Why Mac Security Matters More Than Ever [2025]
You might think Macs are immune to malware. That's a dangerous assumption.
For years, the myth persisted: "Macs don't get viruses." It made sense at the time. Back in the early 2000s, macOS had such a small market share that hackers largely ignored it. Why spend time targeting 5% of computers when Windows dominated 95%?
That changed. Hard.
In recent years, malware targeting macOS has exploded. According to Macworld, between 2020 and 2024, Mac malware detections increased by over 400%, according to security research firms tracking threat landscapes. Adware, spyware, cryptominers, and ransomware now actively target Apple users. The platform's popularity made it a lucrative target. More Macs in the wild meant more potential victims.
Here's what most Mac users don't realize: macOS comes with built-in protections, but they're not enough. Apple's native defenses like XProtect and Gatekeeper help, but they lag behind threats by design. They work passively, scanning known malware signatures. Modern threats? They use polymorphic techniques that change their code constantly to avoid detection.
The stakes are high. A compromised Mac can leak financial data, steal passwords, compromise your identity, or turn your machine into a bot for attacking other systems. Worse, you might never know it's happening. Modern malware often runs silently in the background, siphoning data without any obvious symptoms.
That's why real-time protection matters. That's why security tools exist. And that's why understanding your options isn't paranoid—it's practical.
This guide breaks down everything you need to know about protecting your Mac in 2025. We'll cover how threats work, what built-in protections you already have, which additional tools actually help, and the exact steps to implement a complete security strategy. By the end, you'll understand not just what to do, but why you're doing it.
TL; DR
- Mac malware is real: Threats targeting macOS increased 400% since 2020, making protection essential.
- Native protections exist but are limited: XProtect and Gatekeeper provide passive defense, not active threat hunting.
- Real-time scanning prevents infections: Active monitoring catches threats before they execute, not after.
- Privacy and security are different: Malware protection stops harmful code; privacy tools prevent data harvesting.
- Layered approach works best: Combining built-in tools with third-party protection creates the strongest defense.
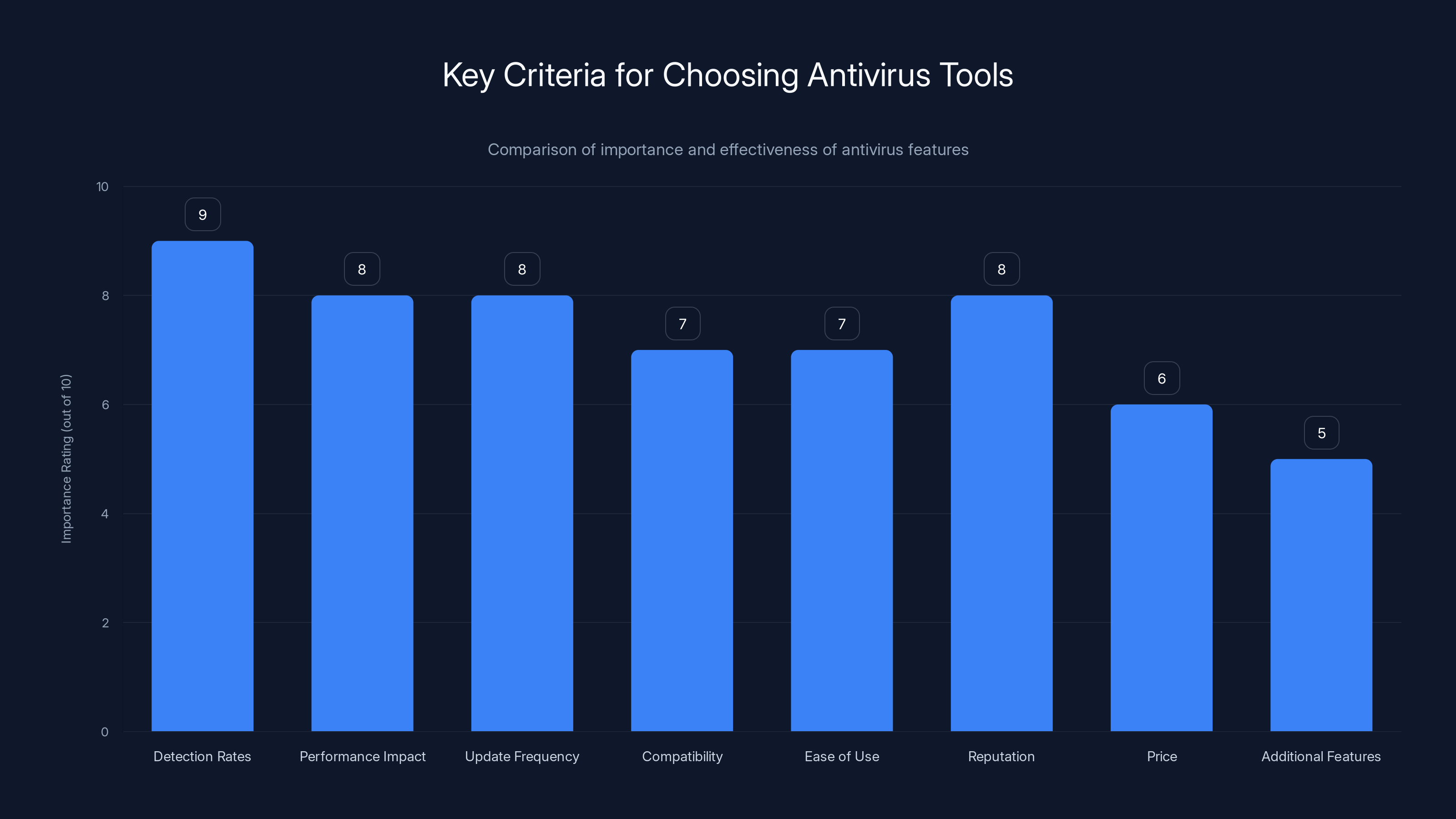
Detection rates and performance impact are the most crucial factors when choosing antivirus tools, followed closely by update frequency and reputation. Estimated data based on typical user priorities.
Understanding Mac Malware: How Threats Actually Work
Before we talk about defense, you need to understand the enemy.
Mac malware isn't monolithic. There are several distinct categories, each requiring different detection strategies. Understanding what you're actually defending against changes how you approach protection.
Trojans and backdoors are the most dangerous. These masquerade as legitimate applications or files. You download what looks like a game, productivity tool, or system update. Once installed, they give attackers remote access to your machine. From there, they can install additional malware, steal files, monitor keystrokes, or use your Mac to attack other systems. The classic example: a trojan bundled with a cracked version of professional software.
