackers.

Future-Proofing Your Security Against Evolving Threats
Attackers evolve. What works today won't work tomorrow. They'll get better at impersonating legitimate accounts. They'll find new ways to create urgency. They'll develop more convincing fake login pages.
How do you protect yourself against threats that haven't been invented yet?
Principle 1: Assume nothing is authentic until verified through independent channels. Don't assume a link is safe because it appears on LinkedIn or comes from someone with a lot of followers. Always verify through official channels.
Principle 2: Understand the attacker's goals. Attackers want your credentials, your data, or your access to systems. Recognize when someone is asking for something that fits those categories, even if they're not explicitly asking for passwords.
Principle 3: Adopt zero-trust thinking. Treat every message, every link, and every request as potentially dangerous until you've verified it. This sounds paranoid, but it's increasingly the standard in security organizations.
Principle 4: Keep learning. Security threats change monthly. Subscribe to security newsletters, follow cybersecurity experts, and stay informed about new attack tactics. Your knowledge is your best defense.
Principle 5: Use security tools effectively. Password managers, authenticator apps, and VPNs aren't perfect, but they raise the cost of attacking you. Most attackers prefer easier targets. Make yourself a harder target.
The Human Element: Why Awareness Beats Technology
Here's something that might surprise you: technology alone won't solve this problem.
LinkedIn has sophisticated security systems. They have machine learning algorithms analyzing millions of comments. They have security researchers detecting new phishing techniques. They have legal teams pursuing attackers. Yet phishing campaigns still succeed.
Why? Because people still click.
The most effective defense against phishing is human awareness. A person who understands the threat, thinks critically before clicking, and verifies requests through official channels is nearly impossible to phish.
Conversely, even the best security systems can't stop someone who ignores all warnings and enters their password on a fake login page.
This is why security training and awareness are so important. They're not optional extras. They're fundamental.
The good news: awareness is learnable. You don't need to be technically sophisticated to avoid phishing. You just need to slow down, think critically, and verify. Most people who fall for phishing attacks aren't stupid. They're just in a hurry and not thinking about security in that moment.
Create a personal habit: Before clicking any link or providing any information, pause for 10 seconds and ask yourself: "Could this be a scam? How would I verify this is legitimate?" That 10-second pause catches most phishing attempts.

Case Study: How a Real Attack Unfolded (Anonymized)
Let's walk through a real example to make this concrete.
A recruiter at a Fortune 500 tech company (let's call her Sarah) was on LinkedIn looking at job postings—she wasn't actually job hunting, but liked to stay aware of market activity. She saw a post about leadership opportunities that seemed relevant to her interests.
The post had hundreds of comments. One comment looked like it was from someone claiming to represent the company, saying: "Verify your background before applying by clicking the link below." The link looked legitimate because it was shortened using LinkedIn's URL shortener.
Sarah didn't think much about it. She clicked.
She was taken to a page that looked almost identical to LinkedIn's login. It asked her to confirm her email and password. She entered them. The page showed an error: "Invalid login." She tried again with the same result. Annoyed, she went back to LinkedIn and checked her email. Everything seemed fine.
She forgot about it.
Three days later, Sarah's IT department called her. Someone had attempted to access her company's employee database from her account. She hadn't done this. Her heart sank. She'd been phished.
What happened:
- Attackers got her LinkedIn password
- They attempted to log into her account from an IP address in Eastern Europe
- LinkedIn's systems flagged this unusual login and required additional verification
- The attackers tried to access Sarah's company network using her credentials
- Her company's security systems blocked it, but her account was flagged
- Her password had to be reset across multiple systems
- Her account was monitored for 30 days for additional suspicious activity
- Her emails were reviewed to see if she'd shared sensitive information
Sarah was lucky. The attackers were blocked before they accessed anything valuable. But she spent two days dealing with incident response, changed passwords on 10 systems, and her professional reputation had to be investigated to make sure she wasn't deliberately leaking information.
All because she clicked a phishing link in a LinkedIn comment.
This happens thousands of times per day. Most victims aren't as lucky as Sarah.
Making This Real: Action Items You Can Take Today
Knowledge without action is useless. Here are specific things you can do right now to protect yourself.
In the next 15 minutes:
- Go to LinkedIn Settings > Account > Login and security
- Enable two-factor authentication
- Set your password to something unique and strong (use a password manager)
In the next hour:
- Review your recent login activity in LinkedIn
- Check if your email address has been breached at haveibeenpwned.com
- Change your password on any platform where you reused the password
This week:
- Install a password manager if you don't have one (Bitwarden is free)
- Set up login notifications on your LinkedIn account
- Add a recovery phone number and backup email to your account
- Watch a 10-minute video on phishing awareness
This month:
- Run a security audit of all your online accounts
- Identify which passwords are weak or reused
- Update them to unique, strong passwords
- Enable 2FA on your email account (this is critical)
- Audit your LinkedIn privacy settings and limit who can see your information
These steps won't make you invincible, but they'll make you significantly harder to attack than the average person. Most attackers go after easy targets. Make yourself a harder target, and they'll likely move on.
FAQ
What exactly is a LinkedIn comment phishing scam?
