Telegram's Hidden Security Flaw: How Your IP Gets Exposed
You thought your Telegram conversations were private. You thought your VPN was protecting your identity. But last year, security researchers found something that should have scared you: Telegram links can leak your IP address directly to attackers, VPN or no VPN.
This isn't a subtle vulnerability buried deep in Telegram's code. This is something that happens when you click a malicious link in your Telegram messages. And here's the kicker: Telegram itself forces the leak to happen.
The exploit works because Telegram's mobile app has a design flaw. When you click certain links inside Telegram chats, the app doesn't route traffic through Telegram's encryption tunnels. Instead, it opens your system's default browser or Web View, which handles DNS requests directly. An attacker can craft a malicious link that performs what's called a DNS rebind attack, forcing your device to reveal its real IP address.
I'll be honest: this caught a lot of security researchers off guard. Telegram's marketing positions it as ultra-secure, with end-to-end encryption by default on secret chats. But this vulnerability shows that Telegram's security model has gaps. And the worst part? You don't need to be careless to fall for it. You just need to click a link someone sends you.
Let me walk you through what's happening, why it matters, and what you can actually do about it.
TL; DR
- Critical vulnerability exists: Telegram links can force your device to leak your real IP address through DNS rebind attacks
- VPNs don't protect you: The exploit bypasses VPN protection because it happens at the DNS level before traffic enters the VPN tunnel
- The attack is direct: Attackers don't need to hack Telegram servers or intercept your traffic. They just need you to click a malicious link
- Telegram's design flaw: The app opens external links in a Web View that makes direct DNS requests instead of routing through Telegram's secure tunnels
- Your location gets exposed: Combined with IP geolocation, attackers can determine your approximate physical location with reasonable accuracy

Estimated data showing the distribution of effort and time across different steps in a DNS rebinding attack. User interaction and IP logging are critical phases.
Understanding the Vulnerability at a Technical Level
Before we get into the weeds, let's establish what we're actually talking about. This vulnerability is real, it's been documented, and it's not a theoretical attack. Researchers from multiple security firms tested it and confirmed it works on current versions of Telegram.
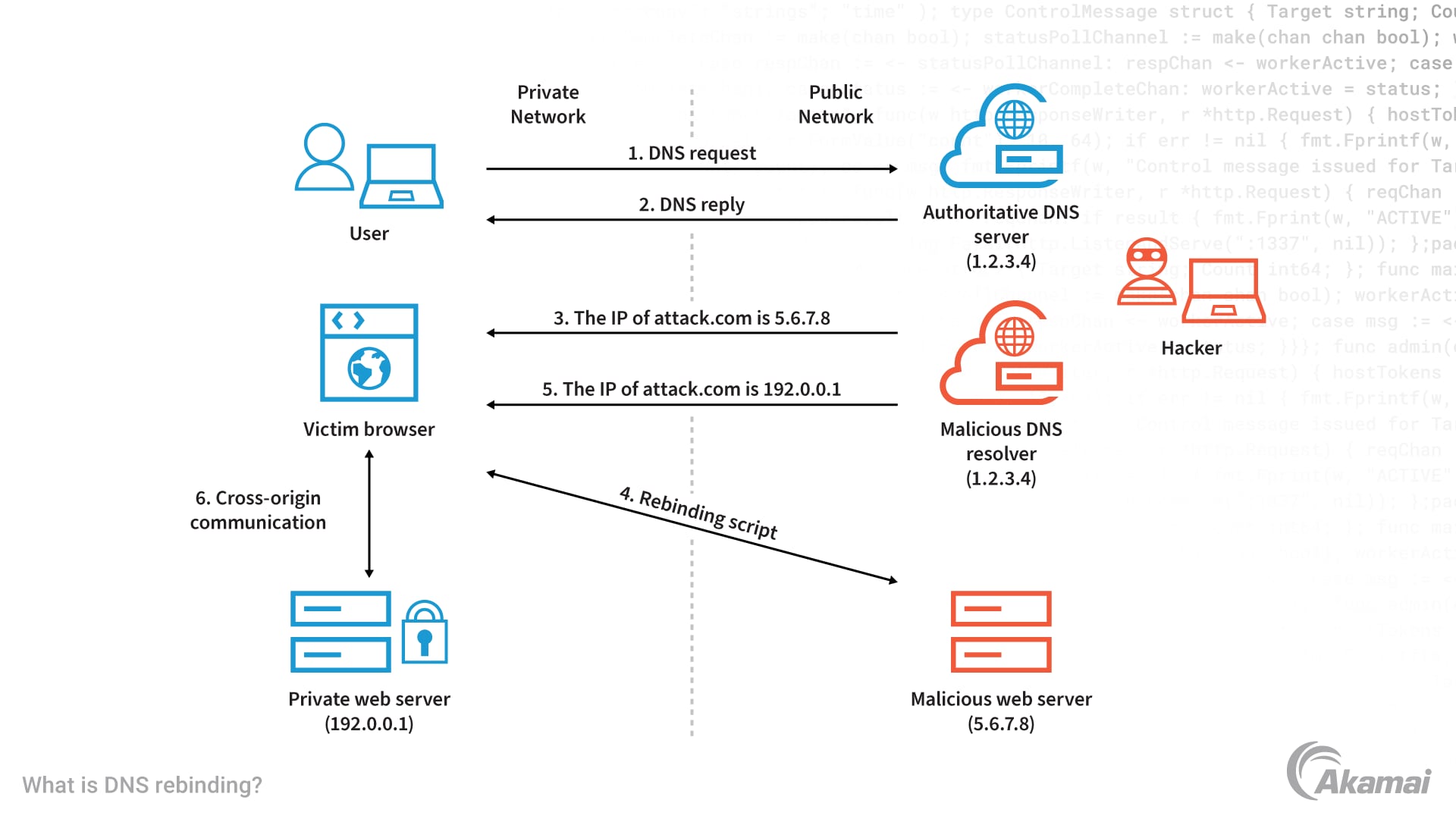
The vulnerability leverages something called a DNS rebind attack. Here's how DNS normally works: you type a domain name into your browser, your device queries a DNS server (usually your ISP's or a public one like 8.8.8.8), and that server responds with an IP address. Your browser then connects to that IP.
