Introduction: The Figure Data Breach That Exposed Nearly a Million
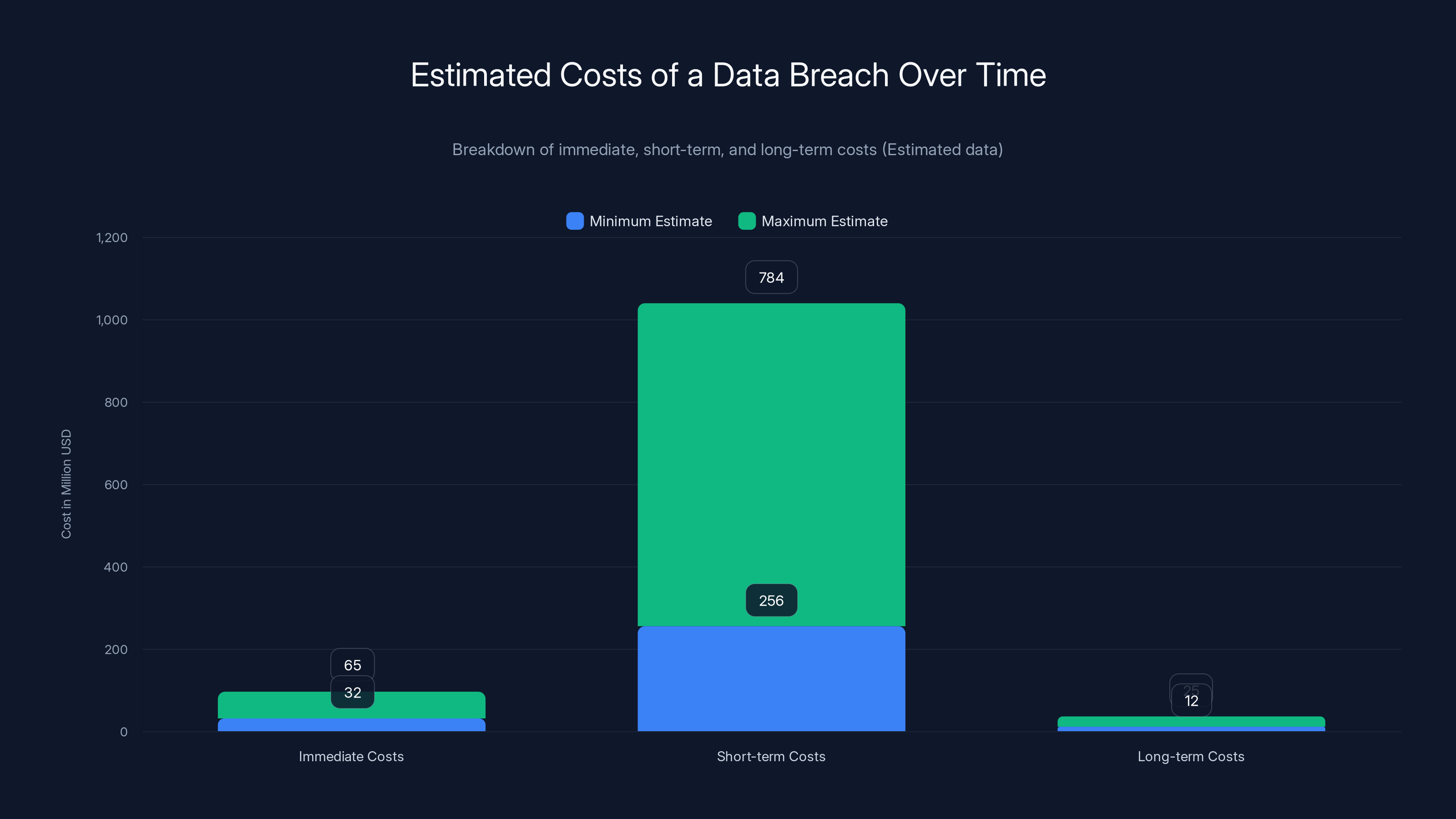
Last week, blockchain-based lending platform Figure Technologies confirmed what many feared: hackers had breached their systems. But the company's initial statement was frustratingly vague. They said attackers stole "a limited number of files" without explaining what that meant or how many people were affected. Then security researcher Troy Hunt stepped in.
Hunt, who runs the breached password database Have I Been Pwned, dug into the stolen data and found something sobering: the breach exposed 967,200 unique email addresses tied to Figure customers. But email addresses were just the beginning. The hackers also grabbed customer names, dates of birth, physical addresses, and phone numbers. This isn't random data loss. This is personal, identifiable information on nearly a million people sitting in the hands of cybercriminals.
The attack came from a group called Shiny Hunters, who published 2.5 gigabytes of stolen data on their leak site. They're using the classic extortion playbook: publish the data, demand payment, and if the company doesn't pay, shame them publicly. Figure, despite multiple attempts to comment, stayed silent. No explanation, no timeline, no apology.
What makes this breach particularly worrying isn't just the number of people affected. It's that Figure operates at the intersection of finance and blockchain, two sectors where hackers specifically target high-value information. When you combine financial data with identity information, you're looking at a perfect storm for fraud, phishing, and identity theft.
This article breaks down everything that happened, why it matters, what Figure customers should do right now, and what this reveals about security failures at fintech companies in 2025.
