Texas Sues TP-Link Over Chinese Ties and Security Vulnerabilities: What You Need to Know
In a landmark case that sent shockwaves through the networking industry, Texas Attorney General Ken Paxton filed a major lawsuit against TP-Link, one of the world's largest router and networking equipment manufacturers. The lawsuit alleges that the company has systematically misled American consumers about its country of origin, hidden its Chinese connections, failed to deliver on security promises, and collected personal data without adequate disclosure or protection, as detailed in StateScoop's report.
This isn't some niche legal battle between obscure companies. TP-Link controls roughly 65% of the US networking device market, meaning millions of American homes and small businesses rely on their routers, mesh networks, and connected devices daily. If the allegations prove true, the implications for consumer privacy, national security, and corporate transparency are massive, as noted by The Register.
The case represents a broader trend of heightened scrutiny on Chinese technology companies operating in the US market. It raises fundamental questions: How much do we really know about the devices sitting on our shelves? Where are they actually made? Who's collecting our data? And what happens when companies make security claims they can't back up?
Let's break down what happened, why it matters, and what it means for anyone using TP-Link products.
The Core Allegations: Made in Vietnam? Not Quite.
The heart of Paxton's lawsuit centers on a simple claim: TP-Link is lying about where its products are made. The company labels its routers and networking devices as "Made in Vietnam," which sounds reassuring to American consumers who often prefer products manufactured outside of China due to national security and intellectual property concerns.
But here's the problem. Vietnam is only the final assembly location. According to the lawsuit, the vast majority of the components inside these devices are manufactured in China. We're talking about circuit boards, processors, firmware, and other critical components that actually determine how the device functions. Vietnam's role is essentially last-mile assembly and packaging, as reported by The Record.
This distinction matters legally and practically. Under Texas consumer protection law, the "Made in" designation is supposed to indicate the country where the product was substantially transformed or manufactured. If components are mostly Chinese-made and simply assembled in Vietnam, the "Made in Vietnam" label could constitute deceptive advertising.
Think of it this way: if you ordered a "Made in America" car but discovered it was 90% assembled from imported parts, you'd feel misled. That's essentially what Paxton is arguing happened here, except we're talking about networking equipment used in homes, schools, and businesses across the country.
The Hidden Chinese Connections: More Than Just Manufacturing
The lawsuit goes beyond manufacturing location. Paxton alleges that TP-Link has deliberately obscured its ties to China and failed to disclose Chinese legal obligations. According to the filing, the company has Chinese parent companies, operates under Chinese corporate structures, and is subject to Chinese laws and regulatory requirements, as detailed by Reuters.
This becomes relevant in the context of national security. Chinese law requires companies operating in the country to cooperate with government surveillance and intelligence gathering if requested. While TP-Link has maintained it's independent from government influence, the lawsuit suggests consumers weren't made aware of these potential obligations.
The company's structure is complex. TP-Link Systems Inc., the division actually being sued, claims to be an independent American operation. However, the corporate hierarchy above it connects back to Chinese parent entities. This layered structure allowed the company to market itself as American while maintaining Chinese ownership and governance.
For consumers, this matters because it affects trust. You might choose one router over another because you believe it's American-made or at least operates under American legal standards. If the company's true structure was disclosed upfront, you could make an informed choice. Instead, the lawsuit argues consumers were deliberately kept in the dark.
The Home Shield Promise: Security Claims That Don't Hold Up
TP-Link's Home Shield feature is marketed as a comprehensive security solution. The company uses language like "100% safeguard" and claims it covers "all security scenarios" against cyber threats and IoT attacks. For average consumers who don't have IT training, this kind of messaging is reassuring. It sounds like TP-Link has their back.
Except, according to the lawsuit, the company hasn't actually delivered on these promises. Over recent years, multiple serious vulnerabilities have affected TP-Link routers and devices. Some of the most notable include:
Volt Typhoon campaign vulnerabilities: Security researchers discovered that Chinese state-sponsored hackers had exploited TP-Link routers as part of a sophisticated campaign targeting critical infrastructure. The attacks went undetected for years.
Flax Typhoon vulnerabilities: Similar sophisticated exploitation of TP-Link equipment by advanced threat actors.
Salt Typhoon campaign: Another major threat actor group successfully compromised TP-Link devices, demonstrating that the company's security protections weren't preventing determined attackers.
SQL injection flaw: A relatively basic but dangerous vulnerability that allowed attackers to manipulate the router's database directly.
Password spraying attacks: TP-Link devices were vulnerable to brute force password attacks, allowing unauthorized access.
These aren't obscure edge cases. They're major security incidents that made headlines in the tech industry. If Home Shield was truly providing a "100% safeguard" against all security scenarios, how did these vulnerabilities exist in the first place?
The lawsuit argues this represents false advertising. Consumers bought TP-Link products partly based on security claims the company clearly couldn't substantiate. When vulnerabilities were discovered, affected users were often left scrambling to patch their systems or upgrade to newer hardware entirely.