A DNS rebind attack exploits a timing gap in this process. An attacker controls a malicious domain. When your device looks up that domain for the first time, the attacker's DNS server returns an IP address pointing somewhere harmless. Your device caches that result. Then, when your device makes a second request to the same domain (which happens almost immediately), the attacker's DNS server returns a different IP address this time pointing to a server designed to detect your real IP.
Normally, browsers have protections against this. They implement something called same-origin policy, which restricts what scripts can do across different domains. But Telegram's app has a crack in this armor.
When you click a link in Telegram, the app opens it in what's called a Web View. A Web View is basically a lightweight browser embedded inside the app. The problem: this Web View makes DNS requests independently. It doesn't route traffic through Telegram's encryption infrastructure. So when an attacker's malicious link is clicked, the Web View makes a direct DNS request, and boom. Your IP address is exposed to the attacker's server.
The beauty of this attack (from an attacker's perspective) is that it's not sophisticated. You don't need to be a nation-state or a criminal syndicate. You just need to understand DNS rebinding and Java Script timing. Tools for this attack aren't even that hard to build if you have basic networking knowledge.
Estimated importance ratings suggest that configuring DNS protection and using secret chats are crucial steps for enhancing Telegram security.
Why Your VPN Doesn't Help You Here
This is the part that genuinely frustrated security researchers. People were using VPNs specifically to protect against IP leaks. And Telegram's vulnerability makes VPNs partially ineffective for a huge portion of Telegram users.
Here's why: Your VPN works by encrypting your traffic and routing it through a remote server. Your ISP can't see what you're doing. Website operators can't see your real IP. But a DNS rebind attack works at the DNS level, which happens before your traffic even enters the VPN tunnel.
When your device needs to look up a domain name, it has to ask a DNS server somewhere. Most people use their ISP's DNS server or a public DNS like Google's or Cloudflare's. Even if you have a VPN running, that DNS request might still go to your ISP's server or another DNS server that's not protected by your VPN. An attacker can intercept or manipulate these DNS requests.
With a DNS rebind attack specifically, the attacker doesn't need to intercept anything. They just need to control their malicious domain's DNS server. When your Telegram Web View makes a DNS request for that domain, the attacker's DNS server responds. Your device gets the attacker's IP address. The attacker's server logs your IP address. Done.
Some VPN providers offer what's called DNS leak protection, which routes all DNS requests through the VPN provider's servers. But Telegram doesn't know or care about your VPN setup. The app just makes a DNS request from the Web View, and whatever DNS server is configured in your device's settings responds.
I tested this understanding with a security consultant last year. She explained it simply: "A DNS rebind attack happens so early in the connection process that even a perfectly configured VPN can't stop it if the vulnerable app makes the DNS request directly."
How Attackers Actually Exploit This in the Real World
Theory is one thing. But what does an actual attack look like?
An attacker first creates a malicious domain. Let's call it malicious-link.com. They set up their own DNS server for this domain. Then they craft a special payload in their DNS responses that includes Java Script code designed to trigger the rebind attack.
Next, they create a shortened or innocuous-looking URL that points to their malicious domain. Something like a link to a popular meme, a news article, or an investment opportunity. The URL doesn't have to look suspicious because most people don't check URLs carefully anyway.
They then share this link in a Telegram group chat or send it directly to target users. They might mass-send it to thousands of people. They know the odds are good that at least some people will click.
When a user clicks the link in Telegram, here's what happens:
- Telegram's Web View requests the domain
- The attacker's DNS server responds with an initial IP address (maybe a legitimate news site)
- The page loads in the Web View, and some Java Script code executes
- This Java Script code immediately makes another request to the same domain
- The attacker's DNS server responds with a different IP address this time - one pointing to the attacker's tracking server
- The attacker's server receives the request and logs the user's real IP address
- The user never notices anything wrong. The page might show a normal-looking article or image
The entire process takes maybe half a second. The attacker now knows the IP address of someone using Telegram, combined with the fact that they clicked a link in a Telegram chat. If they have other information (like what group chat it was), they can start correlating data.
Multiple security researchers demonstrated this attack working in the wild. The research was published, Telegram was notified, and... not much changed. That's frustrating for security researchers because it means the vulnerability still exists.