TL; DR
- Nearly a million compromised: Figure's data breach exposed 967,200 customer email addresses plus names, dates of birth, physical addresses, and phone numbers
- Attackers: Shiny Hunters: Cybercrime group published 2.5 gigabytes of stolen data on their leak site, demanding payment
- Company stayed silent: Figure confirmed a breach but refused to comment on scope, data types, or timeline for notification
- Immediate risk: Exposed personal information puts customers at risk for identity theft, phishing, fraud, and account takeovers
- Security lessons: This breach highlights how fintech companies struggle with security basics like data minimization and breach response transparency
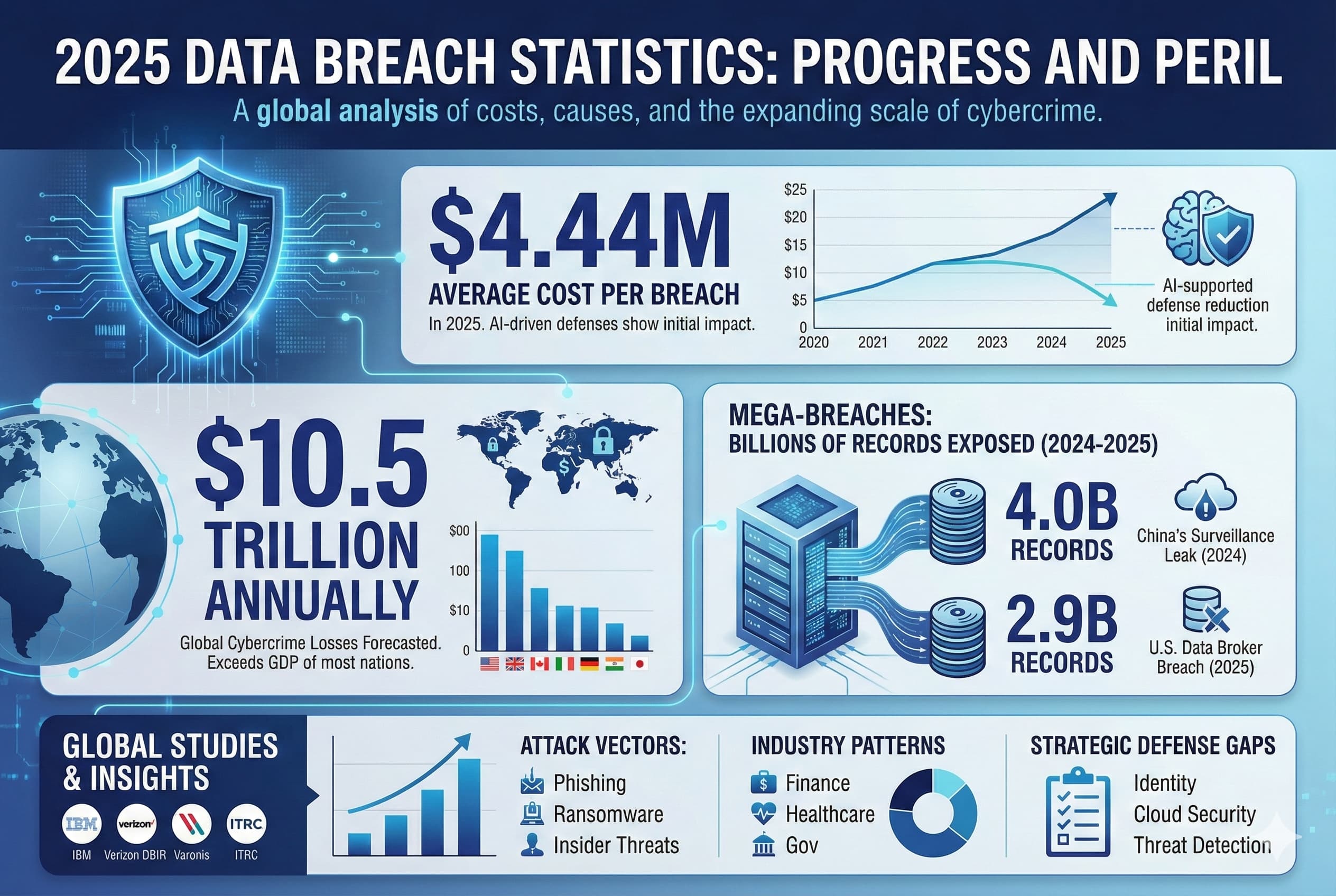
The Figure data breach could cost between $300-700 million, with significant expenses in legal settlements and reputational damage. Estimated data.
What Exactly Was Stolen in the Figure Breach
Let's be specific about what hackers got their hands on. According to Troy Hunt's analysis of the leaked data, the Figure breach exposed:
- Email addresses: 967,200 unique customer emails
- Full names: Names tied to those accounts
- Dates of birth: Complete DOB data
- Physical addresses: Home or business locations
- Phone numbers: Customer contact numbers
This isn't a "limited data loss" as Figure claimed. This is a complete identity profile for nearly a million people. With this information, attackers can:
- Execute phishing attacks: They have real names and company information, making socially engineered emails more convincing
- Commit identity theft: DOB, address, and name are the foundation of most identity fraud schemes
- Facilitate account takeovers: Combined with phishing, this data can be used to reset passwords and access accounts elsewhere
- Enable SIM swapping: Phone numbers are valuable for hijacking accounts that use SMS verification
- Fuel credit fraud: With DOB and address, attackers can apply for credit cards or loans in victims' names
Figure users also hold cryptocurrency and use the platform for lending and borrowing. That means the customer base likely has above-average financial assets, making them high-value targets.
The breach also included metadata about accounts, transaction history, and in some cases, verification documents that customers uploaded. This is the kind of information that doesn't just enable fraud—it enables sophisticated, targeted fraud.
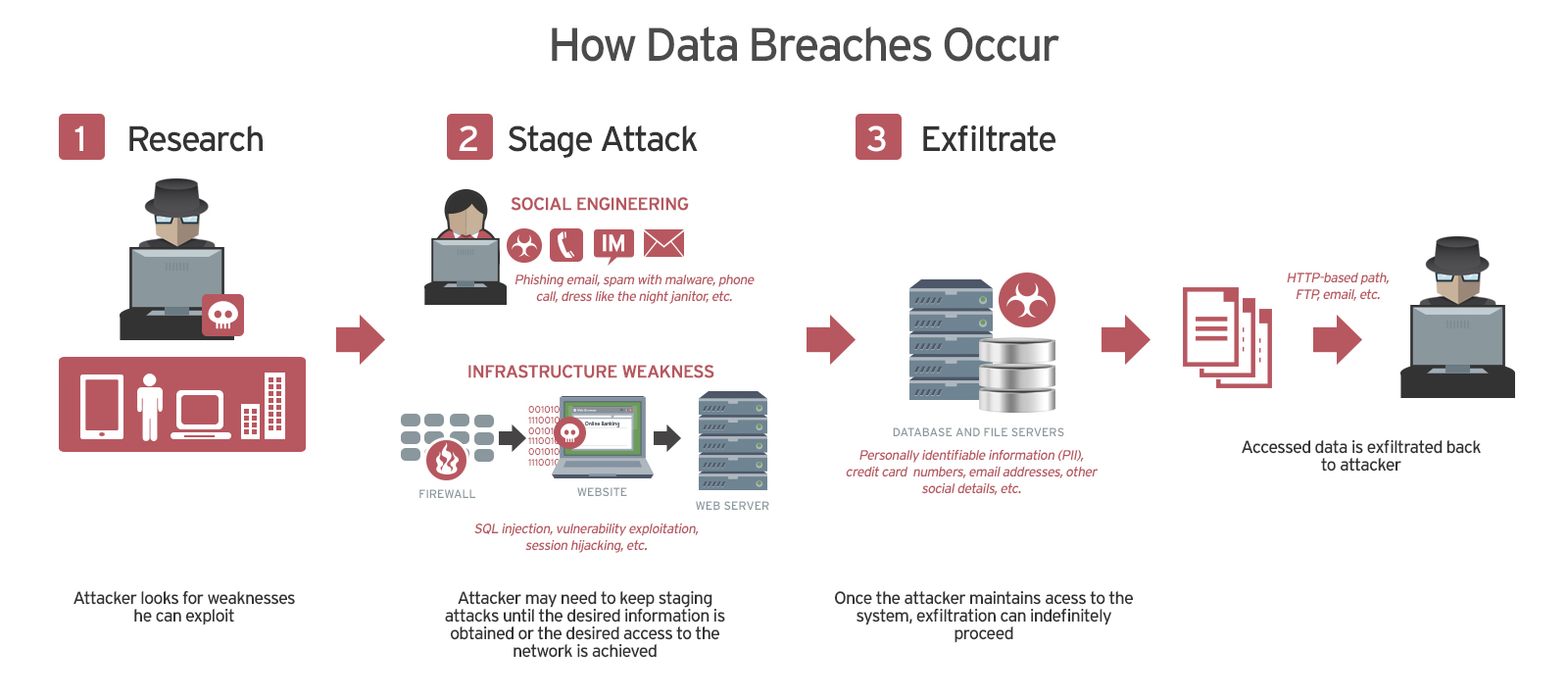