Data Collection: More Than You Probably Know
Beyond security vulnerabilities, the lawsuit highlights another concern: TP-Link's data collection practices. The company operates several apps and platforms that consumers use to manage their networks and smart home devices. These include:
Kasa: Smart home management platform collecting device data Tapo: IoT device ecosystem and control app Deco: Mesh Wi-Fi management platform Tether: Router configuration and monitoring app Home Shield: The security app we already discussed
According to the lawsuit, these apps and platforms collect sensitive information including:
- Email addresses
- Precise GPS location data
- Device identifiers and MAC addresses
- Network configuration information
- Usage patterns and behavior data
The issue isn't that companies collect data—that's standard practice in 2025. The issue is transparency and protection. Did TP-Link clearly disclose what data was being collected? Did consumers actually understand what was happening? Were they given meaningful choices about opting out? And critically, was this data adequately protected from theft or unauthorized access?
The lawsuit suggests the answers to these questions are mostly "no." Consumers installed these apps to manage their networks, likely with no detailed understanding of the extent of data collection occurring in the background.
Consider the location data specifically. Why does a router app need precise GPS location? It could theoretically be used to create detailed maps of when you're home, when you're away, where you travel regularly, and your daily patterns. In the wrong hands, this information could facilitate stalking, burglary, or physical harm.
The Market Power Problem: Why This Matters More Than You Think
Part of what makes this lawsuit significant is TP-Link's market dominance. With roughly 65% of the US networking device market, the company isn't just one option among many. For many consumers, TP-Link isn't a choice—it's the default.
Walk into any Best Buy or browse Amazon's router section, and TP-Link products dominate the affordable segment. This creates a problem: if consumers can't easily choose alternatives, TP-Link has less incentive to be transparent or address security concerns quickly.
This market concentration is why Paxton is seeking significant penalties. The lawsuit requests:
- Civil penalties up to $10,000 per violation (higher for consumers 65 and older)
- Damages potentially exceeding $1 million
- Jury trial
- Injunctive relief to force changes in how the company operates
If each deceptive marketing claim counts as a separate violation, and those claims appear across thousands of products sold to millions of consumers, the math gets large quickly. A $1 million judgment is one thing; penalties in the hundreds of millions would be another.
TP-Link's Defense: "Smear Campaign" and Claims of Independence
TP-Link hasn't stayed silent. The company released a statement asserting that the lawsuit is "without merit and will be proven false." They argue that TP-Link Systems Inc., the specific division being sued, is an independent American company that operates its core infrastructure and operations within the United States, as reported by Bloomberg Law.
The company's position is essentially: "Yes, our parent companies have Chinese connections, but that doesn't mean we're compromised. We run our own show here in America."
TP-Link also claims that recent negative coverage about the company represents a "smear campaign" by competitors like Netgear, designed to paint the company as a national security risk. There's probably some truth to this—competitors do have incentives to raise questions about rivals. But that doesn't necessarily mean the allegations are false.
The company added: "We will continue to vigorously defend our reputation as a trusted provider of secure connectivity for American families." This suggests they're willing to fight the lawsuit rather than settle quickly.
What's notable about TP-Link's defense is what it doesn't directly address. The company doesn't say, "We never made those security claims" or "All our vulnerabilities were patched immediately." Instead, it focuses on the ownership structure question and the suggestion of competitive smearing.
National Security Concerns: Why The Government Cares
You might wonder why a state attorney general is personally involved in what seems like a consumer protection issue. The reason goes beyond fraud—it's national security.
Networking equipment is critical infrastructure. Routers connect every device in a home or business to the internet. They can see all traffic, all data flowing in and out. If a router's firmware is compromised or has backdoors, sophisticated threat actors could monitor everything that happens on that network.
There's also the question of supply chain security. If Chinese-made components are embedded in what Americans think are American or Vietnamese products, where else might backdoors or monitoring capabilities be hidden? How would anyone know?
The Volt Typhoon, Flax Typhoon, and Salt Typhoon campaigns mentioned in the lawsuit aren't random. These are sophisticated threat operations, likely sponsored by advanced adversaries. The fact that they successfully compromised TP-Link equipment suggests either:
- The devices had vulnerabilities that could have been prevented
- The devices had vulnerabilities that weren't patched quickly enough
- There were backdoors or weaknesses intentionally or unintentionally built in
Regardless of which is true, the result is the same: millions of Americans' networks were exposed to sophisticated hackers.
Attorney General Paxton's statement makes this clear: "TP Link will face the full force of the law for putting Americans' security at risk. Let this serve as a clear warning to any Chinese entity seeking to compromise our nation's security."
This isn't just about consumer protection—it's a message about acceptable behavior for any technology company operating in the US market.
The Broader Tech Industry Context: Growing Scrutiny
The TP-Link lawsuit doesn't exist in a vacuum. It's part of a larger wave of scrutiny directed at Chinese technology companies and foreign-owned tech firms operating in the US.
Consider recent events: Texas has sued multiple TV manufacturers, alleging they were "mass surveillance systems" collecting viewer data without proper consent. The FCC has been examining the Cyber Trust Mark Program over Chinese ties. TikTok faces potential bans. Huawei and other Chinese telecom equipment makers have been restricted from US networks. DJI drones face scrutiny over data collection and national security concerns, as noted by Radio Free Europe.