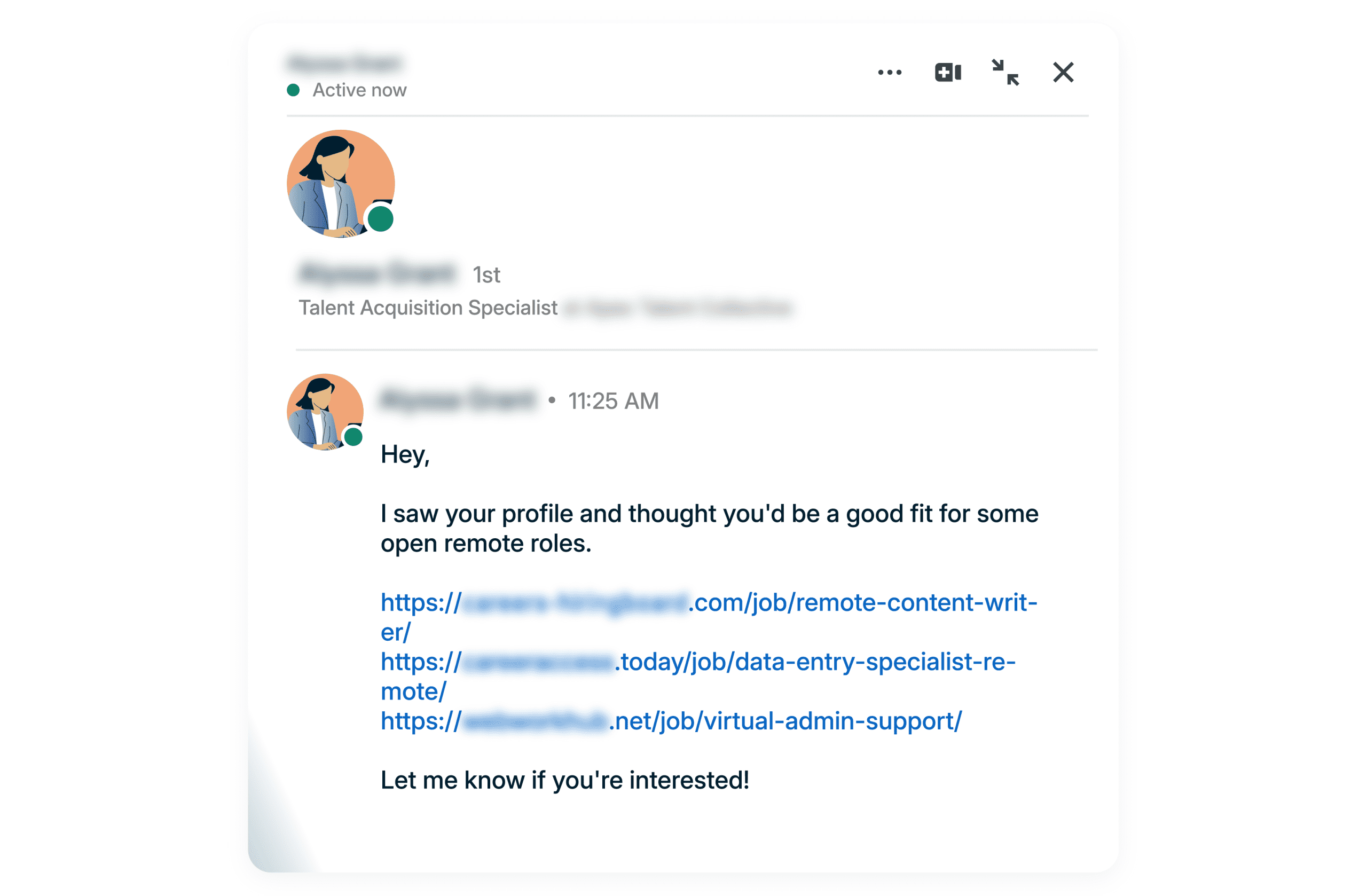
A LinkedIn comment phishing scam is when attackers create fake accounts and post comments on popular LinkedIn posts claiming your account has been locked or suspended. These comments include links to fake login pages designed to steal your credentials. The attackers are betting you'll panic and click without thinking, giving them your email and password, which they can then use to access your real account and steal information or impersonate you.
How can I tell if a LinkedIn comment is a phishing attempt?
Look for several red flags: the account posting the comment has zero followers and no activity history, the link points to a non-LinkedIn domain like netlify.app or herokuapp.com, the message creates artificial urgency with phrases like "act immediately," and the profile picture looks like it was stolen. Most importantly, remember that LinkedIn never communicates account issues through public comments. If you see any of these signs, it's almost certainly a scam.
What should I do if I accidentally clicked a phishing link?
Don't panic. Clicking the link itself doesn't compromise you—what matters is whether you entered your credentials. If you did enter your password, immediately change your LinkedIn password from a different device, and change the password on any other sites where you used the same password. Enable two-factor authentication. Review your LinkedIn account activity for suspicious logins. If you work for a company with IT support, contact them and let them know about the incident. Monitor your accounts for unusual activity.