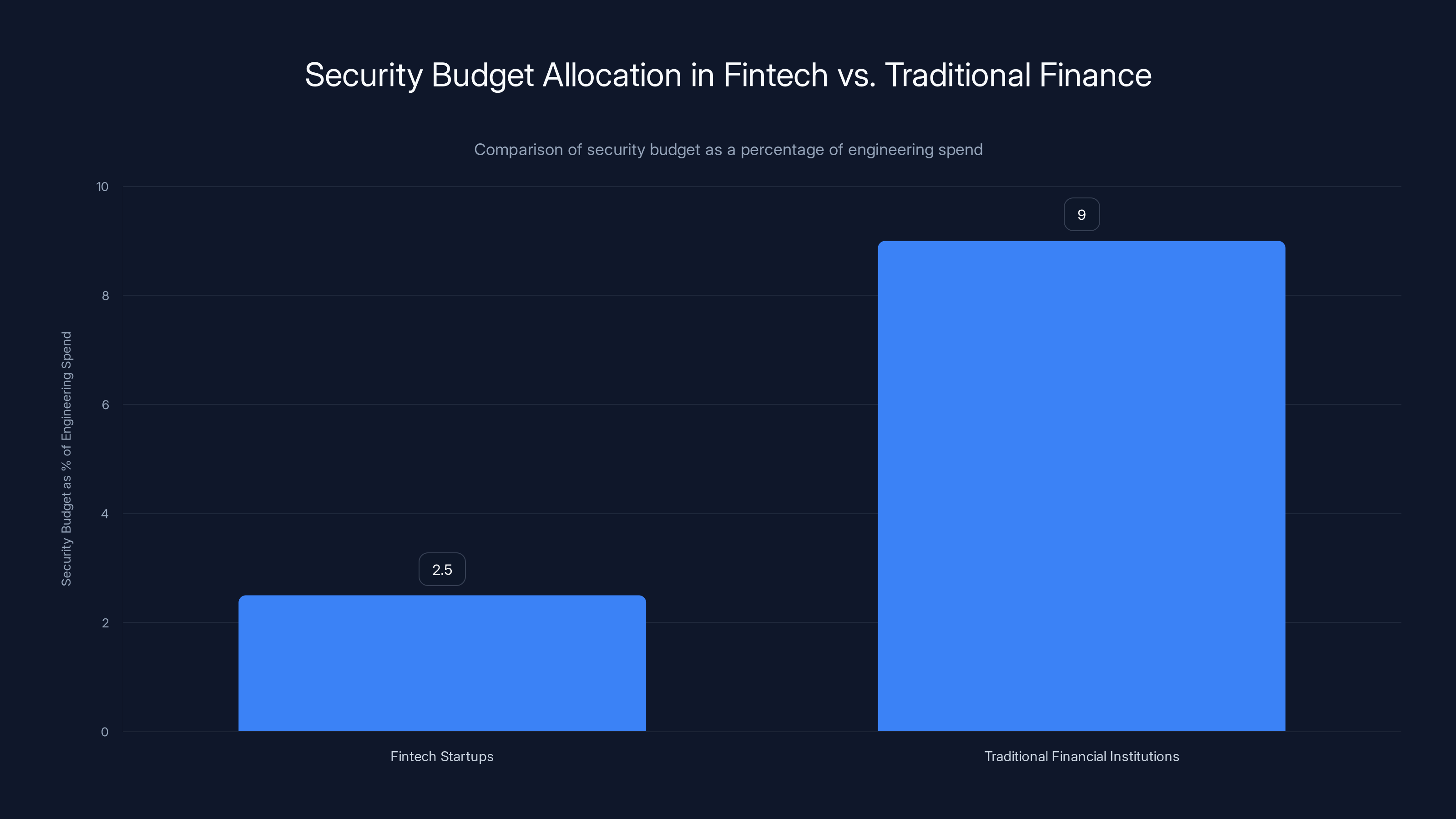
Fintech startups typically allocate only 2-3% of their engineering budget to security, compared to 8-10% in traditional financial institutions. This significant disparity highlights a cultural issue in prioritizing security.
Timeline: How the Figure Breach Unfolded
Understanding the timeline helps explain why this breach was so damaging and why Figure's response was so inadequate.
The cybercrime group Shiny Hunters launched the attack sometime before last week. We don't have an exact date from Figure (they didn't provide one), but the stolen data appeared on Shiny Hunters' leak site last Tuesday. The group claimed credit for the attack and published the 2.5GB of data as proof.
Figure discovered the breach at some point and confirmed it publicly, but without specifics. No date of discovery. No date of when the attack happened. No date when they first identified unauthorized access. This vagueness is intentional in many corporate breach responses, but it's infuriating for customers trying to understand their risk level.
Troy Hunt received tips about the breach and verified the data himself. On Wednesday, he published his findings on Have I Been Pwned, revealing the scope of the breach. Only then did the full picture emerge.
Figure's communications team was contacted multiple times by TechCrunch and declined to comment. Not "we're investigating" or "we'll have details next week"—they just went silent. That silence speaks volumes about the company's security posture and crisis management.
The timeline also suggests Figure either didn't have proper breach detection systems in place, or they detected the breach but delayed public disclosure. Either scenario is bad.
Who Is Shiny Hunters and Why They Target Fintech Companies
Shiny Hunters is a known cybercrime group that's been active for years. They specialize in targeting high-value victims, particularly in the financial services, healthcare, and retail sectors. They're organized, sophisticated, and they have a clear business model: steal data, publish it publicly if companies don't pay extortion demands.
Why fintech? Because fintech companies often have newer security infrastructure than traditional banks, but they handle highly valuable data. They're in that sweet spot of being attractive targets while potentially having fewer defenses than you'd expect. Blockchain and crypto platforms are especially attractive because the customer base is assumed to be tech-savvy and wealthy.