This broader context matters because it suggests the TP-Link lawsuit isn't an isolated action—it's part of a coordinated effort across multiple government agencies and states to scrutinize foreign technology in the US market.
For TP-Link, this means the company is facing headwinds that go beyond the specific lawsuit. Even if it wins in court, the reputational damage and regulatory pressure could be substantial.
What the Vulnerabilities Actually Looked Like: Technical Details
Let's dig deeper into what those security vulnerabilities actually meant for users. When researchers disclosed the Volt Typhoon campaign, they found that sophisticated state-sponsored hackers had compromised TP-Link routers to maintain persistent access to victim networks. These weren't one-off attacks—they were long-term implants that could collect data, monitor communications, and potentially move laterally to other devices on the network.
The SQL injection vulnerability mentioned in the lawsuit is a classic attack vector. It allows an attacker to manipulate the router's backend database by inserting malicious code into input fields. In practice, this could let an attacker:
- Create unauthorized admin accounts
- Modify device settings and credentials
- Access stored data
- Disable security features
- Install firmware backdoors
Password spraying attacks exploit weak default credentials or inadequate account lockout mechanisms. An attacker systematically tries common password combinations until one works. If TP-Link routers were vulnerable to this, anyone on the same internet connection (your neighbor, a hacker at a coffee shop you visit) could potentially gain access to your router and network.
The point isn't that TP-Link was uniquely vulnerable—many router manufacturers have had similar issues. The point is that marketing Home Shield as a "100% safeguard" against all security scenarios, while these vulnerabilities existed, is arguably false advertising.
The Data Collection Ecosystem: How Much Information Is Actually Collected?
When you use TP-Link's various apps, you might not realize the full scope of data being collected. Let's trace what happens:
Installation: You download Kasa or Tapo or Deco app and create an account. TP-Link now has your email address and associated account data.
Device pairing: You add your router or smart devices to the app. TP-Link learns what devices you own and their MAC addresses (unique hardware identifiers).
Location permissions: The app asks for GPS access. If you grant it, TP-Link knows your precise location whenever the app is running.
Usage monitoring: TP-Link tracks when you access the app, what settings you check, what devices you interact with, and when. This creates a behavioral profile.
Network information: The app collects data about your network, including connected devices, internet speed, usage patterns, and more.
Over months and years, this data accumulates into a detailed profile. TP-Link knows:
- Where you live
- When you're home and when you're away
- What devices you use
- Your internet habits
- When you're traveling
- Your daily and weekly patterns
This information has value. To whom? Advertisers, data brokers, insurance companies, and others willing to pay for detailed consumer profiles. The lawsuit doesn't specifically allege that TP-Link is selling this data, but it does allege that the company isn't adequately disclosing what it's collecting or protecting what it collects.
Legal Claims and Damages: What the Lawsuit Actually Seeks
Under Texas state law, companies that engage in deceptive practices can face penalties under the Texas Deceptive Trade Practices Act (DTPA). The lawsuit alleges multiple violations:
Fraudulent concealment of geographic origin: Making "Made in Vietnam" claims while hiding that most components are Chinese-made.
Misrepresentation of security features: Claiming Home Shield provides complete protection when known vulnerabilities existed.
Failure to disclose data collection: Not adequately informing consumers what data is collected or how it's used.
Failure to disclose Chinese affiliation: Not clearly informing consumers about corporate ownership and potential Chinese legal obligations.
For each violation, the DTPA allows damages up to $10,000 per consumer, with higher penalties for vulnerable populations like seniors. If Paxton can demonstrate that millions of Texans were affected by these practices, the potential liability becomes enormous.
The lawsuit also seeks injunctive relief, meaning TP-Link would be forced to change how it labels products, discloses data collection, represents security features, and operates in Texas going forward.
The International Implications: What Other Countries Are Doing
While Texas is pursuing legal action, other countries are taking different approaches. Several nations have begun scrutinizing or restricting Chinese technology imports, particularly for critical infrastructure.
Sweden has banned Chinese companies like Huawei and ZTE from 5G network buildouts, citing security concerns. The UK has restricted Huawei involvement in telecom infrastructure. The EU has proposed regulations requiring greater transparency about data collection and security practices by foreign tech companies.
This global context suggests the TP-Link lawsuit isn't a uniquely American phenomenon. Multiple democracies are grappling with how to balance the benefits of affordable technology with concerns about national security and consumer protection.
In some ways, Texas is following a path others have already started down. In other ways, Texas is taking a more aggressive stance by going after a company for deceptive marketing practices rather than just banning it from certain sectors.
What This Means for Consumers: Practical Implications
If you currently own TP-Link products, what should you do? The short answer: keep using them, but be aware of the security concerns.
TP-Link routers still function fine and still provide the basic connectivity they're designed for. However, the lawsuit does suggest you should:
Update firmware regularly: Don't ignore those update notifications. They patch security vulnerabilities.