Can LinkedIn verify accounts to prevent fake profiles from posting?
LinkedIn could implement stronger verification, but it would add friction for legitimate users. The platform does have some automated detection for fake accounts, but determining which accounts are real and which are fake is genuinely difficult at scale. Some mitigations LinkedIn has discussed include requiring new accounts to wait before posting on public posts, limiting the reach of comments from brand new accounts, and flagging accounts with suspicious characteristics. However, these measures would also affect legitimate new users.
Is my company data at risk if I get phished?
It depends on what information you have access to and what you've shared on LinkedIn. If you've mentioned clients, projects, or sensitive company initiatives on your profile, that information is now exposed. If an attacker gains access to your LinkedIn account, they can impersonate you to your professional contacts and potentially conduct business email compromise scams targeting your company. If you have significant access to company systems or confidential information, a compromised LinkedIn account could be a stepping stone to more serious breaches. Always assume that if one account is compromised, attackers will try to use it to access your work systems.
Do I need to use a VPN to protect myself from LinkedIn phishing?
A VPN (virtual private network) helps protect your data in transit, but it doesn't prevent phishing attacks. Phishing works regardless of whether you're using a VPN because the attack happens at the application level, not the network level. A VPN is useful for general security on public Wi-Fi, but for phishing protection specifically, two-factor authentication, unique passwords, and awareness are much more important.
How often do these LinkedIn comment phishing campaigns happen?
LinkedIn comment phishing is increasingly common, but it's hard to get exact numbers because most people don't report their phishing attempts. Security researchers have documented multiple coordinated campaigns in 2024 and 2025. What's clear is that as LinkedIn's value as a professional network increases, it becomes a more attractive target for attackers. These campaigns will likely continue and evolve as attackers refine their tactics.
Can I get my account back if it's been compromised?
Yes, but it's easier if you act quickly. If you suspect your account is compromised, change your password immediately from a different device. LinkedIn allows you to log out of all sessions, which will force the attacker out. If you've lost access entirely (because the attacker changed your password), use LinkedIn's "Forgot password" option to reset it via email. If that doesn't work, contact LinkedIn support. Have identification ready to prove you own the account. Recovery is usually possible, but the sooner you act, the better.
Should I delete my LinkedIn account to avoid phishing?
Deleting your LinkedIn account would eliminate this particular risk, but for most professionals, LinkedIn is valuable enough that the risk is worth taking—as long as you take protective measures. Instead of deleting, focus on securing your account with strong passwords, two-factor authentication, limited profile information, and awareness. If you do use LinkedIn, treat it as any other valuable account: protect it like you'd protect your bank account.

Final Thoughts: Security Is a Mindset
Phishing attacks succeed because they exploit a gap between awareness and reality. People know phishing exists in theory, but they don't expect it to target them specifically. They're in a hurry. They're distracted. They see something from an apparent authority figure, and their critical thinking takes a back seat.
The fix isn't complicated, but it does require a mindset shift. You need to approach every unexpected link, every request for information, and every claim of authority with healthy skepticism.
This isn't paranoia. It's recognition that you're a valuable target. Your professional network is valuable. Your access to company systems is valuable. Your identity is valuable. Attackers know this, and they're actively trying to compromise you.
But here's the empowering part: you control whether they succeed. A 10-second pause before clicking. A habit of verifying through official channels. Enabling two-factor authentication. These simple actions make you dramatically harder to attack.
LinkedIn will continue to improve its security. Attackers will continue to evolve their tactics. But your personal security practices—your awareness, your habits, your skepticism—are the constant. That's your real defense.
The next time you see a suspicious comment on LinkedIn, don't click. Pause. Verify. Report. You'll protect yourself, and you'll help LinkedIn combat the entire ecosystem of phishing attacks. Security is a shared responsibility. Your actions matter.

Key Takeaways
- LinkedIn comment phishing attacks use fake accounts to post messages claiming account suspension, directing users to fake login pages that harvest credentials
- Red flags include zero-follower accounts, links pointing to non-LinkedIn domains like netlify.app, and messages creating artificial urgency—LinkedIn never communicates policy violations through comments
- Immediate compromise after credential theft includes password changes, lateral movement attempts to company systems, and impersonation of the victim to their professional network
- Layered security defense requires technical controls (2FA, unique passwords), behavioral controls (skepticism of unsolicited links), and ongoing awareness training
- Organizations must implement employee training, update security policies, deploy URL filtering tools, and create rapid incident response procedures for phishing attacks
Related Articles
- Instagram Password Reset Emails: What You Need to Know [2025]
- Instagram Password Reset Incident: What Really Happened [2025]
- Instagram Password Reset Email Bug: What Happened and What You Need to Know [2025]
- Internal Message Spoofing Phishing Campaign: How to Stop It [2025]
- Blue Screen of Death Malware: How ClickFix Attacks Work [2025]
- WhatsApp Security Features: Complete Privacy Guide [2025]
![LinkedIn Comment Phishing: How to Spot and Stop Malware Scams [2025]](https://tryrunable.com/blog/linkedin-comment-phishing-how-to-spot-and-stop-malware-scams/image-1-1768412217259.jpg)