Adware and potentially unwanted programs (PUPs) are more common but less catastrophic. These get bundled with legitimate software during installation. Accept the default setup options, and suddenly your browser has new toolbars, search results are hijacked, and you see pop-up ads everywhere. Technically, you "agreed" to it. Practically, nobody reads those terms.
Spyware silently monitors your activity. It captures passwords, sees what you type, tracks which websites you visit, and sometimes accesses your camera or microphone. It's insidious because you feel no symptoms. Your Mac runs fine. Performance doesn't noticeably degrade. But your privacy is being harvested.
Cryptominers are a special kind of parasite. They use your Mac's processing power to mine cryptocurrency without your permission. Your CPU runs at 100%, your fan never stops spinning, your Mac heats up, and your electricity bill increases. Meanwhile, someone else profits from the computational work your hardware is doing.
Ransomware encrypts your files and demands payment for the decryption key. This was rare on macOS until recently, but it's becoming more common. You wake up to a message saying your files are locked and you need to pay Bitcoin to get them back. Without the key, your files are genuinely inaccessible.
How do these get on your Mac? Usually through several vectors:
Malicious downloads from untrusted websites are the most common entry point. A website promises free software, a cracked version of professional tools, or a utility that will "clean" your Mac. You download and run it. Boom. Infected.
Email attachments remain surprisingly effective. A phishing email claims to be from your bank, Apple, your workplace, or a service you use. The attachment contains malware. You open it thinking it's urgent. The infection happens instantly.
Watering hole attacks compromise legitimate websites you already trust. You visit a site you've been to a hundred times. Unbeknownst to the site owner, attackers have injected malicious code. Your browser executes it. Again, infected.
Software supply chain attacks hit the source. Attackers compromise the update mechanism of a legitimate application or inject malware into an open-source library that thousands of developers depend on. When you update, you unknowingly download the compromised version.
Social engineering exploits human psychology. You get a call claiming to be Apple support. They say there's suspicious activity on your account. They guide you through steps that actually give them remote access. Or you receive a message that your password has been exposed and you need to click a link to "verify" it. That link goes to a fake login page that steals your credentials.
The reason this matters: different attack vectors require different defenses. Real-time scanning catches malware in files and email. Firewall rules block network-based attacks. Two-factor authentication prevents credential-based takeovers. Phishing awareness prevents social engineering. No single tool catches everything. That's why layers matter.
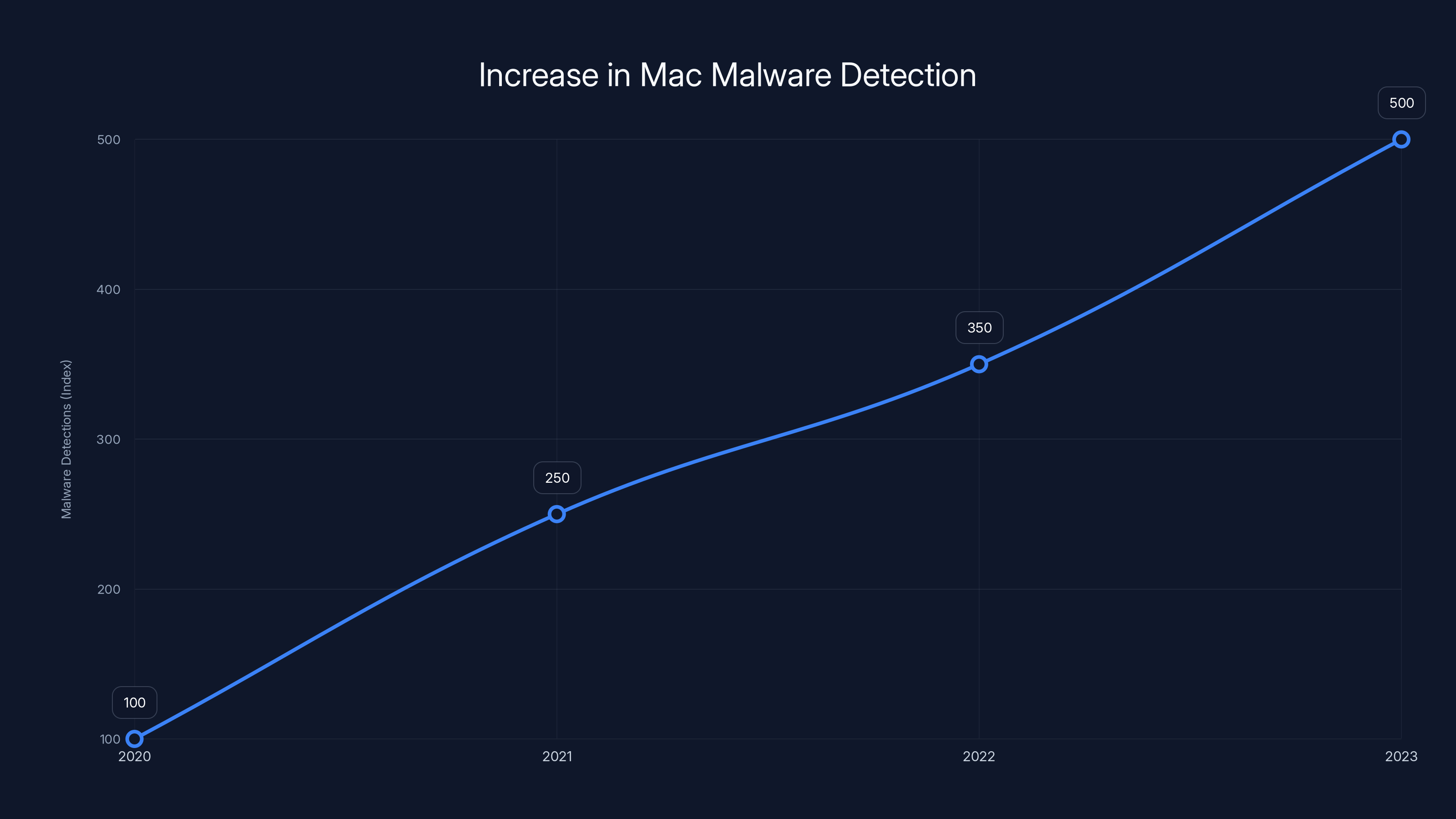
Mac malware detection has increased over 400% since 2020, highlighting the growing need for antivirus protection on macOS. Estimated data.
Built-In Mac Security: What You Already Have
Apple baked protections directly into macOS. These are your first line of defense.
XProtect is Apple's built-in malware detection engine. It's been part of macOS for over a decade, running invisibly in the background. XProtect works by scanning files against a database of known malware signatures. When you download a file or run an application, XProtect checks it. If it matches a known threat signature, the file is quarantined or blocked.
