Microsoft's Security Leadership Shift: What Gallot's Return Means [2025]
Last year, if you were paying attention to enterprise software leadership moves, you'd have noticed something unusual. Microsoft watched one of its most promising executives walk out the door to join Google Cloud. Hayete Gallot took the role of president, customer experience, at Google in October 2024, seemingly cementing a new chapter in her career trajectory.
Then, maybe six months later, she was back. Not just back at Microsoft, but in one of the company's most critical roles: executive vice president of security, reporting directly to CEO Satya Nadella.
This isn't a small personnel shuffle. This is a signal. And if you work in enterprise security, infrastructure, or cloud services, you need to understand what's actually happening here.
Microsoft's security reputation took catastrophic hits over the past few years. Breach after breach knocked the company off its throne as "the trusted enterprise vendor." The Cyber Safety Review Board's 2024 report wasn't just critical—it was brutal. They said flat out that Microsoft's security culture was inadequate and needed an overhaul. That's not industry jargon. That's "your house is burning down" language.
Gallot's return, alongside the restructuring of Charlie Bell's role (the previous security chief who's now moving to focus on engineering quality), tells us that Microsoft is doubling down on a different approach. This article breaks down what's really happening, why it matters, and what you should be watching for.
TL; DR
- Hayete Gallot returns to Microsoft as EVP of security after just months at Google Cloud, signaling the company's commitment to major security overhaul
- Charlie Bell steps into a new role focused on engineering quality and individual contributor work rather than organizational leadership
- Microsoft's Secure Future Initiative is accelerating security improvements across the entire platform, not just compliance
- The move reflects broader industry trends where executives are rotating back to companies to implement large-scale transformations
- Security is now a competitive advantage for enterprise platforms, and Microsoft is betting heavily on proving it