Review app permissions: Go into your phone settings and check what permissions you've granted to Kasa, Tapo, or Deco apps. Do they really need GPS access? Can you turn off location services?
Change default credentials: Never use the default admin username and password for your router. Set a strong, unique password.
Monitor your network: Occasionally check what devices are connected to your network. Unknown devices suggest unauthorized access.
Consider alternatives: If you're shopping for a new router, research other brands. While all companies have security vulnerabilities at some point, TP-Link's market dominance and the alleged security failures might make you want to diversify where you get your networking equipment.
Be cautious with location permissions: Question why your router app needs to know your GPS location. Most functions don't require it.
The Historical Precedent: Similar Cases and Outcomes
This isn't the first time a major tech company has faced allegations of deceptive marketing around security and data collection. Looking at historical precedent can give us insight into likely outcomes:
Facebook/Meta: Faced FTC action over misrepresenting data privacy and selling user data to third parties. Settlement required privacy reforms and significant financial penalties.
Equifax: Data breach lawsuit resulted in nearly $1 billion settlement over inadequate security and notification practices.
Yahoo: Agreed to $350 million reduction in acquisition price after failing to disclose massive data breaches affecting over 3 billion users.
T-Mobile: Agreed to pay hundreds of millions over a data breach affecting millions of customers.
These cases suggest that when companies make security claims they can't back up or fail to disclose security breaches and vulnerabilities adequately, they face serious financial consequences. The TP-Link lawsuit follows a similar pattern.
One key difference: most of those cases involved companies that eventually admitted wrongdoing or settled. TP-Link is taking a more adversarial stance, claiming the lawsuit is without merit. If the company chooses to fight rather than settle, the case could drag on for years through discovery, depositions, and trial.
Expert Opinions and Industry Response
Cybersecurity researchers and industry experts have had varied reactions to the lawsuit. Some view it as overdue accountability for a company that dominates the market while delivering insufficient security. Others suggest that holding one company responsible while allowing similar practices by other firms sets a problematic precedent.
Netgear, TP-Link's major competitor, has presumably been pleased by the lawsuit—though also careful not to appear to be "smear campaigning" as TP-Link alleges. Other router manufacturers like ASUS, Ubiquiti, and Cisco are likely watching carefully to see how this case develops, as it could affect how they market security features and disclose data collection practices.
Security researchers are particularly interested in whether the lawsuit forces TP-Link to implement more robust vulnerability disclosure processes or faster patching timelines. If winning changes industry practices, that would be a significant positive outcome for consumers.
The Timeline: When Will This Be Resolved?
Texas filed the lawsuit, but resolution won't happen quickly. Based on similar cases, here's a realistic timeline:
Months 1-6: TP-Link files motions to dismiss or challenge jurisdiction. The court decides if the case can proceed. Most likely outcome: case survives initial motions and moves forward.
Months 6-18: Discovery phase. Both sides exchange documents, conduct depositions, and gather evidence. This is where the real details come out.
Months 18-30: Pre-trial negotiations. Settlement discussions may intensify if either side realizes their position is weaker than expected.
Months 30+: Trial, if no settlement is reached. Could take months or even over a year.
Realistic timeline: 2-4 years before a final outcome, assuming it goes to trial. If TP-Link settles, it could happen faster—possibly within 1-2 years.
For consumers and the company, this extended timeline means uncertainty. TP-Link's reputation could suffer during the litigation process, even if it ultimately wins. Conversely, if evidence emerges during discovery that confirms the allegations, pressure to settle increases.
Corporate Responsibility and the Bigger Picture
Beyond the legal mechanics, the lawsuit raises important questions about corporate responsibility in the tech industry:
Should companies be held accountable for vulnerabilities? Most would say yes, but how long do manufacturers have to patch known issues? Who bears responsibility—the manufacturer, the user, or shared?
Is transparency about ownership and control the company's responsibility or the consumer's? If you buy a product, shouldn't you know who owns and controls the company? The lawsuit suggests yes.
How much data is reasonable to collect? Companies argue data collection enables better products and services. Consumers increasingly question whether the data collection is necessary or proportional.
Can market dominance enable deceptive practices? When a company controls 65% of a market, does it have greater responsibility to consumers who may lack alternatives?
These questions don't have easy answers, but the TP-Link case is forcing the industry to grapple with them.
Future Outlook: What Happens Next?
Assume for a moment that Texas prevails in this lawsuit, or at minimum, TP-Link settles and agrees to reforms. What would change?
Product labeling: TP-Link would likely be required to disclose component origin more clearly—for example, labeling products as "Assembled in Vietnam from Primarily Chinese Components."
Data collection disclosure: The company would need to clearly explain what data is collected by each app, how it's used, and provide meaningful opt-out options.
Security claims: TP-Link couldn't claim "100% protection" or "all security scenarios" without much more specific caveats about what's covered and what's not.
Transparency reports: The company might be required to publish regular transparency reports about vulnerabilities discovered, patching timelines, and government data requests.
Product separation: The company might be forced to more clearly separate its American operations from Chinese parent companies, potentially even spinning off a truly independent US entity.