The catch? XProtect is signature-based. It knows about threats that are already catalogued. New malware variants, polymorphic threats that constantly change their code, and sophisticated zero-day exploits? XProtect doesn't catch those. It's reactive defense, not proactive.
Gatekeeper controls what software you can run. Out of the box, macOS only allows you to run applications from the Mac App Store or applications signed by verified developers. When you download an unsigned or untrusted app, Gatekeeper warns you. This creates friction, which deters many casual users from installing sketchy software.
But determined attackers work around Gatekeeper. They get legitimate developer certificates, sign malicious code, and distribute it. Or they convince users to override Gatekeeper warnings ("Just click 'Open Anyway'" is common advice on infected websites).
File Vault encrypts your hard drive at rest. If your Mac is stolen, the thief can't access your files without your password. But File Vault doesn't prevent malware from running on your system while it's unlocked. It's data protection, not security.
Secure Boot and System Integrity Protection (SIP) prevent unauthorized modifications to core system files. Attackers can't easily modify the operating system itself or install kernel-level malware. This is genuinely strong protection, raising the bar for attackers significantly.
Firewall (available in System Settings under Security & Privacy) blocks unsolicited incoming connections. It doesn't prevent your applications from connecting outbound to the internet, so it won't stop malware from calling home. But it helps prevent remote access attacks.
Where's the gap? None of these catch sophisticated malware that spreads through non-traditional means. If you download what appears to be a legitimate application from a website (not the Mac App Store), XProtect and Gatekeeper might miss it. If malware is bundled with legitimate software, the entire package passes through.
This is why security researchers recommend additional protection. Your built-in defenses are good. They're not complete.
Real-Time Antivirus Protection: How It Works
Third-party antivirus and security tools add a crucial layer: real-time scanning.
Here's the fundamental difference. XProtect scans files when you download them or run them. That's good. But there's a lag. If malware is bundled cleverly, or if it arrives through an unexpected vector, there's a window of vulnerability.
Real-time antivirus protection watches your entire system continuously. It monitors file access, process execution, and network traffic. When malware tries to run, the security tool catches it immediately—before it can do damage.
The mechanics are straightforward:
File scanning watches your Downloads folder, Desktop, and other common locations. When a file appears, it's scanned against threat databases. Modern tools use multiple detection engines, not just signature matching. Heuristic analysis looks at file behavior and structure. Machine learning models detect suspicious patterns. If a file looks like malware—even if it's never been seen before—the tool quarantines it.
Process monitoring watches what applications do once they're running. Does an application suddenly try to access your password vault? Unusual. Does it attempt to modify system files? Suspicious. Is it creating network connections to known malicious servers? Definitely block it. Real-time tools can terminate processes that behave maliciously.
Email protection scans attachments before you open them. Phishing emails try to get you to click links or run attachments. A security tool intercepts them, scans them, and warns you if they're dangerous.
Browser protection watches for malicious websites. If you're about to visit a site hosting malware, a security tool can warn you or block it automatically.
Behavioral analysis watches how applications interact with your system. A legitimate application behaves predictably. It reads and writes files in expected locations, makes network connections to known servers, uses reasonable amounts of CPU and RAM. Malware behaves oddly. It might try to access files it has no business touching, establish connections to suspicious servers, or consume excessive resources. Tools can detect these anomalies.
The tradeoff is performance. Real-time scanning requires constant monitoring. It uses CPU, RAM, and disk I/O. On a modern Mac with an SSD and multiple cores, the performance impact is minimal—maybe 2-5% CPU overhead. On older machines, it's more noticeable.

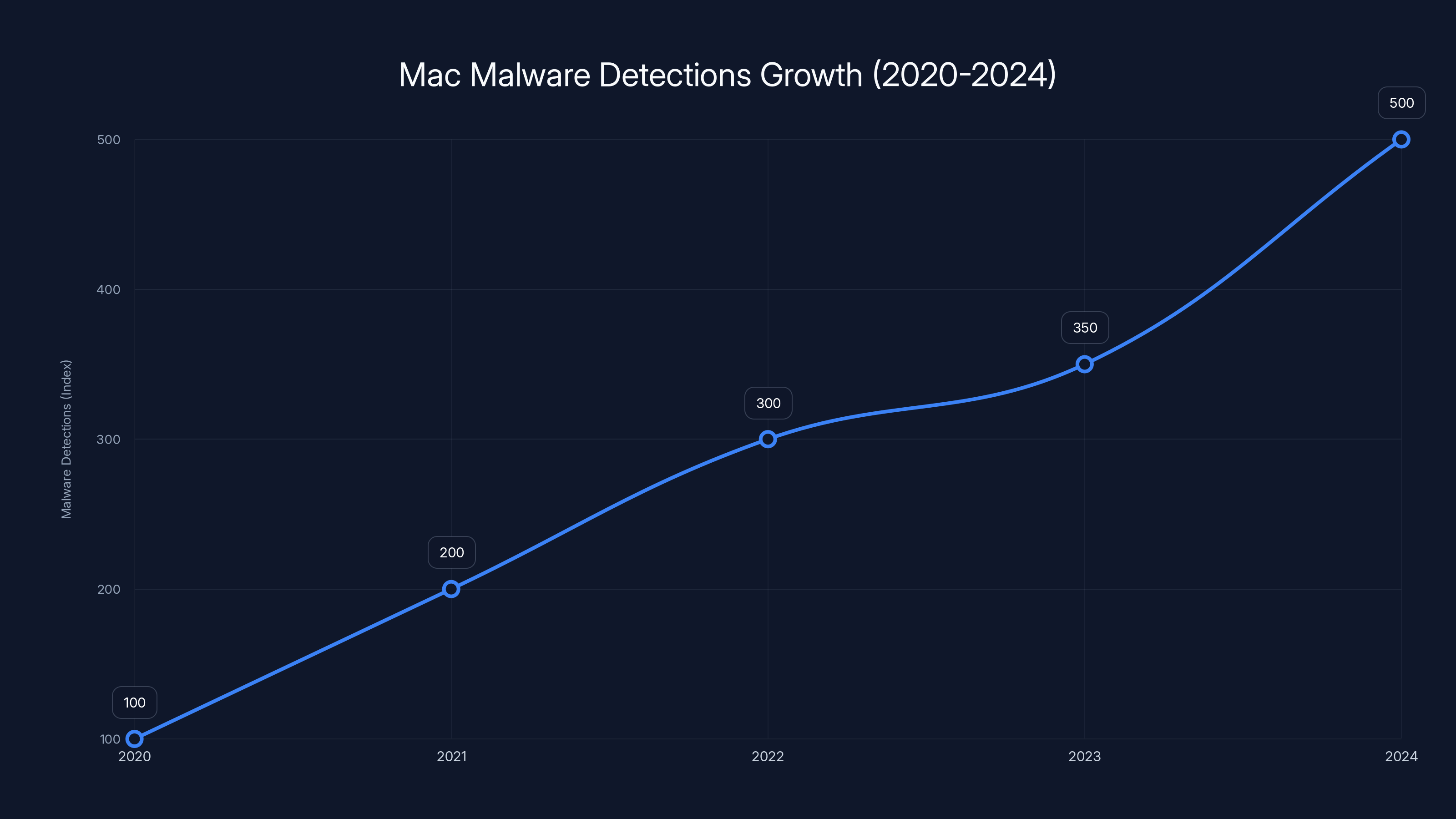
Mac malware detections increased by over 400% from 2020 to 2024, highlighting the growing threat to macOS users. Estimated data.