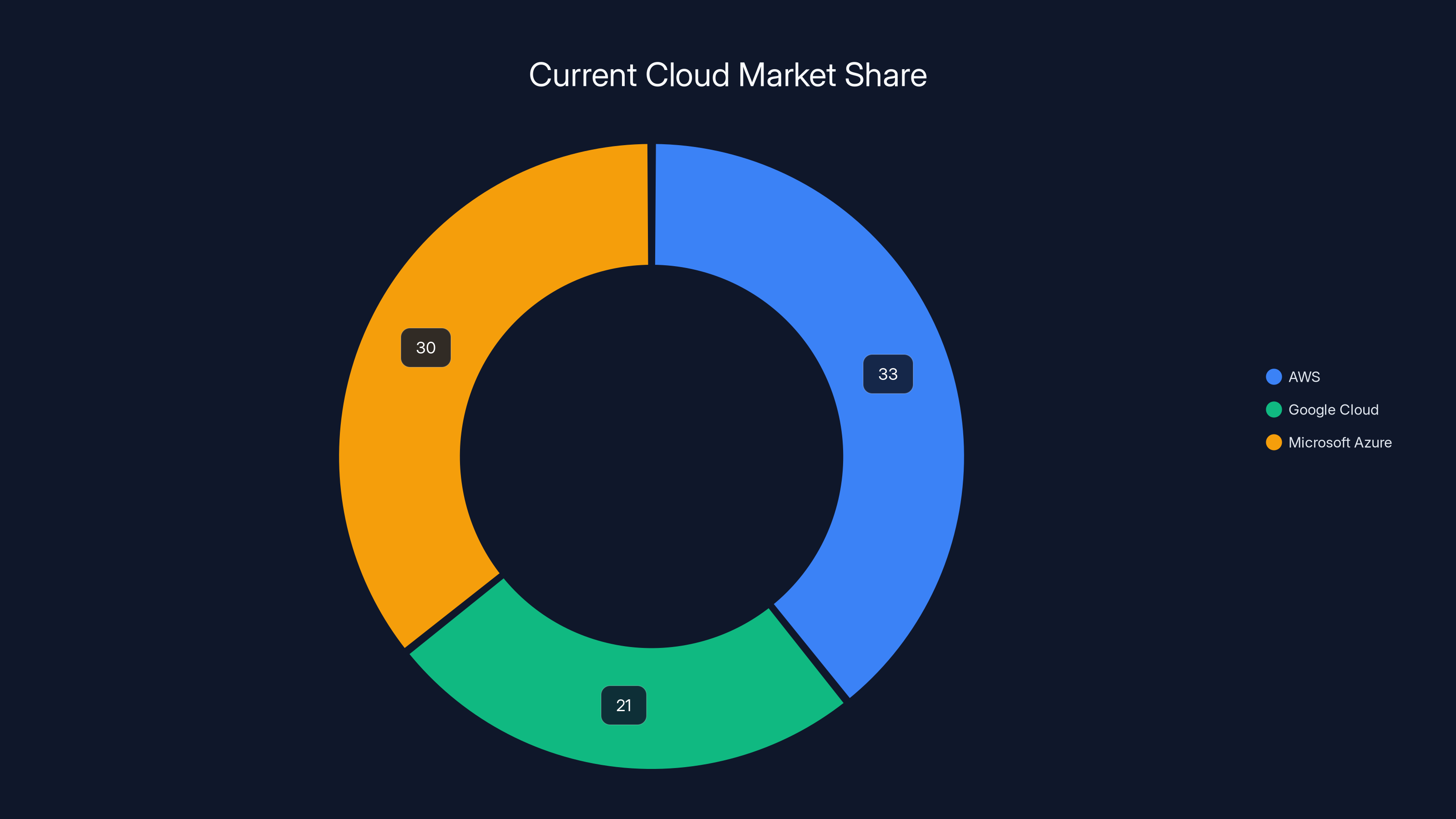
AWS currently leads the cloud market, with Microsoft Azure and Google Cloud following closely. Estimated data based on industry trends.
The Context: Why Microsoft's Security Crisis Matters
You can't understand the Gallot move without understanding just how bad things got at Microsoft. We're not talking about a single incident. We're talking about a cascade.
In 2023 and 2024, CISA and major security researchers uncovered multiple severe vulnerabilities affecting Microsoft's cloud infrastructure. Chinese state-sponsored hackers leveraged a cloud misconfiguration to breach U.S. government email accounts. Think about that for a second. If a nation-state can breach U.S. government systems through your infrastructure, your security posture isn't just broken. It's actively dangerous.
The fallout wasn't just technical. It was political. Congress got involved. Enterprise customers started asking hard questions. Competitors seized the opportunity to market themselves as the "safer choice."
Microsoft's market dominance in enterprise software meant that most companies couldn't just rip out Microsoft products and replace them. But they could pressure Microsoft, demand audits, and start investing in security layers on top of Microsoft's infrastructure. That added cost, complexity, and risk for Microsoft's customers.
The Cyber Safety Review Board's report in March 2024 was the moment of reckoning. The board included representatives from NSA, FBI, CISA, and major security firms. Their conclusion was unambiguous: Microsoft's security culture needed an overhaul. Not improvements. An overhaul. That's the language you use when an organization has fundamentally broken processes.
The report identified specific problems. Microsoft's engineering teams weren't prioritizing security in their development practices. The company had created organizational silos that prevented security information from flowing where it needed to go. There was a gap between what leadership said about security and what actually happened in the code.
This is the environment Hayete Gallot is stepping into. She's not coming back to a stable organization needing incremental improvements. She's coming back to a company that needs to prove it can fix a broken security culture.
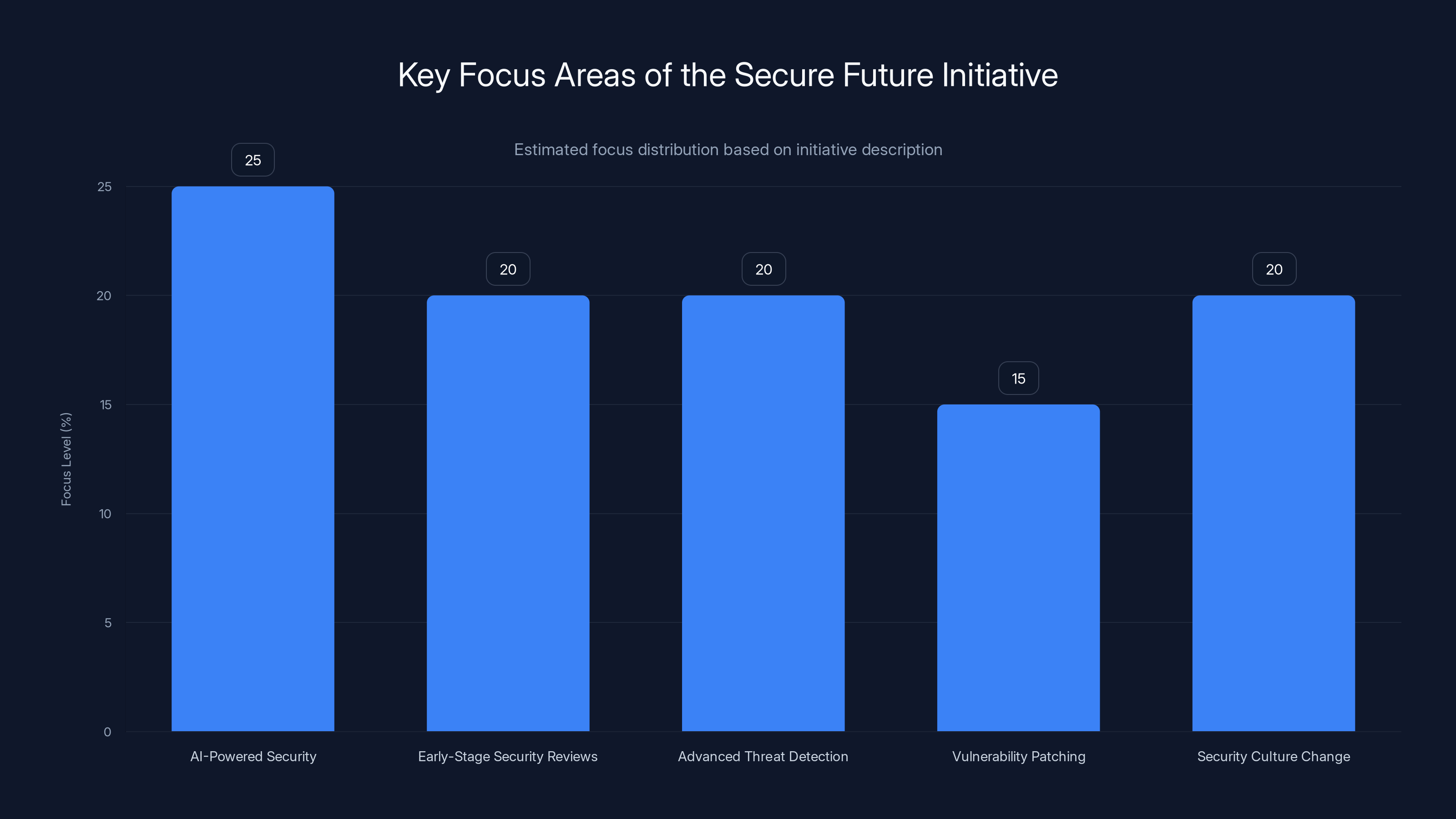
The Secure Future Initiative emphasizes AI-powered security and early-stage security reviews, reflecting a proactive approach to cybersecurity. Estimated data based on initiative goals.
Who Is Hayete Gallot? The Executive Profile
To understand what Gallot's appointment means, you need to know who she actually is.
Gallot spent nearly 16 years at Microsoft before leaving for Google Cloud. That's not a short stint. That's nearly two decades of embedded experience in the company's culture, products, and processes. She didn't spend that time in a single function. She held senior leadership roles across both engineering and sales. That's actually rare at Microsoft, where executives typically specialize in one domain.
Her background in both engineering and sales is crucial. Security leaders who only understand the technical side often struggle to explain why security decisions matter to business teams. Sales leaders who don't understand the technical constraints often push for security theater instead of substance. Gallot apparently had experience bridging both worlds.
When she left for Google Cloud in October 2024, the move seemed strategically sound for her career. Google Cloud is aggressively trying to gain market share from AWS and Microsoft. The customer experience role was high-profile, potentially a stepping stone to even bigger responsibilities. It looked like a conventional tech executive move: proven leader at Company A moves to Company B for a bigger role and equity upside.
Then she came back. In less than a year.
That's the part that matters. Executives don't typically leave lucrative, prestigious roles to return to their previous employer unless something significant changed. Either Google Cloud wasn't what she expected, or Microsoft made an offer she couldn't refuse, or both.
Nadella's statement about Gallot is revealing: "She brings an ethos that combines product building with value realization for customers, which is critical right now." That's not just complimentary language. That's describing exactly what Microsoft needs. A leader who understands that security isn't just a compliance box to check. It's a product feature that customers will pay for and that directly affects revenue.