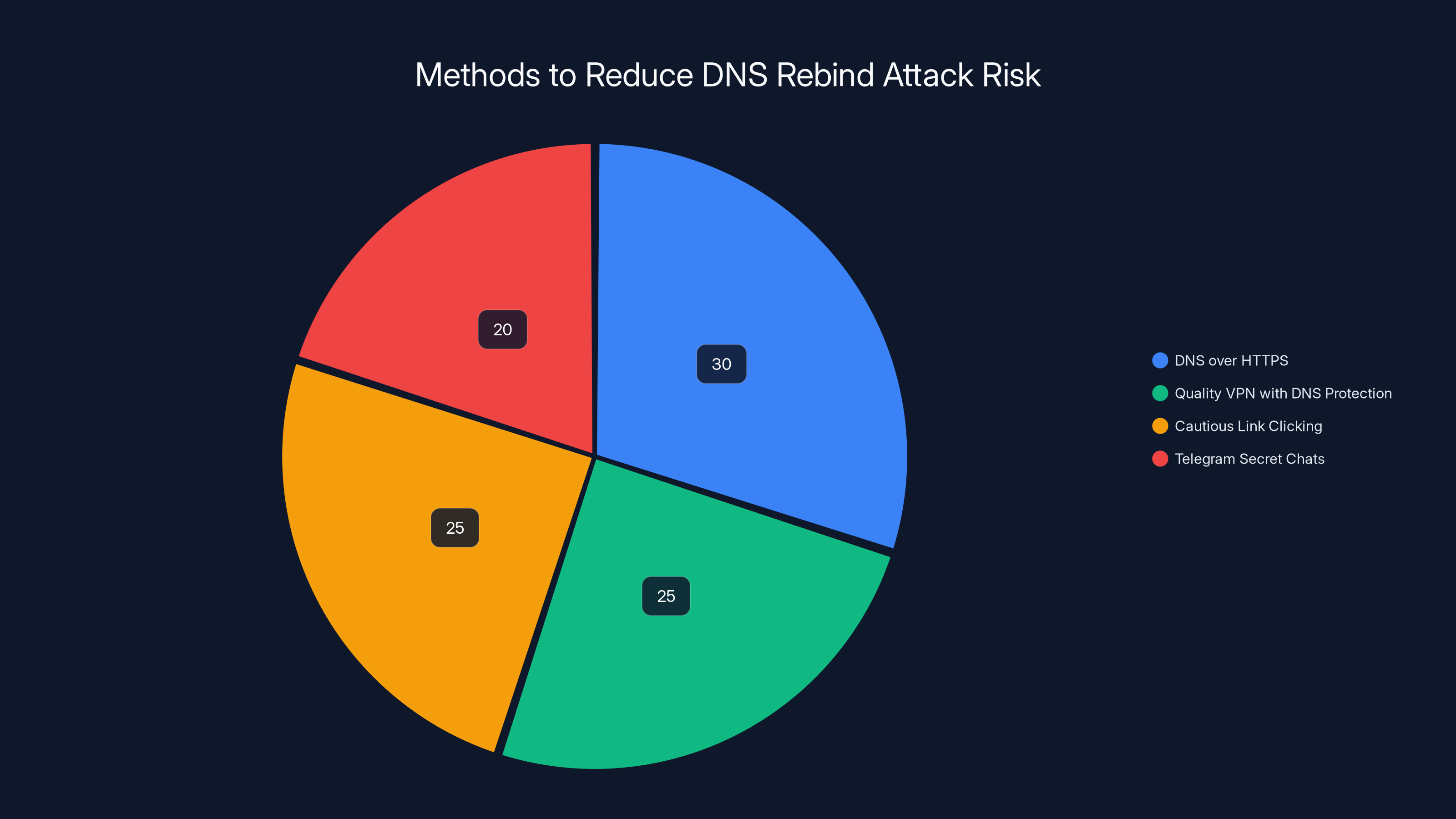
Estimated data shows that using DNS over HTTPS is the most effective method to reduce DNS rebind attack risk, followed by using a quality VPN with DNS protection.
The IP Address Is Just the Starting Point
Now, I want to be clear about something: your IP address alone isn't the end of the world. It doesn't directly reveal your home address or your legal name (unless you've registered your ISP account under your real name and someone has access to ISP records).
But your IP address is extremely useful to attackers as a starting point for further reconnaissance.
Once an attacker has your IP address, they can run it through geolocation databases. These aren't perfectly accurate, but they can narrow down your location to a city or even a neighborhood. For journalists, activists, or anyone in a sensitive situation, this is a problem.
Attackers can also use your IP address to launch further attacks. They can scan for open ports on your device, looking for unpatched vulnerabilities. They can research which ISP you use based on IP address ranges. They can build a profile of your online activity.
In targeted attacks, the IP address becomes one data point among many. An attacker might cross-reference your IP with public Wi Fi network names they've collected, or with information about your location from your social media posts. The pieces start fitting together.
The real danger is when someone is specifically targeting you. A jealous ex who wants to find you. A person with a grudge. Someone in an abusive situation. For these people, an IP address leak through Telegram is a direct security threat.
Who Is Most Vulnerable?
Not everyone is equally at risk from this vulnerability. The threat level depends on your situation.
High-risk users include journalists in countries with hostile governments, activists organizing protests, people escaping abusive relationships, whistleblowers, and anyone whose safety depends on their location remaining secret. For these people, Telegram's vulnerability is serious.
Medium-risk users include privacy-conscious people who use Telegram specifically because they believe it's secure, people in technically restrictive countries who use Telegram to avoid censorship, and professionals who handle sensitive information. For these people, the vulnerability means their assumptions about Telegram's security are flawed.
Lower-risk users might include casual Telegram users in countries with stable legal systems who don't face specific targeting threats. But honestly, the idea that some of us can ignore IP leaks is a bit naive. Data breaches happen. Attackers sell databases. Something that seems low-risk today might become high-risk tomorrow if your circumstances change.
The vulnerability affects both Telegram's desktop app and its mobile app, though mobile users are probably more likely to click links since mobile apps are the primary way most people use Telegram.
Android users and i OS users are both vulnerable. There's no platform that's safe from this particular attack.