Shiny Hunters operates a leak site where they publish data from companies that refuse to pay extortion fees. The threat is straightforward: pay us, or we release your data publicly and damage your reputation. Most companies refuse to pay because it funds criminal activity and encourages more attacks. But the release of data is costly anyway, leading to legal liability, regulatory fines, and customer trust erosion.
In Figure's case, publishing 2.5GB of customer data is a massive reputational hit. The data is now out there, potentially in the hands of dozens of other criminal groups, forever. No takedown will fully erase it.
What's notable is that Figure still hasn't publicly confirmed whether they received an extortion demand, how much was demanded, or whether they negotiated with the attackers. That information is usually disclosed in Form 8-K filings with the SEC if the company is public, but Figure remains private as of 2025.
Data breach costs can range from
How the Breach Stayed Hidden (And Why That Matters)
One of the most troubling aspects of the Figure breach is how long it apparently remained undetected. We don't have exact dates, but the fact that Shiny Hunters had time to extract 2.5GB of data, publish it, make extortion demands, and have the data verified by a third-party researcher before Figure made any public statement suggests the breach went undetected for weeks—possibly months.
This points to fundamental security failures:
Lack of real-time monitoring: Figure apparently didn't have robust intrusion detection systems that would catch attackers copying massive amounts of data in real-time. Most modern data breaches are caught within days because tools like SIEM (Security Information and Event Management) systems flag abnormal data access patterns. The fact that 2.5GB was exfiltrated without immediate detection is shocking.
No data segmentation: If Figure had properly segmented their customer database, attackers wouldn't have had access to all 967,000 records at once. Modern security practice suggests separating sensitive data into isolated environments with additional access controls. Shiny Hunters clearly had broad access to the entire customer database.
Insufficient access controls: Who had permission to access this data? Attackers typically use compromised credentials or unpatched vulnerabilities to gain initial access. Figure's controls either weren't restrictive enough or weren't enforced properly.
Delayed incident response: Even after the breach was detected internally, Figure took time to go public. This is standard practice (companies get legal and PR advice before announcing breaches), but it means customers had no warning while their data was being actively distributed.
The breach stayed hidden because Figure's security infrastructure simply wasn't adequate. This is a company that handles financial data and blockchain transactions—industries where security should be paranoid, obsessive, and multifaceted. Instead, they apparently let attackers steal a million customer records without triggering any alarms.
The Impact on Figure Customers: Immediate and Long-Term Risks
If you're a Figure customer, what does this breach mean for you? The immediate risks are serious, but the long-term risks might be even worse.
Immediate risks include:
-
Phishing attacks: Criminals now have your name, email, and company information. They can craft convincing spear-phishing emails pretending to be from Figure, asking you to "verify your account" or "update payment information." Even smart people fall for well-researched phishing.
-
SIM swapping and account takeovers: With your phone number and date of birth, attackers can call your telecom provider claiming to be you and request a SIM card replacement. Once they have your number, they can reset passwords on any account that uses SMS verification—which is most accounts.
-
Credit card fraud: Your address and DOB are enough for fraudsters to apply for credit cards or loans in your name. You might not notice until collection agencies start calling.
-
Identity theft: The full profile of information stolen is literally the starter kit for identity theft. Criminals can use it to open bank accounts, apply for loans, or commit tax fraud.
Long-term risks include:
Your data is now in the permanent criminal underground. Even if Figure pays for takedowns or gets law enforcement involved, copies already exist in multiple places. Your personal information could be used for fraud attempts years from now. Criminals sell this data to other criminals, so you're not being targeted by just Shiny Hunters—you're being targeted by a distributed network of fraudsters.
You'll also need to monitor your credit reports, watch for suspicious financial activity, and maintain heightened vigilance for years. This is exhausting.
Figure customers should also consider:
- Changing passwords on Figure and any other accounts using the same password
- Setting up two-factor authentication (not SMS-based) on all important accounts
- Enabling alerts on bank and credit card accounts
- Considering identity theft insurance or monitoring services
- Filing a complaint with the FTC's identity theft reporting system
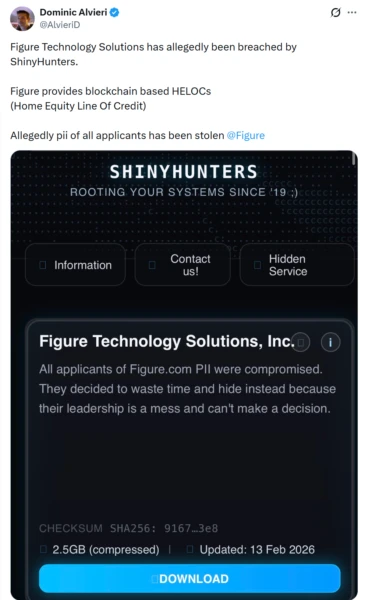
Figure could face over $100 million in liabilities due to state fines, GDPR penalties, class action settlements, FTC penalties, and notification costs. Estimated data based on typical financial impacts.
Regulatory Implications and Legal Liability
Figure now faces significant regulatory and legal exposure. Here's what's likely coming:
State data protection laws: Most states have data breach notification laws that require companies to notify affected customers "without unreasonable delay." Figure must determine whether they've complied. Each violation could mean fines of
GDPR if EU customers were affected: If any Figure customers are in the EU or if any EU citizens' data was in their systems, they're subject to GDPR. The fines there are up to 4% of annual revenue or 20 million euros, whichever is higher. For a fintech with Figure's scale, that's crippling.
SEC filings if Figure is public or has public investors: Companies must disclose material cybersecurity incidents to the SEC within 4 business days. Failing to do so could result in fraud charges or false disclosure lawsuits.
Class action lawsuits: Figure customers will almost certainly file class actions seeking damages for the cost of identity monitoring, credit freezes, time spent managing fraud, and emotional distress. Even if Figure has cyber liability insurance, the coverage might not be enough.
FTC enforcement action: The FTC takes an interest in data breaches at companies that claim to have strong security. If Figure's security practices were inadequate, the FTC could open an investigation and impose consent decrees requiring specific security improvements.
Figure's legal team is probably working around the clock right now. The company could face $100 million+ in total liability when you combine state fines, legal settlements, notification costs, and credit monitoring offers.

How This Breach Compares to Other Fintech Incidents
The Figure breach is significant, but it's not unique. The fintech sector has seen several major breaches in recent years, each revealing similar security weaknesses.
Celsius Network (2022): Crypto lending platform Celsius suffered a breach affecting approximately 4.7 million users. Attackers accessed usernames, emails, phone numbers, and encrypted passwords. Unlike Figure, the actual financial data wasn't directly compromised, but the personal information was enough for phishing and account takeovers.
Gemini (2023): The crypto exchange Gemini had a breach affecting an unspecified number of users. The company was vague about scope and impact, similar to Figure's initial response. This pattern suggests fintech companies have a cultural problem with transparency during security incidents.