Privacy vs. Security: Understanding the Difference
Here's where people get confused. Security and privacy are related but distinct.
Security is about protecting your system from unauthorized access and malicious code. Does malware run on your Mac? Can attackers take control remotely? Can viruses spread from your system? That's security.
Privacy is about protecting your personal information from being collected, tracked, or sold. Does your ISP see what websites you visit? Can advertisers track you across the internet? Do companies harvest your data? That's privacy.
They overlap in important ways. Malware can violate privacy by harvesting your data. Weak privacy practices can enable attackers to phish you more effectively. But they're not the same thing.
A Mac can be technically secure—no malware, no unauthorized access—but have zero privacy if you're connecting to an ISP that sells browsing data, using services that harvest personal information, and leaving your location services on constantly.
Conversely, a Mac can be private but insecure if you haven't patched security vulnerabilities and you're not running protection against malware.
Effective protection requires addressing both:
For security: Install real-time antivirus protection. Keep macOS updated. Enable File Vault. Use strong passwords. Don't disable security warnings.
For privacy: Use a VPN for public Wi-Fi. Disable tracking in browser settings. Review application permissions. Consider privacy-focused browsers and email providers. Minimize data shared with third parties.
Many security tools now offer both. They protect against malware (security) and offer VPN, tracker blocking, and encrypted email (privacy). But understand that you're buying two different services with one tool.
Choosing the Right Protection: What to Look For
Not all antivirus tools are created equal. Here's what matters:
Detection rates matter most. Does it actually catch malware? Security labs like AV-TEST and Gartner regularly test antivirus tools. Look for solutions with detection rates above 95% for known threats. For zero-day and unknown threats, look for heuristic and behavioral detection capabilities.
Performance impact is your second criterion. A tool that catches 100% of malware but makes your Mac unusable is worthless. Test the tool before committing. Does your Mac still feel snappy? Can you work without constant spinning wheels? If not, it's not worth it.
Update frequency determines how quickly you're protected against new threats. Tools that update signatures weekly are better. Tools that update daily are much better. Tools with automatic, real-time updates without user intervention are best.
Compatibility with your macOS version matters. Newer tools might not support older OS versions. Older tools might have bugs on the latest macOS. Check compatibility before buying.
Ease of use shouldn't be underestimated. A complex tool you never configure properly is less useful than a simple tool you understand and trust. Look for intuitive interfaces. Can you understand what's happening? Can you make decisions without a PhD in security?
Reputation and trust matter. Is the company reputable? Do independent reviews recommend it? Has the company had security breaches of its own (which would be embarrassing)? Can you find unbiased reviews from real users?
Price varies widely. Some tools are free. Some cost $100+ per year. More expensive doesn't always mean better. Free tools can be excellent. Expensive tools can be bloatware. Focus on value: what are you getting for the price?
Additional features like VPN, password managers, identity theft monitoring, or encrypted storage might justify higher prices. But you're also increasing your attack surface—more features mean more code, more code means more potential vulnerabilities. Simplicity has value.
Support quality matters when something goes wrong. Can you contact support? Do they respond quickly? Can they actually help? Read reviews about customer support before buying.

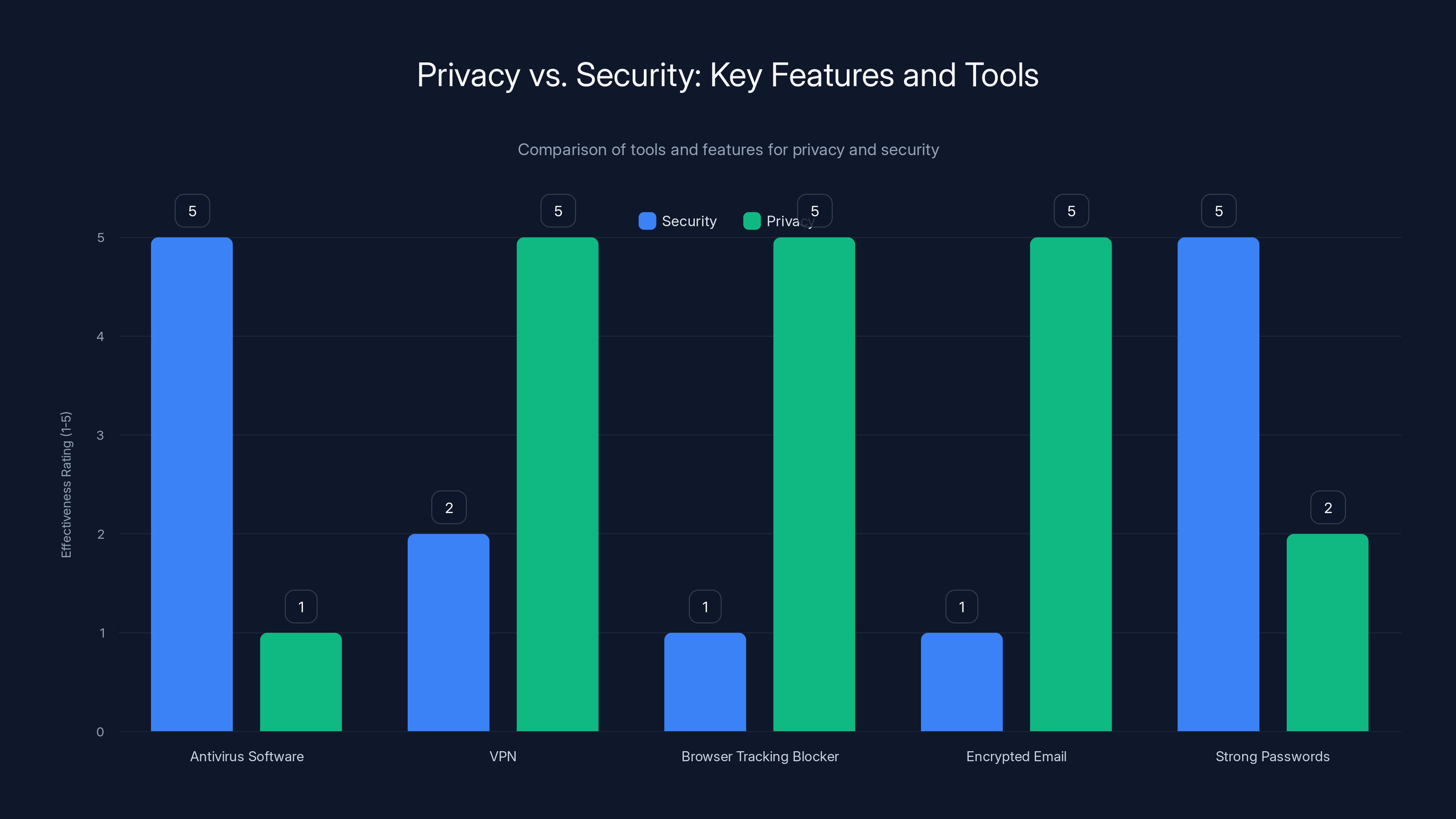
Antivirus software and strong passwords are crucial for security, while VPNs and encrypted email enhance privacy. Many tools offer dual benefits.