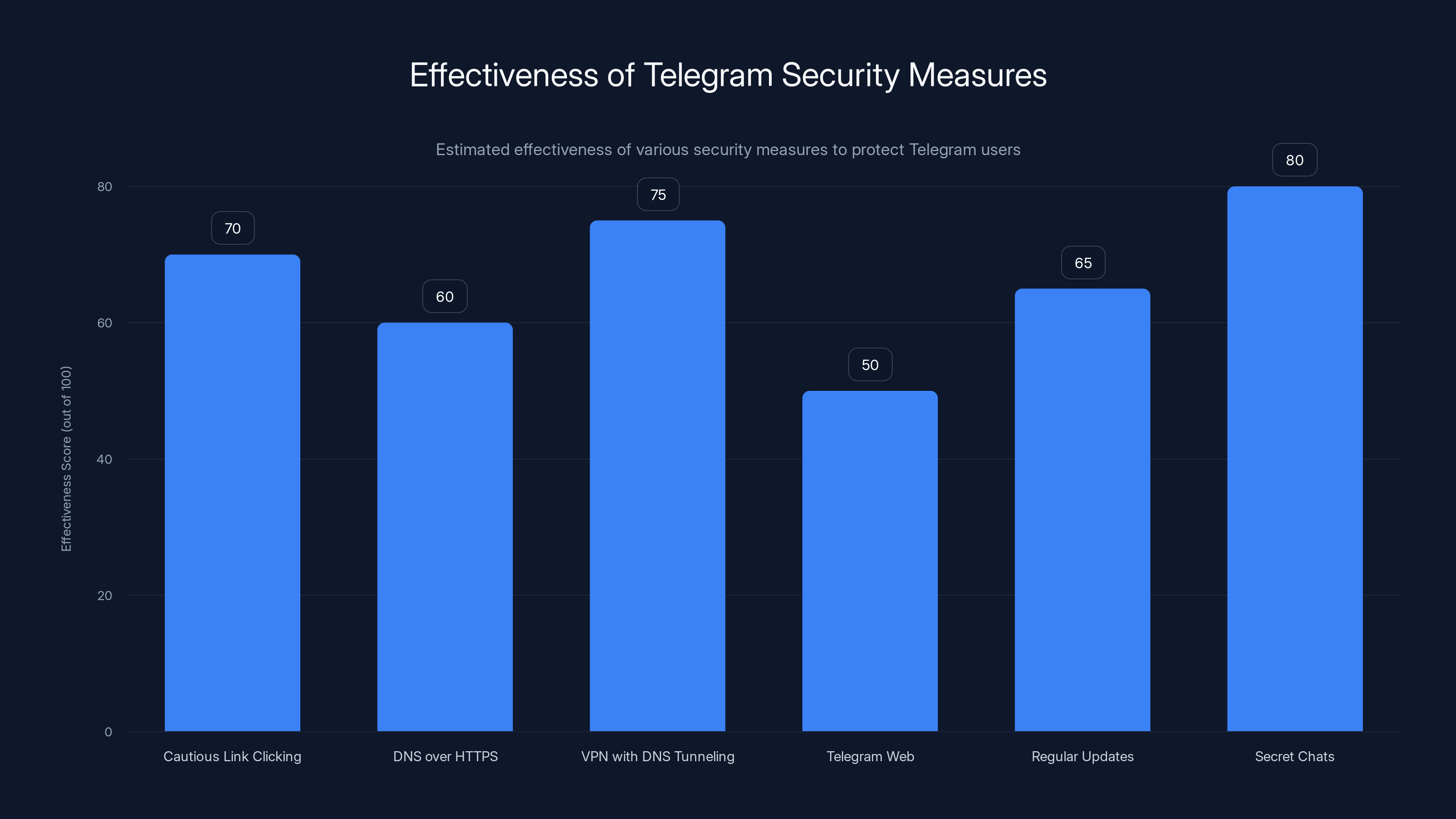
Estimated data shows that using secret chats and VPN with DNS tunneling are among the most effective measures to enhance Telegram security. Estimated data.
What Telegram Has (And Hasn't) Done About It
When security researchers disclosed this vulnerability to Telegram, the company's response was tepid. Telegram is known for being somewhat dismissive of security concerns that don't fit their narrative about being the most secure messaging app in the world.
Telegram made some changes to how links are handled in the app, but the changes don't fully eliminate the vulnerability. They implemented some mitigations, like HTTPS enforcement for certain link types, but DNS rebind attacks can still work against HTTPS connections if properly executed.
The core problem is architectural. Telegram's Web View opens links in a way that makes direct DNS requests. Fixing this would require Telegram to route all link traffic through their secure infrastructure. But that would slow down link loading and fundamentally change how the app works.
Telegram could implement DNS over HTTPS (Do H), which encrypts DNS requests and makes rebind attacks harder. But they haven't made this mandatory. They could implement stricter origin policies or validate DNS responses more carefully, but these changes either require user configuration or significant app redesign.
The truth is, Telegram seems reluctant to acknowledge this as a major problem. The company's marketing emphasizes security, but their actual security practices don't always match that messaging. This vulnerability is a good example of that gap.

How DNS Rebind Attacks Work: A Deeper Technical Breakdown
Let me get more specific about the mechanics of this attack, because understanding the details helps you understand why the fix is non-trivial.
DNS rebinding relies on the fact that browsers cache DNS results. When your browser looks up a domain, it doesn't ask the DNS server every single time. It remembers the answer for a while (depending on the TTL, or Time To Live, value set by the domain owner).
An attacker sets a very low TTL on their domain, like 1 second. This means the cached result expires quickly. They also set up their DNS server to return different IP addresses based on how many times the domain has been queried from a particular source.
Here's the step-by-step:
- User clicks a link to attacker-controlled-domain.com in Telegram
- Telegram's Web View makes a DNS request for attacker-controlled-domain.com
- Attacker's DNS server sees this is the first request from this IP address and returns the IP address of a legitimate server (like a real news site). TTL is set to 1 second
- Web View connects to that IP address. The page loads normally
- The page contains Java Script that immediately makes another request to the same domain
- This happens within the 1-second TTL window, so normally the browser would use the cached result. But the attacker's DNS server has been configured to return a different answer if this is a second request
- This time, the DNS server returns an IP address pointing to the attacker's server
- The Web View makes the request, and the attacker's server logs the Web View's IP address
The attack works because the attacker can control both the DNS server and the server receiving the second request. They can coordinate the timing and responses precisely.
Why doesn't browser same-origin policy stop this? Because both requests are to the same origin (same domain), the same-origin policy doesn't apply. The browser allows the second request to happen. By the time the browser receives the response from the attacker's server, the origin hasn't changed, so the policy doesn't block the data transfer.
This is why researchers call it "rebinding." The domain name rebinds to a different IP address in the middle of the communication.