Square/Block (2023): Multiple data exposures at Square subsidiary TBD affected employee and customer data. The company handled the breaches better with clear communication, but it still exposed the reality that even well-funded fintech companies have security gaps.
Revolut (2024): The neo-bank Revolut suffered a breach in early 2024 affecting customer data. Again, similar personal information was stolen (names, addresses, phone numbers), and the company was initially vague about details.
What these breaches have in common:
- They all affected personal identifying information
- Initial company statements were vague and insufficient
- The actual scope was revealed by security researchers, not the company
- Customer notification was delayed
- Companies focused on legal liability management rather than victim support
Figure's breach fits a depressing pattern. Fintech companies are growing fast, often prioritizing new features and market expansion over security infrastructure. When breaches happen, they follow a template: minimize public disclosure, engage lawyers and PR consultants, hope it blows over.
Securing accounts and monitoring for fraud are top priorities for Figure customers to mitigate risks. Estimated data based on recommended actions.
Security Failures: A Deeper Analysis
What made the Figure breach possible? Several security failures combined:
Initial compromise: Attackers got into Figure's network somehow. This could have been:
- An unpatched vulnerability in a public-facing application
- Phishing an employee with network access
- Compromised credentials from a former employee
- A supply chain compromise through a third-party vendor
Figure hasn't disclosed this, which is concerning. Understanding how attackers got in is critical for preventing future incidents.
Lateral movement and privilege escalation: Once inside Figure's network, attackers moved around until they found the customer database. This suggests:
- Insufficient network segmentation
- Lack of proper access controls
- No monitoring of unusual login activity
- Attackers had time to explore unmolested
Data exfiltration at scale: Moving 2.5GB of data out of Figure's network without triggering alarms suggests:
- No data loss prevention (DLP) systems in place, or they weren't configured properly
- No monitoring of large data transfers
- Attackers were able to download data directly or through legitimate access channels
Extended dwell time: The fact that Shiny Hunters had time to extract, organize, compress, and publish the data before Figure detected the breach suggests attackers had weeks or months of access. This is an extended "dwell time," and it's the security industry's dirty secret—many breaches go undetected for months.
All of this points to a company that didn't invest adequately in security infrastructure. This might sound harsh, but fintech companies handle financial data. That's the most valuable data in the digital world. Security should be obsessive, not afterthought.
What Figure Should Have Been Doing Differently
Let's flip this around. What would a security-first fintech look like?
Data minimization: Figure shouldn't have needed to store full customer names, addresses, and dates of birth in the same database as transaction data. Sensitive personal information should be stored separately with additional encryption and access controls. "Need to know" principles should be enforced strictly.
Encryption everywhere: All customer data should be encrypted both at rest (stored) and in transit (moving across networks). Even if attackers got database access, they should have found gibberish.
Real-time intrusion detection: Modern SIEM systems can detect when someone accesses unusual amounts of data or logs in from unusual locations. Figure should have had alerts firing when 2.5GB of data was being copied.
Incident response planning: Companies should have written plans for how to respond to breaches: who notifies whom, what information is gathered, how customers are contacted. Figure's delayed, vague response suggests no plan was in place.
Regular security audits: Independent security firms should audit fintech companies quarterly. These audits would have caught the lack of data segmentation and monitoring.
Vulnerability management: Companies should have teams constantly scanning for unpatched systems and known vulnerabilities. Figure's initial compromise likely exploited a known vulnerability that hadn't been patched.
Employee training: Phishing is still the #1 attack vector. Regular security training reduces human vulnerability to social engineering.
None of this is exotic or expensive. These are industry-standard practices. That Figure apparently failed on most of these fronts is damning.

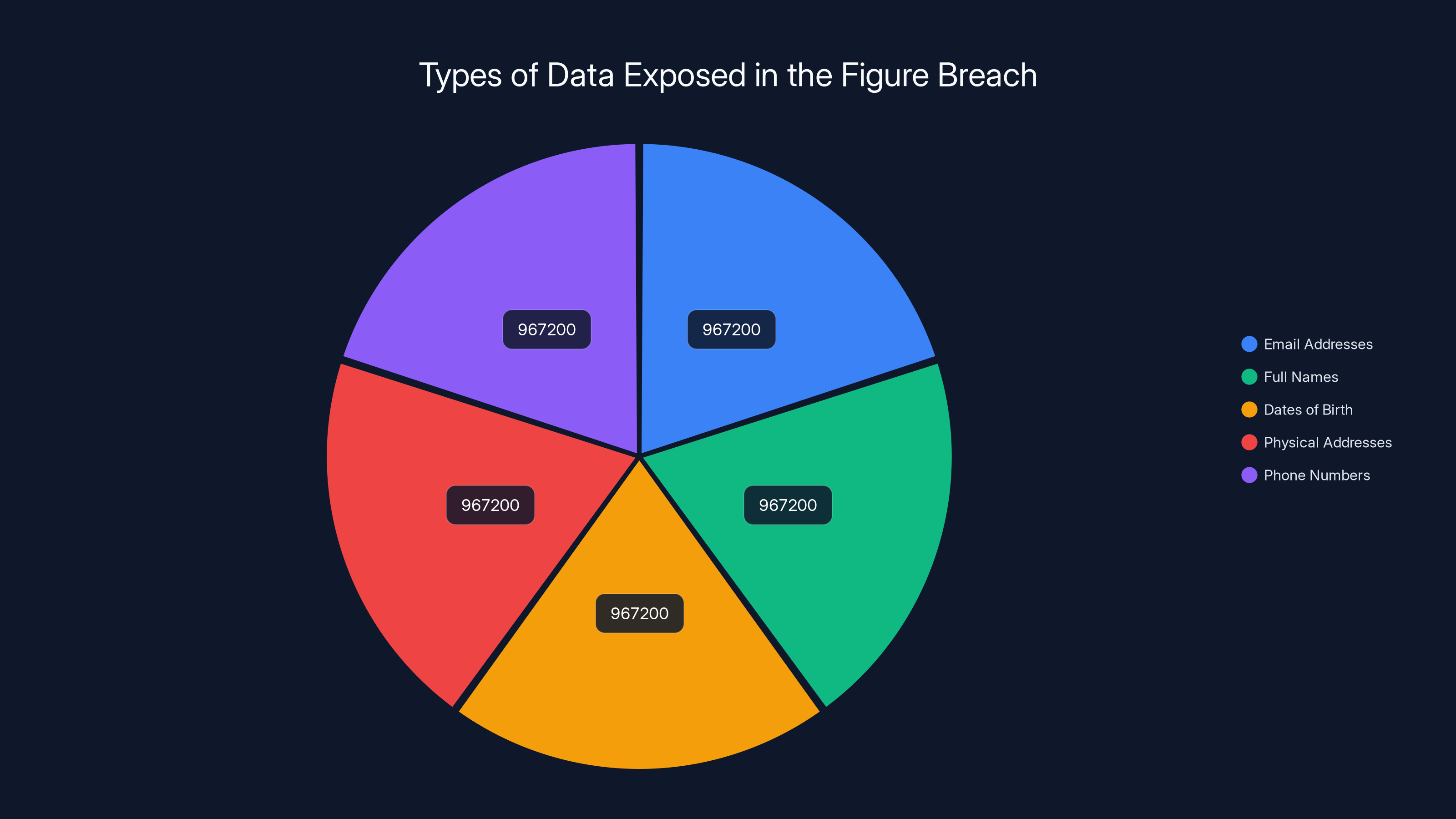
The Figure breach exposed complete identity profiles for nearly a million users, including email addresses, full names, dates of birth, physical addresses, and phone numbers.