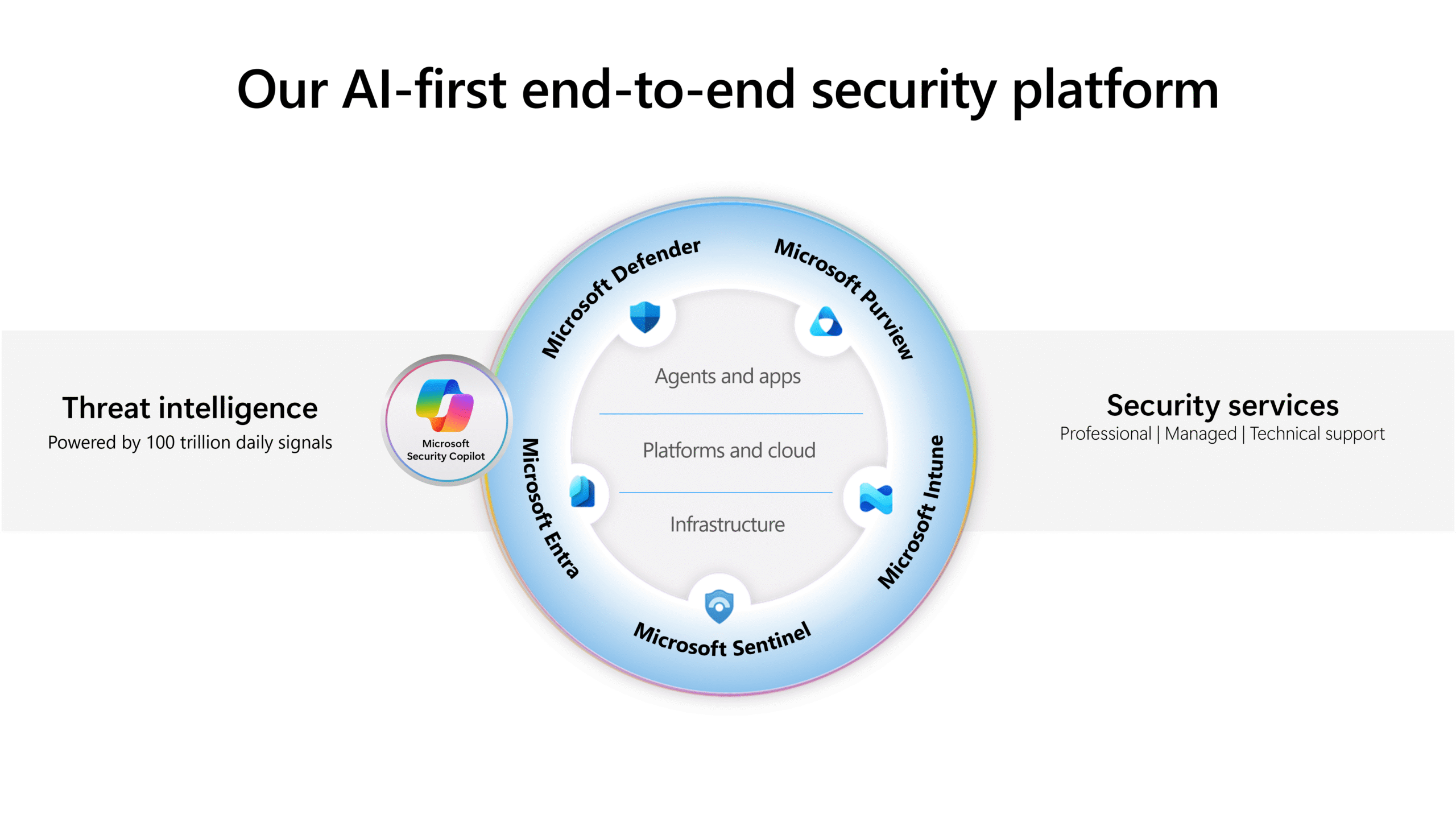
The Secure Future Initiative: Microsoft's Moonshot
Microsoft didn't wait for the Cyber Safety Review Board's report to start fixing security. The company launched the Secure Future Initiative (SFI) months before the report was published, right after the Chinese hacking incident. This wasn't a public relations move. This was serious operational restructuring.
The SFI is comprehensive in scope. It's not just about patching vulnerabilities or implementing new tools. It's about changing how the entire company approaches security in development, deployment, and operations.
One of the most significant aspects of SFI is the focus on "secure by design" principles. Instead of building features first and adding security afterward, Microsoft is trying to make security part of the initial architecture of new products. This requires changing how engineers are trained, how they're evaluated, and what decisions they prioritize.
Implementing this kind of cultural change is extraordinarily difficult. Engineers want to build features that users can see. Security decisions often create constraints that slow down feature development. You need a leader who understands both the technical reality and the cultural dynamics well enough to navigate between them.
The SFI also involves significant investment in security tooling and infrastructure. Microsoft is building new systems to detect anomalies in cloud activity, flag suspicious behaviors, and enable faster incident response. But tools alone don't fix security culture. You need people, processes, and accountability.
Gallot's appointment signals that Microsoft is treating SFI as a multi-year transformation, not a temporary initiative that will wind down once "security looks better." She's coming back as EVP reporting directly to the CEO. That's boardroom-level authority. That's the kind of appointment that signals this is a core business priority, not a compliance project.
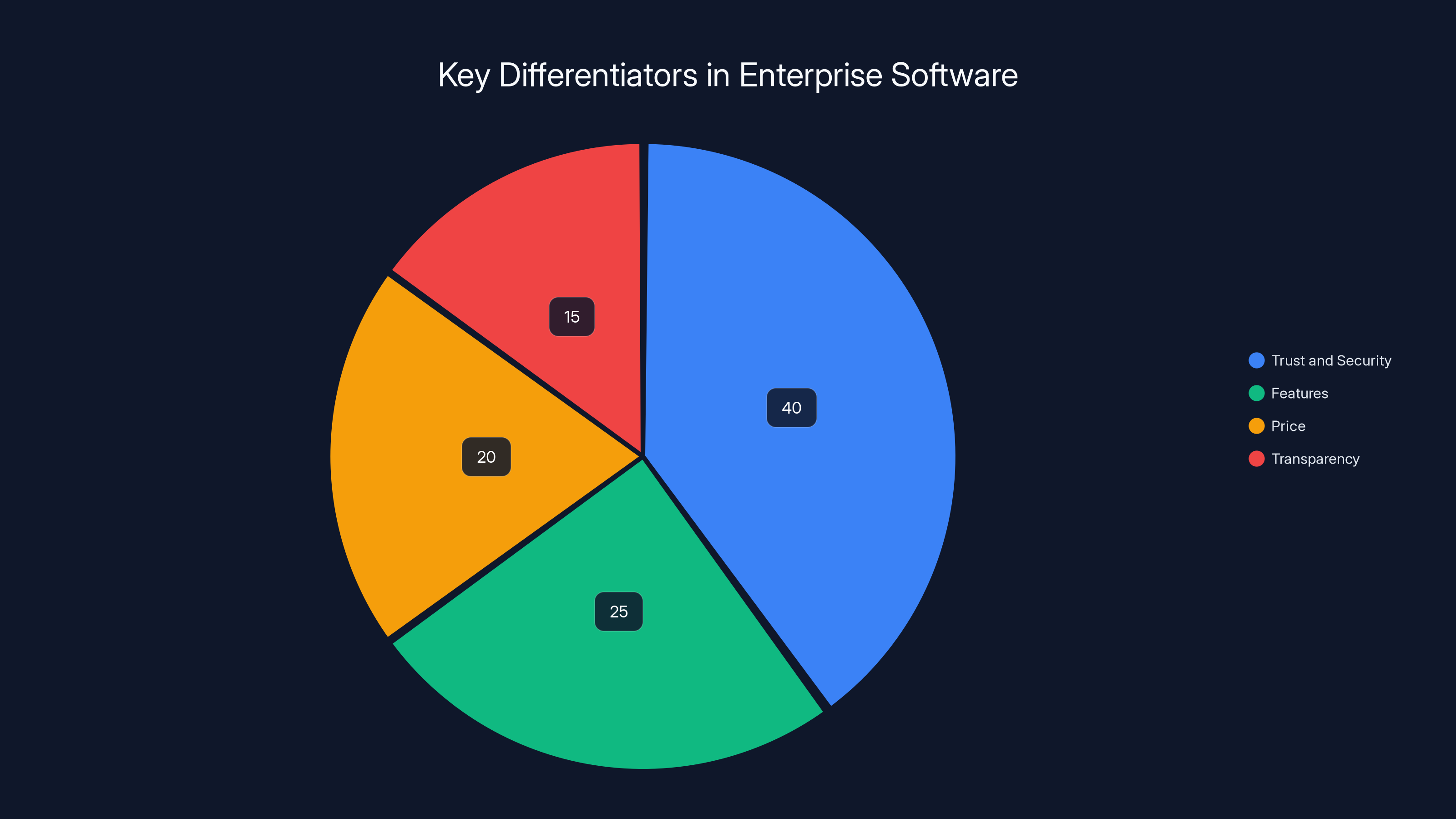
Estimated data suggests trust and security will be the primary differentiators in enterprise software, surpassing features and price.
Charlie Bell's New Role: The Quality-First Engineering Shift
The other part of this announcement is equally important: Charlie Bell is stepping out of the security leadership role and moving into engineering quality.
Bell spent nearly five years leading Microsoft's security, compliance, and identity teams. That's a meaningful tenure during a turbulent period. He built the initial structure of the Secure Future Initiative. He was involved in the operational response to major breaches.
Now he's explicitly moving from organizational leadership to what Nadella calls an "IC engineer" role, IC meaning "individual contributor." This is actually a significant career move, and understanding it matters.
In large tech organizations, the assumption is that "promotion" means moving into management. Bigger team, more direct reports, higher title, better comp package. An executive moving into an individual contributor role looks like a step backward. But Nadella's framing suggests it's actually a lateral move with different focus.
Bell apparently wanted out of organizational leadership. Managing teams, attending meetings, handling personnel issues, managing budgets—these are draining responsibilities for someone who's more interested in technical problems. By moving into engineering quality, Bell can focus on the actual technical challenges of making Microsoft's code and infrastructure more reliable.
This also sends a signal to Microsoft's engineering organization: you don't have to move into management if that's not where your skills are. You can specialize deeply in technical domains and maintain executive-level influence and compensation. That's actually important for organizational health. Not every great engineer wants to manage people.
But it also suggests that the security work in Microsoft is moving from "fix the basics" to "drive transformation." Bell fixed the immediate problems. Gallot is coming in to embed security throughout the organization's DNA.