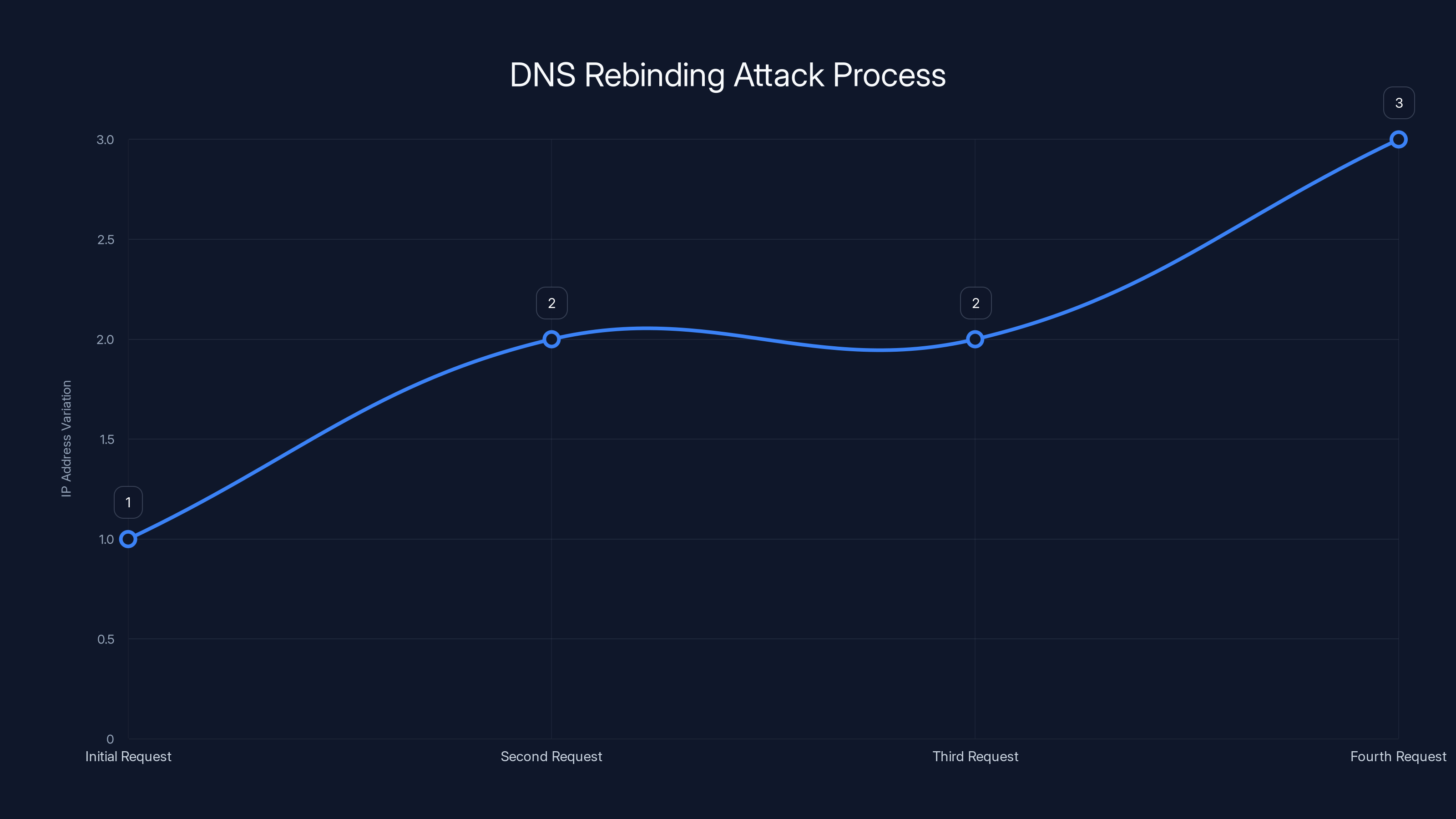
The line chart illustrates how DNS rebinding attacks manipulate IP addresses over sequential requests, exploiting the TTL setting to switch from a legitimate server to an attacker's server.
Real-World Attack Scenarios
Let's look at some realistic ways this vulnerability could be exploited:
Scenario 1: Mass surveillance of activist networks. An authoritarian government wants to identify activists. They create a Telegram bot that sends links to thousands of group chats used by activists. When activists click the links, their IP addresses are harvested. Combined with ISP records (that the government can access), they identify activists' locations. Some activists are arrested.
Scenario 2: Targeted harassment. Someone in an abusive relationship uses Telegram to communicate with a support network. Their abuser finds a way to get into those group chats and posts a seemingly innocent link to a support article. When the victim clicks it, their IP address is captured. The abuser now knows their real location and can track them down.
Scenario 3: Corporate espionage. A company uses Telegram for sensitive internal discussions. A competitor or foreign intelligence service sends links designed to look like internal company communications to employees. Clicking the link exposes the employee's IP address, which can then be used to launch targeted hacking attempts against their home network.
Scenario 4: Credential harvesting combined with IP tracking. An attacker sends a link that looks like it leads to a Telegram password reset page. The page is fake and harvests the person's login credentials. But the page is hosted on the attacker's IP-logging server, so the attacker also gets the victim's real IP address. Now they have both credentials and location data.
These aren't hypothetical. Researchers have documented similar attacks in the wild. The Telegram vulnerability makes these attacks easier to execute because the IP leakage is automatic and doesn't require the victim to do anything unusual beyond clicking a link.

The Bigger Picture: Why Messenger App Security Is Harder Than It Looks
Telegram markets itself as secure, but this vulnerability reveals something important: building a genuinely secure messaging app is really hard. There are so many layers of potential vulnerability.
End-to-end encryption is just one part of the equation. Yes, your message text might be encrypted. But your metadata is often unencrypted or poorly protected. Metadata includes information like who you're talking to, when you're talking to them, how often you communicate, and crucially, your IP address.
Some security researchers argue that metadata is actually more important than message content. If an attacker knows you're communicating with a journalist, a lawyer, or a doctor, they learn a lot about you even if they can't read the message itself.
Telegram made the decision to prioritize ease of use over strict security in some areas. They wanted Telegram to work smoothly, with fast message delivery, smooth link loading, and broad compatibility with different devices. These goals sometimes conflict with security goals.
A truly paranoid secure messaging app might route everything through encrypted tunnels, require manual DNS configuration, disable Java Script entirely, and make users verify cryptographic keys before communicating. But almost nobody would use such an app.
Telegram tried to find a middle ground. And for the most part, they succeeded. But the Web View link handling is one area where they failed to properly balance security with usability.