Step-by-Step: Implementing Complete Mac Security
Let's build a practical security strategy from the ground up.
Step 1: Update everything immediately. Check System Settings > General > Software Update. Install every pending update. Update your applications from the App Store or their developers. Don't skip security updates just because they inconvenience you. Most malware exploits known vulnerabilities. Patching closes those doors.
Step 2: Enable built-in protections. Open System Settings > Privacy & Security. Verify that File Vault encryption is enabled. Check that Secure Boot is enabled (this is typically on by default, but confirm). Enable the firewall. These are free and effective.
Step 3: Review application permissions. In System Settings > Privacy & Security, scroll through each permission category (Camera, Microphone, Location, Contacts, etc.). Disable access for applications that don't need it. An email application doesn't need camera access. A PDF reader doesn't need location data. Principle of least privilege: only grant the permissions applications actually need.
Step 4: Install real-time antivirus protection. Research options. Test a trial version if available. Install your chosen tool. Run a full system scan immediately. Configure it to scan on access (real-time scanning). Verify it's running—check the menu bar or system settings for confirmation.
Step 5: Set strong passwords and enable two-factor authentication. Change your Apple account password to something strong (16+ characters, mixed case, numbers, symbols). Enable two-factor authentication on your Apple ID. Do the same for critical accounts (email, banking, work). Strong passwords and 2FA prevent account takeovers even if malware steals your credentials.
Step 6: Configure your browser securely. In Safari, Privacy tab, enable "Prevent cross-site tracking" and "Block all cookies" (or "Only essential" if you need tracking for websites to function). Disable browser extensions you don't use. Extensions have extensive system access; keep them minimal. Consider using a privacy-focused browser like Firefox with enhanced tracking protection.
Step 7: Be skeptical of downloads. Only download software from official sources (the Mac App Store, official websites, reputable developers). Avoid torrents, cracking sites, and suspicious forums. When you download something, your security tool should scan it. Review warnings carefully. If your antivirus warns you, believe it.
Step 8: Back up your data. Use Time Machine to create automatic hourly backups to an external drive. Or use a cloud backup service like iCloud, Backblaze, or Arq. If malware or ransomware hits, you can restore from backup. Without backups, a ransomware attack is catastrophic.
Step 9: Create a separate user account for potentially risky activities. If you download a lot of files, test applications, or use sketchy websites, use a dedicated user account for those activities. If something gets infected, your main account remains clean.
Step 10: Monitor system activity regularly. Open Activity Monitor (Applications > Utilities > Activity Monitor). Look for unfamiliar processes running, especially those using significant CPU, RAM, or network bandwidth. Research any process you don't recognize. Quit suspicious processes. Don't dismiss system activities without investigation—many malware processes use legitimate-sounding names.
Common Threats You Should Know About
Understanding specific threats helps you recognize and avoid them.
Adware and PUPs are the most common threats Mac users encounter. You'll notice browser redirects, unexpected toolbars, or intrusive pop-ups. The remedy: uninstall the suspicious application. Remove browser extensions you don't remember installing. Reset your browser to default settings.
Cryptominers drain your battery, cause your Mac to run hot, and slow performance. If your Mac fans are constantly running and your activity monitor shows unfamiliar processes, you might be infected. These are hard to find manually but trivial for antivirus tools to detect and remove.
Fake antivirus pop-ups are a classic scam. A website or ad shows an alarming pop-up claiming your Mac is infected and you need to install their tool. Don't. It's malware. Ignore the pop-up (usually a force-quit from the browser gets rid of it) and move on.
Phishing emails claim to be from Apple, your bank, or a service you use. They request you click a link to "verify" something or "confirm" your account. The link goes to a fake website that steals your login credentials. Never click links in unexpected emails. Instead, go directly to the official website by typing the URL yourself.
Mac cleaning tool scams promise to optimize your Mac, clean up junk, or improve performance. Some are legitimate tools. Many are scams that either do nothing or install malware. Unless you have specific problems, you don't need these tools. macOS handles its own cleanup fairly well.
Ransomware is becoming more prevalent. Your files get encrypted and you're asked to pay for the decryption key. Prevention is critical (backups, updates, antivirus). If it happens, restore from backup if you have one. Paying ransom doesn't guarantee you get your files back. Law enforcement discourages it.
Supply chain attacks hit legitimate software. Developers' accounts get compromised, updates get infected, or legitimate libraries get poisoned. You can't always prevent these. Update from official sources only. Monitor suspicious behavior from legitimate applications. Use application sandboxing when available.
Trojanized applications masquerade as legitimate tools. A "screen recording tool" is actually malware. A "system optimizer" steals data. The only real defense: only download from trusted sources, read reviews from multiple sources, and let your antivirus scan everything.