What Gallot's Background in Sales Brings to Security Leadership
Here's where Gallot's dual background becomes really important. She's not just an engineer who moved into security. She's been deeply involved in sales.
In enterprise software, security has traditionally been a "blocking" function. Security teams say no. They create friction. They slow down product launches. From a sales perspective, security people are obstacles. From a security perspective, sales teams are reckless risk-takers who care more about closing deals than protecting systems.
This dynamic is poisonous. And it's exactly what contributed to Microsoft's security problems. When security is positioned as opposed to business success, engineers find ways to work around security requirements. Sales teams pressure engineers to cut corners on security to hit release dates. Executives don't have clear visibility into the trade-offs being made.
Gallot's background in sales means she understands what sales teams actually need and care about. She knows the pressures they face. She also understands that security, when implemented correctly, can be a competitive advantage. A platform that's genuinely secure is more trustworthy. Trustworthy platforms win enterprise deals.
Microsoft needs to flip the narrative. Security shouldn't be "the thing that slows us down." Security should be "the thing that makes customers confident enough to bet their business on us."
This is already starting to happen in the market. Enterprise customers now explicitly ask about security certifications, vulnerability response times, and breach history when evaluating cloud platforms. Security is a product feature that directly affects deal probability and deal size.
Gallot's job is to embed this understanding throughout Microsoft's organization. Not just in the security team, but across engineering, product management, and leadership.

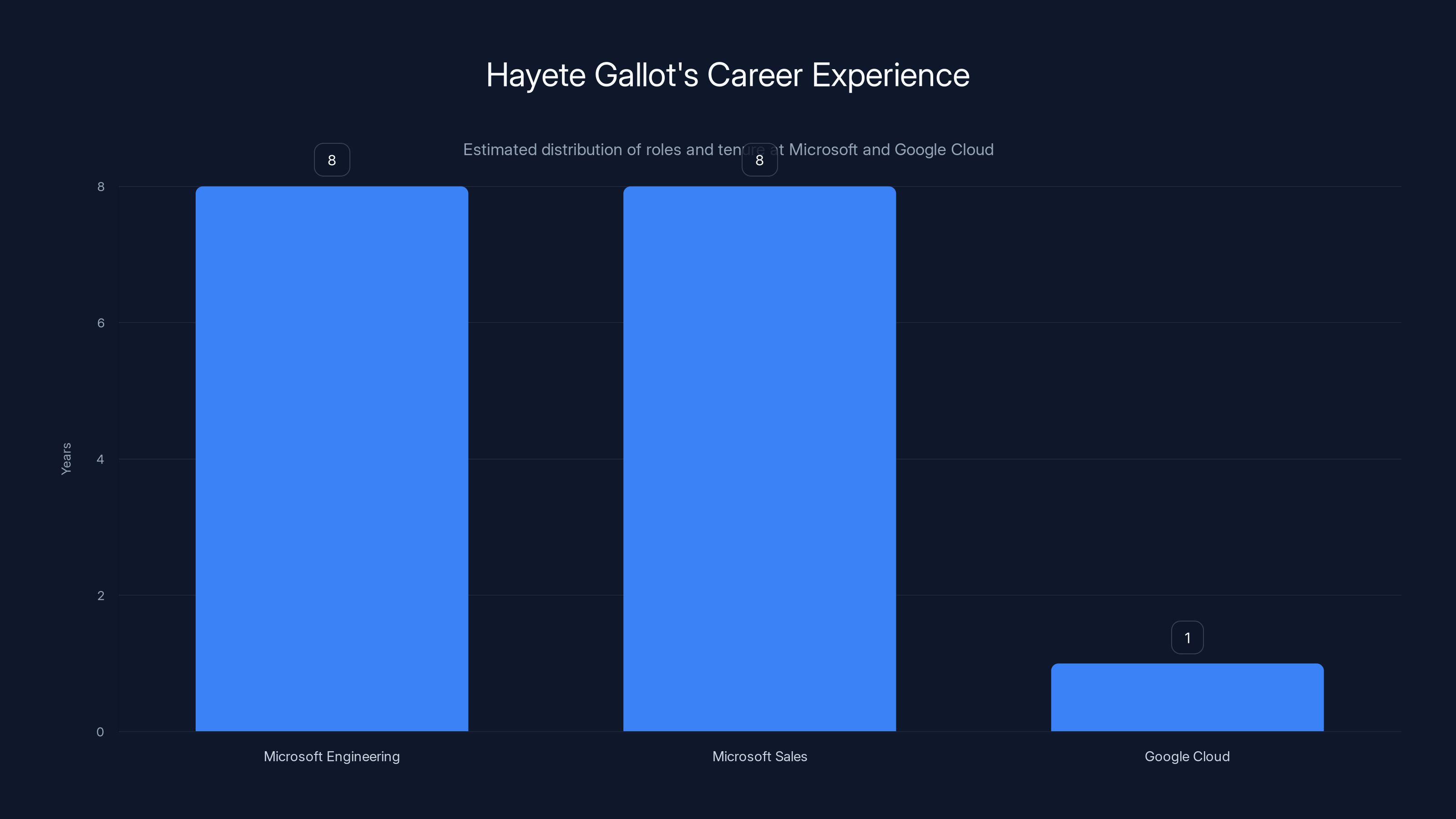
Hayete Gallot spent an estimated 16 years at Microsoft, evenly split between engineering and sales, before a brief tenure at Google Cloud. Estimated data.
The Broader Industry Trend: Security as a Competitive Battleground
Microsoft's move isn't happening in a vacuum. It's part of a much broader shift in how the enterprise software industry treats security.
Five years ago, most cloud platforms competed on features, price, and integration breadth. Security was table stakes, but not a differentiator. You had to be secure enough, but being more secure than competitors wouldn't move the needle.
That's completely changed. AWS now markets security as a core competitive advantage, with entire service lines dedicated to compliance and threat detection. Other cloud providers are following suit.
This shift is driven by real changes in the threat landscape. Ransomware attacks are more sophisticated. Nation-state actors are actively targeting enterprise infrastructure. Regulatory requirements are tightening. Customers are desperate for platforms they can trust.
For Microsoft, this is both a crisis and an opportunity. The crisis is that they lost trust. The opportunity is that trust can be rebuilt, and a company that genuinely fixes security can regain market position.
Gallot's appointment is Microsoft saying: "We're going to win security back. Not by complying with regulations. By building a security-first culture."