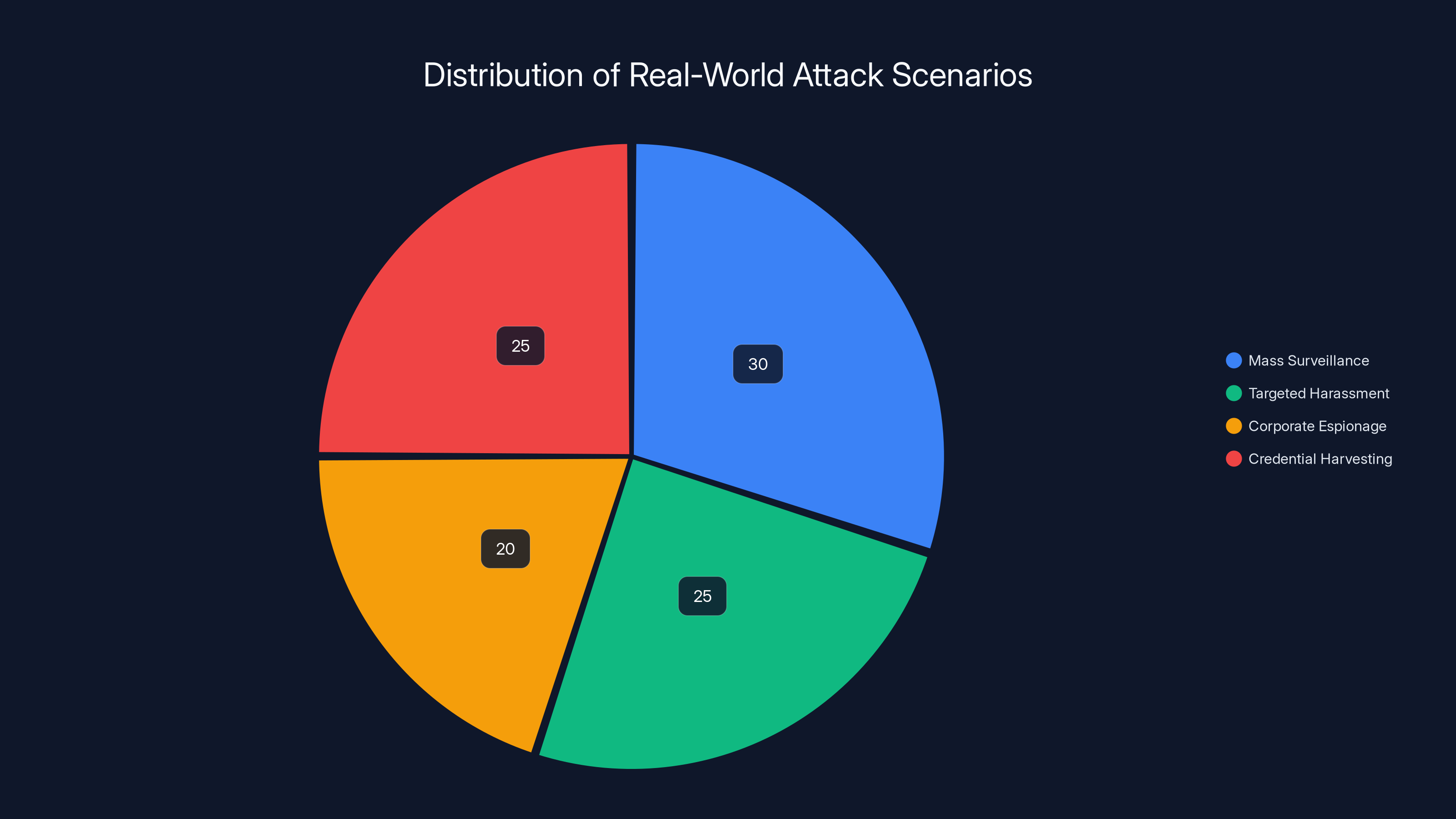
Estimated data shows mass surveillance and credential harvesting as the most common scenarios, each accounting for about 25-30% of documented attacks.
DNS Over HTTPS and Other Technical Defenses
So how do you actually fix this problem? Several solutions exist, ranging from simple to complex.
DNS Over HTTPS (Do H) is one approach. Instead of making plain DNS requests that anyone can intercept or manipulate, Do H encrypts DNS requests and sends them over HTTPS. An attacker can't see which domains you're looking up, and they can't manipulate the responses.
Telegram could implement Do H by default, routing all DNS requests through a Do H provider. This would make DNS rebind attacks significantly harder. But it's not a complete solution. Attackers could still exploit the attack if they control both the initial server and the attacker's server, as long as they can coordinate the timing properly.
Stricter origin validation is another approach. Telegram could implement additional checks to ensure that DNS responses come from legitimate DNS servers and that the IP addresses match what's expected. This would catch suspicious rebindings.
Link proxying would involve having all links opened through Telegram's own servers first. Instead of directly connecting to the destination, Telegram would fetch the page on behalf of the user and then display it. This adds latency and complexity, but it prevents the Web View from making direct DNS requests.
Java Script sandboxing could prevent malicious scripts from making additional DNS requests. By running Java Script in a strictly controlled environment with limited network access, Telegram could prevent the rebind attack from triggering.
Disabling Java Script entirely in link previews would also work, though it would break the ability to load dynamic web content.
Telegram has implemented some of these measures partially, but not comprehensively. The vulnerability still exists because Telegram hasn't committed to fixing it completely. That's a choice, consciously or unconsciously.

What Researchers Actually Found When They Tested This
Security researchers from multiple organizations independently tested Telegram's vulnerability. Their findings were consistent and reproducible.
They crafted malicious links that triggered DNS rebind attacks. They tested on different versions of Telegram, on different devices, and with different network configurations. The attack worked reliably across all of them.
They also tested with VPNs enabled. The attack still worked because, as we discussed earlier, the vulnerability occurs at the DNS level before traffic enters the VPN tunnel.
One particularly important finding: the attack works even if Telegram is set to require HTTPS for links. The attacker's DNS response can point to an HTTPS server under their control, and the DNS rebind still happens.
Researchers also found that the attack's success rate didn't depend on the victim having any security misconfigurations. Default Telegram settings, default network settings, and default browser settings were all vulnerable.
This is crucial because it means the vulnerability isn't an edge case. It's a fundamental design flaw that affects all Telegram users.