The Fintech Security Culture Problem
The Figure breach isn't an isolated incident—it's a symptom of a broader cultural problem in fintech. Here's what's happening:
Fintech companies are startups trying to disrupt banking. They move fast, prioritize features over security, and attract talent from big tech (where security is someone else's problem) rather than financial services (where security is paranoid). Add venture capital pressure to grow fast and raise the next funding round, and security becomes a checkbox, not a core value.
When you talk to fintech founders, they'll tell you they're security-conscious. But in practice, security budgets are often 2-3% of engineering spend, compared to 8-10% at mature financial institutions. The difference is enormous when you scale it up.
Figure, specifically, had raised billions in funding. The company should have had world-class security infrastructure. The breach suggests either:
- They didn't invest in security adequately despite having the resources
- They invested in security theater (policies and certifications) rather than real security
- They know their security is weak but moved forward anyway
None of these are acceptable for a fintech handling customer financial data.
What needs to change: Regulators need to enforce minimum security standards for fintech companies. Not vague guidelines—actual standards: you must use encryption, you must segment data, you must monitor access, you must have incident response plans. Failing these should result in operating license revocation.
Venture capitalists need to ask harder security questions during due diligence. If a company hasn't had external security audits or can't explain their data architecture, that should be a red flag for investment.
And fintech companies themselves need to hire actual security leaders—not just compliance officers, but technical security leaders who have veto power over product launches if security isn't adequate.

Notification Delays and Why Companies Go Silent
One of the most infuriating aspects of the Figure breach is how quiet the company went. They confirmed a breach happened but didn't explain what was stolen or how many people were affected. Why?
Legal strategy: Companies go through lawyers before making any breach announcement. Lawyers want to minimize liability. Any statement could be used against the company in litigation. So statements become vague: "limited number of files," "we're investigating," "no financial data was accessed" (even if true, that's lawyer-speak designed to limit scope).
Determining scope takes time: Companies honestly don't always know immediately how bad a breach is. They have to:
- Identify what systems were accessed
- Determine what data was stored in those systems
- Audit access logs to see what was actually taken
- Verify data integrity
This can take weeks. But customers don't have weeks—they need information now to protect themselves.
PR management: Companies also coordinate with PR firms to manage the narrative. They want to control how the story is told, what sources journalists talk to, when information is released. This is partly legitimate crisis management and partly reputation laundering.
Regulatory requirements: State laws say companies must notify customers "without unreasonable delay." Reasonable is vaguely defined—could be 30 days, could be 60 days. Companies use this ambiguity to delay notification while they figure out their legal and financial exposure.
Figure's complete silence was worse than a bad statement. Silence implies either:
- They don't know how bad it is (incompetence)
- They know how bad it is and don't want to say (deception)
Neither option builds customer trust.
What should happen: Regulators should require initial breach notifications within 48 hours (even if preliminary), with detailed follow-ups weekly until the investigation is complete. Companies should provide customers with credit monitoring and identity theft insurance automatically, not require opt-in. And executives should face personal liability for delayed or false breach notifications.
What Customers Can Do Right Now
If you're a Figure customer or your data might be affected, here are concrete steps to take immediately:
1. Check if you're affected: Go to Have I Been Pwned and search your email address. If it shows up in the Figure breach, assume all your information is compromised.
2. Secure your accounts:
- Change your Figure password to something strong and unique
- Change the password on any other account using the same password
- Enable two-factor authentication on Figure and all financial accounts (use an authenticator app, not SMS if possible)
3. Freeze your credit:
- Contact Equifax, Experian, and Trans Union
- Request a credit freeze (free, permanent until you remove it)
- This prevents anyone from opening accounts in your name without extra verification
4. Monitor for fraud:
- Check your credit reports at annualcreditreport.com (free, all three bureaus)
- Set up alerts on bank and credit card accounts
- Watch for unexpected bills or collection notices
- Consider credit monitoring services (some offer $1 trials)
5. Report to authorities:
- File an FTC complaint at reportidentitytheft.ftc.gov
- File a police report if you suspect fraud
- Report to your state's attorney general
6. Consider legal action:
- Join any class action lawsuit if one is filed (check your email for settlement notices)
- Consult with a personal injury attorney about individual claims
These steps won't prevent all fraud, but they'll significantly reduce your risk and give you some recourse if fraud does occur.
The Broader Question: Is Your Fintech Safe?
This breach raises a deeper question: Is your fintech platform secure? Here's how to evaluate:
Red flags:
- No published security policy or white paper
- Vague statements about encryption or security infrastructure
- No mention of regular security audits
- Previous breaches or security incidents
- CEO/founders with no security background
- No bug bounty program inviting external security researchers
- Rapid growth without proportional security investment
Green flags:
- Published security documentation
- Regular third-party security audits
- Specific details about encryption methods (AES-256, TLS 1.3, etc.)
- A security team with senior leadership (CISO-level)
- Bug bounty program with good researcher reports
- Transparent breach disclosure (if a breach occurred)
- Security certifications (SOC 2 Type II, ISO 27001) with actual audits
Figure apparently had few green flags and many red flags.
Also consider: Does the fintech really need all the data they're collecting? If they're asking for your full date of birth, home address, and phone number when they only need to verify identity for lending, that's a red flag. Data minimization—collecting only necessary data—is both a security best practice and a privacy best practice.
Regulatory Response and Future Enforcement
This breach will likely trigger regulatory responses. Here's what might happen:
OCC and Federal Reserve action: If Figure works with banks or has significant institutional customers, federal banking regulators will likely open inquiries. They're increasingly aggressive about data security at fintech companies.
State attorneys general action: Multiple states' AGs might open investigations for failing to promptly notify customers or for inadequate security practices.
SEC action: If Figure has disclosed anything misleading about cybersecurity or data protection practices, the SEC could open fraud investigations.
FTC action: The FTC has been aggressive about fintech security enforcement. They could open an investigation and ultimately impose consent decrees requiring specific security improvements.