The Secure Future Initiative in Detail: What's Actually Happening
Let's get specific about what the Secure Future Initiative actually entails. This matters because it's where strategy becomes reality.
First, the SFI involves restructuring how security decisions are made in engineering. Traditionally at Microsoft, security reviews happened late in the development cycle. A product team would build something, then security would review it and identify problems. This created pressure to either rework the product (expensive and time-consuming) or find workarounds (technically unsound).
The new approach is security involvement from day one. Before engineers start writing code, security architects are in the room discussing threat models. As code is written, security tools flag problems in real time. This requires different tooling, different processes, and different training for engineers.
Second, the SFI is about building security infrastructure that actually works at scale. Microsoft's cloud operates at an enormous scale. Billions of requests per day. Petabytes of customer data. Millions of virtual machines. Traditional security approaches don't work at this scale. You need systems that can automatically detect anomalies, flag suspicious patterns, and respond quickly without human intervention.
Microsoft is investing heavily in AI and machine learning for security operations. Not just for compliance automation, but for actual threat detection. The idea is that most legitimate enterprise traffic follows patterns. When something breaks those patterns, systems automatically investigate and escalate.
Third, the SFI involves changing how Microsoft manages vulnerabilities and patches. The company has been criticized for slow patch release cycles and poor communication about severity. The new approach is faster, more transparent patch release and much more aggressive vulnerability disclosure.
Fourth, and this is crucial, the SFI involves governance changes. The company is bringing security into budget decisions, product planning, and executive review. Security isn't just a function anymore. It's a dimension of every business decision.
These kinds of changes are extraordinarily difficult to implement. You're asking large organizations to fundamentally change how they work. That requires top-cover from the CEO and board. It requires leadership committed to making hard trade-offs. It requires patience with the fact that this takes years, not months.
Gallot's appointment signals that Microsoft's board and leadership are willing to do all of this. This is not a temporary initiative that will be wound down. This is a multi-year transformation.

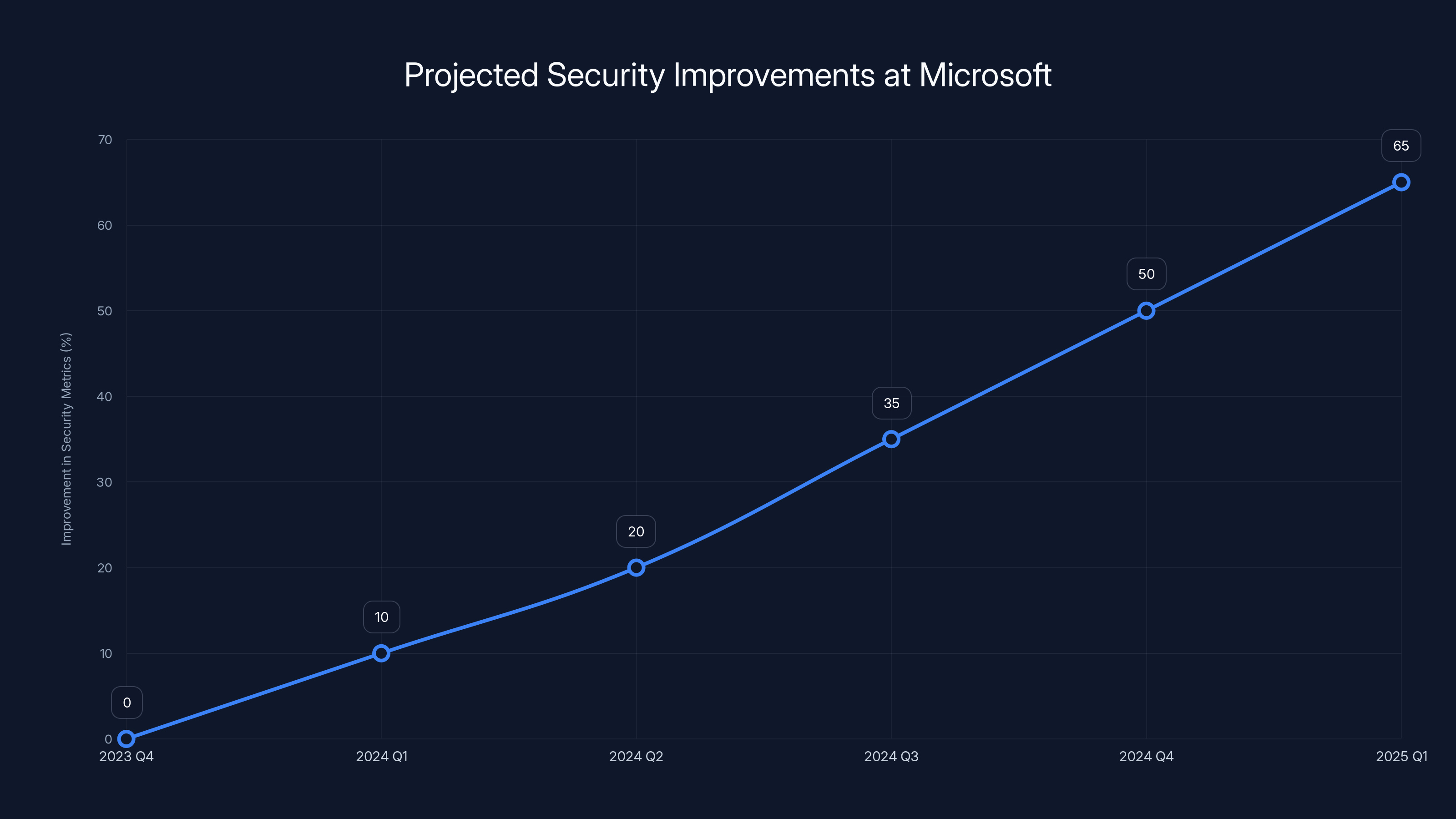
Estimated data suggests Microsoft aims for a 65% improvement in security metrics by early 2025, reflecting their commitment to transforming security culture.
The Enterprise Customer Perspective: What This Means for You
If you work in enterprise IT, procurement, or security, you should care deeply about this announcement.
For the past year, many organizations have been having serious conversations about reducing Microsoft dependency. These conversations range from evaluating alternative cloud providers to consolidating on specific Microsoft services and integrating alternative tools.
Microsoft's security problems made these conversations more urgent. When a major breach affects your vendor's infrastructure, it affects your risk profile. It forces you to make expensive compensating investments in security tooling.
Gallot's appointment is Microsoft signaling that the company is getting serious about fixing the underlying problems, not just responding to incidents.
For enterprise customers, this matters because it affects long-term platform decisions. If Microsoft genuinely rebuilds security culture and implements the Secure Future Initiative effectively, the company's trustworthiness goes up. That means customers can reduce defensive spending. It means longer-term partnerships become more viable. It means you can potentially consolidate on Microsoft services instead of building multi-vendor stacks.
But here's the key: this takes time to prove. You can't just trust Microsoft on faith. You need to see evidence. You need to see security improvements in their products. You need to see faster patch cycles. You need to see transparent communication about vulnerabilities.
The next 18 months are critical. Gallot has maybe two years to show real progress before customers make longer-term commitments based on her leadership. If Microsoft doesn't deliver measurable improvements, customers will start seriously evaluating alternatives. If Microsoft does deliver, the company's competitive position strengthens significantly.