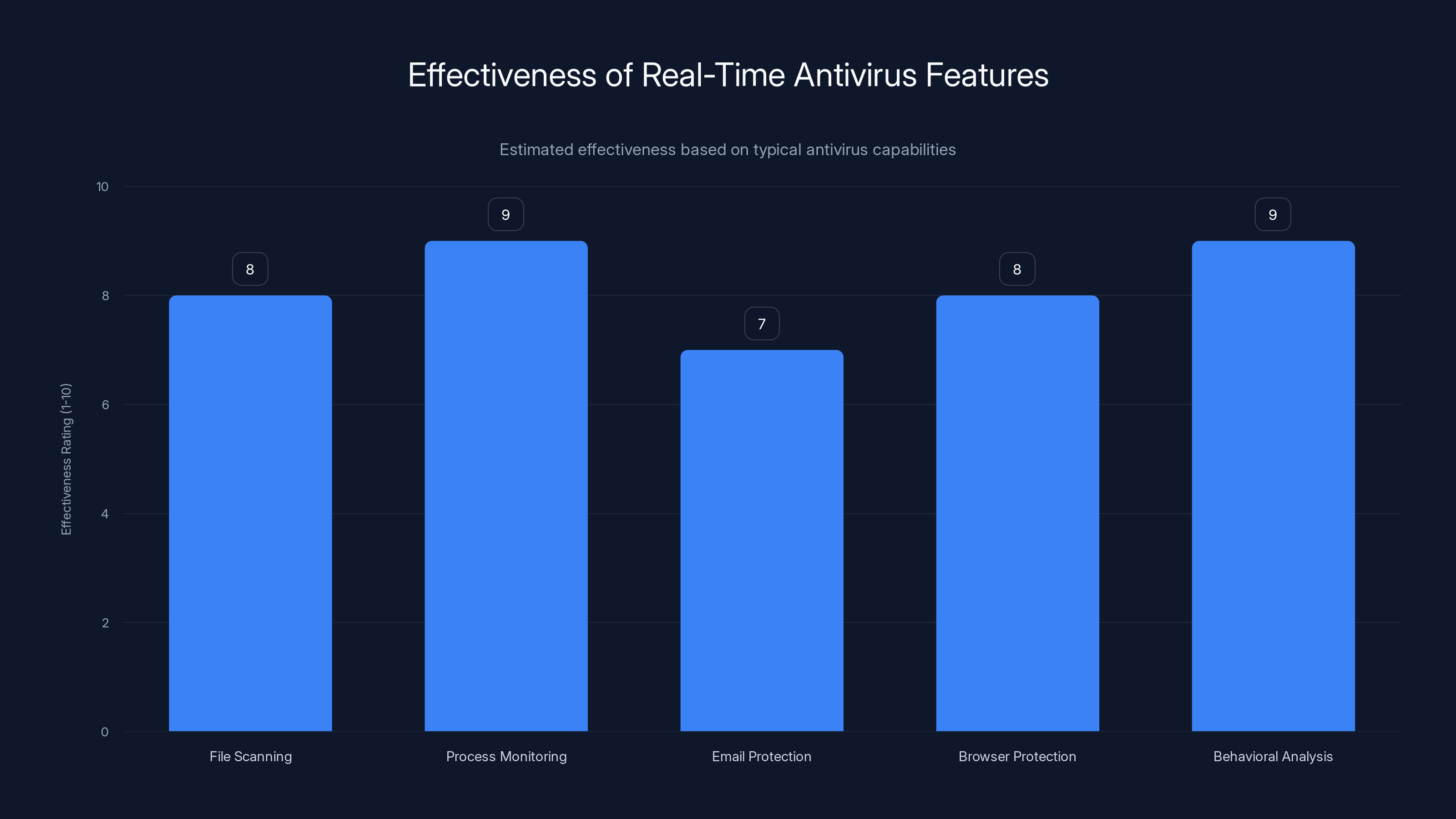
Real-time antivirus features are rated for their effectiveness, with process monitoring and behavioral analysis scoring the highest. Estimated data.
Identifying Infection: Signs Your Mac Might Be Compromised
Catch infections early. Here are warning signs:
Unusual slowness can indicate malware, but be careful about jumping to conclusions. High CPU usage in Activity Monitor is the smoking gun. Look for processes you don't recognize. Research them. But also consider that legitimate applications might be indexing data or updating in the background.
Constant fan noise and heat suggest high CPU usage. Your Mac shouldn't sound like an airplane. If it does, investigate Activity Monitor. Cryptominers cause this constantly.
Battery draining quickly on a laptop without heavy use suggests background activity. Again, check Activity Monitor. What's consuming power? Is it legitimate?
Unexpected pop-ups appear even when you're not browsing. Browser hijacking (changed home page, search engine, new tabs) is a classic sign of adware. Extensions might be the culprit—check Safari > Extensions (or Firefox > Add-ons).
Strange network activity shows up in network monitoring tools. Is your Mac connecting to unknown servers? This is suspicious. Tools that monitor network connections can alert you.
Crashes and freezes can be malware, but also hardware failure or software bugs. If they happen constantly, investigate. Run your antivirus. Check Activity Monitor for culprits.
Unexpected account lockouts or password resets might indicate compromise. If you're locked out of your accounts, change your passwords immediately from a different device. Consider them compromised.
New user accounts appearing without your creation indicates someone gained administrative access. This is serious. You might need professional help.
Unexpected advertisements in places they shouldn't be (within macOS, not just browser) suggest aggressive adware. This is rare on macOS but not impossible.
Disabled security features might indicate tampering. If your antivirus mysteriously stops working, if File Vault gets disabled, if the firewall turns off, something manipulated your system.
If you suspect infection, act immediately:
- Disconnect from the internet (don't let malware communicate with command servers)
- Run your antivirus in safe mode (restart, hold Shift during startup for Big Sur+, or Command-S for older macOS)
- Back up critical files to external drives
- If your antivirus can't clean the infection, restore from backup
- Consider professional help if the infection is severe
Advanced Security Practices: Going Beyond Basics
If you handle sensitive data—financial records, medical information, business secrets—additional measures make sense.
Application sandboxing restricts what an application can access. Older Macs had built-in sandboxing for App Store applications. Newer Macs apply sandboxing more broadly. You can use Terminal to manually sandbox applications, but this is advanced and requires command-line knowledge.
Virtual machines let you run suspicious applications in a completely isolated environment. Tools like Parallels Desktop or UTM let you create virtual Macs. Download a suspicious application? Run it in a VM. If it's malware, it infects the VM, not your real system. Restore the VM to a previous snapshot, and you're back to clean. Downside: requires significant disk space and RAM.
Firewall rules can restrict applications from making outbound connections. macOS has a built-in firewall, but it's limited. Third-party tools like Little Snitch give you granular control: which applications can access the network, and what servers can they contact. This catches malware trying to exfiltrate data or receive commands.
Hardware security keys (like YubiKeys) prevent account takeovers. Even if malware steals your password, it can't access your accounts without the physical key. Expensive but highly secure for critical accounts.
Encrypted communication tools protect sensitive messages. Malware can intercept emails. Using encrypted messaging (Signal, iMessage with end-to-end encryption enabled, ProtonMail) prevents interception.