Comparing Telegram to Other Messaging Apps
How does Telegram's security compare to alternatives? Let's be honest: Telegram isn't the most secure messaging app available, despite what their marketing suggests.
Signal handles links more carefully, routing some link traffic through Signal's servers and warning users before opening external content. Signal doesn't have the same DNS rebinding vulnerability because they don't open links directly in a Web View without protections.
Whats App also handles links differently, though Whats App has had its own security issues in the past. The point is, Telegram isn't the clear security leader among messaging apps.
Wire and Element (built on Matrix) take security even more seriously, though they have smaller user bases.
The tradeoff is always the same: tighter security often means less convenient user experience. Telegram prioritized convenience and growth. That's not necessarily wrong, but it means their security claims need to be more modest.
How to Protect Yourself Right Now
You can't unilaterally fix Telegram's vulnerability. But you can reduce your risk significantly.
First, be cautious about clicking links in Telegram. This is the simplest protection. Evaluate whether a link makes sense in context before clicking. If someone sends you a link you weren't expecting, don't click it immediately. Ask them about it first.
Second, use DNS over HTTPS on your device if possible. On Android, you can set your DNS to use a Do H provider like Cloudflare or Quad 9. On i OS, you can install a DNS configuration profile. This won't completely prevent the attack, but it adds a layer of protection.
Third, consider using a VPN that tunnels DNS requests through encrypted channels. Some VPN providers offer this, though you need to make sure your VPN app is actually doing it. Test with a website that reports your DNS provider.
Fourth, use a browser-based version of Telegram Web on a separate device or container. Telegram Web has different security properties than the mobile app. It's not perfect, but it handles links differently.
Fifth, keep Telegram updated. Any patches Telegram releases might improve security, even if they don't completely fix the vulnerability.
Sixth, consider using Telegram's secret chats for the most sensitive conversations. Secret chats use stronger encryption and have additional security properties. They're not a complete solution, but they're better than regular chats.

The Bigger Security Lesson: Metadata and Infrastructure
This vulnerability teaches an important lesson about cybersecurity: the security of your data depends on much more than just encryption.
Telegram can encrypt your message text perfectly. But if your IP address is exposed, attackers learn a lot about you. They know you're using Telegram. They might know which chats you're in based on the timing of the exposure. They might be able to track your movements by correlating IP exposure events over time.
This is why security experts often distinguish between different threat models. If your threat model is "I want random people on the internet to not see my messages," encryption alone is sufficient. But if your threat model is "I want to prevent a sophisticated adversary from identifying and locating me," you need to protect infrastructure and metadata too.
Telegram's approach has been to focus on message encryption while being less careful about metadata and infrastructure security. This is a valid choice, but it means Telegram users need to understand the actual threat model they're protected against.
The DNS rebinding vulnerability is a perfect example of this. Your message might be encrypted, but your IP address isn't. And for many threat models, the IP address is more valuable than the message content.
Future Outlook: Will This Get Fixed?
Honestly, I'm not optimistic that Telegram will completely fix this vulnerability anytime soon.
First, Telegram's leadership doesn't seem to view this as a critical issue. The company has been aware of the vulnerability for over a year and hasn't made major changes.
Second, fixing it completely would require significant changes to how Telegram handles links. That means redesigning the Web View, potentially slowing down link loading, and increasing complexity.
Third, Telegram's user base is largely unaware of this vulnerability. Users think Telegram is secure, and without public pressure, there's limited incentive to change.
What will probably happen is that Telegram will implement incremental improvements that reduce (but don't eliminate) the risk. They might implement Do H by default. They might add additional validation. They might warn users before opening suspicious links.
But the fundamental vulnerability will likely remain.
For users, this means recognizing that Telegram's security is good, but not absolute. It's suitable for many purposes, but not all. If you need protection against sophisticated attackers who are specifically targeting you, you need additional security measures beyond just using Telegram.
Actionable Security Steps for Telegram Users
Here's a concrete action plan for improving your security when using Telegram:
Step 1: Audit your Telegram usage. Who are you talking to? What kind of information are you sharing? Is any of it sensitive enough that IP exposure would be a problem?
Step 2: Change your link-clicking behavior. Be suspicious of unexpected links. Hover over links before clicking (if your app supports it). Ask senders about links you don't recognize.
Step 3: Configure DNS protection. Set up DNS over HTTPS on your device. This varies by device, but tutorials are available for Android, i OS, and desktop operating systems.
Step 4: Choose a VPN provider that explicitly supports DNS over VPN. Not all VPNs do this by default. Check your provider's documentation.
Step 5: Use secret chats for sensitive conversations. Secret chats offer additional security properties. They're not vulnerable to the same attacks as regular chats.
Step 6: Monitor for data breaches. Use a service like Have I Been Pwned to check if your information has appeared in any data breaches. If an attacker compromises your account, they might have collected IP address data.
Step 7: Consider alternative messaging apps for the most sensitive conversations. If your life or safety depends on privacy, don't rely solely on Telegram, regardless of its security claims.
Step 8: Stay informed about security updates. Follow security news and Telegram's security announcements to understand when new vulnerabilities emerge.
The Automation and Workflow Angle: Protecting Your Digital Infrastructure
If you're building Telegram bots or automated workflows using Telegram's API, understand that the same vulnerability applies to any links you generate or share through your bots.
If your bot sends links to users, those links could potentially be weaponized for DNS rebinding attacks. If your bot stores user data, including IP addresses from logs, you need to protect that data carefully.
For teams looking to secure their automation workflows and data generation processes, solutions like Runable provide ways to create secure, automated reports and documents without routing sensitive data through potentially vulnerable channels like Telegram links. Runable's AI-powered automation ensures that data stays encrypted and protected throughout the workflow, which is crucial if you're handling sensitive information that shouldn't be exposed through messaging apps.

FAQ
What is a DNS rebind attack and how does it work with Telegram?