The Silicon Valley Boomerang Effect: Understanding Executive Mobility
Gallot's move from Microsoft to Google Cloud and back is worth understanding in the broader context of tech executive mobility.
Traditionally, successful Silicon Valley executives move in one direction: up and out. You build expertise at Company A, get recruited to Company B, make a big splash, then move to a more prestigious company or role. The best executives rarely go backward.
But that pattern is shifting. We're seeing increasing numbers of executives who left one company returning to it a few years later, often in even more senior roles. Why?
There are several factors at play. First, the "dream opportunities" are fewer. There are only so many CEO roles or founder-track positions available. Many executives top out on external opportunities and realize their previous employer actually has more upside.
Second, large tech companies are increasingly facing existential problems that require specific expertise. Microsoft's security crisis required someone who understood not just security, but how to build trust with customers and navigate organizational politics. Gallot had proven track record in all three areas.
Third, the compensation gap between returning as a more senior executive and accepting a lateral move elsewhere has narrowed. Microsoft's willingness to bring Gallot back as EVP reporting to the CEO, with presumably significant equity and authority, is likely a more attractive position than what she had at Google.
But the deeper story is about organizational problem-solving. Technology company leaders are increasingly recognizing that the best person to fix a specific problem might be someone who used to work there. You're not starting from zero. They know the culture, the code base, the politics, the key people. They can move faster and more effectively.
This is good news for Microsoft's security efforts. Gallot doesn't need a year to understand the organization. She can hit the ground running and start making changes immediately.

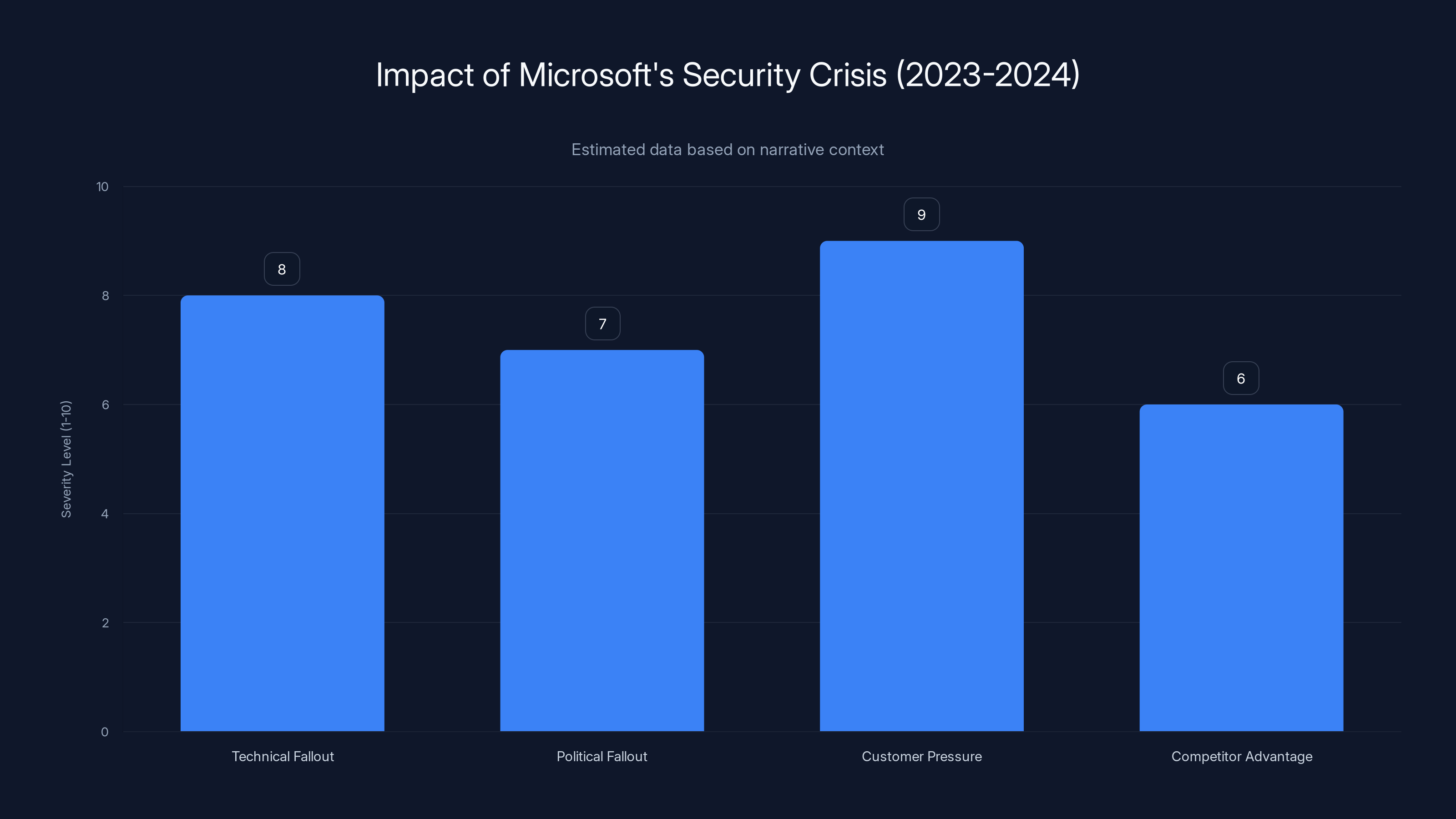
The security crisis at Microsoft had a severe impact across technical, political, and customer domains, with customers exerting significant pressure and competitors gaining an advantage. (Estimated data)
Implementation Challenges: Why This Is Harder Than It Looks
Understanding that Gallot's appointment is important is different from understanding what she's actually going to face.
Building security culture in a massive organization is extraordinarily difficult. Microsoft has hundreds of thousands of employees. The company has built products over decades, many of which were never designed with modern security standards in mind. You can't just rewrite everything.
There's also the problem of time. Nadella hired Gallot to implement the Secure Future Initiative. But how long does this actually take? Security culture change at this scale? Probably three to five years minimum. During that time, any security incidents will be scrutinized through the lens of "is the new leadership failing?" Even if the incident is legacy code behavior, the timing is brutal.
There's also the organizational resistance problem. Large organizations have organizational antibodies. When you try to change how things work, people find ways to resist. The engineer who finds a security requirement inconvenient will find ways around it. The manager who feels security is blocking their product launch will lobby against new processes.
Gallot will need air cover from Nadella to push through this kind of resistance. If Nadella's support wavers, the initiative will slow down and eventually fizzle.
There's also the problem of external perception. No matter how good Microsoft's security becomes, any incident will be covered as "Microsoft has another security problem." The company is starting from a position of low trust. Rebuilding that is a multi-year effort.
And then there's the technology problem. The actual tools and infrastructure that Microsoft is building to implement security at scale? That's genuinely hard engineering. There's no off-the-shelf solution. Microsoft has to build custom systems that work at their unique scale and complexity.
Market Dynamics: How This Affects Cloud Competition
Microsoft's security problems have been a gift to competitors. AWS and Google Cloud have been able to position themselves as "more trustworthy." Both companies have strong security track records, though they've had their own incidents.
Gallot's appointment changes the competitive dynamic. If Microsoft successfully rebuilds security culture, the company regains a key competitive advantage. Enterprise customers might shift from defensive multi-vendor strategies back to consolidated Microsoft deployments.
AWS and Google Cloud know this. The best time for them to lock in customers is right now, while Microsoft's trust is still damaged. Once Microsoft rebuilds reputation, winning customers back becomes much harder.
This creates intense competitive pressure over the next 18 to 24 months. All three major cloud providers will be pushing hard to win enterprise commitments. Microsoft is pushing to prove it's secure. AWS and Google are pushing to convince customers that the damage is permanent.
The winner will likely be the company that demonstrates the most measurable progress toward their claims. This is why transparency about security improvements is so important. If Microsoft can show quantifiable metrics around patch response time, vulnerability disclosure, security testing, and threat detection, they can win customers back.