Lawmaker attention: Members of Congress might call for testimony or new fintech security regulations. This is likely if they see a pattern of breaches.
The cumulative effect: Figure will face substantial regulatory pressure regardless of litigation. The company might face operating restrictions, be required to hire a monitor to oversee security, or be prohibited from offering certain services until security is validated by external auditors.
For the fintech industry more broadly, this breach adds pressure for regulations that are currently absent. Unlike banks (heavily regulated), fintech companies can largely do whatever they want. That's changing.
Industry Standards and What's Missing
The cybersecurity industry has developed standards for protecting financial data. Figure apparently didn't follow them. Here's what should be standard:
NIST Cybersecurity Framework: This framework (developed by the National Institute of Standards and Technology) provides guidance on how to identify, protect against, detect, respond to, and recover from cyber attacks. It's not legally required but is the gold standard for financial institutions.
PCI-DSS (Payment Card Industry Data Security Standard): If Figure handles payment cards, they must comply with PCI-DSS, which is actually enforced by card networks. This standard requires encryption, access controls, monitoring, and vulnerability management. If Figure is PCI-compliant, they shouldn't have had this breach.
SOC 2 Type II audits: This is an audit that verifies a company has controls for security, availability, processing integrity, confidentiality, and privacy. Many enterprise customers require this. Figure should have had this.
The fact that Figure had a major breach suggests they either:
- Weren't compliant with these standards
- Were compliant on paper but not in practice
- Didn't have regular audits checking compliance
Any of these scenarios is unacceptable for a fintech.
How Data Breach Costs Compound Over Time
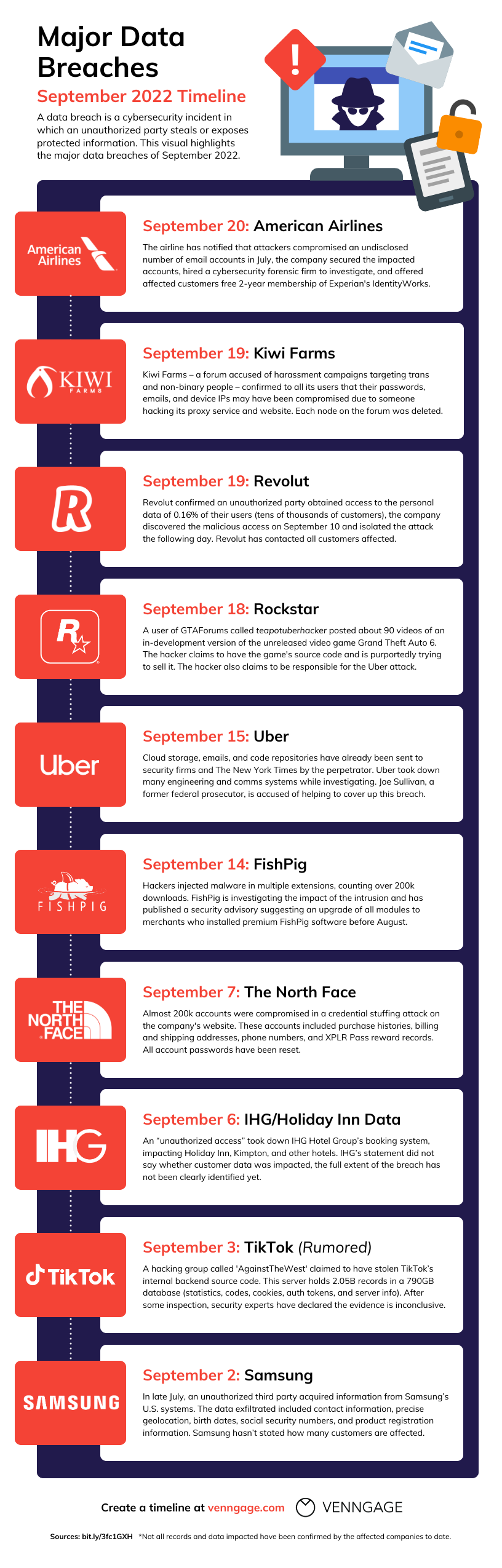
Figure's total cost from this breach will be enormous. Let's estimate:
Immediate costs:
- Credit monitoring offers: Typically 24-48 million**
- Forensic investigation and remediation: $5-10 million
- Legal and PR firm retainers: $2-5 million
- Regulatory notification and compliance: $1-2 million
Short-term costs (year 1):
- State fines: Likely 96-484 million**
- Class action settlements: $50-150 million
- Potential SEC fines: $10-50 million
- Customer churn and lost revenue: Hard to estimate, but potentially $100+ million
Long-term costs:
- Reputational damage and competitive disadvantage
- Increased insurance costs
- Hiring security talent to fix underlying problems
- Regular audits and compliance monitoring
- Potential operating restrictions
Total potential exposure: Easily $300-700 million or more.
For context, this could be 2-10% of Figure's total valuation depending on recent funding rounds. It's a significant event.
The moral: Strong security is vastly cheaper than dealing with breaches. Figure will now spend hundreds of millions trying to fix problems that could have been prevented with a few million in upfront security investment.

Future Predictions: Where Fintech Security Needs to Go
Based on this breach and industry trends, here's what will likely happen:
1. Regulatory tightening: Within 18 months, expect new fintech security regulations at the federal level. These will require minimum security standards, breach notification timelines, and third-party audits. Some states will pass their own requirements too.
2. Capital requirements: Investors will increasingly ask hard security questions before funding fintech startups. Companies with weak security will find it harder to raise money or will have higher capital costs.
3. Insurance costs: Cyber liability insurance will become more expensive for fintech companies, especially those without world-class security. This will incentivize investment in actual security.
4. Talent pressure: Security talent will become more selective about which fintech companies they work for. Companies with poor security cultures will struggle to hire and retain security professionals.
5. Data minimization: Customer privacy becomes a selling point. Fintech companies that collect less data and protect it better will have competitive advantages.
6. Transparency norms: Breach disclosure practices will normalize to faster, more complete information sharing. Companies that do this well will be rewarded with trust.
The fintech industry is at an inflection point. Companies can either invest in real security now or pay far more in regulatory fines, litigation costs, and lost business later.
FAQ
What exactly is Figure and why do they matter?
Figure Technologies is a blockchain-based lending platform that allows users to borrow and lend cryptocurrency and digital assets. They were founded in 2018 and raised significant venture capital funding, making them one of the more high-profile fintech companies. Figure matters because their breach shows that even well-funded fintech companies can have catastrophic security failures affecting nearly a million customers.
How did hackers get into Figure's systems?
Figure hasn't disclosed exactly how the breach happened, which is one of the company's failures. Based on common fintech breach patterns, it could have been an unpatched vulnerability, phishing of an employee with network access, compromised credentials, or a supply chain compromise through a vendor. The lack of transparency is frustrating for customers trying to understand their risk level.