Whether any of this actually happens depends on the lawsuit's outcome. But the pressure—from the government, from consumers, from competitors—is building.
Competitive Implications: Who Wins If TP-Link Loses?
If TP-Link faces significant penalties or is forced to change operations, which competitors benefit?
Netgear: Would gain share in the prosumer and enterprise segments where TP-Link is particularly strong. However, Netgear itself has faced security vulnerabilities over the years.
ASUS: Known for gaming-oriented routers with strong performance. Could position itself as more transparent about security and data practices.
Ubiquiti: Focuses on the professional segment with higher-end equipment. Less affected by the lawsuit but could market itself as more security-conscious.
Cisco: Enterprise-focused but increasingly moving into consumer/prosumer space. Strong reputation for security but commands premium pricing.
Eero (Amazon): Amazon-owned mesh network system with integrated security. Could leverage trust in Amazon's data handling (though not everyone trusts Amazon with their data).
The competitive landscape could shift significantly depending on the lawsuit's outcome and how aggressively competitors position themselves against TP-Link.
Defending Against the Claims: TP-Link's Likely Defense Strategy
While we don't know exactly how TP-Link will defend itself, we can make educated guesses based on the company's statements and typical corporate defense strategies:
Jurisdiction challenge: Argue that the case should be heard in another state or dismissed entirely due to lack of jurisdiction.
"Made in Vietnam" legality: Argue that Vietnam final assembly is sufficient for the "Made in Vietnam" designation under FTC and international standards. Many products do final assembly in one country while components come from another—this is standard global manufacturing.
Home Shield claims: Argue that "100% safeguard" and "all security scenarios" are marketing puffery, not literal claims. They might argue that any reasonable consumer understands these as general descriptions, not absolute guarantees.
Industry standards: Argue that TP-Link's security practices and vulnerability response times are consistent with industry standards and that other manufacturers have similar vulnerabilities.
Regulatory compliance: Argue that the company complies with all applicable FTC, FCC, and state regulations regarding security claims and data collection disclosure.
Independent operation: Emphasize TP-Link Systems Inc.'s operational independence, separate financials, and American management, arguing that Chinese parent company ownership doesn't translate to control or surveillance obligations.
These arguments have some merit, which is why TP-Link might actually be able to mount a credible defense in court. The outcome is genuinely uncertain.
What Consumers Should Know About Router Security Now
Whether the lawsuit succeeds or fails, consumers should understand that router security is a shared responsibility. Here's what you can control:
Change default passwords immediately. Most routers come with default admin credentials. Change them to strong, unique passwords the moment you set up the device.
Enable WPA3 encryption (or WPA2 if your devices don't support WPA3). This encrypts your wireless network so others can't easily intercept your traffic.
Disable WPS (Wi-Fi Protected Setup). It's convenient but adds a security vulnerability.
Turn off remote management. Never allow router access from the internet. There's no legitimate reason for this feature for most home users.
Keep firmware updated. Install updates the day they're released. Use automatic updates if available.
Create a guest network. Use it for visitors and IoT devices that don't need access to your main network.
Monitor connected devices. Periodically check your router's administration panel to see what's connected. Unknown devices suggest unauthorized access.
Use a firewall. Your router has a built-in firewall—enable it.
Consider a mesh network. Modern mesh systems like Eero, Netgear Orbi, or ASUS AiMesh often have better security practices and easier management than traditional routers.
These steps won't prevent every attack, but they significantly reduce your vulnerability to common threats.
The Role of Regulatory Bodies: FTC, FCC, and Beyond
While Texas pursues its lawsuit, federal agencies are also paying attention. The FTC has authority to regulate deceptive marketing practices and data privacy violations. The FCC regulates telecommunications and has security requirements for connected devices.
If the FTC believes TP-Link violated federal law, it could launch its own investigation separate from Texas's lawsuit. This would be more serious than a single state lawsuit because federal penalties can be substantially higher.
The FCC's Cyber Trust Mark Program, which certifies devices as meeting security standards, has itself faced scrutiny over alleged ties to China. This program was meant to provide consumers with an easy way to identify secure devices. If the program itself is compromised, consumers lose an important trust mechanism.
These regulatory efforts, combined with state lawsuits, suggest that pressure on TP-Link and similar companies will continue to mount from multiple directions.
Final Verdict: What This Lawsuit Really Means
The Texas lawsuit against TP-Link is fundamentally about accountability and transparency in the technology industry. The company allegedly misled consumers about where their products were made, overinflated security claims, and collected data without adequate disclosure or protection.
Whether TP-Link ultimately prevails or settles, the lawsuit serves notice that American regulatory bodies and state governments are done tolerating deceptive practices—especially when they affect national security and consumer privacy.
For TP-Link, the lawsuit represents an existential risk. A major judgment could require expensive infrastructure changes, product redesigns, and operational reforms. The reputational damage alone could cost customers and market share even if the company ultimately wins the legal case.
For consumers, the lawsuit hopefully accelerates reforms in how technology companies disclose their ownership, data collection practices, and security vulnerabilities. It reminds us that "Made in" labels might not tell the whole story and that marketing claims about security should be scrutinized carefully.