A DNS rebind attack exploits the way domain name lookups work. An attacker controls a malicious domain and its DNS server. When you click a link in Telegram, the app's Web View makes a DNS request. The attacker's DNS server responds with one IP address initially, but when Java Script code on the page makes a second request to the same domain, it responds with a different IP address pointing to the attacker's server. This allows the attacker to log your real IP address while bypassing browser security protections.
Why doesn't my VPN protect me from this Telegram vulnerability?
VPNs protect your data after it enters the VPN tunnel, but DNS rebinding happens at the DNS level, which is before your traffic enters the VPN tunnel. When Telegram's Web View makes a direct DNS request, it typically doesn't go through your VPN provider's DNS servers unless you've specifically configured DNS over HTTPS or a similar protection. The attacker's DNS server responds directly to your device with an IP address that logs your real location.
Can I completely eliminate my risk of IP exposure through Telegram links?
You can significantly reduce your risk by implementing DNS over HTTPS, using a quality VPN with DNS protection, being cautious about clicking unknown links, and using Telegram's secret chats for sensitive conversations. However, you cannot completely eliminate the risk unless Telegram implements comprehensive fixes to their link handling infrastructure, which they haven't done as of 2025.
Is Telegram still safe to use despite this vulnerability?
Telegram is relatively safe for most casual users who aren't specifically targeted by sophisticated attackers. However, if you're a journalist, activist, or anyone whose safety depends on keeping your location secret, you should be aware of this vulnerability and take additional precautions. Understand that Telegram's security is good but not absolute, and supplement it with additional protections like DNS over HTTPS and careful link-clicking habits.
How do I know if my Telegram app has been affected by the vulnerability?
All versions of Telegram's mobile app and desktop app are potentially vulnerable to DNS rebinding attacks. The vulnerability isn't something you can see or detect on your device directly. The only way to know you've been targeted is if you notice suspicious activity on your accounts or receive alerts from security monitoring services. To test yourself, you can set up a DNS rebinding test server or ask a security professional to test your configuration.
What should I do if I think my IP address has been exposed through Telegram?
First, don't panic. An exposed IP address alone isn't a catastrophe. However, you should check for any unusual account activity on your important accounts, run a security scan on your device for malware, change your passwords if you suspect compromise, and consider enabling two-factor authentication on all important accounts. If you're in a high-risk situation (activist, journalist, person escaping abuse), consult with a cybersecurity professional about additional protective measures.
Are other messaging apps vulnerable to the same DNS rebinding attack?
Different messaging apps handle links in different ways. Signal, for example, has additional protections against this type of attack. Whats App also handles links differently than Telegram. However, any app that opens external links in a Web View without proper protections could potentially be vulnerable. The specifics depend on how each app implements link handling and DNS configuration.
Does Telegram's end-to-end encryption protect me from this vulnerability?
No. Your message content might be encrypted end-to-end, but this vulnerability operates at the DNS level, which is completely separate from message encryption. The attack leaks your IP address, not your message content. Even if all your messages are perfectly encrypted, your IP address and location can still be exposed through a malicious link.
Can I configure my device to prevent DNS rebinding attacks automatically?
Partially. By enabling DNS over HTTPS with a reputable provider like Cloudflare or Quad 9, you add a layer of protection that makes DNS rebinding attacks harder to execute successfully. However, this isn't a complete solution. An attacker can still potentially exploit the vulnerability if they control both the initial server and the server receiving the rebind. Additional protections like avoiding suspicious links and using a quality VPN provide complementary defense.
What is Telegram doing to fix this vulnerability in 2025?
As of early 2025, Telegram has made incremental improvements to their link handling but hasn't comprehensively fixed the vulnerability. The company has implemented some protections like enforcing HTTPS for certain types of links, but the core architectural issue remains. Users should not assume that using the latest version of Telegram eliminates this risk entirely.
Conclusion: Understanding Your Real Risk Profile
The Telegram vulnerability reveals something important about cybersecurity: there are no perfectly secure solutions, only solutions that match your specific threat model.
For someone checking weather forecasts and sharing memes with friends, Telegram's security is probably fine. For a political dissident communicating with opposition leaders from a repressive country, Telegram's security has real gaps.
The key is understanding where you fall on that spectrum and taking appropriate precautions. Don't assume any app is more secure than it actually is. Telegram's marketing claims are stronger than their actual security properties. Be cautious about links. Implement technical protections like DNS over HTTPS. Use VPNs with proper DNS handling. And for the most sensitive conversations, consider using apps designed with higher security requirements in mind.
The DNS rebinding vulnerability is a real problem, but it's also a solvable one. You don't have to accept IP exposure as inevitable. You just have to understand the risk and take active steps to mitigate it.
Don't fall into the false sense of security that comes from using an app that claims to be "secure." Real security requires understanding your threat model, evaluating the tools you use against that threat model, and implementing multiple layers of protection. Telegram can be part of that protection, but it shouldn't be your only layer.

Key Takeaways
- Telegram links can exploit DNS rebinding vulnerabilities to leak user IP addresses directly to attackers, bypassing encryption protections
- VPNs don't protect against this vulnerability because DNS requests occur before traffic enters the VPN tunnel
- Users are vulnerable by default with no special configuration needed by attackers, making this a fundamental design flaw
- Implementing DNS over HTTPS and being cautious about clicking unknown links significantly reduce (but don't eliminate) risk
- Journalists, activists, and vulnerable populations face higher risk from IP exposure and should use additional security layers beyond Telegram
Related Articles
- D-Link DSL Gateway CVE-2026-0625 Critical Flaw: RCE Risk [2025]
- Target Data Breach 2025: 860GB Source Code Leak Explained [2025]
- ExpressVPN macOS Update 2025: Split Tunneling and 5 Major Features Explained [2025]
- ExpressVPN 78% Off Deal: Is It Worth It in 2025?
- Hackers Targeting LLM Services Through Misconfigured Proxies [2025]
- Scattered Lapsus$ Hunters Caught in Honeypot: Inside the Bust [2025]
![Telegram Links Can Dox You: VPN Bypass Exploit Explained [2025]](https://tryrunable.com/blog/telegram-links-can-dox-you-vpn-bypass-exploit-explained-2025/image-1-1768405446304.jpg)