Is my information definitely compromised if I'm a Figure customer?
Yes, if your email address appears on the Have I Been Pwned website for the Figure breach. You should assume your name, address, phone number, and date of birth have been stolen. However, you should check the website to be certain your specific email is in the stolen data.
What's the difference between Figure's initial statement and what Troy Hunt found?
Figure claimed that "a limited number of files" were stolen and initially wouldn't say how many customers were affected. Troy Hunt analyzed the actual data and found nearly a million customer emails plus complete personal information (names, addresses, phone numbers, dates of birth). This massive discrepancy shows Figure was either dishonest or completely incompetent about understanding the scope of the breach.
Should I sue Figure or join a class action lawsuit?
Class action lawsuits will almost certainly be filed against Figure. You should watch for settlement notices in your email from law firms representing Figure customers. You'll likely be able to join without doing anything, and claims can be submitted for time spent on identity monitoring, credit monitoring services purchased, and any fraud that occurred. Individual lawsuits are possible but usually only make sense if you suffered substantial fraud losses.
How long will my personal information be at risk from this breach?
Your information is at risk indefinitely. Once stolen data enters the criminal underground, it's copied, resold, and used across many different fraud schemes for years. However, the acute risk (direct fraud attempts) is highest in the first 12 months after a breach. Credit monitoring and fraud alerts are smart for at least 2 years.
Could this have been prevented with better security practices?
Absolutely. Industry-standard security practices like data minimization, encryption, access controls, real-time monitoring, and regular security audits would have prevented or significantly reduced the impact of this breach. The fact that Figure apparently lacked these basics is damning and suggests the company didn't prioritize security despite handling sensitive financial data.
What should fintech companies do differently after this breach?
Fintech companies should implement minimum security standards including: collecting only necessary customer data, encrypting all sensitive information, segmenting data systems, implementing real-time intrusion detection, conducting regular third-party security audits, maintaining written incident response plans, and training employees on security. Most importantly, they should hire actual security leaders with real authority to enforce these practices.
Will Figure go out of business because of this breach?
It's possible but not certain. Companies have survived major breaches, but it depends on their funding, customer trust, and ability to attract future investment. Figure will face enormous costs and reputational damage, but with sufficient capital reserves and time, they might rebuild. However, customers will have lost trust, which could result in chronic customer loss over years.
How does this compare to other major fintech breaches?
The Figure breach is significant but not unprecedented in scope. Celsius Network affected 4.7 million users, and other fintech breaches have exposed varying amounts of data. What's notable about Figure is the vague initial disclosure ("limited number of files") when the actual breach was massive, and the company's refusal to comment. This pattern of opacity is unfortunately common in fintech.
Conclusion: The Fintech Security Wake-Up Call
The Figure data breach affecting nearly a million customers is a watershed moment for fintech security. It's not the biggest breach ever, but it's important because it exposes a fundamental problem: fintech companies are handling increasingly valuable financial data with inadequate security infrastructure.
Here's what this breach reveals:
First, fintech companies still aren't taking security seriously enough. A company handling customer financial data should have world-class security. The fact that Figure allowed attackers to steal 2.5GB of customer data and remain undetected for weeks suggests fundamental failures in monitoring, access controls, and data segmentation. These aren't advanced security failures—these are basics.
Second, the financial and regulatory costs of breaches are enormous. Figure will likely face $300-700 million in total costs when you combine legal settlements, regulatory fines, credit monitoring, customer churn, and reputational damage. This should incentivize every fintech company to invest aggressively in security infrastructure right now.
Third, customers can't rely on companies to disclose breaches truthfully or quickly. Figure claimed "a limited number of files" when the actual breach affected nearly a million people. Security researchers had to force transparency. This means customers need to protect themselves by monitoring credit reports, freezing credit, and watching for fraud indicators.
Fourth, regulators are finally paying attention. The days of fintech companies operating without oversight are ending. Companies will face new regulatory requirements for security, breach notification timelines, and third-party audits. Those who invest in real security now will have competitive advantages.
What needs to happen:
For customers: Check Have I Been Pwned immediately, freeze your credit with all three bureaus, monitor for fraud, and consider switching to fintech platforms with better security track records.
For fintech companies: Hire actual security leaders (CISOs with real authority), conduct regular independent security audits, implement data minimization practices, and invest in real security infrastructure—not security theater.
For regulators: Establish minimum security standards for fintech companies, enforce breach notification timelines, and impose meaningful penalties for inadequate security practices.
For investors: Ask harder security questions during due diligence. Companies without strong security will face regulatory and legal headwinds.
The Figure breach is a reminder that fintech's rapid growth has outpaced its security maturity. That gap is closing—sometimes painfully. Companies that adapt will thrive. Those that don't will pay enormous costs and lose customer trust they might never recover.
You should take this seriously if you use fintech platforms. Your financial data and personal information are valuable to criminals. You deserve platforms that treat security as a core value, not an afterthought. If your fintech platform isn't actively communicating about security practices, that's a red flag. Consider moving to platforms that take it seriously.
Key Takeaways
- Figure Technologies suffered a major data breach affecting 967,200 customers, exposing names, dates of birth, addresses, phone numbers, and email addresses
- The breach was claimed by cybercrime group ShinyHunters, who published 2.5GB of stolen data and demanded extortion payments
- Figure's initial statement minimized the breach as 'a limited number of files,' but security researcher Troy Hunt revealed the true scope
- Customers face immediate risks including phishing, SIM swapping, identity theft, and long-term fraud stemming from stolen personal information
- The breach reveals systemic security failures: lack of data monitoring, poor access controls, and inadequate incident response that are industry-wide problems
- Figure customers should immediately freeze credit, check Have I Been Pwned, monitor for fraud, and consider joining class action lawsuits
- Total costs to Figure could exceed $300-700 million including regulatory fines, settlements, and lost customer trust
- Fintech companies broadly invest inadequately in security (2-3% of budgets vs 8-10% at traditional banks), creating industry-wide vulnerability
Related Articles
- Billions of Exposed Social Security Numbers: The Identity Theft Crisis [2025]
- Abu Dhabi Finance Summit Data Breach: 700+ Passports Exposed [2025]
- Tenga Data Breach 2025: How a Phishing Email Exposed Customer Data
- Japanese Hotel Chain Hit by Ransomware: What You Need to Know [2025]
- EU Parliament Bans AI on Government Devices: Security Concerns [2025]
- Gabon's Social Media Blackout: Why VPN Demand Surged 8000% [2025]
![Figure Data Breach: What Happened to 967,000 Customers [2025]](https://tryrunable.com/blog/figure-data-breach-what-happened-to-967-000-customers-2025/image-1-1771439873016.jpg)