For the broader industry, the lawsuit sets a precedent: the days of companies quietly outsourcing to China while marketing as something else, making grand security claims without delivering, and collecting data without consent are potentially ending.
Whether that's good news or bad news depends on your perspective. For companies that have been cutting corners, it's bad news. For consumers and national security advocates, it's probably good news.
The legal process will take years to resolve, but the message is already being received throughout the technology industry: operate transparently, deliver on promises, and respect consumer privacy, or face the consequences.
TL; DR
-
TP-Link faces major allegations: Texas Attorney General sued the company over deceptive "Made in Vietnam" claims when most components are actually Chinese-made, with 65% of the US networking market at stake.
-
Security claims don't match reality: Home Shield promised "100% safeguard" against all threats, but multiple sophisticated attacks (Volt Typhoon, Flax Typhoon, Salt Typhoon) successfully compromised TP-Link equipment.
-
Data collection is extensive: TP-Link apps collect email, precise GPS location, device identifiers, and behavioral data with inadequate disclosure of how it's used or protected.
-
Potential damages are enormous: The lawsuit seeks civil penalties up to
1 million given the millions of affected consumers. -
This signals broader accountability: The case reflects growing scrutiny of Chinese technology companies and sets expectations that manufacturers must disclose ownership, be transparent about security practices, and deliver on product claims.
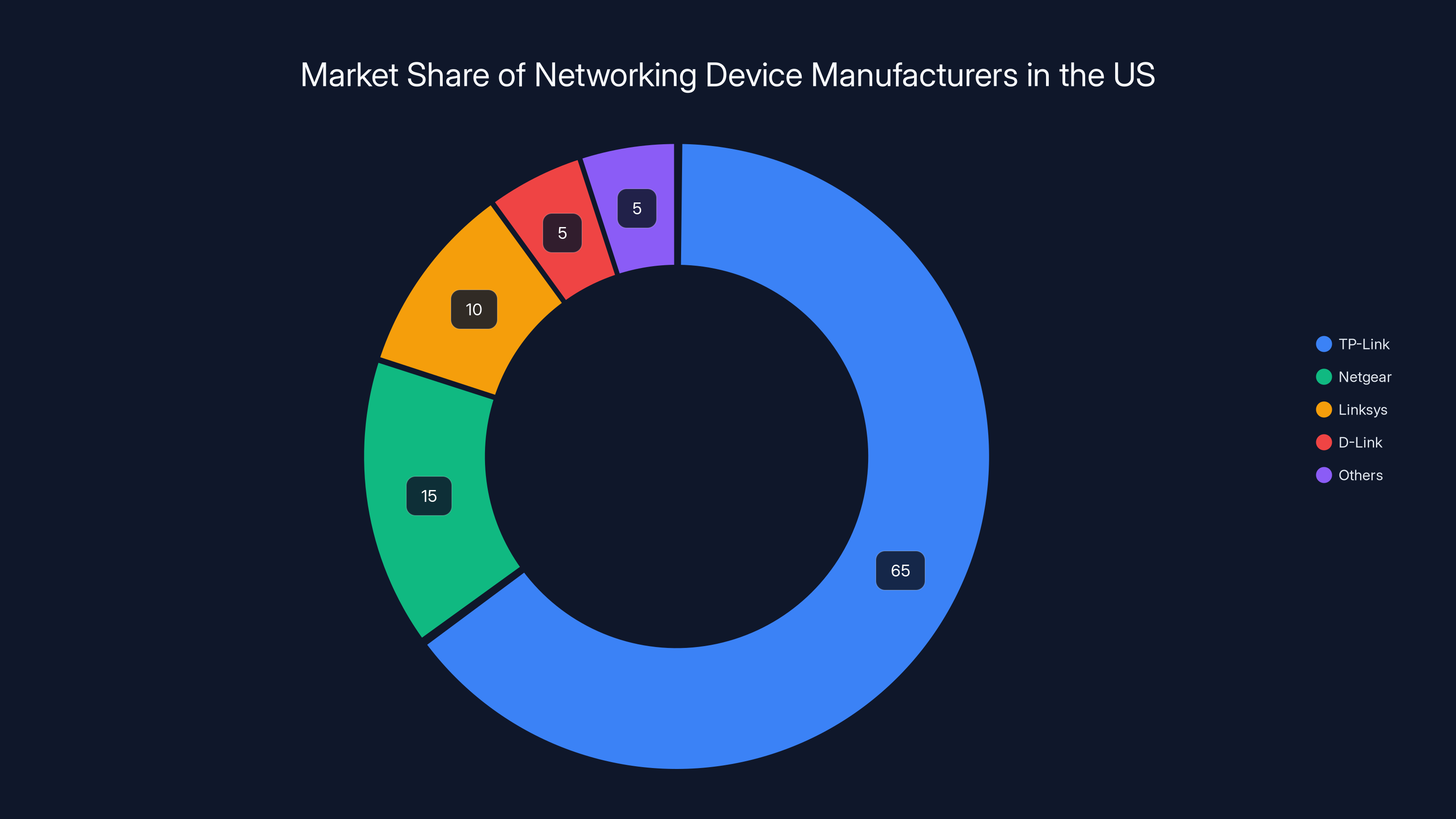
TP-Link controls an estimated 65% of the US networking device market, significantly outpacing competitors like Netgear and Linksys. Estimated data.