The Role of Artificial Intelligence in Modern Security
One aspect that hasn't received enough attention in the Gallot announcement is the AI dimension.
Microsoft is deeply invested in AI. The company has a major partnership with OpenAI. But AI security is genuinely hard. Large language models can be tricked into behaving in unexpected ways. AI systems can amplify human biases. AI-powered security tools can make mistakes with serious consequences.
Gallot's mandate almost certainly includes figuring out how to implement security for Microsoft's AI-first future. The company's enterprise software is increasingly AI-integrated. Azure is increasingly AI-capable. But what does security mean in an AI context?
This is one of the most important and least understood challenges in enterprise software. Gallot is probably walking into an organization where the engineering teams are excited about AI but the security implications are underexplored.
Her job includes figuring out how to build AI systems that are both powerful and trustworthy. This is fundamentally harder than traditional security because AI behaves in ways that are harder to predict and harder to audit.

Timeline and Expectations: What to Watch
Gallot's appointment is essentially a reset. Microsoft is saying: "We're taking security seriously now. Give us time to prove it."
What should you watch over the next 12 to 24 months?
First, watch for measurable improvements in security metrics. Patch response time. Vulnerability disclosure timeframes. Security testing coverage. These should all improve. If they don't, the appointment was just personnel reshuffling, not real commitment.
Second, watch for organizational changes. How many people is Gallot hiring? Where is she positioning security in the organization? Is security integrated into product teams or siloed? The structure she builds will determine whether culture change actually happens.
Third, watch for customer testimony. Are enterprise customers expressing more confidence in Microsoft's security? Are migrations away from Microsoft slowing down? Are security incidents being handled better? These are the real measures of success.
Fourth, watch for transparency. Is Microsoft communicating openly about security incidents and how they're being fixed? Or is the company reverting to defensive postures? Transparency is a key indicator of cultural shift.
Fifth, watch for product changes. Does Microsoft's security product suite improve? Are there new capabilities that reflect lessons learned? Are tools that previously had gaps getting fixed?
If all of these things are happening, the appointment is real and transformative. If only some are happening, or if progress stalls after initial momentum, then Microsoft hasn't solved the underlying problems.

What This Means for the Broader Enterprise Software Industry
Microsoft's move is going to reverberate through the industry.
Other large tech companies have security cultures that are probably also problematic in ways they don't fully acknowledge. The Cyber Safety Review Board's willingness to publicly criticize Microsoft might embolden similar criticism of other major vendors.
Enterprise customers, emboldened by seeing Microsoft take security seriously enough to make executive-level changes, might start demanding similar commitments from other vendors. Procurement teams might start asking AWS and Google why they don't have equivalent high-level security transformation initiatives.
Security leaders within other tech companies are probably watching Gallot's tenure closely. If she succeeds, it validates the idea that security leadership needs executive-level authority and resources. If she fails, it sends a message that security culture change is impossible at massive scale.
There's also a message here about accountability. The Cyber Safety Review Board's public criticism of Microsoft forced this response. If other industry actors face similar public scrutiny, they'll be forced into similar responses. This is actually a healthy dynamic for enterprise customers.

The Human Element: Why Leadership Matters More Than Technology
Here's what's often overlooked in these kinds of discussions: security culture change is primarily a human problem, not a technology problem.
You can buy the best security tools in the world. You can implement the most sophisticated threat detection systems. But if the engineers building your products view security as an inconvenient constraint rather than a core value, bad things will happen.
Gallot's job isn't to implement new technology. It's to change how 50,000+ engineers think about security. That's a different kind of challenge entirely.
It requires leadership that people respect and trust. It requires clear communication about why the change matters. It requires willingness to make hard trade-offs and stick with decisions even when they're unpopular. It requires patience with the fact that cultural change takes years.
The fact that Nadella is giving Gallot direct reporting access and presumably considerable resources suggests he understands this. He's not asking for a technical fix. He's asking for cultural transformation. You don't get that from a technologist. You get it from a leader with credibility across the organization.

Looking Ahead: The Next Phase of Enterprise Software
We're entering a phase where enterprise software companies are going to compete increasingly on trust and security rather than features alone.
For the past decade, the competition was primarily about functionality and price. Who has the most features? Who's the cheapest? Those questions still matter, but they're becoming less differentiated.
What's increasingly differentiating is: Who can I trust with my data? Whose systems actually work when breached? Who's transparent about problems and fixes them quickly? These are becoming the questions that drive enterprise software decisions.
Microsoft's move is a recognition that the company can't win on features and price alone. Microsoft already has both. What Microsoft needs is trust. And trust doesn't come from press releases or marketing. It comes from consistent action over time.
Gallot's appointment is Microsoft saying: "Trust matters. We're going to prove we can be trustworthy. Here's the leadership and resources we're allocating to do it."
For enterprise customers, this is actually good news. It means the company is serious. For competitors, it's a warning that Microsoft is going to fight hard to rebuild position. For investors, it suggests Microsoft's board is making long-term strategic bets, not just reacting to incidents.

The Bottom Line: Why This Moment Matters
Hayete Gallot's return to Microsoft as head of security is significant because it represents a turning point.
Microsoft had two choices after the Cyber Safety Review Board report. Option one: make incremental improvements and hope people forget about the problems. Option two: fundamentally restructure how the company approaches security and bet that transformation can restore trust.
The Gallot appointment is Microsoft choosing option two. It's saying: "We're going to be different. It's going to take time and resources. But we're going to do it."
Whether this actually works depends on factors that go way beyond personnel decisions. It depends on whether the Secure Future Initiative is actually well-designed. It depends on whether Nadella's support remains constant when transformation gets hard. It depends on whether security culture change can actually happen at this scale.
But at least Microsoft is trying. That's actually significant. Most large organizations, when facing security criticism, make performative changes. Microsoft appears to be making substantive ones.
For the industry, for enterprise customers, and for Microsoft itself, the next 18 to 24 months will be crucial. Watch the metrics. Watch the organizational changes. Watch the transparency. That's where you'll see whether this transformation is real.