Network monitoring tools let you see exactly what's communicating over your network. Wireshark (advanced) or GlassWire (simpler) show connection sources and destinations. Detecting malware calling home is easier with visibility.
Regular vulnerability audits involve checking for outdated software, weak passwords, overly permissive account settings, etc. Tools like Homebrew and third-party checkers can automate this.
These practices add friction to your workflow. For most users, they're overkill. For security-conscious professionals, they're justified.

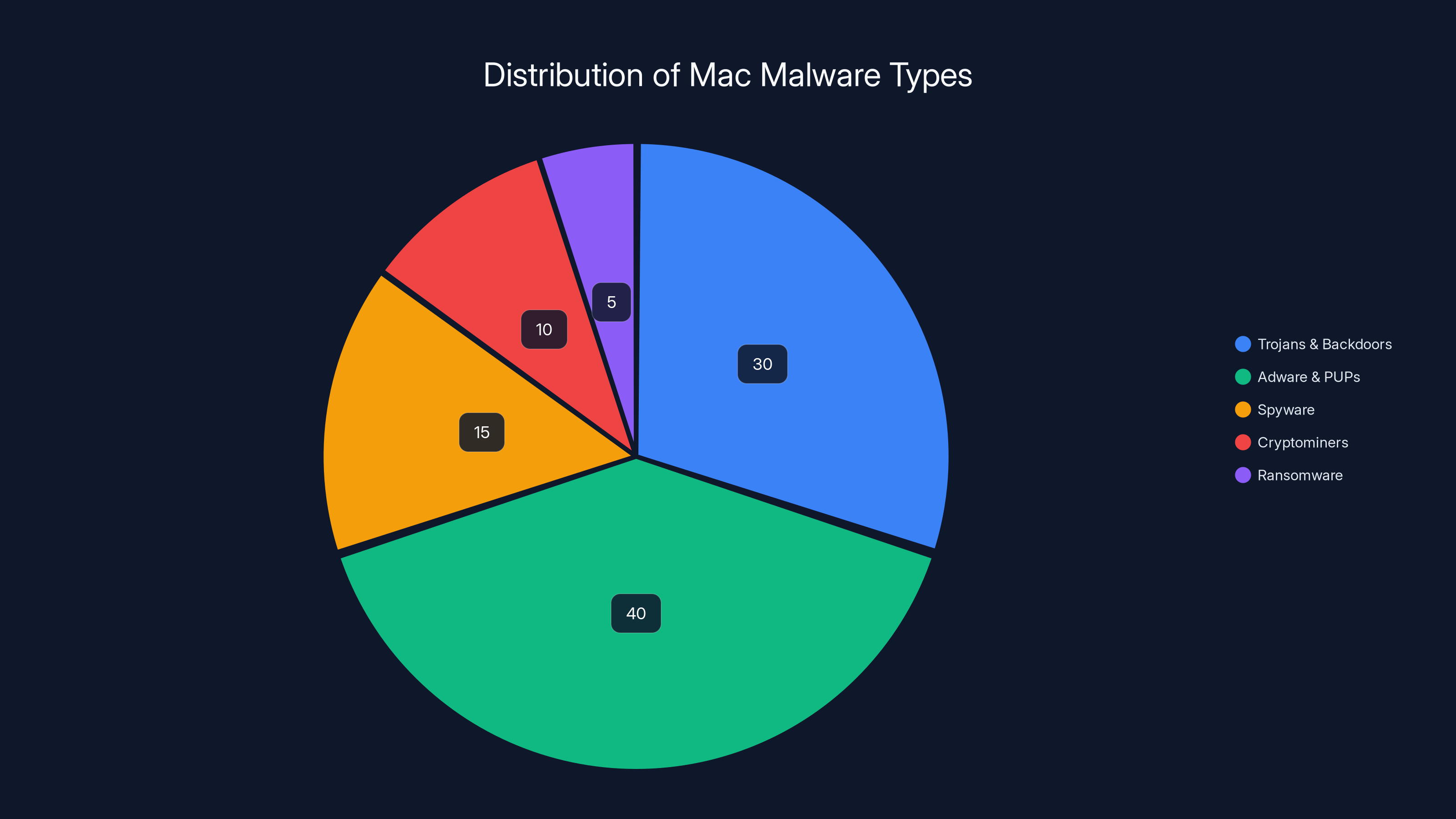
Estimated data suggests that Adware and PUPs are the most common type of Mac malware, followed by Trojans and Backdoors. Ransomware is currently the least common but is on the rise.
The Future of Mac Security: What's Coming
Mac security is evolving. Several trends will shape protection in coming years:
Artificial intelligence and machine learning are improving threat detection dramatically. Rather than checking files against databases of known malware, AI models can identify malware based on behavioral patterns and structural anomalies. These tools catch zero-day threats (attacks exploiting previously-unknown vulnerabilities) far better than signature-based detection.
Hardware-based security is becoming standard. Apple's custom silicon (M1, M2, M3 chips) includes integrated security features. In the future, security might be handled partly by hardware, partly by software. This is harder for attackers to bypass.
Enhanced sandboxing is gradually being applied to more system processes. In the future, even core applications might run in restricted environments, limiting malware's ability to access sensitive system functions or data.
Supply chain security is getting more attention. Apple and third-party developers are implementing stronger code signing, verification of updates, and transparency about what code is running. This makes supply chain attacks harder.
Privacy-first architecture is becoming competitive advantage. As users become more aware of data harvesting, tools that prioritize privacy—not just security—will gain traction.
Threat intelligence sharing between vendors and organizations is improving. When one company detects a new malware variant, that information is shared with others. Response times are shrinking.
These trends are positive. But attackers aren't sitting still. The arms race continues. Your best defense remains the foundation: keep your system updated, use strong passwords, enable two-factor authentication, maintain backups, run real-time antivirus, and think before you click.
Building Your Security Culture
Ultimately, security isn't about technology alone. It's about habits and awareness.
Healthy skepticism is your first defense. That email from "Apple support" asking you to verify your account? Suspicious. Why would they email instead of telling you in System Settings? Click the link, and you're on a fake website. Don't click. Go directly to Apple.com. A download that seems too good to be true? It probably is. That urgent warning about viruses? Probably fake.
Verification takes seconds. Before clicking a link in an email, hover over it (don't click). What's the actual URL? Does it match the official website? Before trusting download links, verify they're on official websites. Type URLs yourself rather than clicking links in emails or messages.
Questions before clicking help. Does this make sense? Why would that company contact me this way? Would I normally receive this? Is there urgency (which encourages mistakes)? Legitimate organizations don't rush you through security decisions.