FAQ
What is the Texas lawsuit against TP-Link about?
The lawsuit alleges that TP-Link deceived consumers by labeling products as "Made in Vietnam" when most components are actually manufactured in China, made false security claims about Home Shield protection, failed to adequately disclose data collection practices, and obscured its Chinese ownership and potential obligations under Chinese law. Attorney General Ken Paxton filed the suit on behalf of Texas consumers who purchased TP-Link products.
Why does it matter that TP-Link is Chinese-connected?
The concern centers on national security and disclosure. Chinese law requires companies operating in China to cooperate with government surveillance and intelligence gathering if requested. Consumers should be able to make informed decisions about which companies control their networking equipment. If you believe you're buying American or Vietnamese-made products but actually own Chinese-controlled equipment subject to Chinese legal obligations, that's a material misrepresentation. Additionally, TP-Link routers are critical infrastructure that see all data flowing in and out of homes and businesses, making the origin and control of this equipment important for national security.
How much of the US router market does TP-Link control?
TP-Link controls approximately 65% of the US networking device market, making it the dominant player by far. This market dominance makes the lawsuit more significant because it means millions of American homes and small businesses rely on TP-Link equipment, and alternatives may be limited. The company's dominant position is relevant to the lawsuit because it reduces consumer choice and may reduce pressure on the company to be transparent or address security issues quickly.
What are the specific security vulnerabilities mentioned in the lawsuit?
The lawsuit cites multiple serious vulnerabilities including Volt Typhoon campaign exploits (used by state-sponsored Chinese hackers to compromise critical infrastructure), Flax Typhoon vulnerabilities, Salt Typhoon campaign compromises, SQL injection flaws that allow database manipulation, and password spraying vulnerabilities that enable brute force attacks. These vulnerabilities allegedly occurred despite TP-Link's marketing claims that Home Shield provides "100% safeguard" and protection against "all security scenarios."
What kind of data does TP-Link collect through its apps?
TP-Link's various apps including Kasa, Tapo, Deco, and Tether collect email addresses, precise GPS location data, device identifiers and MAC addresses, network configuration information, and usage patterns and behavioral data. Over time, this collected data creates detailed profiles of when consumers are home, where they travel, what devices they use, and their daily patterns. The lawsuit alleges this extensive data collection wasn't adequately disclosed to consumers or protected from unauthorized access.
What are the potential penalties if TP-Link loses?
The lawsuit seeks civil penalties of up to
How long will this lawsuit take to resolve?
Based on similar cases, a realistic timeline is 2-4 years if the case goes to trial. The process typically includes initial motions and jurisdictional challenges (months 1-6), discovery and evidence gathering (months 6-18), pre-trial negotiations and possible settlement discussions (months 18-30), and then trial if no settlement is reached (months 30+). If TP-Link settles early, the case could resolve within 1-2 years.
Should I stop using my TP-Link router?
Not necessarily. Your TP-Link router still functions fine for basic connectivity. However, you should update firmware regularly to patch security vulnerabilities, change the default admin password, monitor what devices are connected to your network, review app permissions (particularly location access), and consider alternatives if you're buying new equipment. You might also want to set up separate networks for guest devices and IoT gadgets to limit damage if any device is compromised.
Has the FTC gotten involved?
While the lawsuit is being pursued by Texas's Attorney General, federal agencies like the FTC and FCC are also monitoring the situation. The FTC has authority to regulate deceptive marketing practices and data privacy violations and could launch its own investigation. The FCC is examining the Cyber Trust Mark Program over alleged ties to China. Federal involvement could result in more severe penalties than a single state lawsuit.
What does TP-Link say about these allegations?
TP-Link claims the lawsuit is "without merit and will be proven false." The company states that TP-Link Systems Inc., the division being sued, is an independent American company that operates its core infrastructure and operations within the United States, despite having Chinese parent companies. TP-Link also claims recent negative coverage represents a "smear campaign" by competitors like Netgear. The company says it will "vigorously defend our reputation as a trusted provider of secure connectivity for American families."
What companies could benefit if TP-Link loses market share?
Netgear would gain share in prosumer and enterprise segments where TP-Link is particularly strong. ASUS could position gaming-oriented routers as more transparent about security. Ubiquiti focuses on the professional segment. Cisco could leverage its enterprise security reputation. Eero (owned by Amazon) offers mesh networks with integrated security. The competitive landscape could shift significantly depending on the lawsuit's outcome and how competitors position themselves against TP-Link.