FAQ
What exactly is the Secure Future Initiative and what does it aim to accomplish?
The Secure Future Initiative is Microsoft's comprehensive security overhaul launched in response to major breaches and the Cyber Safety Review Board's 2024 report. The SFI focuses on integrating security into every stage of product development rather than treating it as a post-development review process. It aims to change Microsoft's security culture fundamentally, implement advanced threat detection systems, accelerate vulnerability patching, and ensure security considerations influence business decisions at all levels. The initiative includes investments in AI-powered security operations, early-stage security reviews for new products, and transparent communication about vulnerabilities and fixes.
Why did Hayete Gallot leave Google Cloud to return to Microsoft after just six months?
While the exact reasons weren't publicly disclosed, the most likely explanation is that Google Cloud's customer experience role didn't align with her skills or Microsoft's urgent need for a transformational security leader. Returning to Microsoft as EVP of security with direct CEO reporting is a significantly more powerful position. It's also possible that Microsoft made an attractive offer emphasizing her ability to lead a major transformation, combined with more significant equity incentives. Her return signals that both Gallot and Microsoft believed the security leadership opportunity was more compelling than the Google position.
What does Charlie Bell's move to engineering quality mean for Microsoft's security strategy?
Charlie Bell's transition from security leadership to an individual contributor role focused on engineering quality indicates a strategic shift in Microsoft's security approach. Bell was responsible for initial crisis management and stabilization during the breach response period. His move into technical individual contributor work suggests Microsoft is transitioning from crisis response to building fundamental engineering excellence. This allows Bell to focus on technical problems without organizational management responsibilities, while also signaling that Microsoft values deep technical expertise equal to leadership roles.
How long will it actually take for Microsoft to rebuild its security reputation?
Security culture transformation at Microsoft's scale typically requires three to five years minimum before meaningful improvements become measurable and trustworthy. However, rebuilding enterprise customer trust could take longer, perhaps five to seven years. The timeline depends on Microsoft's ability to implement the Secure Future Initiative effectively, maintain consistent executive support, demonstrate measurable security improvements, and avoid major incidents during the transformation period. Any significant breach during this period would substantially reset the timeline.
What specific improvements should enterprise customers expect to see from the Gallot appointment?
Enterprise customers should watch for faster patch release cycles, more transparent vulnerability disclosure including severity ratings and response timelines, improved security testing across products, better integration of security considerations into product design, reduced time from vulnerability discovery to patch availability, and clearer communication about security incidents and remediation efforts. Additionally, customers should expect improved security tools and features in Microsoft's platform offerings, enhanced threat detection capabilities, and more comprehensive security documentation and best practices guidance.
How does Microsoft's security transformation compare to competitors like AWS and Google Cloud?
AWS and Google Cloud haven't faced security criticisms as public or severe as Microsoft's, but all major cloud providers have experienced security incidents. AWS has built a strong reputation through transparency and has dedicated security service offerings. Google Cloud emphasizes its inherited security culture from Google's own infrastructure. Microsoft's difference is acknowledging systemic culture problems and committing to organizational restructuring to fix them, rather than maintaining that problems are isolated incidents. This approach is more honest but riskier, as failure to deliver on the transformation would be more visible.
What role will AI play in Microsoft's future security strategy?
AI will be central to Microsoft's future security approach, particularly in threat detection and automated response systems. The company is investing in machine learning systems that can identify anomalous behavior across Microsoft's infrastructure at massive scale, AI-assisted security analysis tools, and possibly AI-powered vulnerability discovery. However, securing AI systems themselves is an emerging challenge. Microsoft will need to develop frameworks for building trustworthy AI security tools while also protecting against AI-specific attack vectors. This is an area where the industry is still figuring out best practices.

Conclusion
The announcement that Hayete Gallot is returning to Microsoft as executive vice president of security is far more significant than a typical executive appointment. It represents a strategic decision by Microsoft's leadership and board that the company's security culture requires fundamental transformation, not incremental fixes.
Understanding why this matters requires looking beyond the headlines. Microsoft isn't just reshuffling executives. The company is signaling to enterprise customers, regulators, and competitors that security is now a board-level priority with executive-level authority and resources. The appointment of Gallot specifically, someone who understands both technical engineering and customer business dynamics, suggests Microsoft understands that security culture change requires leadership that can bridge organizational silos.
The Cyber Safety Review Board's 2024 report was a watershed moment. It forced Microsoft to acknowledge that its security culture was fundamentally inadequate. The company's response—launching the Secure Future Initiative and bringing in transformation leadership—suggests the company is taking the criticism seriously.
But acknowledgment and action are different things. Over the next 18 to 24 months, Microsoft needs to demonstrate measurable improvements in security metrics, visible organizational changes that embed security throughout the company, and customer testimony that trust is being rebuilt. The appointment is necessary but not sufficient. Execution is what actually matters.
For enterprise customers evaluating Microsoft, this is a moment to engage directly with Microsoft's security leadership. Document what improvements are promised. Track against actual delivery. Use this as an opportunity to push the company toward greater transparency and accountability.
For competitors, this is a reminder that trust and security are now primary competitive dimensions. The company that can credibly demonstrate trustworthiness will win enterprise contracts. For investors, this is a signal that Microsoft's board is making long-term strategic bets on reputation restoration rather than just financial optimization.
The enterprise software industry is at an inflection point. Companies can no longer compete primarily on features and price. They need to be genuinely trustworthy. Gallot's appointment represents Microsoft betting that trustworthiness can be rebuilt through serious, sustained effort. Whether that bet pays off depends entirely on execution. But at least the company is making the bet. That's a start.

Key Takeaways
- Hayete Gallot's return to Microsoft as EVP of security after six months at Google Cloud signals the company's serious commitment to security transformation, not just personnel shuffling
- The Cyber Safety Review Board's 2024 report concluded Microsoft's security culture was fundamentally inadequate, forcing the company to choose between incremental improvements or substantive transformation
- Microsoft's Secure Future Initiative focuses on embedding security from day one of product development rather than as a post-development review, requiring culture change across hundreds of thousands of engineers
- Charlie Bell's transition from security leadership to engineering quality indicates Microsoft's shift from crisis management to building fundamental engineering excellence and trustworthiness
- Enterprise customers should track specific metrics over 18-24 months including patch response time, transparency about vulnerabilities, organizational changes, and customer confidence to assess whether transformation is real
Related Articles
- Windows 11 Hits 1 Billion Users: What This Milestone Means [2025]
- Palantir: The Enterprise Software Giant Redefining Growth [2025]
- AI Agents & Access Control: Why Traditional Security Fails [2025]
- Vercel v0: Solving the 90% Problem with AI-Generated Code in Production [2025]
- Enterprise AI Race: Multi-Model Strategy Reshapes Competition [2025]
- ShinyHunters SSO Scams: How Vishing & Phishing Attacks Work [2025]
![Microsoft's Security Leadership Shift: What Gallot's Return Means [2025]](https://tryrunable.com/blog/microsoft-s-security-leadership-shift-what-gallot-s-return-m/image-1-1770226597871.jpg)