Regular education keeps you current. Threats evolve. Awareness of common tactics helps you avoid them. Follow security blogs. Read about scams making the rounds. Learn from others' mistakes.
Accountability helps in shared environments. If other people use your Mac—family, roommates, colleagues—ensure they understand security practices. Teach them. Set expectations. Their mistakes become your infection.
Patience with security helps. Yes, enabling two-factor authentication adds a step. Yes, checking security warnings takes time. Yes, updating software seems annoying. These friction points exist for a reason. They've prevented countless compromises. The inconvenience is worth it.
Security is an investment in your peace of mind, your data safety, and your digital life. The upfront effort pays dividends for years.

FAQ
What is the difference between antivirus and antimalware?
Antivirus traditionally refers to software that detects and removes viruses specifically. Antimalware is broader—it protects against all types of malicious software (malware), including trojans, adware, spyware, and ransomware. In modern usage, the terms are often used interchangeably, but antimalware is technically more accurate for comprehensive protection.
Do Macs really need antivirus protection?
Yes. While macOS has built-in protections like XProtect and Gatekeeper, they're reactive and signature-based, meaning they catch known threats but miss zero-day exploits and new variants. Real-time antivirus adds essential proactive protection that catches threats before they infect your system. Mac malware detection increased over 400% since 2020, making protection increasingly important.
How often should I scan my Mac for malware?
If you have real-time antivirus running, it constantly monitors your system—you don't need manual scans. However, running a full system scan monthly is good practice to catch anything that might have slipped through. Some users prefer weekly or bi-weekly scans depending on their risk profile and how much they download.
Can a VPN protect me from malware?
No. A VPN encrypts your internet traffic and hides your IP address from your ISP and websites, protecting your privacy. But it doesn't protect your Mac from malware that's already on your system, nor does it stop you from downloading infected files. Malware protection and privacy are distinct—you need both antivirus and a VPN for comprehensive protection.
What should I do if I think my Mac is infected?
Immediate steps: disconnect from the internet to prevent malware from contacting attackers, run your antivirus in safe mode (restart and hold Shift), perform a full system scan, and quarantine any detected threats. If your antivirus can't remove the infection, back up critical files to external drives and restore from a clean backup if available. For severe infections, seek professional help.
Is it safe to use free antivirus on my Mac?
Many free antivirus tools are legitimate and effective. However, free tools sometimes support themselves through data collection or advertisements. Read privacy policies carefully. Check independent reviews. Reputable free tools exist, but some free tools are low-quality or contain adware themselves. Paid tools offer more resources and support, but aren't necessarily better.
How do I know if a website is malicious before visiting it?
Browser protection features in Chrome, Safari, and Firefox warn you if you're about to visit a known malicious site. Some antivirus tools add additional web protection. Suspicious signs include: poor grammar or design, unusual urgency ("act now or lose access"), requests for personal information, mismatched URLs (website looks like Apple but the URL is applesupport-help.com), or promises that seem too good to be true.
Should I disable security features if they slow my Mac?
No. Modern Macs are fast enough that real-time antivirus typically adds only 2-5% CPU overhead. If security is significantly slowing your system, you either have too many security tools running (uninstall duplicates) or have a malware infection consuming resources. Disabling security to gain speed is trading safety for convenience—a poor trade-off.
How do I remove malware manually if antivirus doesn't catch it?
Manual malware removal is difficult and risky. You need technical knowledge to identify malicious processes, understand what system files are legitimate, and safely remove infections without breaking your system. For most users, the solution is restoring from backup or reinstalling macOS. If you're technically skilled, Activity Monitor and file system inspection can help, but professional help is often safer.
What's the difference between a firewall and antivirus?
A firewall controls network traffic—what connects to your Mac and what your applications can access on the network. Antivirus detects and removes malicious files and processes on your system. Both protect you, but in different ways. Firewalls prevent some network-based attacks; antivirus prevents infections from files and malicious applications. You need both.

Conclusion: Protecting Your Digital Life
You've now got a complete picture of Mac security in 2025. The landscape has shifted dramatically from the days when Macs seemed invulnerable. Threats are real. Protection is necessary. But it's also manageable if you understand what you're doing and why.
Here's what we've covered: Mac malware exists and is growing. Your built-in defenses help but aren't complete. Real-time antivirus adds critical protection. Privacy and security are distinct but complementary. Implementing a layered approach—updates, strong passwords, two-factor authentication, antivirus, firewalls, and careful browsing habits—creates robust protection.
The practical path forward is straightforward:
- Update everything today. Don't delay. Vulnerabilities get exploited quickly.
- Enable File Vault and the firewall. These are free and built-in.
- Install real-time antivirus. Choose a reputable option with good reviews.
- Enable two-factor authentication on critical accounts.
- Back up your data. Regular backups are your insurance policy.
- Maintain awareness. Be skeptical. Think before clicking.
Security isn't a destination—it's ongoing maintenance. Technology changes. Threats evolve. Your practices need to evolve too. But the foundation remains: understanding your risks, implementing appropriate defenses, and maintaining discipline about updating and backing up.
Your Mac is valuable. Your data is valuable. Your privacy is valuable. They're worth protecting. Implement these practices today. You'll sleep better knowing you've done everything reasonable to keep your system and data safe.
The cost of protection—a small annual investment in security software, some time setting up defenses, and a bit of inconvenience from two-factor authentication—is trivial compared to the cost of dealing with a security breach, identity theft, or data loss.
Start now. Don't put it off. Your future self will thank you.
Key Takeaways
- Mac malware detection increased over 400% between 2020-2024, making protection essential and no longer optional for Mac users.
- Built-in macOS protections like XProtect and Gatekeeper are reactive and signature-based, requiring real-time antivirus for proactive threat detection.
- Layered security approach combining updates, strong passwords, two-factor authentication, antivirus, firewalls, and secure practices creates robust protection.
- Privacy and security are distinct concepts requiring separate tools and strategies; addressing both is essential for comprehensive digital safety.
- Regular backups serve as insurance policy against ransomware and data loss, enabling recovery even if malware successfully compromises your system.
Related Articles
- Best Home Antivirus Software & Protection [2025]
- CarGurus Data Breach: 1.7M Records Stolen by ShinyHunters [2025]
- Texas Sues TP-Link Over China Links and Security Vulnerabilities [2025]
- Bluesky's Germ Integration: The First Native E2E Encrypted Messenger [2025]
- Figure Data Breach: What Happened to 967,000 Customers [2025]
- Gabon's Social Media Blackout: Why VPN Demand Surged 8000% [2025]
![Mac Security & Antivirus Protection Guide [2025]](https://tryrunable.com/blog/mac-security-antivirus-protection-guide-2025/image-1-1771583768984.jpg)