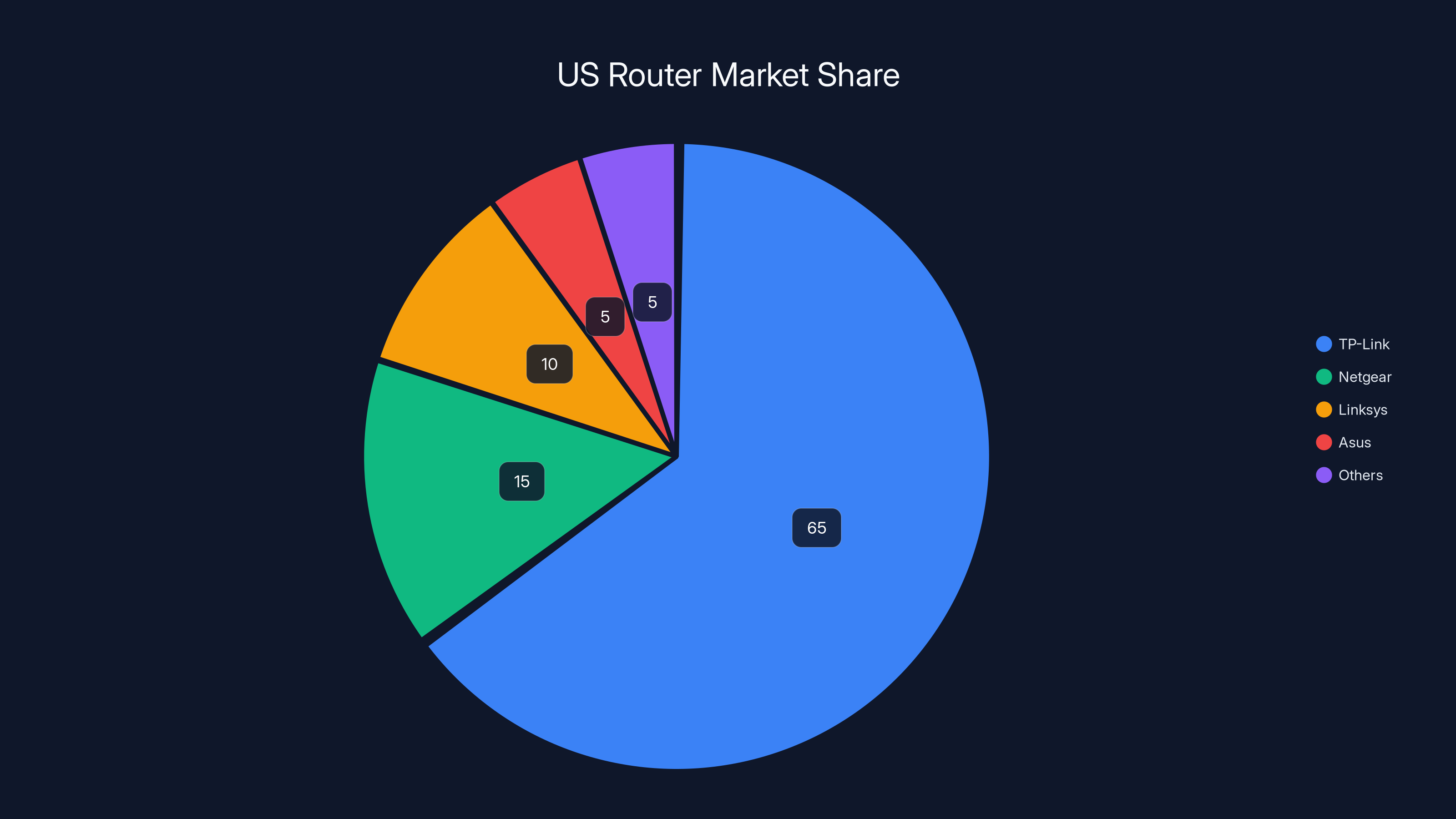
TP-Link controls approximately 65% of the US networking device market, highlighting its dominance and the significance of the lawsuit. Estimated data.
Key Takeaways
- TP-Link's "Made in Vietnam" label masks Chinese component manufacturing and ownership, raising questions about what products really represent
- Security vulnerabilities that affected millions contradict company claims of comprehensive protection, exemplifying a broader pattern of overpromised and under-delivered security
- Data collection through multiple apps creates detailed behavioral profiles without adequate consumer awareness or control
- With 65% market dominance, TP-Link's practices affect millions of Americans, making the lawsuit significant for establishing standards across the industry
- The lawsuit represents growing government scrutiny of foreign technology companies and sets expectations for transparency, security accountability, and consumer protection
Related Articles
- Billions of Exposed Social Security Numbers: The Identity Theft Crisis [2025]
- AI Governance & Data Privacy: Why Operational Discipline Matters [2025]
- FCC Equal Time Rule Debate: The Colbert Censorship Story [2025]
- Data Leadership & Strategy: The Foundation of AI Success [2025]
- Ransomware Targeting Firewalls: The Critical 2025 Security Crisis [2025]
- Prediction Markets Battle: MAGA vs Broligarch Politics Explained
![Texas Sues TP-Link Over China Links and Security Vulnerabilities [2025]](https://tryrunable.com/blog/texas-sues-tp-link-over-china-links-and-security-vulnerabili/image-1-1771519071826.jpg)




